Abstract
With the rapid development of technologies such as wireless communications and the Internet of Things (IoT), the proliferation of IoT devices will intensify the competition for spectrum resources. The introduction of cognitive radio technology in IoT can minimize the shortage of spectrum resources. However, the open environment of cognitive IoT may involve free-riding problems. Due to the selfishness of the participants, there are usually a large number of free-riders in the system who opportunistically gain more rewards by stealing the spectrum sensing results from other participants and accessing the spectrum without spectrum sensing. However, this behavior seriously affects the fault tolerance of the system and the motivation of the participants, resulting in degrading the system’s performance. Based on the energy-harvesting cognitive IoT model, this paper considers the free-riding problem of Secondary Users (SUs). Since free-riders can harvest more energy in spectrum sensing time slots, the application of energy harvesting technology will exacerbate the free-riding behavior of selfish SUs in Cooperative Spectrum Sensing (CSS). In order to prevent the low detection performance of the system due to the free-riding behavior of too many SUs, a penalty mechanism is established to stimulate SUs to sense the spectrum normally during the sensing process. In the system model with multiple primary users (PUs) and multiple SUs, each SU considers whether to free-ride and which PU’s spectrum to sense and access in order to maximize its own interests. To address this issue, a two-layer game-based cooperative spectrum sensing and access method is proposed to improve spectrum utilization. Simulation results show that compared with traditional methods, the average throughput of the proposed TL-CSAG algorithm increased by and the proposed method makes the SUs allocation more fair.
1. Introduction
In recent years, there has been widespread interest in the automation revolution in the industrial, infrastructure, and healthcare fields through the implementation of the Internet of Things (IoT) [1]. However, available wireless spectrum resources are extremely limited, and the large-scale deployment of IoT devices will greatly exacerbate the shortage of spectrum resources and the problem of interference between devices. A large amount of data shows that the utilization of spectrum in the communication field is not high, and many authorized spectrums are not fully utilized, resulting in a huge waste of spectrum resources [2]. To address these challenges, Cognitive Radio (CR) provides an effective solution. In a CR system, Secondary Users (SUs) can access the authorized spectrum of Primary Users (PUs) with little impact on the PUs. Applying CR technology to IoT networks can effectively improve their spectrum utilization efficiency. Therefore, the design and optimization of Cognitive IoT (CIoT) networks based on CR have received considerable attention [3].
Spectrum sensing is a key technology in CR to address the problem of insufficient spectrum resources by reusing underutilized spectrum. However, the detection performance of spectrum sensing may deteriorate significantly due to uncertainties such as noise and channel conditions [4]. Cooperative Spectrum Sensing (CSS) can improve the sensing performance of fading and shadowed channels by combining the results of multiple SUs’ global sensing [5]. Specifically, due to factors such as obstruction, SUs may be located in the shadow of PU transmission signals and unable to detect their signals, which results in interference with PU’s communication. CSS can effectively address the hidden terminal problem by allowing multiple SUs to cooperate and greatly reducing the impact of shadowed areas on sensing. Furthermore, dynamic spectrum access can greatly improve the spectrum utilization efficiency between SUs and PUs [6]. Dynamic spectrum access technology allows SUs to effectively utilize spectrum resources by “leasing” or “sharing” idle spectrum resources, improving spectrum utilization, and also having significant advantages in fairness and efficiency. This technology can be used either in the overlay mode, where the SUs opportunistically utilize the unused spectrum of the PUs, or in the underlay mode, where both PUs and SUs transmit simultaneously under SINR constraints in the same frequency band [7].
Due to the limited battery capacity of IoT devices, it is difficult for them to run for a long time. Energy Harvesting (EH) allows devices to harvest energy from the environment to refill batteries [8]. For any type of energy source, the amount of energy transferred from the energy source to the energy harvester is not deterministic but random. Collecting energy through Radio Frequency (RF) signals can avoid the influence of harsh environments and light, and compared with solar energy and wind energy, the energy harvesting process is more stable. Therefore, RF EH technology has become an important direction for researchers to study the energy efficiency of CIoT [9]. However, since selfish SUs can harvest more energy for system consumption by free-riding during spectrum sensing slots, the application of EH will exacerbate the free-riding behavior of selfish SUs, leading to degraded system detection performance. Therefore, the application of EH technology needs to consider how to deal with the free-riding problem to ensure more stable and reliable system performance.
In recent years, people have been more committed to developing distributed intelligent collaboration systems due to reasons of scalability and high performance [10]. These systems consist of distributed processing nodes with autonomous learning capabilities and usually include a large number of free-riding nodes [11]. However, these free-riding nodes will result in fewer nodes providing resources, and the entire system will face the problem of insufficient utilization of resources, and the purpose of sharing will gradually disappear. In CSS, SUs report their sensing results to the FC by control channel and the final channel state is determined by the FC. However, SUs may be selfish, and they may adopt a free-riding strategy when multiple SUs occupy different sub-bands of a PU’s spectrum and can occasionally overhear the sensing results of other SUs. Free-riders tend to wait for other SUs to sense them first and take advantage of other SUs’ results so that they can reserve more time for their own data transmission. Therefore, due to the existence of free-riding behavior, there are two types of SUs with different sensing attitudes in the system: Contributing Users (CUs) who participate in cooperative sensing and Free-riding Users (FUs) who are dishonest. CUs increase the amount of information, but regardless of how much they contribute, the added information is shared equally among participants. However, if the cost of contribution exceeds the marginal benefit, SUs will be tempted not to contribute. Free-riders severely reduce the fault tolerance and content availability of the peer-to-peer system. In cooperative systems, the key to solving this problem is to establish incentive mechanisms that aim to improve utility by incentivizing nodes to become more cooperative. Ref. [12] proposed a game-theoretic framework for participating in cooperation and free-riding in federated learning to support spectrum sensing for NextG communications.
2. Relate Work
Spectrum sensing is the basis and key to achieving spectrum sharing, improving the efficiency of spectrum utilization, and ensuring the security of spectrum resources in CR technology. So far, many papers have applied spectrum sensing technology in IoT field. For the issue of energy efficiency in spectrum sensing, Ref. [13] investigated how to use spectrum sensing technology to improve the energy efficiency of CIoT networks, and proposed a new two-way information exchange algorithm and optimal transmit power allocation technique to achieve higher dynamic spectrum sensing capability and data throughput. In addition, cooperative spectrum sensing has been studied extensively. Ref. [14] proposes an integrated CSS and access control model to maximize the throughput of the cognitive industrial IoT by jointly optimizing the sensing time, the number of sensing nodes, and the transmit power of each node. Dynamic spectrum access is an important research direction in CIoT networks. It provides an effective way for existing radio networks to optimize system performance, enhance resource utilization, and improve system reliability. In ref. [15], the benefits of cooperative communication and cognitive radio networks (CRN) are merged to meet IoT networks’ needs. In this work, the hybrid overlay-underlay CRN is employed to guarantee both SU stability and an acceptable total throughput. In ref. [16], spectrum aware Ad hoc on-demand distance vector routing protocol is proposed without fixed base stations, aiming to address the routing needs in future IoT environments.
There are now numerous papers focusing on free-riding behavior. In ref. [17], Adar et al. analyzed the user traffic in the Gnutella system and found that there were a large number of free-riding users in the system, with only about 28% of the users sharing files. To address the problem of the behavior of free-riders in the system, Ref. [18] proposes a peer-to-peer protocol with adaptive and self-organizing topology to punish malicious peers and free-riders by considering the trustworthiness. In ref. [19], machine learning based malicious signal detection is employed for cognitive radio networks. In [20], To enhance cooperation among agents, one of the main goals of the multi-agent system is to solve the possible free-riding problem. To address this problem, the authors propose a novel strategy that allows agents to manipulate the utility of each adversary simultaneously, further promoting mutual cooperation among all agents. Although the above literature has emphasized the users’ free-riding problem, it does not consider the scheduling problem of dynamic spectrum access techniques for SUs to further improve the system’s utility.
Game theory [21] is an effective tool for analyzing optimal behavior among rational decision makers. Game theory has been widely used in distributed CR networks to effectively improve system performance and to help SUs make better use of spectrum resources. With the increasingly complex interaction behavior of IoT devices [22], single-layer networks can no longer meet the needs of the system, and the study of multilayer networks has become a key to the development of many fields. To explore the cooperative behavior among rational individuals, researchers have combined complex networks and game theory [23], which is more helpful to study the interaction behavior problem among users in complex networks. Ref. [24] explored an important tradeoff of CSS among SUs in cognitive radio networks and proposed a distributed coalition formation game based on genetic algorithms to select the optimal coalition leader to motivate SUs to actively participate. Ref. [25] proposed a potential game-based spectrum access and power control method to solve the problem of how to achieve optimal throughput in a multibeam cognitive satellite communication network. Furthermore, game theory is also widely applied to solving the free-rider problem. In ref. [26], the free-riding problem was first modeled as a public goods game. In ref. [27], the authors considered an evolutionary game model that allows SUs to choose between free-riding and normal sensing strategies.
Although [12,26,27] considered two sensing attitudes of SUs, they did not address the scheduling problem of SUs when sensing multiple PU channels, which did not work well in multi-channel cooperative spectrum sensing. In the case where SUs cooperatively sense multiple PU channels, most SUs may tend to sense the same PU channel due to geographical location and other factors, resulting in a serious shortage of SUs sensing other PU channels, which greatly affects the detection performance. This may lead to a waste of spectrum resources and even affect the normal communication of PUs. Therefore, it is necessary to consider using dynamic spectrum access to solve the scheduling problem of SUs in this case.
Different from past research, this paper focuses on the problem of SUs’ free-riding behavior in Energy Harvesting CIoT (EH-CIoT) networks. A punishment mechanism is established to stimulate SUs to sense the spectrum normally during the sensing process. For the system model with multiple PUs and SUs, a two-layered game-based cooperative spectrum sensing and access method is proposed to dynamically coordinate the strategies of SUs. Simulation results show that the proposed method significantly improves the overall throughput of the system, and the allocation of SUs in the coalition is more fair compared with traditional methods.
The rest of this paper is organized as follows: Section 3 describes the system model and time slot structure for cooperative spectrum sensing and access and gives the optimization problem modeling of this paper. Section 4 proposes a two-layer game to solve the proposed problems in Section 3. In Section 5, simulation results are presented. Finally, the conclusion is made at last in Section 6.
3. System Model and Problem Description
3.1. System Models
Consider an EH-CIoT network covered by M PU bands, which share channels with N SUs in overlay mode. When the PU bands are not occupied, each SU can only sense and access one band in the same time slot due to the hardware limitation. As shown in Figure 1, when SUs upload their sensing results, there is a possibility that the sensing results will be listened to by other users, and the listeners will decide to become CUs or FUs according to their utility. In each time slot, PU bands are sensed simultaneously. The SUs are divided into M coalitions for sensing different PU bands, and each SU can freely choose the sensing attitudes (to become CU or FU) and the band of which PU to access. In each coalition, the SU with the highest detection probability is considered the Coalition Head (CH). CH plays the role of FC in the coalition.
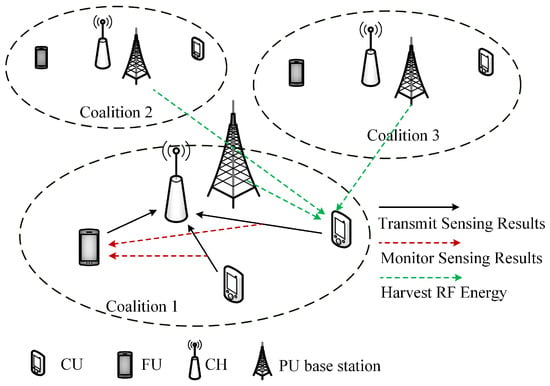
Figure 1.
System model.
Due to its simplicity and low cost, the energy detector is chosen in this paper as the spectrum sensing technique to sense the PU. The noise is assumed to be an independent, identically distributed random process with a zero mean and a variance . In the Rayleigh fading environment, the detection probability and false alarm probability of the i-th secondary user detecting the state of the j-th primary user channel are:
and
where is the detection threshold of PU, m is the time-bandwidth product, and denotes the average signal-to-noise ratio of the received signal from to , is the incomplete gamma function, and is the gamma function. When detecting the PU channel, the probability of missing detection is:
In the coalition , since the control channel transmits sensing results of 0 and 1, the corresponding error reporting probability [28] can be expressed as follows:
where is the average SNR for bit reporting between and CH. The decision fusion criterion at CHs is the OR verdict criterion. By cooperative sensing, the detection probability and the false alarm probability of the coalition are respectively given as follows:
and
where , and are given by Equations (2)–(4).
3.2. Time Slot Structure
In this paper, the harvested energy is derived from the RF energy transmitted by the PU. As shown in Figure 2, the sensing result of the sensing phase directly affects the action of the SU in the next phase. If the PU is present, the SU harvests energy in the data transmission phase, and if the PU is not present, the SU transmits data in the data transmission phase.
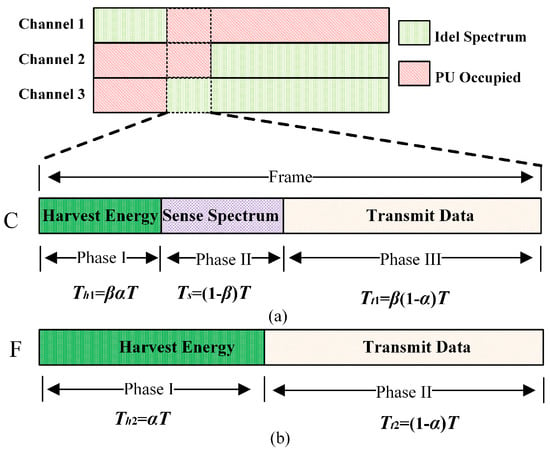
Figure 2.
Time slot structure of the proposed method.
CUs follow the time frame structure shown in Figure 2a, which can be divided into three phases: energy harvesting phase, the spectrum sensing phase, and the data transmission phase. FUs follow the time frame structure shown in Figure 2b and can be divided into two phases, energy harvesting phase and the data transmission phase. Compared with CUs, FUs are not involved in spectrum sensing, so they have more time to harvest energy and transmit data.
If the PU is present, according to the time slot structure, the energy harverted by CUs and FUs can be calculated separately as follows:
and
If the PU is absent, according to the time slot structure, the energy harvested by CUs and FUs can be calculated separately as follows:
and
where is the probility of the presence of PU, and are the weights, and , T is the duration of a time slot, is the energy arrival rate at SU, given by:
where is the transmission power of PU and is the path loss of PU and SU.
When PU is absent, and not detected by SU, the average throughput of SU is
When PU is present, and not detected by SU, the average throughput of the SU is
Let denotes the probability that the PU is absent, then the total throughput of SU is
In dynamic spectrum access, it is required that the SUs’operation should not conflict or interfere with the PUs, and should be very close to one. Moreover, we usually have due to the interference from the PUs to the SUs, the second term on the RHS of (14) is much smaller than the first term on the RHS of (14). To simplify the formulation, the total throughput of SU access PU channel can be expressed as follows:
where denotes the probability that the PU is not present and denotes the average throughput of SU when PU is not present. is the duration of the data transmission phase in a time slot. According to Equation (15), the throughput of CU can be expressed as follows:
where , is the transmission power of SU. Similarly, the throughput of FU can be expressed as follows:
where .
3.3. Optimization Problem Modeling
The SUs aim to accomplish a joint task, which is to protect the PU from interference, achieve a required detection threshold for fusion detection probability through CSS, and obtain high throughput by accessing the PU spectrum. CUs can eavesdrop on sensing results and have more time for their own data transmission. However, if a sufficient number of SUs do not sense the PU channel, all of them may get very low throughput. Therefore, the SUs need to try different strategies in each time period and learn the optimal strategy from their strategic interactions.
The utility of SUs consists of four components: the benefit obtained based on throughput, the benefit obtained from harvesting energy, the cost of consuming energy during data transmission, and the penalty for free-riders based on the coalition detection probability. Considering that FUs do not contribute to the coalition detection probability, a penalty needs to be imposed on them. The penalty function can be expressed as follows:
where is a predetermined parameter defining the harshness of the penalty, and is the detection probability of detecting PU. The sigmoid function for the satisfaction degree of the detection performance is calculated as follows:
where is the predefined requirement for the uncertainty, and decides on the steepness of the satisfactory curve. The utility functions of CUs and FUs can be defined as follows:
and
where the first term on the RHS of Equations (20) and (21) is the satisfaction function of each SU with respect to the achievable throughput, and for simplicity we choose to set , where is the uniform unit parameter for the SUs to convert the throughput into the corresponding benefit, and are the energy consumed by CUs and FUs during data transmission. Then Equations (20) and (21) can be expressed as follows:
and
To improve the utility of SUs, it is crucial to increase the system throughput and enhance the cooperative detection probability to reduce penalties, as indicated Equations (20) and (21), and it can be inferred that system throughput is primarily influenced by the false alarm probability. Increasing the false alarm probability can improve the system’s throughput. In order to improve SUs’ throughput, the problem of whether SUs participate in cooperative sensing and which coalitions SUs choose to access is formulated as an optimization problem. Equations (22) and (23) need to be optimized simultaneously, and the problem formulation is given as follows:
4. Two-Layer Cooperative Sensing and Access Game (TL-CSAG)
As shown in Figure 3, based on evolutionary game and hedonic coalition game models, an iterative algorithm for solving the game problem mentioned above is proposed in this section. In this paper, the cooperative spectrum sensing and access mechanism is modeled as a two-layer game, where the problem of whether SUs participate in cooperative sensing is modeled as an evolutionary game and the problem of which coalitions SUs choose to access is modeled as a hedonic coalition game. In this game, the SUs are considered participants, and is considered a utility function of SU. The SUs’ sensing attitude preference in the coalitions can be described as follows:
where denotes the sensing attitude preference of SU in coalition in the t-th time slot, . indicates that SU will choose to sense PU channel in coalition , and indicates that SU will choose to be a free-rider in coalition . The SU’s strategy is denoted by and denotes the SU choose the coalition . To provide a clearer depiction of how SUs can modify their utility through specific actions, its utility function can be rewritten as follows:
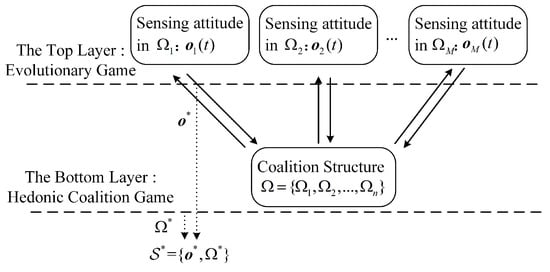
Figure 3.
The structure of TL-CSAG model.
Each SU maximize its utility by optimizing its sensing attitude and then enter a coalition. Thus, the optimization problem is formulated as follows:
From Equations (24)–(27), it can be seen that the strategies of both problems are interdependent. Therefore, the interaction of SUs can be formulated as a noncooperative game. Under the condition of Nash Equilibrium (NE), each SU’s strategy cannot get better utility without changing the strategy of other SUs. To comprehensively consider the feasibility and convergence of the two-level game algorithm, the definition of NE is given as follows:
Definition 1.
Let and be the NEs of the sensing attitude strategy and the coalition formation strategy derived by the proposed TL-CSAG, respectively. , is an NE of TL-CSAG, and it can be given by:
where , is the stable strategy for all SUs except SU.
4.1. The Top Layer Game: Sensing Attitude Strategy in the Coalition
This subsection analyzes the evolution of SUs’ sensing attitudes using the idea of evolutionary game theory. In each time slot, SUs calculate their own utility. If SU’s utility (C) for participating in sensing in is higher than the average utility , then in the next time slot, the probability of SU participating in sensing will increase. To describe the evolution of the sensing attitude of SU in , the following differential equations [29] are constructed as follows:
where is the adjustment step size determined by SU. is the probability that in the t-th time slot SU participates in sensing in .
In the next time slot, the probability of SU participation in sensing in can be calculated as follows:
Equation (30) describes the dynamic process of choosing its sensing attitude, where the sum of the probabilities of participating in sensing and free-riding is equal to 1.
This paper first study the game of two SUs in , i.e., . The payoff table of the two SUs is shown in Table 1 according to Equations (19) and (20), where , , , , , .

Table 1.
Payoff table of a two-user.
Let and denote the probability that and take attitude “C”, respectively, and , then the expected payoff while chooses to contribute is expressed as follows:
The mean utility function of is given by:
Therefore, the replicator dynamics of the two SUs using Equation (26) will be:
and
where , and . According to the conditions of equilibrium, we have and , then, we get four equilibrium points: , and the mixed strategy equilibrium . The Jacobian matrix is formed by taking the partial derivatives of Equations (38) and (39), then we can obtain:
where
From the stability conditions of the Jacobian, the system converges when det and tr. The stability conditions for the four equilibrium points are:
(1) When , the strategies of and converge to (C, F).
(2) When , the strategies of and converge to (F, C).
(3) When and , the strategies of and converge to (C, C).
(4) When and , the strategies of and converge to (C, F) or (F, C) based on the initial adopted strategies.
The above mentioned has demonstrated the of the two SUs. However, due to the different utility functions of different SUs, it is difficult to obtain in the case of multiple SUs. Through repeated games, SUs can autonomously adapt to the changing environment, and each SU has a clear sensing strategy.
4.2. The Bottom Layer Game: Coalition Formation Strategy
Regardless of what sensing attitude is adopted or which coalition is accessed, it will directly affect the utility of SUs. In the bottom layer game, the method used by SUs to solve the problem of which coalition to access is modeled as a hedonic coalition game. Next, the relevant definitions and related theorems are stated and proved.
Definition 2.
(Switch Rule): Given a partition of SUs’ set , SU decides to leave it current coalition and join another coalition , where , if and only if , where is the preference relation of . As a result, .
In order to evaluate the preferences of SU over its own sets of possible coalitions, the concept of preference relation is introduced [30] as follows:
where the relationship of means that SU prefers to join coalition over coalition . The which is the preference function of SU in can be expressed as follows:
where is the utility of in coalition and is the history set of . The history set contains the coalitions that SU has joined prior to formation of the current partition . In general, considering the history set can accelerate the convergence of the system.
According to the preference relationship of SU in Equation (34), it can be considered that when the history set of SU is not considered:
Theorem 1.
In TL-CSAG, the convergence rate of the sensing attitude strategy of SUs always precedes that of the coalition formation strategy. That is, the formation of precedes the formation of .
Proof.
When the sensing attitude strategy does not reach , according to Equation (26), the utility function of SUs has two states, and the utility is unstable. According to the description of Equation (39), when SU exchanges its coalition, it may have and will join coalition . However, in the subsequent time slots, due to the change of , may occur, and SU will switch coalition again. □
After reaches , SUs determines their possible strategy of obtaining high returns , and will focus on the distribution of SUs in the coalition. When a division is a NE, it means that there is no coalition that makes the SU strictly like to join, while the other coalitions are not hurt by the formation of this new coalition. The NE formed by the hedonistic coalition is specifically defined as follows:
Definition 3.
A parition is NE if .
Theorem 2.
Once the sensing attitudes of SUs reache the stability strategy , the final coalition will also achieve the stability strategy .
Proof.
After each switching operation, SUs will obtain higher utility in the new coalition. Given the number of channels M in the CIoT network and the number of SUs N, the total number of different partitions is , which is a finite number. Thus, from any given initial partition , the switching operation always terminates at some point after a finite number of iterations, where the coalition structure converges to the final partition . □
4.3. Algorithm Steps
Based on the analysis of the above two parts, the whole process of the proposed cooperative spectrum sensing and access algorithm based on the two-layer game can be obtained. During the initialization phase, each coalition selects the SU with the highest detection probability among all SUs as its CH. Furthermore, once a CH is selected by a coalition, it cannot be chosen by any other coalition, and it must always have a cooperative attitude. Furthermore, of each coalition’s sensing attitude strategy is obtained by the evolution among the SUs. On the basis of , the formed by SUs can be obtained through the switch rules, and the specific steps are shown in Algorithm 1.
| Algorithm 1: The proposed two-layer cooperative sensing and accsee game |
|
5. Simulation Analysis and Evaluation
In this section, MATLAB is used to simulate the performance of the proposed method. The spatial environment is established in a 1 km × 1 km planar coordinate system with 3 PUs and 15 SUs randomly distributed in the coordinate system; the sampling frequency is MHz, the bandwidth is 2 MHz and the time of each frame is T = 10 ms. The rest of the simulation parameters are shown in Table 2. The method proposed in [31] is used here as a comparison, which is denoted by “Con”. The random algorithm randomizes the sensing attitudes and the coalitons of all SUs, which are denoted by “Random”. In the following section, the final state distribution of SUs, the relationship between detection probability and cooperation probability, which represents the proportion of contributors out of 15 SUs, the factors affecting cooperation probability, the fairness of the SUs distribution in the coalition, and finally the performance of the three algorithms in terms of throughput are investigated.

Table 2.
Simulation parameters.
The initial coalition structure and the final coalition structure obtained from TL-CSGA are shown in Figure 4a,b, respectively. In these two figures, each colored box represents an SU, and the boxes in the same column belong to the same coalition. As can be seen from Figure 4b, SUs are finally distributed in three coalitions, and FUs are all distributed in coalition . When the CIoT network is stable, and for each coalition will be fixed. As FUs do not contribute to the two parameters, switching their coalitions after the system is stable will not affect the interests of other SUs. Eventually, all FUs will be concentrated in the coalition with the highest benefit. Since the number of CUs will affect , it is not advisable for each coalition to have too many CUs; otherwise, it will reduce the throughput of the system. Generally, CUs will be roughly evenly distributed in each coalition.
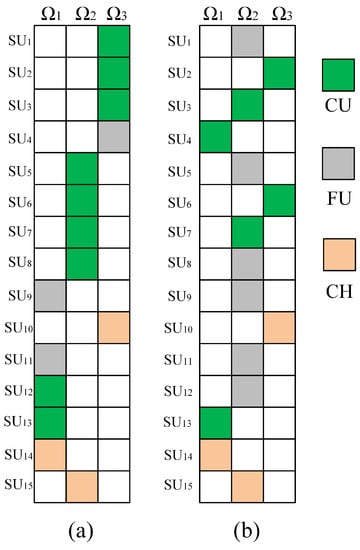
Figure 4.
(a) Initial and (b) Final coalition structures.
Figure 5 shows the relationship curves between the cooperation probability and the detection probability. As can be seen from Figure 5, with a certain number of SUs, the average detection probability of coalitions increases as the cooperation probability increases. In CSS, to avoid interference from SUs to PUs, the coalition detection probability needs to reach a certain threshold of , i.e., . As a certain number of SUs participate, when the cooperation probability reaches a certain value, the coalition detection probability can meet the requirement of . This paper assumes that the coalition detection probability needs to meet .
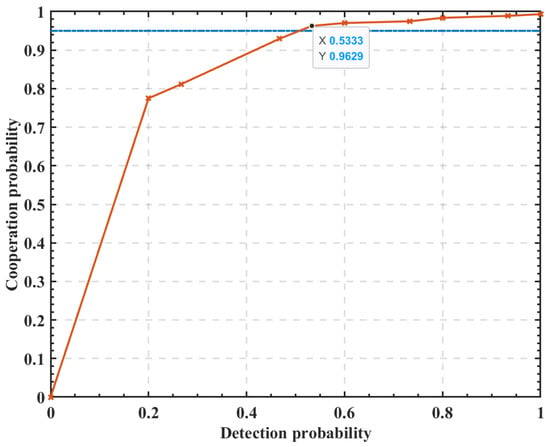
Figure 5.
The relationship between cooperation probability and detection probability.
Figure 6 shows the effect of and on the probability of cooperation with the 15 SUs. It can be seen that the increased value of is more likely to prompt SUs to adopt a cooperative sensing attitude. Moreover, it may also increase the probability of SUs cooperation with increasing values.
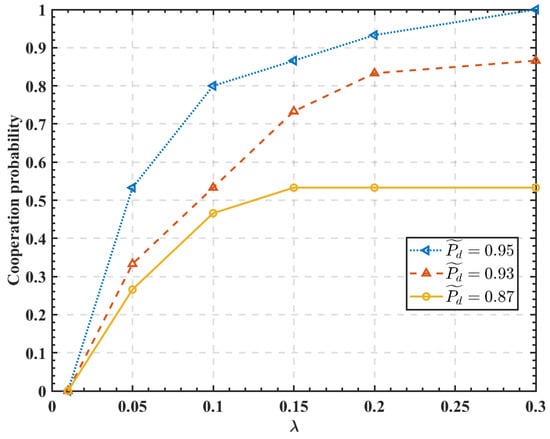
Figure 6.
Effect of the parameters and on the cooperation probability.
Figure 7 shows the effect of , , and detection probability on the penalty function. As shown in Figure 7, the higher the detection probability of the coalition, the smaller the penalty to FUs in the coalition. For the same detection probability, decreasing will reduce the penalty to FUs. In Figure 6, the effect of on the cooperation probability is essentially the effect of on the penalty function, which in turn affects the cooperation probability of SUs.
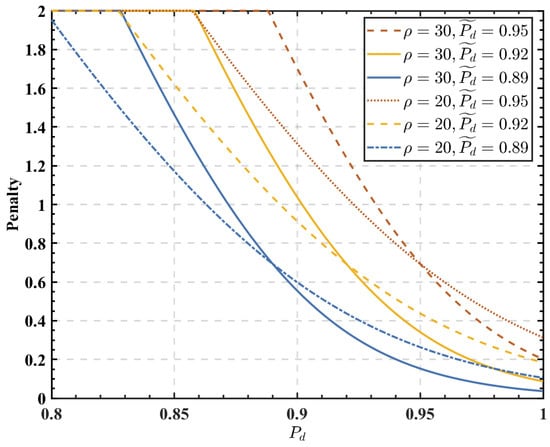
Figure 7.
Effect of the coalition detection probability on the user penalty.
Figure 8 shows the effect of the energy harvested by FUs and the weight factor on the cooperation probability of the system. In Figure 8, it can be observed that the more energy harvested by FUs, the lower the cooperation probability. The reason is that free-riders can obtain high profits by harvesting more RF energy. Similarly, a lower weight factor leads to a lower probability of cooperation. Under a certain amount of energy harvesting by FUs, increasing can improve energy harvesting benefits, reduce consumption during spectrum sensing, and improve data transmission efficiency. The simulation results show that the EH technology can provide more benefits to selfish SUs, and its application may exacerbate their free-riding behavior.
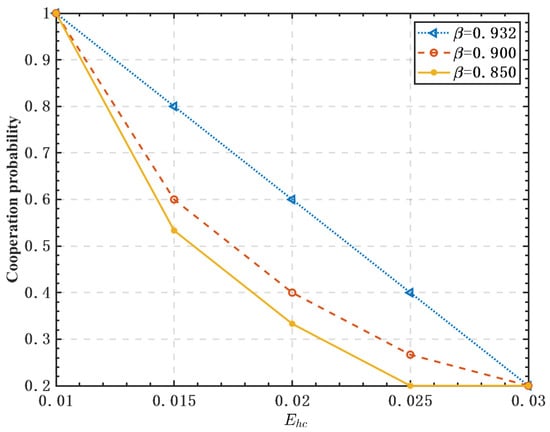
Figure 8.
Effect of the energy harvested by FUs on the cooperation probability.
In order to evaluate the fairness of SUs’ allocation of each coalition, Jain’s fairness is introduced [32], which is defined as follows:
Jain’s fairness evaluates the fairness of a set of values, where there are n coalitions and is the value allocated to SU, and it is located in . corresponds to the minimum fair allocation where only one SU obtains a non-zero value, and 1 corresponds to the maximum fair allocation where all SUs receive the same value.
By adjusting the cooperation probability to ensure , the fairness of different algorithms in SUs’ allocation was analyzed. The fairness indices of the three coalitions in Figure 4b are shown in Table 3, which lists the detection probabilities, false alarm probabilities, and corresponding fairness of the three coalitions using TL-CASG and “Con” algorithms. It can be seen that the fairness index of the TL-CASG algorithm is superior to that of the “Con” algorithm in terms of both detection probability and false alarm probability. This is because the “Con” algorithm only considers the distance between SUs and PUs when forming coalitions without considering the influence of SUs in other coalitions globally.

Table 3.
Coalition fairness analysis.
The relationship between throughput and the number of iterations of three algorithms is compared in Figure 9. By modeling the problem of which PU channel is sensed by SUs, the proposed algorithm can fully utilize the sensing capability of SUs in the multi-PU model and improve the overall system throughput. After reaching an equilibrium state in the “Con” algorithm and TL-CSAG, the average throughput of the proposed TL-CSAG algorithm increased by and , respectively, compared with the “Random” algorithm and “Con” algorithm.
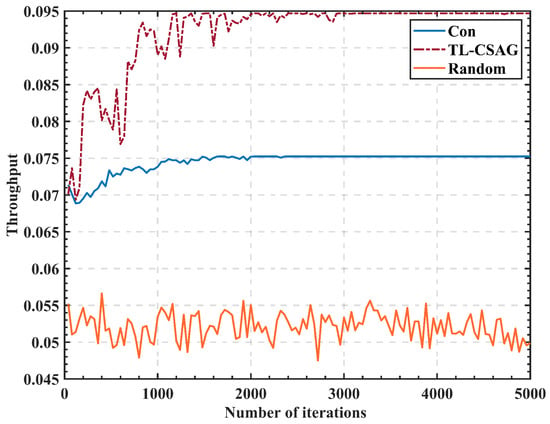
Figure 9.
Curve of throughput with number of iterations.
6. Conclusions
On the basis of the EH-CIoT model, this paper considers the free-riding problem of SUs. In order to prevent low system detection performance due to excessive SUs’ free-riding behavior, this paper establishes a penalty mechanism to stimulate SUs to sense the PU spectrum normally. To address the issue of whether SUs should free-ride and which PU spectrum to sense and access to gain higher benefits, a two-layer game-based cooperative spectrum sensing and access method is proposed to improve spectrum utilization and the fairness of the proposed method. Simulation results show that after the system reaches equilibrium, CUs are uniformly distributed among the three coalitions, but FUs are in the coalition with the highest profit. In the case of a fixed number of SUs, as the probability of cooperation increases, the average detection probability of coalitions also increases. At the same time, this paper also studied the impact of different parameters on the probability of cooperation, and simulation results confirmed that the more energy harvested, the lower the probability of SUs adopting a cooperative sensing attitude. Furthermore, Jain’s fairness concept is introduced to evaluate the higher fairness of the coalition in SUs’ allocation in our algorithm. Finally, this paper studied the impact of using different algorithms on throughput, and the results show that the proposed algorithm improves throughput by and 26.3% compared with traditional algorithms. In the future study, we will further explore the secrecy and energy-efficient resource allocation for our proposed network. In the future study, we will further explore the application of free-riders in mobile networks and optimize algorithm models to achieve faster iteration speeds.
Author Contributions
Conceptualization, K.J. and J.W.; methodology, K.J. and C.M.; software, C.M., J.W. and R.L.; validation, J.W., R.L. and H.H.; formal analysis, K.J., H.H., C.M. and R.L.; investigation, K.J. and C.M.; resources, K.J., H.H. and C.M.; data curation, K.J., H.H. and W.J.; writing—original draft preparation, C.M.; writing—review and editing, C.M., W.J. and H.H.; visualization, C.M., R.L. and J.W.; supervision, K.J. and H.H.; project administration, K.J., C.M. and H.H.; funding acquisition, H.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Natural Science Foundation of China under Grants No. 61871133 and in part by the Industry-Academia Collaboration Program of Fujian Universities under Grants No. 2020H6006.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Voicu, A.M.; Simić, L.; Petrova, M. Survey of Spectrum Sharing for Inter-Technology Coexistence. IEEE Commun. Surv. Tutor. 2018, 21, 1112–1144. [Google Scholar] [CrossRef]
- Giuliano, A.; Hilal, W.; Alsadi, N.; Gadsden, S.A.; Yawney, J. A Review of Cognitive Dynamic Systems and Cognitive IoT. In Proceedings of the 2022 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 1–4 June 2022; pp. 1–7. [Google Scholar]
- Awin, F.; Abdel-Raheem, E.; Tepe, K. Blind Spectrum Sensing Approaches for Interweaved Cognitive Radio System: A Tutorial and Short Course. IEEE Commun. Surv. Tutor. 2019, 21, 238–259. [Google Scholar] [CrossRef]
- Liu, X.; Zheng, K.; Chi, K. Cooperative Spectrum Sensing Optimization in Energy-harvesting Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 2020, 19, 7663–7676. [Google Scholar] [CrossRef]
- Hu, F.; Chen, B.; Zhu, K. Full Spectrum Sharing in Cognitive Radio Networks toward 5G: A Survey. IEEE Access 2018, 6, 15754–15776. [Google Scholar] [CrossRef]
- Liu, X.; Hu, S.; Li, M.; Lai, B. Energy-Efficient Resource Allocation for Cognitive Industrial Internet of Things with Wireless Energy Harvesting. IEEE Trans. Ind. Inform. 2021, 17, 5668–5677. [Google Scholar] [CrossRef]
- Kaswan, A.; Jana, P.K.; Das, S.K. A Survey on Mobile Charging Techniques in Wireless Rechargeable Sensor Networks. IEEE Commun. Surv. Tutor. 2022, 24, 1750–1779. [Google Scholar] [CrossRef]
- Vu, H.S.; Nguyen, N.; Ha-Van, N.; Seo, C.; Le, M.T. Multiband Ambient RF Energy Harvesting for Autonomous IoT Devices. IEEE Microw. Wirel. Compon. Lett. 2020, 30, 1189–1192. [Google Scholar] [CrossRef]
- Gharib, A.; Ejaz, W.; Ibnkahla, M. Distributed Spectrum Sensing for IoT Networks: Architecture, Challenges, and Learning. IEEE Internet Things J. 2021, 4, 66–73. [Google Scholar] [CrossRef]
- Pal, D.; Khethavath, P.; Thomas, J.P.; Mangla, U. KeyPIn-mitigating The Free Rider Problem in the Distributed Cloud Based on Key, Participation, and Incentive. J. Cloud Comput. 2022, 11, 8. [Google Scholar] [CrossRef]
- Sagduyu, Y.E. Free-Rider Games for Federated Learning with Selfish Clients in NextG Wireless Networks. In Proceedings of the 2022 IEEE Conference on Communications and Network Security (CNS), Austin, TX, USA, 3–5 October 2022; pp. 365–370. [Google Scholar]
- Ansere, J.A.; Han, G.; Wang, H. A Reliable Energy Efficient Dynamic Spectrum Sensing for Cognitive Radio IoT Networks. IEEE Internet Things J. 2019, 6, 6748–6759. [Google Scholar] [CrossRef]
- Liu, X.; Jia, M.; Zhou, M. Integrated Cooperative Spectrum Sensing and Access Control for Cognitive Industrial Internet of Things. IEEE Internet Things J. 2023, 10, 1887–1896. [Google Scholar] [CrossRef]
- Moayedian, N.S.; Salehi, S.; Khabbazian, M. Fair resource allocation in cooperative cognitive radio iot networks. IEEE Access 2020, 8, 191067–191079. [Google Scholar] [CrossRef]
- Cicioğlu, M.; Çalhan, A.; Miah, M.S. An Effective Routing Algorithm for Spectrum Allocations in Cognitive Radio Based Internet of Things. Concurr. Comput. 2022, 34, e7368. [Google Scholar] [CrossRef]
- Adar, E.; Huberman, B.A. Free Riding on Gnutella. First Monday 2000, 5, 32–35. [Google Scholar] [CrossRef]
- Condie, T.; Kamvar, S.D.; Garcia-Molina, H. Adaptive Peer-to-Peer Topologies. In Proceedings of the Fourth International Conference on Peer-to-Peer Computing, Zurich, Switzerland, 27 August 2004; pp. 53–62. [Google Scholar]
- Turkyilmaz, Y.; Senturk, A.; Bayrakdar, M.E. Employing Machine Learning Based Malicious Signal Detection for Cognitive Radio Networks. Concurr. Comput. 2023, 35, e7457. [Google Scholar] [CrossRef]
- Li, K.; Hao, D. Cooperation Enforcement and Collusion Resistance in Repeated Public Goods Games. In Proceedings of the AAAI Conference on Artificial Intelligence, Palo Alto, CA, USA, 17 July 2019; pp. 2085–2092. [Google Scholar]
- An, Q.; Cheng, S.; Li, C.; Li, L.; Peng, H. Game Theory-based Control Strategy for Trajectory Following of Four-wheel Independently Actuated Autonomous Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 2196–2208. [Google Scholar] [CrossRef]
- Guo, D.; Fu, M.; Li, H. Cooperation in Social Dilemmas: A Group Game Model with Double-layer Networks. Future Internet 2021, 13, 33. [Google Scholar] [CrossRef]
- Hagen, A.; von Mouche, P.; Weikard, H.P. The Two-stage Game Approach to Coalition Formation: Where We Stand and Ways to Go. Games 2020, 11, 3. [Google Scholar] [CrossRef]
- Rajendran, M.; Duraisamy, M. Distributed Coalition Formation Game for Enhancing Cooperative Spectrum Sensing in Cognitive Radio Ad Hoc Networks. IET Netw. 2020, 9, 12–22. [Google Scholar] [CrossRef]
- Wang, J.; Guo, D.; Zhang, B.; Jia, L.; Tong, X. Spectrum Access and Power Control for Cognitive Satellite Communications: A Game-theoretical Learning Approach. IEEE Access 2019, 7, 164216–164228. [Google Scholar] [CrossRef]
- Kishor, A.; Niyogi, R. A Game-theoretic Approach to Solve The Free-rider Problem. In Proceedings of the 2017 Tenth International Conference on Contemporary Computing (IC3), Noida, India, 10–12 August 2017; pp. 1–6. [Google Scholar]
- Elnahas, O.; Elsabrouty, M.; Muta, O.; Furukawa, H. Game Theoretic Approaches for Cooperative Spectrum Sensing in Energy-harvesting Cognitive Radio Networks. IEEE Access 2018, 6, 11086–11100. [Google Scholar] [CrossRef]
- Hao, X.; Cheung, M.H.; Wong, V.W.S.; Leung, V.C.M. Hedonic Coalition Formation Game for Cooperative Spectrum Sensing and Channel Access in Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 1978, 11, 3968–3979. [Google Scholar]
- Taylor, P.D.; Jonker, L.B. Evolutionary Stable Strategies and Game Dynamics. Math. Biosci. 2012, 40, 145–156. [Google Scholar] [CrossRef]
- Cheng, D.; Xu, T.; Qi, H. Evolutionarily Stable Strategy of Networked Evolutionary Games. IEEE Trans. Neural. Netw. Learn. Syst. 2014, 25, 1335–1345. [Google Scholar] [CrossRef]
- Jiang, C.; Chen, Y.; Gao, Y.; Liu, K.R. Joint Spectrum Sensing and Access Evolutionary Game in Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 2013, 12, 2470–2483. [Google Scholar] [CrossRef]
- Sediq, A.B.; Gohary, R.H.; Schoenen, R.; Yanikomeroglu, H. Optimal Tradeoff between Sum-rate Efficiency and Jain’s Fairness Index in Resource Allocation. IEEE Trans. Wirel. Commun. 2013, 12, 3496–3509. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).