1. Introduction
The industrial internet of things (IIoT) is a system of interconnected devices used in industrial settings to monitor and control machinery, production lines, and human labor in real time to boost efficiency. The notion of “Industry 4.0” refers to a subset of the IIoT that places an emphasis on worker protection and increased output [
1]. Nowadays, the IIoT infrastructure is driven by the internet of things (IoT), cloud and edge computing, cyber security, AI and machine learning, and digital twin [
2]. In order to decrease failures and save time and investment, companies are considering AI-powered visual insights to replace manual inspection business models. Such as in [
3], a classification model between microseismic and blasts events using the convolutional neural network (CNN) was proposed to analyze the mechanical parameters contained in microseismic events for providing accurate information of rockmass. Manufacturers can use machine learning algorithms to detect problems as soon as possible [
4]. On the other hand, “Industry 5.0” refers to a future workplace environment in which humans and smart robots coexist. Industry 5.0 aims to combine cognitive computing capabilities with human intellect and resourcefulness in collaborative operations as robots in the workplace become more intelligent and interconnected [
5]. AI, big data, supply chain, digital transformation, machine learning, and the IoT have all been identified as some of the most popular and widely used enablers for Industry 5.0 [
6]. Moreover, the IoT-enabled industries have a big impact on the environment since they use scarce resources and lots of energy during production, usage, and recycling. In response, the area of research known as the green IoT has emerged to reduce this carbon effect [
7]. The “industrial revolution” is propelled by increased connectivity, openness of data, decentralized and automated decision making, and technological support. Industries may now collect and analyze data in real time through IoT systems for monitoring, exchanging data, and evaluating the state of the environment. When it comes to the IIoT, speed and efficiency are paramount. Large-scale deployments are required for complex systems. Therefore, it is essential that sensors maintain their performance over time while keeping costs reasonable. If the information from these sensors is utilized to make important choices, then latency is a measure of performance. As a popular protocol for the IoT, the message queuing telemetry transport (MQTT) is highly regarded. It is flawless because of its small code size, seamless integration, and outstanding performance [
8]. In addition, an essential feature of the IIoT for cyber–physical systems is the capacity for near real-time data streaming, which is necessary for the seamless integration of the physical and digital worlds. The manufacturer may obtain valuable insights from the acquired data. It is also possible to utilize the data to spot subtle problems with the manufacturing facility’s infrastructure. Furthermore, the data may be used for improvement and prediction, giving the data from the IoT devices real value. Eighty-four percent of businesses surveyed for their big data and cloud strategy cited the need for a unified platform to facilitate the transfer of information to the cloud as a top priority [
9]. Furthermore, the manufacturing industry must modify its practices in response to reducing manpower, economic convenience, and ecological norms. Management of production needs adaptable decision-making procedures and the ability to self-configure. Data collected in real time from the factory floor may help guide strategy. Through real-time monitoring, any advanced system in the IIoT may make choices and delegate authority to various stakeholders in an organization so that they can act on data in real time [
10].
However, there are grave concerns relating to energy savings, real-time performance, cohabitation, compatibility, security, and privacy in the adoption of the “Industry 4.0” level IIoT infrastructure [
11]. In Ref. [
12], the healthcare industrial IoT (HealthIIoT) was proposed to monitor, track, and store patients’ healthcare information for continuous care, with data watermarked before being sent to the cloud for secure, safe, and high-quality health monitoring. However, they did not utilize any AI algorithms or features. According to [
9], service-oriented architecture (SOA) was introduced to handle the heterogeneous data of IoT and IIoT devices. However, they were unable to provide enough details and an appropriate solution for edge IoT sensors that communicate securely with a cloud server. Reference [
10] proposed methods for facilitating the digital transformation of a manufacturing line and tying such methods into the concept of the digital twin. Methods for implementing online monitoring using both traditional and IIoT sensors and collecting the resulting data were discussed. However, this article did not go into sufficient detail on the edge computing devices and the interconnection of the vast IIoT networking architecture. Identical articles, such as [
13,
14,
15,
16,
17,
18,
19], proposed a three-terminal collaborative platform (TTCP), integration of AI and IIoT technologies, transparency relying upon statistical theory (TRUST), deep learning (DL), and AI-enabled software-defined IIoT network (AI-SDIN), to implement “Industry 4.0” and “Industry 5.0” facilities. Nevertheless, each of these approaches brings its own unique perspective, ignoring the global interconnected IIoT networking system. A LoRaWAN-based local IIoT infrastructure was introduced in [
20] while the proposed system covers the global IIoT framework. In addition, the authors implemented a state-of-the-art open-source P2P energy trading platform in [
21] that makes use of IoT and blockchain technology. It was unexpected to discover that they declared Node-RED as their MQTT broker, as Node-RED can only act as a MQTT client while making a connection with a MQTT broker service such as the Mosquitto MQTT broker according to Refs. [
22,
23]. Furthermore, their proposed system is neither https- nor MQTTS-enabled, and customers would have to pay for a limited number of infrastructure components, such as private blockchain service, to use it. On top of that, they have not integrated AI into their system. Similar articles, such as [
24,
25,
26,
27,
28,
29], introduced interesting technologies, such as augmented password-only authentication and key exchange (AugPAKE), attribute-based encryption (ABE), oblivious transfer (OT), generic MQTT protocol with Mosquitto broker, and so on. Each of these publications is unaware of the integrated global IIoT systems and open-source, such as openssl [
30], based remarkable encryption protocols, such as utilizing self-certified certificates in TLS and SSL cryptographic protocols, which provide an extremely secure and incredibly fast communication system in an integrated IIoT infrastructure. Moreover, a simulation-based smart controller device was introduced in [
31] for classifying the contracted load through a data-acquisition approach, whereas the proposed SDAD is integrated and implemented on a real system. The authors in [
32] developed machine-learning-based abnormal voltage regulation detection in PV systems, where the proposed architecture is focused on anomaly data detection in every electrical appliance. For continuous energy flow monitoring purposes [
33], the offered technique develops an AI integrated real-time monitoring system through the IIoT framework.
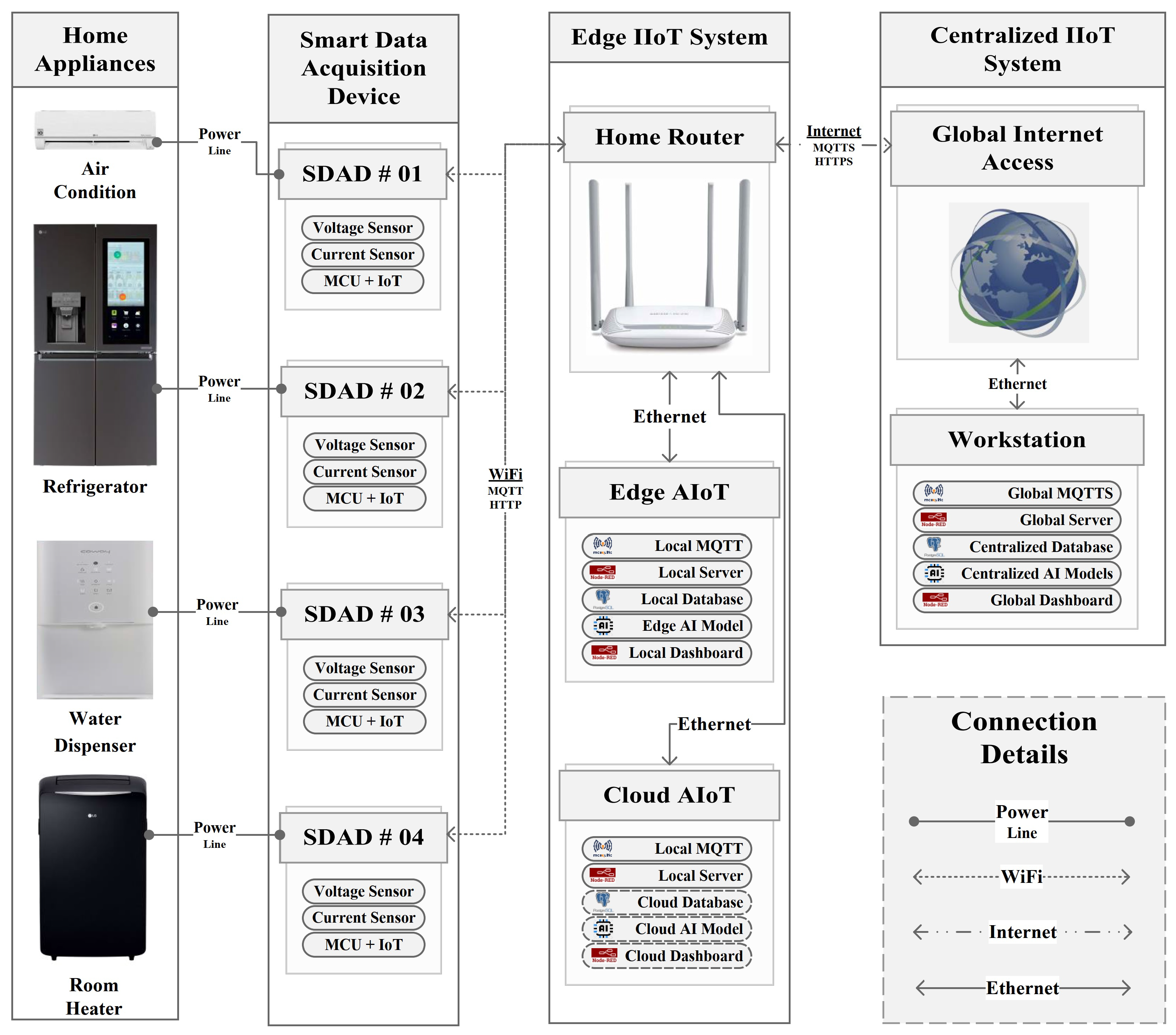
In this article, we implemented a globally distributed, secure, resilient, and integrated IIoT infrastructure for real-time energy data acquisition, management, monitoring, and anomaly detection. Edge and cloud AI were also integrated on the basis of “Industry 4.0” and “Industry 5.0” applications. Several algorithms, flow-charts, as well as customized devices such as SDAD were exposed. Multiple edge servers, a global MQTTS broker, and an integrated cloud server were developed. Open-source-based software such as Node-RED, Mosquitto, openssl, Visual Studio Code, etc., were utilized. In summary, the primary contribution of our research comprises the following:
Design and development of smart data acquisition devices, which are used to measure the power consumption of home appliances, focused on keeping them compact, sturdy, and economical.
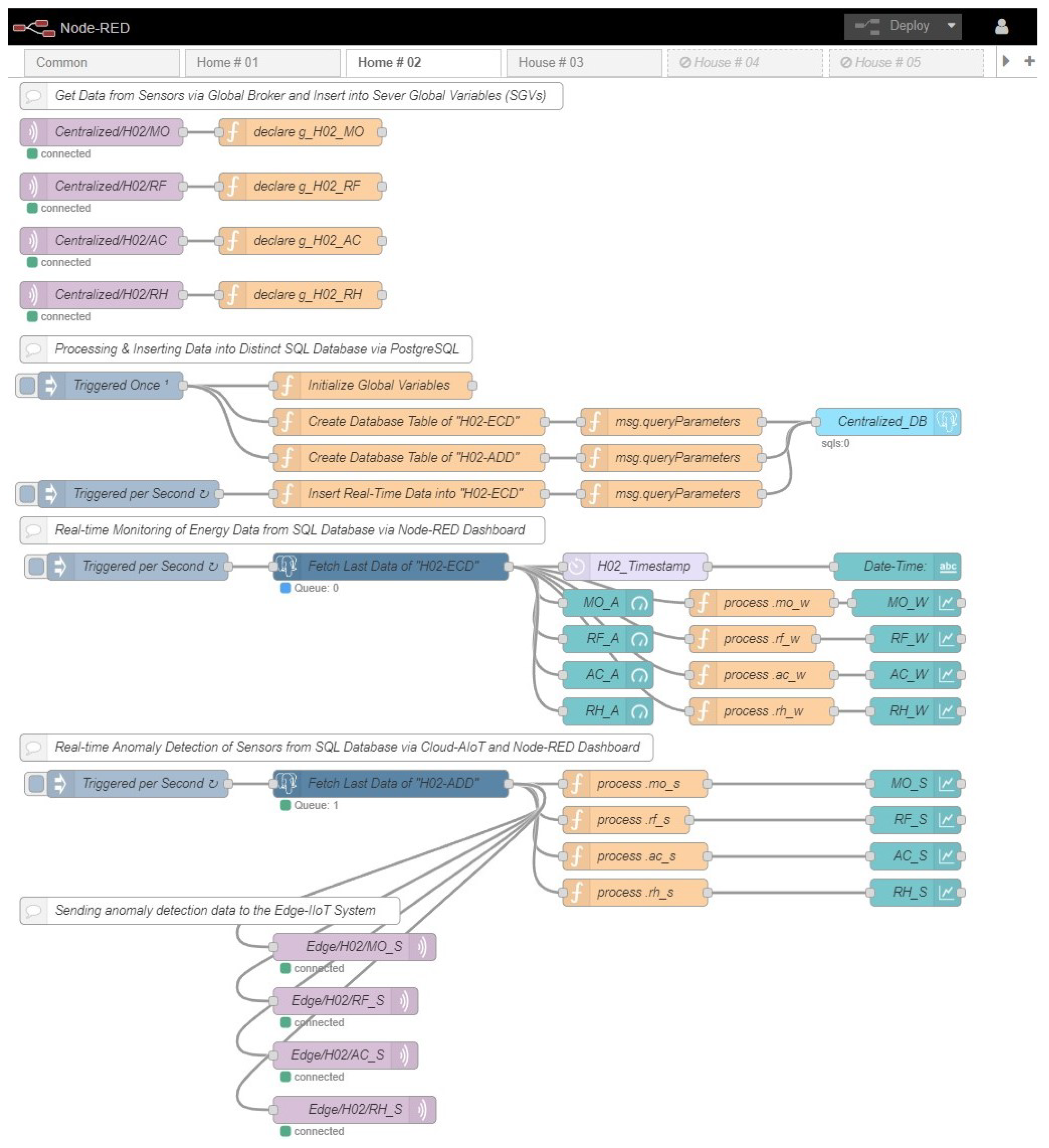
Afterward, HTTPS-enabled edge servers utilizing Node-RED are built for acquiring data from SDADs and inserting these data into databases.
Implementation of a TLS-enabled global MQTTS broker leveraging open-source software “Mosquitto” for sharing information between edge servers and cloud/centralized servers.
Construction of SQL databases through “PostgreSQL” in order to handle heterogeneous big data.
Incorporating edge and cloud AI into the system to identify outliers in the sensor readings.
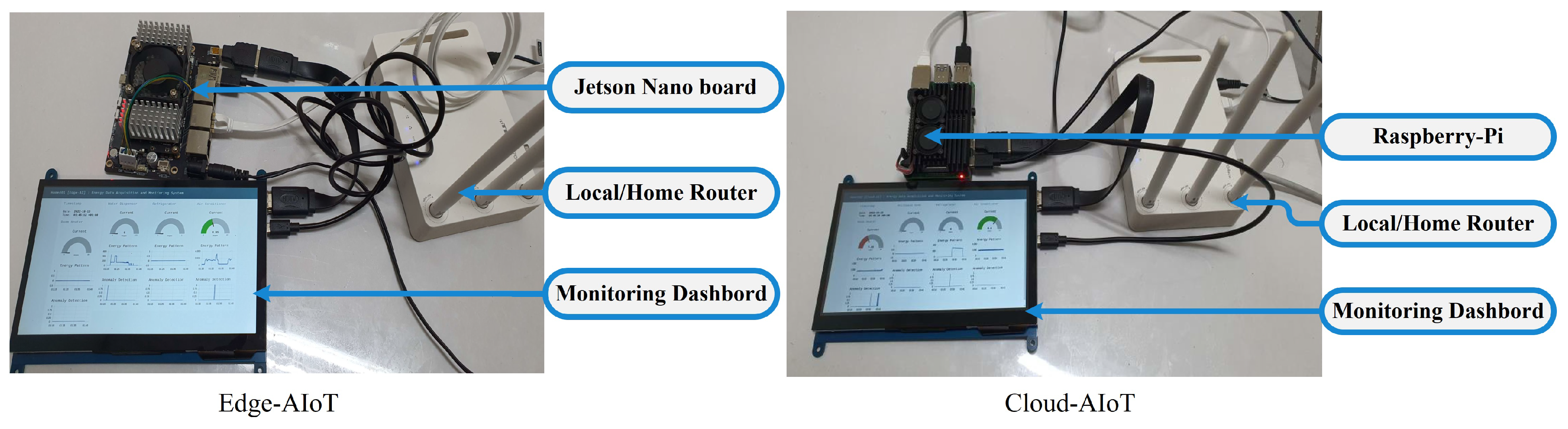
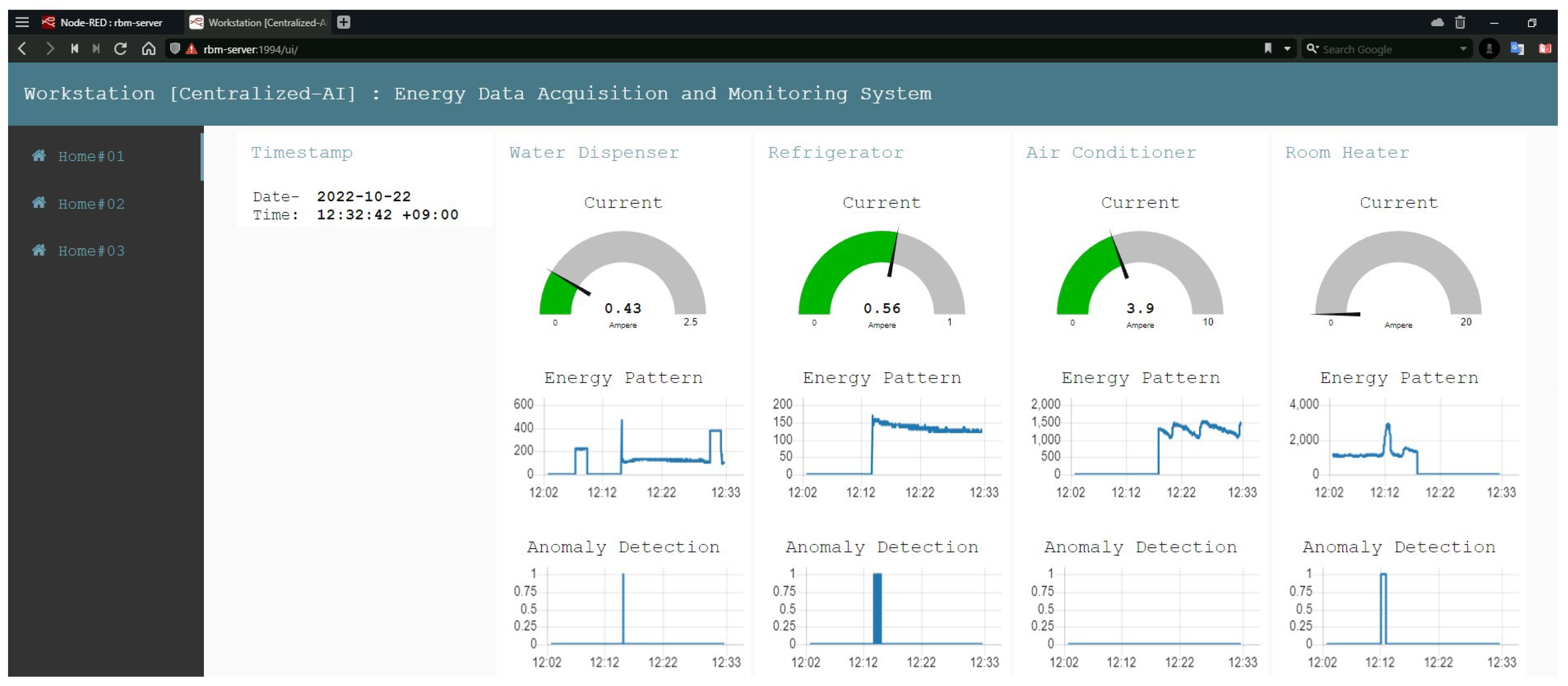
Finally, individual and centralized dashboards were implemented for real-time monitoring of the system.
On the basis of the above contributions, it is clear that our suggested system is highly advantageous in the IIoT system due to its simple architecture, secured and swift connectivity, processing capabilities of heterogeneous massive data, integration with AI, and real-time monitoring dashboards (that anyone with the proper credentials can access at any time, from any location). In addition, open-source software is used in every aspect of the proposed system, resulting in cost savings. The outline of the paper looks like the following: The proposed methodology is described in
Section 2. Implementations of software and hardware are demonstrated in
Section 3.
Section 4 induces system evolution and experimental outcomes. In
Section 5, a brief discussion and the future direction of this study are revealed.
5. Conclusions and Future Work
This article proposes a secure and integrated global IIoT infrastructure that comprises edge and cloud AI. The aforementioned infrastructure was developed to aggregate, analyze, and inspect heterogeneous data in real-time for the purposes of monitoring and anomaly detection. Customized SDADs are developed and implemented to collect various types of data from different sensors. To eliminate transients and distortion of the energy data, two effective algorithms are proposed. TLS protocol, hash-coded authorization, and a public IP address are used to create a globally secure broker system for the IIoT. In order to manage disparate types of large data, the PostgreSQL database system is deployed. Edge IIoT servers with HTTPS support are created so that data can be transmitted securely from sensor nodes to edge and cloud databases via the MQTTS protocol. After data of varying types are extracted from a SQL database, individual AI models can be trained. Our advanced algorithm is used in edge IIoT systems to facilitate real-time anomaly detection. Finally, a comprehensive solution for a trustworthy global AI-enabled IIoT infrastructure is completed with real-time supervisory dashboards.
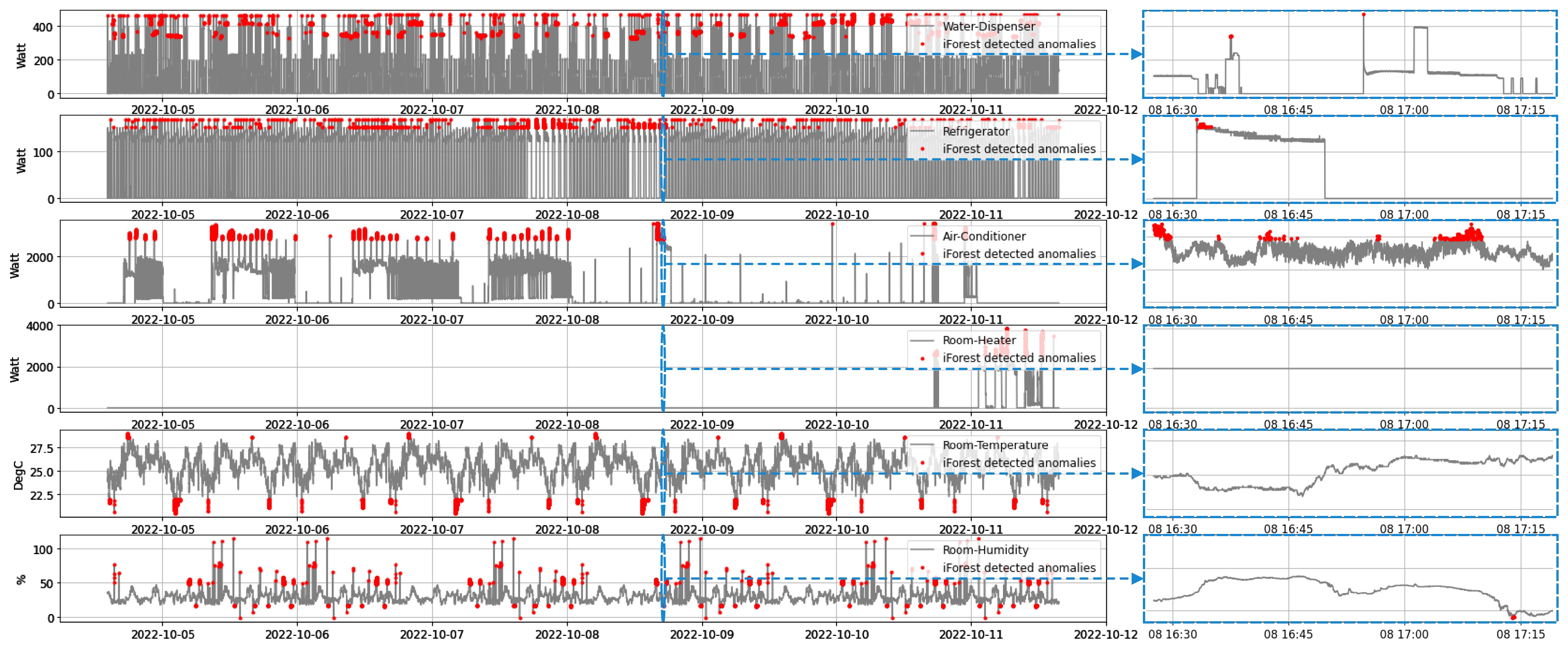
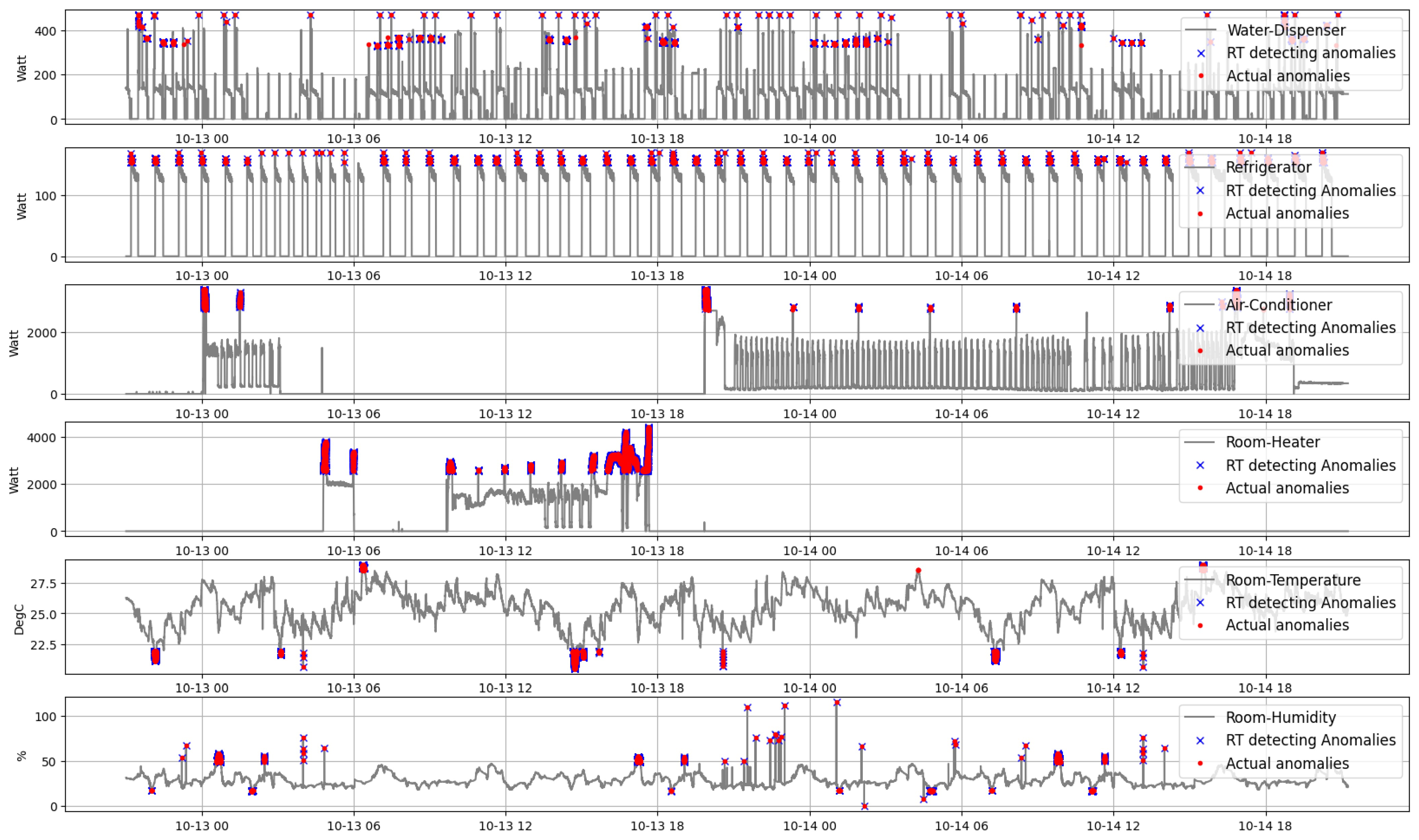
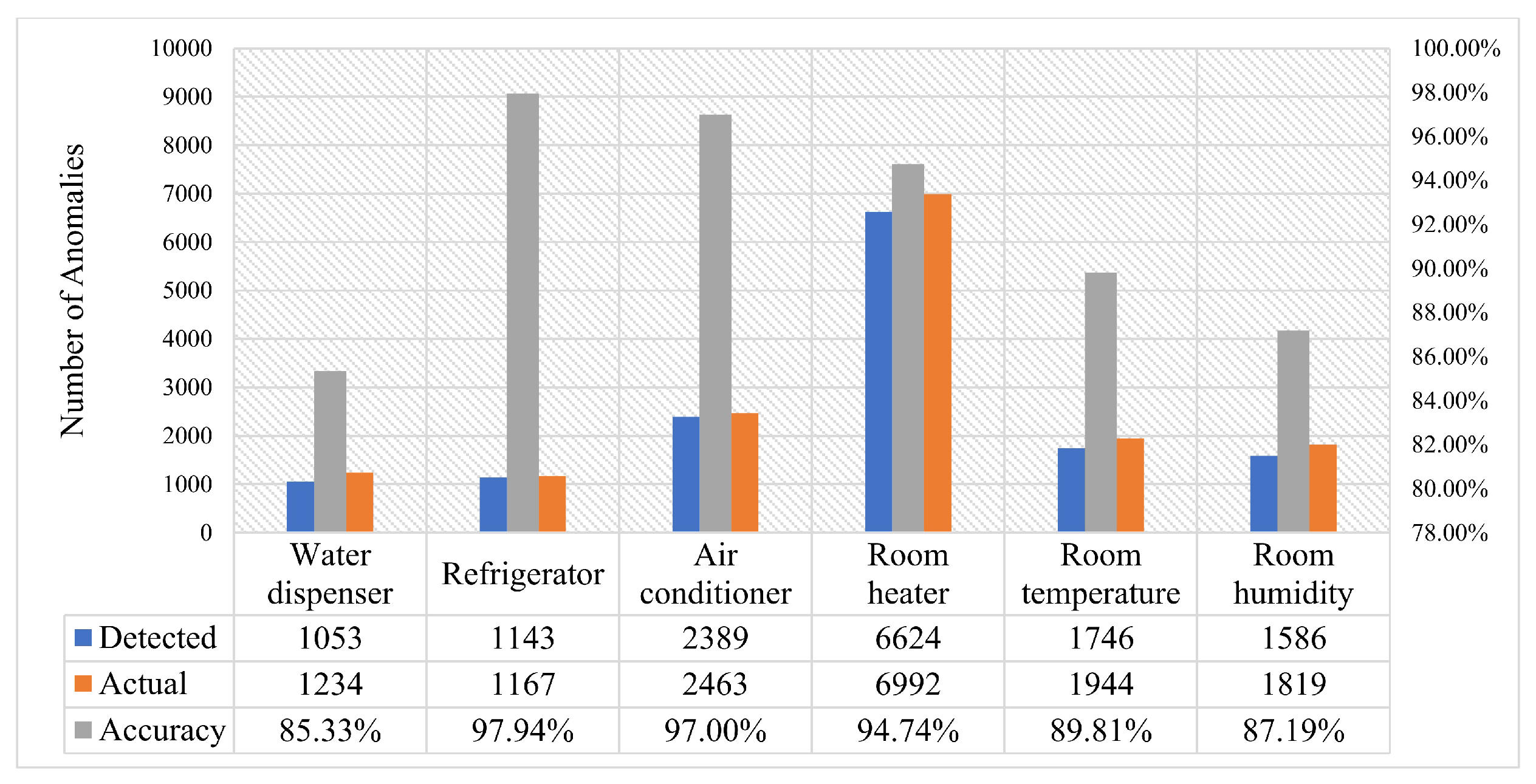
Like plug-in devices, our developed SDADs are very convenient, portable devices that can be simply installed in homes. While ensuring that the specifications of the sensors are chosen to ensure smooth functioning, all parts are coated with electric-insulated glue, and a compact box contains all of them. The security of our proposed system is verified in terms of data exchange, universal dashboards, and global databases. Heterogeneous data are extracted, and multiple AI models are trained individually. The performance of real-time anomaly detection is satisfactory. From our experiments, these models have an average accuracy of around 92%. The monitoring dashboards are implemented for the individual houses and the central server, where statistics on energy and outliers are spontaneously updated every second.
In a nutshell, our proposed infrastructure is a globally accessible, capable of processing heterogeneous data, integrated with AI, secured and interconnected IIoT system for various data acquisition, outliers detection, and real-time observation, which makes it feasible and advantageous for future IIoT applications. For instance, if data discrepancies are eliminated, it is possible to accurately predict energy consumption and examine the characteristics of power utilization. In addition, if a significant number of anomalies are identified, the relay switches can be used inside SDADs to disconnect the power connection. As a conclusion, our developed system might be a practical and comprehensive solution for smart energy management systems, such as the smart grid (SG), virtual power plant (VPP), and building energy management system (BEMS). Our next approach will be to develop a BEMS based on the suggested architecture, including the use of renewable energy.