1. Introduction
Traffic congestion occurs as a result of an imbalance in demand and supply on a spatio-temporal scale. The well-known Braess’ Paradox demonstrates that relying solely on supply side solutions that focus on increasing the capacity of existing infrastructure without regard for traveler behavior may have a negligible or even detrimental effect on the performance of traffic networks. Demand-side strategies employ behavioral interventions to encourage shifts in travel mode, travel routes, and departure times [
1,
2]. Of these, en route re-routing is the most challenging problem due to the inherent dynamics and randomness. Over the last few decades, effective behavioral intervention strategies have been developed, such as toll and incentive mechanisms, using model-based [
3,
4,
5,
6,
7] or model-free [
8,
9,
10] approaches to influence travelers’ en route behavior and thereby alleviate traffic congestion. However, these intervention strategies frequently overlook individual-level heterogeneity, rely on multiple user classes to reflect distinct behavioral patterns, and suffer from computational tractability issues associated with centralized computation.
Emerging connected technologies enable information sharing among vehicles and infrastructure through vehicle-to-everything (V2X) communications in a connected traffic environment [
11,
12,
13,
14,
15], facilitating more informed collaborations among connected vehicles (CVs) in the re-routing process [
16,
17,
18]. Li et al. [
19] proposed a routing method facilitating the navigation through passing time windows in a connected vehicle environment; this has informed the direction of our study. Additionally, Li et al. [
20] developed a self-evolving routing method, which introduces a novel formulation in the spatial domain that resolves the mismatch between routing and planning found in conventional studies. This spatial domain-based planning method represents a key contribution to the field of cooperative routing. Nevertheless, individual heterogeneities are still not captured in these studies.
Wang et al. [
21] proposed a novel incentive mechanism for collaborative routing in a connected and autonomous vehicular environment, which leverages individual heterogeneity in the route preferences to enhance the system performance while ensuring user satisfaction. A decentralized computational framework was developed to enable efficient network-level deployment. On the other hand, individual heterogeneity necessitates that each passenger discloses their personal preferences (e.g., value of time) as model inputs, which can represent sensitive information that can be exploited. Also, as collaborative routing reveals model outputs, travelers’ updated routes, and incentives to other travelers, it raises privacy issues. Moreover, validation of execution (i.e., validating whether each vehicle travels on the route selected in the incentive mechanism) can cause a substantial computation burden and result in more privacy leaks if traditional centralized methods like sharing GPS traces are used. Further, such privacy risks may act as a barrier to participation in the system for societally vulnerable groups (e.g., sharing a low value of time may indicate a low income level), further impairing mobility equity.
Blockchain has been gaining enormous attention since the whitepaper on Bitcoin [
22]. A blockchain is a decentralized ledger with tamper resistance ensured by cryptography. The popularity of blockchain is not limited to cryptocurrencies. Due to its decentralized nature, it has demonstrated its promise in Internet of Things and vehicular ad hoc networks [
23,
24,
25]. However, currently, a blockchain is mainly used to record and share public information such as traffic incidents [
26] rather than sensitive personal information in transportation applications. In other studies [
27], a blockchain is also used to store virtual credits (which quantify the level of trust that users can place in certain users based on their historical behavior). However, route preferences and historical travel routes are sensitive information that can be potentially leaked even if anonymous identities are used in blockchains. As for the anonymity paradox of Bitcoin, though every Bitcoin account is anonymous, identity information can still be leaked through transaction pattern analysis because every transaction is transparent. The historical travel routes associated with an account can be used to deduce that user’s travel pattern and potentially leak their real-world identity. Therefore, on-chain computation alone does not enable a privacy-preserving incentive mechanism for collaborative routing.
Secure multi-party computation (MPC) is a subfield of cryptography which allows a group to jointly compute a function without disclosing any participants’ private inputs. A few studies [
28,
29] leverage MPC in intelligent transportation systems to address privacy concerns. However, none of them address its potential for collaborative routing.
To address privacy concerns in collaborative routing for CVs, this study first proposes a privacy-preserving incentive mechanism based on the decentralized mechanism developed in our previous work [
21]. Specifically, a collaborative routing scheme is developed to enable travelers to update routes and compute associated incentives following an MPC protocol without disclosing their value of time. Then, a blockchain-based route validation scheme is proposed to securely validate travelers’ whereabouts at checkpoints along selected routes with the assistance of nearby vehicles (i.e., witness vehicles) while allowing them to conceal their trajectories in the blockchain. Combining on-chain and off-chain cryptographic protocols, the proposed incentive mechanism protects sensitive personal information throughout peer vehicle collaborations and prevents malicious parties from conducting pattern-analysis attacks on the blockchain, ensuring that the entire collaborative routing process adheres to a high standard of privacy.
It is worth noting that the privacy concerns mentioned earlier are not specifically associated with the collaborative routing strategy presented in [
21]. Rather, they stem from the inherent nature of personalization. To effectively account for the diverse heterogeneities of individual users, personalization necessitates the incorporation of users’ unique characteristics and preferences to generate tailored outputs that cater to their specific interests. Consequently, while [
21] primarily addresses the computational efficiency of enabling personalization within the routing context, the current study emphasizes the implementation of structured privacy protection techniques to mitigate the privacy challenges associated with personalization.
The rest of the paper is organized as follows.
Section 2 provides an overview of the proposed incentive mechanism.
Section 3 presents detailed protocols of the mechanism.
Section 4 discusses numerical studies.
Section 5 concludes the paper by summarizing contributions and future directions.
2. Mechanism Overview
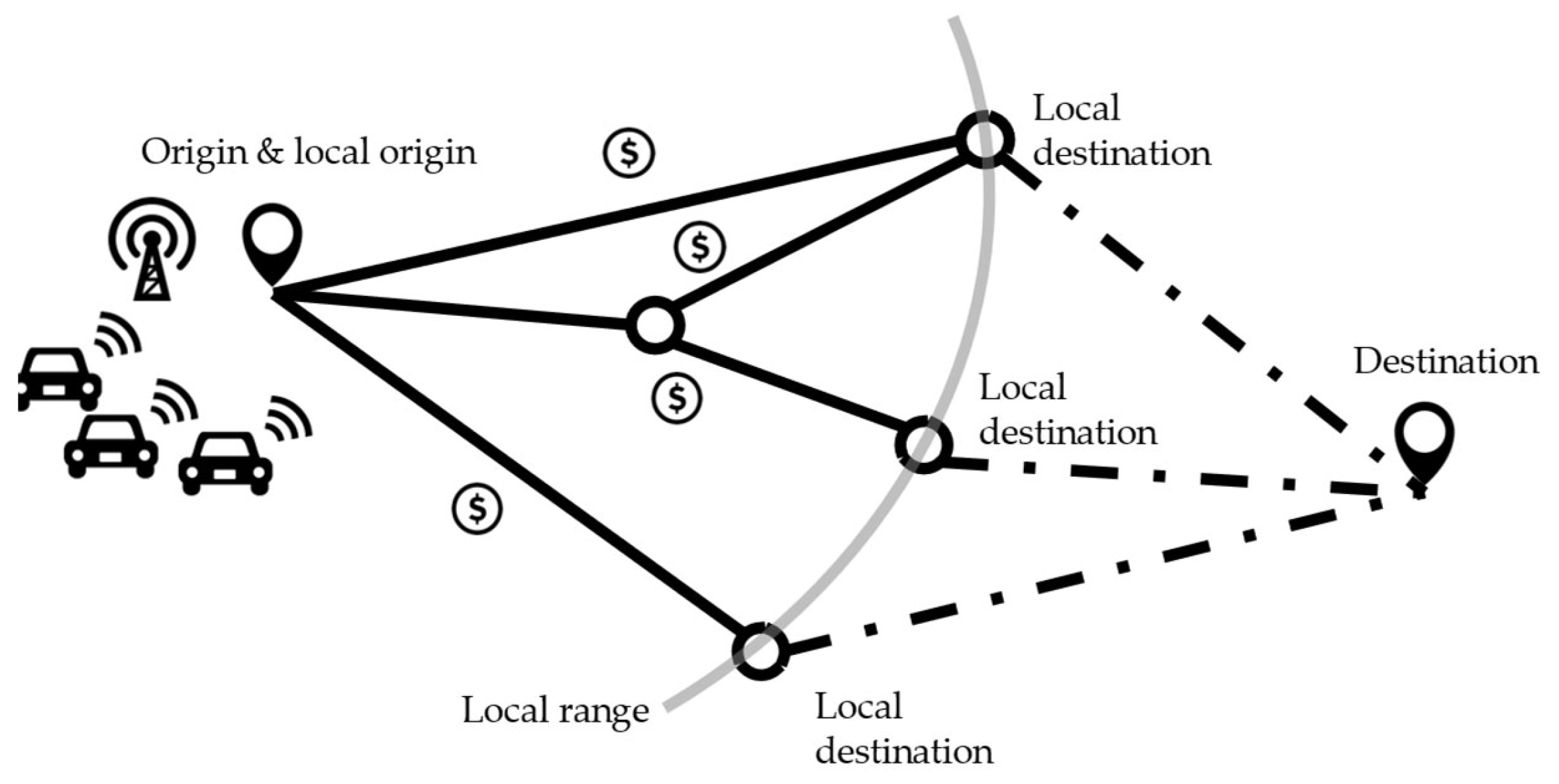
This study’s problem context is similar to that of our prior study [
21]. As depicted in
Figure 1, the major objective is to encourage vehicles to reroute collaboratively during their trips in order to improve system performance (specifically, reducing total travel time in this study). When assigning vehicles, the system performance evaluation is based on vehicles’ estimated travel times. Given the difficulty of precisely estimating long-term travel times in the real world, the method will be executed repeatedly throughout the whole horizon of interest. In each iteration, vehicles reroute based on precisely predicted travel times inside the local range (shown by the gray line in
Figure 1) and approximations of travel times outside the local range. The decentralized incentive system in [
21] follows a hierarchical architecture. Vehicles with the same local origin–destination (OD) pairs are grouped together (the temporary destinations within the defined local range in [
21]). First, a route flow assignment model finds the optimal route flows for all vehicle groups in each iteration (with the same local OD pairs). Then, using these optimal flows and the value of time for each vehicle as inputs, a vehicle assignment model assigns vehicles to various routes within each vehicle group. Then, an envy-free procedure produces incentives for every vehicle in the group to ensure participation willingness and behavioral honesty. Notably, in [
21], the participation willingness did not account for the potential disadvantages associated with individuals’ privacy concerns about sharing sensitive data during the process. Similarly, whereas behavioral honesty implies that users’ utilities are maximized when they reveal their real value of time, the utility functions did not account for the negative consequences of disclosing the value of time.
For instance, there are four local routes for the group of vehicles in
Figure 1. At the end of the current iteration, the vehicles will be provided with four option bundles (incentives calculated by the mechanism are bonded to the corresponding routes). Choosing a certain route determines the bonded amount of incentives. The incentives are designed such that all vehicles picking the bundles that optimize their individual utilities generate a local system-optimal assignment [
21]. However, these benefits come with a price in terms of privacy. The vehicle route assignment and incentive calculation depend on vehicles sharing their values of time. And there seems to be no way to prevent incentive scams in which a vehicle claims to choose the option with the highest incentive but later travels on the route with the shortest travel time.
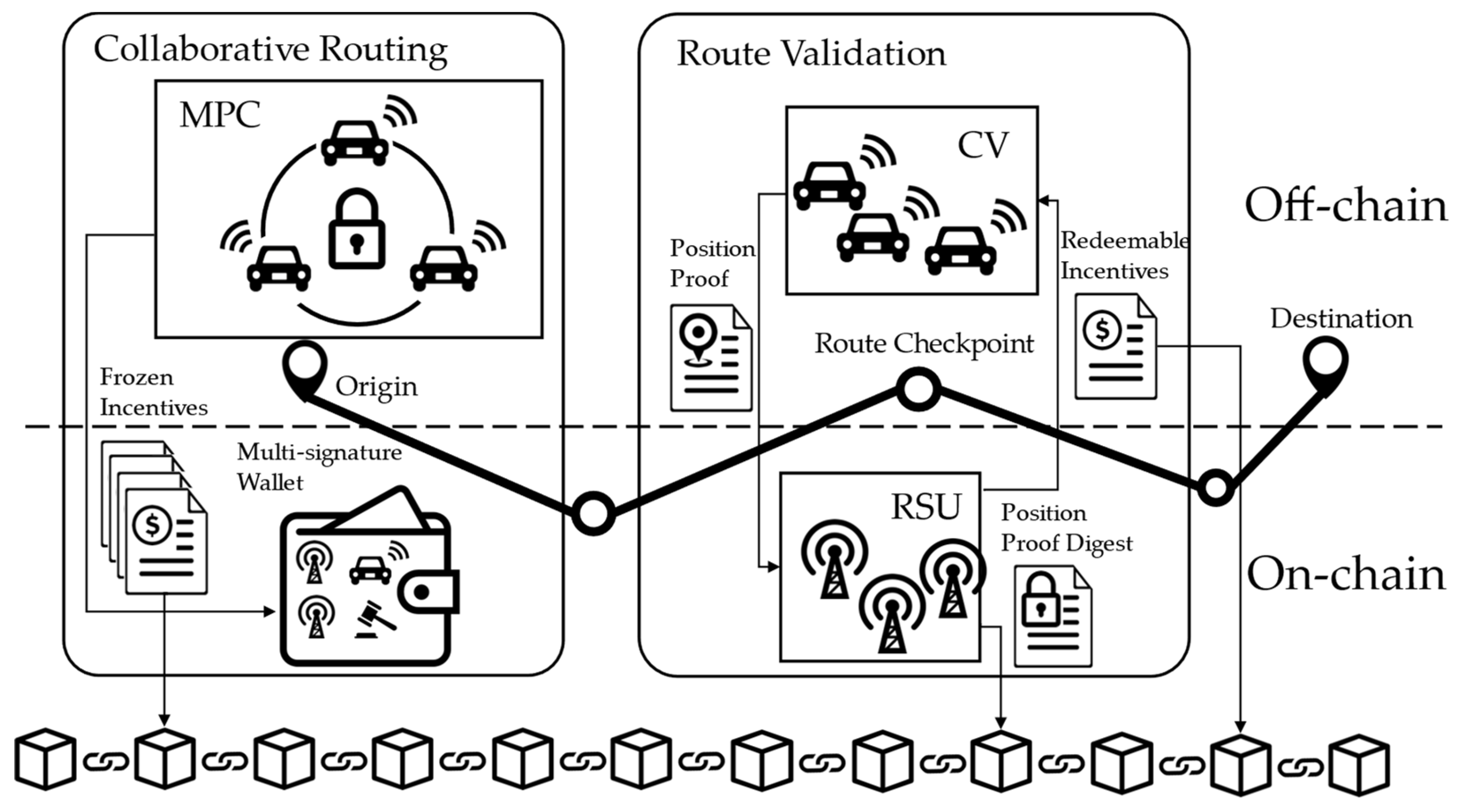
Figure 2 depicts the conceptual structure of the privacy-preserving incentive mechanism for collaborative routing, which consists of a secure collaborative routing scheme at the origin (or local origin), and a route validation scheme at the checkpoints along the selected route. Both schemes employ on-chain and off-chain operations (depending on whether they need logging information on the blockchain for the record), ensuring that just the bare minimum amount of data are safely stored on the blockchain (against pattern-analysis attacks). The collaborative routing scheme leverages MPC to securely execute the protocols defined by the vehicle route assignment model and incentive model (steps 2 and 3 in the hierarchical framework) in [
21]. Users will not receive the incentives corresponding to the routes they choose at the origin. Instead, the incentives will be temporarily frozen, which means they will be sent to a series of multi-signature wallets/accounts from the traffic operator’s account. The incentives in a multi-signature wallet require
m-out-of-
n signatures to become redeemable, where
is the minimum number of signatures required,
is the total number of account holders of the wallet, and both
and
are determined when the wallet is created. Apart from the vehicles receiving these incentives, the account holders of a multi-signature wallet also include one or two verifiers and a mediator. The multi-signature wallets are designed in a cascading manner, such that the frozen incentives can only become redeemable when the user passes the route validation checkpoints along the selected route in order.
When the vehicle is around a checkpoint on the selected route, instead of using GPS information (which can be easily forged by malicious vehicles), it needs to follow the proposed route validation scheme to generate a position proof with the assistance of witness vehicles (nearby vehicles willing to sign on the position proof) and send it to roadside units (RSUs) to verify. The RSUs in the network will verify the proof independently and reach a consensus following the practical byzantine fault tolerance (PBFT) algorithm. If the position proof is valid, a digest of the proof (which is a fixed-size representation of the contents of the proof) will be included in the current block of a consortium blockchain. Meanwhile, the verifier at the checkpoint will sign two multi-signature transactions: one makes the frozen incentives associated with the current checkpoint redeemable for the user; the other one is for the frozen incentives associated with the next checkpoint, which will remain frozen for the time being and requires one more signature to be redeemable. The user does not have to redeem the redeemable incentives (by signing their own signature on the multi-signature transactions and sending them out) at the time he/she receives them. Note that the transactions will be included in the consortium blockchain only when the incentives are redeemed. Therefore, users can hide their trajectories on the blockchain by redeeming the incentives from the checkpoints from multiple trips in arbitrary order.
Leveraging the tamper resistance of the on-chain information while keeping the sensitive information off-chain, the proposed incentive mechanism eliminates both direct privacy leaks (e.g., sharing the value of time in computation) and indirect privacy exposure (e.g., historical trajectories inferred from the transaction pattern or plain position proofs recorded in the blockchain). It also achieves high-standard security in terms of potentially malicious behavior from both the user side and the infrastructure (i.e., RSUs).
4. Privacy-Preserving Incentive Mechanism
Before presenting the details of the proposed incentive mechanism, this section starts with an introduction of the main entities: a trusted authority (TA), CVs, and RSUs, and how they are involved in the proposed incentive mechanism.
Trusted Authority: The TA plays two essential roles in the proposed mechanism: the identity manager () is responsible for generating identities (public key and private key pairs) and relating vehicles’ pseudonyms to their real identities, and the mediator ( unfreezes the frozen incentives to either refund the traffic operator when users behave dishonestly or transact the incentives to users when RSUs behave maliciously (are hacked). Therefore, TA is assumed to be fully secure and trusted. Note that though both and function in a centralized manner, little computation or communication burden is introduced because vehicles only request identities once with when they participate in the mechanism for the first time. only interacts with vehicles and RSUs under malicious behaviors, which are rare because the malicious party can be traced and penalized.
CVs: Each CV is assumed to be able to communicate with RSUs and nearby vehicles using V2X technology. There are initiators/leaders , which initiate the collaborative routing scheme and the route validation scheme, respectively, and corresponding followers The study does not consider attacks in the communication process, implying communication channels are assumed to be secure. Also, each vehicle is assumed to have a tamper-resistant device with which to store sensitive information, including a secret key and value of time securely (vehicle hardware side attacks are not considered).
RSUs: RSUs also play multiple roles in the proposed mechanism. Some RSUs serve as checkpoint signers (
) in the route validation protocol, signing on multi-signature transactions when vehicles pass the validation at the checkpoints. And all RSUs are the nodes of the consortium blockchain, with some authorized RSUs (
) verifying the incentive transactions and position proofs and undertaking the consensus work to generate new blocks. The RSUs are semi-trusted and can be potentially malicious. However, we assume that only a small percentage of RSUs are malicious, which is widely accepted in other consortium blockchain applications [
35,
36].
4.1. Collaborative Routing Scheme
The collaborative routing scheme consists of an off-chain MPC and an on-chain incentive freezing process. The off-chain MPC takes the optimal route flows as public inputs and the value of time of vehicles in the local vehicle group as private inputs to generate route suggestions and associated incentive amounts for vehicles in the group. With the envy-freeness analysis in [
21], rational users will always choose the suggested routes. After confirmation from users, the incentives will be frozen in a series of cascading multi-signature wallets for each vehicle until they pass further route validations.
First, we describe how
generates pseudonyms for vehicles that participate in the mechanism for the first time using an Elliptic Curves Cryptography (ECC) based combined-public key (CPK) scheme. Identity-based CPK derives public keys (pseudonyms) from real-world identities; hence, it does not require certificates as traditional public key encryptions, reducing the key management burden [
37]. In our case, the public keys are derived from the VIN (Vehicle Identification Number) of vehicles. The identity generation process is as follows:
Select an elliptic curve
. Let
be an addition group of points on
, and let
be the generator of
.
is an order of
(most encryption/signature schemes in this study are based on ECC; please refer to [
16] for ECC basics).
Generate an -length master private key vector , where are randomly selected from .
Generate the corresponding public key vector , where .
Using
and
, generate the private key and public key for each vehicle as follows:
where
is the
th bit of the digest of the vehicle’s VIN generated by
. It is trivial to see that
holds, i.e.,
is a valid pair of ECC keys.
Send vehicles their private keys through secure communication channels along with the following information as the public parameters of the cryptographic system , where is a symmetric encryption protocol (given cyphertext ; we can obtain the plaintext , and represents hash functions used in the schemes.
Using the pseudonyms, vehicles can initiate and participate in the collaborative routing scheme, which can be described as follows:
One vehicle (defined as the leader of the collaborative routing scheme ) initiates a request for collaborative route updating by sending nearby vehicles the message , where is the VIN of , is the destination identifier, and is the signature that signs using its secret key on the digest of , .
Vehicles heading to the same destination and interested in joining the collaborative routing scheme (defined as the followers of the collaborative routing scheme ), after verifying the request (), each vehicle can reply a signed bit 1, together with its VIN to .
collects the responses from , verifies the responses (, and counts the total number of vehicles participating in this session, (which is the demand of this specific OD pair).
reports
to the RSU nearby, which will update the flows related to this OD pair iteratively together with other RSUs in a distributed manner following the route flow assignment model in [
21].
At the same time, and start establishing the communication network for the MPC protocol. produces a participation confirmation message, , which generates an order for all participants.
After receive the confirmation message, they start creating secret shares of their value of time. is denoted as the value of time of the th vehicle ( in the confirmation message. The vehicle creates secret shares for the th vehicle and sends it.
After the RSU receives optimal route flows, it broadcasts the information as public inputs of the MPC protocol.
Note that step 6 takes the most time out of the entire process as there are
messages sent. However, this happens while RSUs are solving for the optimal flows, which is also the most time-consuming step in the hierarchical framework in [
21], which mitigates the influence of step 6′s relatively long computation time.
With all required private and public inputs, the vehicles can execute the MPC protocol to produce the private outputs, which consists of their updated routes and corresponding incentives. However, MPC protocols are pre-compiled, which means that they have a fixed number of inputs, while the number of vehicles participating in the collaborative routing scheme varies in the real world. Hence, the vehicle assignment model and incentive mechanism proposed in [
21] are modified as follows. Assume that the MPC protocol requires
vehicles to collaboratively update their routes (
is the maximum number of participants allowed in the scheme, determined by step 6 in practice). According to
Lemma 3 in [
21], the vehicle assignment is to sort vehicles’ value of time. We can create
fake vehicles with zero value of time to complement the number of inputs required by the MPC protocol. In this way, the updated routes of the participants are the same as the ones they are supposed to obtain in the vehicle route assignment model. When determining the incentives, the protocol assumes that fake vehicles take a fake route with the same travel time as the longest travel time of all real routes. According to
Lemma 4 in [
21], the adjustment incentives of the fake vehicles are zero and the real vehicles’ adjustment incentives are the same as those they are supposed to obtain from the incentive mechanism in [
21]. The details of the MPC protocol for route/incentive assignment (Algorithm 1) are described as follows.
| Algorithm 1. MPC protocol for route/incentive assignment |
Private input: individual value of time .
Public input: travel times and optimal route flows for each route , is the route id set ().
Public output: incentives for each route .
Sort
(denote smallest as
and
add
vehicles with λi = 0, and add N − ns flow to route with largest travel time. Duplicate Tk for fk times such that there are N travel times in total. Assign the vehicle with the rth largest value of time, λ(r), to the route with rth shortest travel time T(r) (denoted as η(r)).
as if there were N vehicles.
Return and to the vehicle with |
The MPC protocol also generates the outputs required for the traffic manager to freeze incentives.
Figure 5 shows an example of the process of freezing incentives. The route that the vehicle takes has four checkpoints
. The amount of incentives that the vehicle receives for this trip is divided into four parts
and
, which correspond to the four segments of the route divided by the checkpoints. To ensure that the vehicle follows the route, the traffic manager does not send the incentives to the vehicle directly at the origin. Instead, it sends the segment incentives to a series of cascading multi-signature wallets, which require multiple signatures to be authorized to transfer. The wallet corresponding to the first checkpoint is a two-out-of-three wallet, which requires at least two signatures from three wallet holders: the signer at checkpoint A,
, the vehicle, and the mediator
. In normal operations,
signs on the transaction after the vehicle passes the route verification at checkpoint A, which makes the incentives associated with segment OA redeemable for the vehicle; it can sign on the transaction to meet the two-out-of-three signature requirement when it wants to redeem the incentives.
only plays a role when malicious behaviors are detected. Either the traffic manager or the vehicle can submit evidence to let
sign on the transaction to either refund the frozen incentives to the traffic manager or transmit the frozen incentives to the vehicle. The other wallets are three-out-of-four wallets, which require at least three signatures from four wallet holders: the signer at the upstream checkpoint, the signer at the current checkpoint, the vehicle, and the mediator.
Notably, the secret shares of the private inputs and outputs of Algorithm 1 can be fed into Algorithm 2 to skip the step of generating secret shares of the inputs of Algorithm 2. The outputs from Algorithm 2 are a series of cascading incentive freezing transactions to be signed by the traffic manager. They are marked as public because the signed transactions will be published on-chain to freeze the incentives for each segment in the corresponding multi-signature wallets. Since the signed transactions are recorded in the blockchain, the contents of
are open to everyone. However, the sensitive trip information is protected twofold. First, it is almost impossible to tell which transaction is generated for which segment incentives for whose trip, because the address of a multi-signature wallet does not explicitly show the wallet holders’ identities. As (3) shows, it is a hash of a piece of code. The public keys of the involved vehicle, checkpoints, and the mediator only appear in the code. Recall that hash functions are hiding; it is impossible to reconstruct the code using the wallet address (which is the hash of the code). It is also hard to enumerate the combinations of the wallet holders if each RSU/checkpoint has tens of valid identities registered at
. Second, each trip is divided into multiple segments, which makes identifying the entire trip of a certain vehicle exponentially harder, since it requires unhashing the wallet addresses of all involved transactions.
| Algorithm 2. MPC protocol for incentive freezing |
Private input: individual route choices
Public input: incentives for route denoted as , lengths where is the segment set of route , and , the public key set of signer at checkpoint along route , where is the checkpoint set along route .
Public output: transactions , which are to be signed by the traffic manager to freeze segment incentives.
From: the traffic manager’s address (i.e., its public key)
To: the address of the multi-signature wallet
where ( and are the public key sets of the signer at the beginning and end of segment , respectively), and is the payment script that is used to validate the transaction.
Amount:
- 3.
Return to vehicle
.
|
4.2. Route Validation Scheme
To verify that the vehicle is at a certain checkpoint , needs a position proof. Instead of using traditional GPS information (which can be easily tampered with), the position proof is generated by the witness vehicles at checkpoint . A reasonable assumption entails the presence of a sufficient number of vehicles in proximity to the checkpoints. Consequently, the approach delineated in this section holds significance under congested conditions, where V2X communication and privacy protection are predominantly required. To protect the privacy of the witness vehicles, threshold cryptographic techniques are used in the route validation scheme. Specifically, the signatures of real witness vehicles are mixed with other fake signatures to protect their pseudonyms from being tracked. The route validation scheme can be divided into three stages: a vehicle needing a position proof initiating a request for route validation, witness vehicles replying to the request, and verifiers validating the position proof. The first stage is as follows.
The vehicle that wants to prove that it is at checkpoint (defined as the leader of the route validation scheme ) generates a plaintext describing its current position (e.g., “on xxx link near checkpoint at time yyy”).
requests the number of witnesses required, , from nearby RSUs and calculates the total number of signatures on the position proof as , where is the privacy protection parameter (for larger , the pseudonyms of witness vehicles are mixed with fewer fake identities, and thus they will receive less privacy protection). That is, there should be at least nearby vehicles that witness presence at and they should sign on the position proof. Meanwhile, there should be another fake signature on the position proof as well to protect the privacy of these witness vehicles. Otherwise, anyone can learn from the position proof that these vehicles themselves are near at this specific time. Therefore, needs to generate and include fake signatures in the route validation request such, that the witness vehicles can generate signatures that cannot be distinguished from the fake signatures.
generates fake IDs from the feasible ID set, and the corresponding public keys, .
generates the fake signatures for the fake vehicles. For
, it selects
and computes:
where
is the
coordinate of point
. Note that
is a valid EC Elgamal signature of
, because
. The fake signatures are created but
has no control over the corresponding
.
generates different indexes for further Lagrange polynomial interpolation.
initiates the request of route validation at checkpoint by sending the following message to the nearby vehicles:
Upon receiving the route validation request, nearby vehicles that identify at checkpoint will reply to the request with a signed message back, becoming witness vehicles in ’s position proof. A witness vehicle generates its signature as follows:
constructs a polynomial with degrees defined on Galois field () using Lagrange interpolation, such that and , where .
chooses a random index and generates
randomly selects and generates the EC Elgamal signature of , where
replies to the route validation request by sending a message, , to .
Once
receives more than
responses from the nearby vehicles, it aggregates the fake and collected signatures to generate a position proof
and sends it to the verifiers
:
Each then verifies the position proof as follows:
generates the public keys .
verifies whether the signatures are valid by checking whether holds for .
randomly selects tuples from , reconstructs the polynomial using Lagrange interpolation, such that and , where , and verifies whether holds for all .
accepts the position proof if it passes all verifications.
To prevent malicious behavior by a single
, the position proof is sent to all
in the RSU network, and the PBFT algorithm [
38] is used to generate a consensus mechanism. The presence of malicious nodes will not impact the final consensus when the number of malicious nodes is less than one-third of the participating nodes. When consensus is achieved that the position proof is valid, the digest of the position proof,
, instead of the plaintext
, is written to the latest block of the blockchain.
will sign on the unfreezing transaction after verifying that the position is in the blockchain (which indicates that the position proof has been verified by the majority of the verifiers).
4.3. Privacy and Security Analysis
To ensure that the proposed schemes can prevent privacy leaks and ensure consistency between the routes that vehicles choose and the ones they take, this section analyzes the potential privacy leaks in the scheme steps and discusses how malicious behavior can be managed in the incentive mechanism.
First, the proposed schemes are privacy-preserving in both the collaborative routing and the route validation processes. In the collaborative routing scheme, and hide their real identities with pseudonyms when sending messages. Vehicles receiving messages only know that some vehicles are heading to but cannot connect these messages to nearby vehicles. Also, as the messages are kept off-chain, it is hard to connect the pseudonyms to real identities through pattern analysis. The messages sent to RSUs are aggregated information, . Therefore, no individual privacy information is leaked when RSUs compute optimal route flows. When computing updated routes and incentives thatfollow the MPC protocol, vehicles only send secret shares of their value of time to other vehicles, and outputs are generated by each vehicle using these shares. No meaningful information can be inferred from incomplete shares. In the on-chain incentive freezing process, incentives are sent to different multi-signature wallets. Note that of multi-signature wallets do not need to be the RSUs near the corresponding checkpoints (because verifying position proofs is a cryptographic process independent of the RSU position). Therefore, wallet addresses only provide random signers’ public keys, which cannot be used for privacy pattern analysis. In route validation schemes, the pseudonyms of and are mixed with fake pseudonyms in position proofs, which provides additional privacy protections, as position proofs are sent to all RSUs for PBFT consensus. Before logging into the blockchain, the position proofs are hashed to ensure no position/route information can be inferred from pattern analysis of the information in the blockchain.
Behavioral honesty can also be illustrated for both the collaborative routing and the route validation processes. Given that the MPC protocol ensures no privacy leakage risks, vehicles participating in collaborative routing have no privacy concerns. And [
21] has shown that under this condition, vehicles will behave honestly (i.e., provide genuine inputs to the collaborative routing scheme) to maximize their own utilities. In the route validation scheme, first, the cryptographic tools used in the scheme design mitigate common types of attacks. The identity-based asymmetric key generation mitigates Sybil attacks, in which a single entity operates multiple fake identities simultaneously to undermine the system by gaining the most influence in the network. Also, the EC digital signature algorithm widely applied in the proposed scheme ensures that signatures cannot be forged, and messages are tamper-resistant. Therefore, adversaries cannot launch replay attacks in the route validation scheme by re-sending messages they received before. Also,
cannot generate a fake position proof by forging more than
signatures. Because
has no control over the
corresponding to fake signatures, it can forge at most
signatures to identify
points on
(there is an additional point
) and determine a polynomial with degree
. If it forges more signatures, it cannot ensure that the corresponding
is on the polynomial, which can be easily detected by
.
5. Numerical Studies
Simulation studies are conducted to illustrate the performance of the privacy-preserving incentive mechanism. First, we show the correctness of the proposed incentive mechanism. Then, the computational efficiency of the collaborative routing scheme and the route validation scheme is analyzed under different privacy protection settings. The MPC protocols are implemented in SCALE-MAMBA (
https://github.com/KULeuven-COSIC/SCALE-MAMBA (accessed on 9 January 2024)) and MP-SPDZ (
https://github.com/data61/MP-SPDZ (accessed on 9 January 2024)), and the route validation scheme is implemented using Python.
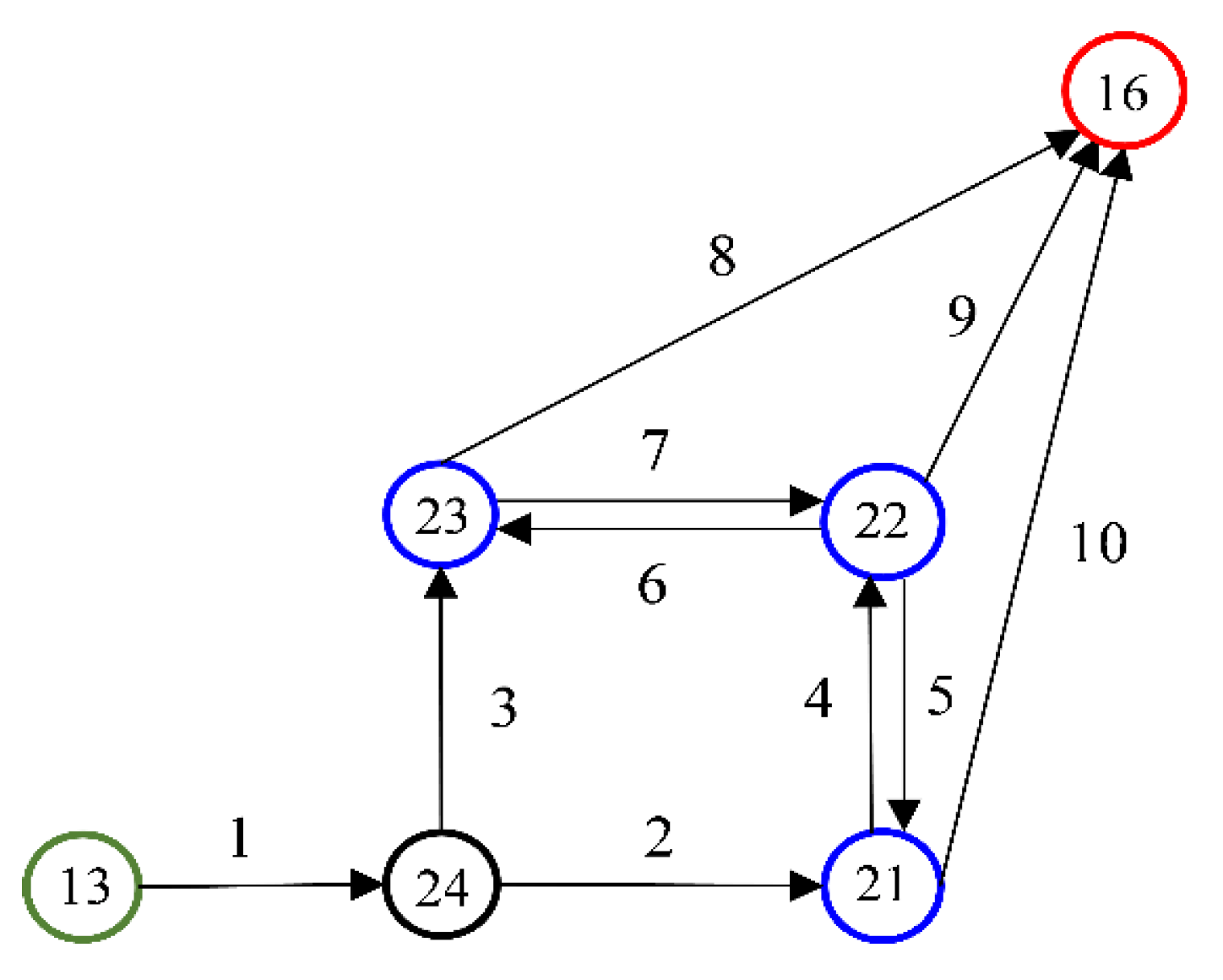
To validate the correctness of the MPC protocol, the example network (see
Figure 6) in [
21] is used to illustrate that the MPC protocol can calculate the same incentives with proper settings. Twenty vehicles depart from node 13 to node 16 in the network. There are three local destinations, nodes 21, 22, and 23, and four alternative routes connecting nodes 13 and 16, as listed in
Table 1 and illustrated in
Figure 6. The desired flows and the corresponding travel costs of the four routes are provided by the route flow assignment model in [
21]. The values of time () for the individual vehicles are shown in
Table 2. With these inputs, the implemented MPC scheme can generate the same vehicle route assignment results
(the id of the route that vehicle
should take) as in [
21]. In terms of the incentives, when the integer representation precision of the MPC protocol is set as 15-bit fixed point numbers with a 5-bit decimal part, the output incentives
are different from the ones calculated in [
21] (although
holds as
). If the precision is increased to 31-bit fixed point numbers with a 16-bit decimal part, the output incentives
(i.e., the implemented MPC scheme can calculate the same incentives as in [
21] under this setting). The total data exchanged among the vehicles when executing the MPC scheme increase from 135.478 MB to 180.649 MB in this case, which is acceptable in the real world.
Next, we validate the computational efficiency of the collaborative routing scheme. Due to our modifications (fake vehicles and routes) to the incentive mechanism, the compiled MPC protocol can be executed by fewer vehicles than the predefined number of parties,
.
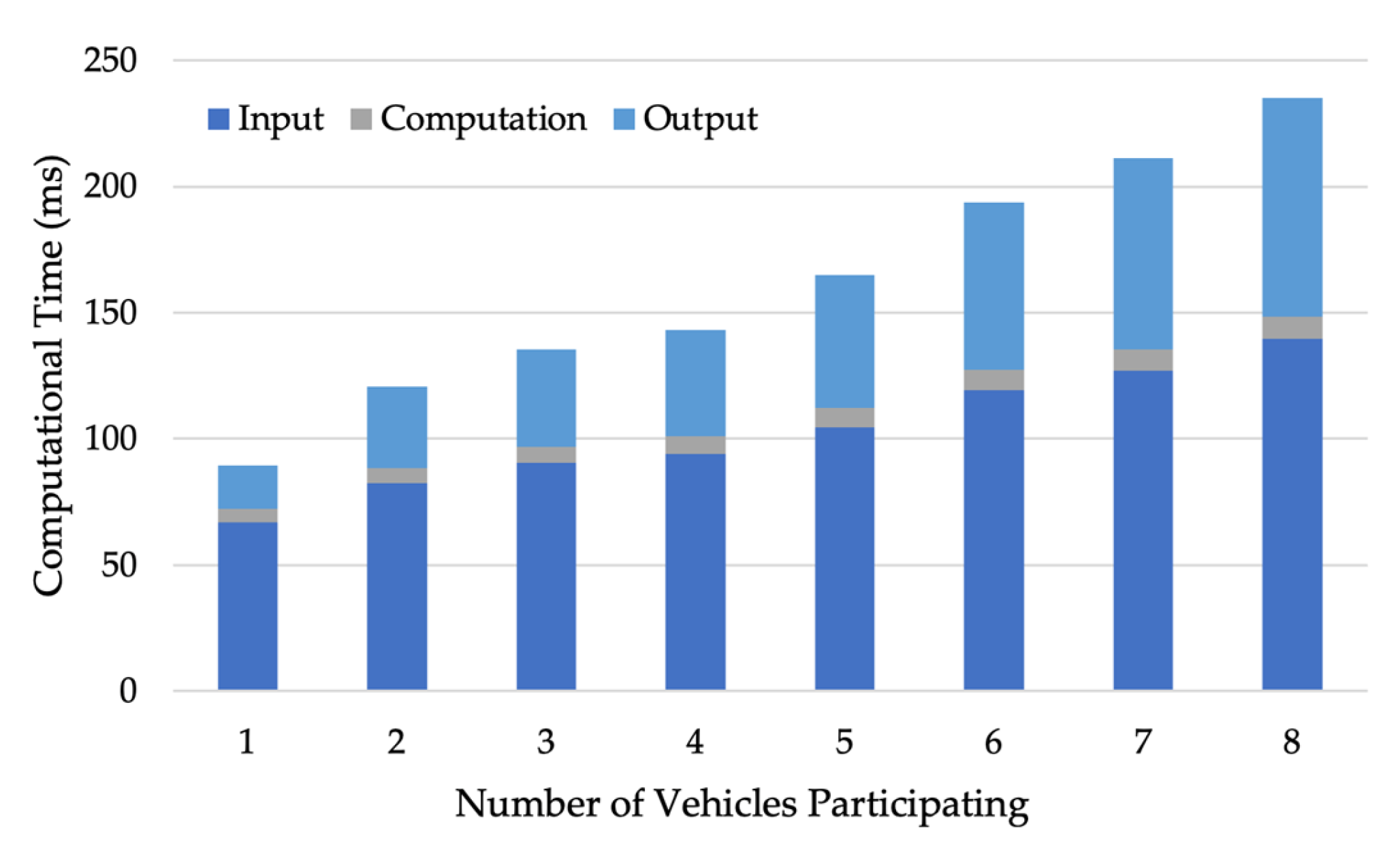
Figure 7 shows how the computational time of different stages changes with the number of participating vehicles (
given a compiled 8-party MPC protocol (
. The computational times of the input and output stages increase with
because fake vehicles’ inputs are pre-determined and do not require outputs. The computation time for the computation stage slightly increases as the number of fake vehicles decreases.
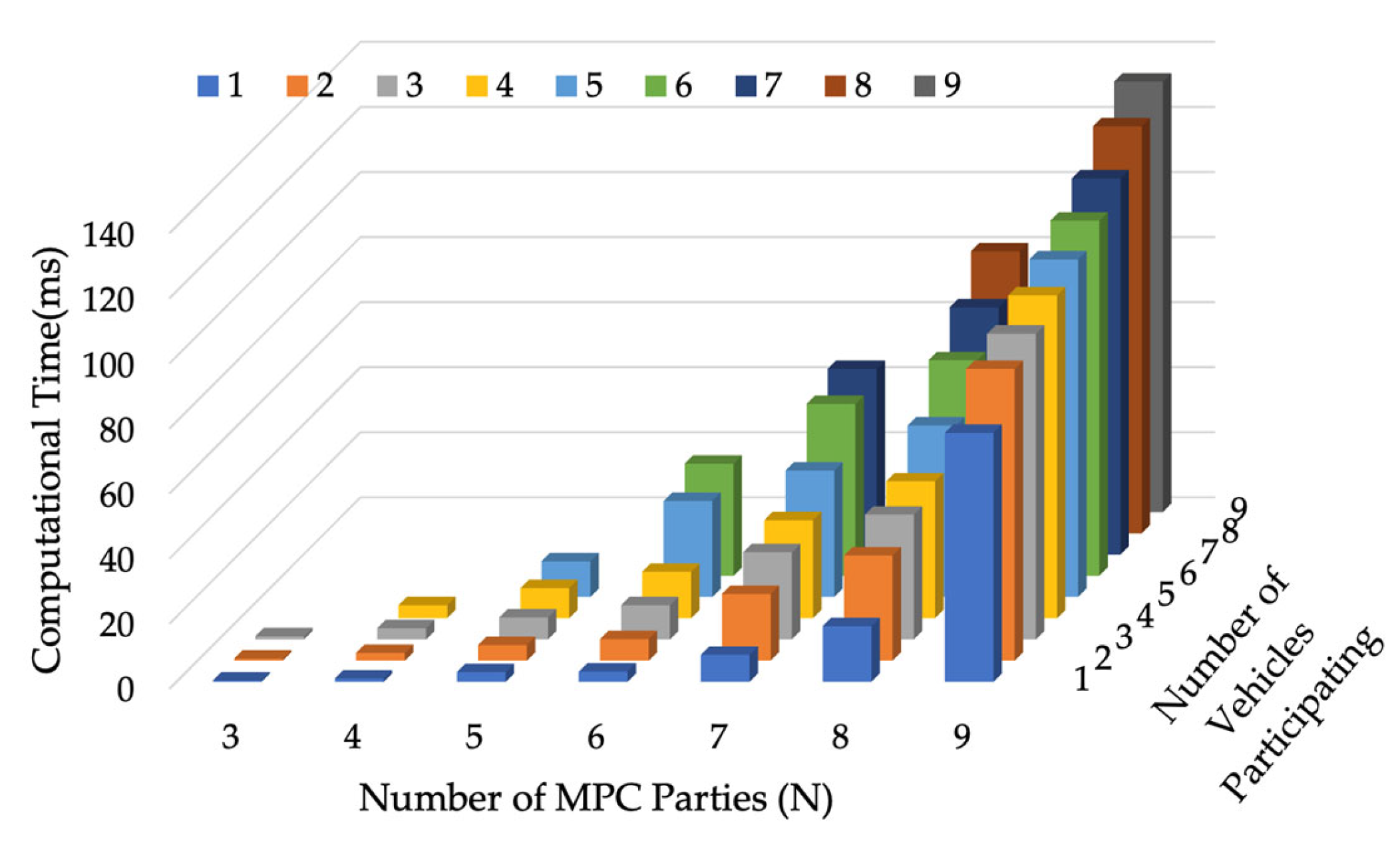
Figure 8 shows how the computational time of the output stage changes with
and
(
. It increases significantly with an increase in the number of MPC parties. To enable real-time implementation, the vehicle group size should be limited to 10. When more than 10 vehicles want to participate, they can be assigned into multiple vehicle groups with the same OD. The flow updating model can accommodate such settings. Also, the simulations were conducted on one desktop with one thread, while in real implementation, outputs can be generated parallelly on all participating vehicles, which can reduce the total computational time as well. Given the exponential increase in the MPC scheme computational time with the increase in MPC parties, a potential refinement is to subdivide the collaborative routing problem into smaller portions. This process would enable the MPC schemes to be executed with a reduced number of parties involved in each smaller subproblem. The results obtained from these smaller subproblems can then be aggregated by another MPC scheme. Structuring MPC in this hierarchical way is likely to address the computational issue associated with a large number of MPC parties.
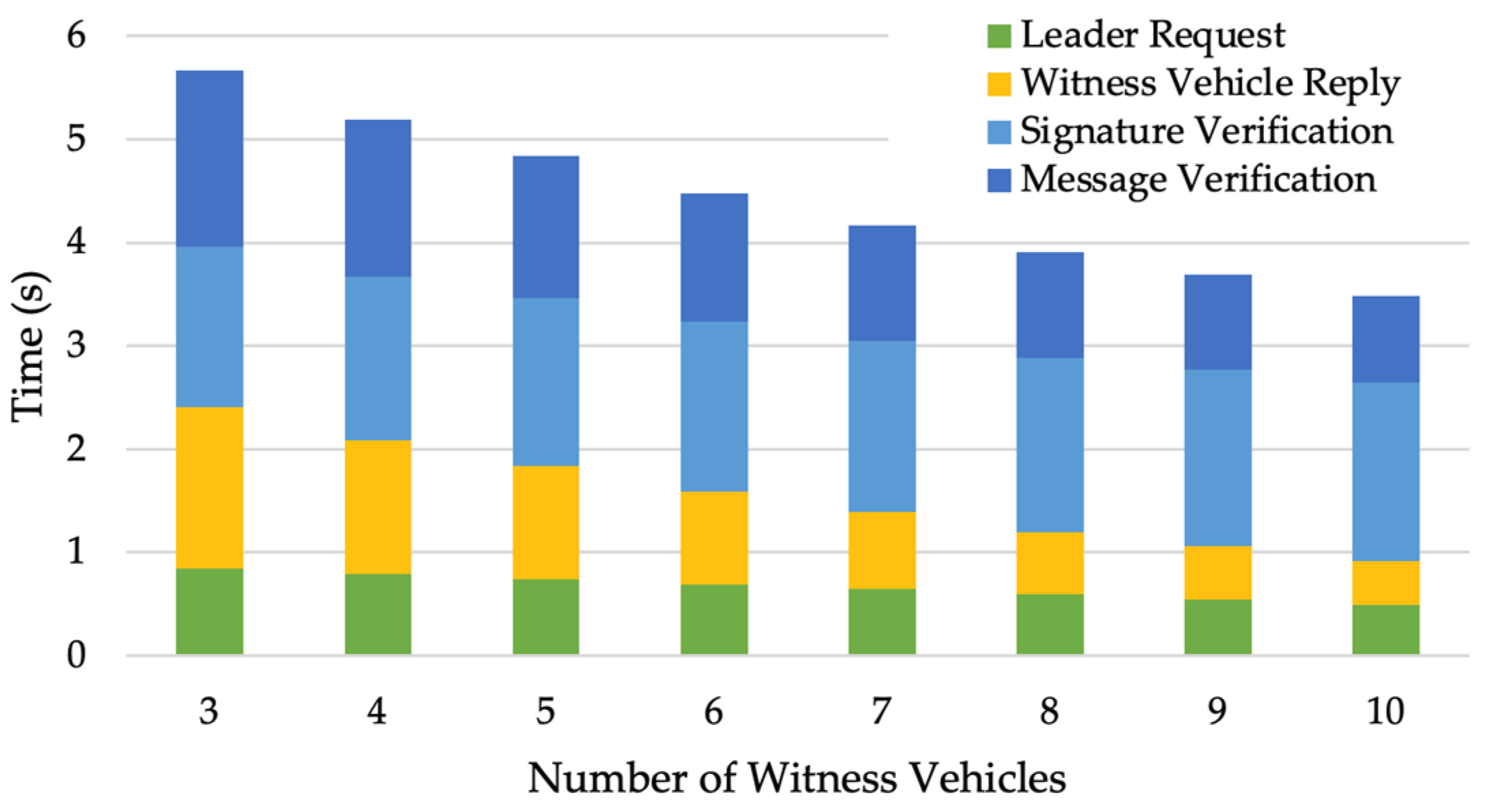
Next, the computational feasibility of the route validation scheme is evaluated. The results in
Figure 9 seem counter-intuitive at first glance; the time the leader vehicle takes to generate the request, the time that witness vehicles take to reply to the leader, and the total computational time all decrease as the number of witness vehicles increases. Since
is fixed, an increase in the number of witness vehicles will result in a decrease in the number of fake signatures that the leader generates; thus, the leader request time is reduced. Also, when witness vehicles generate the replies, the most time-consuming step is constructing the polynomial based on all fake signatures, which takes more time as the number of fake signatures increases. Therefore, the reply times of witness vehicles indicated by the yellow bars in
Figure 9 decrease as the number of witness vehicles increases.
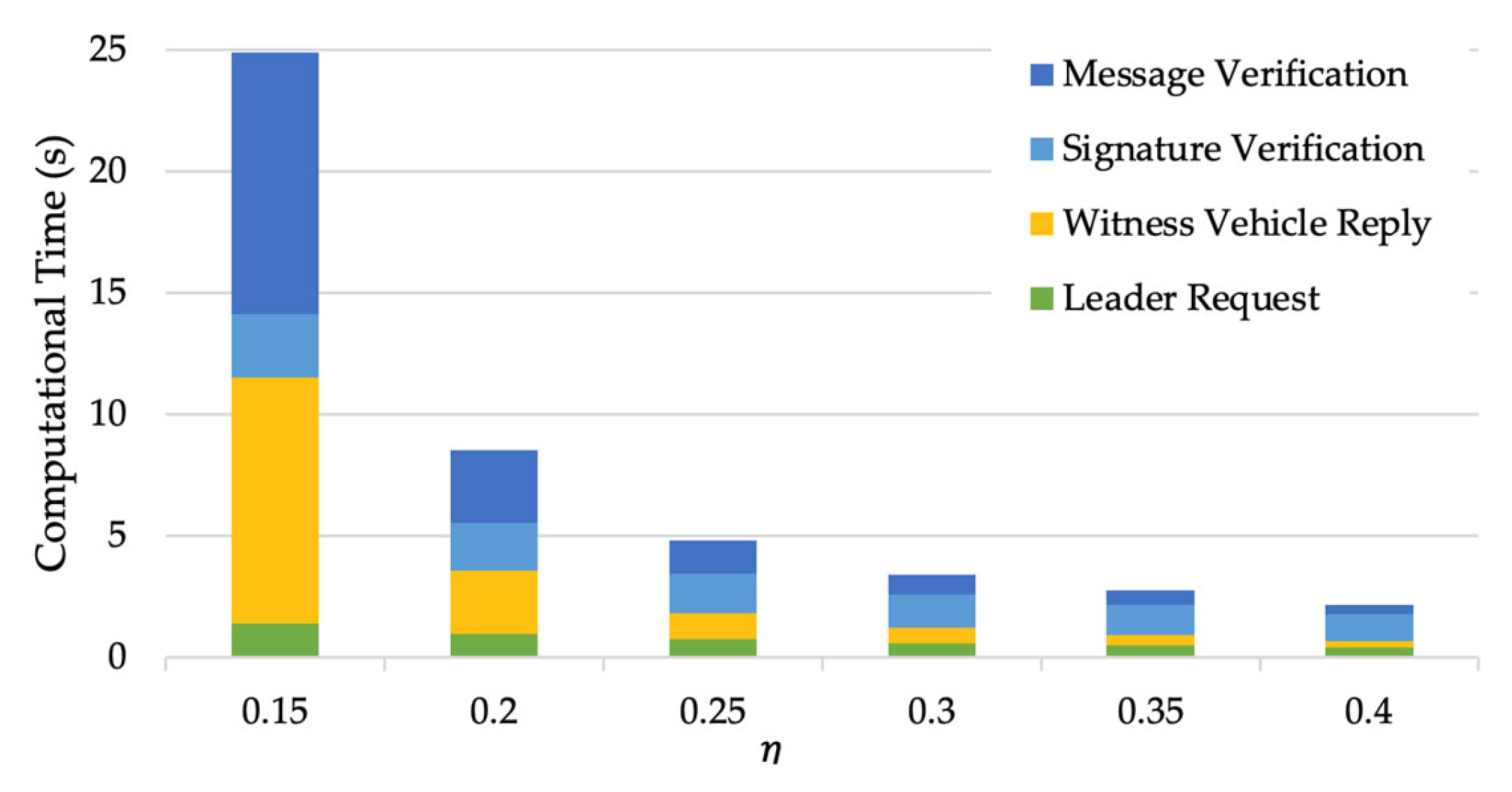
To evaluate how the value of the privacy protection parameter
influences the efficiency of the route validation scheme, we compare the computational time of simulations with different
when the number of required witness vehicles
.
Figure 10 shows that the computational time decreases significantly as
increases, especially the time that witness vehicles take to generate a reply message and the message verification time of
.
It should be noted that the collaborative routing scheme and route validation scheme encompass a variety of critical cryptographic operations, including the EC Elgamal key generation algorithm and signature algorithm. The time complexity of these components is substantially influenced by the parameters of the cryptographic settings, such as the order
of the addition group
. This section predominantly focused on analyzing the effects of parameters that hold greater relevance to the transportation context. In practical applications, the selection of these parameters must strike a balance between privacy security and computational efficiency. Securing privacy is certainly a crucial aspect, but the emphasis should equally be on computational feasibility, especially for vehicular applications. Generally, enhancing privacy protection could imply a potential trade-off in computational efficiency. For instance, using a smaller
affords better privacy protection for witness vehicles, as more fake signatures are blended into the position proof. However, this could concurrently increase the computational times, as indicated in
Figure 10, thus impacting the route validation scheme’s efficiency. Hence, a careful trade-off must be enabled in practice.
6. Conclusions
This study offers several significant contributions. First, collaborative routing facilitates personalization by accounting for user heterogeneities, leading to increased privacy concerns. To address this issue, the proposed method combines MPC with collaborative routing, thereby enabling privacy-preserving collaboration and showcasing a potential solution to privacy concerns associated with personalization. Second, the study introduces a V2V-based position proof approach as an alternative to the widely used GPS, which has raised concerns regarding the sharing of privacy-sensitive information. This alternative allows users to verify their travel history without disclosing their historical positions, a characteristic that has not been achieved previously. Third, the study presents a novel on-chain/off-chain structure that capitalizes on the tamper-resistance property of on-chain data while maintaining sensitive privacy pattern information off-chain. This design offers valuable insights into harnessing the benefits of blockchain technology while circumventing privacy risks associated with its inherent transparency. It should be emphasized that the suggested approach extends significantly beyond the scope of [
21], as the primary objective of the current study is to address potential privacy breaches arising from personalization within transportation systems. The MPC framework may be adapted to alternative application contexts involving personalized demand-side solutions. Furthermore, the position verification technique can be employed in additional applications necessitating the sharing of travel history, thereby safeguarding user privacy.
Potential directions for future research include: (i) making position proofs reusable for witness vehicles to reduce duplication of verification; (ii) refining the MPC structure to allow more vehicles in one vehicle group; and (iii) incorporating the incentive mechanism into the broader intelligent transportation system to form a sustainable incentive ecosystem, where users can spend the incentives they gain, such that pseudonyms do not need to be connected to bank accounts, further protecting privacy.