Enhancing Security of Web-Based IoT Services via XSS Vulnerability Detection †
Abstract
:1. Introduction
2. Related Works
3. Preliminaries
3.1. Concolic Executions
3.2. Dynamic Taint Analysis
3.3. Constraint Solving
4. Proposed Method
4.1. Extended Tomcat Servlet Runner for Concolic Execution
4.2. Instrumentation Module
- User inputs (including cookie and run-time settings) are tainted when analysis starts;
- The left-hand-side variable of the assignment statement is tainted if the right-hand side contains tainted variable(s);
- The variable copied from the function call and return value are tainted if the source is tainted;
- If the tainted variable is used at the taint sink, it is vulnerable.
- Records user inputs that influence the control flow as symbolic values;
- Updates the variable’s symbolic expression when a variable is updated on change of user-input and performs the symbolic evaluation;
- Represents the changes in the control flow of the execution path (such as branch, loop statements, function calls, etc.) as the symbolic expression for regeneration of input data.
4.3. New Input Generation and Code Coverage
5. Applications and Experiments
5.1. Applications
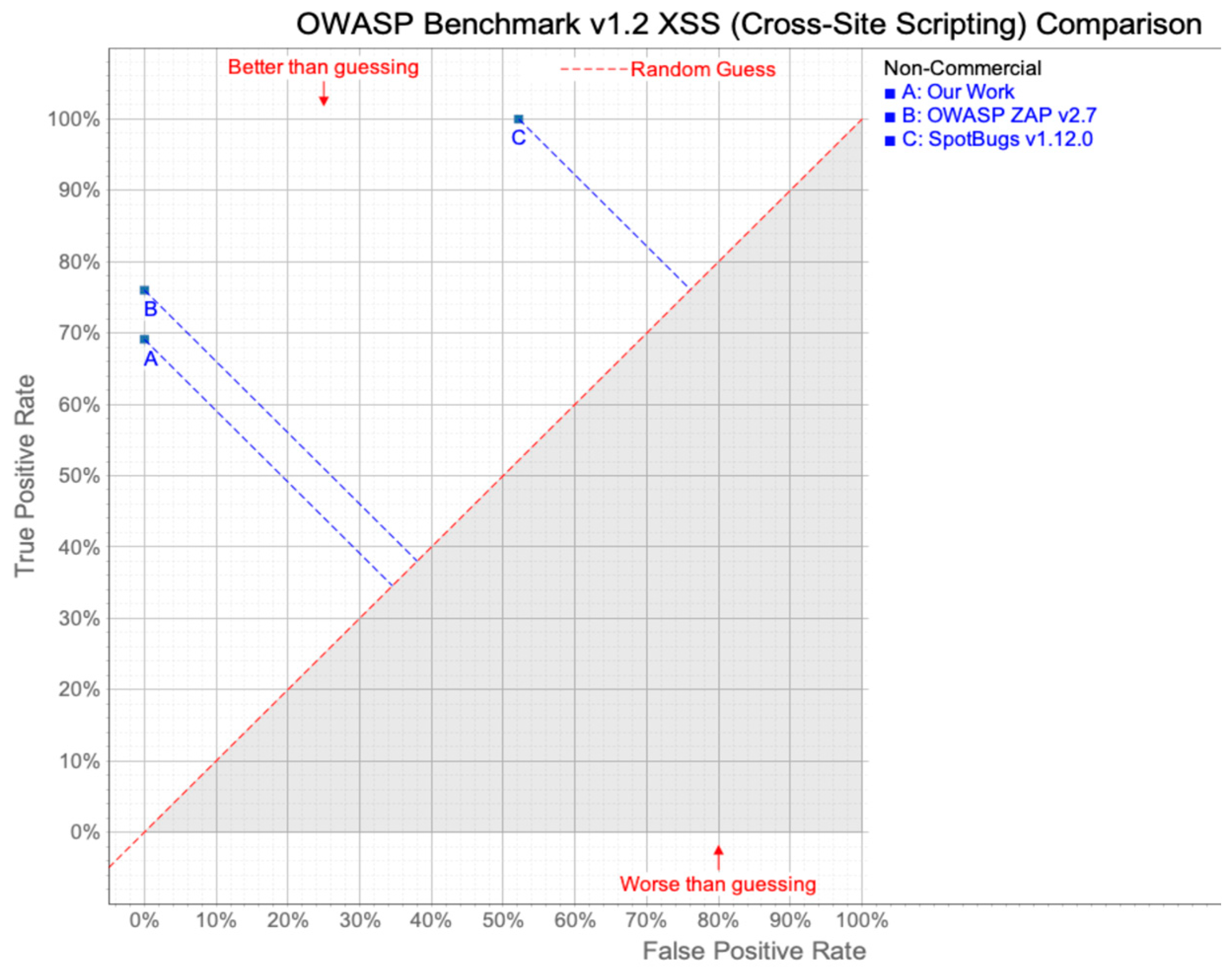
5.2. Experimental Results
6. Conclusions and Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Hassan, R.; Qamar, F.; Hasan, M.K.; Hazah, A.; Aman, M.; Ahmed, A.S. Internet of Things and its applications: A comprehensive survey. Symmetry 2020, 12, 1674. [Google Scholar] [CrossRef]
- Mishra, N.; Pandya, S. Internet of Things Applications, Security Challenges, Attacks, Intrusion Detection, and Future Visions: A Systematic Review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef] [PubMed]
- Tewari, A.; Gupta, B.B. Security, privacy and trust of different layers in Internet-of-Things (IoTs) framework. Future Gener. Comput. Syst. 2020, 108, 909–920. [Google Scholar] [CrossRef]
- Gupta, S.; Gupta, B.B. XSS-immune: A Google chrome extension-based XSS defensive framework for contemporary platforms of web applications. Secur. Commun. Netw. 2016, 9, 3966–3986. [Google Scholar] [CrossRef]
- Delceb, S.; Draskovic, D. Modern javascript frameworks: A survey study. In Proceedings of the 2018 Zooming Innovation in Consumer Technologies Conference (ZINC), Novi Sad, Serbia, 30–31 May 2018; pp. 106–109. [Google Scholar]
- BuiltWith. Available online: https://trends.builtwith.com/framework (accessed on 6 October 2022).
- Sen KMarinov, D.; Agha, G. CUTE: A Concolic Unit Testing Engine for C. In Proceedings of the 10th European Software Engineering Conference Held Jointly with 13th ACM SIGSOFT International Symposium on Foundations of Software Engineering, New York, NY, USA, 5–9 September 2005; pp. 263–272. [Google Scholar]
- Kim, J.; Park, J. Taint Analysis Scheme using Concolic Execution to Find XSS Flaws in Legacy Java Web Applications. In Proceedings of the International Conferences on Next Generation Computing (ICNGC), Jeju, Republic of Korea, 6–8 October 2022; pp. 191–194. Available online: https://www.earticle.net/Article/A419772 (accessed on 20 November 2023).
- Chaudhary, P.; Gupta, B.B.; Singh, A.K.; Kwok Tai, J.C. Cognitive XSS Defensive Approach to Secure Smart Devices. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics—Taiwan, Taipei, Taiwan, 6–8 July 2022; pp. 461–462. [Google Scholar] [CrossRef]
- Chaudhary, P.; Gupta, B.B.; Singh, A.K. Securing heterogeneous embedded devices against XSS attack in intelligent IoT system. Comput. Secur. 2022, 118, 102710. [Google Scholar] [CrossRef]
- Boppana, T.K.; Bagade, P. Security risks in MQTT-based Industrial IoT Applications. In Proceedings of the 2022 IEEE International Conference on Omni-layer Intelligent Systems (COINS), Barcelona, Spain, 1–3 August 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Liu, M.; Zhang, B.; Chen, W.; Zhang, X. A Survey of Exploitation and Detection Methods of XSS Vulnerabilities. IEEE Access 2019, 7, 182004–182016. [Google Scholar] [CrossRef]
- Kieyzun, A.; Guo, P.J.; Jayaraman, K.; Ernst, M.D. Automatic Creation of SQL Injection and Cross-Site Scripting Attacks. In Proceedings of the 31st International Conference on Software Engineering, in ICSE’09, Vancouver, BC, Canada, 16–24 May 2009; IEEE Computer Society: Washington, DC, USA, 2009; pp. 199–209. [Google Scholar] [CrossRef]
- Hydara, I.; Sultan, A.B.; Zulzalil, H.; Admodisastro, N. Current state of research on cross-site scripting (XSS)—A systematic literature review. Inf. Softw. Technol. 2015, 58, 170–186. [Google Scholar] [CrossRef]
- Yavuz, T.; Brant, C. Security Analysis of IoT Frameworks Using Static Taint Analysis. In Proceedings of the Twelfth ACM Conference on Data and Application Security and Privacy, Baltimore, MD, USA, 24–27 April 2022; pp. 203–213. [Google Scholar]
- Wassermann, G.; Su, Z. Static Detection of Cross-Site Scripting Vulnerabilities. In Proceedings of the 30th International Conference on Software Engineering, Leipzig, Germany, 10–18 May 2008; pp. 171–180. [Google Scholar]
- Livshits, V.B.; Lam, M.S. Finding Security Vulnerabilities in Java Applications with Static Analysis. In Proceedings of the 14th Conference on USENIX Security Symposium—Volume 14, in SSYM’05, Baltimore, MD, USA, 31 July–5 August 2005; USENIX Association: Berkeley, CA, USA, 2005; p. 18. [Google Scholar]
- Tripp, O.; Pistoia, M.; Fink, S.J.; Sridharan, M.; Weisman, O. TAJ: Effective Taint Analysis of Web Applications. In Proceedings of the 30th ACM SIGPLAN Conference on Programming Language Design and Implementation, Dublin, Ireland, 15–21 June 2009; Association for Computing Machinery: New York, NY, USA, 2009; pp. 87–97. [Google Scholar]
- Ayewah, N.; Pugh, W.; Hovermeyer, D.; Morgenthaler, J.D.; Penix, J. Using static analysis to find bugs. IEEE Softw. 2008, 25, 22–29. [Google Scholar] [CrossRef]
- Kaur, A.; Nayyar, R. A comparative study of static code analysis tools for vulnerability detection in c/c++ and java source code. Procedia Comput. Sci. 2020, 171, 2023–2029. [Google Scholar] [CrossRef]
- Saxena, P.; Molnar, D.; Livshits, B. SCRIPTGARD: Automatic Context-Sensitive Sanitization for Large-Scale Legacy Web Applications. In Proceedings of the 18th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; Association for Computing Machinery: New York, NY, USA, 2011; pp. 601–614. [Google Scholar]
- Mohammadi, M.; Chu, B.; Lipford, H.R.; Murphy-Hill, E. Automatic Web Security Unit Testing: XSS Vulnerability Detection. In Proceedings of the 11th International Workshop on Automation of Software Test, Austin, TX, USA, 14–22 May 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 78–84. [Google Scholar]
- Mburano, B.; Si, W. Evaluation of web vulnerability scanners based on owasp benchmark. In Proceedings of the 2018 26th International Conference on Systems Engineering (ICSEng), Sydney, NSW, Australia, 18–20 December 2018; pp. 1–6. [Google Scholar]
- Godefroid, P.; Klarlund, N.; Sen, K. DART: Directed Automated Random Testing. In Proceedings of the 2005 ACM SIGPLAN Conference on Programming Language Design and Implementation, Chicago, IL, USA, 12–15 June 2005; Association for Computing Machinery: New York, NY, USA, 2005; pp. 213–223. [Google Scholar]
- Cadar, C.; Dunbar, D.; Engler, D. KLEE: Unassisted and Automatic Generation of High-Coverage Tests for Complex Systems Programs. In Proceedings of the 8th USENIX Conference on Operating Systems Design and Implementation, San Diego, CA, USA, 8–10 December 2008; pp. 209–224. [Google Scholar]
- Sen, K.; Agha, G. CUTE and JCUTE: Concolic Unit Testing and Explicit Path Model-Checking Tools. In Proceedings of the 18th International Conference on Computer Aided Verification, Berlin, Heidelberg, 17–20 August 2006; pp. 419–423. [Google Scholar]
- Luckow, K.; Dimjašević, M.; Giannakopoulou, D.; Howar, F.; Isberner, M.; Kahsai, T.; Rakamarić, Z.; Raman, V. JDart: A Dynamic Symbolic Analysis Framework. In Proceedings of the 22nd International Conference on Tools and Algorithms for the Construction and Analysis of Systems, Berlin, Heidelberg, 2–8 April 2016; Volume 9636, pp. 442–459. [Google Scholar]
- Corin, R.; Manzano, F.A. Taint Analysis of Security Code in the KLEE Symbolic Execution Engine. In Proceedings of the Information and Communications Security: 14th International Conference, ICICS 2012, Hong Kong, China, 29–31 October 2012; pp. 264–275. [Google Scholar]
- Mues, M.; Schallau, T.; Howar, F. Jaint: A Framework for User-Defined Dynamic Taint-Analyses Based on Dynamic Symbolic Execution of Java Programs. In Proceedings of the Integrated Formal Methods: 16th International Conference, IFM 2020, Lugano, Switzerland, 16–20 November 2020; pp. 123–140. [Google Scholar]
- Visser, W.; Mehlitz, P. Model Checking Programs with Java Pathfinder. In Proceedings of the 12th International Conference on Model Checking Software, in SPIN’05, San Francisco, CA, USA, 22–24 August 2005; Springer: Berlin, Heidelberg, 2005; p. 27. [Google Scholar] [CrossRef]
- Baldoni, R.; Coppa, E.; D’elia, D.C.; Demetrescu, C.; Finocchi, I. A Survey of Symbolic Execution Techniques. ACM Comput. Surv. 2018, 51, 1–39. [Google Scholar] [CrossRef]
- Schwartz, E.J.; Avgerinos, T.; Brumley, D. All You Ever Wanted to Know about Dynamic Taint Analysis and Forward Symbolic Execution (but Might Have Been Afraid to Ask). In Proceedings of the 2010 IEEE Symposium on Security and Privacy, in SP’10, Berkeley, CA, USA, 16–19 May 2010; IEEE Computer Society: Washington, DC, USA, 2010; pp. 317–331. [Google Scholar] [CrossRef]
- Cadar, C.; Sen, K. Symbolic Execution for Software Testing: Three Decades Later. Commun. ACM 2013, 56, 82–90. [Google Scholar] [CrossRef]
- De Moura, L.; Bjørner, N. Z3: An Efficient SMT Solver. In Proceedings of the Theory and Practice of Software, 14th International Conference on Tools and Algorithms for the Construction and Analysis of Systems, Berlin, Heidelberg, 29 March–6 April 2008; pp. 337–340. [Google Scholar]
- Tomcat. Available online: https://github.com/apache/tomcat (accessed on 6 October 2022).
- Bruneton, E.; Lenglet, R.; Coupaye, T. ASM: A code manipulation tool to implement adaptable systems. Adapt. Extensible Compon. Syst. 2002, 30, 19. [Google Scholar]
- Livshits, B. Defining a set of common benchmarks for web application security. In Proceedings of the Workshop on Defining the State of the Art in Software Security Tools, Gaithersburg, MD, USA, 10–11 August 2005; Available online: http://too4words.github.io/securibench-micro (accessed on 20 October 2023).
- OWASP-Benchmark Utilities. Available online: https://github.com/OWASP-Benchmark/BenchmarkUtils/blob/main/LICENSE (accessed on 22 November 2023).
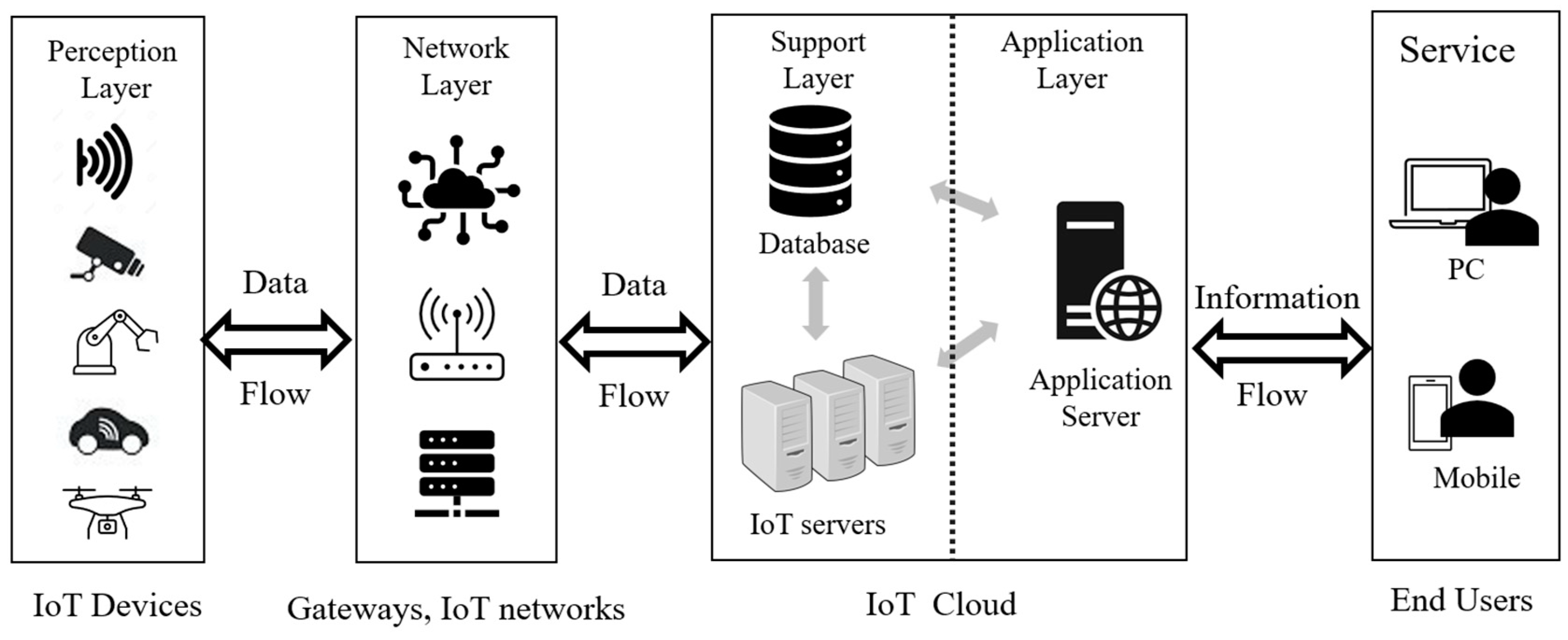
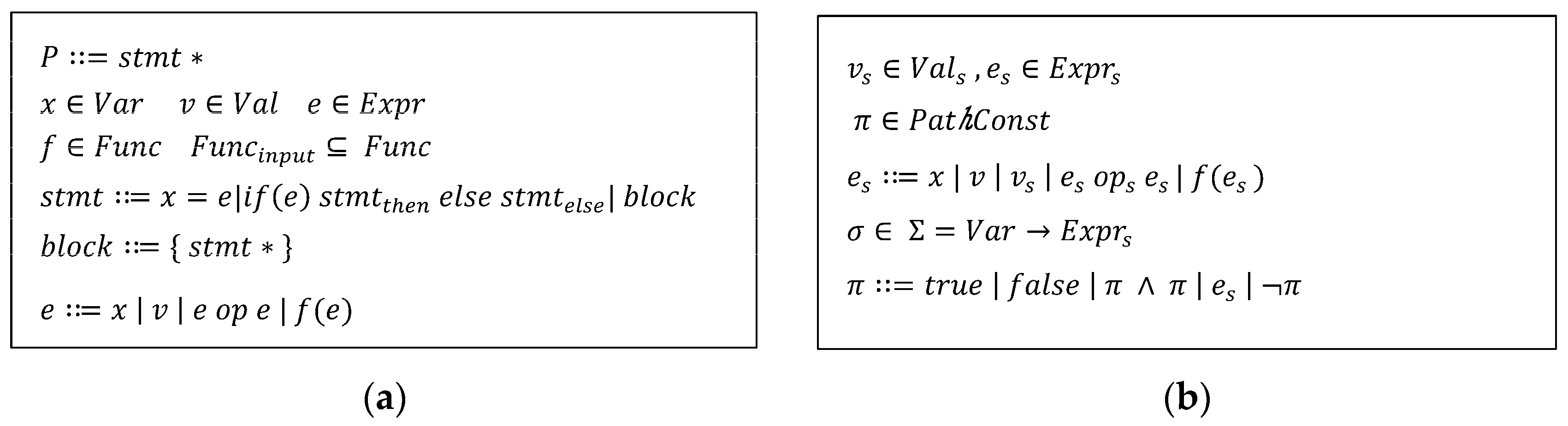





| Layer | Roles | Representative Security Attacks |
|---|---|---|
| Perception Layer | Collect raw data using sensors, actuators, and controllers | Node Capture Attack, Malicious Code Injection Attack, False Data Injection Attack, Side Channel Attack |
| Network Layer | Transport data via networks (BLE, Wifi, 5G, etc.) | Phishing attack, DDoS attack, Data Transit Attack, Routing attack, Storage Attack |
| Support Layer | System-level data processing management (e.g., computing, resource, storage management) | DDoS Attack, Man-in-The-Middle Attack, SQL-injection |
| Application Layer | Interfaces with end-users Provides diverse web-based services | Cross-site Scripting, Access control attack, Malicious Code Injections, Sniffing |
| Method | Parameters | Instrumentation Policy | Roles |
|---|---|---|---|
| TaintSrc | user input | Replace function f with TaintSrc if | Handle user input as tainted (DTA **) Generate symbolic expression of user input (CE ***) |
| Propagate | tainted variable | Add after assignment statement if tainted variable is used | Trace the propagation of tainted variables (DTA) Update symbolic expressions of variables (CE) |
| PrintAndCheck | http output | Replace function f with PrintAndCheck if | Check the taintedness of argument expression and output html (DTA) |
| PcAppend | branch condition (string) | Add es * and es at the head of and for | Conditions of branch are accumulated to trace log (CE) |
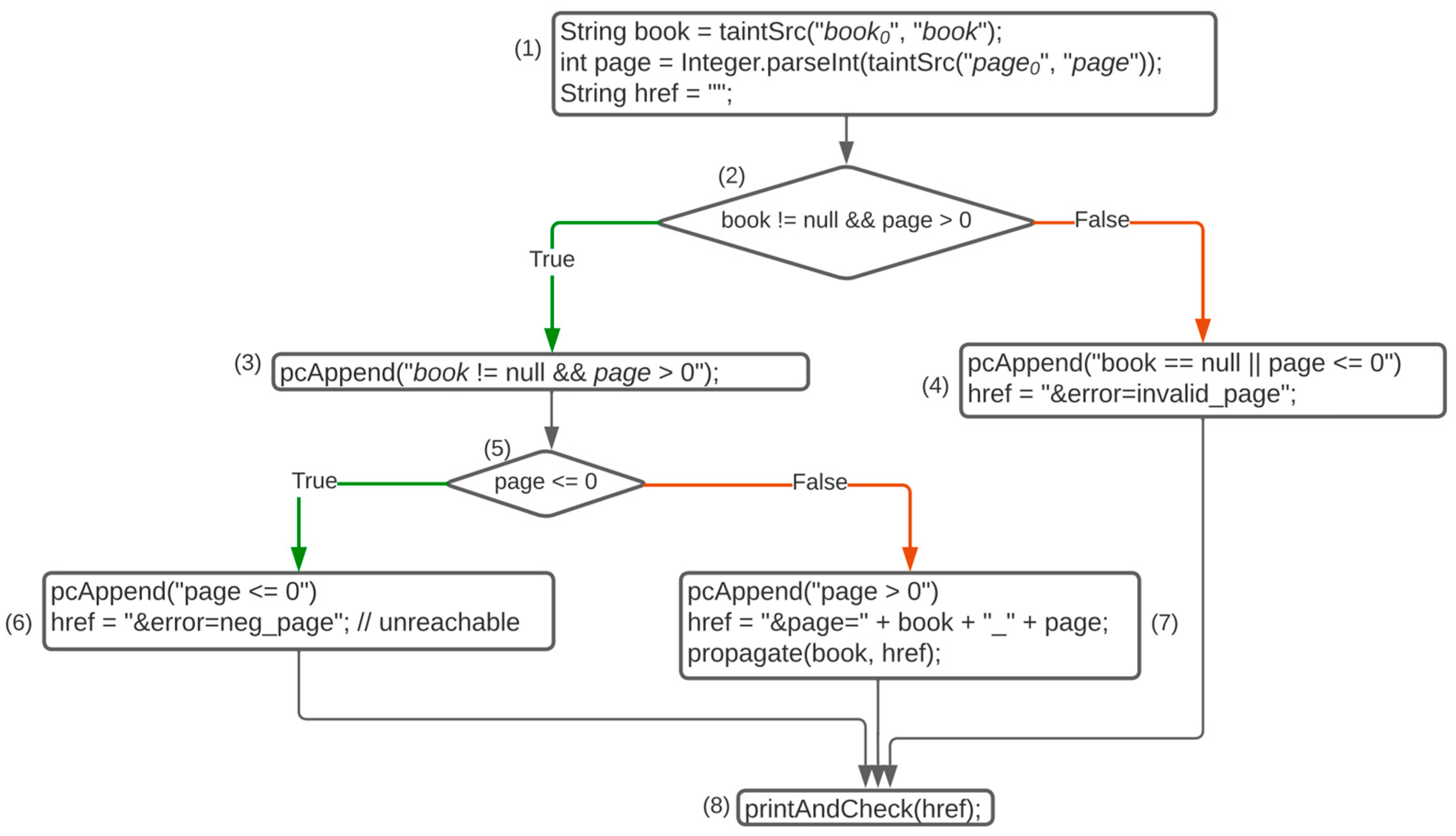
| Variables | Execution Path | Path Constraint | ||||
|---|---|---|---|---|---|---|
| book (conc.) | page (conc.) | book (symb.) | page (symb.) | href (symb.) | ||
| “a” | 10 | book0 | page0 | “&book =” + book0 + “_” +page0 | (1)(2)(3)(5)(7)(8) | (book0 ! = null && page0 > 0) ∧ (page0 > 0) |
| “x” | 0 | book0 | page0 | “&error = invalid_page” | (1)(2)(4)(8) | (book0 == null || page0 ≤ 0) |
| Categorical Sets | XSS Detection Results | |
|---|---|---|
| TP/(TP + FN) | FP/(TN + FP) | |
| Aliasing | 10/10 | 0/2 |
| Arrays | 9/9 | 0/6 |
| Basic | 33/37 | 0/6 |
| Pred | 3/5 | 0/4 |
| Session | 3/3 | 0/1 |
| Strong_updates | 0/0 | 0/4 |
| Total | 58/64 (TPR 90.62%) | 0/23 (FPR 0%) |
| XSS Detection Results | ||||||
|---|---|---|---|---|---|---|
| TP | FN | TN | FP | Total | TPR | FPR |
| 170 | 76 | 209 | 0 | 455 | 69.11% | 0% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, J.; Park, J. Enhancing Security of Web-Based IoT Services via XSS Vulnerability Detection. Sensors 2023, 23, 9407. https://doi.org/10.3390/s23239407
Kim J, Park J. Enhancing Security of Web-Based IoT Services via XSS Vulnerability Detection. Sensors. 2023; 23(23):9407. https://doi.org/10.3390/s23239407
Chicago/Turabian StyleKim, Jemin, and Joonseok Park. 2023. "Enhancing Security of Web-Based IoT Services via XSS Vulnerability Detection" Sensors 23, no. 23: 9407. https://doi.org/10.3390/s23239407
APA StyleKim, J., & Park, J. (2023). Enhancing Security of Web-Based IoT Services via XSS Vulnerability Detection. Sensors, 23(23), 9407. https://doi.org/10.3390/s23239407






