A Novel Efficient Dynamic Throttling Strategy for Blockchain-Based Intrusion Detection Systems in 6G-Enabled VSNs
Abstract
:1. Introduction
1.1. Main Scope and Contributions
- We propose a novel ledger-query strategy, named “Dynamic Throttling Strategy”, that not only works best for the BCDID use case but can be leveraged widely by blockchain networks when simple key–value queries with substantial amounts of data and users are the basic characteristics of these networks.
- We show that the proposed BCDID can be applied in the new VSN context with some modifications to deal with the large number of nodes since the approach proposed in [7] was only tested in a small-scale network. Hence, we address the performance limitations in large-scale application contexts like VSNs and conduct performance analysis to show how our proposed solution can cope and excel in the case of a large number of endpoints in VSNs.
1.2. Literature Review—Collaborative Intrusion Detection Systems
1.2.1. CIDSs Architectures
1.2.2. Alert Correlation
1.2.3. Alert Trustworthiness
2. Blockchain-Based Collaborative Distributed Intrusion Detection (BCDID) System
2.1. Building Blocks and System Model
- query peer ledgers and access information, or
- invoke, namely, create new transactions.
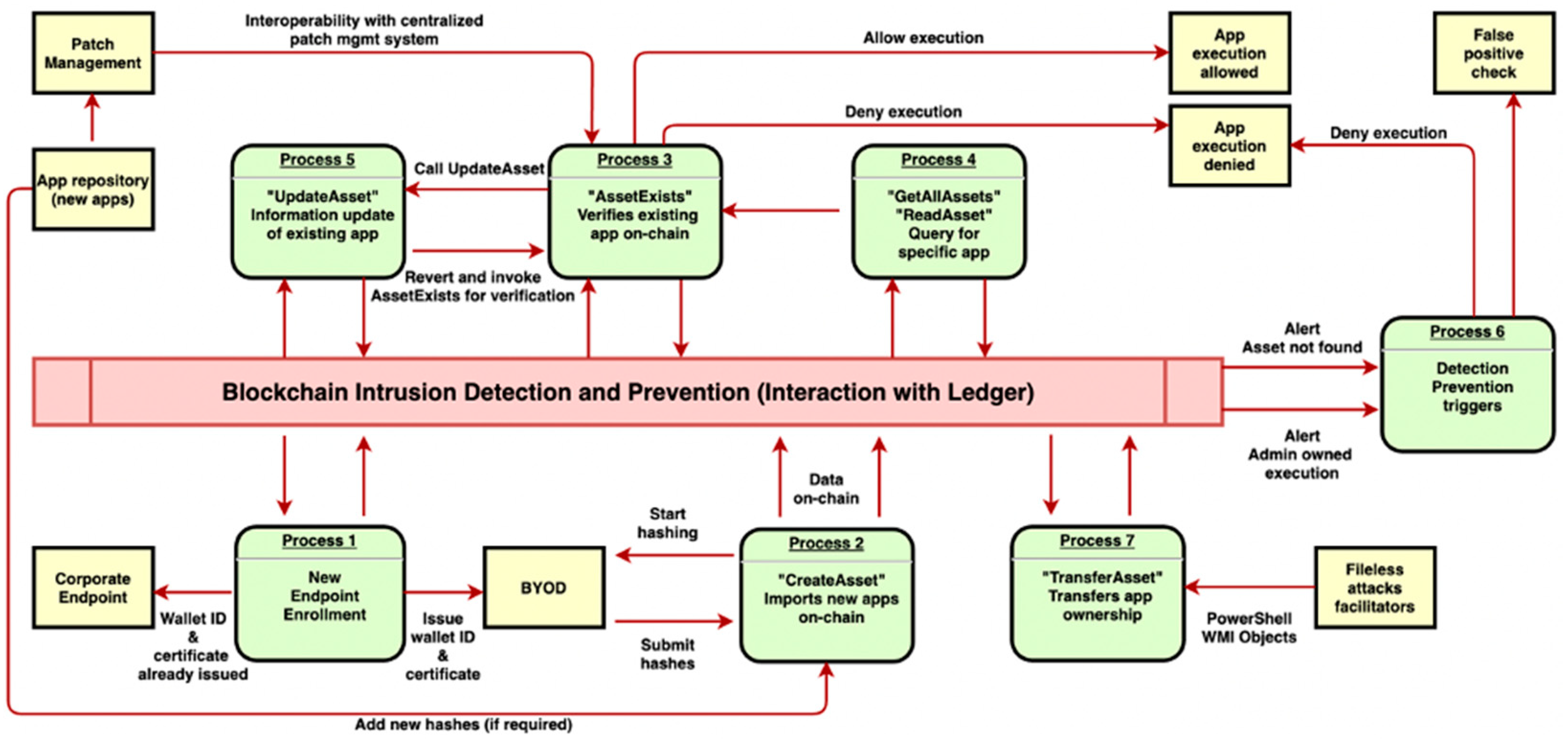
Operation Processes
- Process 1—New endpoint enrolment: At the beginning and whenever the installation of new media devices in the vehicles happens, these new endpoints are enrolled.
- Process 2—Import new apps on-chain: This process utilises the so-called “CreateAsset” app function and chain code, which enables newly hashed social application information to be transferred and recorded on-chain, providing immutability.
- Process 3—Verify existing apps on-chain: This is the core element of whitelisting the “benign” applications, where the presence of an app’s information on the chain is verified, and the execution of the app can be denied if the information is not on the chain. For this, we define the so-called “AssetExists” app function.
- Process 4—Query for a specific app(s): To manually verify the on-chain presence of applications or request certain information for incident triaging, we define “GetAllAssets” or “ReadAsset” apps functions and chaincodes. These allow an administrator to query the ledger for specific information.
- Process 5—Update existing app(s) information: To update certain information fields of applications on-chain, we define the app function and chaincode called “UpdateAsset”.
- Process 6—Detection and prevention triggers: If an app is trying to execute without the relevant data being present on-chain, then an alert is generated. We generate two types of alerts: (1) when an app is trying to execute without the relevant data being present on-chain, and (2) when an admin-owned app (see Process 7 below) is trying to execute. Both cases indicate a potential intrusion. Nonetheless, alerts and rules can be configured and further refined at a later stage to include countless cases.
- Process 7—Transfer app(s) ownership: To transfer the ownership of apps on-chain, we define the app function and chaincode called “TransferAsset”, which creates a sequence and reference in the form of transactions.
2.2. Blockchain-Based Collaborative Distributed Intrusion Detection Mechanism
2.3. Performance Issues
- Transaction proposal: A user belonging to OrgHQ executes a single application chrome.exe, which automatically triggers the “AssetExists” chaincode and therefore submits a signed response with the user’s certificate-transaction proposal to the endorsing organisation OrgHQ peer(s).
- Transaction execution: peer0 belonging to OrgHQ executes the chaincode “ReadAsset” specified in the proposal and generates a proposal response which contains the read-write set. The response is signed by peer0 and is sent back to the user.
- In case the output matches the input, namely, the current hash of chrome.exe is identical to the one existing on-chain, chrome.exe will be allowed execution.
- In case the output of “ReadAsset” returns a hash mismatch, chrome.exe will be denied execution.
- Additionally, an intrusion alert will be triggered, and Process 6 will begin (see Figure 1).
- Transaction endorsement: the transaction will be executed repeatedly for each organisation required by the chaincode endorsement policy. Responses are collected and signed.
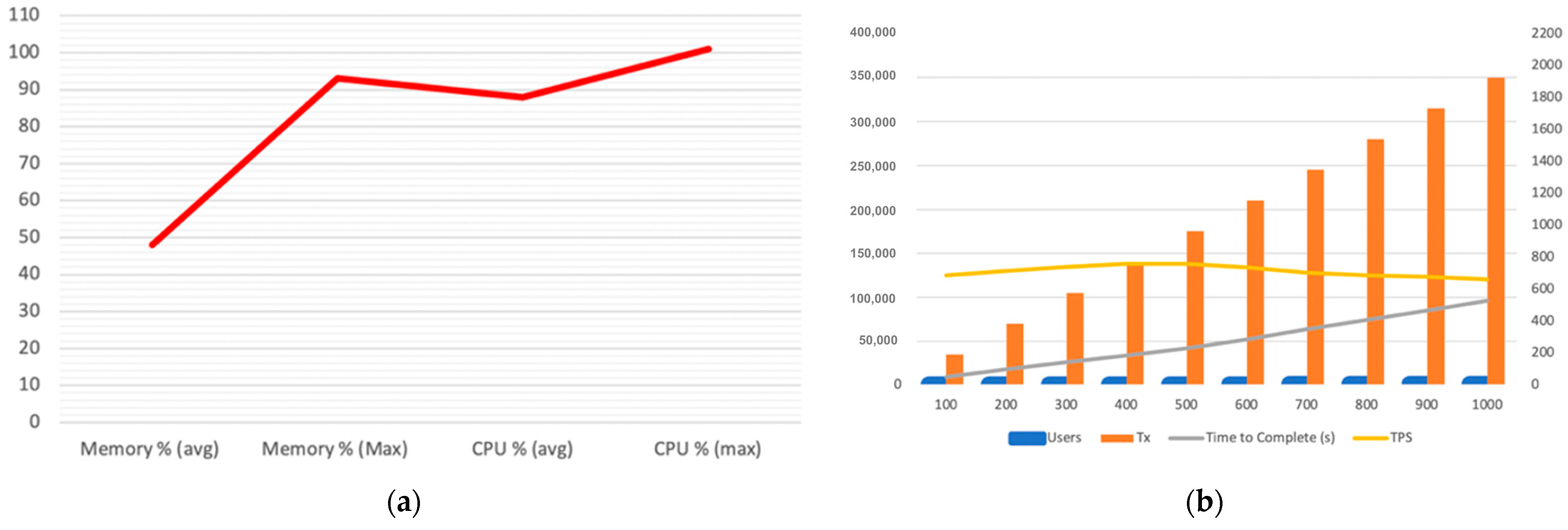
- Observation 1: a performance bottleneck occurs when 400 or more users attempt simultaneous execution, which hinders user experience by significantly increasing the launch time of an application, and thereby the waiting time.
- Observation 2: even before the 400-user threshold, the CPU already operates at 90% usage on average, while the more load we add, the faster it reaches 100% of usage. This causes a resource utilisation problem that ultimately adds up to Observation 1.
2.4. Hyperledger Fabric Performance Related Work
2.5. A Novel Dynamic Throttling Approach to Enhance the BCDID’s Performance
- PREFER_MSPID_SCOPE_SINGLE: evaluates all transactions using the first peer of an organisation that can provide a response. It only switches to another peer if the first peer fails to provide a response for any reason. If the organisation has no peers, then it falls back to all peers specified in the network configuration file.
- ○
- MSPID_SCOPE_SINGLE: follows similar principles as per the above strategy; however, in case of no available peers or no peers at all, the fall-back strategy is to fail exit rather than falling back to all peers within the network configuration file.
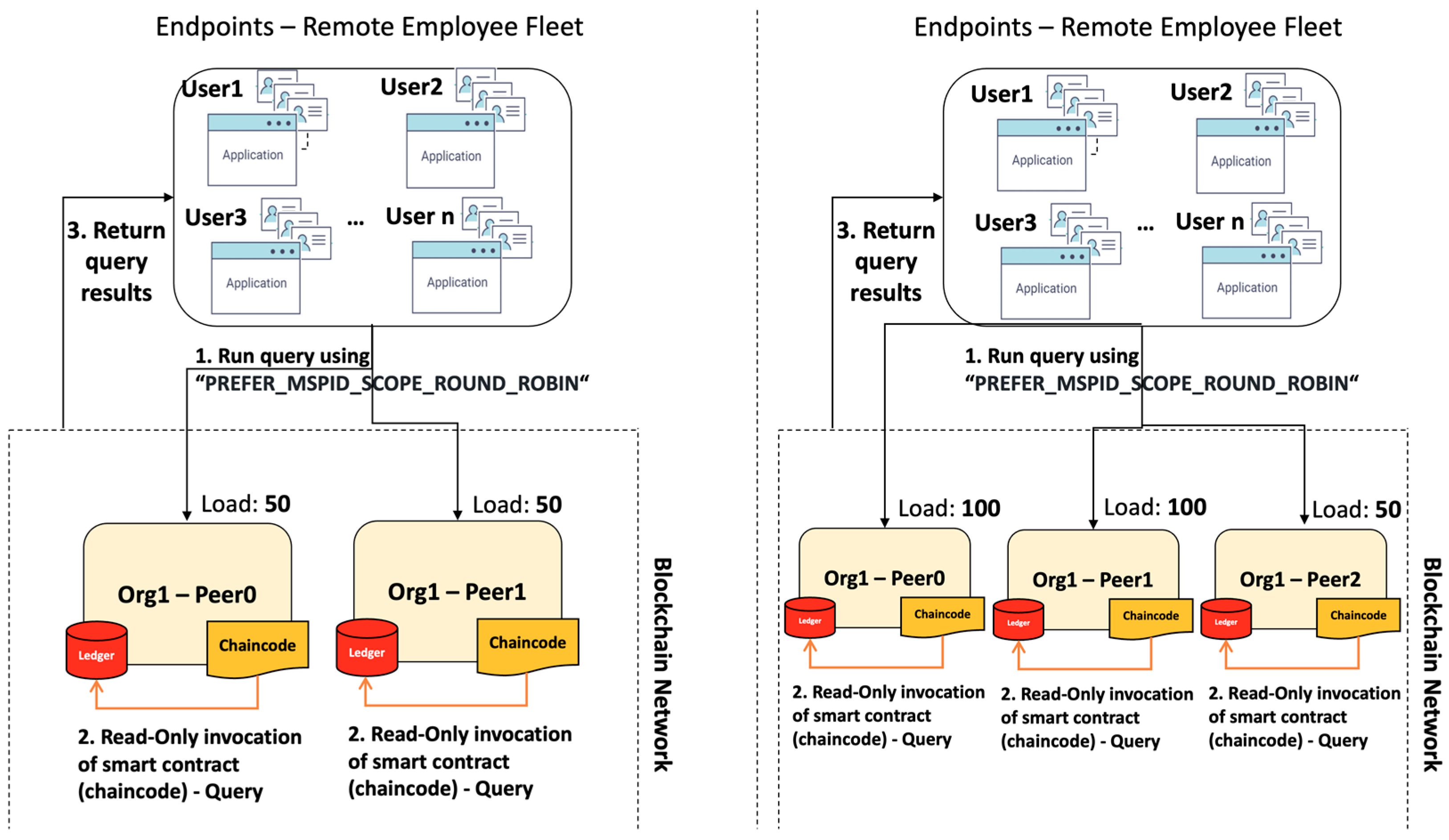
- PREFER_MSPID_SCOPE_ROUND_ROBIN: evaluates a transaction based on the list of peers, starting with the first on that list. Peers will be engaged in order until a response is received or until all peers have been engaged. On the next query, the second peer on the list will be engaged first, and then continue in the list of peers until a response is received. This is an incremental loading strategy that distributes the workload among all responding peers.
- ○
- MSPID_SCOPE_ROUND_ROBIN: follows similar principles as per the above strategy; however, it will fail exit when there are no peers available on the organisation’s list, rather than falling back to all peers within the network configuration file.
2.6. Dynamic Throttling Strategy (DTS)
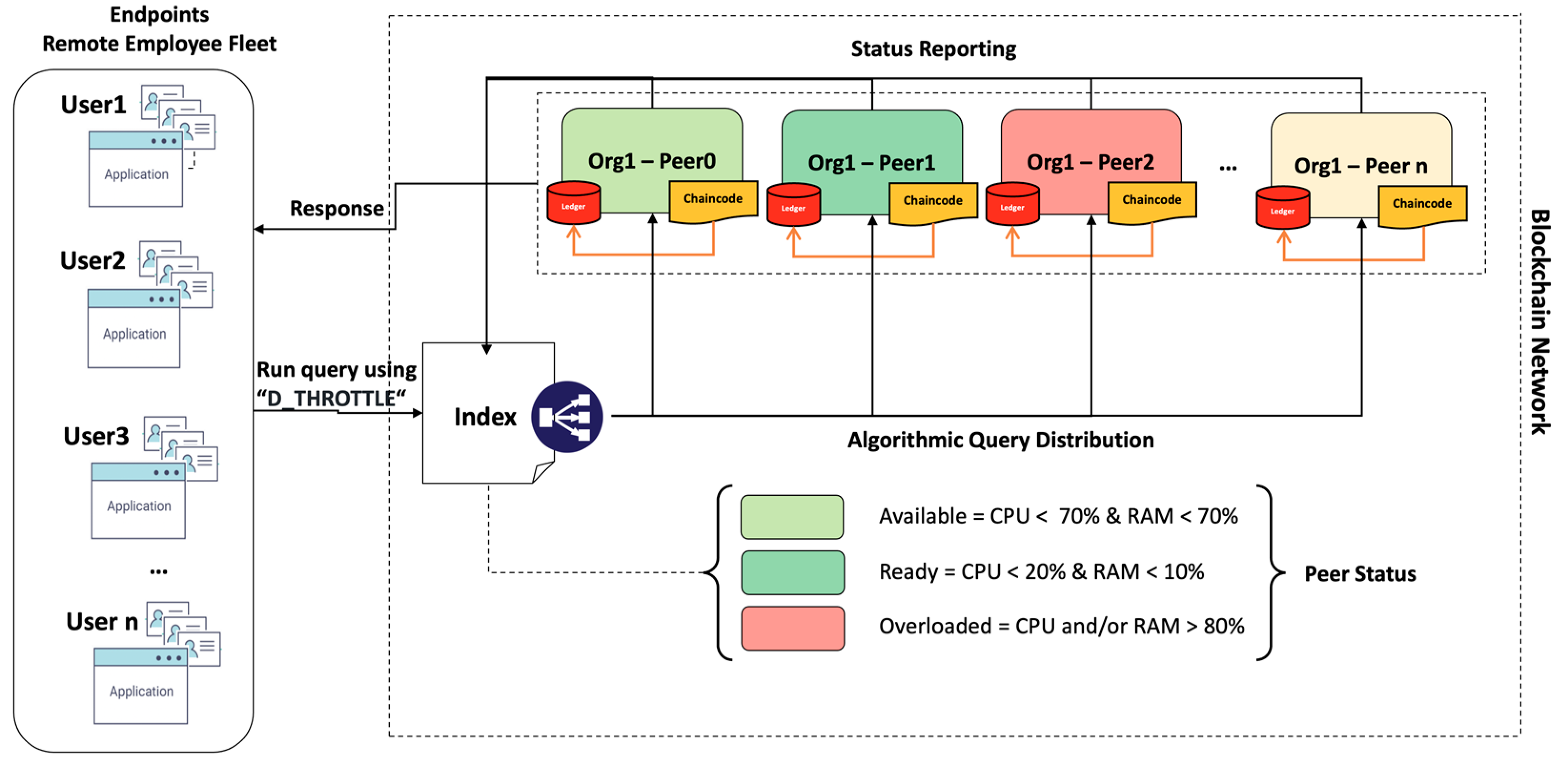
- The peer environment indexing and monitoring is as shown in Figure 3. We define three peer status tags based on our previous observations and measurements of 100–1000 users and up to 350k Tx’s. The peer status definition allows for a generalisation at this point based on the observed loading pattern of a single peer. Nonetheless, a 10% safety threshold for peers tagged as “available” is added. This means that peers in the mentioned state will still be able to manage queries without failures, as a single request will never consume more than 10% of a single peer resource. We also introduce a separate VM that hosts the index of peers’ reports of their CPU and RAM consumption in real-time to the peer index. Peers report in real-time their CPU and RAM consumption; therefore, the index controls the query distribution based on the algorithm. The response is sent directly back to the user.
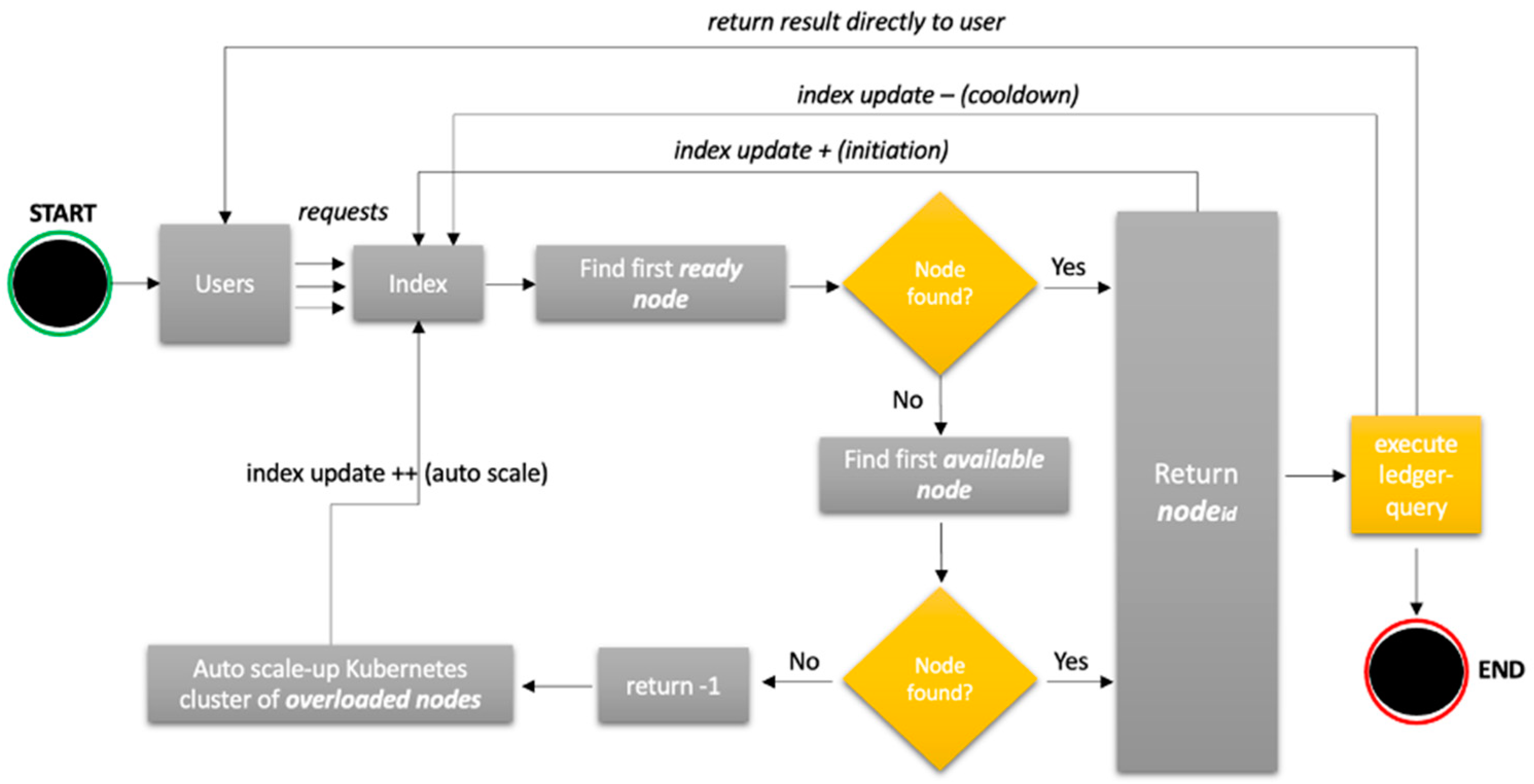
- The dynamic throttling algorithm, as shown in Figure 4 above, is embedded in the blockchain network operating as our own query strategy. The users perform a substantial number of queries in parallel using the “D_THROTTLE” strategy, which triggers the dynamic throttling algorithm. Upon the successful identification of the first available node in a ready state, the index will assign the query to a subject node, while the node id will be registered, and the index will be updated (update +). Once the query is executed, results are returned directly to the user, and the node sends a cooldown signal updating the index (update −) with the current resource status. In the case that a node in a ready state is not available, the same flow will occur, but the index will search for the first available node this time. Conversely, if there is no node in an available state, the index returns error code −1, and the auto scale-up procedure begins to add resources to nodes currently marked as overloaded and updates the index accordingly.
3. Results and Discussion
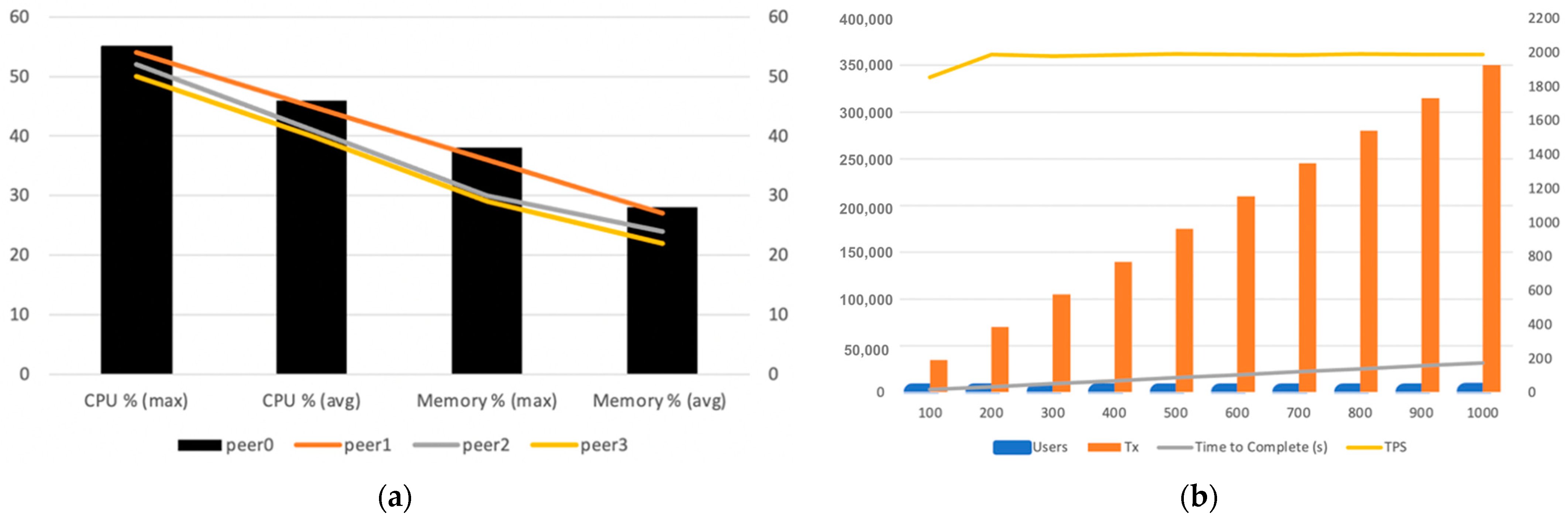
- Observation 1: by adding more nodes and using the “D_THROTTLE” algorithm, we managed to increase considerably the number of Transactions Per Second (TPS) up to 1991, which is double that of the default strategy; see Figure 6b.
- Observation 2: CPU and memory performance on all peers showed a declining trendline for all four peers. Moreover, none of the peers exceeded the 80% threshold to be marked as overloaded, while the average CPU usage for all peers ranged between 40% to 46%. This demonstrates a significant improvement in resource handling compared to the default strategy; see Figure 6a.
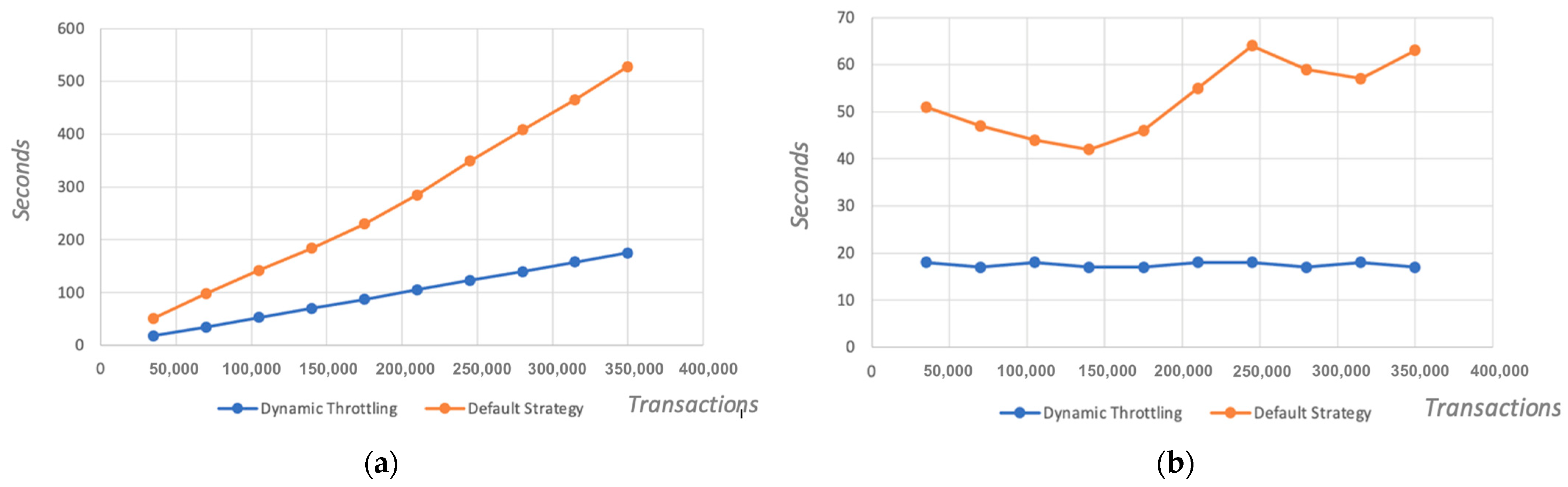
- Observation 3: the overall time to completion comparison chart highlights (1) that the dynamic throttling strategy is significantly faster than without it, and (2) that the more transactions received, a much smoother increase in time is anticipated, compared to the default query strategy; see Figure 7b.
- Observation 4: the time to completion per additional 50k queries is a steady line ranging between 17 to 18 s while using dynamic throttling, proving effective and efficient load balancing. While using the default strategy, however, the time to completion for the first 100 users measured up to 50 s, and it is evident that the peer is quickly allocating resources to complete the transactions but while reaching its threshold the time increases drastically beyond 60 s. Furthermore, once the peer finalises several transactions and frees some resources, there is a slight improvement in performance, yet again allocating all resources and quickly reaching the threshold, eventually leading to delays, as the pattern suggests; see Figure 7a.
4. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Luan, T.H.; Lu, R.; Shen, X.; Bai, F. Social on the road: Enabling secure and efficient social networking on highways. IEEE Wirel. Commun. 2015, 22, 44–51. [Google Scholar] [CrossRef]
- TripAdvisor Inc. TripAdvisor Survey Reveals Three Quarters of U.S. Travelers Sharing Trip Experiences on Social Networks. Available online: https://tripadvisor.mediaroom.com/2012-09-20-TripAdvisor-Survey-Reveals-Three-Quarters-Of-U-S-Travelers-Sharing-Trip-Experiences-On-Social-Networks (accessed on 20 September 2012).
- Helling, B. UberPool: How It Works, Cost, Pricing & More. Available online: https://www.ridester.com/uberpool/ (accessed on 7 April 2023).
- Luan, T.H.; Shen, X.; Bai, F.; Sun, L. Feel bored? Join Verse! Engineering vehicular proximity social networks. IEEE Trans. Veh. Technol. 2015, 64, 1120–1131. [Google Scholar] [CrossRef]
- Eiza, M.; Shi, Q. Social Evolving Graph-Based Connectivity Model for Vehicular Social Networks. In Vehicular Social Networks; CRC Press: Boca Raton, FL, USA, 2017; pp. 41–56. [Google Scholar]
- Eiza, M.; Raschellà, A. A Hybrid SDN-based Architecture for Secure and QoS aware Routing in Space-Air-Ground Integrated Networks (SAGINs). In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC 2023), Glasgow, UK, 26–29 March 2023. [Google Scholar]
- Alevizos, L.; Eiza, M.H.; Ta, V.T.; Shi, Q.; Janet, R. Blockchain-Enabled Intrusion Detection and Prevention System of APTs Within Zero Trust Architecture. IEEE Access 2022, 10, 89270–89288. [Google Scholar] [CrossRef]
- Fung, C.J.; Baysal, O.; Jie, Z.; Aib, I.; Boutaba, R. Trust Management for Host-Based Collaborative Intrusion Detection. In Proceedings of the Managing Large-Scale Service Deployment: 19th IFIP/IEEE International Workshop on Distributed Systems: Operations and Management, DSOM 2008, Samos Island, Greece, 22–26 September 2008. [Google Scholar]
- Duma, C.; Karresand, M.; Shahmehri, N.; Caronni, G. A Trust-Aware, P2P-Based Overlay for Intrusion Detection. In Proceedings of the 17th International Workshop on Database and Expert Systems Applications (DEXA’06), Krakow, Poland, 4–8 September 2006. [Google Scholar]
- Weizhi, M.; Wenjuan, L.; Lam-For, K. Design of intelligent KNN-based alarm filter using knowledge-based alert verification in intrusion detection. Secur. Commun. Netw. 2015, 8, 3883–3895. [Google Scholar]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 20, 50–62. [Google Scholar] [CrossRef]
- Wu, Y.-S.; Foo, B.; Mei, Y.; Bagchi, S. Collaborative Intrusion Detection System (CIDS): A Framework for Accurate and Efficient IDS. In Proceedings of the 19th Annual Computer Security Applications Conference, Las Vegas, NV, USA, 8–12 December 2003. [Google Scholar]
- Nandy, T.; Noor, R.M.; Yamani, I.B.I.; Bhattacharyya, S. T-BCIDS: Trust-Based Collaborative Intrusion Detection System for VANET. In Proceedings of the 2020 National Conference on Emerging Trends on Sustainable Technology and Engineering Applications (NCETSTEA), Durgapur, India, 7–8 February 2020. [Google Scholar]
- Zhou, M.; Han, L.; Lu, H.; Fu, C. Distributed collaborative intrusion detection system for vehicular Ad Hoc networks based on invariant. Comput. Netw. 2020, 172, 122–143. [Google Scholar] [CrossRef]
- Zhang, T.; Zhu, Q. Distributed Privacy-Preserving Collaborative Intrusion Detection Systems for VANETs. IEEE Trans. Signal Inf. Process. Over Netw. 2018, 4, 148–161. [Google Scholar] [CrossRef]
- Nie, L.; Ning, Z.; Wang, X.; Hu, X.; Cheng, J.; Li, Y. Data-Driven Intrusion Detection for Intelligent Internet of Vehicles: A Deep Convolutional Neural Network-Based Method. IEEE Trans. Netw. Sci. Eng. 2020, 7, 2219–2230. [Google Scholar] [CrossRef]
- Anzer, A.; Elhadef, M. A Multilayer Perceptron-Based Distributed Intrusion Detection System for Internet of Vehicles. In Proceedings of the IEEE 4th International Conference on Collaboration and Internet Computing (CIC), Philadelphia, PA, USA, 18–20 October 2018. [Google Scholar]
- Man, D.; Zeng, F.; Lv, J.; Xuan, S.; Yang, W.; Guizani, M. AI-based Intrusion Detection for Intelligence Internet of Vehicles. IEEE Consum. Electron. Mag. 2023, 12, 109–116. [Google Scholar] [CrossRef]
- Benaddi, H.; Ibrahimi, K. A Review: Collaborative Intrusion Detection for IoT integrating the Blockchain technologies. In Proceedings of the 8th International Conference on Wireless Networks and Mobile Communications (WINCOM), Reims, France, 27–29 October 2020. [Google Scholar]
- Li, W.; Tug, S.; Meng, W.; Wang, Y. Designing collaborative blockchained signature-based intrusion detection in IoT environments. Future Gener. Comput. Syst. 2019, 96, 481–489. [Google Scholar] [CrossRef]
- Li, W.; Meng, W. Collaborative Intrusion Detection in the Era of IoT: Recent Advances and Challenges. In Security and Privacy in the Internet of Things; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2021; pp. 123–149. [Google Scholar]
- Alshahrani, H.M. CoLL-IoT: A Collaborative Intruder Detection System for Internet of Things Devices. Electronics 2021, 10, 848. [Google Scholar] [CrossRef]
- Razaque, A.; Bektemyssova, G.; Yoo, J.; Alotaibi, A.; Ali, M.; Amsaad, F.; Amanzholova, S.; Alshammari, M. Malicious Vehicle Detection Using Layer-Based Paradigm and the Internet of Things. Sensors 2023, 23, 6554. [Google Scholar] [CrossRef] [PubMed]
- Shakerian, A.; Eghmazi, A.; Goasdoué, J.; Landry, R. A Secure ZUPT-Aided Indoor Navigation System Using Blockchain in GNSS-Denied Environments. Sensors 2023, 23, 6393. [Google Scholar] [CrossRef]
- Garcia, J.; Autrel, F.; Borrell, J.; Castillo, S.; Cuppens, F.; Navarro, G. Decentralized publish-subscribe system to prevent coordinated attacks via alert correlation. In Proceedings of the Sixth International Conference on Information and Communications Security, Berlin/Heidelberg, Germany, 27–29 October 2004. [Google Scholar]
- Dash, D.; Kveton, B.; Agosta, J.M.; Schooler, E.; Chandrashekar, J.; Bachrach, A.; Newman, A. When Gossip is Good: Distributed Probabilistic Inference for Detection of Slow Network Intrusions. In Proceedings of the Twenty-First National Conference on Artificial Intelligence and the Eighteenth Innovative Applications of Artificial Intelligence Conference, Boston, MA, USA, 16–20 July 2006. [Google Scholar]
- Dain, O.; Cunningham, R.K. Fusing A Heterogeneous Alert Stream into Scenarios. In Applications of Data Mining in Computer Security; Springer: Berlin/Heidelberg, Germany, 2002; pp. 103–122. [Google Scholar]
- Cuppens, F.; Ortalo, R. LAMBDA: A Language to Model a Database for Detection of Attacks. In Proceedings of the International Workshop on Recent Advances in Intrusion Detection, Toulouse, France, 2–4 October 2000. [Google Scholar]
- Cheung, S.; Lindqvist, U.; Fong, M. Modeling multistep cyber attacks for scenario recognition. In Proceedings of the DARPA Information Survivability Conference and Exposition, Washington, DC, USA, 22–24 April 2003. [Google Scholar]
- Templeton, S.J.; Levitt, K. A requires/provides model for computer attacks. In Proceedings of the New Security Paradigms Workshop, Ballycotton, Ireland, 18–21 September 2000. [Google Scholar]
- Janakiraman, R.; Waldvogel, M.; Zhang, Q. Indra: A peer-to-peer approach to network intrusion detection and prevention. In Proceedings of the WET ICE 2003 Proceedings—Twelfth IEEE International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprises, Linz, Austria, 9–11 June 2003. [Google Scholar]
- Chen, R.; Yeager, W. Poblano A Distributed Trust Model for Peer-to-Peer Networks; IEEE: New York, NY, USA, 2001. [Google Scholar]
- Meng, W.; Tischhauser, E.W.; Wang, Q.; Wang, Y.; Han, J. When Intrusion Detection Meets Blockchain Technology: A Review. IEEE Access 2018, 6, 10179–10188. [Google Scholar] [CrossRef]
- Alexopoulos, N.; Vasilomanolakis, E.; Ivánkó, N.R.; Mühlhäuser, M. Towards Blockchain-Based Collaborative Intrusion Detection Systems. In Proceedings of the International Conference on Critical Information Infrastructures Security, Kaunas, Lithuania, 24–26 September 2018. [Google Scholar]
- Golomb, T.; Mirsky, Y.; Elovici, Y. CIoTA: Collaborative IoT Anomaly Detection via Blockchain. In Proceedings of the Workshop on Decentralized IoT Security and Standards (DISS), San Diego, CA, USA, 18 February 2018. [Google Scholar]
- Baliga, A.; Solanki, N.; Verekar, S.; Pednekar, A.; Kamat, P.; Chatterjee, S. Performance Characterization of Hyperledger Fabric. In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018. [Google Scholar]
- Pongnumkul, S.; Siripanpornchana, C.; Thajchayapong, S. Performance Analysis of Private Blockchain Platforms in Varying Workloads. In Proceedings of the 26th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017. [Google Scholar]
- Thakkar, P.; Nathan, S.; Vishwanathan, B. Performance Benchmarking and Optimizing Hyperledger Fabric Blockchain Platform. arXiv 2018, arXiv:1805.11390. [Google Scholar]
- Javaid, H.; Hu, C.; Brebner, G. Optimizing Validation Phase of Hyperledger Fabric. In Proceedings of the IEEE 27th International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems (MASCOTS), Rennes, France, 21–25 October 2019. [Google Scholar]
- Inagaki, T.; Ueda, Y.; Nakaike, T.; Ohara, M. Profile-based Detection of Layered Bottlenecks. In Proceedings of the 2019 ACM/SPEC International Conference on Performance Engineering, New York, NY, USA, 7–11 April 2019. [Google Scholar]
- Androulaki, E.B.A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; Muralidharan, S.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the EuroSys ′18: Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018. [Google Scholar]
- Gorenflo, C.; Lee, S.; Golab, L.; Keshav, S. FastFabric: Scaling Hyperledger Fabric to 20,000 Transactions per Second. arXiv 2019, arXiv:1901.00910. [Google Scholar]
- Sousa, J.; Bessani, A.; Vukolic, M. A Byzantine Fault-Tolerant Ordering Service for the Hyperledger Fabric Blockchain Platform. In Proceedings of the 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Luxembourg, 25–28 June 2018. [Google Scholar]
- Gupta, H.; Hans, S.; Mehta, S.; Jayachandran, P. On Building Efficient Temporal Indexes on Hyperledger Fabric. In Proceedings of the IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7 July 2018. [Google Scholar]
- Lu, Y.; Liu, Z.; Wang, S.; Li, Z.; Liu, W.; Chen, X. Temporal Index Scheme of Hyperledger Fabric System in IoT. Wirel. Commun. Mob. Comput. 2021, 2021, 2–13. [Google Scholar] [CrossRef]
- Foschini, L.; Gavagna, A.; Martuscelli, G.; Montanari, R. Hyperledger Fabric Blockchain: Chaincode Performance Analysis. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020. [Google Scholar]
- Yan, T.; Chen, W.; Zhao, P.; Li, Z.; Liu, A.; Zhao, L. Handling conditional queries and data storage on Hyperledger Fabric efficiently. World Wide Web 2020, 24, 441–461. [Google Scholar] [CrossRef]
- Sukhwani, H.; Wang, N.; Trivedi, K.S.; Rindos, A. Performance Modeling of Hyperledger Fabric (Permissioned Blockchain Network). In Proceedings of the 17th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 1–3 November 2018. [Google Scholar]
| Action vs. Transaction Method | Invoke | Query |
|---|---|---|
| Results in the update of world-state DB | Yes | No |
| Transaction data saved on-chain | Yes | No |
| Requires responses from multiple peers | Yes | No |
| Triggers ordering service and block creation | Yes | No |
| Operating System | Ubuntu 20.04.3 LTS (GNU/Linux 5.11.0-27-generic x86_64) |
| Hard Disk Drives | 25 GB |
| Central Processing Unit | 2.22 GHz Quad Core Intel Core i7-4770HQ |
| Random Access Memory | 6 GB |
| Software | Git, cURL, Docker, JQ, GO, Hyperledger Fabric 2.3, Ubuntu 20x basic installation with advanced package tool (APT) and APT essentials |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alevizos, L.; Ta, V.T.; Eiza, M.H. A Novel Efficient Dynamic Throttling Strategy for Blockchain-Based Intrusion Detection Systems in 6G-Enabled VSNs. Sensors 2023, 23, 8006. https://doi.org/10.3390/s23188006
Alevizos L, Ta VT, Eiza MH. A Novel Efficient Dynamic Throttling Strategy for Blockchain-Based Intrusion Detection Systems in 6G-Enabled VSNs. Sensors. 2023; 23(18):8006. https://doi.org/10.3390/s23188006
Chicago/Turabian StyleAlevizos, Lampis, Vinh Thong Ta, and Max Hashem Eiza. 2023. "A Novel Efficient Dynamic Throttling Strategy for Blockchain-Based Intrusion Detection Systems in 6G-Enabled VSNs" Sensors 23, no. 18: 8006. https://doi.org/10.3390/s23188006
APA StyleAlevizos, L., Ta, V. T., & Eiza, M. H. (2023). A Novel Efficient Dynamic Throttling Strategy for Blockchain-Based Intrusion Detection Systems in 6G-Enabled VSNs. Sensors, 23(18), 8006. https://doi.org/10.3390/s23188006






