Abstract
The Internet of Medical Things (IoMT) is used in the medical ecosystem through medical IoT sensors, such as blood glucose, heart rate, temperature, and pulse sensors. To maintain a secure sensor network and a stable IoMT environment, it is important to protect the medical IoT sensors themselves and the patient medical data they collect from various security threats. Medical IoT sensors attached to the patient’s body must be protected from security threats, such as being controlled by unauthorized persons or transmitting erroneous medical data. In IoMT authentication, it is necessary to be sensitive to the following attack techniques. (1) The offline password guessing attack easily predicts a healthcare administrator’s password offline and allows for easy access to the healthcare worker’s account. (2) Privileged-insider attacks executed through impersonation are an easy way for an attacker to gain access to a healthcare administrator’s environment. Recently, previous research proposed a lightweight and anonymity preserving user authentication scheme for IoT-based healthcare. However, this scheme was vulnerable to offline password guessing, impersonation, and privileged insider attacks. These attacks expose not only the patients’ medical data such as blood pressure, pulse, and body temperature but also the patients’ registration number, phone number, and guardian. To overcome these weaknesses, in the present study we propose an improved lightweight user authentication scheme for the Internet of Medical Things (IoMT). In our scheme, the hash function and XOR operation are used for operation in low-spec healthcare IoT sensor. The automatic cryptographic protocol tool ProVerif confirmed the security of the proposed scheme. Finally, we show that the proposed scheme is more secure than other protocols and that it has 266.48% better performance than schemes that have been previously described in other studies.
1. Introduction
The Internet of Medical Things (IoMT) represents a combination of the healthcare field and the IoT ecosystem that can be used to create, collect, transmit, and analyze medical data through the connection of various healthcare IT systems, healthcare sensors, and healthcare management programs [1,2]. With the continued evolution of IoT technology and the outbreak of COVID-19, IoMT gaining increased interest as it can enable personalized medical information management, real–time health tracking and monitoring but also remote treatment [3].
However, there may be various security problems in the IoMT environment when dealing with sensitive medical information [4,5], such as the following:
- 1.
- First, if malicious cyberattacks can take control of healthcare sensors attached to a patient’s body, this might not only result in inaccurate data collection but also put the patient’s health at risk.
- 2.
- Second, malicious cyberattacks can expose sensitive patient data and medical information.
- 3.
- Third, since IoMT uses low–power wearable healthcare sensors, the protocol used is not lightweight, and it therefore may be difficult to operate normally or to provide real–time service due to the need for time–consuming computation.
Therefore, further develop the IoMT environment, it is crucial to maintain security for medical systems and IoT devices and to support lightweight security protocols for implementing them.
We implemented and analyzed a suitable scheme for IoMT using the following method. For safety, we not only use a simple password base but also introduce a fuzzy extractor, i.e., it is a biometric-based authentication method. We also propose a system model and an attack model to complement the weaknesses of Masud et al. [6]. We analyze the vulnerabilities of Masud et al. [6] based on the system model and attack model and propose our new IoMT scheme. We analyze the safety of the proposed scheme using a formal analysis and an informal analysis and calculate the cost of computation. Lastly, we analyze how efficient the computational cost is compared to those of other schemes.
1.1. Our Contribution
We proposed a secure and lightweight user authentication scheme for IoMT by improving on Masud et al. [6]’s scheme by addressing the possible threats involved. In summary, we make the following contributions:
- 1.
- First, to overcome offline password-guessing attacks, we added biometrics authentication methods that can only authenticate the user when an actual user is present. Further, to protect against replay attacks, we added logic to ensure that the gateway authenticates the user and the freshness of the user’s message in the authentication phase. Finally, to overcome privileged insider attacks, we deleted the secret information that shared between the user and the sensor in the registration phase immediately following the registration phase.
- 2.
- We proposed a lightweight security protocol that mainly uses a hash function and XOR operation to run low-spec healthcare sensors.
- 3.
- The proposed scheme is designed to protect against various security threats such as offline password guessing attacks, privileged insider attacks, user impersonation attacks, replay attacks, and session key disclosure attacks. It also ensures user anonymity.
1.2. Organization of Our Paper
The rest of this paper is organized as follows: Section 3 presents the preliminaries about the fuzzy extractor, system model, and attack model. Section 4 presents the scheme reported by Masud et al. [6]. Section 5 demonstrates the scheme reported by Masud et al. [6]. Section 6 presents our improved scheme. Section 7 provides formal and informal security analysis. Section 8 provides a performance analysis. Section 9 provides discussion of performance. Finally, Section 10 presents our conclusion.
2. Related Work
Even until recently, most healthcare systems could only be accessed using a password. Password-based authentication [7,8] is the most popular method for user authentication. However, it is unfortunately not suitable for use in a sensitive system that requires strong security because it contains various security threats. For example, password-based authentication can lead to unintentional password sharing when someone looks over the user’s shoulder and sees the user’s password. Anyone who knows this password can access the system on behalf of the user. Moreover, a password guessing attack is possible, in which the attacker guesses the user’s password and attempts authentication until finding success.
Password-based authentication schemes can also be exposed to various security threats, so to overcome the security threats of password-based authentication, two–factor authentication using a smart card has been introduced. In 2012, Wu et al. [9] proposed a secure authentication scheme for TMIS using a smart card and a password. However, Debiao et al. [10] pointed out that this scheme was vulnerable to impersonation attacks and insider attacks. Meanwhile, Wei et al. [11] pointed out that the scheme was vulnerable to offline password guessing attacks. To overcome these problems, Debiao et al. [10] proposed a more secure authentication scheme using a smart card and a password. However, Wei et al. [11] pointed out that this scheme also was vulnerable to offline password guessing attacks if the user were to lose his or her smart card. Consequently, a three-factor authentication using a password, a smart card, and biometrics, i.e., fingerprint and face recognition, has been introduced to achieve a higher level of security [12,13,14,15]. Wu et al. [12] proposed an improved and provably secure three-factor user authentication scheme for wireless sensor networks. However, Ryu et al. [13] pointed out that this scheme was vulnerable to user impersonation attacks and that it could not preserve the user’s anonymity could not be preserved. A summary of each scheme’s weaknesses is presented in Table 1.

Table 1.
Summary of related works.
Recently, Masud et al. [6] proposed a lightweight and anonymity preserving user authentication scheme for IoT–based healthcare. In the present study, we specifically focused on the use of lightweight protocols to support resource–constrained devices. However, we found various security threats, since this paper only provides user authentication using a password to remain lightweight. While it is important to keep in mind that supporting lightweight security protocols in an IoMT environment is one of the most important considerations, maintaining security is the most foundational requirement. One of the fatal security threats to which Masud et al. [6]’s scheme is vulnerable is an offline-password attack. If an attacker steals a valid authentication message in any authentication phase that is communicated via a public channel, the attacker can guess the user’s valid password while offline. Masud et al. [6]’s scheme is also vulnerable to replay attacks and privileged insider attacks. Through such attack, an attacker could log in by stealing the user’s password and disguising themselves as the user. An attacker could also enter information on behalf of the user or have access to the user’s information as the user.
Although Masud et al. [6]’s scheme exhibited better performance to maintain security for IoMT, it still has a security challenge. Therefore, we proposed an improved lightweight user authentication scheme for IoMT that improved upon Masud et al. [6]’s scheme and reduces reduced the computational cost compared to related studies.
3. Preliminaries
In this section, we introduce the fuzzy extractor, the system model which we made, and the attack model. The details are as follows:
3.1. Fuzzy Extractor
Biometric information is the best way to authenticate and verify users [16,17,18]. In 2004, Dodis et al. [19] proposed the Fuzzy Extractor to obtain a unique bit string extracted from the biometric template. A fuzzy extractor is a tuple that has two algorithms and , which are expressed as follows [12]:
The above result means that the fuzzy extractor can generate the secret string and . is a ’s original collected biometric data.
The above result means that the fuzzy extractor can recover the secret string that is generated by the algorithm.
3.2. System Model
Figure 1 shows the system model of the proposed scheme. In our scheme, there are three entities: the User, Medical Service Gateway (Gateway), and Healthcare IoT Sensor Node (Sensor Node).
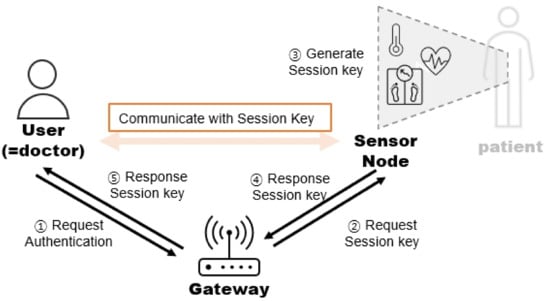
Figure 1.
The system model of our scheme in IoMT.
- 1.
- Medical Service Gateway (Gateway): Since the user and the sensor node do not communicate with each other directly, the gateway is responsible for authentication and passing the communication between the user and the sensor node.
- 2.
- Healthcare IoT Sensor Node (Sensor Node): The Healthcare IoT Sensor Node is attached to the patient’s body and collects the patient’s medical data. The Healthcare IoT Sensor Node is connected to the healthcare network and transmits the patient’s medical data to the user through a Gateway.
- 3.
- Doctor (User): The user is a doctor who can access the patient’s medical information that has been collected from the sensor node to inform the patient’s treatment.
3.3. Attack Model
For security analysis in our scheme, we consider the following attack model [20,21,22]:
- 1.
- The attacker can extract the data in the device that stores some security parameters.
- 2.
- The attacker can access the public communication channel, at which point the attacker can interrupt, return, amend and eliminate or transmit the message.
- 3.
- The attacker can calculate the identity and password in polynomial time.
4. Review of the Scheme Presented by Masud et al. [6]
In this section, we briefly review Masud et al.’s scheme [6] that only uses password protection to only let legitimate users access the IoT sensor node to obtain the patient’s health information. The notations and Masud et al. [6]’s scheme are described in Table 2 and Table 3, respectively.

Table 2.
Notations.

Table 3.
Masud et al.’s [6] scheme.
Masud et al. [6]’s scheme consists of three phases: the User Registration Phase, the Sensor Node Registration Phase, and the Mutual Authentication and Key Agreement Phase.
4.1. User Registration Phase
- 1.
- The user enters and transmits and through the secured channel to the gateway.
- 2.
- The gateway generates and computes and . The gateway stores , , and . Finally, the gateway transmits through the secured channel to the user.
- 3.
- The user derives and computes and . The user then stores , and .
4.2. Sensor Node Registration Phase
- 1.
- The sensor node generates and then transmits and through the secured channel to the gateway.
- 2.
- The gateway generates and computes ⊕ and ⊕. The gateway then stores , and . Finally, the gateway transmits through the secured channel to the sensor.
- 3.
- The sensor node computes and . The sensor node then stores .
4.3. Mutual Authentication and Key Agreement Phase
- 1.
- The user enters and then computes , where and . If Q and are not equal, the procedure is stopped; if they are equal, the user generates and computes and ). Finally, the user transmits , and to the gateway.
- 2.
- The gateway retrieves , after which the gateway checks the freshness of . If is not fresh, the procedure is stopped; else the gateway compares and with the received values. If the values are not identical, the procedure is stopped; else the gateway computes . If and are equal, the user authentication is successful. If they are not equal, the procedure is stopped. To share with the sensor node, the gateway generates , , and . The gateway computes , , and . Finally, the gateway stores and transmits , , , , and through the public channel to the sensor node.
- 3.
- The sensor node retrieves and then checks the freshness of . If is not fresh, the procedure is stopped; else the sensor node computes . If and are equal, the gateway authentication is successful. Then, the sensor node retrieves and the sensor node generates and . The sensor node then computes , , and . Moreover, the sensor node retrieves and derives . The sensor node stores and . Finally, the sensor node transmits and to the gateway.
- 4.
- The gateway retrieves and . The gateway then checks the freshness of . If is not fresh, the procedure is stopped; else the gateway computes and . If and are equal, the mutual authentication between the sensor node and the gateway is successful. Subsequently, the gateway stores , , and . To share SK with the user, the gateway generates and . The gateway then computes , , , and . Finally the gateway stores and and ultimately transmits , , , and to the user.
- 5.
- The user retrieves . The user then checks the freshness of . If is not fresh, the procedure is stopped; else the user computes . If and are equal, the mutual authentication between the gateway and the user is successful. Then the user retrieves and . The user computes and stores and .
5. Weaknesses of Masud et al. [6]’s Scheme
These weaknesses are listed under the assumption that the attacker has recorded the message from a successful mutual authentication and key agreement of the user A.
5.1. Offline Password Guessing Attack
In an offline password guessing attack, the attacker is never actually attempting to login to the gateway server. Suppose the attacker steals the device of user A and obtains from the device. Then, the attacker repeatedly guesses a password and computes offline. If is equal to , the attacker can obtain the correct password . Until the attacker determines a valid user’s password , the gateway does not notice this attack at all because the attacker does not try to login.
Then, in the Mutual Authentication and Key Agreement Phase, the attacker retrieves , and . Eventually, the attacker can obtain an that can be used to access the resource of the gateway and the sensor node.
5.2. Privileged Insider Attack
If a privileged insider of the gateway has obtained the user A’s password , and from the gateway’s database, he is trying to impersonate user A. In the Mutual Authentication and Key Agreement Phase, the privileged insider retrieves and . Eventually, the privileged insider can obtain an that can access the resource of the gateway and the sensor node.
5.3. Replay Attack
Masud et al. [6] claim their scheme is safe from replay attacks because the gateway checks the freshness of nonce and that the nonce cannot be modified since it is secretly enclosed in the password . However, suppose the attacker generates the nonce and then transmits instead of . Upon receiving , the gateway retrieves and then the gateway checks the freshness of . However, since the retrieved is a random number if only freshness is guaranteed, the gateway cannot confirm whether is valid. Briefly, if the attacker can make a nonce that can guarantee freshness, Masud et al. [6]’s scheme cannot resist replay attacks. Further, if freshness is proven since the new identities of user and device , are changed, valid users who do not know the changed identity will no longer be able to authenticate themselves after the replay attack.
6. Proposed Scheme
In this section, we propose a three-factor mutual authentication scheme for the Internet of Medical Things (IoMT) that is intended to overcome the weaknesses of the scheme reported by Masud and colleagues. The proposed scheme only consists of three phases: user registration, sensor node registration, and authentication and key distribution. The proposed scheme is described in Table 4.

Table 4.
The proposed scheme.
6.1. User Registration Phase
- 1.
- The user enters and and generates a random number . The user imprints on a device for biometric collection and computes and . For registration, the user transmits through a secured channel to the gateway.
- 2.
- The gateway generates random numbers , and and computes , and . The gateway stores , , and . is temporarily stored by the gateway until the sensor node registration phase, is transferred from the gateway to the sensor node during the sensor node registration phase, and is then deleted from the gateway. Finally, the gateway transmits , , and through a secured channel to the user.
- 3.
- The user computes , and , and and stores , , , , and .
6.2. Sensor Node Registration Phase
- 1.
- For registration, the sensor node transmits through a secured channel to the gateway.
- 2.
- The gateway generates a random number and computes and stores , . Finally, the gateway transmits , , and through a secured channel to the sensor node and deletes .
- 3.
- The sensor node stores , , , and .
6.3. Mutual Authentication and Key Distribution Phase
- 1.
- The user enters and and imprints on a device for biometric collection and computes , , , , , and . To check the user’s password, the user checks if = ? . If the equation is equal, the password check is passed; if not, the procedure is stopped. To generate an authentication message, the user generates , and and computes , and . Finally the user transmits , , , and through a public channel to the gateway.
- 2.
- To authenticate the user, the gateway retrieves and computes . The gateway checks ’s freshness and if = ? . The gateway also checks for whether or not is a valid range. If and are valid, the user verification is passed; if not, the procedure is stopped. To generate the authentication message, the gateway generates and computes , , , and . Finally the gateway transmits , , , , and through a public channel to the sensor node.
- 3.
- To authenticate the gateway, the sensor node retrieves , , and then computes . The sensor node checks = ? . If the equation is equal, the gateway verification is passed; if not, the procedure is stopped. To generate the session key , the sensor node generates and computes , and . The sensor node replaces by . Finally, the sensor node transmits , and through a public channel to the gateway.
- 4.
- To authenticate the sensor node, the gateway computes and checks if = ? . If the equation is equal, the sensor node verification is passed. To generates an authentication message, the gateway computes and and replaces by . Finally, the gateway transmits , , and through a public channel to the user.
- 5.
- To authenticate the gateway, the user computes , and . The user checks if = ? . If the equation is equal, the gateway verification is passed; if not, the procedure is stopped. To obtain the session key , the user retrieves and computes . The user checks = ? . If the equation is equal, the user obtains the valid session key ; if not, the procedure is stopped.
7. Security Analysis of the Proposed Scheme
In this section, we demonstrate formal and informal security analysis. We use the security verification tool ProVerif to demonstrate that the proposed scheme can satisfy security and authentication features. As an informal security analysis, we show how our proposed scheme meets the security requirements for an IoMT sensor protocol.
7.1. Formal Security Analysis
In this section, the ProVerif tool [23] is used to evaluate the security of the proposed protocol. ProVerif tool is an automatic cryptographic protocol verifier that was developed by Bruno Blanchet [13]. Several studies have used this tool to demonstrate the safety of their protocols [24,25].
We use two types, and four channels in total. Private channel1 and Private channel2 transmit sensitive data between the user and the gateway and between the gateway and the sensor node, respectively. Public channel1 and Public channel2 transmit general data between the user and the gateway and between the gateway and the sensor node, respectively. Table 5 presents the definitions of the channels, variables, and other related parameters. The processes performed by the user, the gateway, and the sensor node are presented in Table 6, Table 7 and Table 8, respectively. Lastly, the queries and main process are detailed in Table 9.

Table 5.
Definitions of channels, variables and other related parameters.

Table 6.
User’s process.

Table 7.
Gateway’s process.

Table 8.
Sensor node’s process.

Table 9.
Queries and main process.
The results of our proposed scheme are presented in Table 10. It can be seen that the proposed protocol kept the session key safe from the attacker.

Table 10.
Result.
When we run the following query in Table 9, we can obtain the following results:
- 1.
- Query inj–event(endEVENTA) ==> inj-event(startEVENTA) is true.
- 2.
- Query inj–event(endEVENTB) ==> inj-event(startEVENTB) is false.
- 3.
- Query not attacker(M) is true.
- 4.
- Query not attacker(M) is false.
“Query inj-event (endEVENTA) == > inj-event (startEVENTA) is true.” means that the process from endEVENTA to startEVENTA has been authenticated. By contrast, “Query inj-event (endEVENTB) == > inj-event (startEVENTB) is false.” means that the authentication from endEVENTB to startEVENTB is not successful. “Query not attacker (M) is true.” means that an attacker cannot acquire a free name M. Finally, “Query not attacker (M) is false.” means that an attacker can trace the M.
7.2. Informal Security Analysis
We performed a formal analysis. However, a formal analysis by itself is not sufficient to prove safety [13,26,27]. Therefore, we further analyzed our scheme using an informal analysis. We present a theoretical analysis of the proposed scheme. The results of the informal security analysis are then briefly described.
- 1.
- Offline Password Guessing Attack: Since our scheme uses biometric information with the unique biological characteristics of individuals that are not stored for user authentication, it is impossible to guess a user’s password without a real user. Therefore our scheme can protect against the offline password guessing attack.
- 2.
- Privileged Insider Attack: Even if the privileged insider steals , , , , and from the gateway’s database, the privileged insider can not obtain the session key SK without secret information that is shared between the user and the sensor node. Therefore our scheme can protect against privileged insider attacks.
- 3.
- User Impersonation Attack: Even if the attacker steals and replaces the user’s , the attacker can not generate valid and without secret information and . When the gateway and the sensor node verify and , respectively, they can find the invalid user. Therefore our scheme can protect against user impersonation attacks.
- 4.
- Server Impersonation Attack: Even if the attacker impersonates the gateway, the attacker does not generate valid and without and . When the sensor node and the user verify and , respectively, they can find the invalid gateway. Therefore our scheme can protect against server impersonation attacks.
- 5.
- Replay Attack: Even if the attacker steals , , , and from a successful mutual authentication and key distribution phase and then resends it to the gateway, the gateway can find whether or not the message is reused because the gateway checks ’s freshness. Moreover, the attacker can not generate and modify and without . Therefore our scheme can protect against replay attacks.
- 6.
- Man-in-the-Middle Attack: In a man-in-the-middle attack, an attacker puts themselves in the middle of two parties so that they can intercept and modify some communicated data to masquerade as the entities. In the mutual authentication and key distribution phase, the attacker intercepts communicated data between the user and the gateway and attempts to modify the message to retrieve the session key. However, in our scheme, the attacker can not modify communicated messages without the secret information and . Therefore our scheme can protect against man-in-the-middle attacks.
- 7.
- Session Key Disclosure Attack: Even if the attacker obtains which includes the session key , the attacker can not obtain the session key without the secret information . Therefore, our scheme can protect against session key disclosure attacks.
- 8.
- Forward Secrecy and Backward Secrecy: Even if someone gains the session key , they can not know the old session key or the new session key because each session key is generated randomly with no relation to the other session keys. Therefore our scheme can preserve forward secrecy and backward secrecy.
- 9.
- Mutual Authentication: The gateway and the user can authenticate each other by verifying and respectively, using the secret information . Therefore our scheme provides mutual authentication.
- 10.
- User Anonymity: Our scheme identifies users using and then replaces it every time with regardless of the old . Therefore our scheme preserves user anonymity.
The results of the security analysis with comparisons to related papers are presented in Table 11.

Table 11.
Comparisons of the security features.
8. Performance Analysis of the Proposed Scheme
Many authentication studies have analyzed their performance in the following manner [9,10,11,12,13,14,15,20,21,22,24,25,26,27,28,29,30,31,32]. We compared each computation amount in terms of the research methods used. We analyze the performance of our scheme as follows.
Our study analyzes the computational cost using the time measurement presented in Table 12 [28,29]. stands for the computational cost of multiplication in the field. stands for the computational cost of the biohash function operation, and stands for the computational cost of the one-way hash function operation. It is assumed that the XOR operation does not affect the cost of operation. Table 13 and Figure 2 compare the computational cost of our scheme with those of other schemes according to Table 12 [6,12,15].

Table 12.
Computational cost of cryptographic calculations (ms).

Table 13.
Comparisons of computational cost.
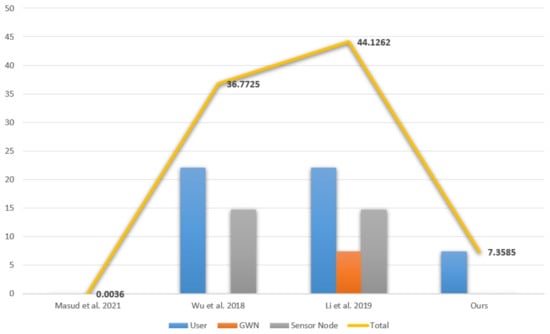
Figure 2.
Graph comparisons of computational cost [6,12,15].
We calculate the computational efficiency of our scheme as follows:
In Formula (3), represents the average cost of computation of the different schemes. Moreover, represents the cost of operation of our scheme.
According to the above formula, the operation of our scheme is 266.48% more efficient in terms of computational cost than the other schemes, and Table 11 shows that our scheme is more secure than the other methods.
9. Discussion of Performance
We proposed a secure and lightweight user authentication scheme for IoMT by improving Masud et al. [6]’s scheme. We compared the performance of three schemes [6,12,15] in Section 8. Our scheme outperforms [12,15] by 399.73% and 499.66% respectively. The performance of [6] is lightweight, but it does not meet basic security requirements such as offline password guessing attacks, privileged insider attacks, and replay attacks. Therefore, our scheme is a suitable lightweight user authentication scheme for IoMT because our scheme not only is improved by addressing the security threats of [6] but also outperforms 266.48% more efficiently than the other schemes.
10. Conclusions
The purpose of our paper was to propose a secure and lightweight user authentication scheme for IoMT by addressing the security threats to which Masud et al. [6]’s scheme is vulnerable. In particular, our scheme can protect against well-known attacks in IoMT i.e., offline password guessing attacks, privileged insider attacks, user impersonation attacks, replay attacks, and session key disclosure attacks, and it ensures user anonymity. We also proved that our scheme is a suitable user authentication scheme for IoMT through formal security analysis by ProVerif. Moreover, we proposed a lightweight security protocol that mainly uses a hash function and XOR operation considering low-spec healthcare sensors. As a result, we showed 266.48% better performance than the average computational cost of the considered schemes [6,12,15]. Our scheme outperforms [12,15], but it does not outperform [6]. Our scheme shows higher safety than the compared schemes [6,12,15]. Our security and performance analysis shows that our scheme is a suitable lightweight user authentication scheme for IoMT. Further studies will be able to improve convenience by combining behavioral biometrics authentication. Behavioral biometric authentication is expected to achieve further improved convenience over biometrics authentication because it uses keystroke dynamics, gait analysis, mouse use characteristics, signature analysis, and cognitive biometrics.
Author Contributions
Conceptualization, K.K.; Methodology, K.K., J.R. and Y.L.; Software, K.K.; Validation, J.R.; Formal analysis, K.K. and Y.L.; Writing—original draft, K.K. and J.R.; Writing—review and editing, J.R., Y.L. and D.W.; Supervision, D.W.; Funding acquisition, D.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
Thiswork was supported by an Institute of Information & Communications Technology Planning Evaluation (IITP) grant funded by the Korea government (MSIT) (No. 2021-0-00558, Development of National Statistical Analysis System using Homomorphic Encryption Technology).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Jha, N.K. Internet-of-Medical-Things. In Proceedings of the Great Lakes Symposium on VLSI (GLSVLSI), Banff, AB, Canada, 10–12 May 2017; p. 7. [Google Scholar]
- Hatzivasilis, G.; Soultatos, O.; Ioannidis, S.; Verikoukis, C.; Demetriou, G.; Tsatsoulis, C. Review of security and privacy for the Internet of Medical Things (IoMT). In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 29–31 May 2019; pp. 457–464. [Google Scholar]
- Dilibal, C.; Davis, B.L.; Chakraborty, C. Generative design methodology for internet of medical things (IoMT)-based wearable biomedical devices. In Proceedings of the 2021 3rd International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 11–13 June 2021; pp. 1–4. [Google Scholar]
- Aman, A.H.M.; Hassan, W.H.; Sameen, S.; Attarbashi, Z.S.; Alizadeh, M.; Latiff, L.A. IoMT amid COVID-19 pandemic: Application, architecture, technology, and security. J. Netw. Comput. Appl. 2021, 174, 102886. [Google Scholar] [CrossRef] [PubMed]
- Khadidos, A.O.; Shitharth, S.; Khadidos, A.O.; Sangeetha, K.; Alyoubi, K.H. Healthcare Data Security Using IoT Sensors Based on Random Hashing Mechanism. J. Sens. 2022, 2022, 8457116. [Google Scholar] [CrossRef]
- Masud, M.; Gaba, G.S.; Choudhary, K.; Hossain, M.S.; Alhamid, M.F.; Muhammad, G. Lightweight and anonymity-preserving user authentication scheme for IoT-based healthcare. IEEE Internet Things J. 2021, 9, 2649–2656. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Liao, I.E.; Lee, C.C.; Hwang, M.S. A password authentication scheme over insecure networks. J. Comput. Syst. Sci. 2006, 72, 727–740. [Google Scholar] [CrossRef]
- Wu, Z.Y.; Lee, Y.C.; Lai, F.; Lee, H.C.; Chung, Y. A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 2012, 36, 1529–1535. [Google Scholar] [CrossRef]
- Debiao, H.; Jianhua, C.; Rui, Z. A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 2012, 36, 1989–1995. [Google Scholar] [CrossRef]
- Wei, J.; Hu, X.; Liu, W. An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 2012, 36, 3597–3604. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. An improved and provably secure three-factor user authentication scheme for wireless sensor networks. Peer-Peer Netw. Appl. 2018, 11, 1–20. [Google Scholar] [CrossRef]
- Ryu, J.; Lee, H.; Kim, H.; Won, D. Secure and efficient three-factor protocol for wireless sensor networks. Sensors 2018, 18, 4481. [Google Scholar] [CrossRef]
- Mao, D.; Liu, H.; Zhang, W. An enhanced three-factor authentication scheme with dynamic verification for medical multimedia information systems. IEEE Access 2019, 7, 167683–167695. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Syst. J. 2019, 14, 39–50. [Google Scholar] [CrossRef]
- Ebrahimi, S.; Bayat–Sarmadi, S. Lightweight fuzzy extractor based on LPN for device and biometric authentication in IoT. IEEE Internet Things J. 2021, 8, 10706–10713. [Google Scholar] [CrossRef]
- Satamraju, K.P.; Malarkodi, B. A PUF-based mutual authentication protocol for internet of things. In Proceedings of the 2020 5th International Conference on Computing, Communication and Security (ICCCS), Patna, India, 14–16 October 2020; pp. 1–6. [Google Scholar]
- Abdaoui, A.; Erbad, A.; Al-Ali, A.K.; Mohamed, A.; Guizani, M. Fuzzy Elliptic Curve Cryptography for Authentication in Internet of Things. IEEE Internet Things J. 2021, 9, 9987–9998. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; pp. 523–540. [Google Scholar]
- Ryu, J.; Lee, H.; Lee, Y.; Won, D. SMASG: Secure Mobile Authentication Scheme for Global Mobility Network. IEEE Access 2022, 10, 26907–26919. [Google Scholar] [CrossRef]
- Kang, D.; Lee, H.; Lee, Y.; Won, D. Lightweight user authentication scheme for roaming service in GLOMONET with privacy preserving. PLoS ONE 2021, 16, e0247441. [Google Scholar] [CrossRef]
- Ryu, J.; Kang, D.; Lee, H.; Kim, H.; Won, D. A secure and lightweight three-factor-based authentication scheme for smart healthcare systems. Sensors 2020, 20, 7136. [Google Scholar] [CrossRef]
- Blanchet, B.; Smyth, B.; Cheval, V.; Sylvestre, M. ProVerif 2.04: Automatic Cryptographic Protocol Verifier, User Manual and Tutorial. Available online: https://proverif.inria.fr/manual.pdf (accessed on 30 November 2021).
- Kang, D.; Jung, J.; Lee, D.; Kim, H.; Won, D. Security analysis and enhanced user authentication in proxy mobile IPv6 networks. PLoS ONE 2017, 12, e0181031. [Google Scholar] [CrossRef]
- Roy, S.; Chatterjee, S.; Das, A.K.; Chattopadhyay, S.; Kumari, S.; Jo, M. Chaotic map–based anonymous user authentication scheme with user biometrics and fuzzy extractor for crowdsourcing Internet of Things. IEEE Internet Things J. 2017, 5, 2884–2895. [Google Scholar] [CrossRef]
- Lee, H.; Lee, D.; Moon, J.; Jung, J.; Kang, D.; Kim, H.; Won, D. An improved anonymous authentication scheme for roaming in ubiquitous networks. PLoS ONE 2018, 13, e0193366. [Google Scholar] [CrossRef]
- Jung, J.; Kim, J.; Choi, Y.; Won, D. An anonymous user authentication and key agreement scheme based on a symmetric cryptosystem in wireless sensor networks. Sensors 2016, 16, 1299. [Google Scholar] [CrossRef] [PubMed]
- Xu, L.; Wu, F. Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J. Med. Syst. 2015, 39, 1–9. [Google Scholar] [CrossRef] [PubMed]
- Das, A.K. A secure and robust temporal credential-based three-factor user authentication scheme for wireless sensor networks. Peer-Peer Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Sahoo, S.S.; Mohanty, S.; Majhi, B. An efficient three-factor user authentication scheme for industrial wireless sensor network with fog computing. Int. J. Commun. Syst. 2022, 35, 3. [Google Scholar] [CrossRef]
- Bahache, A.N.; Chikouche, N.; Mezrag, F. Authentication Schemes for Healthcare Applications Using Wireless Medical Sensor Networks: A Survey. SN Comput. Sci. 2022, 3, 1–25. [Google Scholar] [CrossRef]
- Li, Y.; Tian, Y. A Lightweight and Secure Three-Factor Authentication Protocol With Adaptive Privacy-Preserving Property for Wireless Sensor Networks. IEEE Syst. J. 2022, 16, 6197–6208. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).