Abstract
Internet of Vehicles (IoV) technology has been attracting great interest from both academia and industry due to its huge potential impact on improving driving experiences and enabling better transportation systems. While a large number of interesting IoV applications are expected, it is more challenging to design an efficient IoV system compared with conventional Internet of Things (IoT) applications due to the mobility of vehicles and complex road conditions. We discuss existing studies about enabling collaborative intelligence in IoV systems by focusing on collaborative communications, collaborative computing, and collaborative machine learning approaches. Based on comparison and discussion about the advantages and disadvantages of recent studies, we point out open research issues and future research directions.
1. Introduction
As the fourth industrial revolution, industry 4.0 has started an important development stage and academia, industry and management departments are making efforts to realize the intelligent ecology of industry 4.0 [1,2]. As a necessary foundation of industry 4.0 and key use cases such as smart city and smart industry, Internet of Things (IoT) realizes the intelligent perception, recognition and management of objects and processes through the connection between things and things, and people and things. In recent years, Intelligent Transportation System (ITS) and Intelligent Vehicles (IV) are the research hotspots of many researchers and technology companies. As the most important application fields of the IoT, IoV is an essential key technology for the next generation of ITS, and also one of the most important breakthroughs. The realization of IoV can significantly improve the smart city and the sustainable development of energy. For example, the traffic management system in the environment of IoV and vehicles with autonomous driving function can reduce traffic congestion, traffic accidents, and environmental pollution. Vehicles under the networking of an intelligent vehicle system can provide users with more comprehensive and personalized mobile travel service, such as path planning, service recommendation, and intelligent parking to provide a safe, comfortable, intelligent, and efficient driving experience and transportation services, improving the efficiency of transportation. At the same time, they promote an intelligent level of transportation service for society. Applications of IoV are listed in Figure 1. IoV is not only applied to urban traffic, but also has many applications; for instance, internet of underwater vehicles and internet of aerial vehicles. Drones are used in intelligent logistics, oil and gas equipment inspection, environmental and traffic monitoring, disaster recovery and more scenarios. IoV has attracted a large number of researchers and companies due to its great research value and commercial interests.
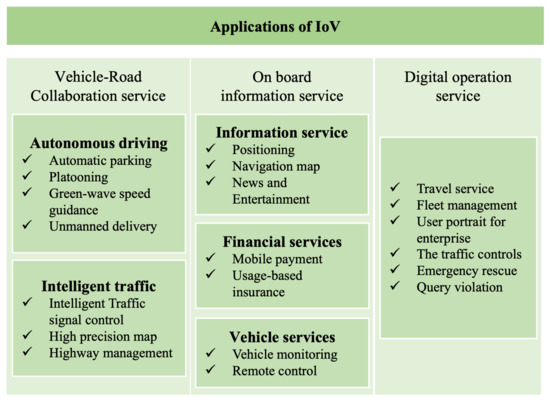
Figure 1.
Application of Internet of Vehicles.
However, the development of the IoV system still needs to overcome many challenges before it can play a big role because of the above characteristics. These challenges include the following. To turn the "Internet of Everything" into reality in the future, there will be more and more network devices and access environments, resulting in entity heterogeneity, dynamic, data diversity and big data challenges. At the same time, a variety of high-quality new applications, such as autonomous driving and automated delivery and other advanced services, require high network, storage, and computing resources. Therefore, to meet the network requirements of low delay, large bandwidth, secure, and efficient computing requirements of the next generation of IoV, efficiently utilizing the existing limited resources to design the IoV system is a major challenge.
To address these challenges, resource-efficient task processing architecture must to be built while effectively utilizing the limited resources at all levels, such as perception, transmission, and application of IoV. All of these demands drive us to research how these various entities might work together to optimize communication, caching, and computing resources between heterogeneous agents. In the past few decades, AI has developed rapidly and has been successfully applied in many research and application fields. Currently, in the field of IoV, there are many studies showing great interest in AI and collaborative intelligence methods. Collaborative intelligence(CI), also known as cooperative intelligence, is able to aggregate the capabilities and intelligence of multiple devices to achieve a common goal and intent [3].
CI can bring AI to the edge, such as vehicles and roadside units. The lack of sensing, computing, and storage capabilities of edges and endpoints can be solved. Letting a single computing device perform complex tasks alone should be avoided, while the lack of sensing, computing and storage capabilities of edges and endpoints can be resolved. This reduces communication latency and protects data privacy by bringing the AI closer to the user. Some studies have confirmed that the collaboration of cloud and mobile edge can improve end-to-end latency, decrease usage of energy, and increase data-center throughput [4,5].
Many articles have reviewed and surveyed research issues from various perspectives in IoV, including 5G technology evolution [6], edge service optimization [7], attacks and detection mechanisms [8], secure and trust management [9,10,11], and big data extraction and decomposition [12]. There are also articles proposing new generic IoV architectures [13,14], applied Software-Defined Networking (SDN) on VANET [15], or studying the deployment and application of IoV in a smart city [16]. In addition, there are many works on the application of new techniques in IoV; for instance, Deep Reinforcement Learning technologies [17], Blockchain [18], Digital Twins, and Federated Learning [19]. These articles well introduce the basic technology, network architecture, and typical applications of IoV, but rarely involve the problem of collaborative intelligence in IoV. There are still a small number of articles discussing the problem of collaborative intelligence in IoV, including collaboration in smart drones and IoT [20], cooperation and collision avoidance in UAVs [21], and sociality of collaborative CAVs [3], but they are limited to specific fields or research problems, and cannot describe the whole picture of the collaborative problem involved in the heterogeneous network of IoV. In addition, the articles on CI are not limited to IoV [22,23], which is a good reference for the study of CI in IoV scenarios, but more targeted work is desired to discuss CI problems according to the characteristics of fast-moving vehicles and high delay requirements of IoV applications.
The research works discussed in this paper cover a wide range of topics for implementing CI in IoV applications, such as radio resource allocation, routing protocols, data sharing, task offloading, security enhancement, and machine learning methods. We will discuss these topics in three sections: collaborative communication, collaborative computing, and collaborative machine learning approaches. Collaborative communication is the coordinated networking technology, including the routing and access selection in V2R, V2P, and V2V collaborative scenarios, security and privacy during communication, etc. Collaborative computing includes big-data-oriented task offloading and mobile edge computing. Collaborative learning technologies include federated learning, ensemble learning, unsupervised learning, and reinforcement learning.
Due to space and energy constraints, we prioritize research works according to their relevance to the subject under discussion, as well as their quality, location, date of publication, and number of citations. Journal papers published in authoritative journals or magazines and conference papers published in international conference proceedings in the last 3 to 5 years are selected. We also include the most cited papers on collaborative intelligence in the IoV.
The rest of this paper is organized as follows: In Section 2, the concepts and features of IoV and CI are introduced. In Section 3, we describe the collaborative communication technology in the collaborative intelligence of the IoV and then discuss its existing difficulties and existing research in detail. In Section 4, technical issues and existing research in collaborative computing, including task offloading and mobile edge computing methods, are discussed. Section 5 summarizes the development and current situation of collaborative machine learning methods such as joint learning, ensemble learning, unsupervised learning clustering, and reinforcement learning in the collaborative intelligence of the IoV, and analyzes the advantages and disadvantages of each method. In Section 6, we propose the future research directions of CI in the IoV. Section 7 is the conclusion of the paper.
2. Internet of Vehicles and Collaborative Intelligence
In this section, the concept, architecture, and characteristics of the Internet of Vehicles are briefly introduced, and then collaborative intelligence and its advantages and challenges in IoV are discussed.
2.1. Internet of Vehicles
The IoV is the integration of IoT and mobile vehicle Internet. It is a huge system composed of multiple nodes connected in the network, such as intelligent vehicles driven by humans or autonomous vehicles, infrastructure integrated with intelligent sensing and V2X communication [24], Mobile Edge Computing (MEC) devices [25], and cloud computing service platforms. It relies on multiple disciplines such as networking, communication, Artificial Intelligence, control, social sciences, and cybersecurity to try to provide rich intelligent applications. In general, IoV technology is a dynamic mobile communication system that connects vehicles and connected devices through vehicle to everything (V2X) communication, enabling all necessary devices to share information and interact. It includes vehicle to vehicle (V2V), vehicle to road (V2R), vehicle to infrastructure (V2I), vehicle to pedestrian and cyclist (V2P), and vehicle to cloud/edge (V2N) communication [24]. The scenario is shown in Figure 2. An IoV system can supervise and guide traffic efficiently in real time and provide more intelligent mobile services through data collection, sharing transmission, storage and computing and analysis capabilities.
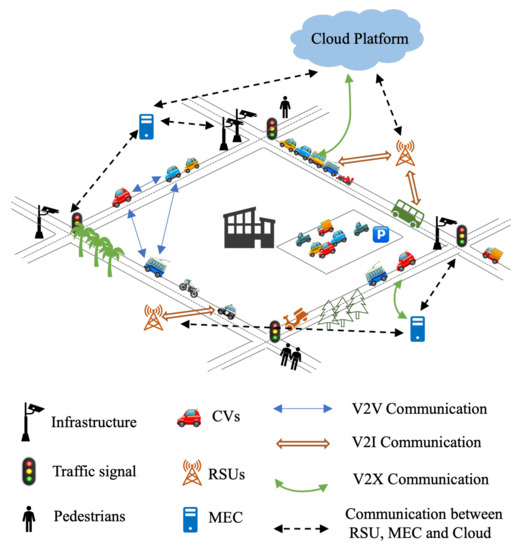
Figure 2.
One scenario of Internet of Vehicles.
The traditional IoV architecture is usually divided into three layers, including the perception layer, the network layer, and the application layer. According to the specific application scenarios or refinement functions, many studies have divided the IoV into four layers [26], five layers [13], seven layers, and other different levels of architecture [27]. Here, we still consider IoV as a three-layer structure, as shown in Figure 3.
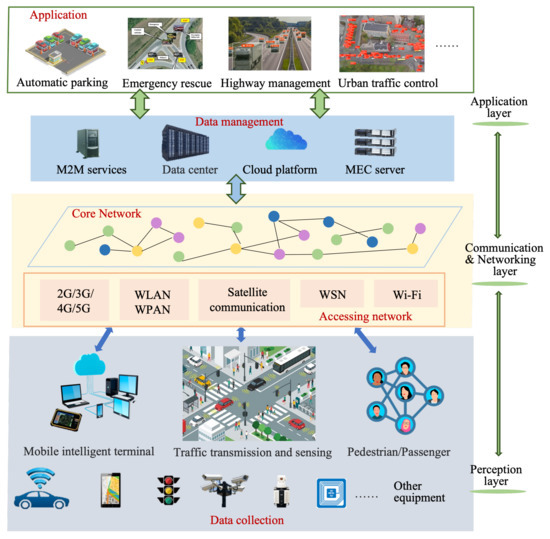
Figure 3.
Three-layer Structure of Internet of Vehicles.
The perception layer is the foundation of IoV and contains all sensors inside and outside the vehicle, which collect environmental data and detect specific events of interest; for instance, vehicle condition, road conditions, traffic lights, and environmental conditions. The goal is to obtain the knowledge of the whole environment by collecting information from multiple angles [28]. After screening, integration, and analysis, these large amounts of collected information can afford data support for the realization of various businesses in the IoV.
The second layer is the networking layer, or communication layer, which supports different V2X wireless communication modes. It allows seamless connectivity with existing and emerging networks such as GSM, Wi-Fi, LTE, Bluetooth, 802.15.4, 5G/6G, etc. This is so that the large amount of data and signals generated at all times can be transmitted everywhere without delay, while minimizing the resource consumption. At present, the main communication standard of IoV is Dedicated Short-Range Communications (DSRC) based on the IEEE 802.11 standard, which is led by the United States and cellular-vehicle to Everything (C-V2X) which is the global unified standard communication technology [29].
The application layer includes statistics, storage management, computing, and processing infrastructure, which provides the analysis, processing, and decision-making of different situations based on big data for ordinary users, management departments, and enterprises. The goal is to be able to fuse information from different systems and technologies to make a unified decision. It involves the allocation of computing tasks and resource management [30].
Internet of vehicles is widely used. At present, research on IoV is mainly focused on low-delay information transmission, traffic safety and efficiency, high reliability, and other aspects, and oriented to big data [27]. In addition, security and privacy protection is an important part of every layer of IoV. Omnidirectional sensing and data sharing require user privacy protection and system security to be in place, so there are many related studies [31,32].
Some features of IoV are as follows:
- Information gathering: Data are collected through the use of various sensors (pollution detection sensors, cameras, road sensors, etc.) that provide drivers with enough information to react to environmental changes in an adequate and effective manner.
- High mobility: Vehicular networks (VNs) have highly mobile nodes, related to the speed of the car, and nodes can be added and disappear in a short period of time, resulting in repeated topology changes.
- Type of information transmitted: Messages are transmitted according to the level of participation in the event triggered. Messages can be sent from an initiator to a destination (unicast), or from an initiator to a specific cluster using multi-hop communication (multicast). Vehicles can also send messages to all other vehicles via broadcast.
- Processing big data: A large number of VNs generate large amounts of data, and vehicular networks use cloud computing to process and store big data.
- Internet facilities: The IoV has the unique feature of accessing the Internet. The connected vehicles can benefit from this huge network.
2.2. Collaborative Intelligent in IoV
Collaborative intelligence is capable of merging the data, power, and intelligence of multiple pieces of connected equipment in order to accomplish a shared objective and purpose. In the IoV system, this usually manifests as real-time communication and interaction, organic combination of data, sharing of computing and storage resources, and synchronization and scheduling of network access IoV entities, including intelligent vehicles, roadside units, users and mobile devices, edge computing servers, cloud computing centers, data centers, etc. In this framework, AI computation and inference will be deployed simultaneously on edges and the cloud. One possible structure is that the front end of the AI model is deployed on edge devices and performs the initial processing and feature computation. Then, intermediate features are sent to the cloud, and the AI back end completes the step of inference [22].
As shown in Figure 4, ideas and methods of CI can be integrated into all aspects of IoV. Through cooperation between communication-related smart devices, agents are connected to form a heterogeneous collaborative network, so as to carry out collaborative sensing, collaborative communication, and collaborative computing on this network, in order to make collaborative decisions.
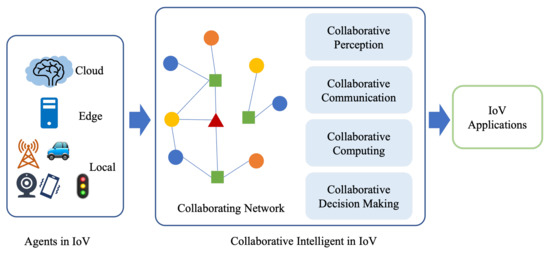
Figure 4.
Collaborative Intelligence in the Internet of Vehicles.
Since AI-based CI methods can produce superior decisions with lower communication overhead by aggregating knowledge and achieving efficient coordination among multiple agents, CI is an inevitable development trend of IoV systems. Specifically, it has the following advantages:
- Collaborative communications over various wireless spectrum types among many transmitters to increase the efficiency of the spectrum utilization.
- Collaborative computing with an end-edge-cloud task processing framework that is resource efficient, meeting a variety of demands on the massive amount of real-time data processing, including exceptionally high throughput and ultra-low latency.
- Collaborative caching among numerous network entities to decrease service latency.
Despite the many benefits of CI, such as communication and computation benefits, it also introduces new challenges in practical applications, so new scientific and technological theories need to be established to attain the optimal design. These challenges include:
- Enable coordination between smart devices.
- Privacy protection and data security issues arising from data and information sharing.
- Efficient collaborative learning with low overhead in scenarios with limited bandwidth and strict latency requirements.
3. Networking Technologies toward Collaborative Intelligence
Internet of Vehicles is a large system network composed of an intra-vehicle network, an inter-vehicle network, and a vehicle–cloud network for radio communication and information interaction. Through the integration of the three networks, V2X communication can be more seamless, more efficient, and less communication dead zone. However, with the development of the IoT and vehicle-related technologies and the increasing demand for new service applications, more and more devices are being connected or are ready to be connected to the network. This requires the transmission and exchange of a large amount of data to achieve the purpose of sensing, transmission, and application. ITS has been revolutionary to change, and every device has the potential to become an intelligent node in IoV to participate in collaboration. This results in the transmission of large-scale signals and data, which must rely on stable, trusted, low-latency communication technology. At the same time, the diversity of access devices and communication approaches, the high dynamic and mobility of vehicles, and frequent topological changes in IoV pose challenges to V2X communication.
Considering CI, networking technologies in IoV are classified from multiple perspectives below:
- From the perspective of communicating objectIt can be divided into V2V, V2I, V2P, and V2N, such as the urban traffic scene in Figure 2. Through V2V communication, the information of the surrounding vehicles can be obtained in the process of vehicle driving, and the vehicles can also constitute an interactive platform, which is often used to transfer control information or safety information between vehicles. Generally, the time delay requirements are high. V2I allows vehicles to communicate with roadside infrastructure (such as traffic cameras, roadside units, bus stations, traffic lights, and parking lots), and through the roadside infrastructure, vehicles can also obtain information about nearby vehicles and send various real-time information. Usually, the amount of data transmission is large, which is mainly used in real-time information service and vehicle monitoring and management. V2P involves communication between vehicles and mobile devices used by vulnerable traffic groups (such as pedestrians and cyclists). V2P communication can be implemented via Bluetooth or Near Field Communication (NFC) technology, and it is often used to avoid traffic accidents and information services. V2N is the connection and information exchange between vehicle or driver and cloud platform or internet through an access network/core network. After storing and processing the acquired data, various applications and services are provided for vehicle users and management departments [33].
- From the perspective of communicating rangeCommunication in IoV can be classified as short-range, medium-range, and long-range communication [34], as shown in Figure 5. Short-range communication technology can be used for in-vehicle device connection or V2P scenarios, including Bluetooth, UWB, ZigBee, etc. At present, Wireless Local Area Network (WLAN) and DSRC are able to provide wireless communication within approximately 300 meters for IoV, which can be used in V2V and V2I scenarios and classified as medium-range communication. Cellular Communication technology enables vehicles to communicate with objects thousands of meters away. Nowadays, there is no one communication method that can meet all the communication needs of IoV. Therefore, how to select and formulate a scheme to ensure the CI between vehicle and vehicle, and vehicle and environment, is a key concern when the above multiple access methods coexist.
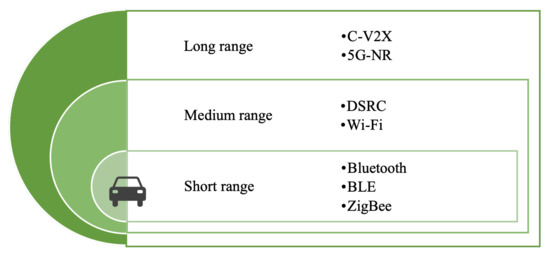 Figure 5. Taxonomy of IoV communication technologies with communication range.
Figure 5. Taxonomy of IoV communication technologies with communication range. - From the perspective of data dissemination and protocolIt is also possible to classify the network technologies of IoV into three categories: unicast communication, geocast, and broadcast communication, which respectively represent from one vehicle to another, from a vehicle to a group of vehicles, and from one vehicle to all other vehicles in the specified range. Important data can be transmitted in a dedicated resource pool using unicast transmission to avoid data transmission, such as platooning and advanced driving. For sensor data sharing or geographical location demanding scenarios, the geocast or broadcast transmission were carried out through the shared resource pool. Broadcast communications are used when collision warnings and traffic jam messages are disseminated [35]. From the perspective of routing, there are single-hop and multi-hop communication methods [36].
Collaborative communication and networking technology is the key to achieving CI tasks between heterogeneous agents in IoV. This section mainly focuses on three different broad topics, namely Radio Access Technology (RAT) selection, routing protocol, and authentication and secure communications in IoV.
3.1. Radio Access Technology Selection in IoV
As mentioned above, there are many types of communication methods that can be used for IoV, and they cannot be replaced with each other. At the same time, the bandwidth demand of users is also increasing, so wireless networks coexist to provide the best service. Vehicles can use different RATS to communicate with other vehicles, infrastructure, networks, etc. Therefore, it is necessary to select the best communication mode and reduce the waste of resources in the multiple access network coexisting environment to ensure cooperation [37].
The RAT selection method can have two schemes [38]. The centralized approach considers the needs of all users in the network and maximizes the throughput or minimizes the delay to centrally optimize the network task. The distributed approach is one in which mobile users improve their own performance as much as possible and regardless of global collaboration, generally using heuristic methods. RAT selection problem is usually treated as a multiple-attribute decision-making problem, or one which uses AI-based algorithms such as neural networks and Q-learning methods. Table 1 summarizes the recent studies on the RAT selection in IoV system.

Table 1.
Recentstudies on RAT selection in IoV.
Table 1.
Recentstudies on RAT selection in IoV.
| Publication | Research Summary | Communication Technology | Scenarios |
|---|---|---|---|
| [39] | A network selection approach that The dynamic Q-learning algorithm was used to verify the necessity of handover, and the fuzzy CNN was used to select the network. | DSRC, 4G-LTE and 5G mmWave | V2V |
| [40] | The communication performance of DSRC and LTE in three typical IoV applications is tested in a real road environment. | DSRC, 4G-LTE | V2V, V2I |
| [41] | An Integrated Approach of 4G LTE and DSRC for IoV by Using a Novel Cluster-Based Efficient Radio Interface Selection Algorithm. | DSRC, 4G-LTE | V2V |
| [42] | A heterogeneous network architecture incorporating multiple wireless interfaces and a Best Interface Selection algorithm are proposed. | WAVE, Wi-Fi, 4G-LTE | V2I |
| [43] | A conceptual multi-RAT OBU architecture for personal mobility vehicles such as shared bikes, segways or electric scooters and its RAT selection approach are discussed. | LPWAN, Wi-Fi, Cellular | V2I, V2N |
| [44] | A vertical handover architecture inside the vehicle is implemented based on the logical interface in TCP/IP mode. | IEEE 802.11P, cellular, Wi-Fi | V2X |
| [45] | A Dynamic Radio Access Selection and Slice Allocation algorithm for 5G and above heterogeneous networks is proposed. | 5G and above: small-cells, macro-cells, Wi-Fi | IoT |
Hussain et al. [39] studies the network selection and routing when different communication modes exist at the same time, including DSRC, 4G LTE, and 5G mmWave. In terms of network selection, the Shannon entropy rule is used to dynamically set the signal strength, and dynamic Q learning is applied to decide whether the communication mode has to be switched. At the same time, a total of 32 fuzzy rules are formulated after considering factors such as distance, line of sight, vehicle density, signal strength, and data type, and then a fuzzy convolutional neural network (CNN) is adopted to execute RAT. In the aspect of routing between vehicles, the objective function based on channel and vehicle state is designed, and the jellyfish optimization algorithm is improved to calculate the routing.
There are also many studies comparing DSRC, Wi-Fi, and cellular factors. In Ref. [40], the communication performance of DSRC and LTE in several application scenarios of IoV is discussed, and corresponding software and hardware are developed for verification. The results show that 4G LTE is more suitable for non-secure applications with low communication speed requirements such as internet access, traffic data transmission, and file download, while DSRC performs better in secure applications such as traffic signs and collision avoidance. Finally, it is suggested to combine the two methods to handle communication problems in IoV, so as to better support high-quality remote information transmission services and security services.
On the premise of studying the advantages and limitations of DSRC and cellular network technology, Hussain et al. [41] proposes an integration scheme combining these two potential networking technologies to complete more efficient vehicle communication. In this paper, an algorithm combining DSRC and 4G-LTE with a new data forwarding protocol based on optimal clustering is proposed. This algorithm is used to intelligently monitor and evaluate the level of packet loss rate to reduce the handover delay.
In Ref. [42], Sherazi et al. proposed a heterogeneous structure that fully integrated several wireless interfaces, along with WAVE, LTE, and Wi-Fi, by utilizing a radio approach for network access. Furthermore, this architecture was proposed to meet requirements such as pervasive connectivity in order to make VANETs adaptable and expandable for IoV to support a wide range of emergency services. This architecture also used the Best Interface Selection algorithm to ensure reliable communication by using the best wireless interfaces to provide suitable connectivity required for successfully forwarding data in vehicular networks in order to avoid single point failure. The results demonstrated the method’s suitability in IoV. Vehicle classification based on application needs is advised in future research in order to avoid access control issues with increasing vehicles and demand.
Sanchez-Iborra et al. [43] considers the incorporation of new environmentally friendly mobile devices, such as motorcycles or bicycles, into collaborative intelligent transportation systems, and a variety of communication techniques—for instance, vehicular Wi-Fi, low-power WAN, and cellular networks—are already available. These communication methods, however, are not fully covered and do not meet the demands of energy consumption and quality of service (QoS). As a result, they propose a decision support frame by applying supervised ML classification to select the best transmission interface in the multi-radio access technology (RAT) device to send a specific message. Various ML algorithms are investigated while considering the computational and energy usage of IoV terminal devices and traffic types. Their method is tested using a decision tree-based microcontroller unit decision support system, and it demonstrates that it can save energy while performing communication tasks and meeting the QoS requirements of some urgent messages.
Vertical handover refers to switching among two distinct networking techniques, while horizontal handover refers to handover among distinct cells of a single network technology. Tuyisenge et al. [44] studies a mobile internal vertical handover mechanism in a Heterogeneous Vehicle network (HVN) with IEEE 802.11P, cellular network, and Wi-Fi. They suggest a vertical handover management strategy that cuts down on setup time to speed up binding updates. By simultaneously connecting to several available networks utilizing the PMIP-HD architecture, this method enhances handover outcomes by predicting the subsequent handover. It uses a proposed logical interface to profit from the connectivity session. The performance of the proposed approach is verified through stimulations of packet delivery rate, packet error rate (PER), handover connection duration and latency, jitter, and throughput.
In tedious scenarios such as the future IoV, the network slicing paradigm has been studied as technology used to solve the dynamic, isolation, and programmability of mobile networks [46]. This is the layering of an infrastructure into many logical network slices (NSs) so that intelligent systems can flexibly allocate system resources to these network slices based on requirements and network conditions. González et al. [45] proposed Dynamic Radio Access Selection and a Slice Assignment algorithm suitable for a heterogeneous network at 5G or above. Multi-attribute decision making and analytical hierarchy process are used in the selection process, which takes into account multiple entities in a network. Their approach handles overload using collaborative game theory, allowing slices to be reallocated on demand and accepting more users with sufficient service awareness. The distinction between premium and ordinary customers ensures that high-priority users receive excellent service quality. The algorithm combines SDN and network function virtualization methods to provide a comprehensive solution for ratio access selection and slice allocation. Since the above methods are proposed in IoT scenarios and slow mobile users are the experimental objects, whether they can also achieve good results in high-speed mobile IoV scenarios needs further experimentation and discussion.
3.2. Routing Protocol in IoV
In recent years, a lot of research of IoV has been carried out on the communication design in the routing protocol. The papers discussed here are listed in Table 2. One type of routing protocol is location based. It designs communication schemes based on location-related information, such as geographical location, topology, and maps [47,48]. In Ref. [48], Ghaffari et al. propose a VANET location-based hybrid opportunistic routing protocol that effectively addresses the location of nodes, as well as the link quality and density of nodes. This process utilizes a greedy forwarding scheme in which the sending vehicle selects the neighborhood with the greatest geographic progress. A mechanism for identifying and remove expired nodes in the routing process has been added, which uses information such as moving direction, velocity, and distance between nodes to measure the lifespan of links. The best candidate node is chosen based on the opportunity and location strategy, and the appropriate data transmission priority is set. Performance is improved in packet delivery ratio, throughput, and end-to-end delay. In Ref. [49], a multi-hop communication protocol based on location information and fuzzy logic is proposed. In Ref. [50], a mobility-prediction-based routing protocol is discussed to lengthen the network lifespan and shorten vehicles’ end-to-end delays. In Ref. [51], the intention of the driver in the vehicle positioning system is used for neighborhood detection, packet transmission, and path recovery in VANET, and a routing protocol based on movement prediction is studied.

Table 2.
Recent studies on Routing Protocol in IoV.
Table 2.
Recent studies on Routing Protocol in IoV.
| Publication | Research Summary | Communication Technology | Scenarios |
|---|---|---|---|
| [47] | A survey about geographic routing protocols of three type of VANETs: Delay Tolerant, Non-Delay Tolerant and hybrid type. | Position based | V2V |
| [48] | An opportunistic and position-based routing protocol with candidate relay node set selection strategy, the priority scheduling scheme and removing the expired links mechanism. | Opportunistic and Position based | V2V |
| [49] | A multi-hop greedy position-based routing algorithm with fuzzy logic techniques is proposed. | Position-based routing with greedy fuzzy logic | V2V |
| [50] | A mobility-aware dynamic-clustering-based routing which forms clusters based on Euclidean distance, uses a Mayfly optimization algorithm to select cluster heads and forwards data to RSU is proposed. | Position-based clustering method | V2I |
| [51] | A routing protocol based on movement prediction is studied using the intention of the driver. | Position based | V2V |
| [52] | An improved position-based routing protocol with a Kalman filter and an extended Kalman filter is studied. | Position based with Kalman filter | V2V |
| [53] | A routing protocol considering network connectivity to dynamically clustered vehicles and select gateway nodes is studied. | Connectivity prediction-Based clustering | V2V |
| [54] | Proposed a vehicle-density-prediction-based routing protocol in which optimal relay nodes are selected on the road grid according to the real-time traffic information. | Grid and vehicle-density- prediction based, neural network | V2V |
| [55] | A method of actively selecting routing and communication interface with Q-learning is proposed in the case of multi-access vehicular edge computing environment. | Reinforcement-learning based | V2V, V2I |
However, the location-based protocol still has some limitations. As the conditions of the traffic environment are changing and becoming more and more complex, the communication links are frequently disconnected because of the mobility of vehicles. Therefore, the communication scheme based on the location information alone cannot fully reflect the communication status between vehicles. Therefore, some studies use a Kalman filter and an extended Kalman filter to improve location-based routing protocols [52], or consider network connectivity to dynamically cluster vehicles, and select gateway nodes in the cluster for communication routing [53]. The reliability of these methods is poor when the distribution of vehicles is uneven, and the effect is not ideal because the scope to be covered is too large and the global structure of the network is not fully structured.
Liu et al. [54] studies a routing protocol named VDPGrid using vehicle density prediction. The vehicle density prediction model uses CNN and long short-term memory (LSTM) to mine spatial and temporal related characteristics in an urban trajectory dataset. The results of the above prediction model are then combined with link quality and path length to assign a weight to each path. In order to reduce communication overhead and computational complexity, after dividing the map into multiple grids, the optimal routing paths are stored in packets, so that data packets can be forwarded between different grids according to road weights. The established vehicle trajectory prediction model can select strategies based on different relay nodes of vehicle cooperation and allocate optimal paths to transmit data packets. This method has less overhead and avoids the grid with poor communication conditions when considering grid selection, so it has better performance in terms of delivery rate. In the process of path selection, the collaborative decision mechanism is adopted, and the overall performance of the method is good.
In Ref. [55], route selection in the edge computing of multi-access vehicles is discussed. The main idea is to learn route selection using the Q-learning method in reinforcement learning, and to actively select routes and communication interfaces to reduce the cost of finding routes after receiving communication requests. A reward rule is designed to learn the route selection method from the feedback of cloud or communication partners and the feedback received by the next hop during the learning process, which is combined with the collaboration of end-edge-cloud and different QoS requirements of delay-sensitive and traffic-intensive applications. Vehicular edge selecting scheme based on fuzzy logic methods is also designed. It can meet the throughput and latency requirements of applications with varying QoS requirements.
3.3. Authentication and Secure Communications in IoV
More and more connected devices are joining the IoV. The comprehensive application of collaborative intelligence in the IoV requires a variety of devices to take part in the data collection, transmission, and calculation processes. This leaves the communication process between vehicles, users, Road Side Units (RSUs), and edge and cloud servers all exposed to network security attacks. This is a very serious problem because it involves a large range of traffic safety issues, and may endanger lives. For example, critical information such as traffic jams, traffic light information, accident reports, and the driving status of nearby vehicles may be intercepted and modified by malicious vehicles or operated RSUs, resulting in missing or incorrect information that can cause damage or accidents. Therefore, protecting the critical data communication in the network is a key link in IoV. In addition to data communication security, another important issue is user privacy protection. The recent studies in authentication and secure communications are listed in Table 3. There are many forms of attacks from all sides in the IoV. In article [56], 14 possible attacks on vehicular ad hoc networks are listed. These include Greedy Drivers, Impersonation Attack, Wormhole Attack, Pranksters, Blackhole Attack, and Denial of Service. Therefore, high requirements are put forward for the IoV system.
A collaborative intelligent vehicle internet environment, from the perspective of privacy and security, must be able to [57]:
- Achieve effective and fast authentication of the validity and integrity of messages.
- Avoid exposing user privacy to anyone other than the licensor.
- Trace the appearance of malicious nodes or false information in the network.
- Ensure that the information transmitted by malicious nodes is irrelevant to the control of vehicles.
- Withstand cryptanalysis attacks by quantum computers.
- Prevent middleman modification, counterfeiting, authentication table theft, replay attacks, etc.

Table 3.
Recent studies on Authentication and Secure Communications in IoV.
Table 3.
Recent studies on Authentication and Secure Communications in IoV.
| Publication | Research Summary |
|---|---|
| [56] | The security and privacy issues in VANETs are reviewed. |
| [57] | A quantum-defended blockchain-assisted data authentication protocol is proposed. |
| [58] | An effective vehicle-centric CRL distribution mechanism is proposed for secure and privacy-preserving IoV. |
| [59] | A blockchain-based data exchange system that is safe and verifiable is investigated. |
| [60] | A bivariate polynomial lightweight mutual authentication and key agreement protocol with blockchain is proposed. |
| [61] | An authenticated key agreement protocol without bilinear pairing is proposed to meet the security requirements of a fog-based vehicular network. |
| [62] | A secure authentication key management protocol for the deployment of IoV based on fog computing is studied to realize the safe communication in vehicle network, RSUs, fog, and cloud servers. |
| [63] | A framework that uses decentralized off-chain dataset and blockchain networks is proposed to increase the security. |
| [64] | A blockchain-based payment strategy for intelligent vehicle refueling to protect sensitive information when data sharing. |
| [65] | A trusted routing scheme based on blockchain and fuzzy logic is proposed to improve discrimination of malicious user in vehicular network. |
Secure communication protocol has always been an active research field. With the development of IoT technology, security authentication protocols in IoV are also developing. In view of the above safety requirements, researchers have carried out many related studies recently. To solve the problems of vehicle identity privacy, distribution of certificate revocation Lists, and computing and communication constraints of vehicular devices intermittently connected to infrastructure, Khodaei et al. [58] designed certificate-based batch authentication technology. However, the fast data communication between vehicles in such schemes and RSUs requires cumbersome certificates, and has a high key storage burden and a long operation time.
In view of the user’s computing power and the sensitive information contained in the access policy, Fan et al. [59] designed an attribute-based ciphertext policy encryption technology for vehicle authentication, and supported information cancellation of vehicles that no longer shared data.
In Ref. [60], a bidirectional authentication scheme based on decentralized key management is designed to automatically enroll, refresh, and withdraw the customer’s public key. But these two methods are vulnerable to quantum attack.
The IoV based on fog clouds is another variant of mobile cloud computing. There are many studies that try to combine fog computing with VANETs to satisfy the requirements for mobility and low latency in practical VANETs. Ma et al. [61] proposed a novel protocol with authenticated key agreement and without bilinear pairing, which realized mutual authentication, generated session keys with security conventions for secret communication, and supported privacy protection. Wazid et al. [62] proposes one lightweight authenticating and key-managing scheme for IoV based on fog computing, which implements authentication key management between vehicle and fog server, RSU and fog server, and cloud server and fog server.
Recently, blockchain technology has been used in many fields as a p2p decentralized computing architecture. In IoV, it is a distributed database retained by multiple entities in the network that can serve as a consensus, privacy, and security protocol to protect V2X communication.
For traffic control of flying vehicles, Allouch et al. [63] presented the blockchain-based lightweight security system UTM-Chain. The visited flight plan or collection of waypoints is saved by the vehicle in a transaction, which is then verified and stored in a block to securely manage vehicle flight. The blockchain is updated with these blocks using cloud servers. A decentralized database is adopted to maintain encrypted vehicle driving records to secure the privacy of information, as well as to lighten the load on the storage capacity of the cars. The system is resilient to different threats and is easily adaptable to the IoV environment, according to the performance evaluation.
To provide clarity, privacy, and trust while erasing any human contact, Jamil et al. [64] discuss a new trading tactic for intelligent vehicle refueling with blockchain. The solution is implemented using a hyperledger structure and is designed so that data sharing between different participants and intelligent vehicle is not allowed.
In Ref. [65], Inedjaren et al. propose a secure and trusted routing scheme for VANET based on blockchain and fuzzy logic. Using blockchain, malicious vehicles’ information can be shared and removed. In order to avoid the burden of a proof-of-work blockchain consensus algorithm, this paper proposes a trust-proof consensus algorithm suitable for a VANET distributed, dynamic, and constrained resource environment. This scheme calculates the trust degree of nodes according to their routing performance. This method uses the Optimized Link State Routing routing protocol and is therefore only used to eliminate the case of malicious vehicles. At the same time, the system overhead is higher than that of other methods.
Gupta et al. [57] designs a new data authentication protocol without a certificate, which is a conditional privacy protection authentication method based on lattice, and realizes the security characteristics of open wireless communication in the IoV. Quantum attacks can be reduced or avoided by using lattice cryptography. On this basis, a reliable blockchain mechanism is proposed, which provides a basis for batch data verification of vehicle reliability and can maintain vehicle anonymity at the same time. In the ideal environment can achieve better communication storage and energy overhead.
The energy consumption and burden of future IoV will be increasingly high, so energy efficiency will be another key issue, and there are quite a few research studies that highlight this [66]. Wang et al. [67] discussed future communication and energy management issues in IoV and proposed an energy-harvesting framework and strategy based on V2I communications to maximize the utility of battery-enabled RSUs and EVs in a V2I communications environment. Cesarano et al. [68] studied the dynamic allocation of RSUs considering the energy consumption and transmission cost of dynamic communication connections between vehicles and RSUs. Sodhro et al. [69] focused on the optimization of QoE and energy consumption in multimedia communication in IoV, and proposed a cache allocation algorithm based on artificial intelligence. As the focus of the sustainable development of green IoV, energy management should be integrated into every link of the IoV system.
4. Collaborative Computing in IoV
Emerging applications in the IoV are committed to providing users with efficient, comfortable and secure services and experiences, which requires not only efficient and stable networking and communication schemes, but also more and more computing and storage resources. This is especially true in the IoV with collaborative intelligence applications. While on-board computing and storage capabilities of connected vehicles have been growing rapidly, they are still insufficient for computationally intensive and delay-sensitive tasks. For this purpose, computing tasks are transferred to other nodes with abundant computing resources, such as utilizing cloud computing. However, the centralized cloud computing method shows unstable connection and long propagation delay in the face of the high-speed dynamics of vehicles in the IoV. Even if 5G communication is used, there will be a non-negligible delay. Mobile edge computing, or multiple access edge computing (MEC), has been introduced into IoV to address the problems associated with delay-sensitive applications [70,71].
In the big data environment of IoV, the current solution trend is to consider vehicle–edge–cloud computing collaboration to deal with a large number of complex computing tasks and quickly obtain results. Through the collaboration between the edge and the cloud, the vehicle can transfer the low-latency or low-computation-intensive tasks that were originally processed by the cloud to the edge near the vehicle to compute. In this way, the computing and storage resources of edge devices can be reasonably utilized while reducing the communication overhead. There are many research directions in the collaboration of vehicle, edge, and cloud, such as resource scheduling problems [72], the computing-task offloading problem [73,74], data security [75], the privacy protection problem [76], etc. In addition, studies have discussed the improvement in communication modes and the optimization of perception after the introduction of edge devices into IoV. In article [77], a vehicle clustering algorithm is proposed for routing selection and communication while edge computing devices are deployed in RSU. Dai et al. [78] discusses the problem of object detection under the edge computing framework.
In IoV multimedia applications, Xu et al. [79] discuss how to manage content caching on edge devices according to service requirements to ensure resource efficiency and quality of service, and propose an edge content caching scheme. Based on edge computing, combined with blockchain, Bayesian, and other technologies, Xiao et al. [80] study the problem of fake news detection in the IoV. Xu et al. [81] study estimation of the amount of multimedia services offloaded on edge servers in the future to accurately schedule and reserve the resources of edge devices.
In this section, we will focus on computing task offloading and storage resource management. These two parts are the most important and must be solved in the collaboration of vehicle, edge and cloud. Therefore, we can classify these existing works on collaborative learning technologies into the following two aspects for discussion, as shown in Table 4.

Table 4.
Recent studies on Collaborative Computing in IoV.
Table 4.
Recent studies on Collaborative Computing in IoV.
| Purpose | Publication | Research Summary |
|---|---|---|
| Task offloading | [82] | The cloud–MEC collaborative computing offloading problem is established by co-optimizing computing offloading decision and computing resource allocation. |
| [83] | Intelligence-Sharing MEC framework with aggregation and representation for context features, relationship mining and reasoning, and knowledge transfer among MEC servers is discussed. | |
| [84] | A deep cooperative hierarchical end–edge framework using data communication, computation offloading, and content caching is proposed. | |
| [85] | An edge caching and computing management problem that jointly optimizes service caching, request scheduling, and resource allocation policies is proposed. | |
| [86] | To balance delay and energy usage, a distributed iterative approach to handle multivariable and time-varying channel conditions for computational offloading methods is proposed. | |
| Data storage and cache management | [87] | A cache service registry on mobile entities and a new metric to evaluate the effectiveness of service discovery are proposed. |
| [88] | A collaborative edge caching scheme is proposed, which shares communication, computation, and caching, and co-optimizes content placement and delivery through flexible trilateral cooperation among macro cells. | |
| [79] | An edge content caching method for service demand prediction in the IoV in smart city scenarios is proposed. |
4.1. Big-Data-Oriented Task Offloading
In MEC architecture, the computing tasks of nodes such as vehicles and RSUs are offloaded to nearby devices with idle resources as much as possible. Zhao et al. [82] proposed a collaborative method based on MEC and cloud computing to offload services to cars in vehicle network, which means using cloud resources to provide more computing power to vehicles. By co-optimizing computing offloading decisions and computing resource allocation, the cloud-MEC collaborative computing offloading problem is established. In the Collaborative Computing Offloading and Resource Allocation Optimization scheme, a distributed computing offloading and resource allocation algorithm is designed to achieve the optimal solution, which allows users to request CC resources through their MEC links instead of letting edge servers make decisions. While it can respond quickly when resources are scarce, it is not well suited to tasks with high computational or storage requirements.
The framework proposed by Guo et al. [83] can share the intelligence of different MEC servers to improve their performance. By using MEC and knowledge transfer, the processing speed and accuracy of object detection in different vehicle network scenarios can be significantly improved.
In Ref. [84], it was stated that collaboration among network users can allow them to pool their sensor data and compute results. This eliminates the need for them to manually perform various tasks and increases the efficiency of their networks. One of the most important factors that affects the performance of computation and caching processes is the availability of bandwidth. This allows them to handle large amounts of content efficiently. In order to effectively manage their networks, both cloud and users need to have the necessary edge servers. These servers can help them with content update policy management and broadcast planning.
By simultaneously optimizing service caching, request scheduling, and resource-allocation policies, an online distributed method combining edge caching and computing management is studied in Ref. [85]. It cost-effectively minimizes the time–average service response latency of randomly arriving service requests, leveraging its online and distributed nature to investigate real-time queue sizes and link states. To address the dynamic and unpredictable challenges of virtual cars, the authors utilize Lyapunov optimization, matching theory, and multiplier consensus alternating directions to solve the problem in an online and distributed manner. Specifically, by using fresh data at each time point, the selection algorithm saves critical storage space and maintains generality, but at the cost of additional resource usage.
For collaborative intelligent optimization in the IoV, energy consumption is another issue that needs to be taken into account. Gu et al. [86] proposed the energy efficiency cost-reduction issue to carry out computational offloading in the vehicle edge computing network in order to balance delay and energy usage. In addition, a distributed iterative method is created to deal with multivariable and time-varying channel conditions. Transmission power, offloading and uploading times, decision-making, and processor frequencies are concurrently adjusted to establish a non-local efficient offloading method, which increases computation flexibility while considering the impact of vehicle motion on communication quality.
In order to strike a balance between energy consumption and delay, it is necessary to reasonably schedule the computation tasks requested by users in the vehicle–edge–cloud cooperative system. Ning et al. [89] studied the problem of task scheduling and energy consumption minimization among MECs when MEC devices are deployed on RSUs, and provided a processing model. Considering the power consumption of RSUs and EVs, task offloading based on the connection between the remaining power and the application is the method proposed by Zhai et al. [90]. Specifically, the cost function is established using the weighted sum of MEC energy consumption and the response time of the application, while combining SDN and fog computing to optimize the computational task. In the MEC–cloud collaboration, Michailidis et al. [91] made the Unmanned Aerial Vehicle (UAV) the air relay, combined with the ground RSUs deploying MEC to process the vehicle’s computing tasks, which reduced the processing delay. However, this may increase the energy consumption, so they proposed a multivariate optimization method to efficiently manage the energy of battery-supported RSUs and EVs. Energy issues and sustainable development are significant parts of IoV, which are crucial to the reliability and effectiveness of the system, and will continue to receive attention [92].
In the vehicle–edge–cloud collaboration, some researchers introduce digital twins (DT) to solve the problem of computational task offloading and resource allocation. DT technology establishes a real-time updated and interactive digital copy of the physical world, called a virtual model, which can be applied to mine information and simulate processes to obtain favorable results and feedback on the physical model, so as to achieve the purpose of optimization or provide new visualization services [93]. Liu et al. [94] adopted the power of digital twins to intelligently screen edge devices and offload tasks. Specifically, in the DT network, blockchain technology is utilized to ensure the consistency of information, and then computing devices with good communication quality and reliability are selected to allocate tasks. In order to solve the offloading balancing problem in edge computing of IoV, Xu et al. [95] chose edge computing devices as agents to apply deep reinforcement learning on the basis of DT technology, and the experiment verified that the proposed method could improve the level of service QoS. Another study [96] combined digital twins, game theory, and a distributed incentive mechanism to solve the problem of computing resource allocation from the perspective of energy efficiency and user recognition.
4.2. Data Storage and Cache Management in IoV
Like computing resources, the distribution of storage resources in the IoV is also uneven and increasingly unable to meet the needs of various large data services under collaborative intelligence. Both vehicles, RSUs, and MEC servers have limited storage space. Therefore, it is necessary to dynamically optimize storage data and cache management by fully considering the capacity and usage of storage resources of each node when computing tasks are uninstalled.
In Ref. [87], a cache service registry on mobile entities and a new metric to evaluate the effectiveness of service discovery are proposed. Caching the service registry makes the content discovery process less interactive with the RSUs. The cached contents of vehicles are available to neighbors. This kind of vehicle cache sharing can improve the discovery rate of accessible services and the utilization rate of services. When integrated into the RSUs content caching scheme, users can switch from edge caching to vehicle content acquisition based on density and mobility. This allows for more flexibility in design and is a great advantage for V2X environments.
Qiao et al. [88] proposed a collaborative edge caching scheme, which is a shared framework for communication, computation, and caching. It co-optimizes content placement and delivery through flexible trilateral cooperation among macro cell stations, roadside units, and intelligent vehicles in vehicle edge computing and networking. Data are cached and shared around infrastructure such as vehicles and RSUs in the form of multiple queues. Different strategies are designed for different time scales. The deterministic policy gradient deep learning algorithm is used to compute the optimal solution, which encourages and optimizes content sharing and reduces latency and packet loss.
In the IoV in the smart city scenario, Xu et al. [79] designed E-cache, an edge content caching framework including road side units and base stations. Combined with the deep spatiotemporal residual network, the traffic flow is predicted, and then the future service demand is predicted. This process can be divided into two stages: (1) the historical traffic flows are arranged into traffic flow vectors by a specific data embedding method and then spliced into tensors with different time dependencies. The future service demand is predicted after predicting the future traffic flow through the deep spatiotemporal residual network. (2) Initialize the edge content caching scheme according to the above selection, then modify the crossover and mutation, and select the reference point to get the optimal edge content caching scheme with the shortest executive time and lowest energy usage.
5. Collaborative Learning Technologies
Machine learning and AI have infiltrated various research and application fields since the Renaissance caused by backpropagation algorithms in the 1980s. AI technology with machine learning methods provides more intelligent solutions to improve the efficiency of IoV. With the development of the field of AI, many excellent machine learning methods have been derived, and also applied to the IoV for intelligent decision-making, which can be optimized for different related problems and needs. For example, unsupervised learning, supervised learning, deep reinforcement learning, and federated learning are used to solve specific problems such as path planning, communication routing protocol, task offloading, load balancing, vehicle blockchain, network attack prevention, and resource management based on traffic prediction.
Federated learning is a distributed machine learning method. Under the guidance of a central server, multiple clients use local data to train a model, then aggregate the model parameters of each client in the central server to integrate the knowledge, and then distribute it to each client. Since only intermediate model parameters are sent to the server instead of raw local user data, this is a way to obtain global knowledge under the premise of protecting user privacy.
Ensemble learning completes the learning task by constructing and combining multiple learners; that is, combining multiple weakly supervised models in order to obtain a better and more comprehensive strongly supervised model. The underlying idea of ensemble learning is that even if a weak classifier makes an incorrect prediction, other weak classifiers can correct the error back.
As shown in Figure 6, both federated learning and ensemble learning are distributed learning methods. They are all parallel learning models. However, the difference is that federated learning has the same model regardless of client or server, while ensemble learning has different models. Note that the ensemble learning uses multiple models to generate a better decision, where the data distributed to different models could be different or the same.
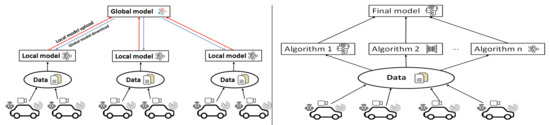
Figure 6.
Learning parallelism (left: data parallelism, the same model; right: model parallelism, different models).
In the following, we provide a detailed discussion of the key learning approaches for collaborative intelligence in IoV, including:
- Federated learning.
- Ensemble learning.
- Supervised learning.
- Reinforcement learning.
5.1. Federated Learning for IoV
Lim et al. [97] discuss FL in detail from the perspectives of communication cost, resource allocation, security and privacy, and applications in mobile edge computing, and point out the challenges and feasible research directions. They believe that FL has strong optimization potential in mobile edge computing, and FL is an important scheme used to realize collaborative machine learning by transforming the centralized cloud computing model into a distributed edge–cloud collaborative computing.
Abreha et al. [98] study the routing protocol, framework, architecture, and hardware requirements of FL, then illustrate its feasibility through two application cases, and explain its advantages and challenges in edge computing from the perspective of engineering applications. The conclusion they come to is that FL is highly suitable for edge computing tasks because it utilizes the data and computing power of edges effectively.
Pokhrel and Choi [99] conduct a theoretical analysis about the latency and loss performance for multiple TCP connections in a Wi-Fi-available vehicular environment, and introduce a FL method to maximize system performances while maintaining the fairness among different TCP flows. Learning models are installed in vehicles, and the learning results are sent to a federal coordinator that is connected to vehicles through RSUs.
Xiong et al. [100] discuss the delay-aware task offloading problem in vehicular edge computing environments, where different types of communication approaches—namely dedicated Short Range Communication (DSRC), cellular vehicle-to-everything (V2X) communication, and millimeter wave (mmWave) communication—are available. In order to efficiently utilize the available communication and computing resources to minimize the task execution delay, they propose a FL-based approach to learn the best allocation policy in complex vehicular environments. Q-learning is used at each FL client to find the local best policies, and the learned results from multiple FL clients are aggregated to deal with different conditions. They use computer simulations to show that the FL-based approach can achieve a higher offloading success rate and better utilization of the communication and computing resources compared to existing baselines.
Fadlullah and Kato [101] consider a aerial–terrestrial networking scenario where the UAVs serve as base stations. They first introduce a distributed heterogeneous computing platform (HCP) integrating UAVs and terrestrial base stations. Then, they propose a two-stage federated learning algorithm to enhance the content caching process. The first stage of local training is conducted at mobile devices, and the second stage of training is conducted at UAVs. HCP aggregates the local models from mobile devices and UAVs to generate the global model.
Zhang et al. [102] discuss the use of federated learning to estimate the intelligence level of computer systems. They propose a vertical federated learning framework to conduct an intelligence ranking of autonomous vehicles without disclosing user data. Experimental results show that the FL-based approach outperforms existing baselines with acceptable time efficiency on both real and simulated data.
Yu et al. [103] discuss the joint communication, computing, and caching resource allocation problem for Ultradense edge computing environments, including smart vehicle systems. They design a DRL approach to minimize the task offloading delay and network resource consumption. A FL approach is also used to train the DRL model in a distributed manner for the purpose of data privacy protection. Experimental results demonstrate the effectiveness of both the DRL and FL.
Shiri et al. [104] consider the control problem of a massive population of UAVs in communication-resource-limited environments. A FL approach is used to distribute the learning process. One UAV is selected as the central unit; the other UAVs are used as FL clients. A neural network model is used at each FL client (UAV). The selection of the central unit is not discussed.
Sun et al. [105] integrates FL technology with digital twin technology for air–ground networks where a drone works as the central server of FL, and ground terminals work as FL clients. Digital twin technology is used to capture network dynamics in the training of the model. Numerical results are used to show the significance of the proposal in terms of learning accuracy and energy efficiency.
In Ref. [106], a FL approach is discussed for image processing applications in vehicular IoT. In addition, a model aggregation method is introduced to improve the accuracy of the global model and minimize the communication overhead for model exchanges. The model aggregation method takes into account the quality of local images, and the computational capability on each candidate for FL client.
Zhang et al. [107] propose a FL-based image classification system for multi-UAV networks. In this system, each UAV updates its local model based on the data from on-board cameras. A ground fusion center aggregates the local machine learning models generated by multiple UAVs to form a global model. The authors use computer simulations to demonstrate that the FL approach is able to reduce the communication cost significantly for a given target test accuracy, compared with the centralized training approach.
Saputra et al. [108] propose a FL-based energy demand prediction method for electric vehicle (EV) networks. In this method, charging stations are the FL clients, and the smart grid provider is the central server aggregating local models. A deep neural network is used as the machine learning model. In addition, taking advantage of the characteristic that charging stations in close geographical locations always have similar numbers of transactions, and similar transaction parameters, they also employ a clustering approach to generate CS clusters in order to reduce the impact of biased prediction results and improve the prediction accuracy.
In Ref. [109], Liu et al. introduce an aerial–ground integrated air-quality-sensing framework using FL based on UAV swarms. This framework includes aerial UAV swarms and ground-sensing systems, where the aerial-sensing part uses UAV cameras and the ground-sensing part uses static monitoring stations. In order to enable collaborative aerial sensing among UAVs from different agencies, UAVs work as FL clients to conduct local training, avoiding the transmission of camera data to other entities. A CNN model is used to learn the mapping between camera data and air-quality level. An UAV is used as the central server, which aggregates the learned model from multiple FL clients.
Thorgeirsson et al. [110] discuss the use of FL in energy demand and driving range prediction for electric vehicles. They consider two different types of learning models, namely, linear regression and neural network. EVs perform training of machine learning models based on local data, and the backend infrastructure (cloud) aggregates the local models to generate the global model. Different driving behaviors are considered by grouping drivers into multiple groups with a clustering technology, where each group defines its own model. They also discuss the effect of different extensions of the federated averaging algorithm on the FL performance.
Wang et al. [111] propose a secure federated learning framework for UAV-assisted crowdsensing applications. The UAVs train local models and send the models to a mobile edge computing (MEC) server, which could be installed on a base station for aggregation. Upon reception of a sensing task request, the MEC server selects a set of UAVs to perform the task. The framework can enable better utilities for UAVs than existing baselines.
Chai et al. [112] propose a hierarchical FL framework for knowledge sharing in IoV based on blockchain technology. Considering the diversity of driving routes and road environments, a hierarchical blockchain is introduced to improve the scalability of the proposed framework in terms of the network size. There are two types of FL clients and two types of blockchains, namely, vehicle client, RSU client, ground chain, and top chain, respectively. First, vehicles act as vehicle clients to train local models and then send the model updates to nearby RSUs. Then, RSUs collaborate with each other to record the model updates to the ground chain. RSU clients use the knowledge stored in the ground train and their own observations to train their models. RSU clients then record the learning results from both RSU clients and vehicle clients to the top chain, for the purpose of exchanging the information with other entities.
Lu et al. [113] propose a scheme for data sharing for IoV based on FL and blockchain technologies. A blockchain approach is employed to ensure the security. Based on the blockchain, an asynchronous FL is introduced to take into account the capability difference in FL clients. The central server selects the FL clients and the corresponding local training parameters in an adaptive approach by considering the capability of FL clients and the dynamic environments.
Yu et al. [114] propose a mobility-aware FL approach for content caching in IoV. Vehicles exchange content caching experience with each other using a FL-based approach, where vehicles are FL clients and RSUs are central servers. Each FL client trains a neural network based on local data related to content caching, and sends the learned experience to a RSU in proximity. A mobility-aware FL client selection approach is also proposed to ensure high-mobility training topology. The client selection considers the channel quality, connection time, and the importance of local data.
Lim et al. [115] propose a FL-based approach to enable distributed machine learning for UAV-Enabled IoV scenarios, including vehicle traffic prediction and parking slot management. A model owner allocates training tasks to UAVs. The whole geographical area is divided into multiple subregions, where each region is allocated to one UAV for training. A multi-dimensional contract-matching-based incentive mechanism is also designed to facilitate the participation of more candidates in the client selection.
Mowla et al. [116] propose a FL-based jamming defense mechanism for flying ad hoc networks. A Q-learning model is used in distributed learning of the best defense policy. Possible movements of UAVs are defined as the actions. UAVs learn the best defense policy by interacting with environments, and the local models are aggregated at an edge computing server such as a base station. By sharing Q-values among multiple UAVs with FL, the convergence speed at each vehicle can be reduced.
Pokhrel and Choi [117] design a blockchain-based decentralized FL approach for IoV. Vehicles act as FL clients, and exchange information with other network entities through a blockchain. The model updates from multiple FL clients are also aggregated by the blockchain network. Without discussing the details of the FL scheme, Ref. [117] discusses the effect of blockchain parameters and wireless channel parameters on the system-level performance.
There are also some studies discussing underlying technologies that better support FL in vehicular environments. Pham et al. [118] consider a FL scenario for mobile devices with limited battery supplies. They propose using UAVs to transfer power to mobile devices to enable sustainable FL-based wireless systems. They focus on UAV resource allocation and UAV placement. Rihan et al. [119] consider some FL-enabled use cases for vehicular IoT, and discuss fog computing architecture for V2X networks. Based on some discussion about the use of deep reinforcement learning (DRL)-based resource allocation and task offloading in vehicular fog computing environments, they also explore the possibility of using FL algorithms to improve the reliability of V2V communications. In Ref. [120], Yang et al. discuss the FL client scheduling problem in mobile networks involving smart phones or vehicles. They develop an analytical model to describe the performance of FL in wireless systems.
Yang et al. [121] propose an over-the-air computation approach to enabling FL in a wireless multiple-access channel. They propose a sparse and low-rank modeling method to facilitate the communication between the FL clients and the central server, allowing more clients to upload their model successfully.
Ng et al. [122] consider a UAV-enabled IoV scenarios where UAVs work as relay nodes to help the communication between a FL client (vehicle) and the central server. They propose a joint auction–coalition formation framework to incentivize UAVs in the forwarding of model updates.
5.2. Ensemble Learning for IoV
Jiang and Yin [123] propose a fault detection approach for vehicular cyber–physical systems based on an ensemble learning scheme. An accurate fault diagnosis requires the support of a large amount of data. However, these data are from different types of sensor devices and show different values in different weather and road conditions. Therefore, the fault detection should consider the variety of sensor data and environments. To conduct a more accurate diagnosis in various conditions, Jiang and Yin use an ensemble learning scheme to improve the adaptability of the fault diagnosis. The procedure of the scheme is as follows. First, different types of sensor information are collected through multiple sensors. Second, the data are processed by multiple models, where each model can recognize a special environmental condition. While each model reflects a limited feature of the whole system, by using the ensemble learning strategy to combine the results from multiple models, the scheme is able to enable more efficient data-driven fault diagnosis in complex vehicular environments.
Alamgir et al. [124] discuss the use of ensemble learning in finding the best modulation and coding scheme (MCS) for communications between underwater vehicles and underwater base stations. They employ the boosting technique, a type of ensemble learning, to analyze a measured sea trial dataset that includes channel parameters under different conditions. They further combine the regression tree technique with a boosting technique to find the best mapping between the MCS level and channel parameters. They claim that their approach can achieve 99.97% accuracy in classifying MCS levels.
Valle et al. [125] use random forests (RF), a well-used ensemble learning method, to better satisfy different service requirements, including extra-low latency and large throughput, in different vehicular scenarios. They consider a heterogeneous network scenario that includes multiples types of networks, including cellular communications through a base station, cellular V2V, and IEEE 802.11p. The objective of the ensemble learning method is to find the best available network according to the current vehicular environment and application requirements. The RF algorithm constructs multiple trees, where each tree is generated by parts of parameters (features) of the data. By using the RF algorithm, Ref. [125] is able to build an efficient system by making a decision based on the knowledge from multiple trees, which is not possible by a single simple algorithm.
Zhang et al. [126] use an ensemble learning approach in real-time driver behavior recognition tasks. They employ a deep CNN with multiple inputs, namely, side video streams, side optical flows, front video streams, and front optical flows, where each input is a weak classifier but has its own advantages in extracting some special features. By merging four different classifiers with the ensemble learning approach, Ref. [126] can improve the classification accuracy compared with existing baselines with low computational complexity.
Making a good prediction about the future network status and user traffic patterns is essential when it comes to providing successful network resource allocation in complex environments. In Ref. [127], Ferreira et al. discuss the use of ensemble learning in forecasting network performance metrics for fifth-generation (5G) networks. They propose a real-time distributed framework that uses multiple algorithms to make better forecasting. They show that an ensemble of multiple good algorithms can achieve a better prediction for different performance metrics. A vehicular network dataset in Porto, Portugal, is used to evaluate the performance of the framework.
Raja et al. [128] use an ensemble learning approach to enable an efficient intrusion detection system in vehicular ad hoc networks (VANETs). They consider the privacy protection of vehicle data and propose a collaborative approach based on private classifiers that are installed on each vehicle. While each vehicle is a weak classifier, using the communications among neighboring vehicles, the results from multiple vehicles are merged with an ensemble learning method, resulting in a much better intrusion detection system. Simulation results show that the ensemble classifier can achieve 96.94% accuracy without violating the user’s privacy.
In Ref. [129], an ensemble learning approach is applied in the path prediction of obstacle vehicles for the purpose of enabling a more advanced driver assistance system. Three different types of sensor data—namely, light detection and ranging (LiDAR), camera, global positioning system (GPS)—are considered trained by the ensemble learning. A recurrent neural network (RNN) is combined with ensemble learning to capture temporal behaviors of vehicles and environments. The authors show that the ensemble learning can improve the robustness of prediction with a network model of small size, which ensures its validity in dynamic road scenarios.
Toprak et al. [130] discuss the pedestrian detection problem in railway driver support systems where existing object detection technologies do not work well. They propose a three-stage system based on ensemble learning. In the first stage, various non-deep feature-classifier models are used to generate bounding boxes. Based on the results of the first stage, the second stage applies multiple deep CNN models to generate multiple individual adapted classification results. The final stage employs an ensemble learning method to combine the individual results to find a better detection result. The ensemble-learning-based system can significantly improve the detection accuracy as compared with well-used existing models.
Zhao et al. [131] propose an ensemble-learning-based approach for short-term vehicle traffic prediction. They use an ensemble learning model with the long short-term memory (LSTM) technique. The approach consists of two stages. In the first stage, different LSTM models repressing different effects of different time lags on the prediction are trained separately. In the second stage, ensemble learning is used to determine the weight coefficient of each LSTM model, and combine different models to make the final decision. They apply six different highway traffic datasets from Seattle, USA, to show that the ensemble-learning-based approach could perform better than six existing traffic flow prediction models.
Zhang et al. [132] propose WBELA, a weight-based ensemble learning algorithm, for intrusion detection in heterogeneous vehicular environments by identifying abnormal messages in the controller area network bus network. They use support vector machine (SVM), K-neighborhood (KNN), and decision tree (DT) methods as the basic classifiers. First, the CAN messages are processed by the basic classifiers for preclassification. Based on the preclassification results, an ensemble learning algorithm is used to optimize the weight of each classifier in order to reach the maximal accuracy and minimal errors. Simulation results are presented to show the advantage of the algorithm as compared with existing baselines in terms of precision and false positive rate.
For the purpose of enabling context-aware computing of smartphone applications, Alotaibi [133] discusses the problem of transportation mode detection of smartphone users, and proposes a method based on an ensemble learning algorithm. The method uses three different basic classifiers, specifically, random forests (RF), gradient boosting (GB), and decision trees (DT). Each classifiers votes independently, and the ensemble learning algorithm makes a better prediction by taking the majority vote of these three classifiers. The simulation results show that the method can achieve better results compared with existing human activity recognition approaches to classifying different transportation modes, namely, walking, standing, riding a train, driving a car, and riding a bus.
Wang et al. [134] propose an ensemble-learning-based method for traffic congestion detection in complex scenarios. The method first uses multiple deep neural networks to extract features from the data. In order to consider different levels of features, including low-level, middle-level, and high-level features, hierarchical feature extraction networks are employed. After that, based on the results from multiple networks, an ensemble learning approach is used to further improve the detection accuracy and generalization ability. Simulation results demonstrate that the deep learning ensemble can achieve a better performance compared with single estimator in complex scenarios.
5.3. Clustering with Unsupervised Learning
While k-means algorithm or its extensions are widely used, there are also some other clustering approaches. Here, we first discuss the use of k-means algorithms for IoV, and then show the applications of other clustering techniques.
Yousif et al. [135] discuss a license plate (LP) recognition problem where multiple types of LPs, namely Arabic–Egyptian license plates and English license plates, are considered. A k-means clustering algorithm is applied to segment the LP characters. Experimental results show that their approach can achieve higher recognition accuracy than existing alternatives.
Pustokhina et al. [136] present a deep-learning-based license plate recognition model that uses a k-means algorithm in character segmentation, and uses CNN in character recognition. Experimental results on three different datasets show the advantage of the model compared with existing baselines.
Yang et al. [137] study the challenges in recognizing the decision-making style of a driver. They introduce an approach that integrates an unsupervised learning approach, specifically, a k-means algorithm, with a supervised learning approach, a k-nearest neighbor (KNN) algorithm. They demonstrate that their approach can improve the traditional KNN algorithm with 72.67% faster recognition time and can shorten the recognition time by more than 72.67%, with higher accuracy.
Rong et al. [138] discuss the challenges of simultaneous localization and mapping in mobile environments, and employ a k-means algorithm to conduct image segmentation for the purpose of better processing dynamic regions. They use experiments to demonstrate the validity of the approach in terms of trajectory accuracy and computing speed.
Bhaumik et al. [139] discuss the clustering problem of a channel impulse response for 60 GHz mmWave multipath channels in vehicular environments. Considering that the performance of the k-means algorithm is dependent on the value of k, they combine the k-means algorithm with a time–amplitude clustering algorithm to group multipath components based on their time delays and amplitudes.
Gedschold et al. [140] discuss a similar multipath clustering problem in vehicle-to-infrastructure (V2I) channels. They employ a variant of the k-means algorithm, namely, K-Power-Means, to conduct the clustering of multipath components. An algorithm is also used to find the best number for clusters before conducting the clustering.
Song et al. [141] study the multi-hop broadcast issue in VNs, which is considered to be useful for disseminating safety-related messages. They introduce a vehicle-clustering-approach-based k-means algorithm. The selected cluster heads are used as forwarder nodes in multi-hop broadcasting. The geographical position of vehicles and inter-vehicle distance are considered in the clustering algorithm. Since the signal quality and vehicle mobility are not discussed in the clustering algorithm, this clustering algorithm requires an enhancement for handling complex vehicular environments.
Sliwa et al. [142] discuss the data transfer problem in for delay-tolerant vehicular applications, such as environmental map construction, traffic monitoring, weather sensing, and so forth. They define some geographical regions as black spots where the transmission rate should be reduced due to insufficient communication capability. Based on vehicular big data, a k-means algorithm is used to conduct clustering of black spots.
Shehzad et al. [143] consider the use of UAVs to improve the communication performance between small cell base stations. The focus on the optimal placement of UAVs for the purpose of serving more small cell base stations. A k-means algorithm is used to solve the problem by considering multiple metrics such as the achievable data rate, available bandwidth, and the capability of UAVs. Numerical results are used to show the superiority of the algorithm over the conventional approach in terms of the achievable data rate and spectral efficiency.
Hoang et al. [144] consider a wireless authentication system that uses UAVs as relay nodes. They discuss the problem of how to detect eavesdropping attacks targeting UAVs. They build a detection model combing one-class support vector machines (OC-SVM) with k-means clustering. Numerical results are presented to show the proposed model in terms of stability.
Targeting for mobile communication systems for high-speed trains and vehicles, Albakay et al. [145] propose an improved k-means algorithm for estimate frequency offset from the in-phase and quadrature constellation of the received signal. They divide the received signal symbols into multiple groups and find the centroid of each group using the modified k-means algorithm. The algorithm is able detect the constellation rotation within a range between −45 degrees and 45 degrees for QPSK signals with additive white Gaussian noise.
He et al. [146] consider a drone-aided emergency communication network in post-disaster scenarios, and employ a modified k-means algorithm to solve the drone deployment problem with the aim of minimizing power consumption of drones while satisfying user requirements regarding the transmission speed. The k-means algorithm is used to find the optimal number, altitude, and transmit power of drones.
Ye et al. [147] discuss the effect of vehicle density on the communications in VANETs, and propose using a clustering approach to reduce the packet collisions in VANETs. They use an improved k-means algorithm to group vehicles into different clusters by considering the similarities in movements, vehicle location, and inter-vehicle distance. Based on the vehicle clusters, a message distribution mechanism is designed. Computer simulations are used to show that the mechanism can achieve a higher packet delivery ratio and lower latency compared with existing baselines.
Different vehicular applications possibly exhibit different levels of service requirements. Network slicing is a promising technology for fulfilling the service requirements involving a large amount of diversity. Cui et al. [148] propose a k-means++ algorithm to group the services into different clusters based on the service-level agreement—including the capacity, coverage area, and QoS requirements—between the service provider and customer. Based on the clustering results, different network slices are provided to different groups of services.
Ozasa et al. [149] consider a communication network where UAVs act as base stations, providing wireless communications services to other terminals. They discuss the joint UAV placement and frequency division problem in multi-UAV environments. A k-means algorithm is used to derive the best horizontal arrangement of UAVs. The frequency division is conducted after the clusters are generated.
Wahlstrom et al. [150] study the smartphone placement problem for smartphone-based driver monitoring. They use a kernel-based k-means clustering approach to infer the placement of smartphones within vehicles (the position of the smartphone with respect to the vehicle). They argue that knowing the placement of the smartphone could provide benefits in many scenarios, such as accident reconstructions and improving driving behaviors.
Yuan et al. [151] study the modeling of the driving cycle of a city tour bus. The driving cycle construction is useful for evaluating vehicle performance and measuring fuel consumption. As the conventional k-means algorithm is sensitive to its initialization parameters, an improved version of k-means—namely, GA-K-means—integrates a genetic algorithm. The GA-K-means algorithm groups micro-trips, specifically, an excursion between two successive time points at which the vehicle is stopped. They further combine GA-K-means with a hidden Markov model to construct the driving cycle of city tour buses in Beijing.
Forster et al. [152] study how to identify multiple characteristic driving cycles from vehicle data representing real driving scenarios. They use a k-means algorithm to find k groups of micro trips to represent different driving cycle features. They show that by choosing only one parameter, k, the k-means algorithm can achieve a scalable solution for different granularities of driving scenarios.
In Ref. [153], the density-based spatial clustering of applications with noise algorithm is employed to design an adaptive clustering scheme for low-power base stations in coordinated multipoint transmission and reception operation. They show that DBSCAN has advantages in identifying geographically isolated low-power base stations and improving system throughput compared with the k-means algorithm.
For the purpose of enabling more intelligent traffic monitoring, Cao et al. [154] discuss the lane determination of vehicles based on millimeter-wave radar data. They propose a kernel line segment adaptive possibilistic c-means clustering algorithm to achieve better clustering. KLSAPCM is able to conduct efficient clustering without knowing the position and angle of the radar. The experimental results are used to show the advantage of KLSAPCM in a lane determination problem over other clustering algorithms, including DBSCAN and k-means algorithms.
In Ref. [155], hierarchical clustering is employed for anomaly detection in VANETs. The anomaly detection is conducted at a roadside unit without revealing the content of user traffic. The anomaly detection also uses dynamic time warping in distance measurement.
Chen et al. [156] discuss the driving cycle prediction problem for hybrid electric vehicles. They employ a k-shape clustering algorithm to group the driving cycle data into six different groups. Simulation results are used to show that the k-shape algorithm performs better than k-means in this problem.
5.4. Reinforcement Learning
In order to achieve a more accurate understanding of the complex vehicular environments, a vehicle has to utilize the information received from other vehicles in the vicinity. However, the vehicle has to ensure that whether the messages received from other vehicles are trustworthy or not. If the messages include fake or misleading information, the perception accuracy degrades drastically, possibly resulting in a fatal error. Therefore, the trust management in vehicular environments is an important consideration for achieving a good decision. Guo et al. [157] propose a context-aware trust management model in VANETs. The context includes internal information, specifically the information collected from the local sensor (the sensor devices installed on the current vehicle), and external information received from other vehicles. A Q-learning-based approach is proposed to set the weights of the internal and external information in making the final decision. The information entropy theory is used in the trust calculation. Simulation results show that the model can achieve a higher precision for trust evaluation with reasonable commotional and communication overhead.
Multi-agent reinforcement learning (MARL) is widely used in vehicular IoT to enable an efficient system in a distributed manner. However, the coordination among vehicles in a dynamic environment is particularly challenging. Yu et al. [158] formulate the coordination problem by using a dynamic coordination graph. They propose coordination-graph-based MARL approaches to optimize the joint maneuvers of multiple vehicles. Experimental results are presented to show the performance of the proposed approaches in the decision making surrounding following or overtaking in highway situations to enable high-level strategic control of vehicles.
Zhou et al. [159] consider the decentralized control of multiple robots, such as UAVs, for patrolling in partially observable environments with unknown prior knowledge. For example, for a post-disaster scenario, while an UAV can patrol continuously over the disaster area and collect information by coordinating with other UAVs, the decentralized control of multiple UAVs is challenging due to the environment, which is unknown and only partially observable for each UAV. The authors formulate the problem as a Bayes-adaptive transition-decoupled partially observable Markov decision process, and propose a Bayesian RL algorithm to improve the coordination and planning process of multiple robots. The experimental outcomes indicate that the proposed algorithm performs better than the existing methods.
It is important to consider stability and efficiency in the design of a RL algorithm, especially for IoV applications, which require ultra-high reliability. Zhang et al. [160] propose a deterministic promotion RL algorithm approach that improves policy evaluation in critique and exploration in action. The action exploration in the proposed algorithm is conducted by a normalization-based evaluation approach in a way that can increase efficiency and decrease the dependencies among the explored actions. They use both computer simulations and real-world experiments to show the advantage of the proposed algorithm in a longitudinal velocity control scenario for vehicular environments.
In Ref. [161], Feng and Haykin discuss the jamming problem in vehicular networks. They investigate anti-jamming V2V communications based on joint control of power and channel selection. The problem is formulated as a multi-armed bandit problem, and a RL-based approach is tailored to solve the problem. Extensive simulations are conducted to show the performance of the approach in terms of multiple performance metrics, including power strategy, channel selection, and throughput.
Xing et al. [162] discuss the importance of trust evaluation in intrusion detection systems. They argue that the trust evaluation of vehicles should be conducted not only by RSUs, but also by the vehicles in the vicinity. However, in order to achieve a trust evaluation based on the collaboration of a large portion of vehicles, an efficient incentive mechanism is required. Therefore, the authors propose a RL-based incentive mechanism to involve the participation of more vehicles. They use computer simulations to show that the mechanism can achieve a higher detection ratio than the conventional approach.
Kapoor et al. [163] discuss the user association problem for small cell dense VNs, where a vehicle could possibly connect to multiple small cell base stations. The mobility of vehicles result in handovers between different base stations, which makes the user association policy—specifically, which base station to connect with at a particular time—very important. In Ref. [163], the authors propose a signal-quality-aware user association algorithm based on Q-learning, a form of RL. The algorithm is able to make a tradeoff between the number of handovers and system performance while guaranteeing the QoS requirements.
Zhou et al. [164] discuss the radio resource allocation at base stations in VNs. They define a Q-learning model where the state is the uplink and downlink data rate against aviate channel resource. The action is the ratio between the resource allocated for uplink and downlink data transmission. The reward is defined based on multiple network status parameters. By using the Q-learning algorithm, Ref. [164] is able to consider the future reward for a resource allocation policy, which can provide a solution with long-term efficiency.
Wu et al. [165] propose a RSU-assisted routing protocol for VANETs based on Q-learning. They use a three-phase routing algorithm. In the first phase, a packet is forwarded from the source node to a nearby RSU. In the second phase, the packet is forwarded between RSUs. In the last phase, the packet is delivered to the destination from a RSU to the destination. Hello messages are used to exchange information among neighbors and update Q-table.
Samir et al. [166] consider a scenario in which UAVs act as relay nodes to improve the coverage of cellular infrastructure. A reinforcement-learning-based approach is proposed to optimize the trajectories of multiple UAVs while minimizing the number of deployed UAVs and energy consumption. The learning is conducted at the central unit that interacts with other network entities to update the model. Numerical results are used to demonstrate the advantage of the RL-based approach over existing baselines.
Raja et al. [167] discuss the communication gateway selection problem in a multi-access vehicular environment where multiple types of radio access technologies, including Wi-Fi and cellular communication, coexist. They propose a Q-learning-based approach to support each vehicle to select the best gateway nodes among a cellular base station and multiple RSUs where RSUs are connected with vehicles through a Wi-Fi interface. In the learning model, the state is defined by the distribution of vehicles, and the action is the selection of the gateway. While each vehicle is a learning agent, the real learning process is conducted a centralized server, and the software defined network (SDN) technology is used to achieve centralized control of the entire vehicular network.
There are some studies which discuss the use of reinforcement learning in improving vehicle path planning. Cao et al. [168] propose a Q-learning algorithm to minimize the delay in transportation. In the Q-learning algorithm, the action is the driving direction, and Q-value represents the probability of satisfying the deadline constraint in transportation. They use both artificial transportation networks and real road networks in Beijing, Munich, and Singapore to evaluate the efficiency of the proposed algorithm.
Zhang et al. [169] propose a RL-based scheme for route planning for hybrid electric vehicles for the purpose of finding the route with minimum energy consumption. The RL model is defined as follows. The state is represented by a vector consisting of vehicle position, power demand, vehicle velocity, and the state of charge for battery. The action is represented by a vector that consists of output torque from engine, gear selection, and direction. The reward is defined based on the energy recuperation level. They conduct computer simulations by using Toyota Prius as the vehicle model, and evaluate the performance of the proposed approach for various navigation tasks.
6. Discussion of Future Research Directions
The rapidly growing paradigm trend of Internet of Vehicles predicts that it will gain attention and development in many fields and industries in the next decade. The main goal of applying collaborative intelligence ideas and technologies to the field of IoV is to integrate the data and resources of a large number of vehicles, users, infrastructure, and networks, providing systems with reliability and connectivity that are easy to manage, control, and operate. Due to the dynamic nature of vehicles, the diversity of devices, the low time delay requirements of applications, and the connectivity of V2X, various special requirements are put forward for the collaboration of this complex system. However, these aspects bring new technical challenges to the design and expansion of the IoV field. Important future research directions that will help to conquer those challenges are presented in Figure 7, as follows:
- Big Data Management: In IoV under collaborative intelligence, multiple types of smart devices generate a large amount of data, which are stored locally or in the cloud. Network latency and insufficient storage affect computation and analysis, and may even break the system. Therefore, the real-time management and analysis of IoV big data has always been a challenge, but will also be a challenge in the future. (1) Comprehensive awareness of the environment: Fusing sensor data and historical knowledge in the collaborative network provides comprehensive awareness of the environment for the whole system and each entity, so as to improve the accuracy and security of decision making. (2) Storage and preprocessing of big data: Effectively utilizing the storage capacity of edge nodes and cloud data centers to further compress the increasing massive data and eliminate a large amount of redundancy is another important research direction. (3) Data transmission and unified standards: In the case of vehicle movement and low latency, big data have more stringent requirements on communication, so reducing the amount of transmitted data and improving communication efficiency is inevitable. Research on more reasonable communication protocols, design of edge computing models with a small amount of data transmission, and use of semantic communication to compress data are all directions which researchers can make further efforts to explore. Furthermore, establishing a unified transmission standard and increasing investment in infrastructure can greatly accelerate the development of IoV.
- Sparse Data: Since most collaborative intelligence requires machine learning methods that are data-driven or interact with the environment, a large amount of training data will be used to train a model for a certain task. This puts forward high requirements for data collection and processing, but some tasks make it difficult to collect corresponding high-quality data in reality, resulting in the problem of data sparsity. In order to overcome this problem, many studies use realistic simulators to generate simulated data for model training, and then transfer to real data to fine-tune the model. On the other hand, the learning model is built and adjusted, or other intelligent methods are combined to optimize the training effect. In addition, expanding the scope of collaboration and deepening the cooperation in collaboration can alleviate the problem of data sparsity to a certain extent. This is also an aspect to which future researchers can devote their energy.
- Stability: Vehicles are dynamic in nature, and the network topology of IoV also changes at any time, so stability is also a major challenge in this field. The stability is reflected in the network connectivity, and the data and signal transmission between agents need high-quality communication capabilities. Although there are many research studies on the cooperative communication of Internet of Vehicles, the Internet facilities for Internet of Vehicles or Internet of Things are not perfect in most areas, and it will take some time to achieve coverage of 5G and the development of 6G. Therefore, the real realization of collaborative intelligent communication in the Internet of Vehicles still needs efforts.
- Reliability: Applications related to intelligent transportation and UAV detection are usually sensitive to safety, because such applications require high reliability, otherwise there will be serious losses of life and property. In the application of Internet of Vehicles, reliability is an important issue due to the large scale of the network, complex computing architecture, and poor network stability.
- Different Purposes, Different models: Collaborative intelligent models based on machine learning are widely used in Internet of Vehicles tasks and have achieved good results, such as reinforcement learning, federated learning, centralized learning, etc. However, in different tasks and objectives, different learning models and methods are usually used. The data demand is large, the processing is tedious, the model parameters are particularly large, the training time is long, and the model is not universal. In future research, this problem can be optimized from two perspectives. (1) Building a unified large model that integrates data and is suitable for multi-class tasks after a simple fine-tuning process. (2) Constructing different models for different purposes to refine tasks and achieve better results.
- Safety: Safety is one of the core challenges in the field of Internet of Vehicles. It is a network that is connected by a variety of devices and integrates different technologies and standards through the Internet to achieve collaborative intelligence. Not only must infrastructure such as roadside units, cloud storage centers, and computing centers be connected to the network, but also most of the vehicle’s devices such as GPS, cameras, sensors, brakes, and accelerators may be accessed remotely. So if the network security is not in place, the attacker may control a large number of network devices or even directly control the vehicle, leading to serious consequences. At present, IoV is not completely secure against all kinds of attacks, such as quantum attacks. Therefore, the discovery and repair of security vulnerabilities, and even the establishment of a more perfect security system are indispensable challenges in the future.
- Privacy Protection: In V2X network, the everything-connected network will create the problem of data and privacy exposure. How to protect user privacy and data is also a very recent concern, including the application of federated learning and blockchain technology in IoV collaboration. The most popular solution in this regard is to use federated learning and blockchain technology, which can avoid the direct transmission of original user data to make task decisions and take advantage of the decentralization and tamper-proof characteristics of blockchain to improve the privacy protection ability. However, the cost of applying these technologies in IoV collaboration is not low, and there are unsolved difficulties.
- Convergence: The problem of training efficiency of machine learning models is often involved in coordinated intelligence methods. Under the strict service requirements of high security, stability and low latency, methods that help the model achieve higher learning accuracy and faster convergence speed are worthy of further improvement.
- Combination with other approaches: At present, the method of deep learning is widely used to realize the collaborative intelligence of Internet of Vehicles, and has achieved good results. On this basis, other effective ideas and approaches, such as fuzzy logic, semantic communication, and digital twins, can be combined to further optimize the task results.
- Seamless integration into the IoT in future: As a part of the future Internet of Things, the Internet of Vehicles must be integrated into the smart city and other next-generation Internet of Everything environment, such as Industry 5.0. Therefore, we believe that the development of IoV technology and the deployment of practical applications should also consider integration and collaboration with other fields, such as smart healthcare. At the same time, the collaboration with human needs to be paid more attention to lay the foundation for providing users with more personalized services.
Figure 7.
Several valuable future research directions of Iov with CI.
7. Conclusions
With the development of Artificial Intelligence, distributed computing, supercomputers, hardware such as GPU and other technologies, autonomous driving under the Internet of Vehicles, and even smart cities under the Internet of everything will certainly become a reality in the near future. In the following emerging applications and services, collaborative intelligence will play an important role because it can integrate the knowledge and capabilities of multiple smart devices, including data, communication, computing, and storage resources. With the increasing interest in collaborative intelligence schemes from both industry and academia, it is particularly important to explore their research in the context of vehicle-borne IoT. In this paper, we discussed the existing research, technical challenges, possible solutions, and open problems of CI for IoV applications. This paper first briefly introduced IoV and the CI problem in IoV, and then expounded its advantages and challenges in the wireless Internet of Things environment. Then, from the aspects of collaborative communication, collaborative computing, and collaborative learning methods, the existing research on the application of CI methods in vehicle-borne Internet of Things was reviewed, and the technical problems were discussed. Finally, the future research direction of the integration of CI and IoV was discussed to accelerate the research process of IoV.
Author Contributions
Conceptualization, S.D. and C.W.; methodology, S.G.; formal analysis, J.B.; investigation, G.H.; writing, original draft preparation, S.D. and J.B.; writing, review and editing, C.W. and G.H.; supervision, C.W.; project administration, S.D. and C.W.; funding acquisition, G.H. and C.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundation of China under Grant No. 62062031, in part by Inner Mongolia natural science foundation grant number 2019MS06035, in part by ROIS NII Open Collaborative Research 22S0601, and in part by JSPS KAKENHI grant numbers 20H00592 and 21H03424.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| AC | Actor–Critic. |
| AI | Artificial Intelligence. |
| CI | Collaborative Intelligence. |
| CNN | Convolutional Neural Network. |
| C-V2X | Cellular Vehicle to Everything. |
| DSRC | Dedicated Short Range Communication. |
| DT | Decision Tree. |
| EV | Electric Vehicle. |
| GB | Gradient Boosting. |
| GPS | Global Positioning System. |
| HCP | Heterogeneous Computing Platform. |
| HVN | Heterogeneous Vehicle Network. |
| IoT | Internet of Things. |
| IoV | Internet of Vehicles. |
| ITS | Intelligent Transportation System. |
| IV | Intelligent Vehicles. |
| KNN | K-Neighborhood. |
| LiDAR | Light Detection and Ranging. |
| LP | License Plate. |
| LSTM | Long Short-Term Memory. |
| MARL | Multi-Agent Reinforcement Learning. |
| MCS | Modulation and Coding Scheme. |
| MEC | Mobile Edge Computing. |
| MIMO | Multiple-Input Multiple-Output. |
| mmWave | Millimeter Wave. |
| NFC | Near Field Communication. |
| NSs | Network Slices. |
| QoS | Quality of Service. |
| RAT | Radio Access Technology. |
| RF | Random Forests. |
| RSU | Roadside Unit. |
| SDN | Software Defined Network. |
| SVM | Support Vector Machine. |
| UAVs | Unmanned Aerial Vehicles. |
| V2I | Vehicle-to-Infrastructure. |
| V2N | Vehicle-to-Cloud/Edge. |
| V2P | Vehicle-to-Pedestrian And Cyclist. |
| V2R | Vehicle-to-Road. |
| V2V | Vehicle-to-Vehicle. |
| VANET | Vehicular Ad Hoc Network. |
| VN | Vehicular Network. |
| WLAN | Wireless Local Area Network. |
References
- Xu, X.; Lu, Y.; Vogel-Heuser, B.; Wang, L. Industry 4.0 and Industry 5.0—Inception, conception and perception. J. Manuf. Syst. 2021, 61, 530–535. [Google Scholar] [CrossRef]
- Chen, C.; Liu, L.; Wan, S.; Hui, X.; Pei, Q. Data Dissemination for Industry 4.0 Applications in Internet of Vehicles Based on Short-term Traffic Prediction. ACM Trans. Internet Technol. 2021, 22, 1–18. [Google Scholar] [CrossRef]
- Loke, S.W. Cooperative Automated Vehicles: A Review of Opportunities and Challenges in Socially Intelligent Vehicles Beyond Networking. IEEE Trans. Intell. Veh. 2019, 4, 509–518. [Google Scholar] [CrossRef]
- Kang, Y.; Hauswald, J.; Gao, C.; Rovinski, A.; Mudge, T.; Mars, J.; Tang, L. Neurosurgeon: Collaborative Intelligence Between the Cloud and Mobile Edge. ACM SIGARCH Comput. Archit. News 2017, 45, 615–629. [Google Scholar] [CrossRef]
- Eshratifar, A.E.; Abrishami, M.S.; Pedram, M. JointDNN: An Efficient Training and Inference Engine for Intelligent Mobile Cloud Computing Services. IEEE Trans. Mob. Comput. 2021, 20, 565–576. [Google Scholar] [CrossRef]
- Storck, C.R.; Duarte-Figueiredo, F. A Survey of 5G Technology Evolution, Standards, and Infrastructure Associated with Vehicle-to-Everything Communications by Internet of Vehicles. IEEE Access 2020, 8, 117593–117614. [Google Scholar] [CrossRef]
- Xu, X.; Li, H.; Xu, W.; Liu, Z.; Yao, L.; Dai, F. Artificial intelligence for edge service optimization in Internet of Vehicles: A survey. Tsinghua Sci. Technol. 2022, 27, 270–287. [Google Scholar] [CrossRef]
- Sakiz, F.; Sen, S. A survey of attacks and detection mechanisms on intelligent transportation systems: VANETs and IoV. Ad Hoc Netw. 2017, 61, 33–50. [Google Scholar] [CrossRef]
- Ali, E.S.; Hasan, M.K.; Hassan, R.; Saeed, R.A.; Hassan, M.B.; Islam, S.; Nafi, N.S.; Bevinakoppa, S. Machine Learning Technologies for Secure Vehicular Communication in Internet of Vehicles: Recent Advances and Applications. Secur. Commun. Netw. 2021, 2021, e8868355. [Google Scholar] [CrossRef]
- Hbaieb, A.; Ayed, S.; Chaari, L. A survey of trust management in the Internet of Vehicles. Comput. Netw. 2022, 203, 108558. [Google Scholar] [CrossRef]
- Siddiqui, S.A.; Mahmood, A.; Sheng, Q.Z.; Suzuki, H.; Ni, W. A Survey of Trust Management in the Internet of Vehicles. Electronics 2021, 10, 2223. [Google Scholar] [CrossRef]
- Bangare, S.L.; Prakash, S.; Gulati, K.; Veeru, B.; Dhiman, G.; Jaiswal, S. The Architecture, Classification, and Unsolved Research Issues of Big Data extraction as well as decomposing the Internet of Vehicles (IoV). In Proceedings of the 2021 6th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 7–9 October 2021; pp. 566–571. [Google Scholar]
- Ji, B.; Zhang, X.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. Survey on the Internet of Vehicles: Network Architectures and Applications. IEEE Commun. Stand. Mag. 2020, 4, 34–41. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Din, S.; Jeon, G.; Piccialli, F. Internet of Vehicles: Key Technologies, Network Model, Solutions and Challenges with Future Aspects. IEEE Trans. Intell. Transp. Syst. 2021, 22, 1777–1786. [Google Scholar] [CrossRef]
- Al-Heety, O.S.; Zakaria, Z.; Ismail, M.; Shakir, M.M.; Alani, S.; Alsariera, H. A Comprehensive Survey: Benefits, Services, Recent Works, Challenges, Security, and Use Cases for SDN-VANET. IEEE Access 2020, 8, 91028–91047. [Google Scholar] [CrossRef]
- Ang, L.-M.; Seng, K.P.; Ijemaru, G.K.; Zungeru, A.M. Deployment of IoV for Smart Cities: Applications, Architecture, and Challenges. IEEE Access 2019, 7, 6473–6492. [Google Scholar] [CrossRef]
- Elmoiz Alatabani, L.; Sayed Ali, E.; Mokhtar, R.A.; Saeed, R.A.; Alhumyani, H.; Kamrul Hasan, M. Deep and Reinforcement Learning Technologies on Internet of Vehicle (IoV) Applications: Current Issues and Future Trends. J. Adv. Transp. 2022, 2022, e1947886. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zhao, J.; Niyato, D.; Guan, Y.L.; Yuen, C.; Sun, S.; Lam, K.-Y.; Koh, L.H. Blockchain for the Internet of Vehicles Towards Intelligent Transportation Systems: A Survey. IEEE Internet Things J. 2021, 8, 4157–4185. [Google Scholar] [CrossRef]
- Jamil, S.; Rahman, M. Fawad A Comprehensive Survey of Digital Twins and Federated Learning for Industrial Internet of Things (IIoT), Internet of Vehicles (IoV) and Internet of Drones (IoD). Appl. Syst. Innov. 2022, 5, 56. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Ma, O.; Ansari, M.S.; Almalki, F.A. Survey on Collaborative Smart Drones and Internet of Things for Improving Smartness of Smart Cities. IEEE Access 2019, 7, 128125–128152. [Google Scholar] [CrossRef]
- Muza, A.J.M.; Kamarulzaman, S.F.; Rahman, M.A.; Murad, S.A.; Kamal, M.A.S.; Alenezi, A. Multiple Vehicle Cooperation and Collision Avoidance in Automated Vehicles: Survey and an AI-Enabled Conceptual Framework. 2022. Available online: https://www.researchsquare.com/article/rs-1676811/latest.pdf (accessed on 11 July 2022). [CrossRef]
- Bajić, I.V.; Lin, W.; Tian, Y. Collaborative Intelligence: Challenges and Opportunities. In Proceedings of the ICASSP 2021–2021 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Virtual, 6–12 June 2021; pp. 8493–8497. [Google Scholar]
- Ha, D.; Tang, Y. Collective Intelligence for Deep Learning: A Survey of Recent Developments. arXiv 2022, arXiv:2111.14377. [Google Scholar] [CrossRef]
- Zhou, H.; Xu, W.; Chen, J.; Wang, W. Evolutionary V2X Technologies Toward the Internet of Vehicles: Challenges and Opportunities. Proc. IEEE 2020, 108, 308–323. [Google Scholar] [CrossRef]
- Siriwardhana, Y.; Porambage, P.; Liyanage, M.; Ylianttila, M. A Survey on Mobile Augmented Reality with 5G Mobile Edge Computing: Architectures, Applications, and Technical Aspects. IEEE Commun. Surv. Tutor. 2021, 23, 1160–1192. [Google Scholar] [CrossRef]
- Sharma, S.; Kaushik, B. A survey on internet of vehicles: Applications, security issues & solutions. Veh. Commun. 2019, 20, 100182. [Google Scholar] [CrossRef]
- Malik, S.; Rana, A. Internet of Vehicles: Features, Architecture, Privacy, and Security Issues. In Internet of Things: Security and Privacy in Cyberspace; Saxena, S., Pradhan, A.K., Eds.; Transactions on Computer Systems and Networks; Springer: Singapore, 2022; pp. 189–208. ISBN 978-981-19158-5-7. [Google Scholar]
- Cui, G.; Zhang, W.; Xiao, Y.; Yao, L.; Fang, Z. Cooperative Perception Technology of Autonomous Driving in the Internet of Vehicles Environment: A Review. Sensors 2022, 22, 5535. [Google Scholar] [CrossRef]
- Ansari, K. Joint use of DSRC and C-V2X for V2X communications in the 5.9 GHz ITS band. IET Intell. Transp. Syst. 2021, 15, 213–224. [Google Scholar] [CrossRef]
- Peng, H.; Shen, X. Deep Reinforcement Learning Based Resource Management for Multi-Access Edge Computing in Vehicular Networks. IEEE Trans. Netw. Sci. Eng. 2020, 7, 2416–2428. [Google Scholar] [CrossRef]
- Fan, K.; Jiang, W.; Luo, Q.; Li, H.; Yang, Y. Cloud-based RFID mutual authentication scheme for efficient privacy preserving in IoV. J. Frankl. Inst. 2021, 358, 193–209. [Google Scholar] [CrossRef]
- Song, L.; Sun, G.; Yu, H.; Du, X.; Guizani, M. FBIA: A Fog-Based Identity Authentication Scheme for Privacy Preservation in Internet of Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 5403–5415. [Google Scholar] [CrossRef]
- He, X.; Wang, K.; Xu, W. QoE-Driven Content-Centric Caching with Deep Reinforcement Learning in Edge-Enabled IoT. IEEE Comput. Intell. Mag. 2019, 14, 12–20. [Google Scholar] [CrossRef]
- Ahangar, M.N.; Ahmed, Q.Z.; Khan, F.A.; Hafeez, M. A Survey of Autonomous Vehicles: Enabling Communication Technologies and Challenges. Sensors 2021, 21, 706. [Google Scholar] [CrossRef]
- Senouci, O.; Aliouat, Z.; Harous, S. A review of routing protocols in internet of vehicles and their challenges. Sens. Rev. 2019, 39, 58–70. [Google Scholar] [CrossRef]
- Du, Z.; Wu, C.; Yoshinaga, T.; Yau, K.-L.A.; Ji, Y.; Li, J. Federated Learning for Vehicular Internet of Things: Recent Advances and Open Issues. IEEE Open J. Comput. Soc. 2020, 1, 45–61. [Google Scholar] [CrossRef]
- Karoui, M.; Mamadou, A.M.; Chalhoub, G. A Novel Distributed Context-Aware Radio Access Technology Selection Scheme For C-ITS Networks. In Proceedings of the 2022 International Wireless Communications and Mobile Computing (IWCMC), Dubrovnik, Croatia, 30 May–3 June 2022; pp. 725–730. [Google Scholar]
- Khawam, K.; Lahoud, S.; Ibrahim, M.; Yassin, M.; Martin, S.; El Helou, M.; Moety, F. Radio access technology selection in heterogeneous networks. Phys. Commun. 2016, 18, 125–139. [Google Scholar] [CrossRef]
- Hussain, S.M.; Yusof, K.M.; Hussain, S.A. Artificial Intelligence-Based Network Selection and Optimized Routing in Internet of Vehicles. Transp. Telecommun. 2021, 22, 392–406. [Google Scholar] [CrossRef]
- Xu, Z.; Li, X.; Zhao, X.; Zhang, M.H.; Wang, Z. DSRC versus 4G-LTE for Connected Vehicle Applications: A Study on Field Experiments of Vehicular Communication Performance. J. Adv. Transp. 2017, 2017, e2750452. [Google Scholar] [CrossRef]
- Hussain, S.M.; Yusof, K.M.; Asuncion, R.; Hussain, S.A.; Ahmad, A. An Integrated Approach of 4G LTE and DSRC (IEEE 802.11p) for Internet of Vehicles (IoV) by Using a Novel Cluster-Based Efficient Radio Interface Selection Algorithm to Improve Vehicular Network (VN) Performance. In Proceedings of the Sustainable Advanced Computing; Aurelia, S., Hiremath, S.S., Subramanian, K., Biswas, S.K., Eds.; Springer: Singapore, 2022; pp. 569–583. [Google Scholar]
- Sherazi, H.H.R.; Khan, Z.A.; Iqbal, R.; Rizwan, S.; Imran, M.A.; Awan, K. A Heterogeneous IoV Architecture for Data Forwarding in Vehicle to Infrastructure Communication. Mob. Inf. Syst. 2019, 2019, e3101276. [Google Scholar] [CrossRef]
- Sanchez-Iborra, R.; Bernal-Escobedo, L.; Santa, J. Machine learning-based radio access technology selection in the Internet of moving things. China Commun. 2021, 18, 13–24. [Google Scholar] [CrossRef]
- Tuyisenge, L.; Ayaida, M.; Tohme, S.; Afilal, L.-E. A mobile internal vertical handover mechanism for distributed mobility management in VANETs. Veh. Commun. 2020, 26, 100277. [Google Scholar] [CrossRef]
- González, C.C.; Pupo, E.F.; Atzori, L.; Murroni, M. Dynamic Radio Access Selection and Slice Allocation for Differentiated Traffic Management on Future Mobile Networks. IEEE Trans. Netw. Serv. Manag. 2022. 16p. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G Wireless Communication Systems: Applications, Requirements, Technologies, Challenges, and Research Directions. IEEE Open J. Commun. Soc. 2020, 1, 957–975. [Google Scholar] [CrossRef]
- Boussoufa-Lahlah, S.; Semchedine, F.; Bouallouche-Medjkoune, L. Geographic routing protocols for Vehicular Ad hoc NETworks (VANETs): A survey. Veh. Commun. 2018, 11, 20–31. [Google Scholar] [CrossRef]
- Ghaffari, A. Hybrid opportunistic and position-based routing protocol in vehicular ad hoc networks. J. Ambient Intell. Humaniz. Comput. 2020, 11, 1593–1603. [Google Scholar] [CrossRef]
- Agrawal, S.; Tyagi, N.; Iqbal, A.; Rao, R.S. An Intelligent Greedy Position-Based Multi-hop Routing Algorithm for Next-Hop Node Selection in VANETs. Proc. Natl. Acad. Sci. India Sect. Phys. Sci. 2020, 90, 39–47. [Google Scholar] [CrossRef]
- Sennan, S.; Ramasubbareddy, S.; Balasubramaniyam, S.; Nayyar, A.; Kerrache, C.A.; Bilal, M. MADCR: Mobility aware dynamic clustering-based routing protocol in Internet of Vehicles. China Commun. 2021, 18, 69–85. [Google Scholar] [CrossRef]
- Ye, M.; Guan, L.; Quddus, M. MPBRP- Mobility Prediction Based Routing Protocol in VANETs. In Proceedings of the 2019 International Conference on Advanced Communication Technologies and Networking (CommNet), Rabat, Morocco, 12–14 April 2019; pp. 1–7. [Google Scholar]
- Jaiswal, R.K. Position-based routing protocol using Kalman filter as a prediction module for vehicular ad hoc networks. Comput. Electr. Eng. 2020, 83, 106599. [Google Scholar] [CrossRef]
- Cheng, J.; Yuan, G.; Zhou, M.; Gao, S.; Huang, Z.; Liu, C. A Connectivity-Prediction-Based Dynamic Clustering Model for VANET in an Urban Scene. IEEE Internet Things J. 2020, 7, 8410–8418. [Google Scholar] [CrossRef]
- Liu, B.; Sheng, Y.; Shao, X.; Ji, Y.; Han, W.; Wang, E.; Xiong, S. Collaborative Intelligence Enabled Routing in Green IoV: A Grid and Vehicle Density Prediction Based Protocol. IEEE Trans. Green Commun. Netw. 2022. 11p. [Google Scholar] [CrossRef]
- Wu, C.; Liu, Z.; Liu, F.; Yoshinaga, T.; Ji, Y.; Li, J. Collaborative Learning of Communication Routes in Edge-Enabled Multi-Access Vehicular Environment. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 1155–1165. [Google Scholar] [CrossRef]
- Malhi, A.K.; Batra, S.; Pannu, H.S. Security of vehicular ad-hoc networks: A comprehensive survey. Comput. Secur. 2020, 89, 101664. [Google Scholar] [CrossRef]
- Gupta, D.S.; Karati, A.; Saad, W.; da Costa, D.B. Quantum-Defended Blockchain-Assisted Data Authentication Protocol for Internet of Vehicles. IEEE Trans. Veh. Technol. 2022, 71, 3255–3266. [Google Scholar] [CrossRef]
- Khodaei, M.; Papadimitratos, P. Scalable & Resilient Vehicle-Centric Certificate Revocation List Distribution in Vehicular Communication Systems. IEEE Trans. Mob. Comput. 2021, 20, 2473–2489. [Google Scholar] [CrossRef]
- Fan, K.; Pan, Q.; Zhang, K.; Bai, Y.; Sun, S.; Li, H.; Yang, Y. A Secure and Verifiable Data Sharing Scheme Based on Blockchain in Vehicular Social Networks. IEEE Trans. Veh. Technol. 2020, 69, 5826–5835. [Google Scholar] [CrossRef]
- Ma, Z.; Zhang, J.; Guo, Y.; Liu, Y.; Liu, X.; He, W. An Efficient Decentralized Key Management Mechanism for VANET with Blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5836–5849. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Wang, H.; Kumar, N.; Choo, K.-K.R. An Efficient and Provably Secure Authenticated Key Agreement Protocol for Fog-Based Vehicular Ad-Hoc Networks. IEEE Internet Things J. 2019, 6, 8065–8075. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.P.C.; Park, Y. AKM-IoV: Authenticated Key Management Protocol in Fog Computing-Based Internet of Vehicles Deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Allouch, A.; Cheikhrouhou, O.; Koubâa, A.; Toumi, K.; Khalgui, M.; Nguyen Gia, T. UTM-Chain: Blockchain-Based Secure Unmanned Traffic Management for Internet of Drones. Sensors 2021, 21, 3049. [Google Scholar] [CrossRef]
- Jamil, F.; Cheikhrouhou, O.; Jamil, H.; Koubaa, A.; Derhab, A.; Ferrag, M.A. PetroBlock: A Blockchain-Based Payment Mechanism for Fueling Smart Vehicles. Appl. Sci. 2021, 11, 3055. [Google Scholar] [CrossRef]
- Inedjaren, Y.; Maachaoui, M.; Zeddini, B.; Barbot, J.-P. Blockchain-based distributed management system for trust in VANET. Veh. Commun. 2021, 30, 100350. [Google Scholar] [CrossRef]
- Wang, J.; Zhu, K.; Hossain, E. Green Internet of Vehicles (IoV) in the 6G Era: Toward Sustainable Vehicular Communications and Networking. IEEE Trans. Green Commun. Netw. 2022, 6, 391–423. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Hu, X.; Wang, L.; Guo, L.; Hu, B.; Wu, X. Future Communications and Energy Management in the Internet of Vehicles: Toward Intelligent Energy-Harvesting. IEEE Wirel. Commun. 2019, 26, 87–93. [Google Scholar] [CrossRef]
- Cesarano, L.; Croce, A.; Martins, L.D.C.; Tarchi, D.; Juan, A.A. A Real-Time Energy-Saving Mechanism in Internet of Vehicles Systems. IEEE Access 2021, 9, 157842–157858. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Luo, Z.; Sodhro, G.H.; Muzamal, M.; Rodrigues, J.J.P.C.; de Albuquerque, V.H.C. Artificial Intelligence based QoS optimization for multimedia communication in IoV systems. Future Gener. Comput. Syst. 2019, 95, 667–680. [Google Scholar] [CrossRef]
- Taleb, T.; Samdanis, K.; Mada, B.; Flinck, H.; Dutta, S.; Sabella, D. On Multi-Access Edge Computing: A Survey of the Emerging 5G Network Edge Cloud Architecture and Orchestration. IEEE Commun. Surv. Tutor. 2017, 19, 1657–1681. [Google Scholar] [CrossRef]
- Feng, C.; Han, P.; Zhang, X.; Yang, B.; Liu, Y.; Guo, L. Computation offloading in mobile edge computing networks: A survey. J. Netw. Comput. Appl. 2022, 202, 103366. [Google Scholar] [CrossRef]
- Cao, B.; Zhang, J.; Liu, X.; Sun, Z.; Cao, W.; Nowak, R.M.; Lv, Z. Edge–Cloud Resource Scheduling in Space–Air–Ground-Integrated Networks for Internet of Vehicles. IEEE Internet Things J. 2022, 9, 5765–5772. [Google Scholar] [CrossRef]
- Xu, X.; Jiang, Q.; Zhang, P.; Cao, X.; Khosravi, M.R.; T. Alex, L.; Qi, L.; Dou, W. Game Theory for Distributed IoV Task Offloading with Fuzzy Neural Network in Edge Computing. IEEE Trans. Fuzzy Syst. 2022. 1p. [Google Scholar] [CrossRef]
- Xu, X.; Gu, R.; Dai, F.; Qi, L.; Wan, S. Multi-objective computation offloading for Internet of Vehicles in cloud-edge computing. Wirel. Netw. 2020, 26, 1611–1629. [Google Scholar] [CrossRef]
- Zhen, Y.; Chui, Y.; Zhang, P.; Liu, H. Multiauthority Attribute-Based Keyword Search over Cloud-Edge-End Collaboration in IoV. Wirel. Commun. Mob. Comput. 2022, 2022, e3513063. [Google Scholar] [CrossRef]
- Liu, W.; Xu, X.; Qi, L.; Zhang, X.; Dou, W. GoDeep: Intelligent IoV Service Deployment and Execution with Privacy Preservation in Cloud-edge Computing. In Proceedings of the 2021 IEEE International Conference on Web Services (ICWS), Virtual, 5–11 September 2021; pp. 579–587. [Google Scholar]
- Zhang, D.; Gong, C.; Zhang, T.; Zhang, J.; Piao, M. A new algorithm of clustering AODV based on edge computing strategy in IOV. Wirel. Netw. 2021, 27, 2891–2908. [Google Scholar] [CrossRef]
- Dai, C.; Liu, X.; Chen, W.; Lai, C.-F. A Low-Latency Object Detection Algorithm for the Edge Devices of IoV Systems. IEEE Trans. Veh. Technol. 2020, 69, 11169–11178. [Google Scholar] [CrossRef]
- Xu, X.; Fang, Z.; Zhang, J.; He, Q.; Yu, D.; Qi, L.; Dou, W. Edge Content Caching with Deep Spatiotemporal Residual Network for IoV in Smart City. ACM Trans. Sens. Netw. 2021, 17, 1–33. [Google Scholar] [CrossRef]
- Xiao, Y.; Liu, Y.; Li, T. Edge Computing and Blockchain for Quick Fake News Detection in IoV. Sensors 2020, 20, 4360. [Google Scholar] [CrossRef]
- Xu, X.; Fang, Z.; Qi, L.; Zhang, X.; He, Q.; Zhou, X. TripRes: Traffic Flow Prediction Driven Resource Reservation for Multimedia IoV with Edge Computing. ACM Trans. Multimed. Comput. Commun. Appl. 2021, 17, 1–21. [Google Scholar] [CrossRef]
- Zhao, J.; Li, Q.; Gong, Y.; Zhang, K. Computation Offloading and Resource Allocation For Cloud Assisted Mobile Edge Computing in Vehicular Networks. IEEE Trans. Veh. Technol. 2019, 68, 7944–7956. [Google Scholar] [CrossRef]
- Guo, J.; Luo, W.; Song, B.; Yu, F.R.; Du, X. Intelligence-Sharing Vehicular Networks with Mobile Edge Computing and Spatiotemporal Knowledge Transfer. IEEE Netw. 2020, 34, 256–262. [Google Scholar] [CrossRef]
- Qin, Z.; Leng, S.; Zhou, J.; Mao, S. Collaborative Edge Computing and Caching in Vehicular Networks. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea, 25–28 May 2020; pp. 1–6. [Google Scholar]
- Zhao, J.; Sun, X.; Li, Q.; Ma, X. Edge Caching and Computation Management for Real-Time Internet of Vehicles: An Online and Distributed Approach. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2183–2197. [Google Scholar] [CrossRef]
- Gu, X.; Zhang, G. Energy-efficient computation offloading for vehicular edge computing networks. Comput. Commun. 2021, 166, 244–253. [Google Scholar] [CrossRef]
- Moon, H.; Baek, K.; Ko, I.-Y. Cache-Sharing Distributed Service Registry for Highly Dynamic V2X Environments. In Proceedings of the 2020 IEEE 44th Annual Computers, Software and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020; pp. 1123–1124. [Google Scholar]
- Qiao, G.; Leng, S.; Maharjan, S.; Zhang, Y.; Ansari, N. Deep Reinforcement Learning for Cooperative Content Caching in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2020, 7, 247–257. [Google Scholar] [CrossRef]
- Ning, Z.; Huang, J.; Wang, X.; Rodrigues, J.J.P.C.; Guo, L. Mobile Edge Computing-Enabled Internet of Vehicles: Toward Energy-Efficient Scheduling. IEEE Netw. 2019, 33, 198–205. [Google Scholar] [CrossRef]
- Zhai, Y.; Sun, W.; Wu, J.; Zhu, L.; Shen, J.; Du, X.; Guizani, M. An Energy Aware Offloading Scheme for Interdependent Applications in Software-Defined IoV with Fog Computing Architecture. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3813–3823. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Miridakis, N.I.; Michalas, A.; Skondras, E.; Vergados, D.J. Energy Optimization in Dual-RIS UAV-Aided MEC-Enabled Internet of Vehicles. Sensors 2021, 21, 4392. [Google Scholar] [CrossRef] [PubMed]
- Shen, X.; Yu, H.; Liu, X.; Bin, Q.; Luhach, A.K.; Saravanan, V. The optimized energy-efficient sensible edge processing model for the internet of vehicles in smart cities. Sustain. Energy Technol. Assess. 2021, 47, 101477. [Google Scholar] [CrossRef]
- Piromalis, D.; Kantaros, A. Digital Twins in the Automotive Industry: The Road toward Physical-Digital Convergence. Appl. Syst. Innov. 2022, 5, 65. [Google Scholar] [CrossRef]
- Liu, T.; Tang, L.; Wang, W.; Chen, Q.; Zeng, X. Digital-Twin-Assisted Task Offloading Based on Edge Collaboration in the Digital Twin Edge Network. IEEE Internet Things J. 2022, 9, 1427–1444. [Google Scholar] [CrossRef]
- Xu, X.; Shen, B.; Ding, S.; Srivastava, G.; Bilal, M.; Khosravi, M.R.; Menon, V.G.; Jan, M.A.; Wang, M. Service Offloading with Deep Q-Network for Digital Twinning-Empowered Internet of Vehicles in Edge Computing. IEEE Trans. Ind. Inform. 2022, 18, 1414–1423. [Google Scholar] [CrossRef]
- Sun, W.; Wang, P.; Xu, N.; Wang, G.; Zhang, Y. Dynamic Digital Twin and Distributed Incentives for Resource Allocation in Aerial-Assisted Internet of Vehicles. IEEE Internet Things J. 2022, 9, 5839–5852. [Google Scholar] [CrossRef]
- Lim, W.Y.B.; Luong, N.C.; Hoang, D.T.; Jiao, Y.; Liang, Y.-C.; Yang, Q.; Niyato, D.; Miao, C. Federated Learning in Mobile Edge Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2020, 22, 2031–2063. [Google Scholar] [CrossRef]
- Abreha, H.G.; Hayajneh, M.; Serhani, M.A. Federated Learning in Edge Computing: A Systematic Survey. Sensors 2022, 22, 450. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J. Improving TCP Performance Over WiFi for Internet of Vehicles: A Federated Learning Approach. IEEE Trans. Veh. Technol. 2020, 69, 6798–6802. [Google Scholar] [CrossRef]
- Xiong, K.; Leng, S.; Huang, C.; Yuen, C.; Guan, Y.L. Intelligent Task Offloading for Heterogeneous V2X Communications. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2226–2238. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Kato, N. HCP: Heterogeneous Computing Platform for Federated Learning Based Collaborative Content Caching Towards 6G Networks. IEEE Trans. Emerg. Top. Comput. 2022, 10, 112–123. [Google Scholar] [CrossRef]
- Zhang, C.; Liu, Y.; Wang, L.; Liu, Y.; Li, L.; Zheng, N. Joint Intelligence Ranking by Federated Multiplicative Update. IEEE Intell. Syst. 2020, 35, 15–24. [Google Scholar] [CrossRef]
- Yu, S.; Chen, X.; Zhou, Z.; Gong, X.; Wu, D. When Deep Reinforcement Learning Meets Federated Learning: Intelligent Multitimescale Resource Management for Multiaccess Edge Computing in 5G Ultradense Network. IEEE Internet Things J. 2021, 8, 2238–2251. [Google Scholar] [CrossRef]
- Shiri, H.; Park, J.; Bennis, M. Communication-Efficient Massive UAV Online Path Control: Federated Learning Meets Mean-Field Game Theory. IEEE Trans. Commun. 2020, 68, 6840–6857. [Google Scholar] [CrossRef]
- Sun, W.; Xu, N.; Wang, L.; Zhang, H.; Zhang, Y. Dynamic Digital Twin and Federated Learning with Incentives for Air-Ground Networks. IEEE Trans. Netw. Sci. Eng. 2022, 9, 321–333. [Google Scholar] [CrossRef]
- Ye, D.; Yu, R.; Pan, M.; Han, Z. Federated Learning in Vehicular Edge Computing: A Selective Model Aggregation Approach. IEEE Access 2020, 8, 23920–23935. [Google Scholar] [CrossRef]
- Zhang, H.; Hanzo, L. Federated Learning Assisted Multi-UAV Networks. IEEE Trans. Veh. Technol. 2020, 69, 14104–14109. [Google Scholar] [CrossRef]
- Saputra, Y.M.; Nguyen, D.; Dinh, H.T.; Vu, T.X.; Dutkiewicz, E.; Chatzinotas, S. Federated Learning Meets Contract Theory: Economic-Efficiency Framework for Electric Vehicle Networks. IEEE Trans. Mob. Comput. 2022, 21, 2803–2817. [Google Scholar] [CrossRef]
- Liu, Y.; Nie, J.; Li, X.; Ahmed, S.H.; Lim, W.Y.B.; Miao, C. Federated Learning in the Sky: Aerial-Ground Air Quality Sensing Framework with UAV Swarms. IEEE Internet Things J. 2021, 8, 9827–9837. [Google Scholar] [CrossRef]
- Thorgeirsson, A.T.; Scheubner, S.; Funfgeld, S.; Gauterin, F. Probabilistic Prediction of Energy Demand and Driving Range for Electric Vehicles with Federated Learning. IEEE Open J. Veh. Technol. 2021, 2, 151–161. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Benslimane, A. Learning in the Air: Secure Federated Learning for UAV-Assisted Crowdsensing. IEEE Trans. Netw. Sci. Eng. 2021, 8, 1055–1069. [Google Scholar] [CrossRef]
- Chai, H.; Leng, S.; Chen, Y.; Zhang, K. A Hierarchical Blockchain-Enabled Federated Learning Algorithm for Knowledge Sharing in Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3975–3986. [Google Scholar] [CrossRef]
- Lu, Y.; Huang, X.; Zhang, K.; Maharjan, S.; Zhang, Y. Blockchain Empowered Asynchronous Federated Learning for Secure Data Sharing in Internet of Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 4298–4311. [Google Scholar] [CrossRef]
- Yu, Z.; Hu, J.; Min, G.; Zhao, Z.; Miao, W.; Hossain, M.S. Mobility-Aware Proactive Edge Caching for Connected Vehicles Using Federated Learning. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5341–5351. [Google Scholar] [CrossRef]
- Lim, W.Y.B.; Huang, J.; Xiong, Z.; Kang, J.; Niyato, D.; Hua, X.-S.; Leung, C.; Miao, C. Towards Federated Learning in UAV-Enabled Internet of Vehicles: A Multi-Dimensional Contract-Matching Approach. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5140–5154. [Google Scholar] [CrossRef]
- Mowla, N.I.; Tran, N.H.; Doh, I.; Chae, K. AFRL: Adaptive federated reinforcement learning for intelligent jamming defense in FANET. J. Commun. Netw. 2020, 22, 244–258. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J. Federated Learning with Blockchain for Autonomous Vehicles: Analysis and Design Challenges. IEEE Trans. Commun. 2020, 68, 4734–4746. [Google Scholar] [CrossRef]
- Pham, Q.-V.; Zeng, M.; Ruby, R.; Huynh-The, T.; Hwang, W.-J. UAV Communications for Sustainable Federated Learning. IEEE Trans. Veh. Technol. 2021, 70, 3944–3948. [Google Scholar] [CrossRef]
- Rihan, M.; Elwekeil, M.; Yang, Y.; Huang, L.; Xu, C.; Selim, M.M. Deep-VFog: When Artificial Intelligence Meets Fog Computing in V2X. IEEE Syst. J. 2021, 15, 3492–3505. [Google Scholar] [CrossRef]
- Yang, H.H.; Liu, Z.; Quek, T.Q.S.; Poor, H.V. Scheduling Policies for Federated Learning in Wireless Networks. IEEE Trans. Commun. 2020, 68, 317–333. [Google Scholar] [CrossRef]
- Yang, K.; Jiang, T.; Shi, Y.; Ding, Z. Federated Learning via Over-the-Air Computation. IEEE Trans. Wirel. Commun. 2020, 19, 2022–2035. [Google Scholar] [CrossRef]
- Ng, J.S.; Lim, W.Y.B.; Dai, H.-N.; Xiong, Z.; Huang, J.; Niyato, D.; Hua, X.-S.; Leung, C.; Miao, C. Joint Auction-Coalition Formation Framework for Communication-Efficient Federated Learning in UAV-Enabled Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 22, 2326–2344. [Google Scholar] [CrossRef]
- Jiang, Y.; Yin, S. Recursive Total Principle Component Regression Based Fault Detection and Its Application to Vehicular Cyber-Physical Systems. IEEE Trans. Ind. Inform. 2018, 14, 1415–1423. [Google Scholar] [CrossRef]
- Alamgir, M.S.M.; Sultana, M.N.; Chang, K. Link Adaptation on an Underwater Communications Network Using Machine Learning Algorithms: Boosted Regression Tree Approach. IEEE Access 2020, 8, 73957–73971. [Google Scholar] [CrossRef]
- Valle, F.; Cespedes, S.; Hafid, A.S. Automated Decision System to Exploit Network Diversity for Connected Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 858–871. [Google Scholar] [CrossRef]
- Zhang, C.; Li, R.; Kim, W.; Yoon, D.; Patras, P. Driver Behavior Recognition via Interwoven Deep Convolutional Neural Nets with Multi-Stream Inputs. IEEE Access 2020, 8, 191138–191151. [Google Scholar] [CrossRef]
- Ferreira, D.; Reis, A.; Senna, C.; Sargento, S. A Forecasting Approach to Improve Control and Management for 5G Networks. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1817–1831. [Google Scholar] [CrossRef]
- Raja, G.; Anbalagan, S.; Vijayaraghavan, G.; Theerthagiri, S.; Suryanarayan, S.V.; Wu, X.-W. SP-CIDS: Secure and Private Collaborative IDS for VANETs. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4385–4393. [Google Scholar] [CrossRef]
- Min, D.; Kim, D.; Park, J.; Huh, K. RNN-Based Path Prediction of Obstacle Vehicles with Deep Ensemble. IEEE Trans. Veh. Technol. 2019, 68, 10252–10256. [Google Scholar] [CrossRef]
- Toprak, T.; Belenlioglu, B.; Aydin, B.; Guzelis, C.; Selver, M.A. Conditional Weighted Ensemble of Transferred Models for Camera Based Onboard Pedestrian Detection in Railway Driver Support Systems. IEEE Trans. Veh. Technol. 2020, 69, 5041–5054. [Google Scholar] [CrossRef]
- Zhao, F.; Zeng, G.-Q.; Lu, K.-D. EnLSTM-WPEO: Short-Term Traffic Flow Prediction by Ensemble LSTM, NNCT Weight Integration, and Population Extremal Optimization. IEEE Trans. Veh. Technol. 2020, 69, 101–113. [Google Scholar] [CrossRef]
- Zhang, Z.; Cao, Y.; Cui, Z.; Zhang, W.; Chen, J. A Many-objective Optimization based Intelligent Intrusion Detection Algorithm for Enhancing Security of Vehicular Networks in 6G. IEEE Trans. Veh. Technol. 2021, 70, 5234–5243. [Google Scholar] [CrossRef]
- Alotaibi, B. Transportation Mode Detection by Embedded Sensors Based on Ensemble Learning. IEEE Access 2020, 8, 145552–145563. [Google Scholar] [CrossRef]
- Wang, Q.; Wan, J.; Li, X. Robust Hierarchical Deep Learning for Vehicular Management. IEEE Trans. Veh. Technol. 2019, 68, 4148–4156. [Google Scholar] [CrossRef]
- Yousif, B.B.; Ata, M.M.; Fawzy, N.; Obaya, M. Toward an Optimized Neutrosophic k-Means with Genetic Algorithm for Automatic Vehicle License Plate Recognition (ONKM-AVLPR). IEEE Access 2020, 8, 49285–49312. [Google Scholar] [CrossRef]
- Pustokhina, I.V.; Pustokhin, D.A.; Rodrigues, J.J.P.C.; Gupta, D.; Khanna, A.; Shankar, K.; Seo, C.; Joshi, G.P. Automatic Vehicle License Plate Recognition Using Optimal K-Means with Convolutional Neural Network for Intelligent Transportation Systems. IEEE Access 2020, 8, 92907–92917. [Google Scholar] [CrossRef]
- Yang, S.; Wang, W.; Lu, C.; Gong, J.; Xi, J. A Time-Efficient Approach for Decision-Making Style Recognition in Lane-Changing Behavior. IEEE Trans. Hum.-Mach. Syst. 2019, 49, 579–588. [Google Scholar] [CrossRef]
- Rong, H.; Ramirez-Serrano, A.; Guan, L.; Cong, X. Robust RGB-D SLAM for Dynamic Environments Based on YOLOv4. In Proceedings of the 2020 IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), Victoria, BC, Canada, 18 November–16 December 2020. 6p. [Google Scholar] [CrossRef]
- Bhaumik, S.; Prokes, A.; Chandra, A. Combined K-Means and Amplitude Clustering of Impulse Response for 60 GHz Vehicular Channels. In Proceedings of the 15th International Symposium on Wireless Communication Systems (ISWCS), Lisbon, Portugal, 28–31 August 2018; pp. 1–5. [Google Scholar]
- Gedschold, J.; Schneider, C.; Kaske, M.; Thoma, R.S.; Galdo, G.D.; Boban, M.; Luo, J. Tracking based Multipath Clustering in Vehicle-to-Infrastructure Channels. In Proceedings of the 2018 IEEE 29th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2018; pp. 68–72. [Google Scholar] [CrossRef]
- Song, W.; Zeng, F.; Hu, J.; Wang, Z.; Mao, X. An Unsupervised-Learning-Based Method for Multi-Hop Wireless Broadcast Relay Selection in Urban Vehicular Networks. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 4–7 June 2017; pp. 1–5. [Google Scholar]
- Sliwa, B.; Adam, R.; Wietfeld, C. Client-Based Intelligence for Resource Efficient Vehicular Big Data Transfer in Future 6G Networks. IEEE Trans. Veh. Technol. 2021, 70, 5332–5346. [Google Scholar] [CrossRef]
- Shehzad, M.K.; Hassan, S.A.; Mahmood, A.; Gidlund, M. On the Association of Small Cell Base Stations with UAVs Using Unsupervised Learning. In Proceedings of the 2019 IEEE 89th Vehicular Technology Conference (VTC2019-Spring), Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–5. [Google Scholar]
- Hoang, T.M.; Nguyen, N.M.; Duong, T.Q. Detection of Eavesdropping Attack in UAV-Aided Wireless Systems: Unsupervised Learning with One-Class SVM and K-Means Clustering. IEEE Wirel. Commun. Lett. 2020, 9, 139–142. [Google Scholar] [CrossRef]
- Albakay, N.; Hempel, M.; Alahmad, M.; Sharif, H. Novel Frequency Offset Estimation Scheme for Reliable Wireless Communication using Modified K-Means Clustering. In Proceedings of the 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 826–829. [Google Scholar]
- He, J.; Wang, J.; Zhu, H.; Gomes, N.J.; Cheng, W.; Yue, P.; Yi, X. Machine Learning based Network Planning in Drone Aided Emergency Communications. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 25–28 May 2020. 5p. [Google Scholar]
- Ye, L.; Chen, Y.; Han, Q.; Zeng, L.; Cheng, S.; Xiao, L.; Ding, X. Vehicle Message Distribution Mechanism Based on Improved K-means Adaptive Clustering Algorithm. In Proceedings of the 2020 IEEE 23rd International Conference on Intelligent Transportation Systems (ITSC), Rhodes, Greece, 20–23 September 2020. 6p. [Google Scholar]
- Cui, Y.; Zheng, H.; Wang, H.; Wu, D. An Intelligent Coordinator Design for Network Slicing in Service-Oriented Vehicular Networks. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020. 6p. [Google Scholar]
- Ozasa, M.; Nakazato, J.; Hirata, K.; Tran, G.K.; Sakaguchi, K. Design of Millimeter-wave UAV Base Station for Access Link. In Proceedings of the 2020 IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), Victoria, BC, Canada, 18 November–16 December 2020. 5p. [Google Scholar]
- Wahlstrom, J.; Skog, I.; Handel, P.; Bradley, B.; Madden, S.; Balakrishnan, H. Smartphone Placement Within Vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 21, 669–679. [Google Scholar] [CrossRef]
- Yuan, M.; Kan, X.; Chi, C.-H.; Cao, L.; Shu, H.; Fan, Y.; Yao, W. Study of Driving Cycle of City Tour Bus Based on Coupled GA-K-Means and HMM Algorithms: A Case Study in Beijing. IEEE Access 2021, 9, 20331–20345. [Google Scholar] [CrossRef]
- Forster, D.; Inderka, R.B.; Gauterin, F. Data-Driven Identification of Characteristic Real-Driving Cycles Based on k-Means Clustering and Mixed-Integer Optimization. IEEE Trans. Veh. Technol. 2020, 69, 2398–2410. [Google Scholar] [CrossRef]
- Ren, Y.; Xu, R. An Adaptive Clustering Scheme Based on Modified Density-Based Spatial Clustering of Applications with Noise Algorithm in Ultra-Dense Networks. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019. 5p. [Google Scholar]
- Cao, L.; Wang, T.; Wang, D.; Du, K.; Liu, Y.; Fu, C. Lane Determination of Vehicles Based on a Novel Clustering Algorithm for Intelligent Traffic Monitoring. IEEE Access 2019, 8, 63004–63017. [Google Scholar] [CrossRef]
- Tan, H.; Gui, Z.; Chung, I. A Secure and Efficient Certificateless Authentication Scheme with Unsupervised Anomaly Detection in VANETs. IEEE Access 2018, 6, 74260–74276. [Google Scholar] [CrossRef]
- Chen, Z.; Yang, C.; Fang, S. A Convolutional Neural Network-Based Driving Cycle Prediction Method for Plug-in Hybrid Electric Vehicles with Bus Route. IEEE Access 2019, 6, 3255–3264. [Google Scholar] [CrossRef]
- Guo, J.; Li, X.; Liu, Z.; Ma, J.; Yang, C.; Zhang, J.; Wu, D. TROVE: A Context-Awareness Trust Model for VANETs Using Reinforcement Learning. IEEE Internet Things J. 2020, 7, 6647–6662. [Google Scholar] [CrossRef]
- Yu, C.; Wang, X.; Xu, X.; Zhang, M.; Ge, H.; Ren, J.; Sun, L.; Chen, B.; Tan, G. Distributed Multiagent Coordinated Learning for Autonomous Driving in Highways Based on Dynamic Coordination Graphs. IEEE Trans. Intell. Transp. Syst. 2020, 21, 735–748. [Google Scholar] [CrossRef]
- Zhou, X.; Wang, W.; Wang, T.; Lei, Y.; Zhong, F. Bayesian Reinforcement Learning for Multi-Robot Decentralized Patrolling in Uncertain Environments. IEEE Trans. Veh. Technol. 2020, 68, 11691–11703. [Google Scholar] [CrossRef]
- Zhang, Y.; Guo, L.; Gao, B.; Qu, T.; Chen, H. Deterministic Promotion Reinforcement Learning Applied to Longitudinal Velocity Control for Automated Vehicles. IEEE Trans. Veh. Technol. 2020, 69, 338–348. [Google Scholar] [CrossRef]
- Feng, S.; Haykin, S. Cognitive Risk Control for Anti-Jamming V2V Communications in Autonomous Vehicle Networks. IEEE Trans. Veh. Technol. 2019, 68, 9920–9934. [Google Scholar] [CrossRef]
- Xing, R.; Su, Z.; Zhang, N.; Peng, Y.; Pu, H.; Luo, J. Trust-Evaluation-Based Intrusion Detection and Reinforcement Learning in Autonomous Driving. IEEE Netw. 2019, 33, 54–60. [Google Scholar] [CrossRef]
- Kapoor, S.; Grace, D.; Clarke, T. User Association in Ultra-Dense Small Cell Dynamic Vehicular Networks: A Reinforcement Learning Approach. J. Commun. Inf. Netw. 2019, 4, 1–12. [Google Scholar] [CrossRef]
- Zhou, Y.; Tang, F.; Kawamoto, Y.; Kato, N. Reinforcement Learning-Based Radio Resource Control in 5G Vehicular Network. IEEE Wirel. Commun. Lett. 2020, 9, 611–614. [Google Scholar] [CrossRef]
- Wu, J.; Fang, M.; Li, H.; Li, X. RSU-Assisted Traffic-Aware Routing Based on Reinforcement Learning for Urban Vanets. IEEE Access 2020, 8, 5733–5748. [Google Scholar] [CrossRef]
- Samir, M.; Ebrahimi, D.; Assi, C.; Sharafeddine, S.; Ghrayeb, A. Trajectory Planning of Multiple Dronecells in Vehicular Networks: A Reinforcement Learning Approach. IEEE Netw. Lett. 2020, 2, 14–18. [Google Scholar] [CrossRef]
- Raja, G.; Ganapathisubramaniyan, A.; Anbalagan, S.; Baskaran, S.B.M.; Raja, K.; Bashir, A.K. Intelligent Reward-Based Data Offloading in Next-Generation Vehicular Networks. IEEE Internet Things J. 2020, 7, 3747–3758. [Google Scholar] [CrossRef]
- Cao, Z.; Guo, H.; Song, W.; Gao, K.; Chen, Z.; Zhang, L.; Zhang, X. Using Reinforcement Learning to Minimize the Probability of Delay Occurrence in Transportation. IEEE Trans. Veh. Technol. 2020, 69, 2424–2436. [Google Scholar] [CrossRef]
- Zhang, Q.; Wu, K.; Shi, Y. Route Planning and Power Management for PHEVs with Reinforcement Learning. IEEE Trans. Veh. Technol. 2020, 69, 4751–4762. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).