An Industrial IoT-Based Blockchain-Enabled Secure Searchable Encryption Approach for Healthcare Systems Using Neural Network
Abstract
:1. Introduction
- Our proposed algorithms converts data into a new reduced structure for attack prevention and poisoning.
- The proposed model detects intrusion and nonintrusion data.
1.1. Motivation
1.2. Contributions
- A detailed literature review of the state-of-the-art patient and participants detection based on encryption ad security algorithms.
- Novel cross-domain and access control policies are proposed using homomorphic encryption.
- We propose the idea and implementation of policies revocation, updates, delete and add using homomorphic encryption.
- We achieve optimum security and anonymous keyword search in the Hyperledger Fabric framework.
- Our proposed research method provides an alternative private key in case the key is lost.
- We achieve efficiency compared to the existing methods, as these methods exhibit more communication and encryption cost because they need to encrypt the data. Our proposed plans provide a more efficient solution to the users.
2. Literature Review
State of the Art
- What are the threats that IIoT can face when blockchain is utilized in the integrated framework?
- How can blockchain transparency impact the exposure of IIoT environments to external threats?
- What are the implications of compromising blockchain nodes within IIoT environments?
3. Preliminary Data
3.1. Blockchain in Healthcare System Using Hyperledger System
Blockchain Technology
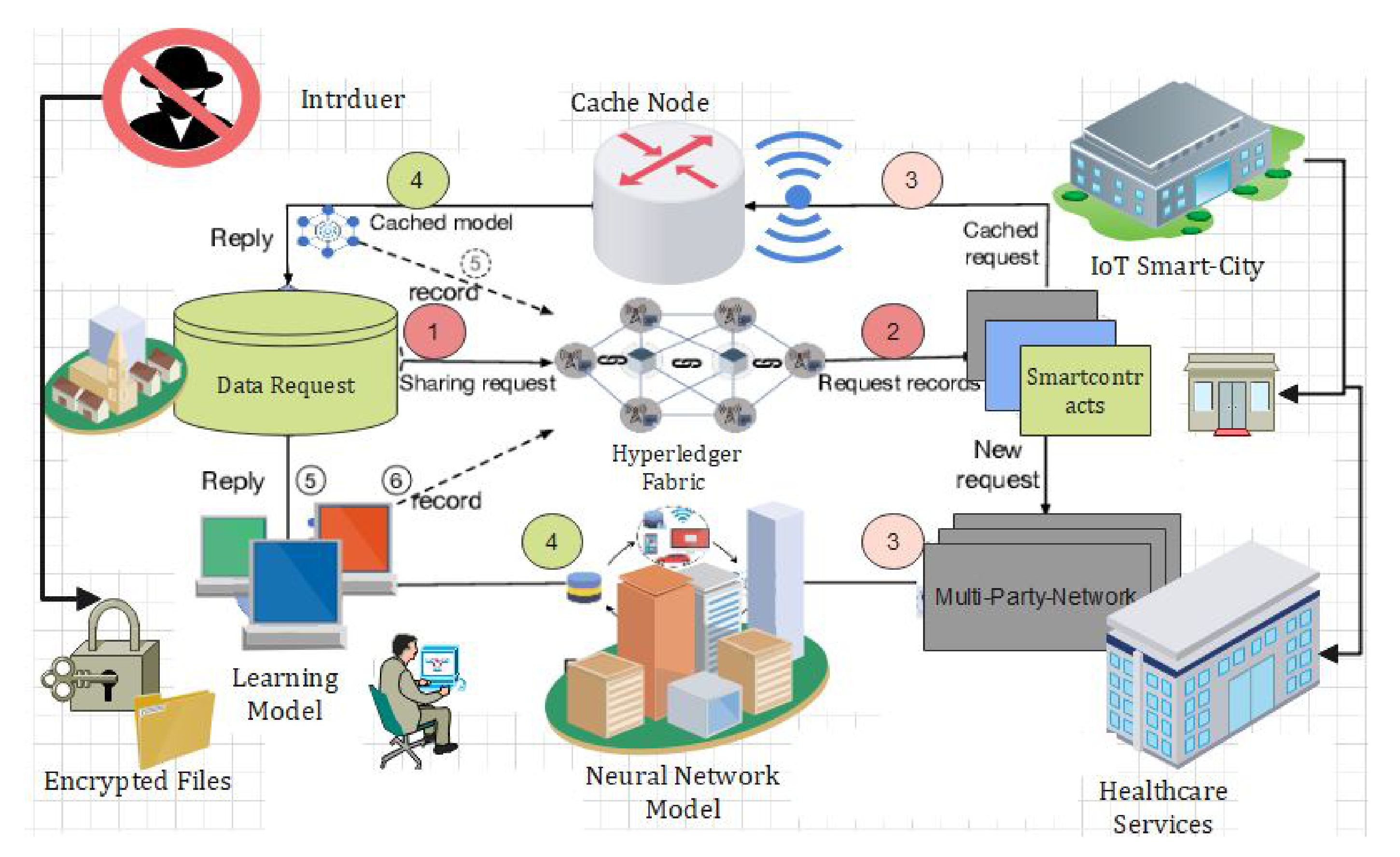
4. Proposed Secure Search Algorithm
| Algorithm 1: Attribute Based Signing Algorithm |
 |
4.1. Proposed Access Control System for Framework
4.2. Proposed Algorithm
4.3. Hybrid Neural Network Algorithm
- Initialization of neural network parameters with a maximum number of iterations.
- Determine the constraints of the optimal solution.
- Evaluation of fitness functions and the constraints that these functions impose.
- The multi-balanced neural network algorithm selects the optimal solution at two levels.
- The group theory optimization algorithm selects the best transaction time.
- The binary search algorithm algorithm selects the best route within the blockchain.
4.4. Revocation Policy for Proposed Framework
4.5. Update Policy and Proposed Algorithm
| Algorithm 2: Homomorphic Encryption |
 |
4.6. Proposed Methodology
4.7. Proposed Data-Sharing Scheme
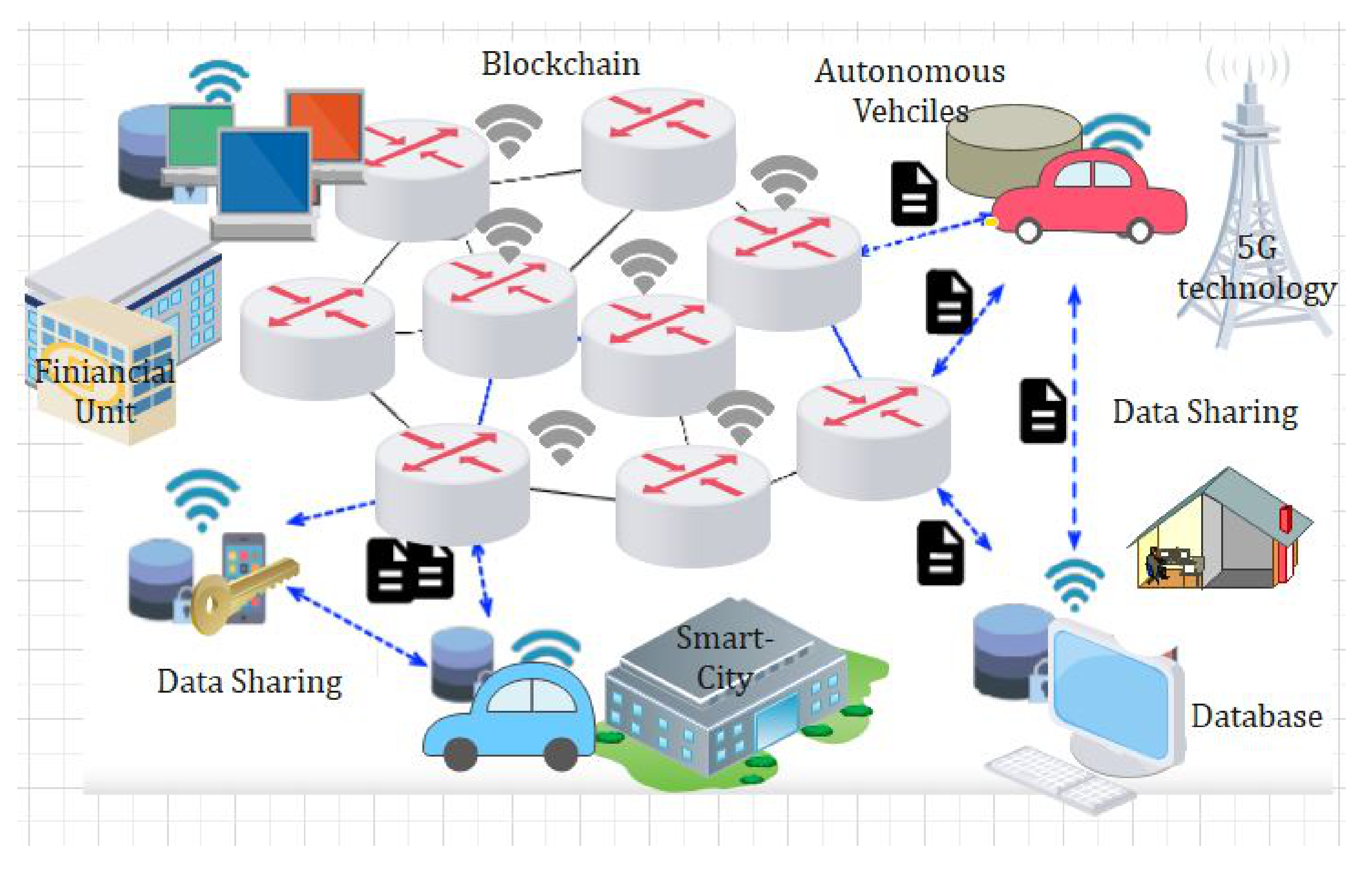

4.8. Security Analysis
4.9. Intrusion Detection Module
4.10. Security Threat Model
- Intended malicious insider: intent to affect the confidentiality, integrity, and/or availability of systems and data.
- Unintended innocent insider: person working for the organization making a human error in their day-to-day duties.
- Compromised insider: involves compromising an employee’s user account due to the lack of security awareness from sources such as phishing and trojans.
- External threats are generated from the exploitation of internal vulnerabilities to assist attackers to gain access to environments.
- Malicious actor.
- Compromised supply chain.
- External insider threats.
| Number of People | FPR | FNR | FDR | ACC |
|---|---|---|---|---|
| 100 | 0 | 0 | 0 | 1 |
| 200 | 0 | 0.022 | 0.025 | 0.96 |
| 300 | 0.002 | 0.029 | 0.035 | 0.87 |
- Internal threats
- External threat attacks
5. Experimental Results
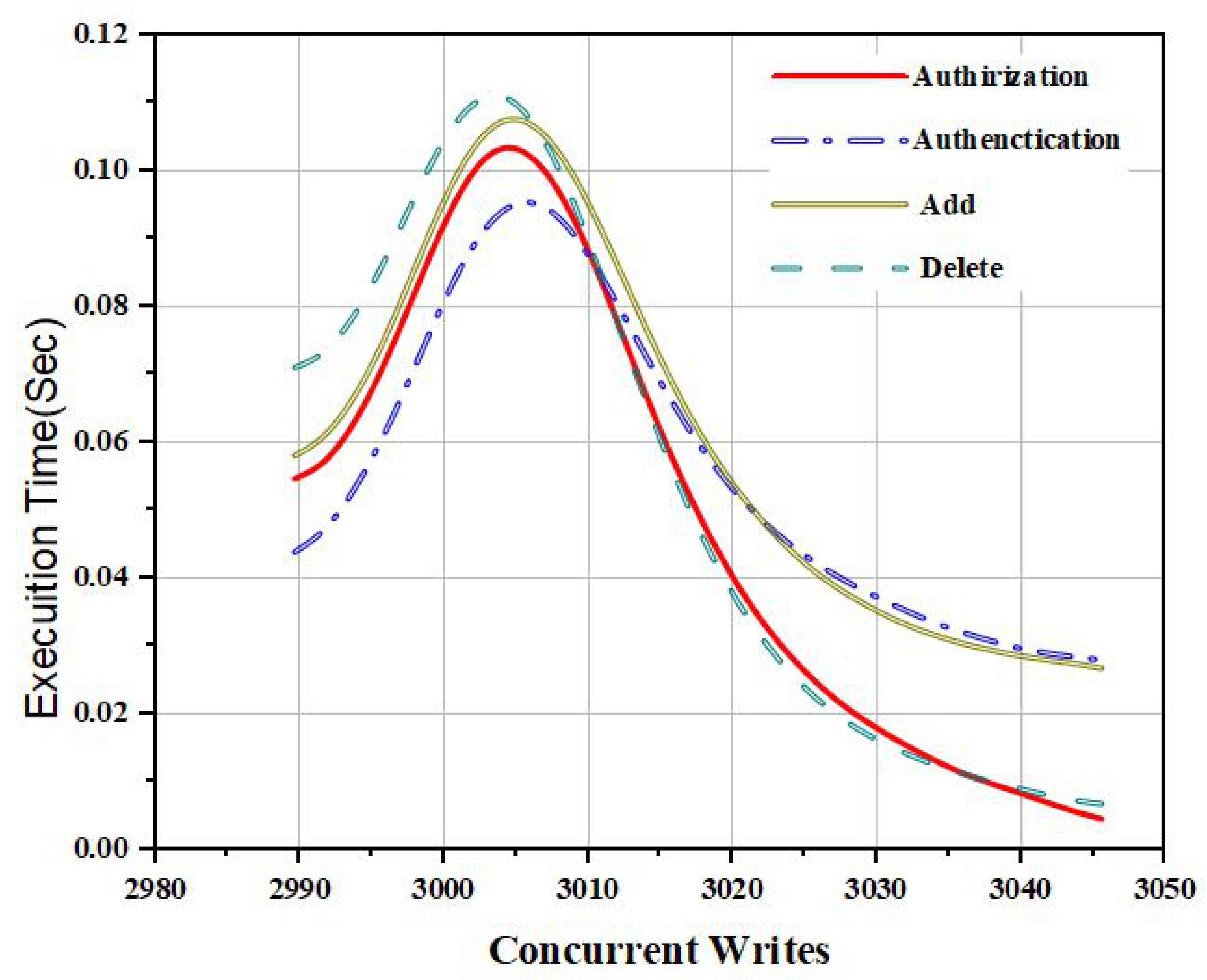


6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Shah, A.A.; Piro, G.; Grieco, L.A.; Boggia, G. A qualitative cross-comparison of emerging technologies for software-defined systems. In Proceedings of the 2019 Sixth International Conference on Software Defined Systems (SDS), Rome, Italy, 10–13 June 2019; pp. 138–145. [Google Scholar]
- Ali, A.; Mehboob, M. Comparative analysis of selected routing protocols for wlan based wireless sensor networks (wsns). In Proceedings of the 2nd International Multi-Disciplinary Conference, Gujrat, Pakistan, 19–20 December 2016; Volume 19, p. 20. [Google Scholar]
- Shah, A.A.; Piro, G.; Grieco, L.A.; Boggia, G. A review of forwarding strategies in transport software-defined networks. In Proceedings of the 2020 22nd International Conference on Transparent Optical Networks (ICTON), Bari, Italy, 19–23 July 2020; pp. 1–4. [Google Scholar]
- Gatteschi, V.; Lamberti, F.; Demartini, C.; Pranteda, C.; Santamaría, V. Blockchain and smart contracts for insurance: Is the technology mature enough? Future Internet 2018, 10, 20. [Google Scholar] [CrossRef] [Green Version]
- Jia, B.; Zhou, T.; Li, W.; Liu, Z.; Zhang, J. A blockchain-based location privacy protection incentive mechanism in crowd sensing networks. Sensors 2018, 18, 3894. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Biswas, K.; Muthukkumarasamy, V. Securing smart cities using blockchain technology. In Proceedings of the 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Sydney, Australia, 12–14 December 2016; pp. 1392–1393. [Google Scholar]
- Fernández-Caramés, T.M.; Froiz-Míguez, I.; Blanco-Novoa, O.; Fraga-Lamas, P. `Enabling the internet of mobile crowdsourcing health things: A mobile fog computing, blockchain and iot based continuous glucose monitoring system for diabetes mellitus research and care. Sensors 2019, 19, 3319. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ali, A.; Naveed, M.; Mehboob, M.; Irshad, H.; Anwar, P. An interference aware multi-channel mac protocol for wasn. In Proceedings of the 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT), Karachi, Pakistan, 5–7 April 2017; pp. 1–9. [Google Scholar]
- Beebeejaun, A. Vat on foreign digital services in mauritius; a comparative study with south africa. Int. J. Law Manag. 2020, 63, 239–250. [Google Scholar] [CrossRef]
- Shah, A.A.; Piro, G.; Grieco, L.A.; Boggia, G. A quantitative cross-comparison of container networking technologies for virtualized service infrastructures in local computing environments. Trans. Emerg. Telecommun. Technol. 2021, 32, e4234. [Google Scholar]
- Kim, H.; Kim, S.-H.; Hwang, J.Y.; Seo, C. Efficient privacy-preserving machine learning for blockchain network. IEEE Access 2019, 7, 136481–136495. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Srivastava, G.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R.; Aledhari, M. Decentralized authentication of distributed patients in hospital networks using blockchain. IEEE J. Biomed. Health Inform. 2020, 24, 2146–2156. [Google Scholar] [CrossRef]
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2019, 25, 1398–1411. [Google Scholar] [CrossRef]
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. Veh. Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- Hang, L.; Kim, D.-H. Design and implementation of an integrated iot blockchain platform for sensing data integrity. Sensors 2019, 19, 2228. [Google Scholar] [CrossRef] [Green Version]
- Yu, B.; Kermanshahi, S.K.; Sakzad, A.; Nepal, S. Chameleon hash time-lock contract for privacy preserving payment channel networks. In Proceedings of the International Conference on Provable Security, Cairns, Australia, 1–4 October 2019; pp. 303–318. [Google Scholar]
- Hameed, K.; Ali, A.; Naqvi, M.H.; Jabbar, M.; Junaid, M.; Haider, A. Resource management in operating systems-a survey of scheduling algorithms. In Proceedings of the International Conference on Intelligent Computing (ICIC), Lanzhou, China, 2–5 August 2016. [Google Scholar]
- Jung, Y.; Peradilla, M.; Agulto, R. Packet key-based end-to-end security management on a blockchain control plane. Sensors 2019, 19, 2310. [Google Scholar] [CrossRef] [Green Version]
- Esposito, C.; Santis, A.D.; Tortora, G.; Chang, H.; Choo, K.-K.R. Blockchain: A panacea for healthcare cloud-based data security and privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar] [CrossRef]
- Choo, C.W. Information Management for the Intelligent Organization: The art of Scanning the Environment; Information Today, Inc.: Medford, NJ, USA, 2002. [Google Scholar]
- Kermanshahi, S.K.; Liu, J.K.; Steinfeld, R.; Nepal, S.; Lai, S.; Loh, R.; Zuo, C. Multi-client cloud-based symmetric searchable encryption. IEEE Trans. Dependable Secur. Comput. 2019, 18, 2419–2437. [Google Scholar] [CrossRef]
- Kermanshahi, S.K.; Liu, J.K.; Steinfeld, R. Multi-user cloud-based secure keyword search. In Proceedings of the Australasian Conference on Information Security and Privacy, Auckland, New Zealand, 3–5 July 2017; pp. 227–247. [Google Scholar]
- Kermanshahi, S.K.; Liu, J.K.; Steinfeld, R.; Nepal, S. Generic multi-keyword ranked search on encrypted cloud data. In Proceedings of the European Symposium on Research in Computer Security, Luxembourg, 23–27 September 2019; pp. 322–343. [Google Scholar]
- Daraghmi, E.-Y.; Daraghmi, Y.-A.; Yuan, S.-M. Medchain: A design of blockchain-based system for medical records access and permissions management. IEEE Access 2019, 7, 164595–164613. [Google Scholar] [CrossRef]
- Rathi, V.K.; Chaudhary, V.; Rajput, N.K.; Ahuja, B.; Jaiswal, A.K.; Gupta, D.; Elhoseny, M.; Hammoudeh, M. A blockchain-enabled multi domain edge computing orchestrator. J. IEEE Internet Things Mag. 2020, 3, 30–36. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Adhi Tama, B.; Shahzad, M.K.; Choi, Y.-H. Secure and Blockchain-Based Emergency Driven Message Protocol for 5G Enabled Vehicular Edge Computing. Sensors 2020, 20, 154. [Google Scholar] [CrossRef] [Green Version]
- Feng, C.; Yu, K.; Bashir, A.K.; Al-Otaibi, Y.D.; Lu, Y.; Chen, S.; Zhang, D. Efficient and secure data sharing for 5G flying drones: A blockchain-enabled approach. IEEE Netw. 2021, 35, 130–137. [Google Scholar] [CrossRef]
- Khujamatov, K.; Reypnazarov, E.; Akhmedov, N.; Khasanov, D. Blockchain for 5G Healthcare architecture. In Proceedings of the 2020 International Conference on Information Science and Communications Technologies (ICISCT), Tashkent, Uzbekistan, 4–6 November 2020; pp. 1–5. [Google Scholar]
- Vivekanandan; Manojkumar; Sastry, V.N.; Srinivasulu Reddy, U. BIDAPSCA5G: Blockchain based Internet of Things (IoT) device to device authentication protocol for smart city applications using 5G technology. Peer Peer Netw. Appl. 2021, 14, 403–419. [Google Scholar] [CrossRef]
- Gao, J.; Agyekum, K.O.O.; Sifah, E.B.; Acheampong, K.N.; Xia, Q.; Du, X.; Guizani, M.; Xia, H. A blockchain-SDN-enabled Internet of vehicles environment for fog computing and 5G networks. IEEE Internet Things J. 2019, 7, 4278–4291. [Google Scholar] [CrossRef]
- Zhou, S.; Huang, H.; Chen, W.; Zhou, P.; Zheng, Z.; Guo, S. Pirate: A blockchain-based secure framework of distributed machine learning in 5g networks. IEEE Netw. 2020, 34, 84–91. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, K.; Moustafa, H.; Wang, S.; Zhang, K. Guest Editorial: Blockchain and AI for Beyond 5G Networks. IEEE Netw. 2020, 34, 22–23. [Google Scholar] [CrossRef]
- Zhao, Y.; Zhao, J.; Zhai, W.; Sun, S.; Niyato, D.; Lam, K.Y. A survey of 6G wireless communications: Emerging technologies. In Proceedings of the Future of Information and Communication Conference, Vancouver, BC, Canada, 29–30 April 2021; pp. 150–170. [Google Scholar]
- Bhattacharya, P.; Tanwar, S.; Shah, R.; Ladha, A. Mobile edge computing-enabled blockchain framework—A survey. In Proceedings of ICRIC 2019; Springer: Cham, Switzerland, 2020; pp. 797–809. [Google Scholar]
- Kaushik, S. Blockchain and 5G-Enabled Internet of Things: Background and Preliminaries. In Blockchain for 5G-Enabled IoT; Springer: Cham, Switzerland, 2021; pp. 3–31. [Google Scholar]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Budhiraja, I.; Tyagi, S.; Tanwar, S.; Kumar, N.; Guizani, M. CR-NOMA Based Interference Mitigation Scheme for 5G Femtocells Users. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018. [Google Scholar]
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A decentralized privacy-preserving healthcare blockchain for iot. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [Green Version]
- Wan, Z.; Guan, Z.; Zhou, Y.; Ren, K. zk-AuthFeed: How to Feed Authenticated Data into Smart Contract with Zero Knowledge. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 83–90. [Google Scholar]
- Jin, H.; Su, L.; Xiao, H.; Nahrstedt, K. Incentive Mechanism for Privacy-Aware Data Aggregation in Mobile Crowd Sensing Systems. IEEE/ACM Trans. Netw. 2018, 26, 2019–2032. [Google Scholar] [CrossRef]
- Pang, X.; Guo, D.; Wang, Z.; Sun, P.; Zhang, L. Towards fair and efficient task allocation in blockchain-based crowdsourcing. CCF Trans. Netw. 2020, 3, 193–204. [Google Scholar] [CrossRef]
- Ali, A.; Rahim, H.A.; Ali, J.; Pasha, M.F.; Masud, M.; Rehman, A.U.; Chen, C.; Baz, M. A Novel Secure Blockchain Framework for Accessing Electronic Health Records Using Multiple Certificate Authority. Appl. Sci. 2021, 11, 9999. [Google Scholar] [CrossRef]
- Ali, A.; Rahim, H.A.; Pasha, M.F.; Dowsley, R.; Masud, M.; Ali, J.; Baz, M. Security, Privacy, and Reliability in Digital Healthcare Systems Using Blockchain. Electronics 2021, 10, 2034. [Google Scholar] [CrossRef]
- Siam, A.I.; Almaiah, M.A.; Al-Zahrani, A.; Elazm, A.A.; El Banby, G.M.; El-Shafai, W.; El-Bahnasawy, N.A. Secure Health Monitoring Communication Systems Based on IoT and Cloud Computing for Medical Emergency Applications. Comput. Intell. Neurosci. 2021, 2021, 8016525. [Google Scholar] [CrossRef]
- Qasem, M.H.; Obeid, N.; Hudaib, A.; Almaiah, M.A.; Al-Zahrani, A.; Al-Khasawneh, A. Multi-Agent System Combined With Distributed Data Mining for Mutual Collaboration Classification. IEEE Access 2021, 9, 70531–70547. [Google Scholar] [CrossRef]
- Ali, A.; Pasha, M.F.; Ali, J.; Fang, O.H.; Masud, M.; Jurcut, A.D.; Alzain, M.A. Deep Learning Based Homomorphic Secure Search-Able Encryption for Keyword Search in Blockchain Healthcare System: A Novel Approach to Cryptography. Sensors 2022, 22, 528. [Google Scholar] [CrossRef]
- Almaiah, M.A. A New Scheme for Detecting Malicious Attacks in Wireless Sensor Networks Based on Blockchain Technology. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer: Cham, Switzerland, 2021; p. 217. [Google Scholar]
- Almaiah, M.A.; Al-Zahrani, M. Multilayer Neural Network based on MIMO and Channel Estimation for Impulsive Noise Environment in Mobile Wireless Networks. Int. J. Adv. Trends Comput. Sci. Eng. 2020, 9, 315–321. [Google Scholar] [CrossRef]

| S. No | Parameters | Details |
|---|---|---|
| 1 | Blockchain network | |
| 2 | Clinician ID | |
| 3 | Lab ID | |
| 4 | Patient health record | |
| 5 | Ring signature | |
| 6 | Username | |
| 7 | Private key | |
| 8 | r | Integer |
| 9 | N | Number of nodes |
| 10 | G | Bilinear order group |
| 11 | Generator of additive group 1 | |
| 12 | Generator of additive group 2 | |
| 13 | Bilinear identifier | |
| 14 | H | Homomorphic encryption |
| 15 | k | Degree of signature |
| Parameters | Details |
|---|---|
| Dataset size | 100 number of blocks + PHR |
| Hardware | GPU-enabled system |
| Software | Ethereum, Hyperledger Fabric |
| Parameters | Block height, number of blocks, no. transac, no. PHR, delay, signature creation |
| Performance metric | Efficiency (average percentage of gas, no. packets, no. dead nodes, no. alive nodes), |
| security (execution time of policies) and cost (execution time of blocks) | |
| Number of simulations | Number of test performed on single dataset |
| Number of rounds or transactions | 5000 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ali, A.; Almaiah, M.A.; Hajjej, F.; Pasha, M.F.; Fang, O.H.; Khan, R.; Teo, J.; Zakarya, M. An Industrial IoT-Based Blockchain-Enabled Secure Searchable Encryption Approach for Healthcare Systems Using Neural Network. Sensors 2022, 22, 572. https://doi.org/10.3390/s22020572
Ali A, Almaiah MA, Hajjej F, Pasha MF, Fang OH, Khan R, Teo J, Zakarya M. An Industrial IoT-Based Blockchain-Enabled Secure Searchable Encryption Approach for Healthcare Systems Using Neural Network. Sensors. 2022; 22(2):572. https://doi.org/10.3390/s22020572
Chicago/Turabian StyleAli, Aitizaz, Mohammed Amin Almaiah, Fahima Hajjej, Muhammad Fermi Pasha, Ong Huey Fang, Rahim Khan, Jason Teo, and Muhammad Zakarya. 2022. "An Industrial IoT-Based Blockchain-Enabled Secure Searchable Encryption Approach for Healthcare Systems Using Neural Network" Sensors 22, no. 2: 572. https://doi.org/10.3390/s22020572
APA StyleAli, A., Almaiah, M. A., Hajjej, F., Pasha, M. F., Fang, O. H., Khan, R., Teo, J., & Zakarya, M. (2022). An Industrial IoT-Based Blockchain-Enabled Secure Searchable Encryption Approach for Healthcare Systems Using Neural Network. Sensors, 22(2), 572. https://doi.org/10.3390/s22020572







