Designing a Private and Secure Personal Health Records Access Management System: A Solution Based on IOTA Distributed Ledger Technology
Abstract
1. Introduction
1.1. Aim of This Study
1.2. Related Works
- IOTA Tangle
- Distributed Ledger Technology (DLT)
- IPFS protocols
- Application Programming Interface (API)
- Proxy Re-encryption (PRE)
- Access Control
1.3. Comparison with Blockchain
2. Materials and Methods
2.1. Comparison with Blockchain
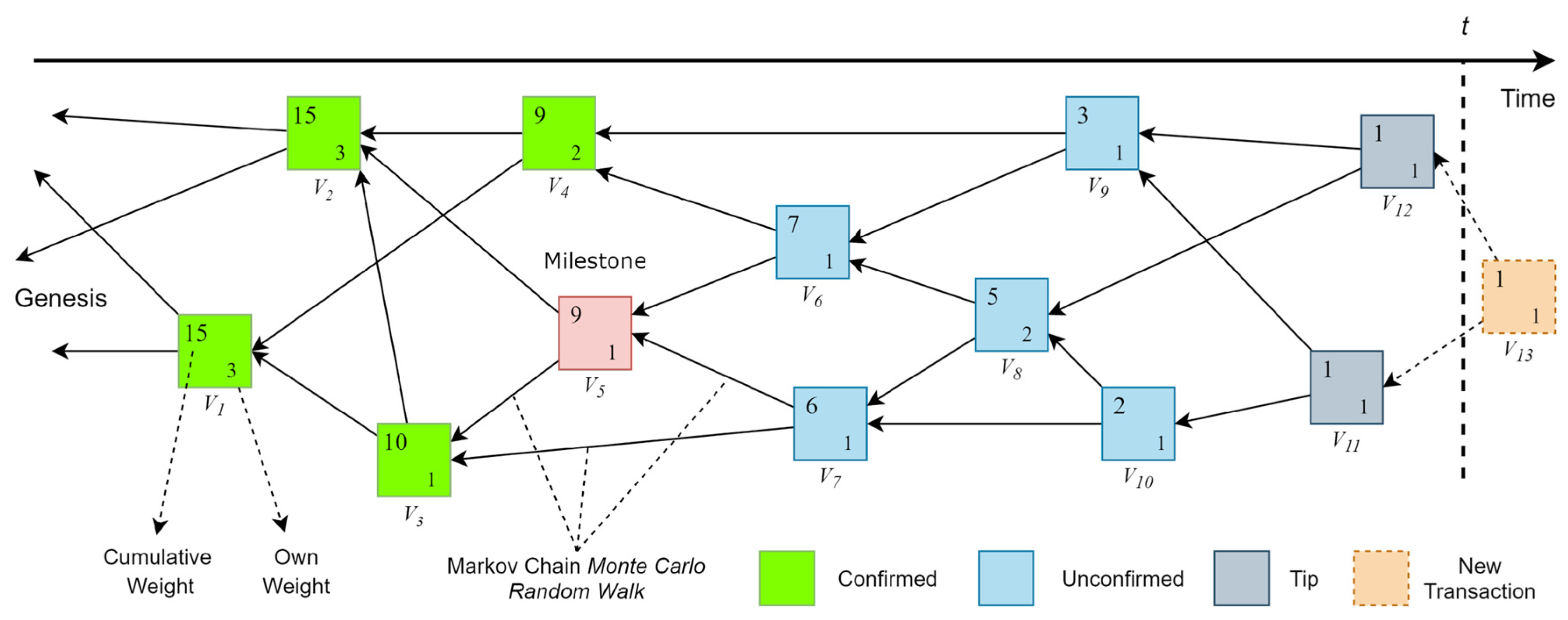
2.1.1. IOTA Tangle
V6(cumulative weight) = 1+ 2 + 1 + 1 + 1 + 1 = 7
2.1.2. IOTA Address Generation
2.1.3. IOTA Message Frame
2.1.4. IOTA Masked Authenticated Messaging (MAM)
2.1.5. Proof of Work
2.1.6. Smart Contracts
2.1.7. Private–Public Key Management
- Key Generation:
- Encryption:
- Decryption (Patient):
- Re-encryption:
- Decryption (Doctor):
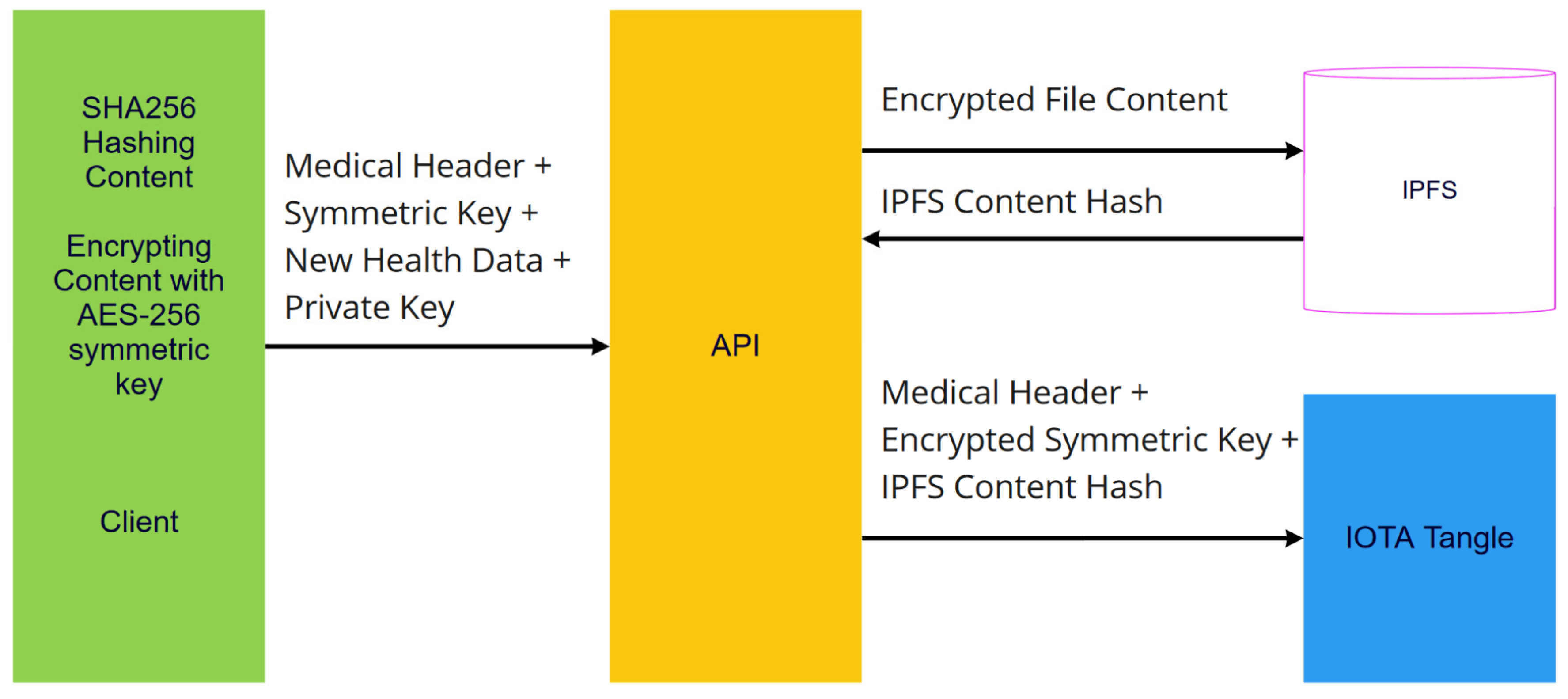
2.1.8. IPFS and File Management
2.2. Proposed Framework for Patient Health Records Access Management System
2.3. Actors and Main Objects of the Framework
2.3.1. Patient
2.3.2. Doctor
2.3.3. Hospital
2.3.4. Web Appointment
2.3.5. QR Scanner
2.3.6. Smart Contracts
2.3.7. Patient Data Visualizer (PDV)
2.3.8. IPFS
2.4. Description of Workflows Used in the Proposed Framework
2.4.1. Hospital Admission
2.4.2. Patient Discharge
2.4.3. Remote Patient Health Data Record
3. Results
3.1. Application 1: Web Appointment with Hospital
Creating Web Appointment
- Patient makes an appointment with doctor through hospital appointment system.
- Patient provides IOTA Address and UUID.
- Web appointment application creates a channel with Doctor Patient Medical Data Visualizer application via IOTA MAM protocol to submit patient information with encrypted private MAM channel; this process is shown in Figure 14.
3.2. Application 2: Doctor Patient Medical Data Visualizer
3.2.1. Creating Doctor Profile
- Doctor provides IOTA Seed.
- Proxy Re-encryption Private Key.
- Proxy Re-encryption Public Key.
- Signature Private Key.
- Signature Public Key, as shown in Figure 15.
3.2.2. Finding Patient Appointments and Retrieving Patient Medical Records
- Doctor selects patient appointment, as can be seen in Figure 16 Step 1.
- Patient IOTA address and UUID are collected from IOTA MAM Channel.
- Patient IOTA address is searched in IOTA Tangle.
- Encrypted IOTA messages are collected from past transactions (Step 2).
- Received IOTA messages are decrypted with patient UUID (Step 3).
- Decrypted IOTA messages are allocated to medical data categories (Step 4).
- Doctor application connects to proxy Re-encryption server.
- Doctor application sends Doctor ID (Doctor Signature Public Key) to server for identification.
- Proxy server sends random data to be signed by doctor.
- Message is hashed using SHA-256 by doctor application and hash signed with Doctor Signature Private Key.
- Proxy server decrypts with Doctor Signature Public Key to confirm Doctor ID.
- If Doctor ID is confirmed, proxy server sends Proxy Re-encrypted Symmetric Key.
- Proxy Re-Encrypted Symmetric Key is decrypted by Doctor Proxy Re-encryption Private Key (Step 5).
- Encrypted PHR is stored in IPFS and is collected using IPFS CID.
- Encrypted Patient Health Record is decrypted with decrypted Proxy Re-encrypted Symmetric Key (Step 6).
3.2.3. Visualizing Patient Medical Record
- Doctor selects categories (Figure 17) to access medical records, which are collected from IPFS.
3.2.4. Assigning an IoT Device to a Patient
- Doctor selects a category and enters the root address of the device to assign IoT Medical Device to a patient.
- Doctor application subscribes to an IoT device channel through private IOTA MAM channel (Figure 18).
3.2.5. Creating New Medical Data
- After the doctor has selected a patient from Find Appointment, the doctor selects categories for new medical data and then writes clinical notes and creates medical data, as shown in Figure 19.
- Created medical data are encrypted with random AES-256 symmetric key.
- Encrypted medical data are stored in IPFS and then IPFS CID is collected.
- Symmetric key is encrypted with patient public key.
- Selected categories, encrypted symmetric key, and IPFS CID are recorded in patient IOT address as a transaction message.
3.3. Application 3: Patient Medical Record Access Control
3.3.1. Creating Patient Profile
- Patient enters IOTA Seed, UUID, Private Key, and Public Key.
- Patient creates new IOTA address with index number.
- Application creates an IOTA address using IOTA Seed and index number.
- Application also creates a barcode to corresponding IOTA address, shown in Figure 20.
3.3.2. Searching Medical Records
- Patient clicks search medical records (Step 1) (Figure 20).
- Patient Application connects to IOTA development server and searches transactions in given IOTA address.
- Messages are extracted from transactions and decrypted with UUID (Step 2).
- Decrypted messages are categorized into five categories (Step 3).
- Medical data are collected from IPFS using IPFS CID (Step 4).
- Symmetric key is decrypted with patient private key.
- Medical data are decrypted with decrypted symmetric key.
3.3.3. Visualizing Medical Records
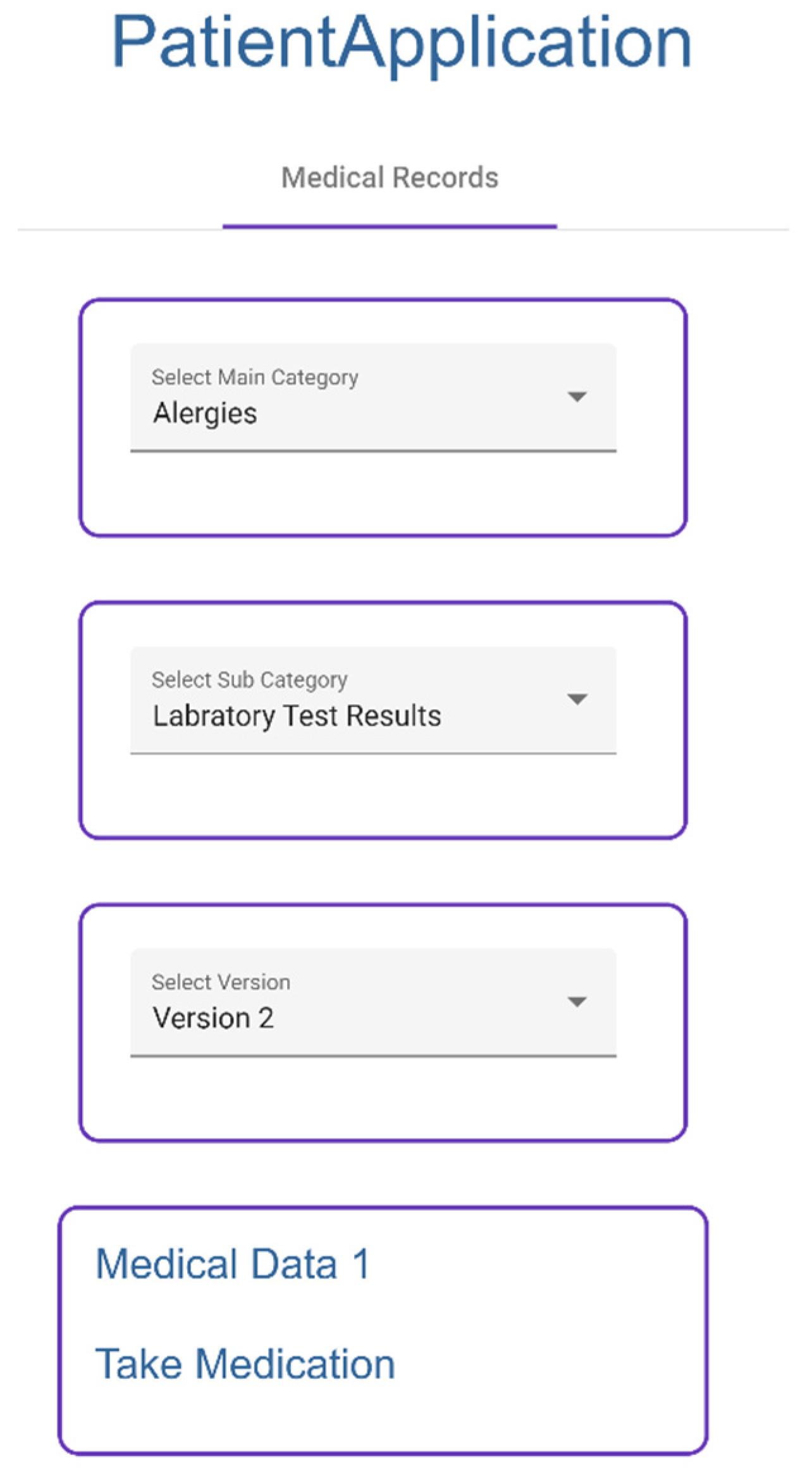
- Patient selects given categories to access medical records, which are collected from IPFS (Figure 21).
3.3.4. Giving Permission to Doctor
- Patient selects categories (Figure 22).
- Patient enters doctor public key and duration of permission to selected categories.
- Application collects the symmetric key of the category.
- Application creates re-encrypted symmetric key using doctor public key and symmetric key.
- Application sends doctor public key, duration, and re-encrypted symmetric key to proxy.
3.4. Application 4: Remote Medical IoT Device
4. Examination and Evaluation of the Proposed Applications
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ABF | Activity-based funding AES |
| AFGH | Ateniese, Fu, Green, and Hohenberger |
| API | Application Programming Interface |
| CID | Content Identifier |
| COVID-19 | Coronavirus Disease 2019 |
| DAG | Directed Acyclic Graph |
| DLT | Distributed Ledger Technology |
| EHR | Electronic Health Records |
| GW | Gigawatt |
| HIPAA | Health Insurance Portability and Accountability Act |
| HL7 | Health Level Seven International |
| FHIR | Fast Healthcare Interoperability Resources |
| ID | Identity |
| IoT | Internet of Things |
| IoMT | Internet of Medical Things |
| IPFS | InterPlanetary File System |
| IPLD | InterPlanetary Linked |
| MCMC | Markov chain Monte Carlo |
| MHR | My Health Record |
| MAM | Masked Authenticated Messaging |
| PDV | Patient Data Visualizer |
| PHR | Personal Health Records |
| PRE | Proxy Re-encryption |
| PoW | Proof of Work |
| P2P | Peer-to-Peer |
| SHA | Secure Hash Algorithm |
| QR | Quick Response |
| URL | Uniform Resource Locator |
| USA | United States of America |
| UUID | Universally Unique Identifier |
References
- Demir, O.; Kocak, B. A Decentralized File Sharing Framework for Sensitive Data. In Proceedings of the Big Data Innovations and Applications, Istanbul, Turkey, 26–28 August 2019; pp. 142–149. [Google Scholar]
- Lederman, R.; Ben-Assuli, O.; Vo, T.H. The role of the Internet of Things in Healthcare in supporting clinicians and patients: A narrative review. Health Policy Technol. 2021, 10, 100552. [Google Scholar] [CrossRef]
- Balaji, S.; Nathani, K.; Santhakumar, R. IoT Technology, Applications and Challenges: A Contemporary Survey. Wirel. Pers. Commun. 2019, 108, 363–388. [Google Scholar] [CrossRef]
- Yarlagadda, R.T. Internet of Things & Artificial Intelligence in Modern Society. SSRN Electron. J. 2018, 6, 374. [Google Scholar]
- Jungwirth, D.; Haluza, D. Information and communication technology and the future of healthcare: Results of a multi-scenario Delphi survey. Health Inform. J. 2019, 25, 161–173. [Google Scholar] [CrossRef] [PubMed]
- Marwaha, J.S.; Landman, A.B.; Brat, G.A.; Dunn, T.; Gordon, W.J. Deploying digital health tools within large, complex health systems: Key considerations for adoption and implementation. NPJ Digit. Med. 2022, 5, 13. [Google Scholar] [CrossRef] [PubMed]
- Jawarneh, M.; Alzubi, S. Factors Affecting the Success of Internet of Things for Enhancing Quality and Efficiency Implementation in Hospitals Sector in Jordan During the Crises of Covid-19. In Internet of Medical Things for Smart Healthcare: Covid-19 Pandemic; Springer: Berlin/Heidelberg, Germany, 2020; pp. 107–140. [Google Scholar]
- Selvaraj, S.; Sundaravaradhan, S. Challenges and opportunities in IoT healthcare systems: A systematic review. SN Appl. Sci. 2019, 2, 139. [Google Scholar] [CrossRef]
- Kelly, J.T.; Campbell, K.L.; Gong, E.; Scuffham, P. The Internet of Things: Impact and Implications for Health Care Delivery. J Med. Internet Res. 2020, 22, e20135. [Google Scholar] [CrossRef]
- Nausheen, F.; Begum, S.H. Healthcare IoT: Benefits, vulnerabilities and solutions. In Proceedings of the 2018 2nd International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2018; pp. 517–522. [Google Scholar]
- De Michele, R.; Furini, M. IoT Healthcare: Benefits, Issues and Challenges. In Proceedings of the 5th EAI International Conference on Smart Objects and Technologies for Social Good, Valencia, Spain, 25–27 September 2019; pp. 160–164. [Google Scholar]
- Adebisi, O.; Oladosu, D.; Busari, O.; Oyewola, Y. Design and implementation of hospital management system. Int. J. Eng. Innov. Technol. (IJEIT) 2015, 5. [Google Scholar] [CrossRef]
- Semantha, F.H.; Azam, S.; Shanmugam, B.; Yeo, K.C.; Beeravolu, A.R. A Conceptual Framework to Ensure Privacy in Patient Record Management System. IEEE Access 2021, 9, 165667–165689. [Google Scholar] [CrossRef]
- Yang, T.; Gentile, M.; Shen, C.-F.; Cheng, C.-M. Combining Point-of-Care Diagnostics and Internet of Medical Things (IoMT) to Combat the COVID-19 Pandemic. Diagnostics 2020, 10, 224. [Google Scholar] [CrossRef]
- Brous, P.; Janssen, M.; Herder, P. The dual effects of the Internet of Things (IoT): A systematic review of the benefits and risks of IoT adoption by organizations. Int. J. Inf. Manag. 2020, 51, 101952. [Google Scholar] [CrossRef]
- de Mello, B.H.; Rigo, S.J.; da Costa, C.A.; da Rosa Righi, R.; Donida, B.; Bez, M.R.; Schunke, L.C. Semantic interoperability in health records standards: A systematic literature review. Health Technol. 2022, 12, 255–272. [Google Scholar] [CrossRef] [PubMed]
- Rezaeibagha, F.; Win, K.T.; Susilo, W. A systematic literature review on security and privacy of electronic health record systems: Technical perspectives. Health Inf. Manag. J. 2015, 44, 23–38. [Google Scholar] [CrossRef] [PubMed]
- Vimalachandran, P.; Liu, H.; Lin, Y.; Ji, K.; Wang, H.; Zhang, Y. Improving accessibility of the Australian My Health Records while preserving privacy and security of the system. Health Inf. Sci. Syst. 2020, 8, 31. [Google Scholar] [CrossRef]
- Sarosh, P.; Parah, S.A.; Bhat, G.M.; Heidari, A.A.; Muhammad, K. Secret sharing-based personal health records management for the Internet of Health Things. Sustain. Cities Soc. 2021, 74, 103129. [Google Scholar] [CrossRef]
- Neves, A.L.; Freise, L.; Laranjo, L.; Carter, A.W.; Darzi, A.; Mayer, E. Impact of providing patients access to electronic health records on quality and safety of care: A systematic review and meta-analysis. BMJ Qual. Saf. 2020, 29, 1019–1032. [Google Scholar] [CrossRef]
- Galetsi, P.; Katsaliaki, K.; Kumar, S. Values, challenges and future directions of big data analytics in healthcare: A systematic review. Soc. Sci. Med. 2019, 241, 112533. [Google Scholar] [CrossRef]
- Zhou, L.; DeAlmeida, D.; Parmanto, B. Applying a user-centered approach to building a mobile personal health record app: Development and usability study. JMIR Mhealth Uhealth 2019, 7, e13194. [Google Scholar] [CrossRef]
- Butpheng, C.; Yeh, K.-H.; Xiong, H. Security and privacy in IoT-cloud-based e-health systems—A comprehensive review. Symmetry 2020, 12, 1191. [Google Scholar] [CrossRef]
- Keshta, I.; Odeh, A. Security and privacy of electronic health records: Concerns and challenges. Egypt. Inform. J. 2021, 22, 177–183. [Google Scholar] [CrossRef]
- Sun, Y.; Lo, F.P.-W.; Lo, B. Security and privacy for the internet of medical things enabled healthcare systems: A survey. IEEE Access 2019, 7, 183339–183355. [Google Scholar] [CrossRef]
- Roehrs, A.; da Costa, C.A.; da Rosa Righi, R. OmniPHR: A distributed architecture model to integrate personal health records. J. Biomed. Inform. 2017, 71, 70–81. [Google Scholar] [CrossRef]
- Semantha, F.H.; Azam, S.; Shanmugam, B.; Yeo, K.C. PbDinEHR: A Novel Privacy by Design Developed Framework Using Distributed Data Storage and Sharing for Secure and Scalable Electronic Health Records Management. J. Sens. Actuator Netw. 2023, 12, 36. [Google Scholar] [CrossRef]
- Semantha, F.H.; Azam, S.; Yeo, K.C.; Shanmugam, B. A systematic literature review on privacy by design in the healthcare sector. Electronics 2020, 9, 452. [Google Scholar] [CrossRef]
- Hylock, R.A.-O.; Zeng, X.A.-O. A Blockchain Framework for Patient-Centered Health Records and Exchange (HealthChain): Evaluation and Proof-of-Concept Study. J. Med. Internet Res. 2019, 21, e13592. [Google Scholar] [CrossRef]
- Thwin, T.; Vasupongayya, S. Blockchain-Based Access Control Model to Preserve Privacy for Personal Health Record Systems. Secur. Commun. Netw. 2019, 2019, 8315614. [Google Scholar] [CrossRef]
- Meier, P.; Beinke, J.H.; Fitte, C.; Schulte to Brinke, J.; Teuteberg, F. Generating design knowledge for blockchain-based access control to personal health records. Inf. Syst. E-Bus. Manag. 2021, 19, 13–41. [Google Scholar] [CrossRef]
- Hussien, H.M.; Yasin, S.M.; Udzir, N.I.; Ninggal, M.I. Blockchain-Based Access Control Scheme for Secure Shared Personal Health Records over Decentralised Storage. Sensors 2021, 21, 2462. [Google Scholar] [CrossRef]
- Rief, J.J.; Hamm, M.E.; Zickmund, S.L.; Nikolajski, C.; Lesky, D.; Hess, R.; Fischer, G.S.; Weimer, M.; Clark, S.; Zieth, C.; et al. Using Health Information Technology to Foster Engagement: Patients’ Experiences with an Active Patient Health Record. Health Commun. 2017, 32, 310–319. [Google Scholar] [CrossRef]
- Datta, A.; Dave, N.; Mitchell, J.; Nissenbaum, H.; Sharma, D. Privacy Challenges in Patient-Centric Health Information Systems. In 1st USENIX Workshop on Health Security and Privacy (HealthSec 10); USENIX Association: Berkeley, CA, USA, 2021. [Google Scholar]
- Foundation, I. EHealth-Enabling Privacy and Control of Healthare Data. Available online: https://www.iota.org/solutions/ehealth (accessed on 10 April 2022).
- SmartOptz. SmartOptz Medical IoT Platform. Available online: https://www.smartoptz.com/wp/ (accessed on 10 April 2022).
- Care, P. Improving Care Access and Remote Care Collaborations. Available online: https://pact.care/ (accessed on 10 April 2022).
- Rochman, S.; Istiyanto, J.E.; Dharmawan, A.; Handika, V.; Purnama, S.R. Optimization of tips selection on the IOTA tangle for securing blockchain-based IoT transactions. Procedia Comput. Sci. 2023, 216, 230–236. [Google Scholar] [CrossRef]
- Sunyaev, A.; Sunyaev, A. Distributed Ledger Technology. In Internet Computing: Principles of Distributed Systems and Emerging Internet-Based Technologies; Springer: Berlin/Heidelberg, Germany, 2020; pp. 265–299. [Google Scholar]
- Kang, P.; Yang, W.; Zheng, J. Blockchain Private File Storage-Sharing Method Based on IPFS. Sensors 2022, 22, 5100. [Google Scholar] [CrossRef] [PubMed]
- Jayabalan, J.; Jeyanthi, N. Scalable blockchain model using off-chain IPFS storage for healthcare data security and privacy. J. Parallel Distrib. Comput. 2022, 164, 152–167. [Google Scholar] [CrossRef]
- Ofoeda, J.; Boateng, R.; Effah, J. Application programming interface (API) research: A review of the past to inform the future. Int. J. Enterp. Inf. Syst. (IJEIS) 2019, 15, 76–95. [Google Scholar] [CrossRef]
- Mahamuni, N.; Pattewar, G.; Nikam, H.; Loka, O.; Patil, R. A Blockchain and Proxy Re-Encryption Based Approach for IoT Data Security: A Review. In Proceedings of the 2nd International Conference on Emerging Technologies and Intelligent Systems: ICETIS 2022 Volume 1; Springer: Berlin/Heidelberg, Germany, 2023; pp. 587–595. [Google Scholar]
- Kan, J.; Zhang, J.; Liu, D.; Huang, X. Proxy re-encryption scheme for decentralized storage networks. Appl. Sci. 2022, 12, 4260. [Google Scholar] [CrossRef]
- Popov, S.; Lu, Q. IOTA: Feeless and Free. In IEEE Blockchain Technical Briefs; Tech Briefs: New York, NY, USA, 2019. [Google Scholar]
- Cullen, A.; Ferraro, P.; King, C.; Shorten, R. On the Resilience of DAG-Based Distributed Ledgers in IoT Applications. IEEE Internet Things J. 2020, 7, 7112–7122. [Google Scholar] [CrossRef]
- Zheng, X.; Sun, S.; Mukkamala, R.R.; Vatrapu, R.; Ordieres-Meré, J. Accelerating Health Data Sharing: A Solution Based on the Internet of Things and Distributed Ledger Technologies. J. Med. Internet Res. 2019, 21, e13583. [Google Scholar] [CrossRef]
- Son, B.; Lee, J.; Jang, H. A Scalable IoT Protocol via an Efficient DAG-Based Distributed Ledger Consensus. Sustainability 2020, 12, 1529. [Google Scholar] [CrossRef]
- Hou, L.-Y.; Tang, T.-Y.; Liang, T.-Y. IOTA-BT: A P2P File-Sharing System Based on IOTA. Electronics 2020, 9, 1610. [Google Scholar] [CrossRef]
- Shafeeq, S.; Zeadally, S.; Alam, M.; Khan, A. Curbing Address Reuse in the IOTA Distributed Ledger: A Cuckoo-Filter-Based Approach. IEEE Trans. Eng. Manag. 2020, 67, 1244–1255. [Google Scholar] [CrossRef]
- Shahid, F.; Khan, A.; Malik, S.U.R.; Choo, K.-K.R. WOTS-S: A Quantum Secure Compact Signature Scheme for Distributed Ledger. Inf. Sci. 2020, 539, 229–249. [Google Scholar] [CrossRef]
- Popov, S.; Moog, H.; Camargo, D.; Capossele, A.; Dimitrov, V.; Gal, A.; Greve, A.; Kusmierz, B.; Mueller, S.; Penzkofer, A. The Coordicide. 2020, pp. 1–30. Available online: https://files.iota.org/papers/20200120_Coordicide_WP.pdf (accessed on 10 April 2022).
- Lindvall, L. How Is Authenthicity and Confidentiality Maintained for MAM Channels on the IOTA Tangle. 2019. Available online: https://varden.info/doc.php?id=7 (accessed on 10 April 2022).
- Saldamli, G.; Upadhyay, C.; Jadhav, D.; Shrishrimal, R.; Patil, B.; Tawalbeh, L.A. Improved gossip protocol for blockchain applications. Clust. Comput. 2022, 25, 1915–1926. [Google Scholar] [CrossRef]
- Rashid, A.; Siddique, M.J. Smart Contracts Integration between Blockchain and Internet of Things: Opportunities and Challenges. In Proceedings of the 2019 2nd International Conference on Advancements in Computational Sciences (ICACS), Lahore, Pakistan, 18–20 February 2019; pp. 1–9. [Google Scholar]
- Li, W.; Jin, C.; Kumari, S.; Xiong, H.; Kumar, S. Proxy re-encryption with equality test for secure data sharing in Internet of Things-based healthcare systems. Trans. Emerg. Telecommun. Technol. 2022, 33, e3986. [Google Scholar] [CrossRef]
- Chen, Y.; Hu, B.; Yu, H.; Duan, Z.; Huang, J. A threshold proxy re-encryption scheme for secure IoT data sharing based on blockchain. Electronics 2021, 10, 2359. [Google Scholar] [CrossRef]
- Manzoor, A.; Liyanage, M.; Braeke, A.; Kanhere, S.S.; Ylianttila, M. Blockchain Based Proxy Re-Encryption Scheme for Secure IoT Data Sharing. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; pp. 99–103. [Google Scholar]
- Muralidharan, S.; Ko, H. An InterPlanetary File System (IPFS) Based IoT Framework. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–2. [Google Scholar]
- Liu, Z.; Wang, S.; Duan, S.; Ren, L.; Wei, J. Dynamic Data Integrity Auditing Based on Hierarchical Merkle Hash Tree in Cloud Storage. Electronics 2023, 12, 717. [Google Scholar] [CrossRef]
- Gonzalez-Amarillo, C.; Cardenas-Garcia, C.; Mendoza-Moreno, M.; Ramirez-Gonzalez, G.; Corrales, J.C. Blockchain-iot sensor (Biots): A solution to iot-ecosystems security issues. Sensors 2021, 21, 4388. [Google Scholar] [CrossRef]
- Alsboui, T.; Qin, Y.; Hill, R.; Al-Aqrabi, H. Enabling distributed intelligence for the Internet of Things with IOTA and mobile agents. Computing 2020, 102, 1345–1363. [Google Scholar] [CrossRef]
- Dixit, S.K.; Sambasivan, M. A review of the Australian healthcare system: A policy perspective. SAGE Open Med. 2018, 6, 2050312118769211. [Google Scholar] [CrossRef]
- De Vries, A. Cryptocurrencies on the road to sustainability: Ethereum paving the way for Bitcoin. Patterns 2023, 4, 1–5. [Google Scholar] [CrossRef]
- Fillmore, A.R.; McKinley, C.D.; Tallman, E.F. Managing privacy, confidentiality, and risk: Towards trust. In Health Information Exchange; Elsevier: Amsterdam, The Netherlands, 2023; pp. 131–147. [Google Scholar]























| Existing Solutions | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Key Contexts | Rezaeibagha et al. [17] | Semantha et al. [13,28] | OmniPHR [26] | Healthchain [29] | Thwin and Vasupongayya [30] | Meier et al. [31] | Hussien et al. [32] | Skaly [35] | Smart Optz [36] | Pact [37] | Our Proposed Framework |
| IOTA Tangle [38] | ⚫ | ⚫ | ⚫ | ⚫ | |||||||
| Distributed Ledger Technology (DLT) [39] | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ | ||
| IPFS protocols [40,41] | ⚫ | ⚫ | ⚫ | ||||||||
| Application Programming Interface (API) [42] | ⚫ | ⚫ | |||||||||
| Proxy Re-encryption (PRE) [43,44] | ⚫ | ⚫ | |||||||||
| Access control [30] | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ | |||||
| Step | Description |
|---|---|
| Step 1 | Patient uses Hospital Web Application to make an appointment. Patient shares IOTA address and UUID. |
| Step 2 | Patient obtains Doctor Public Key from Hospital Web Application. Patient uses Patient Application to give permission to selected Patient Medical Records using Doctor Public Key. |
| Step 3 | Patient Application creates Re-encryption Key using Patient Private Key and Doctor Public Key. Patient Application uses Re-encryption Key to re-encrypt symmetric key that belongs to permissioned Medical Record. |
| Step 4 | Patient Application creates parameters of the Smart Contract 1 (Doctor Public Key, Permissioned Medical Header, duration of permission, and re-encrypted symmetric key). |
| Step 5 | Patient Application creates Smart Contract 1 to share proxy location with doctor for a limited period of time. |
| Step 6 | Smart Contract shares Doctor Public Key, Permissioned Medical Header, duration of permission, and re-encrypted symmetric key with a proxy. |
| Step 7 | Hospital receives patient information from Hospital Web Appointment and creates Smart Contract 2 to validate patient and patient’s insurance. Then, fixed amount of IOTA tokens from insurance or patient IOTA address is withdrawn. |
| Step 8 | Doctor searches patient appointment from Doctor Application (PDV). This information is received from Hospital Web Appointment Application. |
| Step 9 | PDV connects to IOTA node and searches patient address in IOTA Tangle. |
| Step 10 | PDV uses patient address to find old medical transactions in IOTA Tangle. |
| Step 11 | UUID encrypted transaction messages are extracted from messages. |
| Step 12 | Transaction messages are decrypted with UUID symmetric key. |
| Step 13 | Doctor searches patient smart contract. Smart contract validates doctor and sends proxy location. |
| Step 14 | Proxy validates Doctor using signature algorithm and sends medical header and corresponding re-encrypted symmetric key. |
| Step 15 | PDV uses Doctor Private Key to decrypt re-encrypted symmetric key.Patient records are downloaded from IPFS using IPFS hash and decrypted with decrypted symmetric keys and stored in PVR temporarily. |
| Step 16 | After patient records are visualized by PDV, doctor assigns IOT devices to patient using PDV and creates smart contracts with each assigned IOT Device. |
| Step 17 | Each IOT device has a separate smart contract that is linked with Smart Contract 2 to request balance during medication. |
| Step 18 | Smart Contract 3 updates Account Balance during medications. |
| Step 19 | If needed, more IOTA tokens are taken from Smart Contract 2. |
| Step | Description |
|---|---|
| Step 21 | Doctor creates new patient medical data from Doctor Application (PDV). |
| Step 22 | PDV (Patient Data Visualizer) categorizes data according to Medical ID, such as test results, treatments, etc.. |
| Step 23 | After data are collected over a period of time, all data encrypted with random AES-256 symmetric key. |
| Step 24 | Encrypted data uploaded to IPFS. |
| Step 25 | IPFS hash address created. |
| Step 26 | Symmetric key encrypted with patient public key. |
| Step 27 | Using Encrypted symmetric key, IPFS Hash, and Medical ID, a medical header is created. |
| Step 28 | Medical header encrypted with patient UUID and saved in IOT transaction message. |
| Step 29 | Hospital sends patient discharge information to Smart Contract. |
| Step 30 | Smart Contract validates insurance and sends unused IOTA tokens to patient IOTA address. |
| Step | Description |
|---|---|
| Step 31 | Patient accesses the IOT device and starts IoT device. |
| Step 32 | Patient logs into device interface. |
| Step 33 | Patient obtains IOTA MAM Root Address and side key. |
| Step 34 | Patient registers new IOT device using IOTA MAM Root Address. |
| Step 35 | Patient application collects data from root address. |
| Step 36 | After data are collected over a period of time, all data are encrypted with random AES-256 symmetric key. |
| Step 37 | Encrypted data are uploaded to IPFS. |
| Step 38 | IPFS hash address is created. |
| Step 39 | Symmetric key is encrypted with patient private key. |
| Step 40 | Using Encrypted symmetric key, IPFS Hash, and Medical ID, a medical header is created. |
| Step 41 | Medical header is encrypted with patient UUID and saved in IOT transaction message. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Akbulut, S.; Semantha, F.H.; Azam, S.; Pilares, I.C.A.; Jonkman, M.; Yeo, K.C.; Shanmugam, B. Designing a Private and Secure Personal Health Records Access Management System: A Solution Based on IOTA Distributed Ledger Technology. Sensors 2023, 23, 5174. https://doi.org/10.3390/s23115174
Akbulut S, Semantha FH, Azam S, Pilares ICA, Jonkman M, Yeo KC, Shanmugam B. Designing a Private and Secure Personal Health Records Access Management System: A Solution Based on IOTA Distributed Ledger Technology. Sensors. 2023; 23(11):5174. https://doi.org/10.3390/s23115174
Chicago/Turabian StyleAkbulut, Serkan, Farida Habib Semantha, Sami Azam, Iris Cathrina Abacan Pilares, Mirjam Jonkman, Kheng Cher Yeo, and Bharanidharan Shanmugam. 2023. "Designing a Private and Secure Personal Health Records Access Management System: A Solution Based on IOTA Distributed Ledger Technology" Sensors 23, no. 11: 5174. https://doi.org/10.3390/s23115174
APA StyleAkbulut, S., Semantha, F. H., Azam, S., Pilares, I. C. A., Jonkman, M., Yeo, K. C., & Shanmugam, B. (2023). Designing a Private and Secure Personal Health Records Access Management System: A Solution Based on IOTA Distributed Ledger Technology. Sensors, 23(11), 5174. https://doi.org/10.3390/s23115174







