A Review of Asynchronous Byzantine Consensus Protocols
Abstract
1. Introduction
2. Consensus Fundamentals
2.1. Overview of Consensus
2.2. Network Communication Models and Their Corresponding Consensus Protocols
2.2.1. Synchronous Model
2.2.2. Partially Synchronous Model
2.2.3. Asynchronous Model
2.3. Byzantine Generals Problem
2.4. A Brief Literature Review of Partially Synchronous Consensus Protocols
2.5. Summary
3. Asynchronous Byzantine Consensus Protocols and Their Classification
4. Asynchronous Byzantine Consensus Protocols
4.1. DAG-Based Asynchronous Byzantine Consensus Protocols
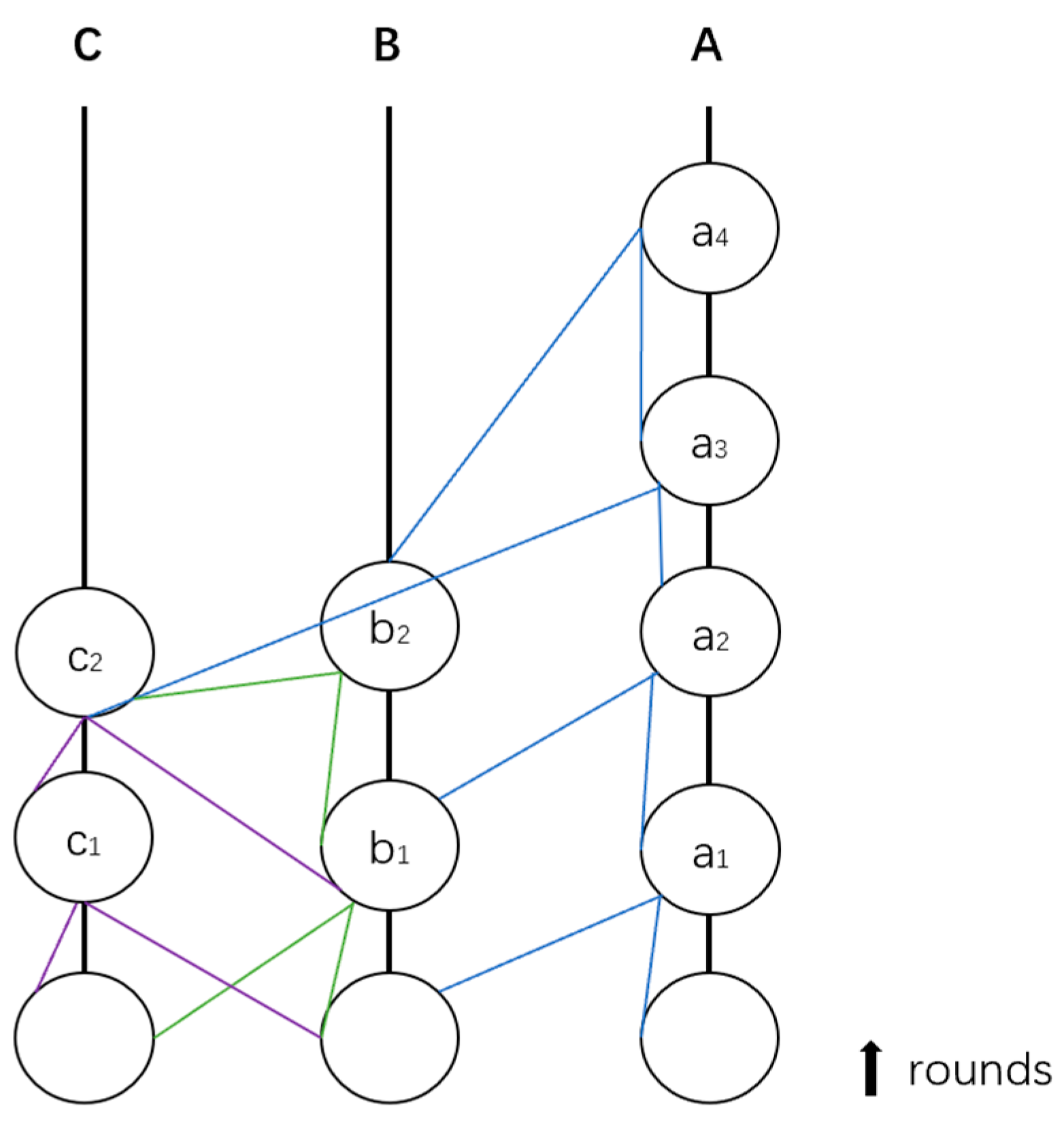
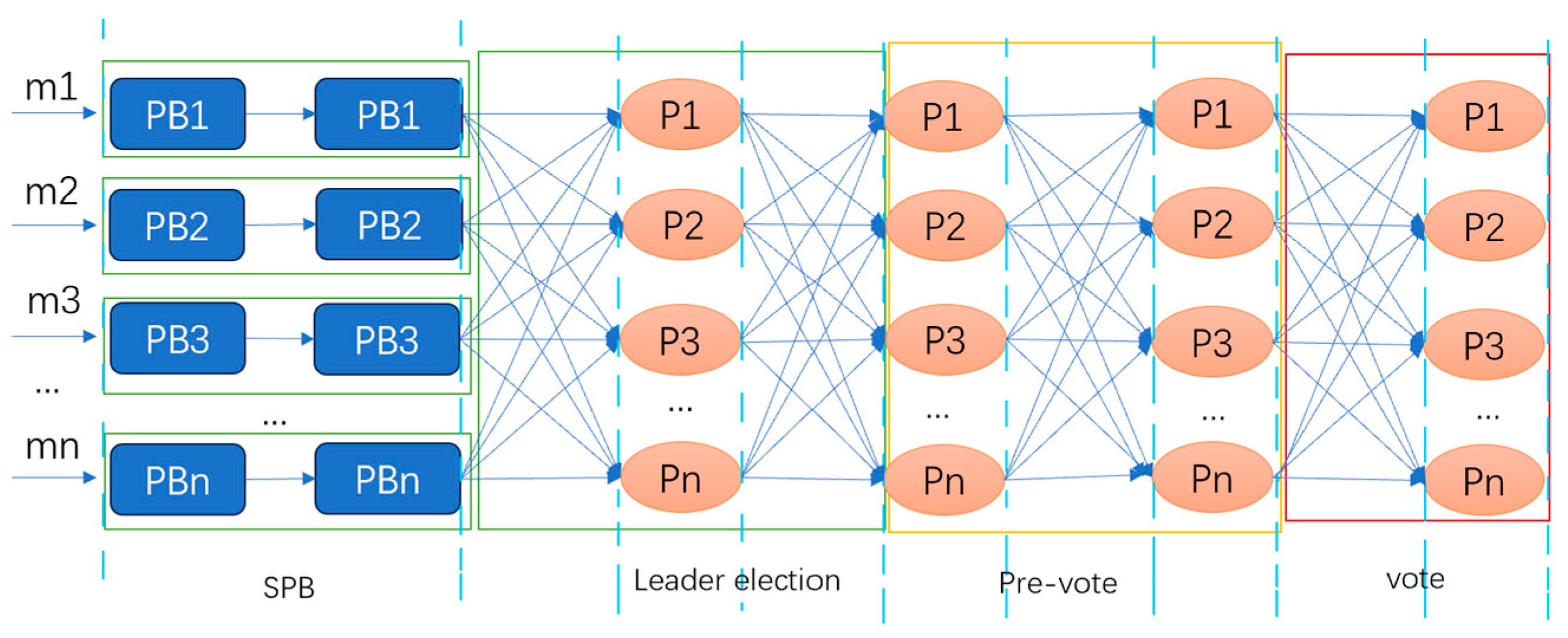
4.1.1. Hashgraph
4.1.2. DAG-Rider
4.1.3. Tusk
4.1.4. Bullshark
4.1.5. Summary
4.2. Asynchronous Byzantine Consensus Protocols Based on ACS Structure
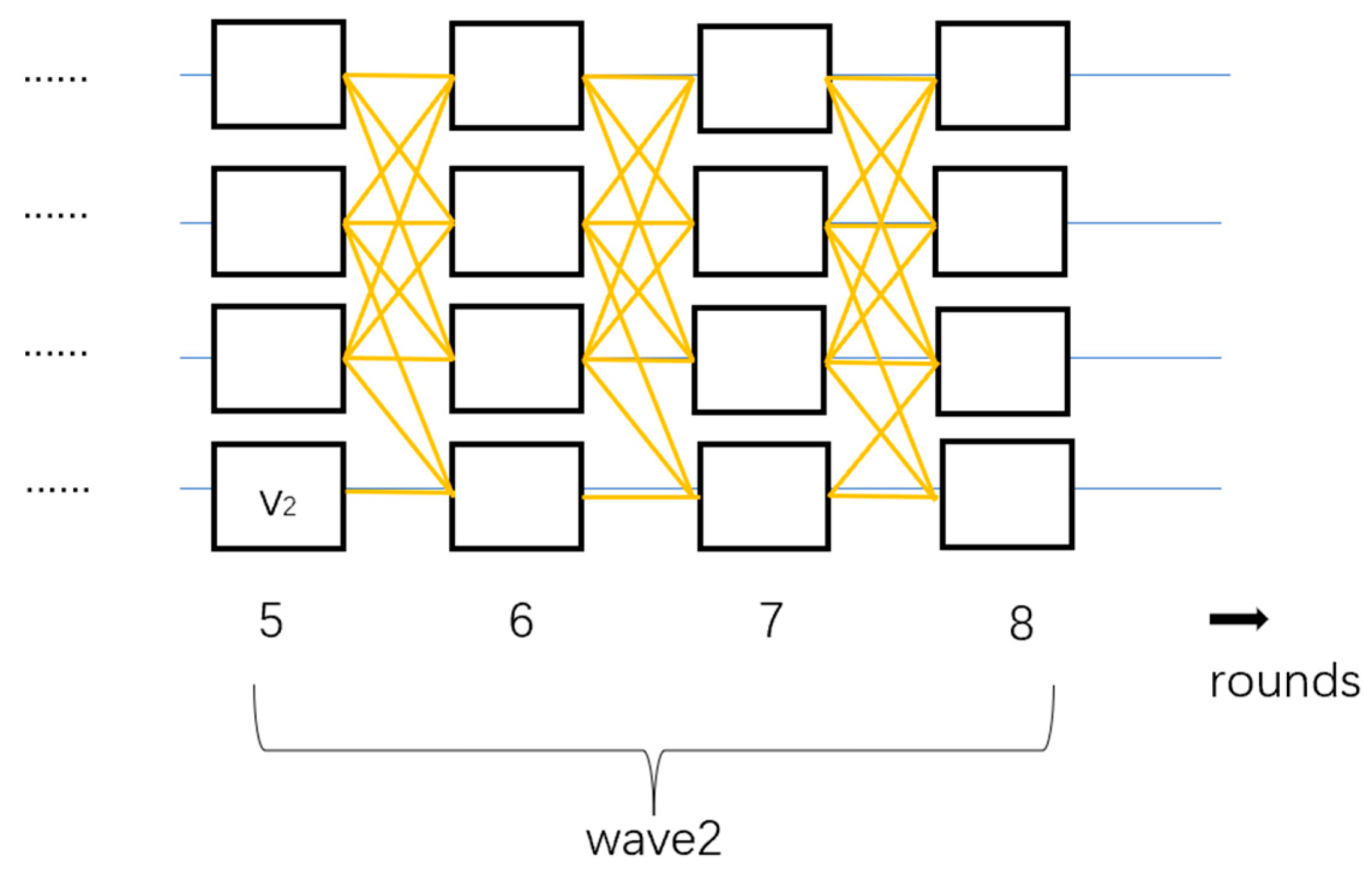
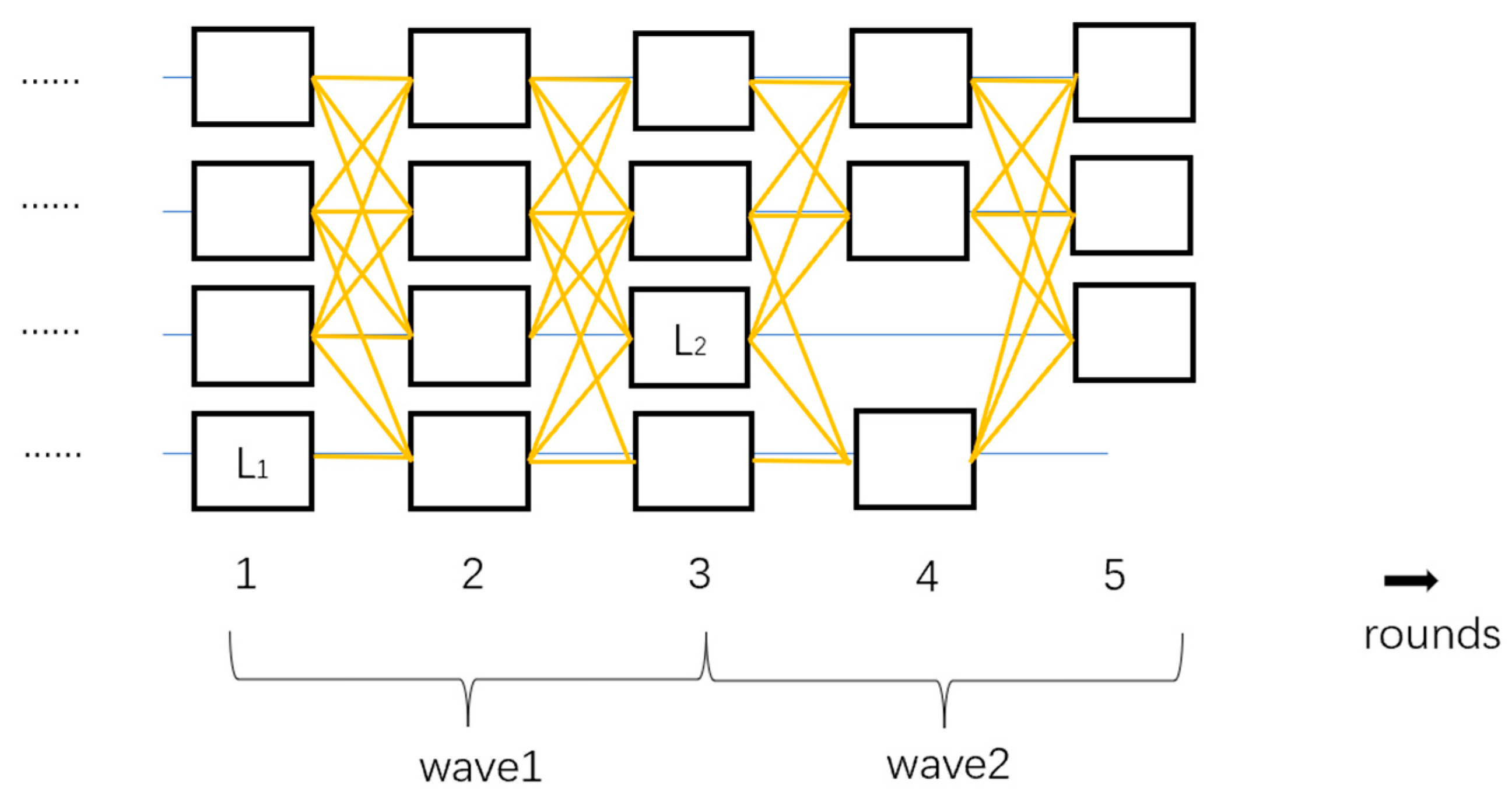
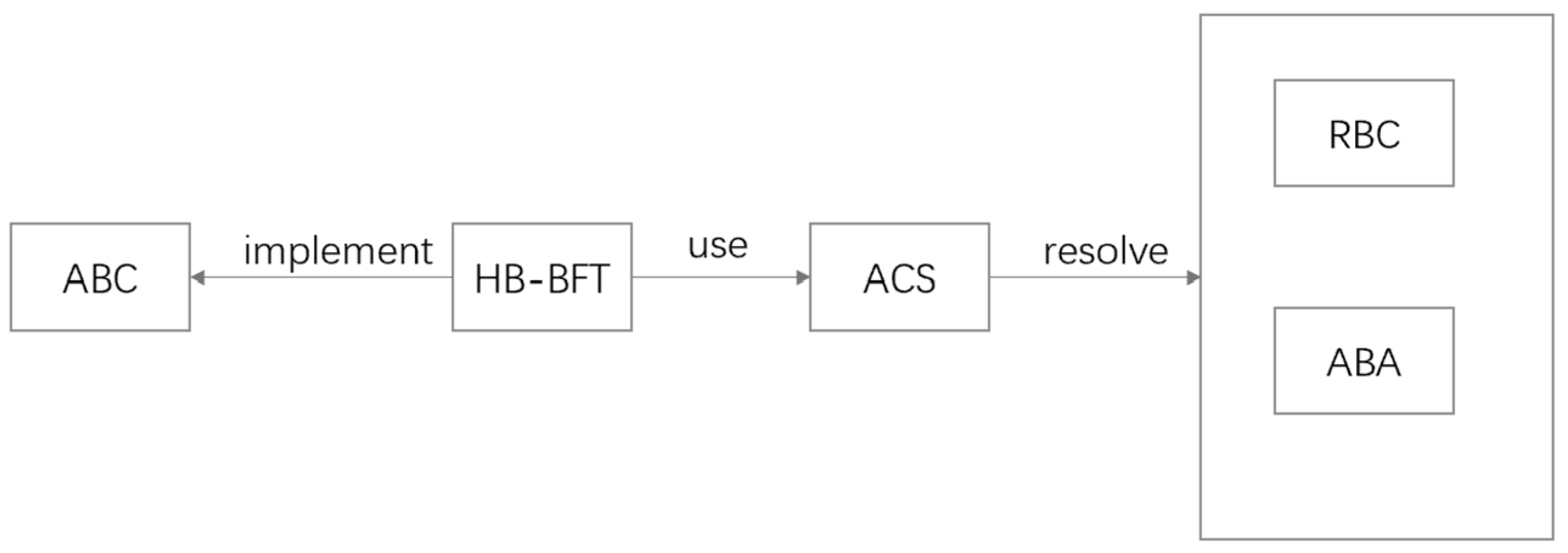
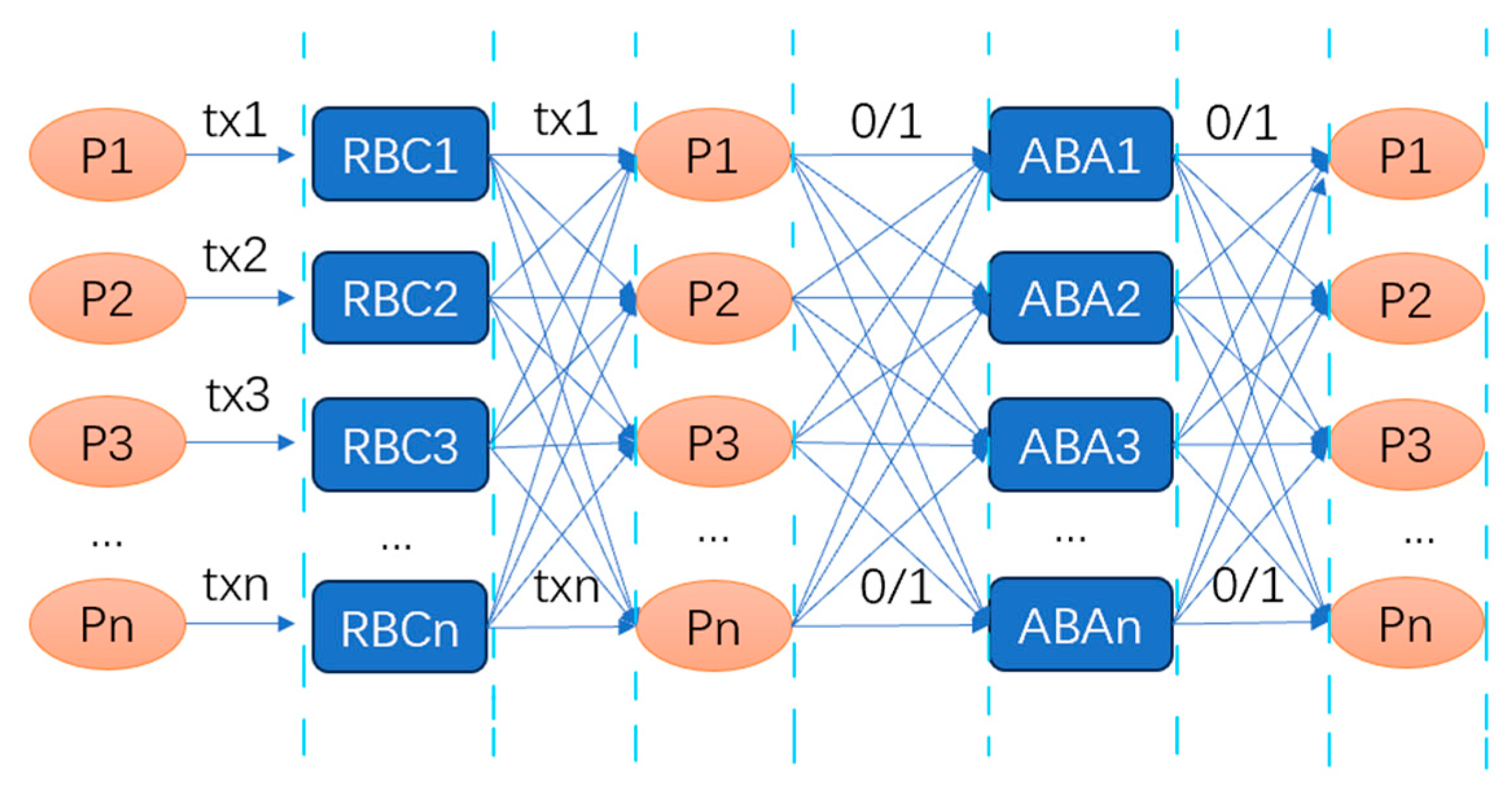
4.2.1. Honey Badger of BFT Protocols (BKR)
4.2.2. DispersedLedger (BKR)
4.2.3. Dumbo (CKPS)
4.2.4. Speeding Dumbo (CKPS)
4.2.5. Summary
5. Performance Analysis
6. Challenges of Asynchronous Byzantine Consensus Protocols
6.1. Performance Challenges
6.2. Technical Challenges
7. Future Research Directions
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Shao, Q.F.; Jin, C.Q.; Zhang, Z.; Qian, W.N.; Zhou, A.Y. Blockchain: Architecture and research progress. Chin. J. Comput. 2018, 41, 969–988. [Google Scholar]
- Dai, C.; Luan, H.; Yang, X.; Guo, X.; Lu, Z.; Niu, B.F. Overview of blockchain technology. Comput. Sci. 2021, 48 (Suppl. S2), 500–508. [Google Scholar]
- Tan, P.L.; Wang, R.S.; Zeng, W.H.; Wang, S.K.; Zou, W.S. Overview of blockchain consensus algorithms. Comput. Sci. 2023, 50 (Suppl. 1), 691–702. [Google Scholar]
- Chen, W.L.; Zheng, Z.B. Blockchain data analysis: A review of status, trends and challenges. J. Comput. Res. Dev. 2018, 55, 1853–1870. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Business Review, 2008. Satoshi Nakamoto. 2008. Available online: http://bitcoin.org/bitcoin.pdf (accessed on 28 November 2024).
- Paramesha, M.; Rane, N.L.; Rane, J. Artificial intelligence, machine learning, deep learning, and blockchain in financial and banking services: A comprehensive review. Partn. Univers. Multidiscip. Res. J. 2024, 1, 51–67. [Google Scholar] [CrossRef]
- Oriekhoe, O.I.; Omotoye, G.B.; Oyeyemi, O.P.; Tula, S.T.; Daraojimba, A.I.; Adefemi, A. Blockchain in supply chain management: A systematic review: Evaluating the implementation, challenges, and future prospects of blockchain technology in supply chains. Eng. Sci. Technol. J. 2024, 5, 128–151. [Google Scholar] [CrossRef]
- Al-Nbhany, W.A.N.A.; Zahary, A.T.; Al-Shargabi, A.A. Blockchain-IoT healthcare applications and trends: A review. IEEE Access 2024, 12, 4178–4212. [Google Scholar] [CrossRef]
- Shahidinejad, A.; Abawajy, J. An all-inclusive taxonomy and critical review of blockchain-assisted authentication and session key generation protocols for IoT. ACM Comput. Surv. 2024, 56, 1–38. [Google Scholar] [CrossRef]
- Dhar Dwivedi, A.; Singh, R.; Kaushik, K.; Rao Mukkamala, R.; Alnumay, W.S. Blockchain and artificial intelligence for 5G-enabled Internet of Things: Challenges, opportunities, and solutions. Trans. Emerg. Telecommun. Technol. 2024, 35, e4329. [Google Scholar] [CrossRef]
- Gangwani, P.; Perez-Pons, A.; Bhardwaj, T.; Upadhyay, H.; Joshi, S.; Lagos, L. Securing environmental IoT data using masked authentication messaging protocol in a DAG-based blockchain: IOTA tangle. Future Internet 2021, 13, 312. [Google Scholar] [CrossRef]
- Zhao, W.; Aldyaflah, I.M.; Gangwani, P.; Joshi, S.; Upadhyay, H.; Lagos, L. A blockchain-facilitated secure sensing data processing and logging system. IEEE Access 2023, 11, 21712–21728. [Google Scholar] [CrossRef]
- King, S.; Nadal, S. Ppcoin: Peer-to-Peer Crypto-Currency with Proof-of-Stake. Self-Published Paper. 19 August 2012. Available online: https://www.peercoin.net/read/papers/peercoin-paper.pdf (accessed on 28 November 2024).
- Yang, F.; Zhou, W.; Wu, Q.; Long, R.; Xiong, N.N.; Zhou, M. Delegated proof of stake with downgrade: A secure and efficient blockchain consensus algorithm with downgrade mechanism. IEEE Access 2019, 7, 118541–118555. [Google Scholar] [CrossRef]
- Miller, A.; Xia, Y.; Croman, K.; Shi, E.; Song, D. The Honey Badger of BFT Protocols. In Proceedings of the 2016 ACM Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar] [CrossRef]
- Guo, B.; Lu, Z.; Tang, Q.; Xu, J.; Zhang, Z. Dumbo: Faster asynchronous bft protocols. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 9–13 November 2020; pp. 803–818. [Google Scholar]
- Guo, B.; Lu, Y.; Lu, Z.; Tang, Q.; Xu, J.; Zhang, Z. Speeding dumbo: Pushing asynchronous bft closer to practice. Cryptol. Eprint Arch. 2022. [Google Scholar] [CrossRef]
- Guo, B.; Lu, Y.; Lu, Z.; Tang, Q.; Xu, J.; Zhang, Z. Dumbo-ng: Fast asynchronous bft consensus with throughput-oblivious latency. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 1187–1201. [Google Scholar]
- Zhou, Y.H.; Jia, L.Y.; Jia, Y.X.; Yang, Y.G. Hashgraph consensus algorithm based on credit. Appl. Res. Comput. 2021, 38, 2590–2593+2599. [Google Scholar]
- Keidar, I.; Kokoris-Kogias, E.; Naor, O.; Spiegelman, A. All you need is dag. In Proceedings of the 2021 ACM Symposium on Principles of Distributed Computing, Virtual Event, 26–30 July 2021; pp. 165–175. [Google Scholar]
- Duan, S.; Zhang, H. Recent progress on BFT in the era of blockchains. Natl. Sci. Rev. 2022, 9, nwac132. [Google Scholar] [CrossRef]
- Sharma, N.; Shamkuwar, M.; Kumaresh, S.; Singh, I.; Goje, A. Introduction to blockchain and distributed systems—Fundamental theories and concepts. In Blockchain for Smart Cities; Elsevier: Amsterdam, The Netherlands, 2021; pp. 183–210. [Google Scholar]
- Yin, M.; Malkhi, D.; Reiter, M.K.; Gueta, G.G.; Abraham, I. HotStuff: BFT consensus in the lens of blockchain. arXiv 2018, arXiv:1803.05069. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. OsDI 1999, 99, 173–186. [Google Scholar]
- Baird, L. The swirlds hashgraph consensus algorithm: Fair, fast, byzantine fault tolerance. Swirlds Tech Reports SWIRLDS-TR-2016-01. Tech. Rep 2016, 34, 9–11. [Google Scholar]
- Danezis, G.; Kokoris-Kogias, L.; Sonnino, A.; Spiegelman, A. Narwhal and tusk: A dag-based mempool and efficient bft consensus. In Proceedings of the Seventeenth European Conference on Computer Systems, Rennes, France, 5–8 April 2022; pp. 34–50. [Google Scholar]
- Spiegelman, A.; Giridharan, N.; Sonnino, A.; Kokoris-Kogias, L. Bullshark: Dag bft protocols made practical. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 2705–2718. [Google Scholar]
- Dwork, C.; Lynch, N.; Stockmeyer, L. Consensus in the presence of partial synchrony. J. ACM (JACM) 1988, 35, 288–323. [Google Scholar] [CrossRef]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine generals problem. ACM Trans. Program. Lang. Syst. 1982, 4, 382–401. [Google Scholar] [CrossRef]
- Qun, W.; Li, F.J.; Ni, X.L.; Xia, L.; Wang, Z.; Liang, G. Survey on blockchain consensus algorithms and application. J. Front. Comput. Sci. Technol. 2022, 16, 1214–1242. [Google Scholar]
- Lu, G.H.; Xie, L.H.; Li, X.Y. Comparative research of blockchain consensus algorithms. Comput. Sci. 2020, 47, 332–339. [Google Scholar]
- Lamport, L. Paxos made simple. ACM SIGACT News 2001, 32, 51–58. [Google Scholar]
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm. In Proceedings of the 2014 USENIX Annual Technical Conference (USENIX ATC 14), Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- Gueta, G.G.; Abraham, I.; Grossman, S.; Malkhi, D.; Pinkas, B.; Reiter, M.; Tomescu, A. Sbft: A scalable decentralized trust infrastructure for blockchains. arXiv 2018, arXiv:1804.01626. [Google Scholar]
- Fischer, M.J.; Lynch, N.A.; Paterson, M.S. Impossibility of distributed consensus with one faulty process. J. ACM (JACM) 1985, 32, 374–382. [Google Scholar] [CrossRef]
- Wang, Y.Q.; Liu, Y.; Li, X.Y.; Liu, X.L.; Cao, H.H. Efficient asynchronous byzantine fault tolerance algorithm for blockchain. Appl. Res. Comput. 2023, 40, 2590–2595. [Google Scholar]
- Hu, J. Research on Parallel Blockchain Consensus Protocol Based on Directed Acyclic Graph. Master’s Thesis, Shanghai Normal University, Shanghai, China, 2022. [Google Scholar]
- Ben-Or, M.; Kelmer, B.; Rabin, T. Asynchronous secure computations with optimal resilience. In Proceedings of the Thirteenth Annual ACM Symposium on Principles of Distributed Computing, Los Angeles, CA, USA, 14–17 August 1994; pp. 183–192. [Google Scholar]
- Cachin, C.; Kursawe, K.; Petzold, F.; Shoup, V. Secure and efficient asynchronous broadcast protocols. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 524–541. [Google Scholar]
- Zhang, H.; Duan, S. Pace: Fully parallelizable bft from reproposable byzantine agreement. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 3151–3164. [Google Scholar]
- Duan, S.; Wang, X.; Zhang, H. Fin: Practical signature-free asynchronous common subset in constant time. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; pp. 815–829. [Google Scholar]
- Yang, L.; Park, S.J.; Alizadeh, M.; Kannan, S.; Tse, D. {DispersedLedger}:{High-Throughput} Byzantine Consensus on Variable Bandwidth Networks. In Proceedings of the 19th USENIX Symposium on Networked Systems Design and Implementation (NSDI 22), Renton, WA, USA, 4–6 April 2022; pp. 493–512. [Google Scholar]
- Lu, Y.; Lu, Z.; Tang, Q. Bolt-dumbo transformer: Asynchronous consensus as fast as the pipelined bft. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 2159–2173. [Google Scholar]





| Classification | Characteristics | Representative Protocols |
|---|---|---|
| Synchronous Consensus Protocols | Requires any message in the network to reach all consensus nodes within a known, predetermined time limit. | PoW [5] |
| Partially Synchronous Consensus Protocols | Any message in the network can reach all consensus nodes within a limited time, but this limit is unknown, and the system eventually assumes synchrony. | HotStuff [23], PBFT [24] |
| Asynchronous Consensus Protocols | There are no restrictions on the message transmission delay in the network. | HB-BFT [15], Dumbo [16], Hashgraph [25], Tusk [26], Bullshark [27] |
| Classification Based on Structural Design | Protocol | Runtime Complexity | Latency | Throughput | Advantages | Disadvantages |
|---|---|---|---|---|---|---|
| DAG-Based Asynchronous Byzantine Consensus Protocols | Hashgraph [17] | O(exp(n)) | low | high | High throughput, fast processing speed | High memory usage |
| DAG-Rider [19] | O(1) | high | low | |||
| Tusk [31] | +∞ | medium | medium | |||
| Bullshark [33] | O(1)/+∞ | low | high | |||
| ACS-Based Asynchronous Byzantine Consensus Protocols | HB-BFT [13] (BKR) | O(log n) | high | low | Requires less memory compared to DAG-based protocols | Decreased performance as the number of nodes increases |
| DispersedLedger [22] (BKR) | O(log n) | medium | medium | |||
| Dumbo [14] (CKPS) | O(log k)/O(1) | medium | medium | |||
| Speeding Dumbo [15] (CKPS) | O(1) | low | high |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ji, Z.; Zhang, X.; Hu, J.; Lu, Y.; Liu, J. A Review of Asynchronous Byzantine Consensus Protocols. Sensors 2024, 24, 7927. https://doi.org/10.3390/s24247927
Ji Z, Zhang X, Hu J, Lu Y, Liu J. A Review of Asynchronous Byzantine Consensus Protocols. Sensors. 2024; 24(24):7927. https://doi.org/10.3390/s24247927
Chicago/Turabian StyleJi, Zhenyan, Xiao Zhang, Jianghao Hu, Yuan Lu, and Jiqiang Liu. 2024. "A Review of Asynchronous Byzantine Consensus Protocols" Sensors 24, no. 24: 7927. https://doi.org/10.3390/s24247927
APA StyleJi, Z., Zhang, X., Hu, J., Lu, Y., & Liu, J. (2024). A Review of Asynchronous Byzantine Consensus Protocols. Sensors, 24(24), 7927. https://doi.org/10.3390/s24247927







