Diffusion of White-Hat Botnet Using Lifespan with Controllable Ripple Effect for Malware Removal in IoT Networks
Abstract
1. Introduction
- (i)
- The method proposes a control method of lifespan for white-hat botnets. The lifespan changes according to the state of the white-hat nodes, where the lifespan can increase or decrease.
- (ii)
- The method controls the ripple effect when diffusing white-hat botnets. The characteristics of the ripple effect are that the range and concentration of white-hat botnets change depending on the parameter settings.
- (iii)
- The evaluation of dynamic lifespan to the diffusion strategies using a white-hat botnet.
2. Related Works
3. Approach of Diffusion Based on Dynamic Lifespan
3.1. Research Problem
- Input: Network nodes (, is a set of infected nodes and is a set of white-hat botnets with initial lifespan L), increase ratio α, decrease β
- Output: Network with nodes where
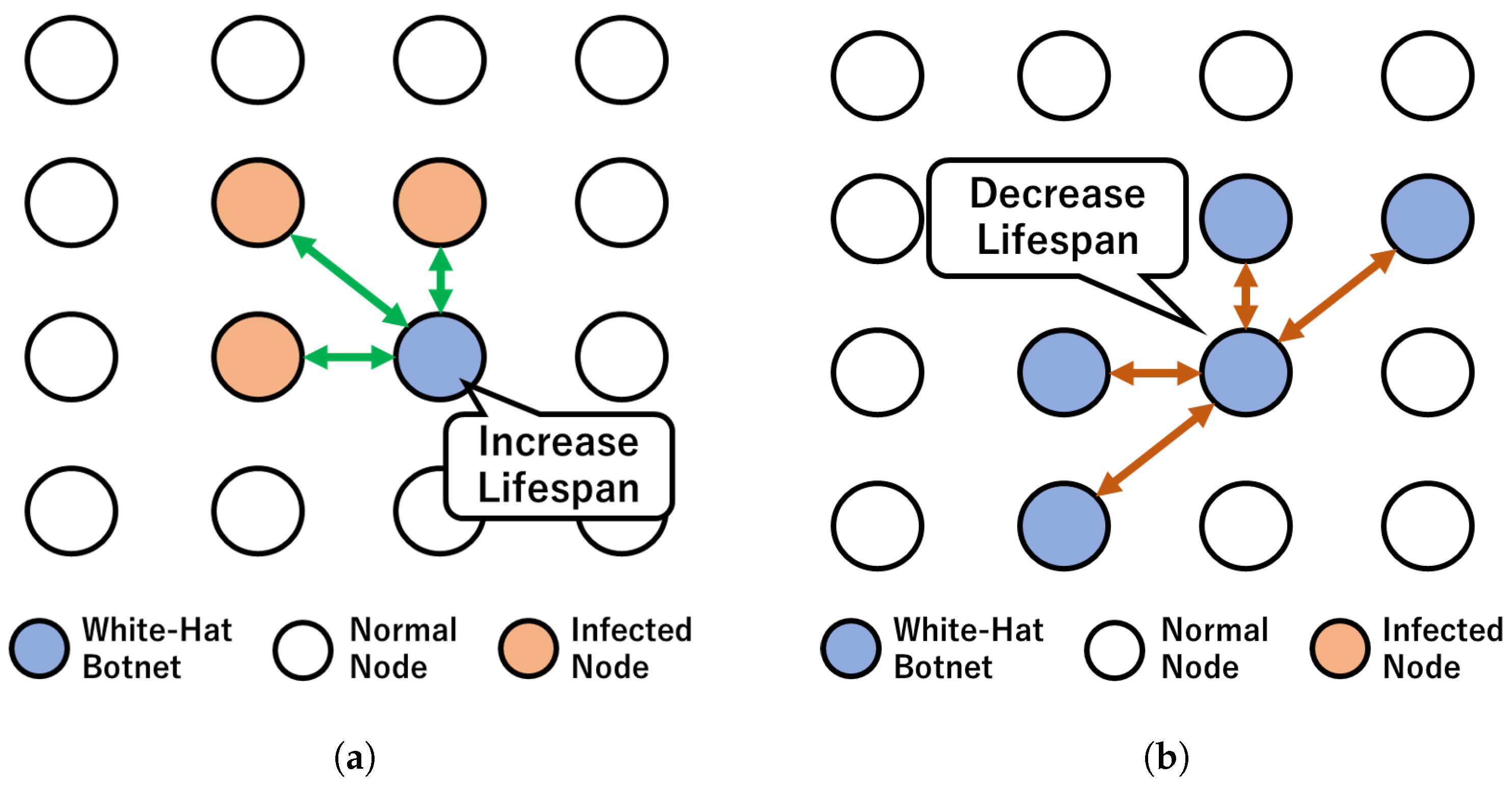
3.2. Lifespan-Based Control Method with Ripple Effect
- Initial Lifespan L: Initial lifespan L is the initial lifespan given to a white-hat botnet when it spreads to another node.
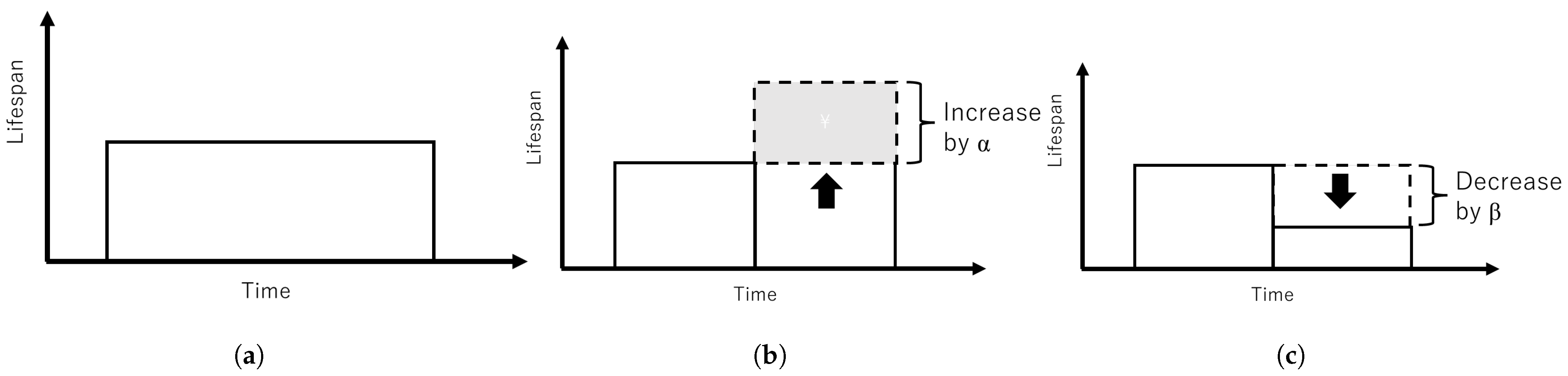
- Increase ratio : Increase ratio is the rate of increase from initial lifespan L such that .
- Decrease ratio : Decrease ratio is the rate of decrease from initial lifespan L such that .
- (i)
- Congregation density D: The density of white-hat botnet nodes or infected nodes that gather within the communication range.
- (ii)
- Lifespan ratio r: Multiplication ratio for increasing or decreasing the current lifespan.
- White-hat botnets in Network of Botnets: We decrease the botnet’s lifespan by 2 times i.e., , and create a new child.We can modify Equation (2) as follows:
- White-hat botnets in Network of Botnets and Malware: We increase the botnet’s lifespan by 2 i.e., and create a new child.We can modify Equation (2) as follows:
- White-hat botnets in Network of Normal Nodes: We normally reduce the lifespan by 1 i.e., and create a new child.We can modify Equation (2) as follows:
- Increase Ratio : Increase ratio is a ratio in which the lifespan ratio is increased when connected nodes of a white-hat botnet are infected nodes. Increased ratio strengthens the defense by building a wall of botnets with longer lifespans when encountering infected nodes.
- Decrease Ratio : Decrease ratio is a ratio that decreases the lifespan when the connected nodes of white-hat botnets are white-hat botnets. It is used to control the congregation density to suppress the overpopulation of white-hat botnets.
| Algorithm 1 Diffusion of White-Hat Botnet |
| Input: Network nodes and is a set of white-hat botnets, Increase Ratio , Reduction Ratio , congregation density and Output: Lifespan L for each node ▹ Diffuse white-hat botnet
|
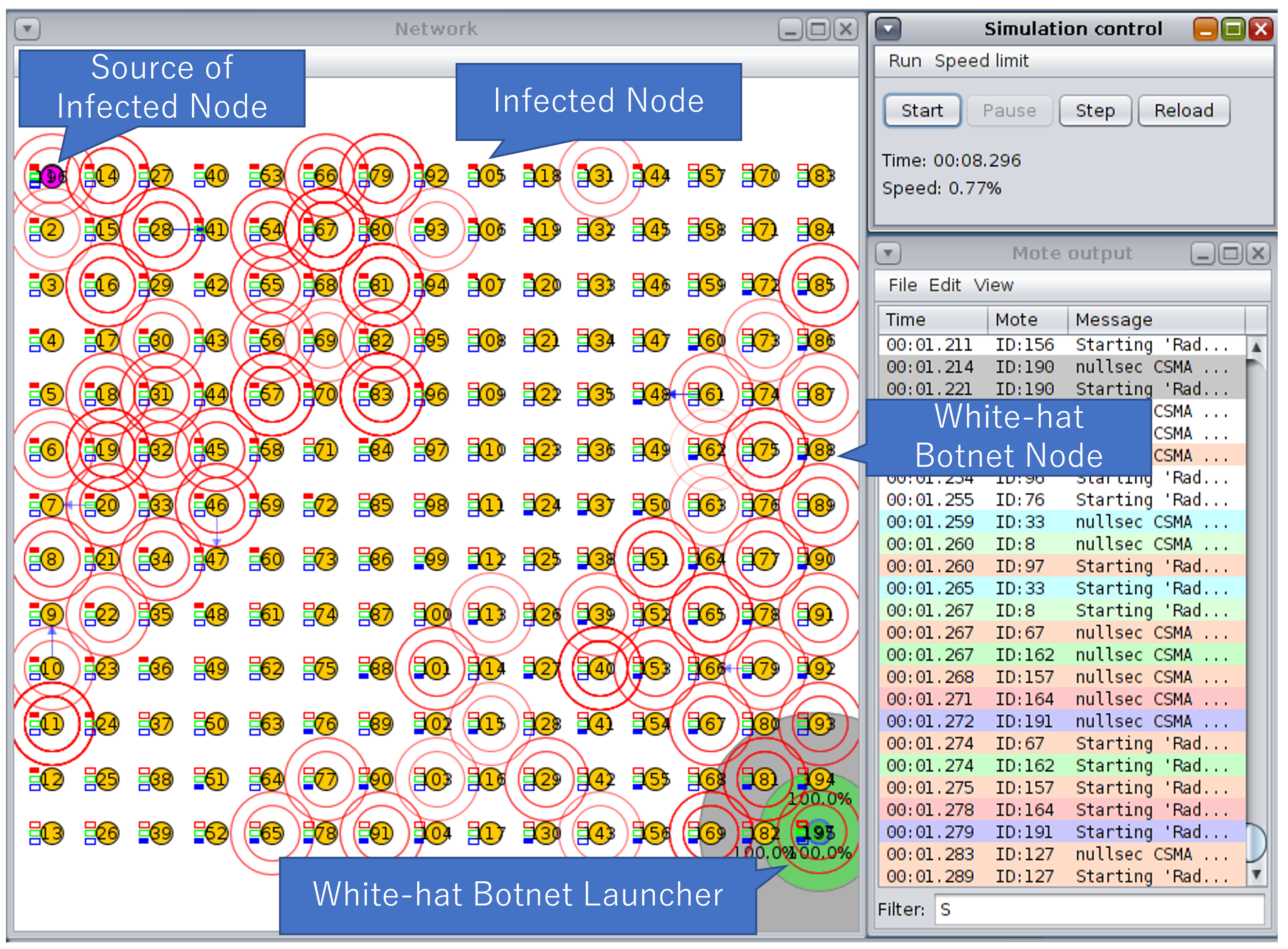
4. Evaluation
4.1. Experiment Design
- (i)
- Fix Ratio: Fixed lifespan with a variation of 5, 10, and 20 where .
- (ii)
- Adjust Increase Ratio: Increase the initial lifespan L within the range of 20, 15, 10, and 5 with the increase ratio larger than ratio where such that and .
- (iii)
- Adjust Decrease Ratio: Decrease the initial lifespan L of 20, 15, 10, and 5 with decrease ratio smaller than ratio where such that and .
- (iv)
- Adjust Increase-Decrease Ratio: Increase initial lifespan L with a variation of 5, 10, and 20 with increase ratio and decrease ratio such that .
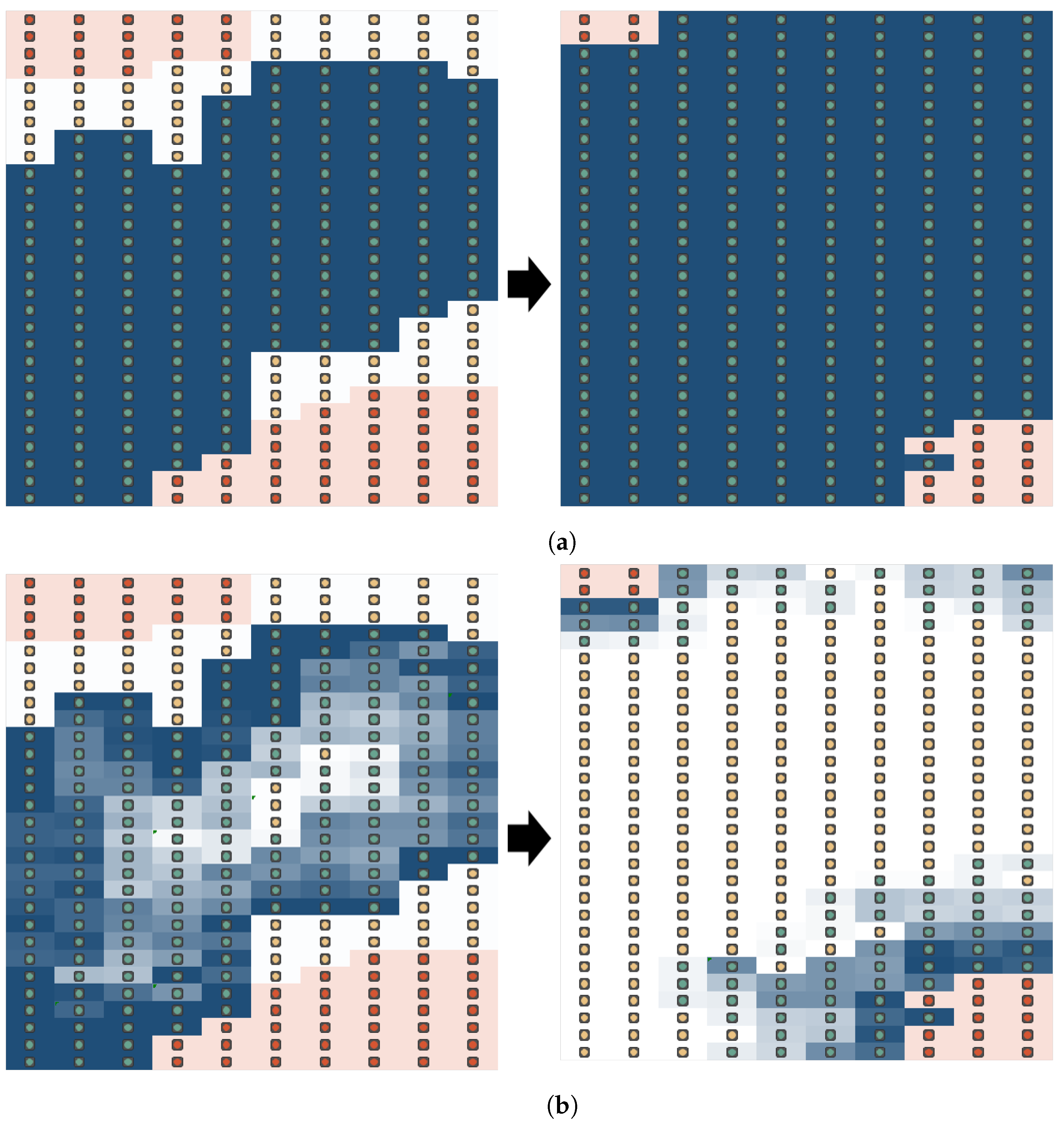
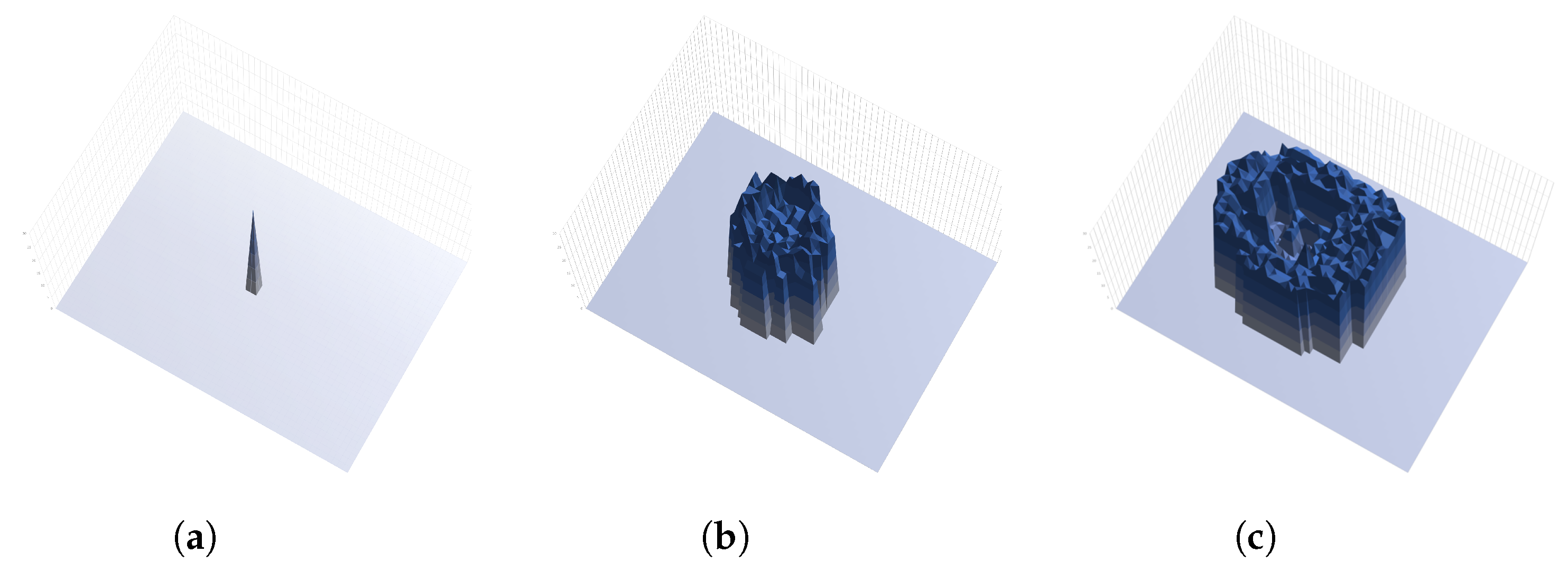
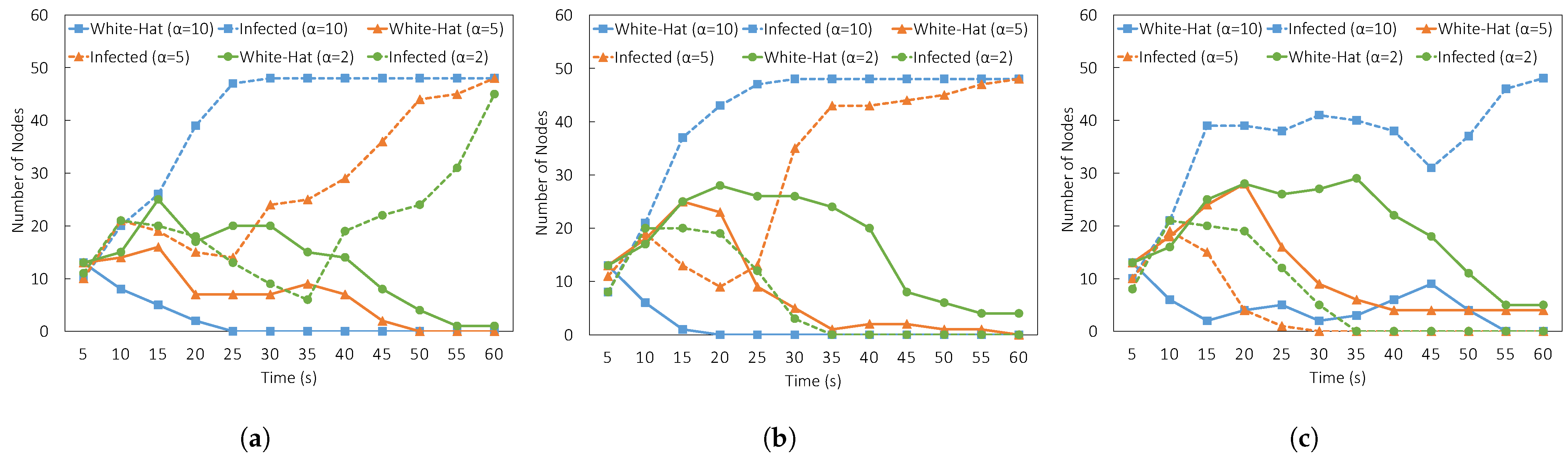
4.2. Evaluation Results
- Fixed Lifespan: The initial lifespan L is fixed to . There is no change in the increase or decrease ratio.
- Low Balanced Ratio: The increase ratio and decrease ratio are set to the same value i.e., . The value is a relatively small value.
- Small Attack—Small Withdrawal Ratio: The increase ratio is set to and the decrease ratio is set to . The decrease ratio is slightly lower than the increase ratio.
- Large Attack—Small Withdrawal Ratio: The increase ratio is set to a large value and the decrease ratio is set to a small value .
- Large Attack—Medium Withdrawal Ratio: The increase ratio is set to a large value and the decrease ratio is set to a relatively medium value .
- Large Attack—Large Withdrawal: The increase ratio and the decrease ratio is set to the same large amount .
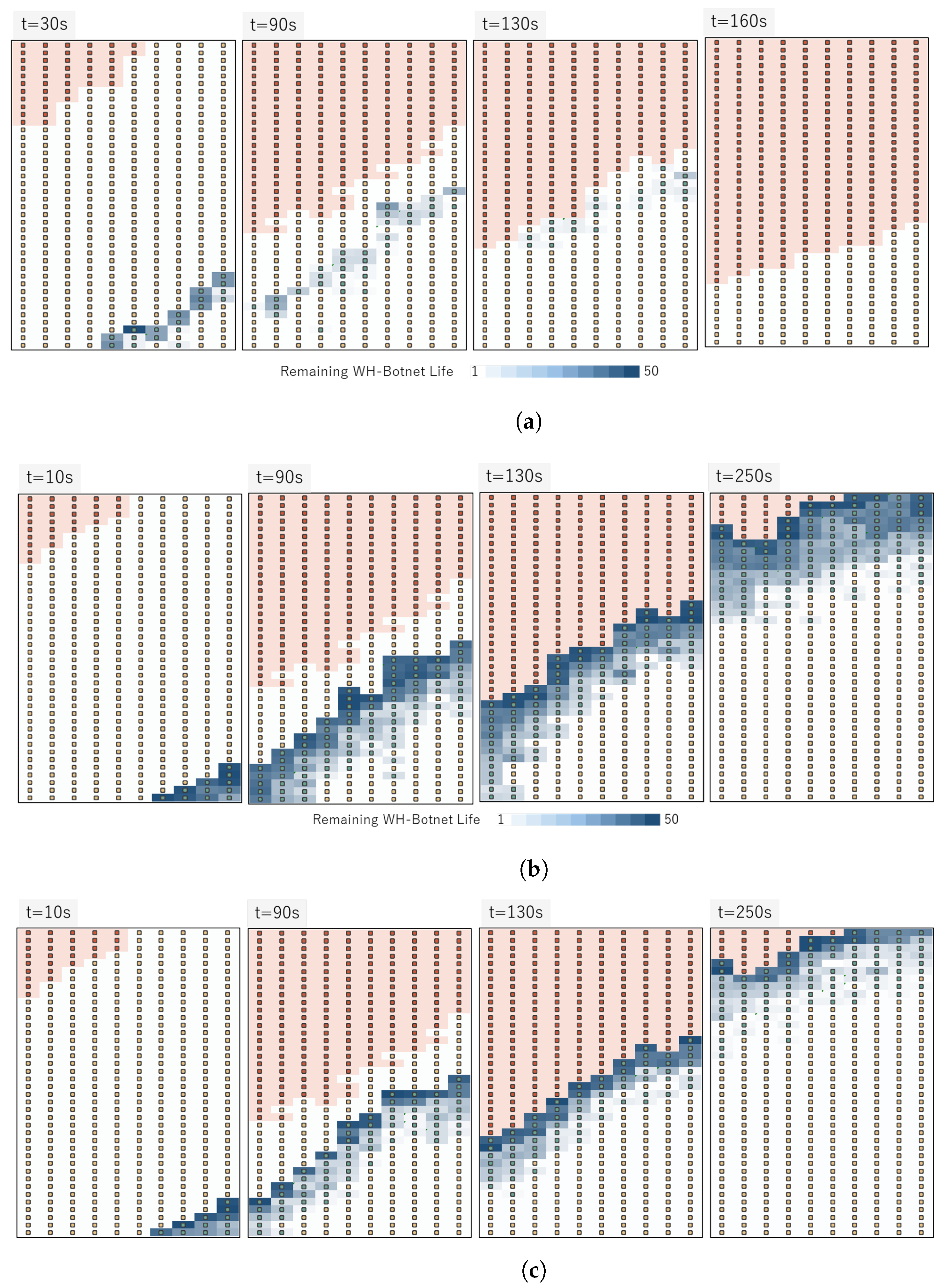
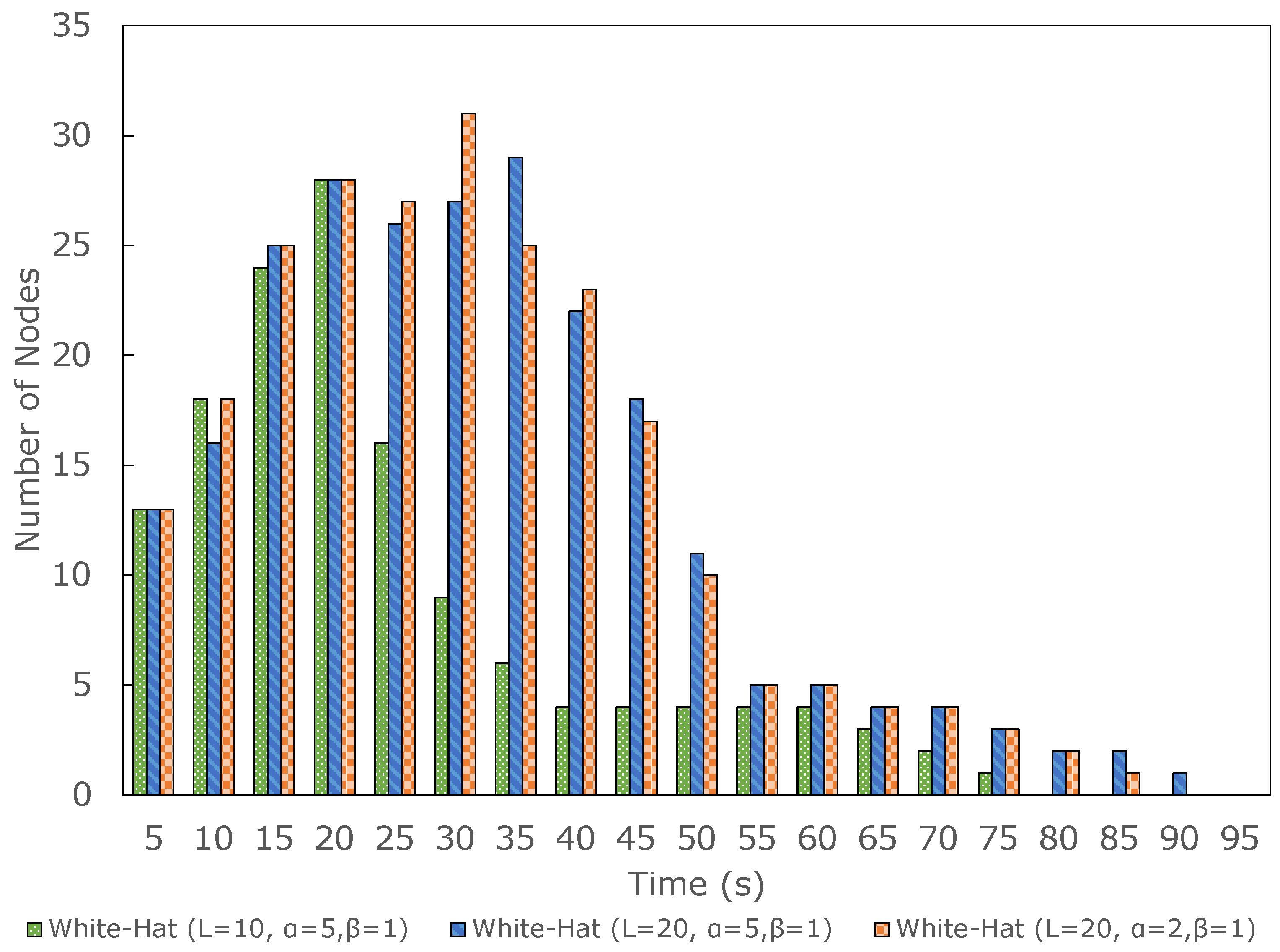
4.3. Discussions
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the Mirai Botnet. In Proceedings of the USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017. [Google Scholar]
- Grammatikakis, K.P.; Koufos, I.; Kolokotronis, N.; Vassilakis, C.; Shiaeles, S. Understanding and Mitigating Banking Trojans: From Zeus to Emotet. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; pp. 121–128. [Google Scholar] [CrossRef]
- Yamaguchi, S.; Gupta, B. Botnet Defense System and White-Hat Worm Launch Strategy in IoT Network. In Advances in Malware and Data-Driven Network Security; IGI Global: Hershey, PA, USA, 2022; pp. 127–147. [Google Scholar] [CrossRef]
- Donno, M.D.; Dragoni, N.; Giaretta, A.; Mazzara, M. AntibIoTic: Protecting IoT Devices Against DDoS Attacks. In Proceedings of the International Conference on Software Engineering for Defence Applications, Rome, Italy, 10 May 2016. [Google Scholar]
- 300,000 Obeying Devices: Hajime Is Conquering the Internet of Things World—kaspersky.com. Available online: https://www.kaspersky.com/about/press-releases/2017_300000-obeying-devices-hajime-is-conquering-the-internet-of-things-world (accessed on 27 December 2022).
- Yamaguchi, S. White-Hat Worm to Fight Malware and Its Evaluation by Agent-Oriented Petri Nets. Sensors 2020, 20, 556. [Google Scholar] [CrossRef] [PubMed]
- Yamaguchi, S. Botnet Defense System: Observability, Controllability, and Basic Command and Control Strategy. Sensors 2022, 22, 9423. [Google Scholar] [CrossRef] [PubMed]
- Kapoor, A.; Gupta, A.; Gupta, R.; Tanwar, S.; Sharma, G.; Davidson, I.E. Ransomware Detection, Avoidance, and Mitigation Scheme: A Review and Future Directions. Sustainability 2022, 14, 8. [Google Scholar] [CrossRef]
- Suastegui Jaramillo, L. Malware Detection and Mitigation Techniques: Lessons Learned from Mirai DDOS Attack. J. Inf. Syst. Eng. Manag. 2018, 3, 19. [Google Scholar] [CrossRef]
- Thakur, M.; Khilnani, D.; Gupta, K.; Jain, S.; Agarwal, V.; Sane, S.; Sanyal, S.; Dhekne, P. Detection and Prevention of Botnets and malware in an enterprise network. Int. J. Wirel. Mob. Comput. 2012, 5, 144–153. [Google Scholar] [CrossRef]
- Namanya, A.P.; Awan, I.U.; Disso, J.P.; Younas, M. Similarity hash based scoring of portable executable files for efficient malware detection in IoT. Future Gener. Comput. Syst. 2020, 110, 824–832. [Google Scholar] [CrossRef]
- Kakisim, A.G.; Nar, M.; Sogukpinar, I. Metamorphic malware identification using engine-specific patterns based on co-opcode graphs. Comput. Stand. Interfaces 2020, 71, 103443. [Google Scholar] [CrossRef]
- Rehman, Z.U.; Khan, S.N.; Muhammad, K.; Lee, J.W.; Lv, Z.; Baik, S.W.; Shah, P.A.; Awan, K.; Mehmood, I. Machine learning-assisted signature and heuristic-based detection of malwares in Android devices. Comput. Electr. Eng. 2018, 69, 828–841. [Google Scholar] [CrossRef]
- Vasan, D.; Alazab, M.; Wassan, S.; Safaei, B.; Zheng, Q. Image-Based malware classification using ensemble of CNN architectures (IMCEC). Comput. Secur. 2020, 92, 101748. [Google Scholar] [CrossRef]
- Liu, K.; Xu, S.; Xu, G.; Zhang, M.; Sun, D.; Liu, H. A Review of Android Malware Detection Approaches Based on Machine Learning. IEEE Access 2020, 8, 124579–124607. [Google Scholar] [CrossRef]
- Botacin, M.; Alves, M.Z.; Oliveira, D.; Grégio, A. HEAVEN: A Hardware-Enhanced AntiVirus ENgine to accelerate real-time, signature-based malware detection. Expert Syst. Appl. 2022, 201, 117083. [Google Scholar] [CrossRef]
- Hussain, F.; Abbas, S.G.; Pires, I.M.; Tanveer, S.; Fayyaz, U.U.; Garcia, N.M.; Shah, G.A.; Shahzad, F. A Two-Fold Machine Learning Approach to Prevent and Detect IoT Botnet Attacks. IEEE Access 2021, 9, 163412–163430. [Google Scholar] [CrossRef]
- Albanese, M.; Jajodia, S.; Venkatesan, S. Defending from Stealthy Botnets Using Moving Target Defenses. IEEE Secur. Priv. 2018, 16, 92–97. [Google Scholar] [CrossRef]
- Amich, A.; Eshete, B. Morphence: Moving Target Defense Against Adversarial Examples. In Proceedings of the Annual Computer Security Applications Conference, Virtual Event, 6–10 December 2021. [Google Scholar] [CrossRef]
- Hwang, S.Y.; Kim, J.N. A Malware Distribution Simulator for the Verification of Network Threat Prevention Tools. Sensors 2021, 21, 6983. [Google Scholar] [CrossRef]
- Sajjad, S.M.; Yousaf, M.; Afzal, H.; Mufti, M.R. eMUD: Enhanced Manufacturer Usage Description for IoT Botnets Prevention on Home WiFi Routers. IEEE Access 2020, 8, 164200–164213. [Google Scholar] [CrossRef]
- Ajmal, A.B.; Shah, M.A.; Maple, C.; Asghar, M.N.; Islam, S.U. Offensive Security: Towards Proactive Threat Hunting via Adversary Emulation. IEEE Access 2021, 9, 126023–126033. [Google Scholar] [CrossRef]
- Chu, Z.; Han, Y.; Zhao, K. Botnet Vulnerability Intelligence Clustering Classification Mining and Countermeasure Algorithm Based on Machine Learning. IEEE Access 2019, 7, 182309–182319. [Google Scholar] [CrossRef]
- Martinelli, F.; Mercaldo, F.; Nardone, V.; Santone, A.; Vaglini, G. Model checking and machine learning techniques for HummingBad mobile malware detection and mitigation. Simul. Model. Pract. Theory 2020, 105, 102169. [Google Scholar] [CrossRef]
- Kepner, J.; Bernays, J.; Buckley, S.; Cho, K.; Conrad, C.; Daigle, L.; Erhardt, K.; Gadepally, V.; Greene, B.; Jones, M.; et al. Zero Botnets: An Observe-Pursue-Counter Approach. arXiv 2022, arXiv:2201.06068. [Google Scholar]
- Yamaguchi, S. Botnet Defense System: Concept, Design, and Basic Strategy. Information 2020, 11, 516. [Google Scholar] [CrossRef]
- Pan, X.; Yamaguchi, S. Machine Learning White-Hat Worm Launcher for Tactical Response by Zoning in Botnet Defense System. Sensors 2022, 22, 4666. [Google Scholar] [CrossRef] [PubMed]
- Nadler, A.; Bitton, R.; Brodt, O.; Shabtai, A. On the vulnerability of anti-malware solutions to DNS attacks. Comput. Secur. 2022, 116, 102687. [Google Scholar] [CrossRef]
- Wichmann, A.; Gerhards-Padilla, E. Using Infection Markers as a Vaccine against Malware Attacks. In Proceedings of the 2012 IEEE International Conference on Green Computing and Communications, Besancon, France, 20–23 November 2012; pp. 737–742. [Google Scholar] [CrossRef]
- Kouliaridis, V.; Kambourakis, G. A Comprehensive Survey on Machine Learning Techniques for Android Malware Detection. Information 2021, 12, 185. [Google Scholar] [CrossRef]
- Moussas, V.; Andreatos, A. Malware Detection Based on Code Visualization and Two-Level Classification. Information 2021, 12, 118. [Google Scholar] [CrossRef]
- Yadav, P.; Menon, N.; Ravi, V.; Viswanathan, S.; Pham, T.D. EfficientNet convolutional neural networks-based Android malware detection. Comput. Secur. 2022, 115, 102622. [Google Scholar] [CrossRef]
- Dinakarrao, S.M.P.; Guo, X.; Sayadi, H.; Nowzari, C.; Sasan, A.; Rafatirad, S.; Zhao, L.; Homayoun, H. Cognitive and Scalable Technique for Securing IoT Networks Against Malware Epidemics. IEEE Access 2020, 8, 138508–138528. [Google Scholar] [CrossRef]
- Pan, X.; Yamaguchi, S.; Kageyama, T.; Kamilin, M.H.B. Machine-Learning-Based White-Hat Worm Launcher in Botnet Defense System. Int. J. Softw. Sci. Comput. Intell. 2022, 14, 1–14. [Google Scholar] [CrossRef]
- Thanh Vu, S.N.; Stege, M.; El-Habr, P.I.; Bang, J.; Dragoni, N. A Survey on Botnets: Incentives, Evolution, Detection and Current Trends. Future Internet 2021, 13, 198. [Google Scholar] [CrossRef]
- Mahboubi, A.; Camtepe, S.; Ansari, K. Stochastic Modeling of IoT Botnet Spread: A Short Survey on Mobile Malware Spread Modeling. IEEE Access 2020, 8, 228818–228830. [Google Scholar] [CrossRef]
- Healey, J. Zero Botnets: Building a Global Effort to Clean Up the Internet; Council on Foreign Relations: New York, NY, USA, 2018. [Google Scholar]
- Bin Ahmadon, M.A.; Yamaguchi, S. Evaluation on White-Hat Worm Diffusion Method Based on The Evolution of Its Lifespan in Wireless Networks. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 7–9 January 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Doroudi, S.; Avgerinos, T.; Harchol-Balter, M. To clean or not to clean: Malware removal strategies for servers under load. Eur. J. Oper. Res. 2021, 292, 596–609. [Google Scholar] [CrossRef]
- Sibi Chakkaravarthy, S.; Sangeetha, D.; Vaidehi, V. A Survey on malware analysis and mitigation techniques. Comput. Sci. Rev. 2019, 32, 1–23. [Google Scholar] [CrossRef]


| Literature | Method | Detection | Prevention | Mitigation | Clean-Up | Static Lifespan | Dynamic Lifespan |
|---|---|---|---|---|---|---|---|
| Namanya et al. [11] | Signature-based | √ | |||||
| Kakisim et al. [12] | Signature-based | √ | |||||
| Rehman et al. [13] | Signature-based | √ | |||||
| Vasan et al. [14] | Machine Learning | √ | |||||
| Liu et al. [15] | Machine Learning | √ | |||||
| Botacin et al. [16] | Signature-based | √ | √ | ||||
| Hussain et al. [17] | Machine Learning | √ | √ | ||||
| Albanese et al. [18] | Moving Target Defense | √ | |||||
| Amich et al. [19] | Moving Target Defense | √ | |||||
| Hwang et al. [20] | Emulation | √ | |||||
| Sajjad et al. [21] | Emulation | √ | |||||
| Ajmal et al. [22] | Emulation | √ | |||||
| Chu et al. [23] | Machine Learning | √ | √ | ||||
| Martinelli et al. [24] | Machine Learning | √ | √ | ||||
| Kepner et al. [25] | Forward Defense | √ | √ | √ | |||
| Yamaguchi et al. [26] | BDS Launcher | √ | √ | √ | √ | ||
| Pan et al. [27] | BDS Launcher | √ | √ | √ | √ | ||
| Our Work | BDS Launcher | √ | √ | √ | √ |
| Experiment Settings | |||||
|---|---|---|---|---|---|
| Fixed Initial Lifespan | N/A | N/A | No | No | Yes |
| Balanced Small Attack—Withdrawal | 2 | 2 | No | No | Yes |
| Small Attack—Small Withdrawal | 2 | 1 | No | No | Yes |
| Large Attack—Small Withdrawal | 5 | 1 | No | Yes | Yes |
| Large Attack—Medium Withdrawal | 5 | 2 | No | Yes | Yes |
| Balanced Large Attack—Withdrawal | 5 | 5 | No | No | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bin Ahmadon, M.A.; Yamaguchi, S. Diffusion of White-Hat Botnet Using Lifespan with Controllable Ripple Effect for Malware Removal in IoT Networks. Sensors 2023, 23, 1018. https://doi.org/10.3390/s23021018
Bin Ahmadon MA, Yamaguchi S. Diffusion of White-Hat Botnet Using Lifespan with Controllable Ripple Effect for Malware Removal in IoT Networks. Sensors. 2023; 23(2):1018. https://doi.org/10.3390/s23021018
Chicago/Turabian StyleBin Ahmadon, Mohd Anuaruddin, and Shingo Yamaguchi. 2023. "Diffusion of White-Hat Botnet Using Lifespan with Controllable Ripple Effect for Malware Removal in IoT Networks" Sensors 23, no. 2: 1018. https://doi.org/10.3390/s23021018
APA StyleBin Ahmadon, M. A., & Yamaguchi, S. (2023). Diffusion of White-Hat Botnet Using Lifespan with Controllable Ripple Effect for Malware Removal in IoT Networks. Sensors, 23(2), 1018. https://doi.org/10.3390/s23021018







