An Efficient Cluster-Based Mutual Authentication and Key Update Protocol for Secure Internet of Vehicles in 5G Sensor Networks
Abstract
1. Introduction
2. Related Work
3. Preliminaries
3.1. One-Way Hash Function
3.2. Physical Unclonable Function
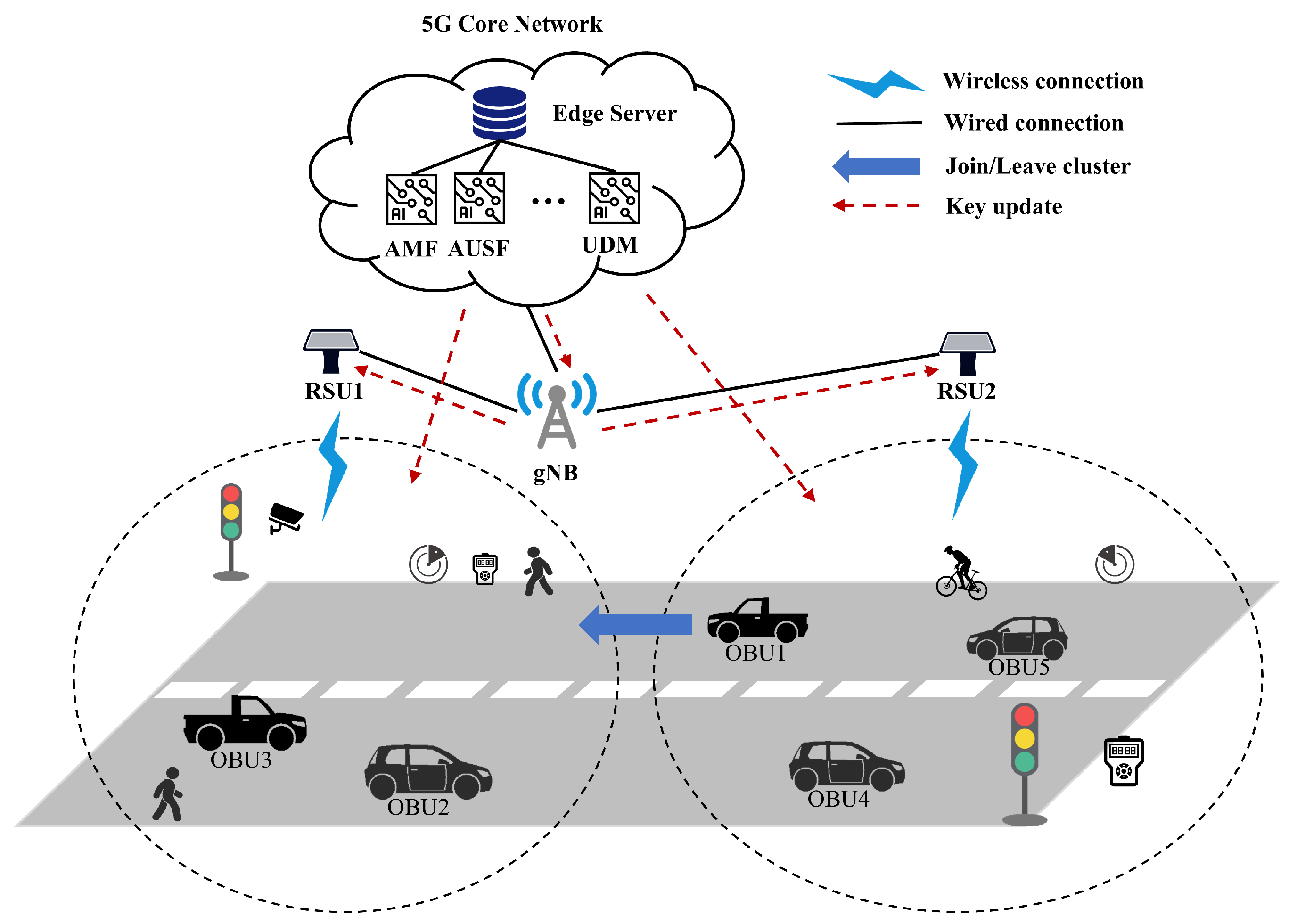
4. System Model
4.1. Authentication Model
4.2. Threat Model
- (1)
- The adversary has the ability to generate random numbers and timestamps;
- (2)
- The adversary may arbitrarily intercept, alter, delete, and relocate messages transmitted in the public channel;
- (3)
- The adversary may attempt to impersonate and track nodes;
- (4)
- The adversary may act as an intermediate node to forge and forward messages;
- (5)
- The adversary may act as an insider attacker to change authorities;
- (6)
- An adversary has the ability to physically capture devices;
- (7)
- The adversary is unable to obtain any secret information from ES regardless of the method used.
5. Proposed Scheme
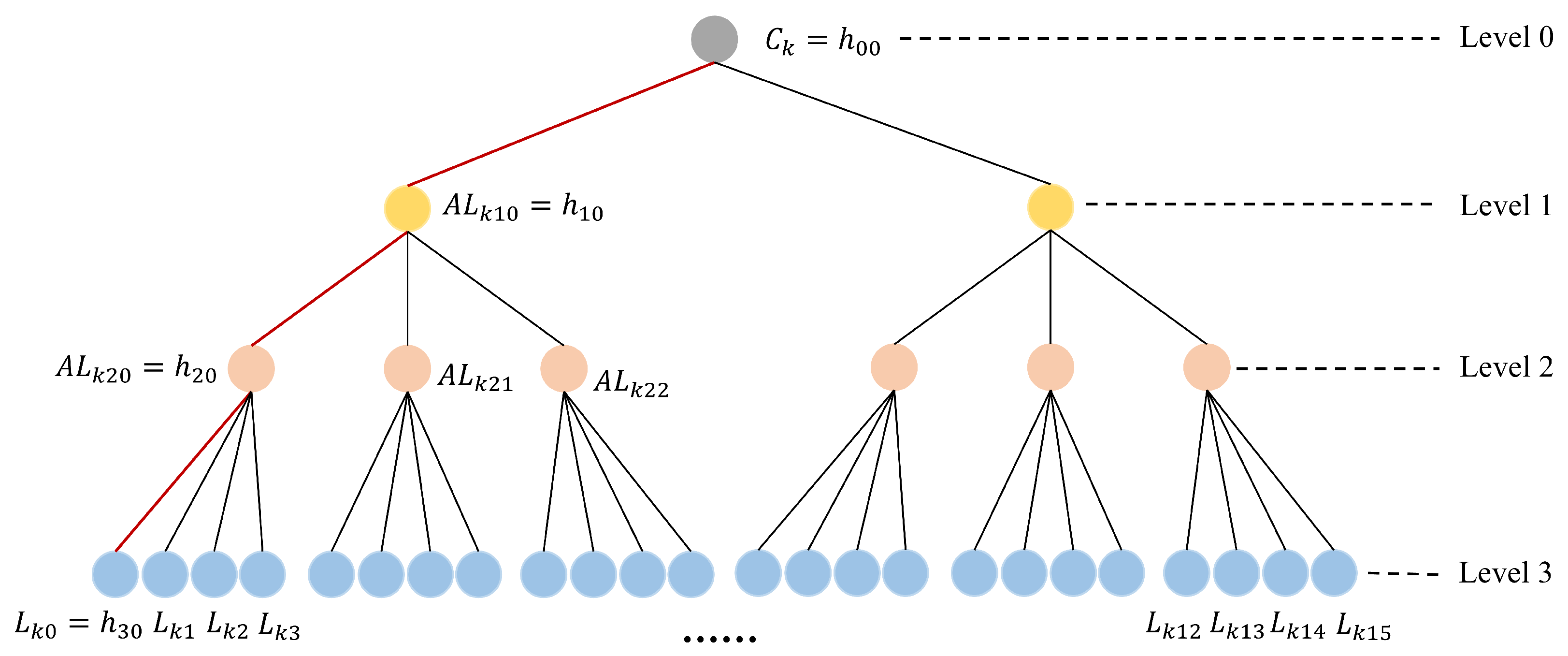
5.1. Parameter Setup Phase
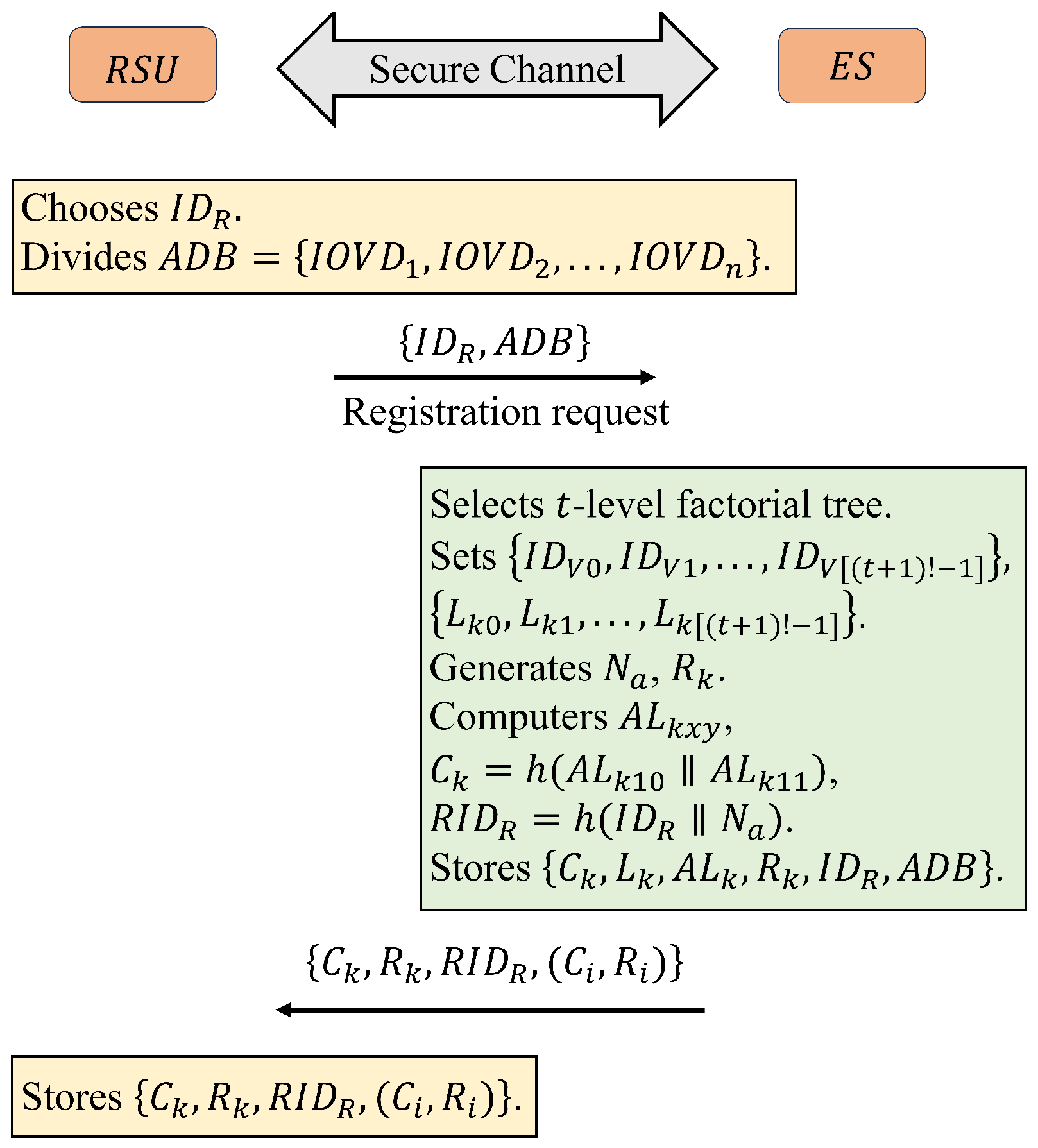
5.2. Registration Phase
- (1)
- Factorial-tree-based fine-grained access control
- (2)
- Registration
5.3. Registration Phase
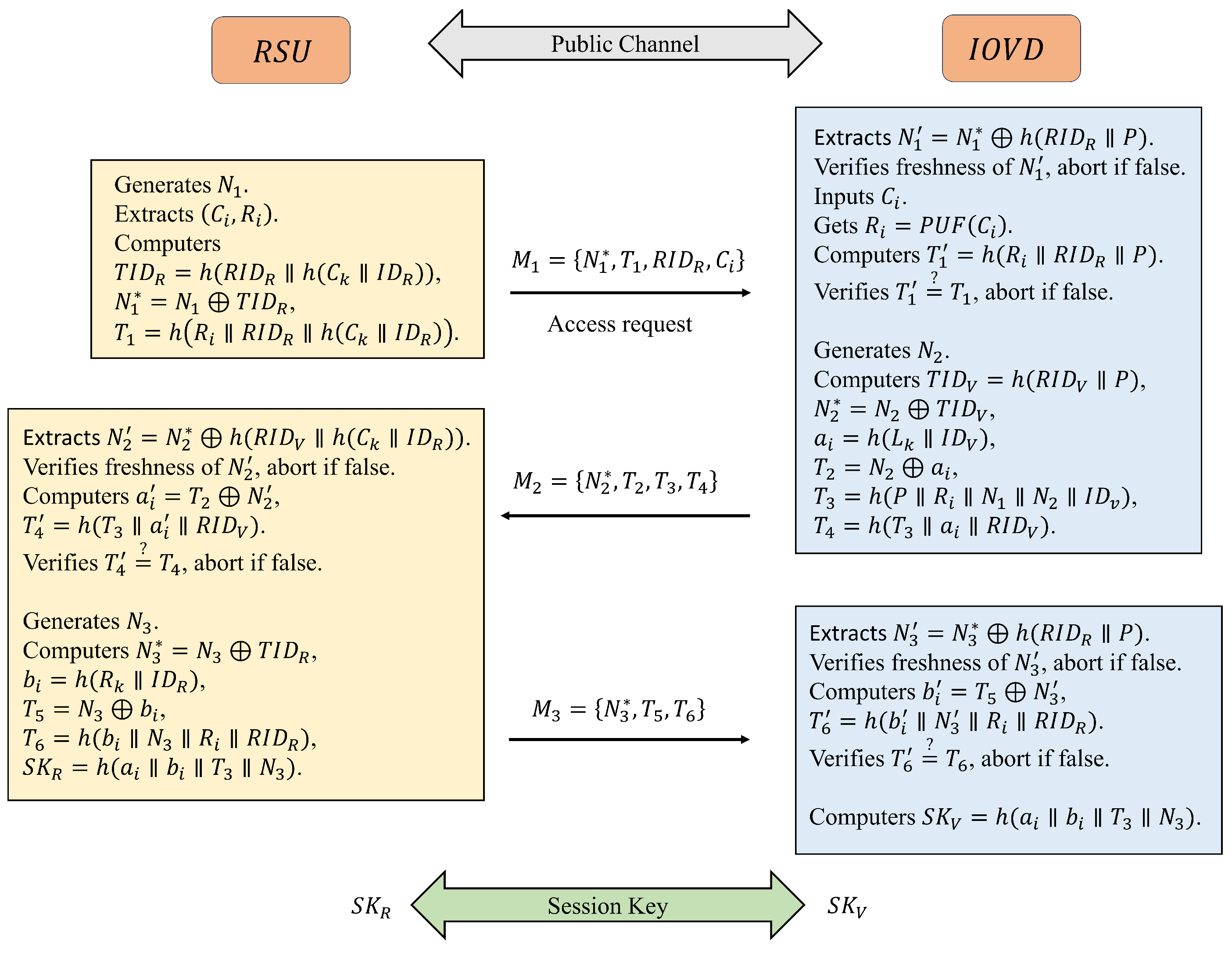
5.4. Mutual Authentication Phase
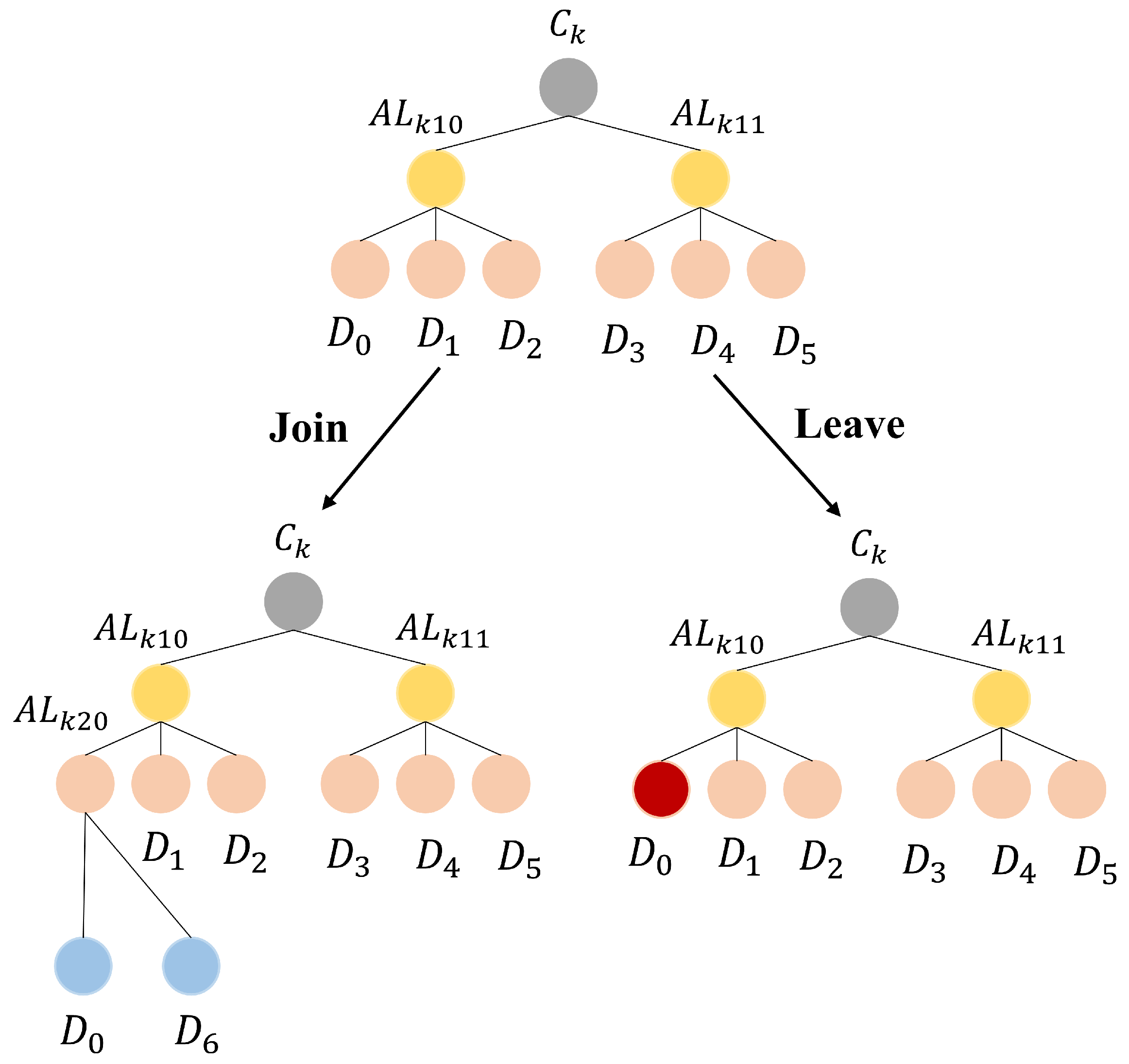
5.5. Dynamic Key Update Phase
- (1)
- joins the cluster
- (2)
- leaves the cluster
6. Security Analysis
6.1. BAN-Logic-Based Formal Security Analysis
- (1)
- Notation and rule
- (2)
- Security goal
- (3)
- Idealized form
- (4)
- Assumption
- (5)
- Security proof
6.2. Informal Security Analysis
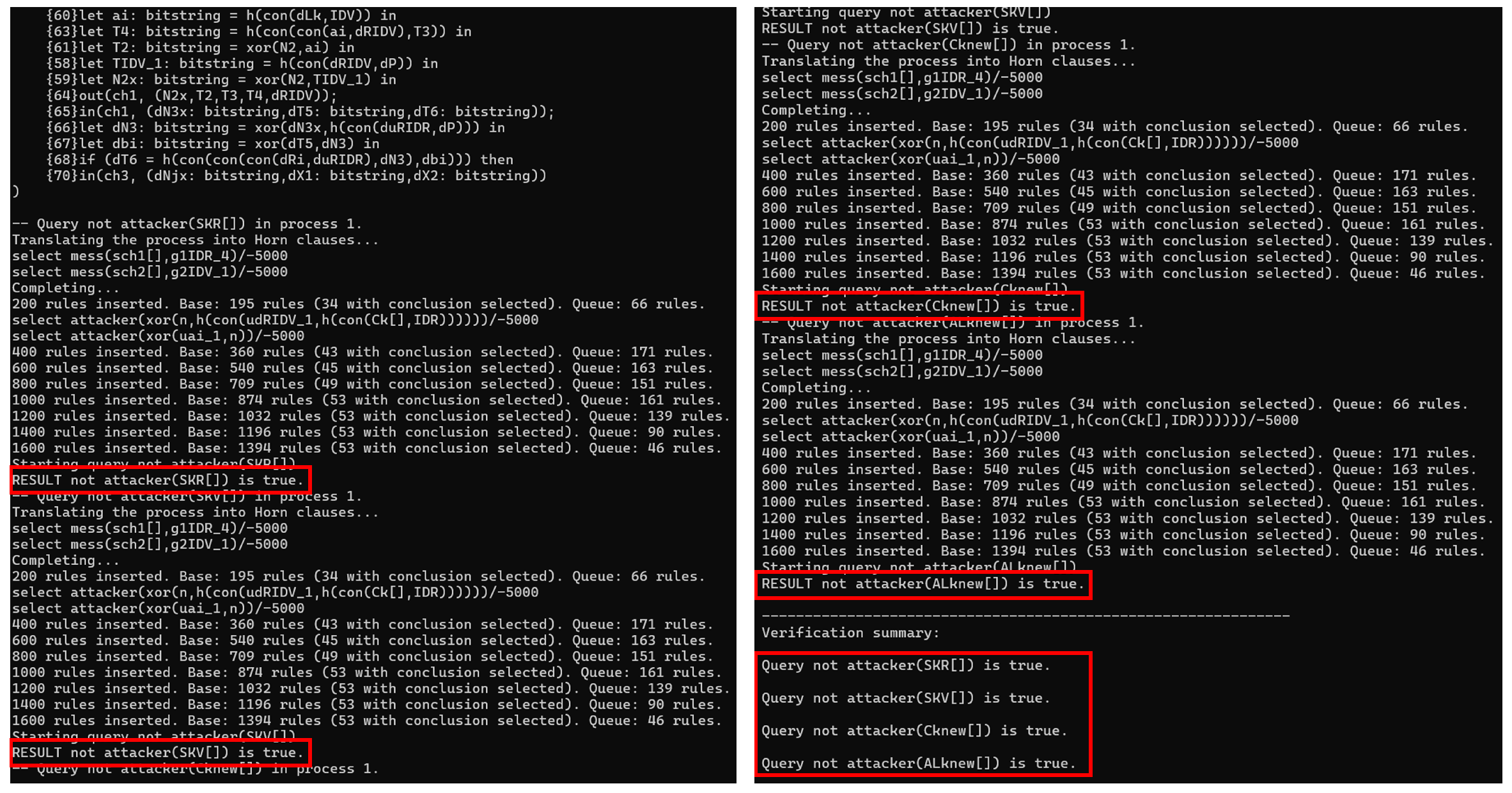
6.3. Formal Verification with Proverif
7. Comparative Analysis
7.1. Calculation Costs Comparison
7.2. Communication Costs Comparison
7.3. Security Features Comparison
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Nizetic, S.; Soli, P.; González-de, D.L.d.I.; Patrono, L. Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future. J. Clean. Prod. 2020, 274, 1–32. [Google Scholar] [CrossRef] [PubMed]
- Wu, C.; Chen, J.; He, K.; Zhao, Z.; Du, R.; Zhang, C. EchoHand: High accuracy and presentation attack resistant hand authentication on commodity mobile devices. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 2931–2945. [Google Scholar]
- Taslimasa, H.; Dadkhah, S.; Neto, E.C.P.; Xiong, P.; Ray, S.; Ghorbani, A.A. Security issues in Internet of Vehicles (IoV): A comprehensive survey. Internet Things 2023, 22, 100809. [Google Scholar] [CrossRef]
- Wu, C.; He, K.; Chen, J.; Zhao, Z.; Du, R. Toward robust detection of puppet attacks via characterizing fingertip-touch behaviors. IEEE Trans. Dependable Secur. Comput. 2021, 19, 4002–4018. [Google Scholar] [CrossRef]
- Tang, T.; Yang, Y.; Wu, D.; Wang, R.; Li, Z. Chaotic moving video quality enhancement based on deep in-loop filtering. Digit. Commun. Netw. 2023, 10, 1708–1715. [Google Scholar] [CrossRef]
- Li, Z.; Gao, X.; Li, Q.; Guo, J.; Yang, B. Edge Caching Enhancement for Industrial Internet: A Recommendation-Aided Approach. IEEE Internet Things J. 2022, 9, 16941–16952. [Google Scholar] [CrossRef]
- Sun, G.; Wang, Z.; Su, H.; Yu, H.; Lei, B.; Guizani, M. Profit Maximization of Independent Task Offloading in MEC-Enabled 5G Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2024, 25, 16449–16461. [Google Scholar] [CrossRef]
- Luo, H.; Zhang, Q.; Sun, G.; Yu, H.; Niyato, D. Symbiotic Blockchain Consensus: Cognitive Backscatter Communications-Enabled Wireless Blockchain Consensus. IEEE/ACM Trans. Netw. 2024, 32, 5372–5387. [Google Scholar] [CrossRef]
- Peng, X.; Song, S.; Zhang, X.; Dong, M.; Ota, K. Task Offloading for IoAV Under Extreme Weather Conditions Using Dynamic Price Driven Double Broad Reinforcement Learning. IEEE Internet Things J. 2024, 11, 17021–17033. [Google Scholar] [CrossRef]
- Wang, Y.; Sun, R.; Cheng, Q.; Ochieng, W.Y. Measurement Quality Control Aided Multisensor System for Improved Vehicle Navigation in Urban Areas. IEEE Trans. Ind. Electron. 2024, 71, 6407–6417. [Google Scholar] [CrossRef]
- Alalwany, E.; Mahgoub, I. Security and trust management in the internet of vehicles (IoV): Challenges and machine learning solutions. Sensors 2024, 24, 368. [Google Scholar] [CrossRef]
- Wu, C.; He, K.; Chen, J.; Zhao, Z.; Du, R. Liveness is not enough: Enhancing fingerprint authentication with behavioral biometrics to defeat puppet attacks. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; pp. 2219–2236. [Google Scholar]
- Wu, C.; Chen, J.; Wang, Z.; Liang, R.; Du, R. Semantic Sleuth: Identifying Ponzi Contracts via Large Language Models. In Proceedings of the 39th IEEE/ACM International Conference on Automated Software Engineering, Sacramento, CA, USA, 27 October–1 November 2024; pp. 582–593. [Google Scholar]
- Sun, J.; Wu, C.; Mumtaz, S.; Tao, J.; Cao, M.; Wang, M.; Frascolla, V. An Efficient Privacy-aware Split Learning Framework for Satellite Communications. IEEE J. Sel. Areas Commun. 2024, 42, 3355–3365. [Google Scholar] [CrossRef]
- Vishwakarma, L.; Nahar, A.; Das, D. LBSV: Lightweight blockchain security protocol for secure storage and communication in SDN-enabled IoV. IEEE Trans. Veh. Technol. 2022, 71, 5983–5994. [Google Scholar] [CrossRef]
- Wu, C.; Cao, H.; Xu, G.; Zhou, C.; Sun, J.; Yan, R.; Liu, Y.; Jiang, H. It’s All in the Touch: Authenticating Users with HOST Gestures on Multi-Touch Screen Devices. IEEE Trans. Mob. Comput. 2024, 23, 10016–10030. [Google Scholar] [CrossRef]
- Wu, C.; Chen, J.; Fang, Q.; He, K.; Zhao, Z.; Ren, H.; Xu, G.; Liu, Y.; Xiang, Y. Rethinking Membership Inference Attacks Against Transfer Learning. IEEE Trans. Inf. Forensics Secur. 2024, 19, 6441–6454. [Google Scholar] [CrossRef]
- Cao, B.; Sun, Z.; Zhang, J.; Gu, Y. Resource allocation in 5G IoV architecture based on SDN and fog-cloud computing. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3832–3840. [Google Scholar] [CrossRef]
- Ji, B.; Chen, Z.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. A vision of IoV in 5G HetNets: Architecture, key technologies, applications, challenges, and trends. IEEE Netw. 2022, 36, 153–161. [Google Scholar] [CrossRef]
- Rani, P.; Sharma, R. Intelligent transportation system performance analysis of indoor and outdoor internet of vehicle (iov) applications towards 5g. Tsinghua Sci. Technol. 2024, 29, 1785–1795. [Google Scholar] [CrossRef]
- Suleski, T.; Ahmed, M.; Yang, W.; Wang, E. A review of multi-factor authentication in the Internet of Healthcare Things. Digit. Health 2023, 9, 20552076231177144. [Google Scholar] [CrossRef]
- El-Kenawy, E.S.M.; Mirjalili, S.; Abdelhamid, A.A.; Ibrahim, A.; Khodadadi, N.; Eid, M.M. Meta-heuristic optimization and keystroke dynamics for authentication of smartphone users. Mathematics 2022, 10, 2912. [Google Scholar] [CrossRef]
- Almadani, M.S.; Alotaibi, S.; Alsobhi, H.; Hussain, O.K.; Hussain, F.K. Blockchain-based multi-factor authentication: A systematic literature review. Internet Things 2023, 23, 100844. [Google Scholar] [CrossRef]
- Khashan, O.A.; Khafajah, N.M. Efficient hybrid centralized and blockchain-based authentication architecture for heterogeneous IoT systems. J. King Saud-Univ.-Comput. Inf. Sci. 2023, 35, 726–739. [Google Scholar] [CrossRef]
- Xie, Q.; Ding, Z.; Tang, W.; He, D.; Tan, X. Provable secure and lightweight blockchain-based V2I handover authentication and V2V broadcast protocol for VANETs. IEEE Trans. Veh. Technol. 2023, 72, 15200–15212. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhao, X.; Jiang, Y.; Shang, F.; Deng, S.; Wang, X. An enhanced privacy-preserving authentication scheme for vehicle sensor networks. Sensors 2017, 17, 2854. [Google Scholar] [CrossRef]
- Wu, L.; Sun, Q.; Wang, X.; Wang, J.; Yu, S.; Zou, Y.; Liu, B.; Zhu, Z. An efficient privacy-preserving mutual authentication scheme for secure V2V communication in vehicular ad hoc network. IEEE Access 2019, 7, 55050–55063. [Google Scholar] [CrossRef]
- Wang, P.; Chen, C.M.; Kumari, S.; Shojafar, M.; Tafazolli, R.; Liu, Y.N. HDMA: Hybrid D2D message authentication scheme for 5G-enabled VANETs. IEEE Trans. Intell. Transp. Syst. 2020, 22, 5071–5080. [Google Scholar] [CrossRef]
- Mun, H.; Seo, M.; Lee, D.H. Secure privacy-preserving V2V communication in 5G-V2X supporting network slicing. IEEE Trans. Intell. Transp. Syst. 2021, 23, 14439–14455. [Google Scholar] [CrossRef]
- Du, Q.; Zhou, J.; Ma, M. EAIA: An Efficient and Anonymous Identity-Authentication Scheme in 5G-V2V. Sensors 2024, 24, 5376. [Google Scholar] [CrossRef]
- Damgård, I.B. A design principle for hash functions. In Conference on the Theory and Application of Cryptology; Springer: Berlin/Heidelberg, Germany, 1989; pp. 416–427. [Google Scholar]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical unclonable functions and applications: A tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Maes, R.; Verbauwhede, I. Physically unclonable functions: A study on the state of the art and future research directions. In Towards Hardware-Intrinsic Security: Foundations and Practice; Springer: Berlin/Heidelberg, Germany, 2010; pp. 3–37. [Google Scholar]
- Cervesato, I. The Dolev-Yao intruder is the most powerful attacker. In Proceedings of the 16th Annual Symposium on Logic in Computer Science—LICS, Citeseer, Boston, MA, USA, 16–19 June 2001; Volume 1, pp. 1–2. [Google Scholar]
- Yıldız, H.; Cenk, M.; Onur, E. PLGAKD: A PUF-based lightweight group authentication and key distribution protocol. IEEE Internet Things J. 2020, 8, 5682–5696. [Google Scholar] [CrossRef]
- Yogesh, P.R. Formal verification of secure evidence collection protocol using BAN logic and AVISPA. Procedia Comput. Sci. 2020, 167, 1334–1344. [Google Scholar] [CrossRef]
- Park, C.S.; Park, W.S. A group-oriented DTLS handshake for secure IoT applications. IEEE Trans. Autom. Sci. Eng. 2018, 15, 1920–1929. [Google Scholar] [CrossRef]
- Su, X.; Xu, Y.; Tong, H.; Li, T. A Cluster-based User Authentication Protocol for Internet of Medical Things Deployment. In Proceedings of the 2023 International Conference on Wireless Communications and Signal Processing (WCSP), Hangzhou, China, 2–4 November 2023; pp. 517–522. [Google Scholar]
- Bussa, S.; Sisto, R.; Valenza, F. Formal Verification of a V2X Privacy Preserving Scheme Using Proverif. In Proceedings of the 2023 IEEE International Conference on Cyber Security and Resilience (CSR), Venice, Italy, 31 July–2 August 2023; pp. 341–346. [Google Scholar]

| Reference | Main Technologies Adopted | Advantages | Disadvantages |
|---|---|---|---|
| [25] | hash, ECC, PUF, blockchain, fuzzy extractor | OBU intrusion attack ✓ device capture attack ✓ MITM attack ✓ impersonation attack ✓ anonymity and untraceability ✓ | privilege-insider attack × forward secrecy × known session key security × high resource cost × fine-grained access control × |
| [26] | hash, asymmetric encryption | key update ✓ mutual authentication ✓ | identity guessing attack × impersonation attack × device capture attack × session key disclosure × high resource cost × fine-grained access control × |
| [27] | hash, asymmetric encryption | guessing attack ✓ session key security ✓ replay attack ✓ anonymity ✓ | impersonation attack × forward secrecy × physical security × device capture attack × fine-grained access control × |
| [28] | hash, digital signature, lookup table | privacy protection ✓ replay attack ✓ message integrity ✓ impersonation attack ✓ MITM attack ✓ | privilege-insider attack × dynamic key update × physical security × anonymity and untraceability × high resource cost × fine-grained access control × |
| [29] | hash, ECC, symmetric encryption | authorization and revocation ✓ privacy protection ✓ MITM attack ✓ privilege-insider attack ✓ anonymity and untraceability ✓ | device capture attack × guessing attack × high resource cost × forward secrecy × fine-grained access control × |
| [30] | hash, ECC | MITM attack ✓ replay attack ✓ forward secrecy ✓ impersonation attack ✓ anonymity and untraceability ✓ | device capture attack × physical security × known session key security × high resource cost × fine-grained access control × |
| Noation | Description |
|---|---|
| , | Road side unit, IoV device |
| Edge server | |
| , | Identity of and |
| , | Pseudo-identity of and |
| , | Temporary identity of and |
| Accessible device table of | |
| Cluster key of | |
| Leaf node key of | |
| ,…, | Auxiliary leaf node keys of |
| Master key of | |
| One-way collision-resistant hash function | |
| Physical unclonable function | |
| PUF-based challenge of | |
| PUF-based response of | |
| ⊕, ‖ | Bitwise XOR and concatenation operations |
| , | Random numbers for registration |
| , , | Random numbers for authentication |
| , | Session keys shared between and |
| Adversary | |
| P sends the message M to Q |
| Protocol | Authentication Total Cost | Time (ms) |
|---|---|---|
| [27] | 0.342 ms | |
| [28] | 172.818 ms | |
| [29] | 167.876 ms | |
| [30] | 11.687 ms | |
| Our | 4.704 ms |
| Protocol | Number of Messages | Size (Bits) |
|---|---|---|
| [27] | 3 | 1216 bits |
| [28] | 5 | 2308 bits |
| [29] | 4 | 3232 bits |
| [30] | 3 | 1672 bits |
| Our | 3 | 1508 bits |
| Feature | Our | [27] | [28] | [29] | [30] |
|---|---|---|---|---|---|
| impersonation attack | ✓ | × | ✓ | — | ✓ |
| impersonation attack | ✓ | × | ✓ | ✓ | ✓ |
| Replay attack | ✓ | ✓ | ✓ | ✓ | ✓ |
| captured Attack | ✓ | × | × | × | × |
| Man-in-the-middle attack | ✓ | × | ✓ | ✓ | ✓ |
| Stolen-verifier attack | — | — | ✓ | — | — |
| Authority modification attack | ✓ | × | × | × | × |
| Insider privilege attack | ✓ | ✓ | × | ✓ | × |
| Off-line password guessing attack | ✓ | ✓ | ✓ | × | × |
| Anonymity and untraceability | ✓ | ✓ | × | ✓ | × |
| Known session key security | ✓ | ✓ | × | × | × |
| Perfect forward secrecy and backward secrecy | ✓ | × | ✓ | × | ✓ |
| Mutual authentication | ✓ | ✓ | ✓ | ✓ | ✓ |
| Key agreement | ✓ | × | ✓ | × | ✓ |
| Physical security | ✓ | × | × | × | × |
| Dynamic key update | ✓ | × | × | × | ✓ |
| Fine-grained access control | ✓ | — | — | — | — |
| Number of authentication messages | 3 | 3 | 5 | 4 | 3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Su, X.; Xu, Y. An Efficient Cluster-Based Mutual Authentication and Key Update Protocol for Secure Internet of Vehicles in 5G Sensor Networks. Sensors 2025, 25, 212. https://doi.org/10.3390/s25010212
Su X, Xu Y. An Efficient Cluster-Based Mutual Authentication and Key Update Protocol for Secure Internet of Vehicles in 5G Sensor Networks. Sensors. 2025; 25(1):212. https://doi.org/10.3390/s25010212
Chicago/Turabian StyleSu, Xinzhong, and Youyun Xu. 2025. "An Efficient Cluster-Based Mutual Authentication and Key Update Protocol for Secure Internet of Vehicles in 5G Sensor Networks" Sensors 25, no. 1: 212. https://doi.org/10.3390/s25010212
APA StyleSu, X., & Xu, Y. (2025). An Efficient Cluster-Based Mutual Authentication and Key Update Protocol for Secure Internet of Vehicles in 5G Sensor Networks. Sensors, 25(1), 212. https://doi.org/10.3390/s25010212






