An Innovative Clustering Hierarchical Protocol for Data Collection from Remote Wireless Sensor Networks Based Internet of Things Applications
Abstract
1. Introduction
1.1. Novelty and Contributions
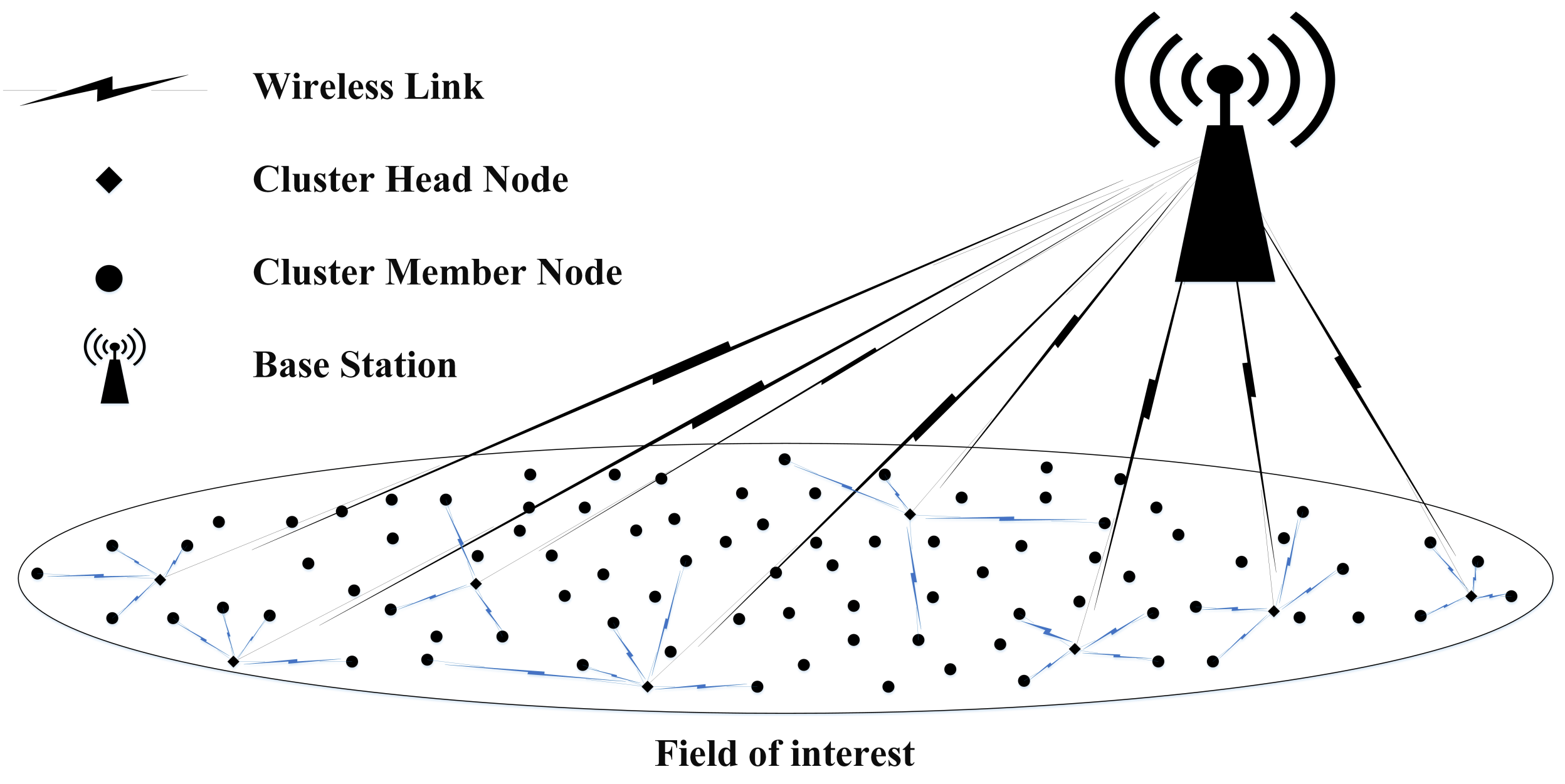
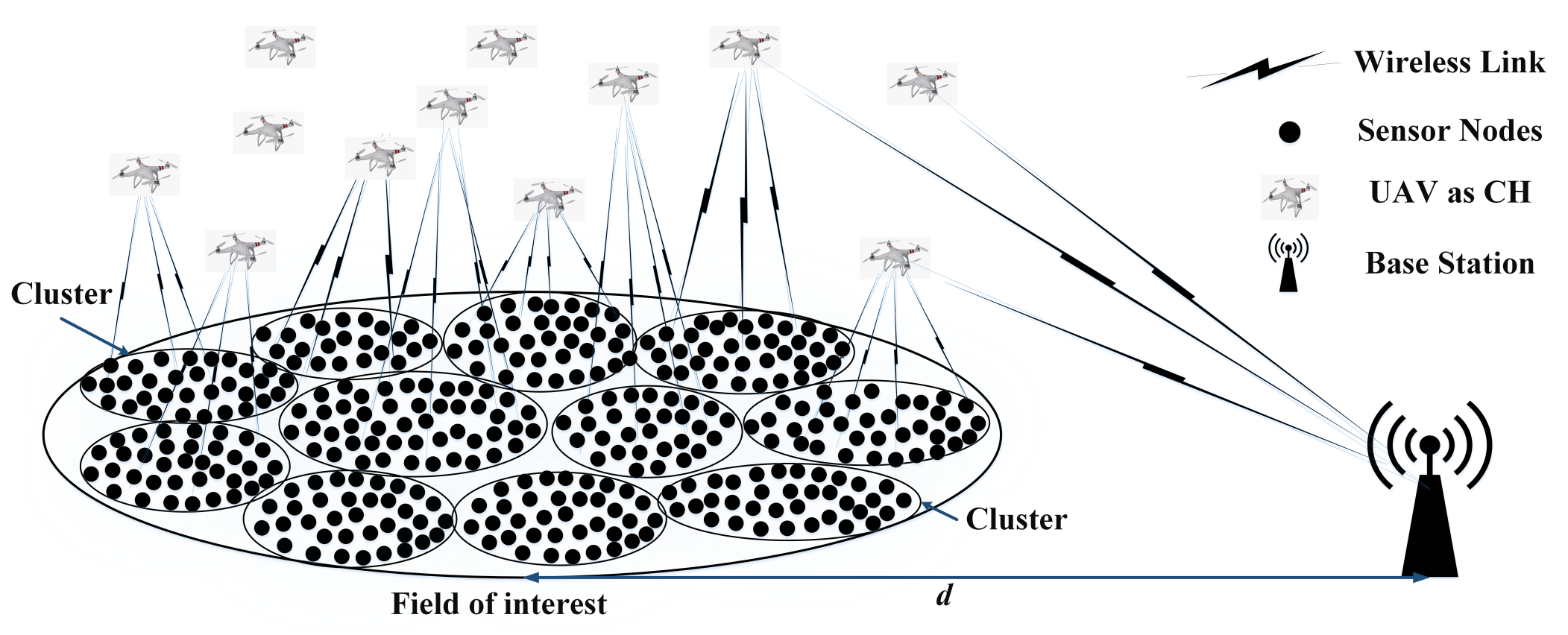
- We design and develop a novel cluster-based routing protocol, EEUCH, for WSN-based applications of IoT in which there is no CH election phase. UAVs act as CHs by default and are responsible for the collection of data packets from the FoI.
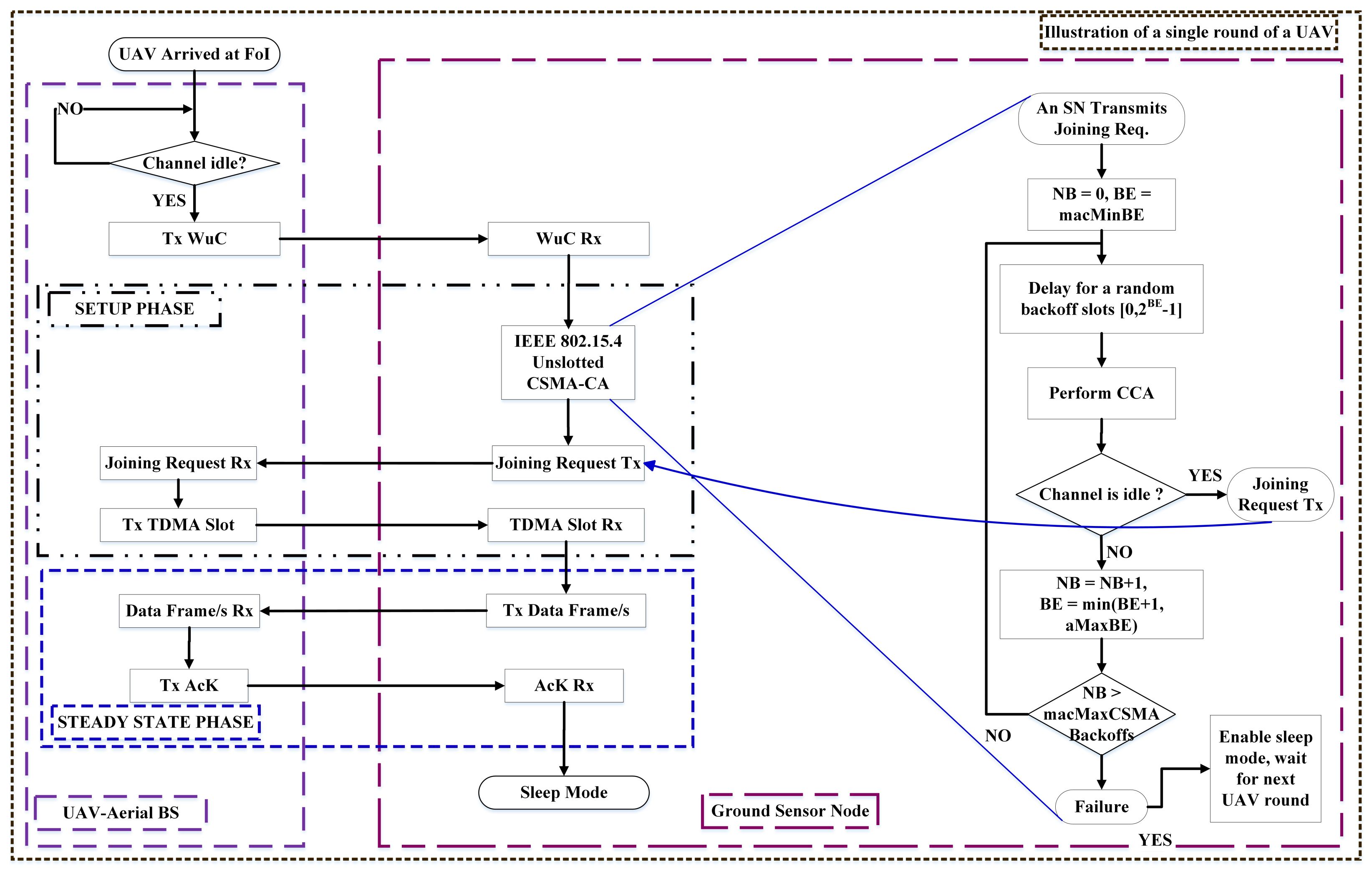
- We create a novel data flow model in which UAVs act as ABSs. This model uses a combination of clear channel assignment (CCA), carrier sense multiple access/collision avoidance (CSMA-CA), and time division multiple access (TDMA) slots to ensure energy-efficient and reliable data collection.
- We extend the concept of WuR to the network layer in EEUCH for two main reasons: to enhance the network lifetime, stability time, energy efficiency, and the overall data collection from the FoI, and to address the challenge of cluster overlapping.
- A novel UAV-assisted clustering hierarchical model for remote data collection that ensures nonoverlapping and independent clusters and offers a high degree of flexibility in network size is presented.
- The results of our proposed protocol outperform the benchmark cluster-based routing protocols (i.e., homogeneous, two-tier, and three-tier heterogeneous) with significant gains in nine key network performance parameters.
1.2. Paper Organization
2. Related Work
- 1.
- LEACH [19] is proposed for homogeneous WSNs, where all the SNs have equal initial energy . The CH is selected randomly from all the deployed N number of SNs who belong to a set G (i.e., set of those SNs which were not selected as CH in the previous rounds). All those SNs who belong to set G generate a random number between 0 and 1, and this number is compared with a threshold function , i.e.,where N is the number of deployed SNs, p is the predefined probability of CHs in SNs which is /, and r is the current round number. An SN from set G becomes a CH if ; otherwise, CM.
- 2.
- In LEACH-C [20], the CH is selected by the BS by considering the remaining energy and location of the SNs. At the end of each round, each SN sends information about its remaining energy and location to the BS. The BS calculates average energy based on the remaining energies of all the SNs. On the basis of the calculated average energy and locations of the SNs, CH is selected for each cluster by the BS.
- 3.
- TEEN [22] and LEACH use the same procedure for CH election, but in the case of TEEN, the CH sends the collected data from its CMs to the upper level of cluster (i.e., a cluster of CHs) which has its own CH that collects data and sends them to the next level of cluster. This process is repeated. At the end, only one CH is reporting to the BS. Furthermore, following the TEEN protocol, SNs sense their environment continuously but do not report until the sensed entity or value is greater than the hard threshold (), which is a predefined value. Whenever the sensed value exceeds , the SN triggers the transmitter to report the value. This is why TEEN sometimes misses some important information from the FoI.
- 4.
- IEE-LEACH [23] considers new threshold function with different probability function of CH selection. The new probability function depends on p, remaining and initial energy of SN which is candidate for CH, average and total energy of WSN, and total number of SNs in the FoI.
- 5.
- SEP [21] is the first protocol which considers the two-tier heterogeneity in WSN in terms of different initial energy for normal and advance SNs. Normal SNs have normal initial energy , while advance SNs are equipped with relatively higher initial energy than . SEP considers the optimal number of CHs, which is derived analytically. Furthermore, SEP defines two different threshold functions for two different types of SNs, i.e., normal and advance, with different probabilities of CH selection.
- 6.
- EEECA-THWSN [24] considers three-tier heterogeneity in WSNs which consists of standard, intermediate, and advanced SNs. Standard SNs have lower initial energy than intermediate SNs, and intermediate SNs have lower initial energy than advanced SNs. Furthermore, EEECA-THWSN proposes three different threshold function with there respective probabilities, for standard, intermediate, and advanced SNs.
3. System Model
3.1. Network Model and Assumptions
- 1.
- All SNs have individually unique identification.
- 2.
- SNs and BSs are stationary.
- 3.
- SNs are not utilized again once dead, i.e., after full consumption of their battery.
- 4.
- All SNs must be equipped with WuR, i.e., they must have a WuRx with extremely low power consumption and MR for data packets transmission.
3.2. Energy Consumption Model
4. Proposed Protocol
4.1. Cluster Formation
4.1.1. Setup Phase
4.1.2. Steady-State Phase
4.2. Data Flow Model
5. Network Performance Parameters
- 1.
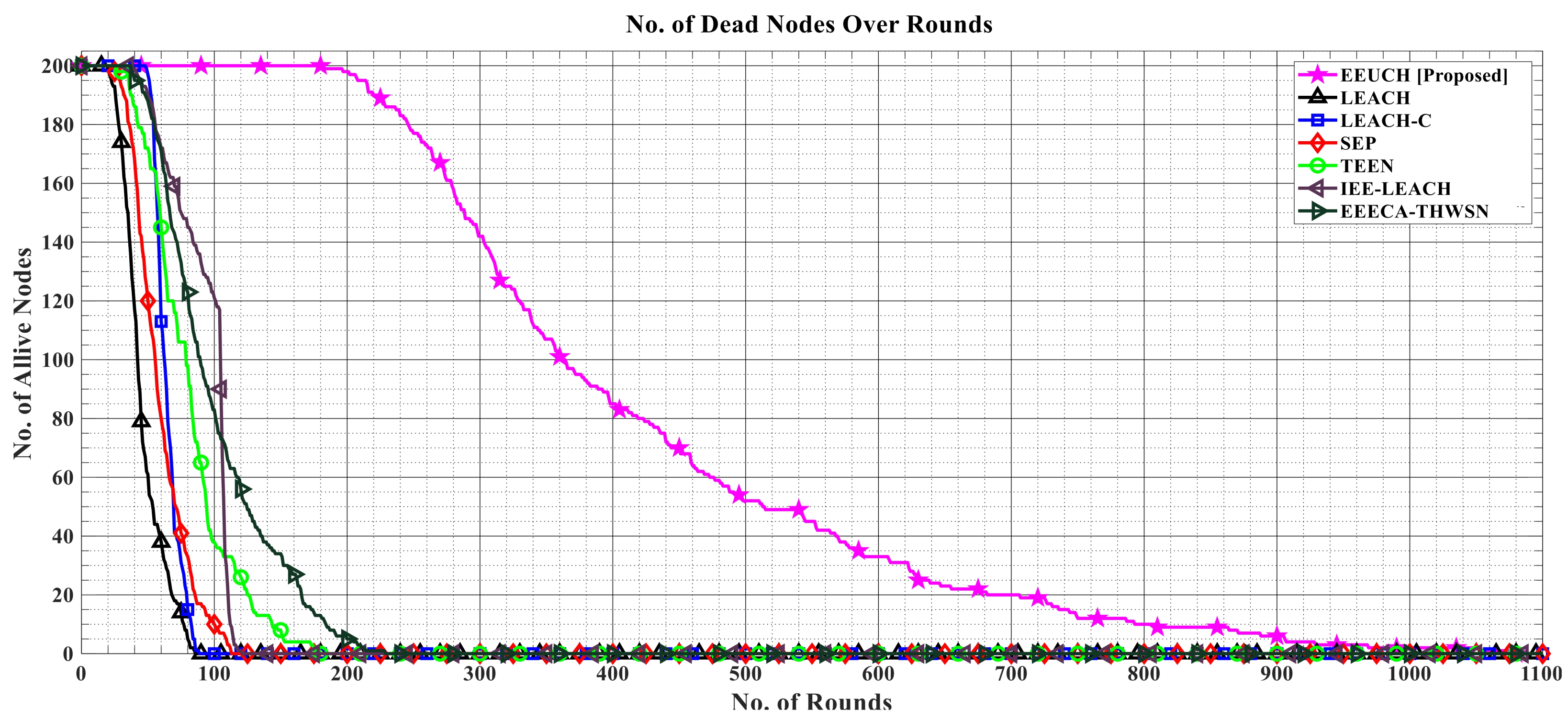
- Number of alive SNs: This parameter represents the number of SNs having residual energy () greater than zero, known as alive SNs, as the rounds pass. Every single data packet transmission consumes a unit energy, and as several data packets are transmitted in a single round from SN to UAV, the SN energy is reduced from initial energy to zero as the rounds pass. This parameter provides an important metric of how many SNs are still operational at a particular round of the protocol. The higher the number of alive SNs, the better the protocol’s efficiency in energy conservation, prolonging the network lifetime.
- 2.
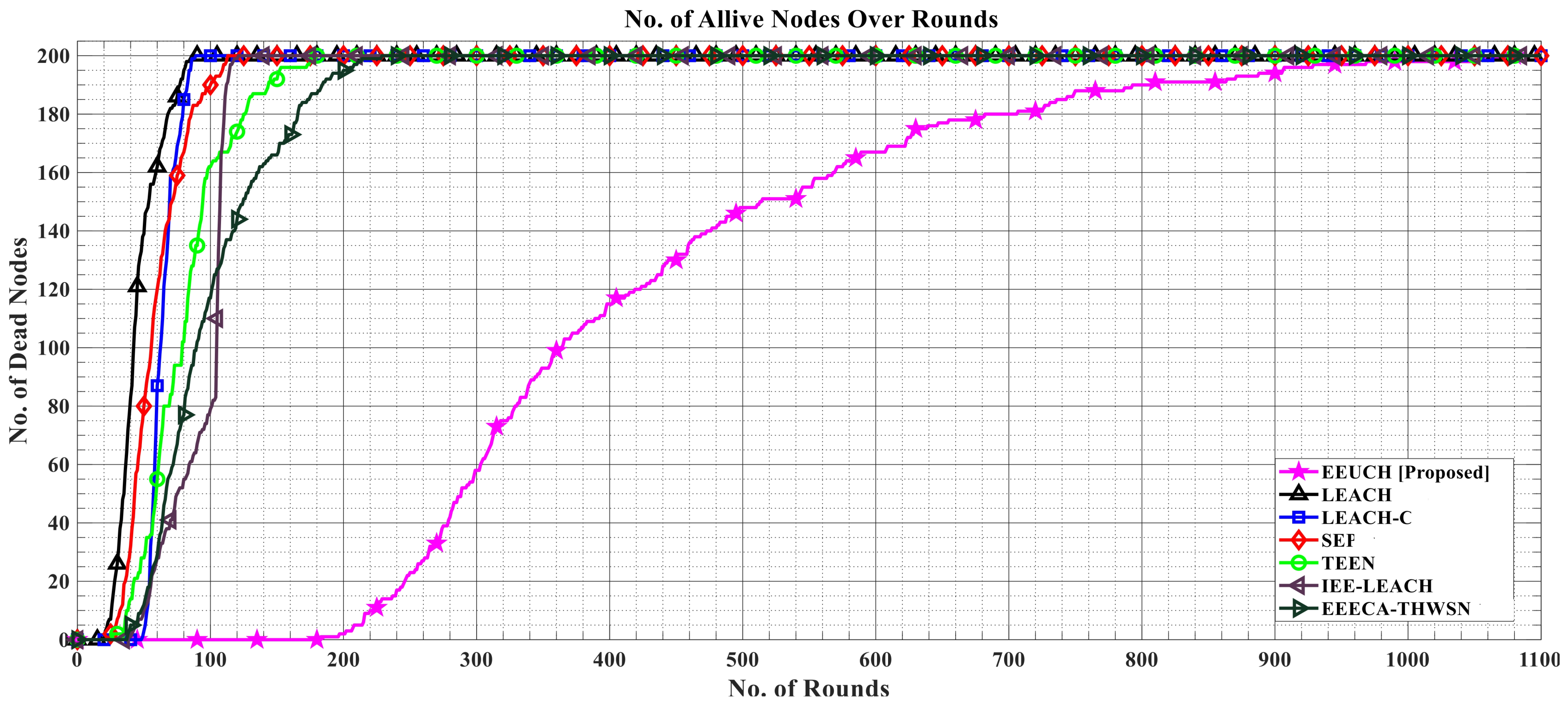
- Number of dead SNs: This parameter indicates the number of SNs whose residual energy drops to zero during the rounds of the protocol. As each data packet transmission consumes a unit of energy, the SNs gradually consume their initial energy and eventually become unable to transmit data. This parameter indicates the number of SNs that have failed and cannot participate in subsequent rounds.
- 3.
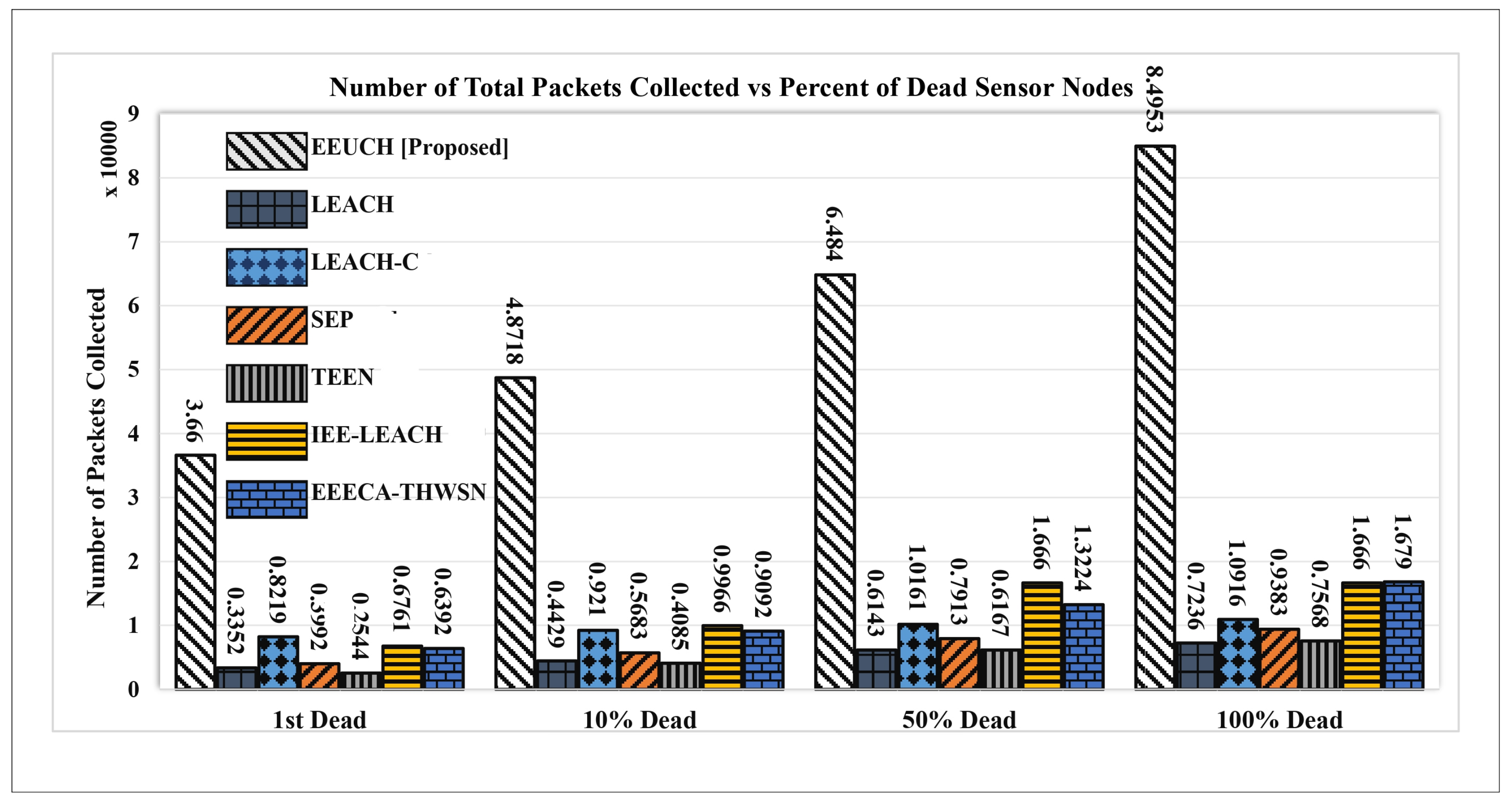
- Total number of packets collected from FoI: This parameter determines the total number of data packets collected from the FoI over the course of the network’s lifetime. This metric demonstrates the overall effectiveness of the protocol in gathering data. A more efficient protocol should be able to collect a larger number of data packets while extending the network lifetime.
- 4.
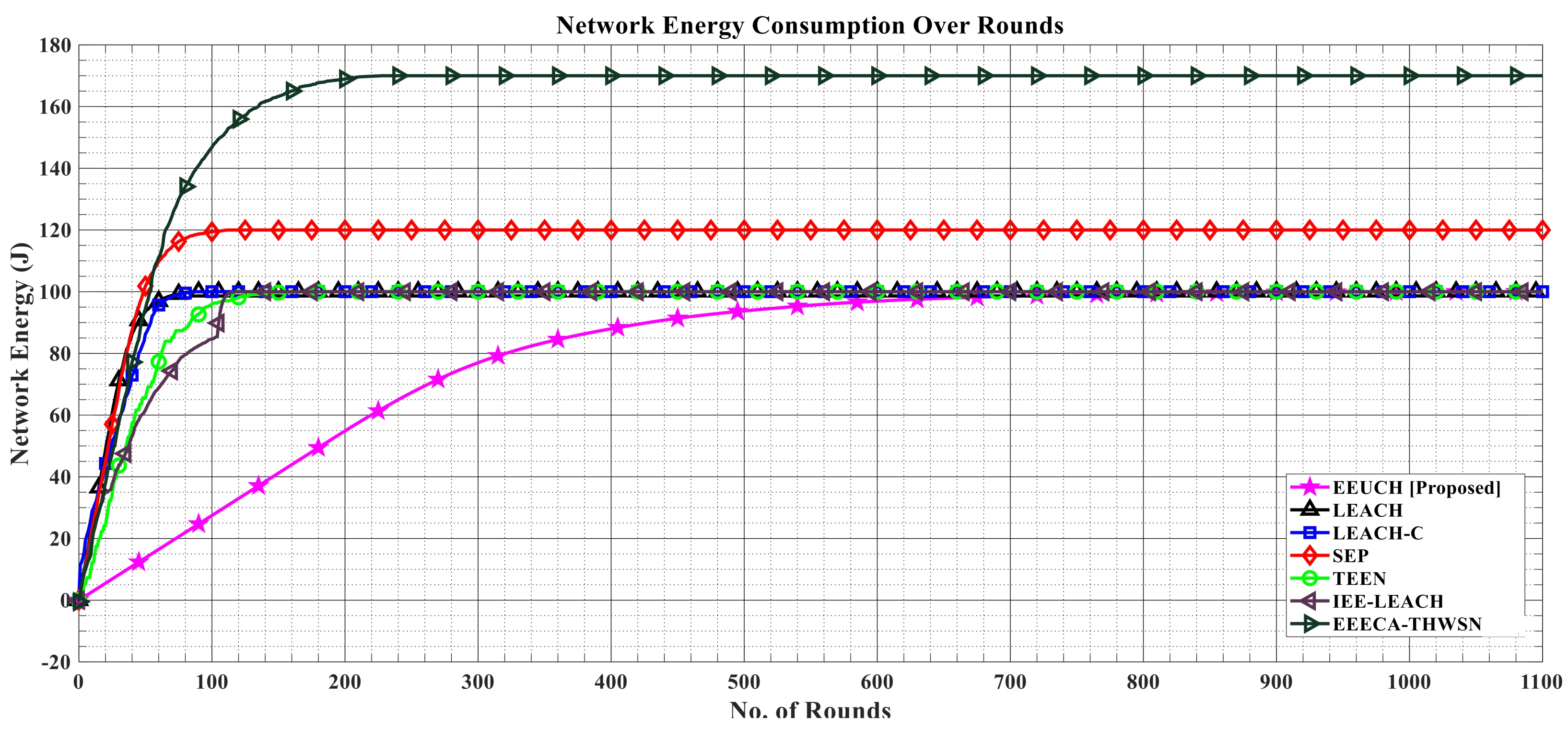
- Remaining network energy over the rounds: This parameter quantifies the amount of network energy that remains as the rounds pass. It reflects the overall network sustainability, which is vital for the longevity of the network lifetime. It is calculated by subtracting the total energy consumed till the current round from the initial network energy. A more efficient protocol should achieve a longer network lifetime by minimizing the rate at which energy is consumed. The total network initial energy is different for homogeneous, two-tier, and three-tier heterogeneous WSNs. For a homogeneous network, initial energy can be calculated using (4) below for which LEACH, LEACH-C, TEEN, IEE-LEACH, and the proposed EEUCH routing protocols are employed, while for two-tier and three-tier heterogeneous networks, we used (5) and (6), in which SEP and EEECA-THWSN routing protocols are employed, respectively. Equations (4)–(6) are given, respectively, below.where denotes the total homogeneous network initial energy, N is the total number of SNs, and is the standard initial energy for an SN.where is the total initial energy for a two-tier heterogeneous network, is the number of normal SNs which have initial energy as each, and is the number of advance SNs which have initial energy as times each. and can be calculated using the following equations:andwhere is the percentage of in N. Furthermore,where is the total initial energy for a three-tier heterogeneous network, is the number of standard SNs having initial energy each, is the number of intermediate SNs having initial energy times each, and is the number of advance SNs having initial energy times each. , , and can be calculated asandwhere and are the percentages of and in N.
- 5.
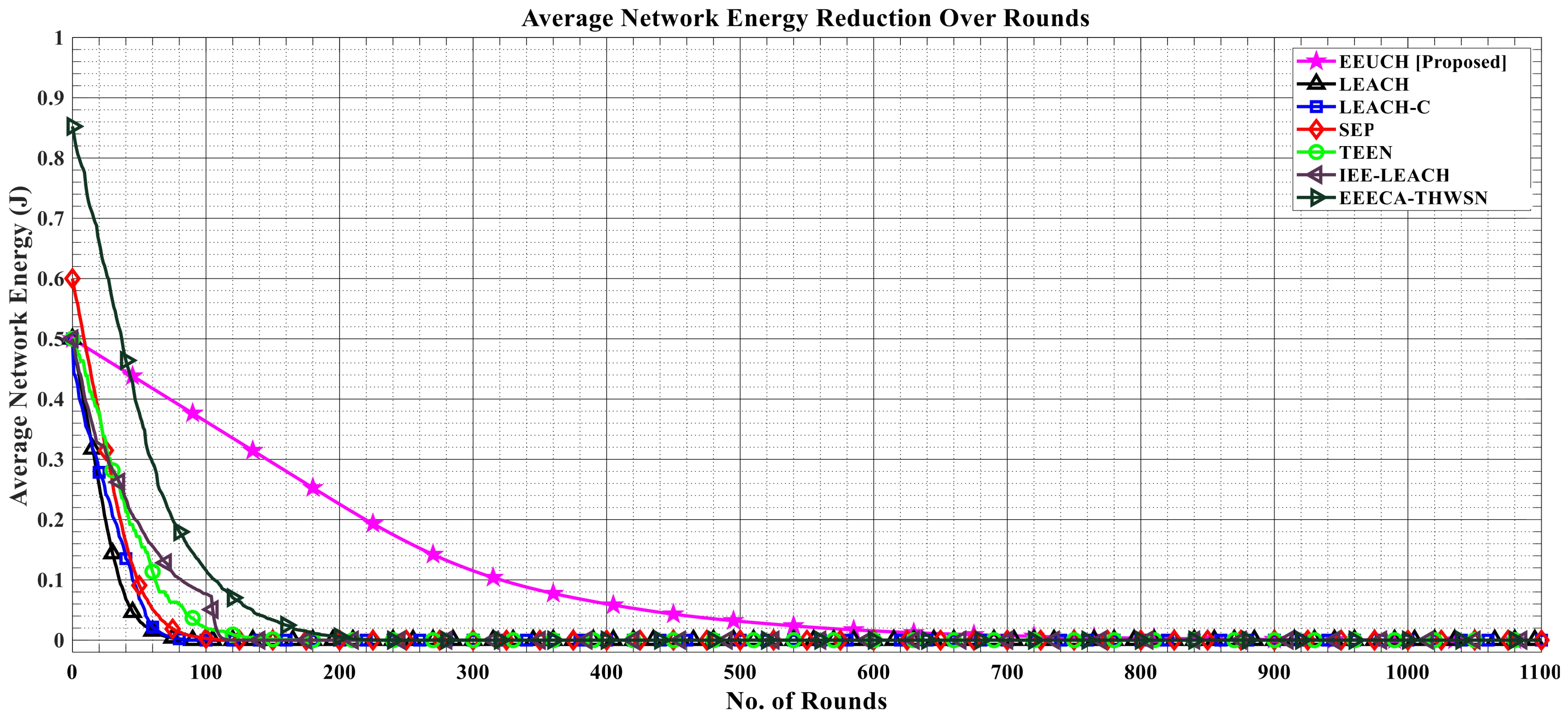
- Average network energy reduction: This shows the decrement in the average energy of the network. A better routing protocol should have slow and linear decrement of average network energy over the rounds. Average energy of the network can be calculated aswhere Here, shows the remaining energy of the total network in a particular round, is the energy consumed till the previous round is completed, and is the initial energy of the network which is different in each case of homogeneous, two-tier, and three-tier heterogeneous networks.
- 6.
- Network energy consumed: This parameter shows the cumulative energy consumption of the network over the rounds. As SNs die and their number decreases with the rounds, the energy consumption decreases. This parameter indicates the accumulated energy consumed by each alive SN and CH node till the previous round was completed. Since the number of alive SNs and CHs in each round varies, there is no fixed formula to calculate the value of . However, network energy consumed in a single round can be calculated aswhere is the energy consumed in a single round, is given in Equation (2), is the total number of alive SNs in the particular round, CH nodes selected from , and is data aggregation energy consumed by CH node.
- 7.
- Network lifetime: This is the time from the start till all the SNs die. More precisely, it is the time taken from the start (i.e., WSN or SNs deployment) till the last SN’s death. Thus,where is network lifetime, is the time in which the data transmission occurs in each round, “” is the number of rounds when all SNs die, and is the time when the WSN starts operating.
- 8.
- Stability time: It refers to the duration of time from the start of the network operation until the first SN in the network dies due to energy depletion. Stability time is an important metric to consider because it gives an indication of the overall network stability and robustness. A longer stability time means that the network is able to sustain its operation for a longer period without any significant disruptions or failures. This is particularly important for applications where the WSN is deployed in remote or inaccessible locations, and maintenance or repair may not be feasible or cost-effective. Stability time can be written aswhere is the stability time and “” is the number of rounds when first SN dies.
- 9.
- Average throughput: It is an essential performance parameter that provides a measure of the amount of data successfully collected from the FoI per unit time in WSNs. A higher average throughput indicates that the protocol is more efficient and effective in delivering data from the FoI. This parameter is crucial for various applications, especially in real-time monitoring and control systems, where timely delivery of data is critical. Therefore, the evaluation and comparison of average throughput among different WSN routing protocols can provide valuable insights into the network’s performance. Average throughput can be calculated asHere, represents the average throughput of the network.
6. Simulations Results and Discussions
6.1. Number of Alive Sensor Nodes over the Rounds
6.2. Number of Dead Sensor Nodes over the Rounds
6.3. Remaining Network Energy over the Rounds
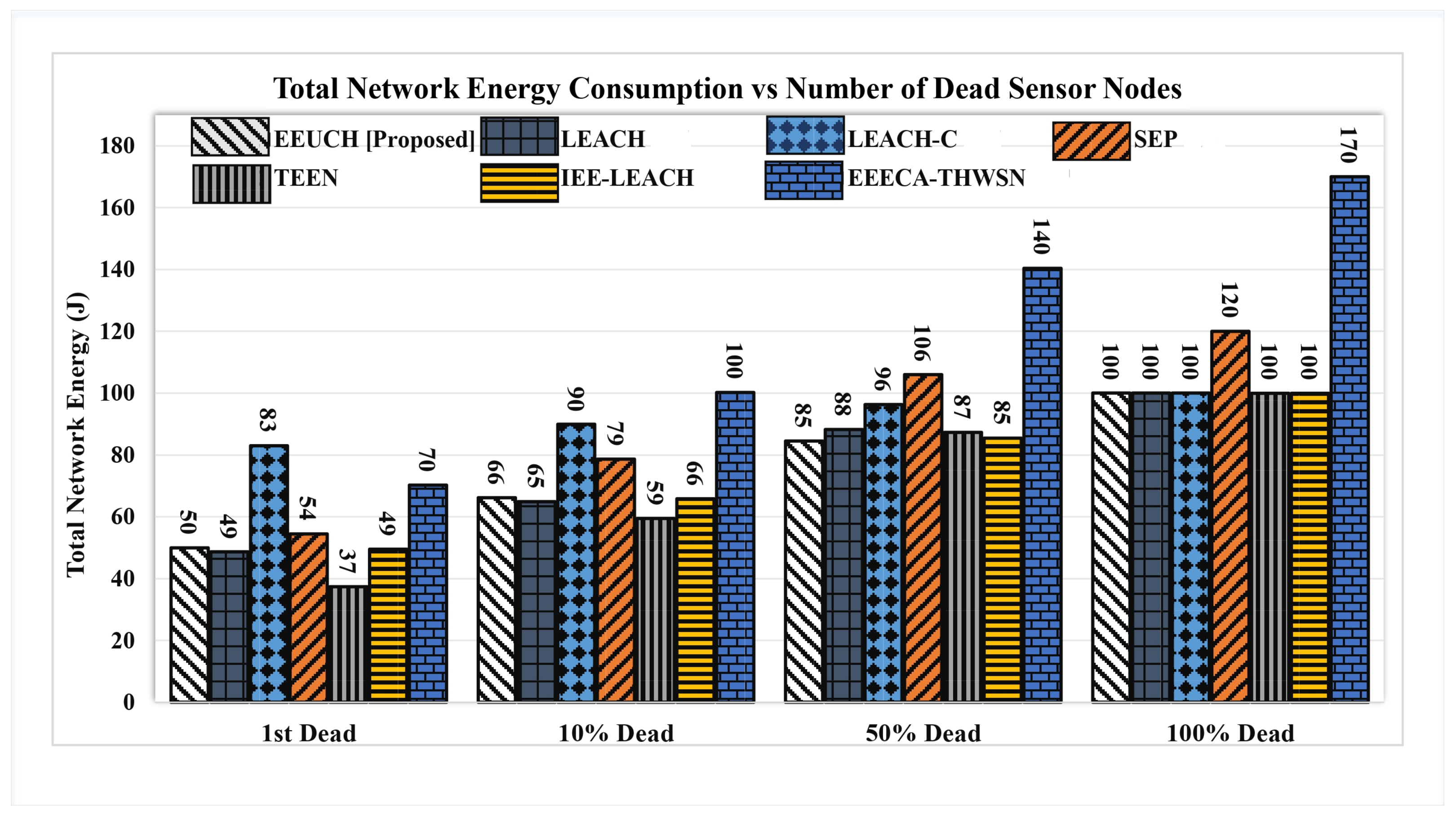
6.4. Total Network Energy Consumption over the Rounds
6.5. Network Average Energy Reduction over the Rounds
6.6. Total Number of Packets Collected over the Rounds
6.7. Network Stability Time
6.8. Network Lifetime
6.9. Average Network Throughput
6.10. Critical Discussion
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AcK | Acknowledgment |
| ARQ | Automatic repeat request |
| ASD | Number of rounds spent when all SNs die |
| BE | Backoff exponent |
| BS | Base station |
| CH | Cluster-head |
| CCA | Clear channel assignment |
| CMs | Cluster members |
| CSMA-CA | Carrier sense multiple access/collision avoidance |
| CTS | Clear to send |
| EEECA-THWSN | Enhanced energy-efficient clustering approach for three-tier heterogeneous |
| wireless sensor networks | |
| EEUCH | Energy-efficient unmanned aerial vehicle (UAV) assisted clustering |
| hierarchical | |
| FoI | Field of interest |
| FSD | Number of rounds spent when first SN dies |
| IEE-LEACH | Improved energy-efficient LEACH |
| IoT | Internet of Things |
| LEACH | Low energy adoptive clustering hierarchy |
| LEACH-C | LEACH centralized |
| LoS | Line of sight |
| MR | Main radio |
| MST | Mode switching time |
| NB | Current number of backoffs |
| PEGASIS | Power-efficient gathering in sensor information systems |
| RR | Rumor routing |
| RTS | Request to send |
| SEP | Stable energy protocol |
| SNs | Sensor nodes |
| TEEN | Threshold sensitive energy effective sensor network |
| TDMA | Time division multiple access |
| UAV | Unmanned aerial vehicle |
| WRP | Wireless routing protocol |
| WSN | Wireless sensor network |
| WuC | Wake-up call |
| WuR | Wake-up radio |
| WuRx | Wake-up receiver |
References
- Majid, M.; Habib, S.; Javed, A.R.; Rizwan, M.; Srivastava, G.; Gadekallu, T.R.; Lin, J.C.W. Applications of wireless sensor networks and Internet of Things frameworks in the industry revolution 4.0: A systematic literature review. Sensors 2022, 22, 2087. [Google Scholar] [CrossRef]
- Shi, K.; Shi, Z.; Yang, C.; He, S.; Chen, J.; Chen, A. Road-Map aided GM-PHD filter for multivehicle tracking with automotive radar. IEEE Trans. Ind. Inform. 2021, 18, 97–108. [Google Scholar] [CrossRef]
- Jondhale, S.R.; Maheswar, R.; Lloret, J. Fundamentals of wireless sensor networks. In Received Signal Strength Based Target Localization and Tracking Using Wireless Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2022; pp. 1–19. [Google Scholar]
- Zhang, F.; Zhang, Y.; Lu, W.; Gao, Y.; Gong, Y.; Cao, J. 6G-enabled smart agriculture: A review and prospect. Electronics 2022, 11, 2845. [Google Scholar] [CrossRef]
- Dhunna, G.S.; Al-Anbagi, I. A low power WSNs attack detection and isolation mechanism for critical smart grid applications. IEEE Sensors J. 2019, 19, 5315–5324. [Google Scholar] [CrossRef]
- Dong, B.; Prakash, V.; Feng, F.; O’Neill, Z. A review of smart building sensing system for better indoor environment control. Energy Build. 2019, 199, 29–46. [Google Scholar] [CrossRef]
- Wang, J.; Wang, Y.; Zhang, D.; Lv, Q.; Chen, C. Crowd-powered sensing and actuation in smart cities: Current issues and future directions. IEEE Wirel. Commun. 2019, 26, 86–92. [Google Scholar] [CrossRef]
- Haque, K.F.; Kabir, K.H.; Abdelgawad, A. Advancement of routing protocols and applications of underwater wireless sensor network (UWSN)—A survey. J. Sens. Actuator Netw. 2020, 9, 19. [Google Scholar] [CrossRef]
- Xu, G.; Shen, W.; Wang, X. Applications of wireless sensor networks in marine environment monitoring: A survey. Sensors 2014, 14, 16932–16954. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Sun, L.; Song, H.; Cao, X. Ubiquitous WSN for healthcare: Recent advances and future prospects. IEEE Internet Things J. 2014, 1, 311–318. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Melodia, T.; Chowdhury, K.R. A survey on wireless multimedia sensor networks. Comput. Netw. 2007, 51, 921–960. [Google Scholar] [CrossRef]
- He, S.; Shi, K.; Liu, C.; Guo, B.; Chen, J.; Shi, Z. Collaborative sensing in Internet of Things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2022, 24, 1435–1474. [Google Scholar] [CrossRef]
- Pantazis, N.A.; Nikolidakis, S.A.; Vergados, D.D. Energy-efficient routing protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2012, 15, 551–591. [Google Scholar] [CrossRef]
- Ma, N.; Zhang, H.; Hu, H.; Qin, Y. ESCVAD: An energy-saving routing protocol based on voronoi adaptive clustering for wireless sensor networks. IEEE Internet Things J. 2021, 9, 9071–9085. [Google Scholar] [CrossRef]
- Braginsky, D.; Estrin, D. Rumor routing algorthim for sensor networks. In Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications, Atlanta, GA, USA, 28 September 2002; pp. 22–31. [Google Scholar]
- Murthy, S.; Garcia-Luna-Aceves, J.J. An efficient routing protocol for wireless networks. Mob. Netw. Appl. 1996, 1, 183–197. [Google Scholar] [CrossRef]
- Lim, H.; Kim, C. Flooding in wireless ad hoc networks. Comput. Commun. 2001, 24, 353–363. [Google Scholar] [CrossRef]
- Lindsey, S.; Raghavendra, C.S. PEGASIS: Power-efficient gathering in sensor information systems. In Proceedings of the IEEE Aerospace Conference, Big Sky, MT, USA, 9–16 March 2002; Volume 3, p. 3. [Google Scholar]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000; pp. 1–10. [Google Scholar]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Smaragdakis, G.; Matta, I.; Bestavros, A. SEP: A stable election protocol for clustered heterogeneous wireless sensor networks. In Proceedings of the Second International Workshop on Sensor and Actor Network Protocols and Applications (SANPA 2004), Boston, MA, USA, 22 August 2004; Volume 3. [Google Scholar]
- Manjeshwar, A.; Agrawal, D.P. TEEN: A routing protocol for enhanced efficiency in wireless sensor networks. In Proceedings of the International Symposium on Parallel and Distributed Processing (IPDPS), San Francisco, CA, USA, 23–27 April 2001; Volume 1, p. 189. [Google Scholar]
- Liu, Y.; Wu, Q.; Zhao, T.; Tie, Y.; Bai, F.; Jin, M. An improved energy-efficient routing protocol for wireless sensor networks. Sensors 2019, 19, 4579. [Google Scholar] [CrossRef]
- Kumar, N.; Rani, P.; Kumar, V.; Athawale, S.V.; Koundal, D. EEECA-THWSN: Enhanced energy-efficient clustering approach for three-tier heterogeneous wireless sensor networks. IEEE Sensors J. 2022, 22, 20053–20062. [Google Scholar] [CrossRef]
- Al-Khafajiy, M.; Baker, T.; Hussien, A.; Cotgrave, A. UAV and fog computing for IoE-based systems: A case study on environment disasters prediction and recovery plans. In Unmanned Aerial Vehicles in Smart Cities; Springer: Berlin/Heidelberg, Germany, 2020; pp. 133–152. [Google Scholar]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Mobile unmanned aerial vehicles (UAVs) for energy-efficient Internet of Things communications. IEEE Trans. Wirel. Commun. 2017, 16, 7574–7589. [Google Scholar] [CrossRef]
- Wei, Z.; Zhu, M.; Zhang, N.; Wang, L.; Zou, Y.; Meng, Z.; Wu, H.; Feng, Z. UAV assisted data collection for Internet of Things: A survey. IEEE Internet Things J. 2022, 9, 15460–15483. [Google Scholar] [CrossRef]
- Lien, S.Y.; Chen, K.C.; Lin, Y. Toward ubiquitous massive accesses in 3GPP machine-to-machine communications. IEEE Commun. Mag. 2011, 49, 66–74. [Google Scholar] [CrossRef]
- Li, J.; Kacimi, R.; Liu, T.; Ma, X.; Dhaou, R. Non-terrestrial networks-enabled Internet of Things: UAV-centric architectures, applications, and open issues. Drones 2022, 6, 95. [Google Scholar] [CrossRef]
- Hsu, C.A.; Tsai, C.H.; Li, F.Y.; Chen, C.; Tseng, Y.C. Receiver-initiated data collection in wake-up radio enabled mIoT networks: Achieving collision-free transmissions by hashing and partitioning. IEEE Trans. Green Commun. Netw. 2021, 5, 868–883. [Google Scholar] [CrossRef]
- Ghose, D.; Li, F.Y.; Pla, V. MAC protocols for wake-up radio: Principles, modeling and performance analysis. IEEE Trans. Ind. Inform. 2018, 14, 2294–2306. [Google Scholar] [CrossRef]
- Magno, M.; Jelicic, V.; Srbinovski, B.; Bilas, V.; Popovici, E.; Benini, L. Design, implementation, and performance evaluation of a flexible low-latency nanowatt wake-up radio receiver. IEEE Trans. Ind. Inform. 2016, 12, 633–644. [Google Scholar] [CrossRef]
- Zhang, M.; Ghose, D.; Li, F.Y. Does wake-up radio always consume lower energy than duty-cycled protocols? In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–5. [Google Scholar]
- Hsu, C.A.; Li, F.Y.; Chen, C.; Tseng, Y.C. Achieving ultra energy-efficient and collision-free data collection in wake-up radio enabled mIoT. In Proceedings of the ICC 2020–2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- IEEE Std 802.11-2020 (Revision of IEEE Std 802.11-2016); IEEE Standard for Information Technology–Telecommunications and Information Exchange between Systems Local and Metropolitan Area Networks–Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 1: Enhancements for High-Efficiency WLAN, in IEEE Std 802.11ax-2021 (Amendment to IEEE Std 802.11-2020). IEEE: Piscataway, NJ, USA, 2021; pp. 1–767. [CrossRef]
- Rappaport, T.S. Wireless Communications: Principles and Practice, 2/E; Pearson Education India: Delhi, NCR, Noida, India, 2010. [Google Scholar]
- IEEE Std 802.15.4-2011 (Revision of IEEE Std 802.15.4-2006); IEEE Standard for Local and Metropolitan Area Networks–Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs). IEEE: Piscataway, NJ, USA, 2011; pp. 1–314. [CrossRef]
- Kim, T.O.; Park, J.S.; Chong, H.J.; Kim, K.J.; Choi, B.D. Performance analysis of IEEE 802.15. 4 non-beacon mode with the unslotted CSMA/CA. IEEE Commun. Lett. 2008, 12, 238–240. [Google Scholar] [CrossRef]
- Forouzan, B.A. Data link control. In Data Communications and Networking; McGraw-Hill Education: New York, NY, USA, 2007; Chapter 11; pp. 307–362. [Google Scholar]
- IEEE Std 802.11-2007 (Revision of IEEE Std 802.11-1999); IEEE Standard for Information Technology—Telecommunications and Information Exchange Between Systems—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: Piscataway, NJ, USA, 2007; pp. 1–1076. [CrossRef]


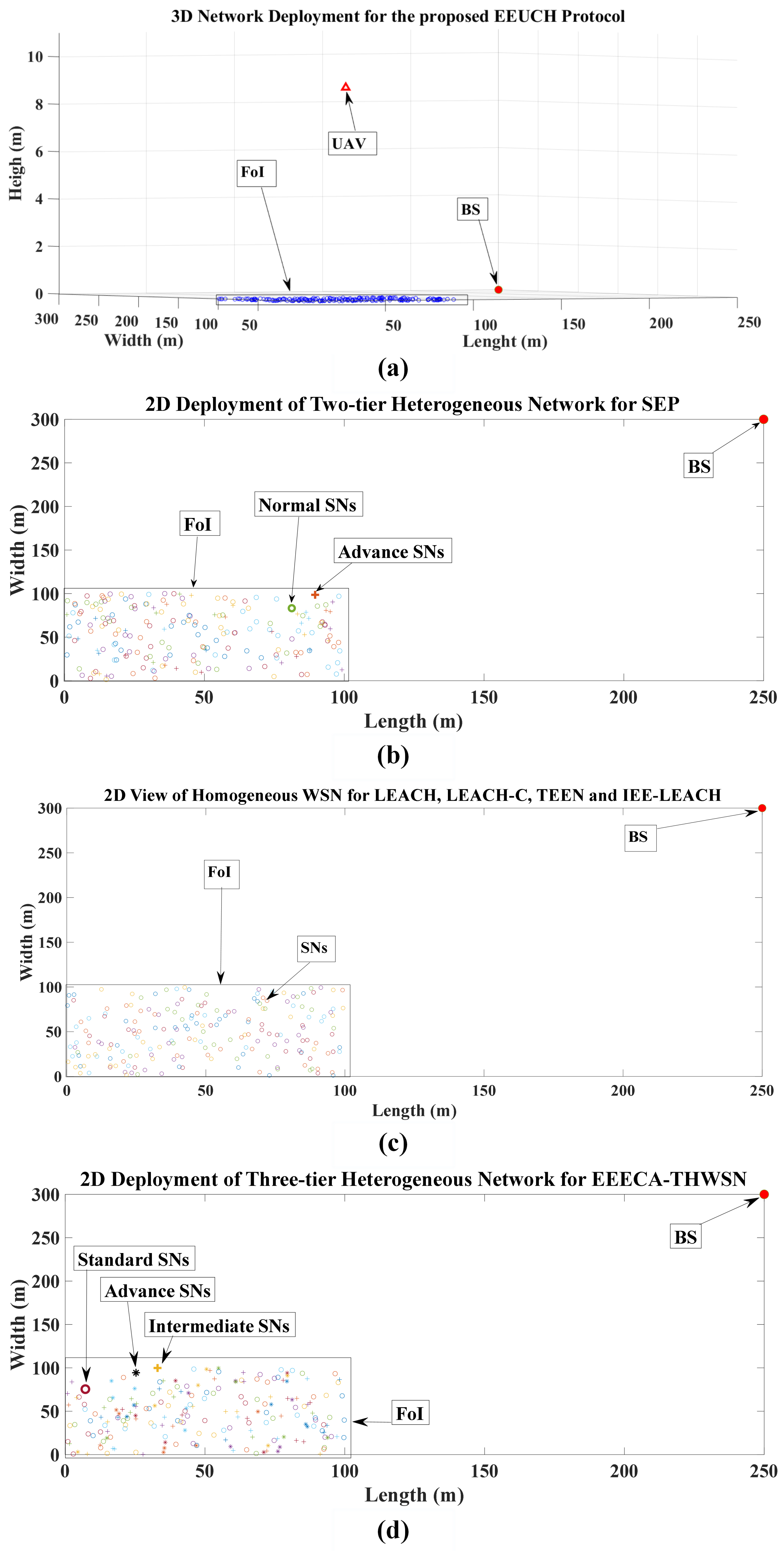





| Metric/Features | EEUCH [Ours] | LEACH [19] | LEACH-C [20] | TEEN [22] | IEE-LEACH [23] | SEP [21] | EEECA-THWSN [24] |
|---|---|---|---|---|---|---|---|
| Network scenario | Homogeneous | Homogeneous | Homogeneous | Homogeneous | Homogeneous | Two-tier heterogeneous | Three-tier heterogeneous |
| Cluster formation and CH election | Each UAV announces itself as a CH for its respective cluster | SNs decide CHs for each cluster randomly | BS decides CHs for each cluster by considering SN’s energy and location | SNs decide CHs for each cluster randomly, also clusters of CHs are formed | SNs decide CHs for each cluster by considering average and total energy of the WSN, residual energy of SN, and round number | SNs decide CHs for each cluster by considering the heterogeneity in SN’s energy | SNs decide CHs by considering the heterogeneity in SN’s energy, current and initial energy of WSN, average distance from BS and SN’s location |
| Location of BS | d distance away from the FoI | In the middle of FoI | In the middle of FoI | In the middle of FoI | In the middle of FoI | In the middle of FoI | In the middle of FoI |
| Simulation software | MATLAB | MATLAB | NS-2 | MATLAB | MATLAB | MATLAB | MATLAB |
| WuR for SNs | Yes | No | No | No | No | No | No |
| Data collection from FoI | Whenever required (Application dependent) | Continuous | Continuous | Continuous | Continuous | Continuous | Continuous |
| Parameter Symbol | Description | Value | Unit |
|---|---|---|---|
| Initial energy of an SN | J | ||
| Network size | m | ||
| N | Number of SNs | 200 | NA |
| p | CH percentage in N | NA | |
| Max. number of rounds | 3000 | NA | |
| m | Packet size | 4000 | bits |
| Transmit electronics energy | J/bit | ||
| Receive electronics energy | J/bit | ||
| Amplification factor of transmitting circuit for free space channel model | J/bit/m | ||
| Amplification factor of transmitting circuit for multipath channel model | J/bits/m | ||
| Threshold distance | m | ||
| Data aggregation energy | J/bit/signal | ||
| BS location | [m, m] | ||
| Coefficient of () for | 2 | NA | |
| Coefficient of () for | 2 | NA | |
| Coefficient of () for | 3 | NA | |
| Probability of | NA | ||
| Probability of | NA | ||
| Probability of | NA | ||
| n | Number of UAVs | 1 | NA |
| h | Height of UAV | 8–10 | m |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shah, S.L.; Abbas, Z.H.; Abbas, G.; Muhammad, F.; Hussien, A.; Baker, T. An Innovative Clustering Hierarchical Protocol for Data Collection from Remote Wireless Sensor Networks Based Internet of Things Applications. Sensors 2023, 23, 5728. https://doi.org/10.3390/s23125728
Shah SL, Abbas ZH, Abbas G, Muhammad F, Hussien A, Baker T. An Innovative Clustering Hierarchical Protocol for Data Collection from Remote Wireless Sensor Networks Based Internet of Things Applications. Sensors. 2023; 23(12):5728. https://doi.org/10.3390/s23125728
Chicago/Turabian StyleShah, Syed Luqman, Ziaul Haq Abbas, Ghulam Abbas, Fazal Muhammad, Aseel Hussien, and Thar Baker. 2023. "An Innovative Clustering Hierarchical Protocol for Data Collection from Remote Wireless Sensor Networks Based Internet of Things Applications" Sensors 23, no. 12: 5728. https://doi.org/10.3390/s23125728
APA StyleShah, S. L., Abbas, Z. H., Abbas, G., Muhammad, F., Hussien, A., & Baker, T. (2023). An Innovative Clustering Hierarchical Protocol for Data Collection from Remote Wireless Sensor Networks Based Internet of Things Applications. Sensors, 23(12), 5728. https://doi.org/10.3390/s23125728









