Research on Oracle Technology Based on Multi-Threshold Aggregate Signature Algorithm and Enhanced Trustworthy Oracle Reputation Mechanism
Abstract
1. Introduction
2. Related Work
- Provable (formerly known as Oraclize), a centralized oracle service, has been operational since 2015. It relies on auditable virtual machines, such as TLSNotary, and deploys a variety of signature algorithms, including ECDSA (Elliptic Curve Digital Signature Algorithm) [12] and other related signature schemes. These algorithms are vital components in constructing authenticity proofs to ensure the authenticity and integrity of data [13].
- TownCrier is a system that provides secure centralized oracle data transmission services. It utilizes data verification through TLSNotary within a Trusted Execution Environment (TEE). The RSA (Rivest–Shamir–Adleman) signature algorithm plays a crucial role in contributing to data authenticity and integrity verification within this framework [14].
- TLS-N is the first oracle solution that relies on content-extractable signatures, making use of the BLS (Boneh–Lynn–Shacham) signature scheme to generate non-interactive session proofs from blockchain smart contracts. The BLS signature scheme plays a crucial role in TLS-N’s functionality by guaranteeing secure and verifiable data transmission [15].
- The DOS Network is a scalable Layer-2 protocol that employs threshold signatures to achieve consensus among nodes. This consensus mechanism is enabled through the frequent use of the BLS (Boneh–Lynn–Shacham) signature scheme, which ensures secure data transmission and verifiable computation oracles within the network [16].
- Chainlink: Chainlink, operating within a distributed trust model, relies on Chainlink nodes and oracle smart contracts. In the context of data verification, Chainlink often utilizes ECDSA (Elliptic Curve Digital Signature Algorithm) and similar signature schemes to ensure the authenticity and security of data transmitted between smart contracts and web APIs [17].
- Truora, an open-source oracle solution developed by WeBank, is designed for consortium blockchains. It employs the RSA (Rivest–Shamir–Adleman) signature algorithm in both centralized and distributed hybrid modes, playing a pivotal role in providing authenticity proofs for acquired data and enhancing data security and integrity [18]. This implementation is crucial for ensuring the reliability and trustworthiness of the data within consortium blockchains, thereby contributing to the overall security and stability of the system.
3. Materials and Methods
3.1. Implementation of Consortium Blockchain and Chainlink
- User smart contracts initiate data requests to the oracle smart contracts;
- Data are sent to the oracle smart contracts by external data sources;
- The oracle smart contracts return data to the user smart contracts, providing feedback.
- Blockchain Network Setup for Agricultural Product Traceability:
- In this oracle solution, a distributed network is constructed using Hyperledger Fabric, a consortium blockchain platform.
- The network encompasses multiple nodes, each maintaining a replica of the ledger data to ensure the comprehensive traceability of agricultural products.
- Identity Authentication and Authorization:
- Users of the oracle solution within the agricultural product traceability system authenticate their identities through a mechanism designed to protect sensitive data.
- Successful authentication leads to the granting of user authorization, specifying their operational scope and permissions regarding agricultural product traceability.
- Creation of Transaction Requests for Agricultural Product Traceability:
- Users submit transaction requests through the oracle solution’s business system, focusing on activities related to agricultural product traceability.
- Transaction requests include detailed information, such as the type of transaction (e.g., data transfer or data querying), the identities of the parties involved, and the transaction amount concerning agricultural products.
- Broadcasting of Transaction Requests Across the Agricultural Product Traceability Network:
- Transaction requests are sent to and broadcasted across all nodes in the blockchain network, ensuring the complete traceability of agricultural products.
- Each node in the network receives transaction requests, adding them to a pending transaction pool, thus facilitating the comprehensive traceability process.
- Transaction Verification and Execution for Agricultural Product Traceability:
- Nodes in the blockchain network meticulously verify transaction requests to ensure the legality and validity of agricultural product traceability processes.
- Verification procedures include thorough checks of digital signatures, validation of the identities of the parties involved, and adherence to predefined rules for transaction amounts within the agricultural product traceability framework.
- Once verified, nodes execute the transactions and diligently update the ledger data, guaranteeing the precision of agricultural product traceability.
- Transaction Confirmation and Packaging to Enhance Agricultural Product Traceability:
- Nodes generate a new block following the successful execution of transactions, packaging the transactions from the pending transaction pool into it.
- The new block acts as a secure repository for verified and executed transactions, contributing to the accuracy of agricultural product traceability.
- Utilization of Consensus Mechanisms for Enhanced Agricultural Product Traceability:
- The agricultural product traceability process relies on consensus mechanisms to validate the generation of new blocks.
- Common consensus algorithms utilized in this oracle solution include Byzantine Fault Tolerance (BFT) and Proof of Stake (PoS) algorithms [26], ensuring the security of agricultural product traceability.
- Nodes actively participate in consensus processes to verify the legality and consistency of adding new blocks to the blockchain, specifically concerning agricultural product traceability.
- Integration of Chainlink Oracle Nodes for Agricultural Product Traceability:
- Within the blockchain network, Chainlink Oracle nodes play a pivotal role in providing external data to smart contracts, a crucial aspect of agricultural product traceability.
- When a transaction request necessitates external data, the oracle solution seamlessly interacts with Chainlink Oracle nodes, which fetch data from various off-chain sources, ensuring the accuracy and reliability of data related to agricultural product traceability.
- The integrated Chainlink nodes ensure that the blockchain network can securely access real-world data, execute transactions based on these data, and maintain a high level of trust within the agricultural product traceability framework.
- Blockchain Update:
- Upon reaching a consensus, a new block is appended to the end of the blockchain, securing transaction records permanently within the agricultural product traceability system.
3.2. Blinding Mechanism Based on Block Height
- Block Height Parameter Generation: In the new blind signature mechanism, both signers and verifiers generate block height parameters based on the blockchain’s block height. The block height is an ever-increasing value on the blockchain and can be considered an immutable global timestamp.
- Block Height-Dependent Blinding: During the process of signature generation and verification, block height parameters are used to blind key parameters in the signature process.
- Signature Generation: Signers use block height parameters to generate blind signatures, ensuring that the signature generation depends on the current blockchain block height. This enhances the verifiability of signatures, as verifiers can check whether the signature is related to a specific block height.
- Signature Verification: Verifiers need to be aware of the relevant block height when verifying the signatures. The validity of the signature depends on whether the block height parameters match the signature.
3.3. Principle and Implementation of MTAS Signature Technology
- 1.
- Public-Key Generation:
- The system administrator generates a set of public–private-key pairs and publishes the public keys for users participating in the signature process.
- The public key includes the following parameters: . Here, p and q are two large prime numbers, g is a primitive root modulo p, and h is the exponent of g. x represents the private key.
- Signers and verifiers generate the parameter, representing the current blockchain block’s height.
- 2.
- Signature Generation:Assuming there are signers who possess the private keys , the following steps are performed when a user wants to generate a signature:
- Choose a random number r and compute . This temporary public key R is used in the signature process.
- Calculate the hash value of the message to be signed, where H is a hash function.
- Compute the blockHeight-dependent blinding parameter:
- Based on the current scenario’s requirements, automatically set a flexible threshold value to ensure security and efficiency. Compute it as follows:Here, represents factors related to the application scenario, such as data sensitivity and risk tolerance. We can use a value between 0 and 1 to indicate its weight, with 1 representing the highest weight. represents factors related to system performance, such as computing resources, network bandwidth, and latency requirements. We can use a value between 0 and 1 to indicate its weight, with 1 representing the highest weight. Here, we use to denote the inverse weight of performance factors, meaning that the higher the performance, the lower the weight. represents the weight of security indicators, used to measure the importance of security, such as avoiding private-key leakage and resisting attacks. We can use a value between 0 and 1 to indicate its weight, with 1 representing the highest weight. Here, we use to denote the quadratic weight of security indicators, emphasizing their importance. represents the weight of efficiency indicators, used to measure the importance of efficiency, such as computational and communication overhead limitations. We can use a value between 0 and 1 to indicate its weight, with 1 representing the highest weight. represents the adjustment parameter used to balance security and efficiency. It can be adjusted based on actual requirements. For example, increasing the value of can reduce the threshold value, thereby improving efficiency but potentially decreasing security.
- If the number of signers participating in the signature reaches or exceeds the threshold value t, perform the signature calculation for . Use instead of R in the signature calculation:where is the signature algorithm.
- Sum up the signatures that satisfy the threshold condition:
- 3.
- Signature Verification:When receiving a signature message , the verifier needs to perform the following steps for verification:
- First, verify whether R is a valid public key by checking whether it satisfies the conditions during the public-key generation phase.
- Calculate the hash value of the message to be verified, ensuring that the hash value used in the verification process is consistent with the one generated during the signature generation phase.
- Recalculate the blockHeight-dependent blinding parameter using the received blockHeight.
- Based on the threshold value set for the current scenario, compute the verification formula:where g and p are parameters from the public key, and t is the threshold value.
- For each signer participating in the signature, compute the verification formula:where is the temporary public key of signer i, and is the signature result of signer i.
- If verification formulas (6) and (7) hold true for all signers i, the signature is considered verified.
| Algorithm 1 MTAS Signature Algorithm |
|
3.4. Security Proof for MTAS Signature Scheme with BlockHeight-Based Blinding
3.4.1. Security Assumptions
- Discrete Logarithm Assumption: The security relies on the computational infeasibility of solving discrete logarithm problems in the finite field defined by large prime numbers p and q.
- Primitive Root Assumption: The selection of g as a primitive root modulo p ensures the difficulty of the discrete logarithm problem.
- BlockHeight Security: We assume the secure generation and utilization of the blockHeight parameter, considering it a trusted and tamper-resistant global timestamp.
- Hash Function Security: The hash function H is assumed to be collision-resistant and preimage-resistant.
- Randomness Assumption: The randomness introduced by the selection of random numbers is assumed to be uniformly distributed and unpredictable.
3.4.2. ECDSA Preliminaries and Hardness Assumptions
- ECDSA Preliminaries: ECDSA is a widely used digital signature algorithm that operates on elliptic curves over finite fields. In ECDSA, key pairs are generated based on the difficulty of solving the elliptic curve discrete logarithm problem. The security of ECDSA relies on the computational infeasibility of deriving a private key from its corresponding public key.
- Elliptic Curve Discrete Logarithm Problem: The elliptic curve discrete logarithm problem involves finding the exponent x in the equation for a given base point P and a point Q on the elliptic curve. This problem is believed to be computationally hard, forming the basis for the security of ECDSA.
- Key Generation Security: In the MTAS, the security of key generation is directly linked to the assumed hardness of the elliptic curve discrete logarithm problem. The generation of the public key y from the private key x is secure because deriving x from y necessitates solving the elliptic curve discrete logarithm problem, which is considered infeasible within the chosen elliptic curve.
- Signature Generation Security: The MTAS algorithm enhances signature generation security by introducing a blockHeight-based blinding parameter . The security analysis of signature generation incorporates the computational infeasibility of solving the elliptic curve discrete logarithm problem, particularly with the added complexity introduced by the blockHeight.
- Signature Verification Security: The security of signature verification in the MTAS relies on the robustness of ECDSA. The verification process involves confirming the validity of the public key, recalculating the blockHeight-dependent blinding parameter , and applying verification formulas. The inherent hardness of the elliptic curve discrete logarithm problem ensures the integrity of the verification process.
3.4.3. Security Proof Overview
- Key Generation Security:The security of key generation remains based on the assumed hardness of the discrete logarithm problem. Given , an adversary attempting to derive x from y would need to solve the discrete logarithm problem, which is considered computationally infeasible in the defined finite field.
- Signature Generation Security:The blockHeight-dependent blinding parameter is introduced to tie each signature to a specific blockHeight, mitigating the potential insecurity associated with the random threshold value t. The security of the signature generation process is contingent upon the computational infeasibility of solving the discrete logarithm problem with the added complexity introduced by the blockHeight.Let S be the signature set and t be the threshold value. For a valid signature, the following condition must hold:The probability of an adversary producing a valid signature without knowledge of the private key x is negligible due to the inherent security properties of the discrete logarithm problem.
- Security of : The security of the blockHeight-dependent blinding parameter is crucial. Its computation involves the temporary public key R and the blockHeight, introducing additional complexity to the discrete logarithm problem.
- Signature Verification Security:The verification process involves confirming the validity of the public key, recalculating the blockHeight-dependent blinding parameter , and applying verification formulas. The security of the verification process relies on the difficulty of deriving a valid signature without the private key.The verification formula iswhere g, p, t, , and are parameters from the public key.For each signer i with a temporary public key and signature , the verification formula isIf an adversary attempts to produce a signature without the private key, the verification equations are unlikely to hold for a sufficient number of signers due to the computational infeasibility of solving the discrete logarithm problem.
3.4.4. Formal Proof
- Choose a random number r.
- Compute .
- Calculate the hash value .
- Compute the blockHeight-dependent blinding parameter: .
- Based on the current scenario’s requirements, automatically set a flexible threshold value t to ensure security and efficiency.
- If the number of signers participating in the signature reaches or exceeds the threshold value t, use instead of R to calculate the signature: .
3.4.5. Proof of Correctness
- AssumptionsWe assume the underlying security of the MTAS signature algorithm based on the discrete logarithm problem.
- Key GenerationLet x be the private key and y be the corresponding public key, calculated as follows:
- Signature GenerationWhen generating a signature for a message M, Alice chooses a random k and computes the intermediate value K:The hash value e of the message is computed as . The signature s is then calculated:
- Signature VerificationUpon receiving the message M and the signature , Bob verifies the signature using the public key y. Bob checks whether y is a valid public key and then computes the hash value e:Bob calculates the temporary values and :Finally, Bob checks whether . If this equation holds, the signature is considered valid.
3.4.6. Advantages of MTAS with Block-Height-Based Blinding Mechanism
- Enhanced Security: The incorporation of a block-height-dependent blinding parameter adds an additional layer of security to the signature generation process. By leveraging the continuously increasing and tamper-resistant nature of blockchain block heights, the algorithm strengthens its resistance to certain types of attacks, such as replay attacks and signature forgery.
- Temporal Dependency: The blinding parameter, determined by the current block height, introduces temporal dependency into signature generation. This means that each signature is uniquely tied to a specific point in time, contributing to the prevention of signature reuse and providing a level of temporal authenticity.
- Protection Against Threshold Randomization: In the MTAS Algorithm 1 proposed above, the random threshold value t introduces an element of randomness that could potentially be exploited. The block-height-based blinding mechanism mitigates this randomness by tying the threshold to a deterministic and publicly verifiable parameter, namely, the block height.
- Blockchain Integration: Leveraging the block height from a blockchain enhances the algorithm’s integration with blockchain-based systems. This integration aligns with the underlying principles of transparency and immutability associated with blockchain technology.
3.5. Reputation Mechanism for Oracle Nodes
3.5.1. The Principle of ETORM
| Algorithm 2 ETORM Reputation Mechanism Algorithm |
| Require: |
|
3.5.2. Formal Proof
- According to the precondition, is a valid node in , and is a valid task.
- Call ExecuteTaskAndCollectData, which executes the task and collects data.
- According to the postcondition, is still in , and its data have been updated with the result of executing the task.
- According to the precondition, is a valid node in , and is valid.
- Call UpdateReputation, which updates ’s reputation based on the submitted data.
- According to the postcondition, is still in , and its reputation has been updated based on the submitted data.
4. Experimental Design and Results Analysis
4.1. Experimental Environment
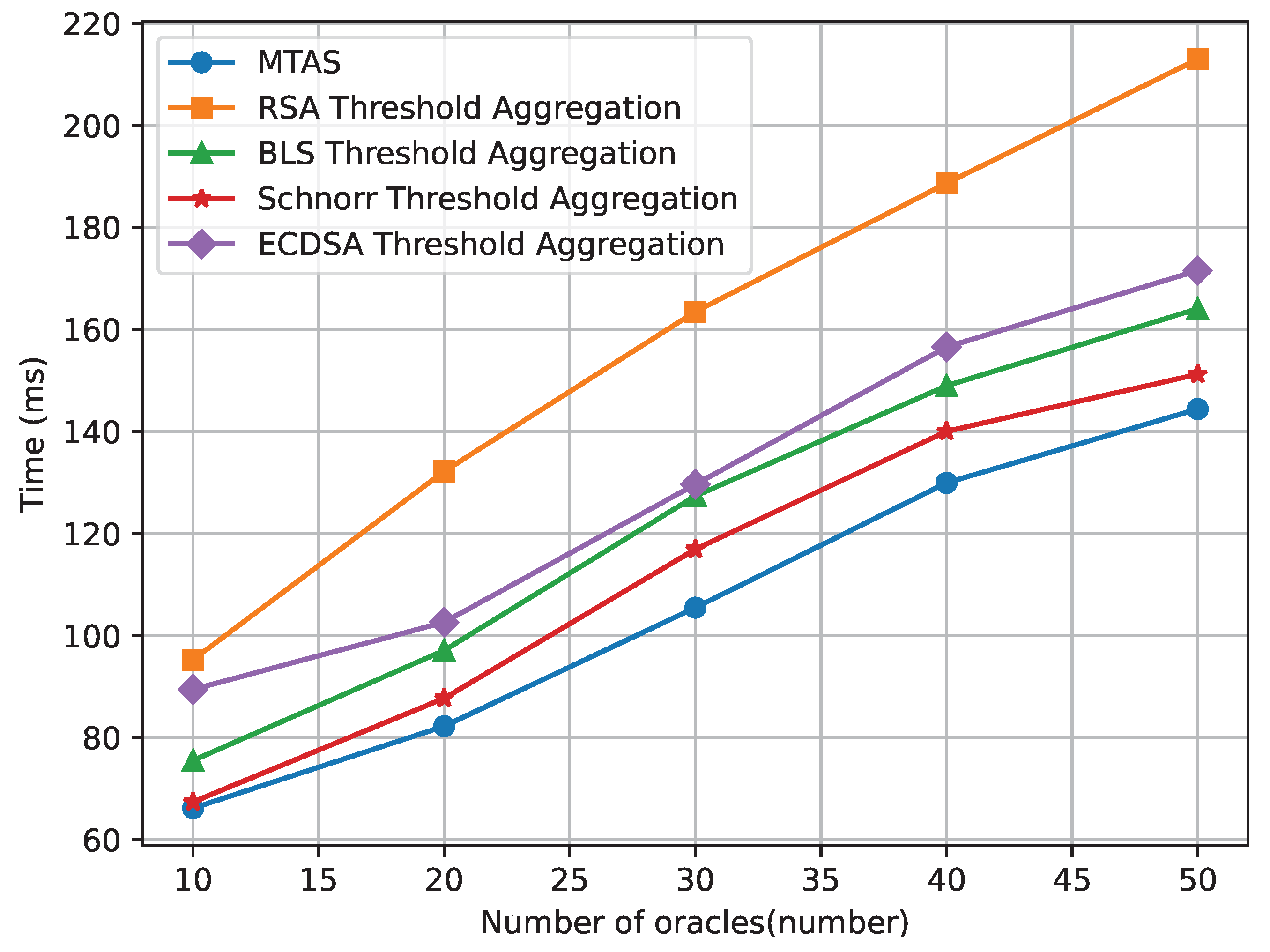
4.2. Comparison of Time Consumption of Each Signature Scheme
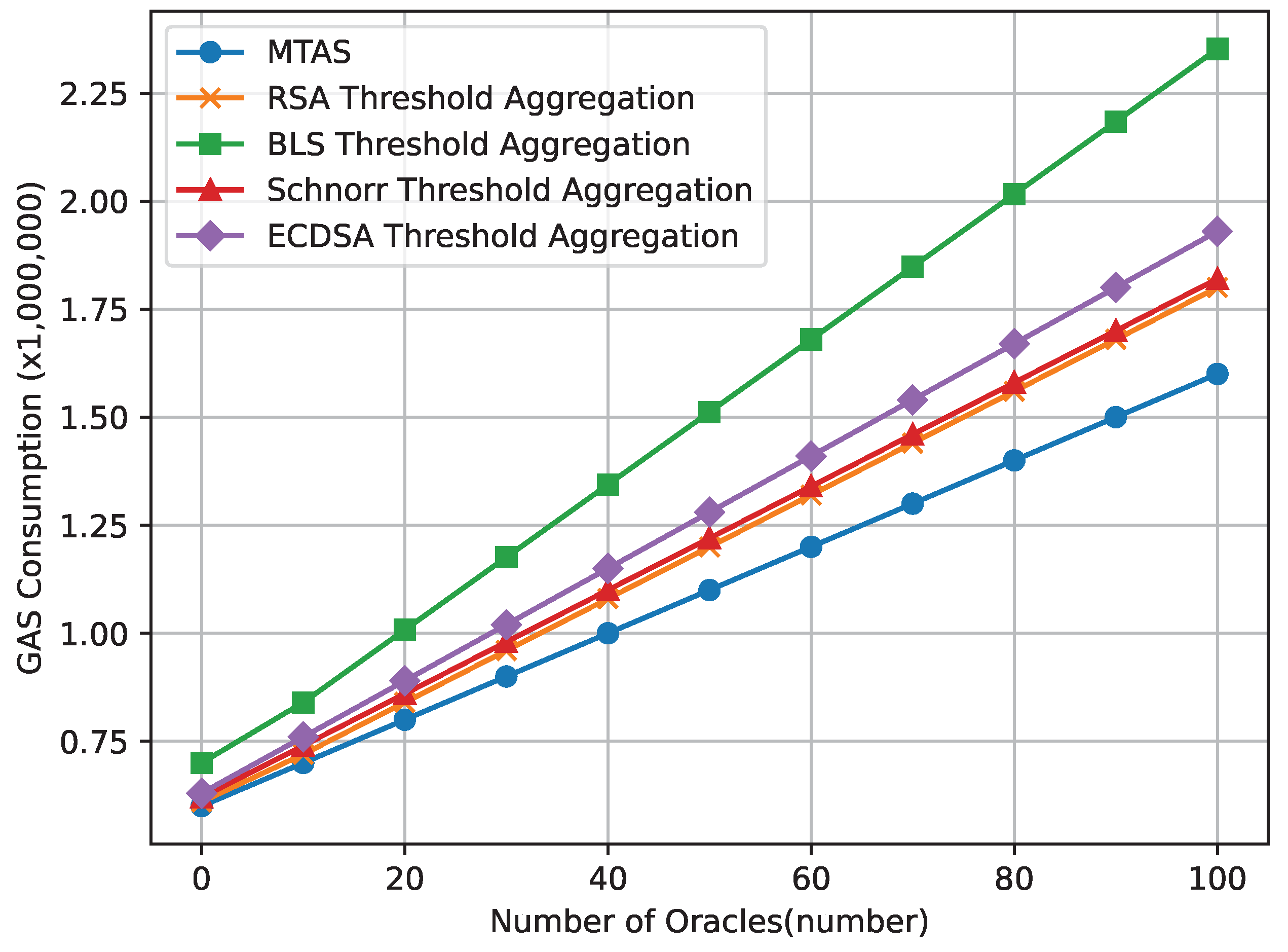
4.3. Comparison of GAS Consumption of Each Signature Scheme
4.4. Reputation Mechanism Evaluation
- The total number of accepted requests by the oracle, comprising both executed and pending requests;
- The number of completed requests, which is used to calculate completion-rate bonus points;
- Bonus points, which are determined by counting the total number of requests and are used to judge whether the contract is acceptable compared to the other oracles’ responses, generally measured as the average of the total number of accepted tasks and the total number of completed tasks;
- Average response-time-score reduction;
- The cumulative number of punishment points, where punishment is due to the improper behavior of the prophet (copying the answers or disclosing or using the service request data), and pledges are deducted from the LINK.
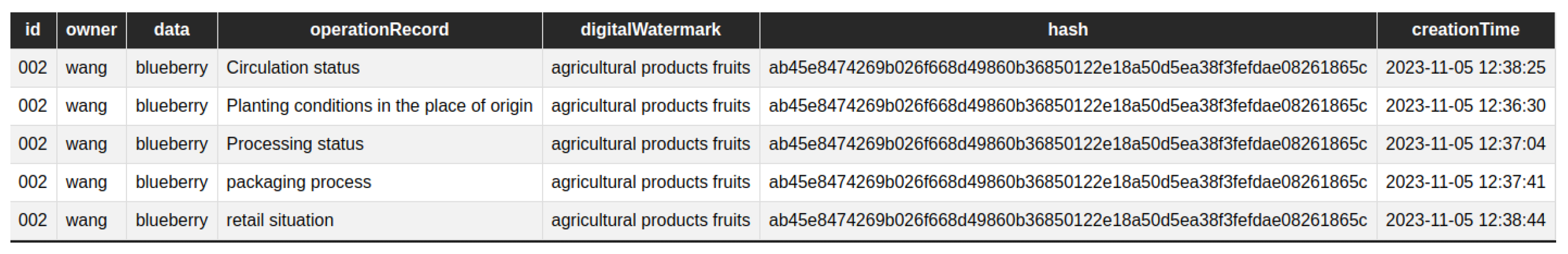
4.5. Agricultural Product Traceability Scenarios
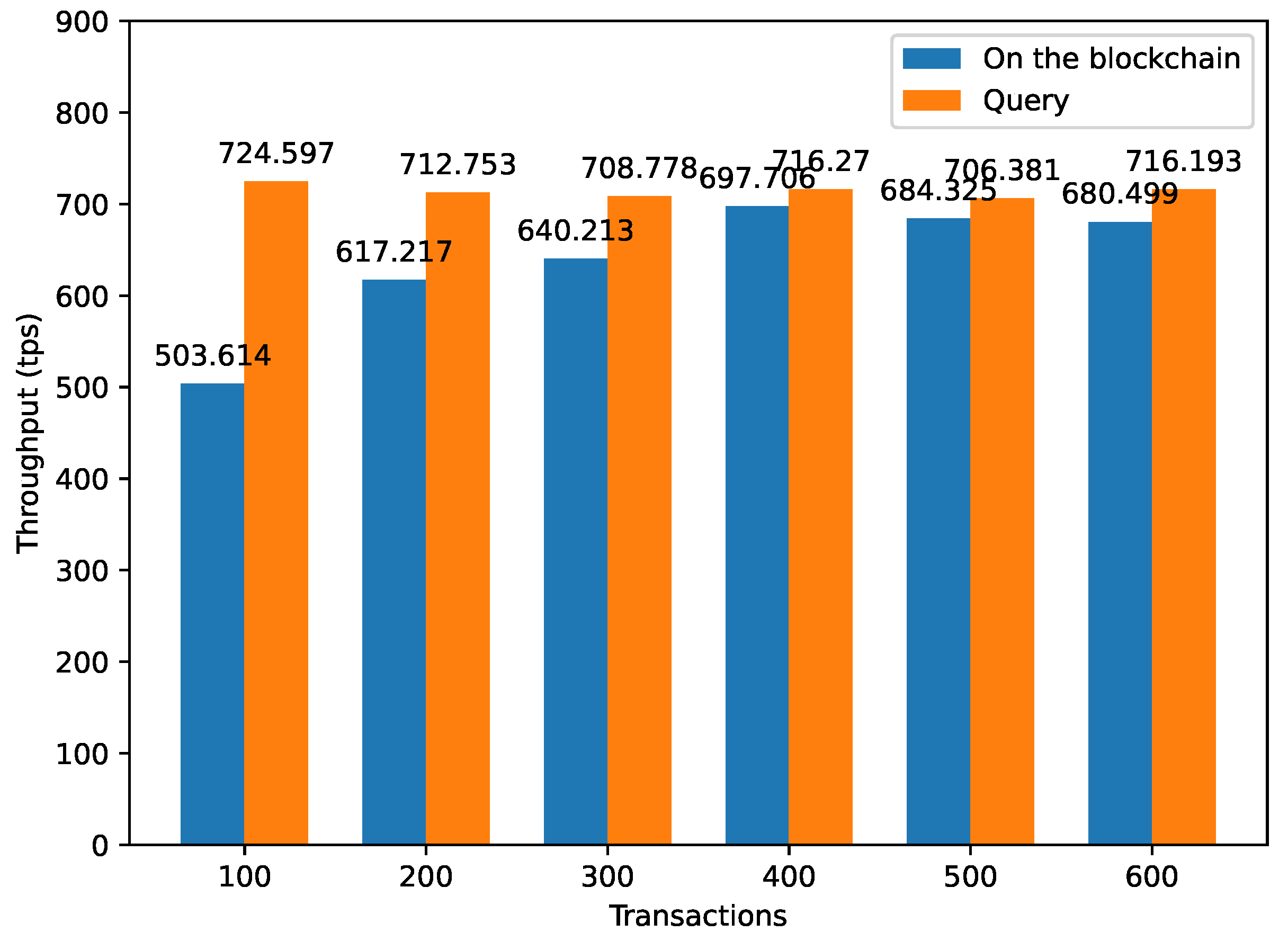
4.6. Throughput Evaluation
5. Evaluation
6. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Consulted 2008. [Google Scholar] [CrossRef]
- Gigli, L.; Zyrianoff, I.; Montori, F.; Aguzzi, C.; Roffia, L.; Felice, M.D. A Decentralized Oracle Architecture for a Blockchain-Based IoT Global Market. IEEE Commun. Mag. 2023, 61, 86–92. [Google Scholar] [CrossRef]
- Dong, J.; Song, C.; Sun, Y.; Zhang, T. DAON: A Decentralized Autonomous Oracle Network to Provide Secure Data for Smart Contracts. IEEE Trans. Inf. Forensics Secur. 2023, 18, 5920–5935. [Google Scholar] [CrossRef]
- Maurya, C.; Chaurasiya, V.K. Collusion-resistant and privacy-preserving data sharing scheme on outsourced data in e-healthcare system. Multimed Tools Appl. 2023, 82, 40443–40472. [Google Scholar] [CrossRef]
- Sadawi, A.A.; Hassan, M.S.; Ndiaye, M. On the Integration of Blockchain With IoT and the Role of Oracle in the Combined System: The Full Picture. IEEE Access 2022, 10, 92532–92558. [Google Scholar] [CrossRef]
- Godawatte, K.; Branch, P.; But, J. Blockchain health sensor network performance analysis on low powered microcontroller devices. In Proceedings of the 2023 IEEE International Systems Conference (SysCon), Vancouver, BC, Canada, 17–20 April 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Yang, F.; Lei, L.; Chen, L. Method of Interaction between Blockchain and the World outside the Chain based on Oracle Machine. In Proceedings of the 2022 IEEE 8th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Jinan, China, 6–8 May 2022. [Google Scholar]
- Sugauchi, S.; Obana, S. Fully Subliminal-Free Schnorr Signature for Nonce. In Proceedings of the 2022 Tenth International Symposium on Computing and Networking (CANDAR), Himeji, Japan, 21–24 November 2022; pp. 179–185. [Google Scholar]
- Mao, W.; Jiang, P.; Zhu, L. BTAA: Blockchain and TEE-Assisted Authentication for IoT Systems. IEEE Internet Things J. 2023, 10, 12603–12615. [Google Scholar] [CrossRef]
- Jyothilakshmi, K.B.; Robins, V.; Mahesh, A.S. A Comparative Analysis between Hyperledger Fabric and Ethereum in Medical Sector: A Systematic Review. In Sustainable Communication Networks and Application; Karrupusamy, P., Balas, V.E., Shi, Y., Eds.; Lecture Notes on Data Engineering and Communications Technologies; Springer: Singapore, 2022; Volume 93. [Google Scholar]
- Kaleem, M.; Shi, W. Demystifying Pythia: A Survey of ChainLink Oracles Usage on Ethereum. In Financial Cryptography and Data Security. FC 2021 International Workshops. FC 2021; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2021; Volume 12676. [Google Scholar] [CrossRef]
- Xiong, H.; Jin, C.; Alazab, M.; Yeh, K.H.; Wang, H.; Gadekallu, T.R.; Wang, W.; Su, C. On the Design of Blockchain-Based ECDSA With Fault-Tolerant Batch Verification Protocol for Blockchain-Enabled IoMT. IEEE J. Biomed. Health Inform. 2022, 26, 1977–1986. [Google Scholar] [CrossRef] [PubMed]
- Olding, W.; Tu, E.; Nava, C. Zipline-A Fault-Proof Blocker Header Oracle. In Proceedings of the 2023 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Dubai, United Arab Emirates, 1–5 May 2023; pp. 1–4. [Google Scholar] [CrossRef]
- Aljabri, A.; Jemili, F.; Korbaa, O. Intrusion detection in cyber-physical system using rsa blockchain technology. Multimed Tools Appl. 2023, 1–22. [Google Scholar] [CrossRef]
- Zhou, Y.; Yu, L.; Jiang, Z.; Zhi, Z.; Kang, J.; Han, Z. An Improved Spectrum Trading Design Based on Dynamic Credit Aggregate-Signature Blockchain. IEEE Wirel. Commun. Lett. 2023, 12, 625–629. [Google Scholar] [CrossRef]
- Sun, Z.; Zhao, P.; Wang, C.; Zhang, X.; Cheng, H. An Efficient and Secure Trading Framework for Shared Charging Service Based on Multiple Consortium Blockchains. IEEE Trans. Serv. Comput. 2023, 16, 2437–2450. [Google Scholar] [CrossRef]
- Schmeelk, S.; Rosado, B.; Black, P.E. Blockchain Smart Contracts Static Analysis for Software Assurance. In Intelligent Computing; Arai, K., Ed.; Lecture Notes in Networks and Systems; Springer: Cham, Switzerland, 2021; Volume 284. [Google Scholar]
- Gupta, R.; Shankar, R. Managing food security using blockchain-enabled traceability system. Benchmarking Int. J. 2023. [Google Scholar] [CrossRef]
- Shang, Y. Efficient and Secure Algorithm: The Application and Improvement of ECDSA. In Proceedings of the 2022 International Conference on Big Data, Information and Computer Network (BDICN), Sanya, China, 20–22 January 2022. [Google Scholar]
- Sober, M.; Scaffino, G.; Spanring, C.; Schulte, S. A Voting-Based Blockchain Interoperability Oracle. In Proceedings of the 2021 IEEE International Conference on Blockchain (Blockchain), Melbourne, Australia, 6–8 December 2021. [Google Scholar]
- Liu, W.; Guo, L.; Xia, Y.; She, W.; Tian, Z. Blockchain Oracle Data Transmission Model Based on Threshold Aggregation Signatures. J. Zhengzhou Univ. Nat. Sci. Ed. 2023, 55, 23–29. [Google Scholar]
- Diao, Z.; Wang, Q.; Gong, B. MSKNP: Multistage Key Negotiation Protocol for IoT-Blockchain Environment. IEEE Internet Things J. 2023, 10, 11975–11984. [Google Scholar] [CrossRef]
- Huang, M.; Cao, S.; Li, X.; Huang, K.; Zhang, X. Defending Data Poisoning Attack via Trusted Platform Module and Blockchain Oracle. In Proceedings of the ICC 2022-IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 1245–1250. [Google Scholar]
- Mishra, R.K.; Yadav, R.K.; Nath, P. Blockchain DrivenAccess control architecture for the internet of things. Multimed Tools Appl. 2023, 82, 31397–31421. [Google Scholar] [CrossRef]
- Capocasale, V.; Gotta, D.; Musso, S.; Perboli, G. A Blockchain, 5G and IoT-based transaction management system for Smart Logistics: An Hyperledger framework. In Proceedings of the 2021 IEEE 45th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 12–16 July 2021; pp. 1285–1290. [Google Scholar]
- Tang, D.; He, P.; Fan, Z.; Wang, Y. Pool competition and centralization in PoS blockchain network. Appl. Econ. 2023, 1–20. [Google Scholar] [CrossRef]
- Zhang, Z.; Chen, H.; Chen, Y. A Provable Secure Signature in the Quantum Random Oracle Model. In Proceedings of the 2022 International Conference on Blockchain Technology and Information Security (ICBCTIS), Huaihua City, China, 15–17 July 2022; pp. 43–46. [Google Scholar]
- Zhang, X.; Chen, T.; Yu, Y.; Duan, Z.; Gao, J. Blockchain data sharing model based on attribute-based encryption. Comput. Appl. Res. 2021, 38, 2278–2283. [Google Scholar]
- Dou, W.; Cui, Z.; Dai, Q.; Song, J.; Wang, D.; Gao, Y.; Wang, W.; Wei, J.; Chen, L.; Wang, H.; et al. Detecting Isolation Bugs via Transaction Oracle Construction. In Proceedings of the 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE), Melbourne, Australia, 14–20 May 2023; pp. 1123–1135. [Google Scholar] [CrossRef]
- Maynard, J.; Rezaei, A. DK Lock: Dual Key Logic Locking Against Oracle-Guided Attacks. In Proceedings of the 2023 24th International Symposium on Quality Electronic Design (ISQED), San Francisco, CA, USA, 5–7 April 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Yu, Z.; Sheng, X.; Xie, G.; Xu, Y.; Sun, Y. Online Fabric Defects Detection Using Convolutional Neural Networks with Two Frameworks. AATCC J. Res. 2023, 10, 356–366. [Google Scholar] [CrossRef]
- Goswami, S.; Danish, S.M.; Zhang, K. Towards a middleware design for efficient blockchain oracles selection. In Proceedings of the 2022 Fourth International Conference on Blockchain Computing and Applications (BCCA), San Antonio, TX, USA, 5–7 September 2022; pp. 55–62. [Google Scholar]
- Rosero-Montalvo, P.D.; Tözün, P.; Hernandez, W. Time-Series Forecasting to Fill Missing Data in IoT Sensor Data. IEEE Sensors Lett. 2023, 7, 5502804. [Google Scholar] [CrossRef]





| Equipment | Parameter |
|---|---|
| CPU | 11th Gen Intel(R) Core(TM) i5-11400H @ 2.70 GHz |
| Memory | 16 GB |
| Hard disk | SSD 1 TB |
| Operating system | Ubuntu 22.04 |
| Golang version | go 1.18.5 |
| Solidity version | solidity 0.7.6 |
| Chainlink version | chainlink 1.13.0 |
| Sensor | MFrontier |
| RFID | RFID high frequency |
| QR code | QR version 40 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Z.; Gao, M.; Lu, G. Research on Oracle Technology Based on Multi-Threshold Aggregate Signature Algorithm and Enhanced Trustworthy Oracle Reputation Mechanism. Sensors 2024, 24, 502. https://doi.org/10.3390/s24020502
Wang Z, Gao M, Lu G. Research on Oracle Technology Based on Multi-Threshold Aggregate Signature Algorithm and Enhanced Trustworthy Oracle Reputation Mechanism. Sensors. 2024; 24(2):502. https://doi.org/10.3390/s24020502
Chicago/Turabian StyleWang, Zhiyuan, Mingan Gao, and Gehao Lu. 2024. "Research on Oracle Technology Based on Multi-Threshold Aggregate Signature Algorithm and Enhanced Trustworthy Oracle Reputation Mechanism" Sensors 24, no. 2: 502. https://doi.org/10.3390/s24020502
APA StyleWang, Z., Gao, M., & Lu, G. (2024). Research on Oracle Technology Based on Multi-Threshold Aggregate Signature Algorithm and Enhanced Trustworthy Oracle Reputation Mechanism. Sensors, 24(2), 502. https://doi.org/10.3390/s24020502





