Lightweight Anonymous Authentication and Key Agreement Protocol Based on CoAP of Internet of Things
Abstract
:1. Introduction
- We propose an anonymous mutual authentication key agreement protocol, which can satisfy the network architecture of CoAP and provide a robust security guarantee.
- We improve the Dolev–Yao Adversary model, and CPN Tools is used to describe and analyze it thoroughly.
- We demonstrate a security protocol modeling and security verification method based on CPN Tools.
- A comprehensive formal and non-formal analysis of the proposed protocol security is carried out.
2. Related Works
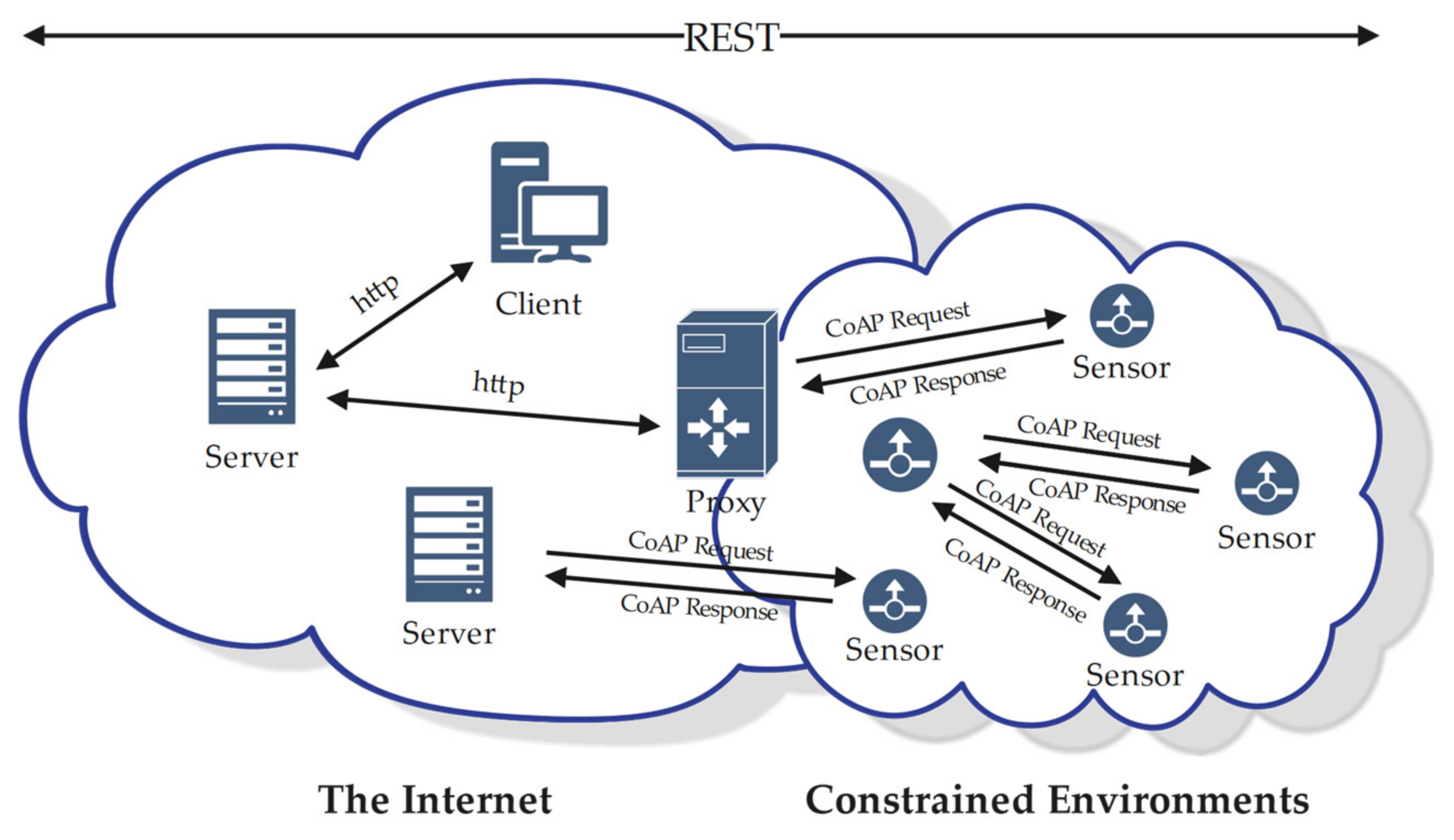
2.1. Secure Key Exchange Schemes for CoAP and IoT
2.2. Applicability of Existing CoAP Secure Key Exchange Schemes
2.3. Formal Analysis Tools for Security Protocols
3. Proposed Scheme
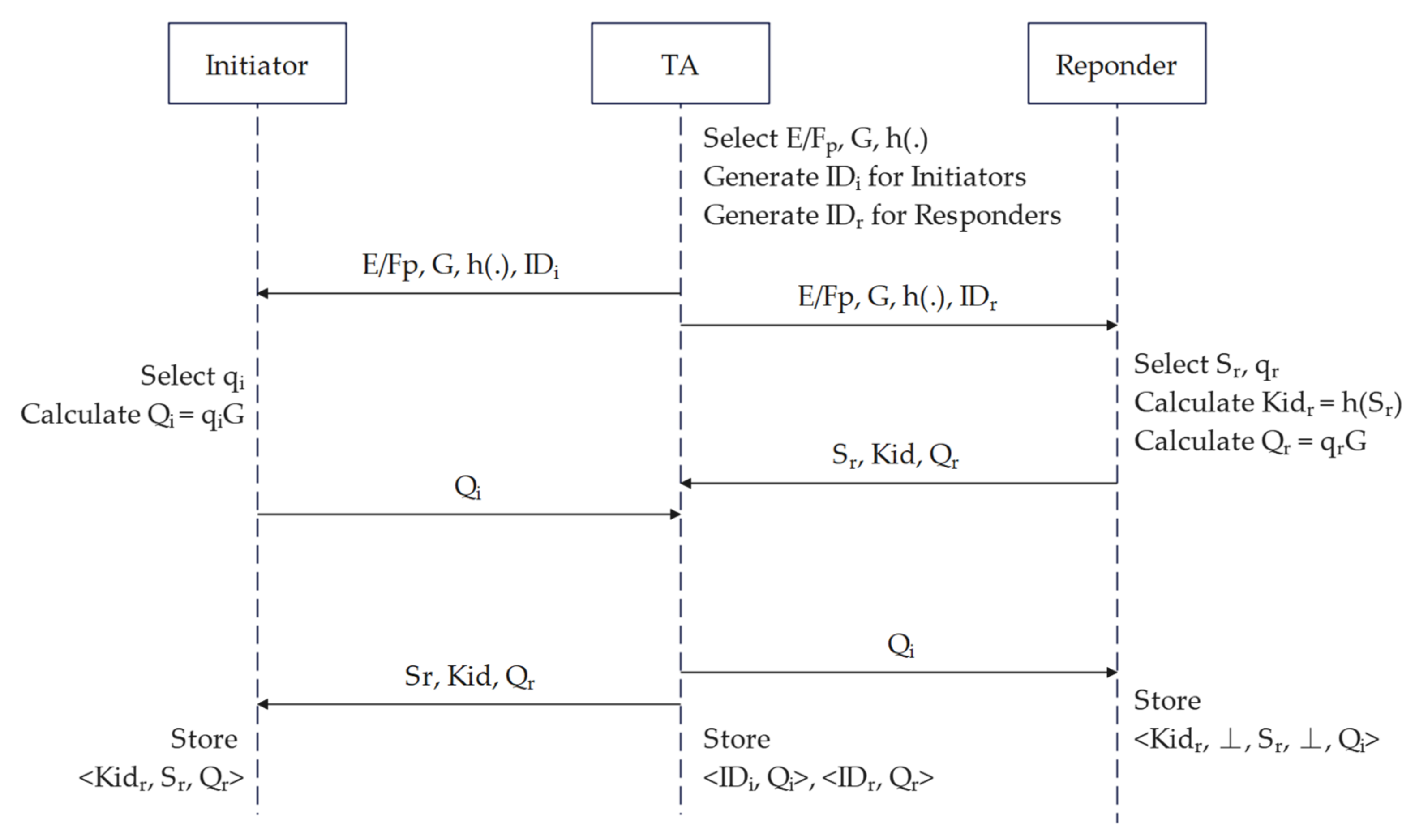
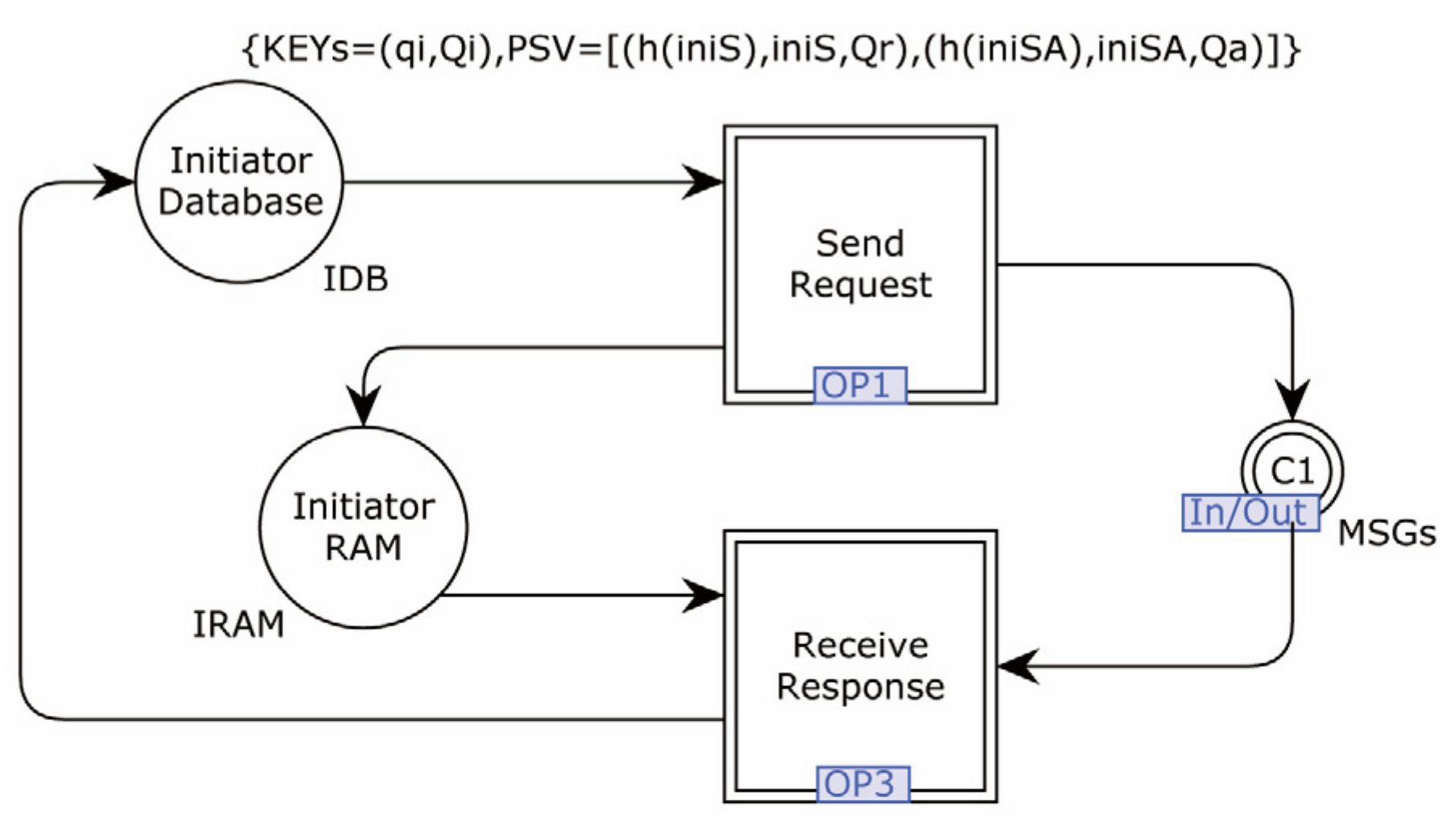
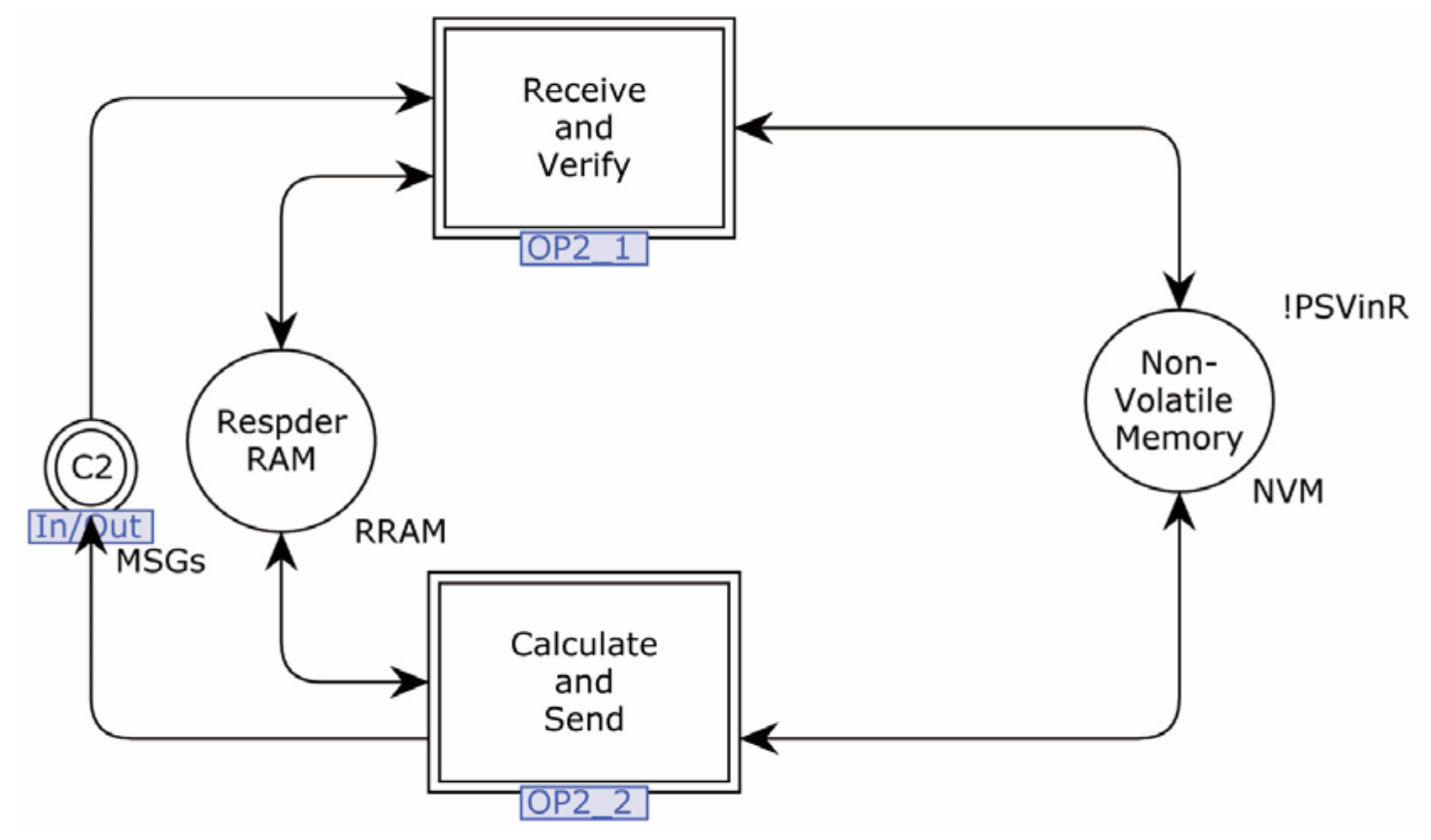
3.1. Initialization and Registration
3.2. Identity Authentication and Key Agreement
- Step 0: Responders power on
- Step 1: Initiator → Responder:
- Step 2: Responder → Initiator:
- Step 3: Initiator confirmation
3.3. Subsequent Instructions
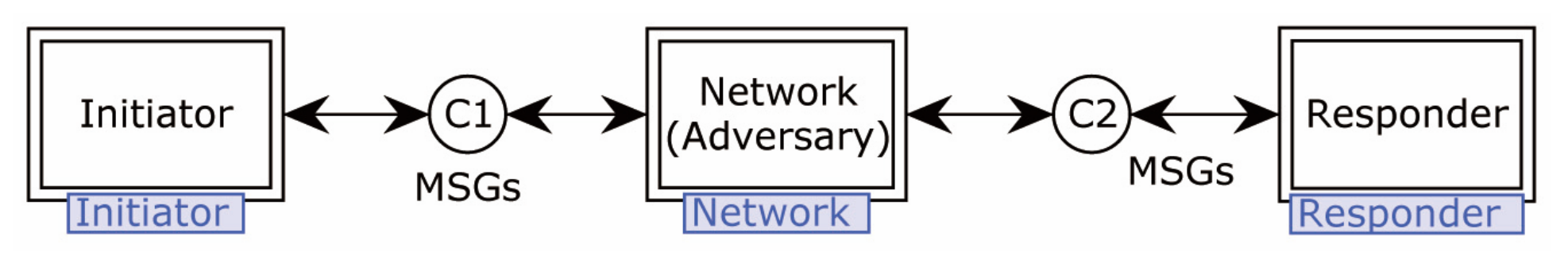
4. Formal Modeling and Security Verification
4.1. Adversary Model
- The Adversary can eavesdrop, block, and intercept any message on the network.
- The Adversary can send and re-send messages.
- The Adversary can combine and decompose messages.
- The Adversary is familiar with encryption, decryption, hash, and other cryptographic operations. They can perform any encryption operations specified in the protocol, and decrypt encrypted messages when the decryption key is known.
- The Adversary is a legitimate member of the system. They have been registered with the system and possess all legitimate security parameters.
- eDY1: When verifying the defense against attacks, such as leaking temporary session information, the Adversary can obtain temporary random numbers to generate session keys.
- eDY2: When verifying characteristics such as perfect forward secrecy, an Adversary can obtain another entity’s current session key or the long-term key.
- eDY3: When verifying an attack caused by disclosing a pre-shared secret, an Adversary can obtain the value of a pre-shared secret between other entities.
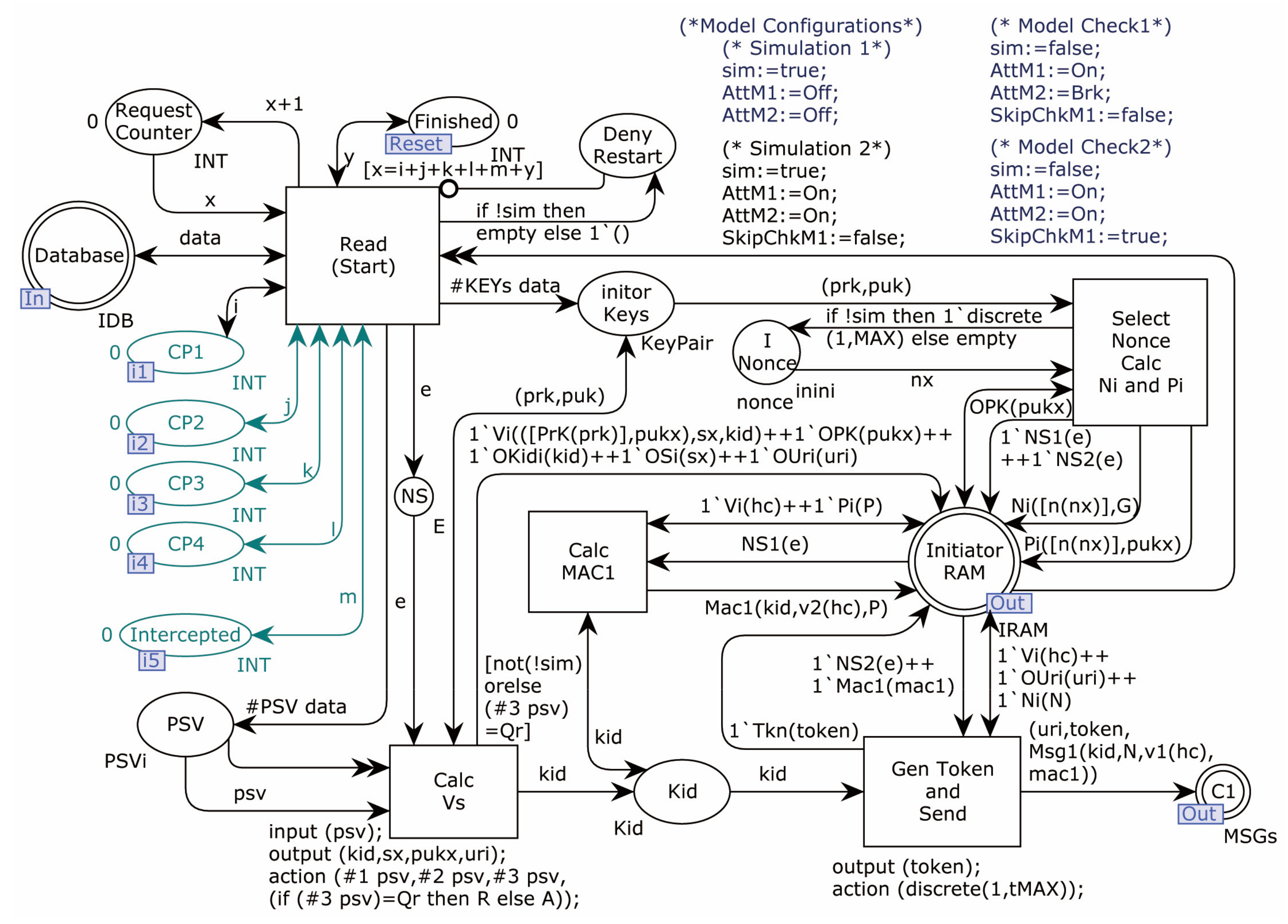
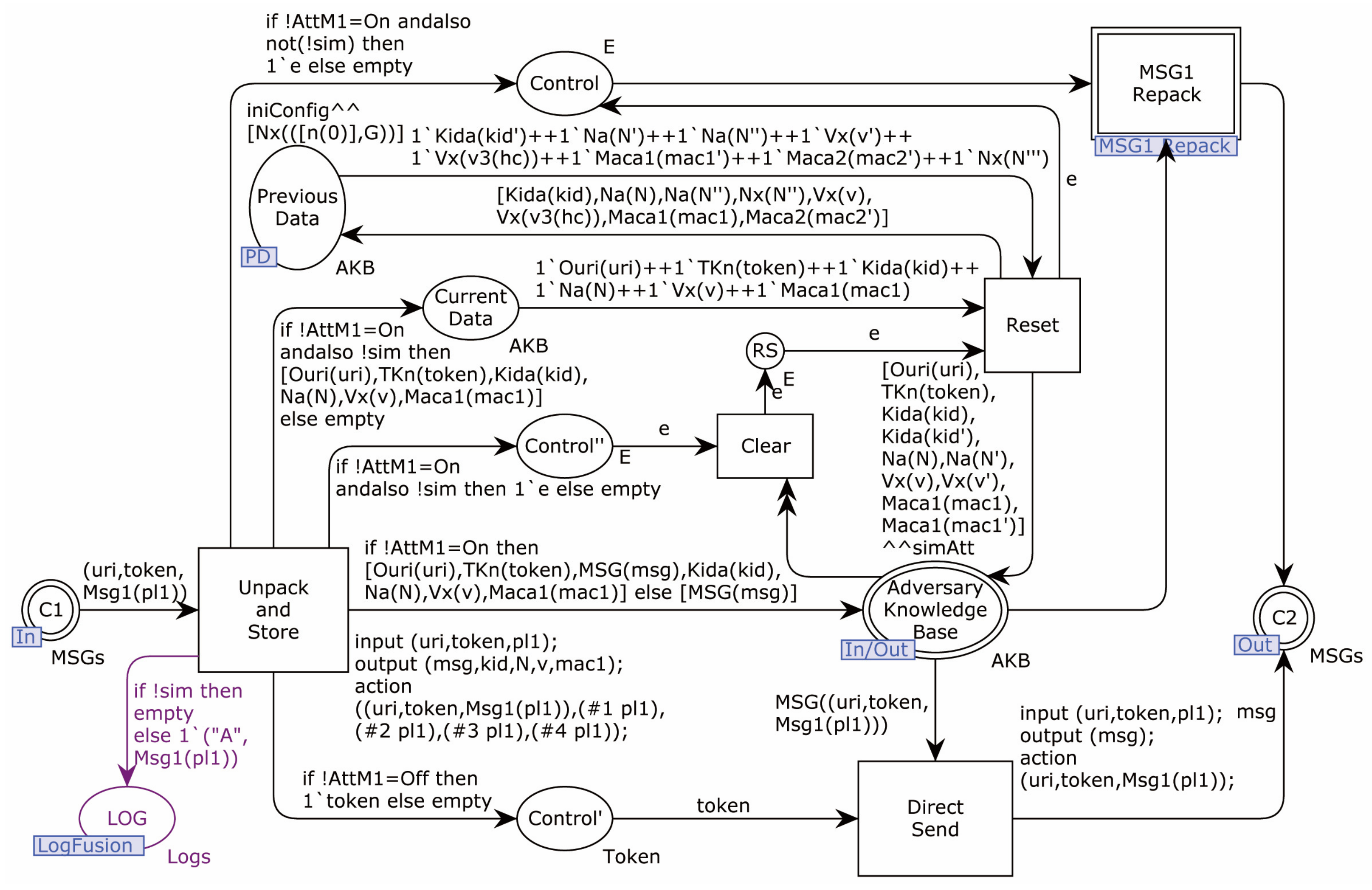
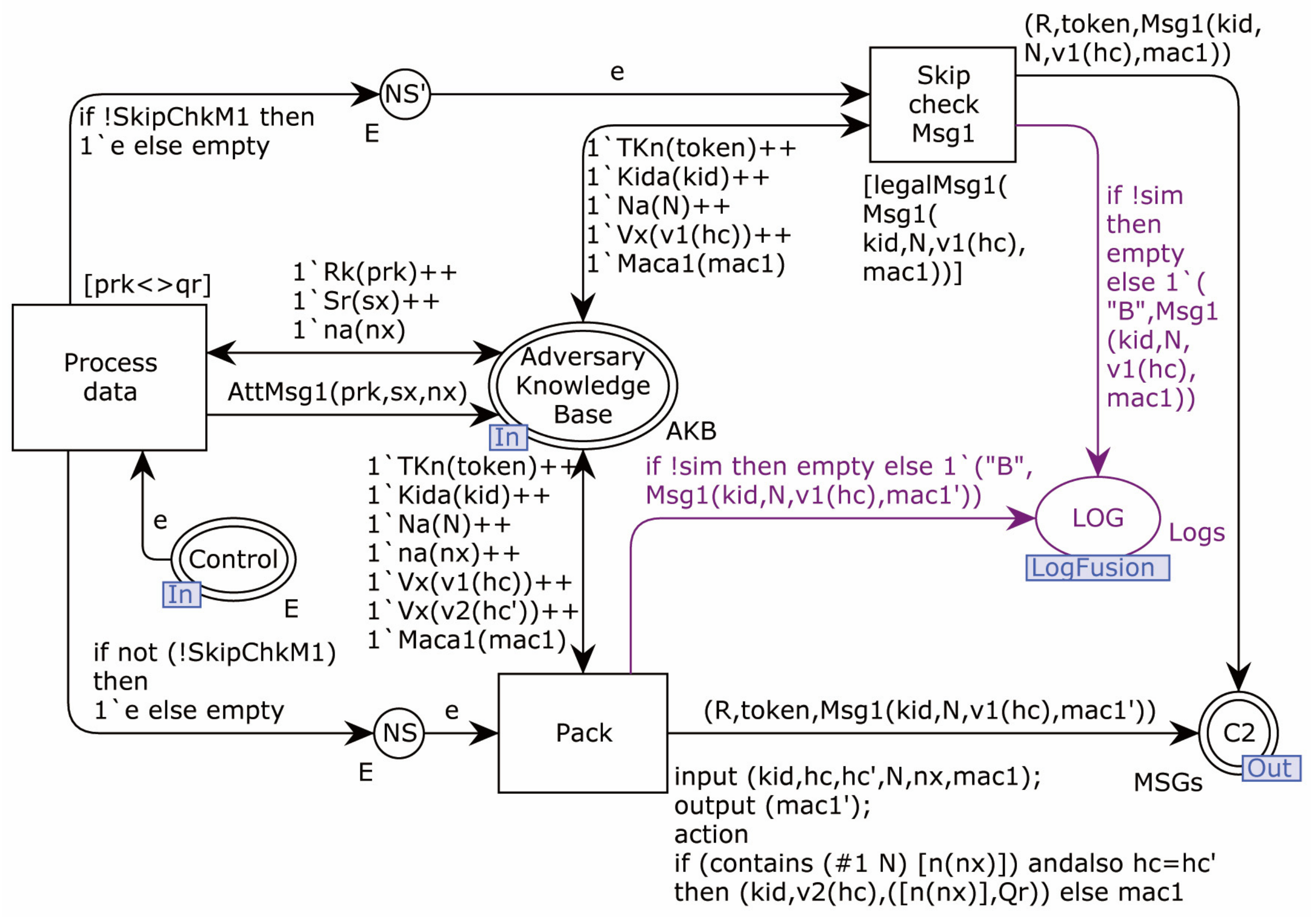
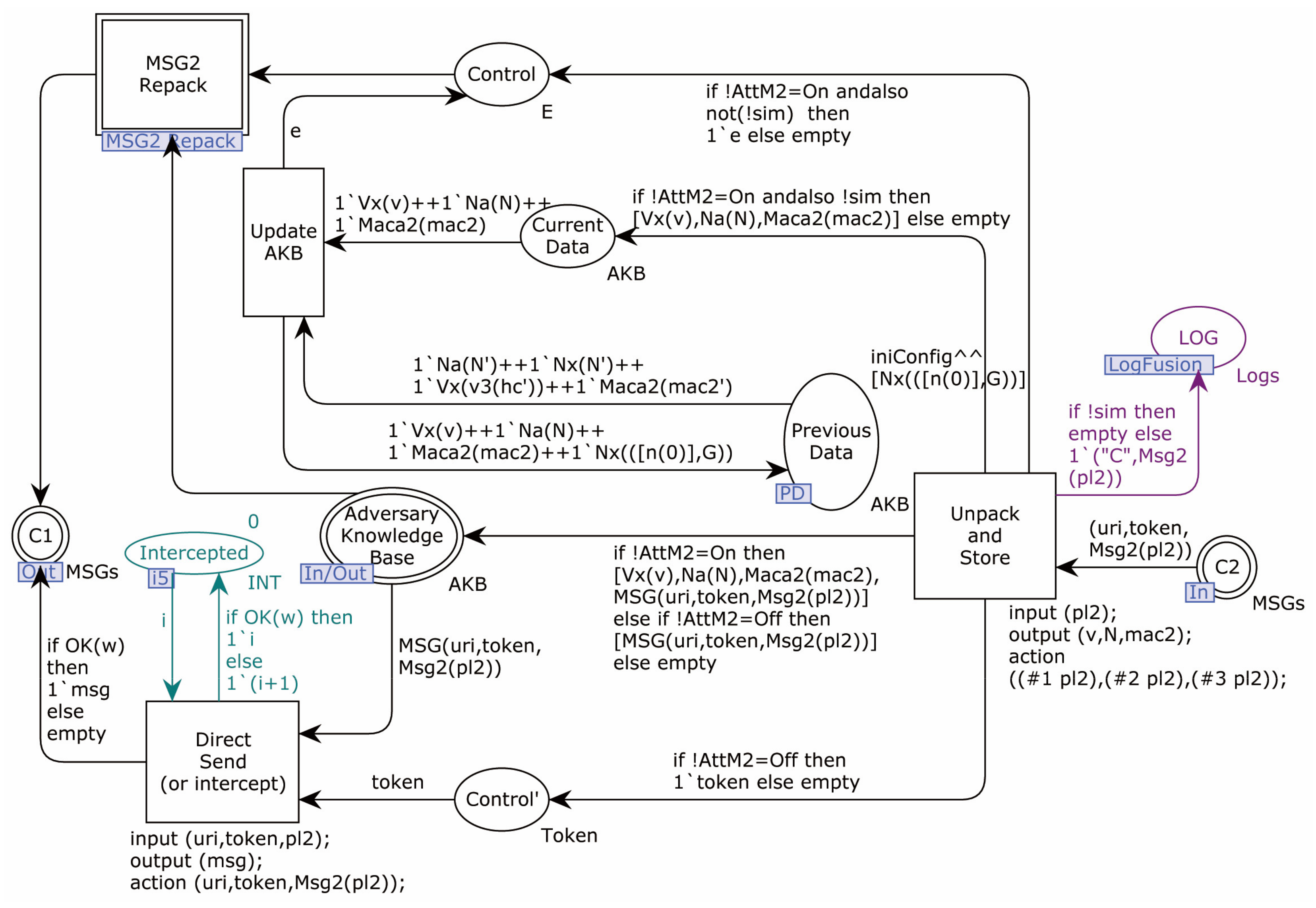
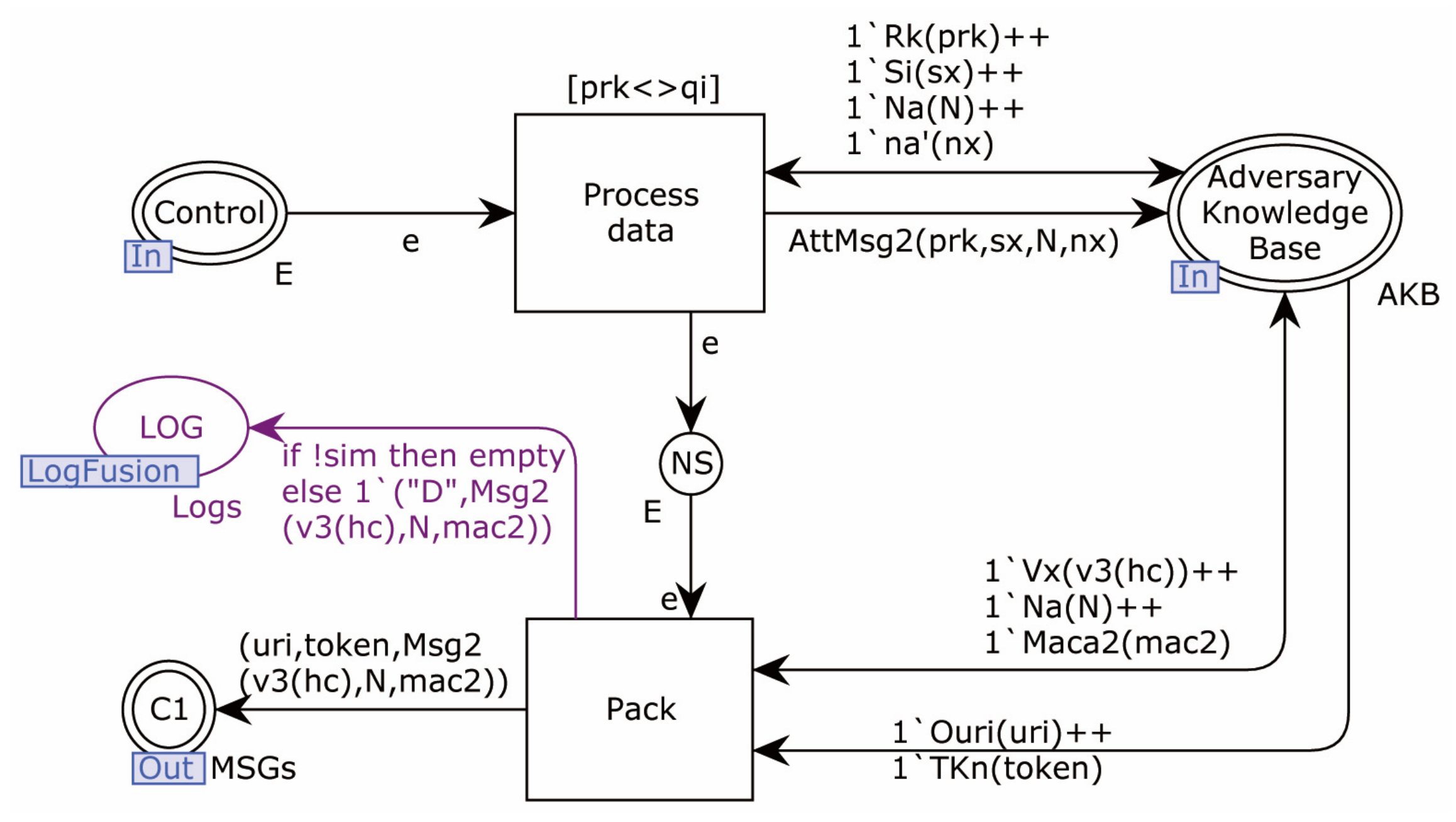
4.2. Formal Modeling
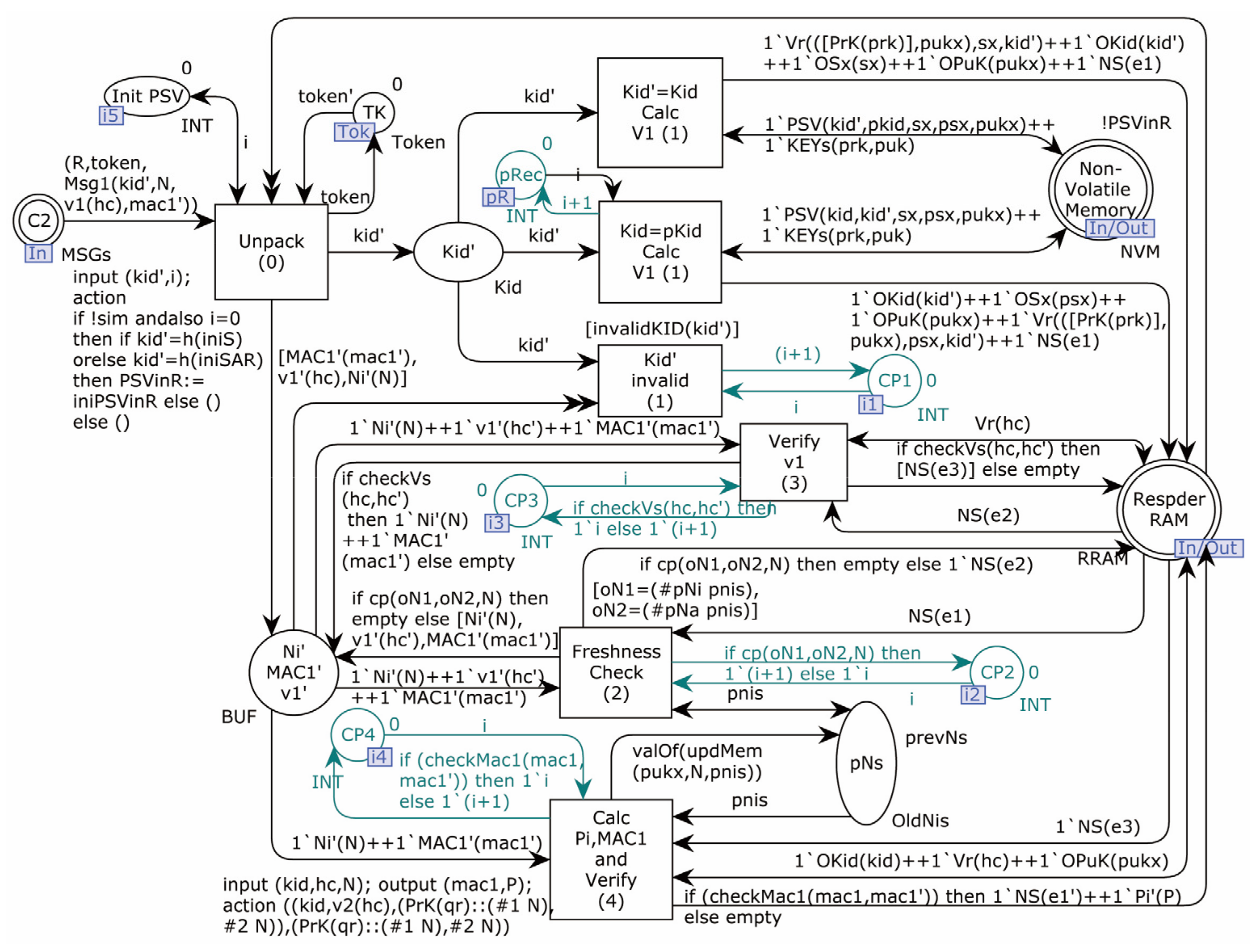
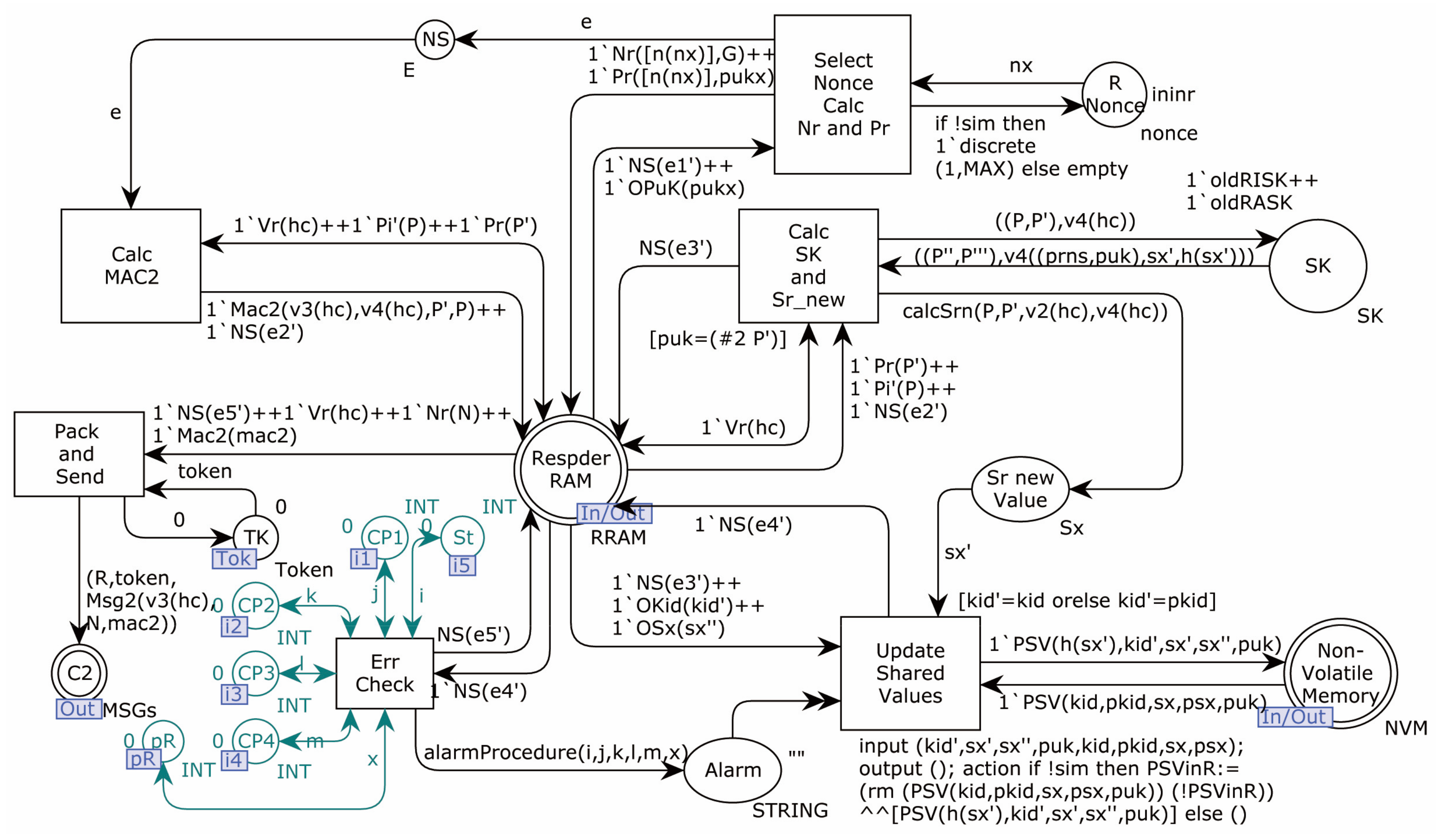
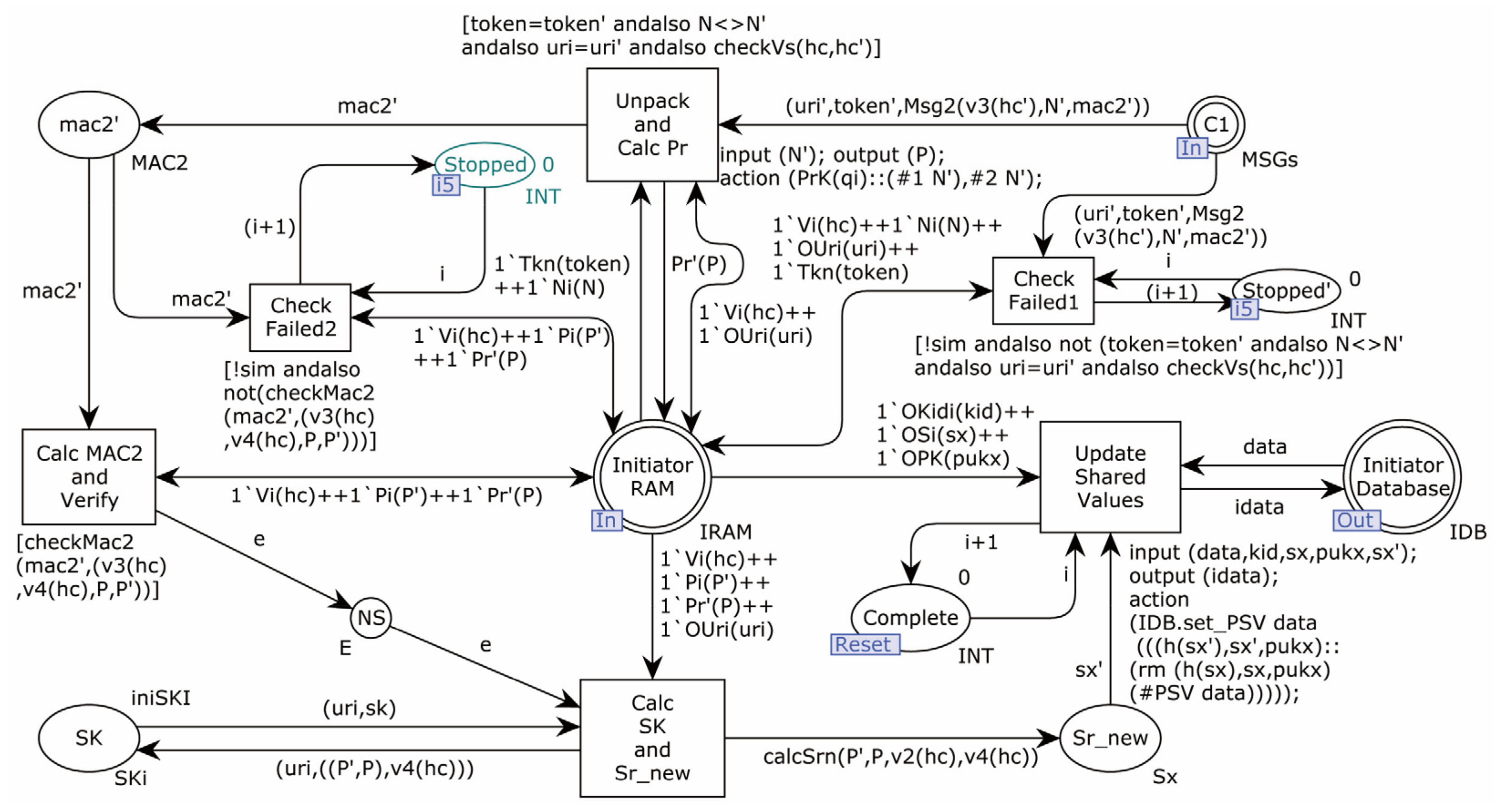
4.2.1. Modeling of the Proposed Protocol
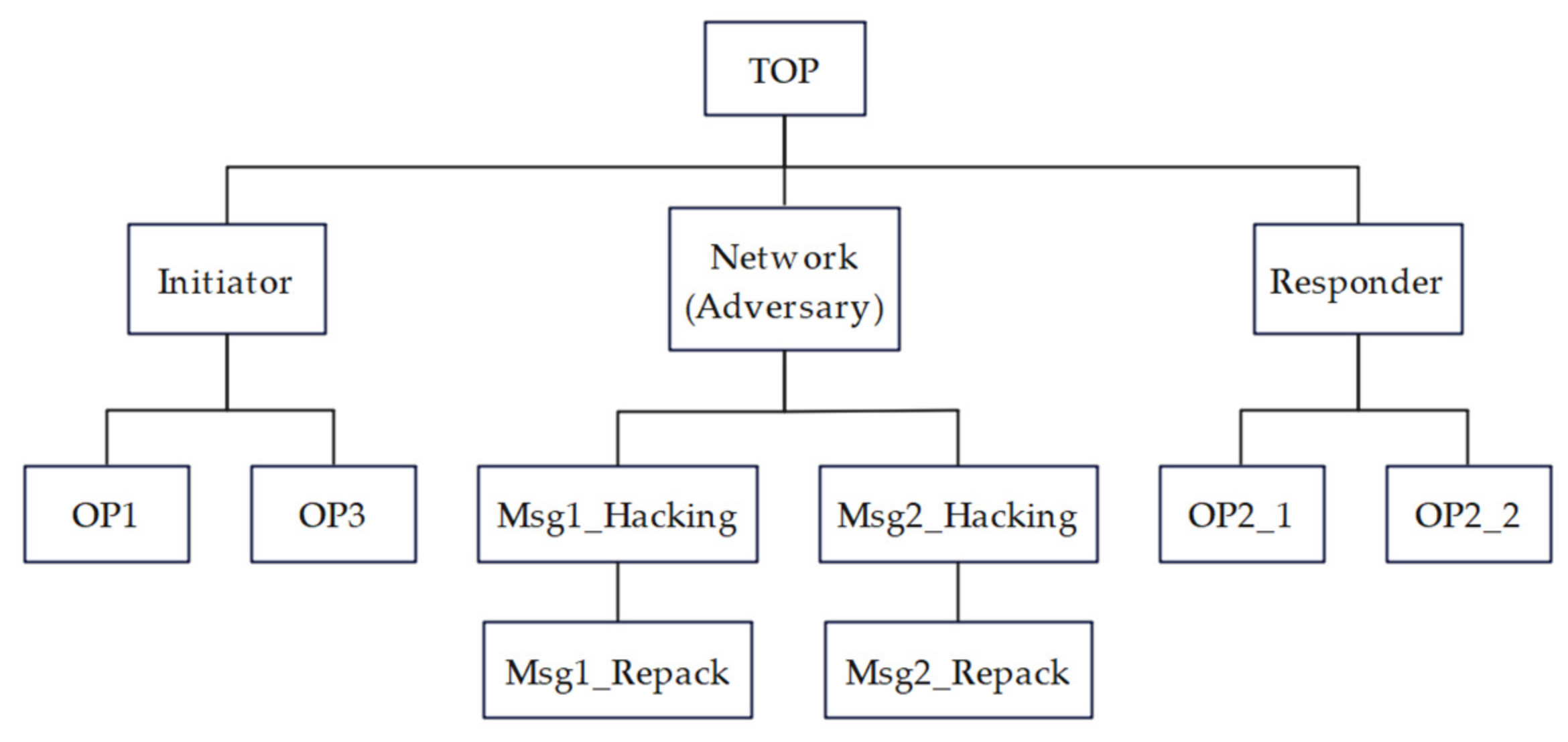
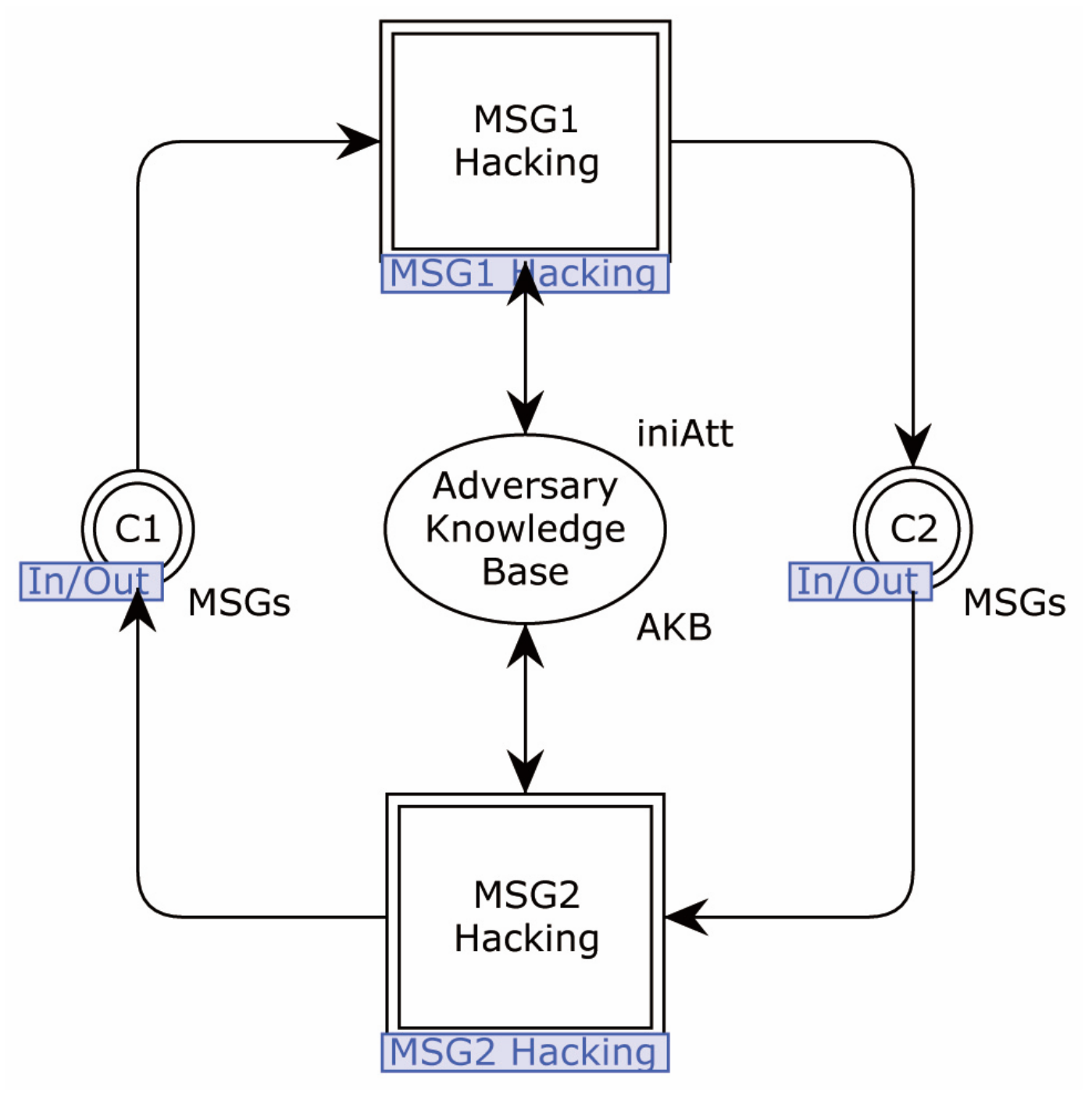
4.2.2. Modeling of Adversary
4.2.3. Security Verification
- A interacts with Responder typically with the shared Sid of the current round.
- A interacts with Responder typically with the shared Sid of the previous round (the number of alarms is 1).
- A transmitted the request sent by Initiator to Responder (without modification).
4.2.4. Protocol Simulation
5. Security Analysis
5.1. Confidentiality
5.2. Data Integrity
5.3. Mutual Authentication
5.4. Perfect Forward and Backward Secrecy
5.5. Device Anonymity and Unlinkability
5.6. Resistance to Impersonation Attack
5.7. Resistance to Man-in-the-Middle Attack
5.8. Resistance to the Privileged Insider Attack
5.9. Resistance to the Known Session-Specific Temporary Information Attack
5.10. Resistance to the Replay Attack
5.11. Resistance to the Key Compromise Impersonation Attack
5.12. Resistance to the Desynchronization Attack
5.13. Key Misbinding Problem
5.14. Resistance to the DoS Attack
5.15. Discussion of the Amplification Attack
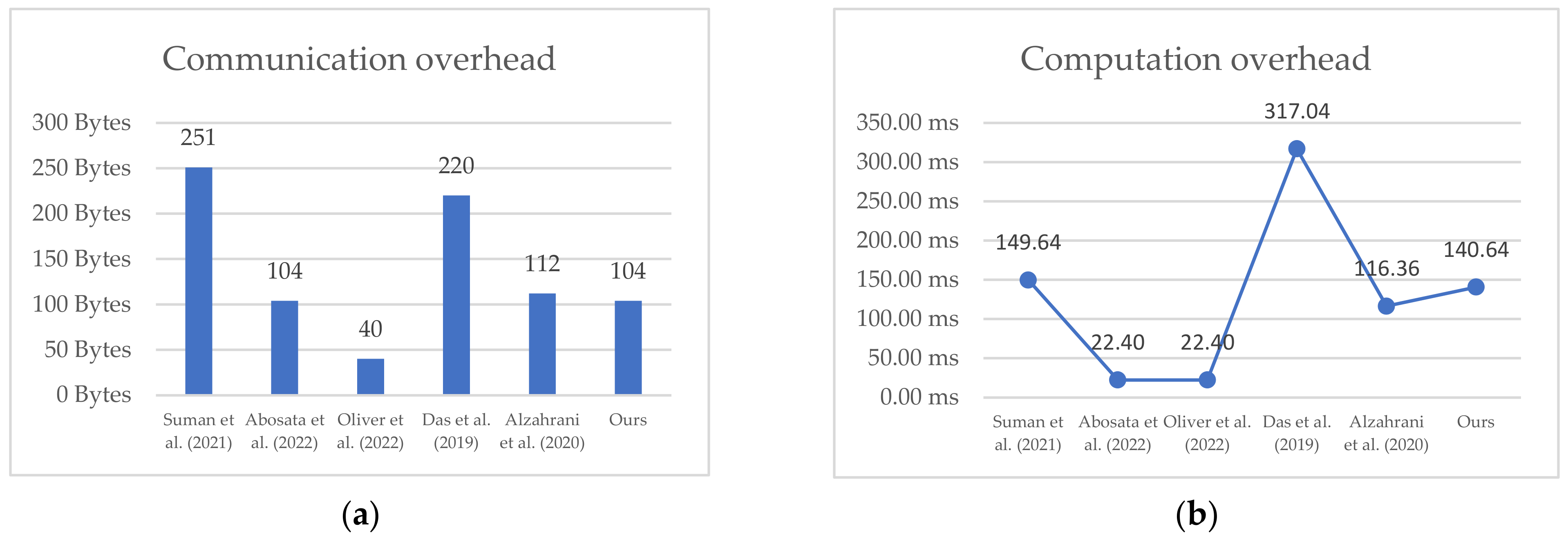
6. Performance and Security Evaluation
6.1. Computation and Communication Overhead Evaluation
| Protocol | Initiator | Responder | Total |
|---|---|---|---|
| Suman et al. [20] | |||
| Abosata et al. [21] | |||
| Oliver et al. [22] | |||
| Das et al. [23] | |||
| Alzahrani et al. [24] | |||
| Our Protocol |
| Protocol | Communication Cost | Flights |
|---|---|---|
| Suman et al. [20] | 4 | |
| Abosata et al. [21] | 4 | |
| Oliver et al. [22] | 2 | |
| Das et al. [23] | 3 | |
| Alzahrani et al. [24] | 3 | |
| Our Protocol | 2 |
| Comparative Point | Scheme | ||||||
|---|---|---|---|---|---|---|---|
| Suman et al. [20] | Abosata et al. [21] | Oliver et al. [22] | Das et al. [23] | Alzahrani et al. [24] | Ours | ||
| Security attributes | Mutual Authentication | √ | √ | √ | √ | √ | √ |
| Perfect forward secrecy | × | × | × | √ | × | √ | |
| Device Anonymity | × | √ | × | × | × | √ | |
| No-synchronized Clocks | × | √ | √ | × | √ | √ | |
| No-stored all expire nonces | √ | × | × | √ | × | √ | |
| Attack Resistance | Replay | √ | × | × | √ | √ | √ |
| Man in the Middle | √ | × | √ | × | √ | √ | |
| Key Compromise Impersonation | × | × | √ | × | × | √ | |
| Privilege-Insider | √ | × | √ | √ | × | √ | |
| Denial of service | × | × | × | √ | √ | √ | |
| Desynchronization | √ | √ | × | √ | √ | √ | |
| Known Specific Temp Info | √ | √ | × | √ | √ | √ | |
| Known Key | × | × | × | √ | √ | √ | |
6.2. Evaluation of Security
7. Conclusions
Supplementary Materials
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Shelby, Z.; Hartke, K.; Bormann, C.; Frank, B. RFC 7252: The Constrained Application Protocol (CoAP). Internet Engineering Task Force (IETF). 2014. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc7252.txt.pdf (accessed on 11 June 2021).
- Iglesias-Urkia, M.; Orive, A.; Urbieta, A.; Casado-Mansilla, D. Analysis of CoAP implementations for industrial Internet of Things: A survey. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 2505–2518. [Google Scholar] [CrossRef]
- Islam, M.M.; Khan, Z.; Alsaawy, Y. A framework for harmonizing internet of things (IoT) in cloud: Analyses and implementation. Wirel. Netw. 2021, 27, 4331–4342. [Google Scholar] [CrossRef]
- Alhaidari, F.A.; Alqahtani, E.J. Securing communication between fog computing and iot using constrained application protocol (coap): A survey. J. Commun. 2020, 15, 14–30. [Google Scholar] [CrossRef]
- Palombini, F.; Seitz, L.; Selander, G.; Mattsson, J. RFC 8613: Object Security for Constrained RESTful Environments (OSCORE). Internet Engineering Task Force (IETF). 2018. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc8613.txt.pdf (accessed on 18 February 2022).
- Bormann, C.; Hoffman, P. RFC 8949: Concise Binary Object Representation (CBOR). Internet Engineering Task Force (IETF). 2020. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc8949.txt.pdf (accessed on 10 April 2022).
- Schaad, J. RFC 8152: Cbor Object Signing and Encryption (Cose). Internet Engineering Task Force (IETF). 2017. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc8152.txt.pdf (accessed on 23 March 2022).
- Villaverde, B.C.; Pesch, D.; Alberola, R.D.P.; Fedor, S.; Boubekeur, M. Constrained application protocol for low power embedded networks: A survey. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Washington, DC, USA, 4–6 July 2012; pp. 702–707. [Google Scholar]
- Glissa, G.; Meddeb, A. 6LowPSec: An end-to-end security protocol for 6LoWPAN. Ad Hoc Netw. 2019, 82, 100–112. [Google Scholar] [CrossRef]
- Karagiannis, V.; Chatzimisios, P.; Vazquez-Gallego, F.; Alonso-Zarate, J. A survey on application layer protocols for the internet of things. Trans. IoT Cloud Comput. 2015, 3, 11–17. [Google Scholar]
- Saqib, M.; Jasra, B.; Moon, A.H. A Systematized Security and Communication Protocols Stack Review for Internet of Things. In Proceedings of the 2020 IEEE International Conference for Innovation in Technology (INOCON), Bangalore, India, 6–8 November 2020; pp. 1–9. [Google Scholar]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A survey of IIoT protocols: A measure of vulnerability risk analysis based on cvss. ACM Comput. Surv. 2020, 53, 1–53. [Google Scholar] [CrossRef]
- Bhattacharjya, A.; Zhong, X.; Wang, J.; Li, X. CoAP—application layer connection-less lightweight protocol for the Internet of Things (IoT) and CoAP-IPSEC Security with DTLS Supporting CoAP. In Digital Twin Technologies and Smart Cities; Springer: Berlin/Heidelberg, Germany, 2020; pp. 151–175. [Google Scholar]
- Arvind, S.; Narayanan, V.A. An overview of security in coap: Attack and analysis. In Proceedings of the 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS), Coimbatore, India, 15–16 March 2019; pp. 655–660. [Google Scholar]
- Figueroa, P.E.; Perez, J.A.; Amezcua, I. Performance evaluation of lightweight and secure protocol for wireless sensor networks: A protocol to enable Web services in IPv6 over low-power wireless personal area networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717715185. [Google Scholar] [CrossRef]
- Van den Abeele, F.; Moerman, I.; Demeester, P.; Hoebeke, J. Secure service proxy: A CoAP (s) intermediary for a securer and smarter Web of Things. Sensors 2017, 17, 1609. [Google Scholar] [CrossRef]
- Ukil, A.; Bandyopadhyay, S.; Bhattacharyya, A.; Pal, A.; Bose, T. Lightweight security scheme for IoT applications using CoAP. Int. J. Pervasive Comput. Commun. 2014, 10, 372–392. [Google Scholar] [CrossRef]
- Bhattacharyya, A.; Bose, T.; Bandyopadhyay, S.; Ukil, A.; Pal, A. LESS: Lightweight establishment of secure session: A cross-layer approach using CoAP and DTLS-PSK channel encryption. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications Workshops, Gwangiu, Korea, 24–27 March 2015; pp. 682–687. [Google Scholar]
- Nathi, R.A.; Sutar, D.S. Embedded payload security scheme using CoAP for IoT device. In Proceedings of the 2019 International Conference on Vision towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019; pp. 1–6. [Google Scholar]
- Majumder, S.; Ray, S.; Sadhukhan, D.; Khan, M.K.; Dasgupta, M. ECC-CoAP: Elliptic curve cryptography based constraint application protocol for internet of things. Wirel. Pers. Commun. 2021, 116, 1867–1896. [Google Scholar] [CrossRef]
- Abosata, N.; Al-Rubaye, S.; Inalhan, G. Lightweight Payload Encryption-Based Authentication Scheme for Advanced Metering Infrastructure Sensor Networks. Sensors 2022, 22, 534. [Google Scholar] [CrossRef]
- Oliver, S.-G.; Purusothaman, T. Lightweight and Secure Mutual Authentication Scheme for IoT Devices Using CoAP Protocol. Comput. Syst. Sci. Eng. 2022, 41, 767–780. [Google Scholar] [CrossRef]
- Das, A.K.; Wazid, M.; Yannam, A.R.; Rodrigues, J.J.; Park, Y. Provably secure ECC-based device access control and key agreement protocol for IoT environment. IEEE Access 2019, 7, 55382–55397. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Chaudhry, S.A.; Barnawi, A.; Al-Barakati, A.; Shon, T. An anonymous device to device authentication protocol using ECC and self certified public keys usable in Internet of Things based autonomous devices. Electronics 2020, 9, 520. [Google Scholar] [CrossRef]
- Hajian, R.; Haghighat, A.; Erfani, S.H. A Secure Anonymous D2D Mutual Authentication and Key Agreement Protocol for IoT. Internet Things 2022, 18, 100493. [Google Scholar] [CrossRef]
- Tsai, W.-C.; Tsai, T.-H.; Wang, T.-J.; Chiang, M.-L. Automatic Key Update Mechanism for Lightweight M2M Communication and Enhancement of IoT Security: A Case Study of CoAP Using Libcoap Library. Sensors 2022, 22, 340. [Google Scholar] [CrossRef]
- Hofer-Schmitz, K.; Stojanović, B. Towards formal verification of IoT protocols: A Review. Comput. Netw. 2020, 174, 107233. [Google Scholar] [CrossRef]
- Luo, F.; Feng, T.; Zheng, L. Formal Security Evaluation and Improvement of Wireless HART Protocol in Industrial Wireless Network. Secur. Commun. Netw. 2021, 2021, 8090547. [Google Scholar] [CrossRef]
- Gehlot, V. A Tutorial Introduction to Colored Petri Nets Framework for Model-Driven System Design and Engineering. In Proceedings of the 2021 Annual Modeling and Simulation Conference (ANNSIM), Fairfax, VA, USA, 19–22 July 2021; pp. 1–12. [Google Scholar]
- Coronado, E.; Valero, V.; Orozco-Barbosa, L.; Cambronero, M.-E.; Pelayo, F.L. Modeling and simulation of the IEEE 802.11 e wireless protocol with hidden nodes using Colored Petri Nets. Softw. Syst. Model. 2021, 20, 505–538. [Google Scholar] [CrossRef]
- Rekha, H.; Siddappa, M. Model Checking M2M and Centralised IOT authentication Protocols. J. Phys. Conf. Ser. 2022, 2161, 012042. [Google Scholar] [CrossRef]
- Rodríguez, A.; Kristensen, L.M.; Rutle, A. Formal modelling and incremental verification of the MQTT IoT protocol. In Transactions on Petri Nets and Other Models of Concurrency XIV; Springer: Berlin/Heidelberg, Germany, 2019; pp. 126–145. [Google Scholar]
- Zroug, S.; Kahloul, L.; Benharzallah, S.; Djouani, K. A hierarchical formal method for performance evaluation of WSNs protocol. Computing 2021, 103, 1183–1208. [Google Scholar] [CrossRef]
- Permpoontanalarp, Y.; Changkhanak, A. On-the-Fly Trace Generation Approach to the Security Analysis of the TMN Protocol with Homomorphic Property: A Petri Nets-Based Method. IEICE Trans. Inf. Syst. 2012, 95, 215–229. [Google Scholar] [CrossRef]
- Igorevich, R.R.; Shin, D.; Min, D. CPN Based Analysis of In-Vehicle Secure Communication Protocol. In Proceedings of the International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness, Seoul, Korea, 7–8 July 2016; pp. 12–21. [Google Scholar]
- Amoah, R.; Camtepe, S.; Foo, E. Formal modelling and analysis of DNP3 secure authentication. J. Netw. Comput. Appl. 2016, 59, 345–360. [Google Scholar] [CrossRef]
- Bai, Y.; Ye, X.; Ma, Y. Formal modeling and analysis of SIP using colored petri nets. In Proceedings of the 2011 7th International Conference on Wireless Communications, Networking and Mobile Computing, Wuhan, China, 23–25 September 2011; pp. 1–5. [Google Scholar]
- Yan, Z.; Gu, C.; Huang, H. Analysis for Threat Models and Improvement Scheme of 5G AKA Protocol Based on Petri-net. In Proceedings of the 2021 IEEE 21st International Conference on Communication Technology (ICCT), Tianjin, China, 13–16 October 2021; pp. 11–17. [Google Scholar]
- Yang, X.; Jiao, J.; Shi, Y.; Liu, Y. Modeling and Security Analysis Method of Quantum Key Distribution Protocol Based on Colored Petri Nets. In Proceedings of the 2019 IEEE 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019; pp. 283–289. [Google Scholar]
- Wang, D.; Li, W.; Wang, P. Measuring two-factor authentication schemes for real-time data access in industrial wireless sensor networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Mattsson, J.P.; Selander, G.; Raza, S.; Höglund, J.; Furuhed, M. CBOR Encoded X.509 Certificates (C509 Certificates). Internet Engineering Task Force. January 2022. Available online: https://datatracker.ietf.org/doc/draft-ietf-cose-cbor-encoded-cert/ (accessed on 14 March 2022).

| Symbol | Description |
|---|---|
| Identity of Initiator (I), Responder (R) | |
| Random nonce chosen by I and R | |
| p | A large prime number |
| A prime finite field | |
| G | Base point over |
| A finite field | |
| Private and Public key pair of I, R | |
| Current and previous secrets shared between I and R. | |
| Current and previous key index shared between I and R | |
| (v1, …, v4) | The value split by |
| SK | Session Key between I and R |
| The elliptic curve points and | |
| pN | previous stored by R |
| Bitwise XOR, Concatenation operation | |
| Null | |
| h(.) | One-way hash function |
| An elliptic curve over prime field defined by non-singular elliptic curve equation: a, b are constants, , and |
| Variable Name | Type | Position | Effects on the Model |
|---|---|---|---|
| sim | Bool | Pages Pallete | If true, enable loop simulation. Allow setting the transition triggers at specified times. |
| AttM1 | Enum | Pages Pallete | On: enable recombined message 1. Off: message 1 will send without modification. |
| AttM2 | Enum | Pages Pallete | On: enable recombined message 1. Off: message 1 will send without modification. Brk: set a breakpoint where message 2 is received. |
| SkipChkM1 | Bool | Pages Pallete | If true, the Adversary combines only legitimate message 1. |
| iniAtt | Enum | Pallete | 0: Initialize the AKB with the original DY. 1: Initialize the AKB with the original DY and eDY1. 2: Initialize the AKB with the original DY and eDY2. 3: Initialize the AKB with the original DY and eDY3. |
| LR | Int | Pallete | When sim = true, set the loss rate of message 2. |
| n | The Initial Knowledge | Verification Content |
|---|---|---|
| 0 | Original data * | Confidentiality, integrity, authentication, Man-in-the-middle Attack, Replay Attack, Device Capture attack, Untraceability, Impersonation Attack |
| 1 | Original data and private key of Initiator (I) and Responder (R) | Perfect forward secrecy, Known-Key Attack, Key Compromise Impersonation Attack |
| 2 | Original data and pre-shared secret between I and R | Privilege-Insider Attack, Pre-shared Information Disclosure Attack |
| 3 | Original data and fresh random nonce of I and R | Known Specific Temporary Information Attack |
| Init KB 1 | Case | Nodes | Dead Markings | Resp 2 | Rm Dupl 3 | Error Count | Illegal Resp 4 | Key Materials 5 |
|---|---|---|---|---|---|---|---|---|
| 0 | 1 | 14,304 | 3322 | 8 | 3 | 1 | 0 | None |
| 2 | 29,762 | 27,004 | 38 | 3 | 1 | 0 | None | |
| 1 | 1 | 29,868 | 6972 | 14 | 3 | 1 | 0 | None |
| 2 | 85,572 | 77,408 | 146 | 3 | 1 | 0 | ||
| 2 | 1 | 22,086 | 5147 | 11 | 3 | 1 | 0 | None |
| 2 | 54,526 | 49,506 | 83 | 3 | 1 | 0 | None | |
| 3 | 1 | 27,004 | 6280 | 22 | 5 | 2 | 0 | |
| 2 | 101,338 | 92,108 | 144 | 5 | 2 | 0 |
| Place | Times | Check Value | Adversary Operations |
|---|---|---|---|
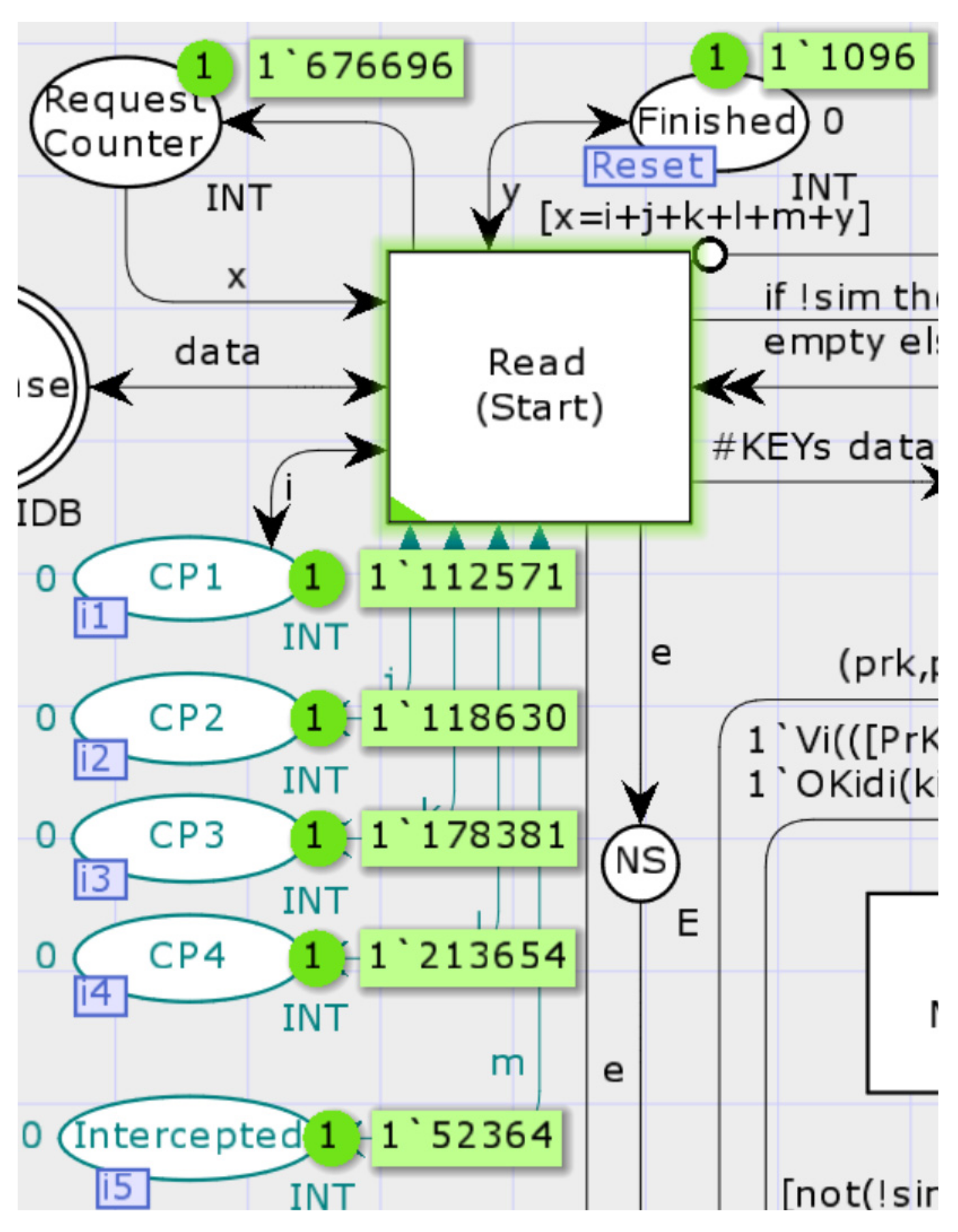
| CP1 | 112,571 | Kidr | Replayed message 1 eavesdropped before the previous interaction or sent a fake message. |
| CP2 | 118,630 | Ni | Replayed previous message 1 directly. |
| CP3 | 178,381 | v1 | Modified the v1 in the message sent by the Initiator. |
| CP4 | 213,654 | MAC1 | Modified Ni in the eavesdropped previous message. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gong, X.; Feng, T. Lightweight Anonymous Authentication and Key Agreement Protocol Based on CoAP of Internet of Things. Sensors 2022, 22, 7191. https://doi.org/10.3390/s22197191
Gong X, Feng T. Lightweight Anonymous Authentication and Key Agreement Protocol Based on CoAP of Internet of Things. Sensors. 2022; 22(19):7191. https://doi.org/10.3390/s22197191
Chicago/Turabian StyleGong, Xiang, and Tao Feng. 2022. "Lightweight Anonymous Authentication and Key Agreement Protocol Based on CoAP of Internet of Things" Sensors 22, no. 19: 7191. https://doi.org/10.3390/s22197191
APA StyleGong, X., & Feng, T. (2022). Lightweight Anonymous Authentication and Key Agreement Protocol Based on CoAP of Internet of Things. Sensors, 22(19), 7191. https://doi.org/10.3390/s22197191






