A Novel Virtual Optical Image Encryption Scheme Created by Combining Chaotic S-Box with Double Random Phase Encoding
Abstract
:1. Introduction
- (1)
- Exploring a chaotic map and conducting the transformation of stretch and fold to construct an efficient and secure S-box. The cryptographic performance of the constructed S-box is testified.
- (2)
- A secure image encryption scheme is developed by integrating the chaotic S-box, DRPE, and IAT. In this scheme, the plaintext information is involved in the control parameters of IAT. All the gray pixel values are substituted by the S-box. We XOR the substituted image with a nonlinear chaotic sequence. Next, the two random-phase masks are generated by a nonlinear chaotic map. The XOR result is encoded by DRPE, and the obtained result is further confused by IAT.
- (3)
- Simulation and security analysis are conducted to verify the effectiveness of the proposed encryption scheme. Simulation results and performance analysis show that the proposed scheme is efficient and secure.
2. Fundamental Knowledge
2.1. Overview of Optical DRPE Cryptosystem
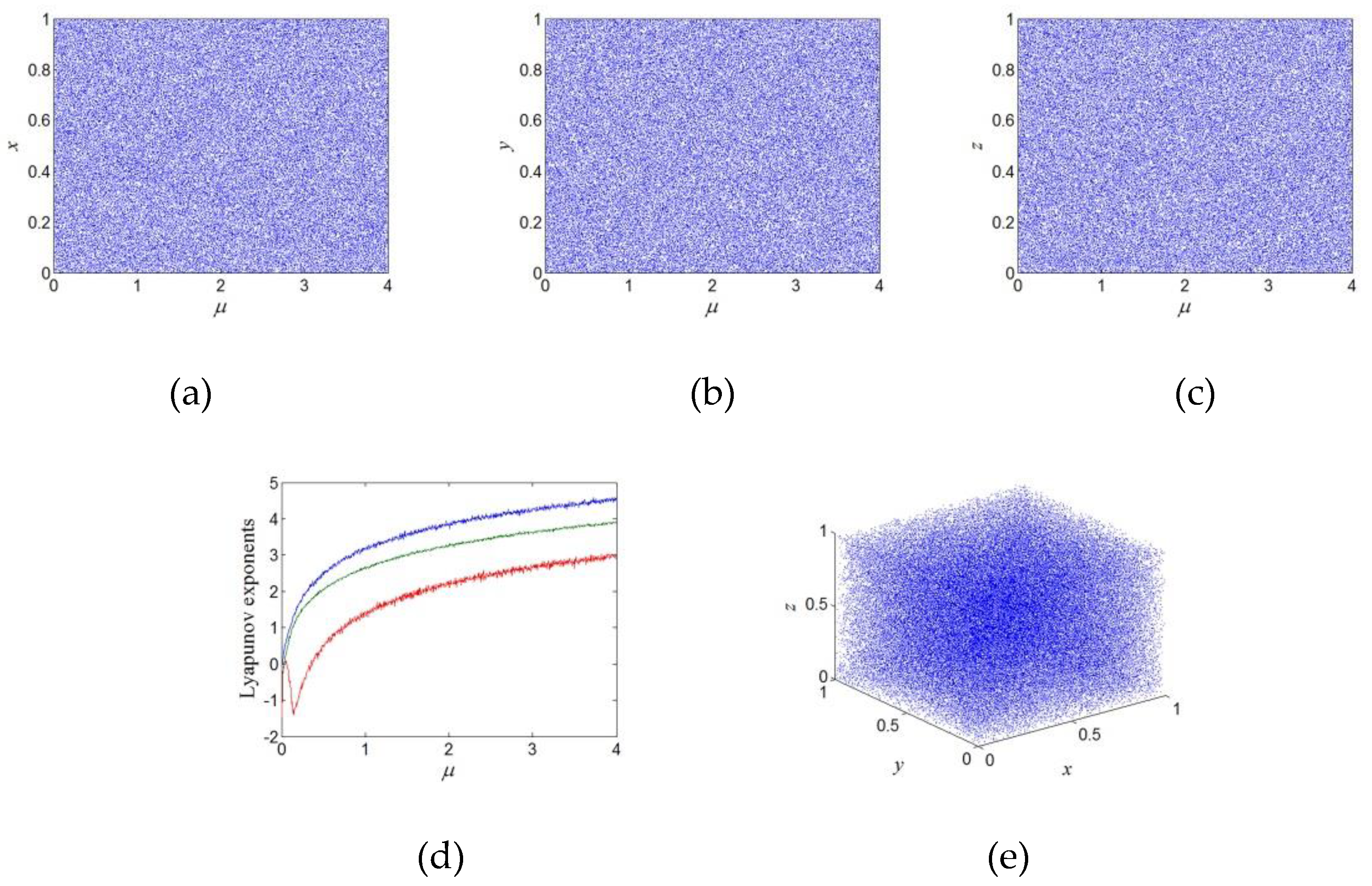
2.2. Nonlinear Chaotic Map
2.3. Improved Arnold Transformation
2.4. Transform of Stretch and Fold
- a.
- The stretch transform of nonadjacent rows and columns
- b.
- The fold transform of a snake line
3. S-Box Construction and Evaluation Criteria
3.1. The Proposed S-Box Generation Scheme
3.2. Performance Analysis of the Designed S-Box
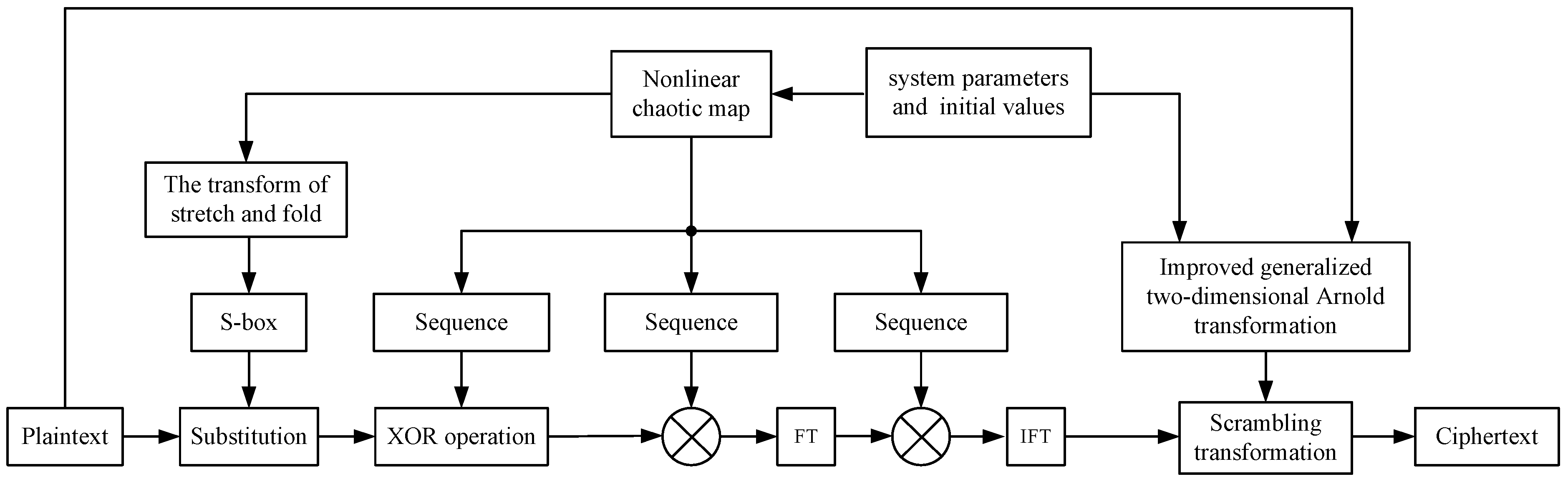
4. Proposed Encryption and Decryption Framework
Encryption Scheme
5. Simulation and Security Analysis
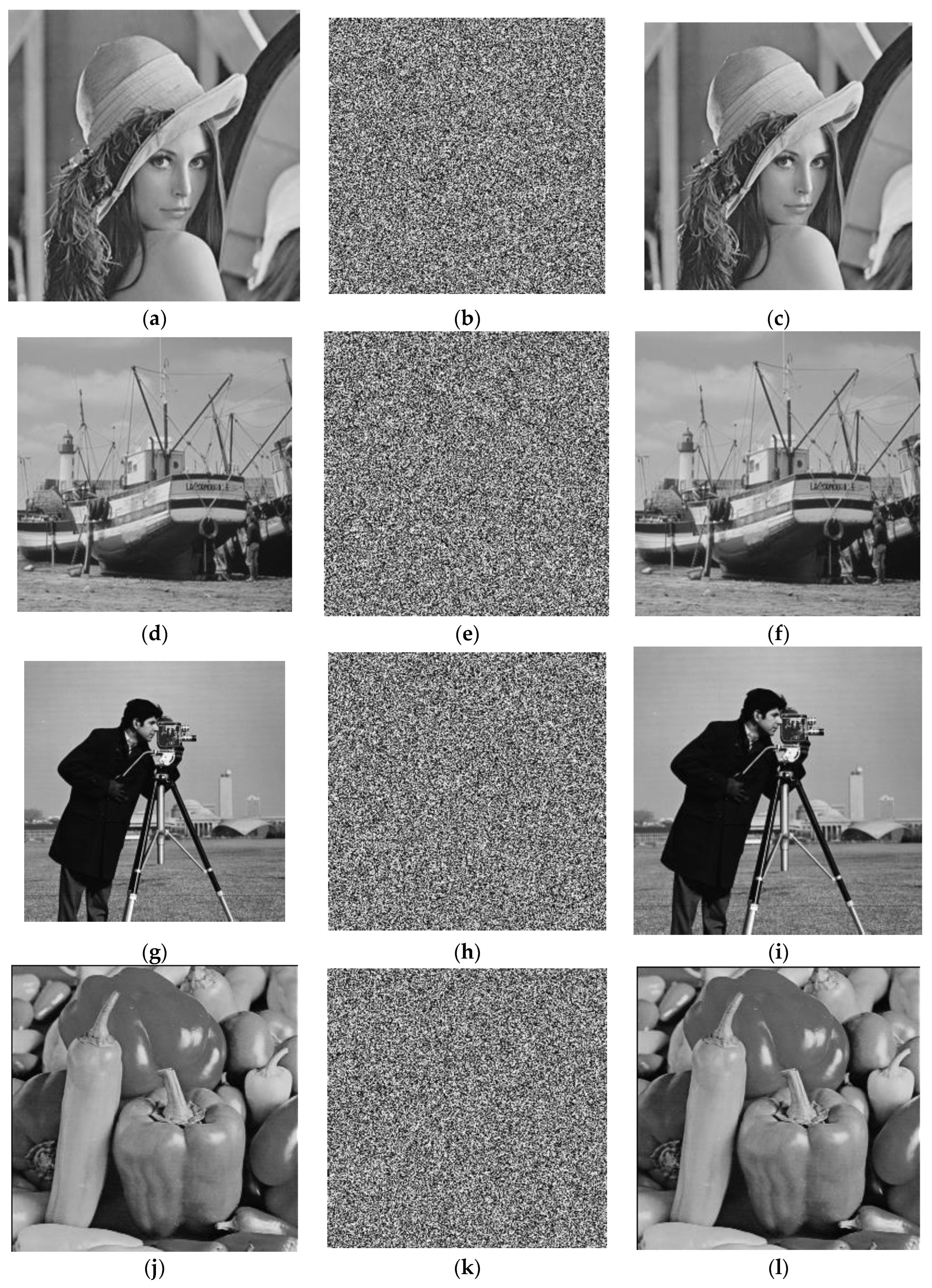
5.1. Simulation Results
5.2. Security Analysis
5.2.1. Key Space Analysis
5.2.2. Key Sensitivity Analysis
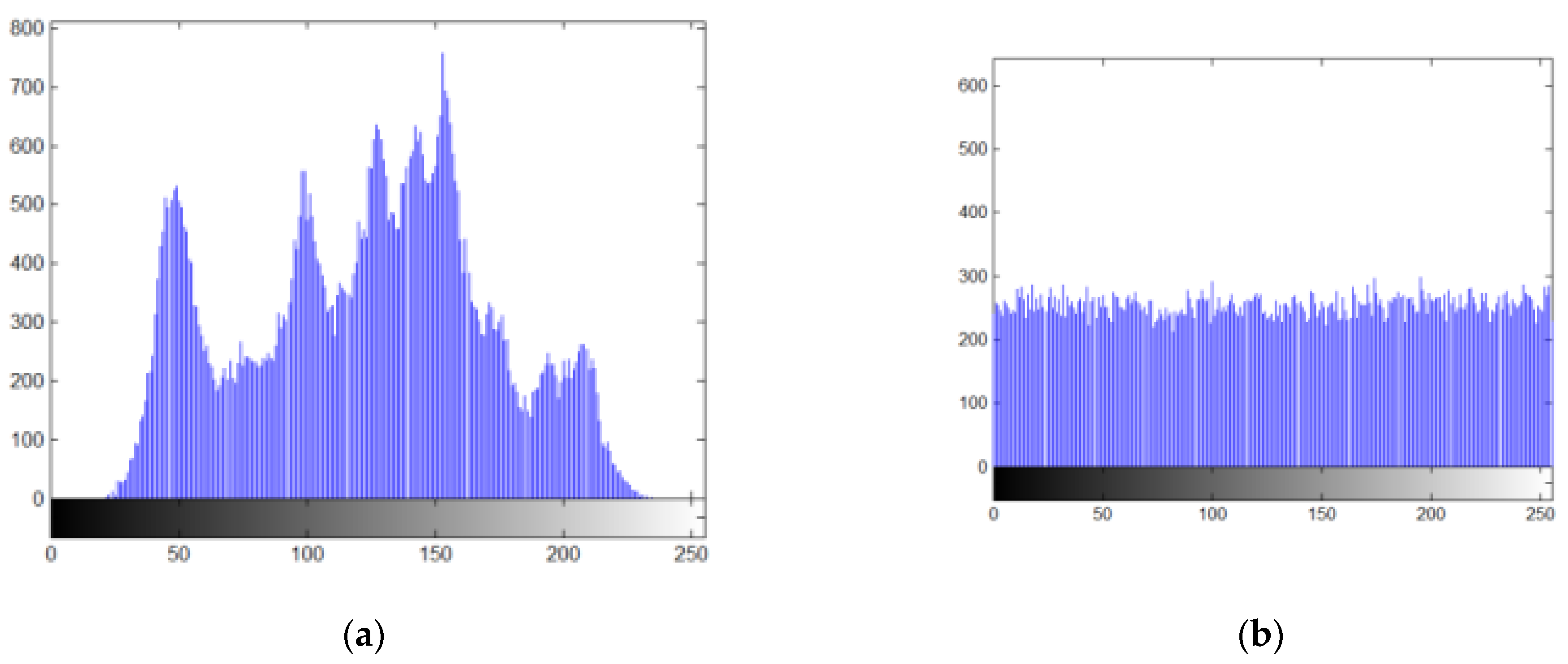
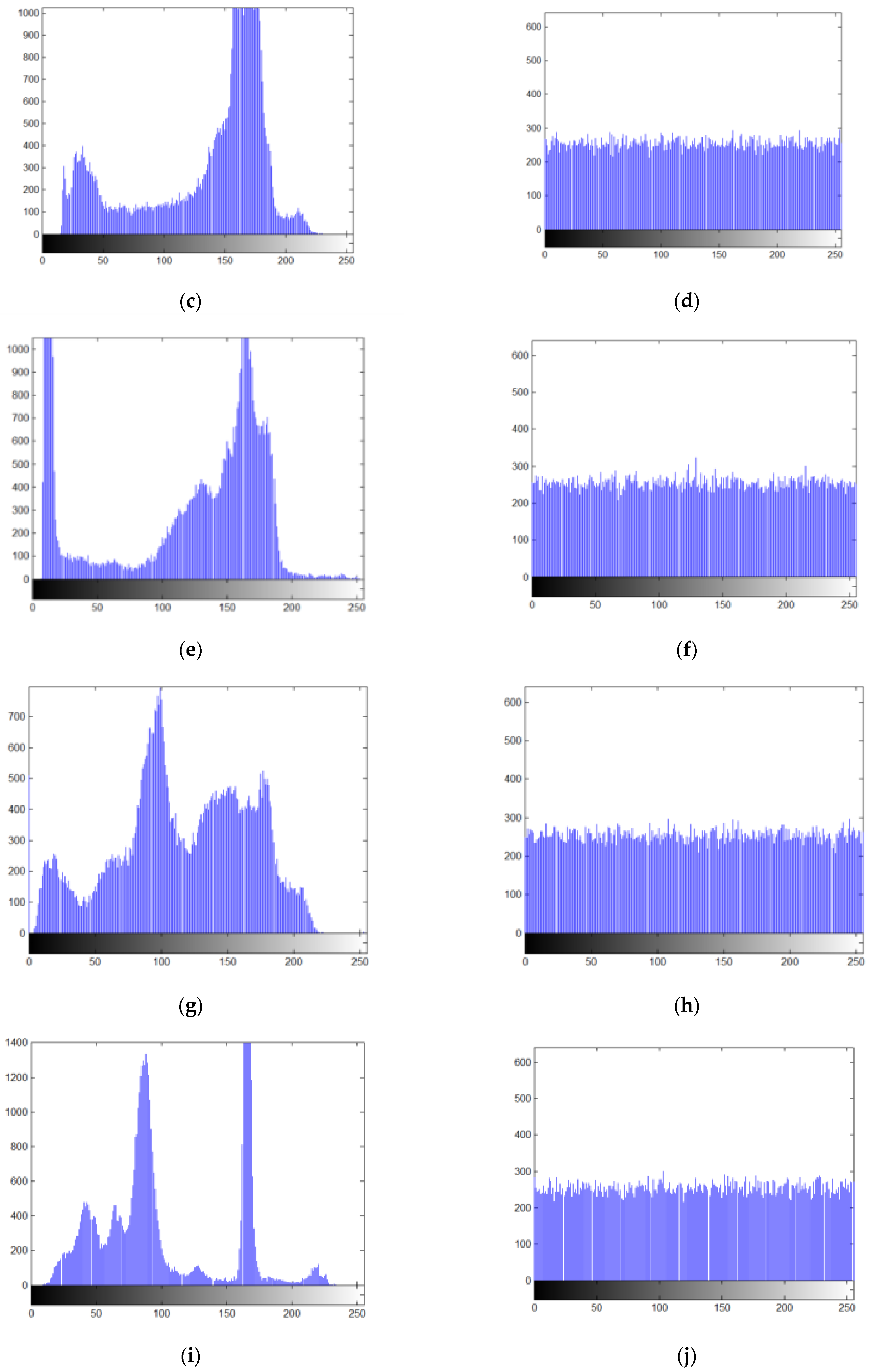
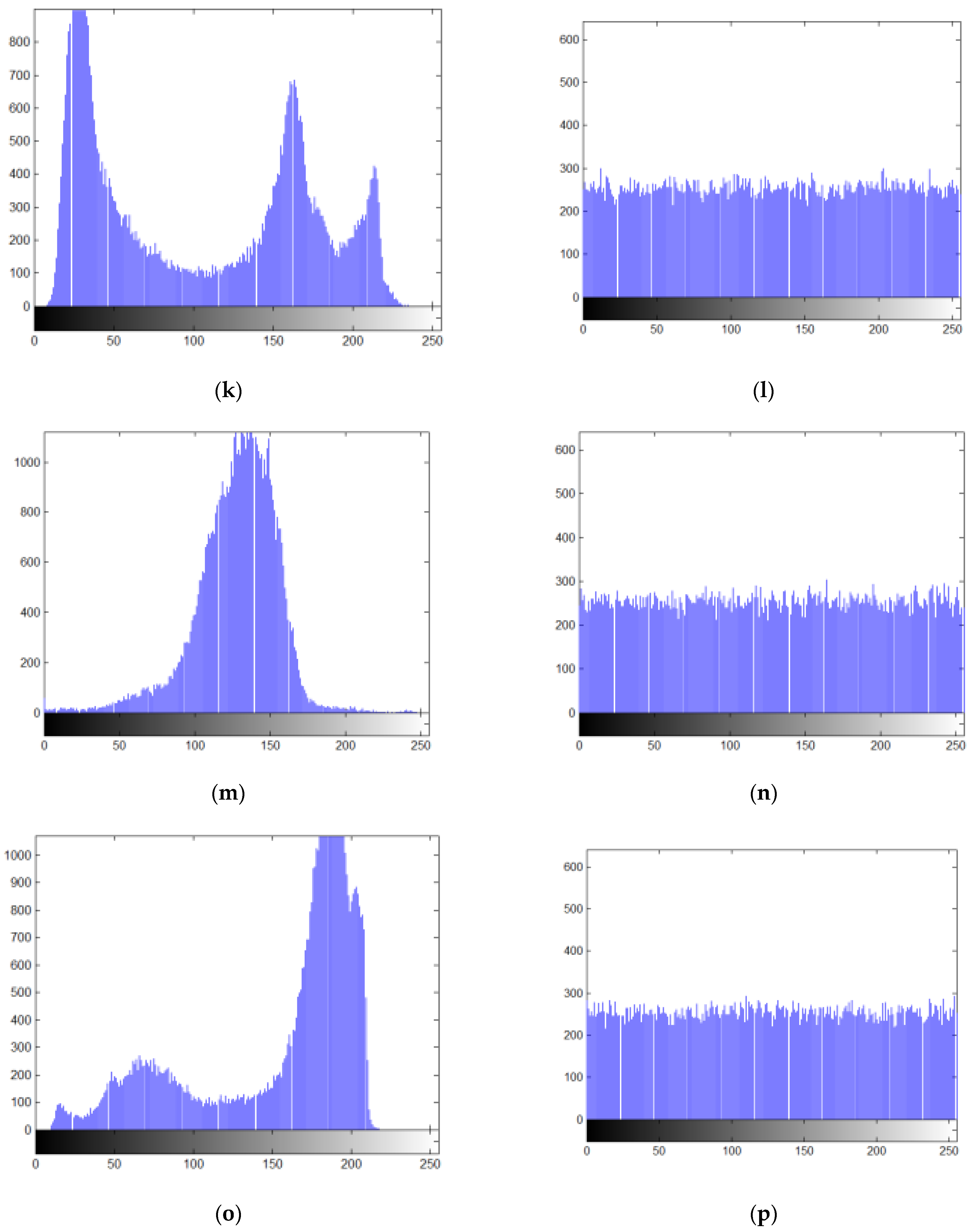
5.2.3. Histogram Analysis
5.2.4. Chi-Square Test Analysis
5.2.5. Mean Squared Error and Peak Signal-To-Noise Ratio Analysis
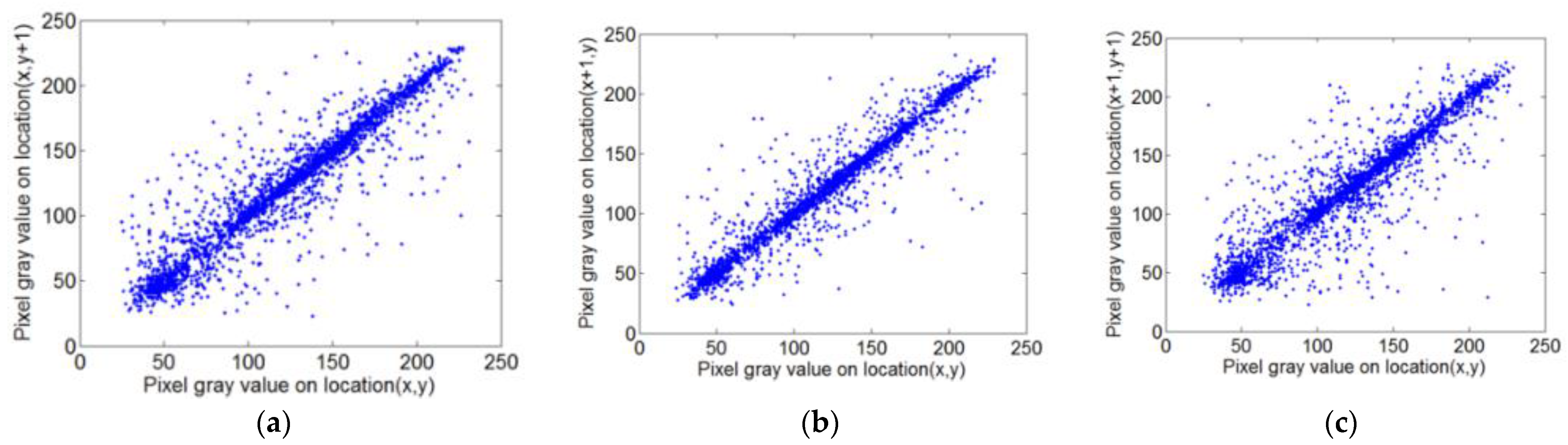
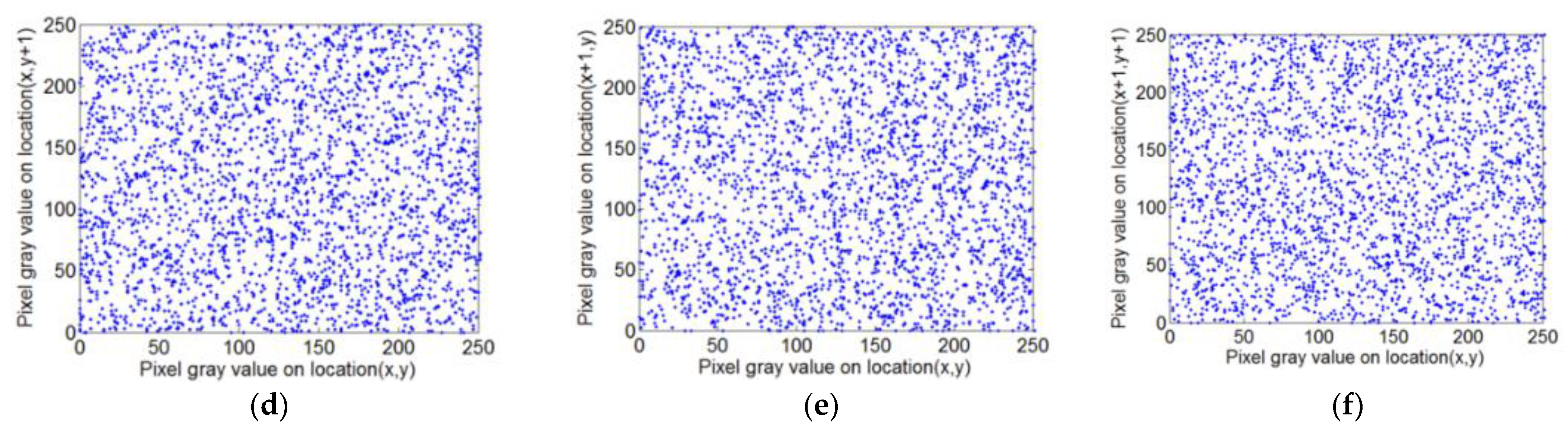
5.2.6. Correlation Analysis
5.2.7. Differential Attack Analysis
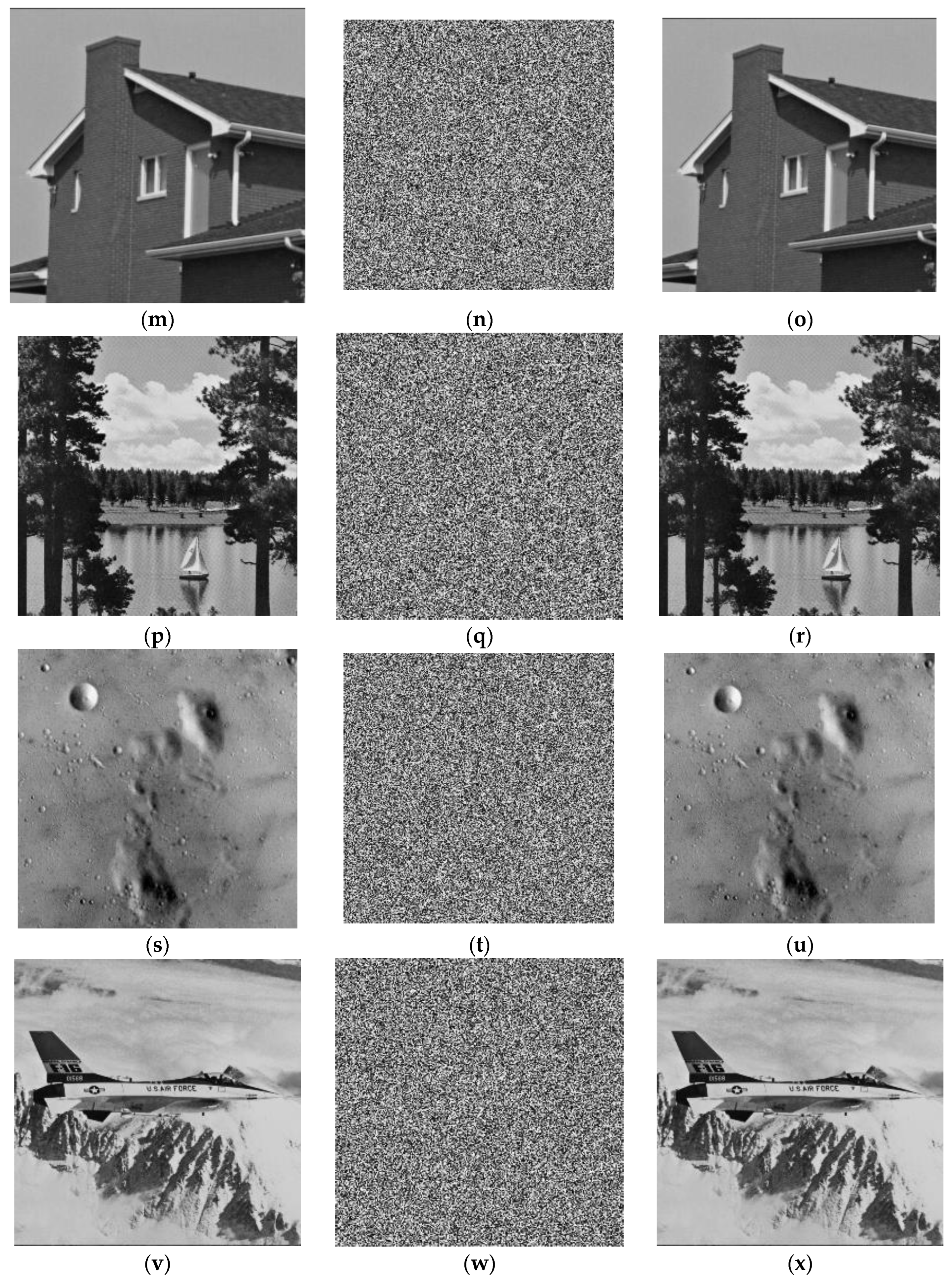
5.2.8. Robustness Analysis
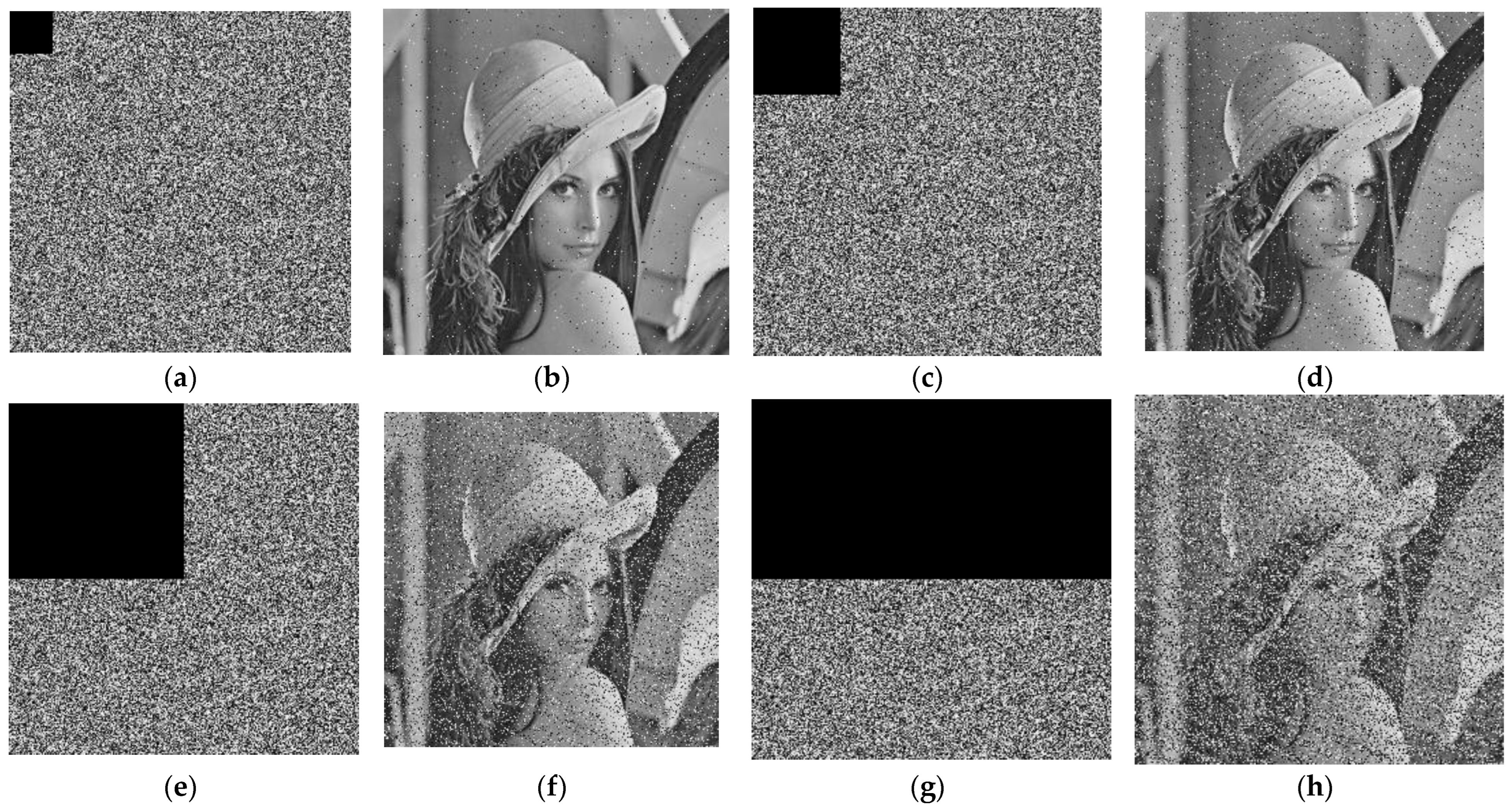
- a.
- Data loss attack
- b.
- Noise attack
5.2.9. Entropy Analysis
5.2.10. Speed Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Amin, M.; Abd El-Latif, A.A. Efficient modified RC5 based on chaos adapted to image encryption. J. Electron. Imaging 2010, 19, 013012. [Google Scholar] [CrossRef]
- Li, L.; Abd-El-Atty, B.; Abd El-Latif, A.A.; Ghoneim, A. Quantum color image encryption based on multiple discrete chaotic systems. In Proceedings of the 2017 Federated Conference on Computer Science and Information Systems (FedCSIS), Prague, Czech Republic, 3–6 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 555–559. [Google Scholar]
- Abd-El-Latif, A.A.; Abd-El-Atty, B.; Venegas-Andraca, S.E.; Mazurczyk, W. Providing end-to-end security using quantum walks in IoT networks. IEEE Access 2020, 8, 92687–92696. [Google Scholar] [CrossRef]
- Wang, C.P.; Wang, X.Y.; Xia, Z.Q.; Zhang, C. Ternary radial harmonic Fourier moments based robust stereo image zero-watermarking algorithm. Inf. Sci. 2019, 470, 109–120. [Google Scholar] [CrossRef]
- Zear, A.; Singh, A.K.; Kumar, P. A proposed secure multiple watermarking technique based on DWT, DCT and SVD for application in medicine. Multimed. Tools Appl. 2018, 77, 4863–4882. [Google Scholar] [CrossRef]
- Abd-El-Atty, B.; Iliyasu, A.M.; Alaskar, H.; El-Latif, A.; Ahmed, A. A robust quasi-quantum walks-based steganography protocol for secure transmission of images on cloud-based E-healthcare platforms. Sensors 2020, 20, 3108. [Google Scholar] [CrossRef]
- Luo, Y.J.; Qin, J.H.; Xiang, X.Y.; Tan, Y.; Liu, Q.; Xiang, L.Y. Coverless real-time image information hiding based on image block matching and dense convolutional network. J. Real-Time Image Proc. 2020, 17, 125–135. [Google Scholar] [CrossRef]
- Matoba, O.; Nomura, T.; Perez-Cabre, E.; Millan, M.; Javidi, B. Optical techniques for information security. P. IEEE 2009, 97, 1128–1148. [Google Scholar] [CrossRef]
- Liu, S.; Guo, C.; Sheridan, J.T. A review of optical image encryption techniques. Opt. Laser Technol. 2014, 57, 327–342. [Google Scholar] [CrossRef]
- Refregier, P.; Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef]
- Zhong, Z.; Chang, J.; Shan, M.G.; Hao, B.G. Fractional Fourier-domain random encoding and pixel scrambling technique for double image encryption. Opt. Commun. 2012, 285, 18–23. [Google Scholar] [CrossRef]
- Liu, Z.J.; Li, S.; Liu, W.; Wang, Y.H.; Liu, S.T. Image encryption algorithm by using fractional Fourier transform and pixel scrambling operation based on double random phase encoding. Opt. Lasers Eng. 2013, 51, 8–14. [Google Scholar] [CrossRef]
- Situ, G.H.; Zhang, J.J. Double random-phase encoding in the Fresnel domain. Opt. Lett. 2004, 29, 1584–1586. [Google Scholar] [CrossRef] [PubMed]
- Chen, W.; Chen, X.D.; Sheppard, C.J.R. Optical color-image encryption and synthesis using coherent diffractive imaging in the Fresnel domain. Opt. Express 2012, 20, 3853–3865. [Google Scholar] [CrossRef] [PubMed]
- Liu, Z.J.; Chen, H.; Liu, T.; Li, P.F.; Dai, J.M.; Sun, X.G.; Liu, S.T. Double-image encryption based on the affine transform and the gyrator transform. J. Opt. 2010, 12, 035407. [Google Scholar] [CrossRef]
- Wang, Q.; Guo, Q.; Lei, L. Double image encryption based on phase-amplitude mixed encoding and multistage phase encoding in gyrator transform domains. Opt. Laser Technol. 2013, 48, 267–279. [Google Scholar] [CrossRef]
- Qin, W.; Peng, X. Asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt. Lett. 2010, 35, 118–120. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, D. A special attack on the asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt. Commun. 2012, 285, 1078–1081. [Google Scholar] [CrossRef]
- Chen, W.; Chen, X. Double random phase encoding using phase reservation and compression. J. Opt. 2014, 16, 025402. [Google Scholar] [CrossRef]
- Wang, Y.; Quan, C.; Tay, C.J. Asymmetric optical image encryption based on an improved amplitude–phase retrieval algorithm. Opt. Laser Eng. 2016, 78, 8–16. [Google Scholar] [CrossRef]
- Dou, S.; Shen, X.; Lin, C. Security-enhanced optical nonlinear cryptosystem based on double random phase encoding. Opt. Laser Technol. 2020, 123, 105897. [Google Scholar] [CrossRef]
- Singh, P.; Kumar, R.; Yadav, A.K.; Singh, K. Security analysis and modified attack algorithms for a nonlinear optical cryptosystem based on DRPE. Opt. Laser Eng. 2021, 139, 106501. [Google Scholar] [CrossRef]
- Faragallah, O.S.; Naeem, E.A.; El-sayed, H.S.; El-Samie, A.; Fathi, E. Efficient compression processing of optically DCT-based DRPE encrypted images. Opt. Quant. Electron. 2022, 54, 273. [Google Scholar] [CrossRef]
- Li, H.J.; Wang, Y.R.; Yan, H.T.; Li, L.B.; Li, Q.Z.; Zhao, X.Y. Double-image encryption by using chaos-based local pixel scrambling technique and gyrator transform. Opt. Laser Eng. 2013, 51, 1327–1331. [Google Scholar] [CrossRef]
- Sui, L.S.; Lu, H.W.; Wang, Z.M.; Sun, Q.D. Double-image encryption using discrete fractional random transform and logistic maps. Opt. Laser Eng. 2014, 56, 1–12. [Google Scholar] [CrossRef]
- Lang, J.; Fu, X.X.; Guo, P. Optical color image asymmetric compressed encryption in fractional Fourier transform domain. Opto-Electron. Eng. 2018, 45, 170732. (In Chinese) [Google Scholar]
- Huang, Z.J.; Cheng, S.; Gong, L.H.; Zhou, N.R. Nonlinear optical multi-image encryption scheme with two-dimensional linear canonical transform. Opt. Laser. Eng. 2020, 124, 105821. [Google Scholar] [CrossRef]
- Abd-El-Atty, B.; Iliyasu, A.M.; Alanezi, A.; Abd El-latif, A.A. Optical image encryption based on quantum walks. Opt. Laser. Eng. 2021, 138, 106403. [Google Scholar] [CrossRef]
- Lambi’c, D. A novel method of S-box design based on chaotic map and composition method. Chaos Solitons Fractals 2014, 58, 16–21. [Google Scholar] [CrossRef]
- Ahmad, M.; Al-Solami, E.; Alghamdi, A.M.; Yousaf, M.A. Bijective S-boxes method using improved chaotic map-based heuristic search and algebraic group structures. IEEE Access 2020, 8, 110397–110411. [Google Scholar] [CrossRef]
- Özkaynak, F.; Yavuz, S. Designing chaotic S-boxes based on time-delay chaotic system. Nonlinear Dyn. 2013, 74, 551–557. [Google Scholar] [CrossRef]
- Ahmad, M.; Haleem, H.; Khan, P.M. A new chaotic substitution box design for block ciphers. In Proceedings of the 2014 International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 20–21 February 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 255–258. [Google Scholar]
- Jakimoski, G.; Kocarev, L. Chaos and cryptography: Block encryption ciphers based on chaotic maps. IEEE Trans. Circuits Syst. 2001, 48, 163–169. [Google Scholar] [CrossRef]
- Tang, G.P.; Liao, X.F.; Chen, Y. A novel method for designing S-boxes based on chaotic maps. Chaos Solitons Fractals 2005, 23, 413–419. [Google Scholar] [CrossRef]
- Tang, G.P.; Liao, X.F. A method for designing dynamical S-boxes based on discretized chaotic map. Chaos Solitons Fractals 2005, 23, 1901–1909. [Google Scholar] [CrossRef]
- Chen, G.; Chen, Y.; Liao, X.F. An extended method for obtaining S-boxes based on three-dimensional chaotic Bakermaps. Chaos Solitons Fractals 2007, 31, 571–579. [Google Scholar] [CrossRef]
- Özkaynak, F.; Özer, A.B. A method for designing strong S-Boxes based on chaotic Lorenz system. Phys. Lett. A 2010, 374, 3733–3738. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Mahmood, H.; Gondal, M.A.; Hussain, I. A novel technique for the construction of strong S-boxes based on chaotic Lorenz systems. Nonlinear Dyn. 2012, 70, 2303–2311. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A. A novel approach for designing substitution-boxes based on nonlinear chaotic algorithm. Nonlinear Dyn. 2012, 70, 1791–1794. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Gondal, M.A. An efficient technique for the construction of substitution box with chaotic partial differential equation. Nonlinear Dyn. 2013, 73, 1795–1801. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T. A construction of novel chaos base nonlinear component of block cipher. Nonlinear Dyn. 2014, 76, 377–382. [Google Scholar] [CrossRef]
- Anees, A.; Ahmed, Z. A technique for designing substitution box based on Van der Pol Oscillator. Wirel. Pers. Commun. 2015, 82, 1497–1503. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Batool, S.I. Construction of S-box based on chaotic Boolean functions and its application in image encryption. Neural Comput. Appl. 2016, 27, 677–685. [Google Scholar] [CrossRef]
- Çavu¸so˘glu, Ü.; Zengin, A.; Pehlivan, I.; Kaçar, S. A novel approach for strong S-box generation algorithm design based on chaotic scaled Zhongtang system. Nonlinear Dyn. 2017, 87, 1081–1094. [Google Scholar] [CrossRef]
- Belazi, A.; El-Latif, A.A. A simple yet efficient S-box method based on chaotic sine map. Optik-Int. J. Light Electron Opt. 2017, 130, 1438–1444. [Google Scholar] [CrossRef]
- Özkaynak, F.; Çelik, V.; Özer, A.B. A new S-box construction method based on the fractional-order chaotic Chen system. Signal Image Video P. 2017, 11, 659–664. [Google Scholar] [CrossRef]
- Tian, Y.; Lu, Z. Chaotic S-box: Six-dimensional fractional Lorenz–Duffing chaotic system and O-shaped path scrambling. Nonlinear Dyn. 2018, 94, 2115–2126. [Google Scholar]
- Ben Farah, M.A.; Farah, A.; Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 2020, 99, 3041–3064. [Google Scholar] [CrossRef]
- Yousaf, M.A.; Alolaiyan, H.; Ahmad, M.; Dilbar, M.; Razaq, A. Comparison of pre and post-action of a finite abelian group over certain nonlinear schemes. IEEE Access 2020, 8, 39781–39792. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Li, J.; Chen, Y.Y.; Yi, S. Design and application of an S-box using complete Latin square. Nonlinear Dyn. 2021, 104, 807–825. [Google Scholar] [CrossRef]
- Alhadawi, H.S.; Majid, M.A.; Lambić, D.; Ahmad, M. A novel method of S-box design based on discrete chaotic maps and cuckoo search algorithm. Multimed. Tools Appl. 2021, 80, 7333–7350. [Google Scholar] [CrossRef]
- Liu, X.; Tong, X.; Wang, Z.; Zhang, M. Efficient high nonlinearity S-box generating algorithm based on third-order nonlinear digital filter. Chaos Solitons Fractals 2021, 150, 111109. [Google Scholar] [CrossRef]
- Zhou, P.; Du, J.; Zhou, K.; Wei, S. 2D mixed pseudo-random coupling PS map lattice and its application in S-box generation. Nonlinear Dyn. 2021, 103, 1151–1166. [Google Scholar] [CrossRef]
- Tong, X.; Liu, X.; Liu, J.; Zhang, M.; Wang, Z. A Novel Lightweight Block Encryption Algorithm Based on Combined Chaotic S-Box. Int. J. Bifurc. Chaos 2021, 31, 2150152. [Google Scholar] [CrossRef]
- Hematpour, N.; Ahadpour, S.; Sourkhani, I.G.; Sani, R.H. A new steganographic algorithm based on coupled chaotic maps and a new chaotic S-box. Multimed. Tools Appl. 2022, 14, 895. [Google Scholar] [CrossRef]
- Zhang, X.; Mao, Y.; Zhao, Z. An efficient chaotic image encryption based on alternate circular S-boxes. Nonlinear Dyn. 2014, 78, 359–369. [Google Scholar] [CrossRef]
- Belazi, A.; Khan, M.; El-Latif, A.A.A.; Belghith, S. Efficient cryptosystem approaches: S-boxes and permutation–substitution-based encryption. Nonlinear Dyn. 2017, 87, 337–361. [Google Scholar] [CrossRef]
- Lu, Q.; Zhu, C.; Deng, X. An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access 2020, 8, 25664–25678. [Google Scholar] [CrossRef]
- Idrees, B.; Zafar, S.; Rashid, T.; Gao, W. Image encryption algorithm using S-box and dynamic Hénon bit level permutation. Multimed. Tools Appl. 2020, 79, 6135–6162. [Google Scholar] [CrossRef]
- Wang, X.; Yang, J. A novel image encryption scheme of dynamic S-boxes and random blocks based on spatiotemporal chaotic system. Optik-Int. J. Light Electron Opt. 2020, 217, 164884. [Google Scholar] [CrossRef]
- Masood, F.; Masood, J.; Zhang, L.; Jamal, S.S.; Boulila, W.; Rehman, S.U.; Khan, F.A.; Ahmad, J. A new color image encryption technique using DNA computing and Chaos-based substitution box. Soft Comput. 2021, 1–17. [Google Scholar] [CrossRef]
- Ali, T.S.; Ali, R. A novel color image encryption scheme based on a new dynamic compound chaotic map and S-box. Multimed. Tools Appl. 2022, 81, 20585–20609. [Google Scholar] [CrossRef]
- Deb, S.; Behera, P.K. Design of key-dependent bijective S-Boxes for color image cryptosystem. Optik-Int. J. Light Electron Opt. 2022, 253, 168548. [Google Scholar] [CrossRef]
- Hussain, I.; Azam, N.A.; Shah, T. Stego optical encryption based on chaotic S-box transformation. Opt. Laser Technol. 2014, 61, 50–56. [Google Scholar] [CrossRef]
- Hussain, I. Optical image encryption based on S-box transformation and fractional Hartley transform. J. Vib. Control 2016, 22, 1143–1146. [Google Scholar] [CrossRef]
- Girija, R.; Singh, H. Enhancing security of double random phase encoding based on random S-Box. 3D Res. 2018, 9, 1–20. [Google Scholar] [CrossRef]
- Shatheesh, S.I.; Devaraj, P.; Bhuvaneswaran, R.S. An efficient quasigroup based image encryption using modified nonlinear chaotic maps. Sens. Imaging 2014, 15, 1–21. [Google Scholar]
- Zhu, H.G.; Zhao, C.; Zhang, X.D.; Yang, L.P. An image encryption scheme using generalized Arnold map and affine cipher. Optik-Int. J. Light Electron. Opt. 2014, 125, 6672–6677. [Google Scholar] [CrossRef]
- Wu, C.M. An improved discrete Arnold transform and its application in image scrambling and encryption. Acta Phys. Sin. 2014, 63, 090504. [Google Scholar]
- Li, J.; Feng, Y.; Yang, X.Q.; Huang, F. Invertible map set based image encryption algorithm. J. Optoelectron.·Laser 2009, 20, 78–83. (In Chinese) [Google Scholar]
- Adams, C.; Tavares, S. The structured design of cryptographically good S-boxes. J. Cryptol. 1990, 3, 27–41. [Google Scholar] [CrossRef]
- Webster, A.F.; Tavares, S.E. On the design of S-boxes. In Proceedings of the Advances in CryptologyCRYPTO 85.Lecture Notes in Computer Science, The University of California, Santa Barbara, CA, USA, 18–22 August 1985; Springer: Berlin/Heidelberg, Germany, 1985; Volume 218, pp. 523–534. [Google Scholar]
- Adams, C.; Tavares, S.E. Good S-boxes are easy to find. In Proceedings of the Advances in CryptologyCRYPTO89, The University of California, Santa Barbara, CA, USA, 20–24 August 1989; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1989; Volume 435, pp. 612–615. [Google Scholar]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. In Proceedings of the Advances in CryptologyCRYPTO 90, The University of California, Santa Barbara, CA, USA, 11–15 August 1990; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1990; Volume 537, pp. 2–21. [Google Scholar]
- Matsui, M. Linear cryptanalysis method for DES cipher. In Proceedings of the Advances in Cryptology EUROCRYPT93, Lofthus, Norway, 23–27 May 1993; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1993; Volume 765, pp. 386–397. [Google Scholar]
- Usc-Sipi Image Database for Research in Image Processing, Image Analysis, and Machine Vision. Available online: http://sipi.usc.edu/database/ (accessed on 6 June 2017).
- Alvarez, G.; Li, S.J. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurcation Chaos Appl. Sci. Eng. 2006, 16, 2129–2151. [Google Scholar] [CrossRef] [Green Version]
- Wang, X.; Chen, X. An image encryption algorithm based on dynamic row scrambling and Zigzag transformation. Chaos, Solitons & Fractals 2021, 147, 110962. [Google Scholar]

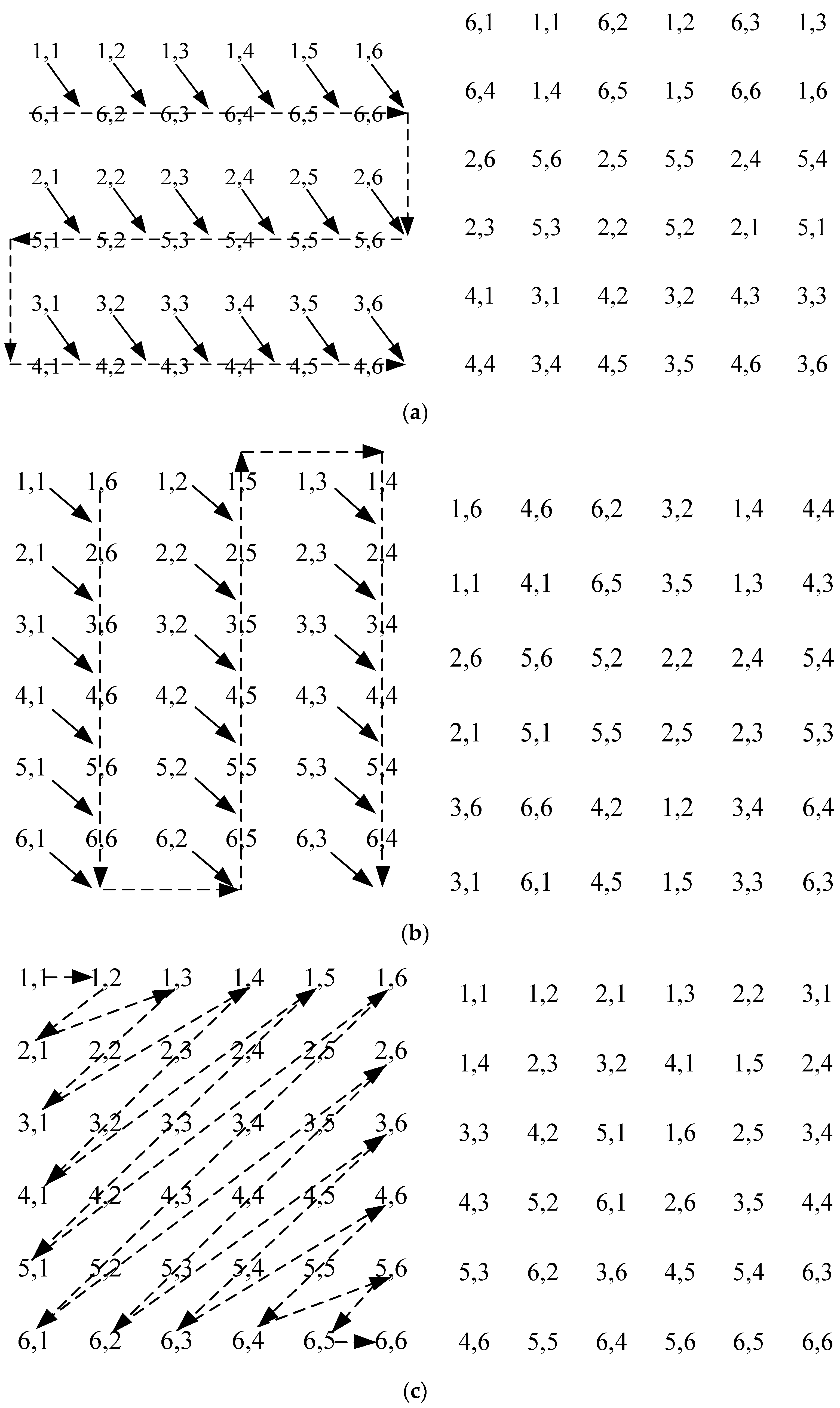

| No. | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 132 | 211 | 219 | 33 | 46 | 9 | 224 | 202 | 155 | 187 | 34 | 154 | 13 | 28 | 102 | 221 |
| 2 | 117 | 228 | 166 | 250 | 63 | 159 | 177 | 100 | 182 | 58 | 85 | 170 | 60 | 52 | 238 | 64 |
| 3 | 142 | 6 | 78 | 247 | 248 | 4 | 108 | 18 | 68 | 107 | 194 | 45 | 209 | 50 | 87 | 119 |
| 4 | 158 | 54 | 37 | 109 | 150 | 114 | 65 | 181 | 234 | 14 | 243 | 123 | 76 | 21 | 72 | 217 |
| 5 | 3 | 24 | 227 | 113 | 0 | 19 | 208 | 17 | 111 | 70 | 171 | 110 | 156 | 2 | 145 | 152 |
| 6 | 5 | 192 | 231 | 89 | 193 | 240 | 244 | 20 | 215 | 149 | 173 | 229 | 180 | 40 | 255 | 49 |
| 7 | 201 | 143 | 179 | 169 | 147 | 32 | 137 | 47 | 15 | 239 | 176 | 253 | 80 | 252 | 204 | 225 |
| 8 | 44 | 165 | 73 | 105 | 56 | 160 | 133 | 134 | 191 | 55 | 206 | 1 | 183 | 12 | 203 | 36 |
| 9 | 35 | 7 | 74 | 184 | 212 | 129 | 8 | 23 | 26 | 127 | 122 | 162 | 172 | 242 | 118 | 214 |
| 10 | 223 | 120 | 16 | 125 | 207 | 199 | 148 | 226 | 144 | 95 | 51 | 71 | 103 | 41 | 77 | 178 |
| 11 | 88 | 222 | 174 | 164 | 146 | 130 | 188 | 126 | 216 | 81 | 200 | 249 | 29 | 140 | 157 | 10 |
| 12 | 189 | 91 | 22 | 98 | 198 | 205 | 61 | 161 | 190 | 151 | 94 | 245 | 233 | 163 | 195 | 136 |
| 13 | 25 | 31 | 97 | 79 | 39 | 82 | 135 | 218 | 141 | 11 | 196 | 168 | 186 | 175 | 101 | 121 |
| 14 | 69 | 27 | 30 | 115 | 53 | 42 | 210 | 246 | 220 | 232 | 96 | 116 | 90 | 43 | 83 | 237 |
| 15 | 48 | 139 | 241 | 213 | 92 | 106 | 59 | 124 | 153 | 86 | 197 | 138 | 112 | 93 | 67 | 254 |
| 16 | 75 | 38 | 84 | 57 | 104 | 251 | 236 | 131 | 66 | 235 | 167 | 230 | 99 | 185 | 128 | 62 |
| S-Boxes | Nonlinearity | SAC | BIC- Nonlinearity | BIC- SAC | DP | LP | ||||
|---|---|---|---|---|---|---|---|---|---|---|
| Min | Max | Avg. | Min | Max | Avg. | |||||
| Proposed | 104 | 110 | 107 | 0.4219 | 0.5781 | 0.4954 | 102.93 | 0.5034 | 0.04688 | 0.148438 |
| Ref. [33] | 100 | 108 | 103.25 | 0.3750 | 0.5938 | 0.5059 | 104.29 | 0.5031 | 0.04688 | 0.125000 |
| Ref. [34] | 104 | 108 | 105 | 0.4063 | 0.5781 | 0.4971 | 103 | 0.5044 | 0.03906 | 0.132813 |
| Ref. [35] | 101 | 108 | 103.88 | 0.3906 | 0.5781 | 0.5059 | 102.68 | 0.4958 | 0.03906 | 0.132813 |
| Ref. [36] | 100 | 106 | 103 | 0.4219 | 0.6094 | 0.5000 | 103.14 | 0.5024 | 0.05469 | 0.132813 |
| Ref. [37] | 100 | 106 | 103.25 | 0.4219 | 0.5938 | 0.5049 | 103.71 | 0.5010 | 0.03906 | 0.132813 |
| Ref. [38] | 96 | 106 | 103 | 0.3906 | 0.6250 | 0.5039 | 100.36 | 0.5010 | 0.03906 | 0.148438 |
| Ref. [39] | 102 | 108 | 104.75 | 0.3906 | 0.5938 | 0.5056 | 104.07 | 0.5022 | 0.04688 | 0.125000 |
| Ref. [40] | 98 | 108 | 104.25 | 0.2813 | 0.6094 | 0.4954 | 102.86 | 0.5048 | 0.04688 | 0.140625 |
| Ref. [41] | 100 | 106 | 104 | 0.3750 | 0.6250 | 0.4946 | 103.21 | 0.5019 | 0.03906 | 0.132813 |
| Ref. [42] | 100 | 106 | 103 | 0.3906 | 0.5938 | 0.5020 | 102.93 | 0.4999 | 0.03906 | 0.140625 |
| Ref. [43] | 84 | 106 | 100 | 0.1250 | 0.6250 | 0.4812 | 101.93 | 0.4967 | 0.06250 | 0.179688 |
| Ref. [44] | 104 | 110 | 106.25 | 0.4219 | 0.5938 | 0.5039 | 103.36 | 0.5059 | 0.03906 | 0.140625 |
| Ref. [45] | 100 | 110 | 105.50 | 0.4063 | 0.6094 | 0.5010 | 103.79 | 0.5036 | 0.04688 | 0.132813 |
| Ref. [46] | 101 | 107 | 104.5 | 0.4219 | 0.5781 | 0.4963 | 103.29 | 0.4938 | 0.03906 | 0.140625 |
| Ref. [47] | 104 | 108 | 106.75 | 0.4063 | 0.6250 | 0.4976 | 103.57 | 0.5022 | 0.03906 | 0.132813 |
| Ref. [48] | 104 | 108 | 106.25 | 0.3594 | 0.6094 | 0.5002 | 103.64 | 0.4993 | 0.03906 | 0.132813 |
| Ref. [49] | 112 | 112 | 112 | 0.4531 | 0.5625 | 0.5051 | 112 | 0.5044 | 0.01560 | 0.062500 |
| Ref. [50] | 102 | 108 | 105.25 | 0.4688 | 0.5938 | 0.5352 | 103.21 | 0.5085 | 0.05469 | 0.140625 |
| Ref. [51] | 106 | 110 | 108.5 | 0.4063 | 0.5781 | 0.4995 | 103.86 | 0.5016 | 0.03906 | 0.132813 |
| Ref. [52] | 110 | 112 | 112.5 | 0.4063 | 0.5938 | 0.4985 | 103.79 | 0.5014 | 0.03906 | 0.132813 |
| Ref. [53] | 104 | 110 | 107 | 0.4219 | 0.5938 | 0.4993 | 103.29 | 0.5051 | 0.03906 | 0.132813 |
| Ref. [54] | 102 | 108 | 105.5 | 0.4219 | 0.5781 | 0.5061 | 103 | 0.5009 | 0.03906 | 0.140625 |
| Ref. [55] | 102 | 110 | 106.5 | 0.4063 | 0.5938 | 0.5010 | 103.43 | 0.4980 | 0.0391 | 0.132813 |
| Cipher Image | Chi-Square Value | Result |
|---|---|---|
| Lena | 246.4219 | Pass |
| Boat | 242.7656 | Pass |
| Cameraman | 244.4688 | Pass |
| Peppers | 248.6797 | Pass |
| House | 262.9219 | Pass |
| Lake | 240.4375 | Pass |
| Moon surface | 287.6328 | Pass |
| Plane | 240.6016 | Pass |
| Test Image | MSE (Original vs. Encrypted) | PSNR (Original vs. Encrypted) | MSE (Original vs. Decrypted) | PSNR (Original vs. Decrypted) |
|---|---|---|---|---|
| Lena | 7802.8866 | 9.2083 | 0 | ∞ |
| Boat | 8263.2444 | 8.9593 | 0 | ∞ |
| Cameraman | 9439.7874 | 8.3812 | 0 | ∞ |
| Peppers | 8193.0659 | 8.9963 | 0 | ∞ |
| House | 8454.3259 | 8.8600 | 0 | ∞ |
| Lake | 10,728.4255 | 7.8254 | 0 | ∞ |
| Moon surface | 6217.3002 | 10.1948 | 0 | ∞ |
| Plane | 8987.5783 | 8.5944 | 0 | ∞ |
| Test Image | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| Plaintext image Lena | 0.9051 | 0.9652 | 0.9293 |
| Encrypted image Lena | −0.0053 | −0.0012 | 0.0050 |
| Ref. [56] | 0.0032 | −0.0003 | 0.0012 |
| Ref. [58] | −0.0056 | 0.0006 | 0.0018 |
| Ref. [59] | −0.0009 | −0.0030 | 0.0062 |
| Test Image | NPCR (%) | UACI (%) |
|---|---|---|
| Lena | 99.6216 | 33.6642 |
| Boat | 99.6017 | 33.3610 |
| Cameraman | 99.5987 | 33.3694 |
| Peppers | 99.6033 | 33.5057 |
| House | 99.5865 | 33.3840 |
| Lake | 99.5987 | 33.4928 |
| Moon surface | 99.5880 | 33.3971 |
| Plane | 99.5941 | 33.4519 |
| Data Loss | 1/16 | 1/8 | 1/4 | 1/2 |
|---|---|---|---|---|
| PSNR | 9.0229 | 8.7816 | 7.6823 | 6.3940 |
| MSE | 8143.1129 | 8608.3023 | 11,087.8870 | 14,917.0311 |
| Noise Type | Salt-and-Pepper Noise | Gaussian White Noise | ||||||
|---|---|---|---|---|---|---|---|---|
| Noise intensity | 0.001 | 0.01 | 0.05 | 0.1 | 0.2 | 0.3 | 0.4 | 0.5 |
| PSNR | 9.2002 | 9.1446 | 8.4837 | 9.2083 | 9.1789 | 9.0572 | 8.8713 | 8.6525 |
| MSE | 7817.4412 | 7918.1615 | 9219.6355 | 7802.8866 | 7855.7743 | 8079.0790 | 8432.4675 | 8868.1909 |
| Test Image | Plaintext Image | Encrypted Image |
|---|---|---|
| Lena | 7.4551 | 7.997286 |
| Boat | 7.1011 | 7.997322 |
| Cameraman | 7.0097 | 7.997325 |
| Peppers | 7.5251 | 7.997258 |
| House | 6.5637 | 7.997106 |
| Lake | 7.3767 | 7.997353 |
| Moon surface | 6.7093 | 7.996827 |
| Plane | 6.9860 | 7.997342 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, P.; Su, R. A Novel Virtual Optical Image Encryption Scheme Created by Combining Chaotic S-Box with Double Random Phase Encoding. Sensors 2022, 22, 5325. https://doi.org/10.3390/s22145325
Tian P, Su R. A Novel Virtual Optical Image Encryption Scheme Created by Combining Chaotic S-Box with Double Random Phase Encoding. Sensors. 2022; 22(14):5325. https://doi.org/10.3390/s22145325
Chicago/Turabian StyleTian, Peiran, and Runzhou Su. 2022. "A Novel Virtual Optical Image Encryption Scheme Created by Combining Chaotic S-Box with Double Random Phase Encoding" Sensors 22, no. 14: 5325. https://doi.org/10.3390/s22145325
APA StyleTian, P., & Su, R. (2022). A Novel Virtual Optical Image Encryption Scheme Created by Combining Chaotic S-Box with Double Random Phase Encoding. Sensors, 22(14), 5325. https://doi.org/10.3390/s22145325





