Research on Multiple-AUVs Collaborative Detection and Surrounding Attack Simulation
Abstract
1. Introduction
- The entire process of AUV formation execution and integrating methods is developed for four different simulation stages of AUV formation;
- The artificial potential field method is effectively employed to calculate obstacle avoidance waypoints for the AUV formation;
- The utilization of LSTM neural networks efficiently predicts the motion trajectories of targets, and the DDPG method is introduced for AUV formation control and a high success rate of the surrounding attack can be achieved.
2. Methodology
| Algorithm 1: Multiple-AUVs Collaborative Detection and Surrounding attack Simulation |
/*Initialization*/
/*First Stage*/
/* Second Stage */
/* Third Stage */
|
2.1. AUV Motion Equations
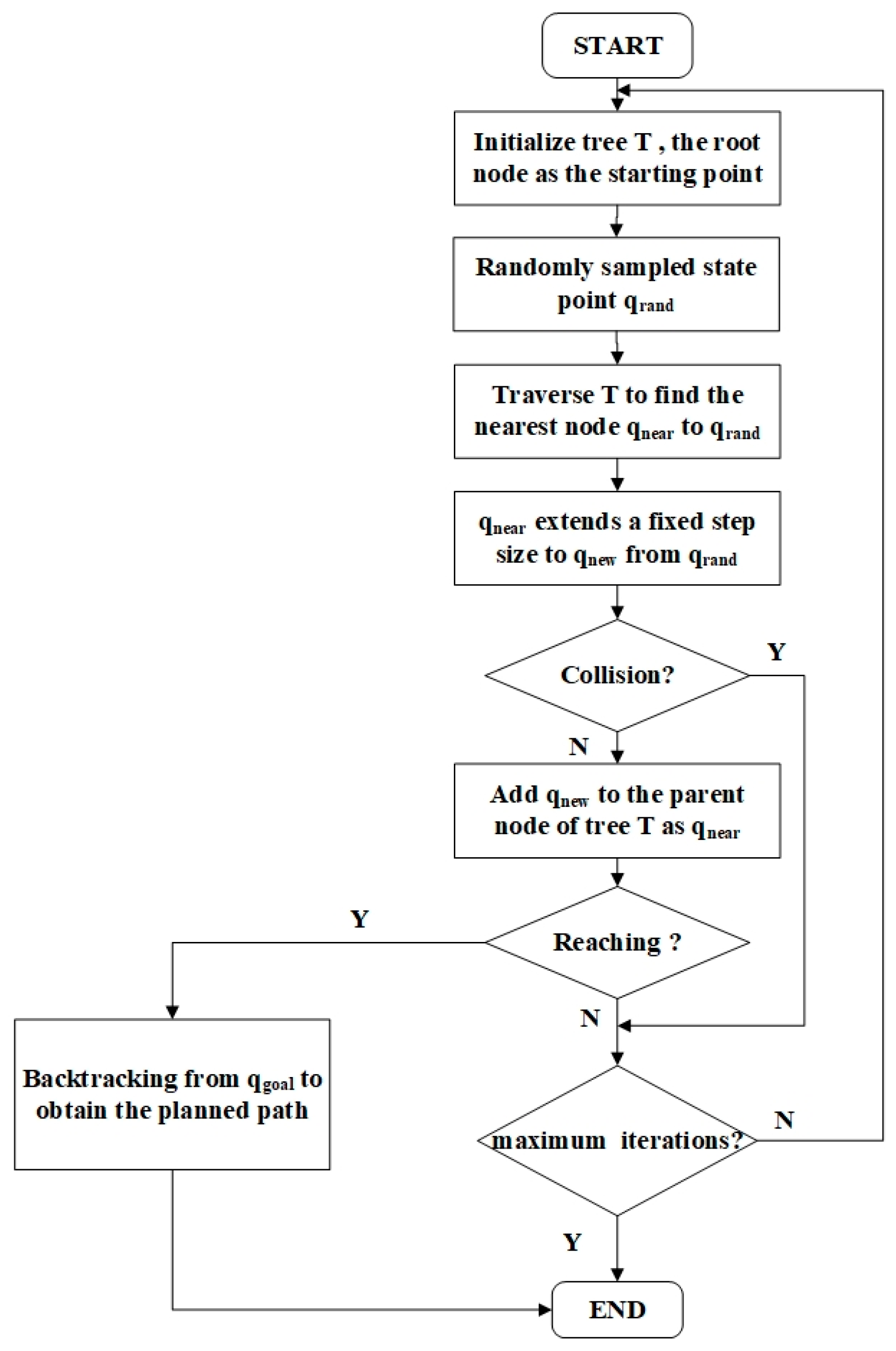
2.2. Path Planning
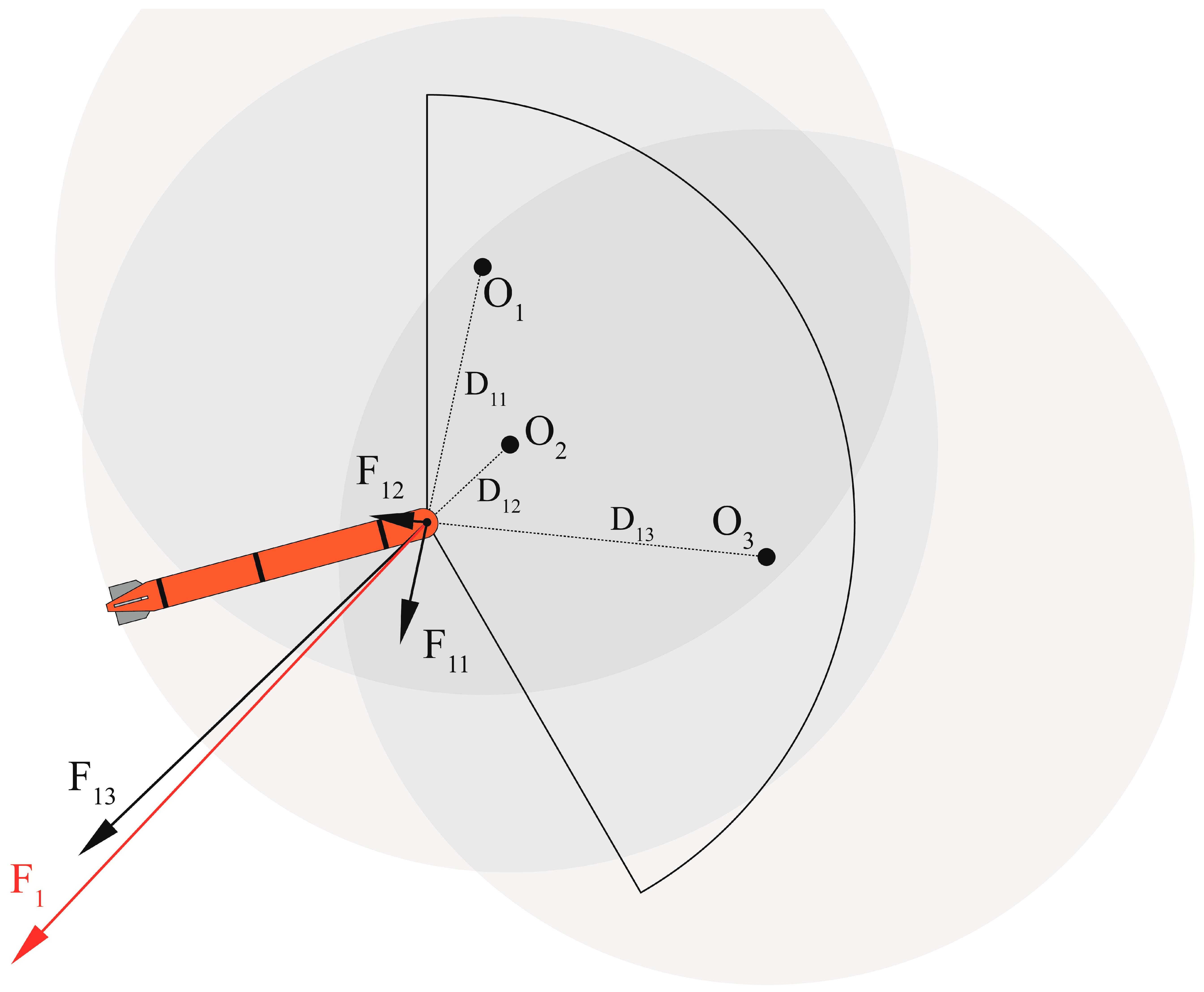
2.3. Dynamic Obstacle Avoidance
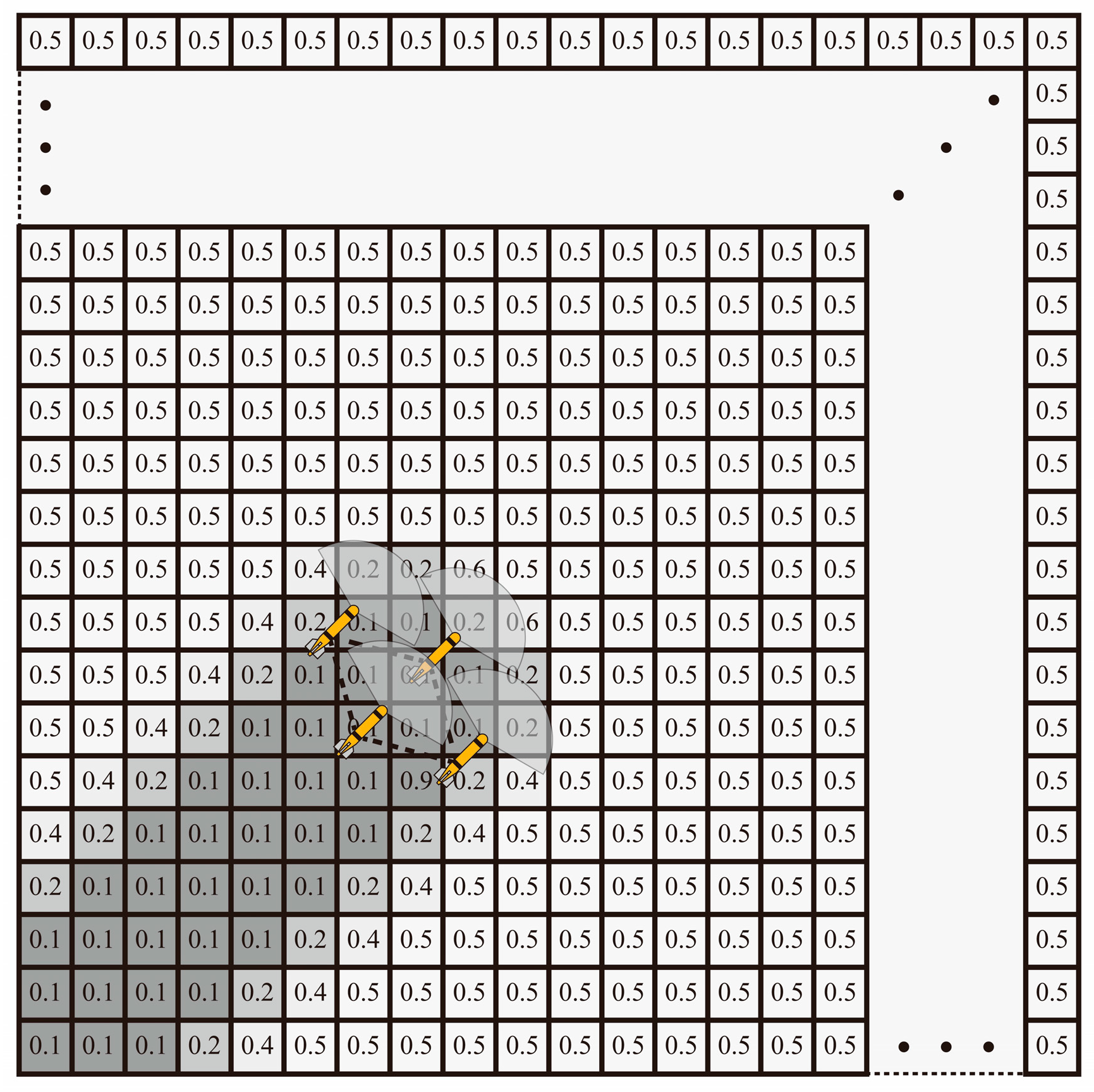
2.4. Cooperative Detection
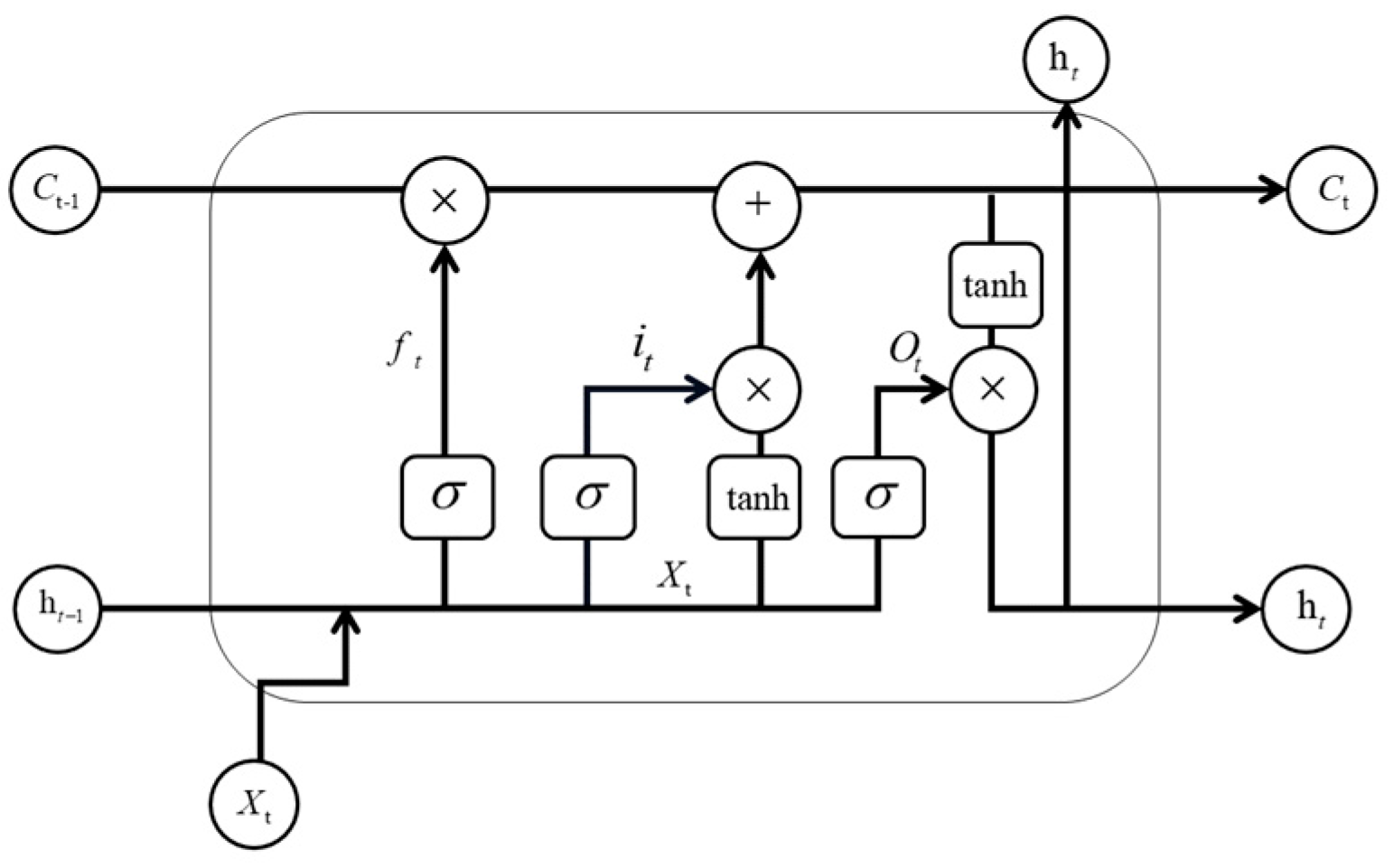
2.5. Target State Prediction Method Based on LSTM
2.6. Collaborative Rounding Method Based on DDPG
2.6.1. DDPG
| Algorithm 2: DDPG algorithm based on the rounding network training |
/*Initialization*/
/*Main Loop*/
|
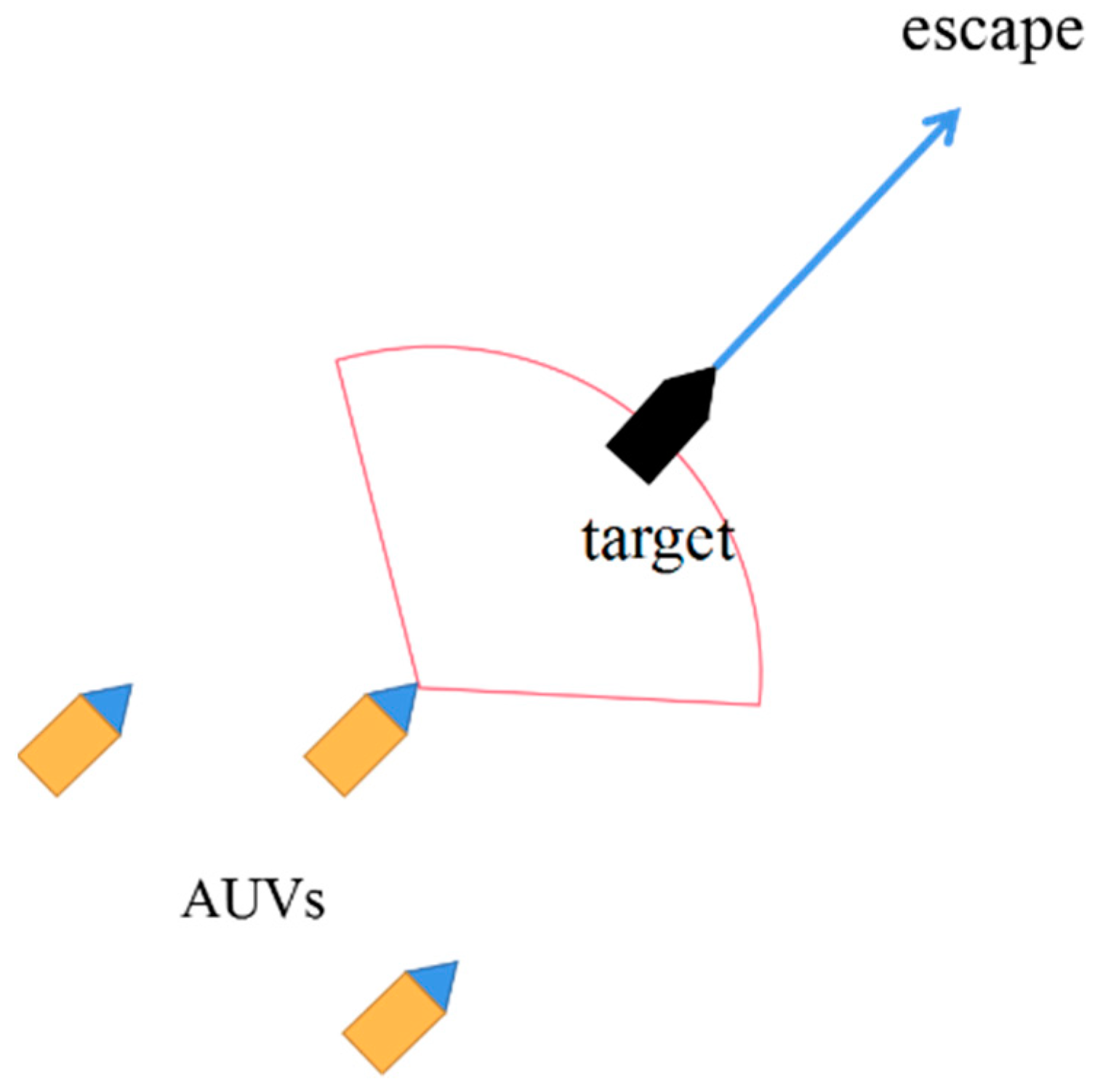
2.6.2. Collaborative Rounding Environment
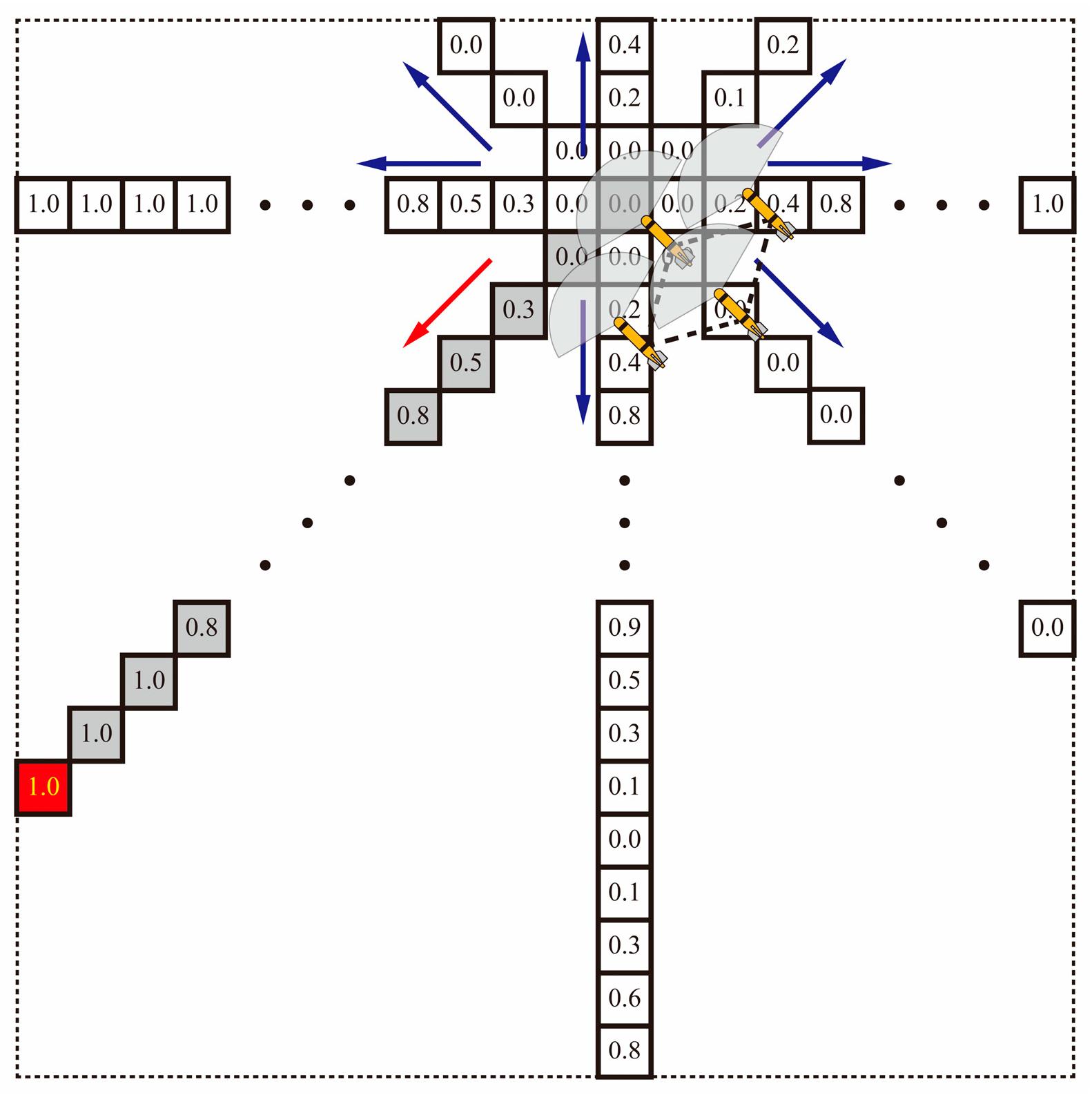
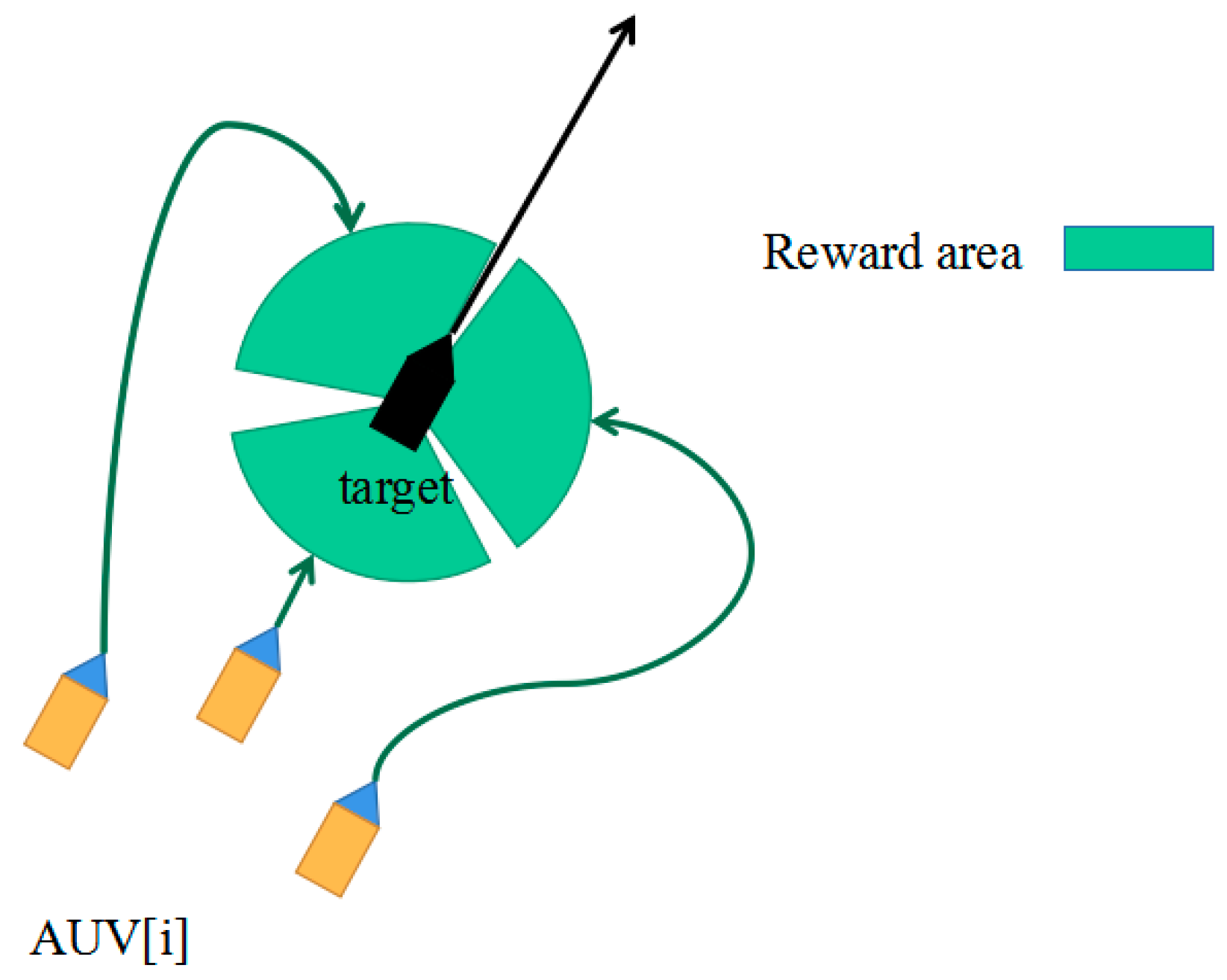
2.6.3. Artificial Potential Field Reward
3. Simulation Results and Analysis
3.1. The Construction of Multi-Cooperative Task Virtual Environment
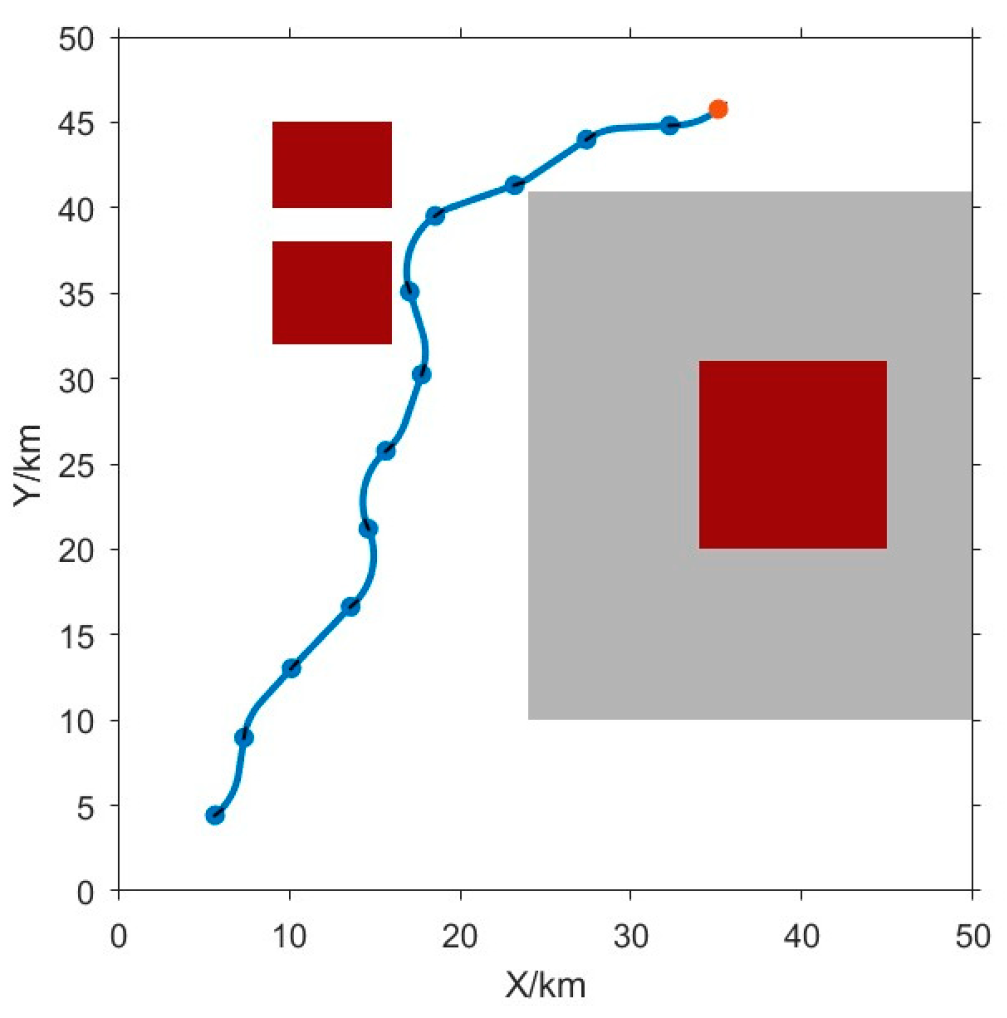
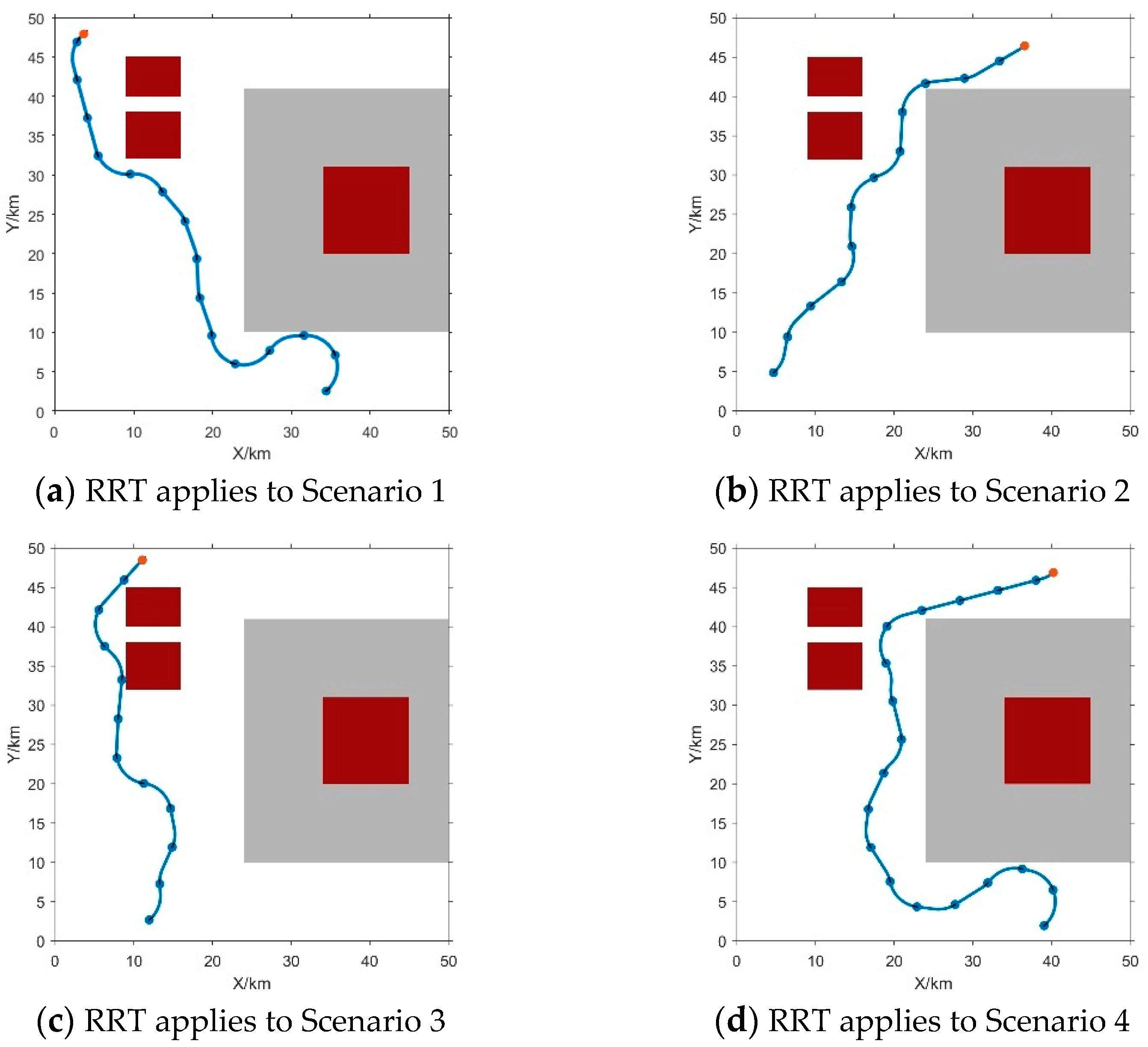
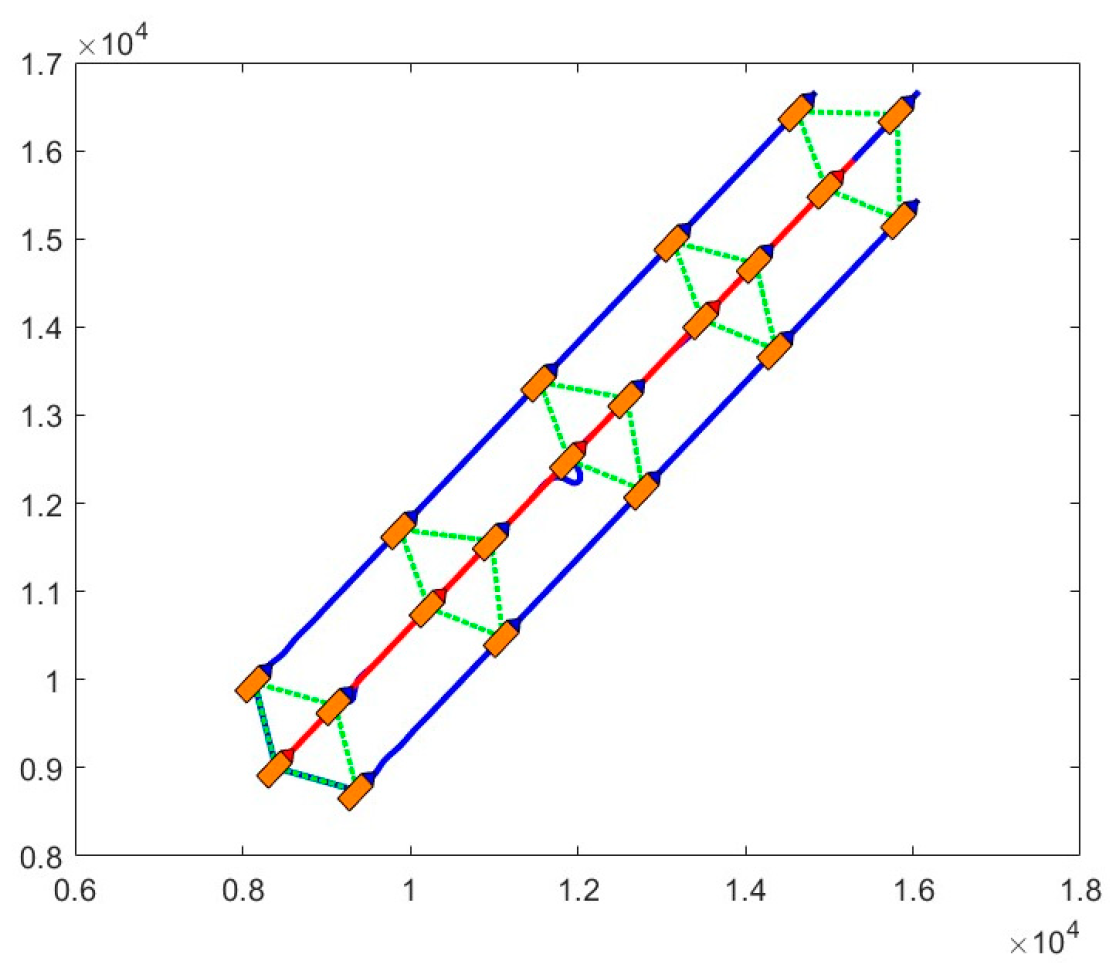
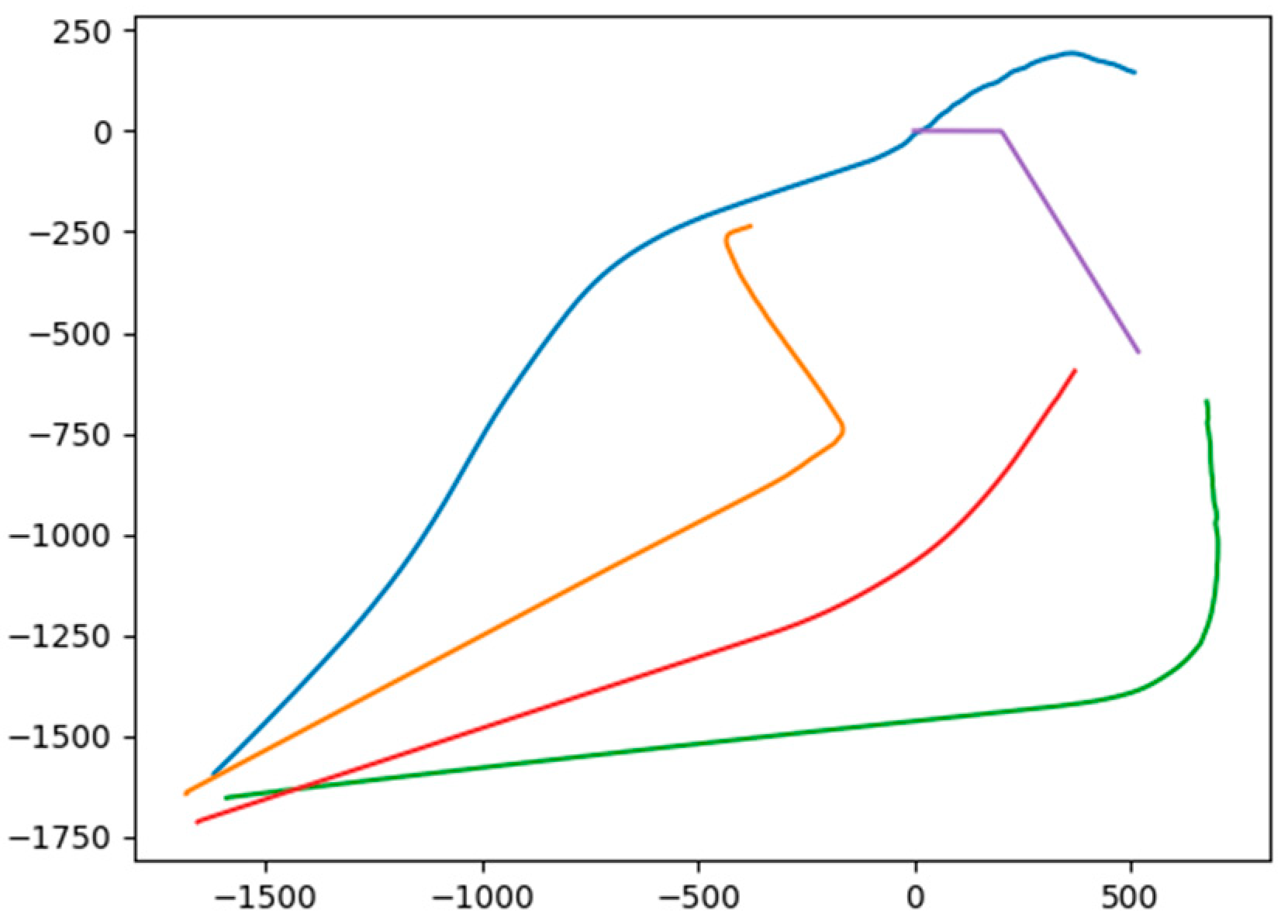
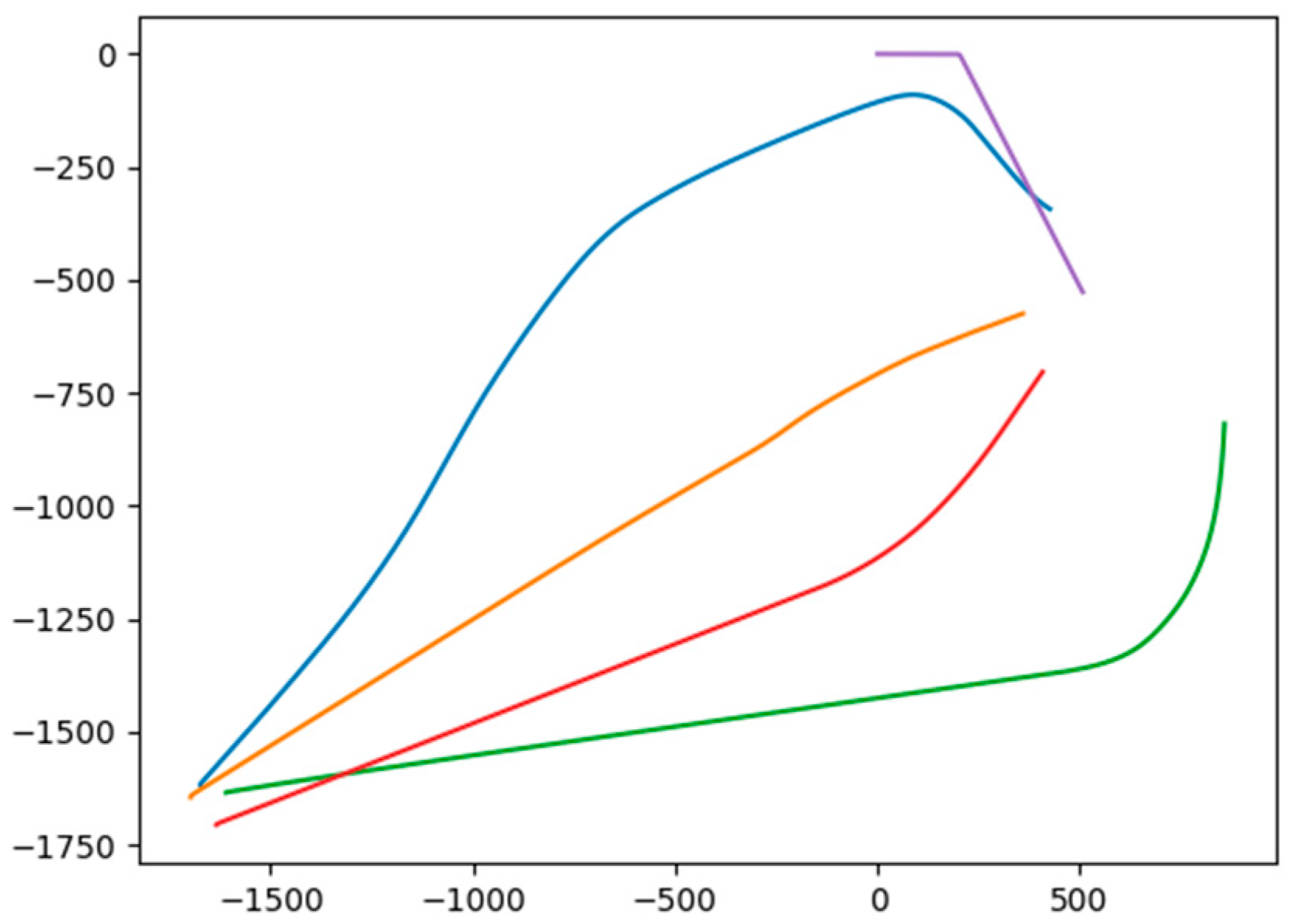
3.2. Simulation Verification of the Proposed RRT Path Planning Algorithm
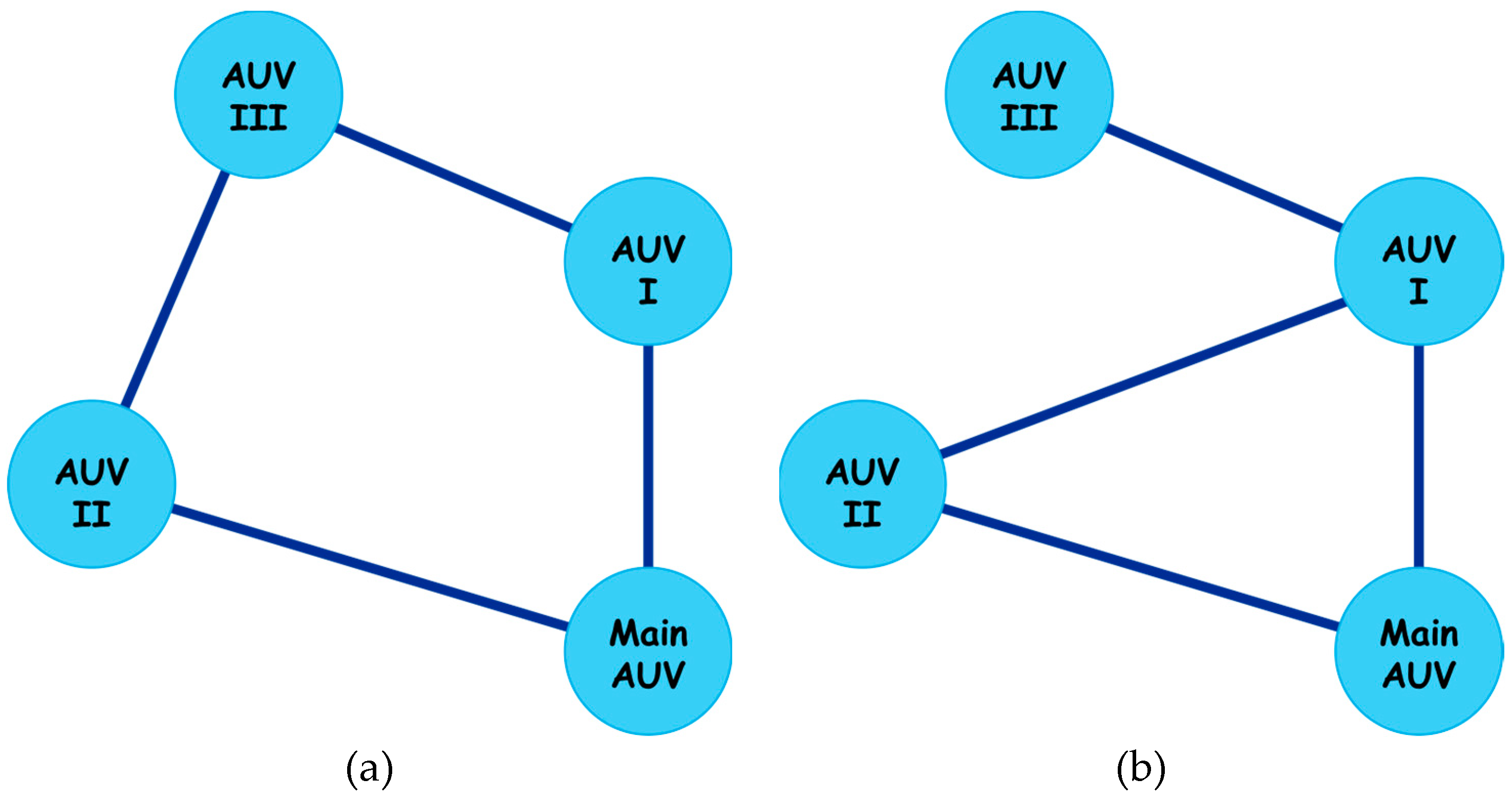
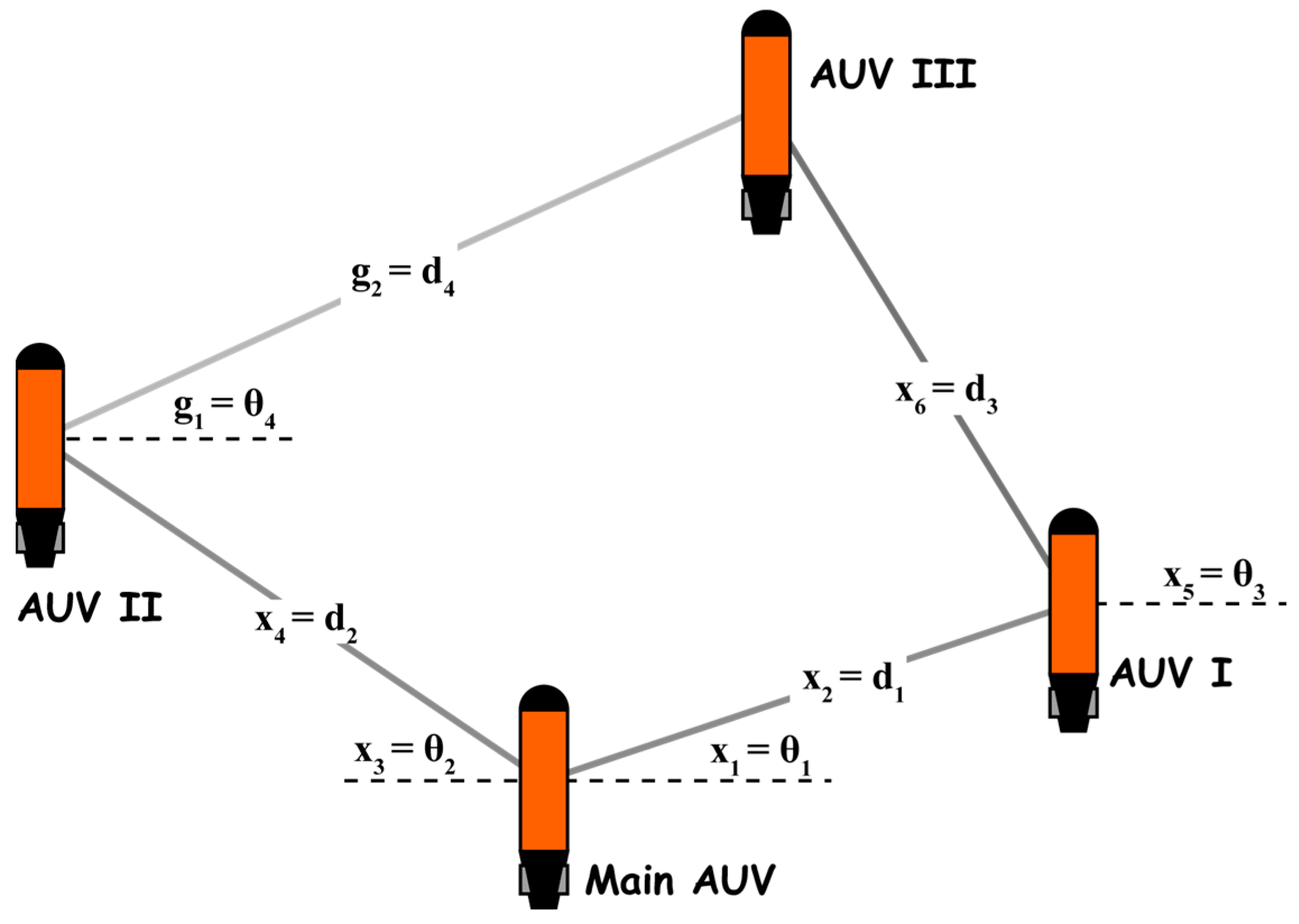
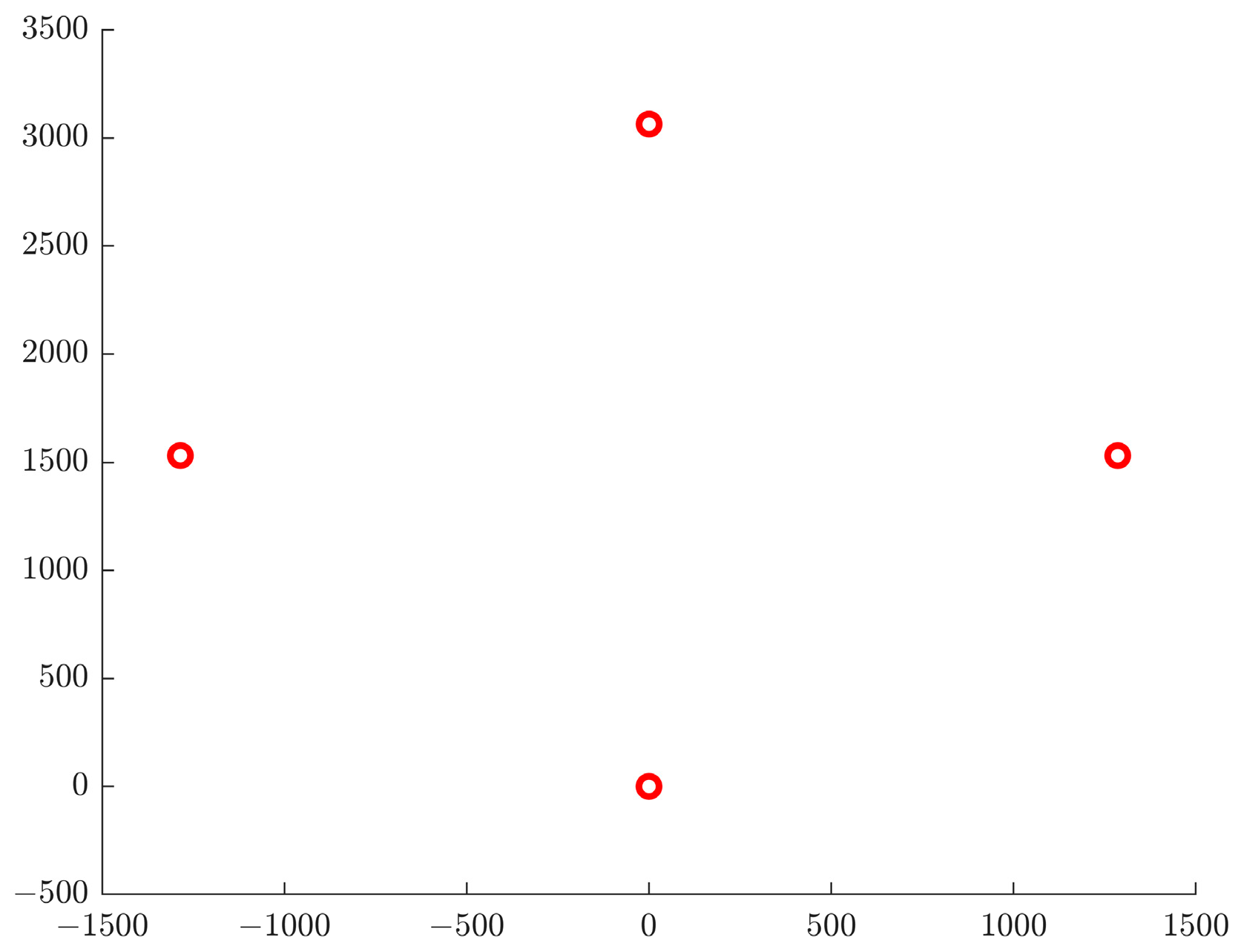
3.3. Formation Optimization
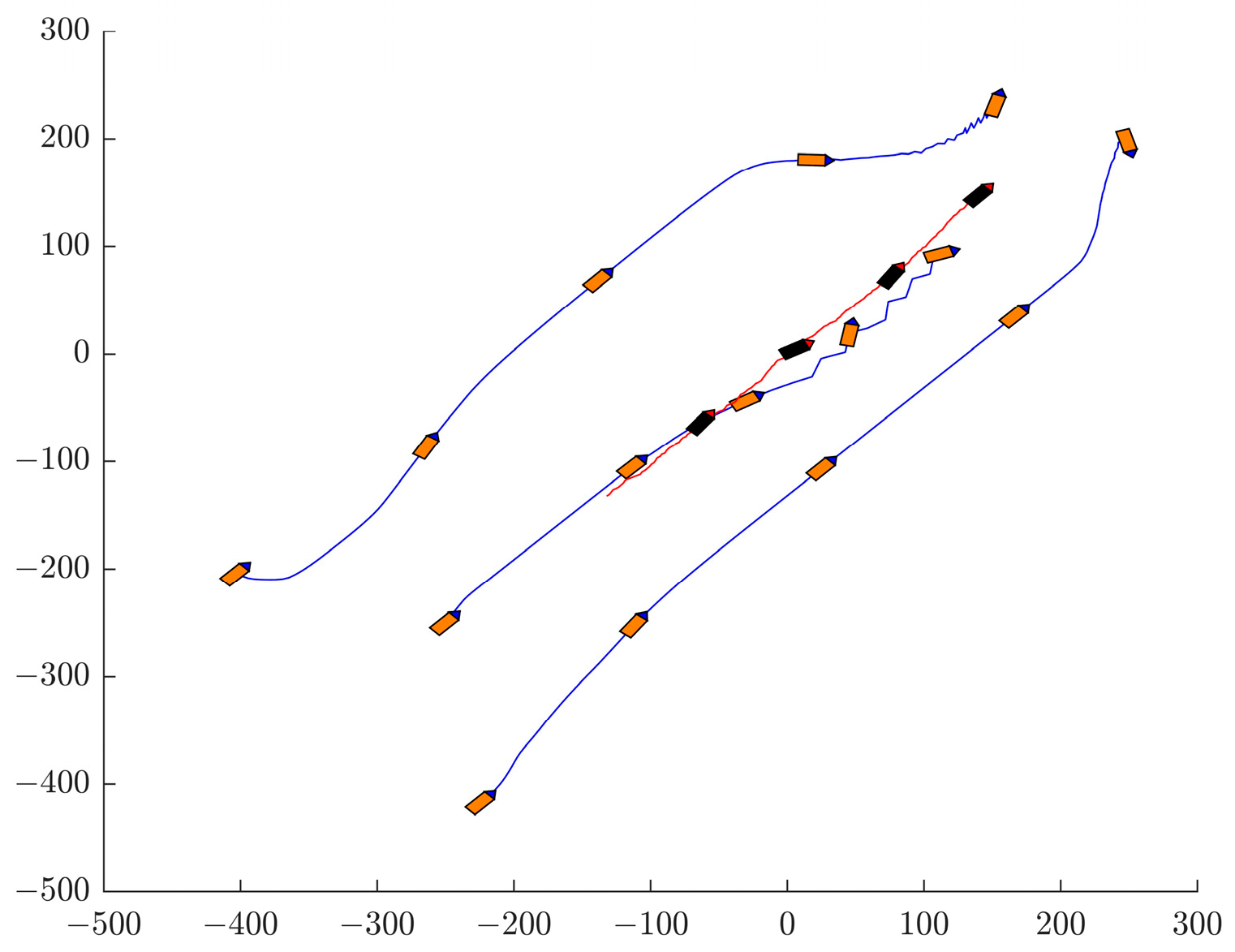
3.4. Collaborative Detection and Dynamic Obstacle Avoidance
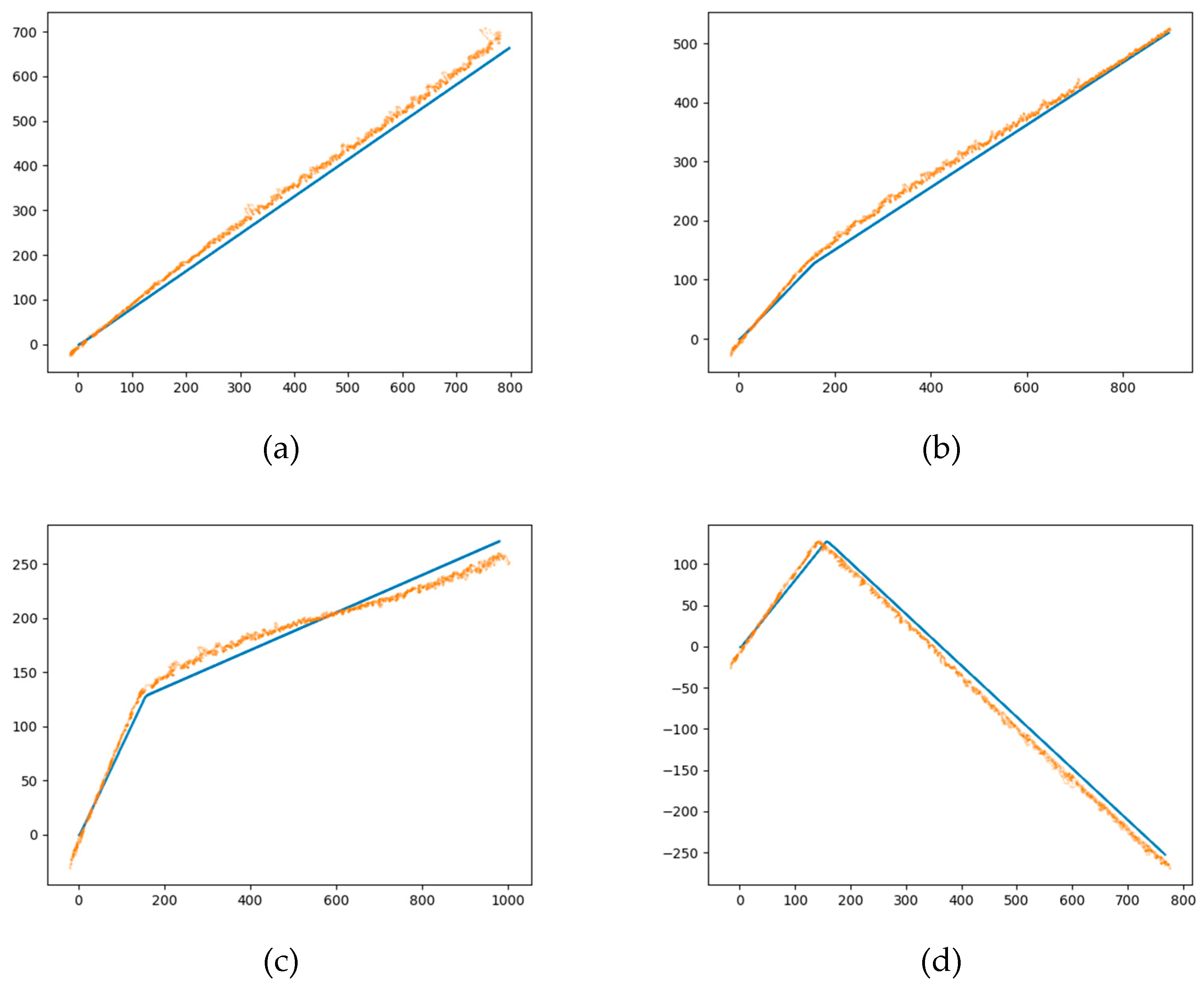
3.5. Trajectory Prediction with LSTM Network
3.6. Simulation Verification of the Target Surrounding Method
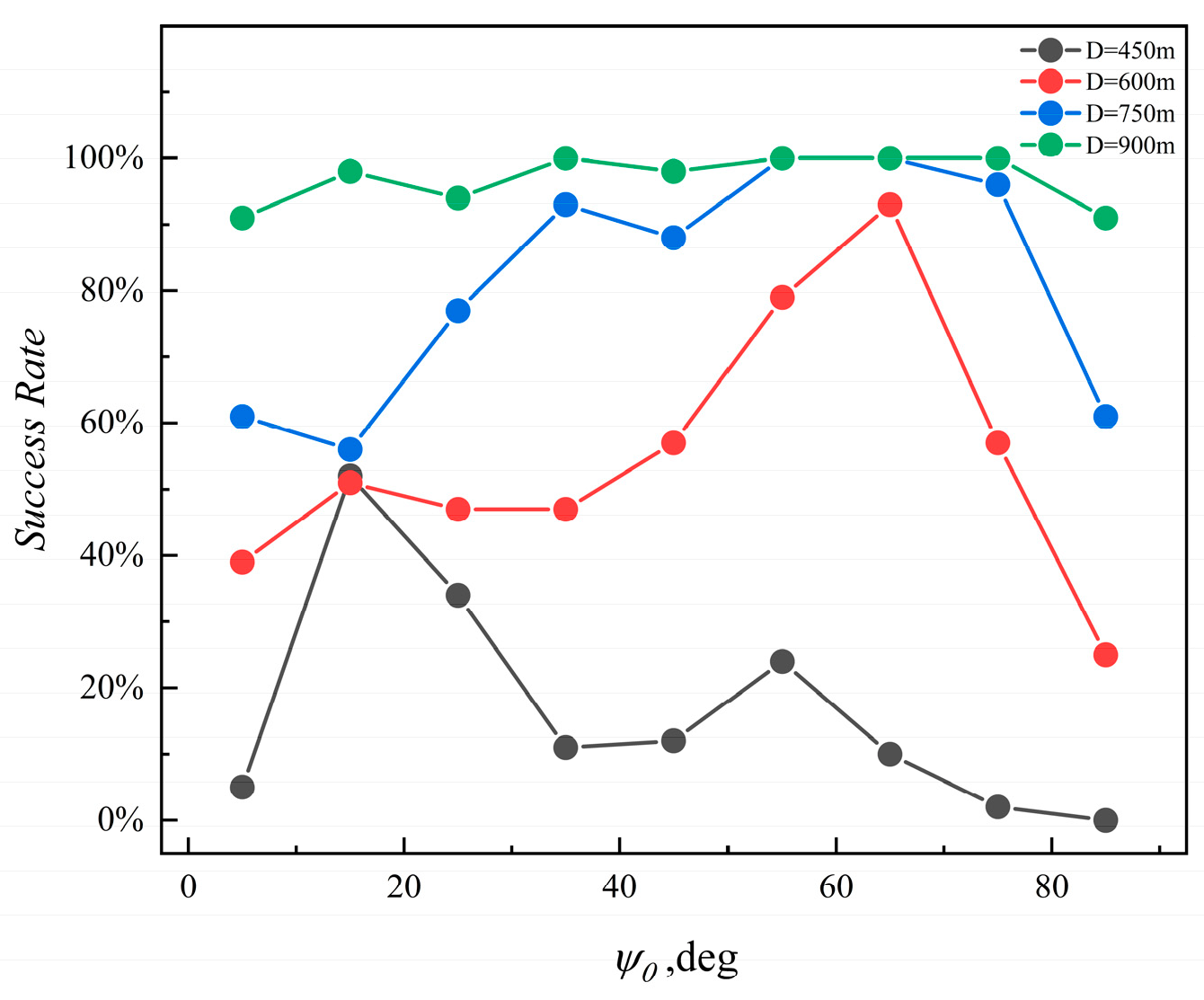
3.7. The Effectiveness Analysis of Surrounding Attack
3.8. Discussion of AUVs Collaborative Environment
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Xin, B.; Zhang, J.; Chen, J.; Wang, Q.; Qu, Y. Overview of Research on Transformation of Multi-AUV Formations. Complex Syst. Model. Simul. 2021, 1, 1–14. [Google Scholar] [CrossRef]
- Yang, Y.; Xiao, Y.; Li, T. A Survey of Autonomous Underwater Vehicle Formation: Performance, Formation Control, and Communication Capability. IEEE Commun. Surv. Tutor. 2021, 23, 815–841. [Google Scholar] [CrossRef]
- Wang, Q.; He, B.; Zhang, Y.; Yu, F.; Huang, X.; Yang, R. An autonomous cooperative system of multi-AUV for underwater targets detection and localization. Eng. Appl. Artif. Intell. 2023, 121, 105907. [Google Scholar] [CrossRef]
- Ma, X.; Chen, Y.; Bai, G.; Liu, J. Multi-AUV Collaborative Operation Based on Time-Varying Navigation Map and Dynamic Grid Model. IEEE Access 2020, 8, 159424–159439. [Google Scholar] [CrossRef]
- Chai, H.; Du, Z.; Xiang, M.; Huang, Z. The research status and development trend of UUVs cooperative localization technology. Bull. Surv. Mapp. 2022, 62, 62–67+92. [Google Scholar]
- Zhang, J.Y.; Ning, X.; Ma, S.C. An improved particle swarm optimization based on age factor for multi-AUV cooperative planning. Ocean Eng. 2023, 287, 115753. [Google Scholar] [CrossRef]
- Hu, X.Y.; Shi, Y.; Bai, G.Q.; Chen, Y.L. Collaborative Search and Target Capture of AUV Formations in Obstacle Environments. Appl. Sci. 2023, 13, 9016. [Google Scholar] [CrossRef]
- Qin, H.D.; Si, J.S.; Wang, N.; Gao, L.Y.; Shao, K.J. Disturbance Estimator-Based Nonsingular Fast Fuzzy Terminal Sliding-Mode Formation Control of Autonomous Underwater Vehicles. Int. J. Fuzzy Syst. 2023, 25, 395–406. [Google Scholar] [CrossRef]
- Pang, W.; Zhu, D.Q.; Yang, S.X. A novel time-varying formation obstacle avoidance algorithm for multiple AUVs. Int. J. Robot. Autom. 2023, 38, 194–207. [Google Scholar] [CrossRef]
- Huang, Z.; Zhu, D.; Sun, B. A multi-AUV cooperative hunting method in 3-D underwater environment with obstacle. Eng. Appl. Artif. Intell. 2016, 50, 192–200. [Google Scholar] [CrossRef]
- Liang, H.; Fu, Y.; Kang, F.; Gao, J.; Qiang, N. A Behavior-Driven Coordination Control Framework for Target Hunting by UUV Intelligent Swarm. IEEE Access 2020, 8, 4838–4859. [Google Scholar] [CrossRef]
- Cao, X.; Xu, X. Hunting Algorithm for Multi-AUV Based on Dynamic Prediction of Target Trajectory in 3D Underwater Environment. IEEE Access 2020, 8, 138529–138538. [Google Scholar] [CrossRef]
- Petritoli, E.; Cagnetti, M.; Leccese, F. Simulation of autonomous underwater vehicles (auvs) swarm diffusion. Sensors 2020, 20, 4950. [Google Scholar] [CrossRef] [PubMed]
- Fossen, T.I. Guidance and Control of Ocean Vehicles. Ph.D. Thesis, University of Trondheim, Trondheim, Norway, 1999. [Google Scholar]
- Zhong, J.; Xiang, G.; Dian, S. Efficient RRT* path planning algorithm for complex environments with narrow passages. J. Appl. Res. Comput. 2021, 38, 23082314. [Google Scholar]
- Zhang, M.; Cai, W. Underwater targets tracking path planning based on task cooperation of multiple AUVs. Chin. J. Sens. Actuators 2018, 31, 1101–1107. [Google Scholar]
- Duan, H.; Zhao, J.; Deng, Y.; Shi, Y.; Ding, X. Dynamic discrete pigeon-inspired optimization for multi-UAV cooperative search-attack mission planning. IEEE Trans. Aerosp. Electron. Syst. 2020, 57, 706–720. [Google Scholar] [CrossRef]
- Yu, Y.; Si, X.; Hu, C.; Zhang, J. A Review of Recurrent Neural Networks: LSTM Cells and Network Architectures. Neural Comput. 2019, 31, 1235–1270. [Google Scholar] [CrossRef] [PubMed]
- Yin, W.; Kann, K.; Yu, M.; Schütze, H. Comparative Study of CNN and RNN for Natural Language Processing. arXiv 2017, arXiv:1702.01923. [Google Scholar]
- Lowe, R.; Wu, Y.I.; Tamar, A.; Harb, J.; Pieter Abbeel, O.; Mordatch, I. Multi-agent actor-critic for mixed cooperative-competitive environments. In Proceedings of the NIPS’17: Proceedings of the 31st International Conference on Neural Information Processing Systems, Long Beach, CA, USA, 4–9 December 2017. [Google Scholar]
- Taieb, S.B.; Sorjamaa, A.; Bontempi, G. Multiple-output modeling for multi-step-ahead time series forecasting. Neurocomputing 2010, 73, 1950–1957. [Google Scholar] [CrossRef]






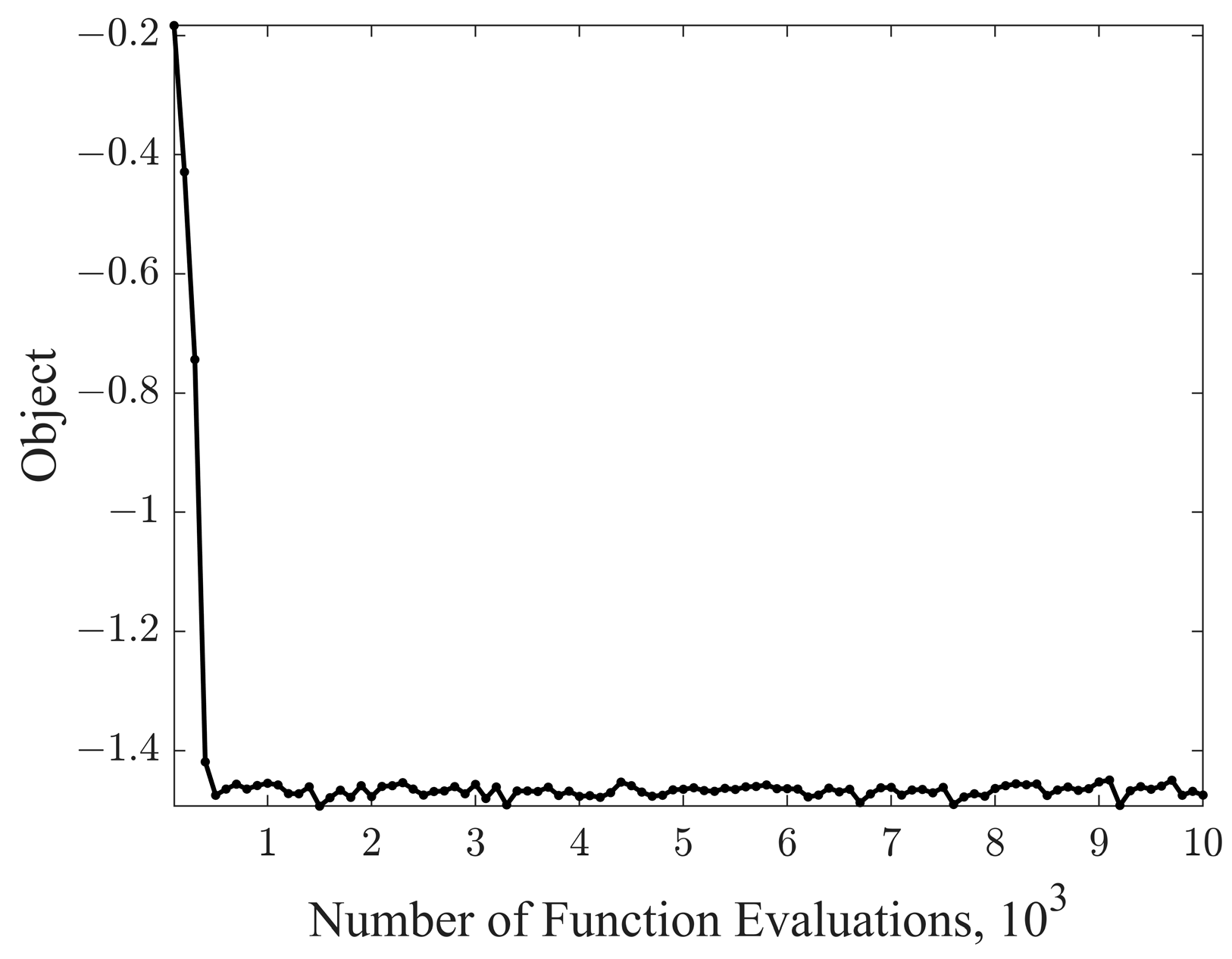
| Algorithm | Design Variables | Objective Variable | |||||
|---|---|---|---|---|---|---|---|
| PSO (w = 0.4) | 0.69 | 1358.97 | 2.37 | 1294.73 | 2.27 | 1529.89 | −0.80 |
| PSO (w = 1) | −0.87 | 2000.00 | 4.01 | 2000.00 | 4.01 | 2000.00 | −1.46 |
| PSO (w = 2) | −0.87 | 2000.00 | 4.01 | 2000.00 | 4.01 | 2000.00 | −1.47 |
| GA | −0.86 | 1865.29 | 4.01 | 1870.17 | 4.01 | 1860.75 | −1.37 |
| Target Velocity (knot) | Maneuver Angle | Not Using the LSTM Model Success Rate | Using the LSTM Model Success Rate |
|---|---|---|---|
| 6 | 90 | 84% ↓ | 100% ↑ |
| 6 | 60 | 77% ↓ | 100% ↑ |
| 6 | 45 | 74% ↓ | 84% ↑ |
| 8 | 90 | 80% ↓ | 98% ↑ |
| 8 | 60 | 72% ↓ | 100% ↑ |
| 8 | 45 | 23% ↓ | 79% ↑ |
| 10 | 90 | 79% ↓ | 98% ↑ |
| 10 | 60 | 79% ↓ | 100% ↑ |
| 10 | 45 | 23% ↓ | 72% ↑ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wen, Z.; Wang, Z.; Zhou, D.; Qin, D.; Jiang, Y.; Liu, J.; Dong, H. Research on Multiple-AUVs Collaborative Detection and Surrounding Attack Simulation. Sensors 2024, 24, 437. https://doi.org/10.3390/s24020437
Wen Z, Wang Z, Zhou D, Qin D, Jiang Y, Liu J, Dong H. Research on Multiple-AUVs Collaborative Detection and Surrounding Attack Simulation. Sensors. 2024; 24(2):437. https://doi.org/10.3390/s24020437
Chicago/Turabian StyleWen, Zhiwen, Zhong Wang, Daming Zhou, Dezhou Qin, Yichen Jiang, Junchang Liu, and Huachao Dong. 2024. "Research on Multiple-AUVs Collaborative Detection and Surrounding Attack Simulation" Sensors 24, no. 2: 437. https://doi.org/10.3390/s24020437
APA StyleWen, Z., Wang, Z., Zhou, D., Qin, D., Jiang, Y., Liu, J., & Dong, H. (2024). Research on Multiple-AUVs Collaborative Detection and Surrounding Attack Simulation. Sensors, 24(2), 437. https://doi.org/10.3390/s24020437








