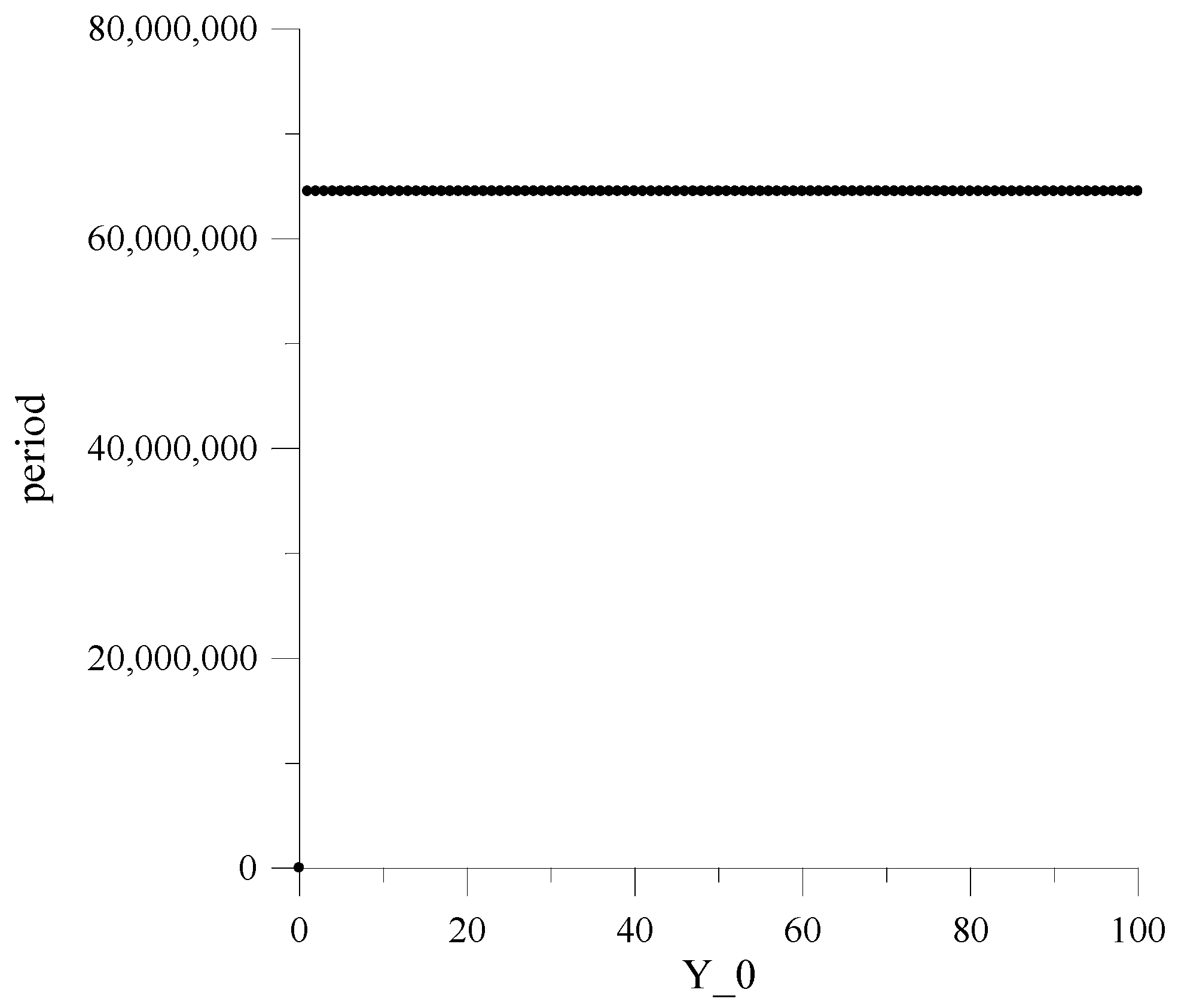Abstract
Random and pseudo-random number and bit sequence generators with a uniform distribution law are the most widespread and in demand in the market of pseudo-random generators. Depending on the specific field of application, the requirements for their implementation and the quality of the generator’s output sequence change. In this article, we have optimized the structures of the classical additive Fibonacci generator and the modified additive Fibonacci generator when they work together. The ranges of initial settings of structural elements (seed) of these generators have been determined, which guarantee acceptable statistical characteristics of the output pseudo-random sequence, significantly expanding the scope of their possible application, including cybersecurity. When studying the statistical characteristics of the modified additive Fibonacci generator, it was found that they significantly depend on the signal from the output of the logic circuit entering the structure. It is proved that acceptable statistical characteristics of the modified additive Fibonacci generator, and the combined generator realized on its basis, are provided at odd values of the module of the recurrent equation describing the work of such generator. The output signal of the combined generator has acceptable characteristics for a wide range of values of the initial settings for the modified additive Fibonacci generator and the classic additive Fibonacci generator. Regarding the use of information security, it is worth noting the fact that for modern encryption and security programs, generators of random numbers and bit sequences and approaches to their construction are crucial and critical.
1. Introduction
Pseudo-random number (PRNG) and bit sequence (PRBSG) generators, in general, pseudo-random sequence generators (PRSG), are used in many fields of science and technology [1,2,3,4,5,6,7]. They play an important role in modeling various processes, in solving industrial problems and cybersecurity problems. The relevance of cybersecurity tasks is growing every year. Such tasks include encryption of information, generation of secret keys, authentication, confidentiality and integrity of information. Additionally, an effective solution to these problems is not possible without the use of PRNG and PRBSG.
Random numbers are an important input for many Internets of Things (IoT) functions [8]. In [9], a deep review is given for lightweight random and pseudo-random number generators designed for constrained devices, such as wireless sensor networks and RFID (Radio Frequency Identification) tags, along with a study of a Trifork pseudo-random number generator for constrained devices. In [10], the authors focus on the security and privacy risks in cloud databases and provide a solution for clients who want to generate the pseudo-random number collaboratively in a distributed way which can be reasonably secure, fast and low-cost to meet the requirements of a cloud database. In [11], the use of evolutionary computation is proposed for designing and optimizing lightweight PRNGs. In [12], the authors introduce a novel approach to implement Pseudo Random Number Generators, by proposing the use of generative adversarial networks (GAN) to train a neural network to behave as a PRNG.
In [13], a text algorithm for watermarks based on a PRNG for use in cryptography was proposed, which has good invisibility and reliability to withstand removal, modification attacks, etc., and can be used in the field of hiding information using cloud computing. An interesting method is proposed in [14], whereby random numbers are generated based on reinforcement learning characteristics that select the optimal behavior considering every possible status up to the point of episode closing to secure the randomness of such random numbers.
A number of questions about the approaches to the construction of PRNG and PRBSG, as well as the requirements for their use in cybersecurity systems are discussed in many works, where the authors explore known methods of constructing such generators, analyze their weaknesses and search for new generation methods [15,16,17,18,19,20,21,22,23,24].
Among PRNG, it is possible to allocate additive Fibonacci generators (AFG) to a separate group [25,26,27,28,29,30,31,32,33], which is characterized by the fact that the sequences at their output have acceptable statistical characteristics. This group of generators is effectively used for mathematical and statistical calculations, as well as in the modeling of various processes. It should be noted that AFG, in contrast to linear congruent generators, can be used in algorithms that are critical to the quality of generated pseudo-random numbers, particular in cryptography. The ever-increasing possibilities for the use of AFG and the new requirements for them pose new challenges to developers in their design and implementation; therefore, in this direction, they are actively working to find new structures of modified additive Fibonacci generators (MAFG) with improved characteristics. In particular [34], the authors propose a five-state real-time generator for the Fibonacci sequence and give formal proof of the correctness of the generator. The proposed five-state Fibonacci sequence generator is optimum in generation steps and is implemented on the smallest known finite state automaton in the number of states. In [35], the researchers sought to determine, between the Fibonacci Random Number Generator and the Gaussian Random Generator, which is better for improving data security in cryptographic software systems.
To assess the quality of PRNG and PRBSG, it is necessary to use statistical testing based on various randomization algorithms and obtain an integral picture of the assessment of the pseudo-random sequence at the generator output. The National Institute of Standards and Technology (NIST), which is part of the American National Standards Institute (ANSI), the International Organization for Standardization (ISO), and national standardization authorities are developing assessment methods, requirements, and standards for PRNG and PRBSG. Among the most popular tests for quality assessment is a set of statistical tests NIST [36,37,38,39,40]. If the generated sequences are aimed to be used in cryptographic applications, it is also necessary to conduct cryptographic testing.
In general, an extremely large number of specialists are involved in the design, construction, quality assessment and application of PRNG and PRBSG.
In comparison with the known ones, the novelty of this work lies in the optimization of the parameters of the MAFG, which includes the possibility of realizing an arbitrary value of the modulus of the recurrent equation of the generated polynomial. Additionally, further improvement was achieved in the output signal characteristics of the pseudo-random generator through the joint work of the MAFG and the classical AFG.
1.1. Related Literature
In [40,41,42,43,44,45,46,47,48,49], we and another scientist proposed MAFG, which differs from that reported in [25,26,27,28,29,30,31,32,33,34,35,36] as follows:
- -
- The possibility of functioning according to recurrent equations, the modules of which can have arbitrary values;
- -
- The presence of an additional logic circuit that can significantly improve the statistical characteristics of the output signals;
- -
- The presence of structures and relevant hardware models, which allows them to be implemented in modern element bases.
Advantages of the new MAFG are demonstrated by examples of their work in accordance with several recurrent equations [40,41,42,43,44,45].
In connection with the emergence of our new MAFG, a number of questions arise, which include the following:
- -
- The choice of polynomials on the basis of which it is possible to synthesize MAFG with acceptable statistical characteristics;
- -
- Determination of the generator’s structural element parameters at which acceptable statistical characteristics are reached;
- -
- The method of joint work of the MAFG with classical AFG in order to further improve the statistical characteristics of the output sequence and increase cryptosecurity;
- -
- The definition and expansion of ranges of structural elements initial installations (seed) at which acceptable statistical characteristics of the output pseudo-random sequence are guaranteed;
- -
- The search for new approaches to the design of the MAFG and methods of their implementation, in particular on the Programmable Logic Device;
- -
- The selection of methods for testing the quality of sequences obtained from such generators for compliance with given conditions.
Table 1 shows a summary of the comparison between the research literature and the work developed in this study. If a column item is marked, the work in that row addresses it. If it is not marked, then the work either does not specify or does not address that item. The items of the table are as follows:

Table 1.
Comparison of related work with the study in this paper.
- Work—contains a reference to research;
- Repetition period—if the work investigated the repetition period of the generator’s output sequence;
- Statistical characteristics—if the work investigated and showed statistical characteristics of the output sequence of the generator;
- Ranges of key—if the work investigated the value ranges of key information;
- Polynomial—if it was possible to use an arbitrary value of the modulus of the recurrent equation of the polynomials forming the algorithm of the generator implemented;
- Compatible work—if the compatible work of several generators was possible;
- Hardware implementation—if the work showed the hardware implementation of the generator, in addition to software.
1.2. Purpose of Work
The aim of the work is to optimize the structures of classical AFG and MAFG in their joint work, to determine the ranges of initial settings of structural elements (seed) AFG and MAFG, which guarantee acceptable statistical characteristics of the output pseudo-random sequence.
2. Materials and Methods
Structure Scheme of the Joint Work of AFG and MAFG and the Principle of Its Work
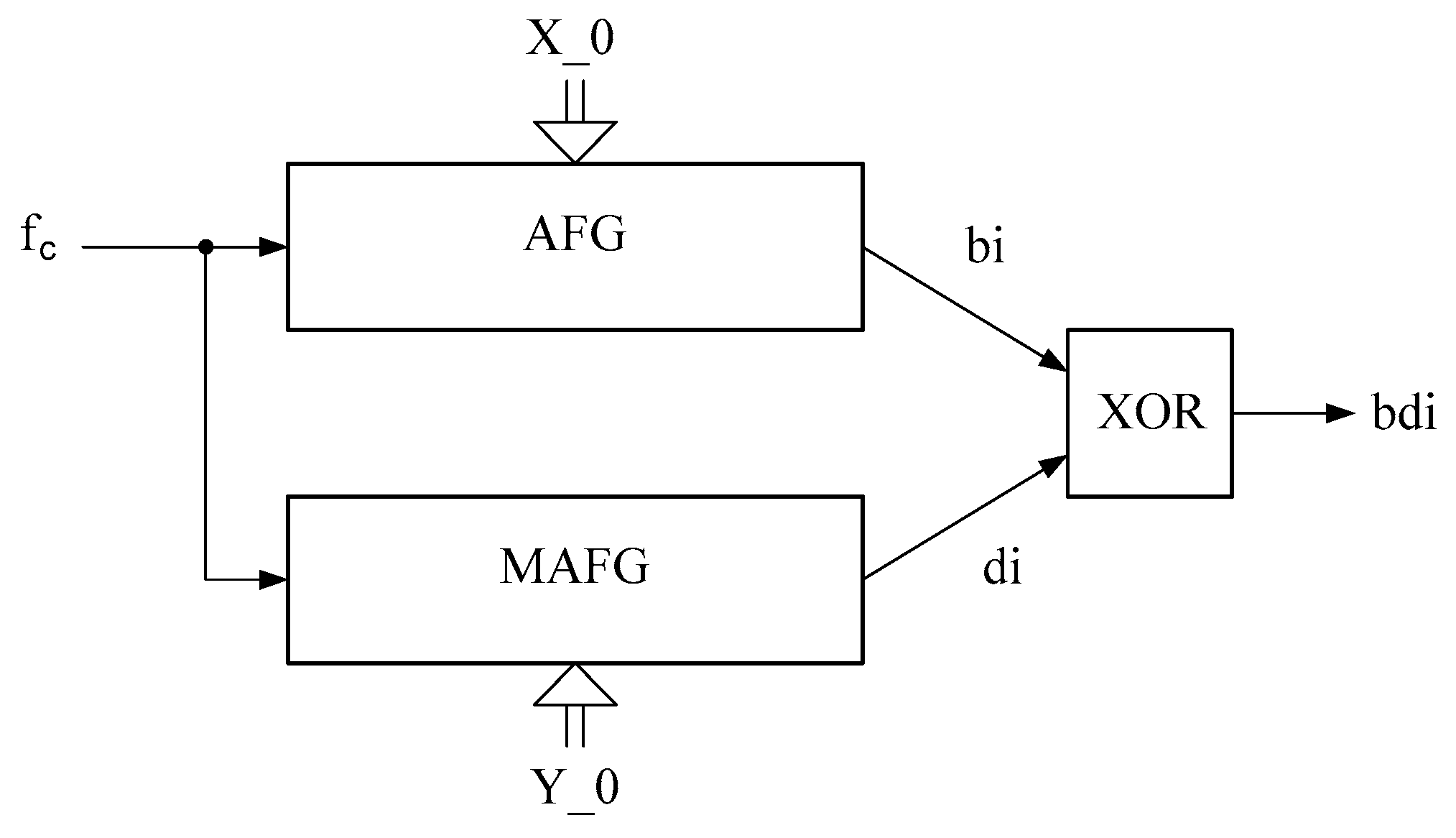
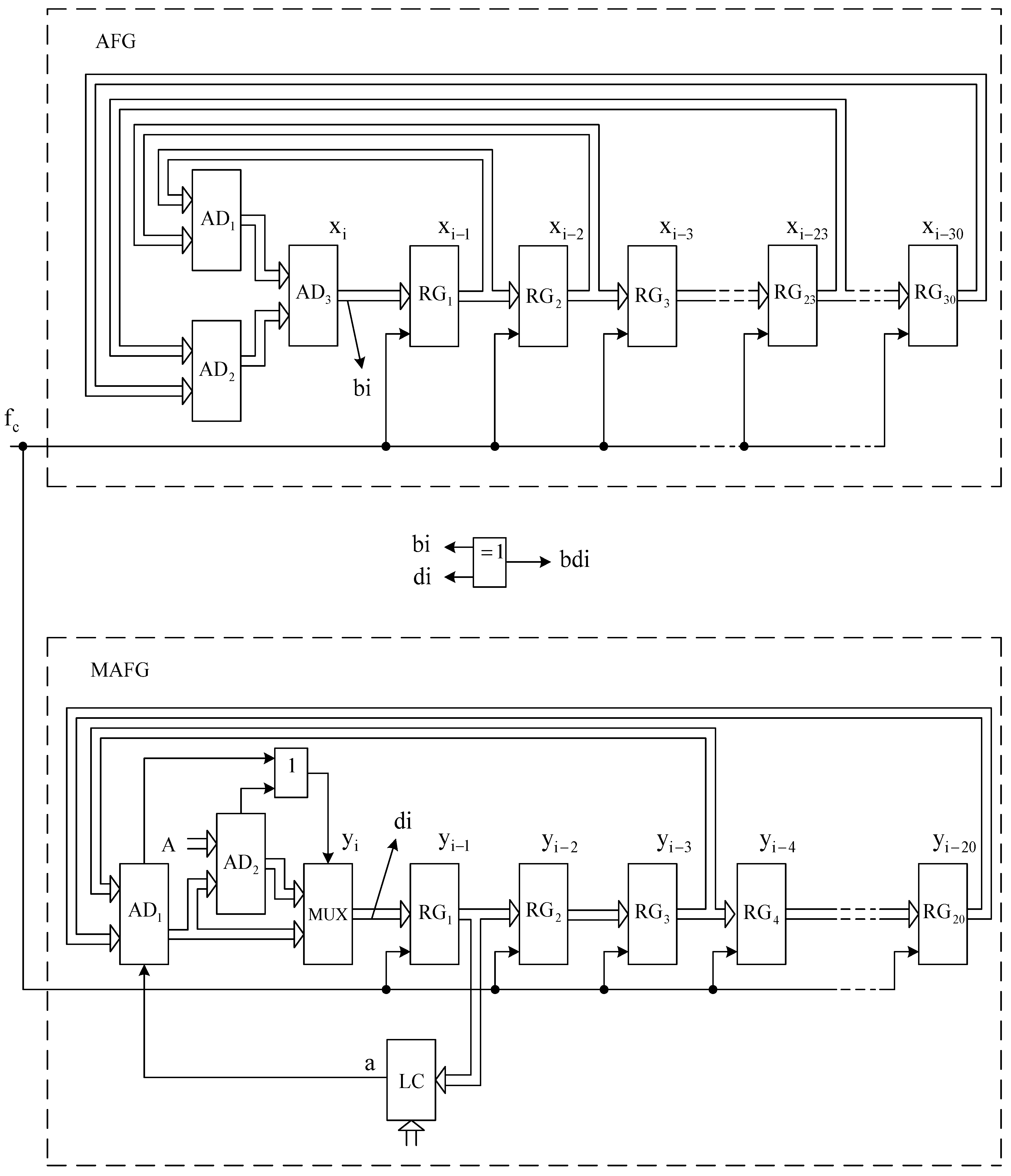
The generalized scheme of joint work of AFG and MAFG is given in Figure 1, and the corresponding detailed structure scheme is given in Figure 2.
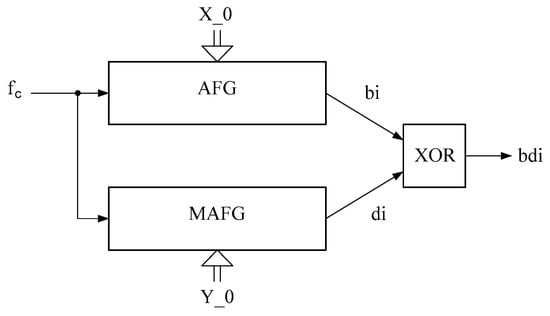
Figure 1.
Generalized scheme of the joint work of AFG and MAFG.
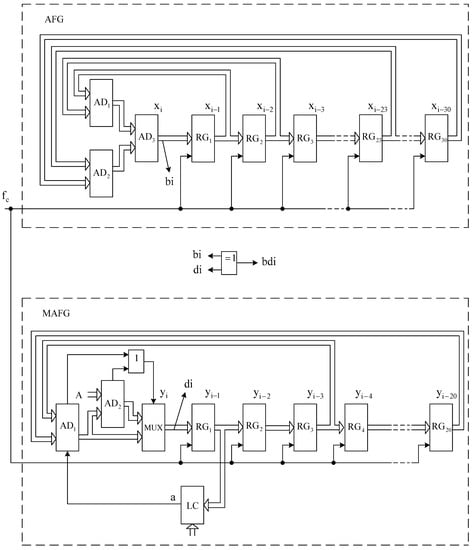
Figure 2.
Structure scheme of the joint work of AFG and MAFG.
The output pseudo-random bit streams AFG— and MAFG— are combined through the logical element XOR, thus forming the output bit sequence—. The inputs AFG and MAFG receive clock pulses—. Before starting the work, the initial values (seed) are written to the AFG and MAFG memory registers and accordingly.
In this paper, the characteristics of the device are investigated, despite the fact that AFG is constructed in accordance with the primitive polynomial
and MAFG is constructed according to the primitive polynomial
The choice of polynomials (1) and (2) was made on the basis of studies of many other variants and was based on achieving acceptable statistical characteristics of the output pseudo-random signal, in the full range of possible values and with minimal hardware costs.
AFG consists of adders and memory registers (Figure 2).
According to polynomial (1), AFG operates on a recurrent equation
where is the adder output number; , , , are numbers at register , , , outputs, respectively; and is the modulus of the recurrent equation, determined, in this case, by the number of binary bits of the structural elements of AFG.
The output bit sequence is formed at the output of the least significant bit of the adder .
The MAFG consists of adders and , multiplexer MUX, memory registers , logic element and logic circuit .
In accordance with polynomial (2) and the new method of its internal construction [42], MAFG operates on a recurrent equation
where is the multiplexer MUX output number; and are register and outputs numbers; is the the module of the recurrent equation, which is determined, in this case, by the number of binary bits of the structural elements of the MAFG and the value of the control code that is coming to the second input of the combination adder ; and a is the output signal of the logic circuit , which is determined by the equation
where () are the bit values of the number , and is the number of its binary bits.
It should be emphasized that, due to its original structure, the MAFG can operate in accordance with a recurrent equation with an arbitrary value of the module, which will be used in further studies of this work.
The output bit sequence is formed at the output of the multiplexer MUX’s least significant bit.
3. Results and Discussion
3.1. Results of AFG Research
The main task of AFG, which works in pair with MAFG, is to ensure a stable repetition period of output pseudo-random sequence on the whole set of initial values in registers that are part of it.
It is known [36] that the maximum period of the AFG output sequence is achieved if it works following the primitive polynomial.
As mentioned earlier in this paper, the selected classical AFG works following the primitive polynomial (1) and, therefore, the recurrent Equation (3).
At , the repetition period of the AFG output signal is equal to for any initial value [43].
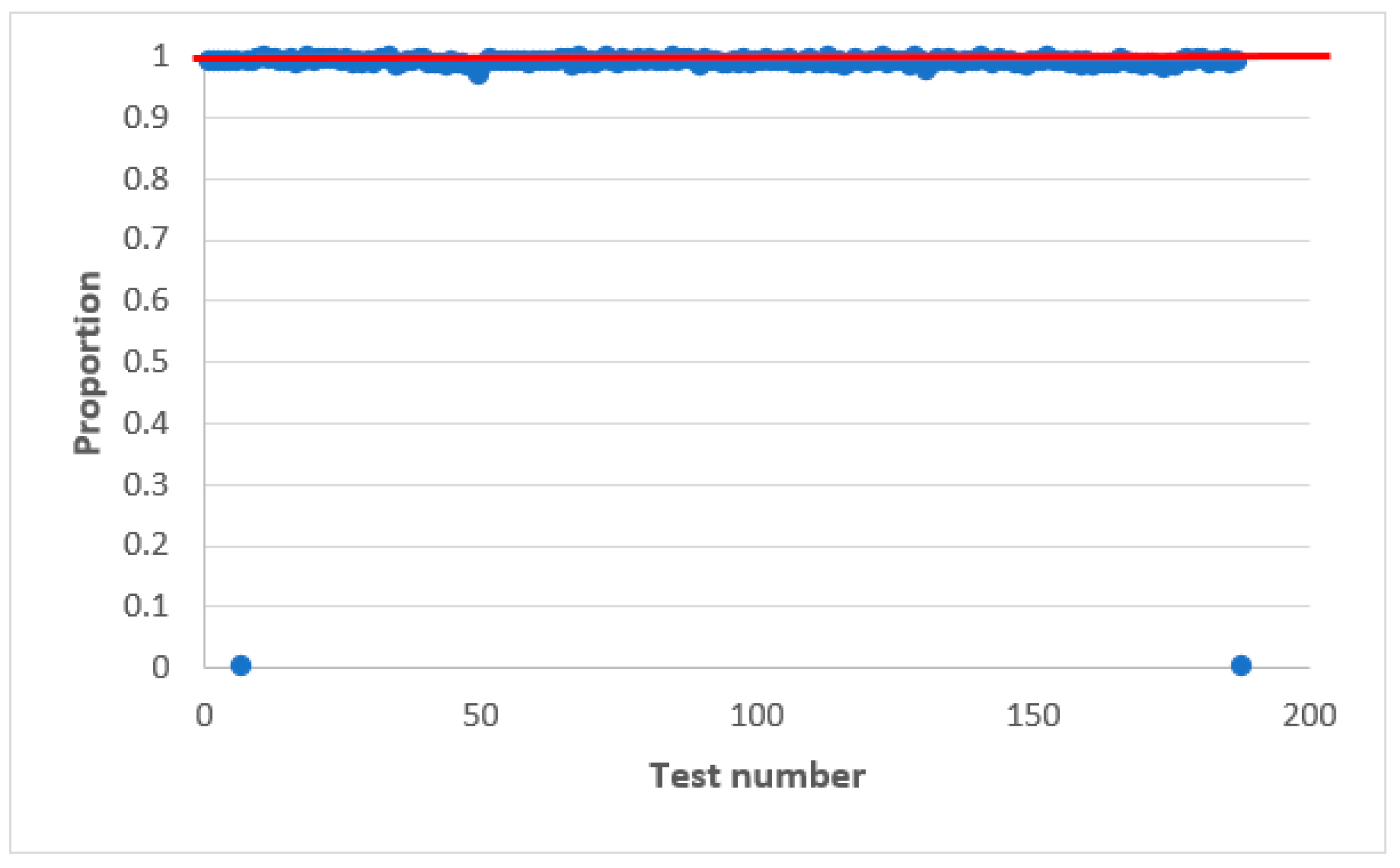
Figure 3 shows the statistical characteristics of the AFG output signal obtained using statistical tests NIST [37,38,39]. The results are presented in the statistical portraits. A statistical portrait is an matrix, where is the number of binary sequences to be tested and is the number of statistical tests [37].
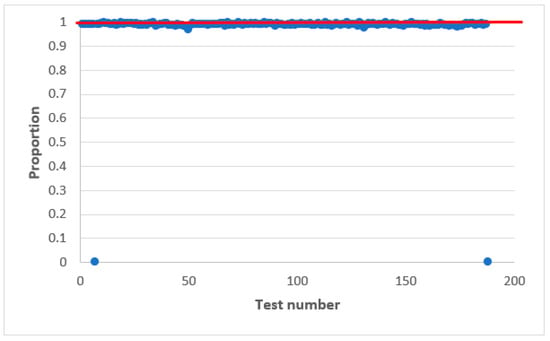
Figure 3.
Statistical portrait of the AFG output sequence.
According to the obtained statistical portrait, the proportion of sequences that passed each statistical test is determined. For this, setting the significance level and the probability values exceeding the established level are calculated for each tests.
It is considered that the generator has passed the test if the value of the coefficient is within . The confidence interval limits are determined by the following expression [37]:
where .
By substituting the corresponding values, namely and , we obtain the limits of the confidence interval . A sequence is said to meet randomness requirements when all test values fall within these limits.
The NIST statistical test set consists of 15 tests, calculating 188 results values [37]. Each of these 188 values is interpreted as the result of a separate test. Each of these 188 values is marked as a dot in the statistical portrait.
The statistical portrait is obtained at the initial value of numbers . Similar statistical portraits were obtained for other values . The output AFG sequence does not pass all the tests from the NIST set, so such a generator is not statistically safe.
3.2. Results of MAFG Research
We will research the characteristics of MAFG for the case of its operation in accordance with the primitive polynomial (2).
Figure 4 and Figure 5 show the dependences of the repetition periods T on the initial values of numbers in the registers . The value is determined by the equation:
where , , …, are the initial values of the numbers in registers .
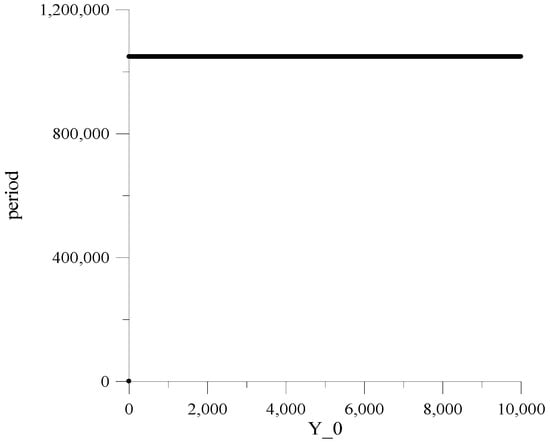
Figure 4.
Dependencies of repetition periods for , and .
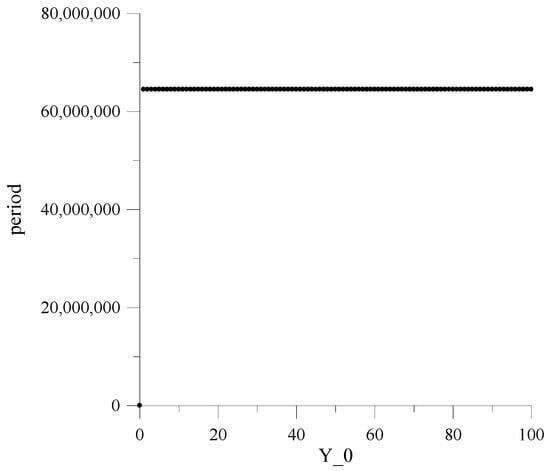
Figure 5.
Dependencies of repetition periods for , and .
Dependencies are obtained only for two values and one value of the output signal because obtaining such dependencies for other values of these parameters requires a significant increase in computing resources and machine time.
Here, it should be emphasized that the constancy of the MAFG output sequence repetition period, for the whole set of the initial values , is guaranteed only at and .
Investigations have shown that for other and values, the repetition period significantly varies depending on , achieving under specific small values, thus generating so-called “weak keys”.
This circumstance is the main reason that leads to further research, provided that the MAFG works in conjunction with the classic AFG, which ensure acceptable minimum values of the period for any values .
Analyses of the statistical characteristics of the MAFG output signal allowed us to make the following conclusions.
Statistical characteristics at even values of h are much better than at odd values. This is due to a certain asymmetry in the formation of the MAFG output signal at odd values of .
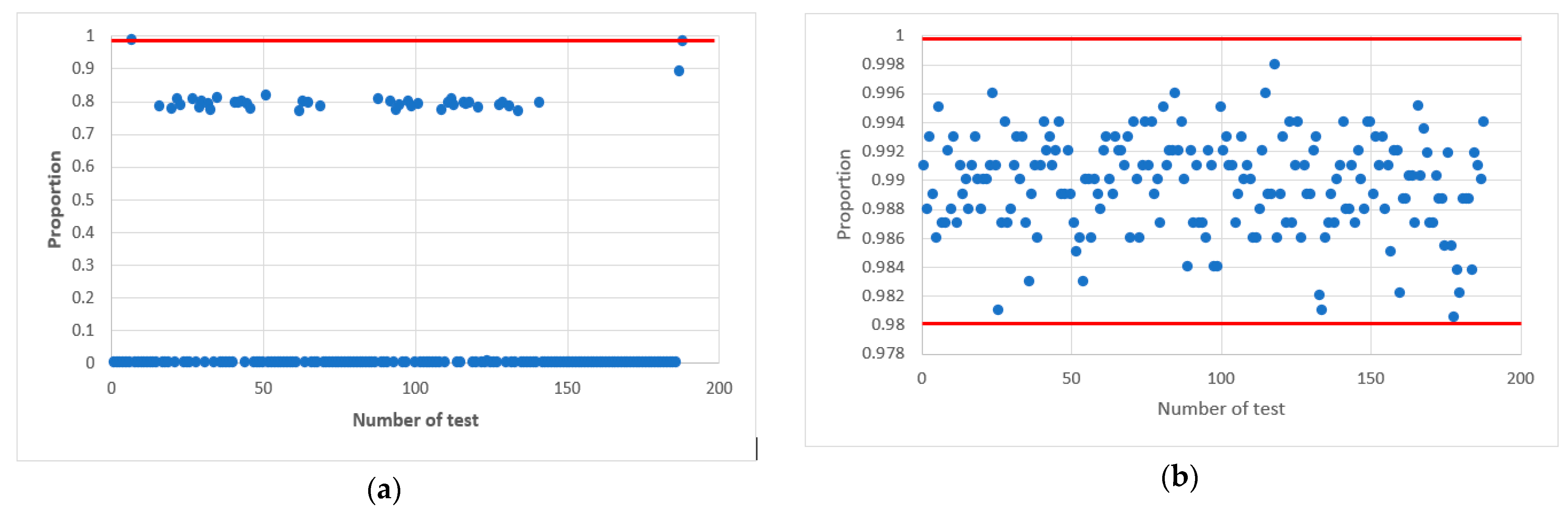
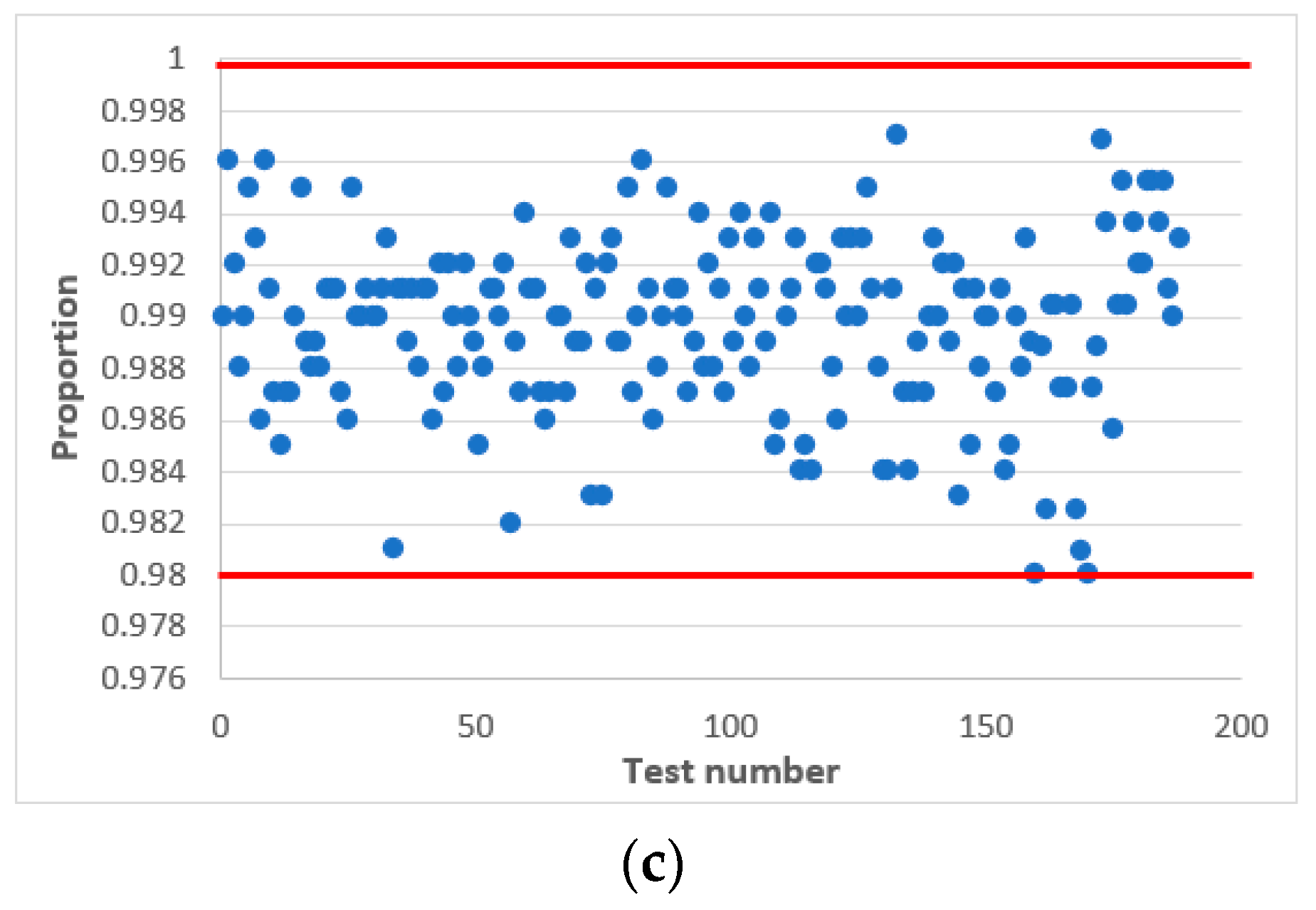
In confirmation of this, Figure 6 shows statistical portraits of the MAFG output signal for Y.
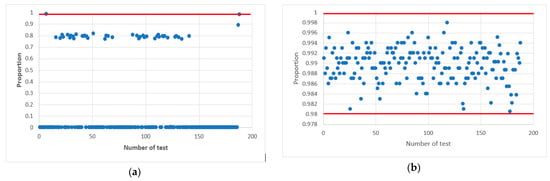
Figure 6.
Statistical portrait of the MAFG output sequence: (a) with an odd value , (b) at an even value .
The graphs show statistical portraits of two generators. Figure 6a shows that such a sequence does not meet the randomness requirements since it passed only 2 out of 15 tests (Cumulative Sums and Serial) (see Table 2) of the NIST set. Figure 6b shows that all values are within the confidence intervals; therefore, such a sequence meet the randomness requirements. Table 2 shows the results of the testing calculations.

Table 2.
Results of testing MAFG by NIST.
It was also found that the statistical characteristics of the MAFG output signal improve when forming the output signal of the following the logic equation
where and are the values of the least and most significant bits of register RG1 in the MAFG structure.
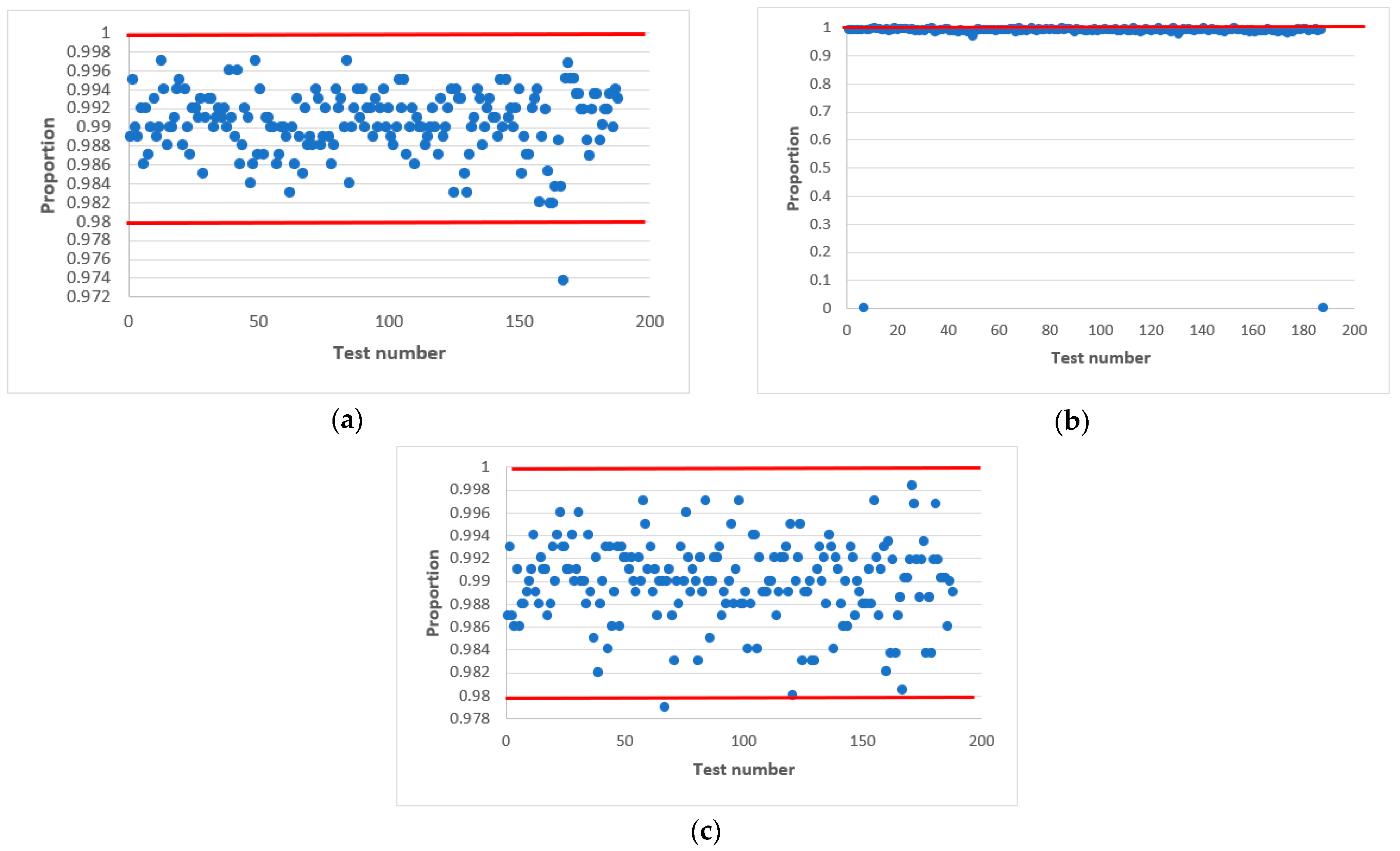
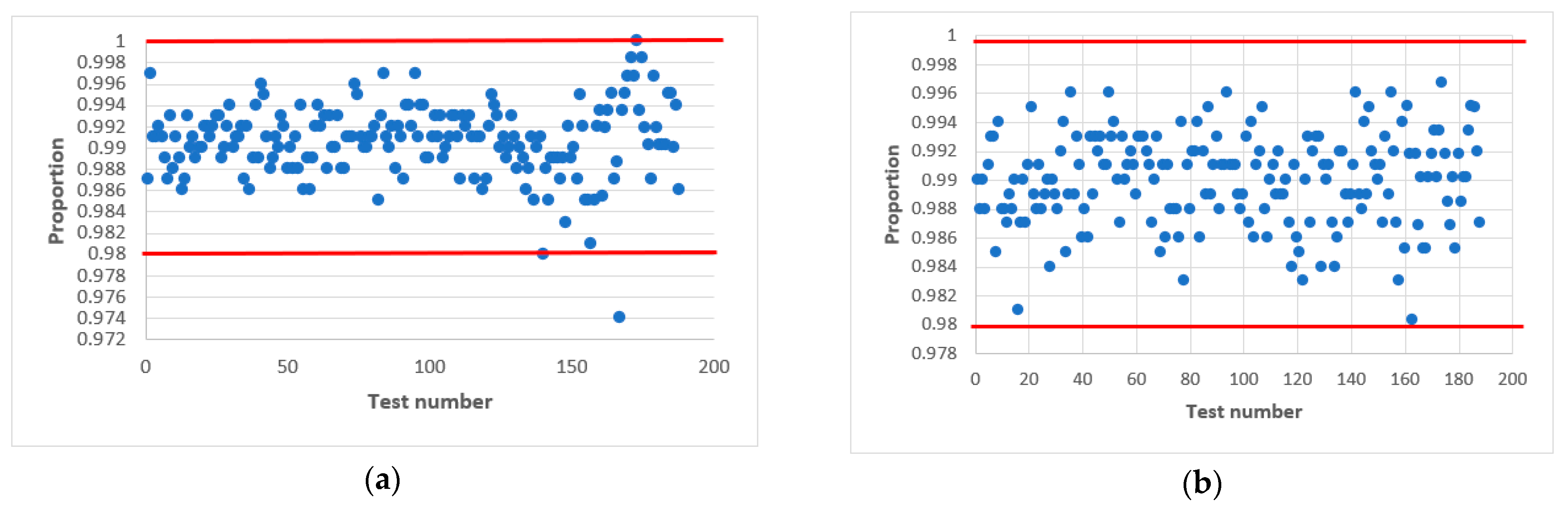
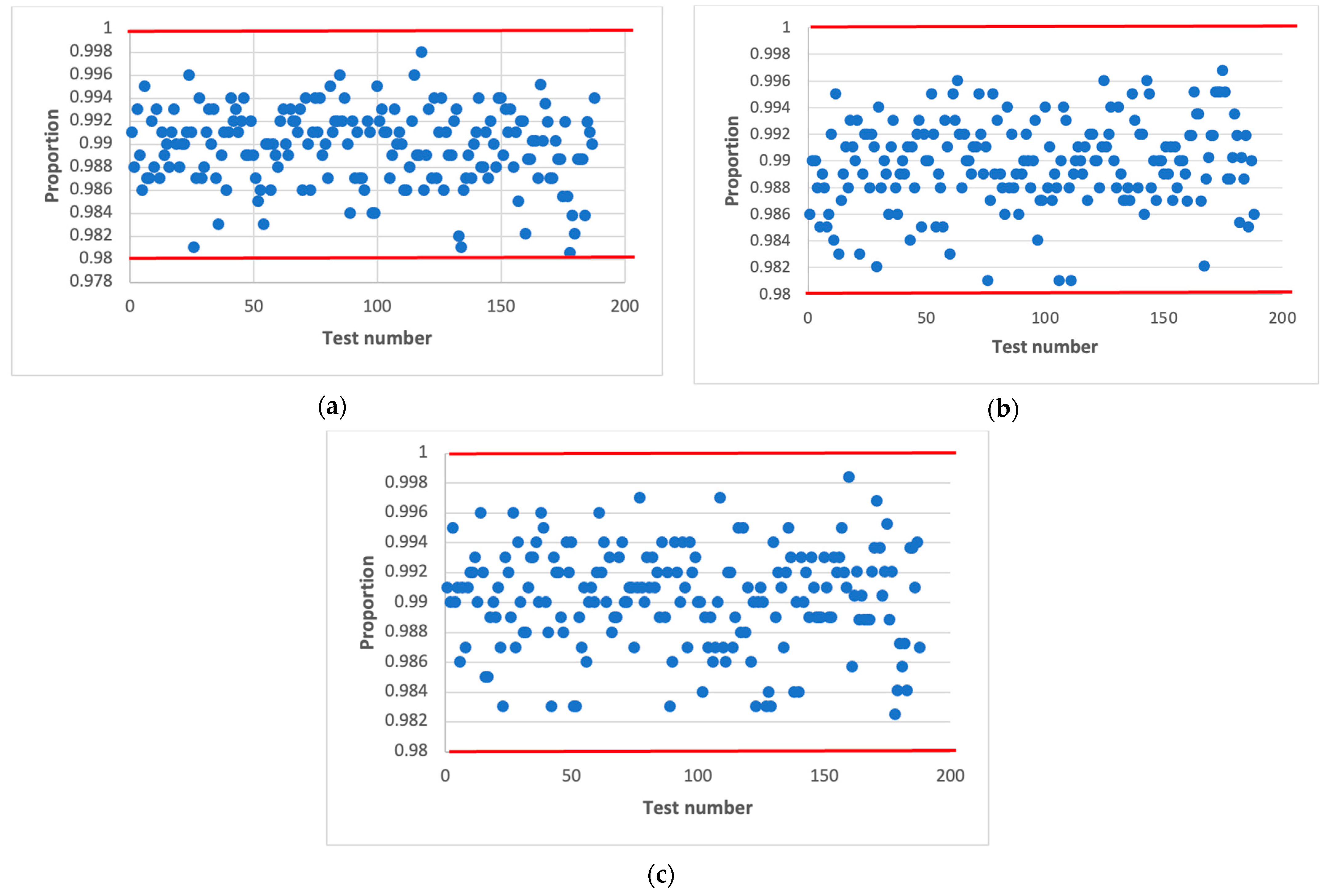
In confirmation of this, Figure 7 and Figure 8 shows statistical portraits of the MAFG output signal for , variable initial values and different values of the output signal: (Figure 7) and (Figure 8).
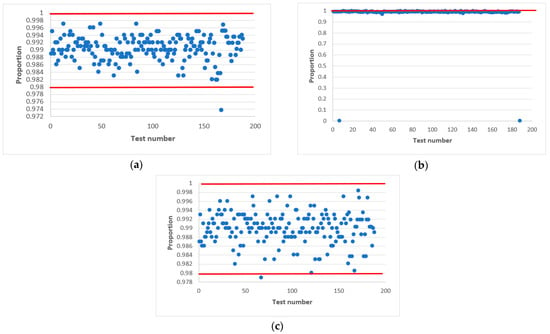
Figure 7.
Statistical portrait of the MAFG output sequence for , with initial values: (a) , (b) , (c) .
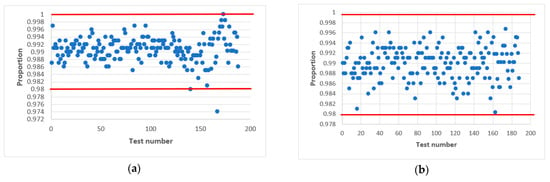
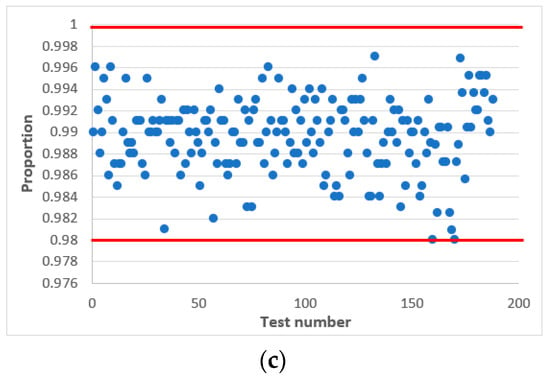
Figure 8.
Statistical portrait of the MAFG output sequence for , with initial values: (a) , (b) , (c) .
Figure 7 shows that by using such initial values, the generator formed a non-random sequence. There are always one or two tests that fail the NIST tests.
Finally, we succeeded in passing all NIST tests at values of 32 and 100. Comparing Figure 7 and Figure 8, we conclude that the quality of the pseudo-random sequence is affected by the value of the output signal of the .
Besides investigating the statistical characteristics of the MAFG, we determined the repetition periods. Table 3 shows some results of the investigation of the MAFG repetition period.

Table 3.
Results of the investigation of the MAFG repetition period.
Therefore, as a result of the research on MAFG statistical characteristics, it is established that they essentially depend on values and .
3.3. Results of Research Combined Steam Generator AFG and MAFG
This section presents the results of the research output sequence of pair AFG and MAFG (Figure 1 and Figure 2), with a proven assumption that the improvement of the MAFG statistical characteristics for any initial value can be achieved by forming the output signal of the logic circuit in such way that the least and most significant bits of the register are fed to the input of the .
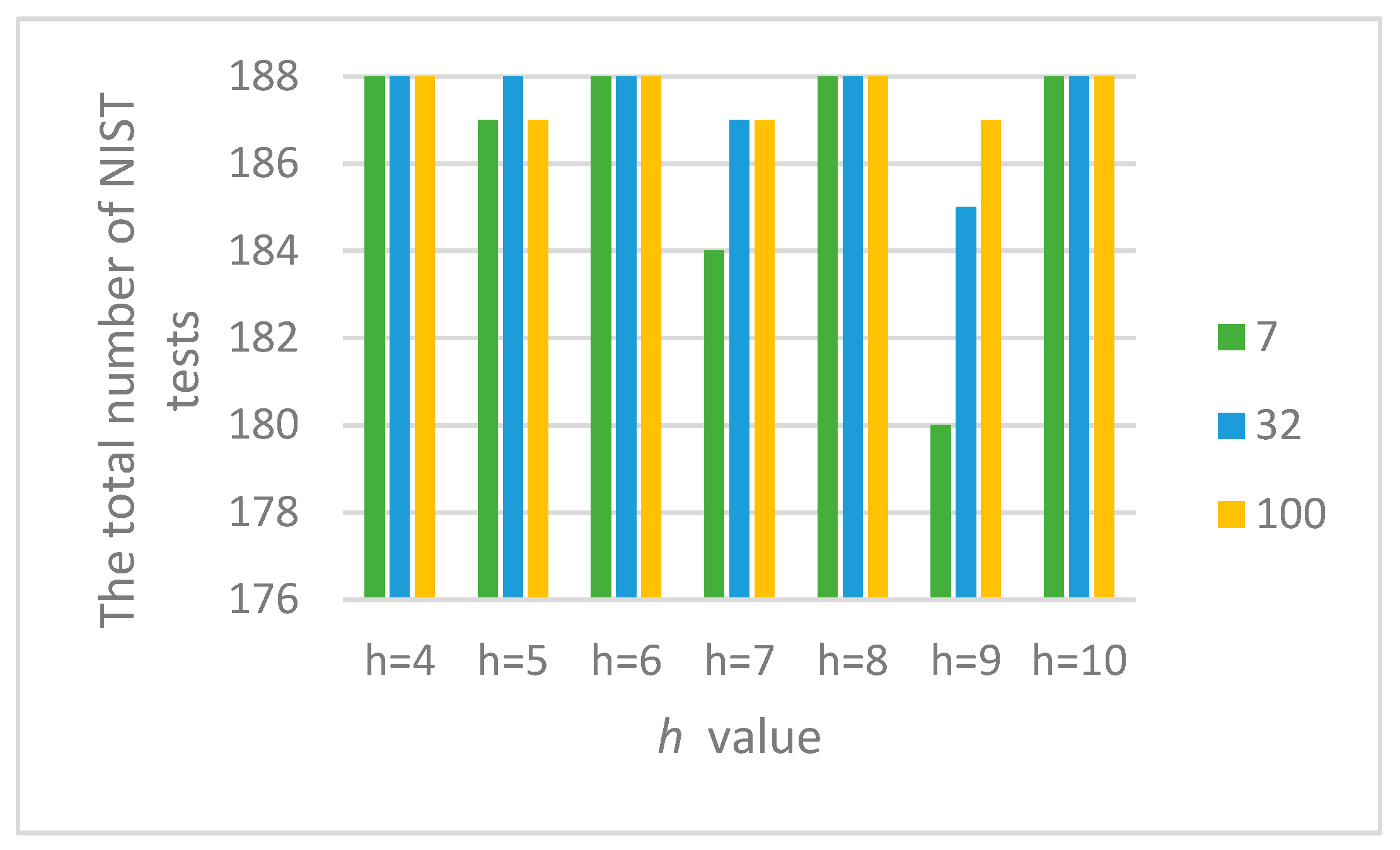
Table 4 shows the parameters of the logic circuit following logic Equation (4) for different values h, in which the statistical characteristics of the output signal of the combined generator (Figure 1 and Figure 2) were studied at different initial values and . Figure 9 presents the results of these studies.

Table 4.
Parameters of the combined generator.
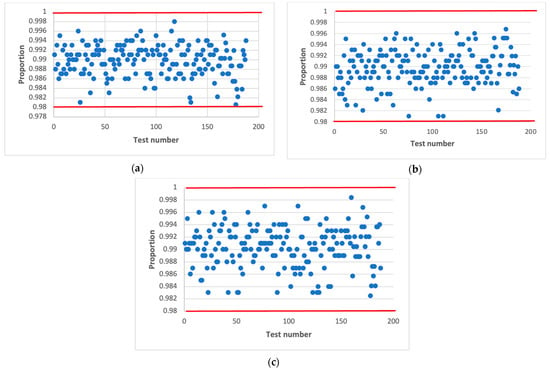
Figure 9.
Statistical portrait of the combined generator output sequence for h = 10, with initial values: (a) , (b) , (c) .
The obtained results (Figure 9) confirm the assumption that at even values of h and upon the formation of the LC output signal following Equation (4), the output signal of the combined generator successfully passes all 188 tests of the NIST set at different initial values of structural elements and , which ensure its statistical security as one of the main components of cryptographic stability.
Figure 9 shows the results of testing the combined generator at h = 10.
Table 5 shows the results of passing the combined generator at , with initial values (generator 1), (generator 2), (generator 3).

Table 5.
p-Values of statistical tests for combined generator.
Figure 10 shows the summary results of testing the combined generator with the parameters displayed in Table 5.
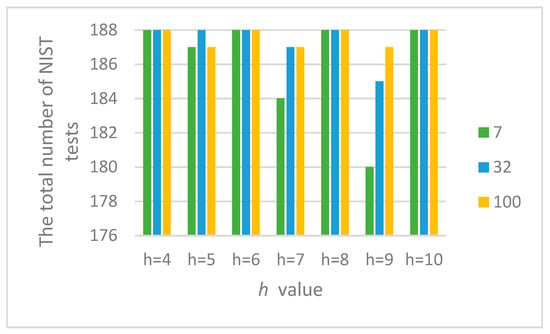
Figure 10.
Results of passing the NIST tests with the combined generator.
Figure 10 shows that combined generators with an even value of h meet the randomness requirements according to the NIST method in a wide range of initial values and , and with an odd value, they do not. We decided to investigate this issue in more detail.
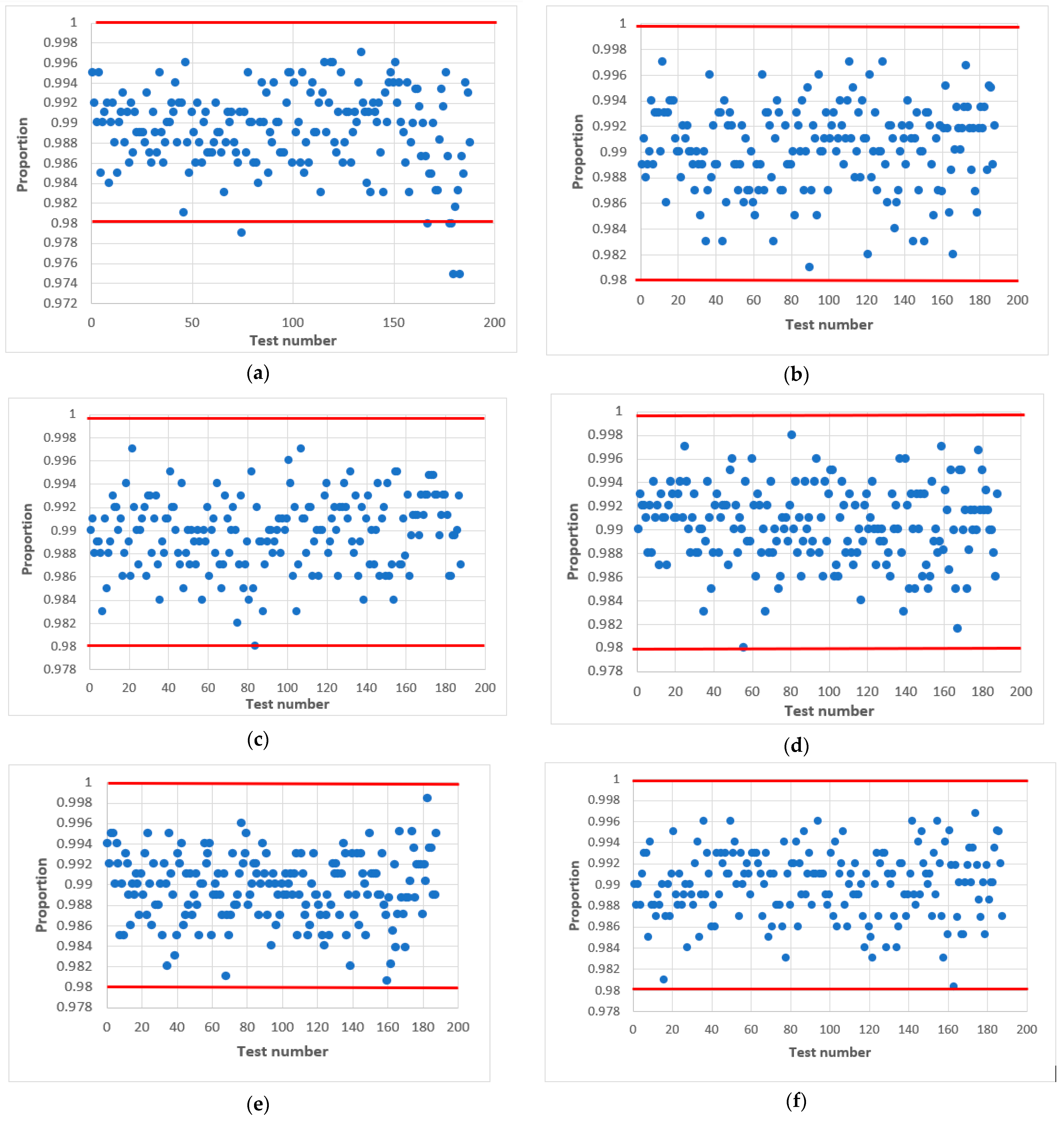
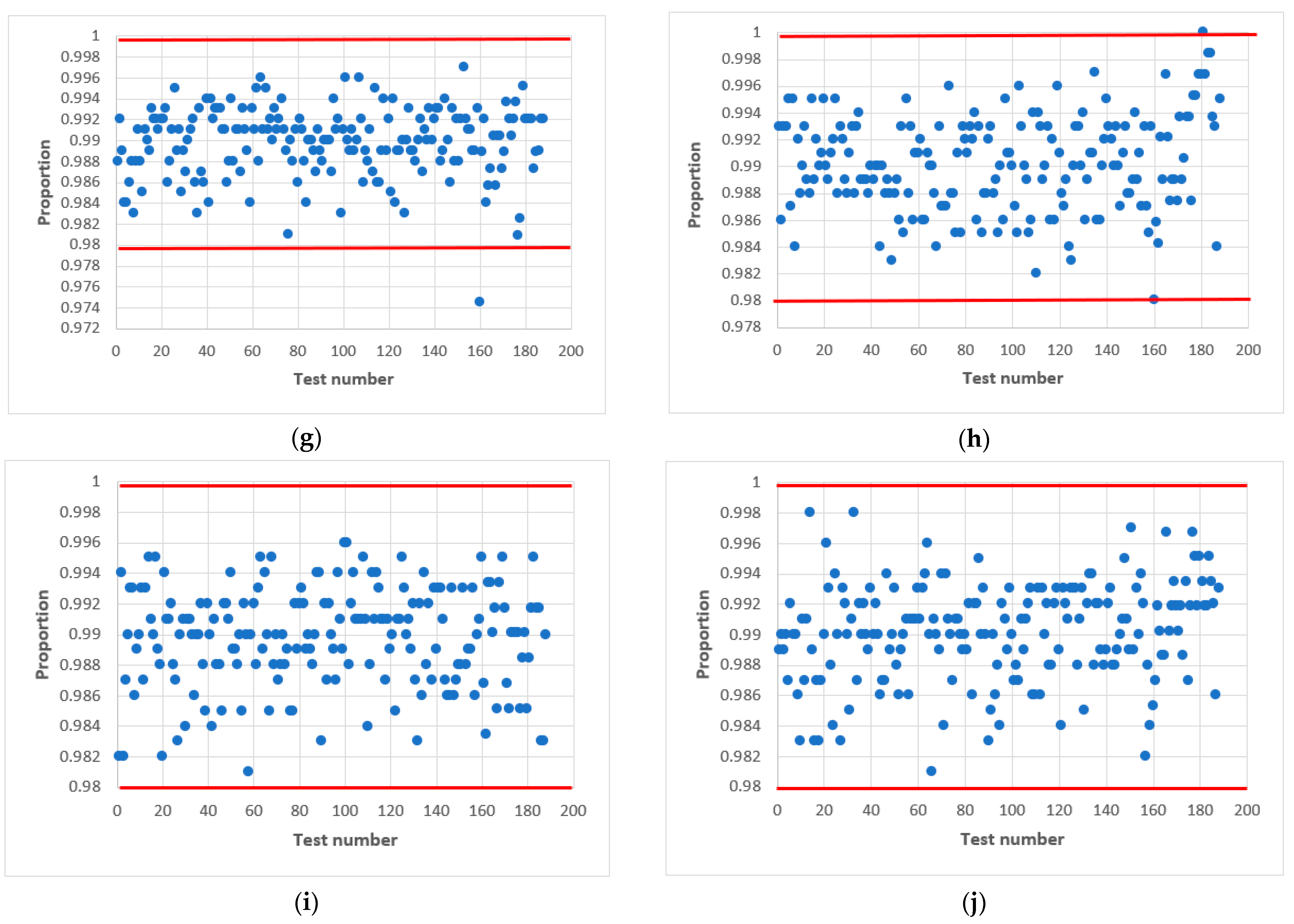
Further research proved that acceptable statistical characteristics of the output signal of the combined generator could also be provided with odd values of h, but in narrower ranges of initial values of and . This is confirmed by the statistical portraits in Figure 11.
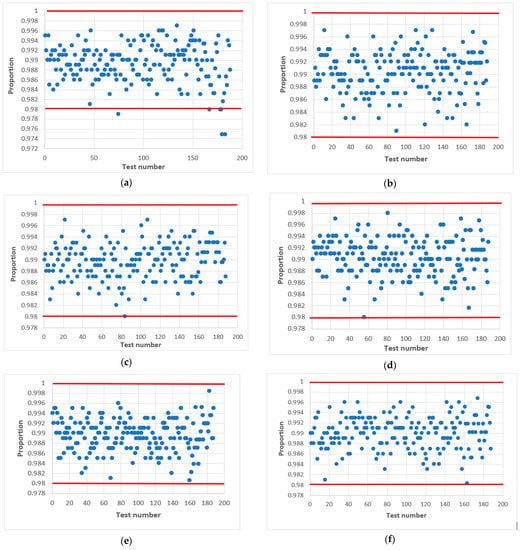
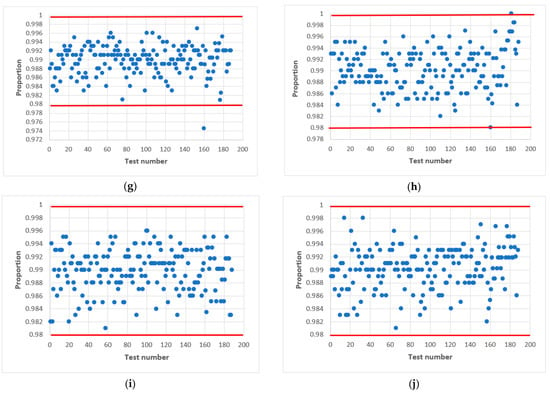
Figure 11.
Statistical portrait of the combined generator for h = 9, with initial values: (a) ; (b) ; (c) ; (d) ; (e) ; (f) ; (g) ; (h) ; (i) ; (j) .
As can be seen from Figure 10, the combined generator with has the worst statistical characteristics. By doing additional research, such as varying the initial numbers in and with the condition that we managed to achieve the passing of all NIST tests.
The results of the tests are shown in Figure 11, where the left side shows the combined generator with initial values , and variables (Figure 11a), 64 (Figure 11c), 71 (Figure 11e), 100 (Figure 11g), 1004 (Figure 11i). On the right side is the combined generator with and variables (Figure 11b), 64 (Figure 11d), 71 (Figure 11f), 100 (Figure 11h), 1004 (Figure 11j). The value of the output signal of the LS for both cases is the same .
The statistical portrait Figure 11 shows that the combined generator at did not pass four NIST tests. This means that the sequence does not meet the randomness requirements. After changing the value of , we see an improvement, and all tests are passed (Figure 11c). The situation is similar to the combined generator (Figure 11g,h). Summarizing, we can conclude that the change of the initial numbers and affects the quality of the statistical characteristics of the combined generator.
Thus, as a result of experimental research, we managed to choose the parameters of the combined generator so that it allows the formation of a sequence with acceptable statistical characteristics for odd h.
4. Conclusions
This work offers a new structure of the combined generator consisting of classical and modified . The output pulse sequence of the combined generator is formed as the sum modulo 2 of the output sequences of and .
At certain values of the , internal parameters provide the maximum value of the repetition period of the output sequence for all possible initial settings of structural elements, thereby providing a repetition period of the combined generator output signal not less than a certain specified value.
It is proved that the statistical characteristics of the output signal and the combined generator are generally acceptable at odd values of the parameter h, determined by the number of bits of the registers, and the method of constructing a logic circuit, at which input signals come from the most and least significant bits of one of the registers. The statistical characteristics of the combined generator output signal are acceptable for a wide range of values of the initial settings and .
The scientific novelty of this paper lies in the further optimization of the MAFG structure with an arbitrary value of the modulus of the recurrent equation, the working principle of which was proposed by the authors in previous works, and the investigation of compatible work with the classical AFG. It allows for significantly improved basic characteristics of additive Fibonacci generators. An essential factor is that the development is aimed, first of all, at the hardware implementation, which allows the high-speed generators to be ensured.
The purpose of further research in this direction will be practical recommendations for the choice of parameters of the combined generator depending on the specific tasks of creating cryptographic or other technical means.
One possible direction for further research in this direction may be to investigate structures with more of AFG and MAFG combined in a different way.
Author Contributions
Conceptualization, V.M.; methodology, V.M., M.S., O.H., P.S. and T.Z.; software, M.S. and O.H.; validation, V.M., P.S. and R.S.; investigation, P.S., O.H., M.S., V.M., T.Z. and R.S.; writing—original draft preparation, V.M., M.S. and O.H.; writing—review and editing, V.M., M.S. and O.H.; funding acquisition, R.S. All authors have read and agreed to the published version of the manuscript.
Funding
The research work reported in this paper was in part supported by the National Centre for Research and Development, Poland under the project no. POIR.04.01.04-00-0048/20.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data cited in this manuscript are available from the published papers or the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
References
- Baldanzi, L.; Crocetti, L.; Falaschi, F.; Bertolucci, M.; Belli, J.; Fanucci, L.; Saponara, S. Cryptographically Secure Pseudo-Random Number Generator IP-Core Based on SHA2 Algorithm. Sensors 2020, 20, 1869. [Google Scholar] [CrossRef] [PubMed]
- Dichtl, M.; Golić, J.D. High-Speed True Random Number Generation with Logic Gates Only. In Cryptographic Hardware and Embedded Systems—CHES 2007; Lecture Notes in Computer Science Book Series; Springer: Berlin/Heidelberg, Germany, 2007; pp. 45–62. [Google Scholar]
- Mandrona, M.N.; Maksymovych, V.N. Comparative Analysis of Pseudorandom Bit Sequence Generators. J. Autom. Inf. Sci. 2017, 49, 78–86. [Google Scholar] [CrossRef]
- Fishman, G.S. Pseudorandom Number Generation. In Discrete-Event Simulation; Springer Series in Operations Research; Springer: New York, NY, USA, 2001; pp. 416–451. [Google Scholar] [CrossRef]
- François, M.; Defour, D.; Berthomé, P. A Pseudo-Random Bit Generator Based on Three Chaotic Logistic Maps and IEEE 754-2008 Floating-Point Arithmetic. In Theory and Applications of Models of Computation—TAMC 2014; Lecture Notes in Computer Science Book Series; Springer: Cham, Switzerland, 2014; Volume 8402. [Google Scholar] [CrossRef]
- Barker, E.B.; Kelsey, J.M. Recommendation for Random Number Generation Using Deterministic Random Bit Generators, ITL Bulletin; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2007. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=919165 (accessed on 20 November 2022).
- Shujun, L.; Xuanqin, M.; Yuanlong, C. Pseudo-random Bit Generator Based on Couple Chaotic Systems and Its Applications in Stream-Cipher Cryptography. In Progress in Cryptology—INDOCRYPT 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 316–329. [Google Scholar] [CrossRef]
- Kietzmann, P.; Schmidt, T.C.; Wählisch, M. A Guideline on Pseudorandom Number Generation (PRNG) in the IoT. ACM Comput. Surv. 2022, 54, 1–38. [Google Scholar] [CrossRef]
- Orúe, A.B.; Hernández Encinas, L.; Fernández, V.; Montoya, F. A Review of Cryptographically Secure PRNGs in Constrained Devices for the IoT. In Proceedings of the SOCO 2017, ICEUTE 2017, CISIS 2017: International Joint Conference SOCO’17-CISIS’17-ICEUTE’17, León, Spain, 6–8 September 2017; Pérez García, H., Alfonso-Cendón, J., Sánchez González, L., Quintián, H., Corchado, E., Eds.; Advances in Intelligent Systems and Computing Book Series. Springer: Cham, Switzerland, 2018; Volume 649. [Google Scholar] [CrossRef]
- Chen, J.; Miyaji, A.; Su, C. Distributed Pseudo-Random Number Generation and Its Application to Cloud Database. In ISPEC 2014: Information Security Practice and Experience; Huang, X., Zhou, J., Eds.; Lecture Notes in Computer Science Book Series; Springer: Cham, Switzerland, 2014; Volume 8434. [Google Scholar] [CrossRef]
- Picek, S.; Yang, B.; Rozic, V.; Vliegen, J.; Winderickx, J.; De Cnudde, T.; Mentens, N. PRNGs for Masking Applications and Their Mapping to Evolvable Hardware. In Smart Card Research and Advanced Applications—CARDIS 2016; Lemke-Rust, K., Tunstall, M., Eds.; Lecture Notes in Computer Science Book Series; Springer: Cham, Switzerland, 2017; Volume 10146. [Google Scholar] [CrossRef]
- De Bernardi, M.; Khouzani, M.H.R.; Malacaria, P. Pseudo-Random Number Generation Using Generative Adversarial Networks. In ECML PKDD 2018: ECML PKDD 2018 Workshops; Lecture Notes in Computer Science Book Series; Springer: Cham, Switzerland, 2019; Volume 11329. [Google Scholar] [CrossRef]
- Gu, X.-C.; Zhang, M.-X. Design and Implementation of a FPGA Based Gaussian Random Number Generator. Chin. J. Comput. 2011, 34, 165–173. [Google Scholar] [CrossRef]
- Park, S.; Kim, K.; Kim, K.; Nam, C. Dynamical Pseudo-Random Number Generator Using Reinforcement Learning. Appl. Sci. 2022, 12, 3377. [Google Scholar] [CrossRef]
- Eastlake, D.; Schiller, J.; Crocker, S. Randomness Requirements for Security; The Internet Society: Reston, VA, USA, 2005; pp. 1–48. [Google Scholar]
- Barker, E.B.; Kelsey, J.M. Recommendation for Random Number Generation Using Deterministic Random Bit Generators; Special Publication (NIST SP); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015. [CrossRef]
- Gutterman, Z.; Pinkas, B.; Reinman, T. Analysis of the Linux random number generator. In Proceedings of the 2006 IEEE Symposium on Security and Privacy (S & P’06), Berkeley/Oakland, CA, USA, 21–24 May 2006; p. 15. [Google Scholar] [CrossRef]
- Ruhault, S. SoK: Security Models for Pseudo-Random Number Generators. IACR Trans. Symmetric Cryptol. 2017, 1, 506–544. [Google Scholar] [CrossRef]
- HÅstad, J.; Impagliazzo, R.; Levin, L.A.; Luby, M. A Pseudorandom Generator from any One-way Function. SIAM J. Comput. 1999, 28, 1364–1396. [Google Scholar] [CrossRef]
- Braverman, M.; Rao, A.; Raz, R.; Yehudayoff, A. Pseudorandom Generators for Regular Branching Programs. In Proceedings of the 2010 IEEE 51st Annual Symposium on Foundations of Computer Science, Las Vegas, NV, USA, 13–16 October 2010; pp. 40–47. [Google Scholar] [CrossRef]
- Degabriele, J.; Paterson, K.G.; Schuldt, J.C.N.; Woodage, J. Backdoors in Pseudorandom Number Generators: Possibility and Impossibility Results. In Advances in Cryptology—CRYPTO 2016; Robshaw, M., Katz, J., Eds.; Lecture Notes in Computer Science Book Series; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9814. [Google Scholar] [CrossRef]
- Barak, B.; Shaltiel, R.; Tromer, E. True Random Number Generators Secure in a Changing Environment. In Cryptographic Hardware and Embedded Systems—CHES 2003; Lecture Notes in Computer Science Book Series; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2779, pp. 166–180. [Google Scholar] [CrossRef]
- Saito, M.; Matsumoto, M.; Baccelli, E. TinyMT32 Pseudorandom Number Generator (PRNG); Internet Engineering Task Force: Wilmington, DE, USA, 2020. [Google Scholar]
- Maksymovych, V.N.; Mandrona, M.N.; Kostiv, Y.M.; Harasymchuk, O.I. Investigating the Statistical Characteristics of Poisson Pulse Sequences Generators Constructed in Different Ways. J. Autom. Inf. Sci. 2017, 49, 11–19. [Google Scholar] [CrossRef]
- Cybulski, R. Pseudo-random number generator based on linear congruence and delayed Fibonacci method: Pseudo-random number generator based on linear congruence and delayed Fibonacci method. Tech. Sci. 2021, 24, 331–349. [Google Scholar] [CrossRef]
- Mascagni, M.; Robinson, M.L.; Pryor, D.V.; Cuccaro, S.A. Parallel Pseudorandom Number Generation Using Additive Lagged-Fibonacci Recursions. In Monte Carlo and Quasi-Monte Carlo Methods in Scientific Computing; Niederreiter, H., Shiue, P.J.S., Eds.; Lecture Notes in Statistics Book Serie; Springer: New York, NY, USA, 1995; Volume 106. [Google Scholar] [CrossRef]
- Mascagni, M.; Srinivasan, A. Parameterizing parallel multiplicative lagged-Fibonacci generators. Parallel Comput. 2004, 30, 899–916. [Google Scholar] [CrossRef]
- Parker, J.D. The period of the Fibonacci random number generator. Discret. Appl. Math. 1988, 20, 145–164. [Google Scholar] [CrossRef]
- Orúe López, A.B.; Hernández Encinas, L.; Martín Muñoz, A.; Montoya Vitini, F. A Lightweight Pseudorandom Number Generator for Securing the Internet of Things. IEEE Access 2017, 5, 27800–27806. [Google Scholar] [CrossRef]
- Bi, Y.; Peterson, G.D.; Warren, G.L.; Harrison, R.J. Poster reception—A reconfigurable supercomputing library for accelerated parallel lagged-Fibonacci pseudorandom number generation. In Proceedings of the 2006 ACM/IEEE Conference on Supercomputing—SC ’06, Tampa, FL, USA, 11–17 November 2006. [Google Scholar] [CrossRef]
- Zulfikar, Z.; Away, Y.; Shahnaz Noor, R. FPGA-based Design System for a Two-Segment Fibonacci LFSR Random Number Generator. Int. J. Electr. Comput. Eng. (IJECE) 2017, 7, 1882. [Google Scholar] [CrossRef]
- Oduwole, H.; Shehu, S.; Adegoke, G.; Onubogu, J. Fibonacci Random Number Generator using Lehmer’s Algorithm. Math. Theory Model. 2013, 3, 56–62. [Google Scholar]
- Orue, A.B.; Montoya, F.; Hernández Encinas, L. Trifork, a New Pseudorandom Number Generator Based on Lagged Fibonacci Maps. J. Comput. Sci. Eng. 2010, 2, 46–51. [Google Scholar]
- Kamikawa, N.; Umeo, H. A construction of five-state real-time Fibonacci sequence generator. Artif. Life Robot. 2016, 21, 531–539. [Google Scholar] [CrossRef]
- Opoku-Mensah, E.; Abilimi, C.A.; Boateng, F.O. Comparative Analysis of Efficiency of Fibonacci Random Number Generator Algorithm and Gaussian Random Number Generator Algorithm in a Cryptographic System. Comput. Eng. Intell. Syst. 2013, 4, 50–57. [Google Scholar]
- Srinivasan, A.; Mascagni, M.; Ceperley, D. Testing parallel random number generators. Parallel Comput. 2003, 29, 69–94. [Google Scholar] [CrossRef]
- Bassham, L.; Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Leigh, S.; Levenson, M.; Vangel, M.; Heckert, N.; Banks, D. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications. Special Publication (NIST SP); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2010. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=906762 (accessed on 21 November 2022).
- Sýs, M.; Říha, Z. Faster Randomness Testing with the NIST Statistical Test Suite. In Security, Privacy, and Applied Cryptography Engineering—SPACE 2014; Chakraborty, R.S., Matyas, V., Schaumont, P., Eds.; Lecture Notes in Computer Science Book Series; Springer: Cham, Switzerland, 2014; Volume 8804. [Google Scholar] [CrossRef]
- A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; NIST SP 800-22 version 1a; NIST: Gaithersburg, MD, USA, 2010. Available online: http://csrc.nist.gov/publications/nistpubs//SP80022rev1a.pdf (accessed on 20 November 2022).
- Maksymovych, V.N.; Mandrona, M.N.; Garasimchuk, O.I.; Kostiv, Y.M. A Study of the Characteristics of the Fibonacci Modified Additive Generator with a Delay. J. Autom. Inf. Sci. 2016, 48, 76–82. [Google Scholar] [CrossRef]
- Maksymovych, V.; Harasymchuk, O.; Karpinski, M.; Shabatura, M.; Jancarczyk, D.; Kajstura, K. A New Approach to the Development of Additive Fibonacci Generators Based on Prime Numbers. Electronics 2021, 10, 2912. [Google Scholar] [CrossRef]
- Maksymovych, V.; Shabatura, M.; Harasymchuk, O.; Karpinski, M.; Jancarczyk, D.; Sawicki, P. Development of Additive Fibonacci Generators with Improved Characteristics for Cybersecurity Needs. Appl. Sci. 2022, 12, 1519. [Google Scholar] [CrossRef]
- Schneier, B. Special Algorithms for Protocols. In Applied Cryptography, 2nd ed.; Wiley: Hoboken, NJ, USA, 2015; pp. 527–557. ISBN 0471128457. [Google Scholar]
- Gorbenko, A.; Popov, V. Reduction of the uncertainty in feature tracking. Appl. Intell. 2018, 48, 4626–4645. [Google Scholar] [CrossRef]
- Guan, S.-U.; Zhang, S. Pseudorandom number generation based on controllable cellular automata. Future Gener. Comput. Syst. 2004, 20, 627–641. [Google Scholar] [CrossRef]
- Mandrona, M.; Maksymovych, V.; Harasymchuk, O.; Kostiv, Y. Generator of pseudorandom bit sequence with increased cryptographic immunity. Metall. Min. Ind. 2014, 6, 24–28. [Google Scholar]
- Maksymovych, V.N.; Harasymchuk, O.I.; Mandrona, M.N. Designing Generators of Poisson Pulse Sequences Based on the Additive Fibonacci Generators. J. Autom. Inf. Sci. 2017, 49, 1–13. [Google Scholar] [CrossRef]
- Maksymovych, V.; Harasymchuk, O.; Opirskyy, I. The Designing and Research of Generators of Poisson Pulse Sequences on Base of Fibonacci Modified Additive Generator. In International Conference on Theory and Applications of Fuzzy Systems and Soft Computing—ICCSEEA 2018: Advances in Computer Science for Engineering and Education, Warsaw, Poland, 27–28 August 2018; Springer: Cham, Switzerland, 2018; Volume 754, pp. 43–53. [Google Scholar] [CrossRef]
- Maksymovych, V.; Mandrona, M.; Harasymchuk, O. Dosimetric Detector Hardware Simulation Model Based on Modified Additive Fibonacci Generator. Adv. Intell. Syst. Comput. 2020, 938, 162–171. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).