Abstract
The development of 5G networks has rapidly increased the use of Industrial Internet of Things (IIoT) devices for control, monitoring, and processing purposes. Biometric-based user authentication can prevent unauthorized access to IIoT devices, thereby safeguarding data security during production. However, most biometric authentication systems in the IIoT have no template protection, thus risking raw biometric data stored as templates in central databases or IIoT devices. Moreover, traditional biometric authentication faces slow, limited database holding capacity and data transmission problems. To address these issues, in this paper we propose a secure online fingerprint authentication system for IIoT devices over 5G networks. The core of the proposed system is the design of a cancelable fingerprint template, which protects original minutia features and provides privacy and security guarantee for both entity users and the message content transmitted between IIoT devices and the cloud server via 5G networks.Compared with state-of-the-art methods, the proposed authentication system shows competitive performance on six public fingerprint databases, while saving computational costs and achieving fast online matching.
1. Introduction
With the development of 5G mobile communication networks, industrial automation is expanding at a rapid pace. This transition is also known as the “Industrial Internet of Things (IIoT)” or “smart factories” [1]. 5G networks have a host of desirable features, such as high transmission rate, low latency, low energy consumption and massive machine-type communication [1]. The development of 5G networks greatly increases the use of IoT/IIoT devices for control, monitoring and processing purposes. Therefore, industries such as manufacturing are utilising the IIoT to make machines more intelligent [2]. Despite the benefits of the 5G reflected by IIoT applications, data security is a critical challenge. For example, a manufacturer can collect raw data from its devices (e.g., sensors) and even assets. These data may contain private information, such as customers’ personal information (e.g., their behavior characteristics) [3], causing information leakage and privacy invasion. Hence, appropriate security measures must be taken to ensure data safety and integrity in the IIoT.
User authentication is key to reliable IIoT applications like advanced manufacturing [4], as it prevents unauthorized or fraudulent access to IIoT devices. A secure authentication system can guarantee that data transfer is between legitimate IIoT users and devices or equipment. Compared with password-based authentication, biometric systems offer practical convenience and enhanced authentication performance. Fingerprint recognition is one of the most established biometric authentication methods, with strong feature extraction and high recognition accuracy [5]. However, raw fingerprint data, stored as templates in central databases or on IoT/IIoT devices, if left unprotected, can be at risk, because everybody’s fingerprint is unique and permanent. Once a raw fingerprint template is stolen, it is lost forever and cannot be re-issued, replaced or destroyed. Fraudulent use of stolen fingerprint template data and privacy invasion make template protection a crucial task in IoT/IIoT-related applications. Unfortunately, most fingerprint authentication systems currently used in the IoT/IIoT do not have template protection [6], endangering the security of raw fingerprint data. Moreover, traditional biometric authentication faces slow, limited database holding capacity and data transmission problems [1].
To address the above issues, in this paper we propose a secure online fingerprint authentication system for IIoT devices over 5G networks. The proposed system features the design of a cancelable fingerprint template, which protects original fingerprint minutia features and therefore provides privacy and security guarantee. To take advantage of 5G’s high-speed transmission and the cloud’s powerful processing capability, the proposed authentication system carries out online fingerprint matching in the encrypted domain in the cloud server. Compared with state-of-the-art methods, the proposed authentication system shows competitive performance on six public fingerprint databases, while saving computational costs and achieving fast online matching. Figure 1 shows the architecture of the proposed fingerprint authentication system. Note that the proposed system is not confined to 5G networks because the architecture of our system suits both 5G and non-5G networks. It is worth mentioning that the desired features of 5G networks improve the speed of online matching, thus increasing the efficiency of the proposed system.
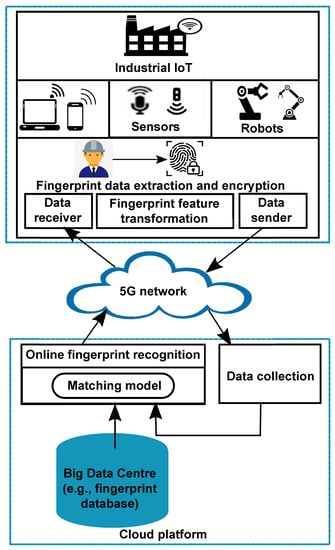
Figure 1.
Architecture of the proposed online fingerprint authentication system.
The contributions of this paper are summarized as follows:
- The proposed online fingerprint authentication system is equipped with template protection. If a stored template is compromised, raw fingerprint data cannot be retrieved and the compromised template can be revoked and replaced with a new one. Thus, data security is heightened in the access control of IIoT devices.
- The proposed authentication system is highly efficient, evidenced by reduced template size, low computational costs and fast online matching, making it suitable for IIoT-related applications.
- Not only does the recognition accuracy of the proposed system with template protection level with the baseline unprotected system, but it also outperforms state-of-the-art fingerprint authentication systems with template protection. The strong performance of the proposed system ensures that critical and/or sensitive data in the IIoT environment are only accessed by genuine (i.e., authorized) users.
The rest of this paper is organised as follows. Section 2 presents the related work of biometric authentication in the IoT and cancelable fingerprint templates. Section 3 details the proposed secure online fingerprint authentication system. The experiment results are reported and discussed in Section 4. The conclusion is given in Section 5.
2. Related Work
2.1. Biometric Authentication in the IoT
Liu et al. [1] proposed an online biometric authentication structure for future 5G communication systems. The authors argued that the security level of the internet can be improved if biological characteristic authentication is applied, such as fingerprint identification. Wilkins [4] reviewed how biometrics can be utilized to better secure manufacturing protocols and processes. The author discussed about the options of choosing correct technologies to improve safety and security in factories. Since hackers continue to find new ways to gain information, the author stated that it is necessary to make systems adaptable, as security is a moving objective. Yang et al. [7] developed a privacy-preserving lightweight fingerprint authentication system for resource-limited IoT devices. The proposed method uses a block logic-based algorithm to minimise the template size and achieve good performance.
Ayub et al. [8] introduced a lightweight secure three-factor biometric-based authentication protocol for e-Healthcare applications in the IoT through the 5G technology. The proposed protocol is cost-effective in terms of computational and communication costs compared to many existing e-Health cloud authentication protocols. Security analyses show that the protocol can resist attacks such as user anonymity, offline password guessing, impersonation and stolen smartcard attacks, but is vulnerable to man-in-the-middle and replay attacks [9].
Sedik et al. [10] used deep learning models, implemented with a dataset of fingerprint images, to detect alterations to biometric modalities and discriminate pristine, adulterated and fake biometrics in 5G-based smart cities. The proposed scheme computes the probability of a biometric which is tampered with. Bedari et al. [11] proposed a two-stage feature transformation-based fingerprint authentication system to protect user privacy in the IoT. The authors designed a weight-based fusion mechanism in the first stage, and a non-invertible transformation in the second stage. With strong performance and energy efficiency, the proposed system is suited to resource-constrained IoT devices.
2.2. Cancelable Fingerprint Templates
Cancelable biometrics is an important biomtric template protection technique. It converts original biometric feature data non-invertibly to a ‘distorted’ version through a one-way transformation. When the stored (transformed) template is compromised, it can be easily revoked and replaced with a new template by changing the user-specific key.
Yang et al. [12] proposed a feature-adaptive random projection-based cancelable fingerprint authentication system. The proposed feature-adaptive random projection can mitigate the negative effect of biometric uncertainty on matching performance. Shahzad et al. [13] designed fingerprint cancelable templates with dual protection to improve security. The dual protection involves the window-shift-XOR model and partial discrete wavelet transform. Bedari et al. [14] developed cancelable fingerprint templates using binary features of the minutia cylinder-code (MCC) [5] based on a dynamic random key model, named Dyno-key model. The Dyno-key model uses randomly generated keys to dynamically select elements from MCC’s binary feature vectors so that uncertainty is added to the generated cancelable template.
Jin et al. [15] proposed cancelable fingerprint templates by transforming real-valued feature vectors [16] into a ranking-based representation using locality sensitive hashing, called index-of-max (IoM) hashing. Later, Kim et al. [17] built on the IoM hashing method in [15] and derived sparse combined index-of-max (SC-IoM) hashing. The SC-IoM method extracts the largest and second largest indices of user-specific randomly projected features and uses a large number of hash functions to obtain satisfactory authentication performance. Abdullahi et al. [18] introduced a cancelable fingerprint hash scheme based on the Fourier-Mellin transform and fractal coding. The proposed method performs well over fingerprint databases of reasonably good image quality, but its performance deteriorates when the quality of fingerprint images is poor.
Li et al. [19] designed Indexing-Min-Max (IMM) hashing-based cancelable fingerprint templates. The proposed method embeds the explicit fixed-length fingerprint feature vector non-linearly into the implicit ordering space. Unlike the original IoM hashing method, the IMM hashing model collects implicit indices of the maximum and minimum values from multiple random tokenized partial Hadamard transforms to enhance security and recognition accuracy simultaneously. Li and Wang [20] proposed a one-factor cancelable fingerprint authentication scheme based on the novel minimum hash signature (NMHS) and secure extended feature vector (SEFV). The NMHS algorithm produces the hash codes of binary fingerprint templates and utilises the XOR operation in the hashing process to improve stability. The SEFV is then used to obtain a pseudo identifier. In the authentication stage, the pseudo identifier is produced with genuine queries using the auxiliary data provided by the system. A fusion rule is introduced to enhance authentication performance.
Li et al. [21] presented a cancelable fingerprint binary code generation scheme based on one permutation hashing. The transformed feature is bit-wise uniformly distributed and offers fast matching. The proposed method also applies the partial Haar transform to strengthen the security of the cancelable fingerprint template. Lee et al. [22] proposed a one-factor cancelable fingerprint template, called extended feature vector (EFV) hashing. The EFV hashing utilizes a permutation key separate from the fingerprint feature data to yield the cancelable template. With XOR encryption, the key is not stored in its original form. Yang et al. [23] designed a linear convolution-based cancelable fingerprint authentication system. The proposed system uses a help vector as the second input to the linear convolution function so as to increase the immunity of resultant templates to errors from the feature data. To protect the help vector, the authors developed a feature-guided index generation method. Despite robust security, the proposed system does not perform well over databases with poor image quality.
A comparison of the above literature is shown in Table 1. It is clear from Table 1 that the existing cancelable fingerprint templates have a limitation on striking a balance between providing strong security and attaining good authentication performance over databases of low image quality. In addition, energy-efficient data storage and low computational costs are critical when designing secure biometric authentication systems for the IoT/IIoT. Hence, more effort is needed in developing lightweight schemes that will reach a balanced trade-off. To this end, in this paper we design a secure online fingerprint authentication system whose core component is a cancelable template for the protection of original fingerprint data. The proposed system not only achieves satisfactory performance over databases with poor-quality images, but it is also efficient with size-reduced templates and fast online matching.

Table 1.
Comparison of state-of-the-art cancelable fingerprint templates.
3. Proposed System
In this section, we propose a secure online fingerprint authentication system for IIoT devices over 5G networks. The core of the proposed system is the design of a cancelable fingerprint template. Figure 2 illustrates the block diagram of the proposed authentication system, which is made up of three steps. The first step is fingerprint feature extraction and representation, where a real-valued, fixed-length feature vector is extracted based on the method in [16]. Since this fixed-length feature vector contains the original minutia information, to protect it, we develop a cancelable fingerprint template in the second step. In the third step, the protected template is transmitted over the 5G network and online fingerprint matching is conducted in the cloud server.
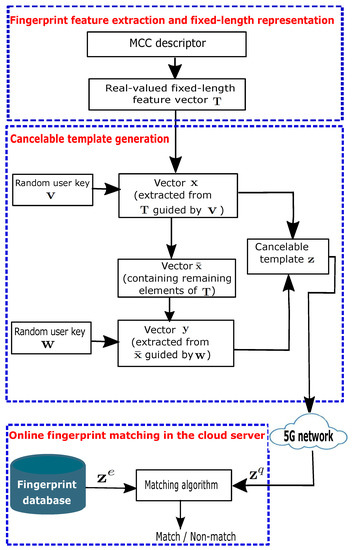
Figure 2.
Block diagram of the proposed authentication system.
3.1. Fingerprint Feature Extraction and Fixed-Length Representation
The well-known fingerprint minutia descriptor, MCC [5] is one of the best performing minutia-based feature extraction methods. The MCC discretizes the neighborhood of each minutia into a three-dimensional cell structure, called cylinder. Each of MCC’s cylinders is represented by a variable-sized binary feature vector. To improve matching speed and the applicability of variable-sized representations in biocryptography-related applications, Jin et al. [16] refined the MCC and proposed fixed-length feature representations. Through kernel learning and point-to-string conversion [16], a real-valued, fixed-length feature vector is derived from MCC’s variable-sized binary features. Let us denote the fixed-length real vector by , expressed as
The derivation of in (1) is detailed in [16]. Vector is real-valued with length m, serving as the input to the proposed cancelable template generation algorithm in the next section.
3.2. Cancelable Template Generation
The fixed-length real vector is unprotected. As it contains the original fingerprint minutia features, there would be serious security and privacy issues (e.g., privacy invasion), if is compromised. That is why we design a cancelable fingerprint template to protect vector .
First, we generate two random vectors and , both of length n, written as
where , and all entries of and are strictly positive integers with and , for all and all . Random vectors and serve as index vectors.
Next, we use to extract elements from vector in (1) whose indices are of the same values as entries in . This forms a new vector of length n, i.e.,
The remaining elements of the vector are put in a vector, called , whose length is . The vector can be expressed as
Then, similar to the handling of vector , we use the index vector in (3) to extract n elements from vector in (5) whose indices coincide with entries of . Thus, we obtain a new vector of length n. That is,
Finally, we find the element-wise average of vectors and . Hence, we have
The real vector is the resultant cancelable template.
The above process transforms the fixed-length real vector in (1) to the vector in (7). This transformation is non-invertible, because it realizes a many-to-one mapping. From the vector , it is highly unlikely to recover the elements of vectors and (see the detailed analysis in Section 4.5). Random vectors and are the parameter keys in the proposed method. This means that different and result in different transformed templates , thus making revocable.
The transformed template provides strong protection to the original MCC features contained in the fixed-length real vector . This protection can be justified in two aspects. First, vector cannot be retrieved even if the transformed template and user-specific keys and are all compromised (see security analysis in Section 4.5). Second, if the transformed template is compromised, a new template can be issued simply by changing the user keys and . The new template is unrelated to the compromised template and can be generated differently from one application to another (see unlinkability analysis in Section 4.4).
The proposed cancelable template design is efficient in that its implementation does not involve any complex computations or time-consuming iterations. The user key generation and cancelable template design can be performed efficiently on IIoT devices.
The size of the transformed template is less than half of the length of the original feature vector . This is because the length of is n and with m being the length of . Therefore, the proposed authentication system attains substantial savings in memory storage, while achieving high recognition accuracy (see the experiment results and analysis in Section 4). Such savings are beneficial to IIoT devices and also reduce matching time (see Analysis of Computational Costs in Section 4.2).
3.3. Online Fingerprint Matching in the Cloud Server
There are usually two stages in biometric authentication—the enrollment stage and the verification stage, which are applicable to online fingerprint authentication in the IIoT. Specifically, in the enrollment stage, the transformed template , where the superscript e denotes ‘enrolled’, is generated by following the process in Section 3.2. The transformed template is stored in a fingerprint database in the cloud’s big data centre. In the verification stage, a user (i.e., the query) intending to access an IIoT device goes through the same procedure in Section 3.2 to generate the query’s (transformed) template , where the superscript q denotes ‘query’. Since is the transformed template of the query, it is protected and should be secure when transmitted through a 5G network to the cloud server, where fingerprint matching is conducted. Thus, to make use of 5G networks’ super-fast transmission and the cloud server’s powerful processing ability, we match the enrolled and query templates online in the cloud server. Note that both the enrolled and query templates are transformed versions of the raw templates. In other words, fingerprint matching is conducted in the transformed or encrypted domain, so no disclosure of raw fingerprint data would occur in the matching process. Moreover, since only the transformed templates rather than the original are transmitted via the 5G network, there should be no security concern about leaking or revealing original fingerprint features.
The similarity score between the (transformed) enrolled and query templates is calculated as
where is the norm of vectors. The above equation is adapted from Equation (32) in [16].
The similarity score ranges from 0 to 1 with 0 meaning that there is no similarity between the enrolled template and the query, and 1 meaning that the query is completely similar to the enrolled template. The higher the score , the more similar the query is to the enrolled template. Therefore, the user is given access to the IIoT device or application only if the similarity score is higher than a predefined threshold.
4. Experiment Results and Analysis
To evaluate the proposed authentication system, we conduct extensive experiments over six public fingerprint databases—FVC2002 DB1-DB3 [24] and FVC2004 DB1-DB3 [25]. Each database consists of 800 fingerprint images with varying qualities, and these fingerprint images were collected from 100 users with 8 impressions per user. In accordance with the requirements of cancelable biometrics, the designed authentication system is evaluated on whether it satisfies performance preservation after transformation, revocability and diversity, unlinkability and non-invertibility.
The commercial fingerprint recognition software VeriFinger SDK [26] is employed to extract minutiae from fingerprint images in the aforementioned databases. The performance of the proposed authentication system is evaluated based on three performance indices—False Acceptance Rate (FAR), False Rejection Rate (FRR) and Equal Error Rate (EER). The FAR represents the probability of mistaking two fingerprints from different entities to be from the same entity, while the FRR means the probability of mistaking two fingerprints from the same entity to be from different entities. The relationship between the Genuine Acceptance Rate (GAR) and the FRR is . The EER is the error rate when the FAR is equal to the FRR.
The performance indices described above are obtained from genuine testing and imposter testing. Genuine testing is conducted by matching two impressions from the same finger, whereas imposter testing is performed by matching two impressions from different fingers. For each database, according to the method in [16], the first to third impressions of each finger are used as the training samples to generate the real-valued, fixed-length feature vector in (1), and the remaining impressions (i.e., fourth to eighth) of each finger are used for testing purposes. In our experiments, vector in (1) acts as the input to the proposed cancelable generation algorithm. The original FVC protocol [27] is adopted in our experiments.
4.1. Performance Evaluation
The performance of the proposed scheme is evaluated under the worse-case scenario, where the user-specific key is lost. We simulated this worst case (i.e., the lost-key scenario) by assigning all the users in a database the same key, namely the same random vector in (2) and the same random vector in (3).
First, we plot the receiver operating characteristic (ROC) curves in Figure 3 for all the six databases in the lost-key scenario, with the key length of and set to . The MCC-based real-valued, fixed-length feature vector in (1) is of length , so is the maximum allowed length to satisfy . We observe from Figure 3 that among the six databases, the proposed authentication system shows the best performance over database FVC2002 DB1 and the worst performance over database FVC2004 DB2. Such performance is attributed to the high quality of fingerprint images in FVC2002 DB1 and the poor quality of fingerprint images in FVC2004 DB2.
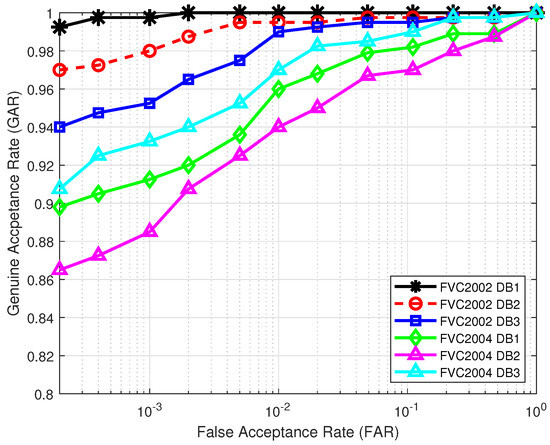
Figure 3.
ROC curves in the lost-key scenario under the original FVC protocol.
Next, we evaluate how the key length affects the performance of the proposed authentication system. In our cancelable template design, there are two randomly generated user-specific keys and , both of length n. User key is responsible for extracting elements from the original MCC-based real-valued, fixed-length feature vector so as to form the vector in (4). User key is in charge of extracting elements from vector in (5) to produce vector in (6). To assess the impact of key length n on the performance of the proposed system, we vary the value of n from large to small. Table 2 illustrates the effect of different key lengths on the matching performance in comparison with the baseline, that is, the unprotected real-valued MCC-based features with fixed-length . It can be seen from Table 2 that for all the databases, EER worsens when the key length n decreases. This is because a small value of n makes the original MCC-based feature vector contribute less to the resultant cancelable template than a large value of n. Figure 4 shows the ROC over database FVC2002 DB2 for different key lengths.

Table 2.
EER (%) of the proposed system when the key length varies.
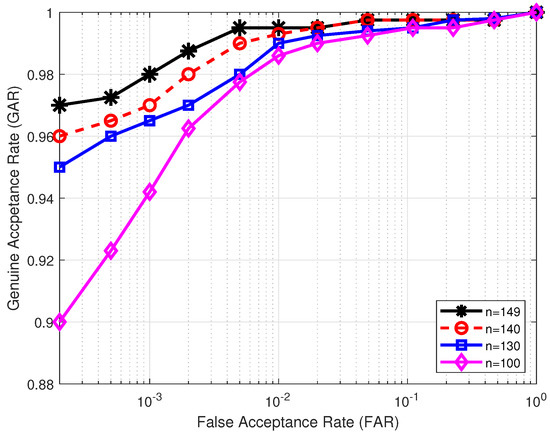
Figure 4.
ROC curves for different key lengths evaluated over database FVC2002 DB2 in the lost-key scenario under the original FVC protocol.
Then, we compare the performance of the proposed authentication system for key length with that of the state-of-the-art cancelable fingerprint templates. This performance comparison is reported in Table 3. It is clear from Table 3 that the proposed system exhibits competitive performance over all six databases, and in particular demonstrates superior performance over databases FVC2002 DB1-DB3 and FVC2004 DB2 and DB3. The strong performance of the proposed method is attributed to our cancelable template design (see Section 3.2), which, by and large, maintains the good performance of the baseline (i.e., the unprotected fixed-length real-valued MCC-based features), as shown in Table 2 when , but our method also plays the role of template protection.

Table 3.
EER (%) comparison between the proposed system and the state-of-the-art cancelable fingerprint templates in the lost-key scenario under the original FVC protocol.
4.2. Analysis of Computational Cost and Template Size
In this section, we investigate the computational cost and template size of the proposed authentication system. Table 4 lists the average time of generating the cancelable template as well as the average matching time using the designed cancelable template and the original MCC-based real-valued, fixed-length feature vector . We can see from Table 4 that the average matching time using the designed cancelable template is much less than that using the original MCC-based feature vector (i.e., the baseline). The savings in matching time come from the reduced template size, because the proposed system shortens the length of the cancelable template by at least 50%, as . Furthermore, Table 5 compares the average time of cancelable template generation of the proposed system with that of the state-of-the-art cancelable template methods. Clearly, the processing speed of the proposed system over all six databases is the fastest among all the methods in Table 5. The results in Table 4 and Table 5 are obtained by running MATLAB 2021a on a computer with a 3.41 GHz Intel (R) Core (TM) i7-6700 CPU.

Table 4.
Average time ( s) for cancelable template generation and fingerprint matching.

Table 5.
Comparison of the cancelable template generation time (in second) between the proposed system and the state-of-the-art cancelable fingerprint templates.
Table 6 reports the template size of the proposed system in comparison with the state-of-the-art cancelable template methods. Clearly, the proposed system has the smallest template size among all the methods in Table 6.

Table 6.
Comparison of the template size (bits) between the proposed system and the state-of-the-art cancelable fingerprint templates. Symbol K represents the number of minutiae in a fingerprint image.
4.3. Revocability and Diversity
In this section, we evaluate the revocability and diversity of the proposed authentication system. Revocability and diversity are considered important properties of cancelable biometrics, which require that if a stored template is compromised, it can be replaced with a new template by altering the user-specific key. The new template and the compromised template should be completely unrelated. To examine the revocability and diversity of the proposed system, we produced 100 transformed templates from the first impression of each finger in database FVC2002 DB2 by randomly generating different user keys and . These pseudo-imposter templates were matched with the original ones. The genuine, pseudo-imposter and imposter distributions are plotted in Figure 5, which shows that the pseudo-imposter and imposter distributions largely overlap. Their mean and standard derivation are very close to each other, given by the mean 0.3902 (pseudo-imposter) and 0.3913 (imposter), and standard derivation 0.055 (pseudo-imposter) and 0.053 (imposter).
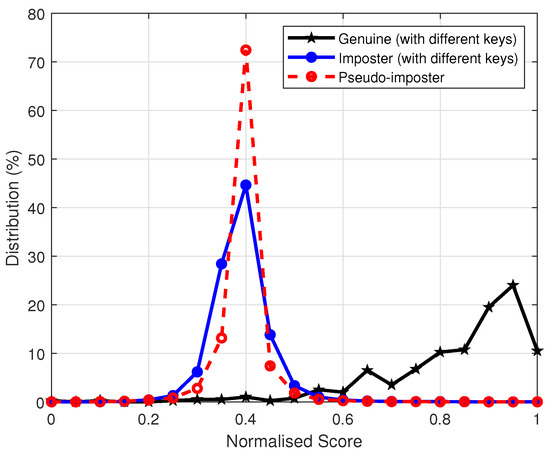
Figure 5.
Genuine, Pseudo-imposter and imposter distributions over FVC2002 DB2.
4.4. Unlinkability
Unlinkability is another essential property of cancelable biometrics. It guarantees the privacy of biometric data and prevents cross-matching when users are registered in different applications using the same biometrics. Based on the framework presented in [28], we assess the unlinkability of the proposed authentication system by determining mated and non-mated sample score distributions at both local and global levels. Mated sample scores are obtained by comparing templates produced from the same impression of a finger using different keys, while non-mated scores are computed by comparing templates generated from different fingers using different keys.
Two unlinkability measures, score-wise linkability and system overall linkability , are defined in [28]. The score-wise linkability determines the amount of linkability of protected templates for each matching score s of mated and non-mated sample score distributions. Thus, for a specific score s, means that two templates are fully unlinakble, while means that two templates are fully linkable. The intermediate values between 0 and 1 indicate the degree of linkability at specific matching scores. On the other hand, the system’s overall linkability estimates the linkability of the entire template protection system, independent of matching scores. When (or ), the template protection system is fully unlinkable (or fully linkable).
To access the unlinkability of the proposed authentication system, we produced 100 transformed templates of the first impression of each finger in database FVC2002 DB2 with random user keys and . We obtained the mated scores by comparing each transformed template with the 100 newly produced templates using different keys, giving 10,000 mated scores. We got the non-mated scores by comparing the transformed template of each finger with all other different fingers, yielding 4950 non-mated scores. Figure 6 shows the mated and non-mated sample score distributions—they mostly overlap. As , the proposed authentication system is almost fully unlinkable.
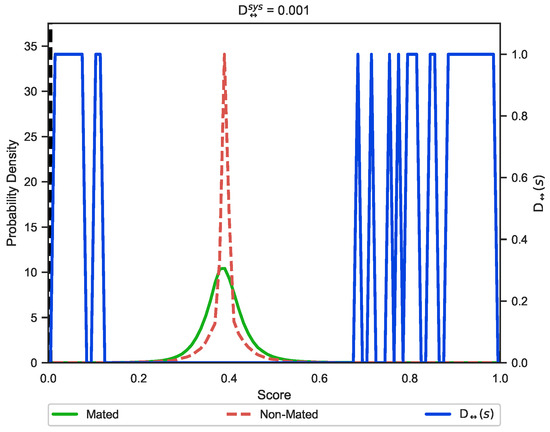
Figure 6.
Unlinkability analysis of the proposed authentication system using mated and non-mated score distributions.
4.5. Security Analysis
In this section, we conduct the security analysis of the proposed authentication system. We first analyze non-invertibility of the proposed method and then examine whether revoked template attacks and masquerade attacks can be defied.
4.5.1. Non-Invertibility Analysis
In the context of cancelable biometrics, non-invertibility refers to the computational infeasibility of retrieving original biometric features from a compromised cancelable template. It is important for secure biometric authentication systems to possess non-invertibility as this property ensures the security of raw biometric data.
We analyze the non-invertibility of the proposed system in the worst-case scenario, where an adversary manages to acquire all possible information, namely the transformed template and user keys and . Since and are only index vectors, even though they are compromised, the adversary is unable to know the specific values of the elements in vectors and whose indices match entries in and , respectively. Moreover, the proposed transformation constitutes a many-to-one mapping, as it follows from (7) that there exist infinitely many possible vectors and that can render the same . Thus, it is computationally infeasible to restore and from the transformed template and index vectors and .
4.5.2. Revoked Template Attacks
We evaluate if the proposed authentication system can defend attacks when an adversary uses a revoked template. We consider the following two attack scenarios [29]:
- Type-I Attack: A revoked template is employed to attack a system containing a renewed template produced from the same impression.
- Type-II Attack: A revoked template is employed to attack a system containing a renewed template produced from another impression of the same finger.
Two different levels of security are assessed in each attack scenario [29] over database FVC2002 DB2:
- Medium security: the matching threshold is set to 0.1% FAR.
- High security: the matching threshold is set to 0% FAR.
A total of 500 (=) Type-I attacks and 1000 (=) Type-II attacks were launched. Table 7 reports the percentage of successful attacks at medium and high security levels. It can be seen from Table 7 that the proposed authentication system can combat revoked template attacks.

Table 7.
Percentage of successful revoked template attacks at medium and high security levels.
4.5.3. Masquerade Attacks
Masquerade attacks are similarity-based attacks where an adversary fakes a synthetic input that is very similar to the actual template. We simulated the masquerade attack by fabricating real-valued input vectors which resemble the original MCC-based feature vector . The faked input of length 299 was generated by randomly choosing a small portion of elements (e.g., 10 out of 299 elements) from the original feature vector and replacing them with values close to the original ones. Hence, the fake input shares a large degree of similarity with .
We evaluate whether the proposed authentication system can tackle masquerade attacks in Type-I and Type-II attack scenarios at medium and high security levels using database FVC2002 DB2. The percentage of successful masquerade attacks is given in Table 8, where it is shown that the proposed system is able to defend masquerade attacks.

Table 8.
Percentage of successful masquerade attacks at medium and high security levels.
5. Conclusions and Future Work
In this paper, we proposed a secure online fingerprint authentication system. Designed to take advantage of the desired features of 5G networks, the proposed authentication system can be applied to protecting data security in the IIoT. The proposed authentication system has the functionality of template protection, empowered by the designed cancelable fingerprint template, which provides strong security to user privacy and critical data. The transformed (protected) template is transmitted over the 5G network so that fast online matching is conducted in the cloud server. Moreover, the proposed system has a size-reduced template compared to the baseline, unprotected system, thus saving computational costs and benefiting IIoT devices. In addition, the extensive experiment results on six public fingerprint databases show the favorable performance of the proposed authentication system, manifested by the low EER, when compared with state-of-the-art cancelable fingerprint templates.
As for future work, since the quality of minutia-based local features plays an important role in authentication performance, we will continue to develop discriminative and robust feature representations. In addition, we will put more effort into the design of secure and lightweight biometric authentication systems that suit the IoT/IIoT environment.
Author Contributions
Conceptualization, A.B., S.W. and W.Y.; methodology, A.B. and S.W.; software, A.B.; writing—original draft preparation, A.B.; writing—review and editing, S.W. and W.Y.; supervision, S.W. and W.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Liu, X.; Wang, P.; Lan, Z.; Shao, B. Biological characteristic online identification technique over 5G network. IEEE Wirel. Commun. 2015, 22, 84–90. [Google Scholar] [CrossRef]
- Natesha, B.V.; Guddeti, R.M.R. Fog-Based Intelligent Machine Malfunction Monitoring System for Industry 4.0. IEEE Trans. Ind. Inform. 2021, 17, 7923–7932. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Dai, Y.; Maharjan, S.; Zhang, Y. Blockchain and Federated Learning for Privacy-Preserved Data Sharing in Industrial IoT. IEEE Trans. Ind. Inform. 2020, 16, 4177–4186. [Google Scholar] [CrossRef]
- Wilkins, J. Can biometrics secure manufacturing? Biom. Technol. Today 2019, 2019, 9–11. [Google Scholar] [CrossRef]
- Cappelli, R.; Ferrara, M.; Maltoni, D. Minutia Cylinder-Code: A New Representation and Matching Technique for Fingerprint Recognition. IEEE Trans. Pattern Anal. Mach. Intell. 2010, 32, 2128–2141. [Google Scholar] [CrossRef] [PubMed]
- Yang, W.; Wang, S.; Sahri, N.M.; Karie, N.M.; Ahmed, M.; Valli, C. Biometrics for Internet-of-Things Security: A Review. Sensors 2021, 21, 6163. [Google Scholar] [CrossRef] [PubMed]
- Yang, W.; Wang, S.; Zheng, G.; Yang, J.; Valli, C. A Privacy-Preserving Lightweight Biometric System for Internet of Things Security. IEEE Commun. Mag. 2019, 57, 84–89. [Google Scholar] [CrossRef]
- Minahil; Ayub, M.F.; Mahmood, K.; Kumari, S.; Sangaiah, A.K. Lightweight authentication protocol for e-health clouds in IoT-based applications through 5G technology. Digit. Commun. Netw. 2021, 7, 235–244. [Google Scholar] [CrossRef]
- Tanveer, M.; Khan, A.U.; Shah, H.; Chaudhry, S.A.; Naushad, A. PASKE-IoD: Privacy-Protecting Authenticated Key Establishment for Internet of Drones. IEEE Access 2021, 9, 145683–145698. [Google Scholar] [CrossRef]
- Sedik, A.; Tawalbeh, L.; Hammad, M.; El-Latif, A.A.A.; El-Banby, G.M.; Khalaf, A.A.M.; El-Samie, F.E.A.; Iliyasu, A.M. Deep Learning Modalities for Biometric Alteration Detection in 5G Networks-Based Secure Smart Cities. IEEE Access 2021, 9, 94780–94788. [Google Scholar] [CrossRef]
- Bedari, A.; Wang, S.; Yang, J. A Two-Stage Feature Transformation-Based Fingerprint Authentication System for Privacy Protection in IoT. IEEE Trans. Ind. Inform. 2022, 18, 2745–2752. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Shahzad, M.; Zhou, W. A cancelable biometric authentication system based on feature-adaptive random projection. J. Inf. Secur. Appl. 2021, 58, 102704. [Google Scholar] [CrossRef]
- Shahzad, M.; Wang, S.; Deng, G.; Yang, W. Alignment-free cancelable fingerprint templates with dual protection. Pattern Recognit. 2021, 111, 107735. [Google Scholar] [CrossRef]
- Bedari, A.; Wang, S.; Yang, W. Design of Cancelable MCC-Based Fingerprint Templates Using Dyno-Key Model. Pattern Recognit. 2021, 119, 108074. [Google Scholar] [CrossRef]
- Jin, Z.; Hwang, J.Y.; Lai, Y.L.; Kim, S.; Teoh, A.B.J. Ranking-Based Locality Sensitive Hashing-Enabled Cancelable Biometrics: Index-of-Max Hashing. IEEE Trans. Inf. Forensics Secur. 2018, 13, 393–407. [Google Scholar] [CrossRef]
- Jin, Z.; Lim, M.H.; Teoh, A.B.J.; Goi, B.M.; Tay, Y.H. Generating Fixed-Length Representation From Minutiae Using Kernel Methods for Fingerprint Authentication. IEEE Trans. Syst. Man Cybern. Syst. 2016, 46, 1415–1428. [Google Scholar] [CrossRef]
- Kim, J.; Jin Teoh, A.B. Sparse Combined Index-of-Max Hashing for Fingerprint Template Protection. In Proceedings of the 2019 12th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI), Suzhou, China, 19–21 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Abdullahi, S.M.; Wang, H.; Li, T. Fractal Coding-Based Robust and Alignment-Free Fingerprint Image Hashing. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2587–2601. [Google Scholar] [CrossRef]
- Li, Y.; Pang, L.; Zhao, H.; Cao, Z.; Liu, E.; Tian, J. Indexing-Min–Max Hashing: Relaxing the Security–Performance Tradeoff for Cancelable Fingerprint Templates. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 6314–6325. [Google Scholar] [CrossRef]
- Li, H.; Wang, X. One factor cancellable fingerprint scheme based on novel minimum hash signature and secure extended feature vector. Multimed. Tools Appl. 2022, 81, 13087–13113. [Google Scholar] [CrossRef]
- Li, Y.; Zhao, H.; Cao, Z.; Liu, E.; Pang, L. Compact and Cancelable Fingerprint Binary Codes Generation via One Permutation Hashing. IEEE Signal Process. Lett. 2021, 28, 738–742. [Google Scholar] [CrossRef]
- Lee, M.J.; Jin, Z.; Teoh, A.B.J. One-factor Cancellable Scheme for Fingerprint Template Protection: Extended Feature Vector (EFV) Hashing. In Proceedings of the 2018 IEEE International Workshop on Information Forensics and Security (WIFS), Hong Kong, China, 11–13 December 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Kang, J.J.; Johnstone, M.N.; Bedari, A. A linear convolution-based cancelable fingerprint biometric authentication system. Comput. Secur. 2022, 114, 102583. [Google Scholar] [CrossRef]
- Fingerprint Verification Competition. 2002. Available online: http://bias.csr.unibo.it/fvc2002/ (accessed on 19 August 2022).
- Fingerprint Verification Competition. 2004. Available online: http://bias.csr.unibo.it/fvc2004/ (accessed on 19 August 2022).
- Neurotechnology, VeriFinger SDK. Available online: http://www.neurotechnology.com/megamatcher.html (accessed on 19 August 2022).
- Ferrara, M.; Maltoni, D.; Cappelli, R. Noninvertible Minutia Cylinder-Code Representation. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1727–1737. [Google Scholar] [CrossRef]
- Gomez-Barrero, M.; Galbally, J.; Rathgeb, C.; Busch, C. General Framework to Evaluate Unlinkability in Biometric Template Protection Systems. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1406–1420. [Google Scholar] [CrossRef]
- Ferrara, M.; Maltoni, D.; Cappelli, R. A two-factor protection scheme for MCC fingerprint templates. In Proceedings of the 2014 International Conference of the Biometrics Special Interest Group (BIOSIG), Darmstadt, Germany, 10–12 September 2014; pp. 1–8. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).