Classification of Events Violating the Safety of Physical Layers in Fiber-Optic Network Infrastructures
Abstract
1. Introduction
2. Related Studies
3. Methodology
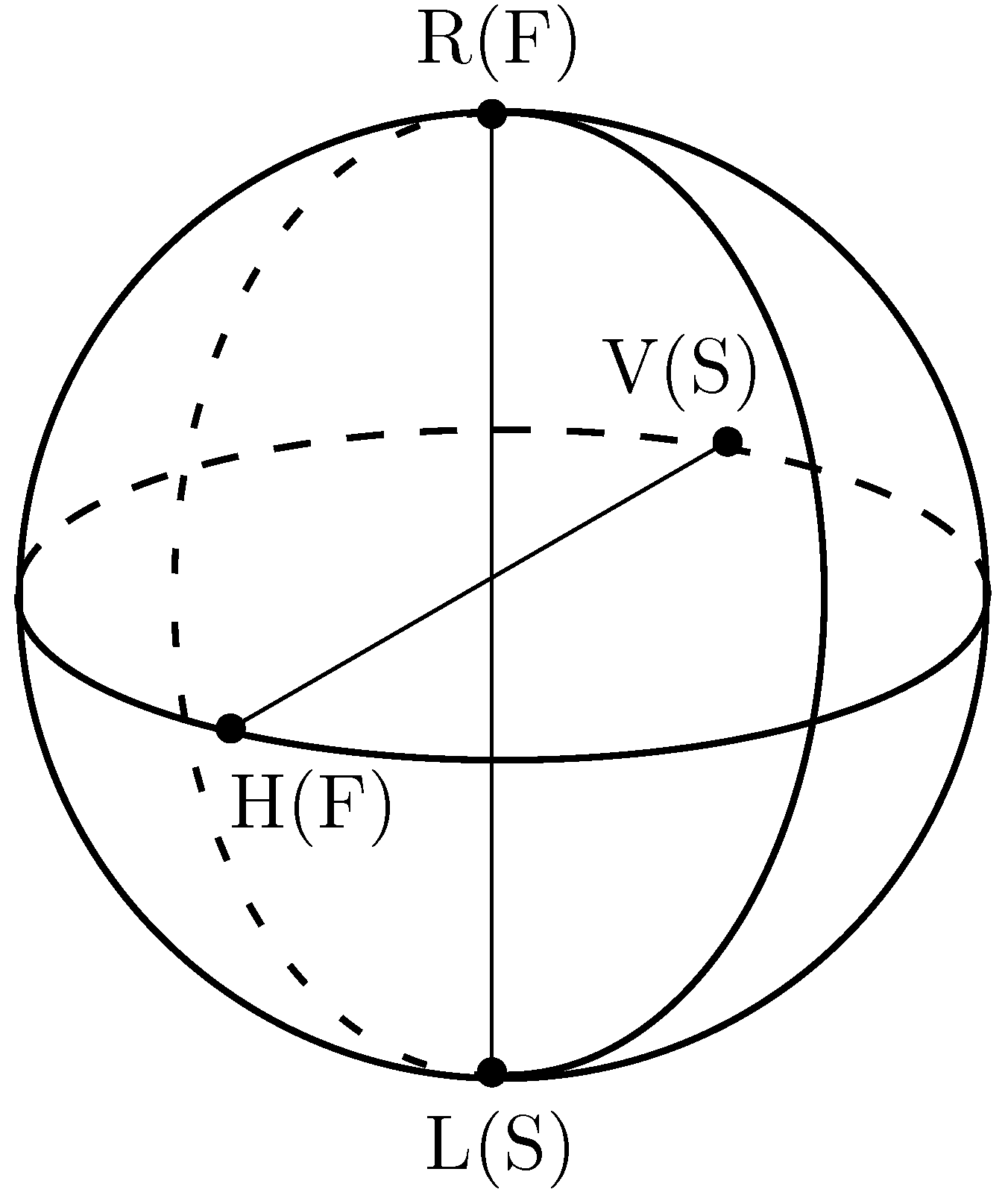
- Linear—electric field concentrated in one plane along the direction of propagation.
- Circular—the electric field consists of two mutually perpendicular components with the same amplitude that are shifted by a phase .
- Elliptic—The electric field can be described by an ellipse due to the different amplitudes and/or different phases of the components.
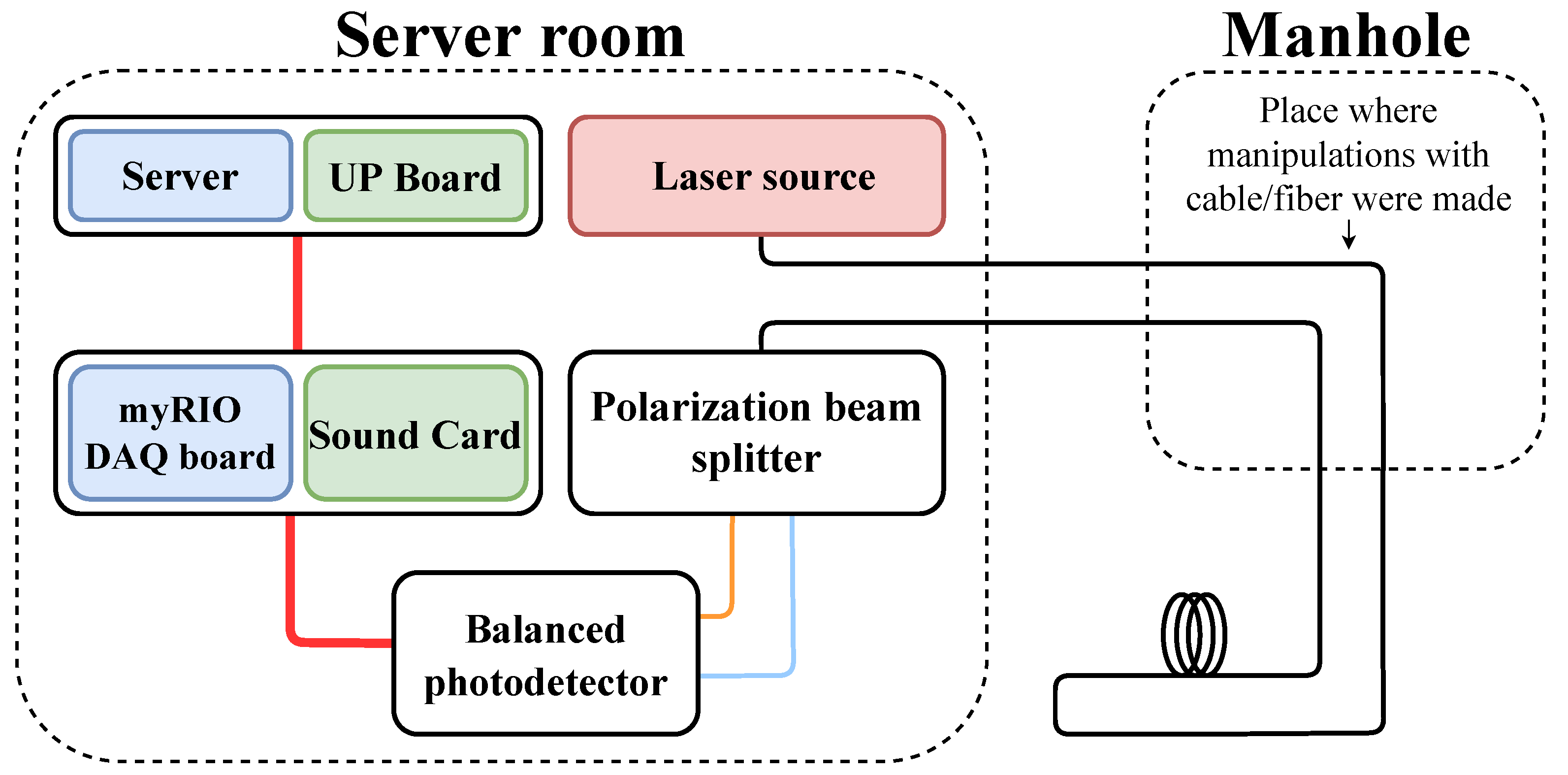
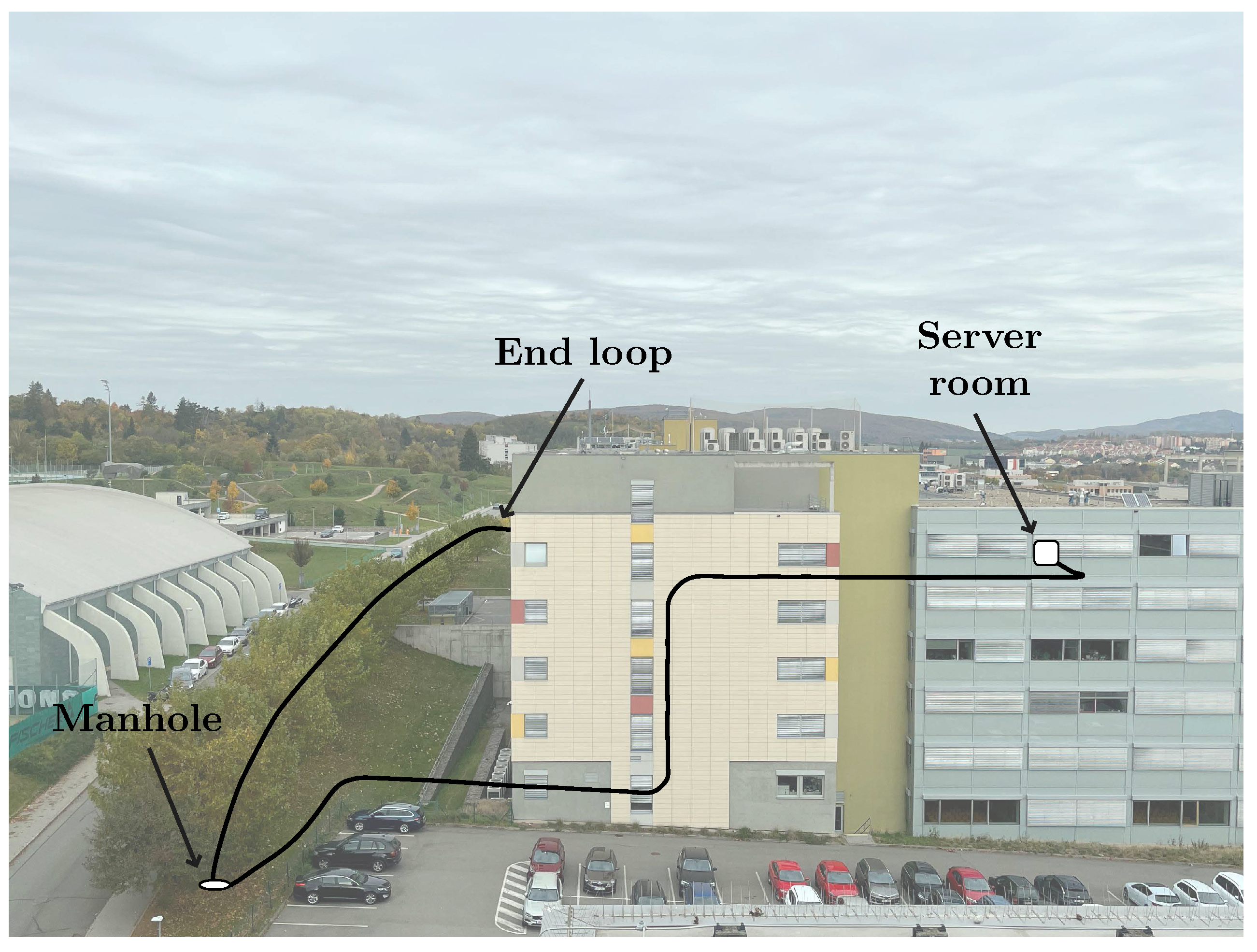
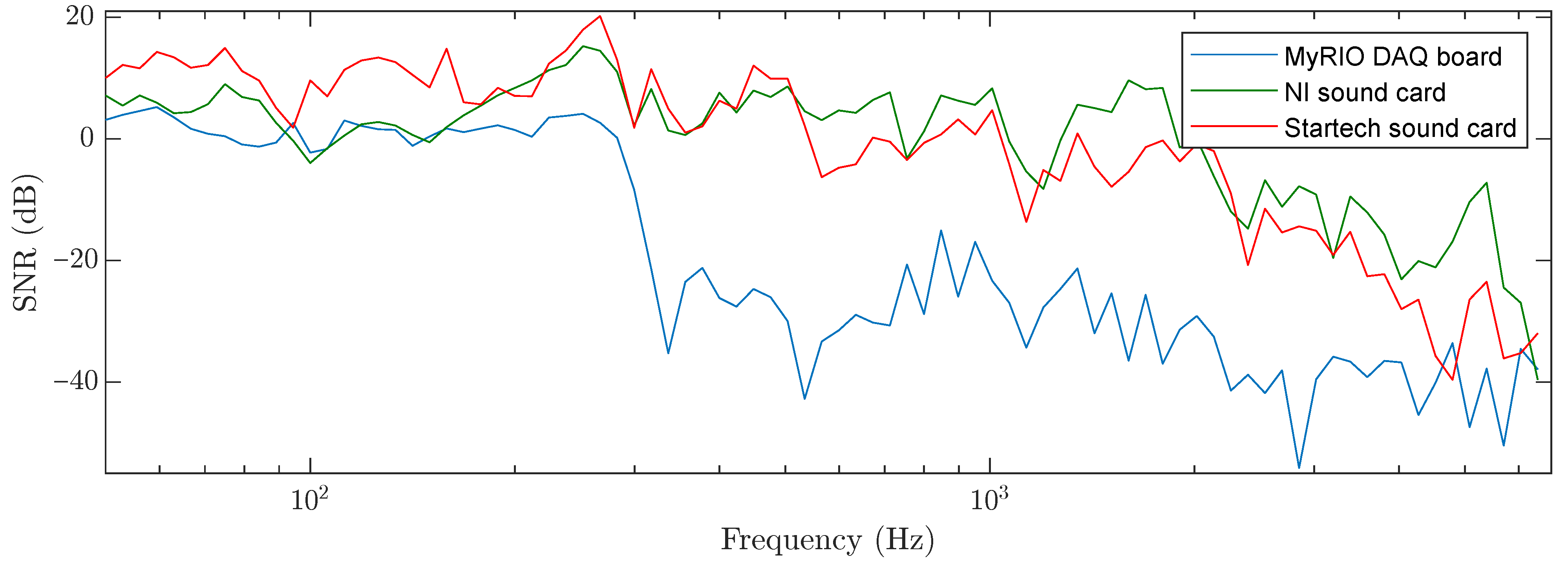
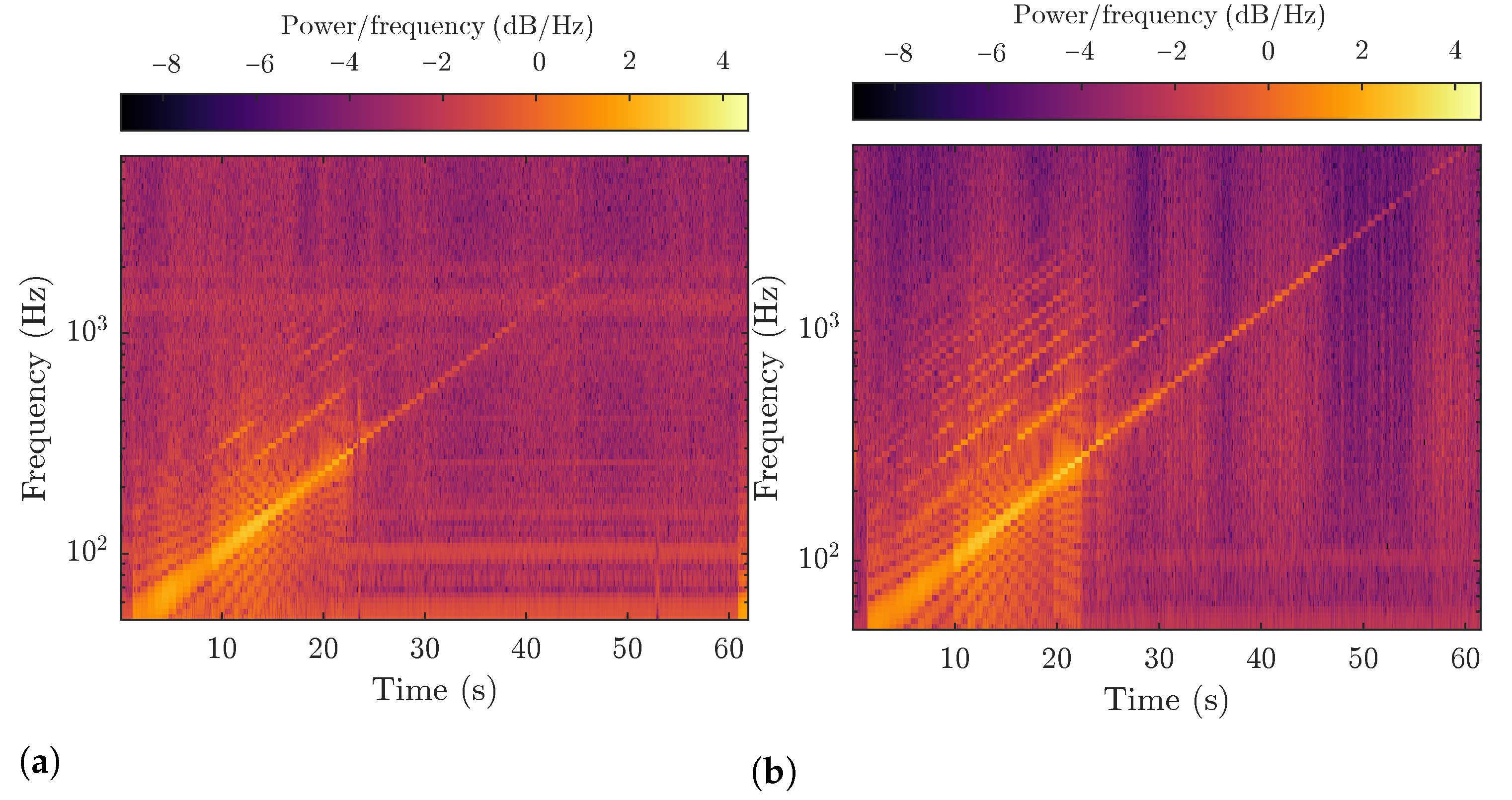
4. Experimental Setup
5. Neural Network Architecture and Training
5.1. Dataset
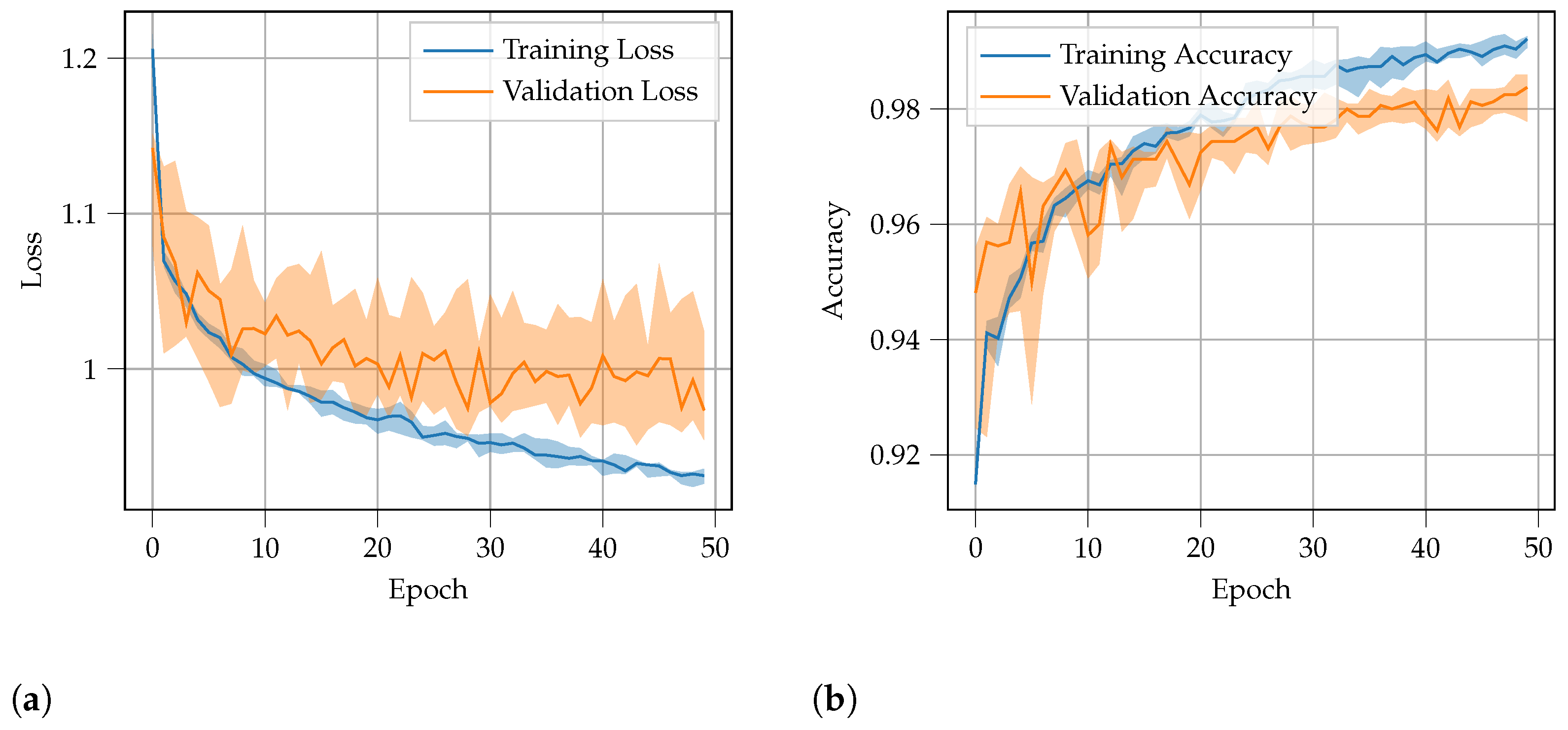
5.2. Training
6. Results and Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Dejdar, P.; Hanak, P.; Munster, P.; Horvath, T. Polarization Monitor for High-speed State of Polarization Changes Detection. Int. J. Adv. Telecommun. Electrotech. Signals Syst. 2021, 10, 13–17. [Google Scholar] [CrossRef]
- Li, J.; Zhou, X.; Zhang, M.; Zhang, J.; Qiao, L.; Zhao, L.; Yin, Z. Temperature Resolution Improvement in Raman-Based Fiber-Optic Distributed Sensor Using Dynamic Difference Attenuation Recognition. Sensors 2020, 20, 6922. [Google Scholar] [CrossRef]
- Dejdar, P.; Záviška, P.; Valach, S.; Münster, P.; Horváth, T. Image Edge Detection Methods in Perimeter Security Systems Using Distributed Fiber Optical Sensing. Sensors 2022, 22, 4573. [Google Scholar] [CrossRef]
- Ershov, I.A.; Stukach, O.V. Choice of Wavelet for Filtering of Signal from Fiber-Optic Temperature Sensor. In Proceedings of the 2022 Moscow Workshop on Electronic and Networking Technologies (MWENT), Moscow, Russia, 9–11 June 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Zhou, R.; Gao, H.; Feng, Z.; Qiao, X. Simulation and hardware implementation of demodulation for fiber optic seismic sensor with linear edge filtering method. Opt. Fiber Technol. 2020, 60, 102384. [Google Scholar] [CrossRef]
- Lou, K.; Peng, C.Y.; Tang, W.S.; Hu, Z.L.; Xu, P.; Tie, X. Application of Acoustic Horns for the Amplification of Fiber Optic Vector Hydrophone Signal. In Proceedings of the 2021 4th International Conference on Information Communication and Signal Processing (ICICSP), Shenzhen, China, 26–28 November 2021; pp. 139–142. [Google Scholar] [CrossRef]
- Spurny, V.; Munster, P.; Tomasov, A.; Horvath, T.; Skaljo, E. Physical layer components security risks in optical fiber infrastructures. Sensors 2022, 22, 588. [Google Scholar] [CrossRef] [PubMed]
- Liu, F.; Zhang, H.; Li, X.; Li, Z.; Wang, H. Intrusion identification using GMM-HMM for perimeter monitoring based on ultra-weak FBG arrays. Opt. Express 2022, 30, 17307–17320. [Google Scholar] [CrossRef] [PubMed]
- Wang, M.; Sun, Z.; Zhang, F.; Min, L.; Li, S.; Jiang, S. Application Research of FBG Vibration Sensor Used for Perimeter Security. In Proceedings of the 2018 IEEE 3rd Optoelectronics Global Conference (OGC), Shenzhen, China, 4–7 September 2018; pp. 94–97. [Google Scholar] [CrossRef]
- Cai, Y.; Yan, W.; Liu, H.; Sun, Y.; Zhou, X. Security monitoring of smart campus using distributed fiber optic acoustic sensing. In Proceedings of the AOPC 2020: Optical Information and Network; Zhang, J., Fu, S., Zhang, H., Eds.; International Society for Optics and Photonics, SPIE: Bellingham, WA, USA, 2020; Volume 11569, p. 115690L. [Google Scholar] [CrossRef]
- Duckworth, G.L.; Ku, E.M. OptaSense distributed acoustic and seismic sensing using COTS fiber optic cables for infrastructure protection and counter terrorism. In Proceedings of the Sensors, and Command, Control, Communications, and Intelligence (C3I) Technologies for Homeland Security and Homeland Defense XII; Carapezza, E.M., Ed.; International Society for Optics and Photonics, SPIE: Bellingham, WA, USA, 2013; Volume 8711, p. 87110G. [Google Scholar] [CrossRef]
- Kishida, K.; Imai, M.; Kawabata, J.; Guzik, A. Distributed Optical Fiber Sensors for Monitoring of Civil Engineering Structures. Sensors 2022, 22, 4368. [Google Scholar] [CrossRef]
- Stepanov, K.V.; Zhirnov, A.A.; Sazonkin, S.G.; Pnev, A.B.; Bobrov, A.N.; Yagodnikov, D.A. Non-Invasive Acoustic Monitoring of Gas Turbine Units by Fiber Optic Sensors. Sensors 2022, 22, 4781. [Google Scholar] [CrossRef]
- Shi, J.; Cui, K.; Wang, H.; Ren, Z.; Zhu, R. An Interferometric Optical Fiber Perimeter Security System Based on Multi-Domain Feature Fusion and SVM. IEEE Sens. J. 2021, 21, 9194–9202. [Google Scholar] [CrossRef]
- Gu, X.; Wang, T.; Hou, S.; Peng, J.; Wang, H.; Xia, Q. Multi-Feature-Based Intrusion Detection for Optical Fiber Perimeter Security System: A Aase Study. In Proceedings of the 2018 IEEE 17th International Conference on Cognitive Informatics & Cognitive Computing (ICCI*CC), Berkeley, CA, USA, 16–18 July 2018; pp. 448–453. [Google Scholar] [CrossRef]
- Wang, N.; Fang, N.; Wang, L. Intrusion recognition method based on echo state network for optical fiber perimeter security systems. Opt. Commun. 2019, 451, 301–306. [Google Scholar] [CrossRef]
- Yin, S.; Ruffin, P.B.; Yu, F.T.S. Fiber Optic Sensors, 2nd ed.; CRC Press: Boca Raton, FL, USA, 2017; pp. 1–477, Cited By:11. [Google Scholar]
- Munster, P.; Horvath, T.; Vojtech, J. Distributed Sensing Based on Interferometry and Polarization Methods for Use in Fibre Infrastructure Protection. Sensors 2019, 19, 1810. [Google Scholar] [CrossRef] [PubMed]
- Yablochkin, K.A.; Dashkov, M.V.; Dashkov, V.M. Investigation of the vibration influences on the optical fiber polarization characteristics. In Proceedings of the Optical Technologies for Telecommunications 2018; Andreev, V.A., Bourdine, A.V., Burdin, V.A., Morozov, O.G., Sultanov, A.H., Eds.; International Society for Optics and Photonics, SPIE: Bellingham, WA, USA, 2019; Volume 11146, p. 111461P. [Google Scholar] [CrossRef]
- Šlapák, M.; Vojtěch, J.; Havliš, O.; Slavík, R. Monitoring of Fibre Optic Links With a Machine Learning-Assisted Low-Cost Polarimeter. IEEE Access 2020, 8, 183965–183971. [Google Scholar] [CrossRef]
- Munster, P.; Horvath, T.; Sysel, P.; Vojtech, J.; Velc, R. Comparison of interferometry based and polarization based sensing systems for use in fiber infrastructure protection. In Proceedings of the 2017 International Workshop on Fiber Optics in Access Network (FOAN), Sarajevo, Bosnia and Herzegovina, 6–8 November 2017; pp. 1–3. [Google Scholar] [CrossRef]
- Wada, A.; Tanaka, S.; Takahashi, N. Simultaneous measurement of vibration and temperature using a Fabry-Perot interferometer in polarization maintaining fiber and laser diodes. In Proceedings of the 25th International Conference on Optical Fiber Sensors; Chung, Y., Jin, W., Lee, B., Canning, J., Nakamura, K., Yuan, L., Eds.; International Society for Optics and Photonics, SPIE: Bellingham, WA, USA, 2017; Volume 10323, p. 1032326. [Google Scholar] [CrossRef]
- Wang, X.; Hu, J.; Wang, F.; Yong, Y.; Zhang, Y.; Xue, M.; Zhang, X.; Pan, S. Multi-vibration detection by probe pulses with ergodic SOPs in a POTDR system. Opt. Express 2018, 26, 28349–28362. [Google Scholar] [CrossRef] [PubMed]
- Shaneman, K.; Gray, S. Optical network security: Technical analysis of fiber tapping mechanisms and methods for detection & prevention. In Proceedings of the IEEE MILCOM 2004. Military Communications Conference, Monterey, CA, USA, 31 October–3 November 2004; Volume 2, pp. 711–716. [Google Scholar] [CrossRef]
- Skorin-Kapov, N.; Furdek, M.; Zsigmond, S.; Wosinska, L. Physical-layer security in evolving optical networks. IEEE Commun. Mag. 2016, 54, 110–117. [Google Scholar] [CrossRef]
- Song, H.; Li, Y.; Liu, M.; Wang, K.; Li, J.; Zhang, M.; Zhao, Y.; Zhang, J. Experimental study of machine-learning-based detection and location of eavesdropping in end-to-end optical fiber communications. Opt. Fiber Technol. 2022, 68, 102669. [Google Scholar] [CrossRef]
- Abdelli, K.; Cho, J.Y.; Azendorf, F.; Griesser, H.; Tropschug, C.; Pachnicke, S. Machine-learning-based anomaly detection in optical fiber monitoring. J. Opt. Commun. Netw. 2022, 14, 365–375. [Google Scholar] [CrossRef]
- Liu, M.; Li, Y.; Song, H.; Tu, Z.; Zhao, Y.; Zhang, J. Experimental Demonstration of Optical Fiber Eavesdropping Detection Based on Deep Learning. In Proceedings of the Asia Communications and Photonics Conference, Chengdu, China, 2–5 November 2019; Optical Society of America: Washington, DC, USA, 2019; p. T1H-4. [Google Scholar]
- Tomasov, A.; Dejdar, P.; Horvath, T.; Munster, P. Physical fiber security by the state of polarization change detection. In Proceedings of the Fiber Optic Sensors and Applications XVIII; Lieberman, R.A., Sanders, G.A., Scheel, I.U., Eds.; International Society for Optics and Photonics, SPIE: Orlando, FL, USA, 2022; Volume 12105, p. 1210507. [Google Scholar] [CrossRef]
- Kumar, A.; Ghatak, A. Basic Concepts of Polarization. In Polarization of Light with Applications in Optical Fibers; SPIE: Bellingham, WA, USA, 2011; pp. 19–46. [Google Scholar] [CrossRef]
- Kumar, A.; Ghatak, A. Jones Vector Representation of Polarized Light. In Polarization of Light with Applications in Optical Fibers; SPIE: Bellingham, WA, USA, 2011; pp. 75–97. [Google Scholar] [CrossRef]
- Kumar, A.; Ghatak, A. The Stokes Parameters Representation. In Polarization of Light with Applications in Optical Fibers; SPIE: Bellingham, WA, USA, 2011; pp. 97–120. [Google Scholar] [CrossRef]
- Padgett, M.J.; Courtial, J. Poincaré-sphere equivalent for light beams containing orbital angular momentum. Opt. Lett. 1999, 24, 430–432. [Google Scholar] [CrossRef] [PubMed]
- Dejdar, P.; Tomasov, A.; Munster, P.; Horvath, T. Vibration caused by train detection using state-of-polarization changes measurement. In Proceedings of the Fiber Optic Sensors and Applications XVIII; Lieberman, R.A., Sanders, G.A., Scheel, I.U., Eds.; International Society for Optics and Photonics, SPIE: Bellingham, WA, USA, 2022; Volume 12105, p. 1210506. [Google Scholar] [CrossRef]
- Xiao, L.; Wang, Y.; Li, Y.; Bai, Q.; Liu, X.; Jin, B. Polarization Fading Suppression for Optical Fiber Sensing: A Review. IEEE Sens. J. 2022, 22, 8295–8312. [Google Scholar] [CrossRef]
- Paszke, A.; Gross, S.; Massa, F.; Lerer, A.; Bradbury, J.; Chanan, G.; Killeen, T.; Lin, Z.; Gimelshein, N.; Antiga, L.; et al. PyTorch: An Imperative Style, High-Performance Deep Learning Library. In Advances in Neural Information Processing Systems 32; Curran Associates, Inc.: Red Hook, NY, USA, 2019; pp. 8024–8035. [Google Scholar]
- Semenov, A.; Boginski, V.; Pasiliao, E.L. Neural Networks with Multidimensional Cross-Entropy Loss Functions. In Proceedings of the International Conference on Computational Data and Social Networks; Springer: Berlin/Heidelberg, Germany, 2019; pp. 57–62. [Google Scholar]
- Phan, T.H.; Yamamoto, K. Resolving class imbalance in object detection with weighted cross entropy losses. arXiv 2020, arXiv:2006.01413. [Google Scholar]
- Kingma, D.P.; Ba, J. Adam: A method for stochastic optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]




| Label / Subset | Training | Validation | Testing | Total |
|---|---|---|---|---|
| Manipulation | 918 | 115 | 115 | 1148 |
| Physical disconnection | 606 | 76 | 76 | 758 |
| Re-connection | 415 | 52 | 51 | 518 |
| Knocking | 93 | 10 | 10 | 113 |
| Regular state | 4247 | 531 | 530 | 5308 |
| Total | 6279 | 774 | 772 | 7845 |
| DAQ Device | ADC | Sample Rate | Bit Resolution | Price (EUR) |
|---|---|---|---|---|
| NI MyRIO 1950 | XADC | up to 500 kHz | 12 | 530 |
| NI Komplete audio 2 | delta-sigma | up to 192 kHz | 24 | 129 |
| Startech ICUSBAUDIO2D | delta-sigma | up to 96 kHz | 24 | 43 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ruzicka, M.; Jabloncik, L.; Dejdar, P.; Tomasov, A.; Spurny, V.; Munster, P. Classification of Events Violating the Safety of Physical Layers in Fiber-Optic Network Infrastructures. Sensors 2022, 22, 9515. https://doi.org/10.3390/s22239515
Ruzicka M, Jabloncik L, Dejdar P, Tomasov A, Spurny V, Munster P. Classification of Events Violating the Safety of Physical Layers in Fiber-Optic Network Infrastructures. Sensors. 2022; 22(23):9515. https://doi.org/10.3390/s22239515
Chicago/Turabian StyleRuzicka, Michal, Lukas Jabloncik, Petr Dejdar, Adrian Tomasov, Vladimir Spurny, and Petr Munster. 2022. "Classification of Events Violating the Safety of Physical Layers in Fiber-Optic Network Infrastructures" Sensors 22, no. 23: 9515. https://doi.org/10.3390/s22239515
APA StyleRuzicka, M., Jabloncik, L., Dejdar, P., Tomasov, A., Spurny, V., & Munster, P. (2022). Classification of Events Violating the Safety of Physical Layers in Fiber-Optic Network Infrastructures. Sensors, 22(23), 9515. https://doi.org/10.3390/s22239515







