Abstract
For the betterment of human life, smart Internet of Things (IoT)-based systems are needed for the new era. IoT is evolving swiftly for its applications in the smart environment, including smart airports, smart buildings, smart manufacturing, smart homes, etc. A smart home environment includes resource-constrained devices that are interlinked, monitored, controlled, and analyzed with the help of the Internet. In a distributed smart environment, devices with low and high computational power work together and require authenticity. Therefore, a computationally efficient and secure protocol is needed. The authentication protocol is employed to ensure that authorized smart devices communicate with the smart environment and are accessible by authorized personnel only. We have designed a novel, lightweight secure protocol for a smart home environment. The introduced novel protocol can withstand well-known attacks and is effective with respect to computation and communication complexities. Comparative, formal, and informal analyses were conducted to draw the comparison between the introduced protocol and previous state-of-the-art protocols.
1. Introduction
Human life is enviable. Science and technology play a vital role in providing safety to human life by developing safer devices using smarter technology. [1,2]. The advances in wireless and sensor technology have played an indispensable role in the rapid adaption of the smart home as an interesting new paradigm of the Internet of Things (IoT) [3,4,5,6,7,8]. This results in gaining a considerable amount of interest from both industry and academic fields alike [9].
A smart-home environment is used to assist individuals in various tasks by appending automation to them, like a smart meter, which can help users by showing the real-time consumption of power, voltage, and load [10,11] along with other interconnected devices. These devices can be various sensors, like a sensor to measure humidity, temperature, occupancy, and even to monitor the equipment. Multiple services can be provided by employing these services, such as turning on the air conditioner (AC) when an individual enters the room or turning on the lights when a person opens the door, and carbon dioxide (CO2) sensors can be employed to monitor the environment and to trigger automatic responses to energy saving [12,13]. In addition, these various smart gadgets can be deployed to oversee the health of the elderly [14]. Smart-home devices can also be accessed through a user’s device, such as a smartphone, without the restriction of place or time.
An innovative irrigation system may assist in conserving tens of dollars each year in addition to thousands of gallons of water. Cyber Rain [15], for example, allows observing and controlling the system from any Internet-connected device and can be customized to fit any size yard. By analyzing the weather prediction for you and modifying the watering plan automatically when rain is noticed, systems like Cyber Rain save the Earth’s limited supply of freshwater. According to the company’s website, users of Cyber Rain reportedly consume 35% less water on average.
Linked feeders provide automatic pet care. Using linked timers, you may water your yard and inside plants. There are many different types of kitchen equipment useable, such as smart coffee machines that can mix a fresh cup automatically at a set time, smart refrigerators that keep track of expiration dates, generate grocery lists, or even create ingredients using ingredients already in the house, toasters, and delayed cookers, and washing machines and dryers for the laundry room [16].
A wide range of applications, from business to government and military uses, may be realized with secure and continuous user access to designated smart home appliances [17]. Due to the sensitive nature of the operations and inherited vulnerabilities of the public channel, such as real-time data manipulation, clogging, replay, jamming, etc., the use of these smart home appliances for such applications is otherwise regarded as problematic [18,19]. Although various security schemes for the smart-home environment have recently been developed, many of these schemes have turned out to be insecure or unworkable. Consequently, the current demand is for an authentication system that can guarantee both security and privacy. To support the automatic security proof of the suggested method, we used a well-known automated program, AVISPA. The research showed that the suggested system could withstand known assaults and offered excellent balance between security and effectiveness [20,21,22,23].
A typical architecture for a smart home is presented in Figure 1. The network model comprises four components that are (i) the end user (), (ii) a trusted authority (), (iii) a gateway node (), and (iv) smart devices (). The s have limited resources and can be used for various tasks such as controlling the temperature, turning on lights [20], etc. The is used as an access point and has enough computation power; it acts as a gateway for and . The is trusted by all the parties involved in the communication. The responsibilities he include (i) system parameters’ generation and assignment, (ii) smart device and user registration, and (iii) key maintenance and management.
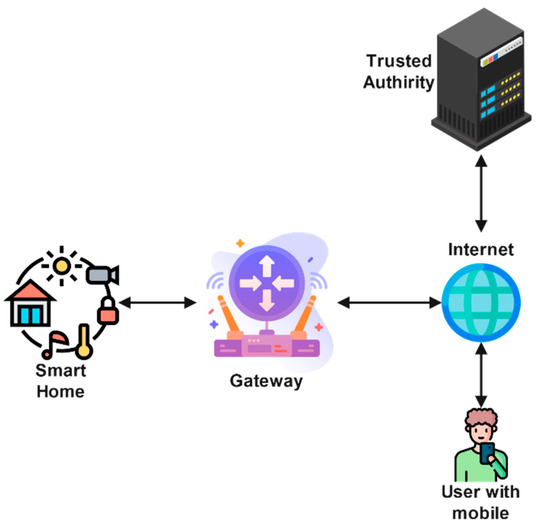
Figure 1.
Smart home environment architecture diagram (adapted from [12]).
This study is arranged as follows: Section 2 presents the motivation and contribution of our research. Section 3 shortly investigates the existing literature. Section 4 presents our proposed protocol. Moreover, Section 5 discusses the security analysis. Section 6 presents the performance analysis. In Section 7, the whole work is summed up.
2. Motivations and Contributions
This section concisely presents the primary contributions of this study:
- We suggested an authentication protocol based on a symmetric key to protect the user–smart device connection. The system was created using a mobile device, biometrics, and a password.
- The security of the proposed work was analyzed by using an automated security tool AVISPA.
- The analysis showed that the suggested system could withstand known attacks and offered an excellent balance between security and effectiveness.
- The computation cost of the proposed protocol was less than that of the protocols with the smart devices as they were resource-constrained and had limited computational power.
- The proposed protocol evaded the clock synchronization issue in timestamp-based two-way authentication protocols.
- Our presented protocol was compared to others in a similar field, showing that the proposed protocol was better in terms of security and performance analysis.
3. Related Work
Recently, various protocols have been introduced to provide security in smart home environments [24,25]. Every protocol has its strengths and weaknesses. Sciancalepore et al. [26] used ECQV and ECDH certificates to accomplish authentication. However, two distinct keys are required to run the scheme, and the efficiency of the key creation function relies on the key derivation function (KDF). Any problem in the KDF may result in a connection interruption between entities. All the keys are generated by using the master key; hence, disclosure of the master key may cause forward secrecy [27]. In [28], the authors present an authentication protocol for an IoT-enabled smart home. The authors state that their protocol is secure and lightweight against numerous attacks.
However, Ref. [27] found that their protocol lacks confidentiality and resistance against a Denial-of-Service attack (DoS) and some known key attacks. Additionally, the communication and computation costs are very high, which is not recommended for a resource-limited environment such as a smart-home environment. Dey and Hossain [29] presented a protocol using a new security model for smart homes. Gaba et al. [27] said that their protocol is efficient in computation and communication cost lacks message freshness and cannot resist a known-key attack.
Kumar et al. [30] introduced a new authentication mechanism for an SH environment. In this scheme, the SK is created by utilizing a small token to achieve authentication and theusingntity. This protocol is secure against various well-known attacks and lightweight in terms of computation and communication costs. However, after analysis, it is evident that their protocol is vulnerable to time synchronization attacks, replay attacks, does not provide anonymity, and has unlink ability issues. Kumar et al. [31] presented a new improved protocol in which the session key is renewed continuously to resist replay attacks. However, their protocol’s computation and communication costs are still very high. Gope and Sikdar [32] introduced a new protocol and claim that it is secure against impersonation, traceability, and physical attacks. However, due to enormous use of hash operations and high communication complexities, their protocol is not recommended for smart-home environments.
Wazid et al. [33] presented a protocol for smart homes. In this study, the use of an XOR operation one-way hand function makes it accessible for smart sensors. In contrast, their scheme is susceptible to a stolen verifier attack because verifier table is stored on the GWN and is vulnerable to a synchronization attack because a time stamp is employed to stop a replay attack. Shuai et al. [34] presented a protocol using ECC for a smart-home environment. They eliminated the need of a verifier table for authentication. However, their protocol incurs high communication and computation costs, which is not recommended in a smart-home environment. Banerjee et al. [23] also proposed a scheme to secure smart-home environments. They stated that their scheme can bear well-known attacks but, in this study, it is shown that their scheme is prone to a stolen gateway node attack, a stolen verifier attack, a gateway node impersonation attack towards a smart device, a broadcast issue which causes inefficient resource utilization, a smart device impersonation and a parallel session attack, and a gateway node impersonation attack towards the user. In this study, a three-factor-based enhanced scheme is introduced to overcome the shortfalls.
4. Proposed Protocol
A lightweight and robust security protocol for smart-home environments (LR-AKAP) is presented, which not only withstands well-known active and passive attacks, but also attains the required functional qualities. The proposed protocol includes six processes: ( the initialization process, ( the smart device enrolment process, ( the gateway node enrolment process, ( the user enrolment process, ( the login and authentication process, and ( the password and biometric update process. Various notations used in this paper are listed in Table 1. The proposed architecture of the scheme is depicted in Figure 2.

Table 1.
Notations guide.
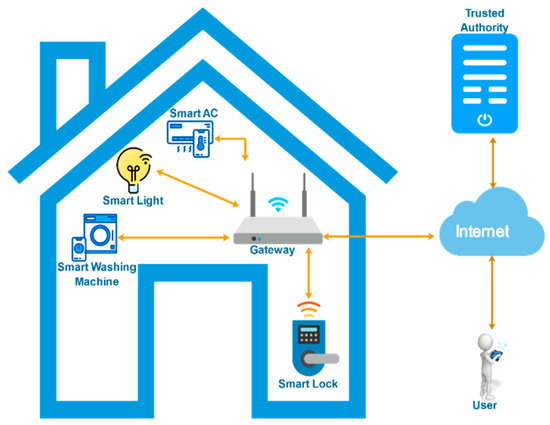
Figure 2.
Proposed architecture for a smart-home environment.
4.1. Assumptions
The following are the assumptions which are taken into consideration to design the introduced protocol:
- The is trusted and there is no energy restriction. Nevertheless, the sensor nodes (smart devices) are powered by batteries, and they have very limited resources [35].
- An may inaugurate only external attacks by employing powerful devices [36].
- The is under the user’s possession, and any wicked intruder cannot control it [37].
4.2. Adversarial Model
- 1.
- A common adversarial model [17,18,19], Refs. [20,21,22] is considered in this article, where the adversary has the subsequent capabilities:
- 2.
- Public/open channel communication fully controlled by the T.
- 3.
- can detain, retransmit, and modify the old message. can also cease or transmit a forged message.
- 4.
- can get the data saved in a smart card through power analysis [17,22].
- 5.
- Any insider/privileged user or outsider can attempt to violate the privacy and security of the system.
- 6.
- The private key of the cannot be compromized.
4.3. Entities Involved in the Proposed Protocol
The network model is made up of four entities: smart device (SD) in the house, gateway node (GWN), end user (U), and trusted authoritie (TA). The smart devices are typically diverse and resource-constrained, and they may be utilized to allow a wide range of use cases including lighting control, surveillance systems, temperature management, and so on. The master node as a GWN installed in the house acts as a link between the user and smart gadgets. The users may remotely operate the various smart home gadgets based on their requirements. Others totally trust the TA’s processing and communication capabilities.
4.4. Proposed Protocol Processes
The proposed protocol is based on six phases as presented in the following subsections:
4.4.1. Initialization Process
In the initialization phase, the Trusted Authority selects a private key .
4.4.2. Smart Device Enrolment Process
picks an identity and forwards to the . computes and store in its own database describe in Table 2.

Table 2.
Proposed smart device enrollment process.
4.4.3. Gateway Node Enrollment Process
Given blow Table 3 selects an identity and sends it to . computes and stores in its own database and sends to the , which it stores in its own memory.

Table 3.
Proposed gateway node enrollment process.
4.4.4. User Enrollment Process
The subsequent procedure is adopted to register a user with the system in Table 4:

Table 4.
Proposed user enrollment process.
- Step 1.
- picks and and computes and sends to the .
- Step 2.
- generates , and calculates . Save tuple in own database. Send , to through private channel.
- Step 3.
- On getting , computes , , , . replaces with in .
4.4.5. Login and Authentication Process
The login and authentication phase describe in Table 5 includes the following steps:

Table 5.
Proposed login and authentication process.
- Step 1.
- Insert SC and input . Calculate and check whether ; if true, further compute . chooses and and computes , , , . Sends to by public channel.
- Step 2.
- First of all, verifies the timeliness of the timestamp by inspecting the condition , if so, searches in database, if it exists, then fetches related and computes and checks if , and if true, then selects and , replaces the with , and computes , , , , . Sends message to through public channel. Also sends back to via open channel.
- Step 3.
- gets the from and checks if , if true, computes , created timestamp , and computed , . At the end, send message to the message to via open/insecure channel.
- Step 4.
- verifies the freshness of by examining the condition . If true, it selects and , checks if if true, then computes , , , , . At the end, sends the message to by public/insecure channel.
- Step 5.
- examines the freshness of the message by inspecting the condition , and if the condition is true, selects timestamp and sends the to via open channel.
- Step 6.
- Upon getting the , validates message freshness through condition . If true, compute , replace with , , . , if true, the session key is saved for secure communication.
4.4.6. Biometric and Password Update Process
A registered user can update a biometric/password. To do so, the user needs to login first as described in the “Login and authentication process”. After a successful login, the user will adopt the subsequent procedure to update his/her biometric/password:
- Step 1.
- User will be prompted to enter a new password biometric .
- Step 2.
- will compute , , , .
- Step 3.
- Finally, will replace with .
5. Security Analysis
In the subsequent subsection, formal and informal security analyses for our proposed protocol are performed.
5.1. Informal Security Analysis
The introduced protocol is secure against well-known attacks as presented in the successive subsections:
5.1.1. Replay Attack
In the introduced protocol, timestamps and random numbers are employed to ensure that the introduced protocol is secure from replay attack. Hence, the replay message will be detected if a timestamp is expired, or a random/arbitrary number is inconsistent. So, a replay attack cannot be launched upon the introduced scheme.
5.1.2. Session Key Freshness Property
In the introduced protocol, a session key is constructed by some distinct identities, random numbers, and timestamps, and for each session, random numbers are unique. Hence, a novel key for every session ensures the key’s freshness.
5.1.3. User Anonymity and Untraceability
In the introduced protocol, the user identity is not shared even with the . Additionally, if an attacker tries to capture messages , none of these messages utter any information about the user. Furthermore, the attacker will not be able to extract from the smart card, because he/she will need a password and a biometric to extract the password, and it is also wrapped by hash a function. In addition, in each session, all the values are unique as they are composed of random numbers, and consequently, they are novel for each authentication session. Hence, an adversary will not be able to recognize any specific user or the location of any specific user. Hence, the introduced protocol ensures the anonymity and untraceability of valid user.
5.1.4. Smart Card Stolen Attack
Assume an attacker steals an authorized user’s smart card or it is mishandled and discovered by an attacker, allowing him/her to get any sensitive data from the . An attacker can extract information from the . But to attain any confidential information from the , an attacker needs the information of , , and , and these values are unknown to . Hence, in the introduced protocol, a stolen attack is not conceivable.
5.1.5. Impersonation Attack
If an attacker tries to imitate a , , or towards any other legal participant, to do so, a valid request messages is required. To impersonate as a , tries to create a login request message . However, the attacker cannot generate a true login message because it necessitates the information of . Therefore, the introduced protocol can resist an impersonation attack.
5.1.6. Man-in-the-Middle Attack
Assume an attacker seizes the message and tries to modify a login request or any other message transferring over the public channel. To do this, the attacker requires the knowledge of secret parameters as described in Section 5.1.5. Therefore, the introduced scheme can withstand this attack.
5.1.7. Perfect Forward Secrecy
The shared session key in the introduced protocol includes random nonces included by both and . So, if the private key is in the knowledge of the adversary, he/she still cannot produce previously shared session keys. Hence, the introduced protocol has the feature of perfect forward secrecy.
5.2. AVISPA Tool Based Automated Formal Security Analysis
AVISPA, a tool relying on the Dolev–Yao threat model, was introduced by Armando et al. [38]. In this situation, the attacker can edit, transmit, and alter messages. This tool is well-accepted for assessing various security protocols. AVISPA uses a “high level protocol specification language (HLPSL)” to describe and design security protocols. The HLPSL requirements are broken down into roles. During the execution of a protocol, several roles are utilized to express the activities of a single agent. Each agent performs a specific role throughout the execution of a protocol. HLPSL’s main objective is to verify security properties including message, agent secrecy and authentication. The security protocol is considered to determine its level of security considering the predetermined objectives.
5.2.1. AVISPA Model Checkers
- On-the-fly model checker (OFMC): OFMC uses lazy data types to develop an efficient on-the-fly model for security protocols with limitless state spaces.
- Constraint-logic-based attack searcher (CL-AtSe): The input of (CL-AtSe) is a protocol stated as a set of restrictions that help identify security protocol assaults in the form of a collection of rewriting rules (IF format).
- SAT-based model checker (SATMC): Depending on the transitional state of the IF specification, creates a propositional formula. According to the propositional formula, every violation of security that might result in an attack is considered.
- “Tree automata-based on automatic approximations for the analysis of security protocols“ (TA4SP) model checker: By accurately estimating the attacker’s capabilities, it exposes the protocol’s weakness and predicts its accuracy.
5.2.2. AVISPA Simulation Steps
Automated validation of the protocol was carried out to demonstrate that the introduced protocol could resist reply and man-in-the-middle attacks. The subsequent steps were executed to simulate our protocol in AVISPA:
- Firstly, the scheme was implemented through High-Level Protocols Specification Language (HLPSL) [33], next, the HLPSL2IF translator was employed to interpret HLPSL into Intermediate Format (IF).
5.2.3. Simulation Details
Setting simulated security goals is the first step in building the HLPSL script for our scheme. Our major goal was to keep certain values, such as , secret. Furthermore, we defined the six roles, which are: (1) the trusted authority’s role, (2) the user’s role, (3) the gateway node’s role, (4) the smart device’s role, (5) the role session that combines the basic roles (role_TA, role_USERS, role_GWN, and role_SD), (6) the role environment that incorporates numerous sessions and consists of functions and global variables and outlines the security goals of the protocol.
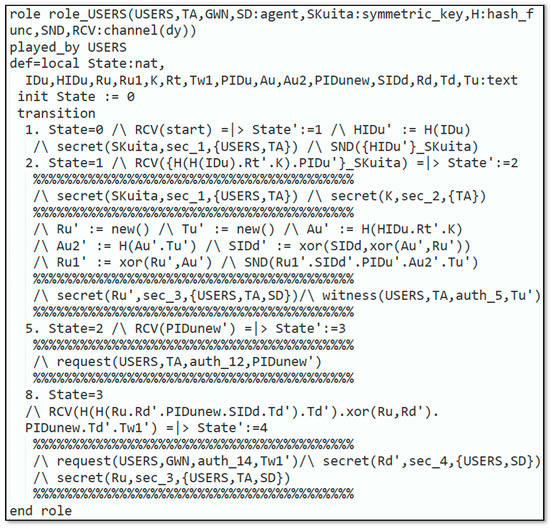
Figure 3.
Role specification for the user.
In Figure 3, the requirement for the role_User that is executed by the user is illustrated. In this role, the knows every agent and the symmetric-key that is joint among the , , the hash function , and the Dolev–Yao model-based send/receive channels . To start the protocol, receives a start message as an indication at the first state (state 0). To register, creates the identity and retransmits after being encrypted with to the . gets and encrypted with coming from the , and the registration process is completed. Next, generates some fresh nonces and computes . Next, transmits to and receives a message from the containing . receives the message coming from the at the next transition. Figure 4. demonstrates the specification for the role_SD which is played by the . In this role, the recognizes all the agents , the symmetric-key which is shared among the and the , the hash function , and the Dolev–Yao-model-based send/receive channels .
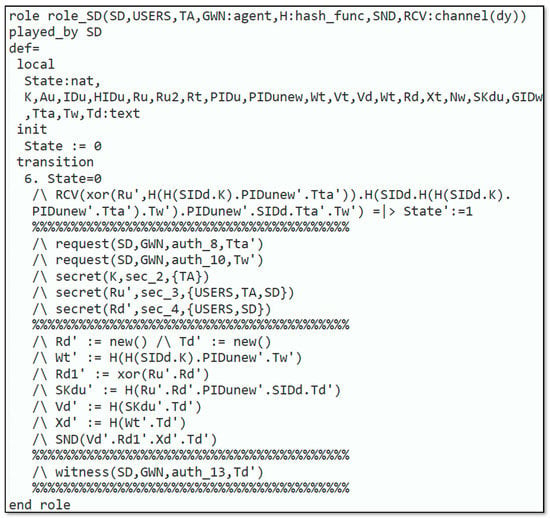
Figure 4.
Role specification for a smart device.
Figure 5 explains the requirement for role_TA, which is executed by the The knows every single agent , the symmetric-key , , and which are common among the and the , and , and among and , respectively. Furthermore, has the knowledge of the and Dolev–Yao-model-based send/receive channels . The remaining part of the requirement defines the various states of the protocol implemented by the TA. Figure 6 displays the specification for role_GWN that is played by the . identifies all the agents , the symmetric-key that is shared amongst the and the , the , and Dolev–Yao-model-based send/receive channels .
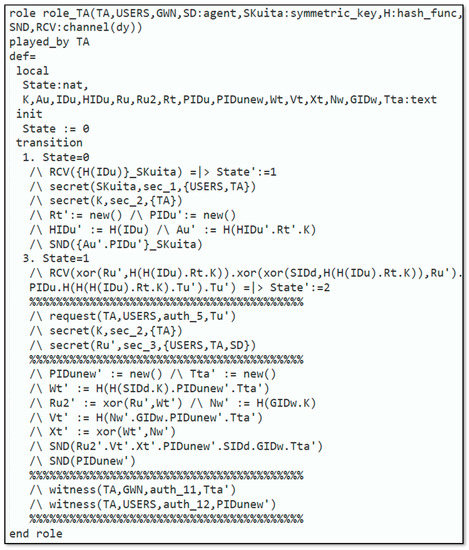
Figure 5.
Role specification for TA.
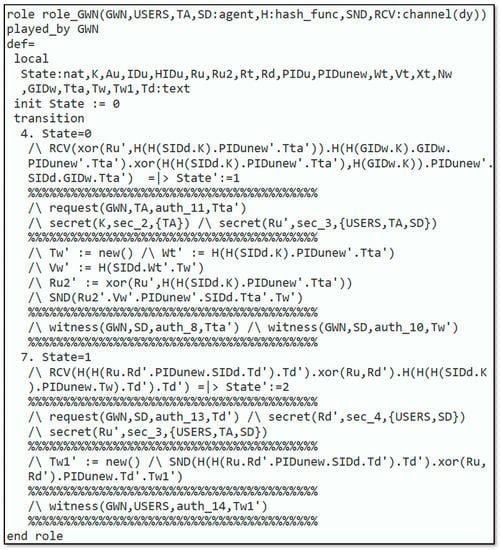
Figure 6.
Role specification for GWN.
Session, environment, and goal roles’ specifications are depicted in Figure 7. In the session role, all roles (role_TA, role_USERS, role_SD, role_GWN) are combined. More than one session is started from the environment role. The constants (ta, users, gwn, sd) represents the agents , respectively. The symmetric key shared among the and is presented by . The hash function is presented by the constant . The applicable parameters that are supposed to be known by the intruder are defined in the intruder knowledge part. We undertake that the intruder has the knowledge of all the agents . The simulation objectives are declared with the help of goal keywords: We are concerned about verifying the secrecy of the subsequent parameters: .
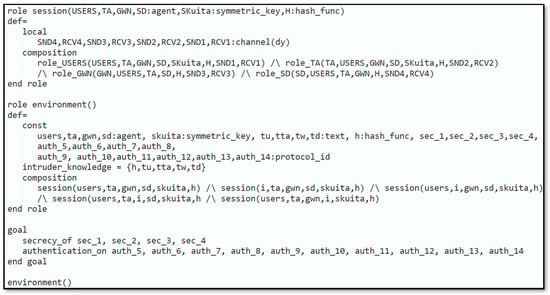
Figure 7.
Role session, environment, and goal.
5.2.4. Simulation Result
Simulation outcomes depicted in Figure 8 and Figure 9 revealed that the introduced protocol was according to the design specifications and could hold out against replay and man-in-the-middle attacks. Based on the AVISPA backend model checker, OFMC and CL-AtSe simulation results are presented. With depth piles in s, nodes were scrutinized in the OFMC backend. The CL-AtSe backend inspected states, the computation and interpretation consumed for the backend were s and s, respectively.
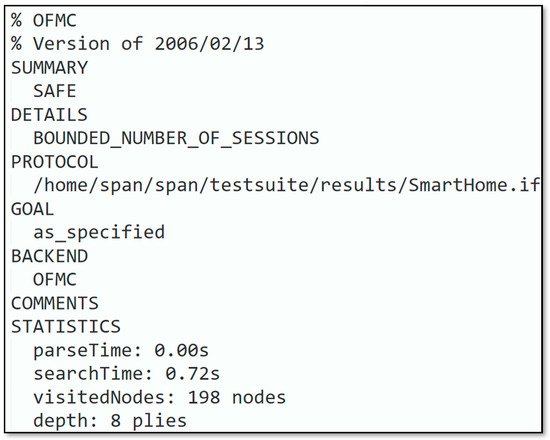
Figure 8.
OFMC backend analysis.
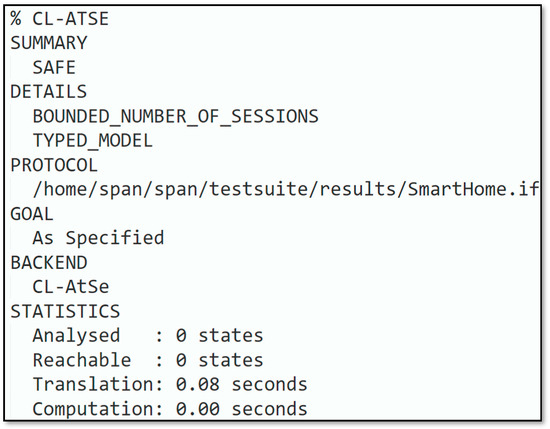
Figure 9.
CL-AtSe backend analysis.
6. Comparative Analysis
This section provides the comparison of our proposed protocol with the existing protocols, which includes those of Banerjee et al. [23], Shuai et al. [34], Yu and Li [39], Naoui et al. [40], Fakroon et al. [41], and Dey and Hossain [29].
6.1. Functionality Comparison
The functionality analysis was performed with respect to the existing and proposed protocols as presented Table 6. As per comparison, the proposed protocol rendered superior security along with enhanced security features in contrast to those of [23] and other compared protocols. Here, is the compared feature/security requirement, shows that the specified parameter exists in this study, and the protocol can resist an attack. Moreover, presents whether the protocol is not able to resist an attack or lacks a specific feature, whereas the − sign shows that a certain security/feature requirement is not applicable.

Table 6.
Comparison of functionality features.
6.2. Comparison of Communication Overhead
In Table 7, the communication expenses estimate is presented. In order to compare, the sizes of various parameters taken were as follows: identities were considered as bits, a timestamp was bits, random nonces were bits, a hash digest was bits (if SHA-1 is employed [42]), cost for ECC point was bits, and size of symmetric enc/decryption block was bits [43,44], respectively.

Table 7.
Communication cost comparison.
The communication cost of was bits, was bits, was bits, was bits, is bits, and cost for was bits. Summing all these, the total cost of communication of the introduced protocol through the login and authentication phase becomes bytes. In addition, Table 7 shows that the communication cost of the introduced protocol was less than that of those in comparison [39,42] and slightly higher than that of [23,34,40,41], but this is justifiable as the introduced protocol provides better security than these other protocols do. Figure 10 also depicts the communication cost of our proposed protocol.
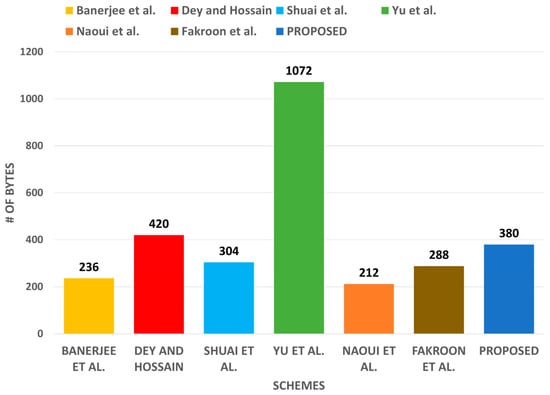
Figure 10.
Communication cost comparison.
6.3. Computation Overhead Comparison
This section compares the computation cost of different protocols. Table 8 shows the approximate computation times expected for different cryptographic procedures and their notations. Based on a real-time environment, an experiment was conducted over a smartphone using MIRACL Library. The smartphone Redmi Note 8 presented as a mobile/user device with the specification of Octa-core Max 2.01 GHz processor, 4 GB RAM, MIUI version 11.0.7, and the underlying Android version was 9. For GSS, over the Ubuntu 16.0 LTS operating system, an HP EliteBook 8460P with 4 GB RAM and an Intel Core i7-2620 M 2.7 GHz processor was used. Additionally, to replicate the smart devices, a Pi3 B+ with Cortex-A53(ARMv8) 64-bit SoC @ 1.4 GHz processor and 1 GB LPDDR2 SDRAM RAM was used. The simulation results on each device are given in Table 8, which shows the approximate computation times expected for different cryptographic procedures in ms and their notations [45]. We assumed here that .

Table 8.
Approximate computation time of various operations.
As represented in Table 9, the computation cost of the proposed protocol is a bit high as compared to those of [23,41]. However, it is justified when compared to the security provided by the introduced protocol, as it is shown in Table 6 that these protocols lack some security features. Figure 11 also depicts the computation cost of the introduced protocol.

Table 9.
Computation cost comparison.
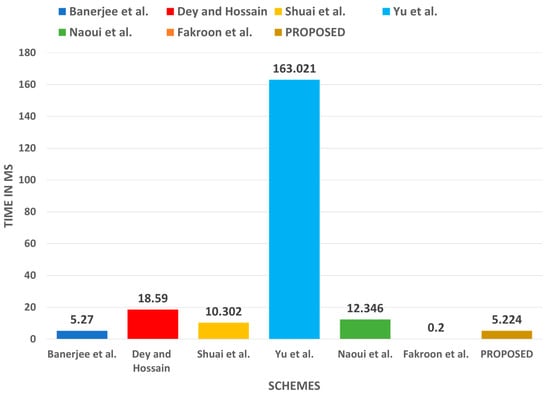
Figure 11.
Computation cost comparison.
7. Conclusions
The Internet of Things (IoT) is turning into the mainstream with each passing day. Applications of the IoT are not limited to only military or industrial use; nowadays, the IoT is employed in homes, agriculture, and even in the medical field. IoT privacy and security issues gradually increase. To subdue the privacy and security issues related to smart homes, various schemes have been introduced and claimed as robust and with anonymous authentication protocols for a smart-home environment. In this paper, we introduced a protocol to overcome the vulnerabilities found in a previous protocol. In the introduced protocol, no parameters are stored in the verifier table whose disclosure can lead to system compromise, a is also included to authenticate the users, and a broadcasting issue is also mitigated to improve resource utilization. Security and comparative analyses of the introduced protocol were performed to show that the introduced protocol was secure and provided better security features with low communication and computation costs. Authentication schemes for a smart-home environment should be lightweight and secure. Many schemes proposed earlier are lightweight but not secure because in achieving lightweight features they neglect security. Similarly, some schemes are more secure but not lightweight, which is undesirable for a smart-home environment. Hence, there is a need to work on both factors at the same time.
Author Contributions
R.M.A.H.-u.-r., conceptualization, methodology, M.L. review; A.H.M.A., supervision; A.A.A., computation cost; M.K.H., formal security analysis; Z.A., draft formatting and draft preparation; R.L.A., literature review. All authors have read and agreed to the published version of the manuscript.
Funding
Under grant FRGS/1/2019/ICT03/UKM/02/1.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
This work was supported by the Faculty of Information Science and Technology, University Kebangsaan Malaysia, Bangi, Selangor, 43600, Malaysia under grant FRGS/1/2019/ICT03/UKM/02/1. The authors, therefore, acknowledge with thanks for the technical and financial support.
Conflicts of Interest
The authors declare no conflict of interests.
References
- Hong, A.; Nam, C.; Kim, S. What will be the possible barriers to consumers’ adoption of smart home services? Telecommun. Policy 2020, 44, 101867. [Google Scholar] [CrossRef]
- Aman, A.H.M.; Hassan, W.H.; Sameen, S.; Attarbashi, Z.S.; Alizadeh, M.; Latiff, L.A. Iomt amid COVID-19 pandemic: Application, architecture, technology, and security. J. Netw. Comput. Appl. 2020, 174, 102886. [Google Scholar] [CrossRef] [PubMed]
- Aman, A.H.M.; Yadegaridehkordi, E.; Attarbashi, Z.S.; Hassan, R.; Park, Y.-J. A Survey on Trend and Classification of Internet of Things Reviews. IEEE Access 2020, 8, 111763–111782. [Google Scholar] [CrossRef]
- Hassan, R.; Qamar, F.; Hasan, M.K.; Aman, A.H.M.; Ahmed, A.S. Internet of Things and Its Applications: A Comprehensive Survey. Symmetry 2020, 12, 1674. [Google Scholar] [CrossRef]
- Sadeq, A.S.; Hassan, R.; Aman, A.H.M.; Sallehudin, H.; Allehaibi, K.; Albogami, N.; Prabuwono, A.S. MAC protocol with grouping awareness GMAC for large scale Internet-of-Things network. PeerJ Comput. Sci. 2021, 7, e733. [Google Scholar] [CrossRef]
- Aman, A.H.M.; Shaari, N.; Ibrahim, R. Internet of things energy system: Smart applications, technology advancement, and open issues. Int. J. Energy Res. 2021, 45, 8389–8419. [Google Scholar] [CrossRef]
- Bringhenti, D.; Valenza, F.; Basile, C. Toward Cybersecurity Personalization in Smart Homes. IEEE Secur. Priv. 2022, 20, 45–53. [Google Scholar] [CrossRef]
- Reig, S.; Fong, T.; Forlizzi, J.; Steinfeld, A. Theory and Design Considerations for the User Experience of Smart Environments. IEEE Trans. Hum.-Mach. Syst. 2022, 52, 522–535. [Google Scholar] [CrossRef]
- Pathy, B.; Sujatha, R. IoT Enabled Smart Connected Homes and Its Social Graces. In Internet of Things and Its Applications; Springer: Cham, Switzerland, 2022; pp. 477–496. [Google Scholar] [CrossRef]
- Zhang, S.; Rong, J.; Wang, B. A privacy protection scheme of smart meter for decentralized smart home environment based on consortium blockchain. Int. J. Electr. Power Energy Syst. 2020, 121, 106140. [Google Scholar] [CrossRef]
- Aubel, P.V.; Poll, E. Smart metering in the netherlands: What, how, and why. Int. J. Electr. Power Energy Syst. 2019, 109, 719–725. [Google Scholar] [CrossRef]
- Jin, M.; Jia, R.; Spanos, C.J. Virtual Occupancy Sensing: Using Smart Meters to Indicate Your Presence. IEEE Trans. Mob. Comput. 2017, 16, 3264–3277. [Google Scholar] [CrossRef]
- Jin, M.; Bekiaris-Liberis, N.; Weekly, K.; Spanos, C.J.; Bayen, A.M. Occupancy detection via environmental sensing. IEEE Trans. Autom. Sci. Eng. 2018, 15, 443–455. [Google Scholar] [CrossRef]
- Taccardi, B.; Rametta, P.; Carcagnì, P.; Leo, M.; Distante, C.; Patrono, L. An innovative AAL system based on neural networks and IoT-aware technologies to improve the quality of life in elderly people. Int. J. Intell. Syst. Technol. Appl. 2020, 19, 589–617. [Google Scholar] [CrossRef]
- Smys, S. A Survey on Internet of Things (IoT) based Smart Systems. J. ISMAC 2020, 2, 181–189. [Google Scholar] [CrossRef]
- Oliveira, R.N.; Roth, V.; Henzen, A.F.; Simao, J.M.; Nohama, P.; Wille, E.C.G. Notification Oriented Paradigm Applied to Ambient Assisted Living Tool. IEEE Lat. Am. Trans. 2018, 16, 647–653. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Eisenbarth, T.; Kasper, T.; Moradi, A.; Paar, C.; Salmasizadeh, M.; Shalmani, M.T.M. On the Power of Power Analysis in the Real World: A Complete Break of the KeeLoq Code Hopping Scheme. In Advances in Cryptology—CRYPTO 2008; Lecture Notes in Computer Science; Wagner, D., Ed.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 203–220. [Google Scholar] [CrossRef]
- Yang, W.-H.; Shieh, S.-P. Password authentication schemes with smart cards. Comput. Secur. 1999, 18, 727–733. [Google Scholar] [CrossRef]
- Hölbl, M.; Welzer, T.; Brumen, B. An improved two-party identity-based authenticated key agreement protocol using pairings. J. Comput. Syst. Sci. 2012, 78, 142–150. [Google Scholar] [CrossRef] [Green Version]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology—CRYPTO’ 99; Wiener, M., Ed.; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Messerges, T.; Dabbish, E.; Sloan, R. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef]
- Farayez, A.; Reaz, M.B.I.; Arsad, N. SPADE: Activity Prediction in Smart Homes Using Prefix Tree Based Context Generation. IEEE Access 2018, 7, 5492–5501. [Google Scholar] [CrossRef]
- Shakeri, M.; Shayestegan, M.; Abunima, H.; Reza, S.S.; Akhtaruzzaman, M.; Alamoud, A.; Sopian, K.; Amin, N. An intelligent system architecture in home energy management systems (HEMS) for efficient demand response in smart grid. Energy Build. 2017, 138, 154–164. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Piro, G.; Boggia, G.; Bianchi, G. Public Key Authentication and Key Agreement in IoT Devices With Minimal Airtime Consumption. IEEE Embed. Syst. Lett. 2016, 9, 1–4. [Google Scholar] [CrossRef]
- Hasan, M.K.; Shafiq, M.; Islam, S.; Pandey, B.; El-Ebiary, Y.A.B.; Nafi, N.S.; Rodriguez, R.C.; Vargas, D.E. Lightweight Cryptographic Algorithms for Guessing Attack Protection in Complex Internet of Things Applications. Complexity 2021, 2021, 5540296. [Google Scholar] [CrossRef]
- Alshahrani, M.; Traore, I. Secure mutual authentication and automated access control for IoT smart home using cumulative Keyed-hash chain. J. Inf. Secur. Appl. 2019, 45, 156–175. [Google Scholar] [CrossRef]
- Dey, S.; Hossain, A. Session-Key Establishment and Authentication in a Smart Home Network Using Public Key Cryptography. IEEE Sens. Lett. 2019, 3, 7500204. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Iinatti, J.; Ylianttila, M.; Sain, M. Lightweight and Secure Session-Key Establishment Scheme in Smart Home Environments. IEEE Sens. J. 2015, 16, 254–264. [Google Scholar] [CrossRef]
- Kumar, P.; Braeken, A.; Gurtov, A.; Iinatti, J.; Ha, P.H. Anonymous Secure Framework in Connected Smart Home Environments. IEEE Trans. Inf. Forensics Secur. 2017, 12, 968–979. [Google Scholar] [CrossRef] [Green Version]
- Gope, P.; Sikdar, B. Lightweight and Privacy-Preserving Two-Factor Authentication Scheme for IoT Devices. IEEE Internet Things J. 2018, 6, 580–589. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure Remote User Authenticated Key Establishment Protocol for Smart Home Environment. IEEE Trans. Dependable Secur. Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Lee, Y.S.; Lee, H.J.; Alasaarela, E. Mutual authentication in wireless body sensor networks (WBSN) based on Physical Unclonable Function (PUF). In Proceedings of the 2013 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013; pp. 1314–1318. [Google Scholar] [CrossRef]
- Khernane, N.; Potop-Butucaru, M.; Chaudet, C. BANZKP: A secure authentication scheme using zero knowledge proof for WBANs. In Proceedings of the 2016 IEEE 13th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Brasilia, Brazil, 10–13 October 2016. [Google Scholar]
- Koya, A.M.; Deepthi, P.P. Anonymous hybrid mutual authentication and key agreement scheme for wireless body area network. Comput. Netw. 2018, 140, 138–151. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar] [CrossRef]
- Yu, B.; Li, H. Anonymous authentication key agreement scheme with pairing-based cryptography for home-based multi-sensor Internet of Things. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719879379. [Google Scholar] [CrossRef]
- Naoui, S.; Elhdhili, M.H.; Saidane, L.A. Novel smart home authentication protocol LRP-SHAP. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019. [Google Scholar]
- Fakroon, M.; Alshahrani, M.; Gebali, F.; Traore, I. Secure remote anonymous user authentication scheme for smart home environment. Internet Things 2020, 9, 100158. [Google Scholar] [CrossRef]
- Eastlake, D., 3rd; Jones, P. US secure hash algorithm 1 (SHA1). RFC 2001, 3174, 1–22. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the internet of things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Alotaibi, M. An Enhanced Symmetric Cryptosystem and Biometric-Based Anonymous User Authentication and Session Key Establishment Scheme for WSN. IEEE Access 2018, 6, 70072–70087. [Google Scholar] [CrossRef]
- Hussain, S.; Chaudhry, S.A.; Alomari, O.A.; Alsharif, M.H.; Khan, M.K.; Kumar, N. Amassing the Security: An ECC-Based Authentication Scheme for Internet of Drones. IEEE Syst. J. 2021, 15, 4431–4438. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).