Abstract
We propose a novel slot-pattern-control based coded compressed sensing for unsourced random access with an outer A-channel code capable of correcting t errors. Specifically, an RM extension code called patterned Reed–Muller (PRM) code is proposed. We demonstrate the high spectral efficiency due to its enormous sequence space and prove the geometry property in the complex domain that enhances the reliability and efficiency of detection. Accordingly, a projective decoder based on its geometry theorem is also proposed. Next, the “patterned” property of the PRM code, which partitions the binary vector space into several subspaces, is further extended as the primary principle for designing a slot control criterion that reduces the number of simultaneous transmissions in each slot. The factors affecting the chance of sequence collisions are identified. Finally, the proposed scheme is implemented in two practical outer A-channel codes: (i) the t-tree code and (ii) the Reed–Solomon code with Guruswami–Sudan list decoding, and the optimal setups are determined to minimize SNR by optimizing the inner and outer codes jointly. In comparison with the existing counterpart, our simulation results confirm that the proposed scheme compares favorably with benchmark schemes regarding the energy-per-bit requirement to meet a target error probability as well as the number of accommodated active users in the system.
1. Introduction
The continuous evolution of massive machine type communication (mMTC+) [1] will still be one of main use cases of sixth-generation (6G) wireless networks [2,3]. In this context, the battery-limited terminals sporadically connected to the network grow exponentially and they are expected to send short information packets for low transmission latency [4,5].
The most promising way is to address grant-free transmission, i.e., the device transmits the packet without requiring coordination among users [6,7,8]. The “Sourced random access (SRA)” case refers to assigning separate dictionaries to individual users, i.e., employing different encoders for users [9,10]. Due to a large number of users, the SRA mechanism will result in exorbitant complexity as the AP does not know which decoder to utilize and is forced to try all possibilities. Therefore, employing the same coding protocol for all users is the most promising approach. Such schemes are known as “Unsourced random access (URA)” [11]. By using this mechanism, AP is not required to recognize active users’ identities and all users are allowed to share the same codebook, avoiding complex identity assignment and authentication processes among a large number of users. Additionally, the access and transmission performance of the overall system are analyzed based on the per-user probability of error (PUPE) for all active users.
Since then, several papers have been published demonstrating fundamental limits for various massive access channel models and configurations (see, e.g., [12,13,14]). Many transmission schemes have been proposed to achieve performance as close to these fundamental limits as possible [15,16,17].
The Background for Unsourced Random Access with Outer A-Channel Codes: The URA benefited greatly from the outer A-channel codes [18,19], e.g., the coded compressed sensing is a divide-and-conquer scheme that uses random inner codes of capacity concatenated with an outer G-ary A-channel code, in which a tree code is a type of A-channel code designed for this purpose. This flexible structure made it easy to adapt to new channel models. Several subsequent studies on URA (e.g., [16,20,21,22,23,24]) made use of an outer A-channel code.
The field of study [19] for a tree code as the outer A-channel code is extended in paper [25], which leverages the approximate message passing (AMP) strategy in conjunction with sparse regression codes. The coded compressed sensing (CCS) strategy is further improved in [16], where the inner AMP decoder and the outer tree decoder are authorized to exchange soft information via a shared message-passing protocol. By using the same sensing matrix as in [19], the authors reduce complexity in [26]. The paper [27] proposes a coded demixing strategy to facilitate the joint detection of high dimensional sparse signals concerning different bases.
The Background for Reed–Muller Sequence: The second-order Reed–Muller-related codebook construction schemes have been widely utilized in compressed sensing [28,29,30,31]. For instance, in [28], the complexity of the chirp reconstruction is dependent on the number of measurements rather than the signal dimension since RM sequences are utilized to build deterministic measurement matrices. In [29], the idea of using a measurement matrix whose columns are codewords of a linear code is proposed. In addition, a quadratic reconstruction algorithm that takes advantage of the multivariable quadratic functions is further employed. According to [31], full-duplex compressed neighbor discovery is supported by on–off RM signatures. Additionally, RM sequences are regarded as excellent options for massive access in mMTC due to their large codebook capacity and ability to be used in low-complexity random access [32]. The non-orthogonal RM sequences are used as signatures for active device detection [33] which is the grant-based access scheme that suffers from low access efficiency and high signaling overhead in mMTC. As described in [34], an incremental massive random access scheme is proposed. Furthermore, RM sequences leveraged as the inner codes for the URA scheme are proposed in [35,36] and the tree coding is used for stitching messages in packetized and slotted transmissions.
In this paper, based on the “patterned” property of the proposed patterned Reed–Muller (PRM) sequences, we design a slot-pattern-control (SPC) criterion that corresponds one-to-one to an information segment to construct the slot occupation guideline for each active user. We then partition the users’ messages into several sub-blocks and add the same SPC segment in each block as a prefix to make up the input signal of the inner encoder. On this basis, each sequence related a single codeword from a proposed common codebook called patterned Reed–Muller codes. For recovering the PRM sequences received at the receiver, an algorithm exploiting the geometry of PRM sequences is proposed. Moreover, the outer tree code is replaced with an error-correcting code and the codewords with a distance at most t from the channel output are recovered by outer codes.
1.1. Main Contributions of the Paper
To summarize, our contributions are listed as follows:
- This paper designs a common codebook that optimizes URA energy efficiency performance by embedding zero bits in the second-order Reed–Muller sequences in accordance with a specific principle, which is the simplified version proposed by Pllaha et al. (2022) [37,38,39], and we denote it as a patterned Reed–Muller (PRM) code.
- Instead of the available common codebook that uses Reed–Muller (RM) properties in the binary domain, we explore its exclusive natures in the complex domain. In detail, we prove the algebraic and geometric properties of the second-order Reed–Muller sequence in the complex field, and related theories for PRM codes are also proven.
- A projective decoder is proposed for the PRM sequence and the fundamental theory for proposing such precise detection algorithm stems from its geometry property.
- The dependencies enlightened by the patterned property of PRM sequences prescribe how the information messages are mapped to the elements in a pool of slot-pattern controls (SPCs). The information message guides a single user to select the corresponding SPC from the pool and users randomly select SPCs as their transmission criteria to reduce collision chance.
- The factors affecting the reliability of the PRM detection are discussed. As a result of our simulations, we conclude that the proposed slot-pattern-control PRM-based scheme offers significant advantages in terms of error probability.
- Instead of the outer tree code proposed by Amalladinne et al. (2020) [19], we couple the proposed slot-pattern-control PRM-based scheme with two practical list recoverable codes. The first is a modification of the tree code called t-tree code and the second is based on the Reed–Solomon codes and Guruswami–Sudan list decoding algorithm. The optimal setups are determined to minimize SNR by optimizing the inner and outer codes jointly. In regimes of practical interest, the proposed scheme compares favorably with benchmark schemes regarding the energy-per-bit requirement to meet a target error probability as well as the number of accommodated active users in the system.
In Section 2, we introduce the system model. Several theorems of RM for the complex field are proved in Section 3. In Section 4, we construct the proposed PRM sequence and design a single-user decoding algorithm based on a proven theorem. Section 5 provides a high-level description of the transmitter architecture, decoding procedures and a proposed slot-pattern-control pool design, followed by Section 6 on the factors influencing the PRM detection ability. The performance of the proposed transmission schemes is assessed via numerical simulations in Section 7. Section 8 concludes the paper.
1.2. Notation
This paper uses lowercase letters to represent scalars. Column vectors and matrices are denoted by boldface letters in lower case and upper case, respectively. We represent as the binary field. Sym denotes the group of binary symmetric matrices. We will denote matrices (resp., vectors) with upper case (resp., lower case) bold letters. will denote the transpose and will denote the inverse transposed column space and the row space of . Since all our vectors are columns, we will typically deal with column spaces. will denote the matrix (complex or binary). denotes the set of unitary complex matrices and H will denote the conjugate transpose of a matrix. The length N column vectors of all zeros and all ones are denoted as and , respectively. We use to represent the I-element vector made up of the elements , where . The result of appending the column vector to has the form of . is an all-zero column vector of length N. denotes a full-zero matrix of size . We denote by a complex standard normal random vector. The symbol is the cardinality of a set. represents the complexity order. denotes the expectation operator and denotes the variance operator. means a probability of the event e. The vector is the decimal number , while conversely we have that , i.e., converts the binary vector to the corresponding decimal number and then increases the result by one.
2. System Model
In this paper, let us reuse the system proposed in [19,36]. Users are always silent in the absence of information to transmit. There are K potential users in the system and components are active, which typically means is far less than K in the mMTC scenario due to the infrequent activity of users. users transmit codewords drawn at random from a common codebook containing entries derived from a G-ary alphabet over T channel uses. The relationship between inputs and outputs of a channel over H slots is expressed as
where represents the inner codeword sent by user k in the m-th message segment, , and the length of the codeword is .
The expectation is that each active user will send B bits of information to the receiver utilizing T channel uses. Specifically, the set for B-bit messages, which contain all messages sent by users, are encoded into H-length G-ary A-channel codes, where , and . We then define the URA code for the A-channel as:
where K is the number of simultaneous appearances in each block, . We require , which means the power limitation. In this article, a proposed slot-pattern-control technique is used to carry out the packetized and slotted transmission; hence, the H-length outer codes are distributed throughout slots and .
At the receiver, after detecting codewords in each slot, the A-channel decoder is used to couple the divided information chunks. Here, a quasi-static Rayleigh fading channel is considered, in which the channel remains constant inside a single slot but fluctuates independently between slots. We assess performance from the perspective of messages and use the miss detection rate (MDR) and the false-alarm rate (FAR) as the primary indicators, which are given as
and
respectively, where . Energy efficiency is of critical importance for the mMTC scenario; our goal is to minimize the energy per bit () spent by each user.
3. Reed–Muller Sequences
The existing unsourced random access systems using Reed–Muller sequences primarily investigate the RM features in the binary domain [35]. In reality, the complex RM sequences are unit norm vectors on , which exhibit subtle algebraic and geometric properties. In this section, we present a novel direction for comprehending the RM sequence by revealing its particular theories in the complex domain, which offer the theoretical bases for constructing RM expansion codes.
3.1. Binary RM Codes
For an binary symmetric matrix and a binary vector , the n-th entry of the complexed RM sequence is denoted as
where n is the decimal expression of binary vector , i.e., . In other words, the RM sequence in (4) is an algebraic equation associated with the time index , where n in represents the decimal time index and is the corresponding binary expression. To facilitate presentation, the index-related RM is illustrated via a simple example and we write out a basis of RM as follows [40,41]:
The first row lists all indices for each bit position within a codeword, which can also be denoted as or directly . Binary Reed–Muller codes consist of the evaluation vectors of multivariate polynomials over the binary field . The codeword RM with parameters m and r consist of all the evaluation vectors of polynomials with m variables and degree no larger than r. The second to the last rows are polynomials of degree two, degree one and zero, respectively. It is noteworthy that the first-order part coincides with the first line (bit position indices) and the above basis is the generation matrix for RM.
3.2. Geometry of Complex RM Sequence
Complex RM sequences are made of two parts: a mask sequence [28] and a Hadamard sequence . Overall, the exponents in (4) are evaluations (modulo 4) of degree 2 polynomials in m variables and therefore the collection is just an exponentiated second-order Reed–Muller code. However, from a geometric perspective, it is not sufficient to consider only the first- and second-order polynomials. This subsection offers a novel interpretation of RM in the complex domain.
As a matter of fact, for Pauli matrices with , the absolute value of cannot exceed 1 (see more details in [42,43,44]). To proceed, we define a notion associated with shift for the Reed–Muller sequence as :
where , is the standard basis vector in m-dimensional space. To conclude, we summarize the related geometry theorem in Theorem 1.
Theorem 1.
is equivalent to implementing a Walsh–Hadamard transform (WHT) on RM sequence .
Proof of Theorem 1.
The formula can be extended as follows:
where . The result of (6) completes the proof. □
In fact, the Hadamard transformations of “shift”, “multiplication” and “shift and multiplication” in Equation (6) show that the process is actually a translation of the “shift-and-multiply” technique into the operation of the Pauli matrices. In essence, this transformation constitutes the difference between the traditional binary RM sequence and the complex one.
The complex RM sequence still has the following theorem.
Theorem 2.
There is a relationship between between and as follows:
where and is the -th element of vector .
Proof of Theorem 2.
where and . This completes the proof. □
Pauli matrices are in one-to-one correspondence to a set of half-space projection operators. Thus, from an estimated , a projection operator
can be constructed, for which we have
4. Expansion of Complex Reed–Muller Sequences
In this section, an alternative code of binary subspace chirp (BSSC) in [39] is proposed, which simplifies the number of subspaces in , preserves the “patterned” behavior and ultimately exhibits less interference than BSSCs. A geometric feature of the proposed code is also demonstrated, which provides the theoretical basis for the proposed decoding algorithm. We finally propose a projective decoder based on its geometry theorem.
4.1. Patterned Reed–Muller Codes
The novel patterned Reed–Muller (PRM) codeword introduces a new parameter that signifies all possible subsets of m. Specifically, all potential subsets for m of rank are denoted as . Thus, the possible count varies with variable . The first-order item of the RM generation matrix (mentioned in Section 3.1) is employed here as the position indices . In order to retrieve the PRM sequence, it is necessary to manipulate the position indices in a precise manner: first, place “0” bits in all positions but , where denotes the sub-sequence of post- bits of vector and is a matrix of size with column vectors , and is the unit vector with non-zero at the r-th position(). Accordingly, matrix is of size with column vectors , where is the complement set of in m. Second, a sequence RM is then added to the above non-zero positions and written as follows:
where and is the symmetric matrix for RM.
As a matter of fact, the PRM sequence simply reduces the subspace matrix to ; we refer the reader to [39] for more details. Let us further define the matrix and write (11) in the following format:
in the case of , equal to 1.
We now depict the PRM sequence with a toy example before concluding its general rule. Let , the vector and matrix are fixed; on this basis, three different dimensional spaces of and in with the corresponding subsets , and are substituted into (11). The resulting sequences are depicted in Figure 1.

Figure 1.
The top line is the indexes of bit position. White = 0, Blue = 1, Purple = , Orange= i, Green = .
We conclude the PRM sequences with the following properties:
- The evidence demonstrates that, given a sequence of length , PRM codes may increase the origin capacity of while maintaining the code distance and the cardinality of the PRM set is equal to
- In PRM sequence construction, the RM is not just inserted into a -length sequence, but has a sign attached (Equation (12) illustrates this). The sign comes from the part, i.e., the constraint of means the post- bits should be equal, which leads to the two identical vector multiplication (modulo 4) equal to the weight of or ;
- The vector and matrix serve as the determinants of the non-zero RM part, where only the upper matrix is valid. Moreover, the subspace and determine the “patterned” form.
4.2. Geometry Property of PRM sequence
This section discusses the geometry property of PRM along the lines of Section 3.2 and summarizes the conclusion in Theorem 3.
Theorem 3.
The PRM sequence fulfills the following equation for any :
where Υ is dimension of the set χ and denotes the unit vector on domain , , while is a -element symmetric binary matrix of rank Υ.
Proof of Theorem 3.
The left term of Equation (14) can be expanded as
where . The equals sign (a) is based on the formula for Pauli matrices (see Equation (14) in [38] for details) and (b) is the process of replacing all variable with . Next, we will develop each item and C in the last equation of (15).
Using process , we expand item A into the following equation
where is the -th diagonal element (from top down) of the matrix . We further employ the equation and and item B can be expressed as
where . Similarly, we have
The following equation can be obtained by substituting (16)–(18) into (15):
where the equals sign (c) uses the equation , while (d) replacing with as well as using the following formula
to eliminate as 1. We use the equation
in (e). Thus, (19) agrees with the conclusion in Theorem 3. □
Lemma 1.
For any , the following projection operator exists
where . For any vector we get
If is fixed, we have
and we get
Lemma 1 is the core idea of the detection algorithm.
4.3. The Proposed Geometry-Based PRM Detection
We model a single-user scenario in which the receiver observes
where is a PRM sequence while represents an additive noise. Unlike the RM sequence decoding algorithm, PRM code needs to decode three items, i.e., . In view of the fact that decoding the second-order RM at non-zero positions can be accomplished only if the subspace is known, the knowledge of subspace matrix should be recovered in priority. Algorithm 1 summarizes the detail of the proposed decoding algorithm.
| Algorithm 1: Estimation of single PRM sequence |
 |
Due to the indeterminate rank of the received PRM sequence, we traverse all possible ranks and reserve L candidate subspaces beneath each rank (line 1). Lines 2–5 describe the process for collecting candidates: for each vector , we compute the related and its summation form
By searching the largest estimatios of , the corresponding set and the subspace matrix are identified and placed as a candidate, in which the relation between and is
We repeat the above steps and keep L candidates in set .
The subsequent RM recovery is based on the subspaces in candidates . As shown in lines 9–18, the symmetric matrix and the vector for decoding RM are recovered layer by layer within the l-th interaction, where the subscript l denotes the current l-th candidate in . Since the matrix is of Kerdock set with symmetric properties, we denote the set of indexes for the rows determined by decoded layers as (). Utilizing the estimated row vectors to complete the symmetric matrix, the current matrix for the -th layer decoding can be represented as . Hence, the search space under the l-th submatrix is limited to
where the value of refers to the i-th row and -th column of matrix . On this basis, for all vectors , an equation written as
is calculated to search the largest values of and herein find the corresponding set based on
We finally get , where is the -th row/column vector for .
In the case of decoding, as can be seen from Lemma 1, we first compute by substituting (31) into (30) and letting :
we then obtain . Therefore, can be obtained immediately as
(33) can be summarized as the relationship of
where .
The power of (subscripts for is omitted) projected with this operator is
where . We see that the halfspace to which the projection of is largest.
We perform a projection operation on the -th layer signal before performing the next layer decoding by employing the projection operator (see line 14 in Algorithm 1). While , the input signal becomes
which indicates that the power of noise is halved within each iteration.
Line 21 evaluates the L results under each rank and retains the optimal solution. Finally, line 23 selects the optimal solution for the results of all ranks.
5. Unsourced Random Access Scheme Using Patterned Reed–Muller Sequence
The k-th active user preferentially converts its message sequence into the corresponding M-length J-ary Reed–Solomon code, which completes the outer A-channel coding. Before conducting the inner encoding, a random prefix message is repeatedly added into M sub-blocks. The combination of the prefix and J-ary bits can produce a G-ary message in each slot. By using this prefix, an slot occupation criterion is selected from a common pool . The binary sequence transformed by a G-ary bit is subsequently mapped to an element in a common codebook and the resulting codeword is then transmitted to the AP side. In the receiver, the AP detects the users’ messages using the proposed projection method. In the sequel, we will describe every module of the proposed URA system in detail.
5.1. Transmitter
The specific structure of the transmitter is shown in Figure 2. This subsection provides a detailed description of how the transmission sequence is generated in the transmitter, followed by the construction of the slot-pattern-control pool.

Figure 2.
The diagram of the transmitter technique in our proposed URA system.
5.1.1. Transmitter Design
The A-channel code used for the outer encoding is derived from paper [22]: the kth user’s message of length B is mapped to a J-ary Reed–Solomon code of length H, designated , , where is the h-th output bit of outer coding. To satisfy the coding rate requirement, we repeatedly append the binary prefix sequence to each J-ary bit to create the G-ary sequence. Thus, the length of the binary sequence is set to and we denote . For further interpretation, a G-ary bit is divided into cosets, each containing components, and this process can be summarized as follows:
where is the bijective mapping: and . By repeating (37) H times, an H-length sequence is obtained, which serves as the input sequence for the inner encoder. We require a one-to-one matching between and codeword from the common codebook (we omit the subscript m here for simplicity), and, herein, is the input signal of the inner encoder while the output codeword is .
Let the message have a length of ; it is evident that . Furthermore, according to the codebook capacity of Equation (13), the size of information bits that a PRM sequence can carry in each slot for user k is . Finally, the output of inner coding over H slots is recorded as . This process of the transmitter is depicted in Figure 2.
5.1.2. The Construction of Slot-Pattern-Control Pool
In the practical encoding procedure, each user inserts its H-length RS code into slots by looking up a criterion from the common dictionary . Specifically, we construct a collection pool for holding the common slot-pattern-control criteria and the k-th user retrieves the matching SPC from the pool based on the specific .
The slot-pattern-control scheme is designed using a manner that refers to the construction of PRM code as a heuristic algorithm: the initial step is to unify all users’ slot indices, which can be managed by utilizing the binary notation to identify each slot. It is evident that, for a time slot of length , the equation is necessary. Next, we extend the subspace generation rule in for the PRM construction to classify time slots into several sub-slots; in detail, let denote the possible number of r dimensional spaces in with and the corresponding subset is represented as . Obviously, the length of is r and . On the condition that r is constant, the slots used to place the -length () outer codeword are labeled as
where the set (span all ) indicates a subspace and the vector controls the cosets of the subspace. Since vector has possibilities, cosets exist for each subspace. On this basis, the pool generates a total of candidates and the length of the information is fixed as . In this way, once the user has acquired the knowledge of (there exists a one-to-one correspondence between -pair and sequence ), an H length codeword is successively inserted into the slots in accordance with (38).
In general, given a SPC and a random slot index , the signals to be sent in slot are formulated as
We let the vector retain the certain bits from vector at locations of and regard as the decimal index of non-zero position in all slots. Moreover, , .
5.2. Slot-Based PRM Detection and Reed–Solomon List Recovery Decoding
The complete signal sent by the active user k is expressed as
after receiving the signals, the AP prioritizes performing decoding operations in each slot. To be more specific, the received signal in time slot n can be expressed as
where denotes the channel coefficient between the active user k and AP in slot n. The coefficients are estimated in the process of identifying the most probable transmitted signals, while is the complex additive white Gaussian noise (AWGN).
In Algorithm 2, we summarize the process of PRM reconstruction in a multi-user scenario within a single slot. We consider the input signal as a linear superposition of users and require the AP to output all the message set . Lines 1–7 of Algorithm 2 summarize the OMP-based inner-code detection algorithm in the multi-user scenario. Since OMP is an iterative algorithm, the number of output codewords is equivalent to the count of decoding iterations . For the outer-decode process, we denote , as the input signal of the outer-decoder, which results from removing the coset sequence from the messages received from inner decoding and connecting the repeated results. This process is described in lines 8–10. Lines 12 to 15 perform the outer Reed–Solomon decoding process and the detailed procedure is suggested in the literature [22]. All possibilities of decoding results for each user are saved in the list .
| Algorithm 2: PRM reconstruction in a multi-user scenario |
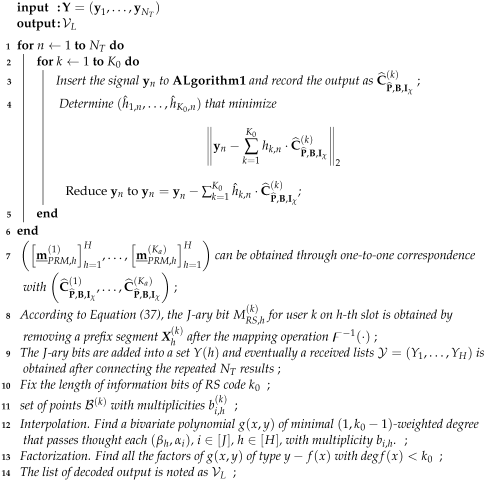 |
6. Performance Analysis
Our proposed URA system depends on the reliability of PRM detection in each chunk and the efficiency of the outer decoder in coupling the information between slots. The purpose of this section is to discuss how the PRM sequence is distributed in each sub-block, which is one of the most crucial factors influencing slot-based inner-code detection performance.
The PRM Distribution for a Single Slot
The number of sequences for a received signal involved in linear superposition is the key factor governing the distribution of codewords within a particular slot.
Next, we define a random variable to further explore the above event and we use to denote the event that “a set corresponding to the selected rule contains a specific slot index”.
To examine the probability that the time slot will be chosen, evaluate the likelihood that the event “a slot is contained in the chosen set ” takes place is sufficient, which can be described as and the probability equals
where and . This result is numerically equivalent to the probability that a coset will be selected when a subspace is provided. As a matter of fact, a specific slot will appear only once in each manner of partitioning the space . Thus, with a total of partition manners, a specific bit will appear times in all conceivable subsets . Furthermore, the number of subgroups is and the exact location is repeated times for a given subspace ; herein, users who choose the same subspace but different subgroups will not collide; in other words, for two random selections within a given subspace, the probability that no conflicts will arise equals the chance of selecting two different subsets.
Next, we use to denote the event “a set corresponding to the selected rule contains a specific slot index”. According to (42), the variable obeys the Bernoulli distribution; we then derive the expectation . As the value of is , the number of probable appearances for slot is formulated as
which holds for arbitrary locations.
Let the random variable denote the total number of simultaneous appearances for users in slot . Consider the case in which users select separate elements from pool , which means that all users are not putting elements back while selecting rules. Thus, the probability mass function (PMF) of is calculated as follows
where , . Accordingly, the variable is expected to be
and variance have the form of
It is assumed that users are not prohibited from selecting the same rules more than once (SPC collisions) and obeys the PMF being
obey the binomial distribution with its expectation and variance expressed as
and
We find that , while . Different strategies for picking rules from pool do not affect the average number of codewords in one slot. Furthermore, when the active users choose from the separate SPCs, the inner codes are distributed more uniformly throughout the slots. In the presence of selecting the same rules more than once, the probability that many PRM sequences could collide in one slot increases, thus resulting in a higher multi-user interference (MUI).
7. Simulation Results
7.1. The Distribution of Slot-Based PRM Sequences
The simulations in this subsection illustrate the probability distribution of the number of PRM codes that can be accommodated simultaneously in one slot, i.e., . We denote “PRM-RS, no collision” and “PRM-RS, collision”, respectively, as the practical simulation results with and without SPC collision. Moreover, we denote “PRM-RS, Equation (44)” and “PRM-RS, Equation (47)”, respectively, as the theoretical results calculated from (44) and (47). The parameters for our PRM-RS scheme are and , and the sequence distributions for and 200 users are, respectively, depicted in Figure 3, Figure 4 and Figure 5. Moreover, Figure 6 illustrates the results with parameters and under . Observations can be drawn from this as follows:

Figure 3.
The distribution of PRM sequences across slots for , and for the benchmark scheme, both under .

Figure 4.
The distribution of PRM sequences across slots for , and for the benchmark scheme, both under .

Figure 5.
The distribution of PRM sequences across slots for , and for the benchmark scheme, both under .

Figure 6.
The distribution of PRM sequences across slots for , and .
- PRM sequences are distributed more evenly when active users employ different SPCs. If collisions occur, more codewords will overlap at one slot, resulting in a rise in multi-user interference (MUI) and an increased probability of failure detection.
- Figure 6 illustrates that the “no collision” case is no longer valid when .
Even though the distribution is only improved under certain conditions (user count less than 200), the proposed inner-code construction and detection algorithm, in conjunction with the outer error correction technique, can improve the overall performance. This will be discussed in more detail in the next subsection.
7.2. The Overall Performance of the SPC-Based CCS for URA System
7.2.1. t-Tree Code as the Outer Code
To begin with, let us employ a decoder capable of correcting up to t errors as the outer code in different URA schemes, i.e., “t-tree code” and “PRM-tree”. The benchmarks called “t-tree code” from [22] are plotted by the green lines in Figure 7. We then evaluated the proposed “PRM-tree” scheme, i.e., the proposed PRM sequence is employed as the inner codeword, in which the former -bit message is filled with the selected SPC, and the remaining J-bit is used to transport the user’s messages; moreover, the decoder capable of correcting t errors continues to make up the outer code. Following [22], we employ the greedy information bits allocation method, assigning the maximum number of information bits at each subsequent slot keeping the constraint to find the minimum (see Section VII in [22] for more details). Based on this, parameters of H, N, , m, , G, J and in the proposed URA scheme are also considered.

Figure 7.
The performance for quasi-static Rayleigh fading channel is expressed as the required per active user vs. the number of active users , given the channel uses , the users’ messages bits and the target error probability , . The optimal parameters in our PRM-based scheme are carefully chosen to minimize the required . The curves are presented as follows: t-tree code for from [22], PRM-tree scheme (optimal parameters are taken from the Table 1 and Table 2), Reed–Solomon scheme from [22] and PRM-RS scheme (optimal parameters are taken from Table 3).
The PRM capacity formula under one rank is shown below:
it is worth noting that and share the similar Formula (48).
Increasing t requires a longer outer-code length H, where . By substituting and r into (48), it is easy to see that the H value directly controls the SPC capacity . On this basis, the optimal setups of H for and are set to be 32 and 64, respectively. However, cases are not valid in our URA setups since is no longer sufficient for and thus is the next choice (H must be a power of two). It can be seen from Equation (42) that the value of related to requires a larger to preserve the average number of probable appearances in each slot, whereas would become smaller under the constraint of (T is fixed and ), which results in the collapse of the inner-code performance. Table 1 presents the optimal G-ary, and J-ary for different t, as well as the outer-code length (and rate). Optimal parameters for the overall system are carefully selected as in Table 2. Simulations are shown in Figure 7, where purple lines illustrate the resulting energy efficiency for and 3 of “PRM-tree”. Based on the simulations, we can infer the following observations:

Table 1.
Optimal G-ary, and J-ary, as well as the outer-code length H (and rate ) for different t.

Table 2.
URA system parameters for “PRM-tree” scheme.
- PRM sequence for a given rank suffices for a user’s message delivery, indicating that the PRM codebook is highly spectral efficient due to its large sequence space.
- The outer-code length is used for and for . Substituting and into (38), we observe that the latter case () performs relatively poorly since it has a greater number of simultaneous appearances, which leads to inner-code failure at for and, for , . This result is consistent with Figure 6.
- For the curves of , the “PRM-tree” scheme corrects the case of the “t-tree code” scheme in which the overall performance degrades as t increases, i.e., an outer code with a larger t performs better on the condition that the inner code has the same length and the required path number is sufficient (“PRM-tree” schemes use paths and paths for “t-tree code”).
7.2.2. PRM-Based Reed–Solomon Scheme
A “PRM-RS” scheme based on the inner PRM code in conjunction with an outer Reed–Solomon code (as illustrated in Algorithm 2) is simulated in this section, and the per-user error probability as a function of for and 200 for this “PRM-RS” scheme is obtained (in Figure 8). The optimal system parameters are depicted in Table 3. It can be seen from Figure 8 that:

Figure 8.
Probability of error vs. for three system loads (number of active users), and 220.

Table 3.
URA system parameters for “PRM-RS” scheme.
- The minimum exceeds when the user count reaches 220.
The energy efficiency is the minimum energy required to serve users with PUPE less than , which is depicted in the blue line in Figure 7 under our optimal setups (see Table 3). We also need to adjust the number of CRC bits to suppress falsely detected messages following the same method as operated in [22]. The benchmark is the RS scheme in [22] which is plotted using an orange line.
The increase of r necessitates a lengthier to maintain the SPC pool capacity and the length of the inner code cannot be increased due to the channel uses T constraint. Furthermore, the decrease in inner-code length also weakens its performance. Therefore, we fix the SPC capacity as with and . On this basis, when the prefix length is fixed, a rise in value G leads to a larger J, which directly increases the outer code rate. Additionally, an increase in the outer code rate would weaken its performance. In light of this, carefully selecting the G value is critical. Simulation demonstrates that it is more efficient than the original RS when is less than 185, even with a constant inner-code length for different user counts.
8. Conclusions
In this paper, We addressed a general framework for CCS under the packetized and slotted transmission protocol based on inner PRM codes and outer error correction codes. First, we propose PRM sequences to transmit information chunks in slots since their geometry property facilitates computationally efficient PRM detection. Furthermore, we extend the space segmenting strategy of PRM sequences to construct a predefined dictionary of SPCs for slot occupation and the SPC selection mechanism is prescribed by an information segment for each user. The factors influencing slot-based PRM detection performance are discussed. We validate the error probability advantage of our proposed PRM-based URA scheme through simulation. We further proposed to use list recoverable codes correcting t errors in the coded compressed sensing scheme. Specifically, we propose two practical constructions of outer codes. The first one is a modification of the tree code. It utilizes the PRM as inner codes and adds a SPC, and the major difference is a decoder capable of correcting up to t errors. The second one is based on the Reed–Solomon codes and Guruswami–Sudan list decoding algorithm. The optimal setups are determined to minimize SNR by optimizing the inner and outer codes jointly. Both schemes provide better energy efficiency compared with the benchmark. In the following study, we will perform a matrix decomposition of the Clifford matrix related to the patterned Reed–Muller sequence and view this decomposition process as a reconstruction of the transmitter design. Moreover, the model is extended to accommodate multiple antennas for the URA system. We will also consider an iterative decoding algorithm to solve the signal recovery at the receiver.
Author Contributions
The work was realized with the collaboration of all the authors. W.X. contributed to the main results and simulation. H.Z. organized the work, supervised the research and reviewed the draft of the paper. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Saad, W.; Bennis, M.; Chen, M. A vision of 6G wireless systems: Applications, trends, technologies, and open research problems. IEEE Netw. 2019, 34, 134–142. [Google Scholar] [CrossRef]
- Guo, F.; Yu, F.R.; Zhang, H.; Li, X.; Ji, H.; Leung, V.C. Enabling massive IoT toward 6G: A comprehensive survey. IEEE Internet Things J. 2021, 8, 11891–11915. [Google Scholar] [CrossRef]
- Wu, Y.; Gao, X.; Zhou, S.; Yang, W.; Polyanskiy, Y.; Caire, G. Massive access for future wireless communication systems. IEEE Wirel. Commun. 2020, 27, 148–156. [Google Scholar] [CrossRef]
- Chen, X.; Ng, D.W.K.; Yu, W.; Larsson, E.G.; Al-Dhahir, N.; Schober, R. Massive access for 5G and beyond. IEEE J. Sel. Areas Commun. 2020, 39, 615–637. [Google Scholar] [CrossRef]
- Chettri, L.; Bera, R. A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet Things J. 2020, 7, 16–32. [Google Scholar] [CrossRef]
- Zhang, J.; Lu, L.; Sun, Y.; Chen, Y.; Liang, J.; Liu, J.; Hernando, F.J.L. PoC of SCMA-based uplink grant-free transmission in UCNC for 5G. IEEE Internet Things J. 2017, 35, 1353–1362. [Google Scholar]
- Masoudi, M.; Azari, A.; Yavuz, E.A.; Cavdar, C. Grant-free radio access IoT networks: Scalability analysis in coexistence scenarios. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–7. [Google Scholar]
- Shahab, M.B.; Abbas, R.; Shirvanimoghaddam, M.; Johnson, S.J. Grant-free non-orthogonal multiple access for IoT: A survey. IEEE Commun. Surv. Tutorials 2020, 22, 1805–1838. [Google Scholar] [CrossRef]
- Chen, X.; Guo, D. Many-access channels: The Gaussian case with random user activities. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Honolulu, HI, USA, 30 June–5 July 2014; pp. 3127–3131. [Google Scholar]
- Chen, X.; Chen, T.Y.; Guo, D. Capacity of Gaussian many-access channels. IEEE Trans. Inf. Theory 2017, 63, 3516–3539. [Google Scholar] [CrossRef]
- Polyanskiy, Y. A perspective on massive random-access. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 2523–2527. [Google Scholar]
- Zadik, I.; Polyanskiy, Y.; Thrampoulidis, C. Improved bounds on Gaussian MAC and sparse regression via Gaussian inequalities. In Proceedings of the 2019 IEEE International Symposium on Information Theory (ISIT), Paris, France, 7–12 July 2019; pp. 430–434. [Google Scholar]
- Kowshik, S.S.; Polyanskiy, Y. Fundamental limits of many-user MAC with finite payloads and fading. IEEE Trans. Inf. Theory 2021, 67, 5853–5884. [Google Scholar] [CrossRef]
- Ngo, K.H.; Lancho, A.; Durisi, G. Unsourced multiple access with random user activity. arXiv 2022, arXiv:2202.06365. [Google Scholar] [CrossRef]
- Pradhan, A.K.; Amalladinne, V.K.; Narayanan, K.R.; Chamberland, J.F. LDPC Codes with Soft Interference Cancellation for Uncoordinated Unsourced Multiple Access. In Proceedings of the IEEE International Conference on Communications (ICC), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Amalladinne, V.K.; Pradhan, A.K.; Rush, C.; Chamberland, J.F.; Narayanan, K.R. Unsourced random access with coded compressed sensing: Integrating AMP and belief propagation. IEEE Trans. Inf. Theory 2022, 68, 2384–2409. [Google Scholar] [CrossRef]
- Truhachev, D.; Bashir, M.; Karami, A.; Nassaji, E. Low-Complexity Coding and Spreading for Unsourced Random Access. IEEE Commun. Lett 2021, 25, 774–778. [Google Scholar] [CrossRef]
- Amalladinne, V.K.; Vem, A.; Soma, D.K.; Narayanan, K.R.; Chamberland, J.F. A coupled compressive sensing scheme for unsourced multiple access. In Proceedings of the 2018 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Calgary, AB, Canada, 15–20 April 2018; pp. 6628–6632. [Google Scholar]
- Amalladinne, V.K.; Chamberland, J.F.; Narayanan, K.R. A Coded Compressed Sensing Scheme for Unsourced Multiple Access. IEEE Trans. Inf. Theory 2020, 66, 6509–6533. [Google Scholar] [CrossRef]
- Fengler, A.; Haghighatshoar, S.; Jung, P.; Caire, G. Non-Bayesian Activity Detection, Large-Scale Fading Coefficient Estimation, and Unsourced Random Access With a Massive MIMO Receiver. IEEE Trans. Inf. Theory 2021, 67, 2925–2951. [Google Scholar] [CrossRef]
- Andreev, K.; Rybin, P.; Frolov, A. Reed-Solomon coded compressed sensing for the unsourced random access. In Proceedings of the 2021 17th International Symposium on Wireless Communication Systems (ISWCS), Berlin, Germany, 6–9 September 2021; pp. 1–5. [Google Scholar]
- Andreev, K.; Rybin, P.; Frolov, A. Coded Compressed Sensing with List Recoverable Codes for the Unsourced Random Access. IEEE Trans. Commun. 2022, 70, 7886–7898. [Google Scholar] [CrossRef]
- Liang, Z.; Zheng, J.; Ni, J. Index modulation–aided mixed massive random access. Front. Commun. Networks 2021, 2, 694557. [Google Scholar] [CrossRef]
- Che, J.; Zhang, Z.; Yang, Z.; Chen, X.; Zhong, C.; Ng, D.W.K. Unsourced random massive access with beam-space tree decoding. IEEE J. Sel. Areas Commun. 2021, 40, 1146–1161. [Google Scholar] [CrossRef]
- Fengler, A.; Jung, P.; Caire, G. SPARCs for unsourced random access. IEEE Trans. Inf. Theory 2021, 67, 6894–6915. [Google Scholar] [CrossRef]
- Ebert, J.R.; Amalladinne, V.K.; Chamberland, J.F.; Narayanan, K.R. A Hybrid Approach to Coded Compressed Sensing Where Coupling Takes Place Via the Outer Code. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Toronto, ON, Canada, 6–11 June 2021; pp. 4770–4774. [Google Scholar]
- Ebert, J.R.; Amalladinne, V.K.; Rini, S.; Chamberland, J.F.; Narayanan, K.R. Coded demixing for unsourced random access. IEEE Trans. Signal Process. 2022, 70, 2972–2984. [Google Scholar] [CrossRef]
- Howard, S.D.; Calderbank, A.R.; Searle, S.J. A fast reconstruction algorithm for deterministic compressive sensing using second order Reed-Muller codes. In Proceedings of the 2008 42nd Annual Conference on Information Sciences and Systems, Princeton, NJ, USA, 19–21 March 2008; pp. 11–15. [Google Scholar]
- Calderbank, R.; Jafarpour, S. Reed Muller sensing matrices and the LASSO. In Proceedings of the Sequences and Their Applications–SETA 2010: 6th International Conference (SETA), Paris, France, 13–17 September 2010; pp. 442–463. [Google Scholar]
- Calderbank, R.; Howard, S.; Jafarpour, S. Sparse reconstruction via the Reed-Muller sieve. In Proceedings of the 2010 IEEE International Symposium on Information Theory (ISIT), Austin, TX, USA, 13–18 June 2010; pp. 1973–1977. [Google Scholar]
- Zhang, L.; Luo, J.; Guo, D. Neighbor discovery for wireless networks via compressed sensing. Perform. Eval. 2013, 70, 457–471. [Google Scholar] [CrossRef]
- Zhang, H.; Li, R.; Wang, J.; Chen, Y.; Zhang, Z. Reed-Muller sequences for 5G grant-free massive access. In Proceedings of the GLOBECOM 2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar]
- Wang, J.; Zhang, Z.; Hanzo, L. Joint active user detection and channel estimation in massive access systems exploiting Reed–Muller sequences. IEEE J. Sel. Top. Signal Process 2019, 13, 739–752. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, Z.; Hanzo, L. Incremental massive random access exploiting the nested Reed-Muller sequences. IEEE Trans. Wirel. Commun. 2020, 20, 2917–2932. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, Z.; Chen, X.; Zhong, C.; Hanzo, L. Unsourced massive random access scheme exploiting reed-muller sequences. IEEE Trans. Commun. 2020, 70, 1290–1303. [Google Scholar] [CrossRef]
- Calderbank, R.; Thompson, A. CHIRRUP: A practical algorithm for unsourced multiple access. Inform. Inference J. IMA 2020, 9, 875–897. [Google Scholar] [CrossRef]
- Tirkkonen, O.; Calderbank, R. Codebooks of complex lines based on binary subspace chirps. In Proceedings of the 2019 IEEE Information Theory Workshop (ITW), Visby, Sweden, 25–28 August 2019; pp. 1–5. [Google Scholar]
- Pllaha, T.; Tirkkonen, O.; Calderbank, R. Reconstruction of multi-user binary subspace chirps. In Proceedings of the 2020 IEEE International Symposium on Information Theory (ISIT), Los Angeles, CA, USA, 21–26 June 2020; pp. 531–536. [Google Scholar]
- Pllaha, T.; Tirkkonen, O.; Calderbank, R. Binary subspace chirps. IEEE Trans. Inf. Theory 2022, 68, 7735–7752. [Google Scholar] [CrossRef]
- Abbe, E.; Ye, M. Reed-Muller codes polarize. IEEE Trans. Inf. Theory 2020, 66, 7311–7332. [Google Scholar] [CrossRef]
- Abbe, E.; Shpilka, A.; Ye, M. Reed–Muller codes: Theory and algorithms. IEEE Trans. Inf. Theory 2020, 67, 3251–3277. [Google Scholar] [CrossRef]
- Calderbank, R.; Howard, S.; Jafarpour, S. Construction of a large class of deterministic sensing matrices that satisfy a statistical isometry property. IEEE J. Sel. Top. Signal Process. 2022, 4, 358–374. [Google Scholar] [CrossRef]
- Rengaswamy, N.; Calderbank, R.; Kadhe, S.; Pfister, H.D. Logical Clifford synthesis for stabilizer codes. IEEE Trans. Quantum Eng. 2020, 1, 1–17. [Google Scholar] [CrossRef]
- Maslov, D.; Roetteler, M. Shorter stabilizer circuits via Bruhat decomposition and quantum circuit transformations. IEEE Trans. Inf. Theory 2018, 64, 4729–4738. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).