Blockchain-Based Security Mechanisms for IoMT Edge Networks in IoMT-Based Healthcare Monitoring Systems
Abstract
:1. Introduction
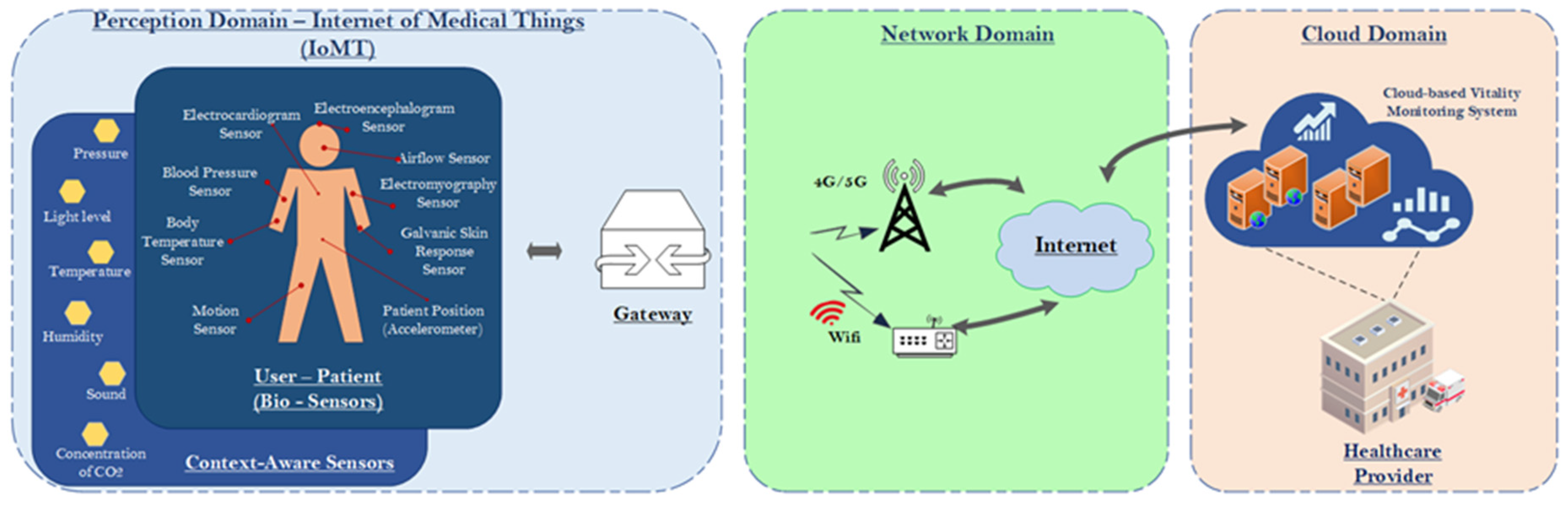
2. IoMT-Based Healthcare Monitoring Systems
3. Blockchain Fundamentals: Consensus and Platforms
3.1. Consensus Mechanisms
3.1.1. Proof of Work
- Proof of Capacity (PoC): in which instead of dependence on computation power, the mining process relies on hard disk capacity [19].
- Proof of Elapsed Time (PoET): is a consensus protocol proposed by Intel. The difference of this protocol with PoW is that the winning miner is selected randomly based on a random waiting time [19].
- Proof of Contribution: is a modification of PoW proposed in [20] by T. Xue et al. in order to increase the efficiency of miners.
- Kumar et al. at [21] proposed a variant of PoW based on statistical likelihood maximization and polynomial matrix factorization. This algorithm presents a significant reduction of memory and energy consumption from the devices as well as reduced convergence time. The authors propose this algorithm as a PoW algorithm suitable for resource constraint devices such as IoT nodes.
3.1.2. Proof of Stake
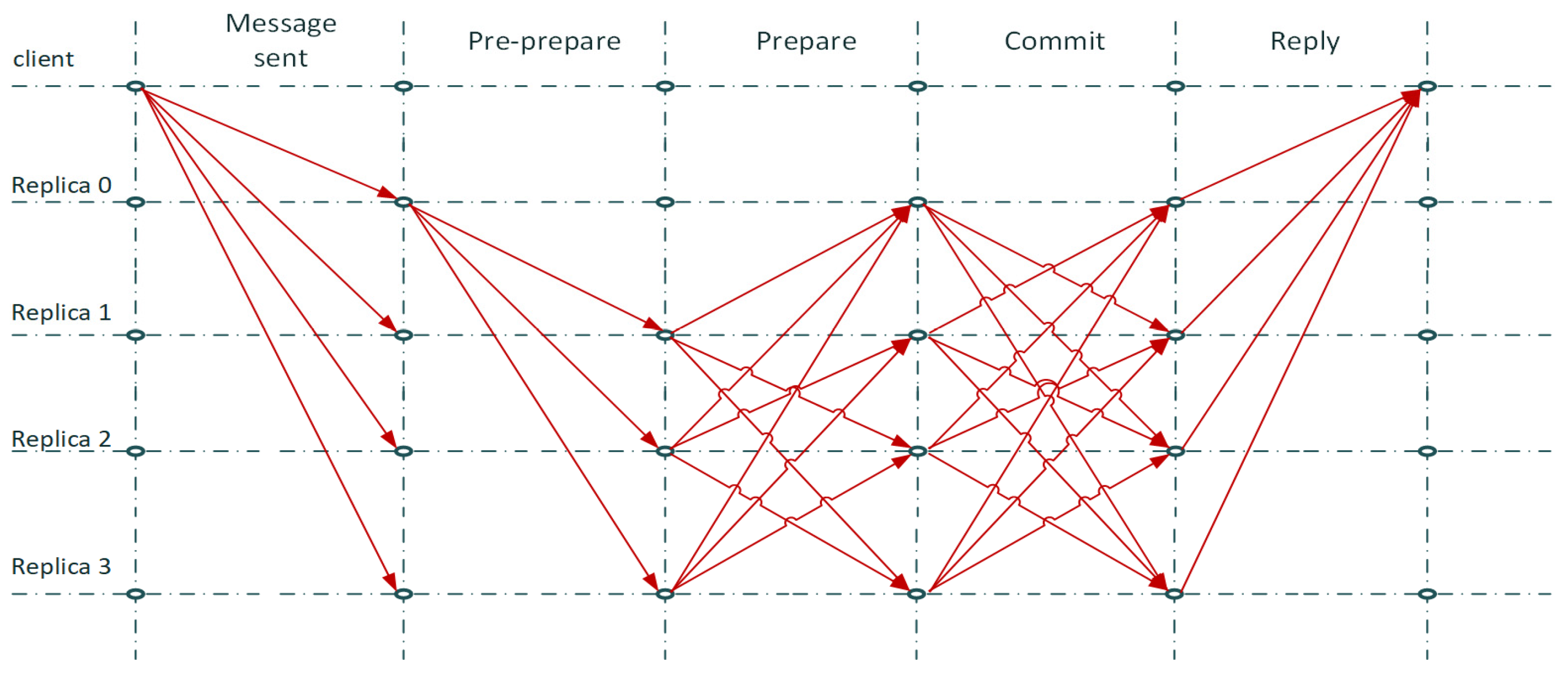
3.1.3. Byzantine Fault Tolerance
- Delegated Byzantine Fault Tolerance (dBFT): this is practically the same as PBFT, but in this case not all the nodes are necessary to participate in order to achieve consensus [19].
- Stellar: it is used for micro finance services and uses federated Byzantine Fault Tolerance (FBFT) [25].
- Ripple: similar to Stellar [26].
- Tendermint: it is a BFT consensus protocol in which the nodes have different voting power in relation to their stakes [27].
3.2. Blockchain Platforms
4. Blockchain-Based Security for IoMT Edge Networks
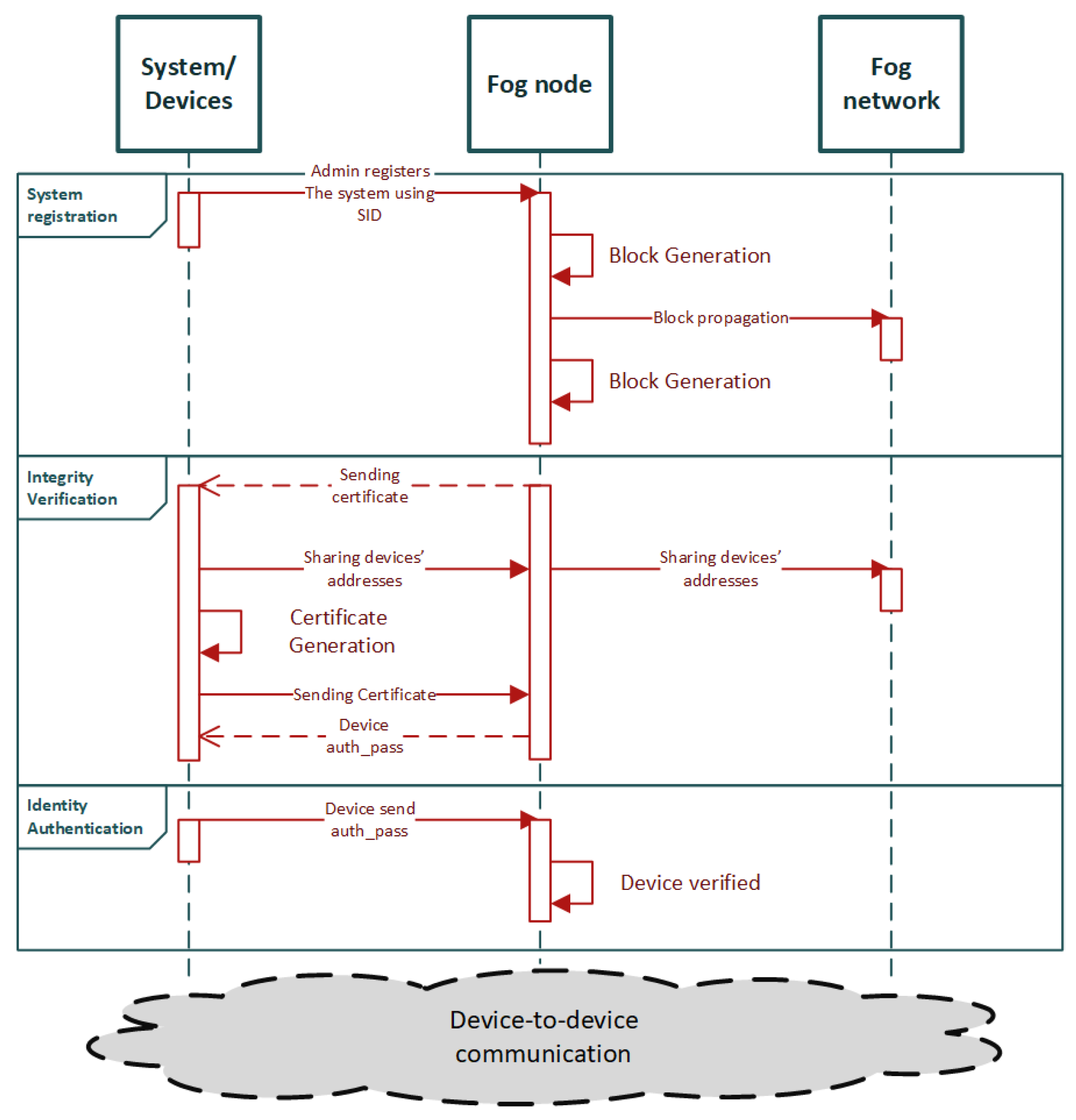
4.1. Blockchain-Based Authentication for IoMT Edge Networks
4.1.1. Existing Blockchain-Based Authentication Mechanisms for IoMT Edge Networks
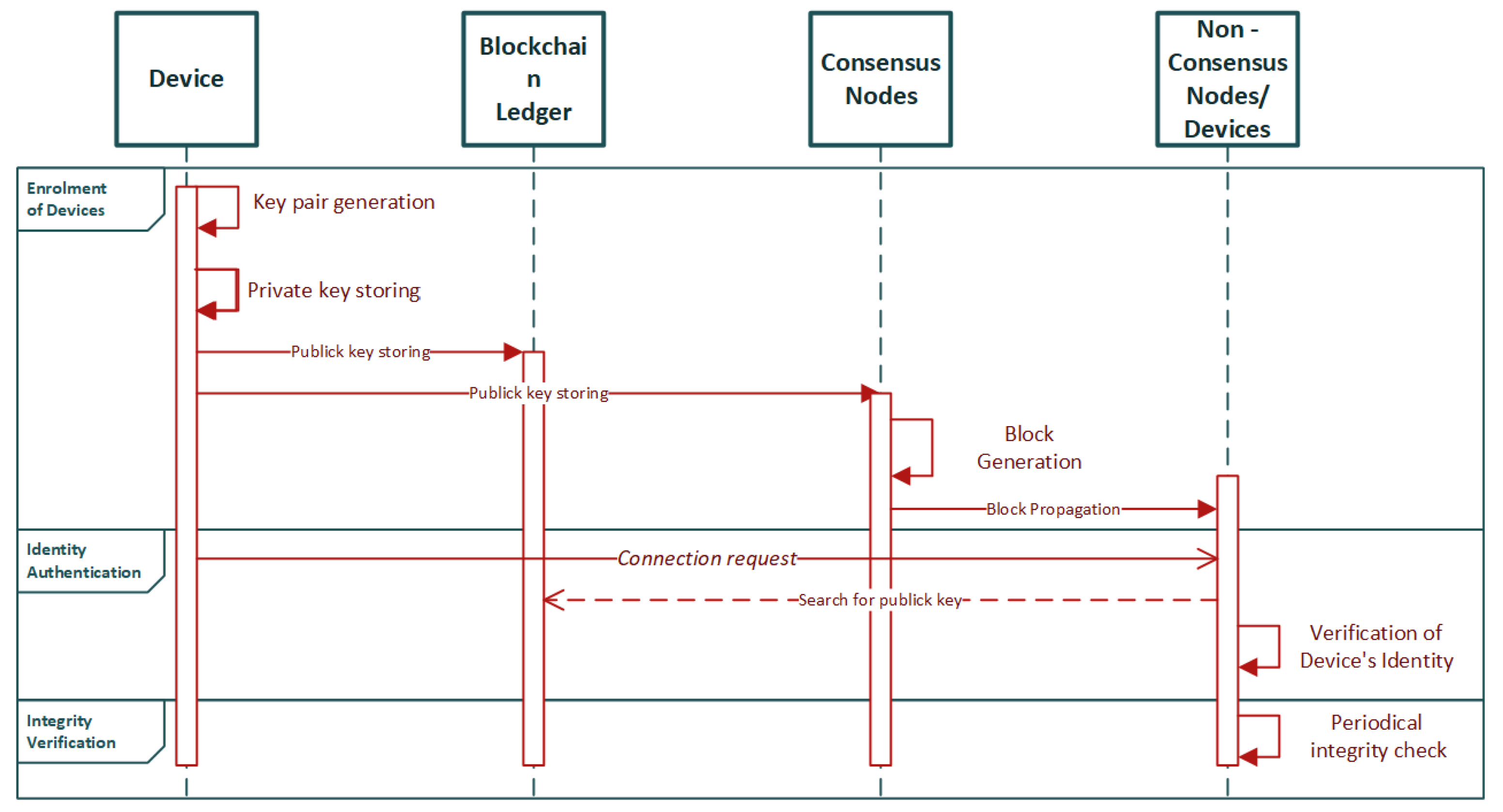
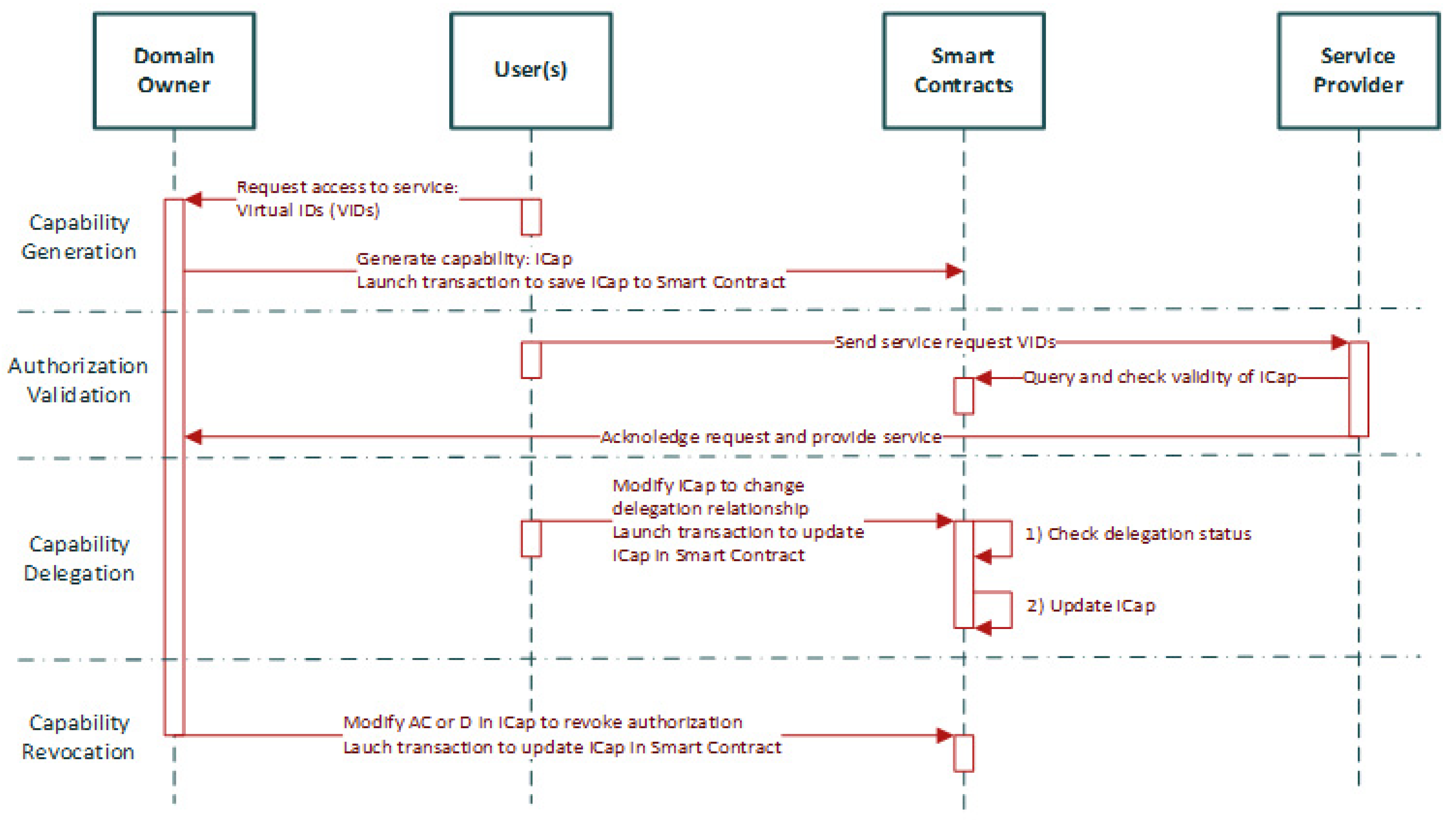
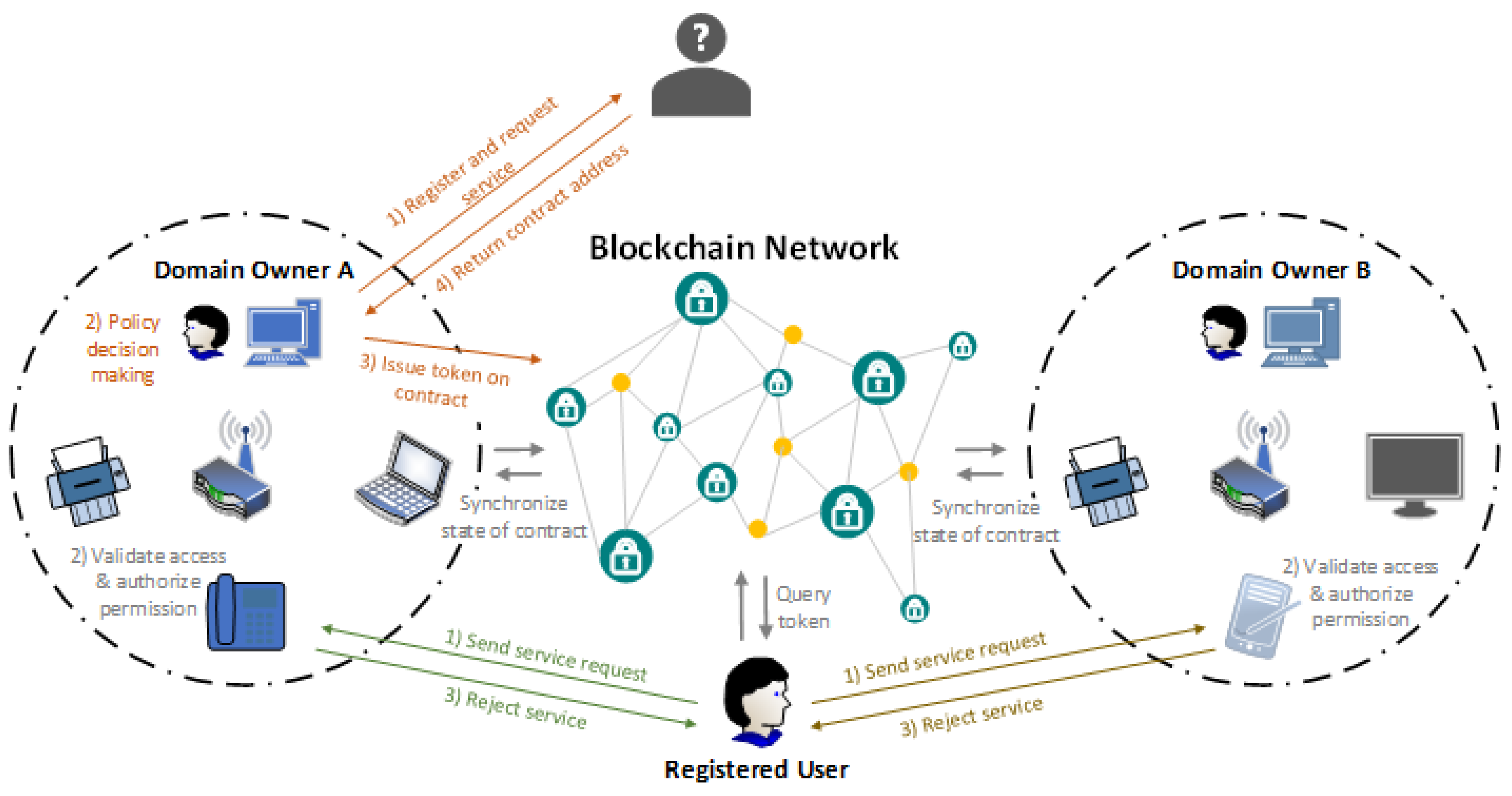
4.1.2. Potential Blockchain-Based Authentication Mechanisms for IoMT Edge Networks
- a user that owns a group of IoT/smart devices functioning as a user node
- a blockchain network with consensus nodes, and
- a smart home network that consists of: (i) a group of smart devices, and (ii) a gateway that connects the smart house to the blockchain network.
- each IoT node has a unique Ethernet address
- cluster head nodes and base stations have certain storage and computing capabilities, and smart contract can be deployed
- as a node manager in a single network, base station is trusted by the nodes in the network; and
- the process of initialization of the nodes is secure.
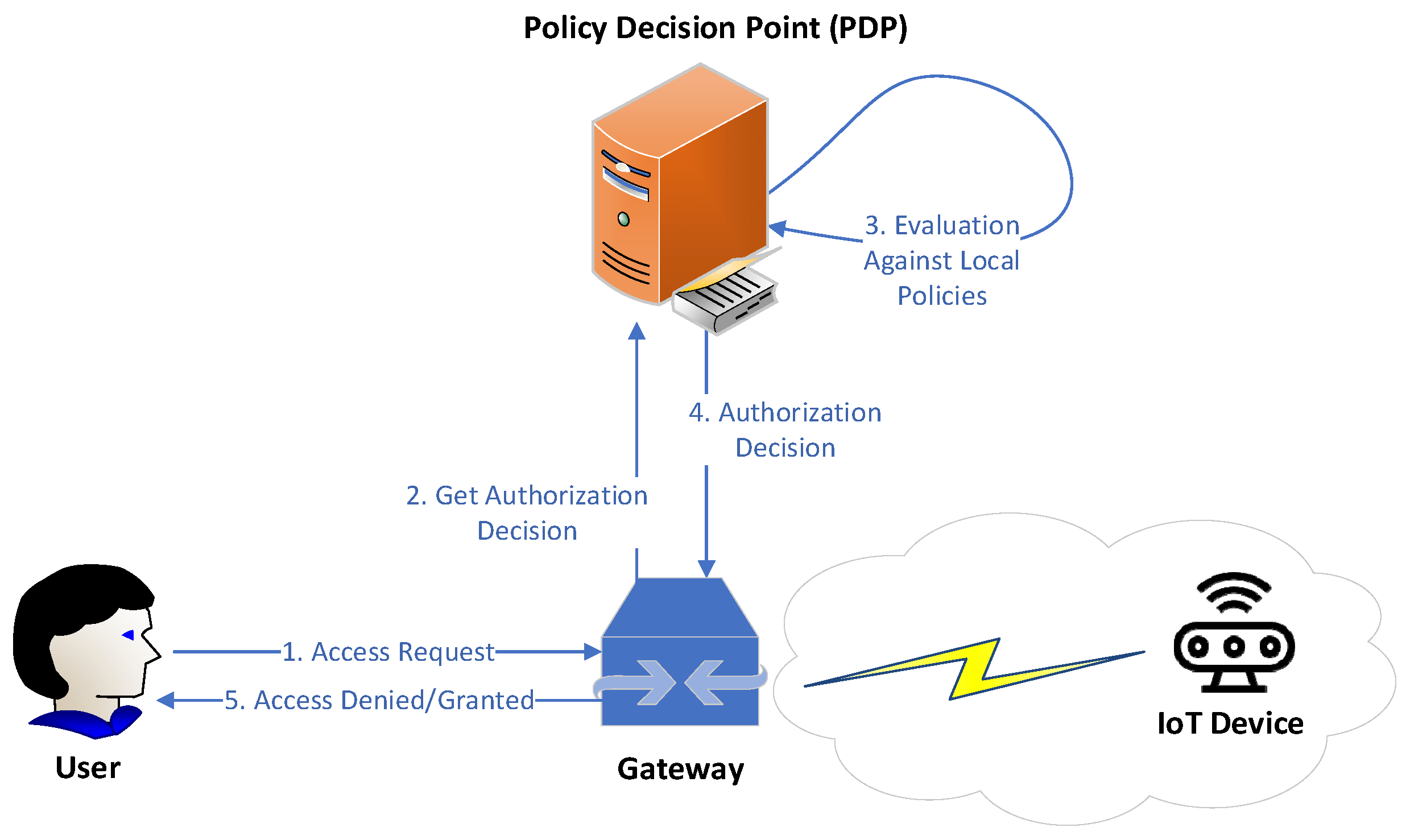
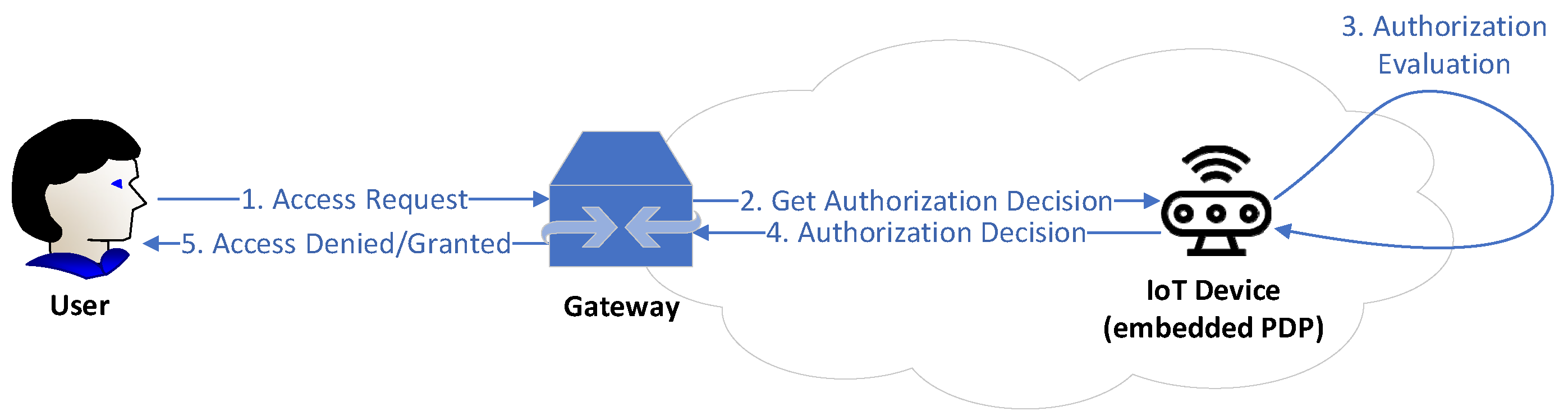
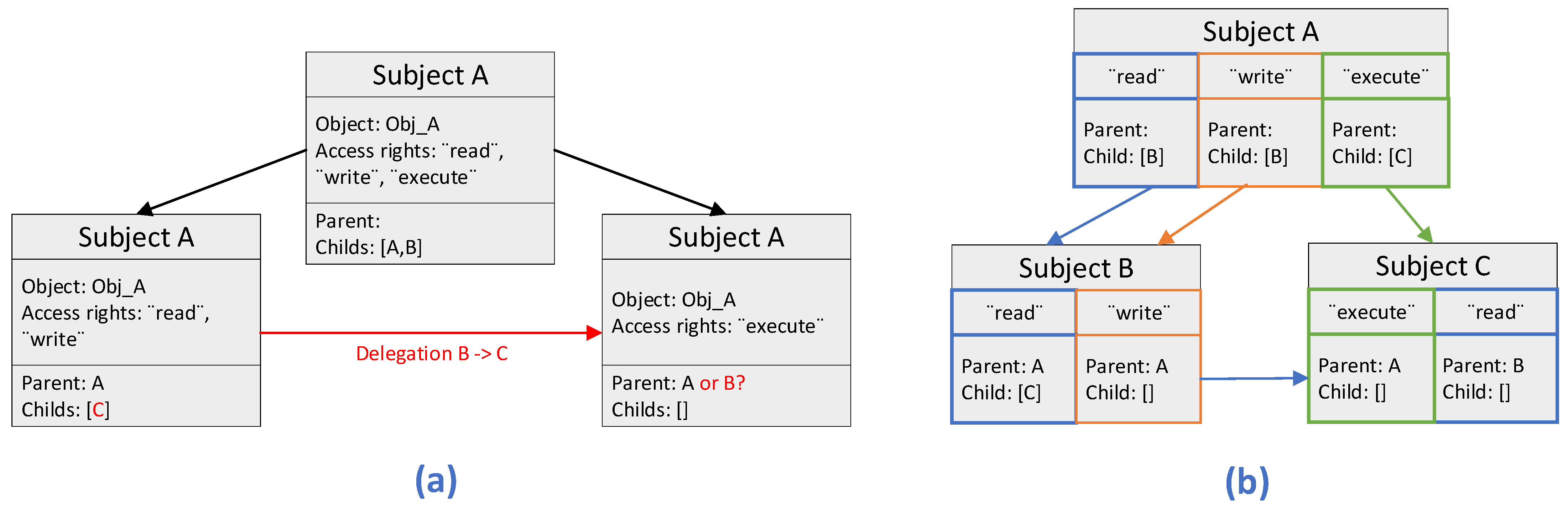
4.2. Blockchain-Based Authorization for IoMT Edge Networks
- a Policy Management Contract (PMC) that is responsible for managing the ABAC policies
- a Subject Attribute Management Contract (SAMC) that is responsible for managing the attributes of subjects (i.e., entities gaining access to resources/objects)
- an Object Attribute Management Contract (OAMC) that is responsible for managing the attributes of objects (i.e., resources being accessed), and
- an Access Control Contract (ACC) that is responsible for performing the access control.
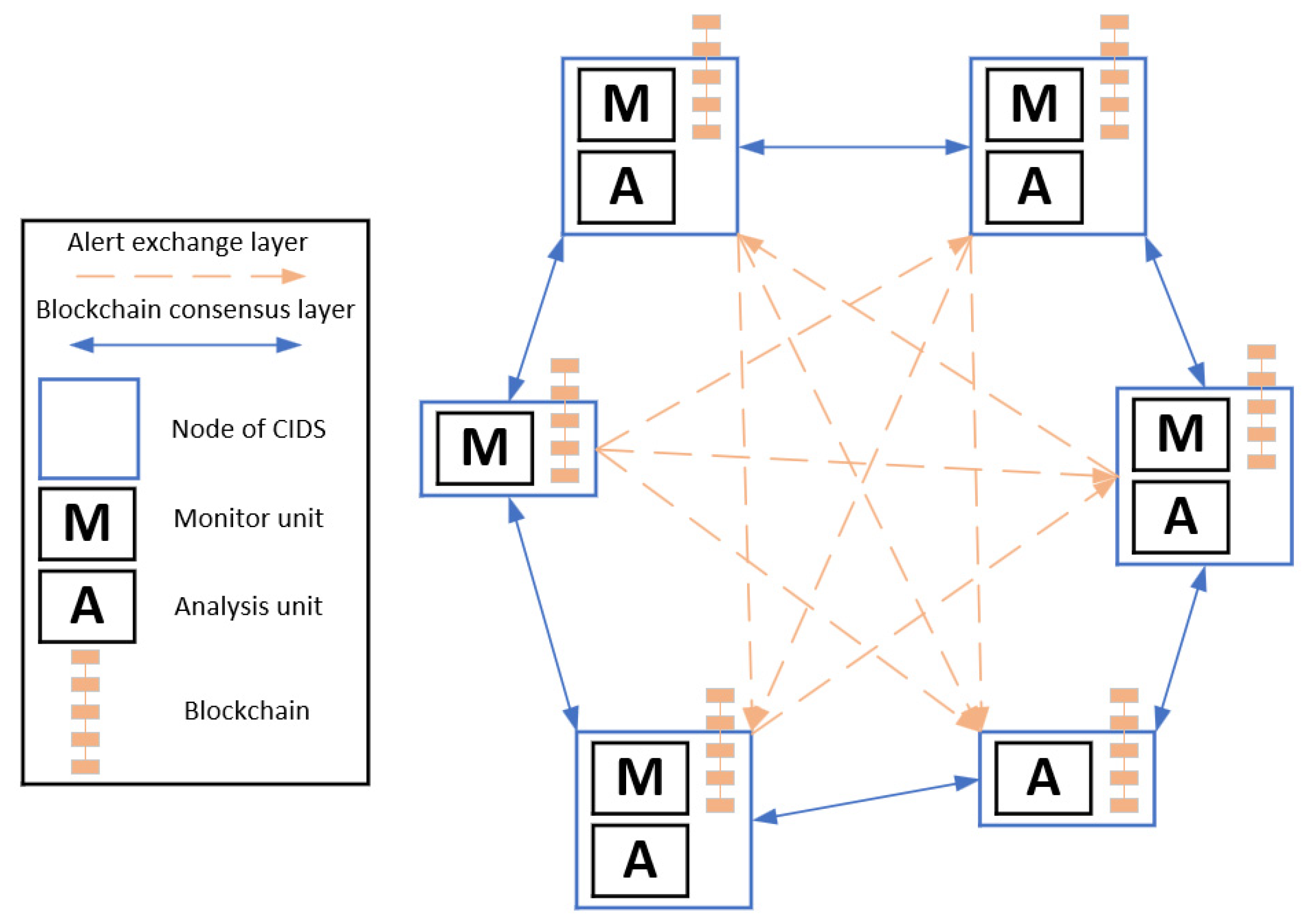
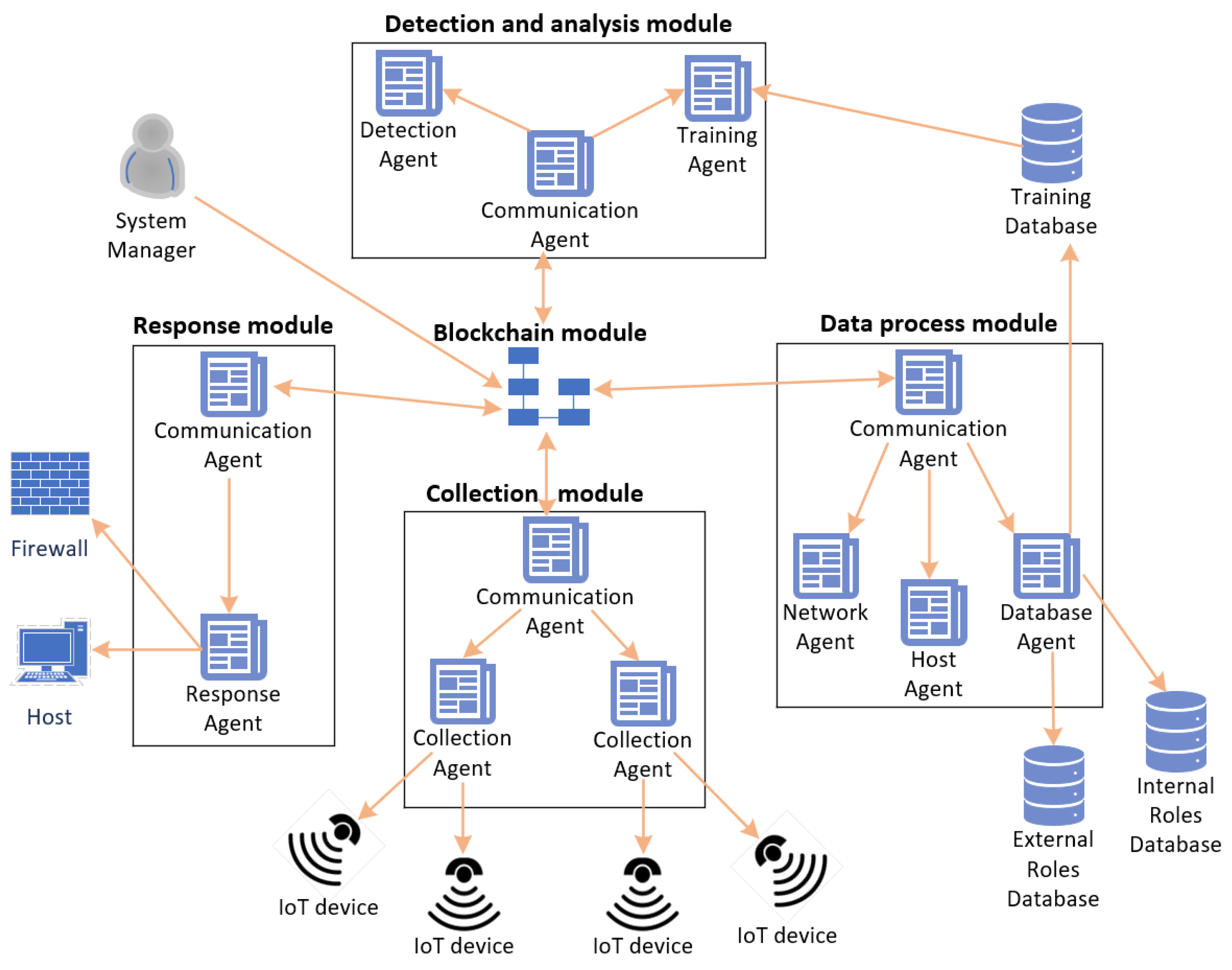
4.3. Blockchain-Based Intrusion Detection Systems (IDS) for IoMT Edge Networks
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Oikonomou, F.P.; Pelekoudas; Ribeiro, J.; Mantas, G.; Bastos, J.M.C.S.; Rodriguez, J. A Hyperledger Fabric-based Blockchain Architecture to Secure IoT-based Health Monitoring Systems. In Proceedings of the 2021 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Athens, Greece, 7–10 September 2021. [Google Scholar]
- Oikonomou, F.P.; Mantas, G.; Cox, P.; Bashashi, F.; Gil-Castineira, F.; Gonzalez, J. A Blockchain-based Architecture for Secure IoT-based Health Monitoring Systems. In Proceedings of the IEEE 26th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Porto, Portugal, 25–27 October 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Papaioannou, M.; Karageorgou, M.; Mantas, G.; Sucasas, V.; Essop, I.; Rodriguez, J.; Lymberopoulos, D. A Survey on Security Threats and Countermeasures in Internet of Medical Things (IoMT). Trans. Emerg. Telecommun. Technol. 2020, 23, e4049. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. BSN-Care: A Secure IoT-Based Modern Healthcare System Using Body Sensor Network. IEEE Sensors J. 2015, 16, 1368–1376. [Google Scholar] [CrossRef]
- Khezr, S.; Moniruzzaman, M.; Yassine, A.; Benlamri, R. Blockchain Technology in Healthcare: A Comprehensive Review and Directions for Future Research. Appl. Sci. 2019, 9, 1736. [Google Scholar] [CrossRef] [Green Version]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of Threats to the Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1636–1675. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Seliem, M.; Elgazzar, K. BIoMT: Blockchain for the internet of medical things. In Proceedings of the 2019 IEEE International Black Sea Conference on Communications and Networking, BlackSeaCom, Sochi, Russia, 3–6 June 2019. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Catarinucci, L.; De Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-Aware Architecture for Smart Healthcare Systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Alkurdi, F.; Elgendi, I.; Munasinghe, K.S.; Sharma, D.; Jamalipour, A. Blockchain in IoT Security: A Survey. In Proceedings of the 28th International Telecommunication Networks and Application Conference (ITNAC 2018), Sydney, NWS, Australia, 21–23 November 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and Iot Integration: A Systematic Survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef] [Green Version]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Y.2060: Overview of the Internet of Things, Telecommunication Standardization Sector of ITU ITU-T Recommendation Database. Available online: https://www.itu.int/rec/T-REC-Y.2060-201206-I (accessed on 30 January 2022).
- Liyanage, M.; Braeken, A.; Kumar, P.; Ylianttila, M. IoT Security: Advances in Authentication; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2019; ISBN 1119527929. [Google Scholar]
- Vukolić, M. The Quest for Scalable Blockchain Fabric: Proof-of-Work vs. BFT Replication. In Lecture Notes in Computer Science; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2016; pp. 112–125. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Business Review. 2008. Available online: https://www.debr.io/article/21260.pdf (accessed on 30 January 2022).
- Salimitari, M.; Chatterjee, M. A Survey on Consensus Protocols in Blockchain for IoT Networks. arXiv 2018, arXiv:1809.05613. [Google Scholar]
- Xue, T.; Yuan, Y.; Ahmed, Z.; Moniz, K.; Cao, G.; Wang, C. Proof of Contribution: A Modification of Proof of Work to Increase Mining Efficiency. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018. [Google Scholar] [CrossRef]
- Kumar, G.; Saha, R.; Rai, M.K.; Thomas, R.; Kim, T.-H. Proof-of-Work Consensus Approach in Blockchain Technology for Cloud and Fog Computing Using Maximization-Factorization Statistics. IEEE Internet Things J. 2019, 6, 6835–6842. [Google Scholar] [CrossRef]
- De Angelis, S.; Aniello, L.; Baldoni, R.; Lombardi, F.; Margheri, A.; Sassone, V. PBFT vs proof-of-authority: Applying the CAP theorem to permissioned blockchain. In Proceedings of the Italian Conference on Cybersecurity, Milan, Italy, 6–9 February 2018. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance and proactive recovery. ACM Trans. Comput. Syst. 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Meshcheryakov, Y.; Melman, A.; Evsutin, O.; Morozov, V.; Koucheryavy, Y. On Performance of PBFT Blockchain Consensus Algorithm for IoT-Applications with Constrained Devices. IEEE Access 2021, 9, 80559–80570. [Google Scholar] [CrossRef]
- Open Source Blockchain for Currencies & Payments-Stellar. Available online: https://www.stellar.org/learn/intro-to-stellar (accessed on 31 January 2022).
- Schwartz, D.; Youngs, N.; Britto, A. The Ripple Protocol Consensus Algorithm. Ripple Labs Inc White Pap. 2014, 5, 151. [Google Scholar]
- Tendermint Core Documentation|Tendermint Core. Available online: https://docs.tendermint.com/master (accessed on 31 January 2022).
- Ethereum.org. Available online: https://ethereum.org/en (accessed on 21 January 2022).
- Solidity Programming Language|The Solidity Language Portal is a Comprehensive Information Page for the Solidity Programming Language. It Features Documentation, Binaries, Blog, Resources & More. Available online: https://soliditylang.org/ (accessed on 31 January 2022).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Muralidharan, S.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Murthy, C.; Ferris, C.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the EuroSys’ 18: Thirteenth EuroSys Conference 2018, Porto, Portugal, 23–26 April 2018. [Google Scholar] [CrossRef] [Green Version]
- HyperLedger. Available online: https://www.hyperledger.org/use/fabric (accessed on 24 January 2021).
- Hyperledger Sawtooth|Hyperledger Sawtooth. Available online: https://sawtooth.hyperledger.org (accessed on 24 January 2022).
- Bitcoin-Open Source P2P Money. Available online: https://bitcoin.org/en (accessed on 24 January 2022).
- Corda|Leading DLT Platform for Regulated Industries. Available online: https://www.corda.net (accessed on 25 January 2022).
- Home|IOTA. Available online: https://www.iota.org/ (accessed on 25 January 2022).
- Akkaoui, R. Blockchain for the Management of Internet of Things Devices in the Medical Industry. IEEE Trans. Eng. Manag. 2021, 1–12. [Google Scholar] [CrossRef]
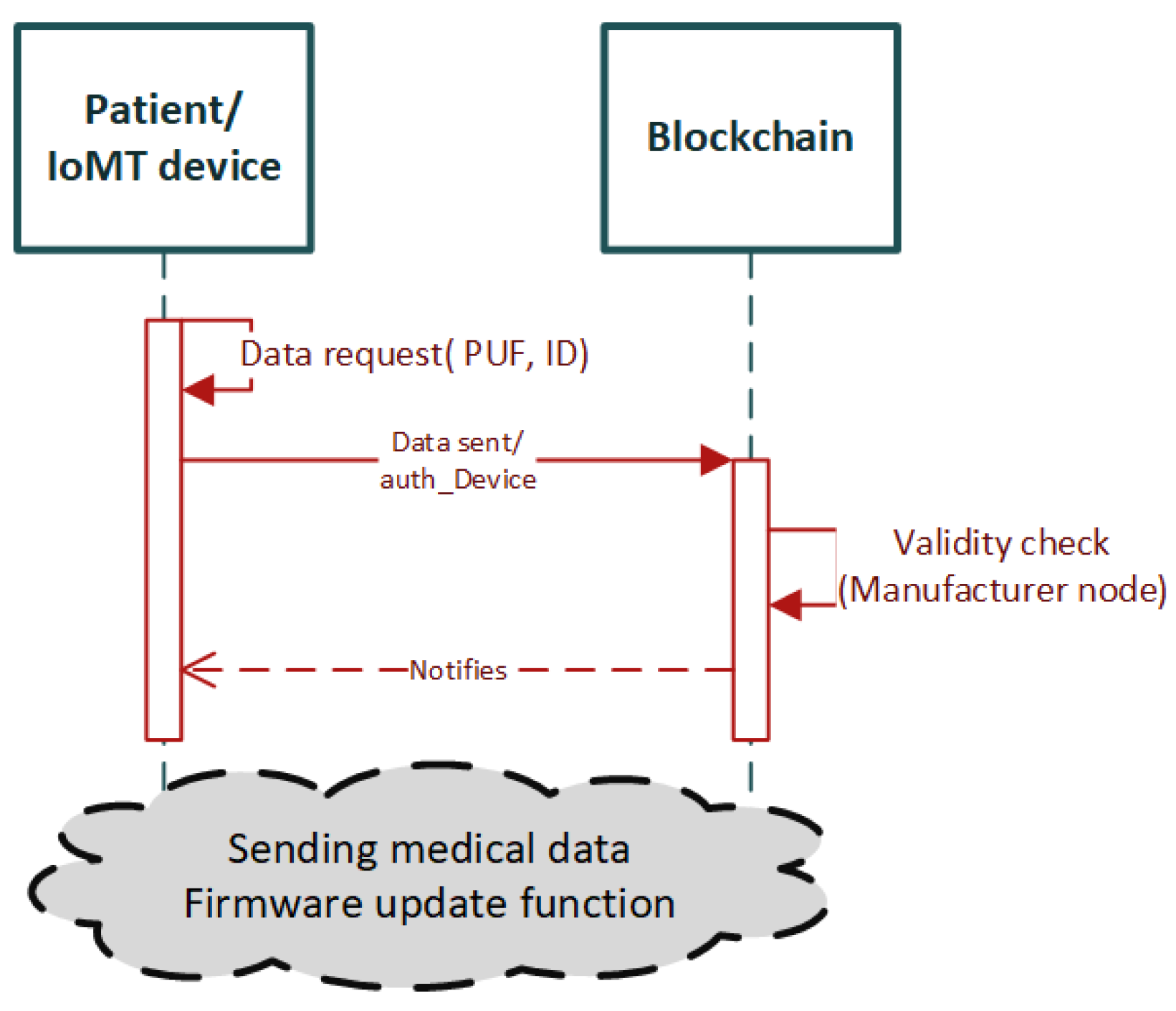
- Fotopoulos, F.; Malamas, V.; Dasaklis, T.K.; Kotzanikolaou, P.; Douligeris, C. A Blockchain-enabled Architecture for IoMT Device Authentication. In Proceedings of the 2020 IEEE Eurasia Conference on IOT, Communication and Engineering (ECICE), Yunlin, Taiwan, 23–25 October 2020. [Google Scholar] [CrossRef]
- Li, D.; Peng, W.; Deng, W.; Gai, F. A Blockchain-Based Authentication and Security Mechanism for IoT. In Proceedings of the 27th International Conference on Computer Communication and Networks (ICCCN 2018), Hangzhou, China, 30 July—2 August 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Khalid, U.; Asim, M.; Baker, T.; Hung, P.C.K.; Tariq, M.A.; Rafferty, L. A decentralized lightweight blockchain-based authentication mechanism for IoT systems. Clust. Comput. 2020, 23, 2067–2087. [Google Scholar] [CrossRef]
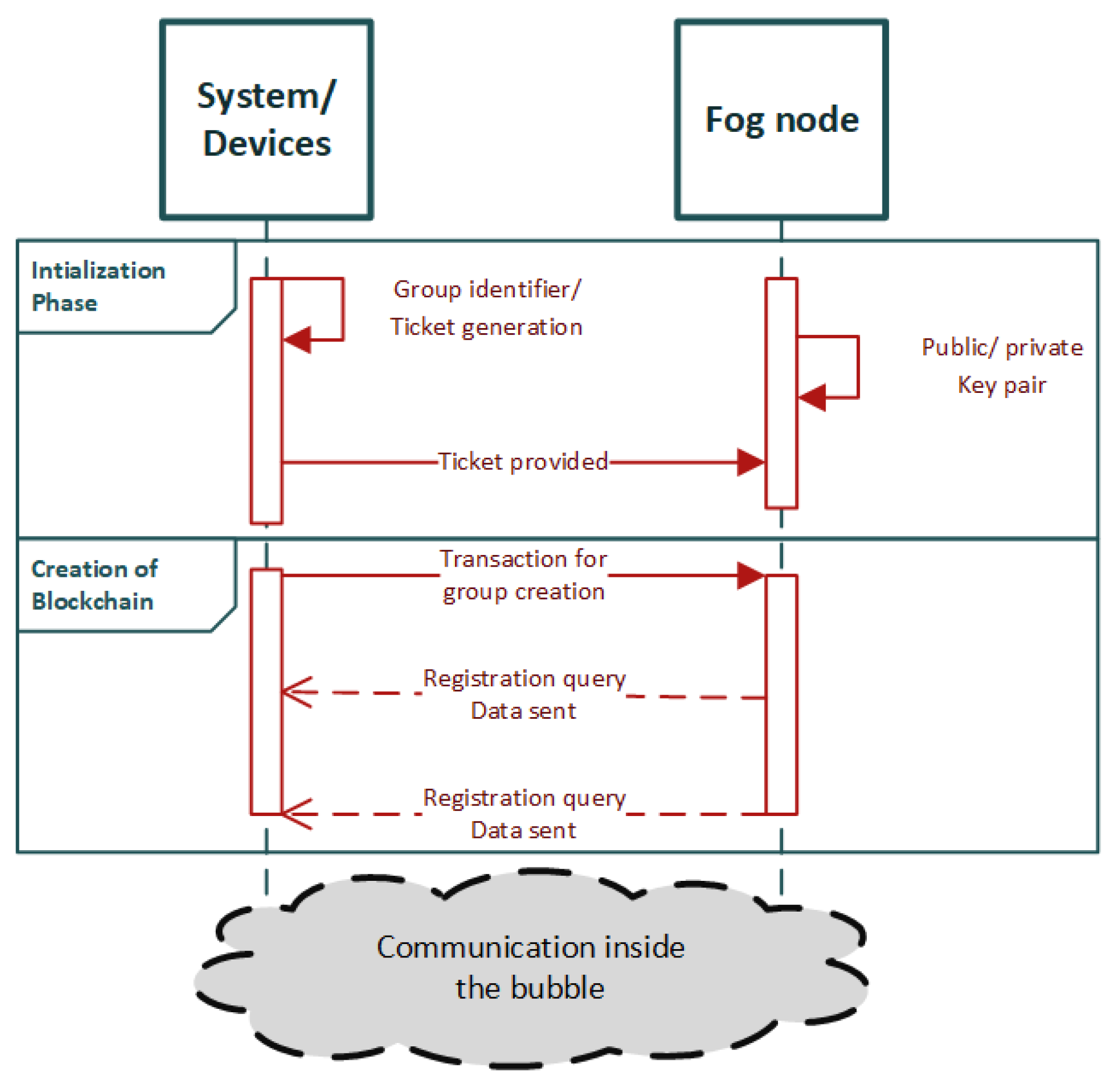
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Zhaofeng, M.; Jialin, M.; Jihui, W.; Zhiguang, S. Blockchain-Based Decentralized Authentication Modeling Scheme in Edge and IoT Environment. IEEE Internet Things J. 2021, 8, 2116–2123. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Huang, X.; Vijayakumar, P.; Choo, K.-K.R. HomeChain: A Blockchain-Based Secure Mutual Authentication System for Smart Homes. IEEE Internet Things J. 2020, 7, 818–829. [Google Scholar] [CrossRef]
- Fan, Q.; Chen, J.; Deborah, L.J.; Luo, M. A secure and efficient authentication and data sharing scheme for Internet of Things based on blockchain. J. Syst. Arch. 2021, 117, 102112. [Google Scholar] [CrossRef]
- Cui, Z.; Xue, F.; Zhang, S.; Cai, X.; Cao, Y.; Zhang, W.; Chen, J. A Hybrid BlockChain-Based Identity Authentication Scheme for Multi-WSN. IEEE Trans. Serv. Comput. 2020, 13, 241–251. [Google Scholar] [CrossRef]
- Xu, R.; Yu, C.; Blasch, E.; Chen, G. Blendcac: A Blockchain-Enabled Decentralized Capability-Based Access Control for Iots. In Proceedings of the IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1027–1034. [Google Scholar]
- Gusmeroli, S.; Piccione, S.; Rotondi, D. A capability-based security approach to manage access control in the internet of things. Math. Comput. Model. 2013, 58, 1189–1205. [Google Scholar] [CrossRef]
- Nakamura, Y.; Zhang, Y.; Sasabe, M.; Kasahara, S. Capability-based access control for the internet of things: An ethereum blockchain-based scheme. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019. [Google Scholar]
- Hernández-Ramos, J.L.; Jara, A.J.; Marin, L.; Skarmeta, A.F. Distributed capability-based access control for the internet of things. J. Internet Serv. Inf. Secur. 2013, 3, 1–16. [Google Scholar]
- Zhang, Y.; Yutaka, M.; Sasabe, M.; Kasahara, S. Attribute-Based Access Control for Smart Cities: A Smart-Contract-Driven Framework. IEEE Internet Things J. 2020, 8, 6372–6384. [Google Scholar] [CrossRef]
- Hu, V.C.; Ferraiolo, D.; Kuhn, R.; Schnitzer, A.; Sandlin, K.; Miller, R.; Scarfone, K. Guide to Attribute Based Access Control (ABAC) Definition and Considerations. Publication 2014, 800, 1–54. [Google Scholar] [CrossRef]
- Sharding-FAQs|Ethereum Wiki. Available online: https://eth.wiki/sharding/Sharding-FAQs (accessed on 25 January 2022).
- Ethereum 2.0 FAQ|ConsenSys. Available online: https://consensys.net/knowledge-base/ethereum-2/faq (accessed on 25 January 2022).
- Decentralizing Access Controls through Blockchain—Nitesh Emmadi, TCS—Cointelegraph.com.au. Available online: https://www.cointelegraph.com.au/videos/blockchain-videos/decentralizing-access-controls-through-blockchain-nitesh-emmadi-tcs (accessed on 25 January 2022).
- Alexopoulos, N.; Vasilomanolakis, E.; Ivánkó, N.R.; Mühlhäuser, M. Towards Blockchain-Based Collaborative Intrusion Detection Systems; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Locasto, M.E.; Parekh, J.J.; Keromytis, A.D.; Stolfo, S.J. Towards collaborative security and p2p intrusion detection. In Proceedings of the Sixth Annual IEEE SMC Information Assurance Workshop, West Point, NY, USA, 15–17 June 2005; pp. 333–339. [Google Scholar]
- Vasilomanolakis, E.; Krügl, M.; Cordero, C.G.; Mühlhäuser, M.; Fischer, M. Skipmon: A locality-aware collaborative intrusion detection system. In Proceedings of the 2015 IEEE 34th International Performance Computing and Communications Conference (IPCCC), Nanjing, China, 14–16 December 2015; pp. 1–8. [Google Scholar]
- Golomb, T.; Mirsky, Y.; Elovici, Y. CIoTA: Collaborative Anomaly Detection via Blockchain. arXiv 2018, arXiv:1803.03807. [Google Scholar] [CrossRef]
- Preuveneers, D.; Rimmer, V.; Tsingenopoulos, I.; Spooren, J.; Joosen, W.; Ilie-Zudor, E. Chained Anomaly Detection Models for Federated Learning: An Intrusion Detection Case Study. Appl. Sci. 2018, 8, 2663. [Google Scholar] [CrossRef] [Green Version]
- Liang, C.; Shanmugam, B.; Azam, S.; Karim, A.; Islam, A.; Zamani, M.; Kavianpour, S.; Idris, N.B. Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent Systems. Electronics 2020, 9, 1120. [Google Scholar] [CrossRef]
- GitHub-Aymwxbb2012/Intrusion_Detection_System_SESS at Develop. Available online: https://github.com/aymwxbb2012/intrusion_detection_system_SESS/tree/develop (accessed on 24 January 2022).
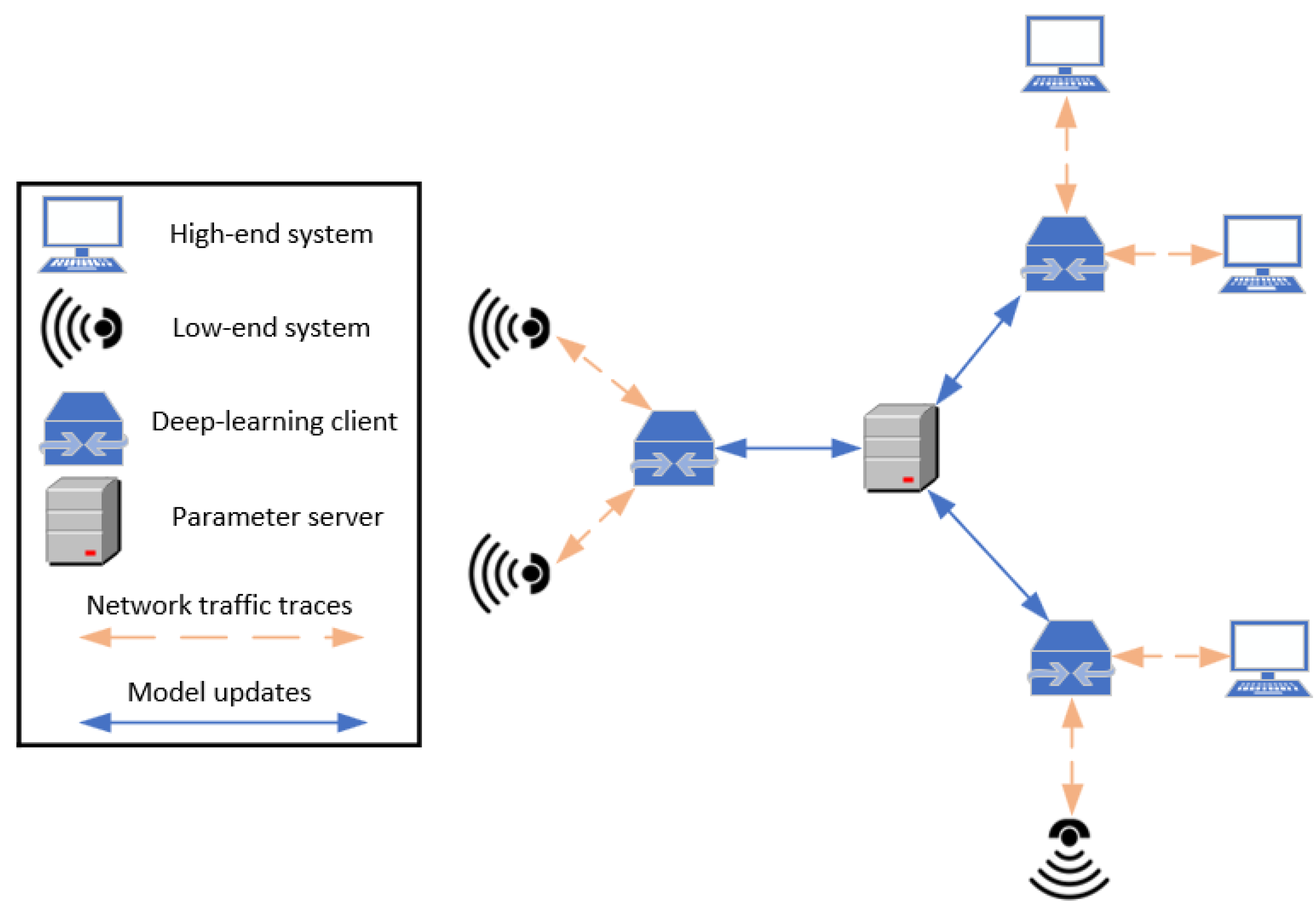
| Consensus Mechanism | Type of Blockchain Used | Advantages | Limitations |
|---|---|---|---|
| PoW | public, permissionless | high security, malicious node tolerant | not efficient, high energy consumption, high computation cost |
| PoS | public, permissionless | power efficient, high security | concept of “stake” is not applicable in IoT |
| PBFT | permissioned | high throughput, low computational overhead | susceptible to Sybil attacks, poor scalability |
| Reference | Type of Blockchain and Blockchain Platform | Advantages | Limitations | Implementation Parameters | Future Work |
|---|---|---|---|---|---|
| [38] | Permissioned, Hyperledger Fabric | decentralization, simplicity, general application | - | Raspberry Pi, Hyperledger Fabric | Management of IoT sensors data |
| [39] | Public, Ethereum Blockchain | decentralization, reduces latency, compliant to security requirements | transaction time delay and high energy consumption due to Ethereum properties | Ganache-cli, Ethereum emulator | Development of a lightweight consensus protocol for better results in terms of energy consumption |
| [36] | Ethereum Blockchain | decentralization, device credibility, patching | needs credible users | Geth client, Ethereum, Ubuntu VM | Investigate zero-knowledge proof encryption, real implementation |
| [40] | Public, Ethereum Blockchain | decentralization, scalability, resistant to attacks | not adapted to real time applications, no initialization phase, limited cryptocurrency rate | HP laptop- Ubuntu 14.04, Raspberry Pi–Rasbian 4.9.41, Ethereum | Controlled communication between bubbles, implementation of mechanism, design of a protocol for miner optimization |
| [41] | Private, Hyperledger fabric 1.4 | suitable for password-based, certificate-based biotechnology- based authentication | high time complexity | virtual box 5.2.8, Ubuntu 16.4 server client Windows 10 pro intel i5-6200 2.30 Ghz CPU | - |
| [42] | private, JUICE blockchain platform | decentralization, anonymity | - | Ubuntu 16.04, Intel Core i7-6700 CPU 3.40 GHZ, 3-GB RAM, nginx-1.11.3, truffle-4.1.13, JUICE-client | Consider the attribute-based cryptographic approach in order to achieve better access control |
| [43] | - | authentication and confidentiality of data sharing | - | Anonymous authentication of IoT | |
| [44] | Private Blockchain | decentralization, scalability | evaluation results are theoretical | Ethernet workshop | - |
| [37] | Private, Hyperledger Fabric | decentralization, data privacy, data integrity, SSI | - | - | Implementation of the designed mechanism in real life applications |
| Reference | Guarantees | Drawbacks |
|---|---|---|
| [53] | Decentralization | Limited in Protected Health Information Storage systems |
| Availability | ||
| Confidentiality | ||
| Integrity | ||
| Immutability | ||
| [45] | Lightweight, scalable, decentralized, and fine-grained access control solution for large-scale IoT systems. | Every domain involves a domain owner, which is a centralized entity; this might cause issues such as single point of failure, bottleneck, performance degradation, etc. |
| A token is stored on the Blockchain which is visible in every participant; this will raise privacy issues. | ||
| [47] | More fine-grained access control and more flexible token management compared with existing capability-based AC schemes. | No results on the feasibility of the proposed scheme under a IoT healthcare system model, which involves several subjects such as users, doctors, nurses, etc. |
| Experiments based on a local Ethereum blockchain demonstrated the feasibility of the scheme in large-scale IoT systems. | ||
| Promising to achieve dynamic and fine-grained access control as ABAC introduces context information and the attributes of subjects and objects into its access control policies. More accurate access control in sensitive applications such as Healthcare by including sufficient attributes. Reduces the burden of maintenance, as access policies can be changed by simply changing the attribute values without the need to change the underlying subject–object relationships. | Although the prototype demonstrates the feasibility of the proposed framework, it can hardly reflect the performance of the framework in large-scale IoT applications such as Healthcare applications. The authors consider as future work the implementation of the proposed framework in environments with larger scales. |
| Requirement | Description |
|---|---|
| Accountability | Participating nodes must be held responsible for their actions. |
| Integrity | The integrity of the alert data should be guaranteed, since the accuracy of the detection depends on the alert data. |
| Resilience | The existence of single-points-of-failure (SPoFs) and the dependence of the system’s normal operations on a small group of nodes should be avoided. |
| Consensus | The proposed system needs to be able to reach a consensus regarding both the quality of individual alert data and the trustworthiness of each participating node. |
| Scalability | The proposed system needs to be scalable to a large number of participating nodes. |
| Minimum Overhead | The proposed system should incur minimum communication and computation overhead. |
| Privacy | The proposed system should provide the participating nodes with the ability to keep their alert data private and to selectively disclose alert data as they wish. Simultaneously, the requirements related to accountability and data integrity should still hold. |
| Design Consideration | Implementation Options |
|---|---|
| Governance of the distributed ledger | 1. Public (permissionless) blockchain |
| 2. Consortium (permissioned) blockchain | |
| Consensus algorithm | 1. Proof-of-Work/Proof-of-Stake designs |
| 2. Practical Byzantine Fault Tolerance (PBFT) designs | |
| Peers participating in the consensus algorithm | 1. All nodes of CIDS participate. |
| 2. Only a subset of nodes of CIDS participate. | |
| Detail of alert data during the dissemination process | 1. Exchange of raw alert data |
| 2. Exchange of compact representations of the alert data (e.g., bloom filters [55,56]) | |
| 3. Hybrid (proposed by the authors): exchange of compact representations in the Consensus layer, and exchange of raw alert data in the Alert Exchange layer. | |
| Data encryption in the Consensus layer | 1. Symmetric key cryptography and distributing keys to specific participants. |
| 2. Exchange of compact representations of the alert data (e.g., bloom filters) |
| Approach | Requirements |
|---|---|
| Record the alert data produced by IDSs | (1) The IoT devices participating in the blockchain network should possess enough computational resources to run the consensus protocol of the blockchain network. |
| (2) The IoT devices participating in the blockchain network should possess enough communication bandwidth to run the consensus protocol of the blockchain network. | |
| (3) The delay related to the inclusion of newly produced alert data to the blockchain ledger should be kept to a minimum. For this purpose, instead of raw alert data, hashes of the alert data can be stored in the distributed ledger. | |
| Support and enhance the federated learning IDS | (1) The IoT devices participating in the blockchain network should possess enough computational resources to run the consensus protocol of the blockchain network. (2) The IoT devices participating in the blockchain network should possess enough computational resources to perform the aggregation of the separately trained ML models and produce the global trained ML model. |
| (3) The IoT devices participating in the blockchain network should possess enough communication bandwidth to run the consensus protocol of the blockchain network. | |
| (4) The delay related to the creation of the global trained model should be kept to a minimum. For this purpose, the separately trained ML model could be stored in the distributed ledger in a compressed form. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pelekoudas-Oikonomou, F.; Zachos, G.; Papaioannou, M.; de Ree, M.; Ribeiro, J.C.; Mantas, G.; Rodriguez, J. Blockchain-Based Security Mechanisms for IoMT Edge Networks in IoMT-Based Healthcare Monitoring Systems. Sensors 2022, 22, 2449. https://doi.org/10.3390/s22072449
Pelekoudas-Oikonomou F, Zachos G, Papaioannou M, de Ree M, Ribeiro JC, Mantas G, Rodriguez J. Blockchain-Based Security Mechanisms for IoMT Edge Networks in IoMT-Based Healthcare Monitoring Systems. Sensors. 2022; 22(7):2449. https://doi.org/10.3390/s22072449
Chicago/Turabian StylePelekoudas-Oikonomou, Filippos, Georgios Zachos, Maria Papaioannou, Marcus de Ree, José C. Ribeiro, Georgios Mantas, and Jonathan Rodriguez. 2022. "Blockchain-Based Security Mechanisms for IoMT Edge Networks in IoMT-Based Healthcare Monitoring Systems" Sensors 22, no. 7: 2449. https://doi.org/10.3390/s22072449
APA StylePelekoudas-Oikonomou, F., Zachos, G., Papaioannou, M., de Ree, M., Ribeiro, J. C., Mantas, G., & Rodriguez, J. (2022). Blockchain-Based Security Mechanisms for IoMT Edge Networks in IoMT-Based Healthcare Monitoring Systems. Sensors, 22(7), 2449. https://doi.org/10.3390/s22072449








