A Contention-Free Cooperative MAC Protocol for Eliminating Heterogenous Collisions in Vehicular Ad Hoc Networks
Abstract
1. Introduction
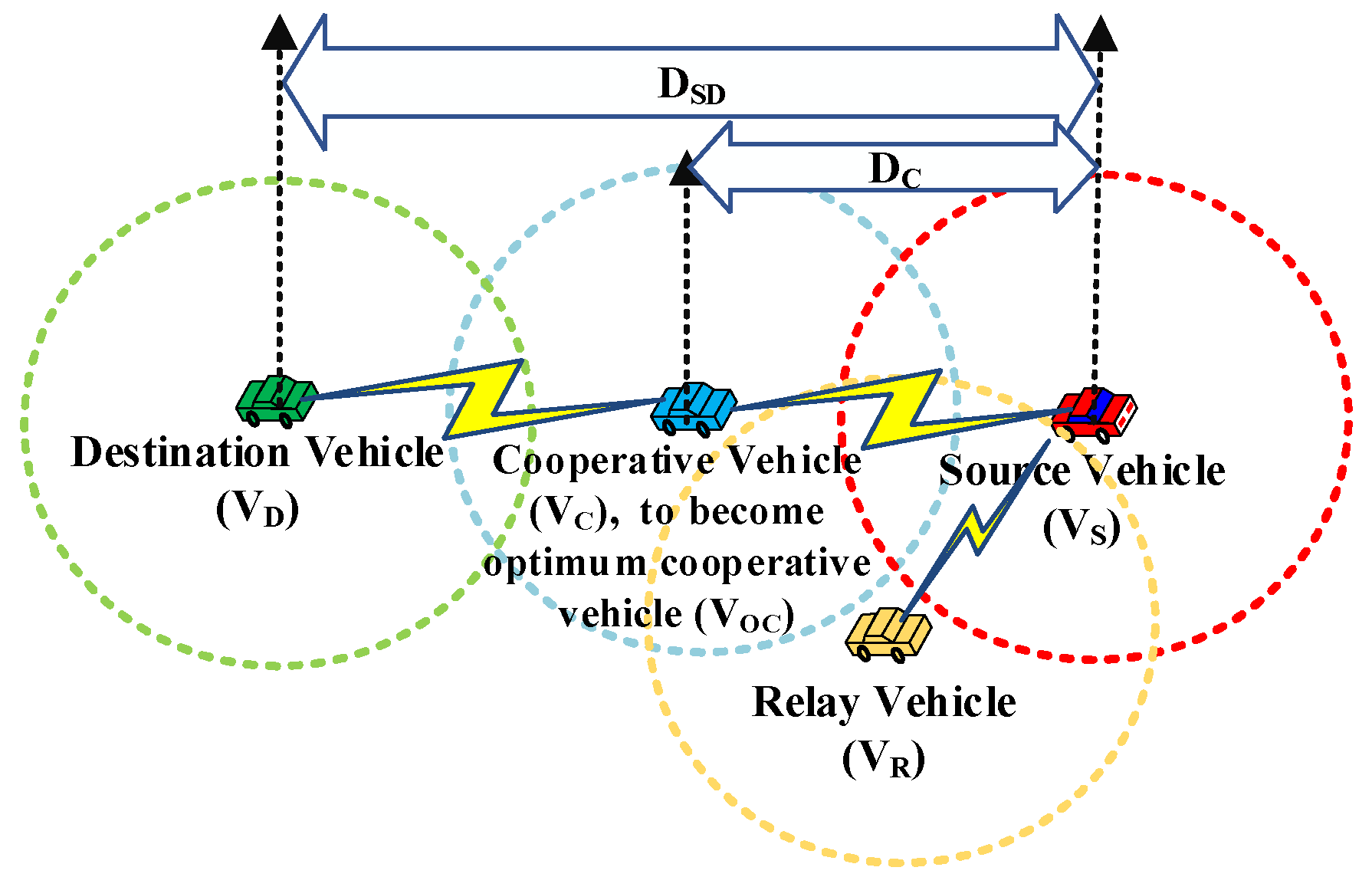
- We develop an optimized traffic model to forward data packets by effectively utilizing cooperative vehicles to improve the probability of successful packet transmission. A limited number of optimum cooperative vehicles are carefully selected by determining the closest position to the midpoint between the source vehicle and the destination vehicle.
- To reduce merging collisions to adapt to the frequent converging and diverging of rapid topology changes in the network due to high vehicle mobility, we propose a vectorized trajectory estimation (VTE) method by comparing the relative velocity of vehicles within a specific time interval by identifying the previous positions.
- Cooperation collisions occur when the cooperative vehicle and relay vehicle are contending to reserve the same time slot. Based on the distinct stochastic traffic scenarios of the proposed system model, we investigate two cases of heterogenous collisions: (1) typical heterogeneous collisions, such as cooperation collisions, access collisions, relay collisions, and reservation collisions; (2) aggregated heterogeneous collisions of the hidden terminals and exposed terminals at dissociated positions (occurring simultaneously but quite independently) and associated positions, respectively. In both cases, we propose the relevant collision-resolving mechanisms of time slot assignment procedures by methodically operating the four distinctive packets after identifying the access vehicles and comparing the received signal strengths.
- We validate the protocol performance by analyzing the collision probability, packet reception probability, and access delay of diversified heterogenous collisions in stochastic traffic scenarios. Extensive simulation experiments are conducted under various traffic conditions with different vehicular networking settings.
2. Related Work
3. System Model
3.1. Fundamental Assumptions
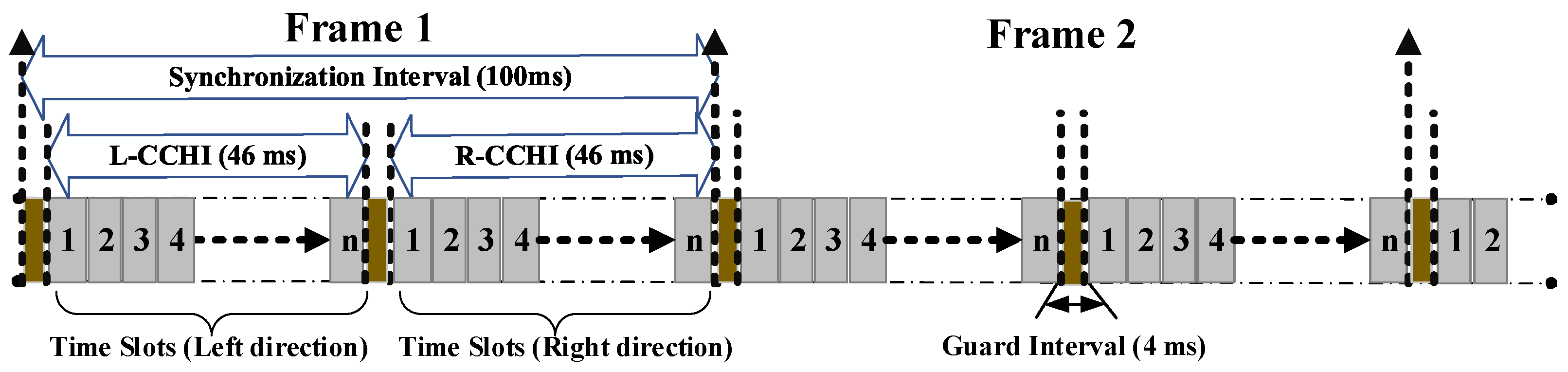
- Communication: To provide reliable communications, we consider that each vehicle is equipped with two transceivers: one transceiver for CCH to listen for the channel status and SM transmission, and the other transceiver for SCH to send NSMs of infotainment services. Our proposed model primarily outlines how to access CCH to broadcast SMs. As depicted in Figure 1, the channel time is divided into synchronization intervals (SIs) of the TDMA frames with a fixed length of 100 ms. Each TDMA frame is split into two sets of time slots: the left CCH interval (L-CCHI) and right CCH interval (R-CCHI); these correspond to the vehicles going in the left and right directions, respectively. A guard interval of 4 ms is appended at the end of each interval set for synchronization.
- Synchronization: Each vehicle is equipped with a global positioning system (GPS) receiver to provide a synchronous reference time. Because low-end GPS receivers can provide a one-pulse-per-second (PPS) signal with an accuracy of fewer than 100 ns and the GPS oscillator is stable, vehicles may preserve synchronization for a while even if the GPS signal is lost temporarily.
- Computation: For road safety, the minimum headway between all vehicles on the road must follow the 2s rule, which means that the distance for V2V connectivity must be equal to 2 times the vehicle velocity [47,48,49]. Vehicles are capable of performing fundamental operations, such as generating random numbers, hash functions (by using this, hashing algorithms can convert data with arbitrary length to a fixed length), and simple matrix algebra calculations.
3.2. System Model of Cooperative Relay
4. CFC-MAC Protocol
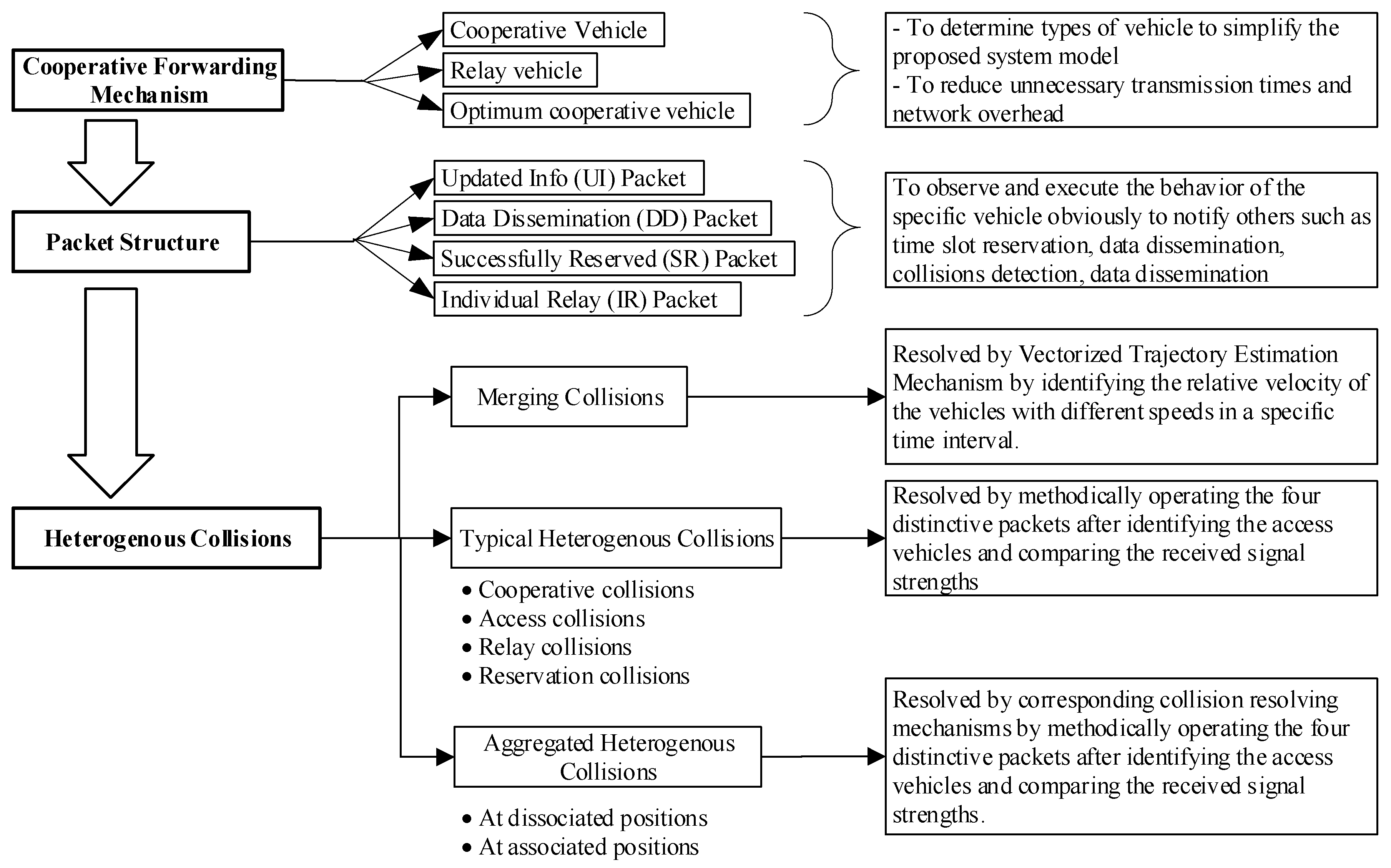
4.1. Cooperative Forwarding Mechanism
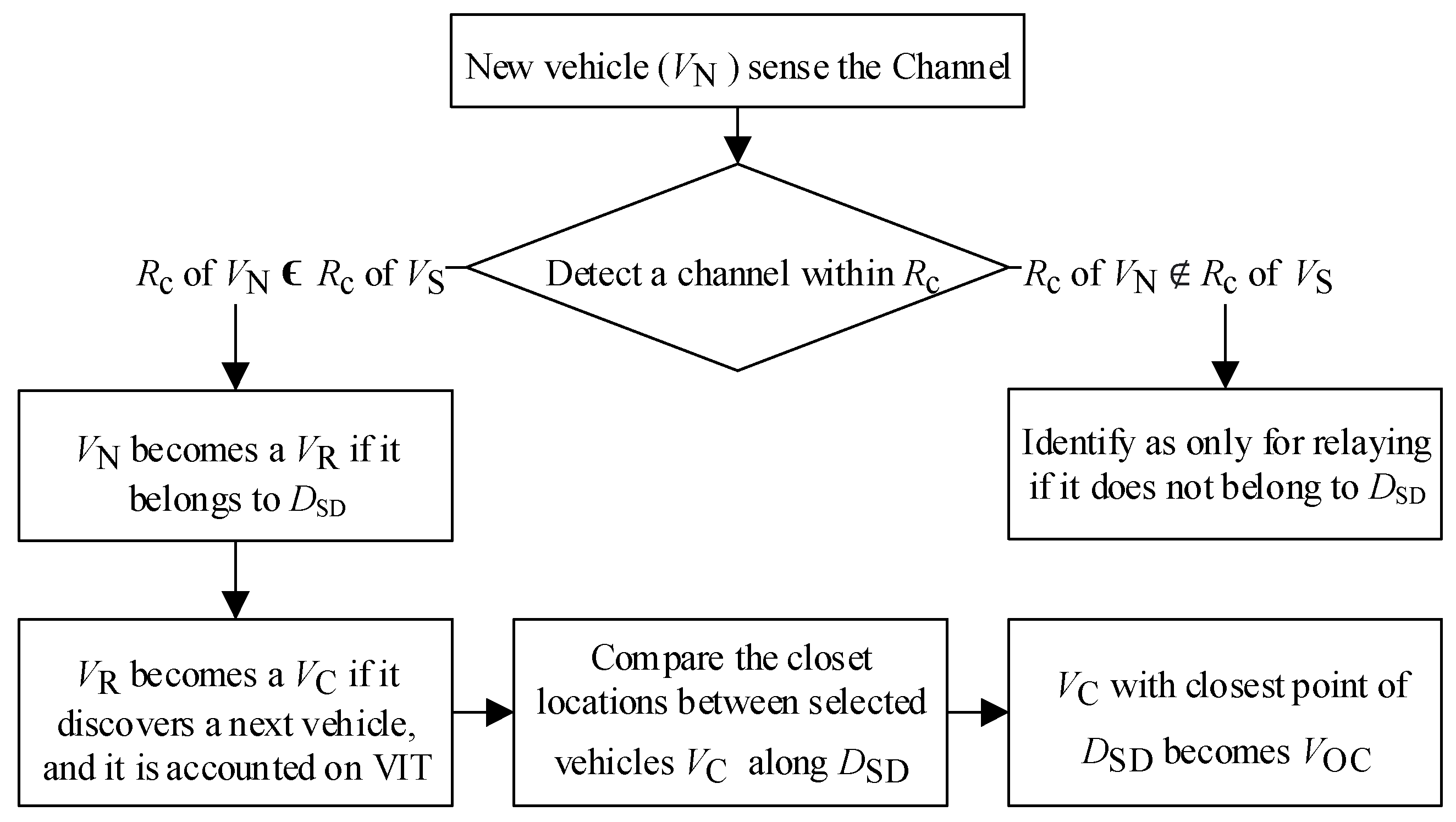
4.1.1. Optimum Cooperative Vehicle Determination
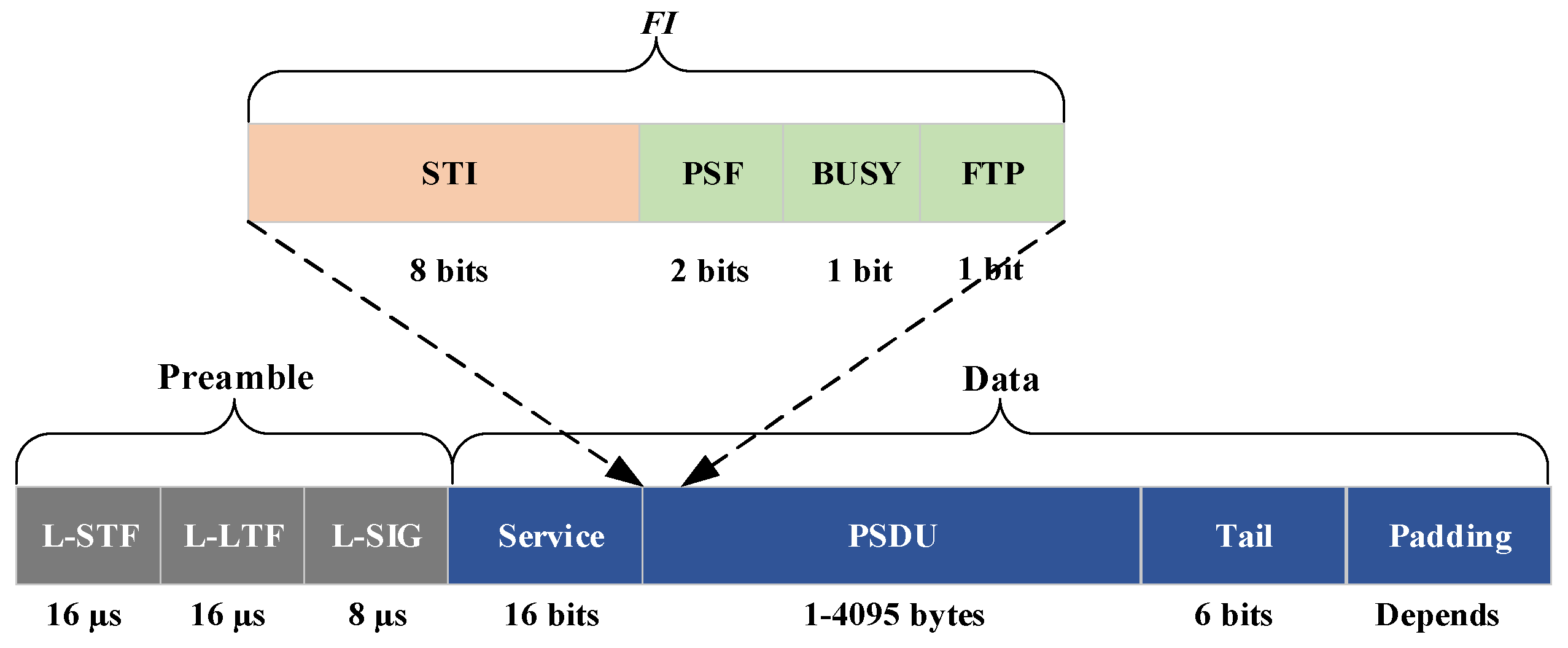
4.1.2. Packet Structure
- Legacy short training field (L-STF): executed for packet sensing, time acquisition, automatic gain control, and coarse frequency correction.
- Legacy long training field (L-LTF): executed for pilot-based channel estimation, fine frequency correction, and fine symbol-timing offset correction.
- Legacy SIGnal (L-SIG): contains metadata from the received configuration packets, such as the modulation coding scheme (MCS), and the physical layer convergence protocol (PLCP) service data unit (PSDU) length.
- Service: to set up the data scrambler.
- PLCP service data unit (PSDU): includes actual user information.
- Tail: executed for terminating convolutional code.
- Padding: executed for ensuring an integer number of symbols.
- Source temporary identifier (STI)—8 bits: the label of the vehicle “heard” by vehicle VN on time slot τj.
- Priority status field (PSF)—2 bits: the field indicates the priority of data transmitted in the time slot.
- BUSY—1 bit: a flag indicating whether time slot τj is free (0) or busy (1).
- File transfer protocol (FTP)—1 bit: executed in point-to-point transmission.
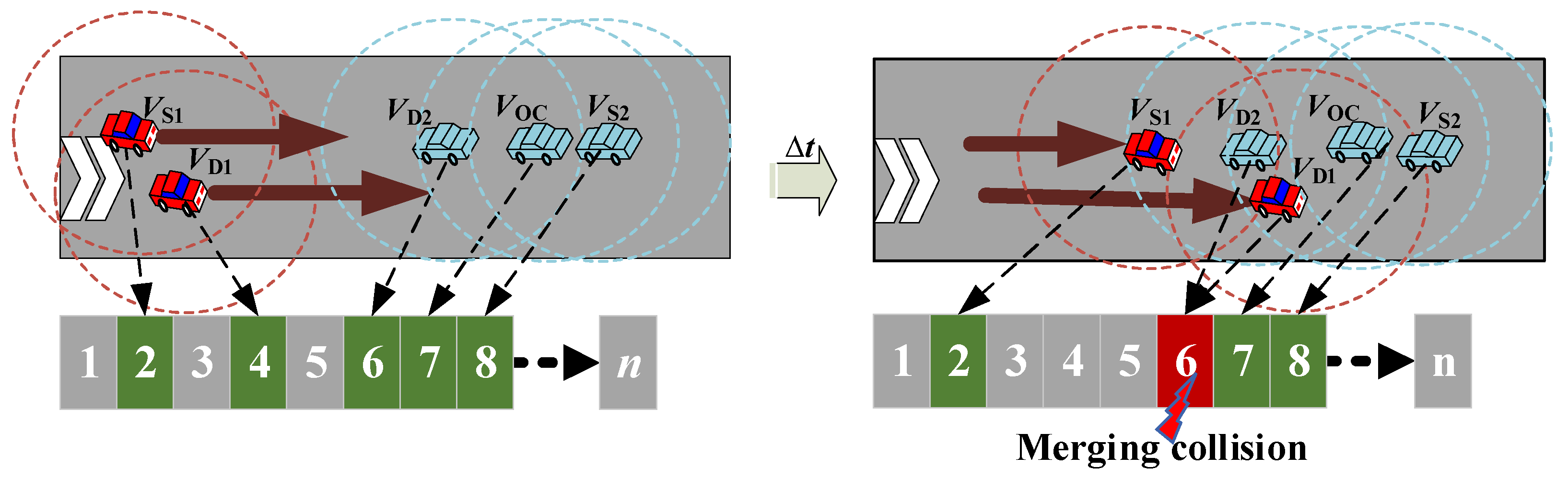
4.2. Vectorized Trajectory Estimation Mechanism
4.3. Heterogenous Collision Resolution
4.3.1. Typical Heterogenous Collision Resolution
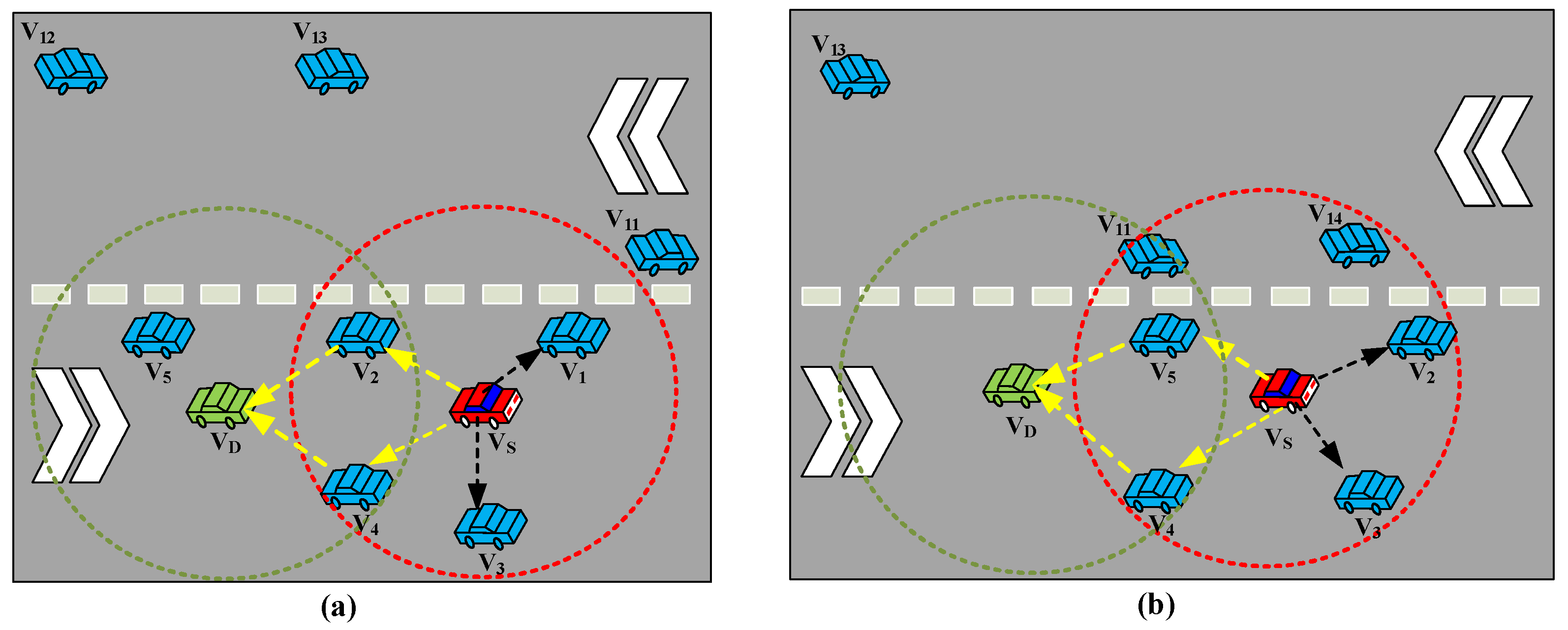
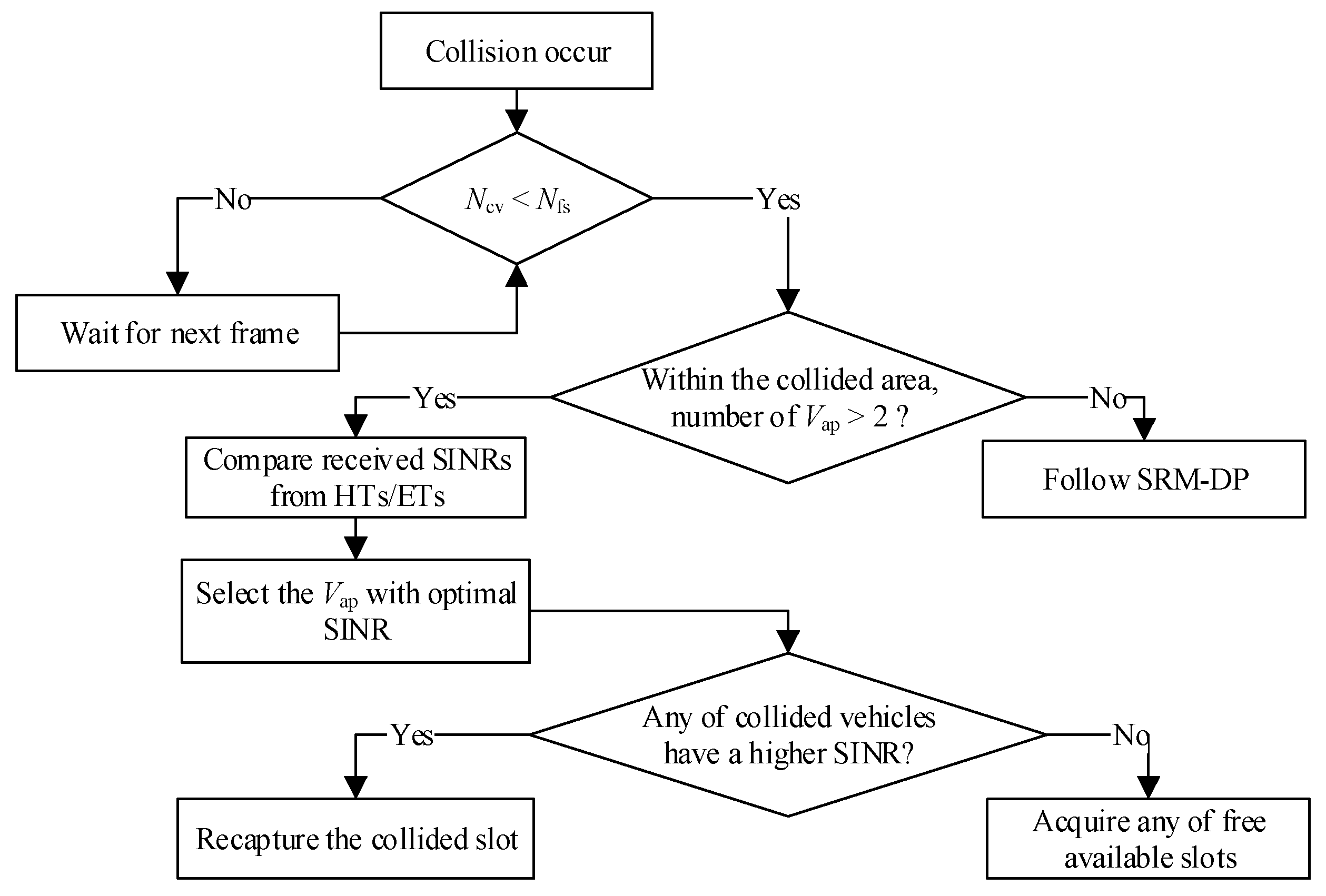
4.3.2. Aggregated Heterogenous Collision Resolutions
- 1.
- Aggregated Heterogenous Collisions of Hidden and Exposed Terminals at Dissociated Positions
- 2.
- Aggregated Heterogenous Collisions of Hidden and Exposed Terminals at Associated Positions
5. Performance Analysis
5.1. Collision Probability
5.2. Packet Reception Probability
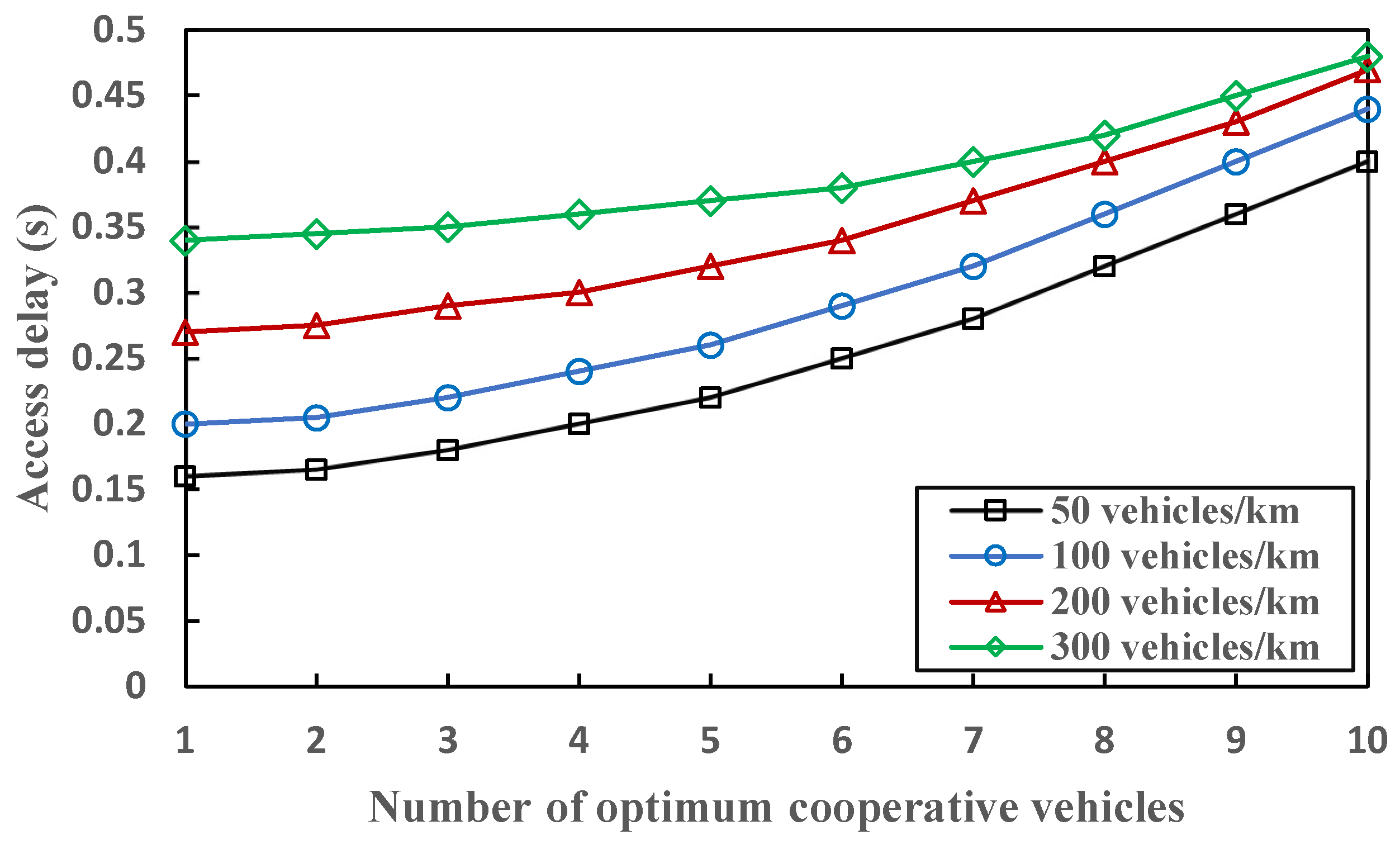
5.3. Access Delay
6. Performance Evaluation
6.1. Simulation Parameters
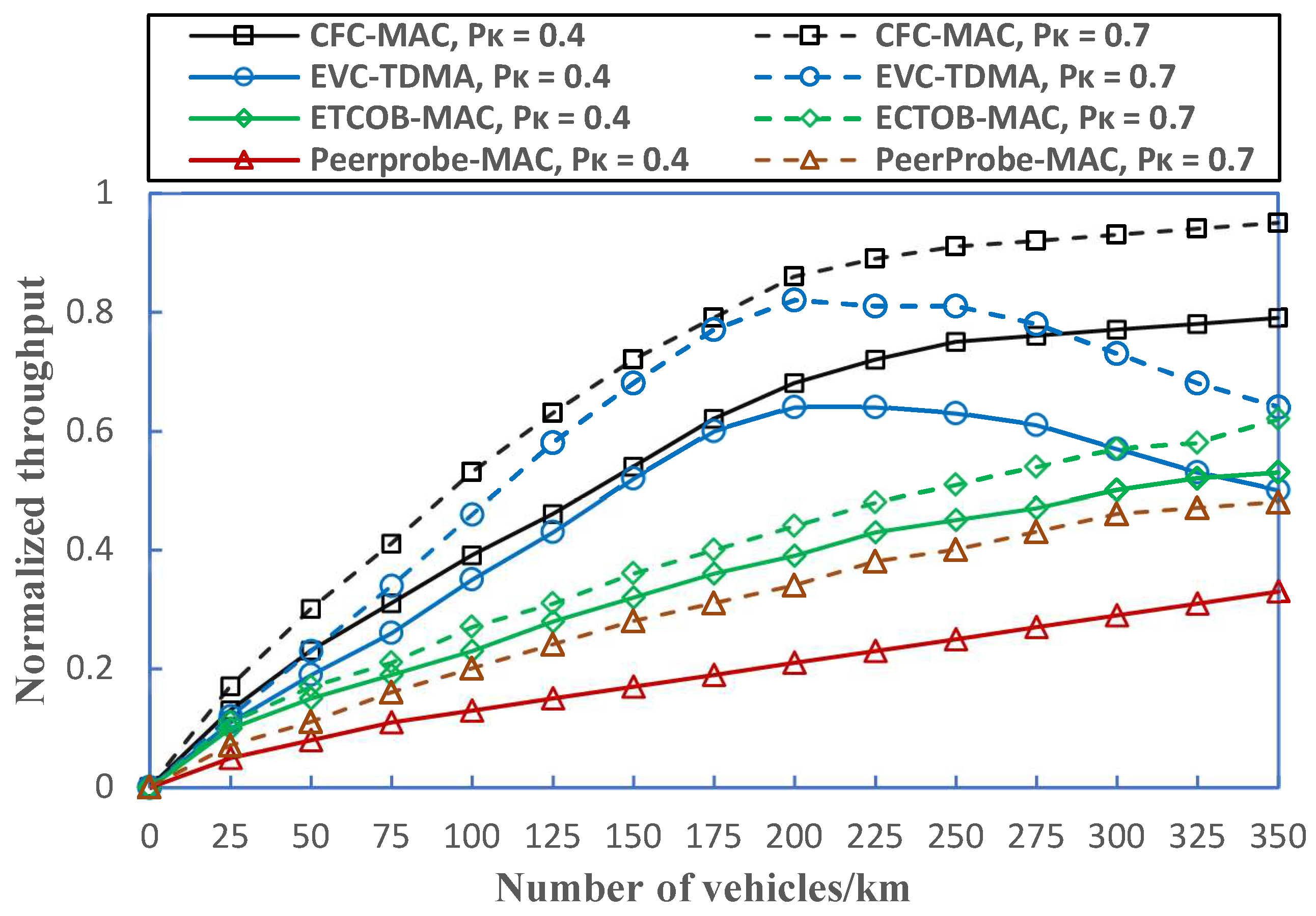
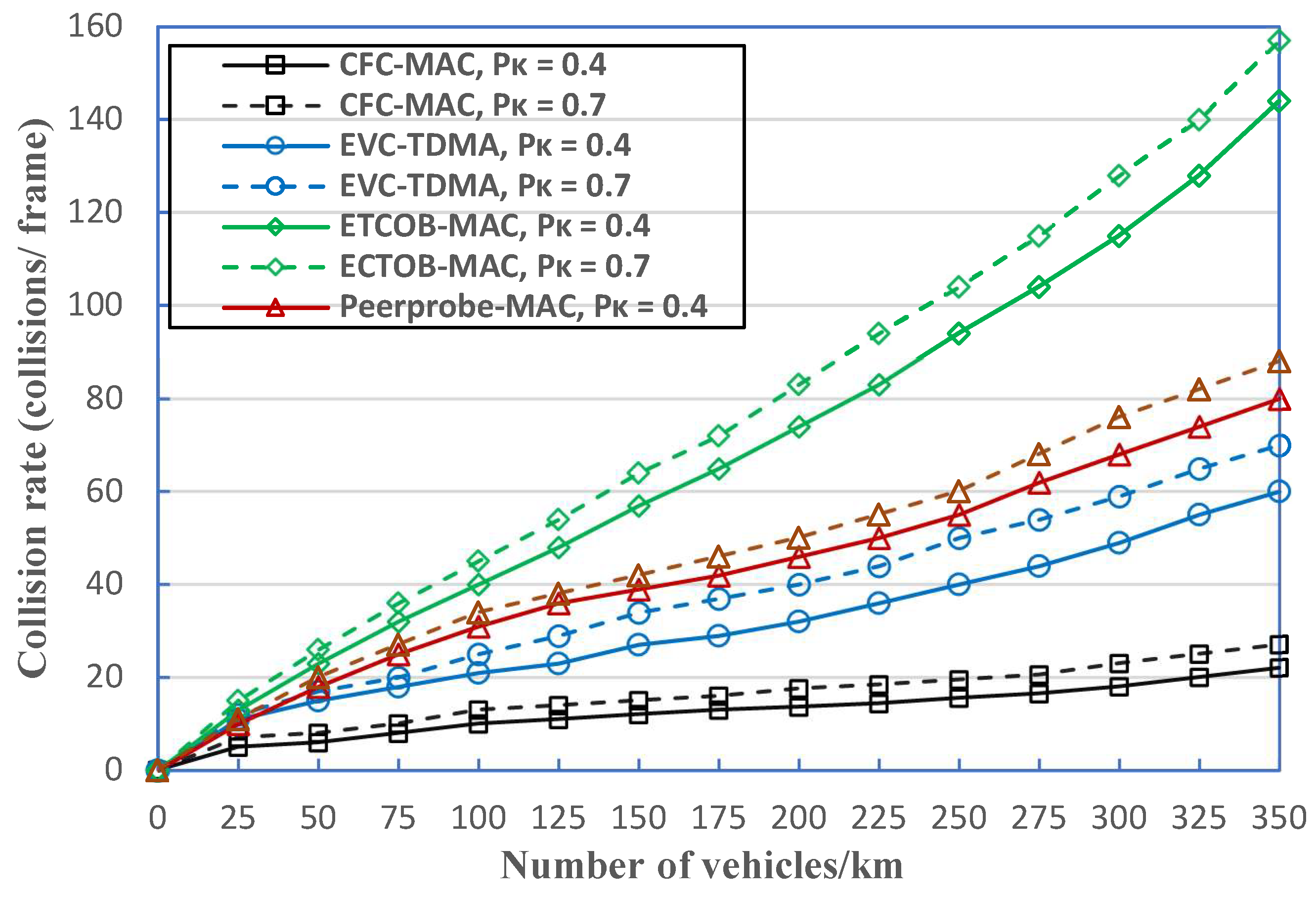
6.2. Performance Evaluation
- Access delay: The time duration required by a new vehicle to access a time slot successfully for data packet transmission. It depends on the number of total vehicles when a vehicle has acquired a time slot and utilizes it in all continuous frames without collision.
- Packet loss ratio: A packet loss denotes that a packet is not received because of a collision or channel fading. The packet loss ratio (PLR) can be defined as
- Throughput: The average number of successful data transmissions per unit of time as a fraction of the channel capacity. It is controlled by bandwidth, the received SINR, and hardware limitations.
- End-to-end (E2E) delay: The time taken for a packet to route through the network from a source vehicle to its destination vehicle.
- Collision rate: The average number of collisions per frame. The collision rate significantly depends on traffic density and the total number of available time slots.
7. Discussion
8. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- ISO. CEN ISO/TR 21186-2:2021; Cooperative Intelligent Transport Systems (C-ITS) Guidelines on the Usage of Standards. ISO: Geneva, Switzerland, 2020.
- ETSI (European Telecommunications Standards Institute). ETSI EN 302 637-2 Intelligent Transport Systems (ITS); Vehicular Communications; Basic Set of Applications; Part 2: Specification of Cooperative Awareness Basic Service V1.4.1; ETSI: Sophia Antipolis, France, 2019; Volume V1.4.1. [Google Scholar]
- IEEE Vehicular Technology Society. IEEE Standard for Wireless Access in Vehicular Environments (WAVE)--Identifiers. IEEE Std 1609.12-2019 (Revision of IEEE Std 1609.12-2016); IEEE: Piscataway, NJ, USA, 2019. [Google Scholar]
- Hussein, N.H.; Yaw, C.T.; Koh, S.P.; Tiong, S.K.; Chong, K.H. A Comprehensive Survey on Vehicular Networking: Communications, Applications, Challenges, and Upcoming Research Directions. IEEE Access 2022, 10, 86127–86180. [Google Scholar] [CrossRef]
- Maaloul, S.; Aniss, H.; Kassab, M.; Berbineau, M. Classification of C-ITS Services in Vehicular Environments. IEEE Access 2021, 9, 117868–117879. [Google Scholar] [CrossRef]
- Sepulcre, M.; Gonzalez-Martin, M.; Gozalvez, J.; Molina-Masegosa, R.; Coll-Perales, B. Analytical Models of the Performance of IEEE 802.11p Vehicle to Vehicle Communications. IEEE Trans. Veh. Technol. 2022, 71, 713–724. [Google Scholar] [CrossRef]
- Zhang, S.; Chen, J.; Lyu, F.; Cheng, N.; Shi, W.; Shen, X. Vehicular Communication Networks in the Automated Driving Era. IEEE Commun. Mag. 2018, 56, 26–32. [Google Scholar] [CrossRef]
- TSGR (Transport System Generic Requirement). TS 136 101-V14.5.0-LTE; Evolved Universal Terrestrial Radio Access (E-UTRA); User Equipment (UE) Radio Transmission and Reception (3GPP TS 36.101 Version 14.5.0 Release 14); ETSI: Sophia Antipolis, France, 2017. [Google Scholar]
- ETSI (European Telecommunications Standards Institute). TR 103 439-V2.1.1-Intelligent Transport Systems (ITS); Multi-Channel Operation Study; Release 2; ETSI: Sophia Antipolis, France, 2021; Volume 1. [Google Scholar]
- Jeong, H.H.; Shen, Y.C.; Jeong, J.P.; Oh, T.T. A Comprehensive Survey on Vehicular Networking for Safe and Efficient Driving in Smart Transportation: A Focus on Systems, Protocols, and Applications. Veh. Commun. 2021, 31, 100349. [Google Scholar] [CrossRef]
- Pan, Q.; Wu, J.; Nebhen, J.; Bashir, A.K.; Su, Y.; Li, J. Artificial Intelligence-Based Energy Efficient Communication System for Intelligent Reflecting Surface-Driven VANETs. IEEE Trans. Intell. Transp. Syst. 2022, 23, 19714–19726. [Google Scholar] [CrossRef]
- Molina-Masegosa, R.; Gozalvez, J.; Sepulcre, M. Comparison of IEEE 802.11p and LTE-V2X: An Evaluation With Periodic and Aperiodic Messages of Constant and Variable Size. IEEE Access 2020, 8, 121526–121548. [Google Scholar] [CrossRef]
- Bhardwaj, P.; Pal, R.; Gupta, N. An Intelligent Scheme for Slot Reservation in Vehicular Ad Hoc Networks. China Commun. 2021, 18, 223–235. [Google Scholar] [CrossRef]
- Zang, J.; Shikh-Bahaei, M. Full Duplex-Based Scheduling Protocol for Latency Enhancement in 5G EV2X VANETs. In Proceedings of the 2021 IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Shah, P.; Kasbe, T. A Review on Specification Evaluation of Broadcasting Routing Protocols in VANET. Comput. Sci. Rev. 2021, 41, 100418. [Google Scholar] [CrossRef]
- Amin, F.; Abbasi, R.; Khan, S.; Abid, M.A. An Overview of Medium Access Control and Radio Duty Cycling Protocols for Internet of Things. Electronics 2022, 11, 3873. [Google Scholar] [CrossRef]
- Johari, S.; Bala Krishna, M. TDMA Based Contention-Free MAC Protocols for Vehicular Ad Hoc Networks: A Survey. Veh. Commun. 2021, 28, 100308. [Google Scholar] [CrossRef]
- Ma, M.; Liu, K.; Luo, X.; Zhang, T.; Liu, F. Review of MAC Protocols for Vehicular Ad Hoc Networks. Sensors 2020, 20, 6709. [Google Scholar] [CrossRef] [PubMed]
- Arena, F.; Pau, G.; Severino, A. A Review on IEEE 802.11p for Intelligent Transportation Systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Srivastava, A.; Prakash, A.; Tripathi, R. A Cross Layer Based Cooperative Broadcast Protocol for Multichannel VANET. Ad Hoc Netw. 2022, 131, 102840. [Google Scholar] [CrossRef]
- Cao, Y.; Zhang, H.; Fang, Y.; Yuan, D. An Adaptive High-Throughput Multichannel MAC Protocol for VANETs. IEEE Internet Things J. 2020, 7, 8249–8262. [Google Scholar] [CrossRef]
- Chakroun, R.; Abdellatif, S.; Villemur, T. LAMD: Location-Based Alert Message Dissemination Scheme for Emerging Infrastructure-Based Vehicular Networks. Internet Things 2022, 19, 100510. [Google Scholar] [CrossRef]
- Huang, C.-M.; Lai, C.-F. The Delay-Constrained and Network-Situation-Aware V2V2I VANET Data Offloading Based on the Multi-Access Edge Computing (MEC) Architecture. IEEE Open J. Veh. Technol. 2020, 1, 331–347. [Google Scholar] [CrossRef]
- Deng, T.; Wei, S.; Liu, X.; Zhou, H.; Dong, M. Distributed Resource Allocation Based on Timeslot Reservation in High-Density VANETs. IEEE Trans. Veh. Technol. 2022, 71, 6586–6595. [Google Scholar] [CrossRef]
- Wu, Y.; Zheng, J. Modeling and Analysis of the Local Delay in an MEC-Based VANET for a Suburban Area. IEEE Internet Things J. 2022, 9, 7065–7079. [Google Scholar] [CrossRef]
- Liu, Y.; Zhou, H.; Huang, J. OCA-MAC: A Cooperative TDMA-Based MAC Protocol for Vehicular Ad Hoc Networks. Sensors 2019, 19, 2691. [Google Scholar] [CrossRef]
- Sudheera, K.L.K.; Ma, M.; Chong, P.H.J. Real-Time Cooperative Data Routing and Scheduling in Software Defined Vehicular Networks. Comput. Commun. 2022, 181, 203–214. [Google Scholar] [CrossRef]
- Zhang, T.; Zhu, Q. EVC-TDMA: An Enhanced TDMA Based Cooperative MAC Protocol for Vehicular Networks. J. Commun. Netw. 2020, 22, 316–325. [Google Scholar] [CrossRef]
- Liu, B.; Deng, D.; Rao, W.; Wang, E.; Xiong, S.; Jia, D.; Wang, J.; Qiao, C. CPA-MAC: A Collision Prediction and Avoidance MAC for Safety Message Dissemination in MEC-Assisted VANETs. IEEE Trans. Netw. Sci. Eng. 2022, 9, 783–794. [Google Scholar] [CrossRef]
- Mosavat-Jahromi, H.; Li, Y.; Ni, Y.; Cai, L. Distributed and Adaptive Reservation MAC Protocol for Beaconing in Vehicular Networks. IEEE Trans. Mob. Comput. 2021, 20, 2936–2948. [Google Scholar] [CrossRef]
- Latif, M.B.; Liu, F.; Liu, K. A TDMA-Based MAC Protocol for Mitigating Mobility-Caused Packet Collisions in Vehicular Ad Hoc Networks. Sensors 2022, 22, 643. [Google Scholar] [CrossRef] [PubMed]
- Tiwari, J.; Prakash, A.; Tripathi, R. A Novel Cooperative MAC Protocol for Safety Applications in Cognitive Radio Enabled Vehicular Ad-Hoc Networks. Veh. Commun. 2021, 29, 100336. [Google Scholar] [CrossRef]
- Mosavat, H.; Li, Y.; Cai, L.; Lu, L. NC–MAC: A Distributed MAC Protocol for Reliable Beacon Broadcasting in V2X. IEEE Trans. Veh. Technol. 2021, 70, 6044–6057. [Google Scholar] [CrossRef]
- Karabulut, M.A.; Shah, A.F.M.S.; Ilhan, H. CoMACAV: Cooperative MAC Protocol for Autonomous Vehicles. In Proceedings of the 2019 IEEE International Symposium on INnovations in Intelligent SysTems and Applications (INISTA), Sofia, Bulgaria, 3–5 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Tiwari, J.; Prakash, A.; Tripathi, R.; Naik, K. A Fair and Cooperative MAC Protocol for Heterogeneous Cognitive Radio Enabled Vehicular Ad-Hoc Networks. IEEE Trans. Cogn. Commun. Netw. 2022, 8, 1005–1018. [Google Scholar] [CrossRef]
- Nyi Linn, N.; Liu, K.; Lu, H. A Clustering-Based Contention-Free MAC Protocol for Vehicular Ad Hoc Networks. In Proceedings of the 2022 7th International Conference on Computer and Communication Systems (ICCCS), Guangzhou, China, 21–24 April 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 560–565. [Google Scholar]
- Tanenbaum, A.S.; Wetherall, D.J. Computer Networks, 5th ed.; Prentice Hall: Englewood Cliffs, NJ, USA, 2011; ISBN 9780132126953. [Google Scholar]
- Abdelkader, G.; Elgazzar, K.; Khamis, A. Connected Vehicles: Technology Review, State of the Art, Challenges and Opportunities. Sensors 2021, 21, 7712. [Google Scholar] [CrossRef]
- Babu, S.; Parthiban, A.R.K. DTMR: An Adaptive Distributed Tree-Based Multicast Routing Protocol for Vehicular Networks. Comput. Stand. Interfaces 2022, 79, 103551. [Google Scholar] [CrossRef]
- Shin, Y.; Choi, H.; Nam, Y.; Lee, E. Data Delivery Protocol Using the Trajectory Information on a Road Map in VANETs. Ad Hoc Netw. 2020, 107, 102260. [Google Scholar] [CrossRef]
- Abbasi, H.I.; Voicu, R.C.; Copeland, J.A.; Chang, Y. Towards Fast and Reliable Multihop Routing in VANETs. IEEE Trans. Mob. Comput. 2020, 19, 2461–2474. [Google Scholar] [CrossRef]
- Ameur, A.I.; Lakas, A.; Yagoubi, M.B.; Oubbati, O.S. Peer-to-Peer Overlay Techniques for Vehicular Ad Hoc Networks: Survey and Challenges. Veh. Commun. 2022, 34, 100455. [Google Scholar] [CrossRef]
- Zhang, H.; Zhang, X.; Sung, D.K. An Efficient Cooperative Transmission Based Opportunistic Broadcast Scheme in VANETs. IEEE Trans. Mob. Comput. 2021, 2, 1. [Google Scholar] [CrossRef]
- Ghaemi, Y.; El-Ocla, H.; Yadav, N.R.; Madana, M.R.; Raju, D.K.; Dhanabal, V.; Sheshadri, V. Intelligent Transport System Using Time Delay-Based Multipath Routing Protocol for Vehicular Ad Hoc Networks. Sensors 2021, 21, 7706. [Google Scholar] [CrossRef]
- Yeferny, T.; Yahia, S. Ben A Markov Chain-Based Data Dissemination Protocol for Vehicular Ad Hoc Networks. Comput. Commun. 2021, 180, 303–314. [Google Scholar] [CrossRef]
- Cai, Y.; Zhu, H.; Chang, S.; Wang, X.; Shen, J.; Guo, M. PeerProbe: Estimating Vehicular Neighbor Distribution With Adaptive Compressive Sensing. IEEE/ACM Trans. Netw. 2022, 30, 1703–1716. [Google Scholar] [CrossRef]
- Abuelenin, S.M.; Elaraby, S. A Generalized Framework for Connectivity Analysis in Vehicle-to-Vehicle Communications. IEEE Trans. Intell. Transp. Syst. 2022, 23, 5894–5898. [Google Scholar] [CrossRef]
- Wang, X.; Weng, Y.; Gao, H. A Low-Latency and Energy-Efficient Multimetric Routing Protocol Based on Network Connectivity in VANET Communication. IEEE Trans. Green Commun. Netw. 2021, 5, 1761–1776. [Google Scholar] [CrossRef]
- Osman, R.A.; Zaki, A.I.; Abdelsalam, A.K. Novel Road Traffic Management Strategy for Rapid Clarification of the Emergency Vehicle Route Based on V2V Communications. Sensors 2021, 21, 5120. [Google Scholar] [CrossRef]
- Hota, L.; Nayak, B.P.; Kumar, A.; Sahoo, B.; Ali, G.G.M.N. A Performance Analysis of VANETs Propagation Models and Routing Protocols. Sustainability 2022, 14, 1379. [Google Scholar] [CrossRef]
- Gao, Q.; Wang, R.; Deng, H.; Luo, X.; Liu, K.; Peng, X.-H.; Liu, G.; Li, A. Performance Analysis of Cooperative Multiple Access With Minimum Interference Range for Large Scale Wireless Networks. IEEE Access 2022, 10, 2154–2169. [Google Scholar] [CrossRef]
- Aung, N.; Zhang, W.; Dhelim, S.; Ai, Y. T-Coin: Dynamic Traffic Congestion Pricing System for the Internet of Vehicles in Smart Cities. Information 2020, 11, 149. [Google Scholar] [CrossRef]
- Pei, Z.; Wang, X.; Lei, Z.; Zheng, H.; Du, L.; Chen, W. Joint Optimization of Multi-Hop Broadcast Protocol and MAC Protocol in Vehicular Ad Hoc Networks. Sensors 2021, 21, 6092. [Google Scholar] [CrossRef]
- C, T.; M G, J. An Enhancement for IEEE 802.11p to Provision Quality of Service with Context Aware Channel Access for the Forward Collision Avoidance Application in Vehicular Ad Hoc Network. Sensors 2021, 21, 6937. [Google Scholar] [CrossRef] [PubMed]
- Siddik, M.; Moni, S.; Alam, M.; Johnson, W. SAFE-MAC: Speed Aware Fairness Enabled MAC Protocol for Vehicular Ad-Hoc Networks. Sensors 2019, 19, 2405. [Google Scholar] [CrossRef]
- Kuhlmorgen, S.; Lu, H.; Festag, A.; Kenney, J.; Gemsheim, S.; Fettweis, G. Evaluation of Congestion-Enabled Forwarding With Mixed Data Traffic in Vehicular Communications. IEEE Trans. Intell. Transp. Syst. 2020, 21, 233–247. [Google Scholar] [CrossRef]
- Zhou, S.; Li, D.; Tang, Q.; Fu, Y.; Guo, C.; Chen, X. Multiple Intersection Selection Routing Protocol Based on Road Section Connectivity Probability for Urban VANETs. Comput. Commun. 2021, 177, 255–264. [Google Scholar] [CrossRef]
- IEEE. Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications, IEEE Std 802.11-2012 (Revision of IEEE Std 802.11-2007); IEEE: Piscataway, NJ, USA, 2012. [Google Scholar]







| Protocol | Beaconing Range | Strategy | Access Delay | Resolving Collisions | Objective |
|---|---|---|---|---|---|
| EVC-TDMA [28] | Multi-hop | One-dimensional Markov | Moderate | Merging collisions | Reduce packet dropping rate, improve throughput |
| NC-MAC [33] | One-hop | Network coding | Low | Hidden terminals, access collisions | Enhance broadcasting reliability |
| ECTOB-MAC [43] | Multi-hop | Quasi- orthogonal | Moderate | Hidden terminals, access collisions | Improve broadcast performance |
| TMR-MAC [44] | Multi-hop | Round-trip time | Moderate | Access collisions | Shortest route to destination |
| MCDP-MAC [45] | Multi-hop | Markov | Moderate | No | High reachability ratio |
| DARP-MAC [24] | Multi-hop | Adaptive Reservation | Low | Hidden terminals, access collisions | Enhance reliability and scalability |
| PeerProbe-MAC [46] | Multi-hop | Adaptive compressive sensing | Moderate | No | High-accuracy neighbor distribution estimation |
| No. of Hop Sets | Vehicle ID | Position | Speed | Moving Direction | Channel No. | Slot No. |
|---|---|---|---|---|---|---|
| 1HS/2HS/3HS | [0, 350] | [20, 120] | Left/Right | [n-a, n-z] |
| Parameter | Value | Description |
|---|---|---|
| MaxSpeed | [80, 200] | The maximum speed that a vehicle can travel (km/h) |
| Entry 2 | [2.2, 18] | The netto-length of a vehicle (m) |
| Width | [1.6, 2] | The width of a vehicle (m) |
| Accel | [2, 5] | The acceleration ability of a vehicle (m/s2) |
| Decel | [3, 8] | The deceleration ability of a vehicle (m/s2) |
| MinGap | [2.5, 5] | The gap to the leader when standing in a jam (m) |
| Sigma | [0.2, 0.7] | The vehicle’s driver imperfection (between 0 and 1) |
| Tau | [0, 1] | The driver’s desired (minimum) time headway |
| Car-following model | Karuss | This model describes how a vehicle follows another one |
| Lane-changing model | LC2013 | This model describes how a driver changes lanes |
| Duration of a Time Slot | SINR Range | Vehicles/km at NOC = 10 | Power (dBm) at NOC = 10 |
|---|---|---|---|
| Lb = 0.5 ms | [40, 60] | [0.059, 0.375] | [–6, 25] |
| Lb = 1 ms | [20, 40] | [0.052, 0.098] | [15.8, 25] |
| Lb = 2 ms | [5, 20] | [0.0573, 0.062] | [20.34, 25] |
| Lb = 4 ms | [1, 5] | [0.05, 0.0278] | [23.4, 25] |
| Parameter | Value | Description |
|---|---|---|
| 5 (km) | Road segment length | |
| [0.05, 0.3] (vehicles/m) | Vehicle density | |
| 4 | Lanes/direction | |
| 27.57 (m/s) | Mean speed value | |
| 6 (Mbps) | Data rate | |
| 10−4.38 | Path loss constant | |
| 3.68 | Path loss exponent | |
| 23 (dBm) | Transmission power | |
| −85 (dBm) | Receiver sensitivity | |
| 3.3 (dBm) | Decoding SINR threshold | |
| W | 180 × 6 (kHz) | Channel bandwidth |
| W × 10−17.4 (mW) | Noise power | |
| ρ | 0.5, 0.7, 0.9 | Correlation factor |
| 500 (s) | Simulation time |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Linn, N.N.; Liu, K.; Gao, Q. A Contention-Free Cooperative MAC Protocol for Eliminating Heterogenous Collisions in Vehicular Ad Hoc Networks. Sensors 2023, 23, 1033. https://doi.org/10.3390/s23021033
Linn NN, Liu K, Gao Q. A Contention-Free Cooperative MAC Protocol for Eliminating Heterogenous Collisions in Vehicular Ad Hoc Networks. Sensors. 2023; 23(2):1033. https://doi.org/10.3390/s23021033
Chicago/Turabian StyleLinn, Nyi Nyi, Kai Liu, and Qiang Gao. 2023. "A Contention-Free Cooperative MAC Protocol for Eliminating Heterogenous Collisions in Vehicular Ad Hoc Networks" Sensors 23, no. 2: 1033. https://doi.org/10.3390/s23021033
APA StyleLinn, N. N., Liu, K., & Gao, Q. (2023). A Contention-Free Cooperative MAC Protocol for Eliminating Heterogenous Collisions in Vehicular Ad Hoc Networks. Sensors, 23(2), 1033. https://doi.org/10.3390/s23021033






