HealthLock: Blockchain-Based Privacy Preservation Using Homomorphic Encryption in Internet of Things Healthcare Applications
Abstract
1. Introduction
- To design an efficient blockchain-based cloud data privacy preservation model using an encryption mechanism for providing high security in the healthcare IoT for the medical information and, further, it is followed by the medical data prediction using the efficient deep learning approach;
- To implement a hybrid encryption framework, fully homomorphic encryption termed OK-HECCFHE, with the integration of ECC and the fully homomorphic encryption technique, where the optimal key is selected using the hybrid encryption framework algorithm for ensuring reduced computational time and memory size in storing the encrypted key in a blockchain database;
- To develop a significant medical data prediction model by combining the essential features of DNN and GRU to achieve high accuracy in the prediction outcome along with the parameter optimization using the adopted approach for enhancing the prediction accuracy and precision;
- To propose a fused heuristic mechanism named ECC (Elliptic Curve Cryptography) for selecting the optimal public key in the data encryption stage using ECC for elevating security performance and optimizing the parameters like hidden neurons in DNN, learning rate in DNN, epochs in GRU, learning rate in GRU, and batch size in GRU for enhancing the accuracy and precision of the prediction results;
- To validate the efficiency of implemented blockchain-based cloud data privacy preservation model by comparing it with conventional algorithms and prediction techniques.
2. Related Work
2.1. Research Problem and Issues
2.2. Blockchain Technology
2.3. ECC Cryptography and Its Impact on Blockchain
2.4. Hybrid Homomorphic Encryption
- N: The total number of transactions sent;
- : The time taken to execute a single transaction (in seconds);
- : The time taken to validate a single transaction (in seconds);
- : The latency or delay in the system (in seconds).
2.5. Hybrid HSBO
- Decentralized Consensus: The fact that blockchain is decentralized makes it possible for numerous parties or nodes to take part in the process of reaching a consensus. Multiple nodes are able to work together and to contribute their own computational resources in order to carry out the search when the algorithm in question is a hybrid heuristic search algorithm. Through the use of distributed computation, the search process can be sped up, which in turn increases the possibility of discovering superior answers.
- Security and Trust: The use of cryptographic techniques, which are provided by blockchain technology, helps to guarantee the reliability and safety of the search algorithm. The algorithm is able to establish secure communications and to validate the participation of all participating nodes thanks to the utilization of public-key cryptography. Moreover, the unchangeable nature of the blockchain prevents any modifications to the search history, contributing to the accuracy of the results generated by the algorithm.
- Incentive Mechanisms: The incorporation of blockchain technology can allow for the introduction of incentive mechanisms like tokens or cryptocurrencies, which can be used to reward individuals who donate computer resources or propose efficient heuristics. These incentives have the potential to foster collaboration and incentivize users to actively participate in the search process. As a result, the algorithm will have increased efficiency and efficacy.
3. Mathematical Modeling
3.1. Processing Latency
3.2. Block Message Transmission and Cost
3.3. Transmission Commit Time
3.4. Commit Message Transmission Cost
- Message: This is the original message that needs to be transmitted. We represent the message as a sequence of n symbols denoted by M = (m1, m2,…, mn).
- Block: In block message transmission, the message is divided into fixed-size blocks. Let the block size be k. The message M can be partitioned into b blocks: , where each block is a sequence of k symbols: .
- Channel: The channel is the medium through which the blocks are transmitted. It can be a noisy channel where errors may occur during transmission.
- Encoding: Before transmission, each block may undergo encoding to add redundancy, error correction codes, or other techniques to enhance reliability [36].
- Decoding: At the receiver’s end, decoding is performed to recover the original message from the received blocks.
- Transmission Model:At the transmitter side, the encoded blocks are sent through the channel. Due to noise or errors in the channel, the received blocks may differ from the transmitted blocks .Mathematically, the relationship between transmitted and received blocks can be represented as follows:
- Decoding Model:At the receiver’s end, the received blocks are decoded to reconstruct the original message .Mathematically, the decoding process can be represented as follows:
3.5. Transmission Latency
3.6. Channel Allocation Cost and Optimization
4. Model Description
4.1. Resource Optimization Approach
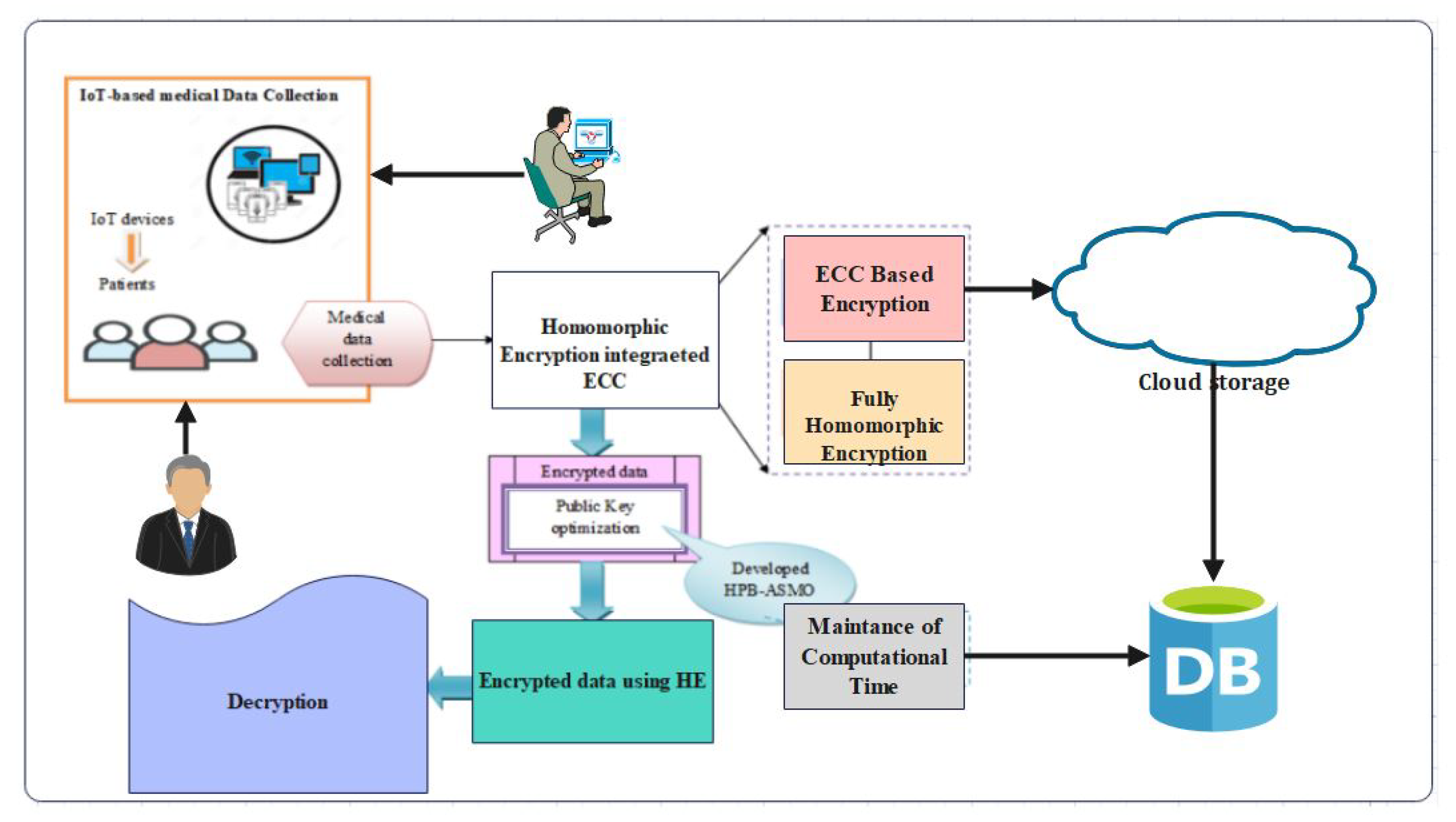
4.1.1. Homomorphic Encryption
4.1.2. Main Objectives
- To investigate the feasibility and effectiveness of homomorphic encryption in preserving privacy and ensuring data confidentiality in the context of IoT healthcare applications;
- To design and develop the HealthLock framework, integrating blockchain technology and homomorphic encryption to provide enhanced privacy preservation in IoT healthcare applications;
- To conduct a comparative analysis with existing privacy preservation approaches in IoT healthcare applications, assessing the advantages and disadvantages of the HealthLock framework;
- To assess the usability and user acceptance of the HealthLock framework through user studies and feedback from healthcare professionals and patients;
- To validate the security of the HealthLock framework by conducting vulnerability analysis, threat modeling, and penetration testing to identify potential vulnerabilities and to propose necessary countermeasures.
5. Problem Statement
- Scalability: Healthcare systems generate a massive volume of data that needs to be securely stored and processed. Ensuring the scalability of the HealthLock framework to handle the increasing amount of data while preserving privacy is a significant challenge.
- Performance: The framework must provide efficient data processing and analysis capabilities, considering the computational overhead introduced by homomorphic encryption. It should strike a balance between privacy preservation and processing efficiency to enable real-time or near-real-time healthcare applications.
- Integration with Existing Infrastructure: Healthcare systems already have established infrastructure and legacy systems. Integrating the HealthLock framework with these existing systems seamlessly and ensuring interoperability can be a complex task.
- User Acceptance: The success of the HealthLock framework relies on its acceptance and adoption by healthcare professionals, patients, and other stakeholders. Ensuring a user-friendly interface, addressing usability concerns, and providing proper training and support are crucial for its successful implementation.
- Regulatory Compliance: Healthcare data are subject to strict regulations and compliance requirements, such as HIPAA (Health Insurance Portability and Accountability Act). The HealthLock framework must adhere to these regulations and ensure compliance to maintain trust and legality.
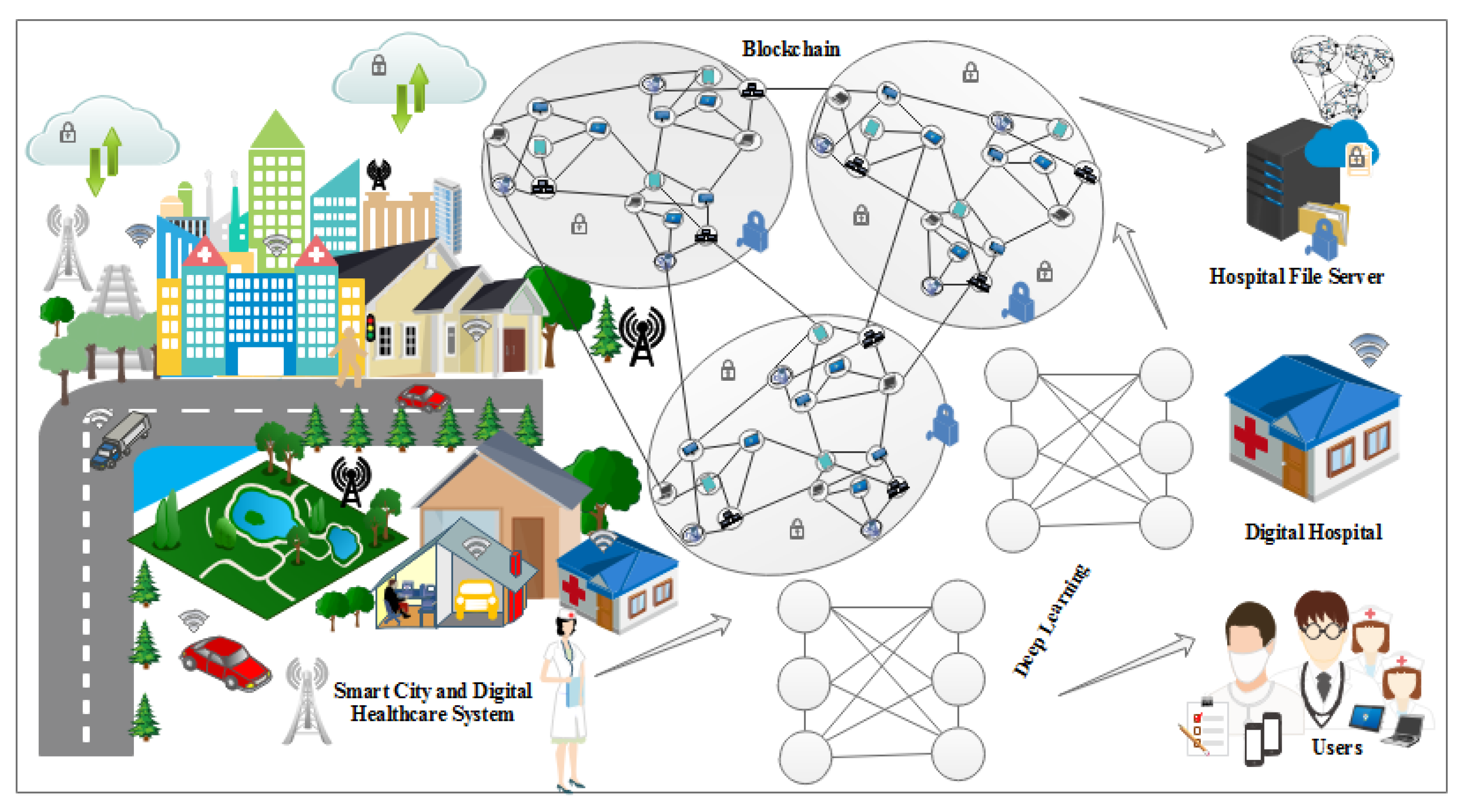
6. Proposed Framework
6.1. System Architecture
- IoT Devices: These devices collect healthcare data from patients, such as vital signs, medical records, and sensor readings. They securely transmit the data to the HealthLock system.
- HealthLock Blockchain: The blockchain forms the core of the framework, providing a decentralized and immutable ledger for storing encrypted healthcare data and transaction records. It ensures data integrity, transparency, and auditability. The blockchain can be implemented using existing platforms like Ethereum or Hyperledger.
- HealthLock Smart Contracts: Smart contracts are deployed on the blockchain to enforce predefined rules and to automate transactions. They handle access control, data sharing permissions, and cryptographic operations.
- Homomorphic Encryption Module: This module enables computations on encrypted data without decrypting it. It ensures privacy by allowing authorized parties to perform computations on the encrypted healthcare data, preserving confidentiality while obtaining useful insights. Advanced homomorphic encryption schemes like partially homomorphic encryption (PHE) or fully homomorphic encryption (FHE) can be utilized.
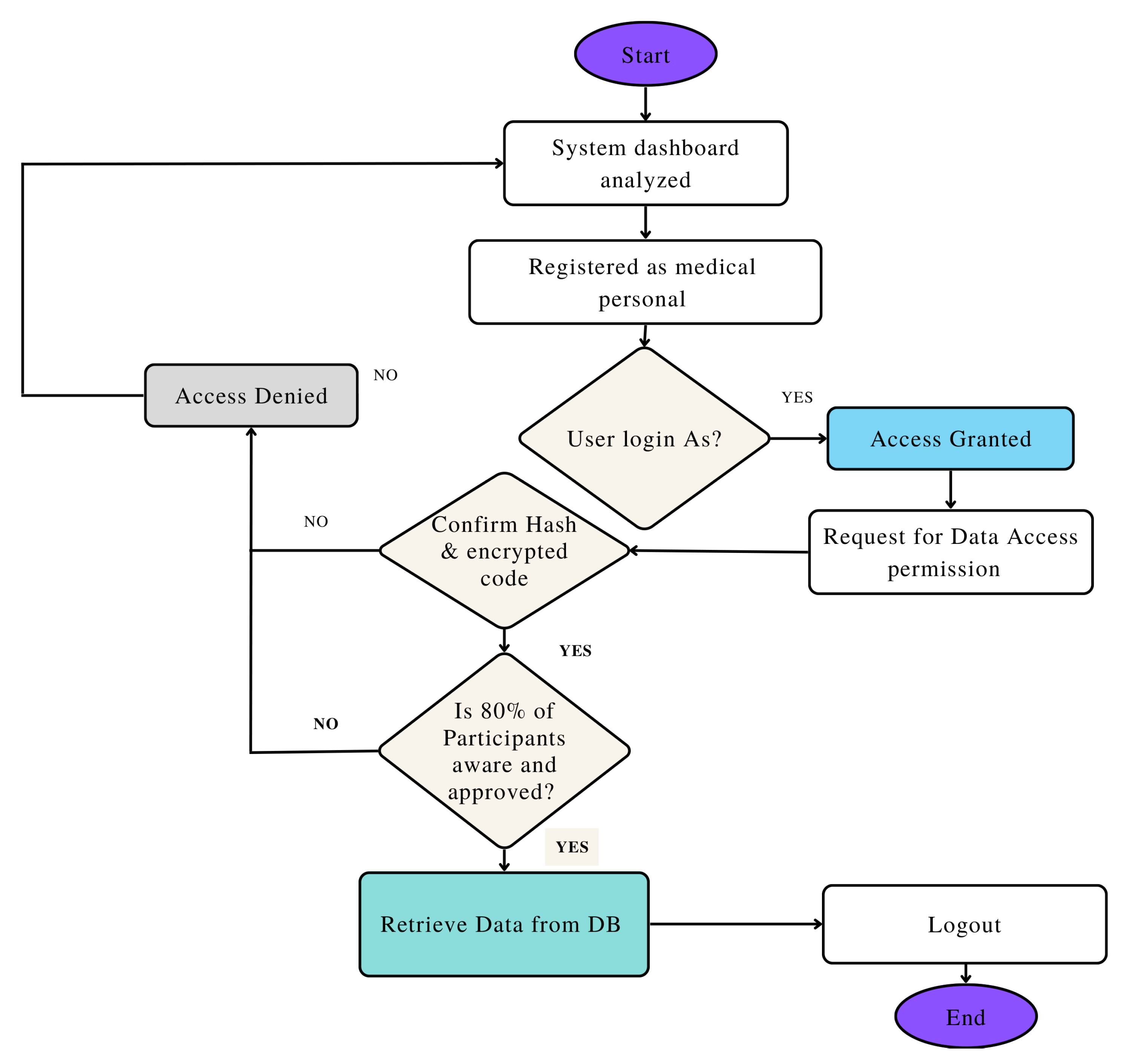
- Data Access Control: HealthLock employs a robust access control mechanism to ensure that only authorized entities can access specific healthcare data. Access control policies are enforced through smart contracts and encryption techniques.
- Data Lifecycle Management: The framework manages the lifecycle of healthcare data through the following stages:
- Data Collection: IoT devices securely collect healthcare data from patients. These data are encrypted using appropriate homomorphic encryption schemes before transmission.
- Data Encryption: The collected healthcare data are encrypted using homomorphic encryption techniques, ensuring confidentiality.
- Data Storage: The encrypted healthcare data are stored in the HealthLock blockchain. Each data entry is associated with a unique identifier, patient information, and access control policies defined by smart contracts.
- Data Sharing: Authorized entities, such as healthcare providers or researchers, can request access to specific healthcare data. Access requests are validated through smart contracts, ensuring compliance with privacy policies.
- Computation on Encrypted Data: Authorized entities can perform computations on the encrypted data without decrypting it, utilizing the homomorphic encryption module. This allows for secure analysis and data processing while preserving privacy.
- Data Audit and Accountability: The blockchain’s transparent nature enables auditing of data access and modifications. Transaction records stored on the blockchain provide an immutable log of data interactions, ensuring accountability and transparency.
- Security and Privacy Considerations: HealthLock incorporates the following security and privacy measures:
- Data Encryption: Sensitive healthcare data are encrypted using homomorphic encryption, ensuring confidentiality.
- Access Control: Smart contracts enforce access control policies, allowing only authorized entities to access specific healthcare data.
- Secure Communication: Data transmission between IoT devices and the HealthLock system is secured using cryptographic protocols, preventing unauthorized access.
- Immutable Ledger: The blockchain provides an immutable and tamper-proof ledger, ensuring data integrity and preventing unauthorized modifications.
- Privacy-Preserving Computation: Homomorphic encryption allows authorized parties to perform computations on encrypted data without compromising privacy.
- -
- Confidentiality: Measure the ability of HealthLock to protect sensitive healthcare data from unauthorized access.
- -
- Anonymity: Evaluate the level of anonymity provided by HealthLock to ensure the privacy of individuals’ identities and health information.
- -
- Data Integrity: Assess the system’s ability to detect and prevent tampering or unauthorized modifications of healthcare data stored on the blockchain.
- -
- Throughput: Measure the number of transactions or data requests that HealthLock can handle per unit of time.
- -
- Latency: Evaluate the time taken for data retrieval, storage, and processing within the HealthLock system.
- -
- Scalability: Assess the system’s ability to handle a growing number of IoT devices, healthcare providers, and data transactions while maintaining performance.
- -
- Computational Overhead: Measure the computational resources required for the execution of cryptographic operations, such as homomorphic encryption and blockchain consensus algorithms.
- -
- Energy Consumption: Evaluate the energy efficiency of the HealthLock system, especially in resource-constrained IoT devices.
- -
- Storage Requirements: Assess the amount of storage space required by the HealthLock blockchain to store encrypted healthcare data.
- -
- Vulnerability Analysis: Conduct a thorough assessment of the system’s security vulnerabilities, including potential attacks on the blockchain, encryption schemes, and smart contracts.
- -
- Penetration Testing: Perform controlled testing to identify any weaknesses or vulnerabilities in the HealthLock system’s infrastructure.
- -
- Threat Modeling: Examine potential hazards and vulnerabilities that could impact the privacy and security of healthcare information within the HealthLock system.
- -
- User Satisfaction: Gather feedback from healthcare professionals, patients, and other stakeholders to evaluate their satisfaction with the HealthLock system’s privacy features and usability.
- -
- User Experience: Assess the ease of use and user-friendliness of the HealthLock system’s interface and functionalities.
- -
- Compare the performance, privacy preservation capabilities, and efficiency of HealthLock with existing privacy preservation approaches in IoT healthcare applications.
- -
- Evaluate the advantages and disadvantages of HealthLock in comparison with other state-of-the-art solutions.
6.2. Analysis of Correctness and Unforgeability of HE
- -
- Ciphertext space: is the set of all possible ciphertexts.
- -
- Key space: is the set of all possible encryption and decryption keys.
- -
- Key generation algorithm: is the algorithm that generates the encryption and decryption keys, i.e., , where is the public key and is the secret key, and represents the security parameter.
- -
- Encryption algorithm: refers to the encryption algorithm which, when given a public key pk and a plaintext message m from set M, results in a ciphertext , i.e., .
- -
- Decryption algorithm: is the decryption algorithm that takes the secret key and a ciphertext and recovers the original plaintext message , i.e., .
- -
- Homomorphic operation: Let ★ be the homomorphic operation supported by the HE scheme. Given ciphertexts and , we can compute , and after decryption, we can obtain , where and are the plaintext messages corresponding to and , respectively.
6.3. Proposed Algorithm
| Algorithm 1 Add node to blockchain network. |
| Input: NewNode Output: UpdatedBlockchain Initialization: nodeID←NewNode’s unique identifier; nodePublicKey←NewNode’s public key; blockchain←Existing blockchain network; Procedure: NewNode sends a request to join the network; Request is approved newBlock←CreateGenesisBlock(); newBlock.header.previousHash←blockchain.getLatestBlock().header.blockHash; newBlock.header.timestamp←CurrentTimestamp(); newBlock.header.nonce←CalculateNonce(); newBlock.header.merkleRoot←CalculateMerkleRoot(); newBlock.header.nodeID←nodeID; newBlock.header.nodePublicKey←nodePublicKey; newBlock.header.blockHash←CalculateBlockHash(newBlock.header); blockchain.addBlock(newBlock) Broadcast the new block to the network; Update the blockchain network; Return UpdatedBlockchain |
| Algorithm 2 Health record search. |
| Input: SearchQuery, Blockchain Output: MatchingRecords Initialization:; MatchingRecords←Empty list; Procedure:; block in Blockchain record in block record matches SearchQuery MatchingRecords.append(record) Return MatchingRecords |
| Algorithm 3 Security and privacy preservation. |
| Input: IncomingRequest Output: Response Initialization:; Response←Empty; Procedure:; IncomingRequest is a DoS attack Response←BlockRequest(); IncomingRequest is a ransomware attack Response←IsolateInfectedSystem(); IncomingRequest is a phishing attack Response←VerifyIdentity(); Response←ProcessRequest(); Return Response; |
Solidity Tool
7. Simulation Setup
- Cache System Configuration: Determine the size and capacity of the cache system, including the number of cache slots or cache memory available for storing data items. Moreover, choose a cache replacement policy, such as Least Recently Used (LRU), Least Frequently Used (LFU), or Random, to manage cache eviction and replacement.
- Data Access Pattern: Generate or simulate a workload that represents the data access pattern in the system. This step consists of a series of requests for specific data items or a stream of data access events [42].
- Cache Hit and Miss Determination: Based on the data access pattern, determine whether each access results in a cache hit (the data item is found in the cache) or a cache miss (the data item is not found in the cache and needs to be retrieved from a slower storage system).
- Search Time Measurement: Measure the time taken to search for a data item in the cache, including the time required to check cache slots, to compare keys, and to retrieve the requested data.
- Cache Hit Rate Calculation: Compute the cache hit rate by determining the ratio of cache hits to the total cache interactions (the sum of hits and misses), expressed as a percentage.
8. Results
- Search Time and Cache Hit Rate Trade-off: Generally, as the cache hit rate increases, the search time tends to decrease. This is because a higher cache hit rate implies a larger proportion of data being found in the cache, reducing the search time required to retrieve the requested items.
- Cache Size Impact: Increasing the cache size typically improves the cache hit rate, as it allows more data items to be stored in the cache. A larger cache size increases the likelihood of finding frequently accessed data items in the cache, leading to shorter search times.
- Cache Replacement Policy: The choice of cache replacement policy can impact both search time and cache hit rate. For example, LRU replacement tends to have a higher cache hit rate for workloads with temporal locality, while LFU replacement may better handle workloads with frequent access to a few specific items.
- Access Pattern Influence: The specific data access pattern in the simulation can affect the relationship between search time and cache hit rate. Workloads with high locality of reference, where the same data items are repeatedly accessed, tend to have higher cache hit rates and shorter search times. It is obvious that the proposed approach outperforms the existing model.
9. Conclusions
- 1
- Scalability and Performance Optimization: One avenue for future work is to explore methods for improving the scalability and performance of the HealthLock framework. This could involve optimizing the blockchain implementation to handle a larger volume of healthcare data and transactions efficiently. Techniques such as sharding, sidechains, or off-chain solutions can be investigated to enhance scalability while maintaining data privacy and security. Research and development of more advanced homomorphic encryption schemes can be pursued to improve the efficiency and functionality of the HealthLock framework. This might involve investigating partially homomorphic encryption (PHE) or fully homomorphic encryption (FHE) methods that allow for advanced calculations on encrypted data, while maintaining confidentiality. Investigating the use of pre-processing techniques, optimization algorithms, and hardware acceleration can also contribute to faster and more practical homomorphic encryption solutions. Moreover, Integrating privacy-preserving analytics and machine learning techniques within the HealthLock framework can be a promising avenue for future work. Developing methods to perform advanced computations, such as statistical analysis, predictive modeling, or anomaly detection, directly on encrypted data can enable valuable insights while maintaining privacy. Exploring techniques like secure multiparty computation (MPC) and federated learning can facilitate collaborative analyses on encrypted data without exposing sensitive information.
10. Future Work
- 2
- Real-World Implementation and Deployment: Conducting real-world pilot studies and deploying the HealthLock framework within healthcare organizations can provide valuable insights into its practical feasibility, performance, and user acceptance. Collaborating with healthcare providers, patients, and regulatory bodies can help address legal and ethical considerations, validate the framework’s effectiveness, and identify potential challenges and improvements in real-world settings.
- 3
- Usability and User Experience: Investigating the usability and user experience aspects of the HealthLock framework is an essential area of future work. Designing intuitive user interfaces, considering user perspectives, and conducting user studies can contribute to the framework’s adoption and acceptance among healthcare professionals, patients, and other stakeholders. Incorporating user feedback and continuously refining the framework’s usability can enhance its practical implementation and ensure that it aligns with user requirements.
- 4
- Security and Threat Analysis: Conducting a comprehensive security and threat analysis is crucial for ensuring the robustness of the HealthLock framework. Performing vulnerability assessments, penetration testing, and adversarial modeling can help identify potential weaknesses or attack vectors.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Shah, A.A.; Piro, G.; Grieco, L.A.; Boggia, G. A qualitative cross-comparison of emerging technologies for software-defined systems. In Proceedings of the 2019 Sixth International Conference on Software Defined Systems (SDS), Rome, Italy, 10–13 June 2019; pp. 138–145. [Google Scholar]
- Ali, A.; Mehboob, M. Comparative analysis of selected routing protocols for wlan based wireless sensor networks (WSNS). In Proceedings of the 2nd International Multi-Disciplinary Conference, Gujrat, Pakistan, 19–20 December 2016; Volume 19, p. 20. [Google Scholar]
- Shah, A.A.; Piro, G.; Grieco, L.A.; Boggia, G. A review of forwarding strategies in transport software-defined networks. In Proceedings of the 2020 22nd International Conference on Transparent Optical Networks (ICTON), Bari, Italy, 19–23 July 2020; pp. 1–4. [Google Scholar]
- Bruce, R.R.; Cunard, J.P.; Director, M.D. From Telecommunications to Electronic Services: A Global Spectrum of Definitions, Boundary Lines, and Structures; Butterworth-Heinemann: Oxford, UK, 2014. [Google Scholar]
- Gatteschi, V.; Lamberti, F.; Demartini, C.; Pranteda, C.; Santamaría, V. Blockchain and smart contracts for insurance: Is the technology mature enough? Future Internet 2018, 10, 20. [Google Scholar] [CrossRef]
- Jia, B.; Zhou, T.; Li, W.; Liu, Z.; Zhang, J. A blockchain-based location privacy protection incentive mechanism in crowd sensing networks. Sensors 2018, 18, 3894. [Google Scholar]
- Biswas, K.; Muthukkumarasamy, V. Securing smart cities using blockchain technology. In Proceedings of the 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Sydney, NSW, Australia, 12–14 December 2016; pp. 1392–1393. [Google Scholar]
- Fernández-Caramés, T.M.; Froiz-Míguez, I.; Blanco-Novoa, O.; Fraga-Lamas, P. Enabling the internet of mobile crowdsourcing health things: A mobile fog computing, blockchain and iot based continuous glucose monitoring system for diabetes mellitus research and care. Sensors 2019, 19, 3319. [Google Scholar] [PubMed]
- Ali, A.; Naveed, M.; Mehboob, M.; Irshad, H.; Anwar, P. An interference aware multi-channel MAC protocol for WASN. In Proceedings of the 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT), Karachi, Pakistan, 5–7 April 2017; pp. 1–9. [Google Scholar]
- Beebeejaun, A. VAT on foreign digital services in mauritius; a comparative study with South Africa. Int. J. Law Manag. 2020, 63, 239–250. [Google Scholar]
- Aziz Shah, A.; Piro, G.; Alfredo Grieco, L.; Boggia, G. A quantitative cross-comparison of container networking technologies for virtualized service infrastructures in local computing environments. Trans. Emerg. Telecommun. Technol. 2021, 32, 4234. [Google Scholar]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R. Blockchain-enabled authentication handover with efficient privacy protection in SDN-based 5G networks. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1120–1132. [Google Scholar] [CrossRef]
- Kim, H.; Kim, S.-H.; Hwang, J.Y.; Seo, C. Efficient privacy-preserving machine learning for blockchain network. IEEE Access 2019, 7, 136481–136495. [Google Scholar] [CrossRef]
- Cirstea, A.; Enescu, F.M.; Bizon, N.; Stirbu, C.; Ionescu, V.M. Blockchain technology applied in health the study of blockchain application in the health system (ii). In Proceedings of the 2018 10th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Iasi, Romania, 28–30 June 2018; pp. 1–4. [Google Scholar]
- Yazdinejad, A.; Srivastava, G.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R.; Aledhari, M. Decentralized authentication of distributed patients in hospital networks using blockchain. IEEE J. Biomed. Health Inform. 2020, 24, 2146–2156. [Google Scholar]
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2019, 25, 1398–1411. [Google Scholar]
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. Veh. Commun. 2020, 23, 100214. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for iot security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Hameed, K.; Ali, A.; Naqvi, M.H.; Jabbar, M.; Junaid, M.; Haider, A. Resource management in operating systems—A survey of scheduling algorithms. In Proceedings of the International Conference on Innovative Computing (ICIC), Lahore, Pakistan, 23–24 September 2016; Volume 1. [Google Scholar]
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A decentralized privacy-preserving healthcare blockchain for iot. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [PubMed]
- Daraghmi, E.-Y.; Daraghmi, Y.-A.; Yuan, S.-M. Medchain: A design of blockchain-based system for medical records access and permissions management. IEEE Access 2019, 7, 164595–164613. [Google Scholar] [CrossRef]
- Jung, Y.; Peradilla, M.; Agulto, R. Packet key-based end-to-end security management on a blockchain control plane. Sensors 2019, 19, 2310. [Google Scholar] [CrossRef] [PubMed]
- Choo, C.W. Information Management for the Intelligent Organization: The Art of Scanning the Environment; Information Today, Inc.: Medford, NJ, USA, 2002. [Google Scholar]
- Hang, L.; Kim, D.-H. Design and implementation of an integrated IOT blockchain platform for sensing data integrity. Sensors 2019, 19, 2228. [Google Scholar] [PubMed]
- Yu, B.; Kermanshahi, S.K.; Sakzad, A.; Nepal, S. Chameleon hash time-lock contract for privacy preserving payment channel networks. In Provable Security, Proceedings of the International Conference on Provable Security, Cairns, QLD, Australia, 1–4 October 2019; Springer: Cham, Switzerland, 2019; pp. 303–318. [Google Scholar]
- Esposito, C.; De Santis, A.; Tortora, G.; Chang, H.; Choo, K.-K.R. Blockchain: A panacea for healthcare cloud-based data security and privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar]
- Kermanshahi, S.K.; Liu, J.K.; Steinfeld, R.; Nepal, S.; Lai, S.; Loh, R.; Zuo, C. Multi-client cloud-based symmetric searchable encryption. IEEE Trans. Dependable Secur. Comput. 2021, 18, 2419–2437. [Google Scholar] [CrossRef]
- Kermanshahi, S.K.; Liu, J.K.; Steinfeld, R. Multi-user cloud-based secure keyword search. In Information Security and Privacy, Proceedings of the 22nd Australasian Conference, ACISP 2017, Auckland, New Zealand, 3–5 July 2017; Springer: Cham, Switzerland, 2017; pp. 227–247. [Google Scholar]
- Kermanshahi, S.K.; Liu, J.K.; Steinfeld, R.; Nepal, S. Generic multi-keyword ranked search on encrypted cloud data. In Computer Security—ESORICS 2019, Proceedings of the 24th European Symposium on Research in Computer Security, Luxembourg, 23–27 September 2019; Springer: Cham, Switzerland, 2019; pp. 322–343. [Google Scholar]
- Rathi, V.K.; Chaudhary, V.; Rajput, N.K.; Ahuja, B.; Jaiswal, A.K.; Gupta, D.; Elhoseny, M.; Hammoudeh, M. A blockchain-enabled multi domain edge computing orchestrator. J. IEEE Internet Things Mag. 2020, 3, 30–36. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Adhi Tama, B.; Shahzad, M.K.; Choi, Y.-H. Secure and blockchain-based emergency driven message protocol for 5G enabled vehicular edge computing. Sensors 2020, 20, 154. [Google Scholar]
- Kaushik, S. Blockchain and 5G-Enabled Internet of Things: Background and Preliminaries. In Blockchain for 5G-Enabled IoT; Springer: Cham, Switzerland, 2021; pp. 3–31. [Google Scholar]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Budhiraja, I.; Tyagi, S.; Tanwar, S.; Kumar, N.; Guizani, M. CR-NOMA Based Interference Mitigation Scheme for 5G Femtocells Users. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018. [Google Scholar] [CrossRef]
- Srinivasu, P.N.; Bhoi, A.K.; Nayak, S.R.; Bhutta, M.R.; Woźniak, M. Blockchain Technology for Secured Healthcare Data Communication among the Non-Terminal Nodes in IoT Architecture in 5G Network. Electronics 2021, 10, 1437. [Google Scholar] [CrossRef]
- Feng, C.; Yu, K.; Bashir, A.K.; Al-Otaibi, Y.D.; Lu, Y.; Chen, S.; Zhang, D. Efficient and secure data sharing for 5G flying drones: A blockchain-enabled approach. IEEE Netw. 2021, 35, 130–137. [Google Scholar]
- Khujamatov, K.; Reypnazarov, E.; Akhmedov, N.; Khasanov, D. Blockchain for 5G Healthcare architecture. In Proceedings of the 2020 International Conference on Information Science and Communications Technologies (ICISCT), Tashkent, Uzbekistan, 4–6 November 2020; pp. 1–5. [Google Scholar]
- Vivekanandan, M.; Sastry, V.N.; Srinivasulu, R.U. BIDAPSCA5G: Blockchain based Internet of Things (IoT) device to device authentication protocol for smart city applications using 5G technology. Peer-to-Peer Netw. Appl. 2021, 14, 403–419. [Google Scholar] [CrossRef]
- Gao, J.; Agyekum, K.O.-B.O.; Sifah, E.B.; Acheampong, K.N.; Xia, Q.; Du, X.; Guizani, M.; Xia, H. A blockchain-SDN-enabled Internet of vehicles environment for fog computing and 5G networks. IEEE Internet Things J. 2019, 7, 4278–4291. [Google Scholar] [CrossRef]
- Zhou, S.; Huang, H.; Chen, W.; Zhou, P.; Zheng, Z.; Guo, S. PIRATE: A blockchain-based secure framework of distributed machine learning in 5G networks. IEEE Netw. 2020, 34, 84–91. [Google Scholar]
- Zhang, Y.; Wang, K.; Moustafa, H.; Wang, S.; Zhang, K. Guest Editorial: Blockchain and AI for Beyond 5G Networks. IEEE Netw. 2020, 34, 22–23. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhao, J.; Zhai, W.; Sun, S.; Niyato, D.; Lam, K.-Y. A survey of 6G wireless communications: Emerging technologies. In Advances in Information and Communication, Proceedings of the 2021 Future of Information and Communication Conference (FICC), Vancouver, BC, Canada, 29–30 April 2021; Springer: Cham, Switzerland, 2021; pp. 150–170. [Google Scholar]
- Bhattacharya, P.; Tanwar, S.; Shah, R.; Ladha, A. Mobile edge computing-enabled blockchain framework—A survey. In Proceedings of the ICRIC 2019; Springer: Cham, Switzerland, 2020; pp. 797–809. [Google Scholar]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, A.; Al-rimy, B.A.S.; Alsubaei, F.S.; Almazroi, A.A.; Almazroi, A.A. HealthLock: Blockchain-Based Privacy Preservation Using Homomorphic Encryption in Internet of Things Healthcare Applications. Sensors 2023, 23, 6762. https://doi.org/10.3390/s23156762
Ali A, Al-rimy BAS, Alsubaei FS, Almazroi AA, Almazroi AA. HealthLock: Blockchain-Based Privacy Preservation Using Homomorphic Encryption in Internet of Things Healthcare Applications. Sensors. 2023; 23(15):6762. https://doi.org/10.3390/s23156762
Chicago/Turabian StyleAli, Aitizaz, Bander Ali Saleh Al-rimy, Faisal S. Alsubaei, Abdulwahab Ali Almazroi, and Abdulaleem Ali Almazroi. 2023. "HealthLock: Blockchain-Based Privacy Preservation Using Homomorphic Encryption in Internet of Things Healthcare Applications" Sensors 23, no. 15: 6762. https://doi.org/10.3390/s23156762
APA StyleAli, A., Al-rimy, B. A. S., Alsubaei, F. S., Almazroi, A. A., & Almazroi, A. A. (2023). HealthLock: Blockchain-Based Privacy Preservation Using Homomorphic Encryption in Internet of Things Healthcare Applications. Sensors, 23(15), 6762. https://doi.org/10.3390/s23156762





