RIS-Enabled Secret Key Generation for Secured Vehicular Communication in the Presence of Denial-of-Service Attacks
Abstract
1. Introduction
- This study extends our previous work introduced in [5] by proposing a RIS-assisted key-extraction method that enhances the signal strength for the designated user’s location while reducing that from the active attacker’s location. Hence, the proposed method improves the key-extraction performance for designated users while mitigating the impact of DoS attacks within the network.
- To accomplish this, a RIS configuration optimization algorithm is designed using the Hadamard matrix codebook. This algorithm optimizes the measurement quantization order based on the optimal configuration’s average SNR estimate.
- The proposed RIS optimization algorithm is practically implemented using a 1-bit RIS with elements and two Universal Serial Radio Peripherals (USRPs) operating in the 5G communication frequency range (3.75 GHz). Finally, the statistical randomness of the extracted keys is measured to demonstrate the extracted key suitability for use as cryptographic keys.
2. Related Works
3. Preliminaries
3.1. Review of the PHY-Layer Secret Key Extraction Scheme in [5]
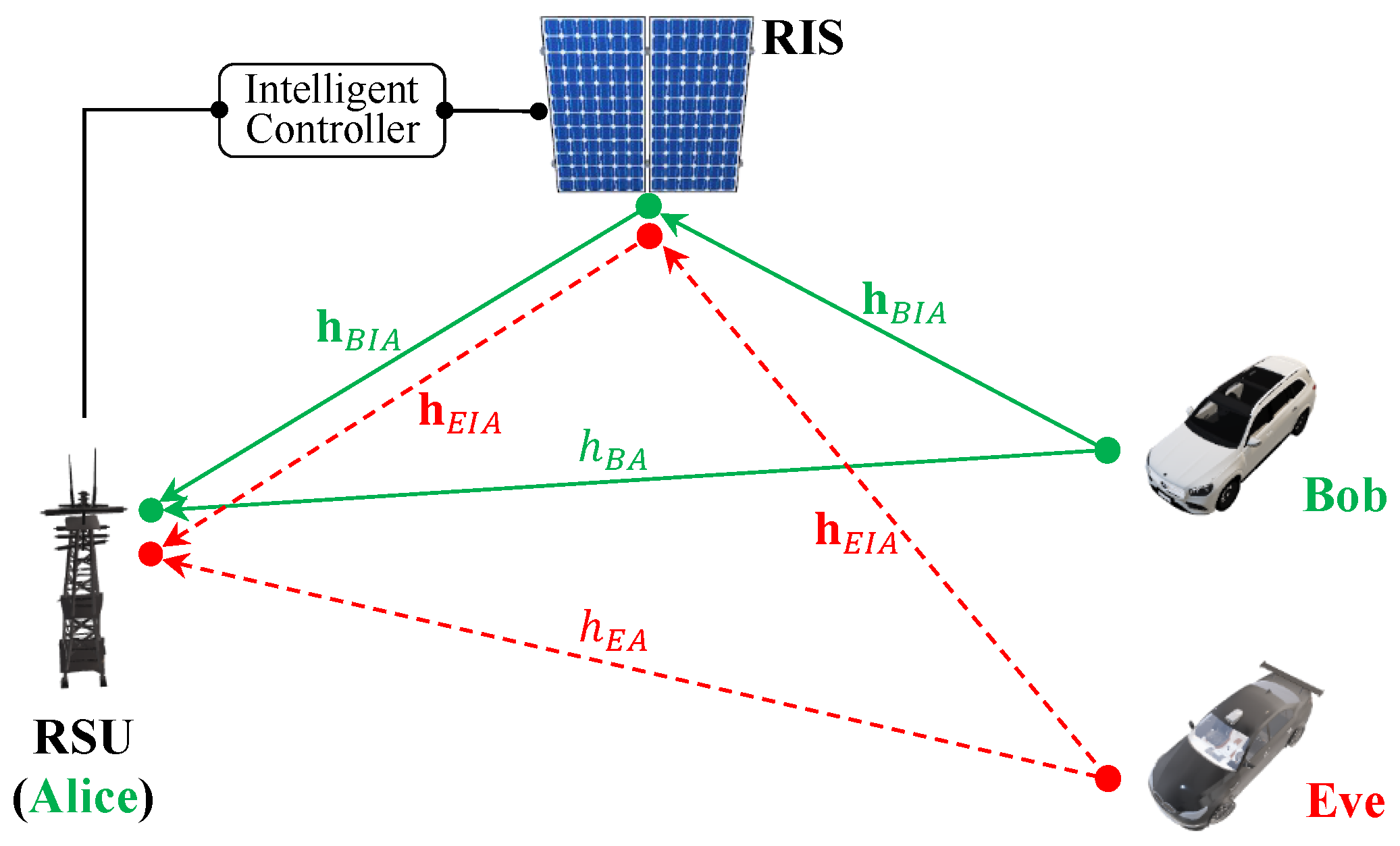
3.2. System Model
- 1.
- The RSU: RSUs are stationary devices located along roads that facilitate wireless communication between themselves and surrounding vehicles within a particular range. Each RSU acts as a relay between vehicles, extending the communication range and improving the network’s reliability. It is equipped with wireless communication capabilities and can support various applications, such as traffic management, safety warnings, and entertainment services. It also has a reliable communication link with the RIS’s intelligent controller, so configurations of reflecting units can be optimized. Through this mechanism, the RSU effectively manages the RIS to enhance the transmission of signals towards a designated direction while simultaneously reducing the strength of signals toward potential unauthorized interceptors, commonly referred to as “Eve”.
- 2.
- The vehicle’s onboard units (OBUs): OBU is a communication device installed within each vehicle in the network. It can communicate with other OBUs and RSUs within range, facilitating the exchange of traffic-related messages in 100–300 ms intervals based on the dedicated short-range communication protocol [26]. In this way, OBUs play a crucial role in the functioning of the vehicular network.
- 3.
- The RIS: RISs are intelligent surfaces that can dynamically change their electromagnetic behaviors to improve the performance of wireless networks. RISs can be used to manipulate the propagation of radio signals, allowing for better signal quality, increased network coverage, and improved energy efficiency. The intelligent controller is an integral component of each RIS. It manages and configures the multiple meta-surface reflecting units (RUs) of order N elements that make up the RIS. It plays a crucial role in optimizing the performance of the RIS in the network.
- 4.
- The adversary Eve: “Eve” is an active attacker who overloads the network with excessive traffic, causing it to become unavailable to legitimate users. In this attack, the adversary overwhelms the target’s resources and prevents it from functioning properly, therefore denying service to its intended users. By constructing and launching a flooding DoS attack, the attacker aims to disrupt the system’s normal functioning and cause inconvenience or harm to its users.
4. RIS-Assisted Secret Key Extraction Method
4.1. Performance Optimization
4.2. Channel Modeling
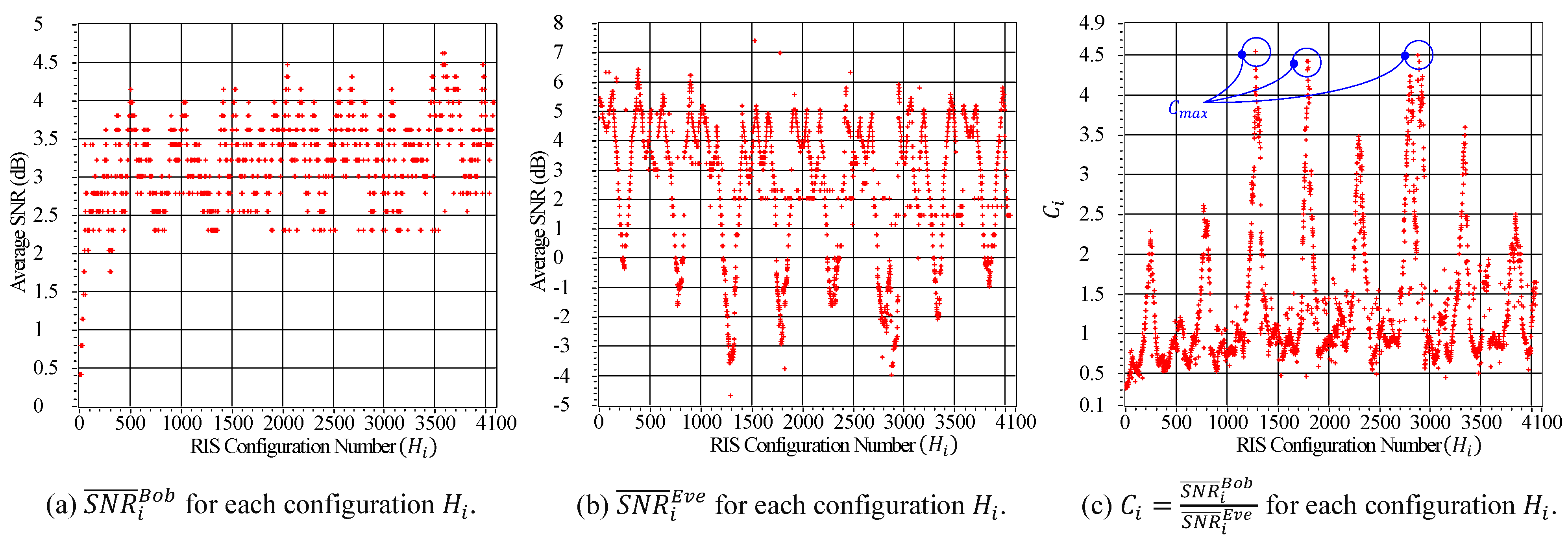
4.3. Optimizing the Best RIS Configuration
- Initialization: Alice initializes the Hadamard codebook , where and are the number of elements in the RIS’s x and y coordinates, respectively.
- Scanning toward Bob: Alice scans the average SNR value for the received OFDM symbols from Bob, denoted as , for each configuration within the set of all possible configurations, , where .
- Scanning toward Eve: Alice scans the average SNR value of the received OFDM symbols from Eve, denoted as , for each configuration within the set of all possible configurations, , where .
- Configuration optimization: Alice computes the ratio of the average SNR for Bob over the average SNR for Eve , denoted as , for . The maximum value of , referred to as , is then determined from the set of all values of . The optimum configuration, denoted as , is identified as the configuration that corresponds to the maximum value of . This calculation maximizes Bob’s average SNR while minimizing Eve’s average SNR.
| Algorithm 1 Optimizing the Best RIS Configuration . | |
| Initialization | |
| 1: | The Hadamard codebook for the RIS reflecting units |
| 2: | Two empty variables, and , used to store the measured SNRs |
| 3: | An empty variable C |
| Alice is communicating with the legitimate terminal (Bob) | |
| 4: | for do |
| 5: | Measuring the average SNR value for each Hadamard matrix |
| 6: | Appending the measured to |
| 7: | end for |
| Alice is communicating with the illegitimate terminal (Eve) | |
| 8: | for do |
| 9: | Measuring the average SNR value for each Hadamard matrix |
| 10: | Appending the measured to |
| 11: | end for |
| Optimizing the best configuration | |
| 12: | for do |
| 13: | Computing |
| 14: | Appending the computed to C |
| 15: | end for |
| 16: | Finding the best configuration () corresponding to |
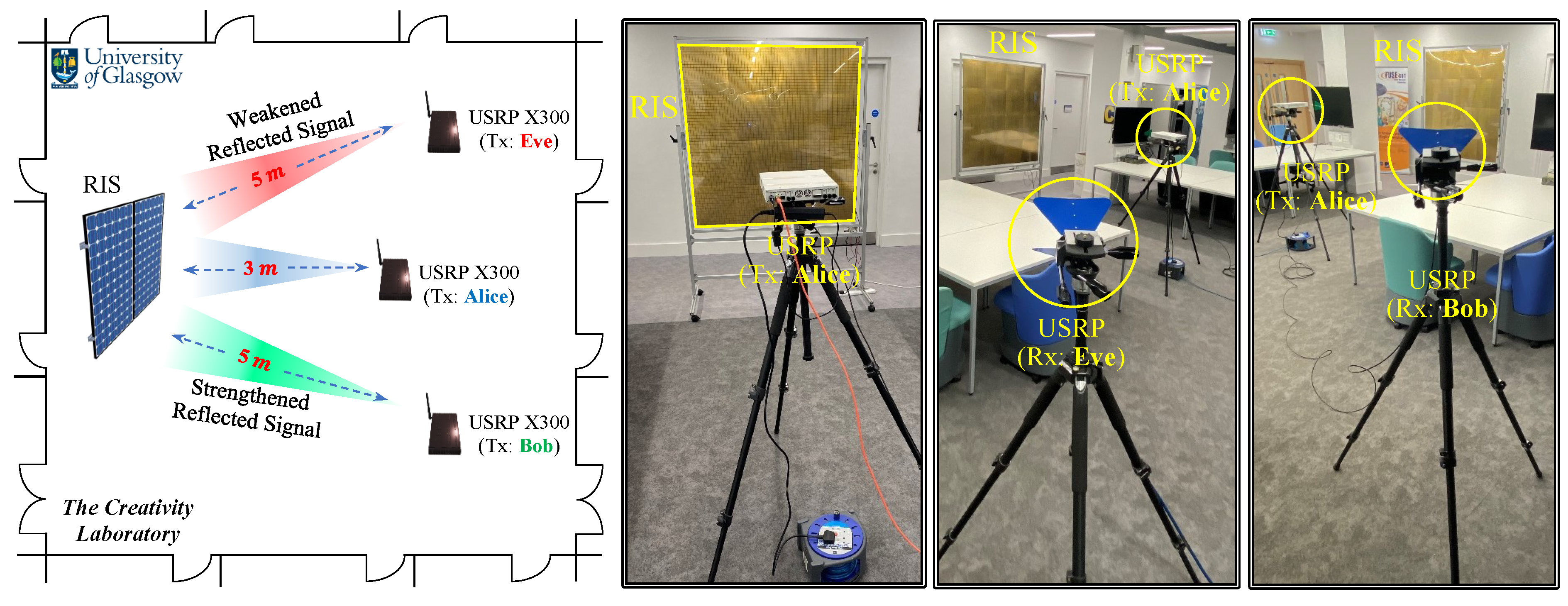
5. Hardware Implementation Analysis
5.1. Experimental Setup and the RIS Configuration Analysis
5.2. Implementation Results and Analysis of the Key-Extraction Process
5.3. Overhead Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Al-Shareeda, M.A.; Anbar, M.; Hasbullah, I.H.; Manickam, S. Survey of Authentication and Privacy Schemes in Vehicular ad hoc Networks. IEEE Sens. J. 2021, 21, 2422–2433. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. A Survey of Security Services, Attacks, and Applications for Vehicular Ad Hoc Networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef] [PubMed]
- Abbas, S.; Talib, M.A.; Ahmed, A.; Khan, F.; Ahmad, S.; Kim, D.-H. Blockchain-Based Authentication in Internet of Vehicles: A Survey. Sensors 2021, 21, 7927. [Google Scholar] [CrossRef] [PubMed]
- Liu, S.; Wei, G.; He, H.; Wang, H.; Chen, Y.; Hu, D.; Jiang, Y.; Chen, L. Intelligent Reflecting Surface-Assisted Physical Layer Key Generation with Deep Learning in MIMO Systems. Sensors 2023, 23, 55. [Google Scholar] [CrossRef]
- Shawky, M.A.; Usman, M.; Imran, M.A.; Abbasi, Q.H.; Ansari, S.; Taha, A. Adaptive Chaotic Map-Based Key Extraction for Efficient Cross-Layer Authentication in VANETs. Veh. Commun. 2023, 39, 100547. [Google Scholar] [CrossRef]
- Maurer, U.M. Secret key agreement by public discussion from common information. IEEE Trans. Inf. Theory 1993, 39, 733–742. [Google Scholar] [CrossRef]
- Wang, X.; Hao, P.; Hanzo, L. Physical-layer authentication for wireless security enhancement: Current challenges and future developments. IEEE Commun. Mag. 2016, 54, 152–158. [Google Scholar] [CrossRef]
- Usman, M.; Althunibat, S.; Qaraqe, M. A Channel State Information-Based Key Generation Scheme for Internet of Things. Secur. Commun. Netw. 2022, 2022, 7976319. [Google Scholar] [CrossRef]
- Ahlswede, R.; Csiszar, I. Common Randomness in Information Theory and Cryptography. I. Secret Sharing. IEEE Trans. Inf. Theory 1993, 39, 1121–1132. [Google Scholar] [CrossRef]
- Cheng, L.; Zhou, L.; Seet, B.-C.; Li, W.; Ma, D.; Wei, J. Efficient Physical-Layer Secret Key Generation and Authentication Schemes Based on Wireless Channel-Phase. Mob. Inf. Syst. (Hindawi) 2017, 2017, 7393526. [Google Scholar]
- Björnson, E.; Wymeersch, H.; Matthiesen, B.; Popovski, P.; Sanguinetti, L.; Carvalho, E. Reconfigurable Intelligent Surfaces: A Signal Processing Perspective with Wireless Applications. IEEE Signal Process. Mag. 2022, 39, 135–158. [Google Scholar] [CrossRef]
- Lin, Z.; Li, Y.; Zhang, X.; Li, Z.; Chen, X. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Champagne, B.; Zhu, W.-P.; Al-Dhahir, N. Secrecy-Energy Efficient Hybrid Beamforming for Satellite-Terrestrial Integrated Networks. IEEE Trans. Commun. 2021, 69, 6345–6360. [Google Scholar] [CrossRef]
- Niu, H.; Li, J.; Zhang, Q.; Zhang, X.; Shen, X.S. Joint Beamforming Design for Secure RIS-Assisted IoT Networks. IEEE Internet Things J. 2023, 10, 1628–1641. [Google Scholar] [CrossRef]
- Shawky, M.A.; Shah, S.T.; Mollel, M.S.; Kazim, J.R.; Imran, M.A.; Abbasi, Q.H.; Ansari, S.; Taha, A. Reconfigurable Intelligent Surface-Assisted Cross-Layer Authentication for Secure and Efficient Vehicular Communications. arXiv 2023, arXiv:2303.08911. [Google Scholar] [CrossRef]
- Lu, X.; Lei, J.; Shi, Y.; Li, W. Intelligent Reflecting Surface Assisted Secret Key Generation. IEEE Signal Process. Lett. 2021, 28, 1036–1040. [Google Scholar] [CrossRef]
- Krishna, N.J.; Prasanth, N. An Insight View on Denial of Service Attacks in Vehicular Ad Hoc Networks. In Advances in Computational Intelligence and Communication Technology; Springer: Singapore, 2022; pp. 273–285. [Google Scholar]
- Bottarelli, M.; Epiphaniou, G.; Ismail, D.K.B.; Karadimas, P.; Al-Khateeb, H. Physical Characteristics of Wireless Communication Channels for Secret Key Establishment: A Survey of the Research. Comput. Secur. 2018, 78, 454–476. [Google Scholar] [CrossRef]
- Koorapaty, H.; Hassan, A.; Chennakeshu, S. Secure Information Transmission for Mobile Radio. IEEE Commun. Lett. 2000, 4, 52–55. [Google Scholar] [CrossRef]
- Mathur, S.; Miller, R.; Varshavsky, A.; Trappe, W.; Mandayam, N. ProxiMate: Proximity-based Secure Pairing using Ambient Wireless Signals. In Proceedings of the 9th International Conference on Mobile Systems, Applications, and Services, Bethesda, MD, USA, 28 June–1 July 2011; pp. 211–224. [Google Scholar]
- Wang, Q.; Su, H.; Ren, K.; Kim, K. Fast and Scalable Secret Key Generation Exploiting Channel Phase Randomness in Wireless Networks. In Proceedings of the IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 1422–1430. [Google Scholar]
- Shehadeh, Y.; Hogrefe, D. An Optimal Guard-Intervals based Mechanism for Key Generation from Multipath Wireless Channels. In Proceedings of the 4th IFIP International Conference on New Technologies, Mobility and Security, Paris, France, 1–5 February 2011. [Google Scholar]
- Bottarelli, M.; Karadimas, P.; Epiphaniou, G.; Ismail, D.K.B.; Maple, C. Adaptive and Optimum Secret Key Establishment for Secure Vehicular Communications. IEEE Trans. Veh. Technol. 2021, 70, 2310–2321. [Google Scholar] [CrossRef]
- Shawky, M.A.; Usman, M.; Imran, M.A.; Abbasi, Q.H.; Ansari, S.; Taha, A. Adaptive and Efficient Key Extraction for Fast and Slow Fading Channels in V2V Communications. In Proceedings of the 2022 IEEE 96th Vehicular Technology Conference (VTC2022-Fall), London, UK, 26–29 September 2022; pp. 1–6. [Google Scholar]
- Kwon, H.; Kim, Y.; Yoon, H.; Choi, D. Optimal Cluster Expansion-Based Intrusion Tolerant System to Prevent Denial of Service Attacks. Appl. Sci. 2017, 7, 1186. [Google Scholar] [CrossRef]
- Kenney, J.B. Dedicated Short-Range Communications (DSRC) Standards in the United states. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- You, C.; Zheng, B.; Zhang, R. Intelligent Reflecting Surface with Discrete Phase Shifts: Channel Estimation and Passive Beamforming. In Proceedings of the IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- NIST. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications, 800th ed.; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2001.




| Symbol | Definition |
|---|---|
| The generator of the cyclic group for the ith subcarrier of the OFDM symbol | |
| The private integer numbers at the sides of Alice and Bob, respectively | |
| The transmission time interval between two subsequent OFDM symbols | |
| The wireless-channel amplitude and phase responses, respectively | |
| The equalized phase estimates at the sides of Alice and Bob, respectively | |
| The Gray code mapping operation that converts final estimates into bit streams | |
| r | The order of the generator and the mapping operation |
| The cumulative distribution function and the error function | |
| The probability of error in the extracted key between two parties | |
| I | The secret key capacity |
| The Hadamard codebook used for optimizing the RIS configuration | |
| The average SNR of the signals transmitted from Bob and Eve, respectively | |
| The optimal configuration for the RIS’s reflecting units |
| Quantization Order | RIS Status (ON/OFF) | |
|---|---|---|
| RIS-OFF | RIS-ON | |
| SNR | SNR | |
| SNR | SNR | |
| NIST Statistical Test Suite (256 bits) | p-Value |
|---|---|
| Key Entropy | |
| Monobit Test | |
| Long Runs Test | |
| Block Frequency Test | |
| Maurer Universal Statistical Test | |
| Overlapping Template Matchings Test | |
| Discrete Fourier Transform (Spectral) Test |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shawky, M.A.; Shah, S.T.; Abbasi, Q.H.; Hussein, M.; Imran, M.A.; Hasan, S.F.; Ansari, S.; Taha, A. RIS-Enabled Secret Key Generation for Secured Vehicular Communication in the Presence of Denial-of-Service Attacks. Sensors 2023, 23, 4104. https://doi.org/10.3390/s23084104
Shawky MA, Shah ST, Abbasi QH, Hussein M, Imran MA, Hasan SF, Ansari S, Taha A. RIS-Enabled Secret Key Generation for Secured Vehicular Communication in the Presence of Denial-of-Service Attacks. Sensors. 2023; 23(8):4104. https://doi.org/10.3390/s23084104
Chicago/Turabian StyleShawky, Mahmoud A., Syed Tariq Shah, Qammer H. Abbasi, Mohamed Hussein, Muhammad A. Imran, Syed Faraz Hasan, Shuja Ansari, and Ahmad Taha. 2023. "RIS-Enabled Secret Key Generation for Secured Vehicular Communication in the Presence of Denial-of-Service Attacks" Sensors 23, no. 8: 4104. https://doi.org/10.3390/s23084104
APA StyleShawky, M. A., Shah, S. T., Abbasi, Q. H., Hussein, M., Imran, M. A., Hasan, S. F., Ansari, S., & Taha, A. (2023). RIS-Enabled Secret Key Generation for Secured Vehicular Communication in the Presence of Denial-of-Service Attacks. Sensors, 23(8), 4104. https://doi.org/10.3390/s23084104










