Meta-Learner-Based Approach for Detecting Attacks on Internet of Things Networks
Abstract
:1. Introduction
- Stacking DL models based on three DL models, recurrent neural Networks (RNN), Long Short-Term Memory Networks (LSTM), and Convolutional Neural Networks (CNN), are designed and developed.
- An approach based on meta-learners is proposed for detecting attacks on IoT attacks. This meta-learner approach is trained using the output of the stacked DL models.
- A thorough evaluation of different meta-learner models is conducted to assess the influence of the stacked DL models on the performance of the meta-learner. Furthermore, a comprehensive evaluation of DL models in detecting unseen IoT attacks.
2. Related Works
3. Background
3.1. IoT Attacks and Their Implications
3.2. Meta-Learning
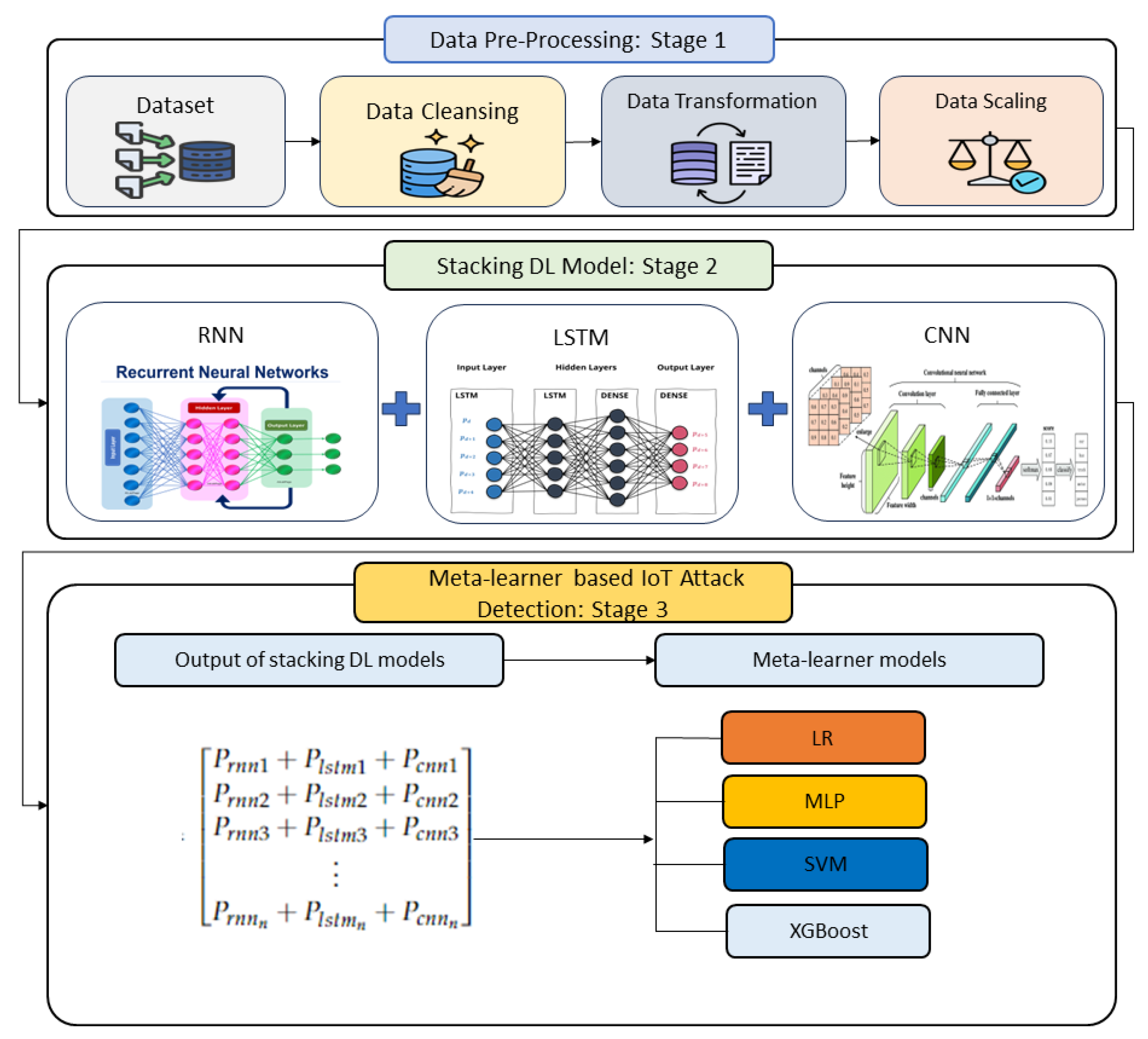
4. Proposed Approach
4.1. Data Preprocessing
4.2. Stacking DL Models
4.2.1. Base Model 1
4.2.2. Base Model 2
4.2.3. Base Model 3
4.2.4. Stacking Prediction Models
| Algorithm 1 Transforming and Stacking Predictions |
|
4.3. Meta-Learning-Based Model for Detecting IoT Attack
| Algorithm 2 Meta-Learner Selection |
|
5. Experimental Results
5.1. Dataset
5.2. Evaluation Metrics
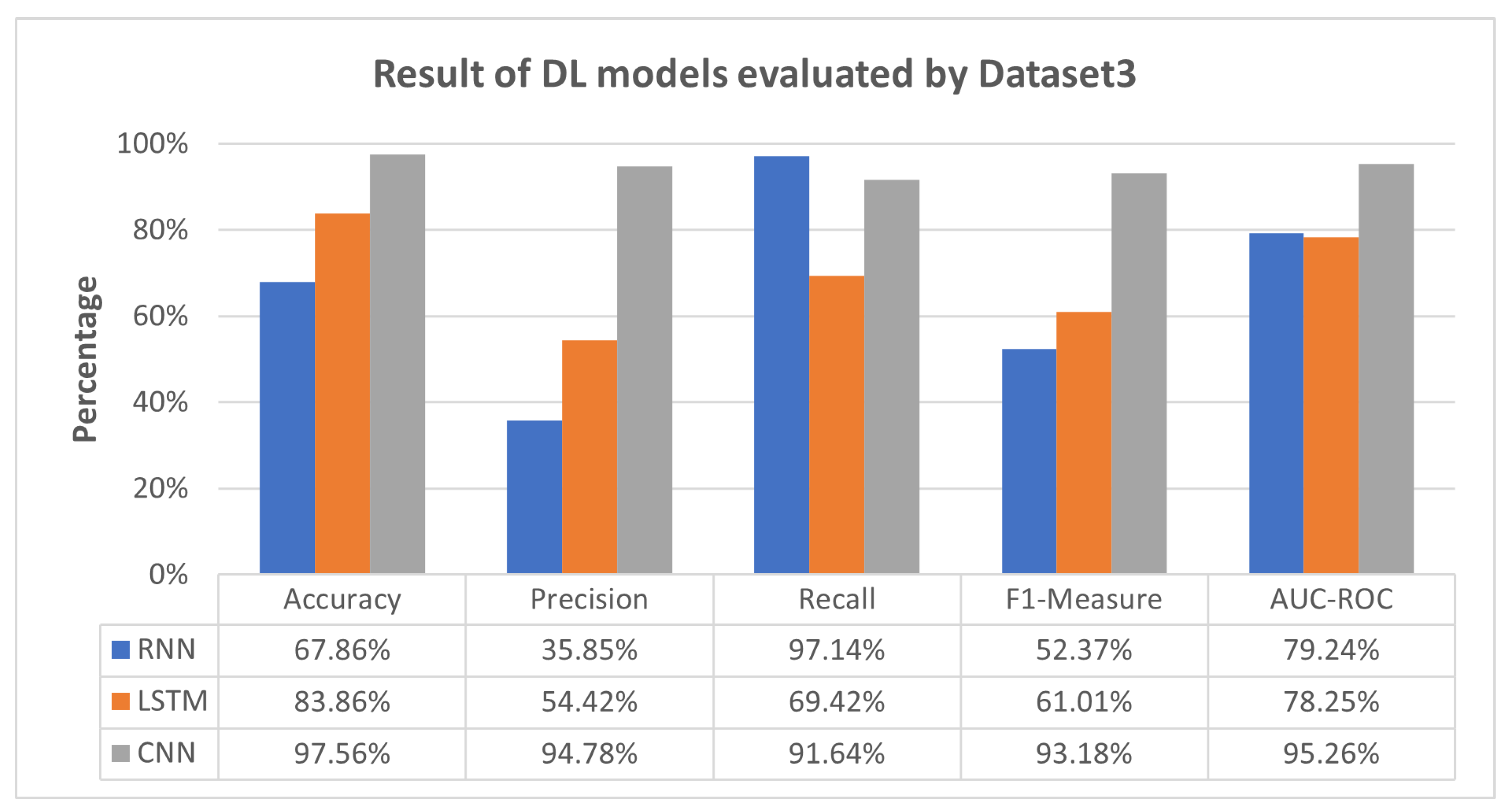
5.3. The Performance of DL Models
5.4. Discussion
6. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bahashwan, A.A.; Anbar, M.; Abdullah, N.; Al-Hadhrami, T.; Hanshi, S.M. Review on Common IoT Communication Technologies for Both Long-Range Network (LPWAN) and Short-Range Network. In Advances on Smart and Soft Computing; Springer: Singapore, 2021; pp. 341–353. [Google Scholar]
- Noor, M.b.M.; Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Inayat, U.; Zia, M.F.; Mahmood, S.; Khalid, H.M.; Benbouzid, M. Learning-based methods for cyber attacks detection in IoT systems: A survey on methods, analysis, and future prospects. Electronics 2022, 11, 1502. [Google Scholar] [CrossRef]
- Zhang, H.; Li, J.L.; Liu, X.M.; Dong, C. Multi-dimensional feature fusion and stacking ensemble mechanism for network intrusion detection. Future Gener. Comput. Syst. 2021, 122, 130–143. [Google Scholar] [CrossRef]
- Gao, X.; Shan, C.; Hu, C.; Niu, Z.; Liu, Z. An adaptive ensemble machine learning model for intrusion detection. IEEE Access 2019, 7, 82512–82521. [Google Scholar] [CrossRef]
- Zhou, Y.; Cheng, G.; Jiang, S.; Dai, M. Building an efficient intrusion detection system based on feature selection and ensemble classifier. Comput. Netw. 2020, 174, 107247. [Google Scholar] [CrossRef]
- Chalé, M.; Bastian, N.D.; Weir, J. Algorithm selection framework for cyber attack detection. In Proceedings of the 2nd ACM Workshop on Wireless Security and Machine Learning, Linz, Austria, 13 July 2020; pp. 37–42. [Google Scholar]
- Ahsan, M.; Gomes, R.; Chowdhury, M.M.; Nygard, K.E. Enhancing machine learning prediction in cybersecurity using dynamic feature selector. J. Cybersecur. Priv. 2021, 1, 199–218. [Google Scholar] [CrossRef]
- Olasehinde, O.O.; Johnson, O.V.; Olayemi, O.C. Evaluation of selected meta learning algorithms for the prediction improvement of network intrusion detection system. In Proceedings of the 2020 International Conference in Mathematics, Computer Engineering and Computer Science (ICMCECS), Ayobo, Nigeria, 18–21 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–7. [Google Scholar]
- Xu, C.; Shen, J.; Du, X. A method of few-shot network intrusion detection based on meta-learning framework. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3540–3552. [Google Scholar] [CrossRef]
- Abu Alghanam, O.; Almobaideen, W.; Saadeh, M.; Adwan, O. An improved PIO feature selection algorithm for IoT network intrusion detection system based on ensemble learning. Expert Syst. Appl. 2023, 213, 118745. [Google Scholar] [CrossRef]
- Syed, N.F.; Ge, M.; Baig, Z. Fog-cloud based intrusion detection system using Recurrent Neural Networks and feature selection for IoT networks. Comput. Netw. 2023, 225, 109662. [Google Scholar] [CrossRef]
- Susilo, B.; Sari, R.F. Intrusion Detection in IoT Networks Using Deep Learning Algorithm. Information 2020, 11, 279. [Google Scholar] [CrossRef]
- Saba, T.; Rehman, A.; Sadad, T.; Kolivand, H.; Bahaj, S.A. Anomaly-based intrusion detection system for IoT networks through deep learning model. Comput. Electr. Eng. 2022, 99, 107810. [Google Scholar] [CrossRef]
- Ahmad, Z.; Khan, A.S.; Nisar, K.; Haider, I.; Hassan, R.; Haque, M.R.; Tarmizi, S.; Rodrigues, J.J. Anomaly detection using deep neural network for iot architecture. Appl. Sci. 2021, 11, 7050. [Google Scholar] [CrossRef]
- Yang, C.; Guan, W.; Fang, Z. IoT Botnet Attack Detection Model Based on DBO-Catboost. Appl. Sci. 2023, 13, 7169. [Google Scholar] [CrossRef]
- Regis Anne, W.; Kirubavathi, G.; Sridevi, U.K. Detection of IoT Botnet Using Machine Learning and Deep Learning Techniques. 2023. Available online: https://www.researchsquare.com/article/rs-2630988/v1 (accessed on 31 August 2023).
- Nguyen, G.L.; Dumba, B.; Ngo, Q.D.; Le, H.V.; Nguyen, T.N. A collaborative approach to early detection of IoT Botnet. Comput. Electr. Eng. 2022, 97, 107525. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.; Moschoyiannis, S.; Janicke, H. Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study. J. Inf. Secur. Appl. 2020, 50, 102419. [Google Scholar] [CrossRef]
- Alomari, E.; Manickam, S.; Gupta, B.; Singh, P.; Anbar, M. Design, deployment and use of HTTP-based botnet (HBB) testbed. In Proceedings of the 16th International Conference on Advanced Communication Technology, Pyeongchang, Republic of Korea, 16–19 February 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1265–1269. [Google Scholar]
- Alieyan, K.; Kadhum, M.M.; Anbar, M.; Rehman, S.U.; Alajmi, N.K. An overview of DDoS attacks based on DNS. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 19–21 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 276–280. [Google Scholar]
- Alashhab, Z.R.; Anbar, M.; Singh, M.M.; Hasbullah, I.H.; Jain, P.; Al-Amiedy, T.A. Distributed Denial of Service Attacks against Cloud Computing Environment: Survey, Issues, Challenges and Coherent Taxonomy. Appl. Sci. 2022, 12, 12441. [Google Scholar] [CrossRef]
- Covington, M.J.; Carskadden, R. Threat implications of the internet of things. In Proceedings of the 2013 5th international conference on cyber conflict (CYCON 2013), Tallinn, Estonia, 4–7 June 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1–12. [Google Scholar]
- Lee, R.T.; Leau, Y.B.; Park, Y.J.; Anbar, M. A survey of interest flooding attack in named-data networking: Taxonomy, performance and future research challenges. IETE Tech. Rev. 2022, 39, 1027–1045. [Google Scholar] [CrossRef]
- Saxena, S.; Bhushan, B.; Ahad, M.A. Blockchain based solutions to secure IoT: Background, integration trends and a way forward. J. Netw. Comput. Appl. 2021, 181, 103050. [Google Scholar] [CrossRef]
- Gaikwad, M.; Doke, A. Survey on Meta Learning Algorithms for Few Shot Learning. In Proceedings of the 2022 6th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 25–27 May 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1876–1879. [Google Scholar]
- Vilalta, R.; Drissi, Y. A perspective view and survey of meta-learning. Artif. Intell. Rev. 2002, 18, 77–95. [Google Scholar] [CrossRef]
- Hospedales, T.; Antoniou, A.; Micaelli, P.; Storkey, A. Meta-learning in neural networks: A survey. IEEE Trans. Pattern Anal. Mach. Intell. 2021, 44, 5149–5169. [Google Scholar] [CrossRef]
- Zoppi, T.; Ceccarelli, A.; Puccetti, T.; Bondavalli, A. Which algorithm can detect unknown attacks? Comparison of supervised, unsupervised and meta-learning algorithms for intrusion detection. Comput. Secur. 2023, 127, 103107. [Google Scholar] [CrossRef]
- Yang, A.; Lu, C.; Li, J.; Huang, X.; Ji, T.; Li, X.; Sheng, Y. Application of meta-learning in cyberspace security: A survey. Digit. Commun. Netw. 2023, 9, 67–78. [Google Scholar] [CrossRef]
- Zelaya, C.V.G. Towards explaining the effects of data preprocessing on machine learning. In Proceedings of the 2019 IEEE 35th international conference on data engineering (ICDE), Macao, China, 8–11 April 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 2086–2090. [Google Scholar]
- Huang, J.; Li, Y.F.; Xie, M. An empirical analysis of data preprocessing for machine learning-based software cost estimation. Inf. Softw. Technol. 2015, 67, 108–127. [Google Scholar] [CrossRef]
- Sherstinsky, A. Fundamentals of recurrent neural network (RNN) and long short-term memory (LSTM) network. Phys. D Nonlinear Phenom. 2020, 404, 132306. [Google Scholar] [CrossRef]
- Elejla, O.E.; Anbar, M.; Hamouda, S.; Faisal, S.; Bahashwan, A.A.; Hasbullah, I.H. Deep-Learning-Based Approach to Detect ICMPv6 Flooding DDoS Attacks on IPv6 Networks. Appl. Sci. 2022, 12, 6150. [Google Scholar] [CrossRef]
- Hochreiter, S.; Schmidhuber, J. Long short-term memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- Gu, J.; Wang, Z.; Kuen, J.; Ma, L.; Shahroudy, A.; Shuai, B.; Liu, T.; Wang, X.; Wang, G.; Cai, J.; et al. Recent advances in convolutional neural networks. Pattern Recognit. 2018, 77, 354–377. [Google Scholar] [CrossRef]
- Alabsi, B.A.; Anbar, M.; Rihan, S.D.A. CNN-CNN: Dual Convolutional Neural Network Approach for Feature Selection and Attack Detection on Internet of Things Networks. Sensors 2023, 23, 6507. [Google Scholar] [CrossRef] [PubMed]
- Soleymanzadeh, R.; Aljasim, M.; Qadeer, M.W.; Kashef, R. Cyberattack and fraud detection using ensemble stacking. AI 2022, 3, 22–36. [Google Scholar] [CrossRef]
- Rashid, M.; Kamruzzaman, J.; Imam, T.; Wibowo, S.; Gordon, S. A tree-based stacking ensemble technique with feature selection for network intrusion detection. Appl. Intell. 2022, 52, 9768–9781. [Google Scholar] [CrossRef]
- Mall, R.; Abhishek, K.; Manimurugan, S.; Shankar, A.; Kumar, A. Stacking ensemble approach for DDoS attack detection in software-defined cyber–physical systems. Comput. Electr. Eng. 2023, 107, 108635. [Google Scholar] [CrossRef]
- Wright, R.E. Logistic regression. Reading and Understanding Multivariate Statistics; American Psychological Association: Washington, DC, USA, 1995. [Google Scholar]
- Taud, H.; Mas, J. Multilayer perceptron (MLP). In Geomatic Approaches for Modeling Land Change Scenarios; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 451–455. [Google Scholar]
- Huang, S.; Cai, N.; Pacheco, P.P.; Narrandes, S.; Wang, Y.; Xu, W. Applications of support vector machine (SVM) learning in cancer genomics. Cancer Genom. Proteom. 2018, 15, 41–51. [Google Scholar]
- Chen, T.; He, T.; Benesty, M.; Khotilovich, V.; Tang, Y.; Cho, H.; Chen, K.; Mitchell, R.; Cano, I.; Zhou, T.; et al. Xgboost: Extreme gradient boosting. R Package Version 0.4-2 2015, Volume 1, pp. 1–4. Available online: https://cran.ms.unimelb.edu.au/web/packages/xgboost/vignettes/xgboost.pdf (accessed on 31 August 2023).
- Ullah, I.; Mahmoud, Q.H. A scheme for generating a dataset for anomalous activity detection in iot networks. In Proceedings of the Canadian Conference on Artificial Intelligence, Ottawa, ON, Canada, 13–15 May 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 508–520. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Tanabe, K. Pareto’s 80/20 rule and the Gaussian distribution. Phys. A Stat. Mech. Its Appl. 2018, 510, 635–640. [Google Scholar] [CrossRef]
- Zhang, J.; Pan, L.; Han, Q.L.; Chen, C.; Wen, S.; Xiang, Y. Deep learning based attack detection for cyber-physical system cybersecurity: A survey. IEEE/CAA J. Autom. Sin. 2021, 9, 377–391. [Google Scholar] [CrossRef]
- Munther, A.; Othman, R.R.; Alsaadi, A.S.; Anbar, M. A Performance Study of Hidden Markov Model and Random Forest in Internet Traffic Classification. In Proceedings of the Information Science and Applications (ICISA); Kim, K.J., Joukov, N., Eds.; Springer: Singapore, 2016; pp. 319–329. [Google Scholar]
- Sahu, A.K.; Sharma, S.; Tanveer, M.; Raja, R. Internet of Things attack detection using hybrid Deep Learning Model. Comput. Commun. 2021, 176, 146–154. [Google Scholar] [CrossRef]
- Roweis, S. EM algorithms for PCA and SPCA. In Proceedings of the 10th International Conference on Neural Information Processing Systems, Denver, CO, USA, 1 December 1997; Volume 10. [Google Scholar]
- Garcia, S.; Parmisano, A.; Erquiaga, M.J. IoT-23: A Labeled Dataset with Malicious and Benign IoT Network Traffic. 2020. Available online: https://www.stratosphereips.org/datasets-iot23 (accessed on 31 August 2023).



| Ref. | Approach and Methods | Algorithms Used | Dataset(s) | Key Findings |
|---|---|---|---|---|
| [4] | Multiple feature fusion, uniform stacking ensemble, Random Forest meta-classifier | Random Forest (RF) | Network traffic data | Ensemble approach for anomaly detection in network traffic. |
| [5] | Adaptive ensemble with decision tree, Random Forest, k-nearest neighbors, deep neural network | Decision Tree, Random Forest, k-nearest neighbors (kNN), Deep Neural Network (DNN) | NSL-KDD Test+ dataset | Ensemble for intrusion detection using majority voting and weighted decisions. |
| [6] | Heterogeneous ensemble with CFS-BA hierarchical feature extraction algorithm | Forest Penalizing Attributes, C4.5, Random Forest (RF) | Not specified | Ensemble with feature enhancement and average voting for base classifiers. |
| [7] | Meta-learning framework for algorithm selection | Meta-learning for algorithm selection | NSL-KDD dataset | Framework for algorithm selection for intrusion detection. |
| [8] | Stacked ensemble with Dynamic Feature Selector, various algorithms including CNN + LSTM, GRU, DT, RF | Dynamic Feature Selector (DFS), CNN + LSTM, Bi-directional LSTM (BiLSTM), GRU, Decision Tree (DT), Random Forest (RF) | NSL-KDD, UNSWNB15 datasets | Feature selection and ensemble approach with significant accuracy improvements. |
| [9] | Stacked ensemble with Naive Bayes, Decision Tree, meta-learning algorithms (MDT, MLR, MMT) | Naive Bayes (NB), Decision Tree (DT), Meta-learning algorithms (MDT, MLR, MMT) | UNSWNB15 dataset | Meta-learning ensemble outperforms base models for intrusion detection. |
| [10] | FC-net, meta-learning framework for intrusion detection based on deep neural networks | Deep Neural Networks (DNNs) | Not specified | Meta-learning framework with versatile intrusion detection capabilities. |
| [11] | LS-PIO ensemble for IoT security with local search algorithm | Local Search (LS) algorithm, Multiple one-class classifiers | BoT-IoT, UNSW-NB15, NSL-KDD, and 99 datasets | Ensemble with LS-PIO method surpasses other NIDS methods. |
| [12] | IoT intrusion detection framework with feature selection, RNNs (SimpleRNN, Bi-LSTM) | Recurrent Neural Networks (RNNs): SimpleRNN, Bi-directional Long Short-Term Memory (LSTM) | BoT-IoT dataset | Feature selection reduces data size while maintaining high recall rates. |
| [13] | Deep machine-learning algorithms for DoS attack detection using RF, CNN, MLP | Random Forest (RF), Convolutional Neural Network (CNN), Multilayer Perceptron (MLP) | Hash chains and IoT datasets | Deep-learning models for DoS attack detection. |
| [14] | CNN-based anomaly-based IDS for IoT with efficient IoT traffic examination | Convolutional Neural Network (CNN) | NID Dataset and BoT-IoT datasets | CNN-based model for IoT IDS with high accuracy rates. |
| [15] | MI-based anomaly detection using deep neural networks (DNNs), compared to CNN, RNN, GRU, LSTM | Deep Neural Networks (DNNs), Convolutional Neural Networks (CNN), Recurrent Neural Networks (RNNs): GRU, LSTM | IoT-Botnet 2020 dataset | DNN-based NIDS model outperforms other deep-learning models in accuracy and FAR reduction. |
| [16] | Enhanced DBO optimization of Catboost parameters for IoT-Botnet detection | Catboost | Real-world IoT traffic datasets | Optimized Catboost parameters outperform other models in accuracy and F1 score. |
| [17] | Machine-learning and deep-learning models with feature engineering for Botnet detection | Machine Learning: Support Vector Machine (SVM), Decision Tree, Random Forest, Naive Bayes; Deep Learning: Convolutional Neural Network (CNN), Gated Recurrent Unit (GRU) | IoT-23 dataset | Machine learning (SVM, Decision Tree, Random Forest) and deep-learning (CNN, GRU) models for Botnet detection. |
| [18] | Collaborative machine-learning model with multiple features for early IoT-Botnet detection | Not specified | IoT-Botnet-specific features | Collaborative model for early IoT-Botnet detection with high accuracy. |
| [19] | Deep learning for cyber security intrusion detection | RNN, DNNs, restricted Boltzmann machines, deep belief networks, CNNs | BoT-IoT | Deep-learning models for IoT-Botnet detection with high accuracy. |
| Attack Type | Description |
|---|---|
| Device spoofing | Malicious actors impersonate legitimate IoT devices to gain unauthorized access to networks or services. This can lead to data breaches and unauthorized control. |
| Firmware exploitation | Attackers target vulnerabilities in IoT device firmware, exploiting them to compromise device functionality or gain unauthorized access. |
| Data manipulation | Tampering with data transmitted between IoT devices leads to the dissemination of false information or unauthorized control. This can disrupt operations and compromise data integrity. |
| Insider threats | Malicious actions by individuals with legitimate access to IoT devices or networks. Detecting and mitigating insider threats is crucial for IoT security. |
| Physical attacks | Involves theft, tampering, or physical damage to IoT devices, leading to security breaches. These attacks can compromise the physical integrity of IoT systems. |
| IoT-Botnet | Botnets of compromised IoT devices are used for various malicious purposes, including DDoS attacks, spam, and malware distribution. IoT botnets exploit vulnerabilities in IoT devices, posing a significant challenge to security. |
| Challenge | Description |
|---|---|
| Data Volume | The extensive use of IoT applications such as smart cities and grids generates vast amounts of sensitive data, which in turn exposes these systems to various security risks and vulnerabilities. |
| Privacy Protection | IoT nodes contain sensitive data that must be safeguarded against identification and traceability. Privacy is a top concern as enterprises continuously process and use data via IoT devices. |
| Resource Limitations | IoT devices often come with limited computational power and memory resources, which presents a significant challenge when it comes to implementing and maintaining standard security protocols. |
| Scalability | The IoT system involves numerous entities, requiring scalable confidentiality and security measures across the network. |
| Heterogeneity | IoT connects diverse devices with varying complexities, capabilities, and technical specifications. Protocols must support these differences to ensure connectivity. |
| Interoperability | It’s crucial for security procedures within IoT systems to be designed in a way that does not compromise the operational capabilities of IoT nodes. Inadequate interoperability between security measures and IoT devices can result in technical problems and ultimately lead to user dissatisfaction. |
| Autonomous control | IoT networks should autonomously configure settings in end devices, eliminating the need for user intervention. |
| Attack Resistance | IoT end devices are often small and lack physical protection, making them vulnerable to natural disasters and sensor damage. |
| Category | Value |
|---|---|
| Total count of normal rows | 40,073 |
| Total count of attack rows | 585,710 |
| Total count of rows (normal+attack) | 625,783 |
| Total count of features | 85 |
| Attack Name | Number of Records |
|---|---|
| Mirai-UDP Flooding | 183,554 |
| Mirai-Hostbruteforceg | 121,181 |
| DoS-Synflooding | 59,391 |
| Mirai-HTTP Flooding | 55,818 |
| Mirai-Ackflooding | 55,124 |
| Scan Port OS | 53,073 |
| MITM ARP Spoofing | 35,377 |
| Scan Hostport | 22,192 |
| Dataset | Training Dataset (80%) | Testing Dataset (20%) |
|---|---|---|
| Dataset 1 Mirai-UDP Flooding | 178,901 | 44,725 |
| Dataset 2 Mirai-Hostbruteforceg | 129,002 | 32,251 |
| Dataset 3 Mirai-HTTP Flooding | 76,664 | 19,196 |
| Testing Dataset | Algorithm | Accuracy | Precision | Recall | F1-Measure | AUC-ROC | |
|---|---|---|---|---|---|---|---|
| Dataset 2 | DNN [15] | 85.47% | 90.43% | 90.22% | 90.22% | 80.67% | |
| Proposed meta-learner | LR | 94.51% | 92.20% | 90.82% | 91.50% | 93.55% | |
| MLP | 94.37% | 91.12% | 91.62% | 91.37% | 93.66% | ||
| SVM | 94.62% | 92.34% | 91.02% | 91.67% | 93.69% | ||
| XGB | 94.97% | 92.22% | 92.32% | 92.27% | 94.28% | ||
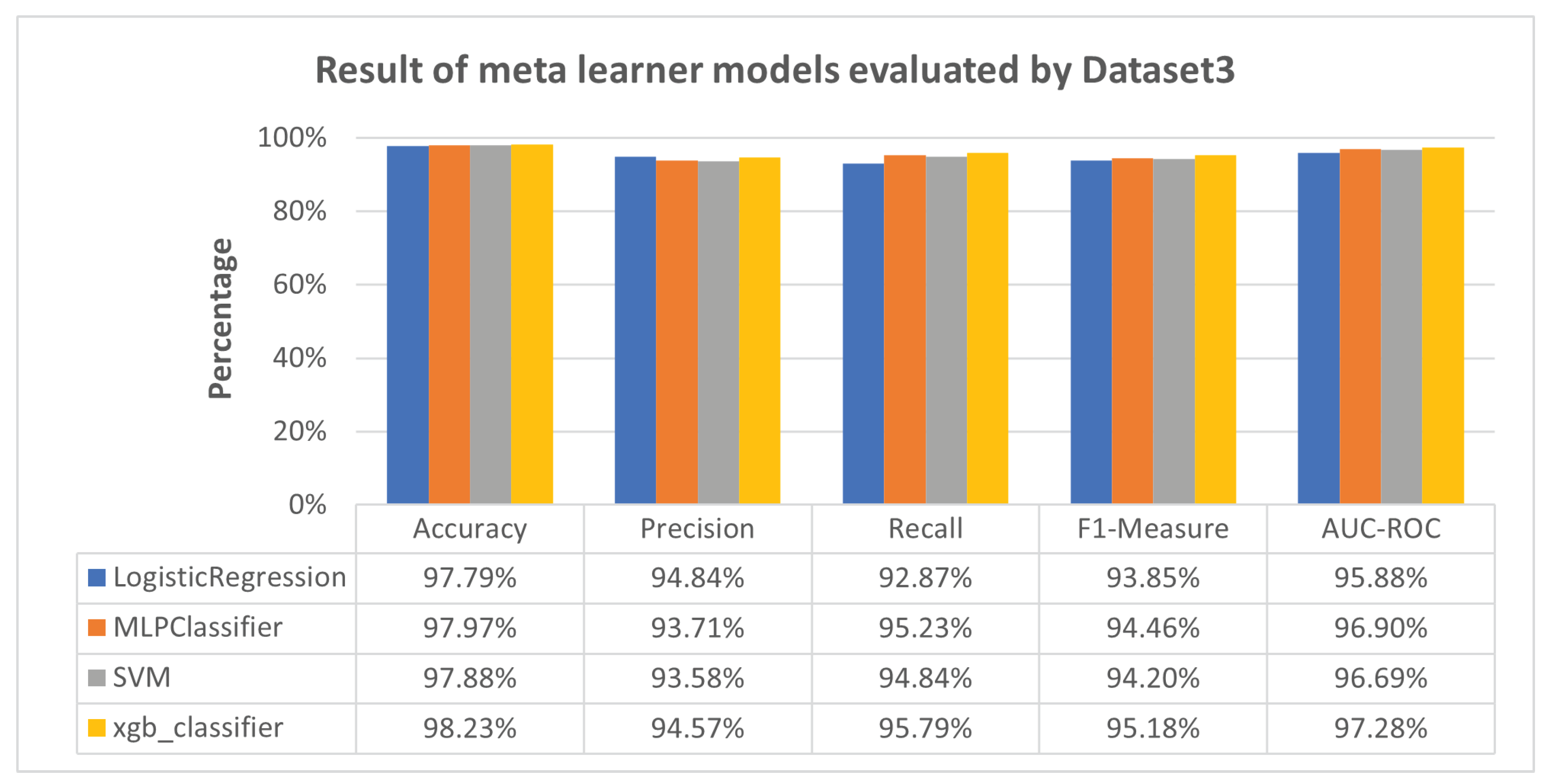
| Dataset 3 | DNN [15] | 72.78% | 69.93% | 93.38% | 79.97% | 68.73% | |
| Proposed meta-learner | LR | 97.79% | 94.84% | 92.87% | 93.85% | 95.88% | |
| MLP | 97.97% | 93.71% | 95.23% | 94.46% | 96.90% | ||
| SVM | 97.88% | 93.58% | 94.84% | 94.20% | 96.69% | ||
| XGB | 98.23% | 94.57% | 95.79% | 95.18% | 97.28% | ||
| Dataset | Classifier | Accuracy |
|---|---|---|
| Work in [19] | ||
| BoT-IoT [46] | DNN | 96.611% |
| RNN | 96.877% | |
| CNN | 96.919% | |
| Work in [16] | ||
| BoT-IoT [46] | IDBO-Catboost | 98.62% |
| Botnet [51] | IDBO-Catboost | 96.10% |
| Work in [17] | ||
| IoT-23 [52] | CNN | 96.69% |
| GRU | 99.87% | |
| Proposed work | ||
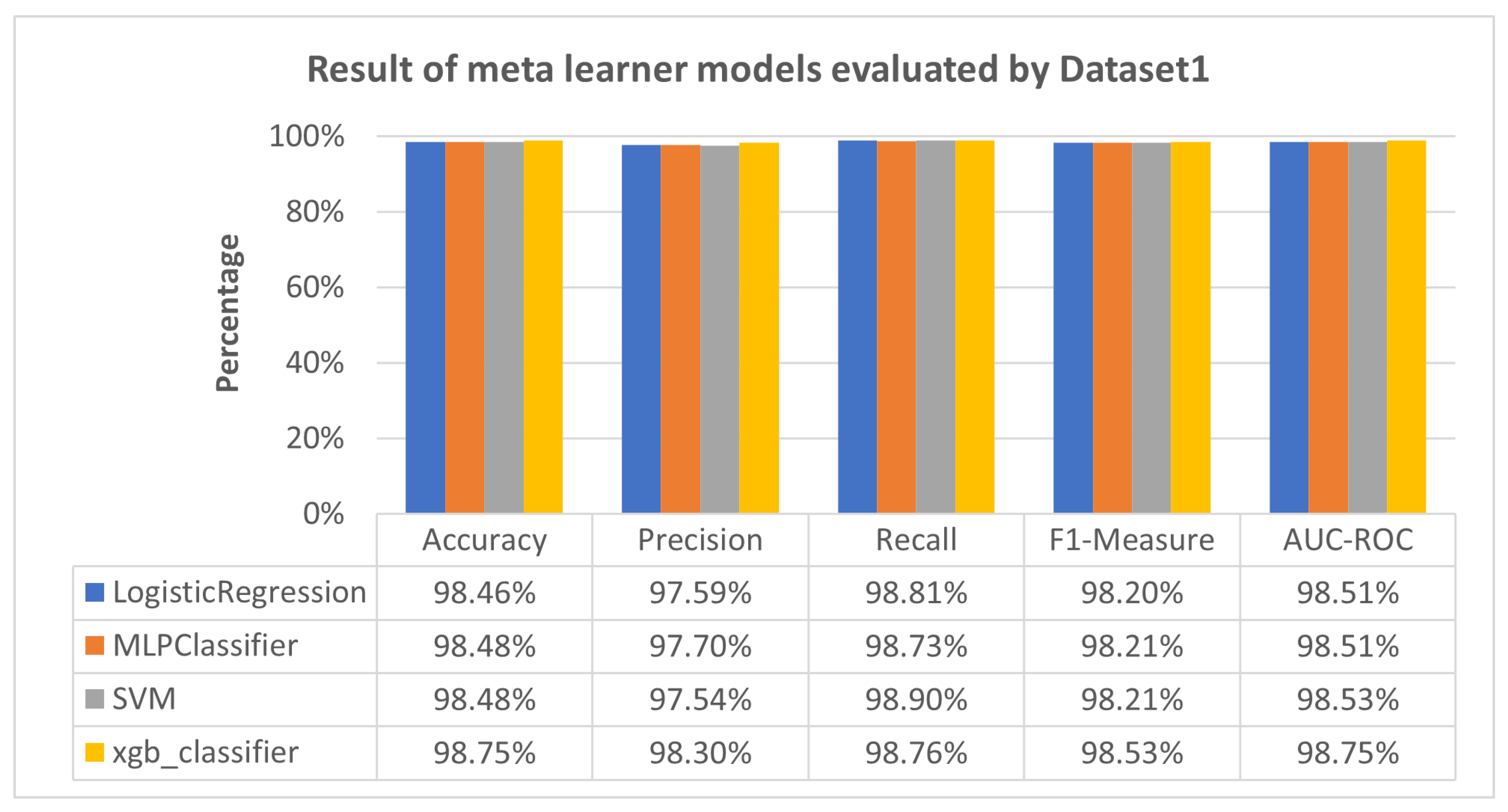
| IoT-Botnet 2020 [45] | LogisticRegression | 98.46% |
| MLPClassifier | 98.48% | |
| SVM | 98.48% | |
| xgb_classifier | 98.75% | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rihan, S.D.A.; Anbar, M.; Alabsi, B.A. Meta-Learner-Based Approach for Detecting Attacks on Internet of Things Networks. Sensors 2023, 23, 8191. https://doi.org/10.3390/s23198191
Rihan SDA, Anbar M, Alabsi BA. Meta-Learner-Based Approach for Detecting Attacks on Internet of Things Networks. Sensors. 2023; 23(19):8191. https://doi.org/10.3390/s23198191
Chicago/Turabian StyleRihan, Shaza Dawood Ahmed, Mohammed Anbar, and Basim Ahmad Alabsi. 2023. "Meta-Learner-Based Approach for Detecting Attacks on Internet of Things Networks" Sensors 23, no. 19: 8191. https://doi.org/10.3390/s23198191
APA StyleRihan, S. D. A., Anbar, M., & Alabsi, B. A. (2023). Meta-Learner-Based Approach for Detecting Attacks on Internet of Things Networks. Sensors, 23(19), 8191. https://doi.org/10.3390/s23198191






