Optimal Cluster Head Selection in WSN with Convolutional Neural Network-Based Energy Level Prediction
Abstract
1. Introduction
1.1. Main Contribution
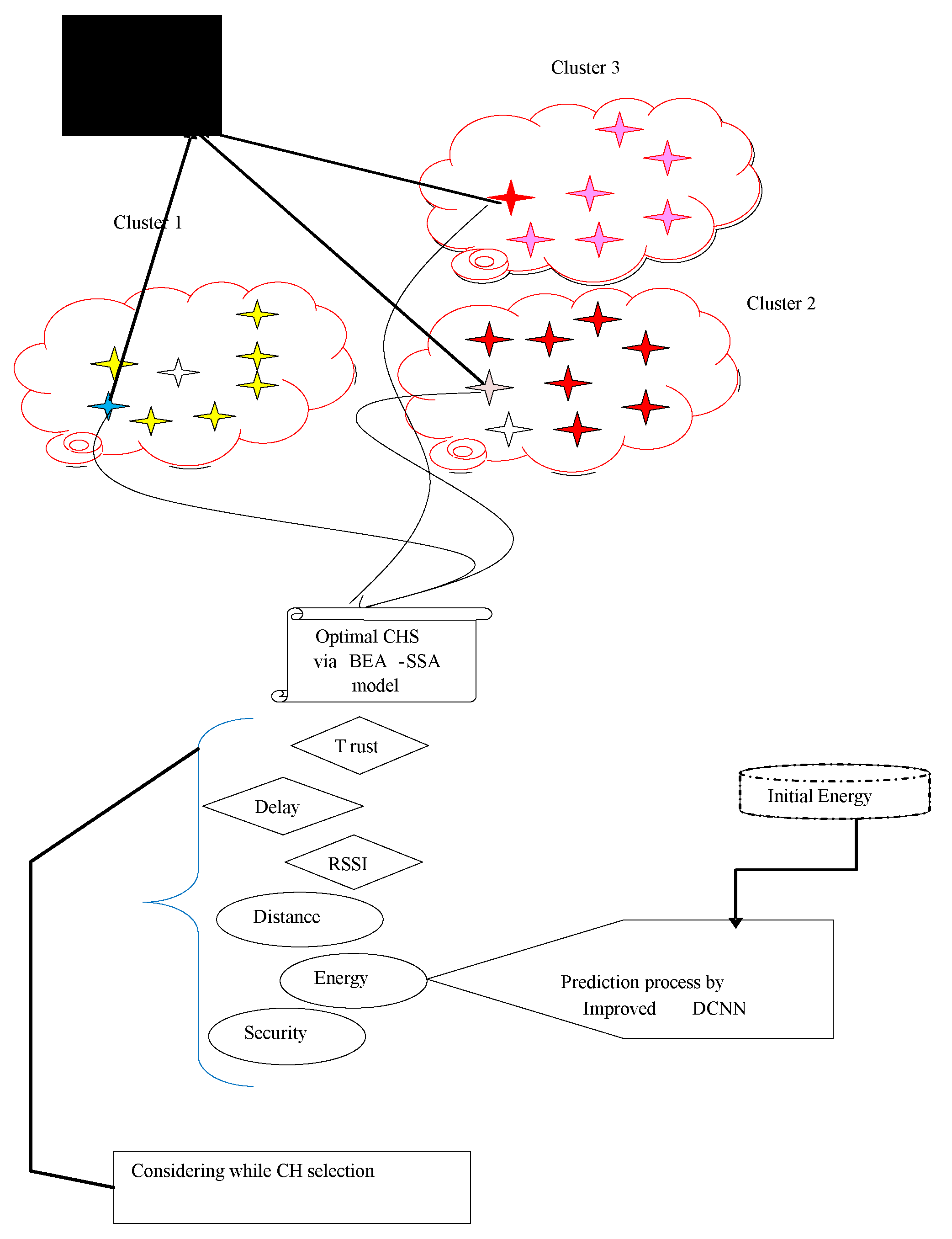
- A CHS model for safe and energy-conscious routing in WSNs has been created. Distance, energy, security (risk likelihood), latency, appraisal of trust (direct and indirect trust), and received signal strength indicators all favor CHS (RSSI).
- The proposed method predicts energy level using enhanced Deep Convolutional Neural Network (DCNN) to select the best CH in WSN. The BEA-SSA is used to select the best CH in the WSN. High RSSI, PDR, and residual energy are presented by the Bald Eagle Assisted SSA (BEA-SSA) model. The enhanced energy evaluation and prediction utilizing DCNN and the implemented BEA-SSA-based CHS are responsible for these improvements.
- The proposed cluster head selection process aids LEACH to preserve the network lifetime. The literature includes research that similarly aids LEACH. This paper presents an advanced approach that supports LEACH more effectively.
1.2. Organization
2. Literature Review
Related Works
| Algorithm 1. Pseudo-code of the Proposed Model. |
| Input: , Output: Optimal CH Choose the estimated energy of Update the energy by using Equation (7) Update the security by using Equation (14) Update the distance by using Equation (17) Update the delay by using Equation (18) Update the trust by using Equation (19) Update the RSSI by using Equation (20) The objective function is given in Equation (28) Solve for optimal cluster head End |
3. A Short Portrayal of the WSN Network
Network Model
4. Parameters for the Optimal Election of CH
- Energy;
- Security;
- Distance;
- Trust (direct and indirect);
- Path quality (reliability);
- Delay.
4.1. Energy Model
4.2. Security
4.3. Distance
4.4. Delay
4.5. Trust
4.6. RSSI
4.7. Objectives
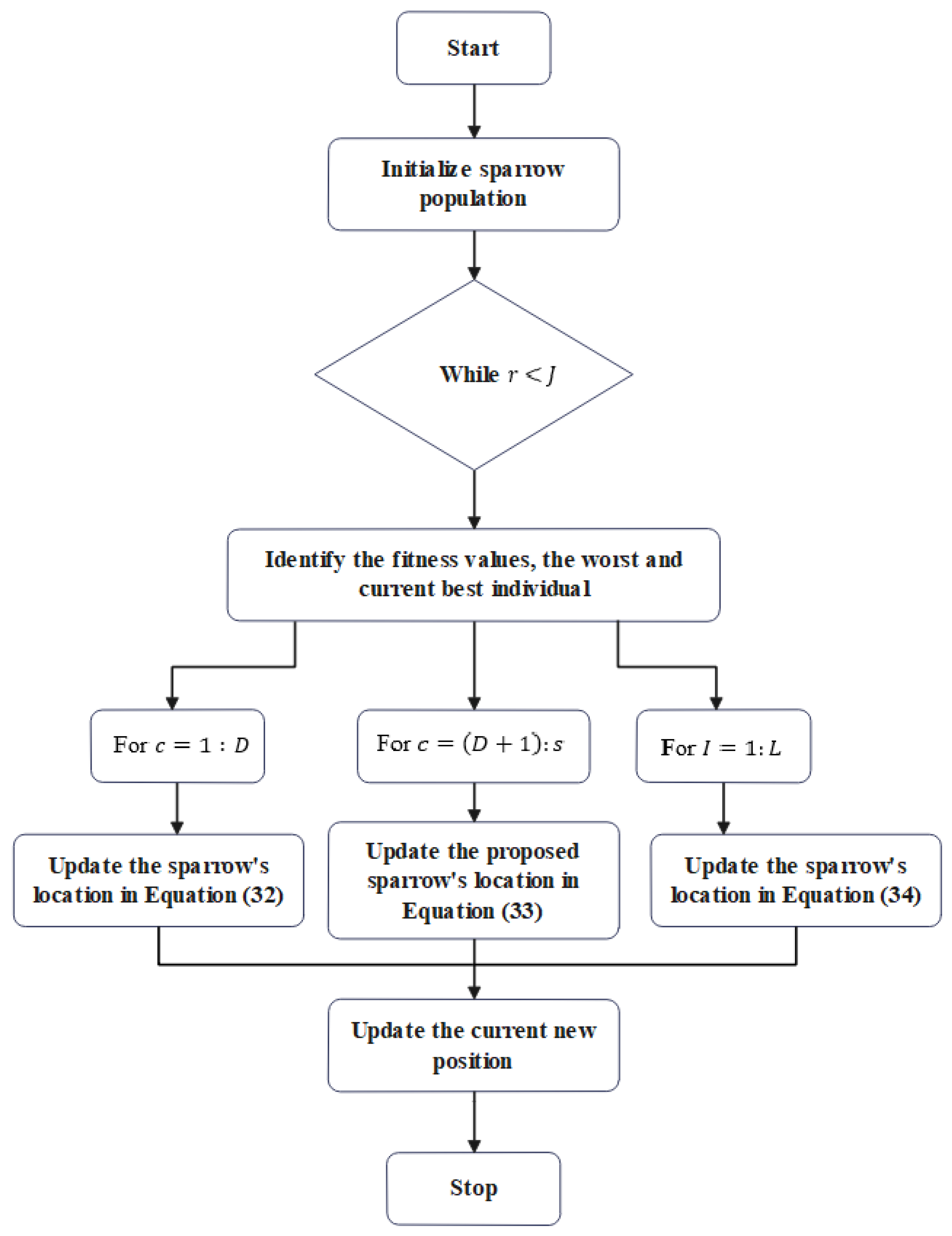
5. Developed BEA-SSA for Optimal CHS
Proposed BEA-SSA Model
- The producers usually have a significant amount of energy and give foraging locations or guidance to all scavengers. Further, it has the responsibility of locating places with abundant food supplies. The level of energy reserves is determined by an evaluation of the individuals’ fitness values.
- Individual sparrows begin to chirp as alarm messages as they detect the predator. When the alarm value exceeds the safety level, the producers must direct all scavengers to the safe zone.
- Every sparrow becomes a producer as much as it seeks out larger food sources; however, the proportion of scroungers and producers remains constant in the entire population.
- The producers would act as the sparrows with the maximum energy. Numerous starving scavengers are inclined to fly toward different locations in search of food to gain energy.
- Scroungers search for food by following the producer who can supply the healthiest food. Meanwhile, some scavengers might keep a close eye on the producers and fight for food to boost their predation rate.
- When the sparrows present at the group’s edge become aware of the danger, they swiftly move into the safe region to obtain a higher position, but the sparrows in the center of the group arbitrarily walk to be adjacent to others.
6. Results and Discussion
6.1. Simulation Procedure
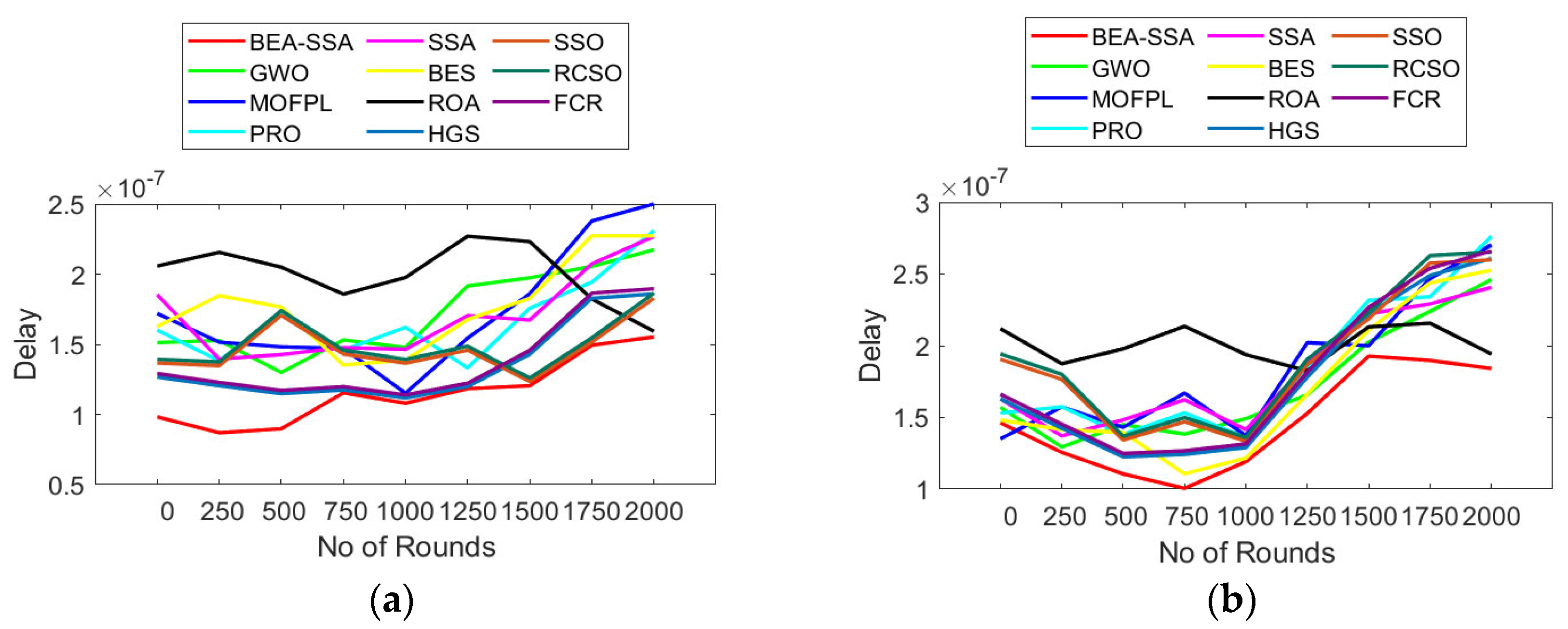
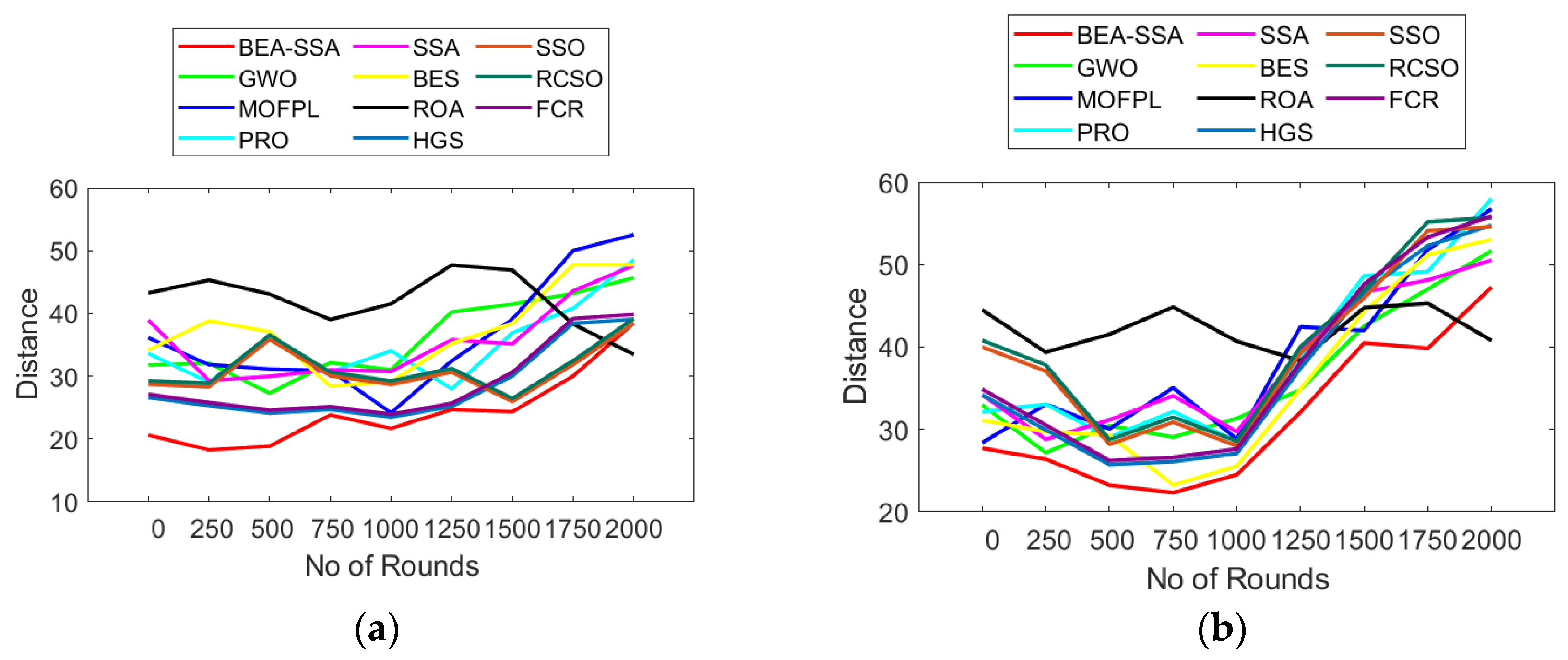
6.2. Analysis of Delay and Distance
6.3. Statistical Performance
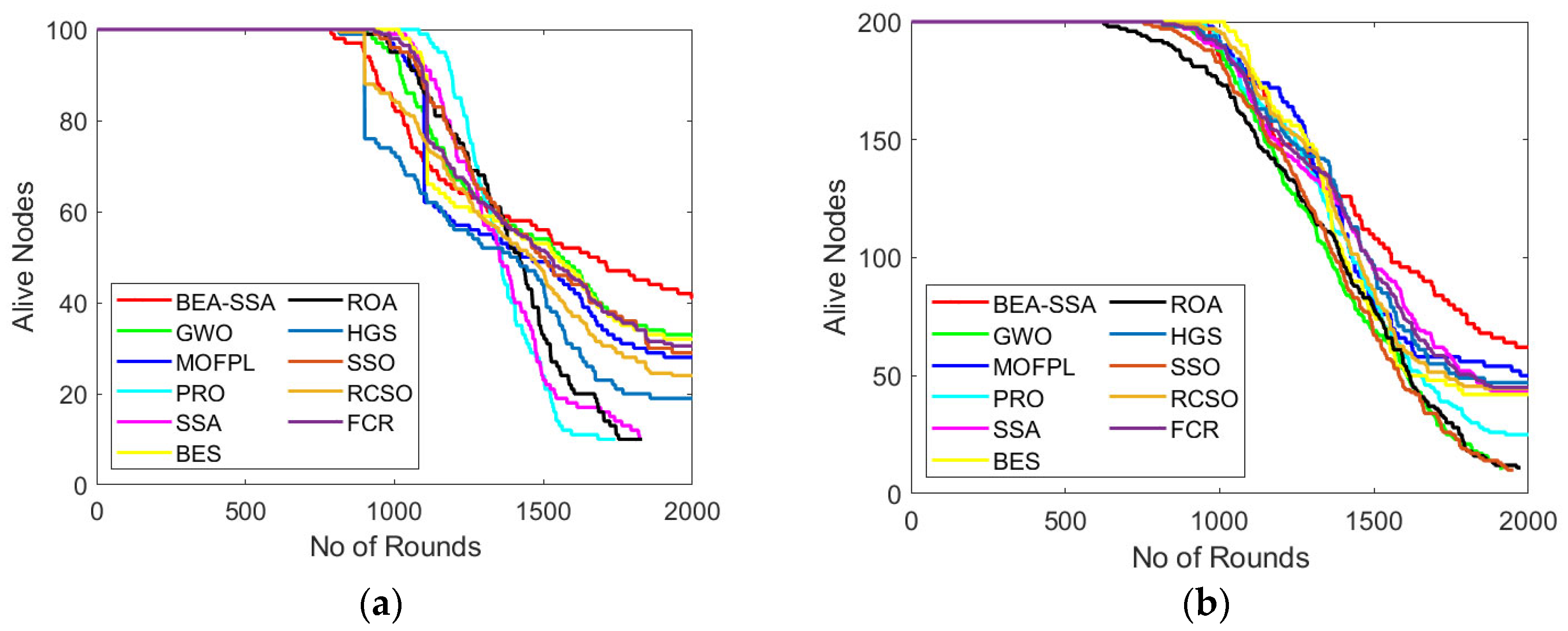
6.4. Analysis of Alive Nodes
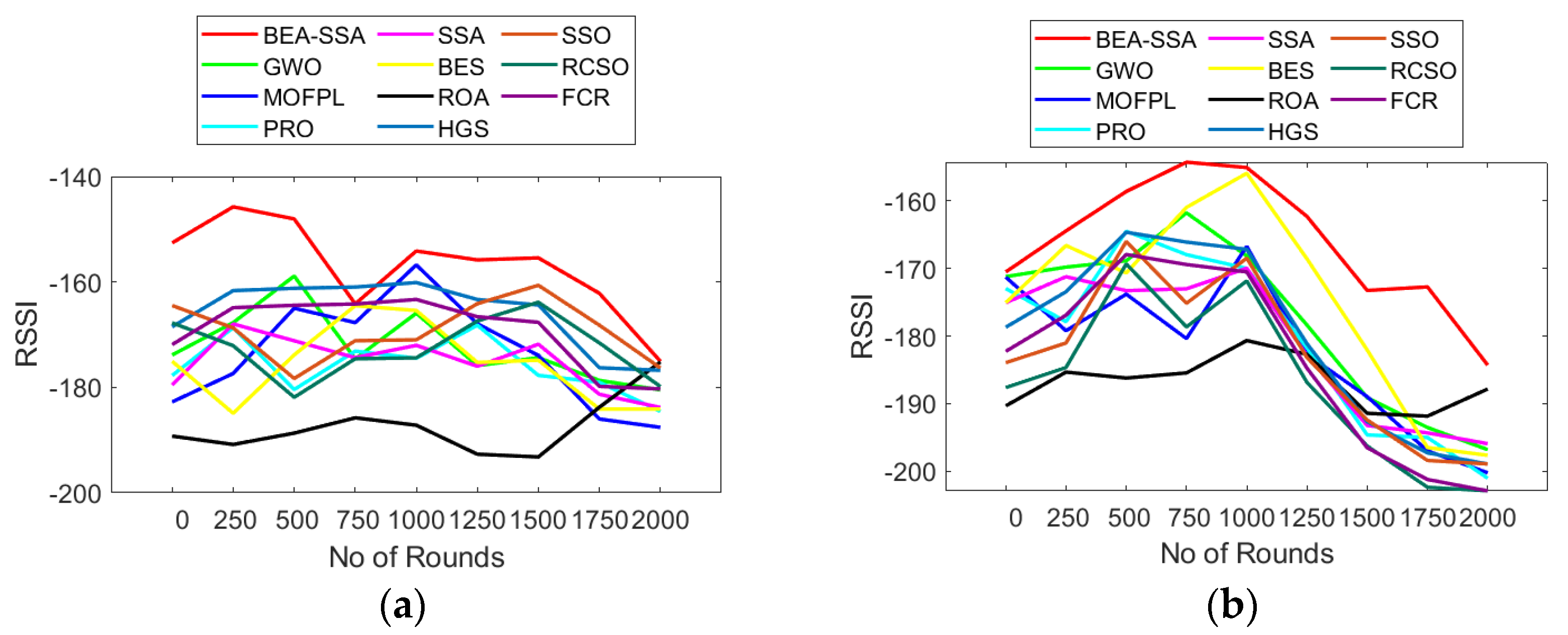
6.5. Analysis of Residual Energy, RSSI, and PDR
6.6. Convergence Analysis
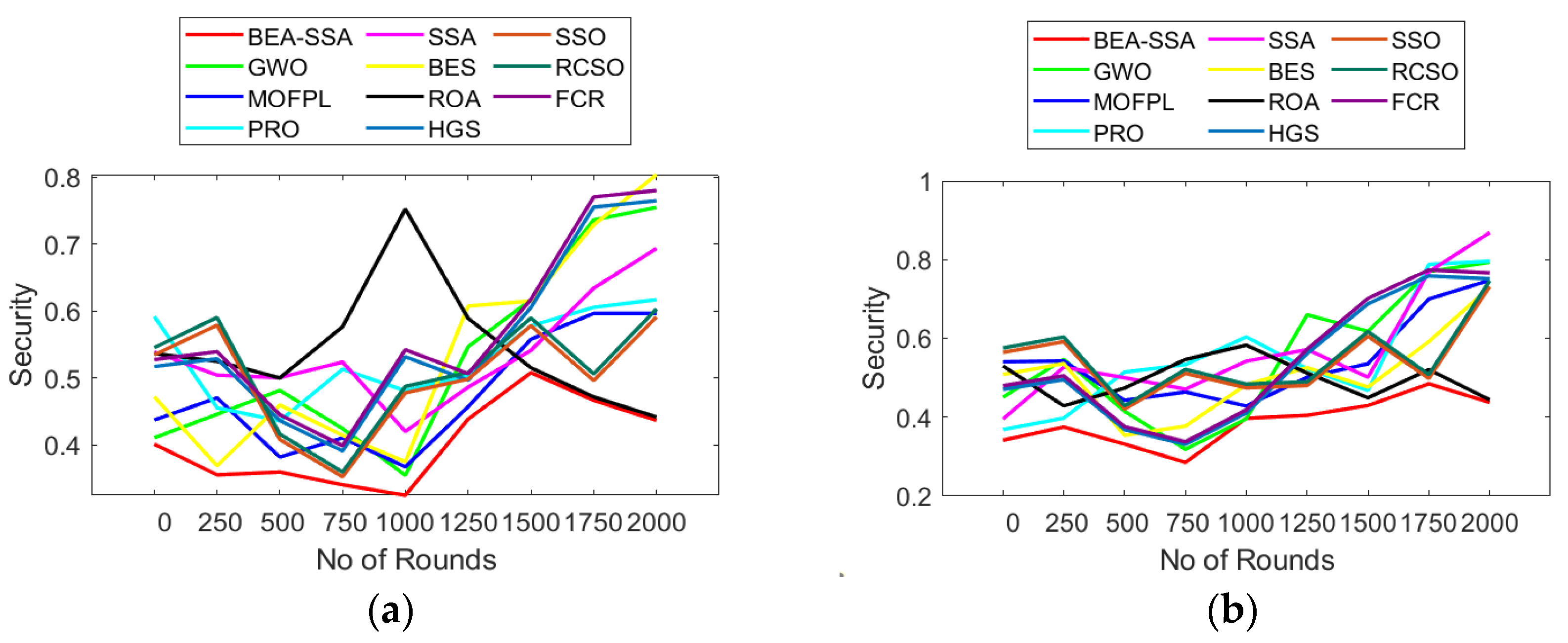
6.7. Analysis of Throughput, Trust, and Security
6.8. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Alagumuthukrishnan, S.; Geetha, K. A Locality Based Clustering and M-Ant Routing protocol for QoS in Wireless Semsor Networks. Dep. Sci. Eng. 2016, 6, 14. [Google Scholar]
- Yuvaraja, M.; Sabrigiriraj, M. Lifetime Enhancement of WSN using Energy-Balanced Distributed Clustering Algorithm with Honey Bee Optimization. Asian J. Res. Soc. Sci. Humanit. 2016, 6, 11. [Google Scholar] [CrossRef]
- Ni, Q.; Pan, Q.; Du, H.; Cao, C.; Zhai, Y. A Novel Cluster Head Selection Algorithm Based on Fuzzy Clustering and Particle Swarm Optimization. IEEE/ACM Trans. Comput. Biol. Bioinform. 2017, 4, 76–84. [Google Scholar] [CrossRef] [PubMed]
- Kang, S.H.; Nguyen, T. Distance Based Thresholds for Cluster Head Selection in Wireless Sensor Networks. IEEE Commun. Lett. 2012, 16, 1396–1399. [Google Scholar] [CrossRef]
- Leu, J.; Chiang, T.; Yu, M.; Su, K. Energy Efficient Clustering Scheme for Prolonging the Lifetime of Wireless Sensor Network with Isolated Nodes. IEEE Commun. Lett. 2015, 19, 259–262. [Google Scholar] [CrossRef]
- Sumathi, J.; Velusamy, R.L. A review on distributed cluster-based routing approaches in mobile wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 835–849. [Google Scholar] [CrossRef]
- Jin, W.; Cao, Y.; Li, B.; Kim, H.; Lee, S. Particle swarm optimization-based clustering algorithm with mobile sink for WSNs. Future Gener. Comput. Syst. 2017, 76, 452–457. [Google Scholar]
- Shishupal, K.; Lal, N.; Chaurasiya, V.K. A forwarding strategy based on ANFIS in internet-of-things-oriented wireless sensor network (WSN) using a novel fuzzy-based cluster head protocol. Ann. Telecommun. 2018, 73, 627–638. [Google Scholar]
- Jia, D.; Zhu, H.; Zou, S.; Hu, P. Dynamic Cluster Head Selection Method for Wireless Sensor Network. IEEE Sens. J. 2016, 16, 2746–2754. [Google Scholar] [CrossRef]
- Mehra, P.S.; Doja, M.N.; Alam, B. Fuzzy based enhanced cluster head selection (FBECS) for WSN. J. King Saud Univ.-Sci. 2020, 32, 390–401. [Google Scholar] [CrossRef]
- Sara, A.; Ouni, R. Reliable and energy-efficient multi-hop LEACH-based clustering protocol for wireless sensor networks. Sustain. Comput. Inform. Syst. 2018, 20, 1–13. [Google Scholar]
- Nigam, G.K.; Dabas, C. ESO-LEACH: PSO based energy efficient clustering in LEACH. J. King Saud Univ.-Comput. Inf. Sci. 2021, 33, 947–954. [Google Scholar] [CrossRef]
- Priyadarshini, R.R.; Sivakumar, N. Cluster head selection based on Minimum Connected Dominating Set and Bi-Partite inspired methodology for energy conservation in WSNs. J. King Saud Univ.-Comput. Inf. Sci. 2018, 33, 1132–1144. [Google Scholar] [CrossRef]
- Daanoune, I.; Abdennaceur, B.; Ballouk, A. A comprehensive survey on LEACH-based clustering routing protocols in Wireless Sensor Networks. Ad Hoc Netw. 2021, 114, 102409. [Google Scholar] [CrossRef]
- Mahajan, S.; Malhotra, J.; Sharma, S. An energy balanced QoS based cluster head selection strategy for WSN. Egypt. Inform. J. 2014, 15, 189–199. [Google Scholar] [CrossRef]
- Muthukumaran, K.; Chitra, K.; Selvakumar, C. An energy efficient clustering scheme using multilevel routing for wireless sensor network. Comput. Electr. Eng. 2018, 69, 642–652. [Google Scholar]
- Darabkh, K.A.; Odetallah, S.M.; Al-qudah, Z.; Khalifeh, A.F.; Shurman, M.M. Energy-Aware and Density-Based Clustering and Relaying Protocol (EA-DB-CRP) for gathering data in wireless sensor networks. Appl. Soft Comput. 2019, 80, 154–166. [Google Scholar] [CrossRef]
- Kannan, G.; Raja, T.S.R. Energy efficient distributed cluster head scheduling scheme for two tiered wireless sensor network. Egypt. Inform. J. 2015, 16, 167–174. [Google Scholar] [CrossRef]
- Palvinder, S.M.; Singh, S. Improved metaheuristic based energy-efficient clustering protocol for wireless sensor networks. Eng. Appl. Artif. Intell. 2017, 57, 142–152. [Google Scholar]
- Sarkar, A.; Murugan, T.S. Analysis on dual algorithms for optimal cluster head selection in wireless sensor network. Evol. Intel. 2022, 15, 1471–1485. [Google Scholar] [CrossRef]
- Shyjith, M.B.; Maheswaran, C.P.; Reshma, V.K. Optimized and Dynamic Selection of Cluster Head Using Energy Efficient Routing Protocol in WSN. Wirel. Pers Commun 2021, 116, 577–599. [Google Scholar] [CrossRef]
- Bhardwaj, R.; Kumar, D. MOFPL: Multi-objective fractional particle lion algorithm for the energy aware routing in the WSN. Pervasive Mob. Comput. 2019, 58, 101029. [Google Scholar] [CrossRef]
- Augustine, S.; Ananth, J.P. Taylor kernel fuzzy C-means clustering algorithm for trust and energy-aware cluster head selection in wireless sensor networks. Wirel. Netw 2020, 26, 5113–5132. [Google Scholar] [CrossRef]
- Goswami, P.; Yan, Z.; Mukherjee, A.; Yang, L.; Routray, S.; Palai, G. An energy efficient clustering using firefly and HML for optical wireless sensor network. Optik 2019, 182, 181–185. [Google Scholar] [CrossRef]
- Toor, A.S.; Jain, A.K. Energy Aware Cluster Based Multi-hop Energy Efficient Routing Protocol using Multiple Mobile Nodes (MEACBM) in Wireless Sensor Networks. AEU-Int. J. Electron. Commun. 2019, 102, 41–53. [Google Scholar] [CrossRef]
- Daneshvar, S.M.M.H.; Mohajer, P.A.A.; Mazinani, S.M. Energy-Efficient Routing in WSN: A Centralized Cluster-Based Approach via Grey Wolf Optimizer. IEEE Access 2019, 7, 170019–170031. [Google Scholar] [CrossRef]
- Maheshwari, P.; Sharma, A.K.; Verma, K. Energy efficient cluster based routing protocol for WSN using butterfly optimization algorithm and ant colony optimization. Ad Hoc Netw. 2020, 110, 102317. [Google Scholar] [CrossRef]
- Sanhaji, F.; Satori, H.; Satori, K. Cluster head selection based on neural networks in wireless sensor networks. In Proceedings of the 2019 International Conference on Wireless Technologies, Embedded and Intelligent Systems (WITS), Fez, Morocco, 3–4 April 2019. [Google Scholar]
- Krishnaraj, N. Selection of Cluster Head in Wireless Sensor Network using Convolution Neural Network Algorithm. IRO J. Sustain. Wirel. Syst. 2022, 4, 46–54. [Google Scholar] [CrossRef]
- Kumar, M.; Mukherjee, P.; Verma, K.; Verma, S.; Rawat, D.B. Improved Deep Convolutional Neural Network Based Malicious Node Detection and Energy-Efficient Data Transmission in Wireless Sensor Networks. IEEE Trans. Netw. Sci. Eng. 2021, 9, 3272–3281. [Google Scholar] [CrossRef]
- Gul, O.M.; Erkmen, A.M.; Kantarci, B. UAV-Driven Sustainable and Quality-Aware Data Collection in Robotic Wireless Sensor Networks. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Gul, O.M.; Erkmen, A.M. Energy-efficient cluster-based data collection by a UAV with a limited-capacity battery in robotic wireless sensor networks. Sensors 2020, 20, 5865. [Google Scholar] [CrossRef] [PubMed]
- Shankar, A.; Jaisankar, N.; Khan, M.S.; Patan, R.; Balamurugan, B. Hybrid model for security-aware cluster head selection in wireless sensor networks. IET Wirel. Sens. Syst. 2019, 9, 68–76. [Google Scholar] [CrossRef]
- Celik, E.; Olson, E.; Titi, E.S. Spectral Filtering of Interpolant Observables for a Discrete-in-Time Downscaling Data Assimilation Algorithm. SIAM J. Appl. Dyn. Syst. 2019, 18, 1118–1142. [Google Scholar] [CrossRef]
- Ivanic, M.; Mezei, I. Distance Estimation Based on RSSI Improvements of Orientation Aware Nodes. In Proceedings of the 2018 Zooming Innovation in Consumer Technologies Conference (ZINC), Novi Sad, Serbia, 30–31 May 2018; pp. 140–143. [Google Scholar] [CrossRef]
- Xue, J.; Shen, B. A novel swarm intelligence optimization approach: Sparrow search algorithm. Syst. Sci. Control Eng. 2020, 8, 22–34. [Google Scholar] [CrossRef]
- Alsattar, H.A.; Zaidan, A.A.; Zaidan, B.B. Novel meta-heuristic bald eagle search optimisation algorithm. ArtifIntell. Rev. 2020, 53, 2237–2264. [Google Scholar] [CrossRef]
- Marsaline Beno, M.; Valarmathi, I.R.; Swamy, S.M.; Rajakumar, B.R. Threshold prediction for segmenting tumour from brain MRI scans. Int. J. Imaging Syst. Technol. 2014, 24, 129–137. [Google Scholar] [CrossRef]
- Renjith, T.; Rangachar, M.J.S. Hybrid Optimization based DBN for Face Recognition using Low-Resolution Images. Multimed. Res. 2018, 1, 33–43. [Google Scholar]
- Devagnanam, J.; Elango, N.M. Optimal Resource Allocation of Cluster using Hybrid Grey Wolf and Cuckoo Search Algorithm in Cloud Computing. J. Netw. Commun. Syst. 2020, 3, 31–40. [Google Scholar]
- Shareef, S.M.; Rao, D.R. A Hybrid Learning Algorithm for Optimal Reactive Power Dispatch under Unbalanced Conditions. J. Comput. Mech. Power Syst. Control 2018, 1, 26–33. [Google Scholar]
- Khan, F.; Zahid, M.; Gürüler, H.; Tarımer, İ.; Whangbo, T. An Efficient and Reliable Multicasting for Smart Cities. Comput. Mater. Contin. 2022, 72, 663–678. [Google Scholar] [CrossRef]
- Khan, F.; Ahmad, S.; Gürüler, H.; Cetin, G.; Whangbo, T.; Kim, C.-G. An Efficient and Reliable Algorithm for Wireless Sensor Network. Sensors 2021, 21, 8355. [Google Scholar] [CrossRef] [PubMed]
- Tay, M.; Senturk, A. A New Energy-Aware Cluster Head Selection Algorithm for Wireless Sensor Networks. Wirel. Pers. Commun. 2022, 122, 2235–2251. [Google Scholar] [CrossRef]






| Author | Proposed Method | Features | Challenges |
|---|---|---|---|
| Amit al. [20] | FCR | High delay High EE | Computational time needs to be analyzed |
| Shyjith et al. [21] | RCSO | Less delay Higher throughput | Should consider cost metrics |
| Reeta and Dinesh [22] | MOFPL | Lesser time Higher network energy | Need to compute cost efficiency |
| Augustine and Ananth [23] | Taylor KFCM model | High energy and throughput Least delay | No concern about practical experimentation |
| Goswamiet al. [24] | FF | Negligible cost function Enhanced EE | Endures from local searching issues |
| Toor and Jain [25] | MEACBM | Minimal energy employment Amplified throughput | No concern about Scalability |
| Daneshvar et al. [26] | GWO | Lower energy utilization Higher network lifespan | No concern about Fault tolerance. |
| Prachi et al. [27] Sanhaji et al. [28] Krishna et al. [29] Kumar et al. [30] Gul et al. [31] Gul et al. [32] | BOA & ACO LEACH Neural Network IDCNN Cluster head Selection Cluster head Selection | High alive nodes Less energy deployment Delay is reduced Loss is also reduced Energy consumption is reduced Throughput is high The energy utilization is low The life span is increased The cost is reduced The energy consumption is reduced | Should deliberate fault tolerance Need to consider the time analysis The experimental result should be considered Need to consider the Stability analysis Need to consider the Scalability analysis The quantity and accuracy of data from various CH robots may vary |
| Symbols | Description |
|---|---|
| Initial Energy | |
| Electronic Energy | |
| Data time aggregation | |
| Distance | |
| Threshold energy | |
| Energy of power allocation | |
| Requisite Energy | |
| Energy for idle state | |
| Energy Cost | |
| Predicted Value | |
| Actual values | |
| Geometric Mean |
| Parameter | Value |
|---|---|
| Path construction | 100 × 100 m2 |
| Sink node location | (50,50)-i.e., center of the node |
| Count of nodes | 100 |
| Initial energy | 0.5 J |
| Transmission energy | 50 nJ |
| Reception energy | 50 nJ |
| Electric energy | 50 nJ |
| Transmit amplifier type | 10 × 10−12 |
| Amplifier energy | 0.0013 |
| Data aggregation energy | 5 nJ |
| Count of rounds | 2000 |
| Data packet size | 4000 |
| PDR | 0.96 to 1 |
| Security | 0 to 5 |
| Metrics | BEA-SSA | GWO [26] | MOFPL [22] | PRO | SSA | BES | ROA | HGS | SSO | RCSO [21] | FCR [20] |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Best | 0.007 | 0.001 | 0.009 | 0.002 | 0.003 | 0.002 | 0.001 | 0.003 | 0.002 | 0.002 | 0.002 |
| Worst | 0.597 | 0.597 | 0.598 | 0.598 | 0.598 | 0.598 | 0.598 | 0.598 | 0.597 | 0.597 | 0.597 |
| Mean | 0.220 | 0.211 | 0.209 | 0.237 | 0.228 | 0.208 | 0.229 | 0.213 | 0.214 | 0.213 | 0.211 |
| Median | 0.170 | 0.159 | 0.161 | 0.217 | 0.196 | 0.158 | 0.199 | 0.167 | 0.167 | 0.167 | 0.162 |
| STD | 0.187 | 0.193 | 0.195 | 0.194 | 0.193 | 0.196 | 0.192 | 0.192 | 0.192 | 0.192 | 0.194 |
| Metrics | BEA-SSA | GWO [26] | MOFPL [22] | PRO | SSA | BES | ROA | HGS | SSO | RCSO [21] | FCR [20] |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Best | 0.009 | 5.430 | 0.0003 | 1.349 | 0.002 | 1.780 | 1.950 | 0.001 | 1.610 | 0.001 | 0.007 |
| Worst | 0.598 | 0.597 | 0.597 | 0.597 | 0.597 | 0.597 | 0.598 | 0.598 | 0.598 | 0.598 | 0.598 |
| Mean | 0.223 | 0.223 | 0.213 | 0.212 | 0.213 | 0.214 | 0.217 | 0.215 | 0.219 | 0.214 | 0.214 |
| Median | 0.175 | 0.184 | 0.165 | 0.165 | 0.166 | 0.166 | 0.173 | 0.167 | 0.177 | 0.167 | 0.166 |
| STD | 0.187 | 0.190 | 0.192 | 0.193 | 0.192 | 0.191 | 0.191 | 0.190 | 0.192 | 0.191 | 0.192 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gurumoorthy, S.; Subhash, P.; Pérez de Prado, R.; Wozniak, M. Optimal Cluster Head Selection in WSN with Convolutional Neural Network-Based Energy Level Prediction. Sensors 2022, 22, 9921. https://doi.org/10.3390/s22249921
Gurumoorthy S, Subhash P, Pérez de Prado R, Wozniak M. Optimal Cluster Head Selection in WSN with Convolutional Neural Network-Based Energy Level Prediction. Sensors. 2022; 22(24):9921. https://doi.org/10.3390/s22249921
Chicago/Turabian StyleGurumoorthy, Sasikumar, Parimella Subhash, Rocio Pérez de Prado, and Marcin Wozniak. 2022. "Optimal Cluster Head Selection in WSN with Convolutional Neural Network-Based Energy Level Prediction" Sensors 22, no. 24: 9921. https://doi.org/10.3390/s22249921
APA StyleGurumoorthy, S., Subhash, P., Pérez de Prado, R., & Wozniak, M. (2022). Optimal Cluster Head Selection in WSN with Convolutional Neural Network-Based Energy Level Prediction. Sensors, 22(24), 9921. https://doi.org/10.3390/s22249921







