Distributed Supervision Model for Enterprise Data Asset Trading Based on Blockchain Multi-Channel in Industry Alliance
Abstract
1. Introduction
2. Related Work
3. Analysis of Key Supervision Information and Problems in Data Trading Process
3.1. Analysis of Data Trading Process and Key Supervision Information
3.2. Problems in Traditional Data Trading Supervision
4. A Distributed Supervision Model for Enterprise Data Asset Trading in Industry Alliance
4.1. Blockchain and Fabric Channel Technology
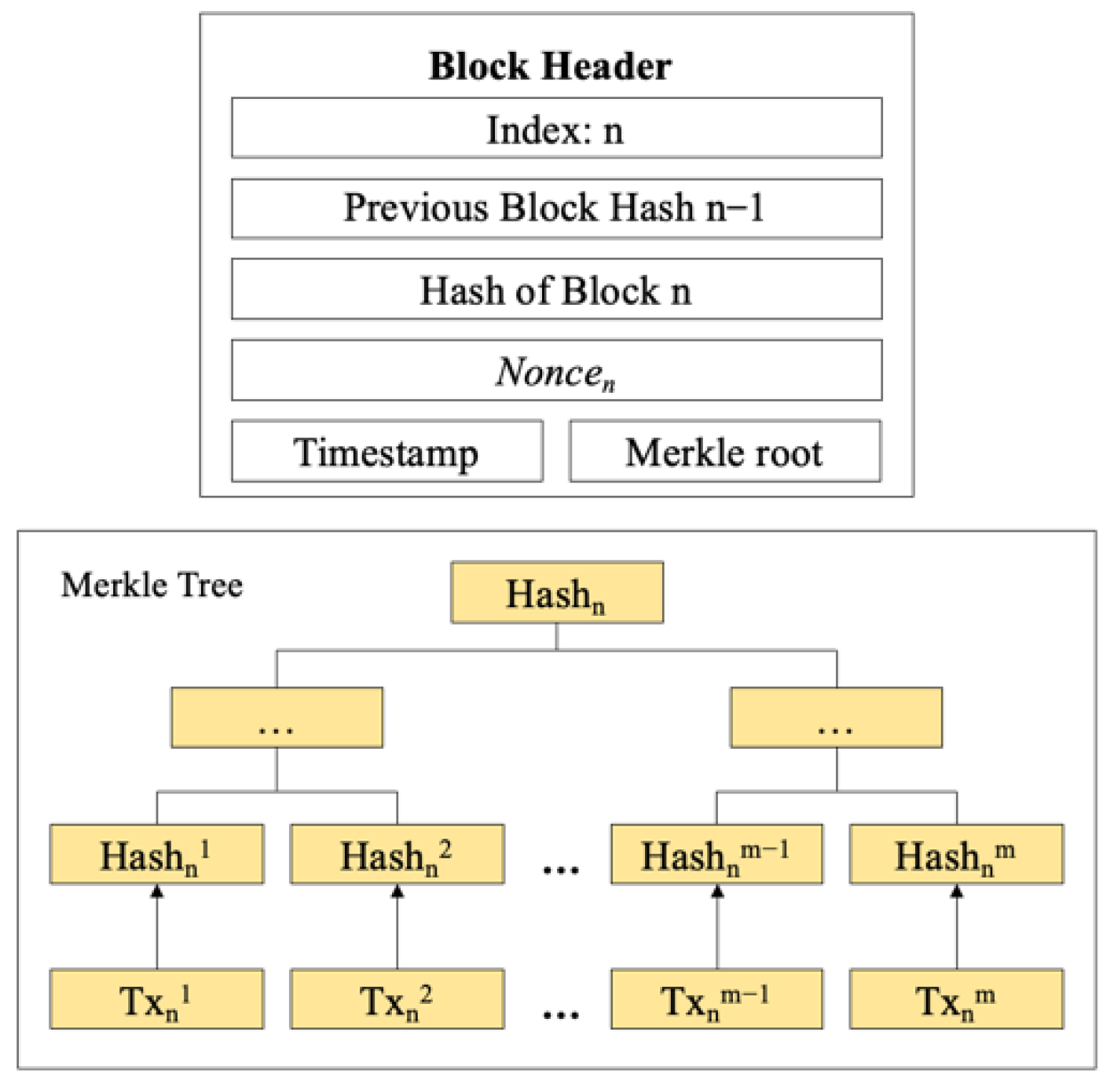
4.1.1. Blockchain Technology
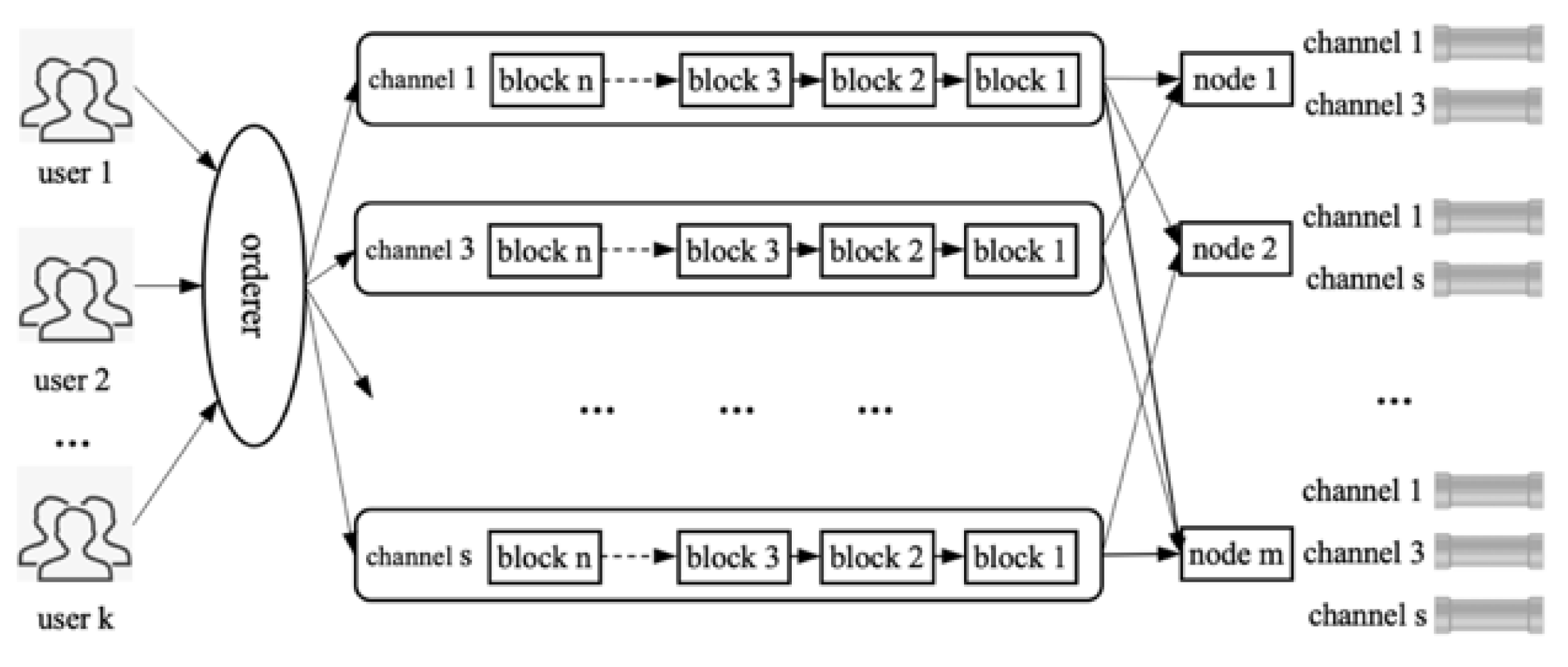
4.1.2. Hyperledger Fabric Multi-Channel Technology
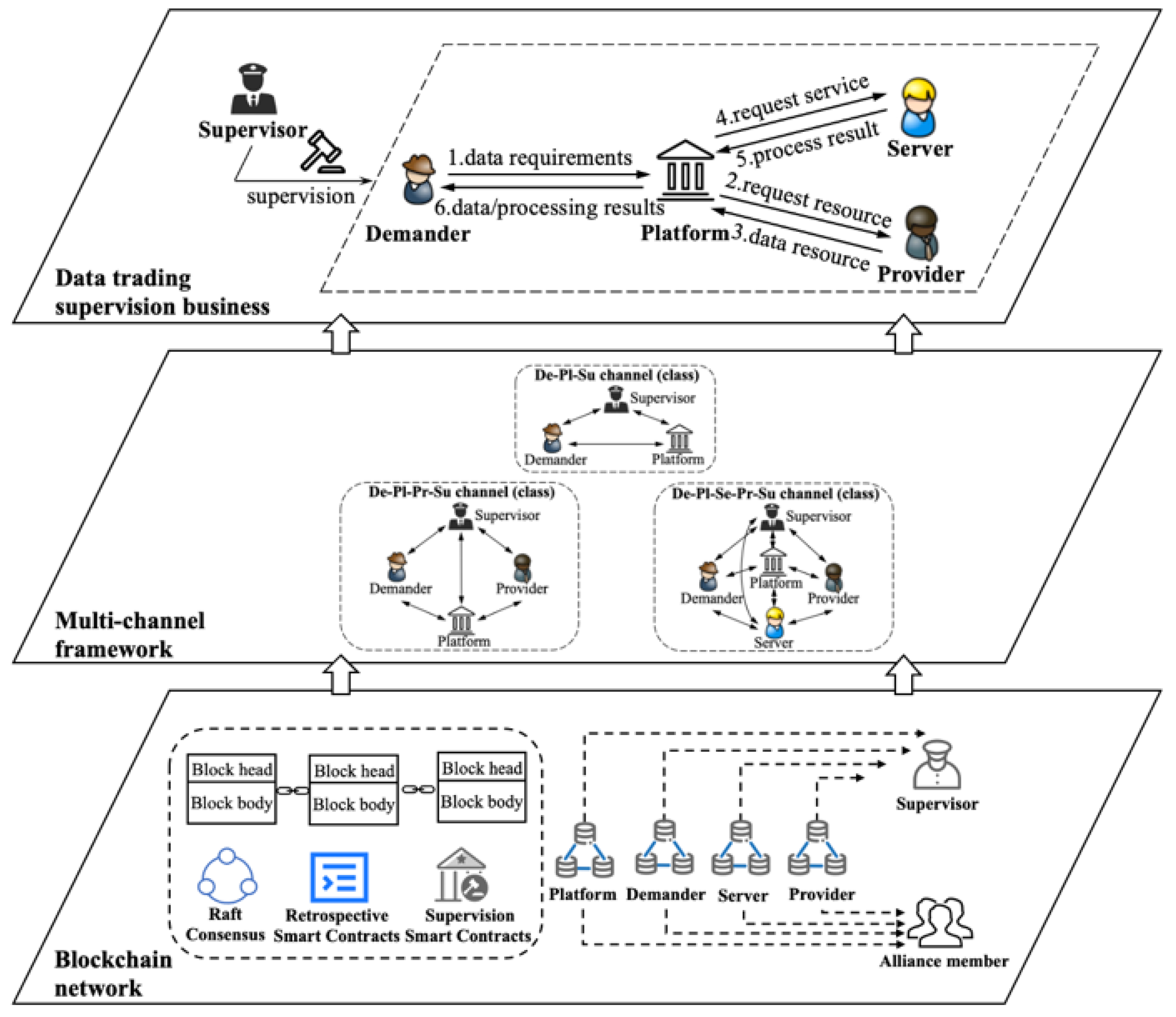
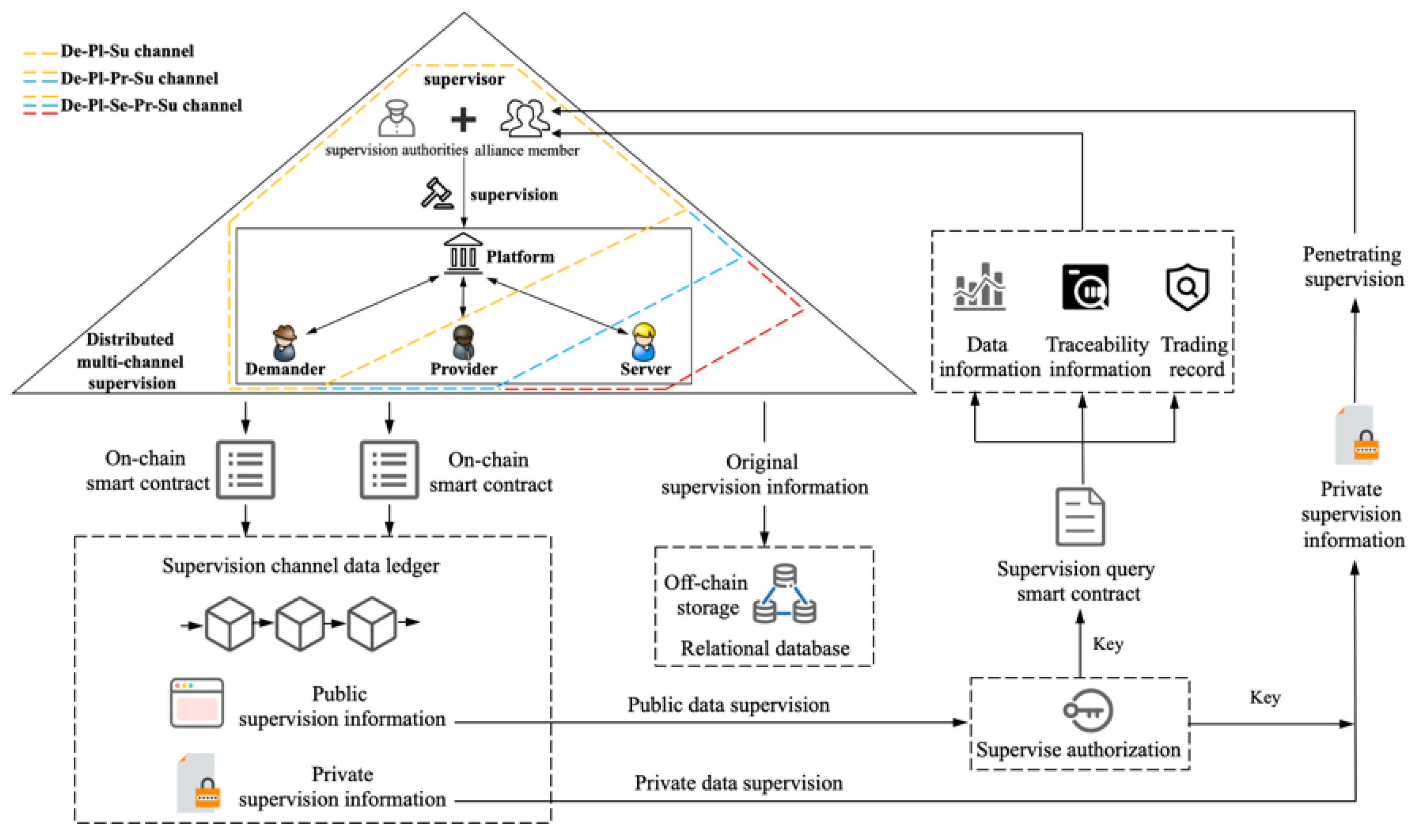
4.2. Distributed Supervision Overall Architecture for Enterprise Data Asset
4.3. Blockchain Multi-Channel Structure for Distributed Supervision
4.4. On-Chain and Off-Chain Hybrid Storage of Data Trading Supervision Information
| Algorithm 1: Smart contract for private supervision information on-chain |
| Input:, , Output:, 1 // Verify the validity of supervision channel authorization file 2 If val() 3 // Pre-chain supervision of trading information 4 if ((isTdTypeLegal() && isTdContentLegal()) 5 // Store the data trading information into the corresponding channel 6 if (wriSupChannel(, , )) 7 return , ; |
| Algorithm 2: Smart contract for public supervision information on-chain |
| Input:, Output:, 1 // Check the format and content of data trading information 2 if ((isTdTypeLegal() && isTdContentLegal()) 3 // Store the data transaction information in the blockchain public area 4 if (wriPubChannel(, )) 5 return , ; |
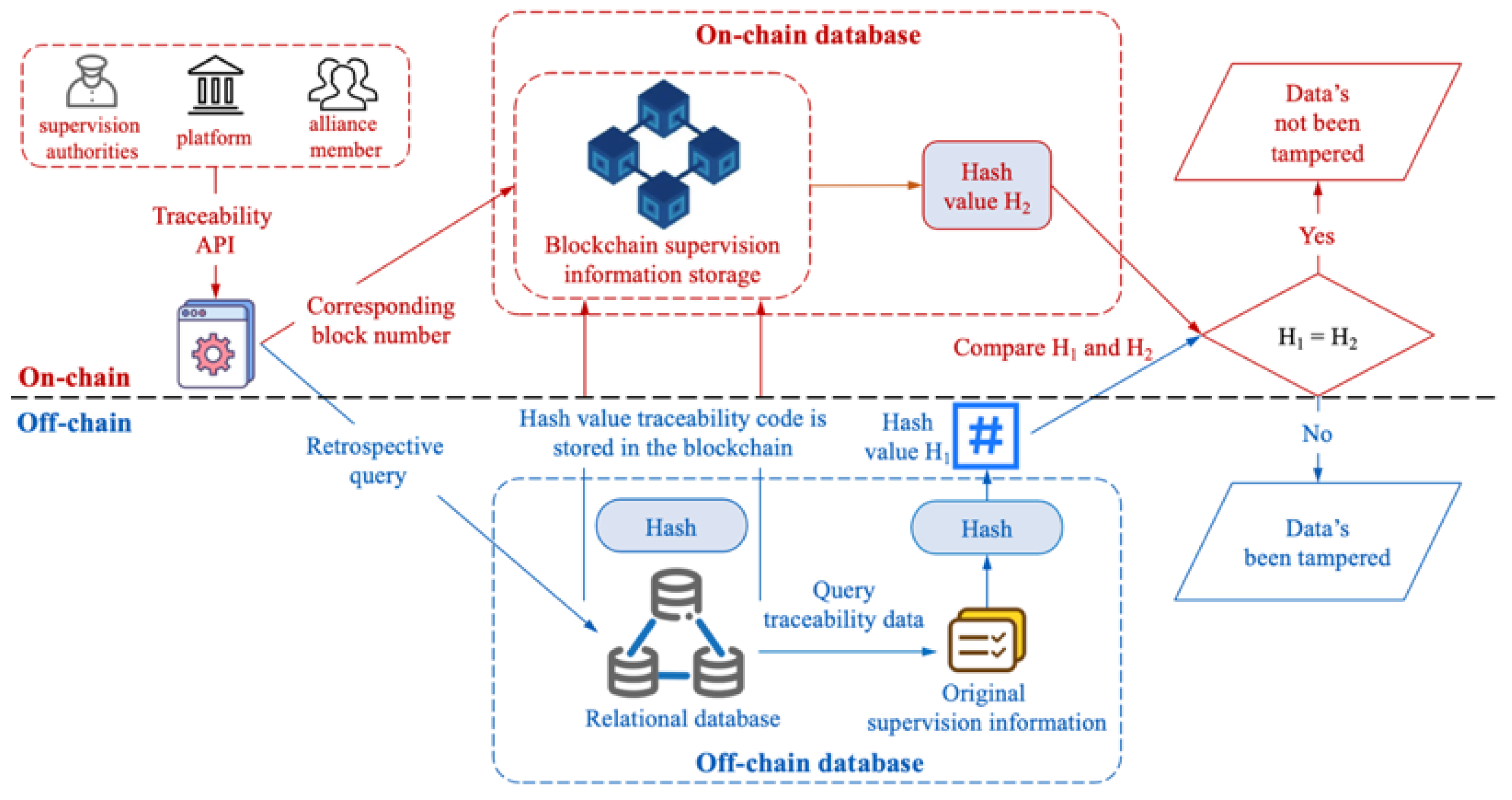
| Algorithm 3: Verification algorithm of data trading information traceability process |
; |
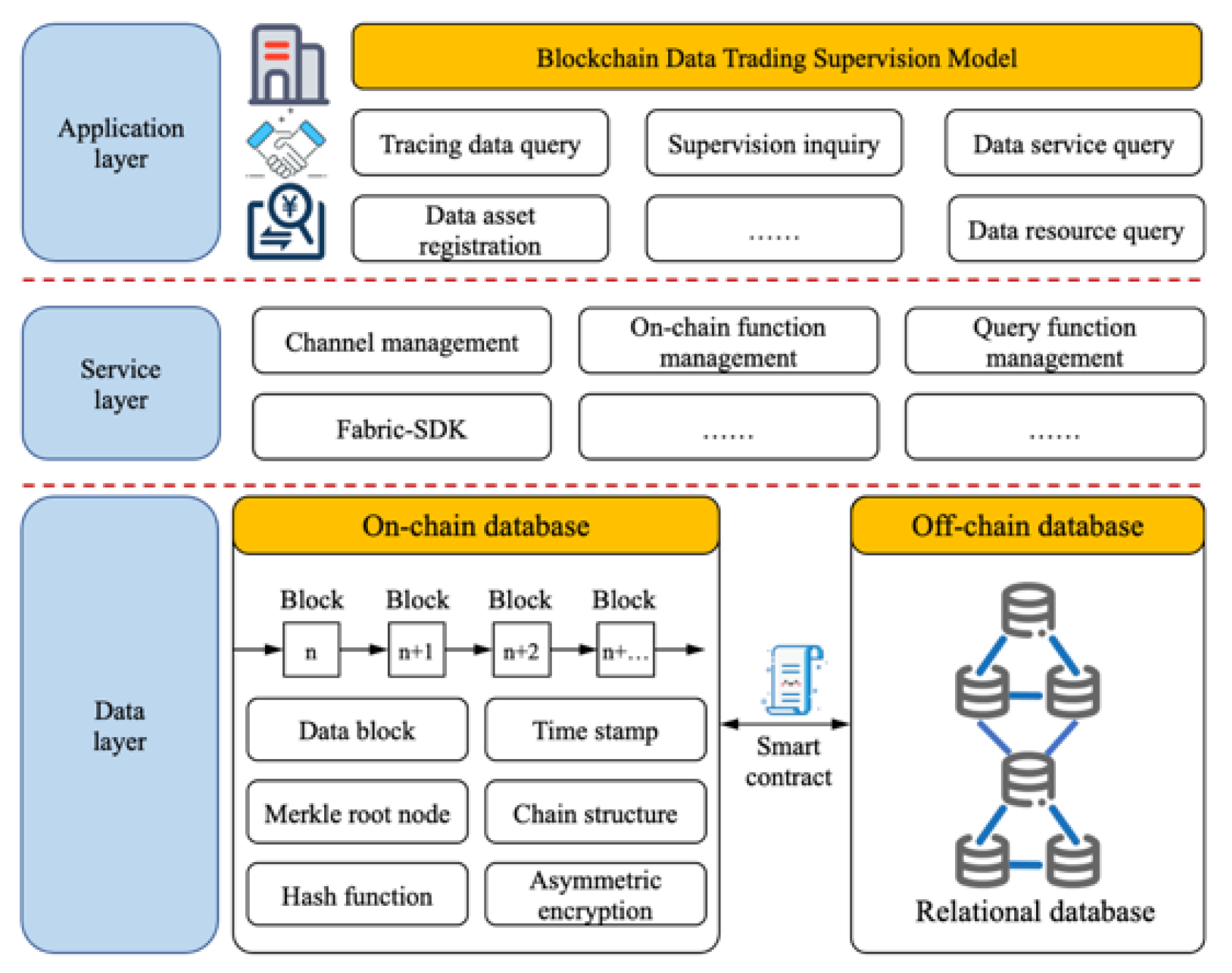
4.5. On-Chain Layer Structure of Data Trading Supervision Model
4.6. Formal Expression of Distributed Supervision Model
5. Performance Testing and Analysis of Distributed Supervision Model
5.1. Performance Testing and Analysis of the Traceability Function
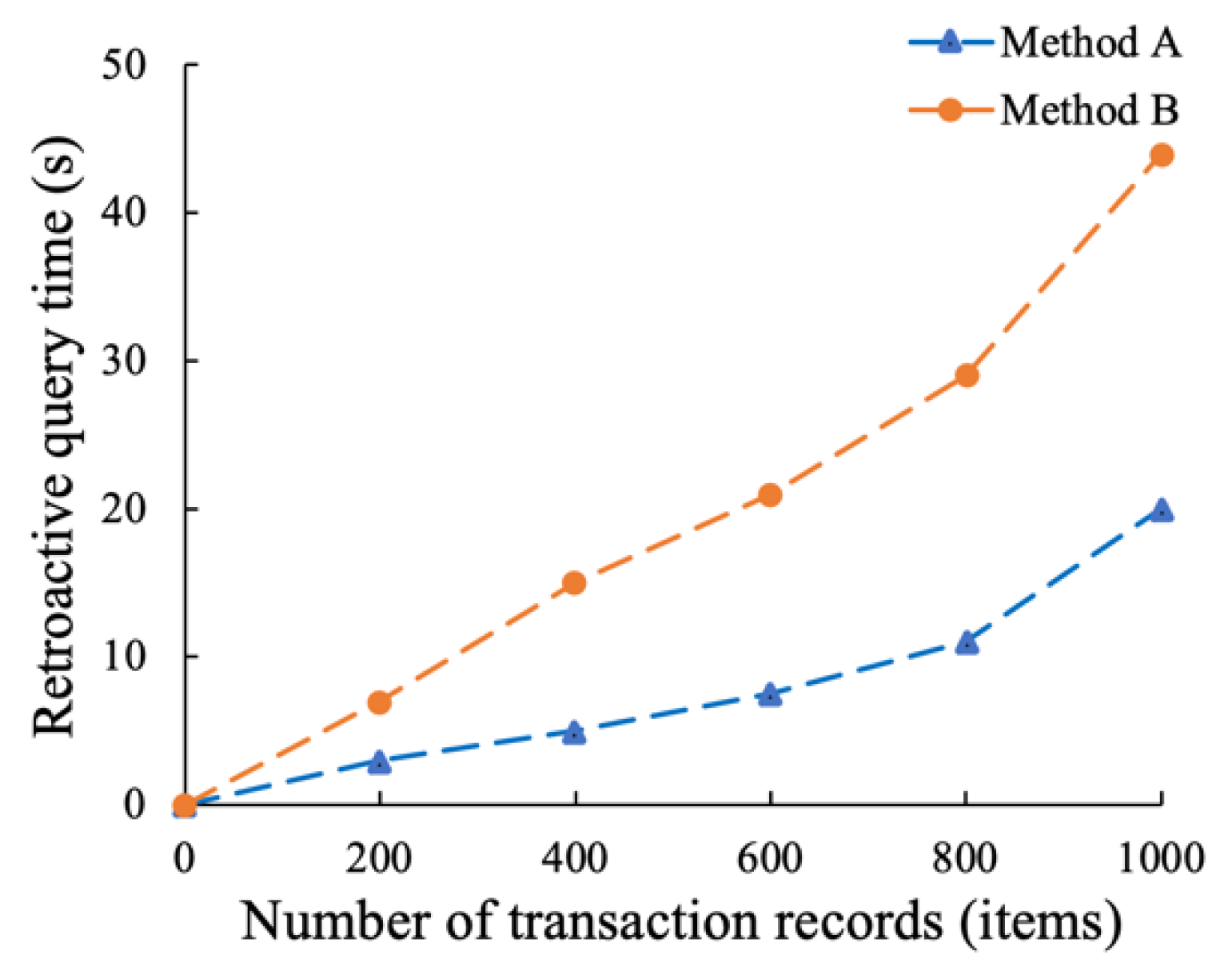
5.1.1. Query Time Testing and Analysis of the Traceability Function
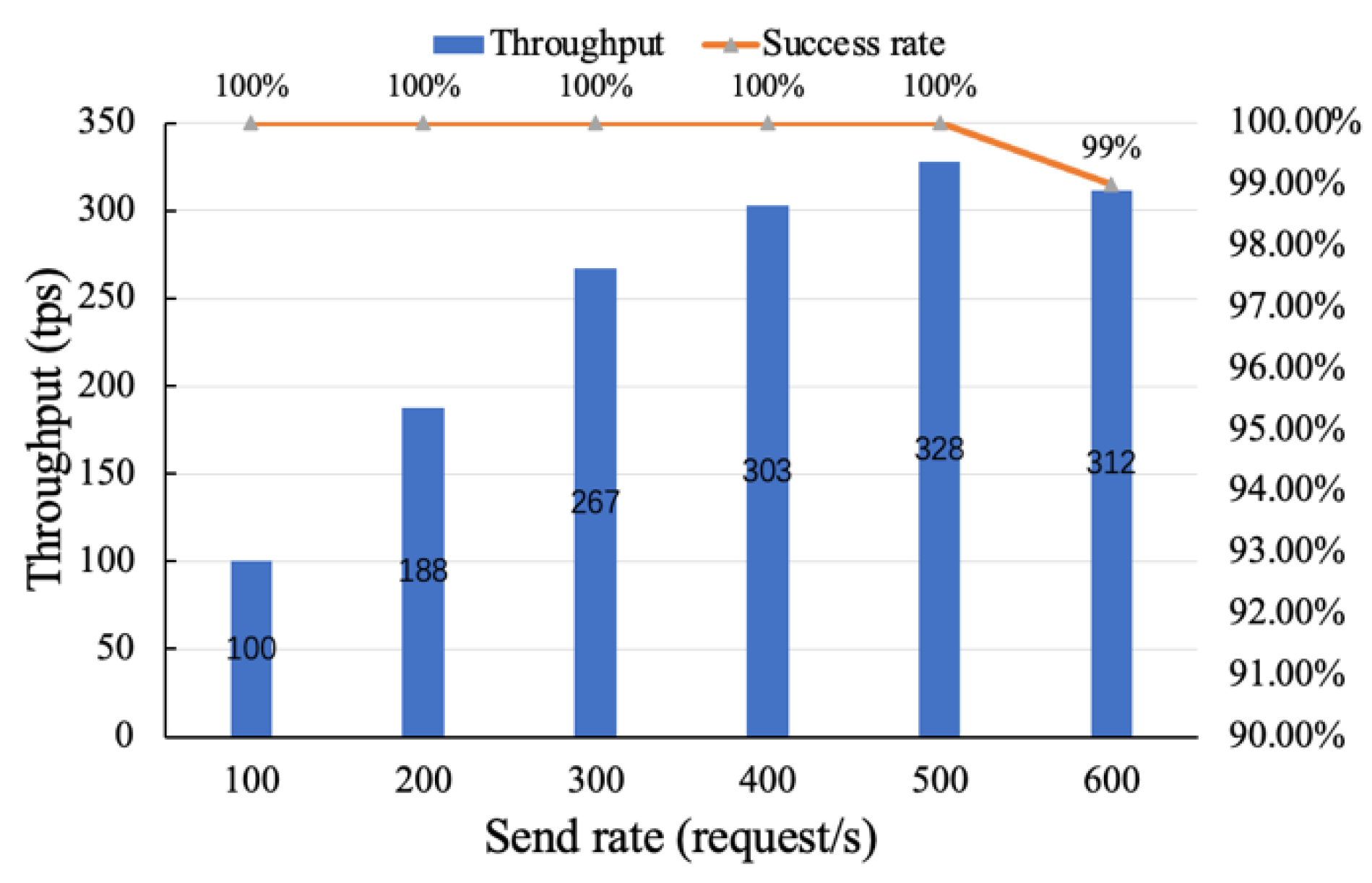
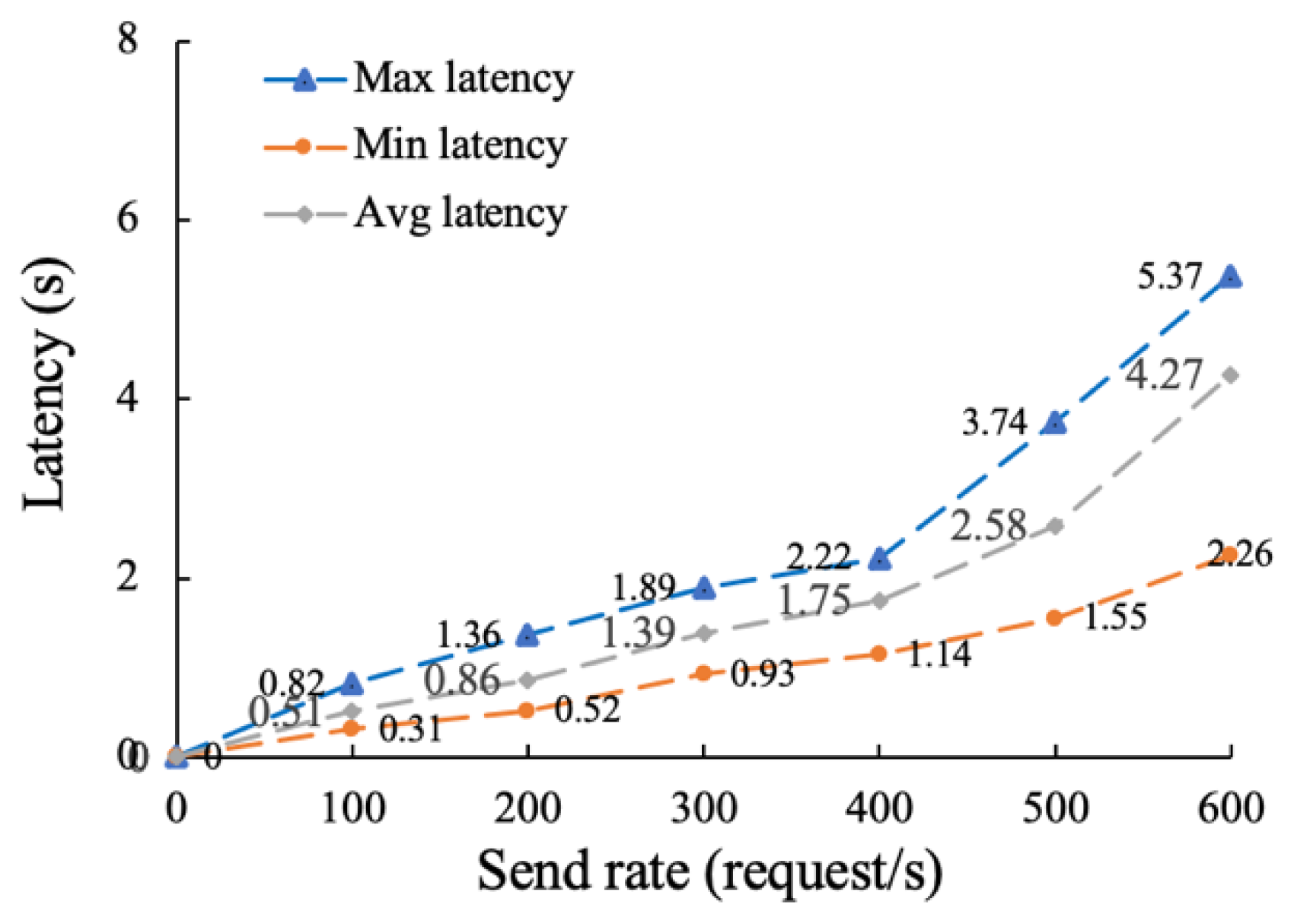
5.1.2. Throughput and Latency Testing of the Traceability Function
5.2. Performance Testing and Analysis of the On-Chain Function
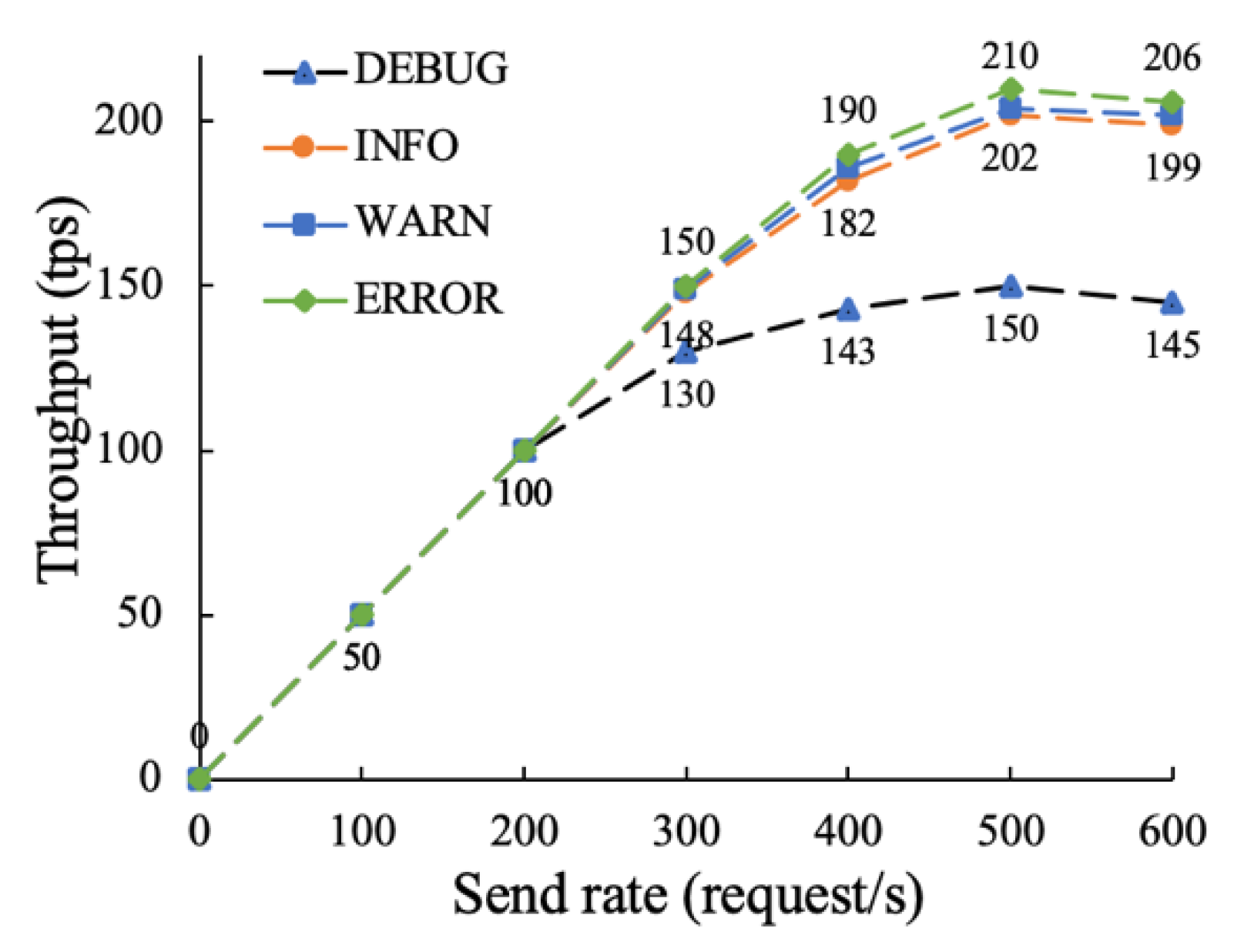
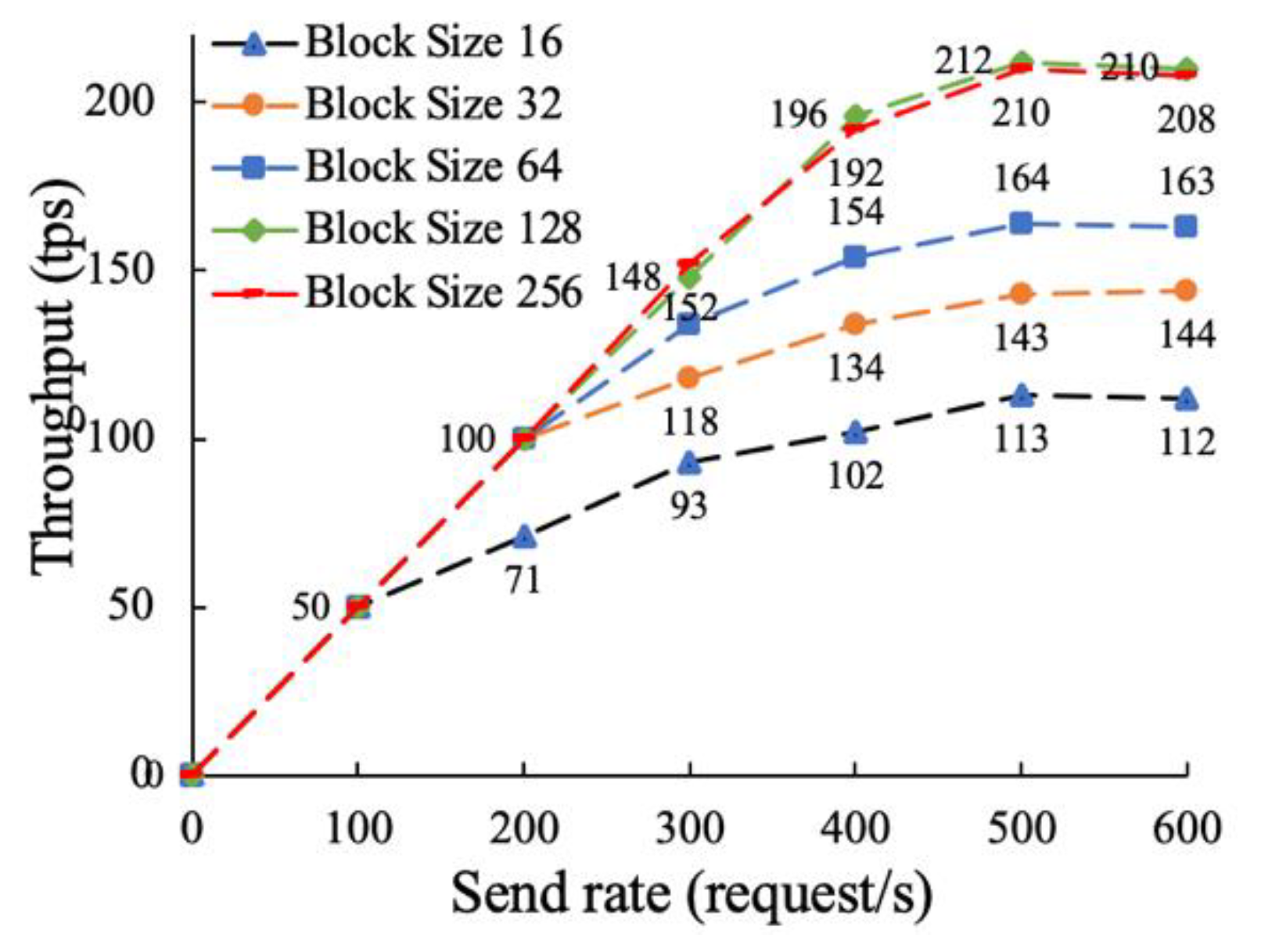
5.2.1. Throughput Testing and Analysis of the On-Chain Function
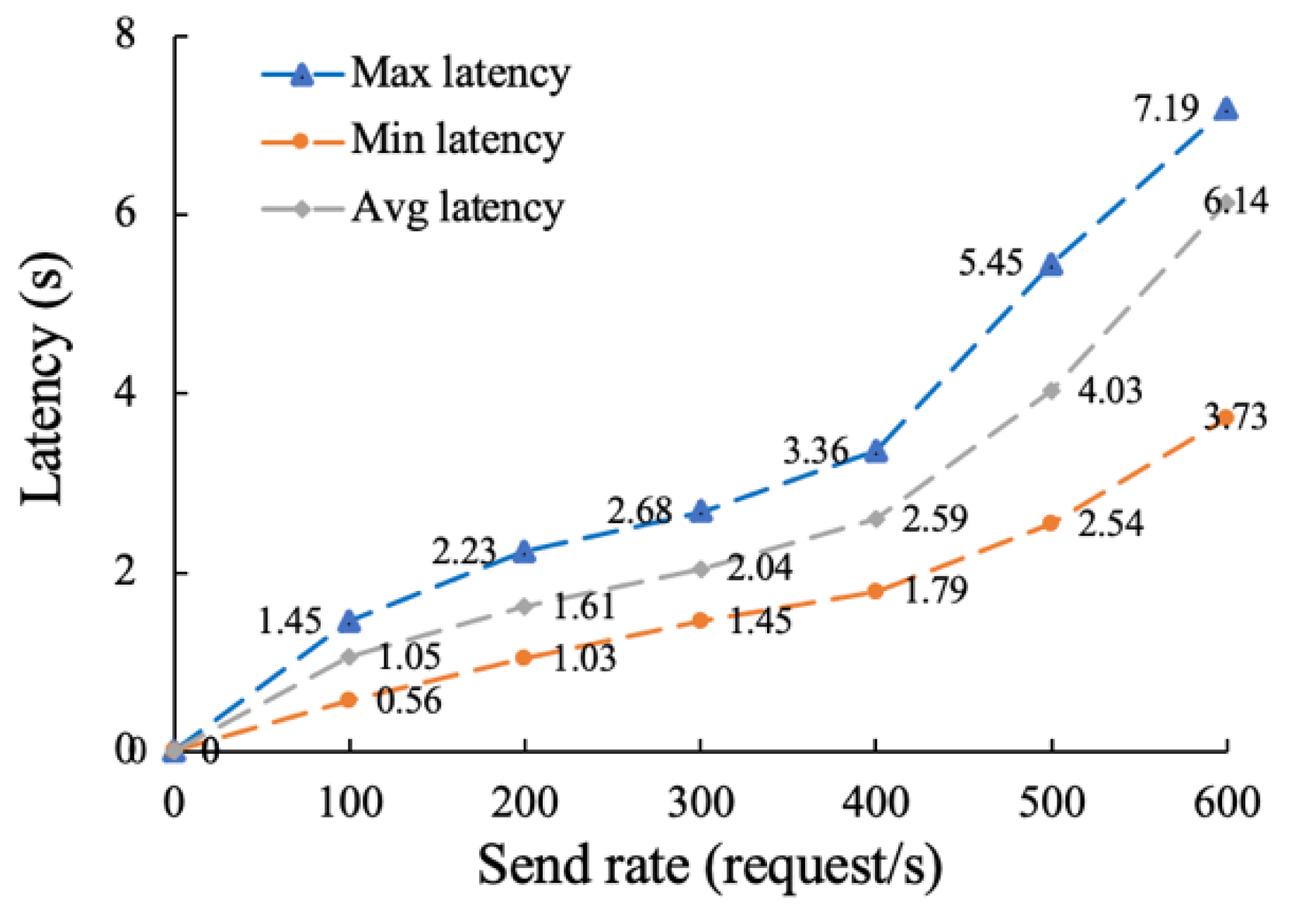
5.2.2. Latency Testing and Analysis of the On-Chain Function
5.3. Security Analysis
5.4. Discussion and Limitations
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Fernandez, R.C.; Subramaniam, P.; Franklin, M.J. Data Market Platforms: Trading Data Assets to Solve Data Problems. arXiv 2020, arXiv:2002.01047. [Google Scholar] [CrossRef]
- Dong, X.; Guo, B.; Shen, Y.; Duan, X.; Shen, Y.; Zhang, H. Data Assets Value Evaluation Model Based on Profit Maximization. Big Data Res. 2020, 6, 13–20. [Google Scholar] [CrossRef]
- Qin, C.; Guo, B.; Shen, Y.; Su, H.; Zhang, Z.; Zhou, M. Security Risk Assessment Model of Blockchain. Acta Electonica Sin. 2021, 49, 117. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Panda, S.S.; Sobhanayak, S. Blockchain Technology: A Survey on Applications and Security Privacy Challenges. Internet Things 2019, 8, 100107. [Google Scholar] [CrossRef]
- Dong, X.; Guo, B.; Shen, Y.; Duan, X.; Shen, Y.; Zhang, H. An Efficient and Secure Decentralizing Data Sharing Model. Chin. J. Comput. 2018, 41, 1021–1036. [Google Scholar] [CrossRef]
- Yue, X.; Wang, H.; Liu, W.; Li, W.; Shi, P.; Ouyang, X. JCDTA: The Data Trading Archtecture Design in Jointcloud Computing. In Proceedings of the 24th International Conference on Parallel and Distributed Systems (ICPADS), Singapore, 11–13 December 2018. [Google Scholar] [CrossRef]
- Zhang, F.; Guo, S.; Qiu, X.; Xu, S.; Qi, F.; Wang, Z. Federated Learning Meets Blockchain: State Channel Based Distributed Data Sharing Trust Supervision Mechanism. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Fan, H. The Digital Asset Value and Currency Supervision Under Deep Learning and Blockchain Technology. J. Comput. Appl. Math. 2022, 407, 114061. [Google Scholar] [CrossRef]
- Guo, B.; Li, Q.; Duan, X.; Shen, Y.; Dong, X.; Zhang, H.; Shen, Y.; Zhang, Z.; Luo, J. Personal Data Bank: A New Mode of Personal Big Data Asset Management and Value-Added Services Based on Bank Architecture. Chin. J. Comput. 2017, 40, 126–143. [Google Scholar] [CrossRef]
- Xiong, F.; Xie, M.; Zhao, L.; Li, C.; Fan, X. Recognition and Evaluation of Data as Intangible Assets. SAGE Open 2022, 12, 21582440221094600. [Google Scholar] [CrossRef]
- Harsasi, M.; Minrohayati. The Impact of Supply Chain Management Practices on Competitive Advantage. Int. J. Econ. Policy Emerg. Econ. 2017, 10, 240–247. [Google Scholar] [CrossRef]
- Leat, D.; Seltzer, K.; Stoker, G. Towards Holistic Governance: The New Reform Agenda; Bloomsbury Publishing: London, UK, 2002. [Google Scholar]
- Di Silvestre, M.L.; Gallo, P.; Guerrero, J.M.; Musca, R.; Sanseverino, E.R.; Sciume, G.; Zizzo, G. Blockchain for Power Systems: Current Trends and Future Applications. Renew. Sustain. Energy Rev. 2020, 119, 109585. [Google Scholar] [CrossRef]
- Pournader, M.; Shi, Y.; Seuring, S.; Koh, S.C. Blockchain Applications in Supply Chains, Transport and Logistics: A Systematic Review of The Literature. Int. J. Prod. Res. 2020, 58, 2063–2081. [Google Scholar] [CrossRef]
- Casino, F.; Kanakaris, V.; Dasaklis, T.K.; Moschuris, S.; Rachniotis, N.P. Modeling Food Supply Chain Traceability Based on Blockchain Technology. Ifac-Pap. 2019, 52, 2728–2733. [Google Scholar] [CrossRef]
- Wang, Q.; Changchun, L.; Baoru, Z. Trusted Transaction Method of Manufacturing Services Based on Blockchain. Comput. Integr. Manuf. Syst. 2019, 25, 3247–3257. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C.M. Blockchain-Based Decentralized Trust Management in Vehicular Networks. IEEE Internet Things J. 2018, 6, 1495–1505. [Google Scholar] [CrossRef]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using Blockchain for Medical Data Access and Permission Management. In Proceedings of the 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016. [Google Scholar] [CrossRef]
- Yang, X.; Zhou, Z.; Hao, X.; Xiao, Y. Analysis of Platform Economic Supervision Mode from the Perspective of Blockchain. Mob. Inf. Syst. 2022, 2022, 3534220. [Google Scholar] [CrossRef]
- Peng, X.; Zhang, X.; Wang, X.; Li, H.; Xu, J.; Zhao, Z.; Wang, Y. Research on the Cross-Chain Model of Rice Supply Chain Supervision Based on Parallel Blockchain and Smart Contracts. Foods 2022, 11, 1269. [Google Scholar] [CrossRef]
- Lin, Y.-P.; Mukhtar, H.; Huang, K.-T.; Petway, J.R.; Lin, C.-M.; Chou, C.-F.; Liao, S.-W. Real-Time Identification of Irrigation Water Pollution Sources and Pathways with A Wireless Sensor Network and Blockchain Framework. Sensors 2020, 20, 3634. [Google Scholar] [CrossRef]
- Dogo, E.M.; Salami, A.F.; Nwulu, N.I.; Aigbavboa, C.O. Blockchain and Internet of Things-Based Technologies for Intelligent Water Management System. In Artificial Intelligence in IoT; Springer: Cham, Switzerland, 2019; pp. 129–150. [Google Scholar] [CrossRef]
- Jung, T.; Li, X.-Y.; Huang, W.; Qiao, Z.; Qian, J.; Chen, L.; Han, J.; Hou, J. Accounttrade: Accountability Against Dishonest Big Data Buyers and Sellers. IEEE Trans. Inf. Forensics Secur. 2018, 14, 223–234. [Google Scholar] [CrossRef]
- Dai, W.; Daia, C.; Choo, K.-K.R.; Cui, C.; Zou, D.; Jin, H. SDTE: A Secure Blockchain-Based Data Trading Ecosystem. IEEE Trans. Inf. Forensics Secur. 2019, 15, 725–737. [Google Scholar] [CrossRef]
- Ramachandran, G.S.; Wright, K.; Zheng, L.; Navaney, P.; Naveed, M.; Krishnamachari, B.; Dhaliwal, J. Trinity: A Byzantine Fault-Tolerant Distributed Publish-Subscribe System with Immutable Blockchain-Based Persistence. In Proceedings of the International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Korea, 14–17 May 2019. [Google Scholar] [CrossRef]
- Wang, D.; Gao, J.; Yu, H.; Li, X. A Novel Digital Rights Management in P2P Networks Based on Bitcoin System. In Frontiers in Cyber Security, Proceedings of the International Conference FCS, Chengdu, China, 5–7 November 2018; Springer; Singapore, 2018. [Google Scholar] [CrossRef]
- Zhao, Y.; Yu, Y.; Li, Y.; Han, G.; Du, X. Machine Learning Based Privacy-Preserving Fair Data Trading in Big Data Market. Inf. Sci. 2019, 478, 449–460. [Google Scholar] [CrossRef]
- Dib, O.; Huyart, C.; Toumi, K. A Novel Data Exploitation Framework Based on Blockchain. Pervasive Mob. Comput. 2020, 61, 101104. [Google Scholar] [CrossRef]
- Niu, C.; Zheng, Z.; Wu, F.; Gao, X.; Chen, G. Trading Data in Good Faith: Integrating Truthfulness and Privacy Preservation in Data Markets. In Proceedings of the 33rd International Conference on Data Engineering (ICDE), San Diego, CA, USA, 19–22 April 2017. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for Secure and Efficient Data Sharing in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2018, 6, 4660–4670. [Google Scholar] [CrossRef]
- Li, Y.; Li, L.; Zhao, Y.; Guizani, N.; Yu, Y.; Du, X. Toward Decentralized Fair Data Trading Based on Blockchain. IEEE Netw. 2020, 35, 304–310. [Google Scholar] [CrossRef]
- Baralla, G.; Pinna, A.; Tonelli, R.; Marchesi, M.; Ibba, S. Ensuring Transparency and Traceability of Food Local Products: A Blockchain Application to A Smart Tourism Region. Concurr. Comput. Pract. Exp. 2021, 33, e5857. [Google Scholar] [CrossRef]
- Wang, L.; Xu, L.; Zheng, Z.; Liu, S.; Liu, X.; Cao, L.; Li, J.; Sun, C. Smart Contract-Based Agricultural Food Supply Chain Traceability. IEEE Access 2021, 9, 9296–9307. [Google Scholar] [CrossRef]
- Li, D.; Gong, Y.; Zhang, X.; Huang, M. An Exploratory Study on the Design and Management Model of Traditional Chinese Medicine Quality Safety Traceability System Based on Blockchain Technology. Secur. Commun. Netw. 2022, 2022, 7011145. [Google Scholar] [CrossRef]
- Yong, B.; Shen, J.; Liu, X.; Liu, F.; Chen, H.; Zhou, Q. An Intelligent Blockchain-Based System for Safe Vaccine Supply and Supervision. Int. J. Inf. Manag. 2020, 52, 102024. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, X.; Xu, J.; Wang, X.; Li, H.; Zhao, Z.; Kong, J. Blockchain-Based Information Supervision Model for Rice Supply Chains. Comput. Intell. Neurosci. 2022, 2022, 2914571. [Google Scholar] [CrossRef]
- Wei, J.; Zhu, Q.; Nie, L.; Shen, Z.; Choo, K.K.R.; Yu, K. A Redactable Blockchain Framework for Secure Federated Learning in Industrial Internet-of-Things. IEEE Internet Things J. 2022, 9, 17901–17911. [Google Scholar] [CrossRef]
- Yu, K.; Tan, L.; Yang, C.; Choo, K.K.R.; Bashir, A.K.; Rodrigues, J.J.; Sato, T. A blockchain-based Shamir’s threshold cryptography scheme for data protection in industrial internet of things settings. IEEE Internet Things J. 2021, 9, 8154–8167. [Google Scholar] [CrossRef]
- Tan, L.; Shi, N.; Yu, K.; Aloqaily, M.; Jararweh, Y. A blockchain-empowered access control framework for smart devices in green internet of things. ACM Trans. Internet Technol. 2021, 21, 1–20. [Google Scholar] [CrossRef]
- Górski, T. Reconfigurable Smart Contracts for Renewable Energy Exchange with Re-Use of Verification Rules. Appl. Sci. 2022, 12, 5339. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhou, C.; Guo, X.; Song, Y.; Chen, C. A Novel Decentralized E-Commerce Transaction System Based on Blockchain. Appl. Sci. 2022, 12, 5770. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Bus. Rev. 2008, 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 31 August 2022).
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain Technology: Beyond Bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Andreas, M. Masteing Bitcoin. Unlocking Digital Cryptocurrencies; O’Reilly Media, Inc.: Newton, MA, USA, 2015; pp. 49–68. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; Caro, A.D.; Ferris, C.; Laventman, G.; Manevich, Y.; Muralidharan, S.; et al. Hyperledger Fabric: A Distributed Operating System For Permissioned Blockchains. In Proceedings of the thirteenth EuroSys conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar] [CrossRef]
- Cachin, C. Architecture of the Hyperledger Blockchain Fabric. Workshop Distrib. Cryptocurrencies Consens. Ledgers 2016, 310, 1–4. [Google Scholar]
- Dhillon, V.; Metcalf, D.; HooperM. The Hyperledger Project. In Blockchain Enabled Applications; Apress: Berkeley, CA, USA, 2017; pp. 139–149. [Google Scholar] [CrossRef]
- Yang, X.; Wang, M.; Xu, D.; Luo, N.; Sun, C. Data storage and query method of agricultural products traceability information based on blockchain. Trans. Chin. Soc. Agric. Eng. 2019, 35, 323–330. [Google Scholar] [CrossRef]
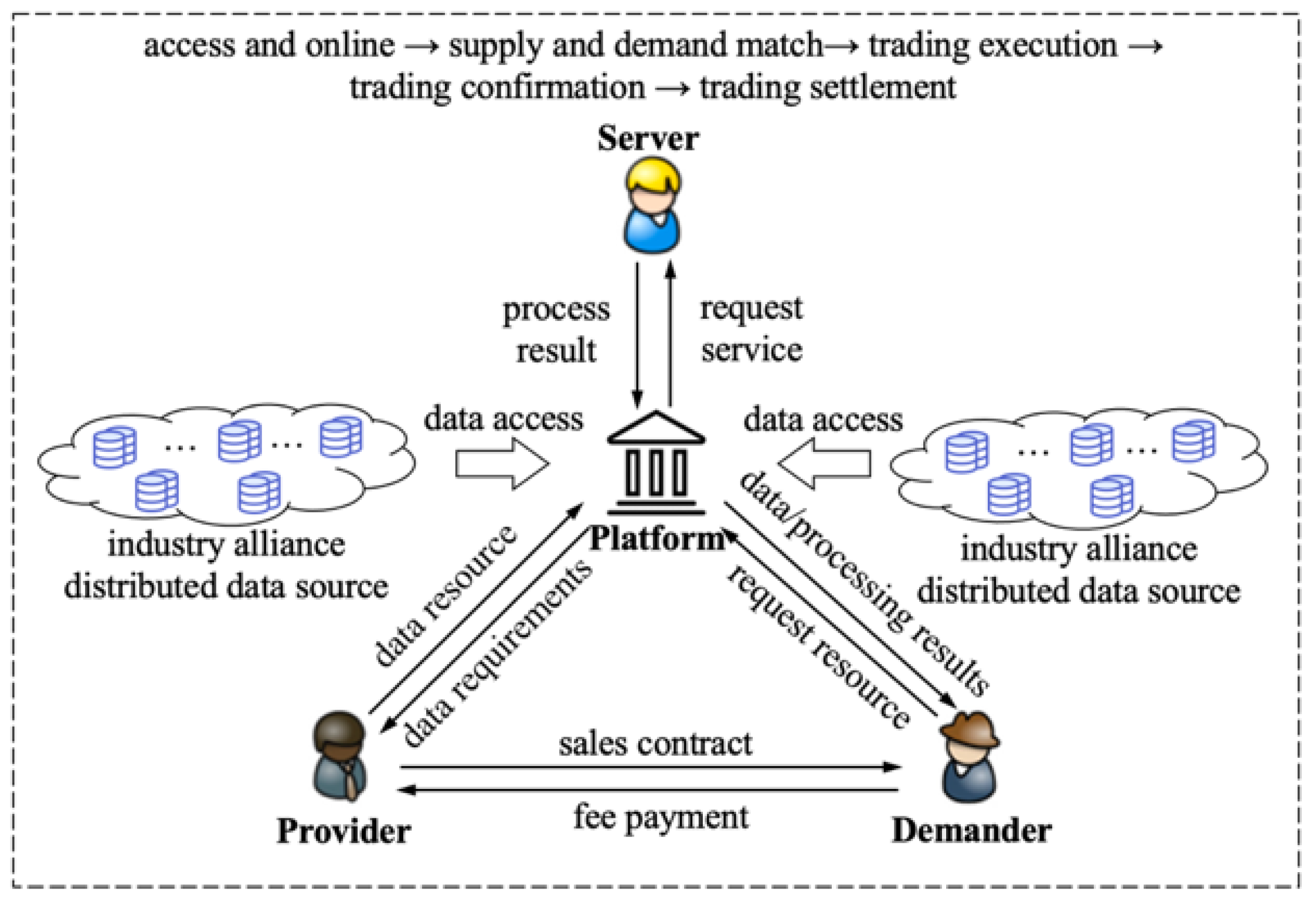
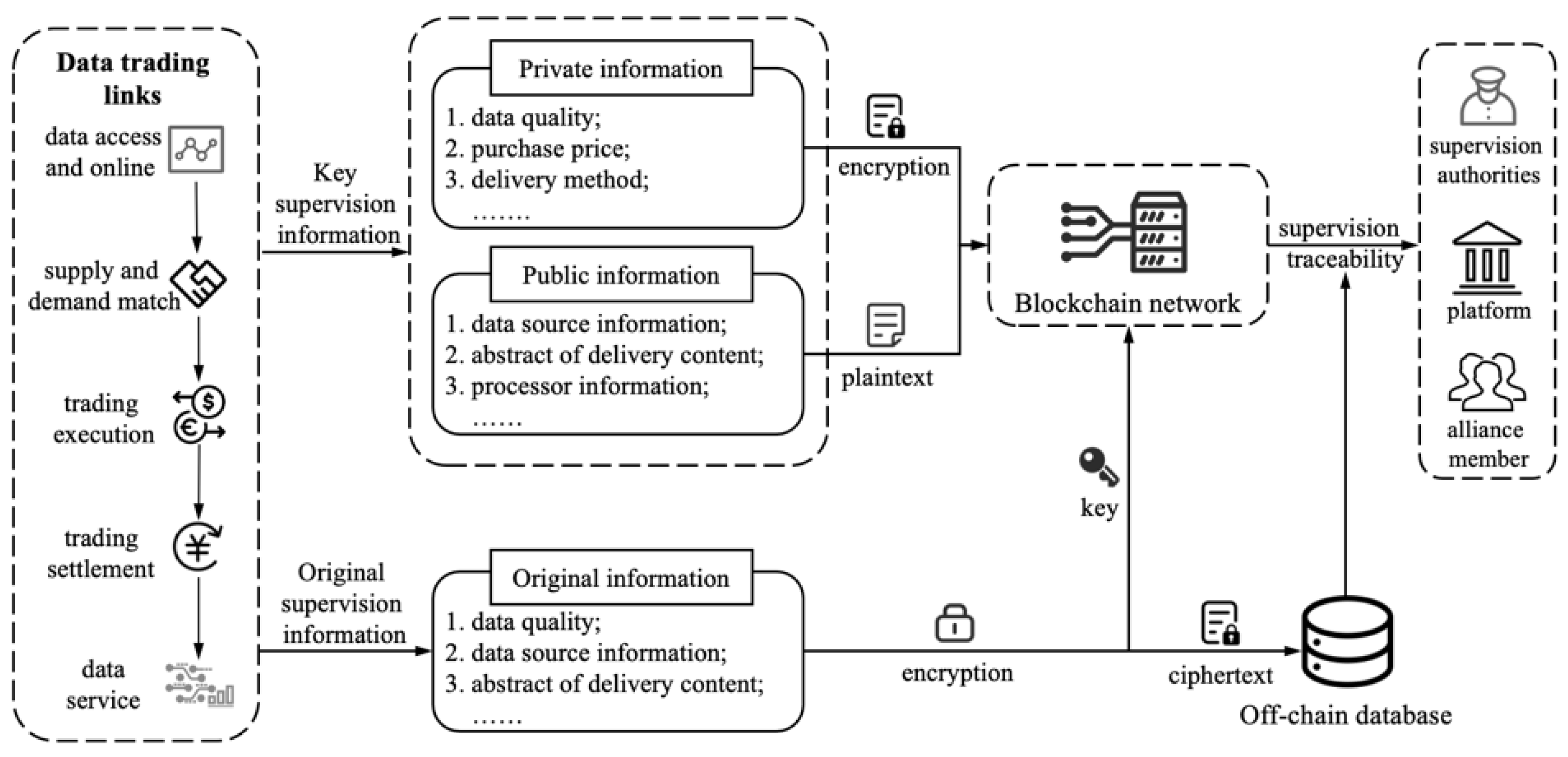
| Data Trading Links | Key Information | |
|---|---|---|
| Public Supervision Information | Private Supervision Information | |
| data access | data source information, data type, data format, data size, update time, preprocessing information. | data quality, sales price, owner information. |
| supply and demand match | functional or target requirements, standards or specifications to be met, purchase quantity, delivery time, dataset size, dataset description. | purchase price, sale price, delivery method, data storage address. |
| trading implementation | purchase method, delivery time, dataset name, data online time, abstract of delivery content. | delivery method, selling company. |
| trading settlement | order number, payment method, payment amount, payment time. | platform handling fee, trading time, trading price. |
| data service | server information, data service requirements, data service type, completion time. | processing price, result delivery method. |
| Symbol | Description |
|---|---|
| The enterprise node. | |
| The supervision node. | |
| Supervision channel authorization file. | |
| Off-chain database authorization file. | |
| Privacy trading supervision information. | |
| Public trading supervision information. | |
| The name of the data trading. | |
| It represents the location of the hash value of the data trading supervision information in the blockchain. | |
| Transaction hash. | |
| Verification results of data trading information traceability process. | |
| The on-chain and off-chain hash values are the same, and the verification passes. | |
| Verification failed because the hash values on-chain and off-chain are inconsistent. |
| Number | Logging Level | Block Size/KB |
|---|---|---|
| 1 | DEBUG/INFO/WARN/ERROR | 64 |
| 2 | INFO | 16/32/64/128/256 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, J.; Guo, B.; Ding, X.; Hu, D.; Jiang, Y. Distributed Supervision Model for Enterprise Data Asset Trading Based on Blockchain Multi-Channel in Industry Alliance. Sensors 2022, 22, 7842. https://doi.org/10.3390/s22207842
Zhang J, Guo B, Ding X, Hu D, Jiang Y. Distributed Supervision Model for Enterprise Data Asset Trading Based on Blockchain Multi-Channel in Industry Alliance. Sensors. 2022; 22(20):7842. https://doi.org/10.3390/s22207842
Chicago/Turabian StyleZhang, Jianxiong, Bing Guo, Xuefeng Ding, Dasha Hu, and Yuming Jiang. 2022. "Distributed Supervision Model for Enterprise Data Asset Trading Based on Blockchain Multi-Channel in Industry Alliance" Sensors 22, no. 20: 7842. https://doi.org/10.3390/s22207842
APA StyleZhang, J., Guo, B., Ding, X., Hu, D., & Jiang, Y. (2022). Distributed Supervision Model for Enterprise Data Asset Trading Based on Blockchain Multi-Channel in Industry Alliance. Sensors, 22(20), 7842. https://doi.org/10.3390/s22207842





