Abstract
To address the complexities, inflexibility, and security concerns in traditional data sharing models of the Industrial Internet of Things (IIoT), we propose a blockchain-based data sharing and privacy protection (BBDSPP) scheme for IIoT. Initially, we characterize and assign values to attributes, and employ a weighted threshold secret sharing scheme to refine the data sharing approach. This enables flexible combinations of permissions, ensuring the adaptability of data sharing. Subsequently, based on non-interactive zero-knowledge proof technology, we design a lightweight identity proof protocol using attribute values. This protocol pre-verifies the identity of data accessors, ensuring that only legitimate terminal members can access data within the system, while also protecting the privacy of the members. Finally, we utilize the InterPlanetary File System (IPFS) to store encrypted shared resources, effectively addressing the issue of low storage efficiency in traditional blockchain systems. Theoretical analysis and testing of the computational overhead of our scheme demonstrate that, while ensuring performance, our scheme has the smallest total computational load compared to the other five schemes. Experimental results indicate that our scheme effectively addresses the shortcomings of existing solutions in areas such as identity authentication, privacy protection, and flexible combination of permissions, demonstrating a good performance and strong feasibility.
1. Introduction
With the rapid advancement of computing, communication, and artificial intelligence technologies, a plethora of traditional internet technologies have been integrated into the Industrial Internet of Things (IIoT), significantly enhancing the rate of data transmission and sharing [1,2]. The core operations in IIoT data transfer and sharing involve the interconnectivity of sensors, communication nodes, and control systems to gather, transmit, and analyze data. This data includes sensitive information about equipment status, production processes, and supply chains [3,4]. However, as the IIoT increasingly merges with traditional information technologies, it faces a growing number of cybersecurity challenges [5]. Due to limitations in resources and hardware, the IIoT cannot implement complex and precise security protections like traditional information systems. This makes it vulnerable to attacks during data transmission and sharing processes [6,7].
In the past year, there have been several reported incidents of data breaches involving the IIoT. For instance, the health management company Intellihartx confirmed that hackers stole the medical information and social security numbers of over half a million patients [8]. The MOVEit file transfer tool (v. 13.0.7, v. 13.1.5, v. 14.0.5, v. 14.1.6, v. 15.0.2) was attacked, leading to the leak of sensitive data from companies like wage service provider Zellis, British Airways, BBC, and Nova Scotia, which used the software [9]. The American pharmaceutical giant PharMerica disclosed that unknown actors accessed its system in March and extracted the personal data of 5.8 million individuals [10]. A ransomware hacker group named BlackCat threatened to leak 80 GB of confidential data they claimed to have stolen from Reddit servers in February [11]. According to a 2022 report by Waterfall Security Solutions, there were 57 cyber-attack incidents related to operational technology, impacting over 150 industrial operations [12]. This suggests an escalation in industrial network security challenges, with projections indicating that upwards of 15,000 industrial sites may face operational cessation due to cyber incursions within the ensuing five-year period [13,14]. In the event of a sustained increase in malicious attacks targeting the industrial internet, the fragility of such networks is expected to be severely threatened, potentially impacting the regular operations of the IIoT systems. [15,16]. Hence, there is an urgent need to develop a convenient, flexible, and secure data sharing solution for the IIoT.
Blockchain technology, as a decentralized and secure distributed ledger system, offers a novel approach to resolving the challenges of secure data sharing within the IIoT. It provides a decentralized platform for data management and sharing, ensuring data security and privacy [17,18]. The distributed and immutable nature of blockchain technology complicates hacking attempts and data tampering. Additionally, blockchain’s consensus mechanism and data auditing capabilities increase the trustworthiness and transparency of data, allowing stakeholders to share and use reliable data [19,20]. However, nodes in a blockchain are required to store and process all transaction data, which significantly increases the blockchain’s storage and computational requirements as data volume grows [21]. The inherent public and transparent nature of blockchain, where all transactions and data are accessible to participating nodes, poses challenges to protecting the privacy of the IIoT users and members [22]. Although blockchain technology opens new possibilities for addressing IIoT data security sharing issues, due to these factors its direct application to the IIoT still faces some difficulties.
Addressing the outlined issues, this work combines weighted threshold secret sharing, zero-knowledge proof, and attribute-based encryption technologies to propose a blockchain-based data sharing and privacy protection (BBDSPP) scheme for the IIoT. This scheme utilizes the weighted threshold secret sharing method to characterize and assign values to attributes, achieving a flexible combination of permissions. This allows terminal members to access system data securely and flexibly. The scheme also incorporates a non-interactive zero-knowledge proof protocol to pre-authenticate data accessors, preventing unauthorized access and data leakage. Moreover, it employs the interplanetary file system (IPFS) for distributed storage of encrypted data, reducing the storage pressure on the blockchain.
1.1. Main Contributions
The main contributions of this paper can be summarized as follows:
- (1)
- Design of Data sharing Architecture: We have summarized the advantages and disadvantages of various existing data sharing schemes and analyzed the security risks associated with data sharing in the IIoT. We designed a data sharing system architecture suitable for the IIoT. This architecture comprehensively considers the flexibility, security, and scalability of data sharing. Based on blockchain technology, it achieves efficient, secure, and transparent data sharing in a decentralized manner, ensuring the confidentiality and integrity of critical data and providing a solution to the security needs of the IIoT;
- (2)
- Improvement of the Data Sharing Scheme: We assign values to attributes based on their characteristics and use a weighted threshold secret sharing scheme to improve the data sharing approach, creating a data sharing scheme with freely combinable permissions. This scheme allows terminal members to freely select the attributes for decryption. Access to specific data is granted once the attribute values meet the preset access threshold. Not only does this scheme ensure the flexibility of data sharing, but it also enhances the rigor of access control, achieving fine-grained access control in the system;
- (3)
- Implementation of Privacy Protection: Based on non-interactive zero-knowledge proof technology, we have designed a lightweight identity verification protocol to pre-validate the identity of data accessors. This ensures that only authorized terminal members can access system data, preventing identity impersonation by unauthorized members and illegal access to sensitive data. Consequently, this secures the privacy of terminal members and the safety of data while also reducing the additional computational overhead caused by illegal access attempts;
- (4)
- Distributed Data Storage: We store a substantial amount of data on the IPFS, and only the corresponding storage addresses are recorded on the blockchain. This storage method not only ensures the security and integrity of the data but also significantly enhances data retrieval efficiency and the scalability of the system. This approach addresses the issue of insufficient storage space in traditional blockchain applications;
- (5)
- Performance Analysis and Validation: We conducted a thorough analysis of the proposed solution in terms of correctness and security, along with a comprehensive theoretical assessment of its functional characteristics and computational costs. Additionally, we validated the practical effectiveness of the solution through experimental design. The experimental results indicate that the scheme effectively overcomes the limitations found in existing data sharing approaches in critical areas such as identity authentication, privacy protection, flexible permission configuration, and off-chain storage, while also demonstrating superior performance and strong feasibility.
1.2. Organization
In Section 2, we describe the related work of this paper; in Section 3, we introduce the basic knowledge; in Section 4, we provide a detailed introduction to the BBDSPP scheme; in Section 5, we analyze the correctness and security of BBDSPP; in Section 6, we further analyze the performance of BBDSPP; and in Section 7, we summarize the content of the entire paper.
2. Related Work
In recent years, blockchain-based data sharing and privacy protection schemes for the IIoT have become a widely researched topic of international interest. Numerous scholars have delved into the exploration of data sharing and privacy protection [23], yielding a series of significant research achievements in these fields. Key developments in this area are outlined in Table 1 and Table 2.

Table 1.
Research achievements in data sharing.

Table 2.
Research achievements in the field of privacy protection.
Based on the analysis of the aforementioned literature, numerous scholars have made significant contributions to research on blockchain technology’s application in data sharing and privacy protection in the IIoT. These studies lay a solid foundation for the research approach of this paper. However, there are still several challenges in these research outcomes, including the complexity of data sharing algorithms, lack of flexibility, insufficient security, and relatively high computational costs. Moreover, these studies have not been closely integrated with the structural characteristics of the industrial internet, limiting their application in complex IIoT environments. Building upon current research, several critical issues need to be addressed, as analyzed below:
- (1)
- Achieving efficient data transmission and sharing without sacrificing algorithm performance;
- (2)
- Effectively managing and verifying the identities of a large number of devices and handling the vast amount of data generated;
- (3)
- Ensuring the integrity and security of data during its collection, transmission, and storage in environments with multiple stakeholders.
Therefore, it is imperative to investigate a data sharing and privacy protection scheme suitable for the IIoT which enables secure and efficient data sharing among terminal members while safeguarding their privacy information. For this purpose, we propose the BBDSPP scheme, which integrates cutting-edge technologies such as weighted threshold secret sharing, zero-knowledge proof, and attribute-based encryption. In this scheme, we assign characteristic values to attributes and optimize the data sharing process, thus implementing a flexible access control mechanism with combinational permissions. Subsequently, utilizing non-interactive zero-knowledge proof protocols, we pre-authenticate the identities of data accessors, effectively preventing unauthorized access. Moreover, we employ the IPFS distributed storage system to alleviate the storage burden on the blockchain, enhancing storage efficiency and system scalability. This approach provides a secure and trustworthy environment for data circulation in the IIoT.
3. Basic Concepts
In this section, we primarily introduce the fundamental mathematical concepts utilized in the BBDSPP scheme, including the three basic properties of bilinear mapping, the definition and three fundamental properties of weighted threshold secret sharing, and the basic principles of zero-knowledge proofs. The zero-knowledge proof protocols encompass both interactive and non-interactive types. In the authentication phase of the BBDSPP scheme, we employ a non-interactive zero-knowledge proof protocol. To facilitate a better understanding for the readers, in this section, we introduce and compare the principles of both interactive and non-interactive zero-knowledge proof protocols. In this scheme, we characterize and assign values to attributes to optimize the data sharing process, achieving a flexible access control mechanism with combinational permission settings.
3.1. Bilinear Mapping
Let , , and be cyclic groups of prime order . A bilinear pairing is a map , where is also a cyclic group of the same order, satisfying the following properties [36]:
- (1)
- Bilinearity: For all , , and , the map satisfies ;
- (2)
- Non-degeneracy: For all and , the map does not send every pair to the identity element of , that is ;
- (3)
- Computability: For all and , there exists an efficient algorithm to compute .
Additionally, the bilinear map is required to have the following uniqueness property: for any , and , if then .
3.2. Weighted Threshold Secret Sharing
Weighted threshold secret sharing (WTSS) is an extension of the threshold secret sharing scheme originally proposed by Shamir in 1979. In traditional threshold secret sharing schemes, each participant is considered to have an equal contribution to the reconstruction of the secret. However, in practical applications, the status and role of participants often differ. To address this issue, researchers have introduced the WTSS mechanism. The core concept of this mechanism is to distribute a secret among a group of participants, where each participant is assigned a weight [37]. This weight reflects the participant’s importance or level of trust within the group.
Definition: In a WTSS scheme, a secret is divided into shares , and distributed to participants. Each participant is assigned a weight . The secret can be reconstructed only when the sum of the weights of the participants who combine their shares is greater than or equal to a predefined threshold .
Properties:
- (1)
- Flexibility: WTSS allows for a flexible and hierarchical structure of trust among participants by assigning different weights to each participant;
- (2)
- Security: The secret cannot be reconstructed unless the weighted shares sum up to at least the threshold, providing security against partial compromise;
- (3)
- Robustness: WTSS schemes are robust against the failure of some participants to provide their shares, as long as the threshold can still be reached with the available shares.
In summary, WTSS provides a means for securely distributing a secret in a manner that reflects the hierarchy and trust levels within a group, ensuring that only a weighted combination of participants can reconstruct the secret [38].
3.3. Zero-Knowledge Proofs
Zero-knowledge proofs can be categorized into interactive and non-interactive types. Interactive zero-knowledge proofs involve multiple rounds of information exchange between the prover and the verifier. In this method, the prover begins with a preliminary proof. Subsequently, the verifier poses a series of random challenges based on this proof, to which the prover must respond appropriately. This process is repeated until the verifier is convinced of the proof’s validity. If the statement to be proven is true, an honest prover can convince the verifier of its truth without revealing any additional information. The Schnorr protocol is a classic example within this category of proofs, used to demonstrate knowledge of a discrete logarithm without disclosing its value [39].
Non-interactive zero-knowledge proofs, on the other hand, involve a one-way transmission of proof from the prover to the verifier without further interaction. The advantage of this method is that the prover can pre-generate a proof and reuse it across multiple scenarios, eliminating the need for ongoing interaction with the verifier. To achieve non-interactivity, techniques such as a “common reference string” or cryptographic tricks like the Fiat–Shamir heuristic are often employed to convert interactive protocols into a non-interactive format. Zero-knowledge succinct non-interactive arguments of knowledge (zk-SNARKs) are a widely-used form of zero-knowledge proofs, particularly applied within blockchain technology and extensively used on platforms like Ethereum [40]. A comparison between interactive and non-interactive zero-knowledge proofs is illustrated in Figure 1.
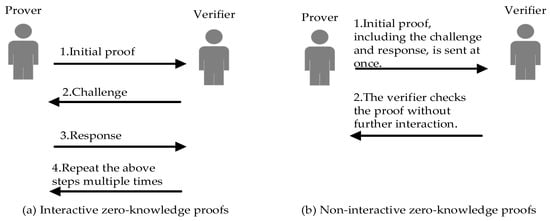
Figure 1.
Comparison between Interactive zero-knowledge proofs and Non-interactive zero-knowledge proofs.
4. Data Security Sharing Schemes
In this section, we provide a detailed introduction to the core components of the BBDSPP scheme, which include the participating entities, the system model, and the execution process. Firstly, we systematically elucidate the functions and responsibilities of the participating entities to ensure that readers have a clear comprehension of each entity’s role within the scheme. Following this, we present the framework of the system model, aiming to furnish readers with a comprehensive understanding of the system’s operational mechanisms. Lastly, we describe the specific steps involved in the implementation of the scheme, covering the application of key technologies and the execution details of each phase. The detailed introduction provided in this chapter aims to offer readers an in-depth and systematic understanding of the BBDSPP scheme.
4.1. Scheme Entities
In this paper, we propose the BBDSPP scheme, which is centered around the core idea of assigning values to attributes based on their characteristics. This is achieved through the utilization of a weighted threshold secret sharing scheme which improves the data sharing process, facilitating a flexible and secure data sharing access control mechanism that allows IIoT end members access to data in the system both flexibly and securely. Moreover, the scheme employs a non-interactive zero-knowledge proof protocol for pre-authenticating the identities of data accessors, preventing the impersonation by unauthorized members, theft of sensitive data, and unnecessary computational overhead. Additionally, the scheme leverages the IPFS distributed storage system to store encrypted shared resources, recording only the storage addresses on the blockchain, significantly alleviating the blockchain’s storage burden.
In this scheme, entities involved in data sharing include: certificate authority (CA), attribute authority (AA), regulatory node (RN), end members, and the interplanetary file system (IPFS). The specific roles are described as follows:
- (1)
- Certificate Authority (CA): As a trusted third party, the CA’s main function is to generate the system’s public parameters and the public keys for end members. It also generates signatures for end members based on the zero-knowledge proof protocol, which are used for identity authentication during data access;
- (2)
- Attribute Authority (AA): The AA is responsible for assigning attributes to end members, associating these attributes with the unique identity identifier of the end members, and registering them. Additionally, the AA categorizes attributes within the system;
- (3)
- Regulatory Node (RN): The RN, a set of pre-selected nodes within a consortium blockchain, is tasked with monitoring and recording a series of data transactions of end members. It forms a public ledger through a secure consensus algorithm;
- (4)
- End Members: End members are smart terminal devices in the IIoT, including data owners (DOs) and data visitors (DVs). DOs are end members that offer data for sharing, primarily focusing on customizing data access policies, encrypting data, and publishing data. DVs are end members that request access to data, mainly submitting data access applications, downloading ciphertext, and decrypting it. The roles of DOs and DVs are interchangeable. A DO can also act as a DV for data querying and access, and vice versa;
- (5)
- Interplanetary File System (IPFS): As a distributed storage platform, IPFS securely stores encrypted shared resources uploaded by DO and returns storage addresses. These addresses serve as clues for DV to download shared resources.
The characters used in this scheme and their meanings are shown in Table 3.

Table 3.
Notations and Their Meanings Used in the Scheme.
4.2. System Model
The BBDSPP scheme’s system model primarily ensures the privacy protection and secure sharing of data information through aspects such as identity authentication, encrypted storage, and access control. The scheme comprises five parts: the initialization phase, registration phase, encryption phase, authentication phase, and decryption phase, and is executed by five participating entities: CA, AA, RN, end members, and IPFS.
The system model of the BBDSPP scheme is depicted in Figure 2.
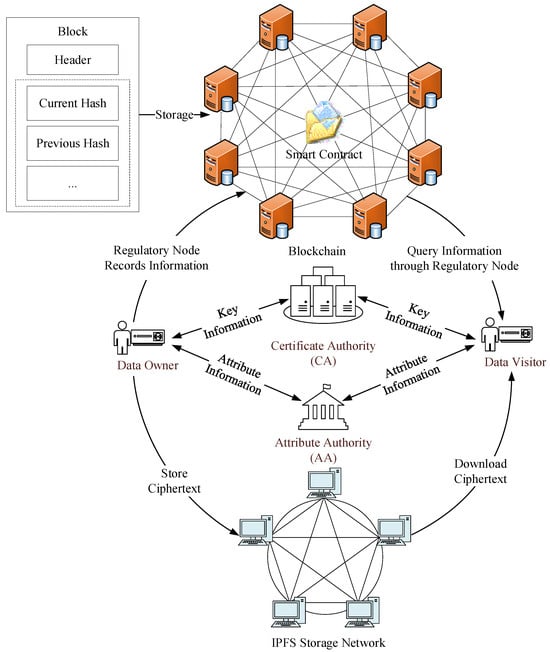
Figure 2.
The BBDSPP scheme’s system model.
During the initialization phase, the CA generates public and private keys for end members based on their identity identifiers. The private key is securely stored and the public key is combined with other parameters to form the system’s public parameters. In the registration phase, the AA first assigns attributes to end members. Then, end members submit their attribute values and public keys to the CA. The CA authenticates end members using a non-interactive zero-knowledge proof protocol, which facilitates anonymous authentication during data access and protects the privacy of data requesters.
In the encryption phase, the DO uses a symmetric encryption algorithm to encrypt the information M to be shared and stores the encrypted ciphertext on the IPFS. The symmetric key is then encrypted using a ciphertext-policy attribute-based encryption method with weighted attributes, yielding the ciphertext and storage address. Subsequently, the RN records the information on the blockchain according to its storage structure and forms a public ledger through a secure consensus algorithm.
In the authentication phase, the DV first locates the storage address of the desired information on the IPFS in the blockchain and submits their zero-knowledge proof to the DO. After the DO verifies the identity of the data requester, they send the data storage address to the data requester.
In the decryption phase, the DV locates and downloads the ciphertext of the desired data from the addressed location. The data is then decrypted using a generated decryption key. Successful decryption and data access occurs only if the attribute weights held by the DV meet the threshold access value; otherwise, decryption is not possible.
Blockchains use a chained structure to store and organize data where each block consists of a block header and a block body. The block header contains information such as the ID of the previous block, version number, and Merkle root, while the block body includes hash operations and transaction information. Blocks are connected to each other through hash pointers. The data storage structure of the blockchain is illustrated as shown in Figure 3.
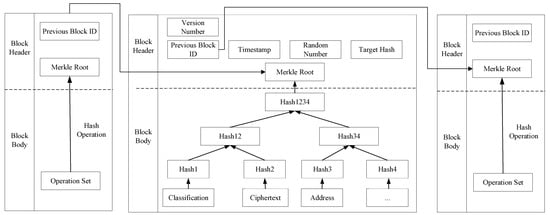
Figure 3.
Blockchain data storage structure.
In this scheme, end members effectively integrate and store the multi-dimensional information and related attributes of data in a blockchain, providing the DV with a more convenient and efficient method for data querying and retrieval. The data information in the blocks includes attribute classification (Classification), encrypted information of the symmetric key (Ciphertext), and storage address (Address), among others. In this scheme, “Classification” provides precise categorization information of accessible attributes, allowing the DV to quickly locate the required data based on their attributes. “Ciphertext” provides encrypted information of the symmetric key encrypted using attribute-based encryption. The DV can access the desired data only after decrypting to obtain the symmetric key. “Address” gives the storage location of the ciphertext in the IPFS, enabling the DV to find and download the ciphertext of the data they wish to access.
4.3. BBDSPP Scheme
Assuming that there are n terminal devices in the entire system, and these n terminal devices are regarded as n end members, then represents the set of these end members. The corresponding set of identity identifiers is , where . Next, we define an ordered set of attributes as , with corresponding attribute values , and corresponding attribute weights , where , indicating the total number of attributes. The BBDSPP scheme consists of five algorithms: initialization, registration, encryption, key generation, and decryption. Below are detailed explanations of the five steps.
- (1)
- Initialization Algorithm
This algorithm is carried out by the CA institution. It takes as input the identity identifier of the end members and outputs the public key of the end member and the public parameters of the system. The specific process is as follows:
- i.
- Randomly select large prime numbers and , choose a bilinear group of prime order , and a cyclic group of prime order , with as the generator of , and as the generator of .
- ii.
- Define a bilinear pairing operation .
- iii.
- Choose three hash functions and , where , and , and compute the public key of the end member as:
- iv.
- Select a random number , and compute the private key of the end member based on as follows:
- v.
- Then compute , hence the public parameters are:
The process of the initialization algorithm is as follows (Algorithm 1):
| Algorithm 1: |
| // Params: identity of terminal member // Returns: public key and public parameters function GeneratePublicKeyAndParams(char[] ) → {, } 01: // Step (i): Select large prime numbers and corresponding groups 02: p = selectLargePrime () 03: q = selectLargePrime () 04: = selectBilinearGroupOfOrder (p) 05: = selectCyclicGroupOfOrder (q) 06: = .generator () // Generator of 07: = .generator () // Generator of 08: // Step (ii): Define bilinear map 09: e = defineBilinearMap (, , ) 10: // Step (iii): Select hash functions 11: = hashFunction (, ) 12: = hashFunction (, ) 13: // Compute public key for terminal member 14: 15: // Step (iv): Select random number and compute private key for terminal member 16: = selectRandomFromZpStar (p) 17: 18: // Step (v): Compute and set public parameters 19: 20: 21: // Return public key and parameters 22: return {, } endfunction |
- (2)
- Registration Algorithm
The algorithm is jointly completed by the CA and the AA. The inputs to the algorithm are the attribute value and the public key . The outputs are the signature and the registration information table. The specific process is as follows:
The end member first submits their unique identity identifier to the AA. Upon receiving the application, the AA will assign attributes to the end member, including the name of the attribute, its value, and the corresponding weight value, and categorize these attributes before securely transmitting them to the end member. Let us assume that for the end member , the corresponding unique identity identifier is , the possessed attribute set is , the corresponding attribute values are , and the corresponding attribute weights are , where , with denoting the sequence number of the end member and representing the number of attributes possessed by the -th end member. Then, the AA registers the assigned attributes in association with the unique identity identifier of the end member. To prevent impersonation by unauthorized individuals, this process is only conducted once.
After receiving the attribute information, the end member sends the attribute information and the unique identity identifier to the CA. Upon receiving the information, the CA registers it and generates a zero-knowledge proof of the private key for the end member using a non-interactive zero-knowledge proof protocol, which serves as identity verification prior to the data access process. The detailed process is as follows:
- i.
- Compute based on and from the public parameters:
- ii.
- Input the attribute values and the private key , then compute the following formula:
Finally, the proof is obtained and sent to the end member through a secure channel, along with the relevant parameters.
The process of the registration algorithm is as follows (Algorithm 2):
| Algorithm 2: |
| // Params: attribute values ; private key // Returns: proof function GenerateSignature(attribute_values [], publicKey ) → function GenerateProof(attribute values [], private key ) → proof 01: // Step (i): Compute T based on the public parameters p and q 02: 03: // Step (ii): Input attribute values and private key 04: // Compute the formula for F 05: F = empty set // Initialize F as an empty set 06: for each attribute value in : 07: // Compute 08: 09: // Square each to get 10: 11: // Add to the set F 12: 13: // Construct the proof 14: 15: return endfunction |
Based on the above process, the CA and AA complete the registration of all end members and establish a registry of end member information for easy querying of member details. The specific contents are shown in Table 4.

Table 4.
End member registration information table.
- (3)
- Encryption Algorithm
This algorithm is executed by the DO, who is an end member. The algorithm takes a message as input and the attribute corresponding weight values , and outputs the ciphertext . The specific process is as follows:
The DO first selects a random number from the group to be used as the symmetric encryption key. Let the symmetric encryption algorithm be denoted by , the DO encrypts the message to be shared by calculating , resulting in the symmetric encrypted ciphertext . The DO stores the ciphertext in IPFS, obtaining the data storage address , and then encrypts the symmetric key . The specific encryption process is as follows:
- i.
- The weight corresponding to the attribute set is , with the total weight denoted as . Randomly select prime numbers , which satisfy the relation . Let , then choose a random number in , and compute the following formula:
- ii.
- Set the attribute weight threshold value as , where . Let , and select an integer such that , then compute the following formula:
Then, the output ciphertext is:
The DO utilizes the regulatory node to store the ciphertext on the blockchain, simultaneously providing a brief description of the ciphertext. This is then associated with the relevant attribute categories and the data storage address.
The process of the encryption algorithm is as follows (Algorithm 3):
| Algorithm 3: |
| // Params: message M, attribute weights // Returns: ciphertext function EncryptMessageWithAttributes(char[] M, int[] ) → 01: // Select a random number from to be used as the symmetric encryption key 02: = selectRandom() 03: // Encrypt the message M with using symmetric encryption 04: = symmetricEncrypt() 05: // Store the encrypted message on IPFS and get the storage address 06: Address_ = IPFS.store() 07: // Step (i): Compute the sum of weights and select prime numbers to 08: 09: selectPrimes() 10: // Select a random number from 11: selectRandom() 12: // Encrypt using the formula given 13: 14: // Step (ii): Set the attribute weight threshold t and compute 15: product() // Product of the first t primes in 16: selectInteger(0, floor() 17: 18: // Construct the ciphertext 19: 20: // Store the ciphertext on the blockchain using a regulatory node 21: blockchain.store() 22: // Provide a description of the ciphertext, link it with the attribute category and data storage address 23: blockchain.associate(, “description”, “attribute category”, Address_) 24: return endfunction |
- (4)
- Authentication Algorithm
This algorithm is jointly executed by the DO and DV within the terminal member environment. The DV inputs their zero-knowledge proof , and the output is the authentication result and the data storage address . The specific process is as follows:
When a DV wishes to access the data , they need to obtain the access address of this data in the IPFS storage system. At this point, the DV needs to submit their zero-knowledge proof to the DO, proving their identity. Once verified, the DO then sends the data storage address to the DV. The detailed process is as follows:
- i.
- Based on the zero-knowledge proof ’s parameter , the DV generates a random parameter within the range and then calculates based on . The calculation formula is as follows:
- ii.
- The DO generates a random sequence and initiates an identity verification challenge to the DV.
- iii.
- Upon receiving the challenge, the DV calculates the response parameter using their private key and sends it to the DO. The specific formula for calculating is as follows:
- iv.
- The DO verifies using the zero-knowledge proof and response parameters , with the calculation formula as follows:
When the equation holds true, the identity verification of the DV is successful. The DO sends the data storage address, , to the DV and calculates the attribute permission parameters based on the DV’s weight values. If the equation does not hold, all operations are terminated.
- v.
- Once the DV’s authentication is successful, the DO calculates the attribute permission parameters based on DVs weight values. The specific calculation formula is as follows:
In the formula, represents the product of any distinct primes chosen from . After calculating the attribute permission parameter , it is sent to the DV along with the data storage address .
The process of the authentication algorithm is as follows (Algorithm 4):
| Algorithm 4: |
| // Params: Zero-knowledge proof // Returns: Authentication result and the data storage address Address() function Verify Access And Retrieve Data (proof ) → {Address_} 01: // Step (i) Generates a random parameter based on T from 02: = select Random From (T) 03: // Compute using 04: 05: // Step (ii) Generates a random sequence E and issues an identity challenge to the DV 06: . 07: sendChallenge (challenge) 08: // Step (iii) Computes the response parameters Res using their private key 09: 10: for j from 1 to r do: 11: 12: sendResponse (Res) // Send the response parameters Res to the DO 13: // Step (iv) Verifies the proof and the response parameter Res 14: 15: for j from 1 to r do: 16: 17: // Verify the equation 18: if : 19: authentication Result = true 20: sendAddress () // DO sends the data storage address to DV 21: // Step (v) Calculate attribute permission parameters based on the DV’s weight values 22: for j from 1 to do: 23: 24: 25: send Permission Parameters (, ) // Send attribute permission parameters and to DV 26: else: 27: authentication Result = false 28: // Terminate any further action if the equation does not hold 29: terminate () 30: // Return the authentication result 31: return {authentication Result} endfunction |
- (5)
- Decryption Algorithm
This algorithm is performed by the DV among end members. It takes the ciphertext and the data storage address as input, and outputs the plaintext . The specific process is as follows:
Based on the brief description of encrypted information by the DO in the blockchain, the DV quickly locates the ciphertext of the desired data in the blockchain. Then, using the obtained attribute permission parameters , the DV decrypts the ciphertext.
- i.
- The following formula is computed based on the attribute permission parameter:
Using the standard Chinese remainder theorem, a unique solution can be calculated:
where . After obtaining , the value of can be solved as .
- ii.
- Locate the symmetrically encrypted data using the data storage address and download it. Then, compute the following formula:
Finally, the desired data is obtained.
The process of the decryption algorithm is as follows (Algorithm 5):
| Algorithm 5: |
| // Params: ciphertext , attribute permission parameters , data storage address Address() // Returns: plaintext message function DecryptMessage ( Address_) → 01: // Retrieve encrypted data using the storage address from IPFS 02: IPFS.retrieve (Address_) 03: // Step (i): Compute μ using the attribute permission parameters 04: computeCRTSolution (, ) 05: // Reverse compute from 06: 07: // Step (ii): Decrypt using C from CT and β 08: publicParameters.u // u is obtained from the system’s public parameters 09: publicParameters. // is a generator of 10: 11: // Decrypt the message using symmetric decryption with 12: symmetricDecrypt () 13: return endfunction // Helper function to compute using Chinese Remainder Theorem and attribute permission parameters function computeCRTSolution (,) → int 01: product () // is the product of 02: 03: // Compute the sum for using the CRT formula 04: for to .length do 05: = modInverse () // Compute the modular inverse 06: 07: return endfunction |
4.4. Blockchain Network Creation and Smart Contract Definition
Considering the target application within the IIoT, where the information stored in the terminal devices is typically highly confidential, we have opted for Hyperledger Fabric, tailored for IioT scenarios, as the development platform. Within this framework, we have designed and deployed two types of smart contracts on the blockchain: static smart contracts and dynamic smart contracts. The static smart contracts primarily take charge of managing pertinent information within the system following the initiation of data sharing requests by members. This encompasses operations such as information querying, updating, and uploading. On the other hand, dynamic smart contracts are responsible for real-time monitoring of members’ operational behaviors and access privileges. This ensures that the data sharing process adheres to the predetermined rule policies, including the enactment and revocation of access permissions.
During node deployment, we positioned the CA node on an isolated host, disconnected from the external internet, thereby effectively shielding the system from unauthorized external access and enhancing the system’s security and trustworthiness. Concurrently, we deployed peer nodes on physical nodes with internet connectivity, ensuring not only the continuity and reliability of external services but also enabling the peer nodes to store smart contract codes and process data access requests. This setup fosters effective interaction between the external environment and the blockchain network. Additionally, we distributed orderer nodes across multiple physical nodes. Together with the other modules of Hyperledger Fabric, these nodes form a highly secure, reliable, and high-performance blockchain network. The core modules of Fabric are detailed in Table 5.

Table 5.
Core modules of fabric.
The specific process of creating a blockchain network is shown in Figure 4.
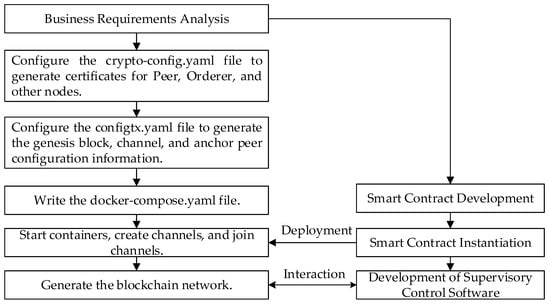
Figure 4.
Blockchain network creation process.
5. Scheme Analysis
In this section, we provide a detailed analysis of the correctness and security of the scheme. Initially, we verify the correctness of the scheme from both theoretical and practical application standpoints, ensuring its stable functionality under various conditions. Subsequently, we explore the security of the scheme, focusing on its privacy protection performance and potential security threats.
5.1. Correctness Analysis
The correctness of this scheme can be demonstrated through the following theorem.
Theorem 1.
Any legitimate end member in the system can prove their legitimacy and download the data resources they wish to access.
Proof of Theorem 1.
In the registration phase of the scheme, each end member is provided with zero-knowledge proof evidence . When a DV applies to a DO for data access, the DO, based on the pre-reserved evidence from the zero-knowledge proof, generates a random sequence and initiates a challenge. Upon receiving this challenge, the DV uses their private key to generate a response parameter and replies accordingly. Since the DV’s private key is kept secret, only the DV can generate the correct response parameter and provide valid proof of their identity. □
Assuming the DV possesses an attribute set with corresponding attribute values , then according to the non-interactive zero-knowledge proof protocol, the identity verification challenge posed by the DO expands from one bit to bits for each session, assuming the challenge process is repeated for rounds. In a one-bit challenge, the probability of the DV correctly guessing is . Therefore, at the end of the challenge, the probability of an impostor DV successfully deceiving the DO is only . When is sufficiently large, approaches zero.
Therefore, any legitimate end member in the system can prove their legitimacy based on the zero-knowledge proof pre-evidence and private key generated for them by the CA institution during the registration process. Once the identity of the DV is verified, the DO sends them the data storage address and calculates the attribute permission parameters based on the weight values of the DV. The DV can then locate the ciphertext of the data resource they wish to access in the IPFS storage system using the storage address and compute the decryption key based on the attribute permission parameters, ultimately obtaining access to the desired data resource.
Theorem 2.
In the system, any end member whose sum of attribute permission values is greater than or equal to the threshold value set during encryption can calculate the decryption key and access the corresponding ciphertext resource.
Proof of Theorem 2.
After the identity of the DV is verified, the DO calculates the attribute permission parameter based on the DV’s weight values. The DV then uses the attribute permission parameter to calculate the decryption key during the decryption phase. When the sum of the attribute permission values possessed by the DV reaches the threshold, , the system of Equation (13) satisfies the congruence . According to the generalized Chinese remainder theorem, Equation (11) has a unique solution within the range , which is . Thus, can be solved. □
Therefore, in the system, any end member whose sum of attribute permission values is greater than or equal to the threshold value set during encryption can calculate the unique solution , that is, , based on the attribute permission parameter generated during the authentication phase, and subsequently solve for . Then, using the ciphertext , the symmetric encryption/decryption key can be calculated as . Following this, the desired data can be computed using the decryption algorithm .
5.2. Security Analysis
Theorem 3.
Any legitimate end member in the system can anonymously access data resources without revealing their identity.
Proof of Theorem 3.
During the registration phase, the CA institution generates zero-knowledge proof evidence based on the private key of the end member . In the authentication phase, the DV only needs to present the evidence , allowing the DO to generate a random sequence based on the parameter in the proof and initiate an identity verification challenge to the DV. Upon receiving the challenge, the DV merely needs to compute the response parameter using their private key and reply to the DO. The DO can then determine whether the DV possesses the corresponding private key by checking if the equation holds true based on the zero-knowledge proof evidence and the response parameter . Throughout this process, the DV does not need to disclose their real identity while still being able to verify their legitimacy. At the same time, impostor members without the correct private key cannot compute the correct response parameter . Since solving is equivalent to factoring , and large integer factorization is a known difficult problem, it is unlikely to be feasible. □
Therefore, any legitimate end member in the system can securely prove the legitimacy of their identity without revealing their own identity, using the non-interactive zero-knowledge proof protocol. They can anonymously access the data resources in the system, ensuring the privacy of their identity with good anonymity.
Theorem 4.
In the system, when the sum of the attribute permission values possessed by the DV is less than the threshold value set by the DO during encryption, the DV cannot access the data resources shared by the DO.
Proof of Theorem 4.
After the identity of the DV is verified, the DO calculates the attribute permission parameter based on the data visitor’s weight values. The DV then computes the decryption key during the decryption phase using the attribute permission parameter they possess. When the sum of the attribute permission values held by the DV is less than the threshold value, holds. According to the generalized Chinese remainder theorem, the solution derived from Equation (16) is uniformly distributed across all congruence classes modulo , meaning that although Equation (16) has solutions, they are not unique, and the solution cannot be determined. Even if the congruence is satisfied, there isn’t enough information to determine the value of , and no secret information can be obtained. □
Therefore, in the system, any end member whose sum of attribute permission values is less than the threshold value set during encryption cannot calculate the unique solution , that is, , based on the attribute permission parameter generated during the authentication phase, and subsequently, they cannot solve for . As a result, they also cannot compute the symmetric encryption/decryption key using the ciphertext . Even if they obtain the data storage address , they cannot calculate the data they wish to access.
6. Performance Analysis
In this section, we conduct a comprehensive evaluation of the proposed scheme’s performance, encompassing both theoretical and experimental aspects. The theoretical analysis primarily involves a comparative study of several relevant algorithms and a deep analysis of computational costs. Building on this, we designed and implemented a series of experiments to further validate the accuracy of the theoretical analysis and the practical performance of the scheme. This combination of theoretical and experimental approaches makes our analysis more comprehensive, ensuring the effectiveness and advancement of the scheme.
6.1. Theoretical Analysis
6.1.1. Algorithm Characteristics Comparison
The data sharing scheme presented in this paper has been compared with the schemes in references [25,26,29,30,31] in terms of blockchain structure, identity authentication, privacy protection, combinational permission, and off-chain storage. The results of this comparison are shown in Table 6.

Table 6.
Comparison of characteristics of various data sharing schemes.
Through comparative analysis with the relevant literature, it has been observed that existing data sharing schemes for the Industrial Internet of Things (IIoT) still possess certain flaws.
Zhang A et al. designed a secure and privacy-preserving sharing mechanism for personal health information in electronic health systems, referred to as BSPP, based on blockchain technology. This scheme established two types of blockchains with specific data structures and consensus mechanisms: a private blockchain for storing personal health information and a consortium blockchain for managing secure indices of this information. However, this scheme lacks identity authentication and the capability for flexible combination of permissions. As a result, its applicability is quite limited and it falls short in terms of security.
Xue Y et al. proposed an attribute-based access control mechanism for data security and access control in public cloud storage environments, referred to as ABCCACS. This mechanism allows for more flexible and finer-grained access control policies, ensuring that only users with specific attributes or conditions can access the encrypted data stored in the cloud. However, the scheme does not verify the identity of users during data sharing, and only encrypts user information. Without authenticating the identities of end members in the system, the scheme cannot effectively prevent unauthorized access.
Zhang Q et al. proposed an access control scheme based on ciphertext-attribute authentication and threshold policies, referred to as AC-CAATP. This scheme employs hidden attribute-based identity authentication and divides permission levels through threshold functions set on user attributes. Users, based on the results of attribute verification, obtain varying levels of permissions, enabling access to data of different sensitivity levels on cloud servers. However, this scheme does not protect user information privacy during identity authentication, leading to the exposure of personal user information.
Liu H et al. proposed a lightweight non-interactive zero-knowledge proof protocol for verifying the existence of user private keys. This protocol allows the transmission of ciphertexts only after successful validation of the user’s private key. This effectively resolves the issue of high bandwidth usage in traditional CP-ABE systems, which is caused by unauthorized or invalid encryption data requests. However, in this scheme, attributes cannot be freely combined, and it involves directly storing encrypted data on the blockchain, increasing the storage burden.
Xu G et al. proposed a new medical data sharing scheme named PPMDS, which incorporates a blockchain-based authorization mechanism and attribute-based encryption algorithms to break system boundaries and enable data sharing among multiple medical institutions. However, this scheme lacks flexibility as it does not support the free combination of attributes in the process of data access control using attribute-based encryption.
Furthermore, the aforementioned schemes do not incorporate searchable capabilities, presenting limitations in retrieving and quickly locating specific data stored within the system. In response to the issues identified in existing data sharing schemes, our solution employs weighted threshold secret sharing technology to improve the data sharing mechanism, enhancing the flexibility and autonomy in permission configuration, making the data sharing process in the IIoT more adaptable. Additionally, the scheme utilizes non-interactive zero-knowledge proof protocols for preliminary authentication of data accessors, effectively preventing unauthorized user intrusion. Moreover, our solution adopts the IPFS distributed storage system to store encrypted resources, recording only storage addresses on the blockchain, significantly reducing the storage load. In summary, our solution addresses the deficiencies of existing schemes in several key areas, including blockchain architecture, identity authentication, privacy protection, flexible combination of permissions, off-chain storage, and fine-grained access control.
6.1.2. Computational Cost Analysis
In data sharing schemes, the computationally intensive operations include hash function computations, bilinear pairing computations, and exponentiation operations, while the computational costs of simple addition and multiplication operations can be negligible. To understand the computational complexity of the aforementioned schemes more clearly, a comparison of computational costs in the key generation phase, authentication phase, encryption phase, and decryption phase between our scheme and five other schemes is made, providing a theoretical basis for further analyzing the computational overhead. Assuming that there are end members participating in the data sharing process in the system, represents the computational cost of hash function operations, represents the computational cost of bilinear pairing operations, and represents the computational cost of exponentiation or modular exponentiation operations. represents the average number of attributes owned by end members and represents the average number of attributes used by DVs for decrypting ciphertext. The comparison of computational costs in the key generation phase, authentication phase, encryption phase, and decryption phase between our scheme and the other five schemes is shown in Table 7, where the key generation phase includes the initialization and registration stages of our scheme and the other schemes.

Table 7.
Comparison of computational costs between our scheme and four others.
As indicated in Table 6, during the key generation phase the computational requirements of BSPP, ABCCACS, AC-CAATP, and ZK-CP-ABE are significantly greater than those of the proposed method. Furthermore, their computational demands increase linearly with the number of attributes held by end members. During the authentication phase, the computational demand of the proposed scheme is minimal when dealing with a small number of attribute values. As the attribute values increase, the computational requirements of this scheme show a linear growth and exceed that of other schemes. This is because the scheme employs a non-interactive zero-knowledge proof protocol. This protocol is used to generate zero-knowledge proofs of private keys for end members, thus ensuring their privacy is maintained throughout the authentication process. During the encryption and decryption phases, the proposed scheme requires the least computational resources when dealing with a small number of attribute values. As the number of attributes increases, the computational demand of this scheme becomes slightly higher than that of ZK-CP-ABE but remains lower than the other four methods. This is because the scheme, by characterizing and assigning values to attributes, achieves a flexible combination of permissions. This allows end members to access system data both flexibly and securely, a feature not realized by the ZK-CP-ABE approach.
6.2. Experimental Analysis
6.2.1. Computational Analysis of Blockchain Operations
To evaluate the blockchain performance utilized in this study, we employed Caliper to test the write and read capabilities of the blockchain. The write operation refers to the DO writing data to the blockchain, which was conducted across four sets of tests. Each set simulated 1500 executions, varying the transaction submission rate. The submission speeds were set at 60 TPS (transactions per second), 90 TPS, 120 TPS, and 150 TPS, respectively. The read operation involves the DV reading data from the blockchain, repeating the procedure. The results of the blockchain system’s write and read throughput tests are presented in Table 8 and Table 9, respectively.

Table 8.
Results of the write operation performance tests in the blockchain system.

Table 9.
Results of the read operation performance tests in the blockchain system.
Based on the test results, the following conclusions are drawn:
- (1)
- The blockchain is capable of processing transactions with a 100% success rate for both write and read operations.
- (2)
- The throughput for write operations approximates the sending rate when it is below 90 TPS. When the sending rate exceeds 90 TPS, the throughput reaches its peak and latency increases sharply, indicating that the limiting sending rate for write operations is 90 TPS.
- (3)
- The throughput for read operations approximates the sending rate when it is below 120 TPS. When the sending rate exceeds 120 TPS, the throughput peaks and latency increases sharply, suggesting that the limiting sending rate for read operations is 120 TPS.
- (4)
- Overall, the average latency for write operations is significantly greater than for read operations, with write operations also exhibiting a higher average delay compared to read operations.
6.2.2. Computational Analysis of the BBDSPP Scheme
To further substantiate the theoretical analysis of each scheme, we conducted simulation tests using a laptop equipped with an i7 7500 u 3.0 GHz processor, 16 GB RAM, and 256 GB storage (Intel, Santa Clara, CA, USA), within a Python 3.12 software environment. To ensure the same level of security strength, the order of the bilinear group is chosen as a 512-bit large prime number, and the order of the bilinear group is selected as a 256-bit large prime number. Multiple operations are conducted, and the average values are taken as the final results. The average time for one hash function operation is approximately 0.00052 ms. The average time for one bilinear pairing operation is about 5.4005 ms, and the average time for one exponentiation or modular exponentiation operation is 2.1875 ms. Four different sets of attribute numbers possessed by end members are set, namely 5, 10, 15, and 20, to compare the time consumption in the four phases of key generation, authentication, encryption, and decryption. The specific time consumption comparison charts are shown in Figure 5, Figure 6, Figure 7 and Figure 8 and the specific values are detailed in Table 10, Table 11, Table 12 and Table 13.
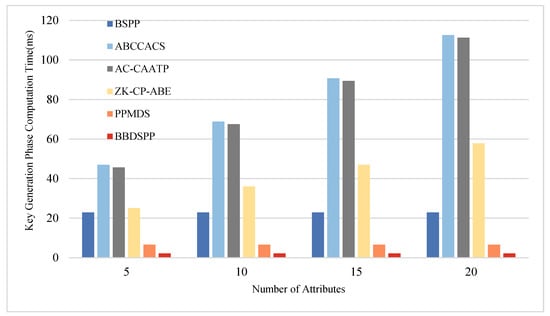
Figure 5.
Comparative analysis of computational time in the key generation phase.
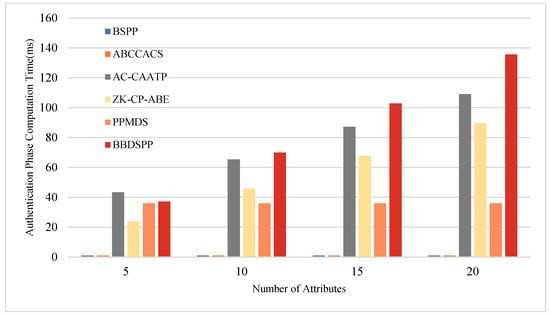
Figure 6.
Comparative analysis of computational time in the authentication phase.
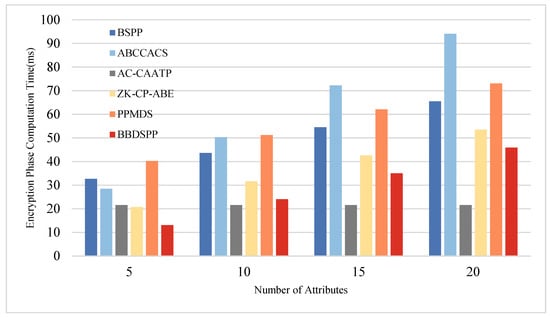
Figure 7.
Comparative analysis of computational time in the encryption phase.
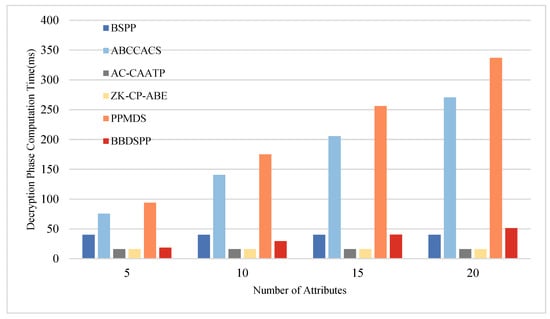
Figure 8.
Comparative analysis of computational time in the decryption phase.

Table 10.
Calculation time result of key generation stage.

Table 11.
Calculation time result of authentication phase.

Table 12.
Calculation time result of encryption phase.

Table 13.
Calculation time result of decryption phase.
During the key generation phase, the computational requirements of BSPP, ABCCACS, AC-CAATP, ZK-CP-ABE, and PPMDS significantly exceed those of our scheme. Moreover, as the number of attributes possessed by terminal members increases, their computational demands increase linearly. This indicates that in terms of key generation, our scheme has an advantage in efficiency, especially when the terminal members have a large number of attributes, resulting in lower computational overhead compared to other schemes.
During the authentication phase, AB-CCACS and ZK-CP-ABE lack an authentication process, resulting in a computational load of zero. When the number of attributes exceeds 10, the computational load of the scheme proposed in this paper is higher than that of the other four schemes. This is attributed to the fact that, in the authentication phase, our scheme generates a zero-knowledge proof for terminal members using attribute values, a process that leads to increased computational overhead with a larger number of attributes.
During the encryption phase, the computational load of the scheme presented in this paper is the lowest when the number of attributes is less than 10. However, when the number of attributes exceeds 10, the computational load of our scheme is only higher than that of AC-CAATP. This indicates that the scheme proposed in this paper is more efficient when dealing with a smaller number of attributes.
During the decryption phase, the computational load of the scheme proposed in this paper is slightly higher than that of AC-CAATP and ZK-CP-ABE. However, the increase in computational load is relatively small as the number of attributes possessed by the terminal members grows. This suggests that when dealing with a larger number of at-tributes, our scheme maintains a certain level of computational efficiency in processing decryption operations, being only marginally higher than certain other schemes.
To facilitate a more direct and visual comparison of the computational costs of our scheme against others, we calculated the total time across all stages for attribute values of 5, 10, 15, and 20, and conducted a comparative analysis. The specific comparison of time consumption is depicted in the line chart in Figure 9, with detailed numerical values provided in Table 14.
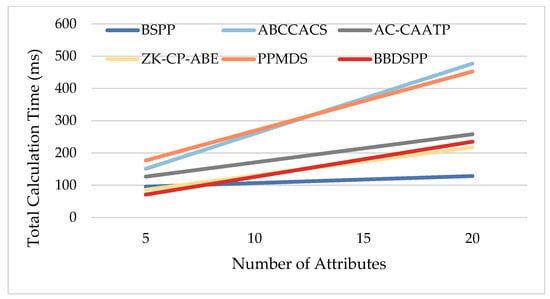
Figure 9.
Comparative analysis of total calculation time for each scheme.

Table 14.
Calculation time result of total calculation time for each scheme.
From the above charts, it is evident that the total computational load of the BBDSPP scheme is consistently lower than that of ABCCACS, AC-CAATP, and PPMDS. It is slightly higher than ZK-CP-ABE when the attribute value exceeds 10. This is because our scheme employs a non-interactive zero-knowledge proof protocol to generate zero-knowledge proofs of private keys for terminal members and characterizes attribute values to realize flexible combination of permissions. This enables terminal members to access system data flexibly and securely. ZK-CP-ABE does not implement this feature. Since the BSPP lacks an identity authentication function, its total computation time is always lower than that of the BBDSPP scheme. In summary, by comparing the computational consumption of various schemes through simulation experiments, it is evident that the scheme proposed in this paper not only addresses the deficiencies of existing schemes but also demonstrates comparable or superior performance in terms of computational consumption, further validating the feasibility of our scheme.
7. Conclusions
In response to the issues of complex communication processes, poor flexibility, and low security in traditional data sharing models of the IIoT, we propose the BBDSPP scheme. Initially, we assign values to attributes based on their characteristics and utilize a weighted threshold secret sharing scheme to improve the data sharing process. This approach facilitates a data sharing access control mechanism that allows for the free combination of permissions. Terminal members can freely choose the attributes to decrypt. As long as the attribute values meet the preset access threshold, they can decrypt and access specific data. This not only ensures the flexibility of data sharing but also guarantees stringent control over data access.
Additionally, we employ non-interactive zero-knowledge proof protocols to pre-authenticate the identities of data accessors, preventing illegal members from impersonating and stealing sensitive data. This not only protects the privacy of terminal members but also avoids the extra computational burden caused by illegal access. It ensures that only legitimate and authorized terminal members can access data in the system, effectively preventing unauthorized access and leakage of sensitive information.
Furthermore, we utilize the IPFS distributed storage system to store encrypted shared resources. By storing a large amount of data on IPFS and only keeping corresponding storage addresses on the blockchain, we effectively resolve the storage efficiency issues prevalent in traditional blockchain applications. This approach not only ensures the security and integrity of data but also significantly enhances the efficiency of data retrieval and the scalability of the system.
Finally, we analyzed the correctness and security of the proposed solution, conducted a theoretical analysis of the solution’s functional characteristics and computational costs, and designed experiments for validation. The results show that the BBDSPP scheme can address the deficiencies in existing solutions in several key areas such as identity authentication, privacy protection, flexible combination of permissions, and off-chain storage, while also maintaining good performance and demonstrating strong feasibility.
However, the BBDSPP scheme still has some potential limitations and areas for improvement. For instance, scalability for large-scale IIoT systems and feasibility of practical deployment require further study. Additionally, performance metrics of the BBDSPP scheme in terms of privacy protection and data security need further optimization. Therefore, future work will focus on addressing these issues and further refining and improving the BBDSPP scheme.
Author Contributions
Conceptualization, W.T. and L.Y.; methodology, W.T. and L.Y.; software, W.T. and L.Y.; validation, L.T., L.Y. and Z.L.; formal analysis, X.J.; investigation, W.T.; resources, Z.L.; data curation, W.T. and L.Y.; writing—original draft preparation, W.T. and L.Y.; writing—review and editing, W.T. and L.Y.; visualization, L.T., Z.L. and X.J.; supervision, Z.L. and X.J.; project administration, W.T.; funding acquisition, W.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by three projects. The first project is the Heilongjiang Province Key Research and Development Program, with the grant number 2023ZX01A12, titled “Research on Communication Performance Enhancement and Predictive Maintenance of Industrial Control Systems Based on Industrial Internet and Knowledge Graph”. The second project is also the Heilongjiang Province Key Research and Development Program, with the grant number 2022ZX01A16, titled “Research on Real-Time Assessment Methods for Industrial Equipment Condition Based on Edge Computing”. The third project is funded by the Harbin Science and Technology Innovation Talent Funds, with the grant number CXRC20231112683, titled “Research on Predictive Maintenance Technology for Space Environment Ground Simulation Devices Based on Blockchain and Knowledge Graph”.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All data are available from the corresponding author upon request.
Acknowledgments
This study was supported by two Heilongjiang Province Key Research and Development Programs and the Harbin Science and Technology Innovation Talent Funds. We extend our sincere gratitude for their support. The contributions of these funding bodies have been instrumental to the success of our research.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Zhao, Q. Presents the technology, protocols, and new innovations in Industrial Internet of Things (IIoT). In Internet of Things for Industry 4.0: Design, Challenges and Solutions; Springer: Cham, Switzerland, 2020; pp. 39–56. [Google Scholar]
- Younan, M.; Houssein, E.H.; Elhoseny, M.; Ali, A.A. Challenges and recommended technologies for the industrial internet of things: A comprehensive review. Measurement 2020, 151, 107198. [Google Scholar] [CrossRef]
- Yang, L.; Zou, W.; Wang, J.; Tang, Z. EdgeShare: A blockchain-based edge data-sharing framework for Industrial Internet of Things. Neurocomputing 2022, 485, 219–232. [Google Scholar] [CrossRef]
- Kumar, R.; Agrawal, N. Analysis of multi-dimensional Industrial IoT (IIoT) data in Edge-Fog-Cloud based architectural frameworks: A survey on current state and research challenges. J. Ind. Inf. Integr. 2023, 35, 100504. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Bit, S.D. A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Khan, W.; Rehman, M.; Zangoti, H.; Afzal, M.; Armi, N.; Salah, K. Industrial internet of things: Recent advances, enabling technologies and open challenges. Comput. Electr. Eng. 2020, 81, 106522. [Google Scholar] [CrossRef]
- Tan, S.F.; Samsudin, A. Recent technologies, security countermeasure and ongoing challenges of Industrial Internet of Things (IIoT): A survey. Sensors 2021, 21, 6647. [Google Scholar] [CrossRef] [PubMed]
- Gebremichael, T.; Ledwaba, L.P.I.; Eldefrawy, M.H.; Hancke, G.P.; Pereira, N.; Gidlund, M.; Akerberg, J. Security and privacy in the industrial internet of things: Current standards and future challenges. IEEE Access 2020, 8, 152351–152366. [Google Scholar] [CrossRef]
- Ke, T.T.; Sudhir, K. Privacy rights and data security: Gdpr and personal data markets. Manag. Sci. 2023, 69, 4389–4412. [Google Scholar] [CrossRef]
- Roman, D.H.; Conlee, K.D.; Abbott, I.; Jones, R.P.; Noble, A.; Rich, N.; Ro, I.; Kaufman, J.; Weikert, R.; Costa, D. The digital revolution comes to US healthcare. Internet Things 2015, 5, 1–54. [Google Scholar]
- Sukiasyan, A.; Badikyan, H.; Pedrosa, T.; Leitao, P. Secure data exchange in Industrial Internet of Things. Neurocomputing 2022, 484, 183–195. [Google Scholar] [CrossRef]
- Sharif, M.H.U.; Mohammed, M.A. A literature review of financial losses statistics for cyber security and future trend. World J. Adv. Res. Rev. 2022, 15, 138–156. [Google Scholar] [CrossRef]
- Akinyede, J.; Ponnle, A.; Olebu, C.; Akinluyi, F.; Thompson, A.; Dahunsi, O.; Alese, B.; Oyinloye, M. Development of a Software System for Realtime Management of Crime Reports in Southwestern Nigeria: The Administrative Approach. Am. J. Sci. Eng. Technol. 2023, 8, 23–32. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.; Page, K.; Nurse, J.R.C.; Montalvo, R.M.; Santos, O.; Maddox, L.; Burnap, P. Cyber risk at the edge: Current and future trends on cyber risk analytics and artificial intelligence in the industrial internet of things and industry 4.0 supply chains. Cybersecurity 2020, 3, 1–21. [Google Scholar]
- Gajek, S.; Lees, M.; Jansen, C. IIoT and cyber-resilience: Could blockchain have thwarted the Stuxnet attack? AI Soc. 2021, 36, 725–735. [Google Scholar] [CrossRef]
- Sui, T.; Mo, Y.; Marelli, D.; Sun, X.-M.; Fu, M. The vulnerability of cyber-physical system under stealthy attacks. IEEE Trans. Autom. Control 2020, 66, 637–650. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Pirbhulal, S.; Muzammal, M.; Zongwei, L. Towards blockchain-enabled security technique for industrial internet of things based decentralized applications. J. Grid Comput. 2020, 18, 615–628. [Google Scholar] [CrossRef]
- Dixit, A.; Singh, A.; Rahulamathavan, Y.; Rajarajan, M. Fast data: A fair, secure and trusted decentralized iiot data marketplace enabled by blockchain. IEEE Internet Things J. 2021, 10, 2934–2944. [Google Scholar] [CrossRef]
- Khan, A.A.; Laghari, A.A.; Shaikh, Z.A.; Dacko-Pikiewicz, Z.; Kot, S. Internet of Things (IoT) Security With Blockchain Technology: A State-of-the-Art Review. IEEE Access 2022, 10, 122679–122695. [Google Scholar] [CrossRef]
- Yaqoob, I.; Salah, K.; Jayaraman, R.; Al-Hammadi, Y. Blockchain for healthcare data management: Opportunities, challenges, and future recommendations. Neural Comput. Appl. 2021, 34, 11475–11490. [Google Scholar] [CrossRef]
- Khan, D.; Jung, L.T.; Hashmani, M.A. Systematic literature review of challenges in blockchain scalability. Appl. Sci. 2021, 11, 9372. [Google Scholar] [CrossRef]
- Selvarajan, S.; Srivastava, G.; Khadidos, A.O.; Khadidos, A.O.; Baza, M.; Alshehri, A.; Lin, J.C.-W. An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems. J. Cloud Comput. 2023, 12, 38. [Google Scholar] [CrossRef]
- Huo, R.; Zeng, S.; Wang, Z.; Shang, J.; Chen, W.; Huang, T.; Wang, S.; Yu, F.R.; Liu, Y. A comprehensive survey on blockchain in industrial internet of things: Motivations, research progresses, and future challenges. IEEE Commun. Surv. Tutor. 2022, 24, 88–122. [Google Scholar] [CrossRef]
- Liu, C.H.; Lin, Q.; Wen, S. Blockchain-enabled data collection and sharing for industrial IoT with deep reinforcement learning. IEEE Trans. Ind. Inform. 2018, 15, 3516–3526. [Google Scholar] [CrossRef]
- Xue, Y.; Xue, K.; Gai, N.; Hong, J.; Wei, D.S.L.; Hong, P. An attribute-based controlled collaborative access control scheme for public cloud storage. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2927–2942. [Google Scholar] [CrossRef]
- Liu, H.; Han, D. Non-interactive Zero Knowledge Proof Based Access Control in Information-Centric Internet of Things. In Proceedings of the International Conference on Algorithms and Architectures for Parallel Processing, Cham, Switzerland, 3–5 December 2021. [Google Scholar]
- Li, J.; Qiao, Z.; Peng, J. Asymmetric group key agreement protocol based on blockchain and attribute for industrial internet of things. IEEE Trans. Ind. Inform. 2022, 18, 8326–8335. [Google Scholar] [CrossRef]
- Chen, C.-L.; Yang, J.; Tsaur, W.-J.; Weng, W.; Wu, C.-M.; Wei, X. Enterprise data sharing with privacy-preserved based on hyperledger fabric blockchain in IIOT’s application. Sensors 2022, 22, 1146. [Google Scholar] [CrossRef]
- Xu, G.; Qi, C.; Dong, W.; Gong, L.; Liu, S.; Chen, S.; Liu, J.; Zheng, X. A privacy-preserving medical data sharing scheme based on blockchain. IEEE J. Biomed. Health Inform. 2022, 27, 698–709. [Google Scholar] [CrossRef]
- Zhang, A.; Lin, X. Towards secure and privacy-preserving data sharing in e-health systems via consortium blockchain. J. Med. Syst. 2018, 42, 140. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Q.; Li, Y.; Li, Z.; Yuan, J.; Gan, Y.; Luo, X. Access control based on ciphertext attribute authentication and threshold policy for the internet of things. Sensors 2019, 19, 5237. [Google Scholar] [CrossRef] [PubMed]
- Li, T.; Wang, H.; He, D.; Yu, J. Permissioned blockchain-based anonymous and traceable aggregate signature scheme for industrial internet of things. IEEE Internet Things J. 2020, 8, 8387–8398. [Google Scholar] [CrossRef]
- Qi, S.; Lu, Y.; Zheng, Y.; Li, Y.; Chen, X. Cpds: Enabling compressed and private data sharing for industrial Internet of Things over blockchain. IEEE Trans. Ind. Inform. 2020, 17, 2376–2387. [Google Scholar] [CrossRef]
- Deebak, B.D.; Memon, F.H.; Khowaja, S.A.; Dev, K.; Wang, W.; Qureshi, N.M.F.; Su, C. A Lightweight Blockchain-Based Remote Mutual Authentication for AI-Empowered IoT Sustainable Computing Systems. IEEE Internet Things J. 2022, 10, 6652–6660. [Google Scholar] [CrossRef]
- Wang, Y.; Che, T.; Zhao, X.; Zhou, T.; Zhang, K.; Hu, X. A blockchain-based privacy information security sharing scheme in Industrial Internet of Things. Sensors 2022, 22, 3426. [Google Scholar] [CrossRef]
- Liu, Y.H.; Chen, R.J. An asymptotically perfect secret sharing scheme based on the Chinese Remainder Theorem. Int. J. Comput. Math. 2017, 94, 1890–1915. [Google Scholar] [CrossRef]
- Chattopadhyay, A.K.; Saha, S.; Nag, A.; Nandi, S. Secret sharing: A comprehensive survey, taxonomy and applications. Comput. Sci. Rev. 2024, 51, 100608. [Google Scholar] [CrossRef]
- Ji, Y.; Xiao, Y.; Gao, B.; Zhang, R. Threshold/Multi Adaptor Signature and Their Applications in Blockchains. Electronics 2023, 13, 76. [Google Scholar] [CrossRef]
- Smart, N.P.; Smart, N.P. Zero-knowledge proofs. In Cryptography Made Simple; Springer: Cham, Switzerland, 2016; pp. 425–438. [Google Scholar]
- Partala, J.; Nguyen, T.H.; Pirttikangas, S. Non-interactive zero-knowledge for blockchain: A survey. IEEE Access 2020, 8, 227945–227961. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).