A Novel Decentralized Blockchain Architecture for the Preservation of Privacy and Data Security against Cyberattacks in Healthcare
Abstract
1. Introduction
- It proposes a decentralized blockchain architecture for privacy and data protection against healthcare cyber-attacks.
- Using blockchain, we are proposing a privacy-preserving and secure hash algorithm.
- The effectiveness of our proposed framework is determined by performing a security review on cyber-attack.
- The performance of our proposed novel decentralized blockchain architecture is evaluated by comparison with the existing models with respect to several performance criteria.
2. Related Work
Research Gap in Current Solution and Motivation
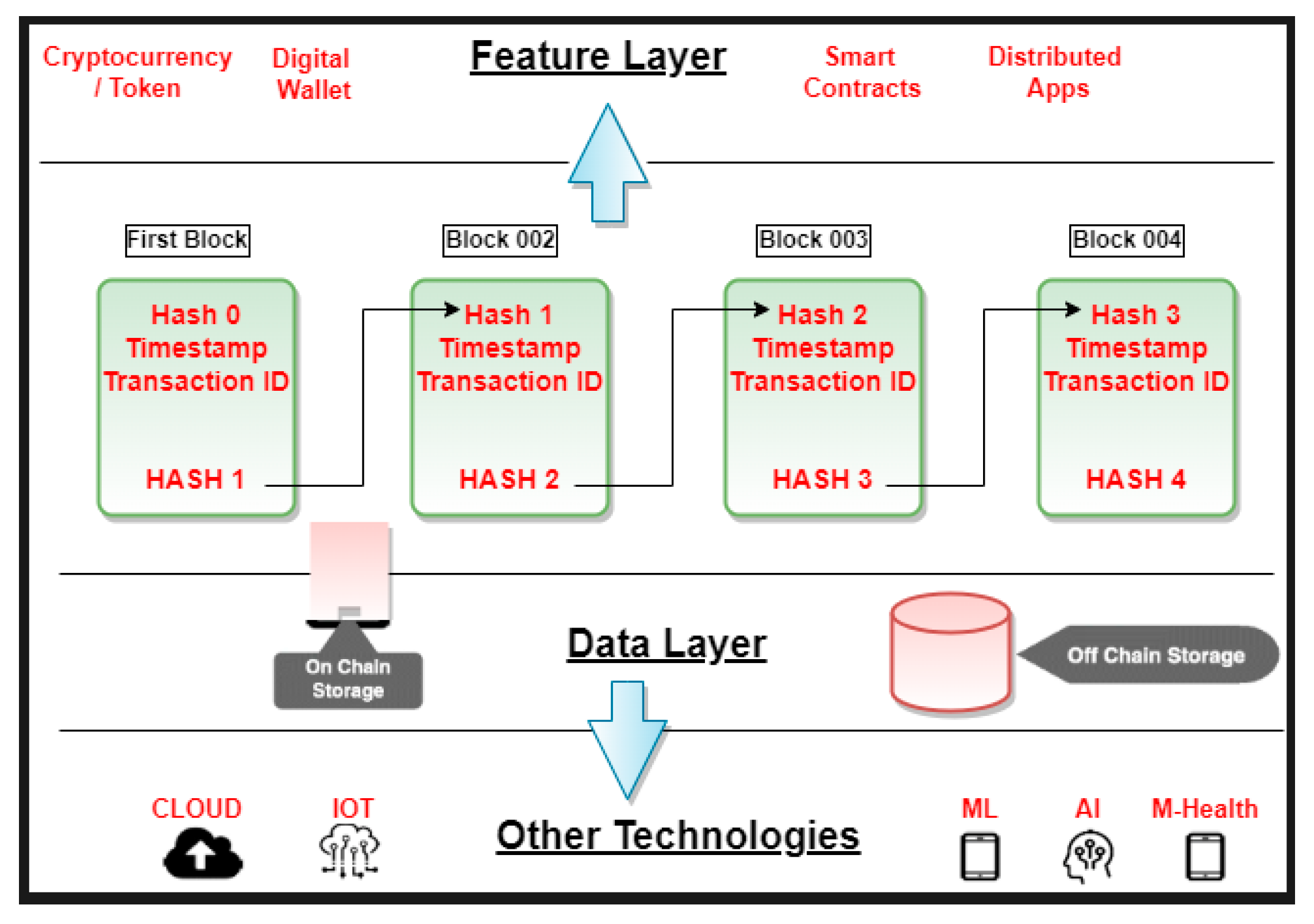
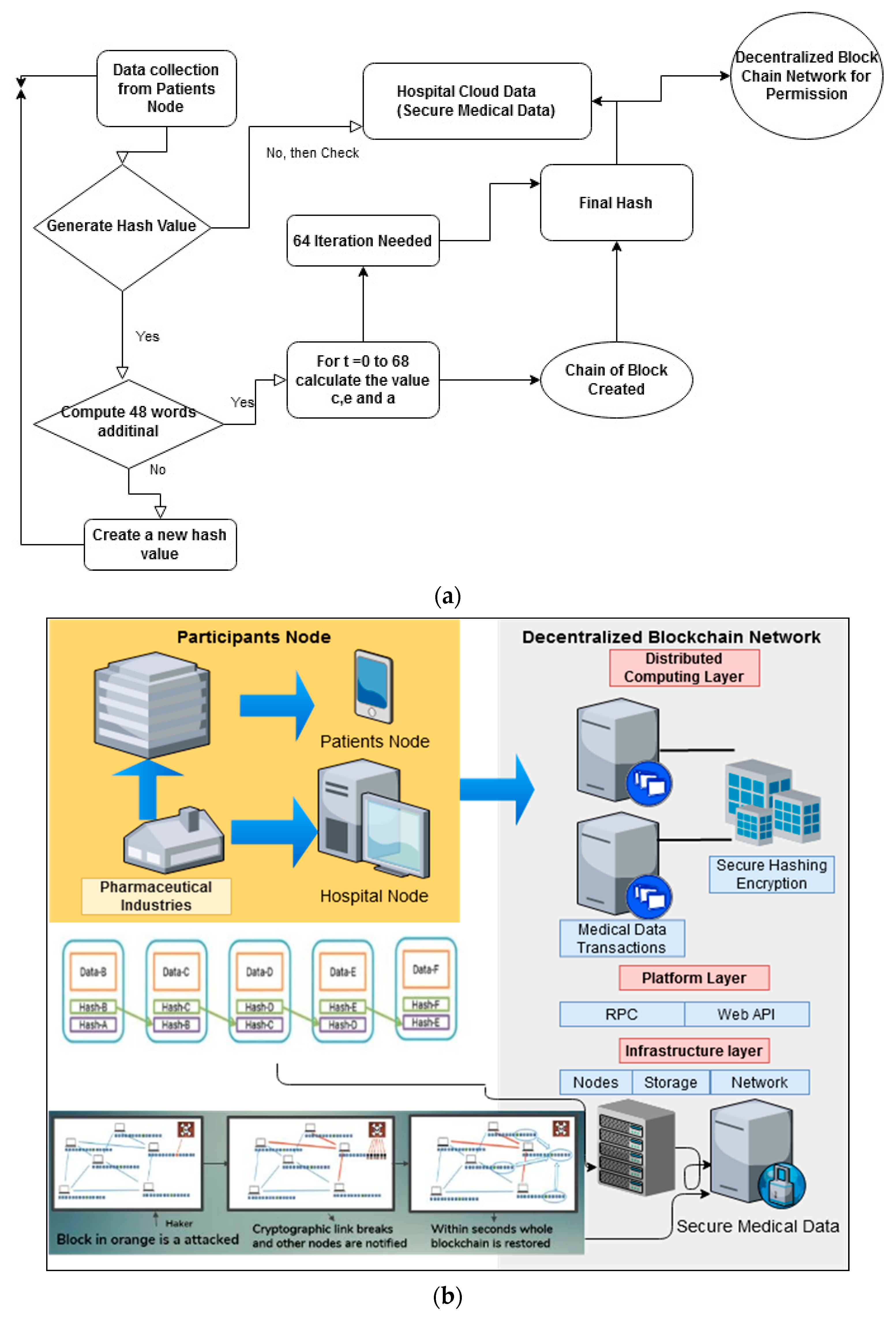
3. The Proposed Approach
3.1. Participant Nodes
3.2. Secure Hashing Encryption
| Algorithm 1 Proposed Algorithm |
| Input: In the blockchain, Input “data.” Data can be anything like a word, a line, a paragraph, or multiple paragraphs. data can be transactions of any digital currency. Output: A block created for every set of data. And as a result, a chain of the block is created known as the blockchain. START: FOR EVERY Step 1: Pre-processing: Generate a hash for the data. The hash depends upon the previous hash and the data in the current hash. Initial hash value (ph = 2,3,5,7,11,13,17,19) Now, we compute additional 48 words, totaling the number of words to 64. Here we compute the 10th word (). Step 4: Generate a new block with hash values (a, b, c, d, e, f, g, h) for other sets of data. Step 5: The chain of the block created is known as the blockchain. Step 6: TO COMPUTE THE FINAL HASH, RUN THE 64 ITERATIONS OF STEP 4. |
4. Experimental Setup and Implementation
4.1. Creating a Blockchain Class
4.2. Proof of Work
4.3. Hash Algorithm: Block Passed in the Method
4.4. Creating Complete Blockchain
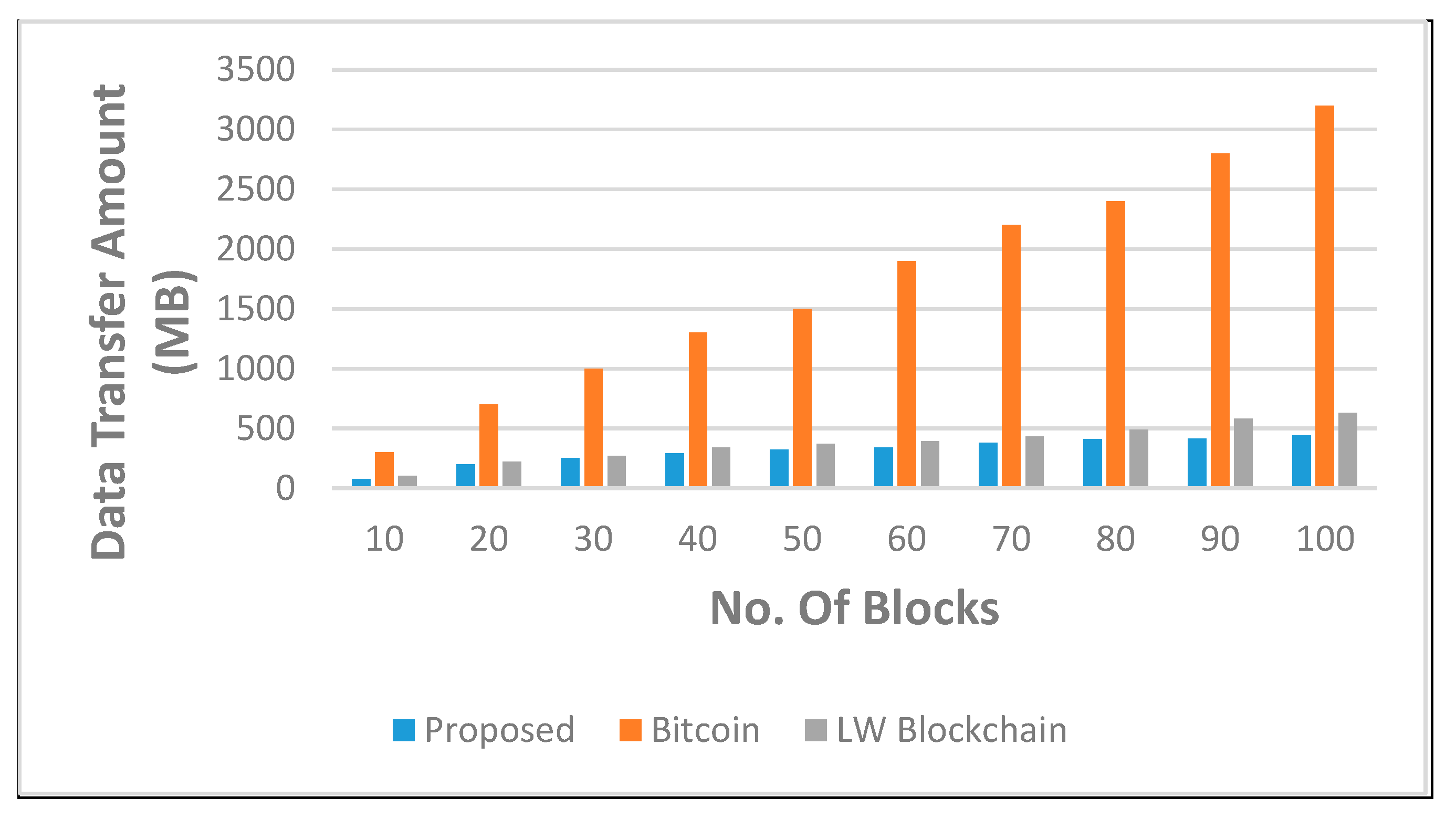
4.5. Performance Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Tufail, A.B.; Ullah, I.; Khan, W.U.; Asif, M.; Ahmad, I.; Ma, Y.K.; Khan, R.; Ali, M. Diagnosis of diabetic retinopathy through retinal fundus images and 3D convolutional neural networks with limited number of samples. Wirel. Commun. Mob. Comput. 2021. [Google Scholar] [CrossRef]
- Banerjee, M.; Lee, J.; Choo, K.K.R. A blockchain future for internet of things security: A position paper. Dig. Commun. Netw. 2018, 4, 149–160. [Google Scholar] [CrossRef]
- Ekblaw, A.; Azaria, A.; Halamka, J.D.; Lippman, A. A case study for blockchain in healthcare: “MedRec” prototype for electronic health records and medical research data. In Proceedings of the IEEE Open & Big Data Conference, Montreal, QC, Canada, 17–19 October 2016; Volume 13, p. 13. [Google Scholar]
- Andoni, M.; Robu, V.; Flynn, D.; Abram, S.; Geach, D.; Jenkins, D.; McCallum, P.; Peacock, A. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 2019, 100, 143–174. [Google Scholar] [CrossRef]
- Razib, A.M.; Javeed, D.; Khan, M.T.; Alkanhel, R.; Muthanna, M.S.A. Cyber Threats Detection in Smart Environments Using SDN-Enabled DNN-LSTM Hybrid Framework. IEEE Access 2022, 10, 53015–53026. [Google Scholar] [CrossRef]
- Cai, C.W. Disruption of financial intermediation by FinTech: A review on crowdfunding and blockchain. Account. Financ. 2018, 58, 965–992. [Google Scholar] [CrossRef]
- Griggs, K.N.; Ossipova, O.; Kohlios, C.P.; Baccarini, A.N.; Howson, E.A.; Hayajneh, T. Healthcare blockchain system using smart contracts for secure automated remote patient monitoring. J. Med. Syst. 2018, 42, 130. [Google Scholar] [CrossRef]
- Islam, U.; Muhammad, A.; Mansoor, R.; Hossain, M.S.; Ahmad, I.; Eldin, E.T.; Khan, J.A.; Rehman, A.U.; Shafiq, M. Detection of Distributed Denial of Service (DDoS) Attacks in IOT Based Monitoring System of Banking Sector Using Machine Learning Models. Sustainability 2022, 14, 8374. [Google Scholar] [CrossRef]
- Raza, A.; Ayub, H.; Khan, J.A.; Ahmad, I.; S Salama, A.; Daradkeh, Y.I.; Javeed, D.; Ur Rehman, A.; Hamam, H. A Hybrid Deep Learning-Based Approach for Brain Tumor Classification. Electronics 2022, 11, 1146. [Google Scholar] [CrossRef]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 136. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y.; Ma, M.; He, J. BlocHIE: A blockchain-based platform for healthcare information exchange. In Proceedings of the IEEE International Conference on Smart Computing (SMARTCOMP), Taormina, Italy, 18–20 June 2018; pp. 49–56. [Google Scholar]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Ichikawa, D.; Kashiyama, M.; Ueno, T. Tamper-resistant mobile health using blockchain technology. JMIR Mhealth Uhealth 2017, 5, e111. [Google Scholar] [CrossRef]
- Featherstone, I.; Keen, J. Do integrated record systems lead to integrated services? An observational study of a multi-professional system in a diabetes service. Int. J. Med. Inform. 2012, 81, 45–52. [Google Scholar] [CrossRef]
- Bocek, T.; Rodrigues, B.B.; Strasser, T.; Stiller, B. Blockchains everywhere—A use-case of blockchains in the pharma supply-chain. In Proceedings of the IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 772–777. [Google Scholar]
- Wang, Y.; Taylan, O.; Alkabaa, A.S.; Ahmad, I.; Tag-Eldin, E.; Nazemi, E.; Balubaid, M.; Alqabbaa, H.S. An Optimization on the Neuronal Networks Based on the ADEX Biological Model in Terms of LUT-State Behaviors: Digital Design and Realization on FPGA Platforms. Biology 2022, 11, 1125. [Google Scholar] [CrossRef]
- Ahmad, S.; Ullah, T.; Ahmad, I.; Al-Sharabi, A.; Ullah, K.; Khan, R.A.; Rasheed, S.; Ullah, I.; Uddin, M.; Ali, M. A Novel Hybrid Deep Learning Model for Metastatic Cancer Detection. Comput. Intell. Neurosci. 2022. [Google Scholar] [CrossRef]
- Ullah, N.; Khan, J.A.; Alharbi, L.A.; Raza, A.; Khan, W.; Ahmad, I. An Efficient Approach for Crops Pests Recognition and Classification Based on Novel DeepPestNet Deep Learning Model. IEEE Access 2022, 10, 73019–73032. [Google Scholar] [CrossRef]
- Ahmad, I.; Liu, Y.; Javeed, D.; Ahmad, S. A decision-making technique for solving order allocation problem using a genetic algorithm. In Proceedings of the 2020 The 6th International Conference on Electrical Engineering, Control and Robotics, Xiamen, China, 10–12 January 2020. [Google Scholar]
- Roehrs, A.; da Costa, C.A.; da Rosa Righi, R. OmniPHR: A distributed architecture model to integrate personal health records. J. Biomed. Inform. 2017, 71, 70–81. [Google Scholar] [CrossRef]
- Alketbi, A.; Nasir, Q.; Talib, M.A. Blockchain for government services—Use cases, security benefits and challenges. In Proceedings of the IEEE 2018 15th Learning and Technology Conference (L&T), Jeddah, Saudi Arabia, 25–26 February 2018; pp. 112–119. [Google Scholar]
- Raj, M.; Singh, A.K. Humanoid gait pattern generation with orbital energy. J. Circuits Syst. Comput. 2021, 30, 2150259. [Google Scholar] [CrossRef]
- Sharma, V.; Chauhan, A.; Saxena, H.; Mishra, S.; Bansal, S. Secure file storage on cloud using hybrid cryptography. In Proceedings of the 5th International Conference on Information Systems and Computer Networks (ISCON), Mathura, India, 22 October 2021; pp. 1–6. [Google Scholar]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using blockchain for medical data access and permission management. In Proceedings of the 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar]
- Kassab, M.; DeFranco, J.; Malas, T.; Neto, V.V.G.; Destefanis, G. Blockchain: A Panacea for Electronic Health Records? In Proceedings of the IEEE/ACM 1st International Workshop on Software Engineering for Healthcare (SEH), Montreal, QC, Canada, 27 May 2019; pp. 21–24. [Google Scholar]
- Hussien, H.; Yasin, S.; Udzir, N.; Zaidan, A.; Bahaa, B. A Systematic Review for Enabling of Develop a Blockchain Technology in Healthcare Application: Taxonomy, Substantially Analysis, Motivations, Challenges, Recommendations and Future Direction. J. Med. Syst. 2019, 43, 320. [Google Scholar] [CrossRef]
- De Aguiar, E.J.; Faiçal, B.S.; Krishnamachari, B.; Ueyama, J. A Survey of Blockchain-Based Strategies for Healthcare. ACM Comput. Surv. 2020, 53, 27. [Google Scholar] [CrossRef]
- Javeed, D.; Gao, T.; Khan, M.T.; Ahmad, I. A Hybrid Deep Learning-Driven SDN Enabled Mechanism for Secure Communication in Internet of Things (IoT). Sensors 2021, 21, 4884. [Google Scholar] [CrossRef]
- Janardhana Swamy, G.B.; Janardhana, D.R.; Vijay, C.P.; Ravi, V. Blockchain-Enabled IoT Integrated Autonomous Sewage Management System. In Convergence of Internet of Things and Blockchain Technologies; Springer: Cham, Switzerland, 2022; pp. 41–56. [Google Scholar]
- Khan, T.U. Internet of Things (IOT) systems and its security challenges. Int. J. Adv. Res. Comput. Eng. Technol. (IJARCET) 2019, 8. [Google Scholar]
- Sinaci, A.A.; Erturkmen, G.B.L. A federated semantic metadata registry framework for enabling interoperability across clinical research and care domains. J. Biomed. Inform. 2013, 46, 784–794. [Google Scholar] [CrossRef]
- Marwa, K.; Turnbull, B.; Sitnikova, E.; Vatsalan, D.; Moustafa, N. Privacy-preserving schemes for safeguarding heterogeneous data sources in cyber-physical systems. IEEE Access 2021, 9, 55077–55097. [Google Scholar]
- Tripathi, R.K.; Jalal, A.S. Novel local feature extraction for age invariant face recognition. Expert Syst. Appl. 2021, 175, 114786. [Google Scholar] [CrossRef]
- Agarwal, R. Local and global features based on ear recognition system. In International Conference on Artificial Intelligence and Sustainable Engineering; Springer: Singapore, 2022; pp. 477–486. [Google Scholar]
- Ali, S.; Javaid, N.; Javeed, D.; Ahmad, I.; Ali, A.; Badamasi, U.M. A blockchain-based secure data storage and trading model for wireless sensor networks. In Proceedings of the International Conference on Advanced Information Networking and Applications, Caserta, Italy, 15–17 April 2020. [Google Scholar]
- Javeed, D.; Gao, T.; Khan, M.T. SDN-Enabled Hybrid DL-Driven Framework for the Detection of Emerging Cyber Threats in IoT. Electronics 2021, 10, 918. [Google Scholar] [CrossRef]
- Bingqing, S.; Guo, J.; Yang, Y. MedChain: Efficient healthcare data sharing via blockchain. Appl. Sci. 2019, 9, 6. [Google Scholar]
- Hyppönen, H.; Reponen, J.; Lääveri, T.; Kaipio, J. User experiences with different regional health information exchange systems in Finland. Int. J. Med. Inform. 2014, 83, 1–18. [Google Scholar] [CrossRef]
- Javeed, D.; Gao, T.; Khan, M.T.; Shoukat, D. A Hybrid Intelligent Framework to Combat Sophisticated Threats in Secure Industries. Sensors 2022, 22, 1582. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-less medical data sharing among cloud service providers via blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Zhang, P.; White, J.; Schmidt, D.C.; Lenz, G.; Rosenbloom, S.T. FHIRChain: Applying blockchain to securely and scalably share clinical data. Comput. Struct. Biotech. J. 2018, 16, 267–278. [Google Scholar] [CrossRef] [PubMed]






| Application Area | Summary of Work Carried Out or Proposed |
|---|---|
| Ekblaw, A. et al. [3] suggested the development of a patient-centered approach for bias-free, non-hidden, authorized access and view of patient medical history (Ethereum model proposed/used) | |
| Xia, Q. et al. [40] applied techniques on cloud databases for sharing medical data. (Ethereum model proposed/used) | |
| Zhang P et al. [41]: An EMR application using the blockchain is proposed (Ethereum model proposed/used) | |
| Fan, K. et al. [10]: An EMR management application using the blockchain is proposed. (Proprietary model proposed/used) | |
| Jiang, S. et al. [11] proposed a system for storage of off chain data and verification of on chain in healthcare sector. (Proprietary model proposed/used). | |
| Dagher, G.G. et al. [12]: A secured EHR system is proposed that secures personal information related to patients’ health. (Ethereum model proposed/used) | |
| Remote patient monitoring (RPM) | Ichikawa, D. et al. [13] suggested a mobile health blockchain-based system for insomnia. (Hyperledger fabric model proposed/used) |
| Griggs, K.N. et al. [7] migrated the use of the IoT with blockchain technology for data collection and security. | |
| Pharmaceutical supply chain (PSC) | Bocek, T. et al. [15]. proposed a system for maintaining the drug temperature record while in transit and transportation. (Ethereum model proposed/used) |
| Bocek, T. et al. [15] suggested a mechanism to explore a blockchain implementation in healthcare for efficient traceability to the drugs supply. | |
| Miler et al. [30] proposed a design on immutable and secure PSC. (Hyperledger fabric model proposed/used) | |
| Health insurance claims (HIC) | Zaman et al. [36] suggested work and implementation on the medical and health insurance claims storage mechanism. (Ethereum model proposed/used) |
| Hardware Setup | Processor | Intel Xeon X5355 2.66 GHz (8 Cores) |
| Memory | 8 GB RAM | |
| Storage | 2 × 146 GM | |
| Network Interface | 1 GbE | |
| Software Setup | Anaconda (Spyder) | IDE Used for Implementation |
| Flask | A web framework for blockchain communication | |
| Postman | Display the information | |
| Simulation Criteria | Block Size | 1 MB |
| Hash Function Size | 256 bytes | |
| Nodes (Blockchain cluster) | 100(10), 200(20), 300(30), and 400(40) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kumar, A.; Singh, A.K.; Ahmad, I.; Kumar Singh, P.; Anushree; Verma, P.K.; Alissa, K.A.; Bajaj, M.; Ur Rehman, A.; Tag-Eldin, E. A Novel Decentralized Blockchain Architecture for the Preservation of Privacy and Data Security against Cyberattacks in Healthcare. Sensors 2022, 22, 5921. https://doi.org/10.3390/s22155921
Kumar A, Singh AK, Ahmad I, Kumar Singh P, Anushree, Verma PK, Alissa KA, Bajaj M, Ur Rehman A, Tag-Eldin E. A Novel Decentralized Blockchain Architecture for the Preservation of Privacy and Data Security against Cyberattacks in Healthcare. Sensors. 2022; 22(15):5921. https://doi.org/10.3390/s22155921
Chicago/Turabian StyleKumar, Ajitesh, Akhilesh Kumar Singh, Ijaz Ahmad, Pradeep Kumar Singh, Anushree, Pawan Kumar Verma, Khalid A. Alissa, Mohit Bajaj, Ateeq Ur Rehman, and Elsayed Tag-Eldin. 2022. "A Novel Decentralized Blockchain Architecture for the Preservation of Privacy and Data Security against Cyberattacks in Healthcare" Sensors 22, no. 15: 5921. https://doi.org/10.3390/s22155921
APA StyleKumar, A., Singh, A. K., Ahmad, I., Kumar Singh, P., Anushree, Verma, P. K., Alissa, K. A., Bajaj, M., Ur Rehman, A., & Tag-Eldin, E. (2022). A Novel Decentralized Blockchain Architecture for the Preservation of Privacy and Data Security against Cyberattacks in Healthcare. Sensors, 22(15), 5921. https://doi.org/10.3390/s22155921











