Cybersecurity Awareness and Training (CAT) Framework for Remote Working Employees
Abstract
:1. Introduction
2. Motivation and Related Work
| Year | Reference | Framework | Objective | Domain | Validation |
|---|---|---|---|---|---|
| 2017 | [22] | Information security awareness program | To provide training delivery method and guidelines | Healthcare | Case Study |
| 2020 | [23] | Cybersecurity Maturity AssessmentFramework | Developed cybersecurity assessment framework for Higher Education Institutions | Education | Case Study |
| 2019 | [33] | National Cyber Governance Awareness Policy Framework | To assess cybersecurity governance and awareness at the government, national, and law prosecution level | Education, management, and administration | Case Study |
| 2020 | [34] | Cyber-Security Culture Awareness Framework | To evaluate organizational readiness from the cybersecurity domain perspective | Organization culture | No validation |
| 2020 | [24] | Effective corporatecommunication after cybersecurity incidents | The proposed framework can provide organizations with awareness into the kinds of actions that are essential after a cybersecurity incident | Business | Case study and interviews from experts |
| 2019 | [5] | Cybersecurity Awareness TrainingModel (CATRAM) | To provide training and awareness to the various organizations by considering the current cyberthreat landscape | Business | Case study |
| 2018 | [6] | Proactive Resilience Educational Framework (Proresilience EF) | Provide cybersecurity Education and Training in Hospitals | Healthcare | No validation |
| 2019 | [7] | Information security education training and awareness (SETA) | To provide sustainable behavioral change regarding cybersecurity by adopting behavior change wheel (BCW) framework | Healthcare | No validation |
| 2020 | [35] | Conceptual Model of Visual Analyticsfor Hands-on Cybersecurity Training | Using visual analytics to provide the sensemaking activities of users engaged in different phases ofthe training life cycle | Organization and education | Experiment by using KYPO cyber range (cloud-based platform) |
| 2022 | [36] | Factor model for online education during the COVID-19 pandemic | The proposed model offered recommendations for the government and universities for reducing the shortcomings regarding online education. | Education | Physical and online students survey |
| 2022 | [25] | Social education level on cybersecurity awareness and behavior | They measure the impact of the education level of the great societies to moderate the correlation in the middle of knowledge and attitude by using the knowledge–attitude–behavior (KAB) model. | Education | Questionnaire survey |
| 2021 | [27] | Cybersecurity awareness of employees | To find out the effect of cybersecurity awareness on worker behavior in Saudi Arabia environment. | Industry | Questionnaire survey |
| 2022 | [28] | Cybersecurity awareness (CSA) model | Proposed CSA model for railway organization in Thailand to detect the prominent factors. | Railway industry | Interview process from experts |
| 2022 | [37] | Cybersecurity Awareness Training Model | They established the significance of cybersecurity awareness training in incorporating with cyber-attacks and threats. | Organization | viCyber [38] Tool |
| 2021 | [39] (p. 19) | Cybersecurity awareness campaigns | To examine the usefulness of vulnerability revelation patterns on Twitter during the COVID-19 pandemic. | Organizations | Case study |
| 2021 | [30] | Cybersecurity awareness training | To investigate the efficiency of home management methods in decreasing cyber-attacks and threat incidents during online situations. | Organizations | Experiment |
| 2022 | [40] | Cybersecurity awareness measurement model | Constructed a method to assess the cybersecurity awareness level in water sector organizations | Water sector organization | Case study |
| 2021 | [41] | Conceptual model for cybersecurity governance | Developed a model to address the challenges related to cybersecurity governance. | Organizations | Survey |
| 2021 | [42] | Cybersecurity Awareness Framework | Recommended a conceptual Cybersecurity Awareness Framework to manage and direct the completion of methods to enhance cybersecurity awareness in the academic institution. | Academia | Survey |
| 2021 | [43] | Global Cyber Security Model | To guide cybersecurity manager to raise and conduct method for cybersecurity awareness among working employees | Organizations | Interview from experts |
Motivation
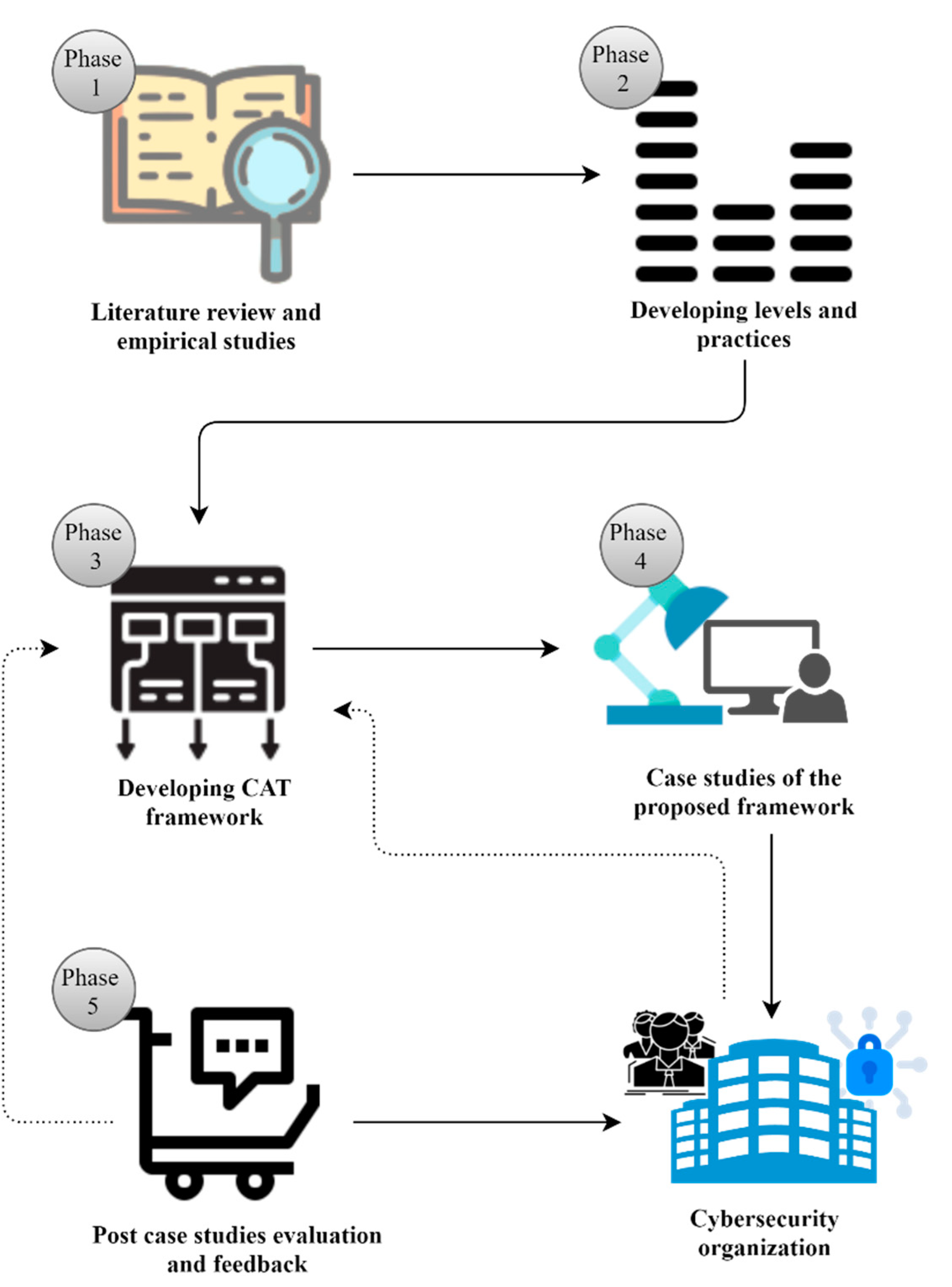
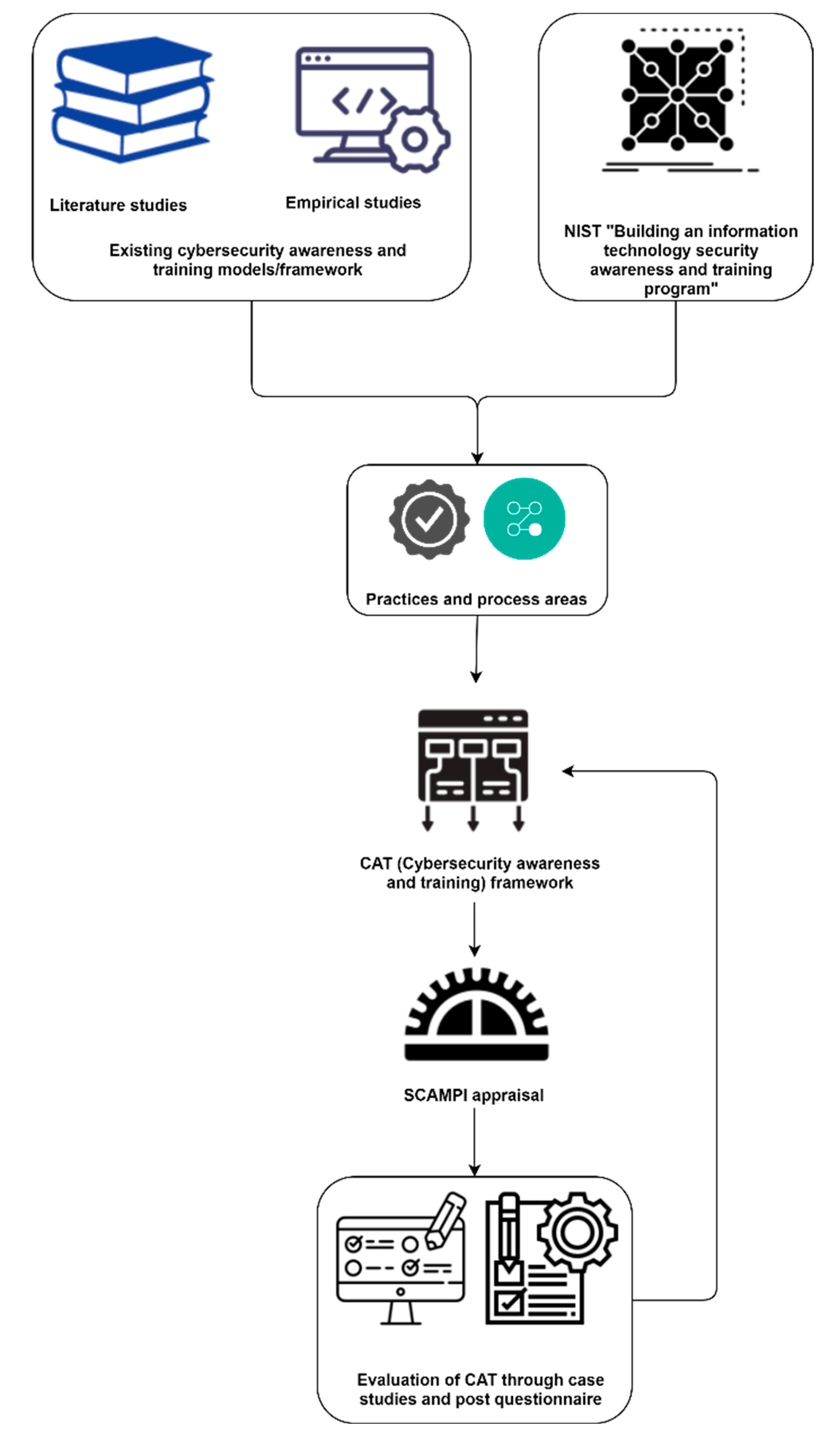
3. Research Methodology
3.1. Literature Review and Empirical Studies
3.2. Development CAT Framework Levels and Practices
3.3. Developing CAT Framework
3.4. Case Studies of the Proposed CAT Framework
3.5. Post-Case-Study Evaluation and Feedback
4. Cybersecurity Awareness and Training (CAT) Framework
4.1. The Development Process of the CAT Framework
4.2. Structure of the CAT Framework
4.3. AI Module
4.3.1. Machine/Deep Learning
4.3.2. Natural Language Processing
4.3.3. Expert Systems
4.4. Adaptive-Knowledge-Based Measurement Module
4.5. Capability Levels Module
4.5.1. Beginner
4.5.2. Medium
- E-posters
- Videos
- Webinars
- Seminars
- Workshops
- Email
- Newsletters
- Web-based
- Online lectures.
4.5.3. Advance
4.6. Capability Levels and Scoring Criteria of the CAT Framework
- Beginner
- Medium
- Advanced
5. Evaluation of CAT
- If the organization did not apply the practice of the CAT framework.
- If the organization partially applied the practice of the CAT framework.
- If the organization completely performed applied the practice of the CAT framework.
5.1. Case Study
5.1.1. Organization I
5.1.2. Organization II
6. The Post-Case-Study Feedback Questionnaire from Case Studies Implemented by Organizations
7. Study Limitations
8. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| Please Fill Each Rows ofTable 1, Table 2 and Table 3 with One of These Values Except the Yellow Colour Row | ||||
| 1 | If this level is Beginner applied for Awareness capability. | |||
| 2 | If this level is Mediumapplied for training capability. | |||
| 3 | If this level is Advanceapplied for practical and assessment capability. | |||
| Range value in % by IBM | Range of Average Value for CAT framework | Capability Level | ||
| 1 | 0–50% | If 0 <Avg. <= 1.5 | Beginner | |
| 2 | 51–80% | If 1.5 <Avg. <= 2.4 | Medium | |
| 3 | 81–100% | If 2.4 <Avg. <= 3 | Advance | |
| ID | Level and Practices | Awareness Level | ||
| Beginner | Medium | Advance | ||
| Level 1 | Awareness | 1 | 2 | 3 |
| P1.1 | Organization business | 3 | ||
| P1.2 | Organization polices and strategies | 3 | ||
| P1.3 | Cybersecurity basics | 2 | ||
| P1.4 | International cybersecurity standards | 2 | ||
| P1.5 | Social engineering | 2 | ||
| P1.6 | Basic cyber-attacks and threats | 2 | ||
| 2 | ||||
| The Outcome of SCAMPI Appraisal for CAT framework awareness level practices which the organization covers is: | Median | Appraisal of Organization Using SCAMPI | ||
| 2 | Medium | |||
| ID | Level and Practices | Training Level | ||
| Understanding | Improvement | Advance | ||
| level 2 | Training | 1 | 2 | 3 |
| Training phases | ||||
| P2.1 | Requirements | 2 | ||
| P2.2 | Design the peer review | 1 | ||
| P2.3 | Development | 2 | ||
| P2.4 | Implementation | 2 | ||
| P2.5 | Post-implementation | 1 | ||
| Training Medium | ||||
| P 2.6 | E-poster | 3 | ||
| P 2.7 | Videos | 3 | ||
| P 2.8 | Webinars | 2 | ||
| P 2.9 | Seminars | 2 | ||
| P 2.10 | Workshops | 1 | ||
| P 2.11 | 2 | |||
| P 2.12 | Newsletter | 3 | ||
| P 2.13 | Web-based | 2 | ||
| P 2.14 | Online lectures | 2 | ||
| 2 | ||||
| The Outcome of SCAMPI Appraisal for CAT framework training level practices which the organization covers is: | Median | Appraisal of Organization Using SCAMPI | ||
| 2 | Medium | |||
| ID | Level and Practices | Practical and Assessment Level | ||
| Understanding | Improvement | Advance | ||
| Level 3 | Practical and assessment | 1 | 2 | 3 |
| P 3.1 | Gamification | 2 | ||
| P 3.2 | Simulation | 2 | ||
| P 3.3 | Emulation | 1 | ||
| P 3.4 | Assessment | 2 | ||
| P 3.5 | Certification/Awards | 2 | ||
| 2 | ||||
| The Outcome of SCAMPI Apprisal for CAT framework practical and assessment level practices which the organazation covers is: | Median | Appraisal of Organization Using SCAMPI | ||
| 2 | Medium | |||
| Overall Summary Report of CAT Framework within Organization Case Study: | ||||
| No. | Three Levels of CAT Framework | Median | Appraisal of Cybersecurity Organization Using SCAMPI | |
| 1 | Awareness | 2 | Medium | |
| 2 | Training | 2 | Medium | |
| 3 | Practical and Assessment | 2 | Medium | |
References
- Kemmerer, R.A. Cybersecurity. In Proceedings of the 25th International Conference on Software Engineering, Portland, OR, USA, 3–10 May 2003; pp. 705–715. [Google Scholar] [CrossRef]
- Khan, F.; Zahid, M.; Gürüler, H.; Tarımer, İ.; Whangbo, T. An Efficient and Reliable Multicasting for Smart Cities. Comput. Mater. Contin. 2022, 72, 663–678. [Google Scholar] [CrossRef]
- Impact of COVID-19 on Cybersecurity. Deloitte Switzerland. Available online: https://www2.deloitte.com/ch/en/pages/risk/articles/impact-covid-cybersecurity.html (accessed on 3 April 2021).
- Hijji, M.; Alam, G. A Multivocal Literature Review on Growing Social Engineering Based Cyber-Attacks/Threats During the COVID-19 Pandemic: Challenges and Prospective Solutions. IEEE Access 2021, 9, 7152–7169. [Google Scholar] [CrossRef] [PubMed]
- Sabillon, R.; Serra-Ruiz, J.; Cavaller, V. An effective cybersecurity training model to support an organizational awareness program: The Cybersecurity Awareness TRAining Model (CATRAM). A Case Study in Canada. J. Cases Inf. Technol. JCIT 2019, 21, 26–39. [Google Scholar] [CrossRef] [Green Version]
- Rajamäki, J.; Nevmerzhitskaya, J.; Virág, C. Cybersecurity education and training in hospitals: Proactive resilience educational framework (Prosilience EF). In Proceedings of the 2018 IEEE Global Engineering Education Conference (EDUCON), Santa Cruz de Tenerife, Spain, 17–20 April 2018; pp. 2042–2046. [Google Scholar] [CrossRef]
- Toward Sustainable Behaviour Change: An Approach for Cyber Security Education Training and Awareness|Semantic Scholar. Available online: https://www.semanticscholar.org/paper/Toward-Sustainable-behaviour-Change%3A-an-Approach-Alshaikh-Naseer/35cf5519240bb2aa624a21132c762159511bb3f4 (accessed on 31 January 2021).
- Hash, J.; Wilson, M. Building an information technology security awareness and training program. Natl. Inst. Stand. Technol. NIST 2012, 800–850. [Google Scholar]
- ISO. ISO 9126/ISO, IEC (Hrsg.): International Standard ISO/IEC 9126: Information Technology-Software Product Evaluation. Qual. Charact. Guidel. Their Use 1991, 12–15. [Google Scholar]
- Realpe-Munoz, P.; Collazos, C.A.; Hurtado, J.; Granollers, T.; Velasco-Medina, J. An integration of usable security and user authentication into the ISO 9241-210 and ISO/IEC 25010: 2011. In Proceedings of the International Conference on Human Aspects of Information Security, Privacy, and Trust, Toronto, ON, Canada, 17–22 July 2016; pp. 65–76. [Google Scholar]
- McGraw, G. Software Security: Building Security; Addison-Wesley Professional: Boston, MA, USA, 2006; Volume 1. [Google Scholar]
- Bowen, P.; Kissel, R. Program Review for Information Security Management Assistance (PRISMA); US Department of Commerce; Technology Administration; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2007.
- Mouratidis, H.; Giorgini, P. Security Attack Testing (SAT)—Testing the security of information systems at design time. Inf. Syst. 2007, 32, 1166–1183. [Google Scholar] [CrossRef] [Green Version]
- Dhillon, G. Principles of Information Systems Security: Texts and Cases; John Wiley & Sons Incorporated: Hoboken, NJ, USA, 2007. [Google Scholar]
- Al Hanaei, E.H.; Rashid, A. DF-C2M2: A capability maturity model for digital forensics organisations. In Proceedings of the 2014 IEEE Security and Privacy Workshops, San Jose, CA, USA, 17–18 May 2014; pp. 57–60. [Google Scholar]
- Khan, F.; Ahmad, S.; Gürüler, H.; Cetin, G.; Whangbo, T.; Kim, C.-G. An Efficient and Reliable Algorithm for Wireless Sensor Network. Sensors 2021, 21, 8355. [Google Scholar] [CrossRef]
- Woodhouse, S. An ISMS (Im)-Maturity Capability Model. In Proceedings of the 2008 IEEE 8th International Conference on Computer and Information Technology Workshops, Sydney, NSW, Australia, 8–11 July 2008; pp. 242–247. [Google Scholar] [CrossRef]
- Almuhammadi, S.; Al-Saleh, M.A. Information Security Maturity Model for Nist Cyber Security Framework. Comput. Sci. Inf. Technol. CS IT 2017, 7, 51–62. [Google Scholar] [CrossRef]
- Kassou, M.; Kjiri, L. SOASMM: A novel service oriented architecture Security Maturity Model. In Proceedings of the 2012 International Conference on Multimedia Computing and Systems, Tangiers, Morocco, 10–12 May 2012. [Google Scholar] [CrossRef]
- White, G.B. The community cyber security maturity model. In Proceedings of the 2011 IEEE International Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 15–17 November 2011. [Google Scholar] [CrossRef]
- Thomson, K.-L.; von Solms, R. Towards an Information Security Competence Maturity Model. Comput. Fraud Secur. 2006, 2006, 11–15. [Google Scholar] [CrossRef]
- Ghazvini, A.; Shukur, Z. A Framework for an Effective Information Security Awareness Program in Healthcare. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 193–205. [Google Scholar] [CrossRef] [Green Version]
- Aliyu, A.; Maglaras, L.; He, Y.; Yevseyeva, I.; Boiten, E.; Cook, A.; Janicke, H. A Holistic Cybersecurity Maturity Assessment Framework for Higher Education Institutions in the United Kingdom. Appl. Sci. 2020, 10, 3660. [Google Scholar] [CrossRef]
- Knight, R.; Nurse, J.R. A framework for effective corporate communication after cyber security incidents. Comput. Secur. 2020, 99, 102036. [Google Scholar] [CrossRef]
- Hong, W.C.H.; Chi, C.; Liu, J.; Zhang, Y.; Lei, V.N.-L.; Xu, X. The influence of social education level on cybersecurity awareness and behaviour: A comparative study of university students and working graduates. Educ. Inf. Technol. 2022, 1–32. [Google Scholar] [CrossRef] [PubMed]
- Sabillon, R.; The Cybersecurity Awareness Training Model (CATRAM). Research Anthology on Advancements in Cybersecurity Education. 2022. Available online: https://www.igi-global.com/chapter/the-cybersecurity-awareness-training-model-catram/www.igi-global.com/chapter/the-cybersecurity-awareness-training-model-catram/292128 (accessed on 19 September 2022).
- Alghamdi, M.I. Determining the impact of cyber security awareness on employee behaviour: A case of Saudi Arabia. Mater. Today Proc. 2021. [Google Scholar] [CrossRef]
- Ungkap, P.; Daengsi, T. Cybersecurity Awareness Modeling Associated with Influential Factors Using AHP Technique: A Case of Railway Organizations in Thailand. In Proceedings of the 2022 International Conference on Decision Aid Sciences and Applications (DASA), Chiangrai, Thailand, 23–25 March 2022; pp. 1359–1362. [Google Scholar] [CrossRef]
- Daengsi, T.; Wuttidittachotti, P.; Pornpongtechavanich, P.; Utakrit, N. A Comparative Study of Cybersecurity Awareness on Phishing among Employees from Different Departments in an Organization. In Proceedings of the 2021 2nd International Conference on Smart Computing and Electronic Enterprise (ICSCEE), Cameron Highlands, Malaysia, 15–17 June 2021; pp. 102–106. [Google Scholar] [CrossRef]
- Back, S.; Guerette, R.T. Cyber Place Management and Crime Prevention: The Effectiveness of Cybersecurity Awareness Training Against Phishing Attacks. J. Contemp. Crim. Justice 2021, 37, 427–451. [Google Scholar] [CrossRef]
- Corallo, A.; Lazoi, M.; Lezzi, M.; Luperto, A. Cybersecurity awareness in the context of the Industrial Internet of Things: A systematic literature review. Comput. Ind. 2022, 137, 103614. [Google Scholar] [CrossRef]
- Zhang-Kennedy, L.; Chiasson, S. A Systematic Review of Multimedia Tools for Cybersecurity Awareness and Education. ACM Comput. Surv. 2022, 54, 1–39. [Google Scholar] [CrossRef]
- Bou, H. National Cyber Governance Awareness Policy and Framework. Int. J. Leg. Inf. 2019, 47, 70–89. [Google Scholar]
- Georgiadou, A.; Mouzakitis, S.; Bounas, K.; Askounis, D. A Cyber-Security Culture Framework for Assessing Organization Readiness. J. Comput. Inf. Syst. 2020, 62, 452–462. [Google Scholar] [CrossRef]
- Conceptual Model of Visual Analytics for Hands-on Cybersecurity Training-IEEE Journals & Magazine. Available online: https://ieeexplore.ieee.org/document/9018081 (accessed on 31 January 2021).
- Khan, F.; Tarimer, I.; Taekeun, W. Factor Model for Online Education during the COVID-19 Pandemic Using the IoT. Process 2022, 10, 1419. [Google Scholar] [CrossRef]
- Dash, B.; Ansari, M.F. An Effective Cybersecurity Awareness Training Model: First Defense of an Organizational Security Strategy. Int. Res. J. Eng. Technol. (IRJET) 2022, 9. [Google Scholar]
- Hodhod, R.; Wang, S.; Khan, S. Cybersecurity Curriculum Development Using AI and Decision Support Expert System. Int. J. Comput. Theory Eng. 2018, 10, 111–115. [Google Scholar] [CrossRef] [Green Version]
- Bahl, A.; Sharma, A.; Asghar, M.R. Vulnerability disclosure and cybersecurity awareness campaigns on twitter during COVID -19. Secur. Priv. 2021, 4, e180. [Google Scholar] [CrossRef]
- Marnewick, A.; Von Solms, S. The Development of Cybersecurity Awareness Measurement Model in the Water Sector. In Proceedings of the 17th International Conference on Cyber Warfare and Security, Albany, NY, USA, 17–18 March 2022; Volume 17, pp. 211–218. [Google Scholar] [CrossRef]
- Yusif, S.; Hafeez-Baig, A. A Conceptual Model for Cybersecurity Governance. J. Appl. Secur. Res. 2021, 16, 490–513. [Google Scholar] [CrossRef]
- Khader, M.; Karam, M.; Fares, H. Cybersecurity Awareness Framework for Academia. Information 2021, 12, 417. [Google Scholar] [CrossRef]
- Trim, P.; Lee, Y.-I. The Global Cyber Security Model: Counteracting Cyber Attacks through a Resilient Partnership Arrangement. Big Data Cogn. Comput. 2021, 5, 32. [Google Scholar] [CrossRef]
- Khan, F.; Khan, A.W.; Khan, S.; Qasim, I.; Habib, A. A secure core-assisted multicast routing protocol in mobile ad-hoc network. J. Internet Technol. 2020, 21, 375–383. [Google Scholar]
- Ahmed, S.R. Secure Software Development: Identification of Security Activities and Their Integration in Software Development Lifecycle. 2007. Available online: https://www.semanticscholar.org (accessed on 2 January 2021).
- Almusaher, H.; Alam, G. How Feasible Moving Target Defense is Within ICS Environment. In Proceedings of the International Petroleum Technology Conference, Dhahran, Saudi Arabia, 13–15 January 2020. [Google Scholar] [CrossRef]
- Abbas, S.; Abu Talib, M.; Ahmed, A.; Khan, F.; Ahmad, S.; Kim, D.-H. Blockchain-Based Authentication in Internet of Vehicles: A Survey. Sensors 2021, 21, 7927. [Google Scholar] [CrossRef]
- Yin, R.K. Case study research: Design and methods Sage publications. Thousand Oaks 2009, 5. [Google Scholar]
- Eisenhardt, K.M. Building theories from case study research. Acad. Manage. Rev. 1989, 14, 532–550. [Google Scholar] [CrossRef]
- Federal Information Security Management Act of 2002. Wikipedia. 2 January 2021. Available online: https://en.wikipedia.org/w/index.php?title=Federal_Information_Security_Management_Act_of_2002&oldid=997751107 (accessed on 8 March 2021).
- Office of Management and Budget. The White House. Available online: https://www.whitehouse.gov/omb/ (accessed on 8 March 2021).
- 7 Ways to Improve Security of Your Machine Learning Workflows|AWS Security Blog. 31 March 2021. Available online: https://aws.amazon.com/blogs/security/7-ways-to-improve-security-of-your-machine-learning-workflows/ (accessed on 20 September 2022).
- Šerbec, I.N.; Žerovnik, A.; Rugelj, J. Machine Learning Algorithms Used for Adaptive Modelling. J. Appl. Econ. Bus. 2013, 1, 5–12. [Google Scholar]
- CyberSift, Machine Learning Techniques Applied to Cyber Security, Medium, 10 September 2017. Available online: https://towardsdatascience.com/machine-learning-techniques-applied-to-cyber-security-d58a8995b7d7 (accessed on 9 March 2021).
- Madnani, N.; Aoife, C. Automated scoring: Beyond natural language processing. In Proceedings of the 27th International Conference on Computational Linguistics, Santa Fe, NM, USA, August 2018; pp. 1099–1109. [Google Scholar]
- Litman, D. Natural Language Processing for Enhancing Teaching and Learning. Proc. Conf. AAAI Artif. Intell. 2016, 30. Available online: https://ojs.aaai.org/index.php/AAAI/article/view/9879 (accessed on 9 March 2021). [CrossRef]
- Haynes, J.A.; Pilato, V.H.; Malouf, D.B. Expert Systems for Educational Decision-Making. Educ. Technol. 1987, 27, 37–42. Available online: https://www.jstor.org/stable/44424889 (accessed on 9 March 2021).
- Hwang, G.-J.; Sung, H.-Y.; Chang, S.-C.; Huang, X.-C. A fuzzy expert system-based adaptive learning approach to improving students’ learning performances by considering affective and cognitive factors. Comput. Educ. Artif. Intell. 2020, 1, 100003. [Google Scholar] [CrossRef]
- DFARS|Acquisition.GOV. Available online: https://www.acquisition.gov/dfars (accessed on 8 March 2021).
- Federal Information Security Modernization Act|CISA. Available online: https://www.cisa.gov/federal-information-security-modernization-act (accessed on 8 March 2021).
- Health Insurance Portability and Accountability Act|IT Governance USA. Available online: https://itgovernanceusa.com/hipaa (accessed on 8 March 2021).
- 14:00–17:00, ISO 22301:2019, ISO. Available online: https://www.iso.org/cms/render/live/en/sites/isoorg/contents/data/standard/07/51/75106.html (accessed on 8 March 2021).
- ISO-ISO/IEC 27001—Information Security Management. Available online: https://www.iso.org/isoiec-27001-information-security.html (accessed on 8 March 2021).
- NIST Cybersecurity Framework (CSF)|IT Governance USA. Available online: https://itgovernanceusa.com/nist-cybersecurity-framework (accessed on 8 March 2021).
- Krombholz, K.; Hobel, H.; Huber, M.; Weippl, E. Advanced social engineering attacks. J. Inf. Secur. Appl. 2015, 22, 113–122. [Google Scholar] [CrossRef]
- Abraham, S.; Chengalur-Smith, I. An overview of social engineering malware: Trends, tactics, and implications. Technol. Soc. 2010, 32, 183–196. [Google Scholar] [CrossRef]
- Irani, D.; Balduzzi, M.; Balzarotti, D.; Kirda, E.; Pu, C. Reverse social engineering attacks in online social networks. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment; Springer: Berlin/Heidelberg, Germany, 2011; pp. 55–74. [Google Scholar]
- Mouton, F.; Leenen, L.; Venter, H.S. Social engineering attack examples, templates and scenarios. Comput. Secur. 2016, 59, 186–209. [Google Scholar] [CrossRef] [Green Version]
- Cone, B.D.; Thompson, M.F.; Irvine, C.E.; Nguyen, T.D. Cyber Security Training and Awareness Through Game Play. In IFIP International Information Security Conference; Springer: Boston, MA, USA, 2006; Volume 201, pp. 431–436. [Google Scholar] [CrossRef] [Green Version]
- Hendrix, M.; Al-Sherbaz, A.; Bloom, V. Game Based Cyber Security Training: Are Serious Games suitable for cyber security training? Int. J. Serious Games 2016, 3, 1. [Google Scholar] [CrossRef]
- Cone, B.D.; Irvine, C.E.; Thompson, M.F.; Nguyen, T.D. A video game for cyber security training and awareness. Comput. Secur. 2007, 26, 63–72. [Google Scholar] [CrossRef]
- Shunami, B. Council Post: The Gamification of Cybersecurity Training. Forbes. Available online: https://www.forbes.com/sites/forbestechcouncil/2020/03/17/the-gamification-of-cybersecurity-training/ (accessed on 9 March 2021).
- Cybersecurity|NOVA Labs|PBS. Available online: https://www.pbs.org/wgbh/nova/labs/lab/cyber/ (accessed on 9 March 2021).
- LEO GRC Academy|Innovative Digital Learning|LEO Learning. Available online: https://leolearning.com/leo-grc-academy/ (accessed on 9 March 2021).
- Welcome|Keep Tradition Secure. Available online: https://keeptraditionsecure.tamu.edu/ (accessed on 9 March 2021).
- PricewaterhouseCoopers, Game of Threats. PwC. Available online: https://www.pwc.co.uk/issues/cyber-security-services/game-of-threats.html (accessed on 9 March 2021).
- Ahmad, S.; Khan, F.; Whangbo, T.K. Performance Evaluation of Topological Infrastructure in Internet-of-Things-Enabled Serious Games. Comput. Mater. Contin. 2022, 71, 2653–2666. [Google Scholar] [CrossRef]
- Wen, Z.A.; Lin, Z.; Chen, R.; Andersen, E. What.Hack: Engaging Anti-Phishing Training Through a Role-playing Phishing Simulation Game. In Proceedings of the Proceedings of the 2019 CHI Conference on Human Factors in Computing Systems, New York, NY, USA, 2 May 2019; pp. 1–12. [Google Scholar] [CrossRef]
- Jalali, M.S.; Siegel, M.; Madnick, S. Decision-making and biases in cybersecurity capability development: Evidence from a simulation game experiment. J. Strat. Inf. Syst. 2018, 28, 66–82. [Google Scholar] [CrossRef]
- Burris, J.; Deneke, W.; Maulding, B. Activity Simulation for Experiential Learning in Cybersecurity Workforce Development. In Proceedings of the HCI in Business, Government, and Organizations, Cham, Switzerland, 15 July 2018; pp. 17–25. [Google Scholar] [CrossRef]
- Mehmood, S.; Ahmad, I.; Khan, M.A.; Khan, F.; Whangbo, T. Sentiment Analysis in Social Media for Competitive Environment Using Content Analysis. Comput. Mater. Contin. 2022, 71, 5603–5618. [Google Scholar] [CrossRef]
- Six Free Tools for Creating a Cyber Simulator. Available online: https://insights.sei.cmu.edu/sei_blog/2019/04/six-free-tools-for-creating-a-cyber-simulator.html (accessed on 9 March 2021).
- Mufti, Y.; Niazi, M.; Alshayeb, M.; Mahmood, S. A Readiness Model for Security Requirements Engineering. IEEE Access 2018, 6, 28611–28631. [Google Scholar] [CrossRef]

| No. | Range Value in % by IBM | Range of Median Value for CAT | Capability Level |
|---|---|---|---|
| 1 | 0–50% | If 0 < Med <= 1.5 | Beginner |
| 2 | 51–80% | If 1.5 < Med <= 2.4 | Medium |
| 3 | 81–100% | If 2.4 < Med <= 3 | Advance |
| No. | CAT Framework Ease of Use | Organizations’ Viewpoint (n = 2) | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Strongly Agree and Agree | Strongly Disagree and Disagree | Neutral | |||||||
| Strongly Agree | Agree | Percentage of Strongly Agree or Agree | Strongly Disagree | Disagree | Percentage of Strongly Disagree or Disagree | Neutral | Percentage of Neutral | ||
| 1 | CAT framework demonstration is straightforward to understand and learn. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| 2 | Basic knowledge applicable to cybersecurity is essential to be able to make use of the CAT framework. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| 3 | The practices for processes are important to understand and learn for each CAT framework level. | 0 | 2 | 100 | 0 | 0 | 0 | 0 | 0 |
| 4 | It is crucial to use the CAT framework to measure an organization employee’s capability for CAT framework levels and practices. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| 5 | Awareness and training are needed to enable the use of CAT framework. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| No. | CAT Framework User Satisfaction | Organizations’ Perception (n = 2) | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Strongly Agree and Agree | Strongly Disagree and Disagree | Neutral | |||||||
| Strongly Agree | Agree | Percentage of Strongly Agree or Agree | Strongly Disagree | Disagree | Percentage of Strongly Disagree or Disagree | Neutral | Percentage of Neutral | ||
| 1 | CAT framework can be applied to highest number of organizations. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| 2 | Every Single practice of CAT framework is easy and useable. | 0 | 2 | 100 | 0 | 0 | 0 | 0 | 0 |
| 3 | CAT framework can identify the weak and strong spots in organizations employee’s relation to CAT framework levels and their practices which they perform. | 0 | 2 | 100 | 0 | 0 | 0 | 0 | 0 |
| 4 | The use of CAT framework would improve cybersecurity awareness and training. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| 5 | If the CAT framework were available in my organization, I believe to use it. | 0 | 2 | 100 | 0 | 0 | 0 | 0 | 0 |
| 6 | I agree with the cybersecurity levels and practices documented by CAT framework. | 0 | 2 | 100 | 0 | 0 | 0 | 0 | 0 |
| 7 | Utilizing the CAT framework as a practical software tool is essential to cybersecurity training and awareness for measuring the organization’s employee capability. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| No. | CAT Framework Structure | Organizations’ Perception (n = 2) | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Strongly Agree and Agree | Strongly Disagree and Disagree | Neutral | |||||||
| Strongly Agree | Agree | Percentage of Strongly Agree or Agree | Strongly Disagree | Disagree | Percentage of Strongly Disagree or Disagree | Neutral | Percentage of Neutral | ||
| 1 | Every level of the CAT framework is understandable and intends no further clarification for acceptable use. | 0 | 2 | 100 | 0 | 0 | 0 | 0 | 0 |
| 2 | Every level of the CAT framework is satisfactory and applicable to the awareness and training of the organization’s employees. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| 3 | CAT framework can be applied excellently to identify cybersecurity weaknesses of the organization with an aim to grow up organization’s employee’s capability for awareness and training of cybersecurity. | 0 | 2 | 100 | 0 | 0 | 0 | 0 | 0 |
| 4 | The distribution of cybersecurity practices among different levels (e.g., Beginner, medium and Advance) is useful. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| 5 | The three levels of the CAT framework are helpful. | 2 | 0 | 100 | 0 | 0 | 0 | 0 | 0 |
| Question | Response | ||
|---|---|---|---|
| Organization I | Organization II | Outcome | |
| Do you think there is a missing practice that needs to be added to the CAT framework? Please provide reasons for your answer. | Revise the practices again, may be some practices are missed | No | Encouraging |
| Do you have any recommendations to make better the proposed CAT framework? | No | Provide full documentation of the practices that guides novice workers in the area having no knowledge and experience in cybersecurity. | Encouraging |
| Any comments or suggestions expected on the assessment method of the CAT framework? | Would be better to provide an automated tool in the future to make it easy for the organization to assess their employees/workers capability. | No | Encouraging |
| Have any CAT framework level practices been inaccurately categorized? | No | No | Very Positive |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hijji, M.; Alam, G. Cybersecurity Awareness and Training (CAT) Framework for Remote Working Employees. Sensors 2022, 22, 8663. https://doi.org/10.3390/s22228663
Hijji M, Alam G. Cybersecurity Awareness and Training (CAT) Framework for Remote Working Employees. Sensors. 2022; 22(22):8663. https://doi.org/10.3390/s22228663
Chicago/Turabian StyleHijji, Mohammad, and Gulzar Alam. 2022. "Cybersecurity Awareness and Training (CAT) Framework for Remote Working Employees" Sensors 22, no. 22: 8663. https://doi.org/10.3390/s22228663
APA StyleHijji, M., & Alam, G. (2022). Cybersecurity Awareness and Training (CAT) Framework for Remote Working Employees. Sensors, 22(22), 8663. https://doi.org/10.3390/s22228663






