Security–Reliability Analysis of AF Full-Duplex Relay Networks Using Self-Energy Recycling and Deep Neural Networks
Abstract
:1. Introduction
1.1. Related Work and Motivation
1.2. Contributions
- We propose a novel SWIPT-assisted AF-FD relay network to evaluate security and reliability trade-offs. In particular, in order to increase EH, the relay can harvest energy from the source and reuse the self-interference channel based on the PS protocol to attain battery-free operation;
- We derive the approximate OP for legitimate communications and the approximate IP for the eavesdropper’s channel. The asymptotic expressions for the OP and IP are also examined to give some insight into the system configuration under consideration. In order to verify the derived expressions, Monte-Carlo simulation is adopted;
- The suggested DNN performs almost as well as the simulation while drastically lowering the computing complexity. In comparison to existing machine learning-based regression models for OP/IP prediction, our suggested DNN technique has the lowest root mean square error (RMSE) and takes the shortest time to execute. When system attributes and channel circumstances vary, the data rate of the considered system can be customized based on the estimated OP/IP.
1.3. Organization
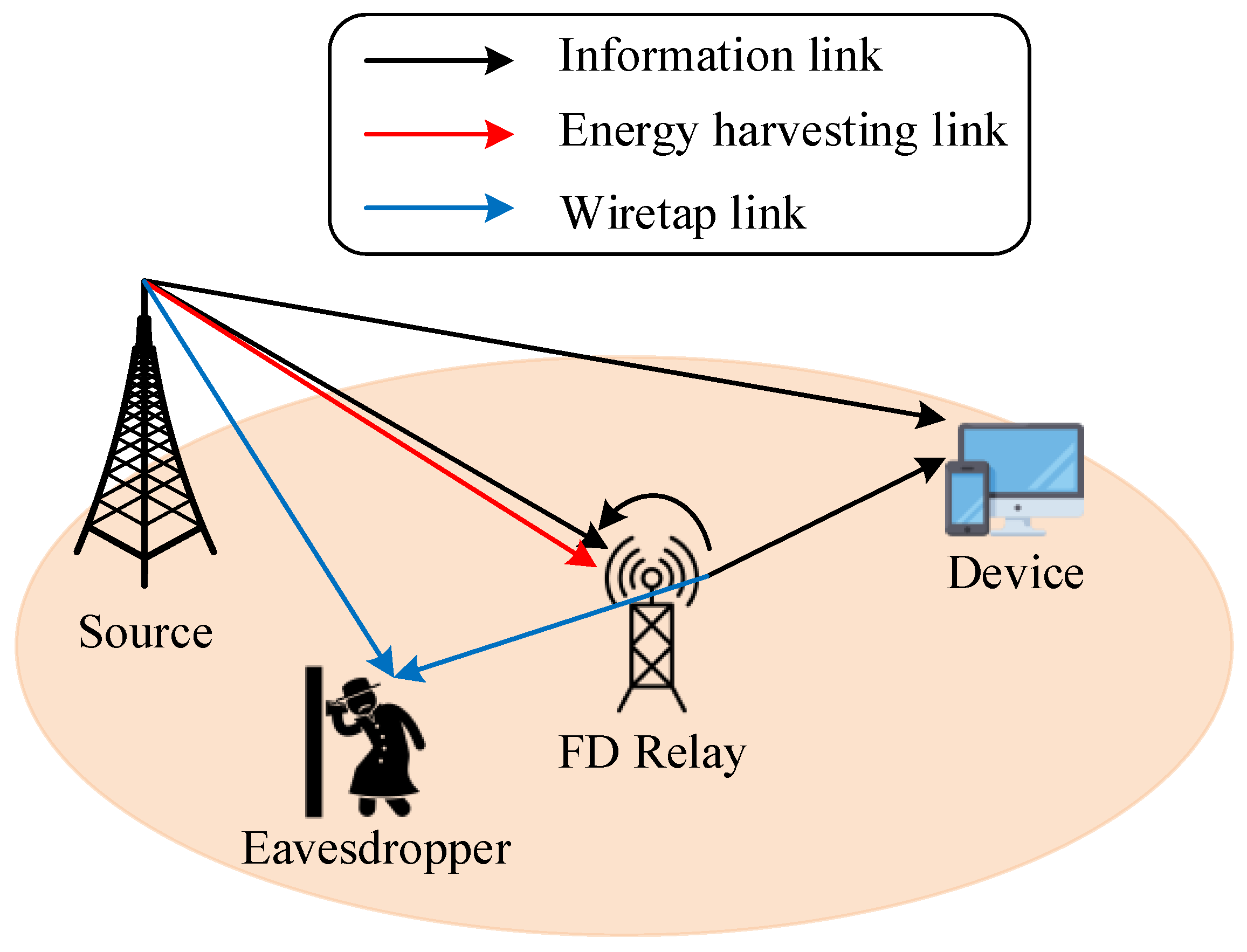
2. System Model
2.1. Energy Harvesting Model
2.2. Fading Channel Model
2.3. Transmission Model
3. Performance Analysis
3.1. Outage Probability Analysis
3.2. Intercept Probability Analysis
4. Asymptotic Analysis
4.1. Op Analysis
4.2. Ip Asymptotic Analysis
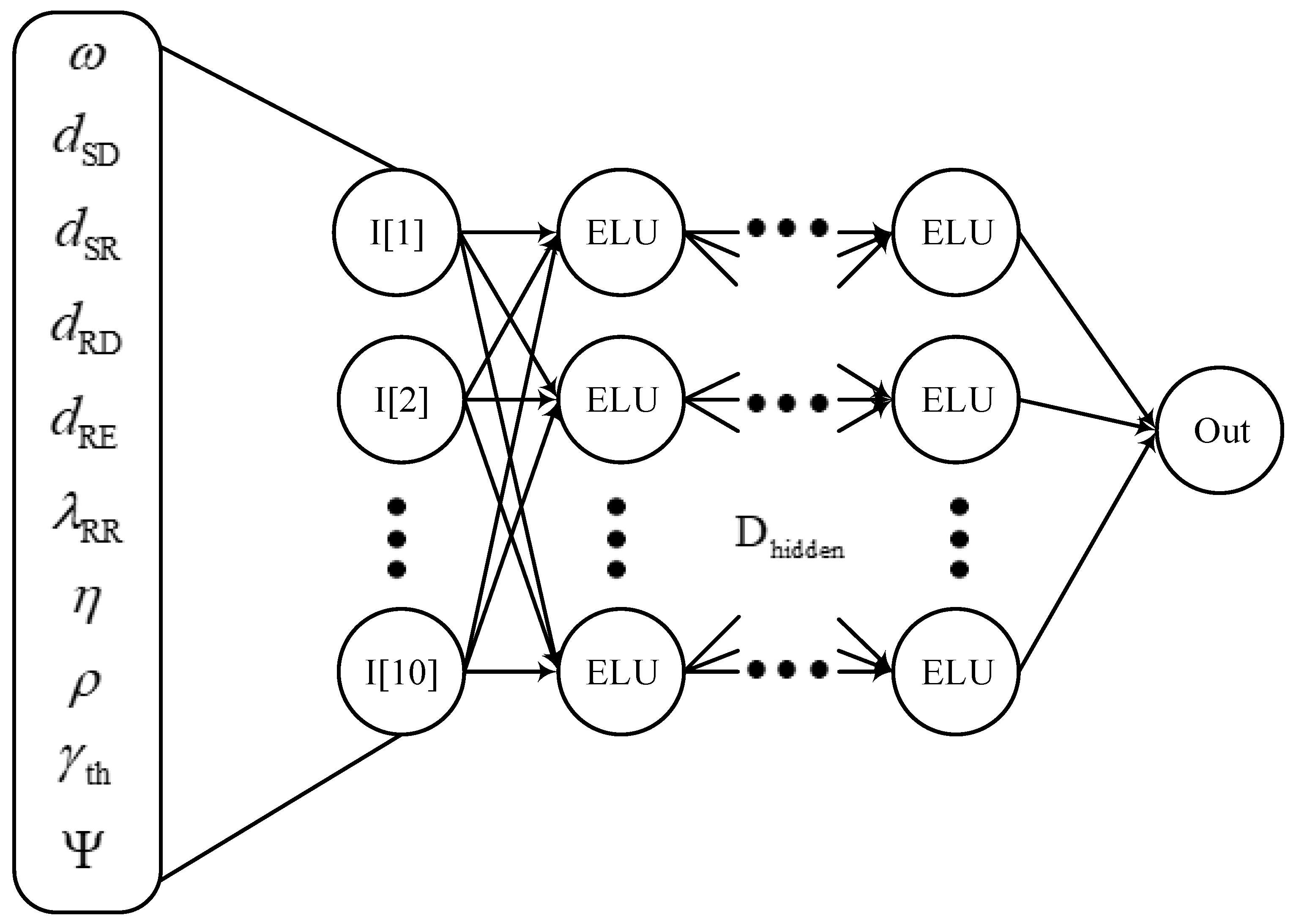
5. Dnn Network
5.1. The DNN Design Description
- Data is sent to the input layer so that the DNN model may determine how the system parameters relate to the relevant OP/IP. The number of neurons in the input layer is, therefore, equal to the number of parameters and does not serve as an activation function;
- The number of hidden layers primarily determines the relationship between the input and output data. In order to accurately calculate the relationship, each connection in each hidden neuron has a separate weight and bias. In order to enhance computational effectiveness, each hidden neuron also has a nonlinear activation function;
- The output layer combines the findings of various hidden layers to predict OP/IP. As a result, there is just one neuron in the output layer. The neuron in the output layer lacks an activation function, much like the input layer.
5.2. Dataset Setup
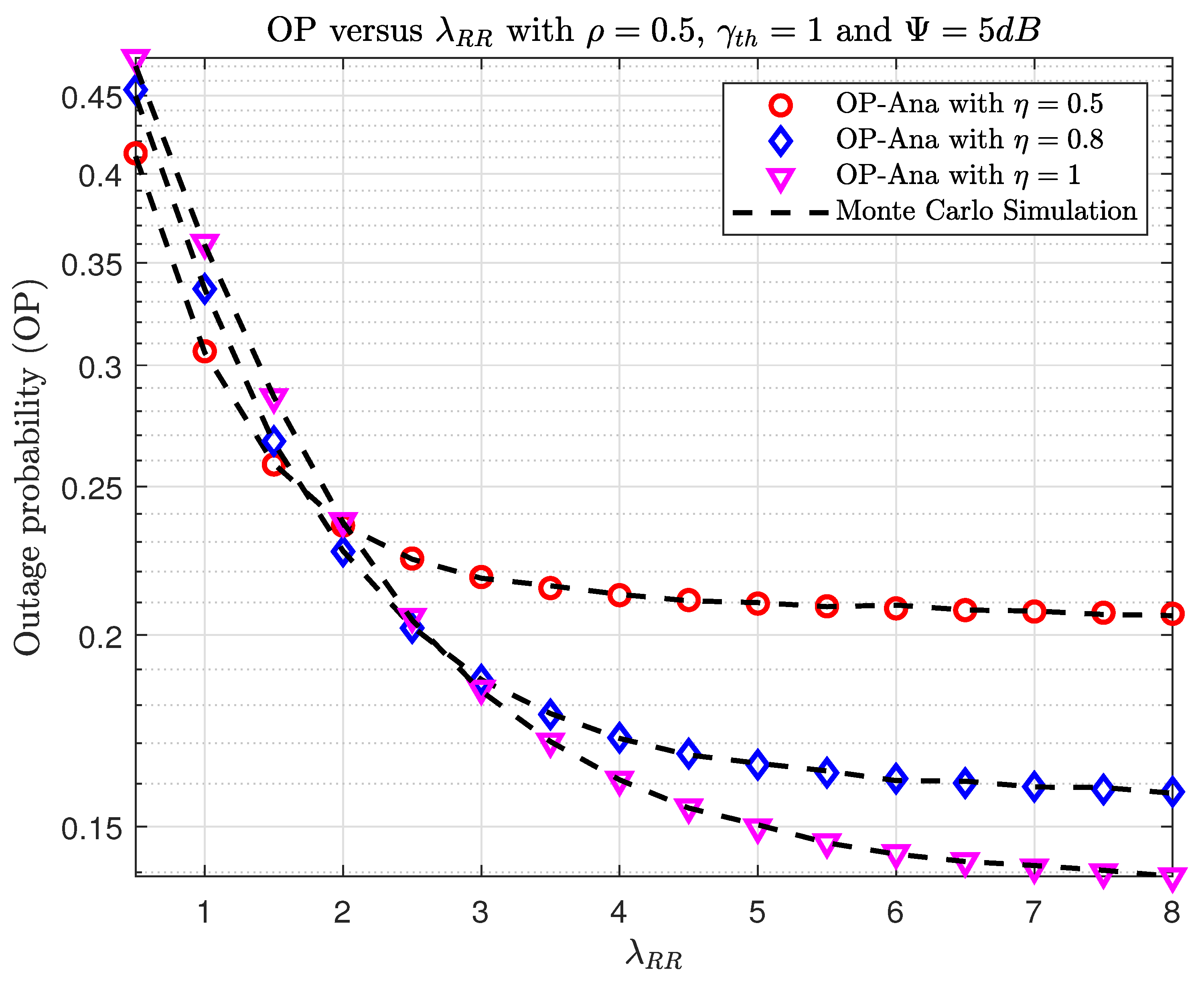
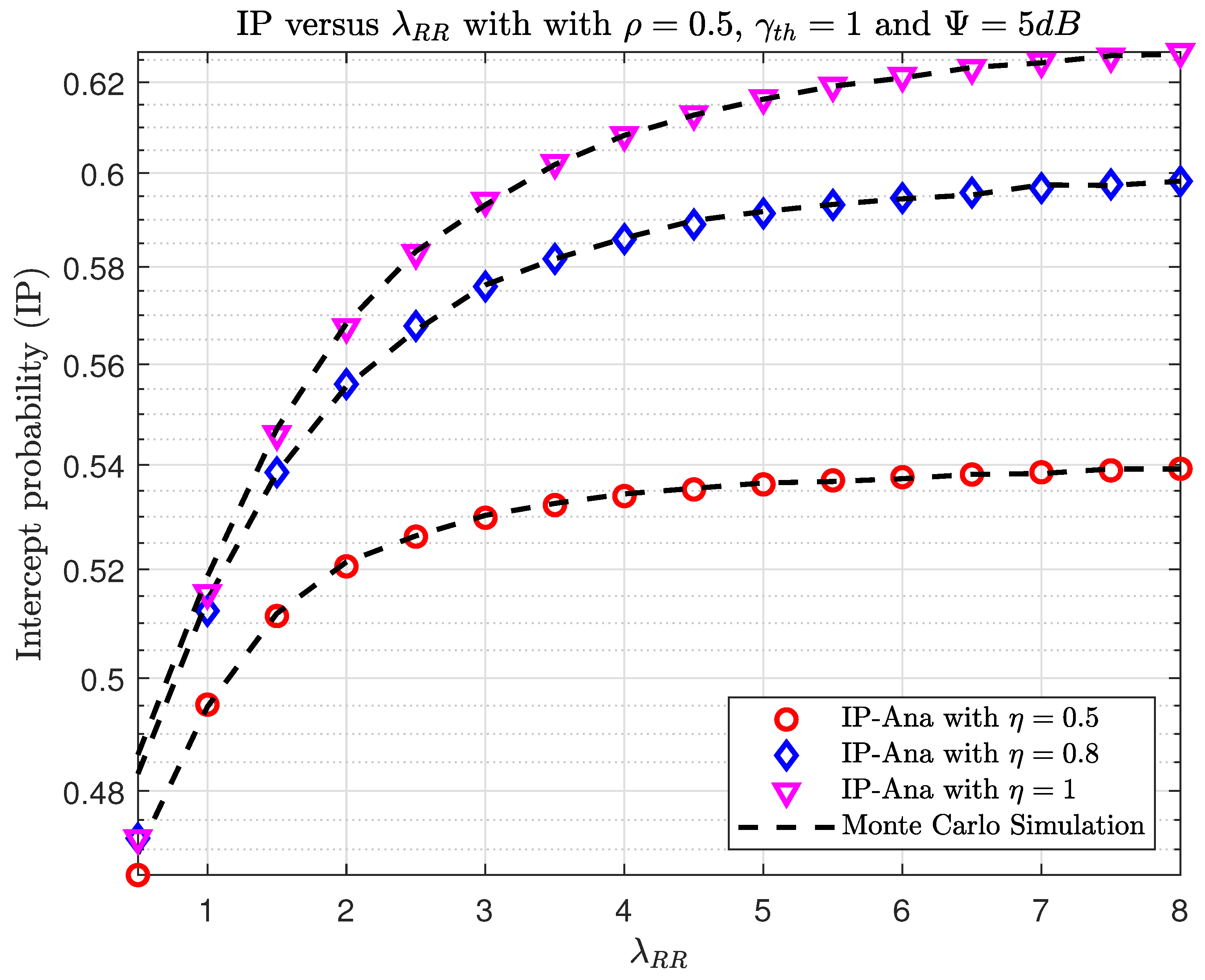
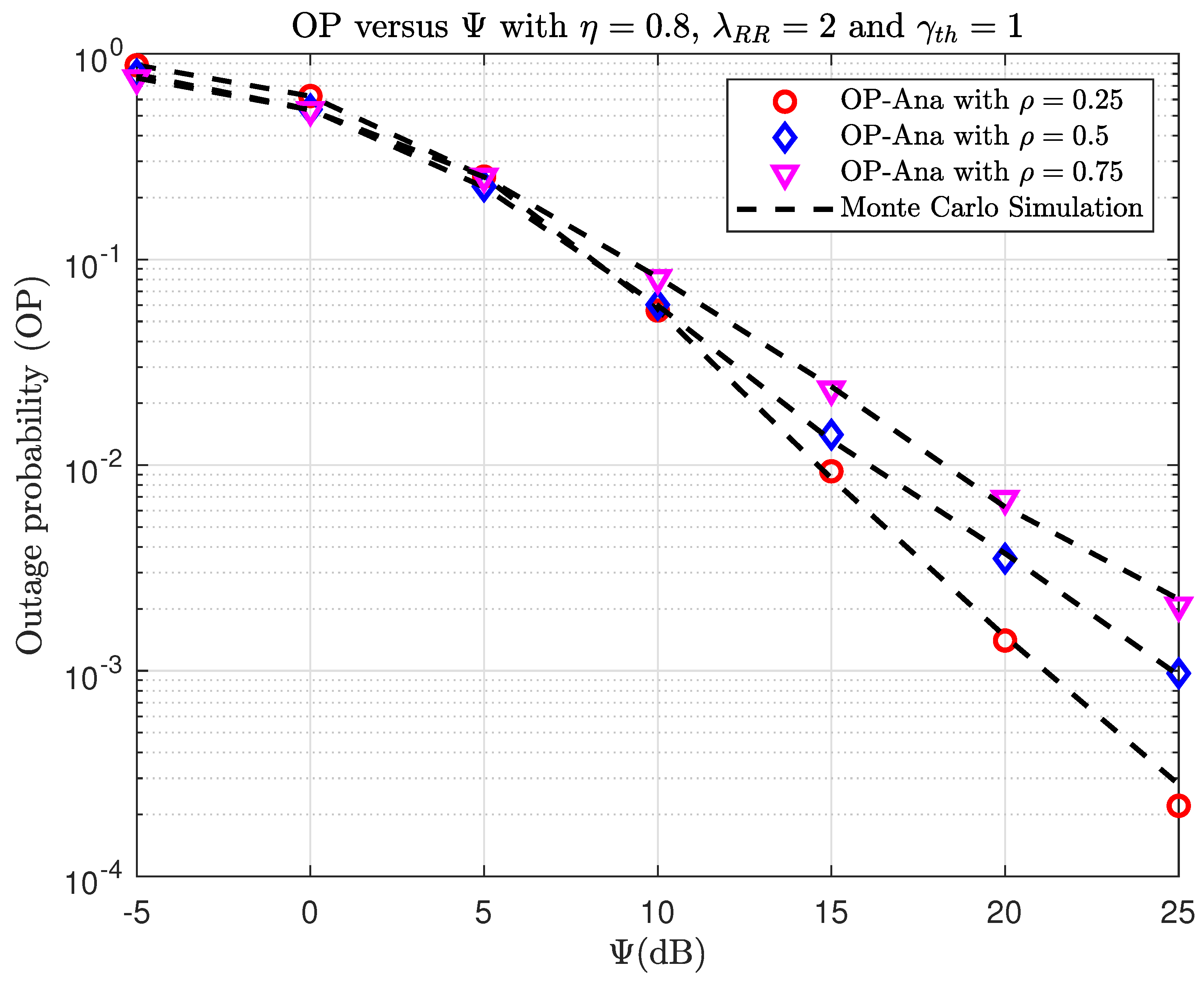
6. Numerical Results
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Jacob, S.; Menon, V.G.; Joseph, S.; Vinoj, P.; Jolfaei, A.; Lukose, J.; Raja, G. A novel spectrum sharing scheme using dynamic long short-term memory with CP-OFDMA in 5G networks. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 926–934. [Google Scholar] [CrossRef]
- Chinnadurai, S.; Yoon, D. Energy efficient MIMO-NOMA HCN with IoT for wireless communication systems. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 17–19 October 2018; pp. 856–859. [Google Scholar]
- Wei, Z.; Zhu, X.; Sun, S.; Huang, Y.; Dong, L.; Jiang, Y. Full-duplex versus half-duplex amplify-and-forward relaying: Which is more energy efficient in 60-GHz dual-hop indoor wireless systems? IEEE J. Sel. Areas Commun. 2015, 33, 2936–2947. [Google Scholar] [CrossRef]
- Razlighi, M.M.; Zlatanov, N. Buffer-aided relaying for the two-hop full-duplex relay channel with self-interference. IEEE Trans. Wirel. Commun. 2017, 17, 477–491. [Google Scholar] [CrossRef]
- Nguyen, B.C.; Pham, T.Q.; Thang, N.N.; Hoang, T.M.; Tran, P.T. Improving the performance of wireless half-duplex and full-duplex relaying networks with intelligent reflecting surface. J. Frankl. Inst. 2023, 360, 3095–3118. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Hoang, V.T.; Tran, M.H.; Le, T.T.H.; Tran, X.N. Secrecy performance analysis of UAV-based full-duplex two-way relay NOMA system. Perform. Eval. 2023, 161, 102352. [Google Scholar] [CrossRef]
- Nguyen, T.L.; Nguyen, T.L.; Nguyen, V.V.; Phu, T.T. Outage Performance of Full-Duplex Unmanned Aerial Vehicle-aided co-operative Non-orthogonal Multiple Access. Adv. Electr. Electron. Eng. 2023, 21, 1–8. [Google Scholar]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Dynamic resource allocation in MIMO-OFDMA systems with full-duplex and hybrid relaying. IEEE Trans. Commun. 2012, 60, 1291–1304. [Google Scholar] [CrossRef]
- Mohammadi, M.; Shi, X.; Chalise, B.K.; Ding, Z.; Suraweera, H.A.; Zhong, C.; Thompson, J.S. Full-Duplex Non-Orthogonal Multiple Access for Next Generation Wireless Systems. IEEE Commun. Mag. 2019, 57, 110–116. [Google Scholar] [CrossRef]
- Chen, X.; Liu, G.; Ma, Z.; Zhang, X.; Fan, P.; Chen, S.; Yu, F.R. When Full Duplex Wireless Meets Non-Orthogonal Multiple Access: Opportunities and Challenges. IEEE Wirel. Commun. 2019, 26, 148–155. [Google Scholar] [CrossRef]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V. Improving Wireless Physical Layer Security via Cooperating Relays. IEEE Trans. Signal Process. 2010, 58, 1875–1888. [Google Scholar] [CrossRef]
- Wang, D.; Bai, B.; Chen, W.; Han, Z. Achieving High Energy Efficiency and Physical-Layer Security in AF Relaying. IEEE Trans. Wirel. Commun. 2016, 15, 740–752. [Google Scholar] [CrossRef]
- Shim, K.; Do, T.N.; Nguyen, T.V.; da Costa, D.B.; An, B. Enhancing PHY-Security of FD-Enabled NOMA Systems Using Jamming and User Selection: Performance Analysis and DNN Evaluation. IEEE Internet Things J. 2021, 8, 17476–17494. [Google Scholar] [CrossRef]
- Lim, J.T.; Kim, T.; Bang, I. Impact of Outdated CSI on the Secure Communication in Untrusted In-Band Full-Duplex Relay Networks. IEEE Access 2022, 10, 19825–19835. [Google Scholar] [CrossRef]
- Hoang, T.M.; Dung, L.T.; Nguyen, B.C.; Tran, X.N.; Kim, T. Secrecy Outage Performance of FD-NOMA Relay System With Multiple Non-Colluding Eavesdroppers. IEEE Trans. Veh. Technol. 2021, 70, 12985–12997. [Google Scholar] [CrossRef]
- Li, X.; Jiang, J.; Wang, H.; Han, C.; Chen, G.; Du, J.; Hu, C.; Mumtaz, S. Physical Layer Security for Wireless-Powered Ambient Backscatter Cooperative Communication Networks. IEEE Trans. Cogn. Commun. Netw. 2023, 9, 927–939. [Google Scholar] [CrossRef]
- Zheng, G.; Krikidis, I.; Li, J.; Petropulu, A.P.; Ottersten, B. Improving Physical Layer Secrecy Using Full-Duplex Jamming Receivers. IEEE Trans. Signal Process. 2013, 61, 4962–4974. [Google Scholar] [CrossRef]
- Ding, Q.; Liu, M.; Deng, Y. Secrecy Outage Probability Analysis for Full-Duplex Relaying Networks Based on Relay Selection Schemes. IEEE Access 2019, 7, 105987–105995. [Google Scholar] [CrossRef]
- Nguyen, B.V.; Jung, H.; Kim, K. Physical Layer Security Schemes for Full-Duplex Cooperative Systems: State of the Art and Beyond. IEEE Commun. Mag. 2018, 56, 131–137. [Google Scholar] [CrossRef]
- Lv, L.; Zhou, F.; Chen, J.; Al-Dhahir, N. Secure Cooperative Communications With an Untrusted Relay: A NOMA-Inspired Jamming and Relaying Approach. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3191–3205. [Google Scholar] [CrossRef]
- Chen, G.; Gong, Y.; Xiao, P.; Chambers, J.A. Physical Layer Network Security in the Full-Duplex Relay System. IEEE Trans. Inf. Forensics Secur. 2015, 10, 574–583. [Google Scholar] [CrossRef]
- Elsaid, L.; Jiménez-Rodríguez, L.; Tran, N.H.; Shetty, S.; Sastry, S. Secrecy Rates and Optimal Power Allocation for Full-Duplex Decode-and-Forward Relay Wire-Tap Channels. IEEE Access 2017, 5, 10469–10477. [Google Scholar] [CrossRef]
- Moya Osorio, D.P.; Benitez Olivo, E.E.; Alves, H. Secrecy Performance for Multiple Untrusted Relay Networks Using Destination-Based Jamming with Direct Link. In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; pp. 1–5. [Google Scholar]
- Saeed, N.; Celik, A.; Al-Naffouri, T.Y.; Alouini, M.S. Localization of energy harvesting empowered underwater optical wireless sensor networks. IEEE Trans. Wirel. Commun. 2019, 18, 2652–2663. [Google Scholar] [CrossRef]
- Ha, D.H.; Nguyen, T.N.; Tran, M.H.Q.; Li, X.; Tran, P.T.; Voznak, M. Security and Reliability Analysis of a Two-Way Half-Duplex Wireless Relaying Network Using Partial Relay Selection and Hybrid TPSR Energy Harvesting at Relay Nodes. IEEE Access 2020, 8, 187165–187181. [Google Scholar] [CrossRef]
- Tin, P.T.; Dinh, B.H.; Nguyen, T.N.; Ha, D.H.; Trang, T.T. Power Beacon-Assisted Energy Harvesting Wireless Physical Layer Cooperative Relaying Networks: Performance Analysis. Symmetry 2020, 12, 106. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, P.T.; Vozňák, M. Power splitting–based energy-harvesting protocol for wireless-powered communication networks with a bidirectional relay. Int. J. Commun. Syst. 2018, 31, e3721. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, M.; Nguyen, T.L.; Ha, D.H.; Voznak, M. Multisource Power Splitting Energy Harvesting Relaying Network in Half-Duplex System over Block Rayleigh Fading Channel: System Performance Analysis. Electronics 2019, 8, 67. [Google Scholar] [CrossRef]
- Liu, X.; Xu, B.; Wang, X.; Zheng, K.; Chi, K.; Tian, X. Impacts of Sensing Energy and Data Availability on Throughput of Energy Harvesting Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2023, 72, 747–759. [Google Scholar] [CrossRef]
- Hou, L.; Tan, S.; Zhang, Z.; Bergmann, N.W. Thermal energy harvesting WSNs node for temperature monitoring in IIoT. IEEE Access 2018, 6, 35243–35249. [Google Scholar] [CrossRef]
- Tin, P.T.; Nguyen, T.N.; Tran, D.H.; Voznak, M.; Phan, V.D.; Chatzinotas, S. Performance Enhancement for Full-Duplex Relaying with Time-Switching-Based SWIPT in Wireless Sensors Networks. Sensors 2021, 21, 3847. [Google Scholar] [CrossRef]
- Li, X.; Wang, Q.; Liu, M.; Li, J.; Peng, H.; Piran, M.J.; Li, L. Cooperative Wireless-Powered NOMA Relaying for B5G IoT Networks With Hardware Impairments and Channel Estimation Errors. IEEE Internet Things J. 2021, 8, 5453–5467. [Google Scholar] [CrossRef]
- Zhang, R.; Ho, C.K. MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef]
- Nguyen, H.N.; Dang, H.P.; Le, S.P.; Le, T.D.; Do, D.T.; Voznak, M.; Zdralek, J. Enabling D2D transmission mode with energy harvesting and information transfer in heterogeneous networks. Adv. Electr. Electron. Eng. 2018, 16, 178–184. [Google Scholar] [CrossRef]
- Phan, V.D.; Nguyen, T.L.; Phu, T.T.; Nguyen, V.V. Reliability-Security in Wireless-Powered Cooperative Network with Friendly Jammer. Adv. Electr. Electron. Eng. 2023, 20, 584–591. [Google Scholar] [CrossRef]
- Sun, W.; Song, Q.; Zhao, J.; Guo, L.; Jamalipour, A. Adaptive Resource Allocation in SWIPT-Enabled Cognitive IoT Networks. IEEE Internet Things J. 2022, 9, 535–545. [Google Scholar] [CrossRef]
- Chen, X.; Yuen, C.; Zhang, Z. Wireless energy and information transfer tradeoff for limited-feedback multiantenna systems with energy beamforming. IEEE Trans. Veh. Technol. 2013, 63, 407–412. [Google Scholar] [CrossRef]
- Huynh, T.P.; Son, P.N.; Voznak, M. Exact Throughput Analyses of Energy-Harvesting Cooperation Scheme with Best Relay Selections Under I/Q Imbalance. Adv. Electr. Electron. Eng. 2017, 15, 585–590. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Duy, T.T.; Tran, P.T.; Voznak, M. Performance evaluation of user selection protocols in random networks with energy harvesting and hardware impairments. Adv. Electr. Electron. Eng. 2016, 14, 372–377. [Google Scholar] [CrossRef]
- Pan, G.; Tang, C.; Li, T.; Chen, Y. Secrecy performance analysis for SIMO simultaneous wireless information and power transfer systems. IEEE Trans. Commun. 2015, 63, 3423–3433. [Google Scholar] [CrossRef]
- Feng, R.; Li, Q.; Zhang, Q.; Qin, J. Robust secure transmission in MISO simultaneous wireless information and power transfer system. IEEE Trans. Veh. Technol. 2014, 64, 400–405. [Google Scholar] [CrossRef]
- Wu, W.; Wang, B. Efficient transmission solutions for MIMO wiretap channels with SWIPT. IEEE Commun. Lett. 2015, 19, 1548–1551. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- El Hammouti, H.; Ghogho, M.; Zaidi, S.A.R. A machine learning approach to predicting coverage in random wireless networks. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Bao, T.; Zhu, J.; Yang, H.C.; Hasna, M.O. Secrecy outage performance of ground-to-air communications with multiple aerial eavesdroppers and its deep learning evaluation. IEEE Wirel. Commun. Lett. 2020, 9, 1351–1355. [Google Scholar] [CrossRef]
- Zheng, K.; Jia, X.; Chi, K.; Liu, X. DDPG-Based Joint Time and Energy Management in Ambient Backscatter-Assisted Hybrid Underlay CRNs. IEEE Trans. Commun. 2023, 71, 441–456. [Google Scholar] [CrossRef]
- Saman, A.; Nathan, R.; Yindi, J.; Malin, P. Source-Based Jamming for Physical-Layer Security on Untrusted Full-Duplex Relay. IEEE Commun. Lett. 2019, 23, 842–846. [Google Scholar]
- Pandey, A.; Yadav, S. Physical layer security in cooperative amplify-and-forward relay networks over mixed Nakagami-m and double Nakagami-m fading channels: Performance evaluation and optimisation. IET Commun. 2020, 14, 95–104. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Tran, D.H.; Van Chien, T.; Phan, V.D.; Voznak, M.; Tin, P.T.; Chatzinotas, S.; Ng, D.W.K.; Poor, H.V. Security–reliability tradeoff analysis for SWIPT-and AF-based IoT networks with friendly jammers. IEEE Internet Things J. 2022, 9, 21662–21675. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Duy, T.T.; Tran, P.T.; Voznak, M.; Li, X.; Poor, H.V. Partial and full relay selection algorithms for AF multi-relay full-duplex networks with self-energy recycling in non-identically distributed fading channels. IEEE Trans. Veh. Technol. 2022, 71, 6173–6188. [Google Scholar] [CrossRef]
- Lee, D. Secrecy Analysis of Relay-User Selection in AS-AF Systems Over Nakagami Fading Channels. IEEE Trans. Veh. Technol. 2021, 70, 2378–2388. [Google Scholar] [CrossRef]
- Liu, H.; Kim, K.J.; Kwak, K.S.; Poor, H.V. Power splitting-based SWIPT with decode-and-forward full-duplex relaying. IEEE Trans. Wirel. Commun. 2016, 15, 7561–7577. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products; Academic Press: Cambridge, MA, USA, 2014. [Google Scholar]
- Wei, L.; Wang, K.; Pan, C.; Elkashlan, M. Secrecy Performance Analysis of RIS-Aided Communication System With Randomly Flying Eavesdroppers. IEEE Wirel. Commun. Lett. 2022, 11, 2240–2244. [Google Scholar] [CrossRef]
- Li, X.; Zhao, M.; Liu, Y.; Li, L.; Ding, Z.; Nallanathan, A. Secrecy Analysis of Ambient Backscatter NOMA Systems Under I/Q Imbalance. IEEE Trans. Veh. Technol. 2020, 69, 12286–12290. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Chien, T.V.; Tran, D.H.; Phan, V.D.; Voznak, M.; Chatzinotas, S.; Ding, Z.; Poor, H.V. Security-Reliability Trade-Offs for Satellite-Terrestrial Relay Networks with a Friendly Jammer and Imperfect CSI. IEEE Trans. Aerosp. Electron. Syst. 2023, 1–16. [Google Scholar] [CrossRef]
- Vu, T.H.; Nguyen, T.V.; Kim, S. Cooperative NOMA-Enabled SWIPT IoT Networks With Imperfect SIC: Performance Analysis and Deep Learning Evaluation. IEEE Internet Things J. 2022, 9, 2253–2266. [Google Scholar] [CrossRef]
- Clevert, D.A.; Unterthiner, T.; Hochreiter, S. Fast and Accurate Deep Network Learning by Exponential Linear Units (ELUs). arXiv 2016, arXiv:1511.07289. [Google Scholar]
- Kingma, D.P.; Ba, J. Adam: A method for stochastic optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]
- Van Chien, T.; Tu, L.T.; Chatzinotas, S.; Ottersten, B. Coverage Probability and Ergodic Capacity of Intelligent Reflecting Surface-Enhanced Communication Systems. IEEE Commun. Lett. 2021, 25, 69–73. [Google Scholar] [CrossRef]
- Hoang, T.M.; Huyen, L.T.T.; Tran, X.N.; Hiep, P.T. Outage Probability of Aerial Base Station NOMA MIMO Wireless Communication With RF Energy Harvesting. IEEE Internet Things J. 2022, 9, 22874–22886. [Google Scholar] [CrossRef]






| Our Work | [47] | [48] | [49] | [50] | [51] | |
|---|---|---|---|---|---|---|
| Co-operative AF relaying network | √ | √ | √ | √ | √ | √ |
| FD | √ | √ | ||||
| EH | √ | √ | √ | |||
| PLS | √ | √ | √ | √ | √ | |
| DNN | √ |
| Notation | Definition |
|---|---|
| The transmit power at S | |
| The transmit power at R | |
| The transmit signal at S with | |
| The transmit signal at R with | |
| The conversion efficiency with | |
| The PS ratio with | |
| The target rate | |
| , , , | The AWGN with variance |
| The path loss exponent | |
| The distance from S to D | |
| The distance from S to R | |
| The distance from S to E | |
| The distance from R to D | |
| The distance from R to E | |
| The expectation operator | |
| The modified Bessel function of the second kind with -th order: |
| Input | Value | Input | Value |
|---|---|---|---|
| 2 | [2,4] | ||
| 1.5 | 0.8 | ||
| 1 | 0.25 | ||
| 0.5 | [0.5,1] | ||
| 1 | [−5,25] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nguyen, T.N.; Minh, B.V.; Tran, D.-H.; Le, T.-L.; Le, A.-T.; Nguyen, Q.-S.; Lee, B.M. Security–Reliability Analysis of AF Full-Duplex Relay Networks Using Self-Energy Recycling and Deep Neural Networks. Sensors 2023, 23, 7618. https://doi.org/10.3390/s23177618
Nguyen TN, Minh BV, Tran D-H, Le T-L, Le A-T, Nguyen Q-S, Lee BM. Security–Reliability Analysis of AF Full-Duplex Relay Networks Using Self-Energy Recycling and Deep Neural Networks. Sensors. 2023; 23(17):7618. https://doi.org/10.3390/s23177618
Chicago/Turabian StyleNguyen, Tan N., Bui Vu Minh, Dinh-Hieu Tran, Thanh-Lanh Le, Anh-Tu Le, Quang-Sang Nguyen, and Byung Moo Lee. 2023. "Security–Reliability Analysis of AF Full-Duplex Relay Networks Using Self-Energy Recycling and Deep Neural Networks" Sensors 23, no. 17: 7618. https://doi.org/10.3390/s23177618
APA StyleNguyen, T. N., Minh, B. V., Tran, D.-H., Le, T.-L., Le, A.-T., Nguyen, Q.-S., & Lee, B. M. (2023). Security–Reliability Analysis of AF Full-Duplex Relay Networks Using Self-Energy Recycling and Deep Neural Networks. Sensors, 23(17), 7618. https://doi.org/10.3390/s23177618






