A Comprehensive Review of Internet of Things: Technology Stack, Middlewares, and Fog/Edge Computing Interface
Abstract
:1. Introduction
- A comprehensive insight into IoT technology stack, adaptation and growth trends.
- The detailed investigation of IoT Functional blocks at every layer (referred to as horizontal fabric), state-of-the-art research corresponding these elements, and the associated challenges.
- The characterization of Middleware, enterprise platforms and integration challenges for enterprise solutions (referred to as vertical markets).
- Future directions to optimize the IoT Technology Stack and its integration with enterprise systems.
- Interfacing Fog/Edge network to extend coverage, convergence and deployment scope for IoT networks.
- State-of-the-art research in Fog/Edge networks, open challenges and directions towards IoT interfacing, thus enhancing application of vertical markets.
2. Research Design
Research Questions
- What is the current state of IoT technology stack (referred to as horizontal fabric) and application scenario (referred to as vertical markets)? This question aims to identify the current state-of-the-art of IoT technology, growth trends, associated challenges and the range of applications and domains.
- What is the impact of utilizing middlewares in existing enterprise IoT applications? This question allowed us to classify the current state of middlewares currently being deployed for enterprise applications.
- What are the current technological and integration challenges, and how can the current technology stack be optimized? This question focuses on the integration effect, feasibility, and scope of these IoT application domains. It further aims at providing gaps and solutions to optimize the IoT technology stack from a layered perspective.
- How can Fog/Edge networks extend the capabilities of current IoT applications? This question is aimed at investigating the current state of Fog/Edge networks and the possibilities of extending these services to IoT deployments.
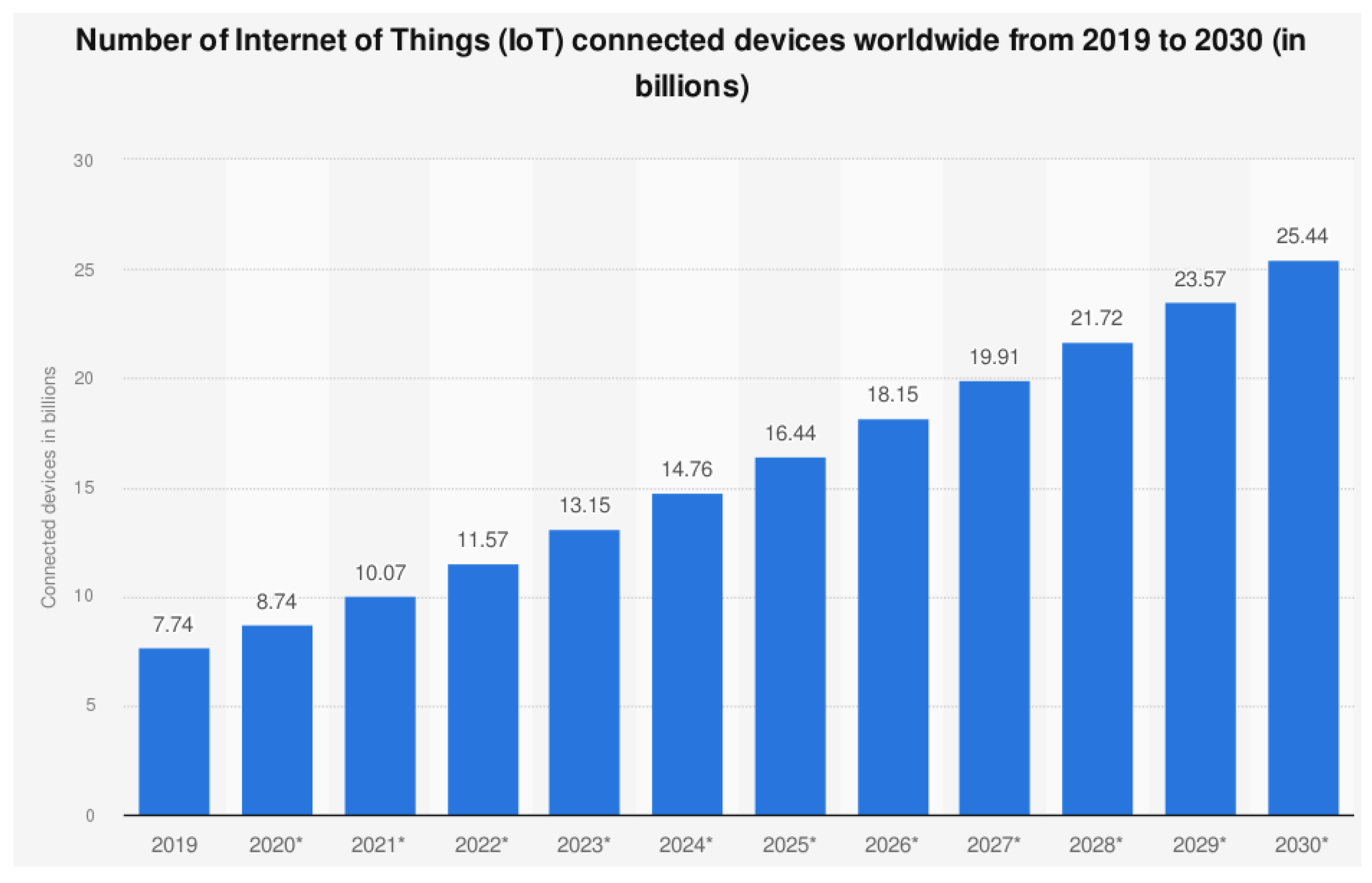
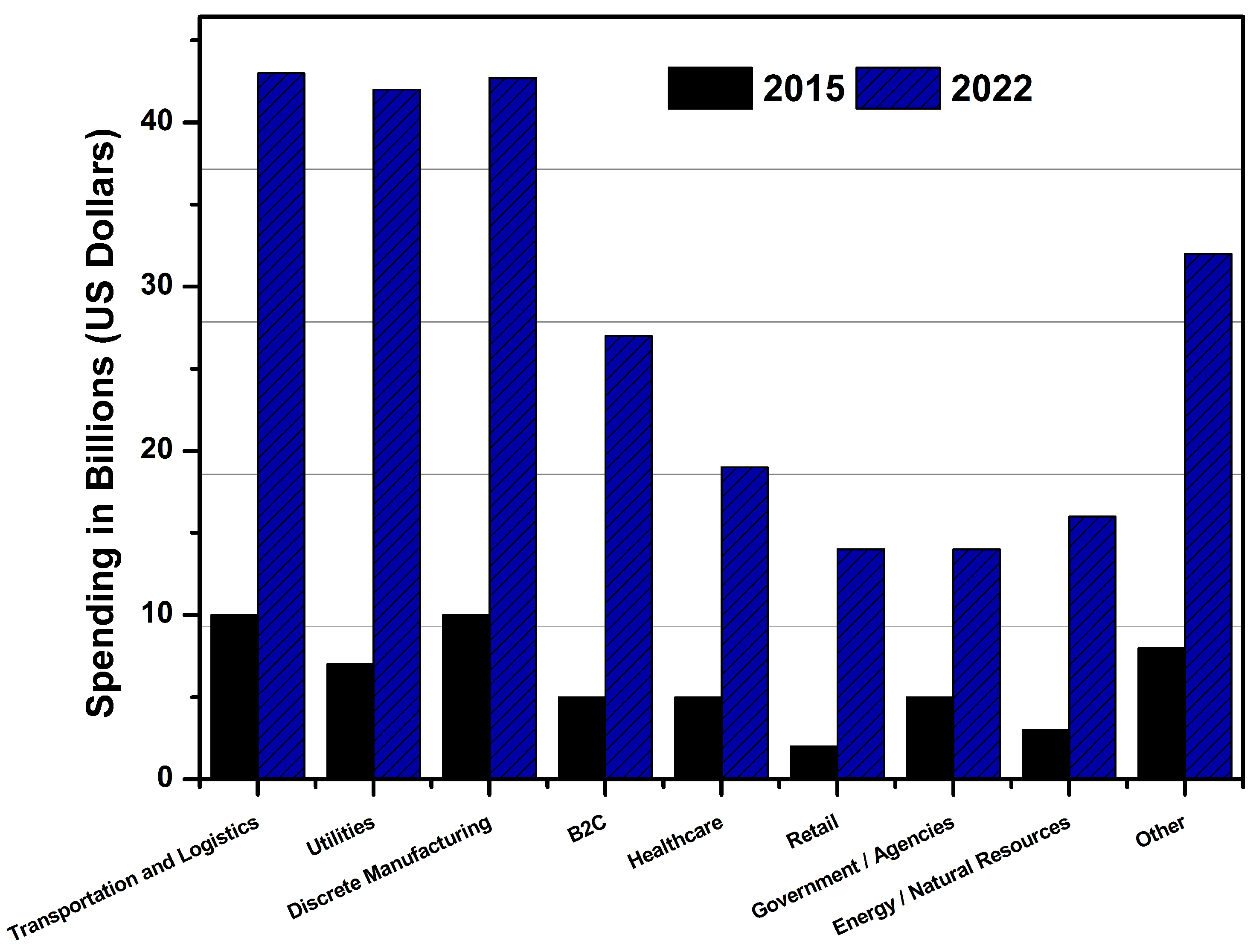
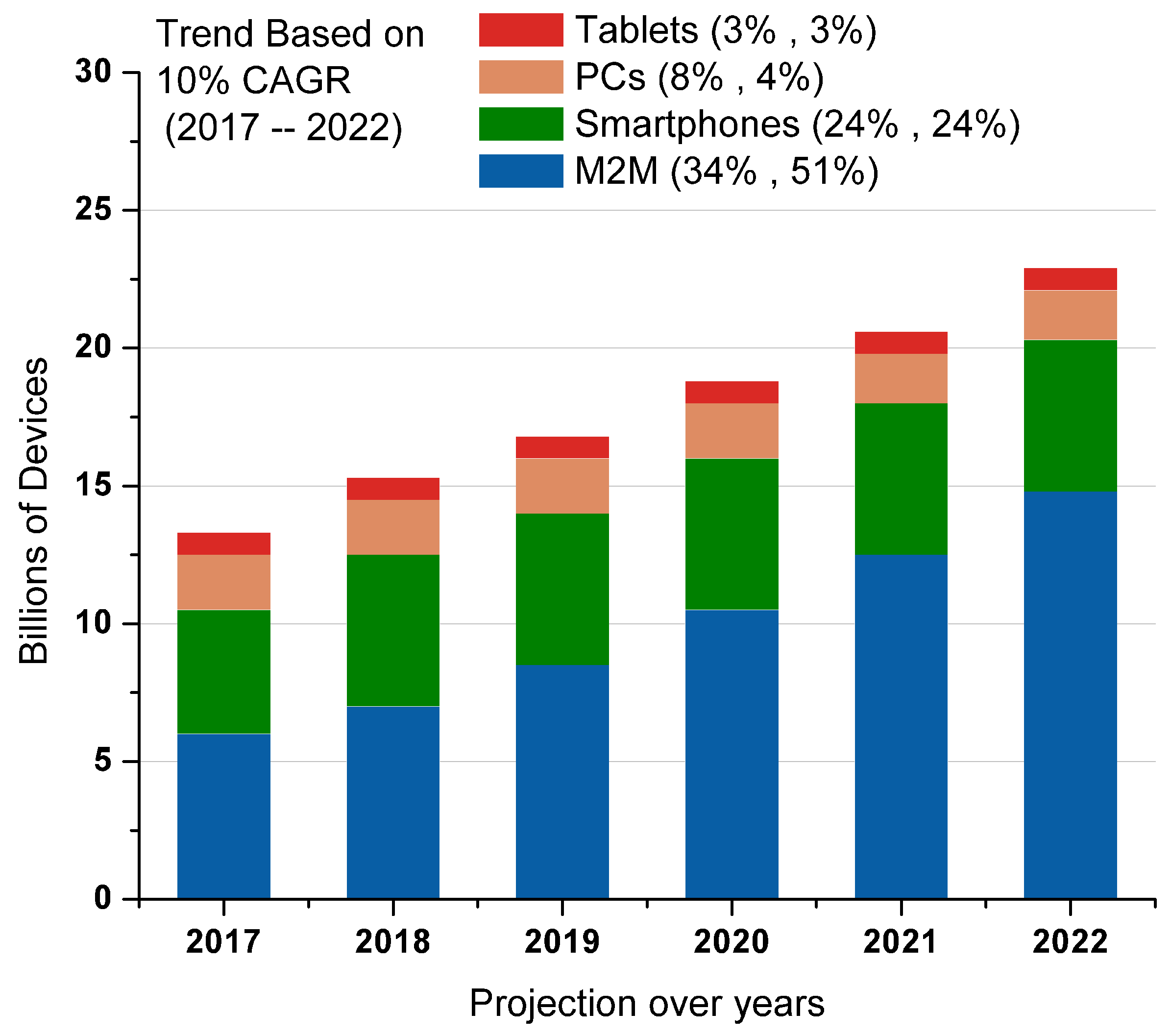
3. IoT Market Growth by Industry Sectors
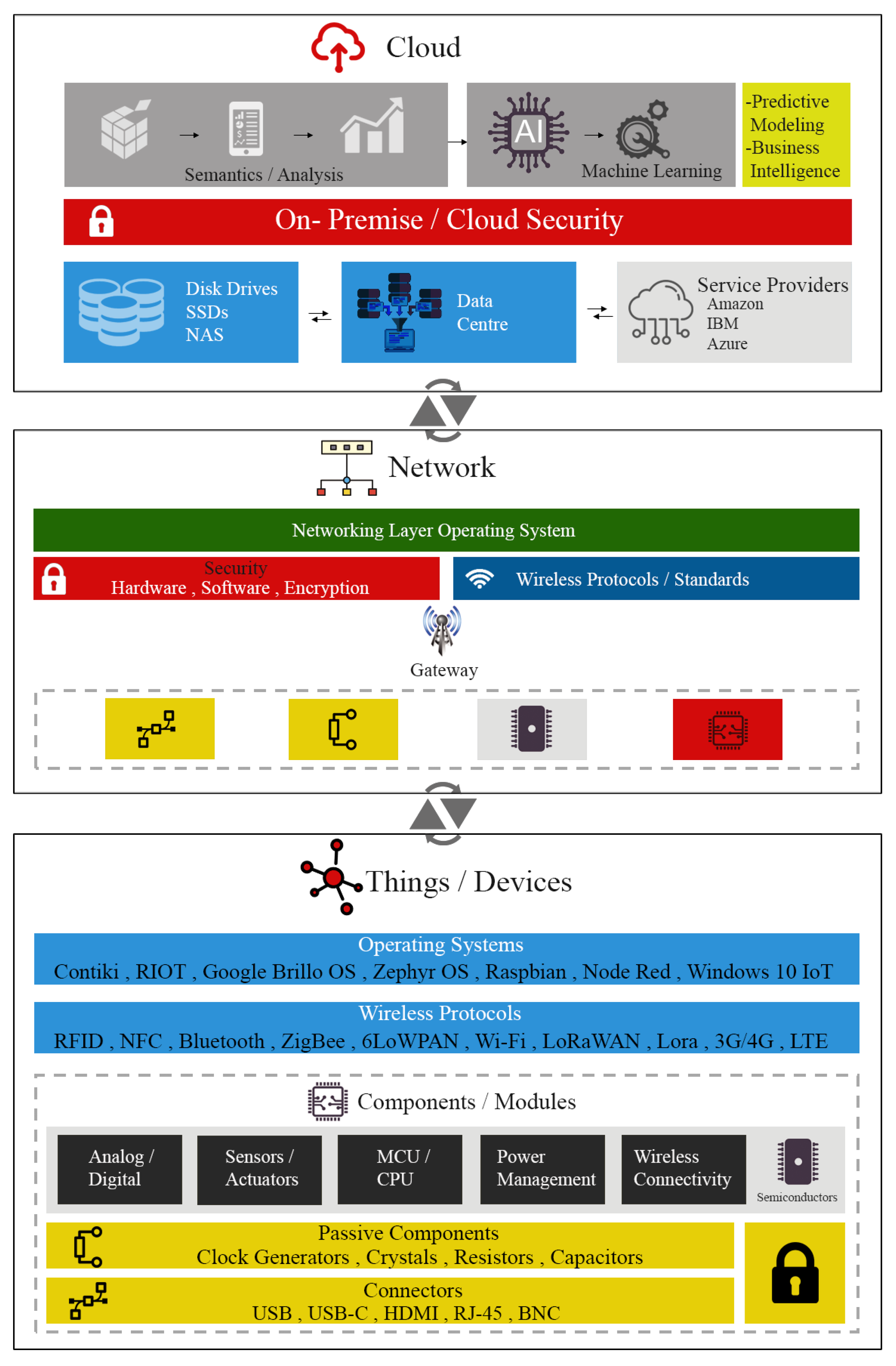
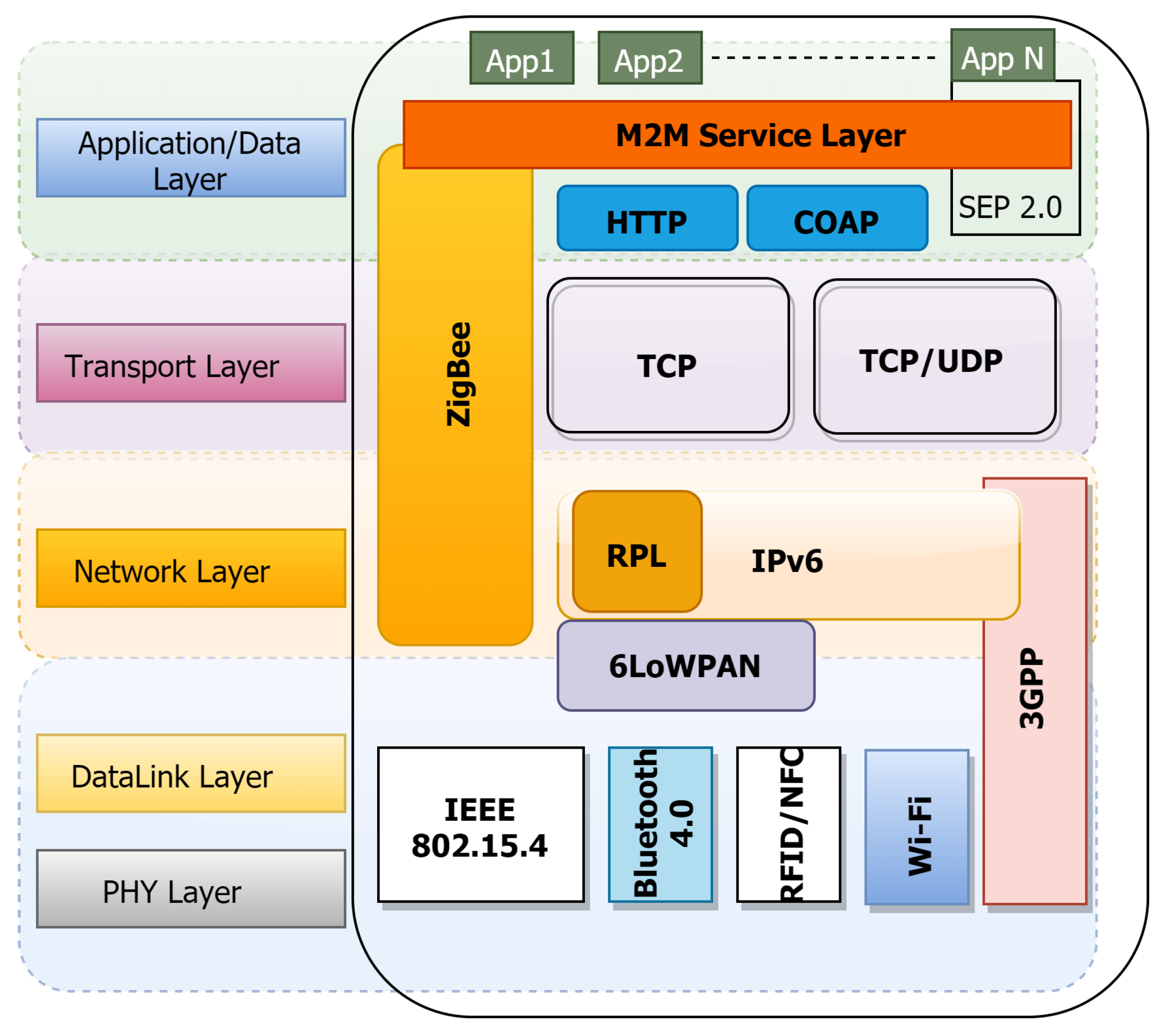
4. IoT Architectures, Platforms and Technology Stack
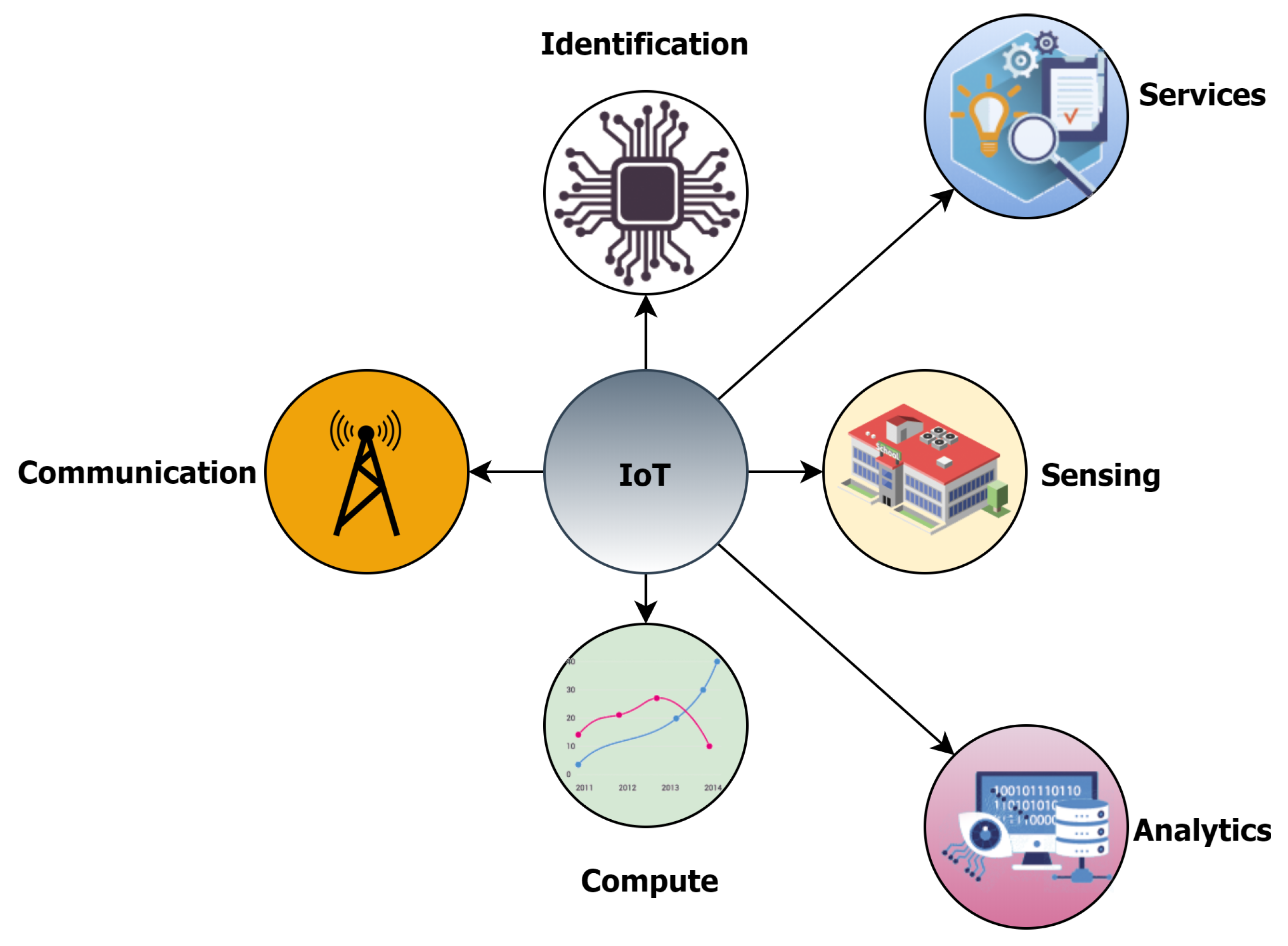
5. Understanding IoT Functional Blocks
5.1. Identification
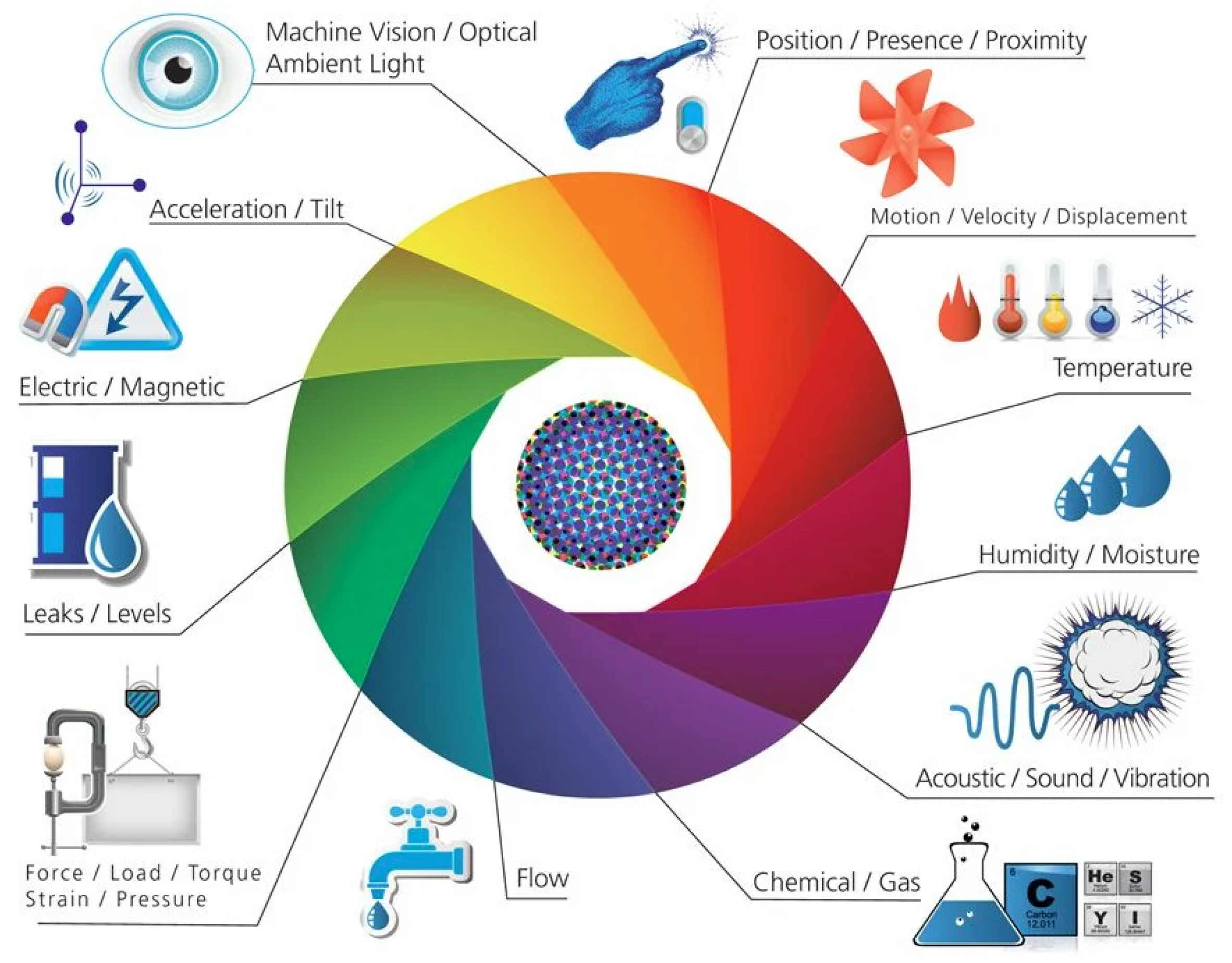
5.2. Sensing
5.3. Communication
5.4. Compute
5.5. Services
5.6. Semantics and Analytics
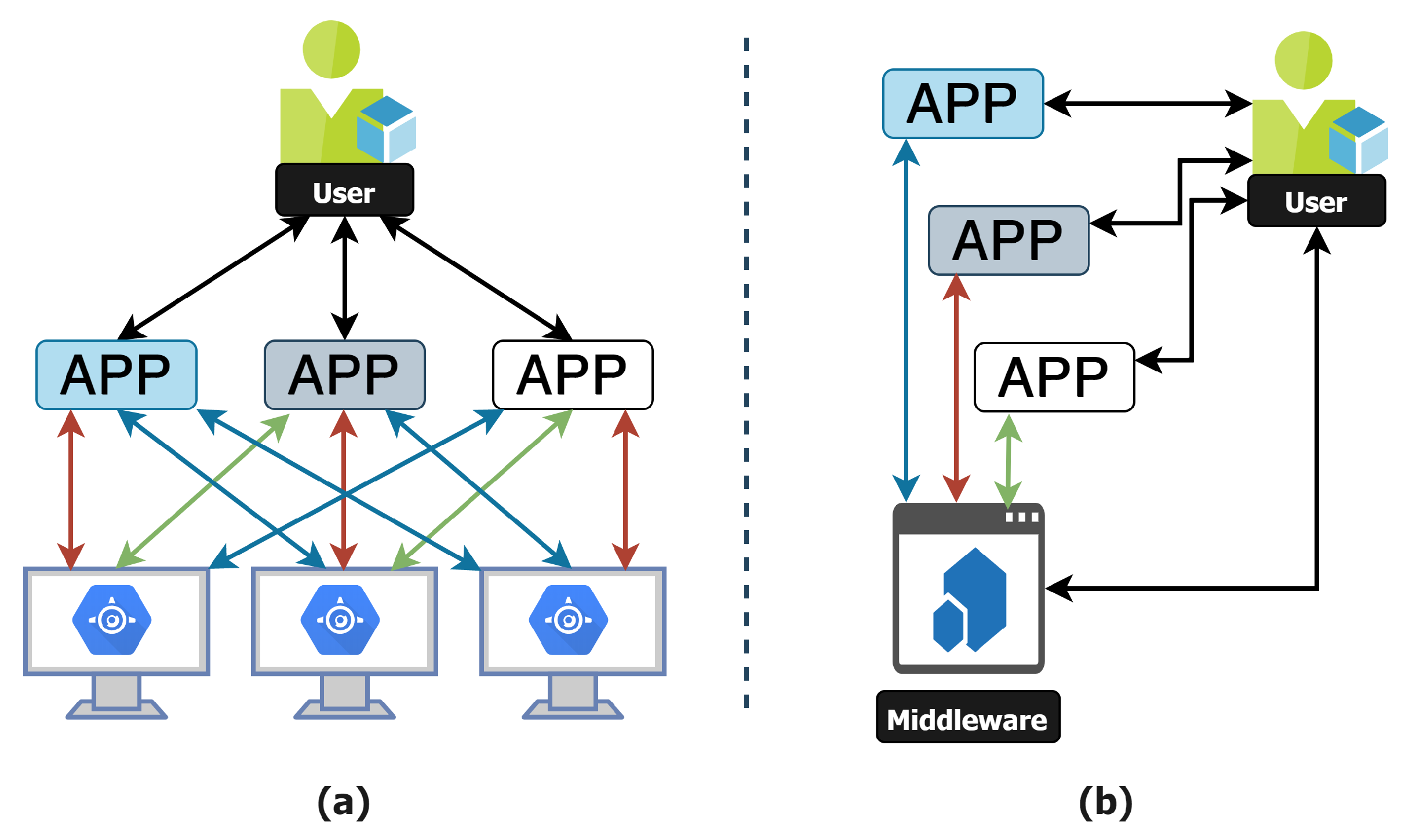
6. Characterizing Middlewares for the IoT
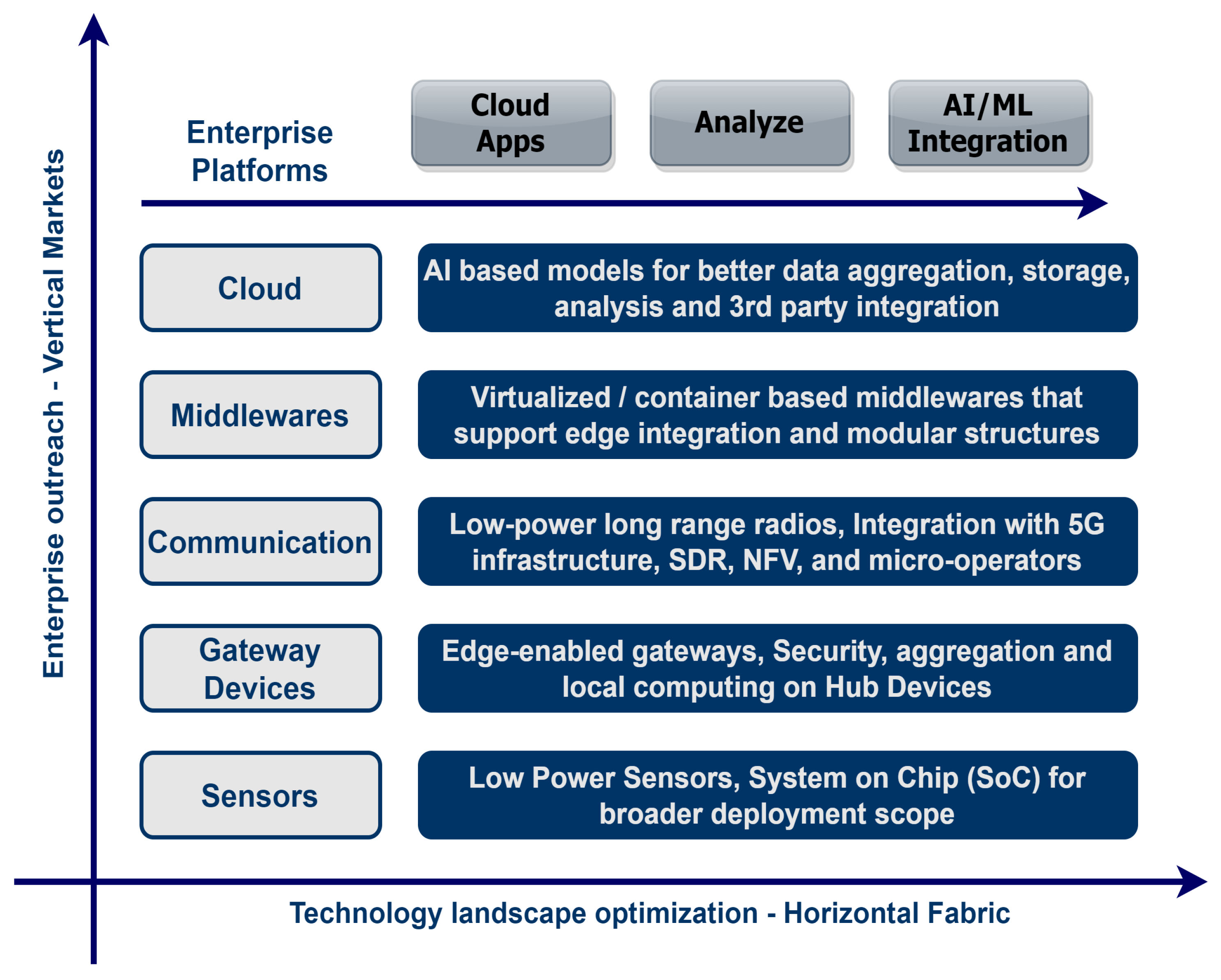
7. IoT Stack Optimization
- First: complete vendor dependability to deploy one-off application solely run and managed by the vendors in the cloud;
- Intermediary: on-premise solution deployment managed by end business as well as vendors. Thus, opens room for expansion and optimization;
- Mature: an end-to-end ecosystem either deployed on-premise, on-cloud or a hybrid solution that demands a complete optimization of the entire IoT stack.
8. Fog/Edge Computing: Technological Advancements, Integration Challenges and Edge-Enabled Vertical Markets
- Reduced network latency;
- Enhanced compute, storage and network capacity;
- Increased network bandwidth;
- An overall increase in system response time;
- Privacy and node-aware security;
- Fault-tolerance and mitigation at node level;
- Energy conservation by reducing the amount of data sent to the cloud;
- Network robustness—by improving the network hierarchy.
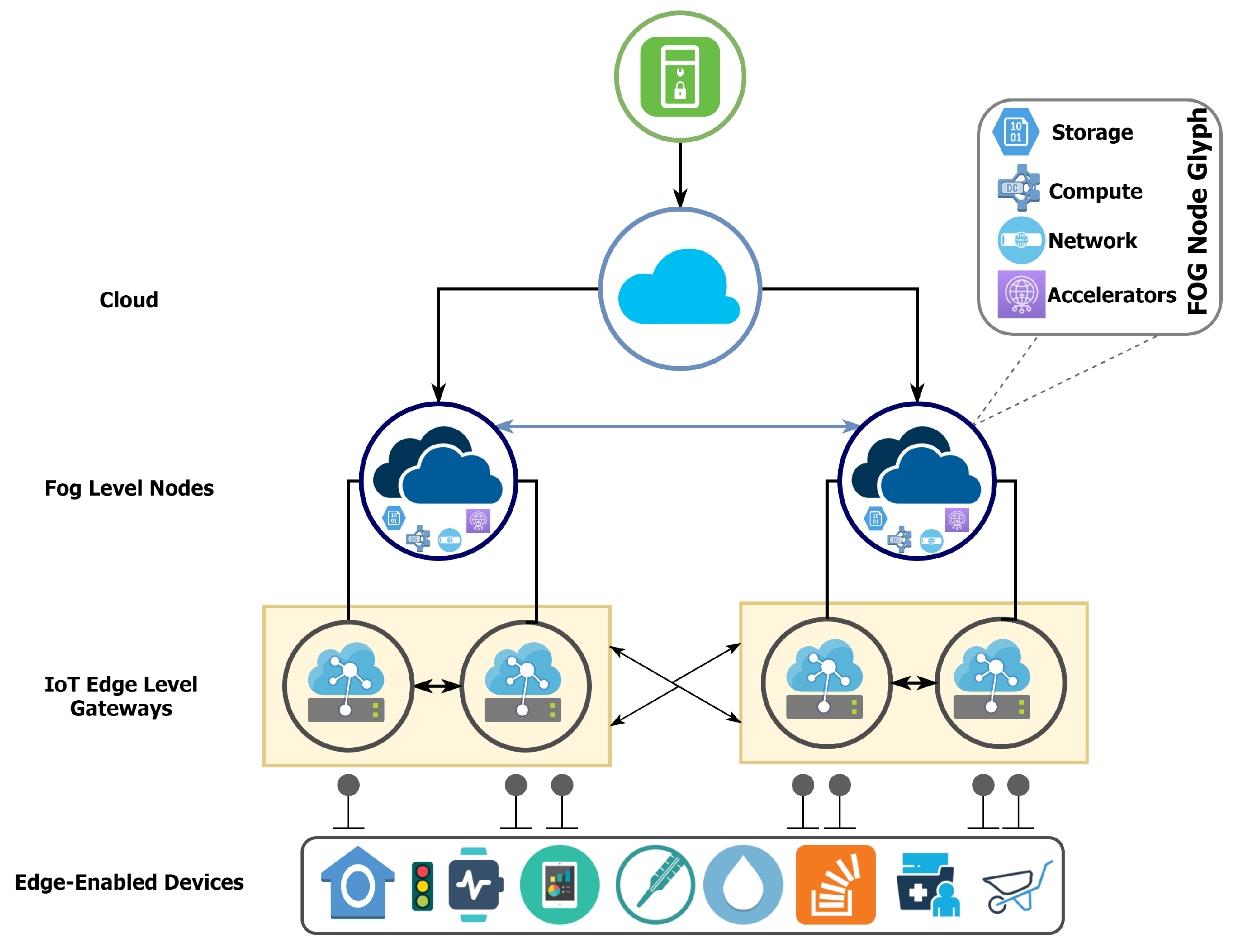
8.1. Fog/Edge Architecture Model
8.2. Security and Orchestration
9. Discussion
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Statista. Number of Internet of Things (IoT) Connected Devices Worldwide from 2019 to 2030. 2020. Available online: https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/ (accessed on 26 November 2021).
- Evans, D. The Internet of Things: How the Next Evolution of Internet Is Changing Everything. 2011. Available online: http://www.cisco.com/web/about/ac79/docs/innov/IoT_IBSG_0411FINAL.pdf (accessed on 26 November 2021).
- Keoh, S.L.; Kumar, S.S.; Tschofenig, H. Securing the Internet of Things: A Standardization Perspective. IEEE Internet Things J. 2014, 1, 265–275. [Google Scholar] [CrossRef]
- Moghadam, A.Q.; Imani, M. A new method of IPv6 addressing based on EPC-mapping in the Internet of Things. In Proceedings of the 2018 4th International Conference on Web Research (ICWR), Tehran, Iran, 25–26 April 2018; pp. 92–96. [Google Scholar] [CrossRef]
- Rooney, T. Putting IPv6 to Work. 2015. Available online: https://www.rmv6tf.org/wp-content/uploads/2015/10/BT-Diamond-IP-IPv6-and-IoT-Print-Version-3.compressed.pdf (accessed on 26 November 2021).
- Nizzi, F.; Pecorella, T.; Esposito, F.; Pierucci, L.; Fantacci, R. IoT Security via Address Shuffling: The Easy Way. IEEE Internet Things J. 2019, 6, 3764–3774. [Google Scholar] [CrossRef] [Green Version]
- Savolainen, T.; Soininen, J.; Silverajan, B. IPv6 Addressing Strategies for IoT. IEEE Sens. J. 2013, 13, 3511–3519. [Google Scholar] [CrossRef]
- Ali, O.; Ishak, M.K.; Bhatti, M.K.L. Emerging IoT domains, current standings and open research challenges: A review. PeerJ Comput. Sci. 2021, 7, e659. [Google Scholar] [CrossRef]
- Cisco. Cisco Visual Networking Index: Forecast and Trends, 2017–2022. 2018. Available online: https://www.cisco.com/c/en/us/solutions/collateral/service-provider/visual-networking-index-vni/white-paper-c11-741490.pdf (accessed on 26 November 2021).
- Statista. Spending on Internet of Things Worldwide by Vertical in 2015 and 2020 (in Billions USD). 2018. Available online: https://www.statista.com/statistics/666864/iot-spending-by-vertical-worldwide/ (accessed on 26 November 2021).
- Torchia, M. IDC Forecasts Worldwide Technology Spending on the Internet of Things to Reach 1.2 Trillion USD in 2022. 2018. Available online: https://www.idc.com/getdoc.jsp?containerId=prUS43994118 (accessed on 26 November 2021).
- ITU. An Overview of Internet of Things. 2012. Available online: https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-Y.2060-201206-I!!PDF-E&type=items (accessed on 26 November 2021).
- Stankovic, J.A. Research Directions for the Internet of Things. IEEE Internet Things J. 2014, 1, 3–9. [Google Scholar] [CrossRef]
- Puneet Gupta, S.S.I. Goodbye, Motherboard. Hello, Silicon-Interconnect Fabric. IEEE Spectr. 2019, 56, 28–33. [Google Scholar] [CrossRef]
- Conti, F.; Schilling, R.; Schiavone, P.D.; Pullini, A.; Rossi, D.; Gürkaynak, F.K.; Muehlberghuber, M.; Gautschi, M.; Loi, I.; Haugou, G.; et al. An IoT Endpoint System-on-Chip for Secure and Energy-Efficient Near-Sensor Analytics. IEEE Trans. Circuits Syst. I Regul. Pap. 2017, 64, 2481–2494. [Google Scholar] [CrossRef] [Green Version]
- Liu, X.; Sánchez-Sinencio, E. A Highly Efficient Ultralow Photovoltaic Power Harvesting System with MPPT for Internet of Things Smart Nodes. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2015, 23, 3065–3075. [Google Scholar] [CrossRef]
- Urbina, M.; Acosta, T.; Lázaro, J.; Astarloa, A.; Bidarte, U. Smart Sensor: SoC Architecture for the Industrial Internet of Things. IEEE Internet Things J. 2019, 6, 6567–6577. [Google Scholar] [CrossRef]
- Bhuiyan, M.N.; Rahman, M.M.; Billah, M.M.; Saha, D. Internet of Things (IoT): A Review of Its Enabling Technologies in Healthcare Applications, Standards Protocols, Security, and Market Opportunities. IEEE Internet Things J. 2021, 8, 10474–10498. [Google Scholar] [CrossRef]
- Ray, P.P.; Dash, D.; Salah, K.; Kumar, N. Blockchain for IoT-Based Healthcare: Background, Consensus, Platforms, and Use Cases. IEEE Syst. J. 2021, 15, 85–94. [Google Scholar] [CrossRef]
- Surantha, N.; Atmaja, P.; Wicaksono, M. A Review of Wearable Internet-of-Things Device for Healthcare. Procedia Comput. Sci. 2021, 179, 936–943. [Google Scholar] [CrossRef]
- Mamdiwar, S.D.; Shakruwala, Z.; Chadha, U.; Srinivasan, K.; Chang, C.Y. Recent advances on IoT-assisted wearable sensor systems for healthcare monitoring. Biosensors 2021, 11, 372. [Google Scholar] [CrossRef] [PubMed]
- Laroui, M.; Nour, B.; Moungla, H.; Cherif, M.A.; Afifi, H.; Guizani, M. Edge and fog computing for IoT: A survey on current research activities & future directions. Comput. Commun. 2021, 180, 210–231. [Google Scholar] [CrossRef]
- Kalyani, Y.; Collier, R. A Systematic Survey on the Role of Cloud, Fog, and Edge Computing Combination in Smart Agriculture. Sensors 2021, 21, 5922. [Google Scholar] [CrossRef] [PubMed]
- Shafique, K.; Khawaja, B.A.; Sabir, F.; Qazi, S.; Mustaqim, M. Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios. IEEE Access 2020, 8, 23022–23040. [Google Scholar] [CrossRef]
- Hamdan, S.; Ayyash, M.; Almajali, S. Edge-computing architectures for internet of things applications: A survey. Sensors 2020, 20, 6441. [Google Scholar] [CrossRef] [PubMed]
- Zhang, X.; Cao, Z.; Dong, W. Overview of Edge Computing in the Agricultural Internet of Things: Key Technologies, Applications, Challenges. IEEE Access 2020, 8, 141748–141761. [Google Scholar] [CrossRef]
- Nižetić, S.; Šolić, P.; González-de, D.L.d.I.; Patrono, L. Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future. J. Clean. Prod. 2020, 274, 122877. [Google Scholar] [CrossRef]
- Moore, S.J.; Nugent, C.D.; Zhang, S.; Cleland, I. IoT reliability: A review leading to 5 key research directions. CCF Trans. Pervasive Comput. Interact. 2020, 2, 147–163. [Google Scholar] [CrossRef]
- Lee, U.; Han, K.; Cho, H.; Chung, K.M.; Hong, H.; Lee, S.J.; Noh, Y.; Park, S.; Carroll, J.M. Intelligent positive computing with mobile, wearable, and IoT devices: Literature review and research directions. Ad Hoc Netw. 2019, 83, 8–24. [Google Scholar] [CrossRef]
- Srinidhi, N.; Dilip Kumar, S.; Venugopal, K. Network optimizations in the Internet of Things: A review. Eng. Sci. Technol. Int. J. 2019, 22, 1–21. [Google Scholar] [CrossRef]
- Yu, W.; Liang, F.; He, X.; Hatcher, W.G.; Lu, C.; Lin, J.; Yang, X. A survey on the edge computing for the Internet of Things. IEEE Access 2017, 6, 6900–6919. [Google Scholar] [CrossRef]
- Sethi, P.; Sarangi, S.R. Internet of things: Architectures, protocols, and applications. J. Electr. Comput. Eng. 2017, 2017. [Google Scholar] [CrossRef] [Green Version]
- Gough, D.; Oliver, S.; Thomas, J. An Introduction to Systematic Reviews; Sage: Thousand Oaks, CA, USA, 2017. [Google Scholar]
- Boland, A.; Cherry, G.; Dickson, R. Doing a Systematic Review: A Student’s Guide; Sage: Thousand Oaks, CA, USA, 2017. [Google Scholar]
- Carcary, M.; Maccani, G.; Doherty, E.; Conway, G. Exploring the determinants of IoT adoption: Findings from a systematic literature review. In Proceedings of the International Conference on Business Informatics Research, Stockholm, Sweden, 24–26 September 2018; pp. 113–125. [Google Scholar]
- Palmaccio, M.; Dicuonzo, G.; Belyaeva, Z.S. The internet of things and corporate business models: A systematic literature review. J. Bus. Res. 2021, 131, 610–618. [Google Scholar] [CrossRef]
- Gantz, J.; Reinsel, D. The Digital Universe in 2020: Big Data, Bigger Digital Shadows, and Biggest Growth in Far East. 2012. Available online: https://www.cs.princeton.edu/courses/archive/spring13/cos598C/idc-the-digital-universe-in-2020.pdf (accessed on 1 November 2021).
- Krotov, V. The Internet of Things and new business opportunities. Bus. Horiz. 2017, 60, 831–841. [Google Scholar] [CrossRef]
- Sutija, D. The Dash Button Was Just the Beginning: Expanding Commerce Everywhere. 2018. Available online: https://martechtoday.com/dash-button-just-beginning-expanding-commerce-everywhere-210826 (accessed on 26 November 2021).
- Insights, F.B. Internet of Things (IoT) Market Size, Share and Industry Analysis By Platform. 2019. Available online: https://www.fortunebusinessinsights.com/industry-reports/internet-of-things-iot-market-100307 (accessed on 26 November 2021).
- Lueth, K.L. IoT Market Analysis: Sizing the Opportunity. IoT Analytic Report. March 2015. Available online: http://iot-analytics.com/wp/wp-content/uploads/2015/03/2015-March-Whitepaper-IoT-Market-analysis-Sizing-the-opportunity.pdf (accessed on 1 November 2021).
- Marti, A.R. The Economic Impact of IoT: Putting Numbers on a Revolutionary Technology. 2018. Available online: https://www.frontier-economics.com/media/1167/201803_the-economic-impact-of-iot_frontier.pdf (accessed on 26 November 2021).
- Rossman, D.M. Unlocking the Business Value of IoT in Operations. 2018. Available online: https://www.capgemini.com/wp-content/uploads/2018/03/dti-research_iot_web.pdf (accessed on 16 November 2021).
- Accenture. Winning with the Industrial Internet of Things. 2016. Available online: https://www.accenture.com/t20160909T042713Z__w__/us-en/_acnmedia/Accenture/Conversion-Assets/DotCom/Documents/Global/PDF/Dualpub_11/Accenture-Industrial-Internet-of-Things-Positioning-Paper-Report-2015.pdfla=en (accessed on 16 November 2021).
- Fortino, G.; Guerrieri, A.; Russo, W.; Savaglio, C. Towards a Development Methodology for Smart Object-Oriented IoT Systems: A Metamodel Approach. In Proceedings of the 2015 IEEE International Conference on Systems, Man, and Cybernetics, Kowloon Tong, Hong Kong, 9–12 October 2015; pp. 1297–1302. [Google Scholar] [CrossRef]
- International, C. Testing our Trust: Consumers and the Internet of Things. 2017. Available online: https://www.consumersinternational.org/media/154746/iot2017review-2nded.pdf (accessed on 16 November 2021).
- Singh, D.; Tripathi, G.; Jara, A. Secure layers based architecture for Internet of Things. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 321–326. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Fortino, G.; Trunfio, P. Internet of Things Based on Smart Objects; Internet of Things; Springer: Abingdon, UK, 2014; p. 105. [Google Scholar] [CrossRef]
- Kiljander, J.; D’Elia, A.; Morandi, F.; Hyttinen, P.; Takalo-Mattila, J.; Ylisaukko-Oja, A.; Soininen, J.P.; Cinotti, T.S. Semantic Interoperability Architecture for Pervasive Computing and Internet of Things. IEEE Access 2014, 2, 856–873. [Google Scholar] [CrossRef]
- Alsubaei, F.A.A.; Shiva, S. An Overview of Enabling Technologies for the Internet of Things. In Internet of Things A to Z; Book Section 3; John Wiley & Sons, Inc., Wiley Online Library: Hoboken, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Krčo, S.; Pokrić, B.; Carrez, F. Designing IoT architecture(s): A European perspective. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 79–84. [Google Scholar] [CrossRef]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 2012 10th International Conference on Frontiers of Information Technology, Islamabad, Pakistan, 17–19 December 2012; pp. 257–260. [Google Scholar] [CrossRef] [Green Version]
- da Cruz, M.A.A.; Rodrigues, J.J.P.C.; Al-Muhtadi, J.; Korotaev, V.V.; de Albuquerque, V.H.C. A Reference Model for Internet of Things Middleware. IEEE Internet Things J. 2018, 5, 871–883. [Google Scholar] [CrossRef]
- Spiess, P.; Karnouskos, S.; Guinard, D.; Savio, D.; Baecker, O.; Souza, L.M.S.D.; Trifa, V. SOA-Based Integration of the Internet of Things in Enterprise Services. In Proceedings of the 2009 IEEE International Conference on Web Services, Los Angeles, CA, USA, 6–10 July 2009; pp. 968–975. [Google Scholar] [CrossRef]
- Chaqfeh, M.A.; Mohamed, N. Challenges in middleware solutions for the internet of things. In Proceedings of the 2012 International Conference on Collaboration Technologies and Systems (CTS), Denver, CO, USA, 21–25 May 2012; pp. 21–26. [Google Scholar] [CrossRef]
- Guinard, D.; Trifa, V.; Karnouskos, S.; Spiess, P.; Savio, D. Interacting with the SOA-Based Internet of Things: Discovery, Query, Selection, and On-Demand Provisioning of Web Services. IEEE Trans. Serv. Comput. 2010, 3, 223–235. [Google Scholar] [CrossRef] [Green Version]
- ITU. The BUTLER Project Overview. 2012. Available online: https://www.slideshare.net/legallf/butler-project-overview (accessed on 3 November 2021).
- Zhihong, Y.; Yingzhao, Y.; Yu, Y.; Yufeng, P.; Xiaobo, W.; Wenji, L. Study and application on the architecture and key technologies for IOT. In Proceedings of the 2011 International Conference on Multimedia Technology, Hangzhou, China, 26–28 July 2011; pp. 747–751. [Google Scholar] [CrossRef]
- Patel, Z.D. A Review on Service Oriented Architectures for Internet of Things (IoT). In Proceedings of the 2018 2nd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 11–12 May 2018; pp. 466–470. [Google Scholar] [CrossRef]
- IETF. IPv6 over Low-Power Wireless Personal Area Networks (6LoWPAN). 2007. Available online: https://tools.ietf.org/pdf/rfc4919.pdf (accessed on 3 November 2021).
- Korte, K.D.; Tumar, I.; Schönwälder, J. Evaluation of IPv6 over low-power wireless personal area networks implementations. In Proceedings of the 2009 IEEE 34th Conference on Local Computer Networks, Zurich, Switzerland, 20–23 October 2009; pp. 881–888. [Google Scholar] [CrossRef]
- Aftab, H.; Gilani, K.; Lee, J.; Nkenyereye, L.; Jeong, S.; Song, J. Analysis of identifiers in IoT platforms. Digit. Commun. Netw. 2020, 6, 333–340. [Google Scholar] [CrossRef]
- Kamina, T.; Aoki, T.; Eto, Y.; Koshizuka, N.; Yamada, J.; Sakamura, K. Verifying Identifier-Authenticity in Ubiquitous Computing Environment. In Proceedings of the 21st International Conference on Advanced Information Networking and Applications Workshops (AINAW’07), Niagara Falls, ON, Canada, 21–23 May 2007; Volume 2, pp. 403–408. [Google Scholar] [CrossRef]
- Koshizuka, N.; Sakamura, K. Ubiquitous ID: Standards for Ubiquitous Computing and the Internet of Things. IEEE Pervasive Comput. 2010, 9, 98–101. [Google Scholar] [CrossRef]
- Seike, H.; Hamada, T.; Sumitomo, T.; Koshizuka, N. Blockchain-Based Ubiquitous Code Ownership Management System without Hierarchical Structure. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018; pp. 271–276. [Google Scholar] [CrossRef]
- Bryzek, D.J. Roadmap for the Trillion Sensor Universe. 2013. Available online: https://www-bsac.eecs.berkeley.edu/scripts/show_pdf_publication.php?pdfID=1365520205 (accessed on 26 November 2021).
- PostScape. What Exactly Is the Internet of Things. 2015. Available online: https://www.postscapes.com/what-exactly-is-the-internet-of-things-infographic/ (accessed on 26 November 2021).
- Wai, L.; Sharma, A. Smart sensing for IoT applications. In Proceedings of the 2016 13th IEEE International Conference on Solid-State and Integrated Circuit Technology (ICSICT), Hangzhou, China, 25–28 October 2016; pp. 362–364. [Google Scholar] [CrossRef]
- Martinez, B.; Monton, M.; Vilajosana, I.; Prades, J.D. The Power of Models: Modeling Power Consumption for IoT Devices. IEEE Sens.J. 2015, 15, 5777–5789. [Google Scholar] [CrossRef] [Green Version]
- Kansal, A.; Hsu, J.; Zahedi, S.; Srivastava, M.B. Power management in energy harvesting sensor networks. ACM Trans. Embed. Comput. Syst 2007, 6, 32. [Google Scholar] [CrossRef]
- Belleville, M.; Fanet, H.; Fiorini, P.; Nicole, P.; Pelgrom, M.J.M.; Piguet, C.; Hahn, R.; Van Hoof, C.; Vullers, R.; Tartagni, M.; et al. Energy autonomous sensor systems: Towards a ubiquitous sensor technology. Microelectron. J. 2010, 41, 740–745. [Google Scholar] [CrossRef]
- Amarlingam, M.; Mishra, P.K.; Prasad, K.V.V.D.; Rajalakshmi, P. Compressed sensing for different sensors: A real scenario for WSN and IoT. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; pp. 289–294. [Google Scholar] [CrossRef]
- Ali, O.; Ishak, M.K.; Bhatti, M.K.L. Adaptive clear channel assessment (A-CCA): Energy efficient method to improve wireless sensor networks (WSNs) operations. AEU—Int. J. Electron. Commun. 2021, 131, 153603. [Google Scholar] [CrossRef]
- Al-Sarawi, S.; Anbar, M.; Alieyan, K.; Alzubaidi, M. Internet of Things (IoT) communication protocols: Review. In Proceedings of the 2017 8th International Conference on Information Technology (ICIT), Amman, Jordan, 17–18 May 2017; pp. 685–690. [Google Scholar] [CrossRef]
- Ray, P. A survey on Internet of Things architectures. J. King Saud Univ.—Comput. Inf. Sci. 2018, 30, 291–319. [Google Scholar] [CrossRef] [Green Version]
- Want, R. An introduction to RFID technology. IEEE Pervasive Comput. 2006, 5, 25–33. [Google Scholar] [CrossRef]
- Lian, X.; Zhang, X.; Weng, Y.; Duan, Z. Warehouse Logistics Control and Management System Based on RFID. In Proceedings of the 2007 IEEE International Conference on Automation and Logistics, Jinan, China, 18–21 August 2007; pp. 2907–2912. [Google Scholar] [CrossRef]
- Welbourne, E.; Battle, L.; Cole, G.; Gould, K.; Rector, K.; Raymer, S.; Balazinska, M.; Borriello, G. Building the Internet of Things Using RFID: The RFID Ecosystem Experience. IEEE Internet Comput. 2009, 13, 48–55. [Google Scholar] [CrossRef]
- Aghdam, Z.N.; Rahmani, A.M.; Hosseinzadeh, M. The Role of the Internet of Things in Healthcare: Future Trends and Challenges. Comput. Methods Programs Biomed. 2021, 199, 105903. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K. The Internet of Things for Health Care: A Comprehensive Survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Amendola, S.; Lodato, R.; Manzari, S.; Occhiuzzi, C.; Marrocco, G. RFID Technology for IoT-Based Personal Healthcare in Smart Spaces. IEEE Internet Things J. 2014, 1, 144–152. [Google Scholar] [CrossRef]
- Wu, F.; Rüdiger, C.; Redouté, J.; Yuce, M.R. WE-Safe: A wearable IoT sensor node for safety applications via LoRa. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 144–148. [Google Scholar] [CrossRef]
- Lee, H.C.; Ke, K.H. Monitoring of Large-Area IoT Sensors Using a LoRa Wireless Mesh Network System: Design and Evaluation. IEEE Trans. Instrum. Meas. 2018, 67, 2177–2187. [Google Scholar] [CrossRef]
- Alsulami, M.M.; Akkari, N. The role of 5G wireless networks in the internet-of- things (IoT). In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Ijaz, A.; Zhang, L.; Grau, M.; Mohamed, A.; Vural, S.; Quddus, A.U.; Imran, M.A.; Foh, C.H.; Tafazolli, R. Enabling Massive IoT in 5G and Beyond Systems: PHY Radio Frame Design Considerations. IEEE Access 2016, 4, 3322–3339. [Google Scholar] [CrossRef]
- Angelo, G.D.; Ferretti, S.; Ghini, V. Simulation of the Internet of Things. In Proceedings of the 2016 International Conference on High Performance Computing & Simulation (HPCS), Innsbruck, Austria, 18–22 July 2016; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- McKee, D.W.; Clement, S.J.; Ouyang, X.; Xu, J.; Romanoy, R.; Davies, J. The Internet of Simulation, a Specialisation of the Internet of Things with Simulation and Workflow as a Service (SIM/WFaaS). In Proceedings of the 2017 IEEE Symposium on Service-Oriented System Engineering (SOSE), Francisco, CA, USA, 6–9 April 2017; pp. 47–56. [Google Scholar] [CrossRef] [Green Version]
- Dandala, T.T.; Krishnamurthy, V.; Alwan, R. Internet of Vehicles (IoV) for traffic management. In Proceedings of the 2017 International Conference on Computer, Communication and Signal Processing (ICCCSP), Chennai, India, 10–11 January 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Srivastava, J.R.; Sudarshan, T.S.B. Intelligent traffic management with wireless sensor networks. In Proceedings of the 2013 ACS International Conference on Computer Systems and Applications (AICCSA), Ifrane, Morocco, 27–30 May 2013; pp. 1–4. [Google Scholar] [CrossRef]
- Yang, F.; Wang, S.; Li, J.; Liu, Z.; Sun, Q. An overview of Internet of Vehicles. China Commun. 2014, 11, 1–15. [Google Scholar] [CrossRef]
- Xu, X.J. Technology Is Changing What a Premium Automotive Brand Looks Like. 2018. Available online: https://hbr.org/2018/05/technology-is-changing-what-a-premium-automotive-brand-looks-like (accessed on 27 November 2021).
- Riedel, T.; Fantana, N.; Genaid, A.; Yordanov, D.; Schmidtke, H.R.; Beigl, M. Using web service gateways and code generation for sustainable IoT system development. In Proceedings of the 2010 Internet of Things (IOT), Tokyo, Japan, 29 November–1 December 2010; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Dohndorf, O.; Krüger, J.; Krumm, H.; Fiehe, C.; Litvina, A.; Lück, I.; Stewing, F. Towards the Web of Things: Using DPWS to bridge isolated OSGi platforms. In Proceedings of the 2010 8th IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), Mannheim, Germany, 29 March–2 April 2010; pp. 720–725. [Google Scholar] [CrossRef] [Green Version]
- Gigli, M.; Koo, S. Internet of Things: Services and Applications Categorization. Adv. Internet Things 2011, 01, 27–31. [Google Scholar] [CrossRef] [Green Version]
- Yongfu, L.; Dihua, S.; Weining, L.; Xuebo, Z. A service-oriented architecture for the transportation Cyber-Physical Systems. In Proceedings of the 31st Chinese Control Conference, Hefei, China, 25–27 July 2012; pp. 7674–7678. [Google Scholar]
- Leng, Y.; Zhao, L. Novel design of intelligent internet-of-vehicles management system based on cloud-computing and Internet-of-Things. In Proceedings of the 2011 International Conference on Electronic & Mechanical Engineering and Information Technology, Harbin, China, 12–14 August 2011; Volume 6, pp. 3190–3193. [Google Scholar] [CrossRef]
- Di, H. Logistics management inventory model based on 5G Network and Internet of Things system. Microprocess. Microsys. 2020, 103429. [Google Scholar] [CrossRef]
- Maguire, E.; Moreno, K.W.; Moreno, H.S.; Gagnon, R. IoT Marches into the Enterprise, Transformation Follows Quickly. 2018. Available online: https://www.iotjournaal.nl/wp-content/uploads/2018/12/1-REPORT-FINAL-WEB.pdf (accessed on 27 November 2021).
- Hullum, C. How Rogue Ales Makes a Great Beer from Wet Hops, Clean Water and Innovation. 2018. Available online: https://blogs.intel.com/iot/2018/02/06/how-rogue-ales-makes-a-great-beer-from-wet-hops-clean-water-and-innovation/#gs.hpkby6 (accessed on 27 November 2021).
- Yang, G.; Xie, L.; Mantysalo, M.; Zhou, X.; Pang, Z.; Xu, L.D.; Kao-Walter, S.; Chen, Q.; Zheng, L.R. A Health-IoT Platform Based on the Integration of Intelligent Packaging, Unobtrusive Bio-Sensor, and Intelligent Medicine Box. IEEE Trans. Ind. Inform. 2014, 10, 2180–2191. [Google Scholar] [CrossRef] [Green Version]
- Jara, A.J.; Alcolea, A.F.; Zamora, M.A.; Skarmeta, A.F.G.; Alsaedy, M. Drugs interaction checker based on IoT. In Proceedings of the 2010 Internet of Things (IOT), Tokyo, Japan, 29 November–1 December 2010; pp. 1–8. [Google Scholar] [CrossRef]
- Gerla, M.; Lee, E.; Pau, G.; Lee, U. Internet of vehicles: From intelligent grid to autonomous cars and vehicular clouds. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 241–246. [Google Scholar] [CrossRef]
- Stewart, J. Google Is to Start Building Its Own Self-Driving Cars. 2014. Available online: https://www.bbc.com/news/technology-27587558 (accessed on 27 November 2021).
- Lumb, D. Waymo’s Autonomous Cars Have Driven 4 Million Miles. 2017. Available online: https://www.engadget.com/2017/11/27/waymo-autonomous-cars-drove-4-million-miles/ (accessed on 27 November 2021).
- Uzcategui, R.A.; Sucre, A.J.D.; Acosta-Marum, G. Wave: A tutorial. IEEE Commun. Mag. 2009, 47, 126–133. [Google Scholar] [CrossRef]
- U.S. Department of Transportation. Factsheet: Improving Safety and Mobility through Vehicle-to-Vehicle Communication Technology. 2014. Available online: https://www.its.dot.gov/factsheets/pdf/safetypilot_nhtsa_factsheet.pdf (accessed on 1 November 2021).
- Zhang, H.; Lu, X. Vehicle communication network in intelligent transportation system based on Internet of Things. Comput. Commun. 2020, 160, 799–806. [Google Scholar] [CrossRef]
- Transportation. Vehicle-to-Vehicle Communications: Readniess of V2V Technology for Applications. 2014. Available online: https://www.nhtsa.gov/sites/nhtsa.dot.gov/files/readiness-of-v2v-technology-for-application-812014.pdf (accessed on 27 November 2021).
- Xu, X.; Han, M.; Nagarajan, S.M.; Anandhan, P. Industrial Internet of Things for smart manufacturing applications using hierarchical trustful resource assignment. Comput. Commun. 2020, 160, 423–430. [Google Scholar] [CrossRef]
- Kumar, A.; Saha, R.; Alazab, M.; Kumar, G. A Lightweight Signcryption Method for Perception Layer in Internet-of-Things. J. Inf. Secur. Appl. 2020, 55, 102662. [Google Scholar] [CrossRef]
- Kushner, D. The Real Story of Stuxnet. 2013. Available online: https://spectrum.ieee.org/telecom/security/the-real-story-of-stuxnet (accessed on 27 November 2021).
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Future Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Tung, T.; Malek Ben Salem, A.H. Security for the Industrial Internet of Things. 2016. Available online: https://www.accenture.com/t20160823T035009Z__w__/ph-en/_acnmedia/PDF-28/Accenture-Security-Industrial-IoT-v3.pdf (accessed on 27 November 2021).
- Chen, T.M.; Abu-Nimeh, S. Lessons from Stuxnet. Computer 2011, 44, 91–93. [Google Scholar] [CrossRef]
- MindSphere, S. MindSphere: Enabling the World’s Industries to Drive Their Digital Transformations. 2017. Available online: https://www.plm.automation.siemens.com/media/global/en/Siemens-MindSphere-Whitepaper-69993_tcm27-29087.pdf (accessed on 27 November 2021).
- Gea, T.; Paradells, J.; Lamarca, M.; Roldán, D. Smart Cities as an Application of Internet of Things: Experiences and Lessons Learnt in Barcelona. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Taichung, Taiwan, 3–5 July 2013; pp. 552–557. [Google Scholar] [CrossRef]
- Jin, J.; Gubbi, J.; Marusic, S.; Palaniswami, M. An Information Framework for Creating a Smart City Through Internet of Things. IEEE Internet Things J. 2014, 1, 112–121. [Google Scholar] [CrossRef]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of Things for Smart Cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Pan, J.; Jain, R.; Paul, S.; Vu, T.; Saifullah, A.; Sha, M. An Internet of Things Framework for Smart Energy in Buildings: Designs, Prototype, and Experiments. IEEE Internet Things J. 2015, 2, 527–537. [Google Scholar] [CrossRef] [Green Version]
- Mohanty, S.P.; Choppali, U.; Kougianos, E. Everything you wanted to know about smart cities: The Internet of things is the backbone. IEEE Consum. Electron. Mag. 2016, 5, 60–70. [Google Scholar] [CrossRef]
- Acampora, G.; Cook, D.J.; Rashidi, P.; Vasilakos, A.V. A Survey on Ambient Intelligence in Health Care. Proc. IEEE Inst. Electr. Electron. Eng. 2013, 101, 2470–2494. [Google Scholar] [CrossRef] [Green Version]
- Wu, J.; Chou, D.; Jiang, J. The Virtual Environment of Things (VEoT): A Framework for Integrating Smart Things into Networked Virtual Environments. In Proceedings of the 2014 IEEE International Conference on Internet of Things (iThings), and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom), Taipei, Taiwan, 1–3 September 2014; pp. 456–459. [Google Scholar] [CrossRef]
- Hall, M.W.; Gil, Y.; Lucas, R.F. Self-Configuring Applications for Heterogeneous Systems: Program Composition and Optimization Using Cognitive Techniques. Proc. IEEE 2008, 96, 849–862. [Google Scholar] [CrossRef]
- Matsuda, M.; Hase, T. Self-configuring and auto-executing audio-visual system for consumer use. IEEE Trans. Consum. Electron. 2003, 49, 642–646. [Google Scholar] [CrossRef]
- Sheth, A. Internet of Things to Smart IoT Through Semantic, Cognitive, and Perceptual Computing. IEEE Intell. Syst. 2016, 31, 108–112. [Google Scholar] [CrossRef]
- Datta, S.K.; Bonnet, C. Describing things in the Internet of Things: From CoRE link format to semantic based descriptions. In Proceedings of the 2016 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Nantou, Taiwan, 27–29 May 2016; pp. 1–2. [Google Scholar] [CrossRef]
- Yu, J.; Kwon, S.; Kang, H.; Kim, S.; Bae, J.; Pyo, C. A Framework on Semantic Thing Retrieval Method in IoT and IoE Environment. In Proceedings of the 2018 International Conference on Platform Technology and Service (PlatCon), Jeju, Korea, 29–31 January 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Barnaghi, P.; Wang, W.; Henson, C.; Taylor, K. Semantics for the Internet of Things. Int. J. Semant. Web Inf. Syst. 2012, 8, 1–21. [Google Scholar] [CrossRef] [Green Version]
- Compton, M.; Barnaghi, P.; Bermudez, L.; García-Castro, R.; Corcho, O.; Cox, S.; Graybeal, J.; Hauswirth, M.; Henson, C.; Herzog, A.; et al. The SSN ontology of the W3C semantic sensor network incubator group. J. Web Semant. 2012, 17, 25–32. [Google Scholar] [CrossRef]
- Consortium, W.W.W. Efficient XML Interchange (EXI) Format 1.0 (Second Edition). 2014. Available online: https://www.w3.org/TR/exi/ (accessed on 27 November 2021).
- Rahman, H.; Hussain, M.I. A light-weight dynamic ontology for Internet of Things using machine learning technique. ICT Express 2021, 7, 355–360. [Google Scholar] [CrossRef]
- Padiya, T.; Bhise, M.; Rajkotiya, P. Data Management for Internet of Things. In Proceedings of the 2015 IEEE Region 10 Symposium, Macao, China, 1–4 November 2015; pp. 62–65. [Google Scholar] [CrossRef]
- Hasemann, H.; Kröller, A.; Pagel, M. RDF provisioning for the Internet of Things. In Proceedings of the 2012 3rd IEEE International Conference on the Internet of Things, Wuxi, China, 24–26 October 2012; pp. 143–150. [Google Scholar] [CrossRef]
- Maarala, A.I.; Su, X.; Riekki, J. Semantic Reasoning for Context-Aware Internet of Things Applications. IEEE Internet Things J. 2017, 4, 461–473. [Google Scholar] [CrossRef] [Green Version]
- Xu, C.; Wang, X. Transient content caching and updating with modified harmony search for Internet of Things. Digit. Commun. Netw. 2019, 5, 24–33. [Google Scholar] [CrossRef]
- Razzaque, M.A.; Milojevic-Jevric, M.; Palade, A.; Clarke, S. Middleware for Internet of Things: A Survey. IEEE Internet Things J. 2016, 3, 70–95. [Google Scholar] [CrossRef] [Green Version]
- Farahzadi, A.; Shams, P.; Rezazadeh, J.; Farahbakhsh, R. Middleware technologies for cloud of things: A survey. Digit. Commun. Netw. 2018, 4, 176–188. [Google Scholar] [CrossRef]
- Ali, O.; Ishak, M.K.; Bhatti, M.K.L. Internet of Things Security: Modelling Smart Industrial Thermostat for Threat Vectors and Common Vulnerabilities. In Intelligent Manufacturing and Mechatronics; Springer: Berlin/Heidelberg, Germany, 2021; pp. 175–186. [Google Scholar]
- Yao, X.; Farha, F.; Li, R.; Psychoula, I.; Chen, L.; Ning, H. Security and privacy issues of physical objects in the IoT: Challenges and opportunities. Digit. Commun. Netw. 2021, 7, 373–384. [Google Scholar] [CrossRef]
- Ngu, A.H.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, M.Z. IoT Middleware: A Survey on Issues and Enabling technologies. IEEE Internet Things J. 2016, 4, 1. [Google Scholar] [CrossRef]
- Fortino, G.; Guerrieri, A.; Russo, W.; Savaglio, C. Integration of agent-based and Cloud Computing for the smart objects-oriented IoT. In Proceedings of the 2014 IEEE 18th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Hsinchu, Taiwan, 21–23 May 2014; pp. 493–498. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Compton, M.; Christen, P.; Georgakopoulos, D. Semantic-Driven Configuration of Internet of Things Middleware. In Proceedings of the 2013 Ninth International Conference on Semantics, Knowledge and Grids, Beijing, China, 3–4 October 2013; pp. 66–73. [Google Scholar] [CrossRef] [Green Version]
- Conzon, D.; Bolognesi, T.; Brizzi, P.; Lotito, A.; Tomasi, R.; Spirito, M.A. The VIRTUS Middleware: An XMPP Based Architecture for Secure IoT Communications. In Proceedings of the 2012 21st International Conference on Computer Communications and Networks (ICCCN), Munich, Germany, 30 July–2 August 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Palade, A.; Cabrera, C.; White, G.; Razzaque, M.A.; Clarke, S. Middleware for Internet of Things: A quantitative evaluation in small scale. In Proceedings of the 2017 IEEE 18th International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), Macau, China, 12–15 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Autili, M.; Inverardi, P.; Tivoli, M. CHOREOS: Large scale choreographies for the future internet. In Proceedings of the 2014 Software Evolution Week—IEEE Conference on Software Maintenance, Reengineering, and Reverse Engineering (CSMR-WCRE), Antwerp, Belgium, 3–6 February 2014; pp. 391–394. [Google Scholar] [CrossRef]
- Rajagopalan, R.; Vishal Kelkar, D.M. Optimizing the Internet of Things: Key Strategies for Commercial Insurers. 2017. Available online: https://www.cognizant.com/whitepapers/optimizing-the-internet-of-things-key-strategies-for-commercial-insurers-codex2295.pdf (accessed on 27 November 2021).
- Ciccia, S.; Giordanengo, G.; Vecchi, G. Energy Efficiency in IoT Networks: Integration of Reconfigurable Antennas in Ultra Low-Power Radio Platforms Based on System-on-Chip. IEEE Internet Things J. 2019, 6, 6800–6810. [Google Scholar] [CrossRef]
- Adegbija, T.; Rogacs, A.; Patel, C.; Gordon-Ross, A. Microprocessor Optimizations for the Internet of Things: A Survey. IEEE Trans.-Comput.-Aided Des. Integr. Circuits Syst. 2018, 37, 7–20. [Google Scholar] [CrossRef] [Green Version]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Premsankar, G.; Francesco, M.D.; Taleb, T. Edge Computing for the Internet of Things: A Case Study. IEEE Internet Things J. 2018, 5, 1275–1284. [Google Scholar] [CrossRef] [Green Version]
- Chen, X.; Li, Z.; Chen, Y.; Wang, X. Performance Analysis and Uplink Scheduling for QoS-Aware NB-IoT Networks in Mobile Computing. IEEE Access 2019, 7, 44404–44415. [Google Scholar] [CrossRef]
- Morabito, R. Virtualization on Internet of Things Edge Devices with Container Technologies: A Performance Evaluation. IEEE Access 2017, 5, 8835–8850. [Google Scholar] [CrossRef]
- Jong, G.; Wang, Z.; Hsieh, K.S.; Hsieh, K.; Horng, G. A Novel Adaptive Optimization of Intragrated Network Topology and Transmission Path for IoT System. IEEE Sens. J. 2019, 19, 6452–6459. [Google Scholar] [CrossRef]
- Lundqvist, C.; Keränen, A.; Smeets, B.; Fornehed, J.; Azevedo, C.R.B.; von Wrycza, P. Massive IoT Devices: Key Technology Choices. 2019. Available online: https://www.ericsson.com/48f890/assets/local/publications/ericsson-technology-review/docs/2019/key-technology-choices-for-optimal-massive-iot-devices.pdf (accessed on 27 November 2021).
- Barcelo, M.; Correa, A.; Llorca, J.; Tulino, A.M.; Vicario, J.L.; Morell, A. IoT-Cloud Service Optimization in Next Generation Smart Environments. IEEE J. Sel. Areas Commun. 2016, 34, 4077–4090. [Google Scholar] [CrossRef]
- Ning, H.; Li, Y.; Shi, F.; Yang, L.T. Heterogeneous edge computing open platforms and tools for internet of things. Future Gener. Comput. Syst. 2020, 106, 67–76. [Google Scholar] [CrossRef]
- IIConsortium. OpenFog: Reference Architecture for Fog Computing. 2017. Available online: https://www.iiconsortium.org/pdf/OpenFog_Reference_Architecture_2_09_17.pdf (accessed on 27 November 2021).
- Fodor, G.; Dahlman, E.; Mildh, G.; Parkvall, S.; Reider, N.; Miklós, G.; Turányi, Z. Design aspects of network assisted device-to-device communications. IEEE Commun. Mag. 2012, 50, 170–177. [Google Scholar] [CrossRef]
- Hong, K.; Lillethun, D.; Ramachandran, U.; Ottenwälder, B.; Koldehofe, B. Mobile fog: A programming model for large-scale applications on the internet of things. In Proceedings of the Second ACM SIGCOMM Workshop on Mobile Cloud Computing, Hong Kong, China, 12–16 August 2013; pp. 15–20. [Google Scholar]
- Wang, T.; Zhang, G.; Liu, A.; Bhuiyan, M.Z.A.; Jin, Q. A Secure IoT Service Architecture With an Efficient Balance Dynamics Based on Cloud and Edge Computing. IEEE Internet Things J. 2019, 6, 4831–4843. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog Computing: A Platform for Internet of Things and Analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Springer International Publishing: Cham, Switzerland, 2014; pp. 169–186. [Google Scholar] [CrossRef]
- Lien, S.; Chen, K.; Lin, Y. Toward ubiquitous massive accesses in 3GPP machine-to-machine communications. IEEE Commun. Mag. 2011, 49, 66–74. [Google Scholar] [CrossRef]
- Yeow, W.L.; Westphal, C.; Kozat, U. Designing and embedding reliable virtual infrastructures. In Proceedings of the Second ACM SIGCOMM Workshop on Virtualized Infrastructure Systems and Architectures, New Delhi, India, 3 September 2010; pp. 33–40. [Google Scholar]
- Mehrotra, S.; Chen, H.; Jain, S.; Li, J.; Li, B.; Chen, M. Bandwidth management for mobile media delivery. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 1901–1907. [Google Scholar] [CrossRef] [Green Version]
- Wamser, F.; Zinner, T.; Tran-Gia, P.; Zhu, J. Dynamic bandwidth allocation for multiple network connections: Improving user QoE and network usage of YouTube in mobile broadband. In Proceedings of the 2014 ACM SIGCOMM Workshop on Capacity Sharing Workshop, Chicago, IL, USA, 18 August 2014; pp. 57–62. [Google Scholar]
- Salem, M.; Adinoyi, A.; Rahman, M.; Yanikomeroglu, H.; Falconer, D.; Kim, Y. Fairness-aware radio resource management in downlink OFDMA cellular relay networks. IEEE Trans. Wirel. Commun. 2010, 9, 1628–1639. [Google Scholar] [CrossRef]
- Niyato, D.; Wang, P.; Hossain, E.; Saad, W.; Han, Z. Game theoretic modeling of cooperation among service providers in mobile cloud computing environments. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference (WCNC), Paris, France, 1–4 April 2012; pp. 3128–3133. [Google Scholar] [CrossRef]
- Balakrishnan, H.; Rahul, H.S.; Seshan, S. An integrated congestion management architecture for Internet hosts. SIGCOMM Comput. Commun. Rev. 1999, 29, 175–187. [Google Scholar] [CrossRef]
- Aryafar, E.; Keshavarz-Haddad, A.; Wang, M.; Chiang, M. RAT selection games in HetNets. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 998–1006. [Google Scholar] [CrossRef]
- Wong, F.M.F.; Joe-Wong, C.; Ha, S.; Liu, Z.; Chiang, M. Mind your own bandwidth: An edge solution to peak-hour broadband congestion. arXiv 2013, arXiv:1312.7844. [Google Scholar]
- Im, Y.; Joe-Wong, C.; Ha, S.; Sen, S.; Kwon, T.T.; Chiang, M. AMUSE: Empowering Users for Cost-Aware Offloading with Throughput-Delay Tradeoffs. IEEE Trans. Mob. Comput. 2016, 15, 1062–1076. [Google Scholar] [CrossRef] [Green Version]
- Zhou, W. PSO based offloading strategy for cache-enabled mobile edge computing UAV networks. Phys. Commun. 2021, 99, 1–8. [Google Scholar]
- Zhou, W.; Chen, L.; Tang, S.; Lai, L.; Xia, J.; Zhou, F.; Fan, L. Offloading strategy with PSO for mobile edge computing based on cache mechanism. Clust. Comput. 2021, 24, 1–13. [Google Scholar] [CrossRef]
- Wang, L.; Kuo, G.G.S. Mathematical Modeling for Network Selection in Heterogeneous Wireless Networks—A Tutorial. IEEE Commun. Surv. Tutor. 2013, 15, 271–292. [Google Scholar] [CrossRef]
- Demirbas, M.; Yilmaz, Y.S.; Bulut, M.F. Eywa: Crowdsourced and cloudsourced omniscience. In Proceedings of the 2013 IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), San Diego, CA, USA, 18–22 March 2013; pp. 193–198. [Google Scholar] [CrossRef] [Green Version]
- Rula, J.P.; Navda, V.; Bustamante, F.E.; Bhagwan, R.; Guha, S. No “one-size fits all” towards a principled approach for incentives in mobile crowdsourcing. In Proceedings of the 15th Workshop on Mobile Computing Systems and Applications, Santa Barbara, CA, USA, 26–27 February 2014; pp. 1–5. [Google Scholar]
- Rula, J.; Bustamante, F.E. Crowd (soft) control: Moving beyond the opportunistic. In Proceedings of the Twelfth Workshop on Mobile Computing Systems & Applications, San Diego, CA, USA, 28–29 February 2012; pp. 1–6. [Google Scholar]
- Miluzzo, E.; Cornelius, C.T.; Ramaswamy, A.; Choudhury, T.; Liu, Z.; Campbell, A.T. Darwin phones: The evolution of sensing and inference on mobile phones. In Proceedings of the 8th International Conference on Mobile Systems, Applications, and Services, San Francisco, CA, USA, 15–18 June 2010; pp. 5–20. [Google Scholar]
- Pipes, S.; Chakraborty, S. Multitiered inference management architecture for participatory sensing. In Proceedings of the 2014 IEEE International Conference on Pervasive Computing and Communication Workshops (PERCOM WORKSHOPS), Budapest, Hungary, 24–28 March 2014; pp. 74–79. [Google Scholar] [CrossRef]
- Ibrahim, G.; Chadli, Y.; Kofman, D.; Ansiaux, A. Toward a new Telco role in future content distribution services. In Proceedings of the 2012 16th International Conference on Intelligence in Next Generation Networks, Berlin, Germany, 8–11 October 2012; pp. 22–29. [Google Scholar] [CrossRef] [Green Version]
- Saucez, D.; Barakat, C.; Turletti, T. Leveraging Information Centric Networking in Over-The-Top Services. 2012. Available online: https://hal.inria.fr/hal-00684458 (accessed on 27 November 2021).
- Li, S.; Zhang, Y.; Raychaudhuri, D.; Ravindran, R.; Zheng, Q.; Dong, L.; Wang, G. IoT Middleware Architecture over Information-Centric Network. In Proceedings of the 2015 IEEE Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015; pp. 1–7. [Google Scholar] [CrossRef]
- D’Ambrosio, M.; Dannewitz, C.; Karl, H.; Vercellone, V. MDHT: A hierarchical name resolution service for information-centric networks. In Proceedings of the ACM SIGCOMM Workshop on Information-Centric Networking, Toronto, ON, Canada, 19 August 2011; pp. 7–12. [Google Scholar]
- Peng, M.; Yan, S.; Zhang, K.; Wang, C. Fog-computing-based radio access networks: Issues and challenges. IEEE Netw. 2016, 30, 46–53. [Google Scholar] [CrossRef] [Green Version]
- Rachuri, K.K.; Efstratiou, C.; Leontiadis, I.; Mascolo, C.; Rentfrow, P.J. METIS: Exploring mobile phone sensing offloading for efficiently supporting social sensing applications. In Proceedings of the 2013 IEEE International Conference on Pervasive Computing and Communications (PerCom), San Diego, CA, USA, 18–22 March 2013; pp. 85–93. [Google Scholar] [CrossRef] [Green Version]
- Ren, S.; Schaar, M.v.d. Efficient Resource Provisioning and Rate Selection for Stream Mining in a Community Cloud. IEEE Trans. Multimed. 2013, 15, 723–734. [Google Scholar] [CrossRef]
- Li, Q.; Niu, H.; Papathanassiou, A.; Wu, G. Edge Cloud and Underlay Networks: Empowering 5G Cell-Less Wireless Architecture. In Proceedings of the European Wireless 2014; 20th European Wireless Conference, Barcelona, Spain, 14–16 May 2014; pp. 1–6. [Google Scholar]
- Kholghi, M.; Keyvanpour, M. An analytical framework for data stream mining techniques based on challenges and requirements. arXiv 2011, arXiv:1105.1950. [Google Scholar]
- Won, S.; Cho, I.; Sudusinghe, K.; Xu, J.; Zhang, Y.; van der Schaar, M.; Bhattacharyya, S.S. A Design Methodology for Distributed Adaptive Stream Mining Systems. Procedia Comput. Sci. 2013, 18, 2482–2491. [Google Scholar] [CrossRef] [Green Version]
- Madsen, H.; Burtschy, B.; Albeanu, G.; Popentiu-Vladicescu, F. Reliability in the utility computing era: Towards reliable Fog computing. In Proceedings of the 2013 20th International Conference on Systems, Signals and Image Processing (IWSSIP), Bucharest, Romania, 7–9 July 2013; pp. 43–46. [Google Scholar] [CrossRef]
- Stolfo, S.J.; Salem, M.B.; Keromytis, A.D. Fog Computing: Mitigating Insider Data Theft Attacks in the Cloud. In Proceedings of the 2012 IEEE Symposium on Security and Privacy Workshops, San Francisco, CA, USA, 20–23 May 2012; pp. 125–128. [Google Scholar] [CrossRef] [Green Version]
- Wang, C.; Chow, S.S.M.; Wang, Q.; Ren, K.; Lou, W. Privacy-Preserving Public Auditing for Secure Cloud Storage. IEEE Trans. Comput. 2013, 62, 362–375. [Google Scholar] [CrossRef] [Green Version]
- Lu, R.; Heung, K.; Lashkari, A.H.; Ghorbani, A.A. A Lightweight Privacy-Preserving Data Aggregation Scheme for Fog Computing-Enhanced IoT. IEEE Access 2017, 5, 3302–3312. [Google Scholar] [CrossRef]
- Sharma, P.K.; Chen, M.Y.; Park, J.H. A software defined fog node based distributed blockchain cloud architecture for IoT. IEEE Access 2017, 6, 115–124. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A Survey on Mobile Edge Computing: The Communication Perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef] [Green Version]
- Deng, R.; Lu, R.; Lai, C.; Luan, T.H.; Liang, H. Optimal Workload Allocation in Fog-Cloud Computing Towards Balanced Delay and Power Consumption. IEEE Internet Things J. 2016, 3, 1. [Google Scholar] [CrossRef]
- La, Q.D.; Ngo, M.V.; Dinh, T.Q.; Quek, T.Q.; Shin, H. Enabling intelligence in fog computing to achieve energy and latency reduction. Digit. Commun. Netw. 2019, 5, 3–9. [Google Scholar] [CrossRef]
- Park, S.H.; Simeone, O.; Shamai Shitz, S. Joint Optimization of Cloud and Edge Processing for Fog Radio Access Networks. IEEE Trans. Wirel. Commun. 2016, 15, 7621–7632. [Google Scholar] [CrossRef]
- Sun, X.; Ansari, N. EdgeIoT: Mobile Edge Computing for the Internet of Things. IEEE Commun. Mag. 2016, 54, 22–29. [Google Scholar] [CrossRef]
- Wen, Z.; Yang, R.; Garraghan, P.; Lin, T.; Xu, J.; Rovatsos, M. Fog Orchestration for Internet of Things Services. IEEE Internet Comput. 2017, 21, 16–24. [Google Scholar] [CrossRef] [Green Version]
- Li, J.; Jin, J.; Yuan, D.; Zhang, H. Virtual Fog: A Virtualization Enabled Fog Computing Framework for Internet of Things. IEEE Internet Things J. 2018, 5, 121–131. [Google Scholar] [CrossRef]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog Computing for the Internet of Things: Security and Privacy Issues. IEEE Internet Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S. The Fog computing paradigm: Scenarios and security issues. In Proceedings of the 2014 Federated Conference on Computer Science and Information Systems, Warsaw, Poland, 7–10 September 2014; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X.S. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2018, 20, 601–628. [Google Scholar] [CrossRef]

| Year | Article | Title | Major Contributions |
|---|---|---|---|
| 2021 | [18] | Internet of Things (IoT): A Review of Its Enabling Technologies in Healthcare Applications, Standards Protocols, Security, and Market Opportunities | Investigation of security, privacy, and Quality of Services (QoS) in IoT based healthcare applications. |
| 2021 | [19] | Blockchain for IoT-Based Healthcare: Background, Consensus, Platforms, and Use Cases | Investigation of a few methodologically presented use cases to demonstrate how key features of the IoT and blockchain can be used to support healthcare services and ecosystems. |
| 2021 | [20] | A Review of Wearable Internet-of-Things Device for Healthcare | A systematic literature review on smart wearables and its usage in an IoT health-care setting. |
| 2021 | [21] | Recent advances on IoT-assisted wearable sensor systems for healthcare monitoring | Detailed investigation of various IoT technologies that are used in wearable and health-care environments. |
| 2021 | [22] | Edge and fog computing for IoT: A survey on current research activities & future directions | Investigation of Edge–IoT architecture environment issues including scheduling, SDN/NFV, virtualization, and security. |
| 2021 | [8] | Emerging IoT domains, current standings and open research challenges: a review | A comprehensive survey on fast emerging IoT ecosystems that require technical advancements and technology integration. |
| 2021 | [23] | A Systematic Survey on the Role of Cloud, Fog, and Edge Computing Combination in Smart Agriculture | A systematic literature review focusing on IoT, Cloud, and Edge computing in Smart-Agriculture domain. |
| 2020 | [24] | Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios | An in-depth examination of IoT technology from a bird’s eye perspective, including statistical/architectural trends, use cases, challenges, and future prospects, as well as a link between 5G and IoT scenarios. |
| 2020 | [25] | Edge-computing architectures for internet of things applications: A survey | Classification of Edge–IoT networks based on orchestration, security, and big data perspective. |
| 2020 | [26] | Overview of Edge Computing in the Agricultural Internet of Things: Key Technologies, Applications, Challenges | Edge computing in the agricultural Internet of Things is examined, as well as the use of Edge computing in conjunction with Artificial Intelligence, Blockchain, and Virtual/Augmented Reality technology. |
| 2020 | [27] | Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future | Systematic research on IoT applications in sustainable environment, smart cities, e-health and AmI systems. |
| 2020 | [28] | IoT reliability: a review leading to 5 key research directions | An in-depth review for the quantification of data reliability and optimization in IoT. |
| 2019 | [29] | Intelligent positive computing with mobile, wearable, and IoT devices: Literature review and research directions | A conceptual framework for bridging the gap between IoT networks and next-generation computing services. |
| 2019 | [30] | Network optimizations in the Internet of Things: A review | State-of-the art literature survey to suggest network optimization in future IoT networks. |
| 2018 | [31] | A survey on the edge computing for the Internet of Things | Architecture-based investigation of Edge computing to enhance IoT performance |
| 2017 | [32] | Internet of things: architectures, protocols, and applications | A comprehensive literature review of IoT technologies, applications and implementation. In addition, the research provides a unique perspective in designing and optimizing future IoT systems. |
| Parameters | WiFi | WiMAX | LR-WPAN | Mobile | LoRa |
|---|---|---|---|---|---|
| Standard | IEEE 802.11 a/c/b/d/g/n | IEEE 802.16 | IEEE 802.15.4 (ZigBee) | 2G-GSM, CDMA, 3G-UMTS, CDMA 2000, 4G-LTE | LoRa WAN R1.0 |
| Frequency Band | 5–60 GHz | 2–66 GHz | 868/915 MHz, 2.4 GHz | 865 MHz, 2.4 GHz | 868/900 MHz |
| Data Rate | 1 Mb/s–6.75 Gb/s | 1 Mb/s–1 Gb/s(Fixed) 50–100 Mb/s (Mobile) | 40–250 Kb/s | 2G: 50–100 Kb/s 3G: 200 Kb/s 4G: 0.1–1 Gb/s | 0.3–50 Kb/s |
| Range | 20–100 m | <50 Km | 10–20 m | Entire Cellular Coverage | <30 Km |
| Energy Consumption | High | Medium | Low | Medium | Very Low |
| Cost | High | High | Low | Medium | High |
| Product | Module Cost | Frequency | Range | Data Rate |
|---|---|---|---|---|
| STM32WL55JCI6 | $11 | 150 MHz to 960 MHz | 10 Km | ~300 kbps |
| RFM95W | $50 | 430/868/915 MHz | ~100 Km | ~300 kbps |
| RFM95W | $8 | 430/868/915 MHz | ~60 Km | ~120 kbps |
| Sigfox S2-LP | $3 | 452 MHz–527 MHz, 904 MHz–1055 MHz | ~50 Km | ~500 kbps |
| CC2640P | $5 | 2.4 GHz | ~300 m | ~2 Mbps |
| DIGI XBEE-900HP | $50 | 900 MHz | ~5 Km | ~200 kbps |
| Contiki | TinyOS | RIOT | FreeRTOS | uClinux | Mbed | |
|---|---|---|---|---|---|---|
| Architecture | Monolithic | Monolithic | Microkernel RTOS | Microkernel RTOS | Monolithic | Monolithic |
| Programming Model | Event-driven, protothreads | Event-driven | Multi-threading | Multi-threading | Multi-threading | Event-driven, single thread |
| Process Scheduler | Cooperative | Cooperative | Preemptive, tickless | Preemptive, tickless | Preemptive | Preemptive |
| Programming Languages | C | nesC | C,C++ | C | C | C,C++ |
| Supported Hardware Platform | AVR, MSP 430, ARM Cortex, PIC-32 | AVR, MSP 430 | AVR, MSP 430, ARM Cortex-M, x86 | AVR, MSP 430, ARM, x86, 8052, Renesas | ARM 7, ARM Cortex-M | ARM Cortex-M |
| License | BSD | BSD | LGPLv2 | modified GPL | GPLv2 | Apache License 2.0 |
| Parameters | Arduino Uno Rev3 | Intel Galileo Gen 2 | Intel Edison | ESP8266 | BeagleBone X15 | Banana Pi BPI-P2 Zero | Raspberry Pi 4 B |
|---|---|---|---|---|---|---|---|
| Date Released | September 2010 | 10 July 2014 | Q3 2014 | August 2014 | November 2015 | July 2018 | June 2019 |
| Processor | ATmega 328 P | Intel Quark SoC X1000 | Intel Quark SoC X1000 | RISC based L106 32-bit | TI AM5728 2 × 1.5 GHz ARM Coretex-A15 2 × 700 MHz | H2 Quadcore Cortex-A7 | Broadcom SoC BCM 2711 |
| GPU | No | No | No | No | PowerVR Dual Core SGX544 | Mali 400 MP2 | Broadcom VideoCore VI |
| Clock Speed | 16 MHz | 400 MHz | 100 MHz | 80 MHz | 800 MHz | 800 MHz | 800 MHz |
| System Memory | 2 KB | 256 MB | 1 GB | 32 KB | 512 MB | 512 MB | 4 GB |
| Flash Memory | 32 KB | 8 MB | 4 GB | 80 KB | 4 GB | 8 GB | 4 GB |
| Communications | IEEE 802.11 (b/g/n), IEEE 802.15.4 433RF, BLE 4.0, Ethernet, Serial | IEEE 802.11 (b/g/n), IEEE 802.15.4 433RF, BLE 4.0, Ethernet, Serial | IEEE 802.11 (b/g/n), IEEE 802.15.4 433RF, BLE 4.0, Ethernet, Serial | IEEE 802.11 (b/g/n), IEEE 802.15.4 433RF, BLE 4.0 | IEEE 802.11 (b/g/n), IEEE 802.15.4, 433RF, BLE 4.0, Dual Gigabit Ethernet, Serial | IEEE 802.11 (b/g/n), IEEE 802.15.4 433RF, BLE 4.0, Ethernet, Serial | IEEE 802.11 (b/g/n/ac), IEEE 802.15.4 433RF, BLE 4.2, Ethernet, Serial |
| Development Environment | Arduino IDE | Arduino IDE | Arduino IDE, Eclipse, Intel XDK | Arduino, ESP Easy, Espruino | Arduino IDE, Eclipse, Cloud 9 IDE | NOOBS | NOOBS |
| I/O Connectivity | SPI, I2C, UART, GPIO | SPI, I2C, UART, GPIO | SPI, I2C, UART, I2S, GPIO | SPI, I2C, GPIO, UART | SPI, I2C, UART, I2S, GPIO, CAN Bus | SPI, I2C, UART, I2S, GPIO | SPI, DSI, UART, SDIO, CSI, GPIO |
| Programming Language | Wiring | Wiring, Wyliodrin | Wiring, C/C++, HTML5 | C/C++, Python, Ruby | C/C++, Debian, Python, Ruby, Java, Shell | C/C++, Python, Java | C/C++, Python, Java, Scratch |
| Approximate Cost | $20 | $70 | $50 | $4 | $270 | $30 | $35 |
| IoT Functional Elements | Standards/Technologies | |
|---|---|---|
| Identification | Naming | EPC, Code |
| Addressing | IPV4, IPV6 | |
| Sensing | RFID Tags, Smart Sensors, Wearable sensors, embedded sensors, Compact and Low power sensors, actuators and relay sensors | |
| Communication | RFID, NFC, UWB, NB-IoT, Bluetooth, BLE, IEEE 802.15.4, Z-Wave, WiFi, LTE-A, LoRa | |
| Compute | Hardware | Arduino, Raspberry Pi, Beaglebone, Banana Pi, Intel Galileo, Intel Edison, Node MCU, Smartphones and Smart sensors |
| Software | Operating Systems: (Windows 10 IoT), Raspbian, Contiki, TinyOS, LiteOS, Riot OS Cloud Solutions (NodeRed, NimBits, Azure IoT, IBM Watson, Kaa) | |
| Services | Identity-related (Logistics) Information Aggregation (Intelligent Transportation) Collaborative-aware (Self-driving cars) Ubiquitous (Smart cities) | |
| Semantics & Analytics | RDF, EN, JSON-LD, EXI |
| Parameter | Nature | Impact |
|---|---|---|
| Characteristics of IoT Infrastructure | ||
| Heterogeneity | Multi-vendor, multi-capability devices from low-cost to high-end, capable of performing heavy work | Making resources/environment dynamic, thus adding complexity for middleware to support interoperability |
| Resource Constraints | Small size, low power, small memory and computing capabilities | An additional challenge to implement the middleware software layer |
| Spontaneous Interaction | M2M communication, real-time event triggers | Automated, real-time, machine to machine interactions may require a system that is ubiquitous and requires no human intervention |
| Ultra large-scale Networks | Ultra-large number of events in multiples of billions every day | Event congestion, resource exhaustion, added data backups and event aggregation workload |
| Dynamic Network Conditions | Mesh, Ad-hoc, cellular networks or in some cases relay gateways for long-distance connectivity | Inadequate or disconnected network link outages may result in truncated, duplicated or lost data, which requires self-adjusting software to account for transmissions over such networks |
| Context-aware application | Spatial and temporal context from sensing nodes | Requires adaptive and autonomous behavior in software stack to analyze and interpret the data |
| Characteristics of IoT Applications | ||
| Diversity | Applications range from event-driven to time-driven IoT domains | Added complexity for middleware to adapt to different application deployments providing multiple services, such as: transportation and logistics, that deploy the same hardware but demand different services |
| Real-time | Applications range from mission critical to time-critical IoT domains | Real-time application deployments such as in health-care, would demand an added layer of reliability and data integrity |
| Security | Global connectivity versus open attack surface | Small computing capability, device and network heterogeneity and a provision for global access adds complexity for middleware to mitigate security threats |
| Privacy | Personal versus critical data | IoT applications may contain data from health-care, financial, internal stocks to industrial deployments. The data privacy acts vary from region to region, thus adding another complexity for middleware to provide flexibility to comply with data protection acts |
| Domains | Semantic Web & Web Services | Sensor Networks & RFID | Robotics | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Approach | Task Computing | Triple-Space Based | UBIWARE | SOA Approach | GSN | Fosstrack | TinyRest | Robotic-Based | ||
| Challenges Addressed | Interoperability | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | ||
| Scalability | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | |||||
| Abstraction | I/O Hardware Devices | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | ||||
| H/S Interfaces | 🗸 | 🗸 | 🗸 | |||||||
| Data Streams | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | ||
| Physicality | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | ||
| Development Process | 🗸 | 🗸 | 🗸 | 🗸 | ||||||
| Spontaneous Interaction | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | ||||
| Unfixed Infrastructure | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | ||||
| Multiplicity | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | 🗸 | ||||
| Security and Privacy | 🗸 | 🗸 | 🗸 | |||||||
| Platform | Technology | Addresses Security & Privacy? | Drawbacks |
|---|---|---|---|
| Service-based IoT Middleware | |||
| Hydra/LinkSmart | Web Services, XML, Symmetric Keys using Certificate Authority (CA) | Partially, by encrypting user data | Signed certificates for billions of devices is practically impossible. No policy-based access model. No secure user data storage |
| GSN | Access Control | Partially, by encryption and electronic signatures | High complexity implementation. Complex query and semantics operation on data streams. |
| OpenIoT | Message Digests, Public/Private Key Cryptography, Flexible access controls | Fully | Generic security framework model, which is very difficult to implement. No implementation details provided for third-party applications. |
| Virtus | XMPP, Event-driven communications, isolation of instances | Partially, by encryption at Transport Layer using TLS and Authentication by SASL protocol | Huge payloads. Increased entity versus digest bundles. |
| Cloud-based IoT Middleware | |||
| Webinos | Personal zones, Virtual user defined overlay networks | Partially, by de-coupling contextualized data, automatic filtering on personal data | Limited object access and identification outside overlay networks |
| ThingWorx | Query and Analysis based engine | Partially, by intelligent queries and innovative 3D data offloading | Enterprise mode. A limited number of devices can be attached, which further limits large-scale deployments of distributed networks. |
| Actor-based IoT Middleware | |||
| Node-Red | Server-side scripting, event-driven flow-based approach | None. Open access to IP and ports | Vulnerable to security threats as it only provides a programming interface and does not implement security. Can only be used as a visual programming interface for rapid prototyping |
| Platform/Service | Edge Solution |
|---|---|
| FogHorn | The power of machine learning and advanced cognitive analytics on-premise edge |
| Xnor.ai | Scaled machine learning and deep learning models for edge networks |
| SWIM | Consistent advanced real-time device-level analytics throughout edge and cloud |
| Pixeom | Software-Defined Edge computing platform that extends cloud functionalities to on-premise |
| Deeplite | Artificial Intelligence (AI) based deep neural network optimizer from cloud to edge |
| Hailo | Deep learning microchips for IoT edge and Fog devices |
| Always.ai | A platform for developing deep learning-based computer vision applications for edge solutions |
| Xi IoT | AI-driven processing and real-time analytics at the edge |
| Zededa | Edge virtualization service to provide Industrial IoT analytics |
| Project EVE | An open-source edge virtualization engine allowing cloud-native application development for Edge and IoT |
| Scope | Articles | Contributions & Impact on Edge Networks |
|---|---|---|
| Fog based IoT Architectures | [160] | The design approach to tackle resource management for underlying cellular networks |
| [161] | A high-level programming model supporting distributed, large scale fog applications | |
| [162] | Trust evaluation using service templates to incorporate cloud-edge computing | |
| [163] | Fog presence and its characteristics viability to support IoT services and vertical applications. | |
| [164] | M2M communications, challenges and solutions in the air interface | |
| Bandwidth & Resource Management on Physical (PHY) layer | [165] | Disaster recovery management design of reliable virtual infrastructures to support network nodes during physical outages |
| [166] | Bandwidth management and congestion control strategies for underlying communication links | |
| [167] | An Over-The-Top (OTT) virtual access network (VAN) architecture to support application-specific resource scheduling | |
| [168] | A centralized resource management scheme that is queue-aware to support fair scheduling and load-balancing | |
| [169] | Modeling of collective resource provisioning for mobile and cloud networks | |
| Network selection, deployment & configuration | [170] | A congestion avoidance architecture for adaptive applications |
| [171] | Hysteresis based selection and convergence of radio access technologies (RATs) | |
| [172] | Network bandwidth allocation based on applications as well as device priorities | |
| [173] | User traffic offloading based on cellular budget and future predictive usage. | |
| [174,175] | Proposed cache-replacement technique while offloading IoT data on to Edge networks for improved system latency. | |
| [176] | A mathematical model with multiple decision-making attributes for network selection | |
| Network Inference | [177] | A network inference vision that employs relevance over the choice approach to utilize cloud backed machine learning powers |
| [178] | An experimental study to outline and eliminate the human intervention in crowdsourcing applications improving inference | |
| [179] | Improving inferencing and associated network services by pairing network services with applications | |
| [180] | A framework to enable network inferencing from collaborative sensing and classification techniques for large scale mobile phone-based deployment | |
| [181] | An architecture to mask context-aware information in order to manage value Versus risk on sensor data | |
| Content Management | [182] | Provided a framework to extend Telco content delivery network (CDN) with enhanced and extended control plane for future edge applications |
| [183] | A framework to incorporate Content-Centric Networks (CCN) to empower the Over-The-Top (OTT) services in future IP networks | |
| [184] | Information-Centric Network (ICN) based IoT Middleware Architecture envisioning a unified IoT platform | |
| [185] | A distributed name resolution scheme for future Information-Centric Networks (ICN) | |
| [186] | An insight into software-defined network coupled with network functions virtualization for future Fog based networks | |
| Edge Analytics & Data Mining | [187] | A mobile sensing, efficient task distribution and adaptive platform that can be utilized on Edge networks |
| [188] | An adaptive cloud-based resource rate selection algorithm to support real-time stream mining applications on the edge | |
| [189] | An improved edge cloud framework model featuring virtualization, edge computing and local traffic offloading | |
| [190] | A comprehensive review of data stream mining challenges and available techniques | |
| [191] | A distributed dynamic data-driven mining scheme for adaptive edge vertical applications | |
| Security, Privacy & Trustworth- iness | [192] | An insight into the reliability aspect of the network extending from cloud to edge networks |
| [193] | A model framework based on offensive decoy to mitigate data attacks on the resident data in the cloud and fog networks | |
| [194] | Third-party auditing based public data integrity auditing scheme with no exposure to content in the clouds | |
| [195] | A light-weight privacy preservation data aggregation scheme for hybrid heterogeneous IoT based networks | |
| [196] | A distributed Block-chain based software-defined network architecture to run on Fog nodes |
| Scope | Articles | Major Contribution |
|---|---|---|
| Resource Management | [197] | Radio and Computational resource management in Mobile Edge Computing. Summarized MEC Models. Classification of Resource Management. |
| [198] | Workload allocation estimation between fog and cloud. Minimum power consumption versus service delays modeling. | |
| [199] | Device-driven and human-driven ML based intelligence schemes. Cross-layers optimization involving efficient MAC layer scheduling and fog data offloading. | |
| Access Networks | [186] | System architecture for F-Radio Access Networks (RANs). Edge caching, software-defined networking and network-function virtualization. |
| [200] | Model design of cache management in enhanced remote radios | |
| Networks: Management, Virtualization & Orchestration | [201] | Compute enabled Fog Nodes. Process and resources isolation using virtual machine Fog Node architecture. Inter and Intra Fog Nodes communication, VM migration and traffic minimization by software-defined core. |
| [202] | Models a Fog orchestration scenario for network functions. | |
| [203] | Virtual Fog framework to support Object and Network virtualization. | |
| Security & Privacy | [204] | The proposed model to revoke security certificates for improved privacy and security in IoT Networks. |
| [205] | Models a security attack on a Fog device. | |
| [206] | Security threats and solutions overview for Fog and IoT applications. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, O.; Ishak, M.K.; Bhatti, M.K.L.; Khan, I.; Kim, K.-I. A Comprehensive Review of Internet of Things: Technology Stack, Middlewares, and Fog/Edge Computing Interface. Sensors 2022, 22, 995. https://doi.org/10.3390/s22030995
Ali O, Ishak MK, Bhatti MKL, Khan I, Kim K-I. A Comprehensive Review of Internet of Things: Technology Stack, Middlewares, and Fog/Edge Computing Interface. Sensors. 2022; 22(3):995. https://doi.org/10.3390/s22030995
Chicago/Turabian StyleAli, Omer, Mohamad Khairi Ishak, Muhammad Kamran Liaquat Bhatti, Imran Khan, and Ki-Il Kim. 2022. "A Comprehensive Review of Internet of Things: Technology Stack, Middlewares, and Fog/Edge Computing Interface" Sensors 22, no. 3: 995. https://doi.org/10.3390/s22030995
APA StyleAli, O., Ishak, M. K., Bhatti, M. K. L., Khan, I., & Kim, K.-I. (2022). A Comprehensive Review of Internet of Things: Technology Stack, Middlewares, and Fog/Edge Computing Interface. Sensors, 22(3), 995. https://doi.org/10.3390/s22030995







