Blockchain-Driven Intelligent Scheme for IoT-Based Public Safety System beyond 5G Networks
Abstract
1. Introduction
1.1. Applications of Blockchain in 6G Network
1.1.1. Smart Healthcare
1.1.2. Smart Manufacturing
1.1.3. Smart City
1.1.4. Smart Vehicles
1.1.5. Smart Grid
1.1.6. Smart Agriculture
1.2. Motivation
- Most of the existing literature focuses on the role of blockchain in 6G-based applications; however, there are a few research articles available in which the authors studied the drivers, enablers, security requirements, and applicability of blockchain in 6G-based smart applications.
- From the literature review, we observed that no comprehensive work exists that considers the security and privacy challenges of IoT-based public safety applications using blockchain technology.
- Thus, there is a stringent requirement to provide exhaustive work on the applicability of blockchain in IoT-based public safety applications underlying a 6G network.
1.3. Research Contributions
- Through this article, we propose a detailed work on the applicability of blockchain in a 6G network. We also analyze the 6G-based smart applications and discuss how blockchain features provide trust, security, authenticity, confidentiality, and privacy.
- We explore different 6G-network-based services and discuss the influence of blockchain in delivering 6G-based services to various smart applications.
- We consider a blockchain- and 6G-based case study for public safety applications to showcase the adoption of blockchain technology in the 6G network interface. Further, the case study is assessed by considering blockchain scalability, 6G latency, and AI statistical measures parameters.
- Lastly, we perform an in-depth analysis and identify the research challenges of the adoption of blockchain in the 6G network to motivate the researchers working on the same domain.
2. Related Works
Organization
3. Role of Blockchain in 6G Services
3.1. Network Slicing
3.2. Spectrum Sharing
3.3. Data Sharing
3.4. Resource Management
| Author | Year | 6G Application | Objective | Implication of Blockchain | Methodology | Remarks | |
|---|---|---|---|---|---|---|---|
| Network slicing | Abdulqadder et al. [39] | 2022 | NFV and SDN | Context-aware authentication handover. | The proposed scheme tackle security, QoS guarantee, and improper resource utilization challenges through network slicing and load balancing. | Generative adversarial network and DAG-blockchain. | Not focused on the privacy threats of the 6G. |
| He et al. [40] | 2021 | NFV and SDN | Multi domain network slicing. | Offers end-to-end network slice orchestration services and privacy-preserving scheme for private network. | CoNet consensus algorithm. | The scheme does not consider time complexity for multiparty computation. | |
| Chen et al. [41] | 2020 | IoT | Optical network slices for user. | To provide user’s data security and trust. | Blockchain-based optical network slicing approach. | Does not consider other performance evaluation parameters such as throughput, scalability. | |
| Spectrum sharing | Liu et al. [48] | 2021 | IoT, cloud | Radio spectrum resource sharing -tructure in eURLLC. | Integrate blockchain with hybrid cloud to register and manage the information of IoT devices. | Reinforcement learning. | Does not discuss energy efficiency. |
| Zhang et al. [49] | 2021 | IoT | To manage a large-scale IoT network with heterogeneous devices. | DAG-blockchain for user-autonomy spectrum sharing. | A dynamic tip selection and swarm intelligence method. | Focused on the unlicensed bands. | |
| Manogaran Manogaran et al. [50] | 2020 | MTC | Secure reliable service delegation in 6G. | Incorporates blockchain with security measure that provide access control, security, and privacy-preserving for the resources and the users. | Q-learning. | The proposed scheme focused on the virtual resource sharing. | |
| Data sharing | Khowaja et al. [51] | 2022 | VSN | Efficient and secure data sharing. | The scheme proposed Hyperledger Fabric for data-sharing security. | Stacked autoencoders and density-based clustering method. | The presented scheme is not able to handle broadcasting security issues. |
| Zhang et al. [52] | 2021 | FL | State-channel-based distributed data sharing for sandbox. | They proposed permissioned blockchain with FL for data sharing. | Fine-grained data access control model. | Does not take time complexity and computation overhead. | |
| Li et al. [53] | 2020 | VANET | Distributed data storage for vehicles and fine-grained access for VANET data. | They integrated blockchain with ciphertext-based attribute encryption. | HECP-ABE algorithm. | Does not consider data security in term of level of anonymity and stateless access. | |
| Resource management | Li et al. [58] | 2022 | MEC and IoT | Intelligent resource allocation. | They incorporate practical Byzantine fault tolerance protocol for the data privacy. | Collective reinforcement learning. | Does not consider the user’s privacy and task offloading scenario when the user is outside of the covered area. |
| Jain et al. [59] | 2021 | IoE | Optimal resource allocation. | Introduced blockchain for system’s monitoring, assuring safety, managing, and sharing resources effectively. | Metaheuristic with blockchain. | The proposed scheme does not talk about the computation overhead of the system. | |
| Yang et al. [60] | 2020 | MEC and IIoT | To optimize the IIoT device’s energy allocation. | They combined blockchain with MEC to solve the joint optimization problem. | Deep Q-learning. | They do not focus on the network access scenario when large-scale devices are connected. |
4. Case Study: Blockchain, 6G, and UAV-Based Collaborative Architecture for Public Safety Application
4.1. Data Layer
4.2. Intelligence Layer
4.2.1. Dataset Description
4.2.2. ML Classification Approach
4.3. Blockchain Layer
4.4. Application Layer
4.5. Communication Layer
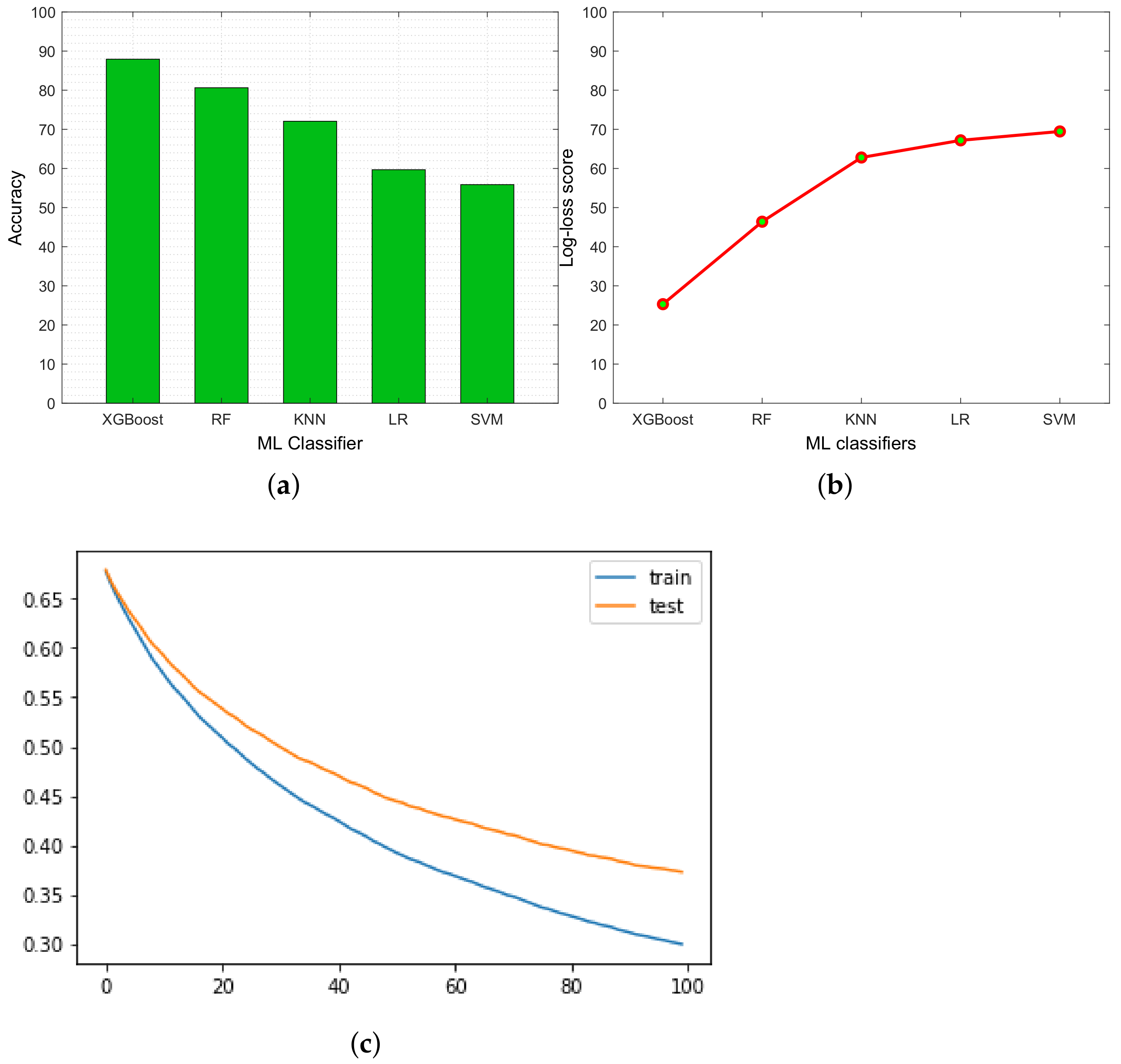
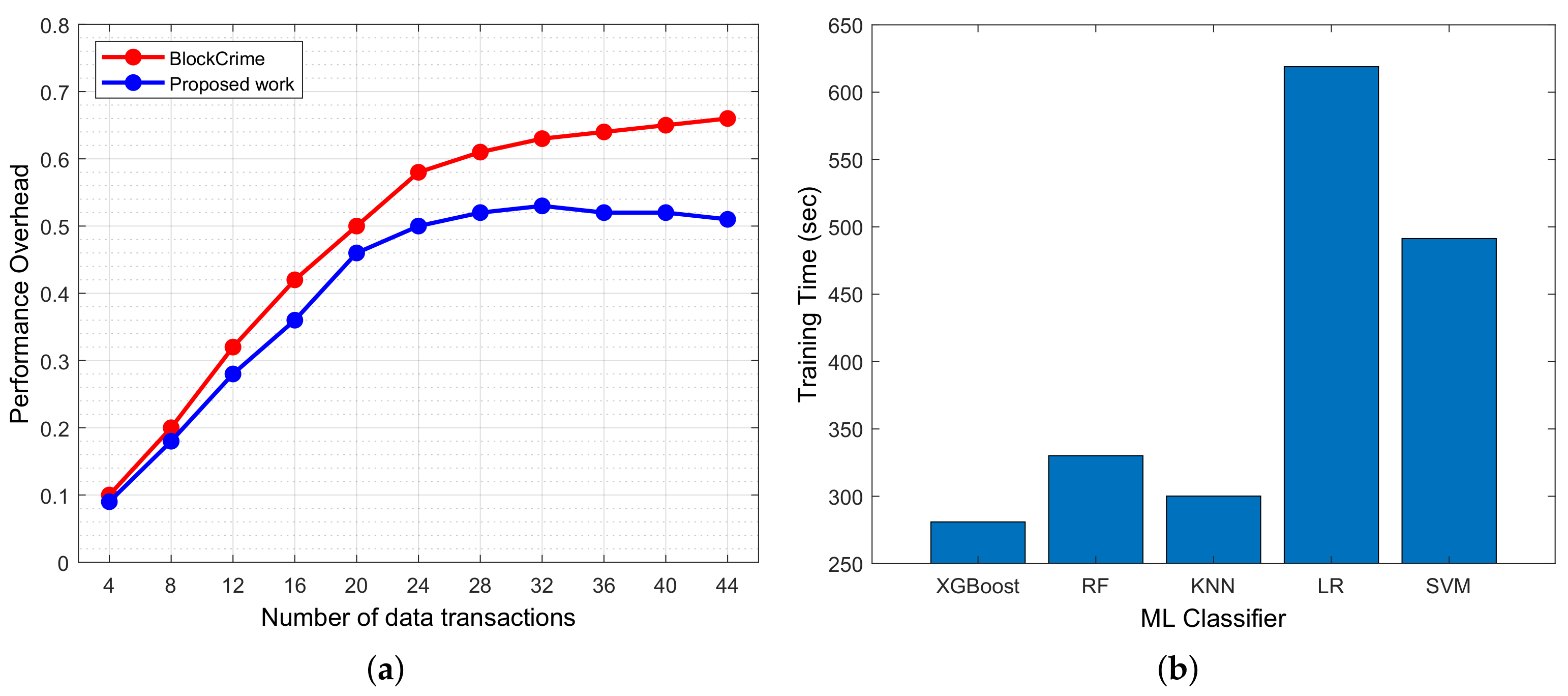
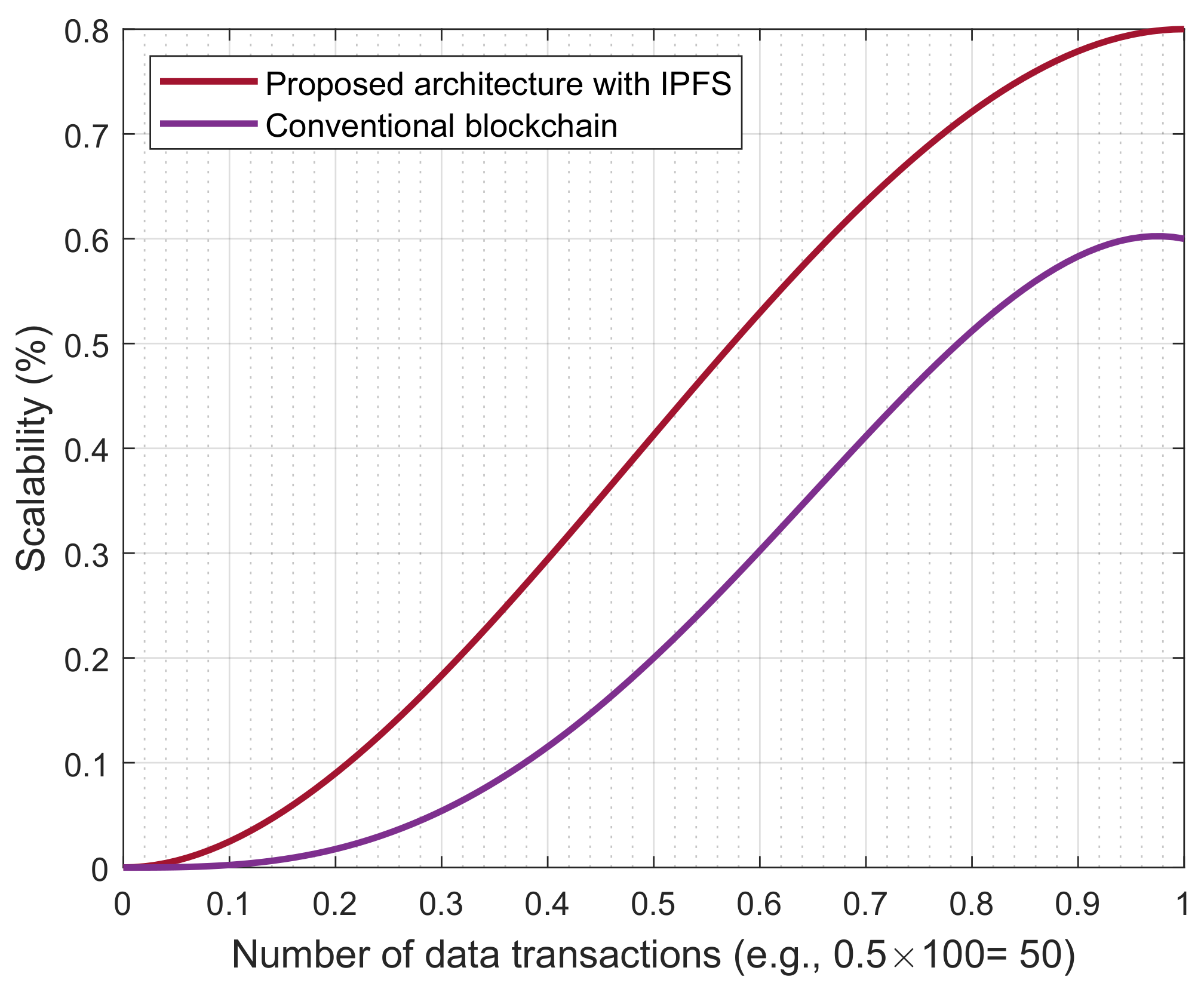
5. Result and Discussion
5.1. Experimental Setup
5.2. Performance Evaluation of the Proposed Architecture
6. Challenges of Adoption of Blockchain in 6G Network
6.1. Storage Capacity
6.2. Poor Efficiency of Consensus Mechanism
6.3. Cross-Network or Cross-Domain Sharing
6.4. Computation Overhead
6.5. Dynamically Changing Environment
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Raja, G.; Sai, S.G.; Rajakumar, B.R.; Gurumoorthy, S.; Dev, K.; Magarini, M. Nexus of 6G and Blockchain for Authentication of Aerial and IoT Devices. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Gupta, R.; Reebadiya, D.; Tanwar, S. 6G-enabled Edge Intelligence for Ultra—Reliable Low Latency Applications: Vision and Mission. Comput. Stand. Interfaces 2021, 77, 103521. [Google Scholar] [CrossRef]
- Sekaran, R.; Patan, R.; Raveendran, A.; Al-Turjman, F.; Ramachandran, M.; Mostarda, L. Survival Study on Blockchain Based 6G-Enabled Mobile Edge Computation for IoT Automation. IEEE Access 2020, 8, 143453–143463. [Google Scholar] [CrossRef]
- Singh, R.; Tanwar, S.; Sharma, T.P. Utilization of blockchain for mitigating the distributed denial of service attacks. Secur. Priv. 2020, 3, e96. [Google Scholar] [CrossRef]
- Velliangiri, S.; Manoharan, R.; Ramachandran, S.; Rajasekar, V. Blockchain Based Privacy Preserving Framework for Emerging 6G Wireless Communications. IEEE Trans. Ind. Informatics 2022, 18, 4868–4874. [Google Scholar] [CrossRef]
- Bindu, G.; Iwin Thanakumar, J.S.; Kanakala, V.R.; Niharika, G.L.K.; Raj, B.E. Impact of Blockchain Technology in 6G Network: A Comprehensive survey. In Proceedings of the 2022 International Conference on Inventive Computation Technologies (ICICT), Lalitpur, Nepal, 20–22 July 2022; pp. 328–334. [Google Scholar] [CrossRef]
- Senkyire, I.B.; Kester, Q.A. Validation of Forensic Crime Scene Images Using Watermarking and Cryptographic Blockchain. In Proceedings of the 2019 International Conference on Computer, Data Science and Applications (ICDSA), Accra, Ghana, 17–19 July 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Gupta, R.; Shukla, A.; Tanwar, S. BATS: A Blockchain and AI-Empowered Drone-Assisted Telesurgery System Towards 6G. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2958–2967. [Google Scholar] [CrossRef]
- Patel, K.; Mehta, D.; Mistry, C.; Gupta, R.; Tanwar, S.; Kumar, N.; Alazab, M. Facial Sentiment Analysis Using AI Techniques: State-of-the-Art, Taxonomies, and Challenges. IEEE Access 2020, 8, 90495–90519. [Google Scholar] [CrossRef]
- Gupta, R.; Shukla, A.; Tanwar, S. AaYusH: A Smart Contract-Based Telesurgery System for Healthcare 4.0. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Pradhan, N.R.; Rout, S.S.; Singh, A.P. Blockchain Based Smart Healthcare System for Chronic—Illness Patient Monitoring. In Proceedings of the 2020 3rd International Conference on Energy, Power and Environment: Towards Clean Energy Technologies, Meghalaya, India, 5–7 March 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, S.; Wang, J.; Wang, X.; Qiu, T.; Yuan, Y.; Ouyang, L.; Guo, Y.; Wang, F.Y. Blockchain-Powered Parallel Healthcare Systems Based on the ACP Approach. IEEE Trans. Comput. Soc. Syst. 2018, 5, 942–950. [Google Scholar] [CrossRef]
- Leng, J.; Ye, S.; Zhou, M.; Zhao, J.L.; Liu, Q.; Guo, W.; Cao, W.; Fu, L. Blockchain-Secured Smart Manufacturing in Industry 4.0: A Survey. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 237–252. [Google Scholar] [CrossRef]
- Leng, J.; Yan, D.; Liu, Q.; Xu, K.; Zhao, J.L.; Shi, R.; Wei, L.; Zhang, D.; Chen, X. ManuChain: Combining Permissioned Blockchain With a Holistic Optimization Model as Bi-Level Intelligence for Smart Manufacturing. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 182–192. [Google Scholar] [CrossRef]
- Lee, C.K.M.; Huo, Y.Z.; Zhang, S.Z.; Ng, K.K.H. Design of a Smart Manufacturing System With the Application of Multi-Access Edge Computing and Blockchain Technology. IEEE Access 2020, 8, 28659–28667. [Google Scholar] [CrossRef]
- Teng, Y.; Li, L.; Song, L.; Yu, F.R.; Leung, V.C.M. Profit Maximizing Smart Manufacturing Over AI-Enabled Configurable Blockchains. IEEE Internet Things J. 2022, 9, 346–358. [Google Scholar] [CrossRef]
- Khalil, U.; Mueen-Uddin; Malik, O.A.; Hussain, S. A Blockchain Footprint for Authentication of IoT-Enabled Smart Devices in Smart Cities: State-of-the-Art Advancements, Challenges and Future Research Directions. IEEE Access 2022, 10, 76805–76823. [Google Scholar] [CrossRef]
- Bai, Y.; Hu, Q.; Seo, S.H.; Kang, K.; Lee, J.J. Public Participation Consortium Blockchain for Smart City Governance. IEEE Internet Things J. 2022, 9, 2094–2108. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Srivastava, G.; Gupta, G.P.; Tripathi, R.; Gadekallu, T.R.; Xiong, N.N. PPSF: A Privacy-Preserving and Secure Framework Using Blockchain-Based Machine-Learning for IoT-Driven Smart Cities. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2326–2341. [Google Scholar] [CrossRef]
- Rahman, M.A.; Rashid, M.M.; Hossain, M.S.; Hassanain, E.; Alhamid, M.F.; Guizani, M. Blockchain and IoT-Based Cognitive Edge Framework for Sharing Economy Services in a Smart City. IEEE Access 2019, 7, 18611–18621. [Google Scholar] [CrossRef]
- Chattaraj, D.; Bera, B.; Das, A.K.; Saha, S.; Lorenz, P.; Park, Y. Block-CLAP: Blockchain-Assisted Certificateless Key Agreement Protocol for Internet of Vehicles in Smart Transportation. IEEE Trans. Veh. Technol. 2021, 70, 8092–8107. [Google Scholar] [CrossRef]
- Xia, S.; Lin, F.; Chen, Z.; Tang, C.; Ma, Y.; Yu, X. A Bayesian Game Based Vehicle-to-Vehicle Electricity Trading Scheme for Blockchain-Enabled Internet of Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 6856–6868. [Google Scholar] [CrossRef]
- Ghourab, E.M.; Azab, M.; Ezzeldin, N. Blockchain-Guided Dynamic Best-Relay Selection for Trustworthy Vehicular Communication. IEEE Trans. Intell. Transp. Syst. 2022, 23, 13678–13693. [Google Scholar] [CrossRef]
- Liang, X.; An, N.; Li, D.; Zhang, Q.; Wang, R. A Blockchain and ABAC Based Data Access Control Scheme in Smart Grid. In Proceedings of the 2022 International Conference on Blockchain Technology and Information Security (ICBCTIS), Huaihua, China, 15–17 July 2022; pp. 52–55. [Google Scholar] [CrossRef]
- Samy, S.; Azab, M.; Rizk, M. Towards a Secured Blockchain-based Smart Grid. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Vegas, NV, USA, 27–30 January 2021; pp. 1066–1069. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Chen, J.; Sun, X.; Ye, Z.; Zhou, Z. SPDS: A Secure and Auditable Private Data Sharing Scheme for Smart Grid Based on Blockchain. IEEE Trans. Ind. Informatics 2021, 17, 7688–7699. [Google Scholar] [CrossRef]
- Hao, X.; Ren, W.; Choo, K.K.R.; Xiong, N.N. A Self-Trading and Authenticated Roaming Scheme Based on Blockchain for Smart Grids. IEEE Trans. Ind. Informatics 2022, 18, 4097–4106. [Google Scholar] [CrossRef]
- Zhang, F.; Zhang, Y.; Lu, W.; Gao, Y.; Gong, Y.; Cao, J. 6G-Enabled Smart Agriculture: A Review and Prospect. Electronics 2022, 11, 2845. [Google Scholar] [CrossRef]
- Tran, Q.N.; Turnbull, B.P.; Wu, H.T.; de Silva, A.J.S.; Kormusheva, K.; Hu, J. A Survey on Privacy-Preserving Blockchain Systems (PPBS) and a Novel PPBS-Based Framework for Smart Agriculture. IEEE Open J. Comput. Soc. 2021, 2, 72–84. [Google Scholar] [CrossRef]
- Vangala, A.; Sutrala, A.K.; Das, A.K.; Jo, M. Smart Contract-Based Blockchain-Envisioned Authentication Scheme for Smart Farming. IEEE Internet Things J. 2021, 8, 10792–10806. [Google Scholar] [CrossRef]
- Yang, X.; Li, M.; Yu, H.; Wang, M.; Xu, D.; Sun, C. A Trusted Blockchain-Based Traceability System for Fruit and Vegetable Agricultural Products. IEEE Access 2021, 9, 36282–36293. [Google Scholar] [CrossRef]
- Ihinosen, A.B.; Mhlanga, S.T.; Lall, M. Enhancing safety and security in a dynamic rideshare service. In Proceedings of the 2020 5th International Conference on Computing, Communication and Security (ICCCS), Patna, India, 14–16 October 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Xu, R.; Nikouei, S.Y.; Chen, Y.; Blasch, E.; Aved, A. BlendMAS: A Blockchain-Enabled Decentralized Microservices Architecture for Smart Public Safety. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 564–571. [Google Scholar] [CrossRef]
- Fitwi, A.; Chen, Y.; Zhu, S. A Lightweight Blockchain-Based Privacy Protection for Smart Surveillance at the Edge. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 552–555. [Google Scholar] [CrossRef]
- Makhdoom, I.; Hayawi, K.; Kaosar, M.; Mathew, S.S.; Masud, M.M. Blockchain-based Secure CIDS Operation. In Proceedings of the 2021 5th Cyber Security in Networking Conference (CSNet), Abu Dhabi, United Arab Emirates, 12–14 October 2021; pp. 103–106. [Google Scholar] [CrossRef]
- Wu, H.; Zhong, B.; Li, H.; Chi, H.L.; Wang, Y. On-site safety inspection of tower cranes: A blockchain-enabled conceptual framework. Saf. Sci. 2022, 153, 105815. [Google Scholar] [CrossRef]
- Yu, K.; Tan, L.; Yang, C.; Choo, K.K.R.; Bashir, A.K.; Rodrigues, J.J.P.C.; Sato, T. A Blockchain-Based Shamir’s Threshold Cryptography Scheme for Data Protection in Industrial Internet of Things Settings. IEEE Internet Things J. 2022, 9, 8154–8167. [Google Scholar] [CrossRef]
- Na, D.; Park, S. Blockchain-Based Dashcam Video Management Method for Data Sharing and Integrity in V2V Network. IEEE Access 2022, 10, 3307–3319. [Google Scholar] [CrossRef]
- Abdulqadder, I.H.; Zhou, S. SliceBlock: Context-Aware Authentication Handover and Secure Network Slicing Using DAG-Blockchain in Edge-Assisted SDN/NFV-6G Environment. IEEE Internet Things J. 2022, 9, 18079–18097. [Google Scholar] [CrossRef]
- He, G.; Su, W.; Gao, S.; Liu, N.; Das, S.K. NetChain: A Blockchain-Enabled Privacy-Preserving Multi-Domain Network Slice Orchestration Architecture. IEEE Trans. Netw. Serv. Manag. 2022, 19, 188–202. [Google Scholar] [CrossRef]
- Chen, F.; Li, Z.; Li, B.; Deng, C.; Tian, Z.; Lin, N.; Wan, Y.; Bao, B. Blockchain-based Optical Network Slice Rental Approach for IoT. In Proceedings of the 2020 IEEE Computing, Communications and IoT Applications (ComComAp), Beijing, China, 20–22 December 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Vora, J.; Kaneriya, S.; Tanwar, S.; Tyagi, S.; Kumar, N.; Obaidat, M. TILAA: Tactile Internet-based Ambient Assistant Living in fog environment. Future Gener. Comput. Syst. 2019, 98, 635–649. [Google Scholar] [CrossRef]
- Liu, X.; Lam, K.Y.; Li, F.; Zhao, J.; Wang, L.; Durrani, T.S. Spectrum Sharing for 6G Integrated Satellite-Terrestrial Communication Networks Based on NOMA and CR. IEEE Netw. 2021, 35, 28–34. [Google Scholar] [CrossRef]
- Tyagi, S.; Tanwar, S.; Gupta, S.K.; Kumar, N.; Rodrigues, J.J. A lifetime extended multi-levels heterogeneous routing protocol for wireless sensor networks. Telecommun. Syst. 2015, 59, 43–62. [Google Scholar] [CrossRef]
- Saha, R.K. Approaches to Improve Millimeter-Wave Spectrum Utilization Using Indoor Small Cells in Multi-Operator Environments Toward 6G. IEEE Access 2020, 8, 207643–207658. [Google Scholar] [CrossRef]
- Lu, W.; Si, P.; Huang, G.; Han, H.; Qian, L.; Zhao, N.; Gong, Y. SWIPT Cooperative Spectrum Sharing for 6G-Enabled Cognitive IoT Network. IEEE Internet Things J. 2021, 8, 15070–15080. [Google Scholar] [CrossRef]
- Gupta, R.; Kumari, A.; Tanwar, S. Fusion of blockchain and artificial intelligence for secure drone networking underlying 5G communications. Trans. Emerg. Telecommun. Technol. 2021, 32, e4176. [Google Scholar] [CrossRef]
- Liu, L.; Liang, W.; Mang, G.; Dong, Z. Blockchain Based Spectrum Sharing over 6G Hybrid Cloud. In Proceedings of the 2021 International Wireless Communications and Mobile Computing (IWCMC), Harbin, China, 28 June–2 July 2021; pp. 492–497. [Google Scholar] [CrossRef]
- Zhang, H.; Leng, S.; Wu, F.; Chai, H. A DAG Blockchain-Enhanced User-Autonomy Spectrum Sharing Framework for 6G-Enabled IoT. IEEE Internet Things J. 2022, 9, 8012–8023. [Google Scholar] [CrossRef]
- Manogaran, G.; Rawal, B.S.; Saravanan, V.; Kumar, P.M.; Martínez, O.S.; Crespo, R.G.; Montenegro-Marin, C.E.; Krishnamoorthy, S. Blockchain based integrated security measure for reliable service delegation in 6G communication environment. Comput. Commun. 2020, 161, 248–256. [Google Scholar] [CrossRef]
- Khowaja, S.A.; Khuwaja, P.; Dev, K.; Lee, I.H.; Khan, W.; Wang, W.; Qureshi, N.M.F.; Magarini, M. A secure data sharing scheme in Community Segmented Vehicular Social Networks for 6G. IEEE Trans. Ind. Inform. 2022, 19, 890–899. [Google Scholar] [CrossRef]
- Zhang, F.; Guo, S.; Qiu, X.; Xu, S.; Qi, F.; Wang, Z. Federated Learning Meets Blockchain: State Channel based Distributed Data Sharing Trust Supervision Mechanism. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Li, H.; Pei, L.; Liao, D.; Chen, S.; Zhang, M.; Xu, D. FADB: A Fine-Grained Access Control Scheme for VANET Data Based on Blockchain. IEEE Access 2020, 8, 85190–85203. [Google Scholar] [CrossRef]
- Cao, H.; Du, J.; Zhao, H.; Luo, D.X.; Kumar, N.; Yang, L.; Yu, F.R. Toward Tailored Resource Allocation of Slices in 6G Networks With Softwarization and Virtualization. IEEE Internet Things J. 2022, 9, 6623–6637. [Google Scholar] [CrossRef]
- Sadi, Y.; Erkucuk, S.; Panayirci, E. Flexible Physical Layer based Resource Allocation for Machine Type Communications Towards 6G. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Dai, H.; Zhang, C.; Luo, J.; Li, C.; Wang, B. QoE- Driven Resource Allocation for Secure URLLC in 6G-Enabled IoT Networks. In Proceedings of the 2021 13th International Conference on Wireless Communications and Signal Processing (WCSP), Changsha, China, 20–22 October 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Lin, K.; Li, Y.; Zhang, Q.; Fortino, G. AI-Driven Collaborative Resource Allocation for Task Execution in 6G-Enabled Massive IoT. IEEE Internet Things J. 2021, 8, 5264–5273. [Google Scholar] [CrossRef]
- Li, M.; Pei, P.; Yu, F.R.; Si, P.; Li, Y.; Sun, E.; Zhang, Y. Cloud-Edge Collaborative Resource Allocation for Blockchain-Enabled Internet of Things: A Collective Reinforcement Learning Approach. IEEE Internet Things J. 2022, 9, 23115–23129. [Google Scholar] [CrossRef]
- Jain, D.K.; Tyagi, S.K.S.; Neelakandan, S.; Prakash, M.; Natrayan, L. Metaheuristic Optimization-Based Resource Allocation Technique for Cybertwin-Driven 6G on IoE Environment. IEEE Trans. Ind. Inform. 2022, 18, 4884–4892. [Google Scholar] [CrossRef]
- Yang, L.; Li, M.; Si, P.; Yang, R.; Sun, E.; Zhang, Y. Energy-Efficient Resource Allocation for Blockchain-Enabled Industrial Internet of Things With Deep Reinforcement Learning. IEEE Internet Things J. 2021, 8, 2318–2329. [Google Scholar] [CrossRef]
- Crimes in Chicago. Available online: https://www.kaggle.com/datasets/currie32/crimes-in-chicago (accessed on 15 November 2022).
- ConsenSys. Fundamentals of THz Technology for 6G. Available online: https://www.rohde-schwarz.com/in/solutions/test-and-measurement/wireless-communication/cellular-standards/6g/white-paper-fundamentals-of-thz-technology-for-6g-by-rohde-schwarz-registration-255934.html (accessed on 17 November 2022).
- Patel, D.; Sanghvi, H.; Jadav, N.K.; Gupta, R.; Tanwar, S.; Florea, B.C.; Taralunga, D.D.; Altameem, A.; Altameem, T.; Sharma, R. BlockCrime: Blockchain and Deep Learning-Based Collaborative Intelligence Framework to Detect Malicious Activities for Public Safety. Mathematics 2022, 10, 3195. [Google Scholar] [CrossRef]
- Arigela, S.S.D.; Voola, P. Detecting and Identifying Storage issues using Blockchain Technology. In Proceedings of the 2022 International Conference on Advances in Computing, Communication and Applied Informatics (ACCAI), Chennai, India, 28–29 January 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Pawar, M.K.; Patil, P.; Sharma, M.; Chalageri, M. Secure and Scalable Decentralized Supply Chain Management Using Ethereum and IPFS Platform. In Proceedings of the 2021 International Conference on Intelligent Technologies (CONIT), Hubli, India, 25–27 June 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Gadekallu, T.R.; Srivastava, G. SP2F: A secured privacy-preserving framework for smart agricultural Unmanned Aerial Vehicles. Comput. Netw. 2021, 187, 107819. [Google Scholar] [CrossRef]
- Wan, Y.; Tang, J.; Lao, S. Distributed Conflict-Detection and Resolution Algorithm for UAV Swarms Based on Consensus Algorithm and Strategy Coordination. IEEE Access 2019, 7, 100552–100566. [Google Scholar] [CrossRef]
- Zhang, J.; Yan, J.; Zhang, P.; Kong, X. Collision Avoidance in Fixed-Wing UAV Formation Flight Based on a Consensus Control Algorithm. IEEE Access 2018, 6, 43672–43682. [Google Scholar] [CrossRef]
- Hao, Y.; Cao, H.; Wang, Y.; Xiong, L.; Liu, X.; Yang, L.; Ni, J. Blockchain-Enabled Secure and Transparent Cross-Regional Model Updating and Sharing Approach in Smart Grid. In Proceedings of the 2021 IEEE 10th Data Driven Control and Learning Systems Conference (DDCLS), Suzhou, China, 14–16 May 2021; pp. 959–963. [Google Scholar] [CrossRef]
- Xue, L.; Huang, H.; Xiao, F.; Wang, W. A Cross-domain Authentication Scheme Based on Cooperative Blockchains Functioning with Revocation for Medical Consortiums. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2409–2420. [Google Scholar] [CrossRef]
- Chai, H.; Leng, S.; He, J.; Zhang, K.; Cheng, B. CyberChain: Cybertwin Empowered Blockchain for Lightweight and Privacy-Preserving Authentication in Internet of Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 4620–4631. [Google Scholar] [CrossRef]
- Mao, B.; Tang, F.; Kawamoto, Y.; Kato, N. Optimizing Computation Offloading in Satellite-UAV-Served 6G IoT: A Deep Learning Approach. IEEE Netw. 2021, 35, 102–108. [Google Scholar] [CrossRef]
- Ahmed, M.; Moustafa, N.; Akhter, A.F.M.S.; Razzak, I.; Surid, E.; Anwar, A.; Shah, A.F.M.S.; Zengin, A. A Blockchain-Based Emergency Message Transmission Protocol for Cooperative VANET. IEEE Trans. Intell. Transp. Syst. 2022, 23, 19624–19633. [Google Scholar] [CrossRef]
- Muhs, J. How Does Blockchain Technology Help Deliver the Future…Now_? Available online: https://economictimes.indiatimes.com/small-biz/security-tech/technology/how-does-blockchain-technology-help-deliver-the-futurenow/articleshow/86313876 (accessed on 23 September 2022).
- Xiao, W.; Liu, C.; Wang, H.; Zhou, M.; Hossain, M.S.; Alrashoud, M.; Muhammad, G. Blockchain for Secure-GaS: Blockchain-Powered Secure Natural Gas IoT System with AI-Enabled Gas Prediction and Transaction in Smart City. IEEE Internet Things J. 2021, 8, 6305–6312. [Google Scholar] [CrossRef]




| Author | Year | Objective | 6G | Security | Approach | Pros | Cons |
|---|---|---|---|---|---|---|---|
| Xu et al. [33] | 2019 | Smart public safety system. | ✗ | Blockchain. | BlendMAS. | The scheme offers secure and smart data sharing with access control. | Does not yet explore 6G networks. |
| Ihinosen et al. [32] | 2020 | Safety and security in rideshare service. | ✗ | Using facial recognition API. | GPS tracking and 2-way rating system. | Developed mobile ridesharing scheme enhance the security | Did not consider latency and delay. |
| Fitwi et al. [34] | 2020 | Video surveillance systems security. | ✗ | Blockchain. | Lib-Pri scheme. | The scheme offers real-time video analytics by identifying fugitives using facial features. | Did not consider data confidentiality and scalability. |
| Makhdoom et al. [35] | 2021 | To prevent cyberattack incidents. | ✗ | Blockchain. | Blockchain-enabled collaborative intrusion detection systems. | The scheme enabled node and application authorization. | Does not discuss the scalability of the system. |
| Wu et al. [36] | 2022 | On-site safety for tower cranes. | ✗ | Blockchain. | Smart contract, consensus, and Hyperledger-Fabric-based framework. | The scheme enhanced the safety performance. | Did not consider latency, throughput, and computation overhead analysis. |
| Yu et al. [37] | 2022 | Security and privacy of IIoT data. | ✗ | Blockchain and cryptography. | STCChain. | The scheme prevented data stealing and attacks. | Does not incorporate 6G-based solution. |
| Na et al. [38] | 2022 | Crime and accident prevention for autonomous vehicles. | ✗ | Blockchain. | Multisignature-enabled access control using GPS data. | The scheme offers privacy and security of the image and video data with lower latency. | The scheme limits verifying the reliability of GPS data. |
| Proposed scheme | 2022 | Public safety to monitor criminal activity. | ✓ | Blockchain. | Layered architecture incorporating blockchain and 6G to detect crime. | The scheme uses different ML classifier to identify the attack and nonattack from the criminal activity dataset. | - |
| Hyperparameters Used by ML Classifiers | |
|---|---|
| ML Classifiers | Parameters Used |
| XGBoost | n_estimators: 100, learning_rate: 0.1, max_depth: 1 |
| RF | n_estimators: 200, max_depth: 5 |
| KNN | n_neighbors: 5, weights: ‘uniform’ |
| LR | random_state:1, solver: ‘lbfgs’, max_iter: 100 |
| SVM | gamma: ‘auto’, probability: True, kernel: [‘rbf’,‘linear’] |
| Communication Layer Parameters | |
| Frequency range | 75–110 GHz |
| Sub-carrier spacing | 240 KHz |
| Channel coding | Polar coding |
| Channel fading | com.Rayleigh fading channel |
| Modulation | OFDMA |
| Blockchain Layer Parameters | |
| Compiler language | Solidity |
| Network | Rinkeby’s |
| Environment | Remix VM |
| Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) | |
|---|---|---|---|---|
| XGBoost | 87.93 | 85.45 | 80.32 | 83.23 |
| RF | 80.63 | 79.34 | 76.21 | 74.43 |
| KNN | 72.06 | 71.21 | 69.32 | 70.21 |
| LR | 59.68 | 55.43 | 51.22 | 52.10 |
| SVM | 55.87 | 52.32 | 50.32 | 51.21 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rathod, T.; Jadav, N.K.; Tanwar, S.; Sharma, R.; Tolba, A.; Raboaca, M.S.; Marina, V.; Said, W. Blockchain-Driven Intelligent Scheme for IoT-Based Public Safety System beyond 5G Networks. Sensors 2023, 23, 969. https://doi.org/10.3390/s23020969
Rathod T, Jadav NK, Tanwar S, Sharma R, Tolba A, Raboaca MS, Marina V, Said W. Blockchain-Driven Intelligent Scheme for IoT-Based Public Safety System beyond 5G Networks. Sensors. 2023; 23(2):969. https://doi.org/10.3390/s23020969
Chicago/Turabian StyleRathod, Tejal, Nilesh Kumar Jadav, Sudeep Tanwar, Ravi Sharma, Amr Tolba, Maria Simona Raboaca, Verdes Marina, and Wael Said. 2023. "Blockchain-Driven Intelligent Scheme for IoT-Based Public Safety System beyond 5G Networks" Sensors 23, no. 2: 969. https://doi.org/10.3390/s23020969
APA StyleRathod, T., Jadav, N. K., Tanwar, S., Sharma, R., Tolba, A., Raboaca, M. S., Marina, V., & Said, W. (2023). Blockchain-Driven Intelligent Scheme for IoT-Based Public Safety System beyond 5G Networks. Sensors, 23(2), 969. https://doi.org/10.3390/s23020969







