DataMesh+: A Blockchain-Powered Peer-to-Peer Data Exchange Model for Self-Sovereign Data Marketplaces
Abstract
1. Introduction
- We introduced DataMesh+, an innovative blockchain-powered P2P data exchange model for decentralized self-sovereign data marketplaces (SSDMs). DataMesh+ advances the data mesh concept by integrating blockchain and decentralized storage technologies to enhance decentralization in data trading. It prioritizes user control by employing blockchain-based smart contracts to enable fair, transparent, reliable, and secure data trading marketplaces and empowers users to be sovereign and retain full control over their data. Smart contracts execute self-enforcing agreements between buyers and sellers, facilitating trustworthy transactions among globally disparate and anonymous parties without relying on centralized TTPs.
- We leveraged the Ethereum blockchain [27] to build a prototype that validates the practicality and effectiveness of our approach. To achieve pseudo-anonymity, users are identified through externally owned accounts (EOAs) provided by the Ethereum blockchain, which are secured with private and public cryptographic key pairs. Data ownership is determined by public-private key pairs, digital signatures, and account addresses. Digital signatures authenticate participant identities by cryptographically verifying transaction origins and holding them accountable by providing verifiable proof of their involvement in blockchain-recorded activities. Smart contracts track the participant activities and enforce the consequences of their actions. The InterPlanetary File System (IPFS) [29] provides resilient and highly available data storage and sharing capabilities in a secure, decentralized, and censorship-resistant manner, thus increasing the robustness of the proposed framework.
- We provided a comprehensive literature review addressing the design considerations, principles, and challenges associated with the development of a decentralized P2P data marketplace based on blockchain.
- We have outlined the operational workflow and architectural framework of the proposed model and its implementation. We assessed the acceptability and reliability of the proposed model through experimental testing and validation. Furthermore, we evaluated the security and performance in terms of smart contract deployment and transaction execution costs, the blockchain, and storage network performance.
2. Literature Review and Preliminaries
2.1. Online Data Marketplaces
2.2. Data Mesh, Blockchain and Smart Contracts
2.3. Blockchain-Enabled Data Marketplaces
2.4. Cryptographic Primitives and Digital Signature
- Elliptic curve digital signature algorithm (ECDSA) [53] is used for signing and verifying transactions. Its key pairs are associated with certain domain parameters consisting of an elliptic curve E represented over a finite field (). E is characterized by a base point G ∈ E() [53]. In practice, the parameters of a domain D are defined as (q, FR, a, b, G, n, h), which include q, the field size, where q is equal to p, an odd prime number, or 2m. FR denotes the field specification for elements of . Parameters a and b refer to the field elements of the elliptic curve E over , as defined in Equation (1) for the case where p > 3 and Equation (2) for the case where p > 2 [53].
- G is a finite point of the curve, defined by xG and yG in as G = (xG, yG) with prime order in E(). n is the order of G such that n > 2160 and n > 4 and h is the cofactor, defined as h = #E()/n [53]. A domain can have parameters that are either shared by multiple entities or unique to a particular user.
- Private and public keys: The private key is an arbitrary 256-bit integer k, multiplied by a predefined generator point G over the elliptic curve to produce another point from which the public key K is derived, as defined in Equation (4) [52,53]. The ECDSA key pair generation and validation algorithms are detailed in [53].
- Keccak256/SHA-3 (Secure hash algorithm 3): The Keccak256 hash function, also known as the SHA-3 cryptographic hash algorithm [27], computes the hash value of data stored in a blockchain. Equation (5) computes the Keccak256 hash of a given memory input and returns a 32-byte size hash value.
- Ethereum address: Ethereum addresses comprise 40 hexadecimal characters, unique identifiers derived from the corresponding ECDSA public key or the contract’s Keccak256 hash function (specifically its last 20 bytes), as follows [27,52]. Note that when the address is computed, the prefix (hex) 04 of the public key is omitted.
2.5. InterPlanetary File System and Access Control
3. DataMesh+: Proposed Secure and Reliable Decentralized P2P Data Exchange Model
3.1. DataMesh+ Model Overview
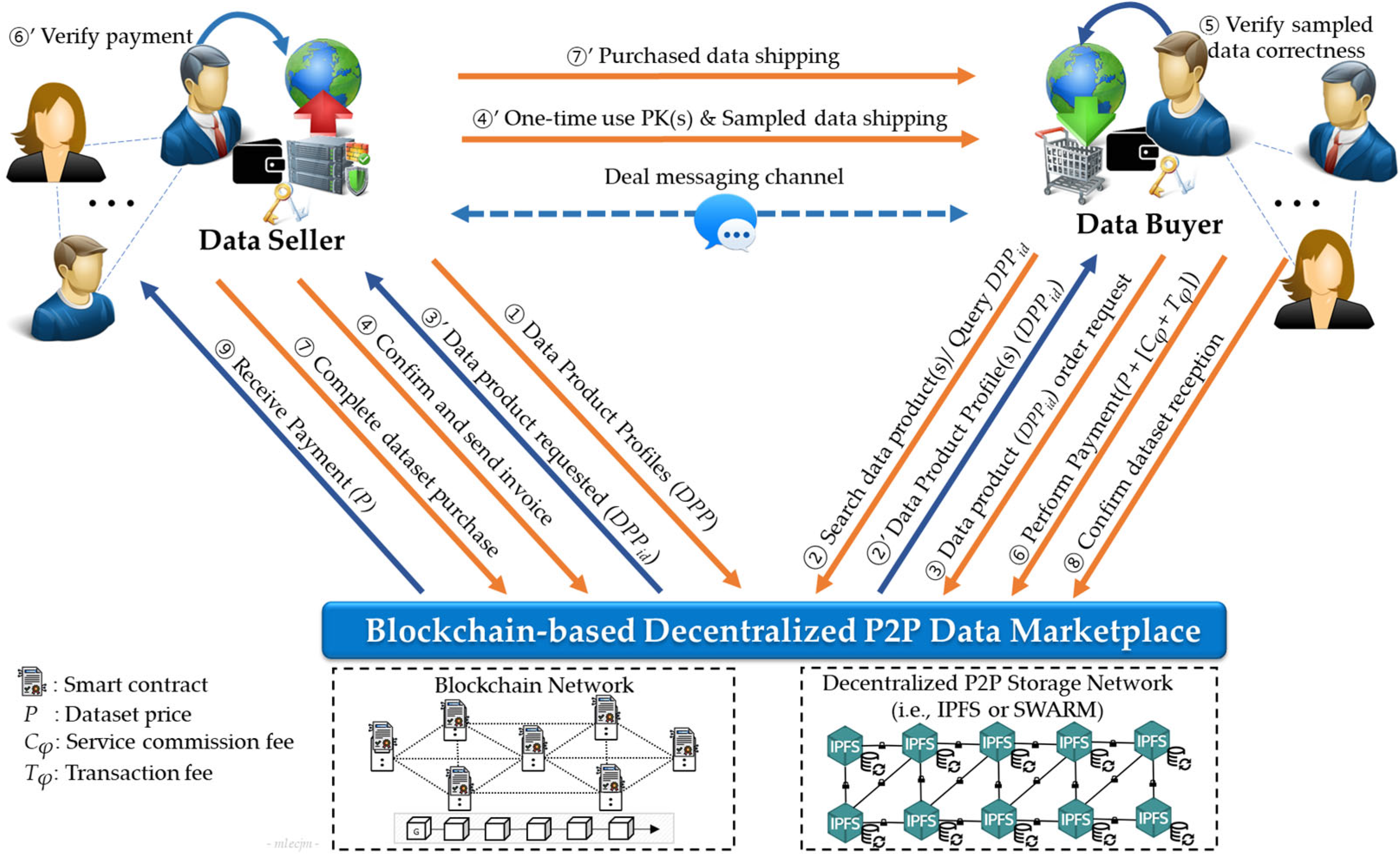
- ①
- First, data sellers, denoted as S = {S1, S2, …, Sn} create a set of data product profiles (DPP), defined as DPP = {DPP1, DPP2, …, DPPm}, which are indexed in the blockchain. These profiles are subsequently published on marketplaces to make them available for sale.
- ②
- Any data buyer Bi of a set B = {B1, B2, …, Bk} can search or query a specific DPPid that matches her/his preferences.
- ③
- The buyer sends a data product DPPid order request, ③’ which is automatically forwarded to the corresponding data seller Sj.
- Upon receiving the request, the seller confirms the order and sends an invoice. ④’ Simultaneously, a single-use decryption key and sample data are sent to the requester for verification and confirmation.
- ④
- Upon receiving the sample data, the buyer verifies its correctness. The buyer can cancel the order request after deeming the data unsatisfactory.
- ⑤
- If the buyer is satisfied with the sample data, he/she can make a payment, which is temporarily held in an escrow smart contract. The total amount paid (Tota) is the sum of data price P, service commission fee (Cφ), and transaction processing fee (Tφ), as defined in Equation (9). Cφ is the multiplication of data price P by α which is a predefined commission rate (i.e., α = 0.05%), as expressed by Equation (10). Tφ is the sum of the transaction-related costs, as defined in Equation (11). ⑥’ After receiving the payment notification, the seller verifies the payment status.
- ⑥
- Subsequently, the seller proceeds with the purchase and ships the purchased dataset to Bi, the corresponding buyer.
- ⑦
- Upon receiving the purchased dataset, the buyer verifies its correctness and ⑧’ confirms data reception for the seller to receive the payment. The buyer can cancel the deal and request a refund if the dataset is unsatisfactory.
- ⑧
- Upon confirming data reception, the smart contract releases funds and transfers P into the seller’s account.
3.2. Architectural Framework
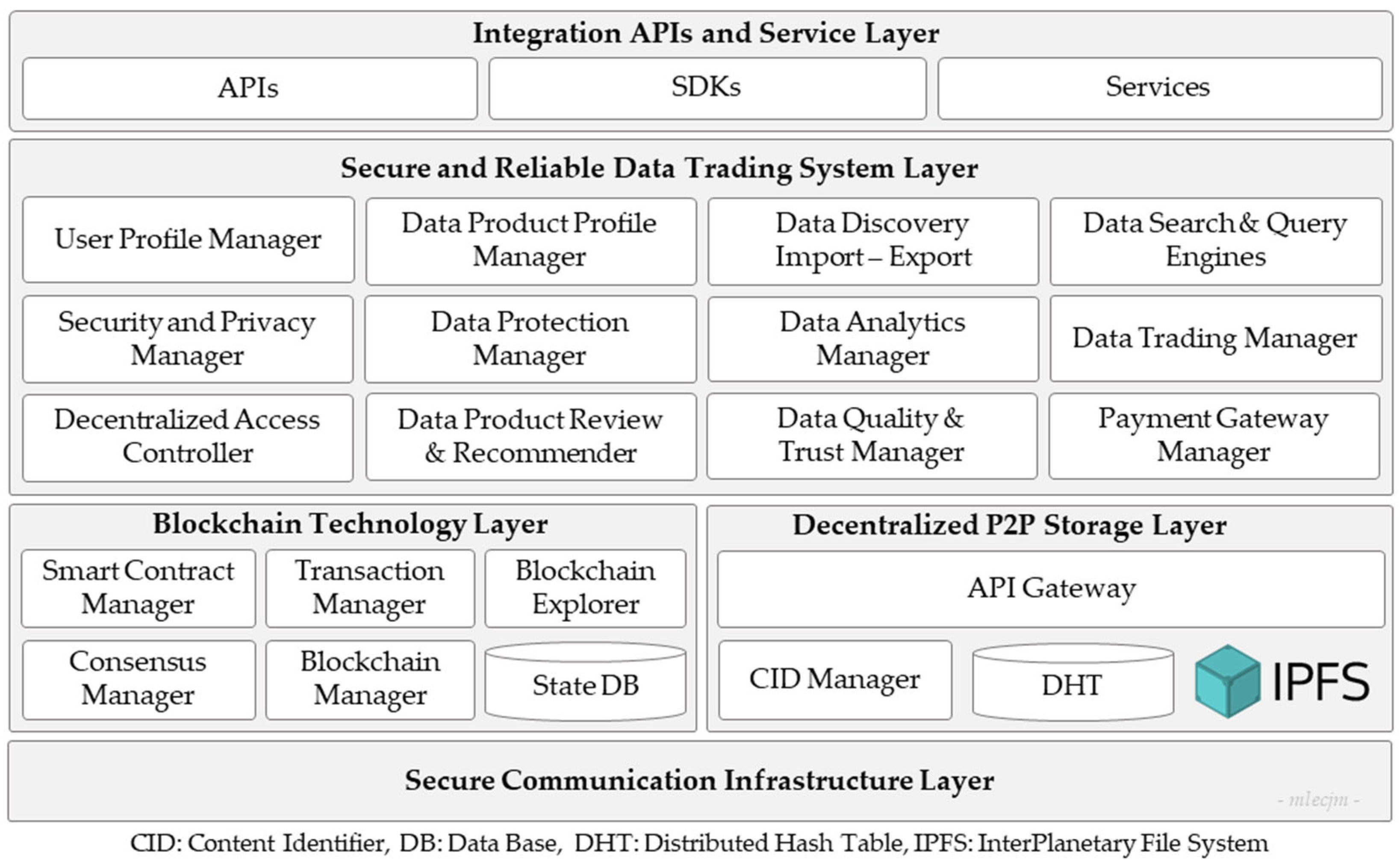
- The Integration APIs and Service Layer provides the necessary application programming interfaces (APIs), software development kits (SDK), and services that facilitate interoperability, accessibility, and interaction between the data trading system layer and external systems or services. This layer enables various applications and services from data import/export to interaction with the system, thereby facilitating a diverse range of data exchange services and improving platform usability.
- The Secure and Reliable Data Trading System Layer is a middleware that provides fair, transparent, secure, and trustworthy data trading features. It comprises the following principal modules: The user profile manager manages user profile credentials, roles, authentication, and authorization, ensuring accurate maintenance and secure access to user data. The data product profile manager allows the creation and management of data product profiles, which include metadata and usage terms associated with the datasets being traded. It also ensures accurate cataloging and retrievability of data products. The data protection manager enforces data protection policies, ensuring compliance with regulations and safeguarding data integrity. The data search and query engines facilitate efficient searching and querying within the marketplace, enabling users to find the data they need based on various search criteria. The data discovery, import, and export module facilitates the discovery, import, and export of data within the system, ensuring data integrity and accurate formatting during the process. The data analytics manager provides data processing and analytical capabilities, transforming raw data into actionable and valuable insights. The data product review and recommender collect user feedback on data products and recommend products to users based on their profiles, preferences, and past behavior. The data quality and trust manager maintains the data quality and manages trust scores for data products, ensuring adherence to high standards. The data trading manager facilitates data trading between users by overseeing transactions and enforcing the terms of agreed trade deals, including transaction validation, execution, and settlement. In addition, it provides features such as data product profile listing, price modeling, order management, and invoice management. The payment gateway manager handles financial transactions, allowing users to make payments for data products or receive payments within the marketplace. The security and privacy manager ensures that all transactions and data exchanges adhere to the highest security and privacy standards. The decentralized access controller ensures that data access is governed by decentralized policies, thereby enhancing security and user control.
- The Blockchain Technology Layer ensures the security, immutability, and transparency of transaction data. It facilitates the integration with the blockchain network for managing the distributed ledger and executing smart contracts. This layer comprises the following main components: The smart contract manager that govern the deployment, execution, and lifecycle of smart contracts governing data exchange agreements. The transaction manager acts as a facilitator within the blockchain, enabling the creation, validation, and processing of transactions. The state DB stores the current state of smart contracts and transaction data in a secure and accessible database. The consensus manager uses consensus algorithms to achieve agreement among network participants regarding the validity of transactions. The blockchain manager oversees the overall operation and maintenance of the blockchain network, including node management and network configuration. The blockchain explorer provides users with a graphical interface to explore and analyze blockchain data, including transaction history and smart contract details.
- The Decentralized P2P Storage Layer oversees a reliable IPFS-based decentralized data storage and access control across a P2P storage network. This layer comprises the following components: The API gateway serves as an interface for accessing and interacting with the IPFS network, allowing users to upload, retrieve, and manage data stored on IPFS. The CID manager manages content identifiers (CIDs) for data stored on IPFS, ensuring unique identification and retrieval of stored content. The distributed hash table (DHT) facilitates decentralized peer discovery and routing within the IPFS network, enabling efficient data retrieval and distribution. The IPFS protocol enables storage and sharing of data in a distributed and censorship-resistant manner, leveraging a network of peer nodes to ensure data availability and integrity.
- The Secure Communication Infrastructure Layer provides secure and reliable communication services built on dedicated secure Internet channels, such as scalability, control, and isolation on next-generation networks (SCION) [61]. SCION provides strong end-to-end encryption and protection against potential cyber threats [61]. Prioritizing scalability, control, and isolation, SCION enhances security compared with traditional Internet protocols. It uses path-aware routing and secure packet forwarding to mitigate common threats such as distributed denial-of-service (DDoS) attacks, route hijacking, and traffic analysis [61].
3.3. Data Trading Algorithms
| Listing 1. Dataset profile data schema. |
| struct Dataset { string id; string name; string data_type; string description; string hash_value; uint256 size; string size_unit; uint256 price; string currency; string cid; string url; address owner; string signature; address previous_owner; bool isOpenForSell; bool isOrdered; bool isSold; uint256 lastUpdate; } |
| Algorithm 1: Data product profile creation |
| Parameters: Smart contract address SCa, account address Aa Input: Seller Sj and DPP details as {id, η, τ, ω, h, s, υ, ν, p, c, σ} Output: Txh, Blockno
|
| Listing 2. Purchase order data schema |
| struct Order { string order_no; address buyer; string dataset_id; uint256 price; string currency; uint256 fee_cost; uint256 total_amount; address seller; bool isPaid; bool isConfirmed; bool isCompleted; bool isCancalled; bool isRefundPaid; uint256 lastUpdate; } |
| Algorithm 2: Data order creation |
| Parameters: Smart contract address SCa, account address Aa Input: Ono, DPPid, Bi, Tφ Output: Txh, Blockno
|
| Algorithm 3: Order payment |
| Parameters: Smart contract address SCa, account address Aa Input: Ono, Bi, Pa // Pa: Paid amount Output: Txh, Blockno
|
| Algorithm 4: Confirm order reception |
| Parameters: Smart contract address SCa, account address Aa Input: Ono, Bi Output: T xh, Blockno
|
| Algorithm 5: Payment transfer and dataset ownership update |
| Parameters: Smart contract address SCa, account address Aa Input: Ono, msg.sender Output: T xh, Blockno
|
| Algorithm 6: Dataset order cancellation |
| Parameters: Smart contract address SCa, account address Aa Input: Ono, Bi Output: Txh, Blockno
|
| Algorithm 7: Payment refund to the buyer |
| Parameters: Smart contract address SCa, account address Aa Input: Ono, msg.sender Output: Txh, Blockno
|
4. Implementation and Evaluation
4.1. Experimental Environment Setup and Performance Metrics
4.2. Operational Cost Evaluation
- Smart contract deployment cost: The deployment cost encompasses the code deposit, execution, and transaction costs. The code deposit cost is the maximum amount of gas required for successful contract creation by placing the code into the state [27,52]. It varies with the size of the bytecode generated from the compiled contract source code. Table 3 presents the measurements of core smart contract deployment gas costs, including dataset management and data trading management contracts. Deployment cost is expressed in Gwei, Ether, and USD, with a gas price of 1 ETH = $1.283.23 (2022.12.09). Although gas prices fluctuate, we used this price for simplicity in our evaluation. Our smart contracts were optimized for cost-effectiveness, with the deployment cost for DatasetMgr.sol and DataTradingMgr.sol smart contracts being approximately 0.00234 Ether ($3.03) and 0.0052 Ether ($6.73), respectively.
- Execution cost: The execution cost is the overall computational gas cost to execute transaction operations using an EVM, as defined in Equation (12).
- Transaction cost: Transaction costs, also referred to as gas fees or the amount of gas used (Gcost), are fees paid by users to miners for processing transactions and ensuring the security of the the blockchain network [27,52]. These fees play a crucial role in resource allocation and network stability. The transaction gas fee (Tfee) is calculated by multiplying the amount of gas used Gu by the gas price Gp, as shown in Equation (13). It is worth noting that transaction costs on the blockchain can fluctuate because of factors such as network congestion, gas prices, and the complexity of the smart contract functions involved in the transaction [52]. Table 4 provides a summary of the operational transaction execution gas costs in Gwei, Ether, and USD. The experimental results indicate that, on average, the transaction execution cost is 0.0001 Ether (0.14 USD) for writing operations and 0.000029 Ether (0.04 USD) for reading operations. Tasks that primarily involve retrieving data (getter functions) generally incur lower fees because they do not change the state of the ledger. Conversely, tasks that involve frequent data updates (setter functions) are likely to incur higher costs depending on their complexity.
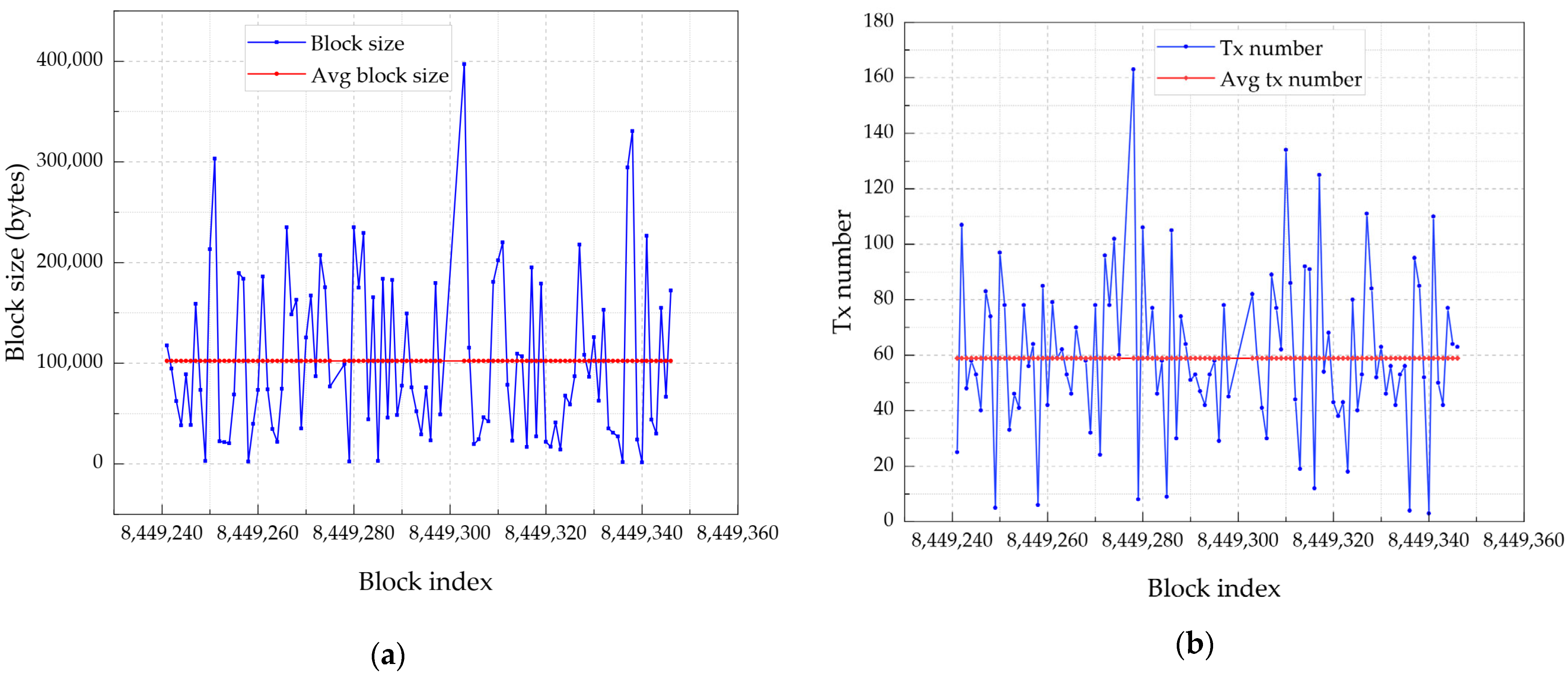
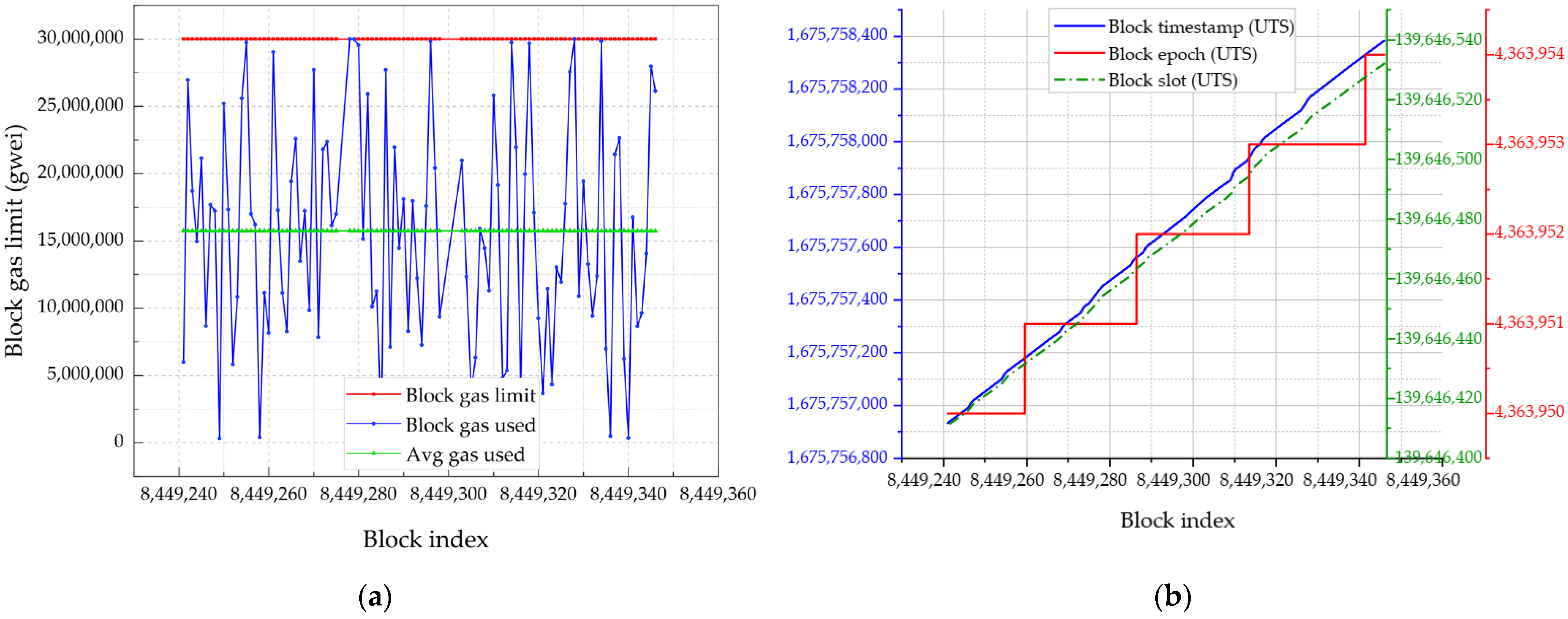
4.3. Blockchain and IPFS Performance
4.4. Security Analysis
- Entity and data origin authentication: Participant entities are identified by Ethereum EOAs, which are authenticated using public-private key pairs and digital signatures [27,52]. Each party possesses a unique private key that is used to generate digital signatures. Verification of the digital signature using the corresponding public key allows the receiving party to authenticate the sender’s identity. The data origin is authenticated and verified through ownership and signature proofs stored on the blockchain.
- Data confidentiality and security: Blockchain and IPFS technologies ensure data integrity and non-repudiation security [27,29,52]. Digital signatures uphold the integrity of the traded data; any alteration to the data would invalidate the signature [52,53]. In addition, they ensure non-repudiation, preventing the sender from denying sending the data. Once signed and transmitted, the signature serves as an irrefutable proof of consent. However, as a public blockchain, neither Ethereum nor IPFS provides data confidentiality. To address this issue, the data are encrypted before storage in IPFS, while the metadata are stored in the blockchain. The proposed system mitigates replay attacks in which the same signature is repeatedly used (“replayed”) for unauthorized actions [52,62]. For example, a payee resubmitting a signature to claim a second payment (double spending attack) poses a serious security risk [62,63]. The security model of the PoA consensus algorithm integrates digital signatures and a tamper-proof ledger to ensure that historical records remain untampered with [54]. This prevents malicious actors from forging payments or falsely reporting asset transfers.
- Accountability, transparency, and fairness: Each participant is held accountable for their actions through activity history recorded in a cryptographically secure and tamper-proof blockchain-based ledger [22,26,27]. This ledger serves as an immutable record that fosters transparency and traceability for every transaction. It ensures that participants’ actions are transparent and traceable, thus fostering a culture of accountability [40,47,48,49,50,51]. To prevent data misuse and maintain fairness, trade history—encompassing ownership transfers and usage terms—is securely stored on the blockchain. This approach facilitates continuous monitoring and auditing of activities, promoting fairness in the data exchange process. Furthermore, the blockchain-based decentralized P2P storage network enhances transparency, prevents fraud, fosters trust among participants, and promotes ethical behavior within the data marketplace ecosystem.
- High availability and reliability: The integration of blockchain and IPFS networks with our proposed system guarantees censorship resistance and robustness, ensuring globally consistent availability and high reliability [29,54,55,56,57,58]. However, the gas fee required to perform transactions introduces a risk of insufficient gas [62,63,64,65], which may affect users’ ability to operate within the system. To mitigate this issue, users are advised to maintain a sufficient balance in their system operating accounts.
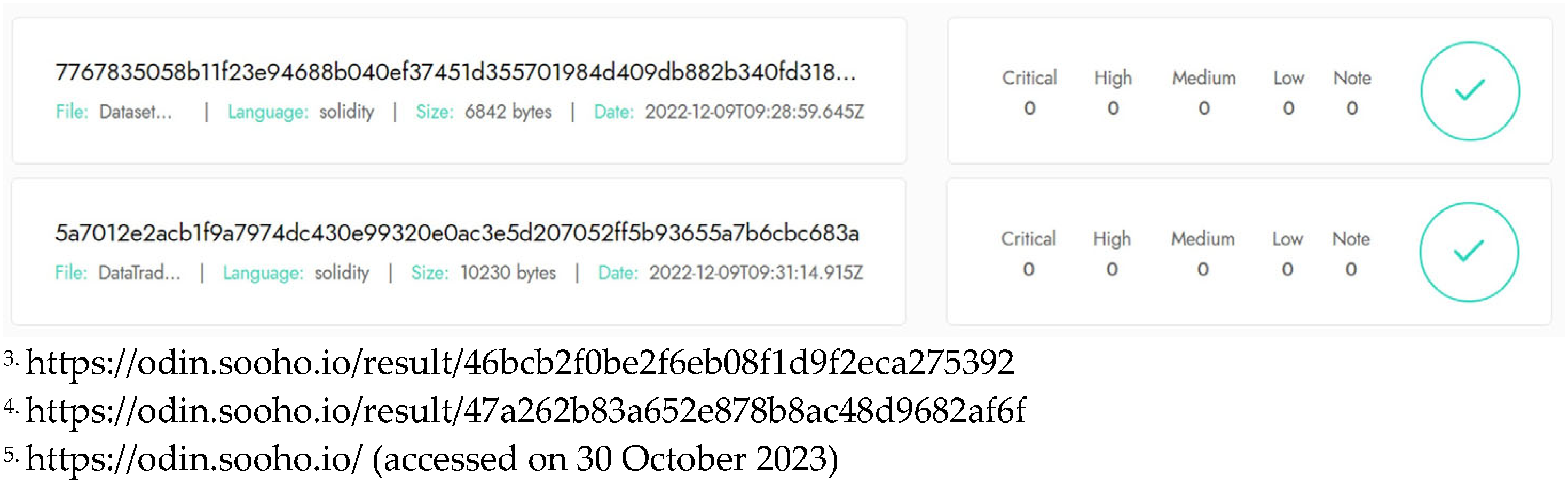
- Smart contract vulnerabilities: Ensuring that smart contracts do not contain bugs or security flaws is crucial before their deployment on the blockchain because they cannot be patched or modified once they are deployed [52,63,66]. Our developed DatasetMgr.sol3 and DataTradingMgr.sol4 smart contracts were successfully analyzed using SOOHOOdin5, a state-of-the-art smart contract security vulnerability analyzer. As shown in Figure 9, they are robust against up-to-date smart contract vulnerabilities, including reentrancy, integer overflow/underflow, unchecked external calls, unprotected ether withdrawal, and gas limit issues [62,63,64,65,66].
- Reentrancy attacks: Malicious actors may exploit reentrancy vulnerabilities in smart contracts to repeatedly invoke functions, potentially withdrawing funds or causing unexpected behavior [62,63]. With the proposed model, such reentrancy attacks can be mitigated by implementing secure coding practices, e.g., using the "Checks-effects-interactions" pattern [63,64,65,66] to ensure that state changes are made before interacting with external contracts or transferring funds.
- Front-running attacks: Malicious actors can execute front-running attacks by monitoring pending transactions and strategically submitting their transactions to exploit price changes or manipulate the transaction order [52,67]. To mitigate such attacks with the proposed model, mechanisms such as commit-reveal schemes or encrypted order submissions can be implemented to obscure transaction details until execution on the blockchain, preventing attackers from preempting legitimate transactions.
- Smart contract bugs: Bugs or logical vulnerabilities in smart contracts can be exploited by attackers to bypass access controls, manipulate data, or cause unexpected behavior in the system [64,65,66]. These risks can be mitigated through comprehensive code reviews, the use of formal verification techniques, and the introduction of bug bounty programs that incentivize security researchers to identify and report vulnerabilities.
- Sybil Attacks: In a Sybil attack, malicious entities create multiple fake identities to gain control over a significant portion of network resources and influence system behavior [68]. To mitigate Sybil attacks, robust identity verification mechanisms, such as proof-of-individuality protocols or reputation systems, can be implemented to prevent the propagation of fake identities and maintain network integrity.
5. Discussion
- Transaction gas fees: Transaction fees, particularly in blockchain networks such as Ethereum, pose a major challenge because of their unpredictability and volatility [27,52]. During periods of heightened network activity, gas fees surge as miners compete for limited block space. Consequently, transaction costs escalate, affecting user experience and increasing the risk of transactions running out of gas mid-execution. Such occurrences can result in transaction failures or partial execution, leading to resource wastage and frustrating user experiences [62,63,64,65]. Effective mitigation strategies involve meticulous estimation of gas limits and costs before transaction execution and optimization of smart contract code to ensure efficient gas usage [63,66].
- Smart contract legal design and upgradability considerations: Smart contract design should include dispute resolution considerations covered by legal regulations. In contrast to traditional software, smart contracts lack upgradability once they are deployed on the blockchain [52,63,64,65]. This limitation poses challenges in adapting to evolving legal frameworks, particularly in e-commerce and related marketplaces. Although smart contracts enhance efficiency and transparency, they also present the challenge of adapting to unforeseen circumstances [32,64]. Predefined terms can restrict their flexibility, leading to suboptimal outcomes in dynamic trading environments. Developing smart contract-driven reliable and fair protocols requires meticulous coding and a deep understanding of the underlying business logic to minimize loopholes or unintended consequences [63,64]. External factors such as market manipulation or regulatory changes exacerbate smart contract limitations. Addressing these concerns requires innovative smart contract design to improve adaptability and resilience to external influences. Thus, exploring complementary mechanisms such as DApps, rigorous testing, and auditing processes to mitigate potential risks remains an area of future research interest.
- P2P data marketplace governance: The absence of a central authority in the proposed P2P data marketplace system necessitates efficient and reliable decentralized governance and trading moderation protocols. Challenges arise from the lack of global data protection regulations, varying jurisdictions, and governance structures governing data sovereignty in P2P data marketplaces.
- Computing resource and energy consumption: The PoA consensus algorithm is renowned for its efficient computing resource and energy consumption scheme [54], which drives its widespread adoption. In contrast, the PoW consensus algorithm is slower and requires considerable computing resources and energy to solve complex mathematical problems [26,27]. In addition, IPFS network nodes exhibit low computation overhead and bandwidth consumption.
- Network scalability: The system’s scalability depends on the underlying blockchain and IPFS networks, both grappling with scalability challenges [27,28,29,55,56]. Balancing scalability, decentralization, and security is essential. Addressing these challenges involves improvements in blockchain scalability and smart contract code optimization, as well as the development of layer 2 scaling solutions and protocol upgrades. These measures mitigate network congestion, reduce gas fees, and enhance network efficiency and throughput.
6. Conclusions and Future Work
7. Patents
- In, H.P.; Merlec, M. M. Blockchain-based safe and reliable data transaction method, and data transaction platform providing system. WIPO (PCT), WO2022145679A1, 7 July 2022.
- In, H.P.; Merlec, M. M. Blockchain-based secure and trusted data trading methods and platform system. Korean Patent, KR102540415B1, 5 June 2023.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- IDC; Statista Inc. Volume of Data/Information Created, Captured, Copied, and Consumed Worldwide from 2010 to 2020, with Forecasts from 2021 to 2025 (in Zettabytes). 2021. Available online: https://www.statista.com/statistics/871513/worldwide-data-created/ (accessed on 10 December 2023).
- Statista Inc. Fortune Business Insights. Size of The Big Data Analytics Market Worldwide from 2021 to 2029 (in Billion U.S. Dollars). 2022. Available online: https://www.statista.com/statistics/1336002/big-data-analytics-market-size/ (accessed on 10 December 2023).
- Kai, K.; Poikola, A.; Honko, H. Mydata a Nordic Model for Human-Centered Personal Data Management and Processing. 2015. Available online: https://julkaisut.valtioneuvosto.fi/bitstream/handle/10024/78439/MyData-nordic-model.pdf (accessed on 10 December 2023).
- Cooper, B.F.; Garcia-Molina, H. Peer-to-peer data trading to preserve information. ACM Trans. Inf. Syst. 2002, 20, 133–170. [Google Scholar] [CrossRef]
- Spiekermann, M. Data marketplaces: Trends and monetisation of data goods. Intereconomics 2019, 54, 208–216. [Google Scholar] [CrossRef]
- Cao, T.D.; Pham, T.V.; Vu, Q.H.; Truong, H.L.; Le, D.H.; Dustdar, S. MARSA: A marketplace for realtime human sensing data. ACM Trans. Internet Technol. 2016, 16, 1–21. [Google Scholar] [CrossRef]
- Parra-Arnau, J. Optimized, direct sale of privacy in personal data marketplaces. Info. Sci. 2018, 424, 354–384. [Google Scholar] [CrossRef]
- Oh, H.; Park, S.; Lee, G.M.; Heo, H.; Choi, J.K. Personal Data Trading Scheme for Data Brokers in IoT Data Marketplaces. IEEE Access 2019, 7, 40120–40132. [Google Scholar] [CrossRef]
- Hatamian, M. Technological Barriers of (non)Blockchain Enabled IoT Data Marketplaces. In Proceedings of the 2021 25th International Computer Science and Engineering Conference (ICSEC), Chiang Rai, Thailand, 16 November 2021; pp. 39–44. [Google Scholar]
- Fruhwirth, M.; Rachinger, M.; Prlja, E. Discovering Business Models of Data Marketplaces. In Proceedings of the 53rd Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2020; pp. 5738–5747. [Google Scholar]
- Van de Ven, M.; Abbas, A.E.; Kwee, Z.; de Reuver, M. Creating a Taxonomy of Business Models for Data Marketplaces. In Proceedings of the 34th Bled eConference-Digital Support from Crisis to Progressive Change, Online, 27–30 June 2021; pp. 313–325. [Google Scholar]
- de la Vega, F.; Soriano, J.; Jimenez, M.; Lizcano, D. A peer-to- peer architecture for distributed data monetization in fog computing scenarios. Wirel. Commun. Mob. Comput. 2018, 2018, 5758741. [Google Scholar] [CrossRef]
- Sabounchi, M.; Wei, J. Blockchain-enabled peer-to-peer data trading mechanism. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1410–1416. [Google Scholar]
- Serrano, N.; Cuenca, F. A Peer-to-Peer Ownership-Preserving Data Marketplace. In Proceedings of the 2021 IEEE International Conference on Blockchain (Blockchain), Melbourne, Australia, 6–8 December 2021; pp. 394–400. [Google Scholar]
- Klems, M.; Eberhardt, J.; Tai, S.; Härtlein, S.; Buchholz, S.; Tidjani, A. Trustless intermediation in blockchain-based decentralized service marketplaces. In Proceedings of the Service-Oriented Computing: 15th International Conference, ICSOC 2017, Malaga, Spain, 13–16 November 2017; pp. 731–739. [Google Scholar]
- Abbas, A.E.; Agahari, W.; van de Ven, M.; Zuiderwijk, A.; de Reuver, M. Business Data Sharing through Data Marketplaces: A Systematic Literature Review. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 3321–3339. [Google Scholar] [CrossRef]
- Andres, S.A.; Laoutaris, N. A survey of data marketplaces and their business models. SIGMOD Rec. 2022, 51, 18–29. [Google Scholar]
- Abbas, A.E. Designing Data Governance Mechanisms for Data Marketplace Meta-Platforms. In Proceedings of the 34th Bled eConference–Digital Support from Crisis to Progressive Change, Online, 27–30 June 2021; pp. 695–707. [Google Scholar]
- De Capitani di Vimercati, S.; Foresti, S.; Livraga, G.; Samarati, P. Toward owners’ control in digital data markets. IEEE Syst. J. 2021, 15, 1299–1306. [Google Scholar] [CrossRef]
- Merlec, M.M.; Lee, Y.K.; Hong, S.-P.; In, H.P. A Smart Contract-Based Dynamic Consent Management System for Personal Data Usage under GDPR. Sensors 2021, 21, 7994. [Google Scholar] [CrossRef]
- Nasonov, D.; Visheratin, A.A.; Boukhanovsky, A. Blockchain-Based Transaction Integrity in Distributed Big Data Marketplace; Springer International Publishing: Cham, Switzerland, 2018; pp. 569–577. [Google Scholar]
- Wang, H.; Qin, H.; Zhao, M.; Wei, X.; Shen, H.; Susilo, W. Blockchain-based fair payment smart contract for public cloud storage auditing. Inf. Sci. 2020, 519, 348–362. [Google Scholar] [CrossRef]
- Voigt, P.; von dem Bussche, A. The EU General Data Protection Regulation (GDPR), A Practical Guide; Springer International Publishing AG: Cham, Switzerland, 2017. [Google Scholar]
- Dehghani, Z. How to Move Beyond a Monolithic Data Lake to a Distributed Data Mesh. 2019. Available online: https://martinfowler.com/articles/data-monolith-to-mesh.html (accessed on 10 December 2023).
- Dehghani, Z. Data Mesh: Delivering Data-Driven Value at Scale; O’Reilly Media: Sebastopol, CA, USA, 2022. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Xu, X.; Weber, I.; Staples, M.; Zhu, L.; Bosch, J.; Bass, L.; Pautasso, C.; Rimba, P. A taxonomy of blockchain-based systems for architecture design. In Proceedings of the 2017 IEEE International Conference on Software Architecture (ICSA), IEEE, Gothenburg, Sweden, 3 April 2017; pp. 243–252. [Google Scholar]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Machado, I.A.; Costa, C.; Santos, M.Y. Data Mesh: Concepts and Principles of a Paradigm Shift in Data Architectures. Procedia Comput. Sci. 2022, 196, 263–271. [Google Scholar] [CrossRef]
- Majchrzak, J.; Balnojan, S.; Siwiak, M. Data Mesh in Action; Simon and Schuster: New York, NY, USA, 2023. [Google Scholar]
- Khan, S.N.; Loukil, F.; Ghedira-Guegan, C.; Benkhelifa, E.; Bani-Hani, A. Blockchain smart contracts: Applications, challenges, and future trends. Peer Peer Netw. App. 2021, 14, 2901–2925. [Google Scholar] [CrossRef]
- Subramanian, H. Decentralized blockchain-based electronic marketplaces. Comm. of the ACM 2017, 61, 78–84. [Google Scholar] [CrossRef]
- Kabi, O.R.; Franqueira, V.N.L. Blockchain-Based Distributed Marketplace. In Business Information Systems Workshops; Abramowicz, W., Paschke, A., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 197–210. [Google Scholar]
- Weber, T.; Prinz, W. Trading User Data: A Blockchain Based Approach. In Proceedings of the 2019 Sixth International Conference on IoT: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; pp. 547–554. [Google Scholar]
- Lawrenz, S.; Sharma, P.; Rausch, A. Blockchain technology as an approach for data marketplaces. In Proceedings of the 2019 International Conference on Blockchain Technology, Honolulu, HI, USA, 15 March 2019; pp. 55–59. [Google Scholar]
- Hyunkyung, Y.; Ko, N. Blockchain based data marketplace system. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), IEEE, Jeju, Republic of Korea, 21–23 October 2020; pp. 1255–1257. [Google Scholar]
- Banerjee, P.; Ruj, S. Blockchain Enabled Data Marketplace–Design and Challenges. arXiv 2018, arXiv:1811.11462. [Google Scholar]
- Li, J.; Grintsvayg, A.; Kauffman, J.; Fleming, C. LBRY: A Blockchain-Based Decentralized Digital Content Marketplace. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 3–6 August 2020; pp. 42–51. [Google Scholar]
- Dai, W.; Dai, C.; Choo, K.K.R.; Cui, C.; Zou, D.; Jin, H. SDTE: A secure blockchain-based data trading ecosystem. IEEE Trans. Inf. Forensics Secur. 2019, 15, 725–737. [Google Scholar] [CrossRef]
- Xiong, W.; Xiong, L. Smart contract based data trading mode using blockchain and machine learning. IEEE Access 2019, 7, 102331–102344. [Google Scholar] [CrossRef]
- Hu, D.; Li, Y.; Pan, L.; Li, M.; Zheng, S. A blockchain-based trading system for big data. Comput. Netw. 2021, 191, 107994. [Google Scholar] [CrossRef]
- Miehle, D.; Meyer, M.M.; Luckow, A.; Bruegge, B.; Essig, M. Toward a decentralized marketplace for self-maintaining machines. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14 July 2019; pp. 431–438. [Google Scholar]
- Christidis, J.; Karkazis, P.A.; Papadopoulos, P.; Leligou, H.C. Decentralized Blockchain-Based IoT Data Marketplaces. J. Sens. Actuator Netw. 2022, 11, 39. [Google Scholar] [CrossRef]
- Suliman, A.; Husain, Z.; Abououf, M.; Alblooshi, M.; Salah, K. Monetization of IoT data using smart contracts. IET Netw. 2019, 8, 32–37. [Google Scholar] [CrossRef]
- Gupta, P.; Kanhere, S.; Jurdak, R. A decentralized IoT data marketplace. arXiv 2019, arXiv:1906.01799. [Google Scholar]
- Özyilmaz, K.R.; Doğan, M.; Yurdakul, A. IDMoB: IoT data marketplace on blockchain. In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018; pp. 11–19. [Google Scholar]
- Bajoudah, S.; Dong, C.; Missier, P. Toward a decentralized, trust-less marketplace for brokered IoT data trading using blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 339–346. [Google Scholar]
- Chen, C.; Wu, J.; Lin, H.; Chen, W.; Zheng, Z. A secure and efficient blockchain-based data trading approach for internet of vehicles. IEEE Trans. Veh. Technol. 2019, 68, 9110–9121. [Google Scholar] [CrossRef]
- Zichichi, M.; Ferretti, S.; Rodríguez-Doncel, V. Decentralized Personal Data Marketplaces: How Participation in a DAO Can Support the Production of Citizen-Generated Data. Sensors 2022, 22, 6260. [Google Scholar] [CrossRef] [PubMed]
- Travizano, M.; Sarraute, C.; Dolata, M.; French, A.M.; Treiblmaier, H. Wibson: A case study of a decentralized, privacy-preserving data marketplace. In Blockchain and Distributed Ledger Technology Use Cases; Springer: Cham, Switzerland, 2020; pp. 149–170. [Google Scholar]
- Antonopoulos, A.M.; Wood, G. Mastering Ethereum: Building Smart Contracts and Dapps; O’Reilly Media: Sebastopol, CA, USA, 2018. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). IJIS 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Islam, M.M.; Merlec, M.M.; In, H.P. A comparative analysis of proof-of-authority consensus algorithms: Aura vs Clique. In Proceedings of the 2022 IEEE International Conference on Services Computing (SCC), Barcelona, Spain, 10–16 July 2022; pp. 327–332. [Google Scholar]
- Naz, M.; Al-zahrani, F.A.; Khalid, R.; Javaid, N.; Qamar, A.M.; Afzal, M.K.; Shafiq, M. A secure data sharing platform using blockchain and interplanetary file system. Sustainability 2019, 11, 7054. [Google Scholar] [CrossRef]
- Merlec, M.M.; Islam, M.M.; Lee, Y.K.; In, H.P. A consortium blockchain-based secure and trusted electronic portfolio management scheme. Sensors 2022, 22, 1271. [Google Scholar] [CrossRef]
- Cruz, J.P.; Kaji, Y.; Yanai, N. RBAC-SC: Role-Based Access Control Using Smart Contract. IEEE Access 2018, 6, 12240–12251. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E. Decentralized Access Control for IoT Based on Blockchain and Smart Contract. In Modeling and Design of Secure Internet of Things; Wiley: Hoboken, NJ, USA, 2018; pp. 505–528. [Google Scholar]
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. The KECCAK Reference, Version 3.0, January 2011. Available online: http://keccak.noekeon.org/Keccak-reference-3.0.pdf (accessed on 10 December 2023).
- Blockscan Chat. Available online: https://chat.blockscan.com/ (accessed on 10 December 2023).
- Zhang, X.; Hsiao, H.; Hasker, G.; Chan, H.; Perrig, A.; Andersen, D. Scion: Scalability, control, and isolation on next-generation networks. In Proceedings of the 2011 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 22–25 May 2011; pp. 212–227. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In Proceedings of the International Conference on Principles of Security and Trust, Uppsala, Sweden, 22–29 April 2017; pp. 164–186. [Google Scholar]
- Diligence, ConsenSys. Ethereum Smart Contract Best Practices-Known Attacks. 2018. Available online: https://ethereum-contract-security-techniques-and-tips.readthedocs.io/en/latest/ (accessed on 10 December 2023).
- Huang, Y.; Bian, Y.; Li, R.; Zhao, J.L.; Shi, P. Smart contract security: A software lifecycle perspective. IEEE Access 2019, 7, 150184–150202. [Google Scholar] [CrossRef]
- Kushwaha, S.S.; Joshi, S.; Singh, D.; Kaur, M.; Lee, H.N. Systematic review of security vulnerabilities in Ethereum blockchain smart contract. IEEE Access 2022, 10, 6605–6621. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Eskandari, S.; Moosavi, S.; Clark, J. SoK: Transparent Dishonesty: Front-Running Attacks on Blockchain; Springer International Publishing: New York, NY, USA, 2020; Volume 11599, pp. 170–189. [Google Scholar]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil Attacks and Their Defenses in the Internet of Things. IEEE Internet Things J. 2014, 1, 372–383. [Google Scholar] [CrossRef]
- Liang, F.; Yu, W.; An, D.; Yang, Q.; Fu, X.; Zhao, W. A survey on big data market: Pricing trading and protection. IEEE Access 2018, 6, 15132–15154. [Google Scholar] [CrossRef]
- Yang, J.; Zhao, C.; Xing, C. Big data market optimization pricing model based on data quality. Complexity 2019, 2019, 5964068. [Google Scholar] [CrossRef]
- Azcoitia, S.A.; Iordanou, C.; Laoutaris, N. Measuring the price of data in commercial data marketplaces. In Proceedings of the 1st International Workshop on Data Economy, Rome, Italy, 9 December 2022; pp. 1–7. [Google Scholar]
- Li, B.; Wu, M.; Li, Z.; Sun, Y. A pricing model for subscriptions in data transactions. Connect. Sci. 2022, 34, 529–550. [Google Scholar] [CrossRef]
- Avyukt, A.; Ramachandran, G.; Krishnamachari, B. A Decentralized Review System for Data Marketplaces. In Proceedings of the 2021 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Sydney, Australia, 3–6 May 2021; pp. 1–9. [Google Scholar]
- Park, J.S.; Youn, T.Y.; Kim, H.B.; Rhee, K.H.; Shin, S.U. Smart contract-based review system for an IoT data marketplace. Sensors 2018, 18, 3577. [Google Scholar] [CrossRef] [PubMed]
- Putra, G.D.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. Blockchain for trust and reputation management in cyber-physical systems. In Handbook on Blockchain; Springer: Cham, Switzerland, 2022; pp. 339–362. [Google Scholar]
- Khaqqi, K.N.; Sikorski, J.J.; Hadinoto, K.; Kraft, M. Incorporating seller/buyer reputation-based system in blockchain-enabled emission trading application. Appl. Energy 2018, 209, 8–19. [Google Scholar] [CrossRef]
- Abubaker, Z.; Khan, A.U.; Almogren, A.; Abbas, S.; Javaid, A.; Radwan, A.; Javaid, N. Trustful data trading through monetizing IoT data using BlockChain based review system. Concurr. Comput. Pract. Exper. 2022, 34, e6739. [Google Scholar] [CrossRef]
- Rizwan, M.; Sohail, M.N.; Asheralieva, A.; Anjum, A.; Angin, P. SAID: ECC-Based Secure Authentication and Incentive Distribution Mechanism for Blockchain-Enabled Data Sharing System. In Proceedings of the 2021 IEEE International Conference on Blockchain (Blockchain), Melbourne, Australia, 6–8 December 2021; pp. 530–537. [Google Scholar]



| Ref./ Features | Data Mesh | P2P 1 | Blockchain | DDM 2 | SC 3 | IPFS 4 | W2WM 5 | COC 6 | DACS 7 | S & T 8 | T & T 9 | Fairness | Accountability | Built PE 10 | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [4] | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ |
| [6] | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ |
| [7] | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ |
| [8] | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ |
| [12] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ |
| [13] | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| [14] | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ |
| [15] | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ |
| [34] | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ |
| [35] | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ |
| [37] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ |
| [39] | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ |
| [40] | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| [41] | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| [42] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| [43] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ |
| [45] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ |
| [46] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ |
| [47] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ |
| [48] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| [49] | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ |
| [51] | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✓ | ✓ | ✗ |
| This work | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Parameters | Values |
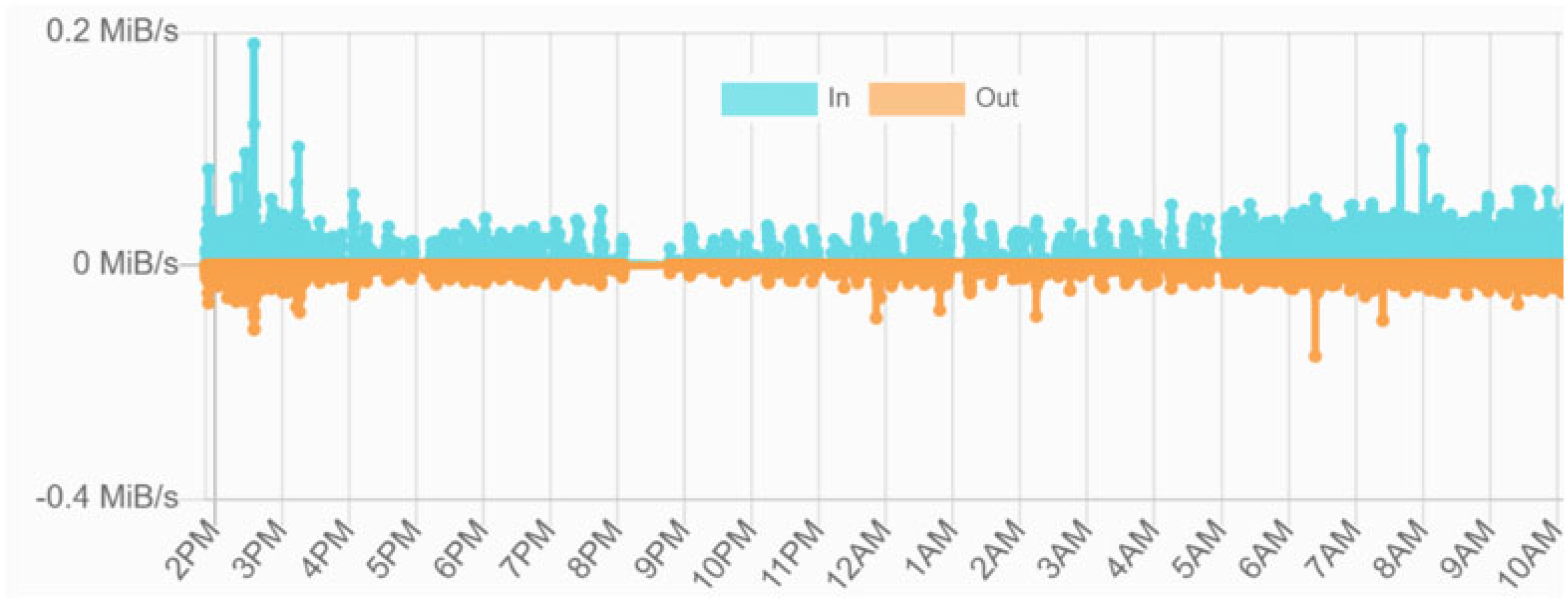
| Network Network ID Chain ID Consensus Protocol Number of nodes Epoch interval Step period Total difficulty Gas limit Average transaction size (bytes) Transaction throughput (TPS) Average transaction latency (sec) Average block size (KB) Average number of Tx per block Number of block confirmations Average block time (sec) Blockchain network utilization (%) Smart contract language Compiler version EVM Version Digital wallet Dapp frameworks and IPAs Average encryption time per DPP (ms) IPFS node & kubo agent IPFS storage time per DPP object (ms) Average size per DPP object (kb) IPFS network bandwidth usage (kb/s) | Goerli Testnet (https://goerli.net/ accessed on 9 December 2022) 5 5 PoA Clique 30 30,000 15 10,790,000 30,000,000 3760 24 36 102.34 60 16 15 61.40 Solidity v0.8.17 London MetaMask v10.23.3 React, nodejs, hardhat, web3.js 25.4 v0. 26.0 & v0.18.1 39.6 38 109.70 (in)/83.12 (out) |
| No | Smart Contract | Deployment Cost | ||
|---|---|---|---|---|
| Gas Used (Gwei) | ETH | USD † | ||
| (1) (2) | DatasetMgr.sol 1 DataTradingMgr.sol 2 | 2,361,016 5,243,074 | 0.00236102 0.00524307 | 3.029726562 6.728069849 |
| No | Smart Contract | Operational Cost | ||
|---|---|---|---|---|
| Gas Used (Gwei) | ETH | USD † | ||
| (1) | newDataSet | 406,619 | 0.00040662 | 0.52178570 |
| (2) | getDatasetDetail | 53,166 | 0.00005317 | 0.06822421 |
| (3) | isOpenForSale | 25,499 | 0.00002550 | 0.03272108 |
| (4) | openForSale | 48,897 | 0.00004890 | 0.06274610 |
| (5) | isSold | 25,478 | 0.00002548 | 0.06274610 |
| (6) | closeSale | 26,953 | 0.00002695 | 0.03458690 |
| (7) | getDataPrice | 29,117 | 0.00002912 | 0.03736381 |
| (8) | changePrice | 44,198 | 0.00004420 | 0.05671620 |
| (9) | getOwner | 25,493 | 0.00002549 | 0.03271338 |
| (10) | changeOwnership | 44,155 | 0.00004416 | 0.05666102 |
| (11) | newOrder | 287,227 | 0.00028723 | 0.36857830 |
| (12) | getOrderDetail | 41,097 | 0.00004110 | 0.05273690 |
| (13) | getOrderAmount | 29,096 | 0.00002910 | 0.03733686 |
| (14) | isPaid | 25,454 | 0.00002545 | 0.03266334 |
| (15) | payOrder | 48,800 | 0.00004880 | 0.06262162 |
| (16) | confirmReception | 36,633 | 0.00003663 | 0.04700856 |
| (17) | sendPayment | 74,048 | 0.00007405 | 0.09502062 |
| (18) | isRefunded | 25,500 | 0.00002550 | 0.03272237 |
| (19) | refundOrder | 76,039 | 0.00002550 | 0.03272237 |
| (20) | withdraw | 35,185 | 0.00007405 | 0.09502062 |
| (21) | getBalanceOf | 22,234 | 0.00002223 | 0.02853134 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Merlec, M.M.; In, H.P. DataMesh+: A Blockchain-Powered Peer-to-Peer Data Exchange Model for Self-Sovereign Data Marketplaces. Sensors 2024, 24, 1896. https://doi.org/10.3390/s24061896
Merlec MM, In HP. DataMesh+: A Blockchain-Powered Peer-to-Peer Data Exchange Model for Self-Sovereign Data Marketplaces. Sensors. 2024; 24(6):1896. https://doi.org/10.3390/s24061896
Chicago/Turabian StyleMerlec, Mpyana Mwamba, and Hoh Peter In. 2024. "DataMesh+: A Blockchain-Powered Peer-to-Peer Data Exchange Model for Self-Sovereign Data Marketplaces" Sensors 24, no. 6: 1896. https://doi.org/10.3390/s24061896
APA StyleMerlec, M. M., & In, H. P. (2024). DataMesh+: A Blockchain-Powered Peer-to-Peer Data Exchange Model for Self-Sovereign Data Marketplaces. Sensors, 24(6), 1896. https://doi.org/10.3390/s24061896







