Ensemble Siamese Network (ESN) Using ECG Signals for Human Authentication in Smart Healthcare System
Abstract
1. Introduction
- Proposing an Ensemble Siamese network (ESN) using ECG signals to compare a new sample with the saved records from the claimed identity in the repository.
- Saving encoded data from registered users in a repository instead of having the raw information to increase data safety.
- Using a modified Fourier transform customized for this application to extract more reliable features from the input samples, which results in training a more robust network.
- Developing a strong authentication method that can enroll new users at run time while being robust to imbalance sample conditions.
2. Related Work
3. The Proposed Method
3.1. Data Collection
- Wearable devices: ECG sensors can be integrated into wearable devices such as smartwatches, wristbands, or patches.
- Electrodes: ECG electrodes can be attached to the user’s chest, arms, or legs to collect the ECG signal.
- Smartphones: Some smartphones have built-in ECG sensors that can collect the user’s ECG signal.
- Holter monitors: Holter monitors are portable ECG machines that can continuously monitor the user’s ECG signal for up to 24 h.
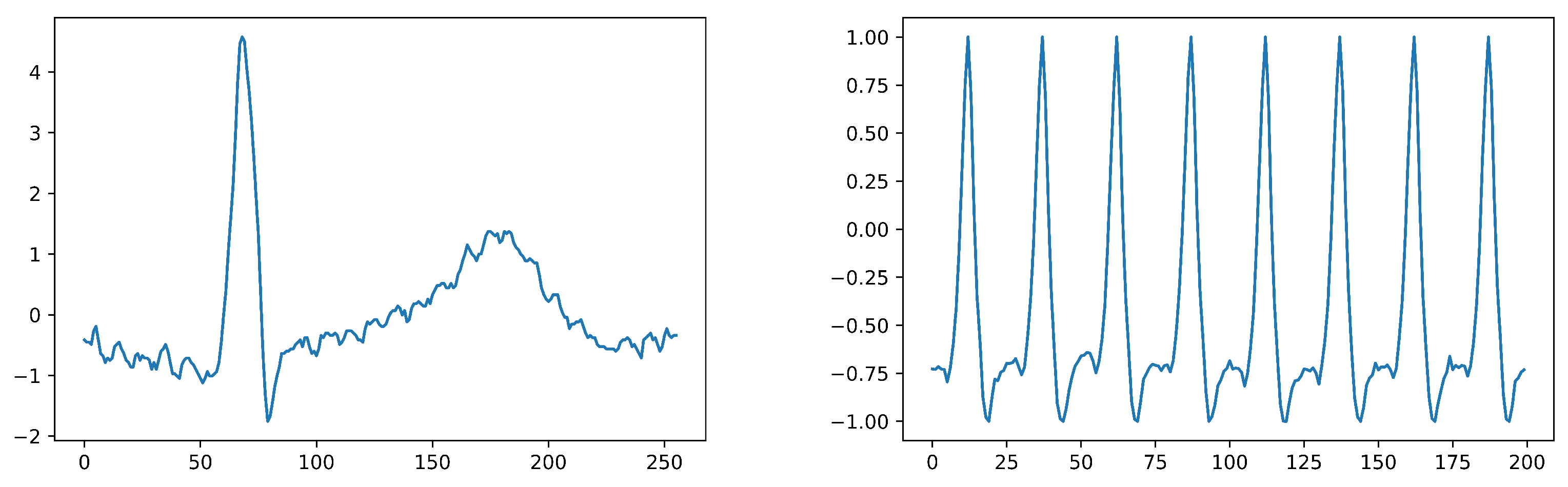
3.2. Preprocessing and Data Preparation
- Using machine learning models on raw ECG signals: In this approach, the raw ECG signal is used as input to a machine learning model such as a neural network or a support vector machine.
- Using Fourier transform and then machine learning: In this approach, the ECG signal is first transformed into the frequency domain using Fourier transform. The resulting frequency spectrum is then used as input to a machine learning model.
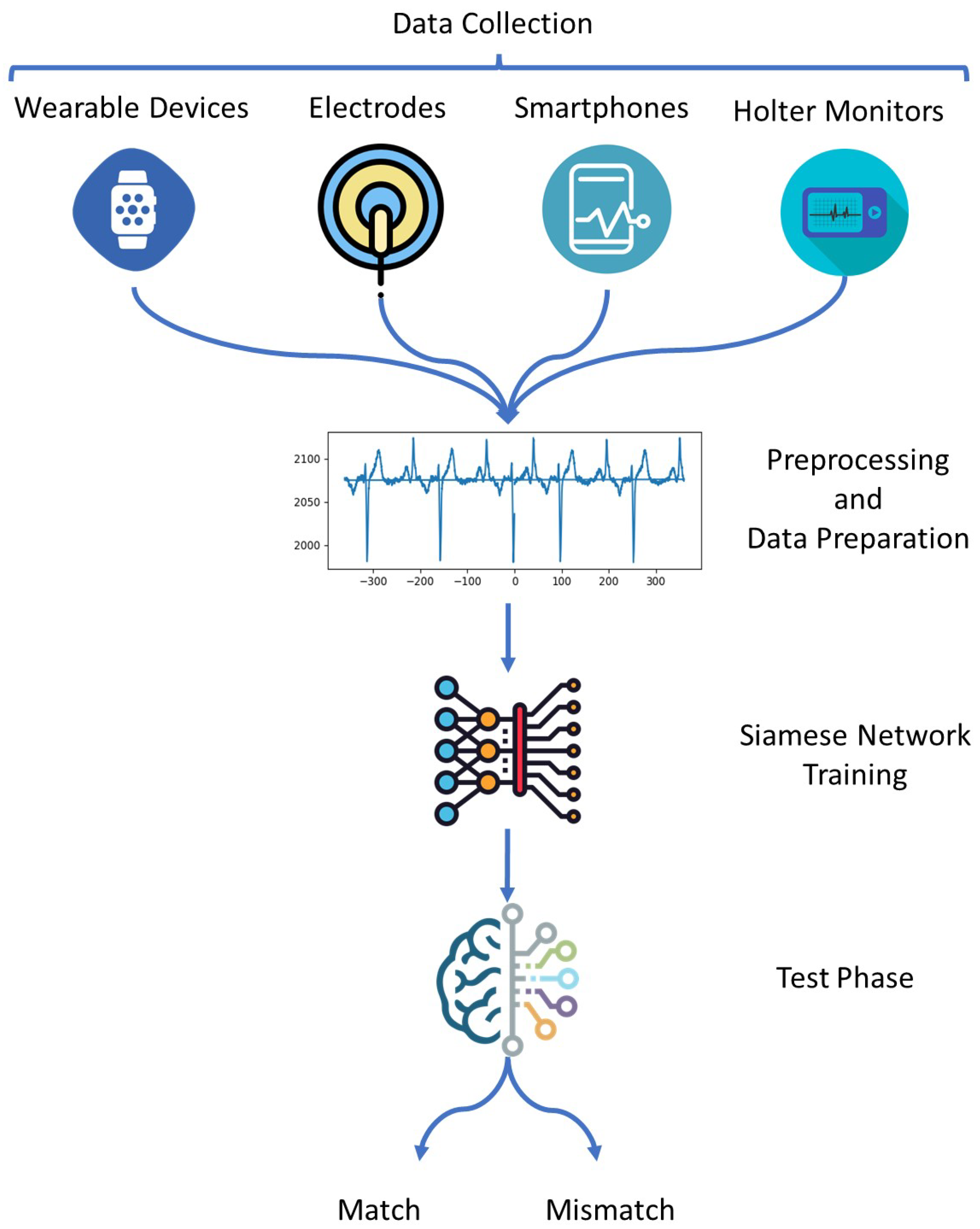
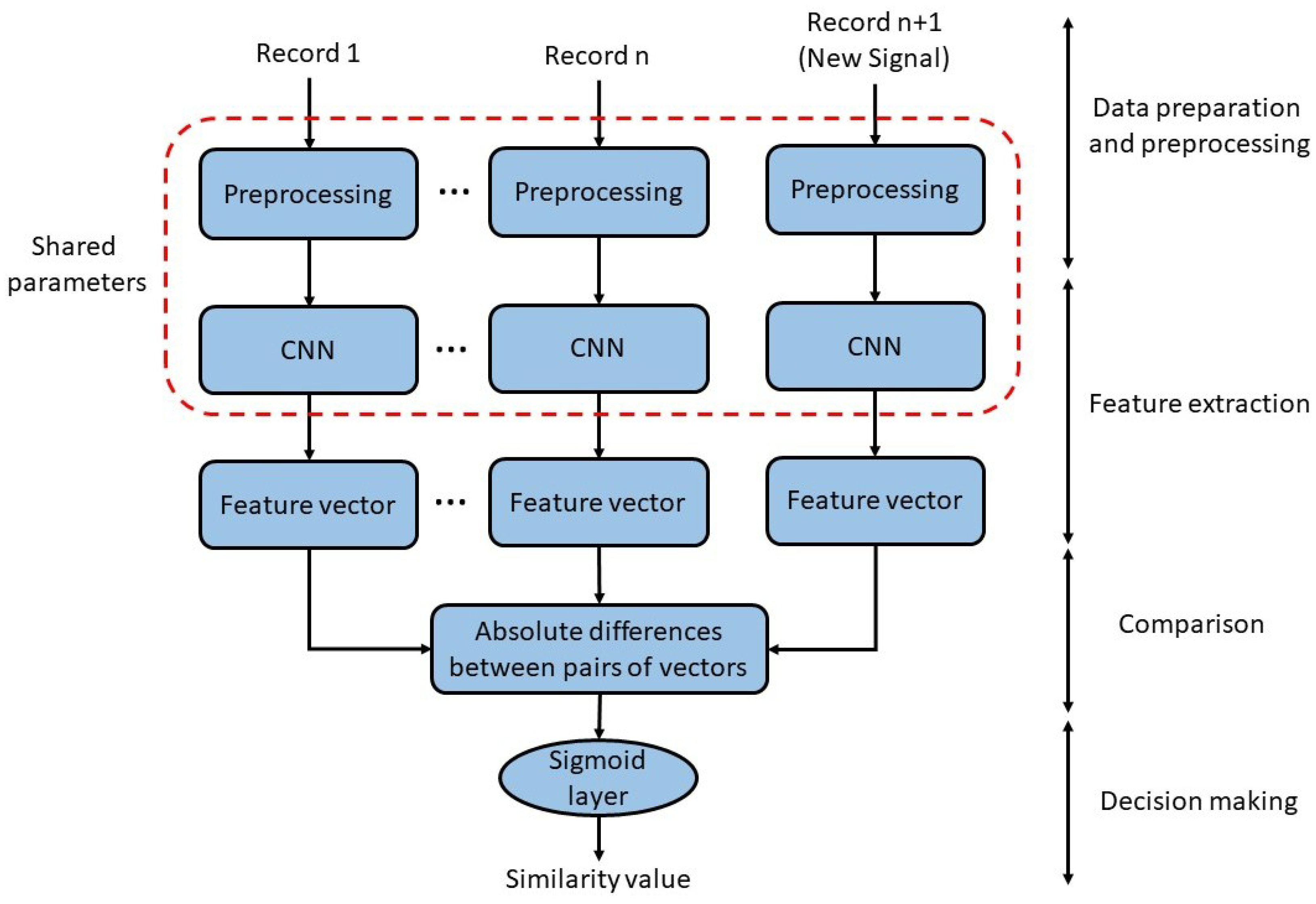
3.3. Training the Siamese Network
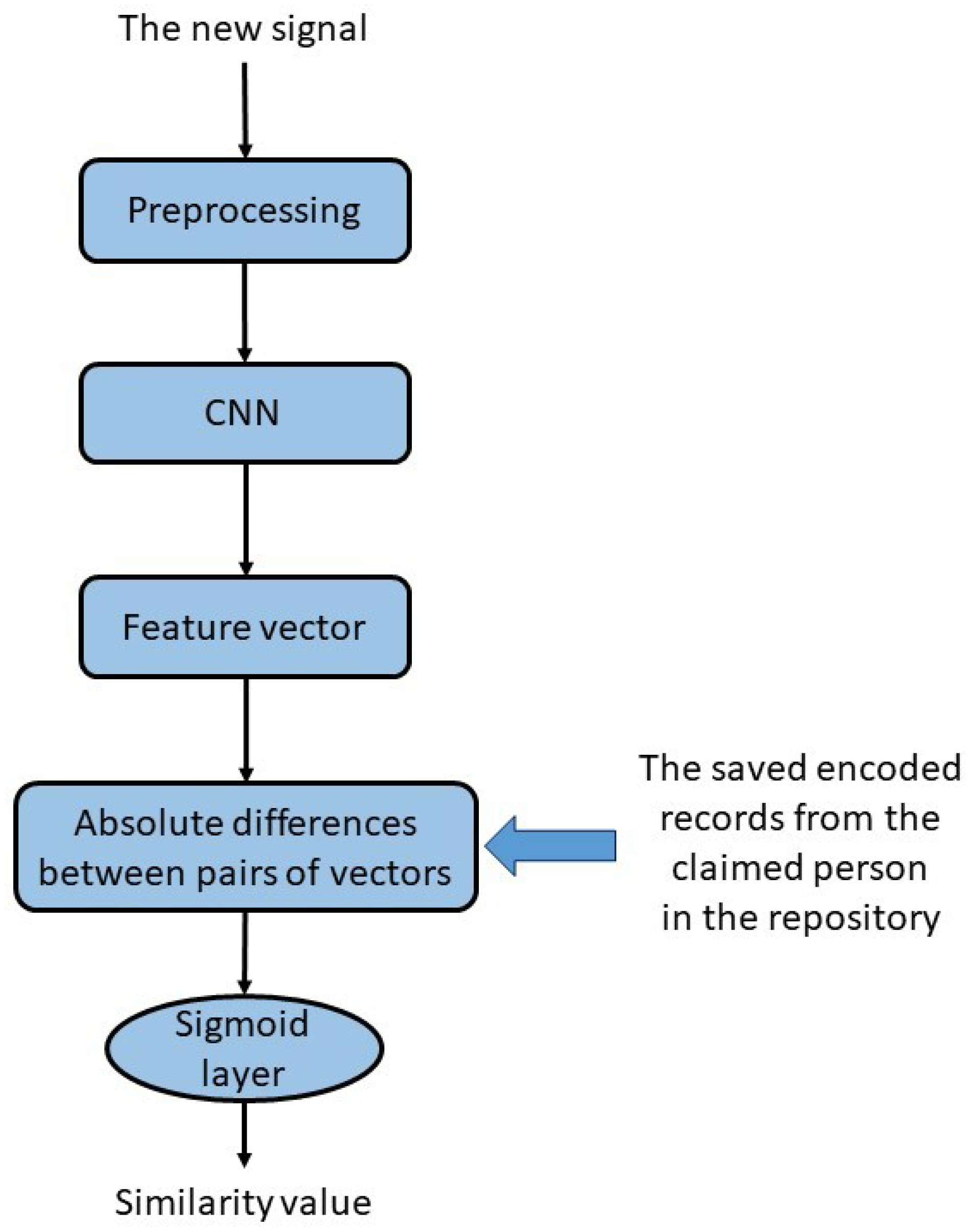
3.4. Test Phase
4. Experimental Results
4.1. Dataset
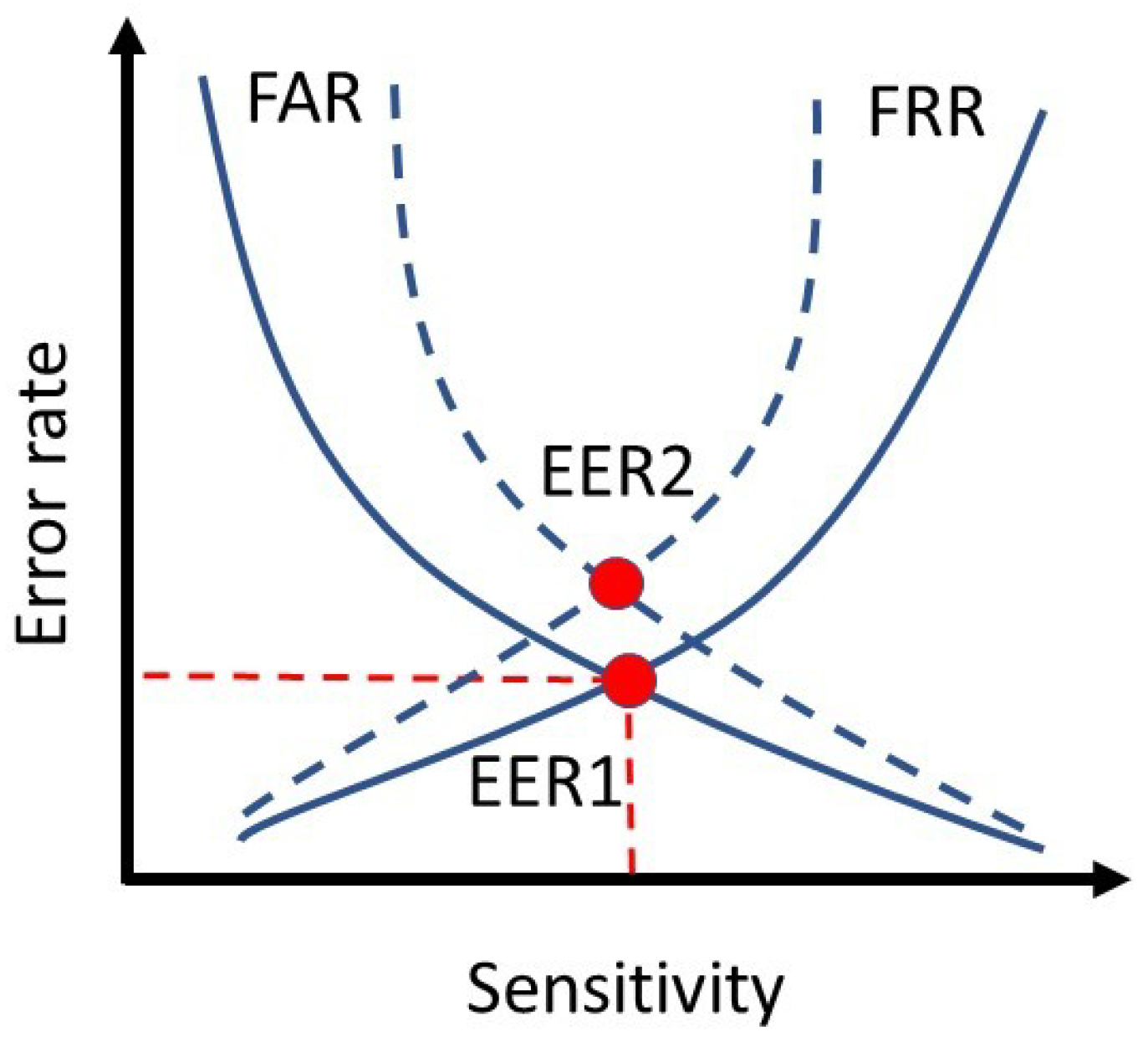
4.2. Evaluation Metrics
4.3. Hyper Parameters and Experimental Results
5. Conclusions and Future Work
- Utilizing ECG signals in a Siamese Network platform that can be trained using a few samples.
- The robustness of the model using a CNN for feature extraction and the capability to handle imbalanced datasets are strengths of our approach.
- Utilizing an ensemble of some samples that can tolerate changes in signal conditions and increase the model robustness.
- Directly registering new users in the system by encoding their data using the trained CNN layers and storing them in a repository. This way, feature extraction on saved records is not required for online applications, which leads to a decrease in the processing time. Furthermore, data vulnerability can be avoided by accessing the unknown entity.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Rowlands, D. What is digital health? And why does it matter. In Health Informatics Society of Australia; White Paper; Australian Institute of Digital Health (AIDH): South Melbourne, Australia, 2019. [Google Scholar]
- Wiig, S.; Aase, K.; Billett, S.; Canfield, C.; Røise, O.; Njå, O.; Guise, V.; Haraldseid-Driftland, C.; Ree, E.; Anderson, J.E.; et al. Defining the boundaries and operational concepts of resilience in the resilience in healthcare research program. BMC Health Serv. Res. 2020, 20, 330. [Google Scholar] [CrossRef]
- Carthey, J.; de Leval, M.; Reason, J. Institutional resilience in healthcare systems. BMJ Qual. Saf. 2001, 10, 29–32. [Google Scholar] [CrossRef] [PubMed]
- Thomas, A.; Suresh, M. Readiness for sustainable-resilience in healthcare organisations during COVID-19 era. Int. J. Organ. Anal. 2022, 31, 91–123. [Google Scholar] [CrossRef]
- Wadhwani, P.; Gankar, S. E-Learning Market Size by Technology (Online E-Learning, Learning Management System (LMS), Mobile E-Learning, Rapid E-Learning, Virtual Classroom), By Provider (Service, Content), By Application (Academic [K-12, Higher Education, Vocational Training], Corporate [SMBs, Large Enterprises], Government), Industry Analysis Report, Regional Outlook, Growth Potential, Competitive Market Share & Forecast. pp. 2020–2026, 2019. Available online: https://www.gminsights.com/industry-analysis/elearning-market-size (accessed on 20 March 2023).
- Ibtehaz, N.; Chowdhury, M.E.; Khandakar, A.; Kiranyaz, S.; Rahman, M.S.; Tahir, A.; Qiblawey, Y.; Rahman, T. EDITH: ECG biometrics aided by Deep learning for reliable Individual Authentication. IEEE Trans. Emerg. Top. Comput. Intell. 2021, 6, 928–940. [Google Scholar] [CrossRef]
- Labati, R.D.; Muñoz, E.; Piuri, V.; Sassi, R.; Scotti, F. Deep-ECG: Convolutional neural networks for ECG biometric recognition. Pattern Recognit. Lett. 2019, 126, 78–85. [Google Scholar] [CrossRef]
- Israel, S.A.; Irvine, J.M.; Cheng, A.; Wiederhold, M.D.; Wiederhold, B.K. ECG to identify individuals. Pattern Recognit. 2005, 38, 133–142. [Google Scholar] [CrossRef]
- Evans, G.F.; Shirk, A.; Muturi, P.; Soliman, E.Z. Feasibility of using mobile ECG recording technology to detect atrial fibrillation in low-resource settings. Glob. Heart 2017, 12, 285–289. [Google Scholar] [CrossRef] [PubMed]
- Kim, H.; Chun, S.Y. Cancelable ECG biometrics using compressive sensing-generalized likelihood ratio test. IEEE Access 2019, 7, 9232–9242. [Google Scholar] [CrossRef]
- Guglielmi, A.V.; Muraro, A.; Cisotto, G.; Laurenti, N. Information theoretic key agreement protocol based on ECG signals. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Kashou, A.H.; May, A.M.; Noseworthy, P.A. Comparison of two artificial intelligence-augmented ECG approaches: Machine learning and deep learning. J. Electrocardiol. 2023, 79, 75–80. [Google Scholar] [CrossRef]
- Prakash, A.J.; Patro, K.K.; Hammad, M.; Tadeusiewicz, R.; Pławiak, P. BAED: A secured biometric authentication system using ECG signal based on deep learning techniques. Biocybern. Biomed. Eng. 2022, 42, 1081–1093. [Google Scholar] [CrossRef]
- Pereira, T.M.; Conceição, R.C.; Sebastião, R. Initial Study Using Electrocardiogram for Authentication and Identification. Sensors 2022, 22, 2202. [Google Scholar] [CrossRef]
- Hazratifard, M.; Gebali, F.; Mamun, M. Using Machine Learning for Dynamic Authentication in Telehealth: A Tutorial. Sensors 2022, 22, 7655. [Google Scholar] [CrossRef]
- Hazrati Fard, S.M.; Hashemi, S. Sparse representation using deep learning to classify multi-class complex data. Iran. J. Sci. Technol. Trans. Electr. Eng. 2019, 43, 637–647. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef] [PubMed]
- Kim, N.; Park, H.; Lee, G.H.; Han, J.; Oh, H.; Choi, J.K. Hierarchical User Status Classification for Imbalanced Biometric Data Class. In Proceedings of the 2022 International Conference on Artificial Intelligence in Information and Communication (ICAIIC), Jeju Island, Republic of Korea, 21–24 February 2022; pp. 246–250. [Google Scholar]
- Dong, X.; Shen, J. Triplet loss in siamese network for object tracking. In Proceedings of the European conference on computer vision (ECCV), Munich, Germany, 8–14 September 2018; pp. 459–474. [Google Scholar]
- Zhong, D.; Yang, Y.; Du, X. Palmprint recognition using the Siamese network. In Proceedings of the Chinese Conference on Biometric Recognition, Urumqi, China, 11–12 August 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 48–55. [Google Scholar]
- Kokol, P.; Kokol, M.; Zagoranski, S. Machine learning on small size samples: A synthetic knowledge synthesis. Sci. Prog. 2022, 105, 00368504211029777. [Google Scholar] [CrossRef] [PubMed]
- Hamad, R.A.; Kimura, M.; Lundström, J. Efficacy of imbalanced data handling methods on deep learning for smart homes environments. SN Comput. Sci. 2020, 1, 204. [Google Scholar] [CrossRef]
- Behrouzi, P.; Shirkani, B.; Hazratifard, M. Using ECG Signals in Siamese Networks for Authentication in Digital Healthcare Systems. J. ISSN 2022, 3, 1367–1373. [Google Scholar] [CrossRef]
- Amritha, V.S.; Aravinth, J. Matcher performance-based score level fusion schemes for multi-modal biometric authentication system. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 March 2020; pp. 79–85. [Google Scholar]
- Srivastva, R.; Singh, A.; Singh, Y.N. PlexNet: A fast and robust ECG biometric system for human recognition. Inf. Sci. 2021, 558, 208–228. [Google Scholar] [CrossRef]
- Melzi, P.; Tolosana, R.; Vera-Rodriguez, R. Ecg biometric recognition: Review, system proposal, and benchmark evaluation. IEEE Access 2023, 11, 15555–15566. [Google Scholar] [CrossRef]
- Diab, M.O.; Seif, A.; Sabbah, M.; El-Abed, M.; Aloulou, N. A review on ECG-based biometric authentication systems. Hidden Biom. 2020, 17–44. [Google Scholar] [CrossRef]
- Pereira Coutinho, D.; Silva, H.; Gamboa, H.; Fred, A.; Figueiredo, M. Novel fiducial and non-fiducial approaches to electrocardiogram-based biometric systems. IET Biom. 2013, 2, 64–75. [Google Scholar] [CrossRef]
- Kumar, A.K.; Ritam, M.; Han, L.; Guo, S.; Chandra, R. Deep learning for predicting respiratory rate from biosignals. Comput. Biol. Med. 2022, 144, 105338. [Google Scholar] [CrossRef]
- Hammad, M.; Zhang, S.; Wang, K. A novel two-dimensional ECG feature extraction and classification algorithm based on convolution neural network for human authentication. Future Gener. Comput. Syst. 2019, 101, 180–196. [Google Scholar] [CrossRef]
- Bhaskar, S.; Thasleema, T. LSTM model for visual speech recognition through facial expressions. Multimed. Tools Appl. 2023, 82, 5455–5472. [Google Scholar] [CrossRef]
- Singh, A.; Dargar, S.K.; Gupta, A.; Kumar, A.; Srivastava, A.K.; Srivastava, M.; Kumar Tiwari, P.; Ullah, M.A. Evolving long short-term memory network-based text classification. Comput. Intell. Neurosci. 2022, 2022, 4725639. [Google Scholar] [CrossRef]
- Kim, B.H.; Pyun, J.Y. ECG identification for personal authentication using LSTM-based deep recurrent neural networks. Sensors 2020, 20, 3069. [Google Scholar] [CrossRef]
- Zhu, F.; Ye, F.; Fu, Y.; Liu, Q.; Shen, B. Electrocardiogram generation with a bidirectional LSTM-CNN generative adversarial network. Sci. Rep. 2019, 9, 6734. [Google Scholar] [CrossRef]
- Tirado-Martin, P.; Sanchez-Reillo, R. BioECG: Improving ECG Biometrics with Deep Learning and Enhanced Datasets. Appl. Sci. 2021, 11, 5880. [Google Scholar] [CrossRef]
- Fard, S.M.H.; Hashemi, S. Employing deep learning and sparse representation for data classification. In Proceedings of the 2017 Artificial Intelligence and Signal Processing Conference (AISP), Shiraz, Iran, 25–27 October 2017; pp. 289–293. [Google Scholar]
- Centeno, M.P.; van Moorsel, A.; Castruccio, S. Smartphone continuous authentication using deep learning autoencoders. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 147–1478. [Google Scholar]
- Ivanciu, L.; Ivanciu, I.A.; Farago, P.; Roman, M.; Hintea, S. An ECG-based authentication system using Siamese neural networks. J. Med. Biol. Eng. 2021, 41, 558–570. [Google Scholar] [CrossRef]
- Rabcan, J.; Levashenko, V.; Zaitseva, E.; Kvassay, M. Review of methods for EEG signal classification and development of new fuzzy classification-based approach. IEEE Access 2020, 8, 189720–189734. [Google Scholar] [CrossRef]
- Prasad, B.P.; Parthasarathy, V. Detection and classification of cardiovascular abnormalities using FFT based multi-objective genetic algorithm. Biotechnol. Biotechnol. Equip. 2018, 32, 183–193. [Google Scholar] [CrossRef]
- Venkat N, G.; Vijay, V.R.; Venu, G.; Rao, C. Cognitive Computing: Theory and Applications; Elsevier: Amsterdam, The Netherlands, 2020. [Google Scholar]
| Database | # of Records | # of Subjects | Resolution | The Nominal Range |
|---|---|---|---|---|
| ECG-ID | 310 | 90 (44 men and 46 women) | 12-bit | ±10 mV |
| PTB | 549 | 290 (209 men and 81 women) | 16-bit | ±16.384 mV |
| Method | Accuracy (%) | FAR (%) | FRR (%) | EER (%) |
|---|---|---|---|---|
| The proposed model (ESN) | 93.6 | 1.69 | 1.84 | 1.76 |
| Behrouzi et al. [23] | 92.1 | 1.91 | 1.99 | 1.94 |
| Ibtehaz et al. [6] | 88.3 | 2.36 | 2.20 | 2.29 |
| Ivanciu et al. [38] | 86.4 | 2.77 | 3.06 | 2.95 |
| CNN-LSTM | 86.8 | 2.16 | 2.11 | 2.13 |
| LSTM | 91.4 | 2.04 | 2.12 | 2.09 |
| Bi-LSTM | 89.1 | 2.04 | 2.17 | 2.07 |
| Method | Accuracy (%) | FAR (%) | FRR (%) | EER (%) |
|---|---|---|---|---|
| The proposed model (ESN) | 96.8 | 1.73 | 1.66 | 1.69 |
| Behrouzi et al. [23] | 95.3 | 1.89 | 2.01 | 1.94 |
| Ibtehaz et al. [6] | 90.4 | 1.99 | 1.93 | 1.97 |
| Ivanciu et al. [38] | 92.3 | 2.20 | 2.39 | 2.27 |
| CNN-LSTM | 91.7 | 2.11 | 2.01 | 2.06 |
| LSTM | 92.3 | 2.03 | 1.87 | 1.92 |
| Bi-LSTM | 90.9 | 1.86 | 2.05 | 1.98 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hazratifard, M.; Agrawal, V.; Gebali, F.; Elmiligi, H.; Mamun, M. Ensemble Siamese Network (ESN) Using ECG Signals for Human Authentication in Smart Healthcare System. Sensors 2023, 23, 4727. https://doi.org/10.3390/s23104727
Hazratifard M, Agrawal V, Gebali F, Elmiligi H, Mamun M. Ensemble Siamese Network (ESN) Using ECG Signals for Human Authentication in Smart Healthcare System. Sensors. 2023; 23(10):4727. https://doi.org/10.3390/s23104727
Chicago/Turabian StyleHazratifard, Mehdi, Vibhav Agrawal, Fayez Gebali, Haytham Elmiligi, and Mohammad Mamun. 2023. "Ensemble Siamese Network (ESN) Using ECG Signals for Human Authentication in Smart Healthcare System" Sensors 23, no. 10: 4727. https://doi.org/10.3390/s23104727
APA StyleHazratifard, M., Agrawal, V., Gebali, F., Elmiligi, H., & Mamun, M. (2023). Ensemble Siamese Network (ESN) Using ECG Signals for Human Authentication in Smart Healthcare System. Sensors, 23(10), 4727. https://doi.org/10.3390/s23104727







