Abstract
This paper studies the secrecy coding analysis achieved by the self-jamming technique in the presence of an eavesdropper by considering a short-packet Full-Duplex (FD) transmission developed based on iterative blind or semi-blind channel estimation and advanced decoding algorithms. Indeed, the legitimate receiver and eavesdropper can simultaneously receive the intended signal from the transmitter and broadcast a self-jamming or jamming signal to the others. Unlike other conventional techniques without feedback, the blind or semi-blind algorithm applied at the legitimate receiver can simultaneously estimate, firstly, the Self-Interference (SI) channel to cancel the SI component and, secondly, estimate the propagation channel, then decode the intended messages by using 5G Quasi-Cyclic Low-Density Parity Check (QC-LDPC) codes. Taking into account the passive eavesdropper case, the blind channel estimation with a feedback scheme is applied, where the temporary estimation of the intended channel and the decoded message are fed back to improve both the channel estimation and the decoding processes. Only the blind algorithm needs to be implemented in the case of a passive eavesdropper because it achieves sufficient performances and does not require adding pilot symbols as the semi-blind algorithm. In the case of an active eavesdropper, based on its robustness in the low region of the Signal-to-Noise Ratio (SNR), the semi-blind algorithm is considered by trading four pilot symbols and only requiring the feedback for channel estimation processes in order to overcome the increase in noise in the legitimate receiver. The results show that the blind or semi-blind algorithms outperform the conventional algorithm in terms of Mean Square Error (MSE), Bit Error Rate (BER) and security gap (). In addition, it has been shown that the blind or semi-blind algorithms are less sensitive to high SI and self-jamming interference power levels imposed by secured FD transmission than the conventional algorithms without feedback.
1. Introduction
The development of future wireless technologies such as massive MIMO systems, machine type communications, millimeter wave transmissions, and especially the Internet of Things (IoT) has led to not only new challenges but also new opportunities in the 5G security domains [1]. In order to achieve enhanced security performances for the wireless communications, a better strategy is setting up based on the physical layer directly, which is a method that belongs to the information theory field. This category of security solutions, also known as Physical Layer Security (PLS), has recently emerged as a new security or additional security layer, especially in 5G networks and beyond [2,3]. The wiretap channel was first introduced by Wyner in 1975 and became fundamental in characterizing PLS problems, where the intended transmitter sends a message to the legitimate receiver while the passive eavesdropper tries to listen and decode this message [4]. A decade later, Ozarow and Wyner introduced the second type of wiretap channel, known as wiretap channel II, where the active eavesdropper not only listens to the intended transmitter but also transmits a jamming signal to the legitimate receiver [5]. Therefore, the presence of an active eavesdropper can more strongly destroy the reception behavior of the legitimate receiver than that of the passive eavesdropper in the secrecy of wireless communication links [6]. As a metric of PLS, the security gap was first introduced in [7], which is calculated as the ratio of the Bit Error Rate (BER) on the linear scale or the difference of the BERs on the log scale achieved by the legitimate receiver and the eavesdropper to ensure that the legitimate receiver can reliably receive the intended message and to maintain security throughout transmission.
Due to the improved spectral efficiency, Full-Duplex (FD) communication systems that simultaneously transmit and receive information using the same time-frequency channel resource became an essential approach in 5G and beyond communication networks, especially in IoT transmissions and green communications [8,9]. However, Self-Interference (SI) cancellation is still the biggest challenge of any FD system due to the channel estimation error caused by the complexity of the SI channel, particularly in the case of short-frame transmission [10,11,12]. The presence of SI will reduce the Signal-to-Noise Ratio (SNR) at the receiver and leads to low overall performance. Considering the PLS in FD transmission, the security approaches involving the simultaneous transmission of the self-jamming or Artificial Noise (AN) have attracted a huge research interest due to their robustness promising performance [13,14]. The self-jamming technique is usually used to make the interception and the correct message decoding impossible for the eavesdroppers, even if they have equivalent or better channel conditions than the legitimate receiver. Therefore, the self-jamming approach has been widely studied and extended in numerous schemes to enhance the PLS, i.e., the FD transceiver can simultaneously receive the intended message and broadcast the AN to degrade the eavesdropper channel [15,16,17]. The AN technique is also used for secure transmission in cognitive wiretap networks with FD receivers [18] or FD relay systems [19]. Usually, the PLS mechanism related to the self-jamming and AN has been studied assuming that the eavesdropper cannot estimate the wiretap channel or jamming channel based on the known training pilots and transmitted power [20]. However, a large number of training pilots are required to be involved, and it is still not a satisfying solution in terms of time, bandwidth, and power consumption, especially for short-frame FD transmission, because the training requires a huge number of data symbols to obtain a good second-order statistic of the received signal. Furthermore, channel secrecy capacity and transmission message reliability can be a problem for communications with finite block length or short-packet [6]. Therefore, the PLS on short-packet transmission has recently become an open area to be focused on in 5G and beyond, especially for IoT transmissions and green communications.
Furthermore, new radio channel coding schemes such as 5G Quasi-Cyclic Low-Density Parity Check (QC-LDPC) codes can also be chosen for the PLS problem due to their higher error correction performance and powerful decoding for both on and below the reliability threshold [1,7], as well as sufficient performance in ultra-reliable Low Latency Communication (uRLLC) in short-packet 5G transmission systems [21]. In recent years, many researchers have focused on secrecy channel coding techniques in the wiretap channel [22,23,24,25]. In particular, the authors in [23] evaluated the reliability and security over the flat and fast-fading Gaussian wiretap channel for the construction of various LDPC codes with the puncturing and scrambling techniques. Furthermore, the authors in [26] used the McEliece coding method based on LDPC Code to guarantee both information reliability between intended users and the security metric with respect to eavesdroppers in PLS. The authors in [24] also studied the combination of LDPC codes and AN by designing the scrambling matrix to reduce the probability of outage and improve PLS. Then, the authors in [25] proposed combining the LDPC codes at the transmitter and an iterative decoding algorithm at the receiver to reduce the security gap in the Gaussian wiretap channel. The results obtained show that their proposed scheme outperforms the punctured scheme in terms of the equivocation rate and the security gap. Last but not least, the authors in [27,28] proposed joint iterative blind and semi-blind algorithms for channel estimations and decoding processes in short-packet FD transmission. The results show that these algorithms outperform the conventional algorithms without feedback in terms of not only Mean Square Error (MSE) and BER performances but also processing time and computational complexity, which are suitable for IoT transmissions and green communications.
Therefore, in this paper, we propose and implement a new scheme that combines joint iterative channel estimation and decoding using 5G QC-LDPC codes with FD self-jamming of the legitimate receiver to enhance security and reliability, which means that the eavesdropper does not catch the information and the indented information is less affected or corrupted by the jamming signal, respectively, in two scenarios: a passive eavesdropper and an active eavesdropper. For the rest of this paper, the performance evaluations of the proposed algorithms are based on three metrics: MSE, BER, and security gap (. The contributions of this paper can be summarized as follows:
- We evaluate a combination of self-jamming techniques with a joint iterative blind or semi-blind channel estimation and decoding for a FD short-packet transmissions in the cases of passive and active eavesdroppers, respectively;
- We characterize that the system developed based on the new proposed algorithms have better performance compared to the conventional algorithms without feedback in terms of security metrics;
- We point out that the legitimate receivers are less sensitive to self-interference as well as the jamming power from the eavesdropper in our approach.
- We emphasize that the proposed algorithms provides a higher robustness not only to the security and reliability factors but also to the power consumption by reducing the SNR at the legitimate receiver for decoding the message, which suits short-packet FD IoT transmissions and green communications.
The remainder of this paper is organized as follows. Section 2 briefly describes the general system model of the FD transceiver in the passive/active eavesdropper scenarios. The conventional schemes without feedback and security gaps are also mentioned in this section. Section 3 studies the application of the joint iterative blind channel estimation and decoding algorithm at the legitimate receiver in the case of passive eavesdroppers, with numerical results and comparisons with the conventional blind algorithm without feedback. Section 4 introduces the semi-blind algorithm for SI channel estimation and equalization processes in the legitimate receiver in case of active eavesdropper and simulation results. Finally, some highlights and conclusions will be discussed in Section 5. The notations in this paper are summarized in Table 1.

Table 1.
List of Notations.
2. Full-Duplex Transceiver with Passive/Active Eavesdropper Transmission System
2.1. General System Model
We consider a short-packet FD transmission wiretap channel between three users, such as user B (transmitter), user A (legitimate receiver), and user E (eavesdropper), as shown in Figure 1, where the transmitter is equipped with only one antenna for transmission while the receiver and the eavesdropper are attached with one transmitter and one receiver antenna each to simultaneously receive the intended information message and transmit self-jamming or jamming signals. The 5G QC-LDPC codes, which are considered fundamental codes for short-packet uplink and downlink transmissions [29,30,31], are used in all transceivers.
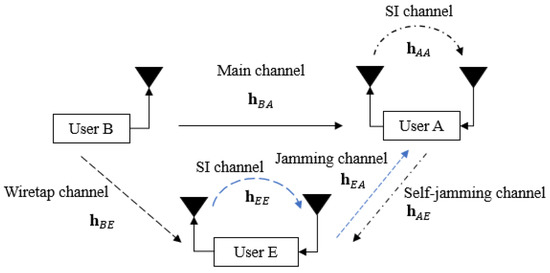
Figure 1.
General system model.
At the transmitter, the 5G QC-LDPC encoding process between the exponent parity check matrix and the information bit sequence is based on the Gauss–Jordan elimination algorithm [32], where K and N denote the lengths of the information message and the code word message, respectively. Let us denote the channel gain between two users and the SI channel gain of itself as and , respectively, in which and , where represent user A, user B, and user E, respectively. In this paper, the SI channel is modeled as quasi-static Rayleigh fading in the digital domain due to the assumption that the Line-of-Sight (LoS) component is fully suppressed by antenna and analog cancellation techniques, whereas the residual SI is the Non-Line-of-Sight (NLoS) component [8,33]. Note that and are i.i.d complex Gaussian random variables with [34,35]. Moreover, the transmitted power of each user is denoted as , where , and we further denote as the complex background noise at user Y with , where . Based on the background noise as reference and without loss in generality, we further denote and as the power-to-noise ratio provided by the self-jamming or jamming channel from user X to user Y and the SI channel at user Y, respectively. We also denote and as the SNR at user A and user E, where and are the noise powers at user A and user E, respectively.
2.2. Conventional Schemes without Feedback
The conventional blind scheme without feedback and the semi-blind scheme without feedback have been studied in [27,28], respectively, and are presented in Figure 2. At the receiver side, the received signal will pass through a Digital Self-Interference Cancellation (DSIC) process based on an adaptive filter with the Recursive Least Square (RLS) algorithm [36] to firstly estimate the SI channel and then reconstruct and cancel the SI component. Then, the residual signal will go to an equalizer to firstly estimate the intended channel and then obtain the equalized signal. In the semi-blind scheme without feedback, it is noted that the pilot symbols are attached to the information sequence at the transmitter side, and they are also used for the DSIC and equalizer processes. Then, they will be removed from the equalized signal, and this signal continuously goes to the demodulator to obtain the Log Likelihood Ratio (LLR) belief sequence. Finally, the Sum Product Algorithm (SPA) decoding algorithm [37,38] with an efficient message-passing schedule will be implemented in the 5G LDPC decoding process at user A and user E to reconstruct the binary input signal of user B. The principle of SPA involves the message repetitively passing from the check nodes to the symbol nodes for guessing the transmitted bits from each other at each iteration j until it reaches the maximum number of iterations, . For the rest of this paper, this DSIC process and decoding scheme are called blind scheme without feedback or semi-blind scheme without feedback, respectively.
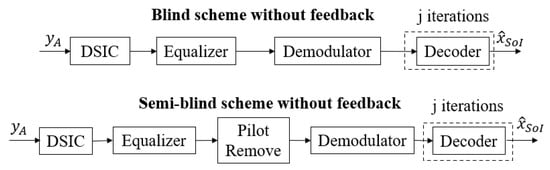
Figure 2.
Conventional schemes without feedback.
In this paper, we assume the following hypotheses:
- In case of a passive eavesdropper, only blind channel estimation is used, where there is no knowledge about the channel state information at all communication users;
- In case of an active eavesdropper, both blind and semi-blind channel estimations, where all transceivers share a few pilot symbols, are mainly implemented;
- User E knows the parity check matrix of user B and performs the SPA decoding mechanism; user E also uses an RLS algorithm in the DSIC process of user A in case of an active eavesdropper;
- Both user A and user E have equal computation capabilities, and the location of user E is close enough to user A to broadcast its jamming signal as well as to be attacked by the self-jamming signal from user A;
- The channel gains at the receiver and the eavesdropper are constant within a code word and change from one to another in fading channels;
- The impact of hardware impairments on the SI cancellation is not considered (which is outside the scope of this study but essential in practice). Moreover, the problem of the synchronization process between the transceivers is also not taken into account. Last but not least, the bit resolution of DAC/ADC is chosen to be high enough to bypass the effect of the quantization noise, i.e., larger than 6 bits for both DAC/ADC process. Alternatively, the oversampling should be applied in the ADC process if the green communication system and IoT applications are considered with low-bit ADC [39].
2.3. Security Gap
In the practical context of the wiretap channel when the short-packet is used for transmission, the typical BER performance criteria are usually used to ensure two aspects of performance such as reliability and secrecy conditions [23]. Let us denote and as the average BER of user A and user E, respectively. While and are the maximum BER that user A can achieve and the minimum BER that user E can obtain, respectively. The reliability condition holds when , which means that the BER of user A should be maintained at a low value to enhance the reliability condition. Meanwhile, the security condition is achieved when , which means that the BER of user E should remain at a sufficiently high value to guarantee the security.
According to [7,17], the security gap, which is the minimum difference of SNRs (in dB) required to guarantee the legitimate receiver security over the eavesdropper, is calculated as:
where is the minimum SNR corresponding to , where user A has to operate to make sure the BER is below some reliability thresholds, i.e., , which is a sufficient level for practical applications [23]. Similarly, is the maximum SNR corresponding to in which the BER of user E can approximately reach a threshold, that is, , which is called the security threshold because user E cannot exactly decode the information message in this region [7].
The graphical presentation of security gap is shown in Figure 3. In fact, the size of the security gap indicates the minimum cost of the difference in SNRs between user A and user E that maintains the possibility of secure communication, the higher values of will lead to a higher transmission cost. Therefore, the objective of this paper is to reduce the size of the security gap as much as possible. In particular, the SNR of user A, (dB), on the main channel must be small enough to ensure that user A can correctly decode the information message from user B assuming the lowest possible power. In contrast, the SNR of user E, (dB), on the wiretap channel must be as large as possible to guarantee that the self-jamming broadcasting from user A still affects the decoding process of user E.
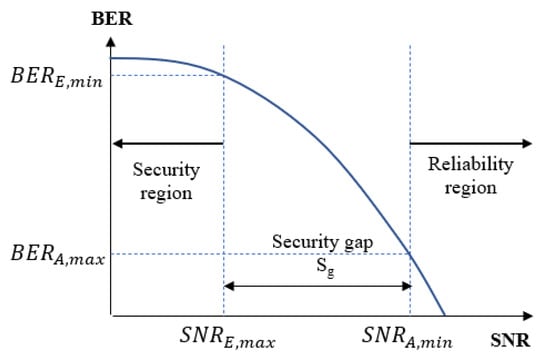
Figure 3.
Security gap.
Next, we will consider the first case with passive eavesdropper and the presence of a blind feedback algorithm.
3. Case I: Passive Eavesdropper
3.1. Passive Eavesdropper System Model
The wiretap channel system models with the use of FD self-jamming and a passive eavesdropper are shown in Figure 4 and Figure 5, where user A is operated in FD transmission mode to simultaneously receive the intended information message from user B and transmit the self-jamming signal to destroy the decoding ability of user E, while user E just tries to listen and decode the message from user B. The transmission strategy of the proposed scheme is as follows. User B wants to send his encoded message to the legitimate receiver user A through the main channel , while passive eavesdropper user E tries to listen and decode user B’s message through the wiretap channel . The received signals in the digital domain at user A and user E are given by the following:
where and are the complex Gaussian background noise of the receiver channel of user A and user E, with and , respectively, and is the convolution operation.
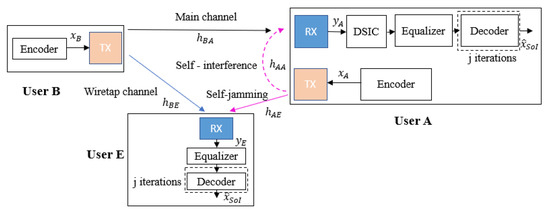
Figure 4.
Blind scheme without feedback at user A in case of a passive eavesdropper.
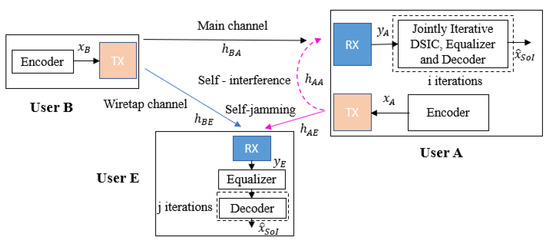
Figure 5.
Blind feedback scheme at user A in case of a passive eavesdropper.
The legitimate receiver user A obtains the signal and performs two possible decoding strategies to eliminate the SI component and obtain the estimation of the intended signal . First, it may use a classical blind scheme without feedback where the DSIC and decoding processes are independent, as presented in Figure 4. Second, it can use a more efficient scheme based on joint iterative blind channel estimation and decoding through feedback, as shown in Figure 5, which we call the blind feedback scheme. At the same time, user E also tries to listen to the transmission over the wiretap channel and only performs the equalization process and the classical SPA decoding process to obtain the original signal .
Next, we will briefly describe the joint iterative blind channel estimation and decoding processes, which were studied in [27].
3.2. Blind Feedback Scheme
The conventional scheme without feedback with the RLS algorithm and the SPA decoding algorithm is an optimal estimation [40] and decoding algorithm, but with a high computational complexity [41], because it requires an updated LLR sequence and decoding for each iteration. It is not suitable for short-packet FD transmission due to the high estimation error of the SI channel [10] and power consumption in IoT applications and green communications due to the high latency of the 5G QC-LDPC decoder [42,43]. To overcome these drawbacks, the authors in [27] proposed a joint iterative algorithm for blind channel estimation and decoding, named the blind feedback scheme. The fundamental process of the blind feedback scheme is that the SI cancellation, intended channel estimation, and decoding processes of the desired signal can benefit from each other through the temporary decoding and feedback loop. Hence, the proposed scheme will only consider one iteration of SPA decoding () for each joint iteration i, called temporary decoding, and it will then perform the re-encoding, re-interleaving, and re-modulating to form a feedback loop of the intended signal in order to improve the SI cancellation process in the next joint iterations. This is continue until the system reaches the maximum number of joint iterations . The proposed algorithm can not only decrease the processing time and computational complexity, but it can also improve the overall performance, which is illustrated in [27]. The flow chart of the proposed blind algorithm is described in Figure 6, which has four main steps and can be summarized as follows:
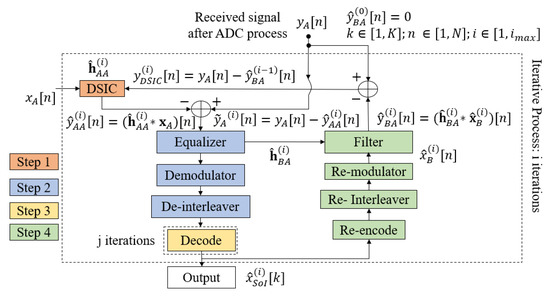
Figure 6.
Joint iterative blind algorithm flowchart.
Step 1: The mixed signal at the receiver side is firstly used to estimate the SI channel and cancel the SI component based on the reference transmitted signal ;
Step 2: The residual signal received from Step 1 is continuously used to estimate the intended channel and obtain the equalized signal by an equalizer. Here, the blind channel estimation method is applied with no knowledge of the transmitting signal from the transmitter. Then, this equalized signal goes to the demodulator and de-interleaver to obtain the LLR belief information sequence.
Step 3: In this step, the estimation of the binary intended signal is achieved by using 5G QC-LDPC decoding with the SPA algorithm.
Step 4: When the maximum number of joint iterations () is not reached, the temporary message obtained from the previous Step is re-encoded, re-interleaved, and re-modulated. Then, this signal is filtered with the estimation version of the intended channel achieved in Step 2 to form the intended feedback signal . Consequently, the intended feedback signal is used to temporarily remove the intended component from the received signal in order to optimize the SI channel estimation process for the next joint iteration.
3.3. Simulation Specifications
To evaluate the secrecy performance of our proposed schemes, MSE, BER, and security gap will be computed by using Monte Carlo simulations in MATLAB. For the rest of this paper, the MSE of the channel estimation in the intended receiver user A and the eavesdropper user E are given by [44]:
and
respectively.
For 5G QC-LDPC codes, the base graph matrix BG2 [30] is implemented for all simulations. The SI channel and self-jamming or jamming channel are fixed with three taps based on Rayleigh distribution with . The intended main channel and wiretap are fixed with four taps and the power of each tap is according to the ITU–R channel model [45]. These channels are generated independently in each transmission frame. The simulation parameters of this paper are summarized in Table 2.

Table 2.
Simulation Specifications.
3.4. MSE Performances
3.4.1. MSE at the Legitimate Receiver User A
First, the MSEs of SI channel and main channel at user A are computed for different values of self-interference-to-noise ratio . For instance, Figure 7a,b show the MSEs of the SI channel versus of the legitimate receiver user A in the blind without feedback and blind feedback schemes, respectively. Similarly, Figure 8a,b illustrate the MSEs of the main channel versus the at user A in the blind without feedback and blind feedback schemes, respectively. It can be seen that MSEs increase significantly as the self-interference-to-noise ratio of user A () increases, and the blind feedback scheme outperforms the scheme without feedback. It can also be observed that the increase in the self-interference-to-noise ratio of user A has less effect on the blind feedback scheme than the scheme without feedback. For example, maintaining at , when increases from 0 to 30 dB, requires an increase of only around 2.5 to 3 dB in the blind feedback scheme. However, it requires an increase of roughly 10 dB in the scheme without feedback. Therefore, the use of the blind feedback scheme can improve the channel estimation processes at user A significantly.
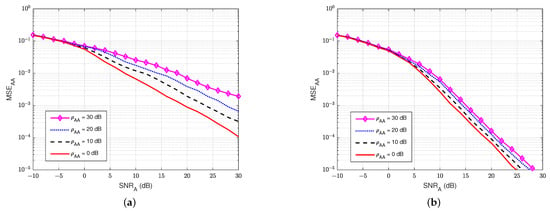
Figure 7.
versus in case of passive eavesdropper: (a) Blind without feedback; (b) Blind feedback.
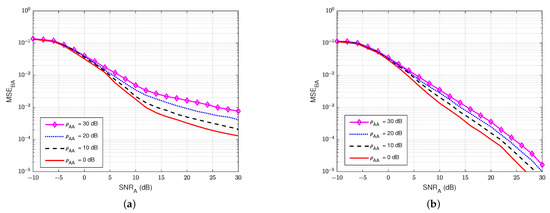
Figure 8.
versus in case of passive eavesdropper: (a) Blind without feedback; (b) Blind feedback.
3.4.2. MSE at the Eavesdropper User E
Next, we also evaluate the MSE of the wiretap channel versus the signal-to-noise ratio at the eavesdropper user E () for various values of the self-jamming-to-noise ratio from user A, . Based on Figure 9, it can be clearly observed that user E cannot estimate the wiretap channel well, especially in the case of a high value of the self-jamming-to-noise ratio of user A, i.e., when increases higher than 10 dB. This behavior is due to the lack of knowledge of the reference signal of the transmitter as well as the power of the self-jamming signal from user A, which is much greater than the power of the intended signal. So, we can conclude that user E cannot accurately estimate the wiretap channel in passive mode.
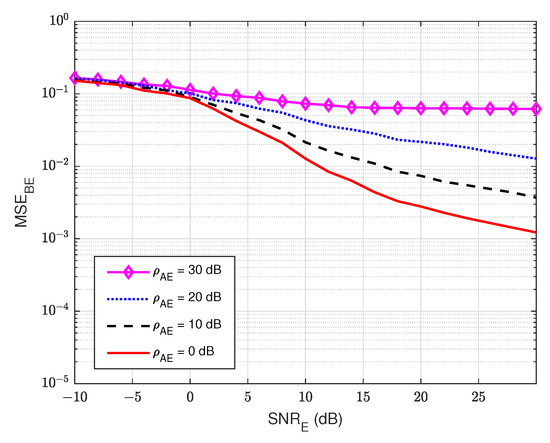
Figure 9.
versus in case of passive eavesdropper.
3.5. BER Performances
3.5.1. BER at the Legitimate Receiver User A
The BER performances versus the of user A, for different values of the self-interference-to-noise ratio of user A (), are presented in Figure 10a,b for both the without feedback and blind feedback schemes, respectively. We can observe that the self-interference-to-noise ratio also significantly impacts the BER’s performance, i.e., the BER increases as the increases, and the increase in the BER is bigger for larger . It also shows an interesting result that when maintaining and increasing the self-interference-to-noise ratio from 0 to 30 dB, the blind feedback scheme needs about 2 to 3 dB in to obtain that BER, while the scheme without feedback requires more than 5 dB in to achieve comparable results. Therefore, in the passive eavesdropper case, the increase in the self-interference-to-noise ratio has less effect on the blind feedback scheme in the BER performance at the legitimate receiver user A.
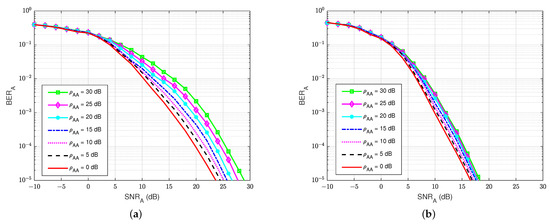
Figure 10.
versus in case of a passive eavesdropper: (a) Blind without feedback; (b) Blind feedback.
3.5.2. BER at the Eavesdropper User E
At the eavesdropper user E, the BER’s performances versus are also calculated to evaluate how much user E can decode the message sent from user B. For the rest of this paper, we have decided to keep the same BER ranges ( to ) without focusing on the useful ranges in order to allow for a visual comparison of the different schemes and especially the performance differences between legitimate user A and eavesdropper E. As shown in Figure 11, it is shown that the presence of a self-jamming signal from user A has a significant impact on the estimation and decoding processes of user E, regardless of the knowledge of the channel coding used for decoding. The best BER that user E can obtain is about at dB. Furthermore, when the self-jamming-to-noise ratio is greater than 15 dB, user E almost cannot decode the intended message from user B. It can be explained that user A can estimate the SI channel well and cancel the SI component because user A has its generated self-jamming signal as reference. Moreover, applying the blind feedback scheme also improves the channel estimation and decoding processes, although user A also has no knowledge about the reference signal from user B. In contrast, user E has no knowledge about the reference signal of user B and the self-jamming signal of user A, and there is no interference cancellation mechanism applied; instead, it uses only the SPA decoding scheme to decode the intended message.
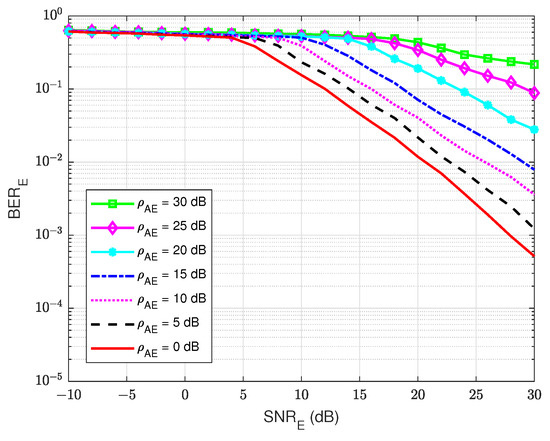
Figure 11.
versus the in case of a passive eavesdropper.
Therefore, user E cannot operate efficiently in the estimation and decoding processes. In summary, by applying the joint iterative estimation and decoding to the legitimate receiver, user A can significantly improve the secrecy reliability factor in FD wiretap transmission.
3.6. Security Gap Performance
On the one hand, there is an assumption concerning the relative positions of the various transmitters/receivers. In particular, for the case of user A and user E, it seems coherent and acceptable to consider that the powers of the background noises and are identical. On the other hand, under the assumption of channels without loss (unified mean deviations on all the paths) for and , it is possible to simplify the notations and to denote in general the self-jamming power-to-noise ratio as for both self-interference and self-jamming channels. Since, in these conditions, we have . The security gap is clearly related to the error rate achieved on the receiver side of user A and user E. In order to adapt to the practical applications, we set up and for the maximum and minimum average errors that user A and user E can reach, respectively. Based on the results in Figure 10 and Figure 11, the minimum SNR at the legitimate user A, the and the maximum SNR at the eavesdropper user E, and to obtain and , respectively, can be pointed out. Then, these values are recorded corresponding to different levels of the general self-jamming power-to-noise ratio . Finally, the security gap is calculated and summarized in Table 3.

Table 3.
Security gap in case of passive eavesdropper.
Figure 12 shows the security gap versus the various values of the self-jamming power-to-noise ratio () in the case of blind without feedback and blind feedback at user A. The result shows that the increase in the self-jamming power-to-noise ratio leads to a decrease in the security gap . For example, the security gap can be dramatically reduced from 7 to 10 dB when the blind feedback scheme is applied. Therefore, it obtains an important goal of the PLS, which is to maintain the security gap as small as possible. In summary, the use of joint iterative blind estimation and decoding at the legitimate receiver user A significantly reduces the security gap in FD wiretap transmission. Furthermore, when using the blind feedback scheme, the of user A is reduced when performing channel estimation or decoding messages, compared with the blind scheme without feedback, which emphasizes that the system not only maintains security but also enhances power consumption by reducing the transmission power.
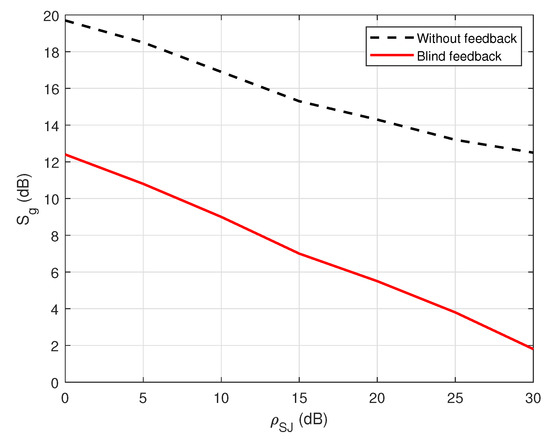
Figure 12.
versus in the case of a passive eavesdropper.
In the next section, we will consider the second case, where user E can also send their jamming message to destroy the reception and decoding processes of user A, which we refer to as an active eavesdropper.
4. Case II: Active Eavesdropper
4.1. Active Eavesdropper System Model
The wiretap channel system model with the use of FD self-jamming and an active eavesdropper is shown in Figure 13.
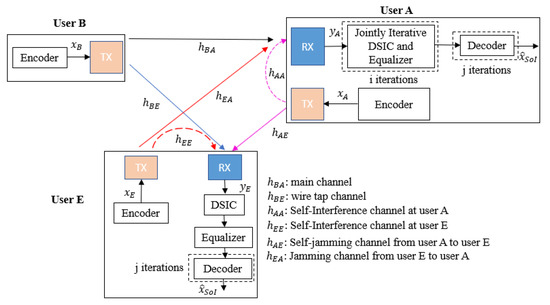
Figure 13.
Wiretap Full-Duplex transmission with self-jamming in case of an active eavesdropper.
In this case, both user A and user E operate in the FD transmission mode to simultaneously receive the intended information message from user B and transmit the self-jamming or jamming signal to other users. In particular, user B wants to send his encoded message to the legitimate receiver user A by the main channel, while the eavesdropper user E not only tries to listen to and decode user B’s message by the wiretap channel but also simultaneously broadcasts their jamming signal to user A. Consequently, the received signals in the digital domain at user A and user E are given by:
and
respectively.
It can be seen that the signal-to-noise ratio at user A is reduced due to the impact of the jamming signal from user E, which leads to an increase in noise at the receiver of user A. Therefore, in addition to the proposed blind feedback scheme, the joint iterative SI channel estimation and equalization processes with the semi-blind algorithm, which have been studied in [28], should be used at user A in order to eliminate the SI component and estimate the intended signal because the proposed semi-blind algorithm shows its robustness in the low region of the SNR, compared to the blind algorithm. Indeed, the principle of this algorithm is to use at least four pilot symbols between the transceivers (which is a sufficient number of pilot symbols, as shown in [28]) to perform the channel estimation processes as well as the feedback loop. At the receiver side of user E, in order to distinguish the decoding behavior of the legitimate receiver (user A) and the eavesdropper (user E) and to also show the robustness of two proposed feedback schemes over the conventional schemes without feedback, user E will only use the blind scheme without feedback and the semi-blind scheme without feedback. In case of the semi-blind scheme without feedback, it is also assumed that four pilot symbols are observed by user E.
Next, we will briefly mention and summarize the joint iterative semi-blind channel estimation and equalization processes and name it the semi-blind feedback scheme.
4.2. Semi-Blind Feedback Scheme
In the case of a passive eavesdropper, it is shown that the performance is better when using the blind feedback scheme. However, in the case of an active eavesdropper, the presence of a jamming signal from user E leads to significant destruction of the reception behavior of user A. Therefore, small sharing of known symbols or pilot symbols between user B and user A should be established to guarantee the reliability and security of transmissions.
The processing flowchart of the semi-blind algorithm is presented in Figure 14. In general, it is nearly similar to the joint iterative blind feedback algorithm in Section 3.2, except that the temporary decoding and encoding processes are skipped. Instead, the known pilot symbols, which are added to the information sequence on the transmitter side, are used to form the intended signal and the feedback loop. In particular, for (first iteration of the iterative algorithm), a first SI cancellation and intended channel estimation are performed for all symbols in order to overcome a larger number of errors and achieve a sufficient level of convergence. When , the known pilot symbols (symbols) are used to form the feedback loop. When it reaches the maximum number of iterations (), the algorithm is stopped, the SI component can be canceled, and the equalized signal can be fully achieved by the estimation versions of the SI channel and the intended channel. After that, the known pilot symbols are suppressed, and the equalized signal will undergo the demodulation, de-interleaver, and decoding processes to obtain the final decoded message. Here, it is noticed that the SPA decoding algorithm also performs only one iteration ( in the decoding step when the system achieves the best channel estimation ().
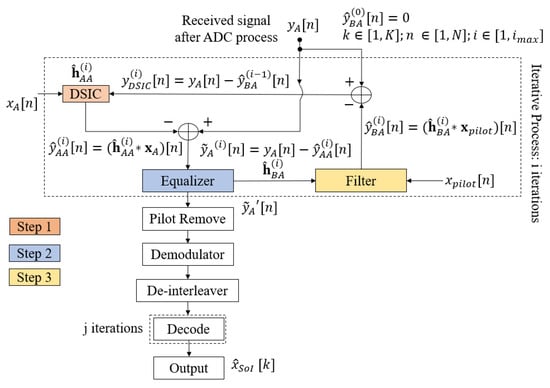
Figure 14.
Joint iterative semi-blind algorithm flow chart.
The proposed semi-blind algorithm can be summarized in three steps:
Step 1: The received signal is used to estimate the SI channel and to cancel the SI component based on the reference transmitted signal ;
Step 2: The residual signal after step 1 will go to an equalizer to estimate the intended channel ;
Step 3: Using pilot symbols that are added to the information sequence on the transmitting side, a feedback loop is created with the estimation version of the intended channel to form . This signal is passed to the subtraction process from the received signal and performs the next joint iterations.
Next, we will introduce the performance in terms of the MSE, BER, and security gap in the case of an active eavesdropper.
4.3. Mean Square Error (MSE) Performance
4.3.1. MSE at the Legitimate Receiver User A
First of all, Figure 15 and Figure 16 illustrate the MSEs of the SI channel and the main channel at user A for the blind feedback scheme and the semi-blind feedback scheme, respectively, versus for different power values of the jamming-to-noise ratio broadcast from user E, while the self-interference-to-noise ratio at user A, , is fixed at 30 dB. It can be seen that the presence of the jamming signal from user E significantly impacts the SI channel estimation at user A, where it increases the noise level at the receiver side at user A, compared with the passive case. Indeed, the gain between each MSE’s curve is bigger than in the passive case, whatever the algorithm used, which means that the system requires higher to estimate the channel. Furthermore, the semi-blind feedback scheme outperforms the blind feedback scheme, i.e, it converges faster to the error floor and achieves better results than the blind feedback scheme because the traces of four pilot symbols is used. Therefore, using the semi-blind algorithm can improve the channel estimation processes and reduce the impact of the jamming signal from the eavesdropper.
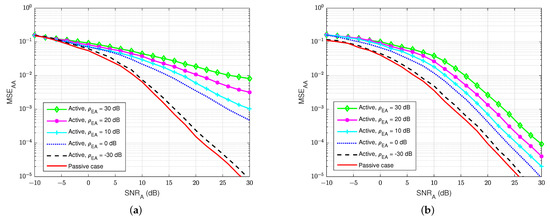
Figure 15.
versus , dB in case of active eavesdropper: (a) Blind feedback; (b) Semi-blind feedback.
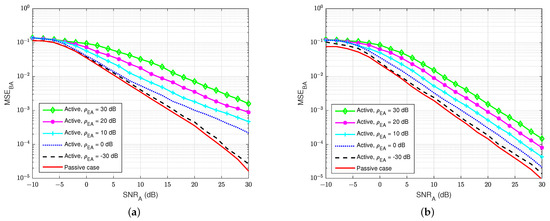
Figure 16.
versus , dB in case of an active eavesdropper: (a) Blind feedback; (b) Semi-blind feedback.
4.3.2. MSE at the Eavesdropper User E
Next, Figure 17 and Figure 18 show the MSEs of the SI channel and the wiretap channel versus at the eavesdropper user E for various values of the self-jamming-to-noise ratio from user A, . The self-interference-to-noise ratio at user E, , is fixed at 30 dB. It can be clearly observed that user E cannot estimate the wiretap channel and the SI channel well, especially if there is a high self-jamming-to-noise ratio from user A, i.e., increases higher than 20 dB. So, the self-jamming signal provided by user A significantly influences the receiver side of user E, where user E cannot perform the wiretap channel estimation well in active mode, although user E also knows the pilot symbols. Moreover, the power of the combination of the self-jamming of user A and the SI component at user E is also higher than the power level of the intended message from user B. Therefore, the blind scheme without feedback and the semi-blind scheme without feedback, which are applied to user E, cannot estimate the channels well.
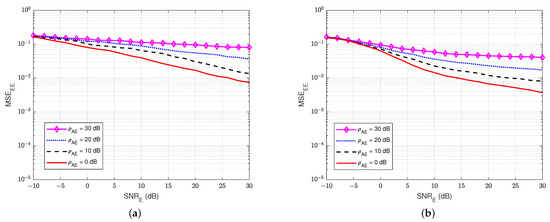
Figure 17.
versus , = 30 dB in case of an active eavesdropper. (a) Blind without feedback; (b) Semi-blind without feedback.
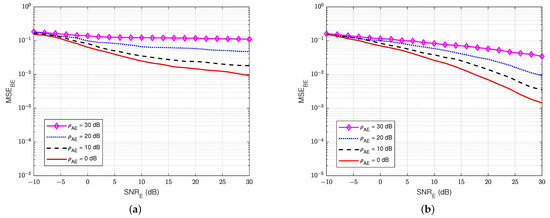
Figure 18.
versus , = 30 dB in case of an active eavesdropper: (a) Blind without feedback; (b) Semi-blind without feedback.
4.4. Bit-Error-Rate (BER) Performance
4.4.1. BER at the Legitimate Receiver User A
The BER performances versus at user A for different values of the jamming-to-noise ratio from user E () are illustrated in Figure 19a,b for both the blind feedback scheme and the semi-blind scheme at user A, respectively. The self-interference-to-noise ratio at user A () is set at 30 dB. We can observe that the BER increases as the jamming-to-noise ratio of user E () increases, and the increase in the BER is bigger for larger values compared with the passive case. We can also remark that the semi-blind scheme is less sensitive to the jamming from user E than the blind feedback scheme, and it also converges faster to the error floor than the other. In particular, when maintaining and increasing the jamming-to-noise ratio from 0 to 30 dB, the blind feedback scheme needs about 5 dB in , while the semi-blind feedback scheme requires only 2.5 to 3 dB to reach that result. Therefore, the semi-blind feedback scheme is suitable in the case of an active eavesdropper because the increase in jamming power from the active user E has less influence on the BER performance at the legitimate receiver user A. In fact, it can considerably improve the reliability factor of secrecy in FD wiretap transmission in the case of an active eavesdropper.
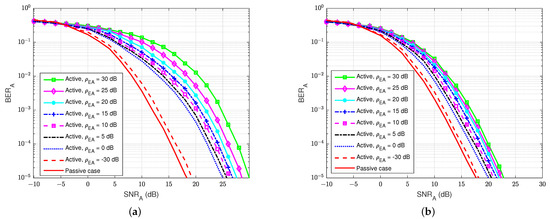
Figure 19.
versus , dB in case of an active eavesdropper: (a) Blind feedback; (b) Semi-blind feedback.
4.4.2. BER at the Eavesdropper User E
At the active eavesdropper user E, the BER performances versus are also calculated to evaluate the amount of the message that user E can decode. As shown in Figure 20, it can be seen that the combination of both the jamming signal from user A and the self-interference component at user E themself has a major impact on the estimating and decoding process of user E. This is because the combined power of these two signals is larger than the power of the intended signal, and user E only uses the blind or semi-blind scheme without feedback for channel estimation and decoding, regardless of the knowledge of channel coding used for decoding and the four pilot symbols. The best BER that user E can obtain is about at dB, corresponding to the lowest level of the self-jamming-to-noise ratio from user A, dB. Consequently, when the power of the self-jamming signal from user A increases, user E needs a very large to decode the intended message from user B.
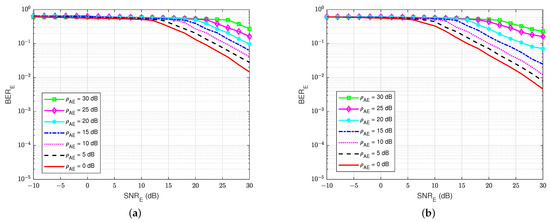
Figure 20.
versus , dB in case of an active eavesdropper: (a) Blind without feedback; (b) Semi-blind without feedback.
Furthermore, Figure 21 shows the BER of user E versus the for various values of the self-interference-to-noise ratio of itself, , while the self-jamming-to-noise ratio of user A, is fixed at 30 dB. It shows that if user E tries to increase the power of the jamming signal that is sent to user A, it leads to an increase in their BER because of the increase in the self-interference-to-noise ratio . Although SI can be suppressed by the knowledge of the SI signal by the classical DSIC process, the interference from the self-jamming signal from user A still significantly impacts the blind scheme without feedback and the semi-blind scheme without feedback. It looks like the case of a passive eavesdropper when user E cannot suppress the interference from the jamming signal of user A well. However, the BER of user A is less sensitive to the increased power of user E, especially for the semi-blind feedback scheme, as shown in Figure 19.
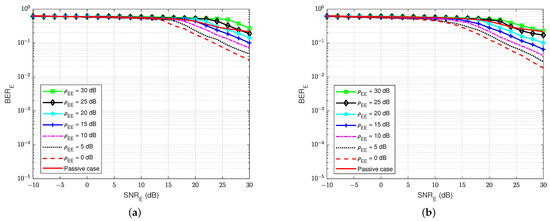
Figure 21.
versus , dB in case of an active eavesdropper: (a) Blind without feedback; (b) Semi-blind without feedback.
Therefore, it can be concluded that user E cannot decode the message well, regardless of using the blind scheme without feedback or the semi-blind scheme without feedback.
4.5. Security Gap Performance
Considering the same assumptions that have been made for background noises and propagation channels in the case of a passive eavesdropper in Section 3.6, it is also possible to simplify the notations and to denote in general the self-jamming power-to-noise ratio as for both self-jamming and jamming channels. Since, in these conditions, we have , adapting for practical applications, we also set and for the maximum and minimum average errors that user A and user E can obtain, respectively. According to the results in Figure 19 and Figure 20, in order to achieve and , the minimum SNR at the legitimate user A, , and the maximum SNR at the eavesdropper user E, , can be pointed out for different values of the general self-jamming power-to-noise ratio () and for different decoding schemes at user A and user E. Then, the security gap is calculated based on and and summarized in Table 4 and Table 5 when using the blind scheme without feedback and the semi-blind scheme without feedback at user E, respectively.

Table 4.
The security gap when applying the blind scheme without feedback at user E.

Table 5.
The security gap when applying the semi-blind scheme without feedback at user E.
Figure 22 shows the comparison of the security gap with the various values of the general self-jamming power-to-noise ratio, , between the application of the blind feedback scheme and the semi-blind feedback scheme on the decoding side of user A. It indicates that the increase in the self-jamming power-to-noise ratio leads to a decrease in the security gap for all cases. The proposed semi-blind feedback scheme also allows for reducing the security gap from about 5 to 7 dB compared to the blind feedback scheme, regardless of the use of the blind or semi-blind scheme without feedback in user E. Therefore, it can keep the security gap as small as possible, which is the most important factor in PLS. Furthermore, the of user A is reduced when performing channel estimation or decoding the message using the semi-blind feedback scheme, compared to the blind feedback scheme, which means that the system not only guarantees the security factor but also improves power consumption.
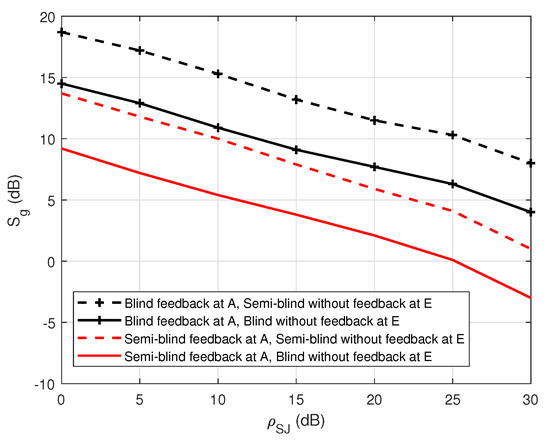
Figure 22.
versus in case of an active eavesdropper.
5. Conclusions
The secrecy analysis of FD short-packet transmission in a wiretap channel for both passive and active eavesdroppers has been implemented, subject to the constraints of the MSE, BER, security gap . This paper highlights that the presence of a jamming signal has a major effect on the reliability and security factors in PLS. To deal with this effect, a joint iterative SI channel estimation, propagation channel estimation, and decoding algorithm in FD transmissions via feedback were applied at the legitimate receiver, including blind feedback or semi-blind feedback schemes in the case of passive and active eavesdroppers, respectively. The numerical results presented show that the proposed algorithms, such as the blind feedback scheme in the passive case and the semi-blind feedback scheme in the active case, outperform the conventional algorithms without feedback, where the security gap is significantly reduced. Moreover, it can be noticed that the blind feedback scheme in the case of a passive eavesdropper and the semi-blind feedback scheme in the case of an active eavesdropper are less sensitive to the increase in self-jamming power. Moreover, the SNR of the legitimate receiver is reduced when applying the proposed schemes to decode the intended message, which means that the system not only ensures the security factor well, but it also significantly improves the power consumption by reducing the transmitting power. It is also noted that the proposed blind and semi-blind algorithms have better performances in terms of processing time and computational complexity, which are shown in [27,28]. Therefore, the presence of joint iterative estimation and decoding with blind and semi-blind algorithms at the legitimate receiver is highly recommenced to enhance the security of FD wiretap transmission, especially in short-packet transmission-specific to IoT applications and green communications.
6. Future Works
In the near future, several interesting investigations should be established in the context of the physical layer security field, especially in FD short-packet transmission. First, the location of the eavesdropper will be considered to emphasize the outperformance of the proposed algorithm with the conventional algorithm. Moreover, a hardware implementation based on Software-Defined Radio (SDR) will be considered to emphasize the performance of the proposed schemes in realistic transmission scenarios for IoT applications and green communications.
Author Contributions
Conceptualization, B.Q.V., A.F. and R.G.; methodology, B.Q.V., A.F. and R.G.; software, B.Q.V. and C.D.-S.; validation, M.M., A.F. and R.G.; formal analysis, B.Q.V., A.F. and R.G.; investigation, B.Q.V., R.G. and A.F.; resources, B.Q.V. and C.D.-S.; data curation, B.Q.V. and A.F.; writing—original draft preparation, B.Q.V. and A.F.; writing—review and editing, B.Q.V., R.G., A.F., M.M. and C.D.-S.; visualization, B.Q.V., A.F. and M.M.; supervision, R.G. and M.M.; project administration, R.G.; funding acquisition, R.G., A.F. and M.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research is jointly supported by the IBNM (Brest Institute of Computer Science and Mathematics), CyberIoT Chair of Excellence at the University of Brest (UBO), and the Brittany region—Pôle d’Excellence Cyber.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Acknowledgments
The authors would like to thank to the University of Brest (UBO), the Direction Europe and International (DEI), the IBNM (Brest Institute of Computer Science and Mathematics) CyberIoT Chair of Excellence, and the Brittany region—Pôle d’Excellence Cyber for their funding.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| 3GPP | The Third-Generation Partnership Project |
| 5G | The Fifth Generation |
| ADC | Analog-to-Digital Converter |
| BER | Bit Error Rate |
| DAC | Digital-to-Analog Converter |
| DSIC | Digital Self-interference Cancellation |
| FD | Full-Duplex |
| IoT | Internet of Things |
| ITU | International Telecommunication Union |
| LLR | Log Likelihood Ratio |
| LoS | Line-of-Sight |
| MSE | Mean Square Error |
| NLoS | Non-Line-of-Sight |
| PLS | Physical Layer Security |
| QC-LDPC | Quasi-Cyclic Low-Density Parity Check |
| QPSK | Quadature Phase Shift Keying |
| RF | Radio Frequency |
| RLS | Recursive Least Square |
| SDR | Software-Defined Radio |
| SI | Self-Interference |
| SPA | Sum Product Algorithm |
| uRLLC | Ultra-reliable Low-Latency Communication |
References
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.K.; Gao, X. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef] [Green Version]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V. Improving Wireless Physical Layer Security via Cooperating Relays. IEEE Trans. Signal Process. 2012, 58, 1875–1888. [Google Scholar] [CrossRef]
- Nguyen, B.V.; Jung, H.; Kim, K. Physical Layer Security Schemes for Full-Duplex Cooperative Systems: State of the Art and Beyond. IEEE Commun. Mag. 2018, 56, 131–137. [Google Scholar] [CrossRef] [Green Version]
- Wyner, A.D. The Wire-Tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Ozarow, L.H.; Wyner, A.D. Wire-Tap Channel II. Bell Syst. Tech. J. 1984, 63, 2135–2157. [Google Scholar] [CrossRef]
- Arı, N.; Thomos, N.; Musavian, L. Active Eavesdropping in Short Packet Communication: Average Secrecy Throughput Analysis. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Klinc, D.; Ha, J.; McLaughlin, S.W.; Barros, J.; Kwak, B.J. LDPC Codes for the Gaussian Wiretap Channel. IEEE Trans. Inf. Forensics Secur. 2011, 6, 532–540. [Google Scholar] [CrossRef]
- Ahmed, E.; Eltawil, A.M. All-Digital Self-Interference Cancellation Technique for Full-Duplex Systems. IEEE Trans. Wirel. Commun. 2015, 14, 3519–3532. [Google Scholar] [CrossRef] [Green Version]
- Khan, R.; Tsiga, N.; Asif, R. Interference Management with Reflective In-Band Full-Duplex NOMA for Secure 6G Wireless Communication Systems. Sensors 2022, 22, 2508. [Google Scholar] [CrossRef]
- Liu, Y.; Zhu, X.; Lim, E.G.; Jiang, Y.; Huang, Y. Fast Iterative Semi-Blind Receiver for URLLC in Short-Frame Full-Duplex Systems With CFO. IEEE J. Sel. Areas Commun. 2019, 37, 839–853. [Google Scholar] [CrossRef]
- Zhang, J.; He, F.; Li, W.; Li, Y.; Wang, Q.; Ge, S.; Xing, J.; Liu, H.; Li, Y.; Meng, J. Self-Interference Cancellation: A Comprehensive Review from Circuits and Fields Perspectives. Electronics 2022, 11, 172. [Google Scholar] [CrossRef]
- Chen, Y.; Ding, C.; Jia, Y.; Liu, Y. Antenna/Propagation Domain Self-Interference Cancellation (SIC) for In-Band Full-Duplex Wireless Communication Systems. Sensors 2022, 22, 1699. [Google Scholar] [CrossRef] [PubMed]
- Wang, H.M.; Wang, C.; Ng, D.W.K. Artificial Noise Assisted Secure Transmission Under Training and Feedback. IEEE Trans. Signal Process. 2015, 63, 6285–6298. [Google Scholar] [CrossRef]
- Silva, A.; Gomes, M.; Vilela, J.; Harrison, W. SDR Proof-of-Concept of Full-Duplex Jamming for Enhanced Physical Layer Security. Sensors 2021, 21, 856. [Google Scholar] [CrossRef] [PubMed]
- Zheng, G.; Krikidis, I.; Li, J.; Petropulu, A.P.; Ottersten, B. Improving Physical Layer Secrecy Using Full-Duplex Jamming Receivers. IEEE Trans. Signal Process. 2013, 61, 4962–4974. [Google Scholar] [CrossRef] [Green Version]
- Li, W.; Ghogho, M.; Chen, B.; Xiong, C. Secure Communication via Sending Artificial Noise by the Receiver: Outage Secrecy Capacity/Region Analysis. IEEE Commun. Lett. 2012, 16, 1628–1631. [Google Scholar] [CrossRef]
- Dryer, Z.; Nickerl, A.; Gomes, M.A.C.; Vilela, J.P.; Harrison, W.K. Full-Duplex Jamming for Enhanced Hidden-Key Secrecy. In Proceedings of the ICC 2019—2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Shang, Z.; Zhang, T.; Cai, Y.; Yang, W.; Wu, H.; Zhang, Y.; Tao, L. Secure Transmission in Cognitive Wiretap Networks with Full-Duplex Receivers. Appl. Sci. 2020, 10, 1840. [Google Scholar] [CrossRef] [Green Version]
- Li, Y.; Zhao, R.; Tan, X.; Nie, Z. Secrecy performance analysis of artificial noise aided precoding in full-duplex relay systems. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Yan, S.; Zhou, X.; Yang, N.; Abhayapala, T.D.; Swindlehurst, A.L. Secret Channel Training to Enhance Physical Layer Security With a Full-Duplex Receiver. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2788–2800. [Google Scholar] [CrossRef] [Green Version]
- Sybis, M.; Wesolowski, K.; Jayasinghe, K.; Venkatasubramanian, V.; Vukadinovic, V. Channel Coding for Ultra-Reliable Low-Latency Communication in 5G Systems. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Merhav, N. Encoding Individual Source Sequences for the Wiretap Channel. Entropy 2021, 23, 1694. [Google Scholar] [CrossRef]
- Macro, B.; Nicola, M.; Giocomo, R.; Franco, C. Security gap analysis of some LDPC coded transmission schemes over the flat and fast fading Gaussian wire-tap channels. EURASIP J. Wirel. Commun. Netw. 2015, 15, 232. [Google Scholar] [CrossRef] [Green Version]
- Yang, Z.; Fan, Y.; Wang, A. Artificial noise and LDPC code aided physical layer security enhancement. In Proceedings of the 2014 International Conference on Information and Communications Technologies (ICT 2014), Nanjing, China, 15–17 May 2014; pp. 1–6. [Google Scholar]
- Du, J. A Partially Coupled LDPC Coded Scheme for the Gaussian Wiretap Channel. IEEE Commun. Lett. 2020, 24, 7–10. [Google Scholar] [CrossRef]
- Li, L.; Xing, Y.; Yao, X.; Luo, Y. McEliece Coding Method based on LDPC Code with Application to Physical Layer Security. In Proceedings of the 2021 7th International Conference on Computer and Communications (ICCC), Chengdu, China, 10–13 December 2021; pp. 2042–2045. [Google Scholar] [CrossRef]
- Vuong, B.Q.; Gautier, R.; Fiche, A.; Marazin, M.; Ta, H.Q.; Nguyen, L.L. Joint Iterative Blind Self-Interference Cancellation, Propagation Channel Estimation and Decoding Processes in Full-Duplex Transmissions. IEEE Access 2022, 10, 22795–22807. [Google Scholar] [CrossRef]
- Vuong, B.Q.; Gautier, R.; Ta, H.Q.; Nguyen, L.L.; Fiche, A.; Marazin, M. Joint Semi-Blind Self-Interference Cancellation and EqualisationProcesses in 5G QC-LDPC-Encoded Short-Packet Full-Duplex Transmissions. Sensors 2022, 22, 2204. [Google Scholar] [CrossRef] [PubMed]
- Bae, J.H.; Abotabl, A.; Lin, H.P.; Song, K.B.; Lee, J. An overview of channel coding for 5G NR cellular communications. Trans. Signal Inf. Process. 2019, 8, e17. [Google Scholar] [CrossRef] [Green Version]
- 3GPP. TS 38.212 NR- Multiplexing and Channel Coding. 2018. Available online: https://www.etsi.org/deliver/etsi_ts/138200_138299/138212/15.02.00_60/ts_138212v150200p.pdf (accessed on 29 June 2018).
- Li, H.; Bai, B.; Mu, X.; Zhang, J.; Xu, H. Algebra-Assisted Construction of Quasi-Cyclic LDPC Codes for 5G New Radio. IEEE Access 2018, 6, 50229–50244. [Google Scholar] [CrossRef]
- Clapham, C.; Jordan, N. The Concise Oxford Dictionary of Mathematics; Oxford University Press: Oxford, UK, 2013. [Google Scholar]
- Everett, E.; Sahai, A.; Sabharwal, A. Passive Self-Interference Suppression for Full-Duplex Infrastructure Nodes. IEEE Trans. Wirel. Commun. 2014, 13, 680–694. [Google Scholar] [CrossRef] [Green Version]
- Koohian, A.; Mehrpouyan, H.; Nasir, A.A.; Durrani, S.; Blostein, S.D. Residual self-interference cancellation and data detection in full-duplex communication systems. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017. [Google Scholar]
- Kim, T.; Kyungsik, M.; Park, S. Self-Interference Channel Training for Full-Duplex Massive MIMO Systems. Sensors 2021, 21, 3250. [Google Scholar] [CrossRef]
- Haykin, S. Adaptive Filter Theory; Pearson: London, UK, 1993; Volume 29. [Google Scholar]
- Sharon, E.; Litsyn, S.; Goldberger, J. An efficient message-passing schedule for LDPC decoding. In Proceedings of the 2004 23rd IEEE Convention of Electrical and Electronics Engineers in Israel, Tel-Aviv, Israel, 6–7 September 2004; pp. 223–226. [Google Scholar]
- Zhang, X.; Siegel, P.H. Quantized iterative message passing decoders with low error floor for LDPC codes. IEEE Trans. Commun. 2014, 62, 1–14. [Google Scholar]
- Vuong, B.Q.; Gautier, R.; Fiche, A.; Marazin, M. Full-Duplex Efficient Channel Codes for Residual Self-Interference/Quantization Noise Cancellation. In Proceedings of the IEEE 15th International Conference on Signal Processing and Communication Systems (ICSPCS), Sydney, Australia, 13–15 December 2021. [Google Scholar]
- Despina-Stoian, C.; Digulescu-Popescu, A.; Alexandra, S.; Youssef, R.; Radoi, E. Comparison of Adaptive Filtering Strategies for Self-Interference Cancellation in LTE Communication Systems. In Proceedings of the 13th International Conference on Communications (COMM), Bucharest, Romania, 18–20 June 2020. [Google Scholar]
- Mostari, L.; Taleb ahmed, A. High performance short-block binary regular LDPC codes. AEJ Alex. Eng. J. 2018, 57, 2633–2639. [Google Scholar] [CrossRef]
- Iscan, O.; Lentner, D.; Xu, W. A Comparison of Channel Coding Schemes for 5G Short Message Transmission. In Proceedings of the 2016 IEEE Globecom Workshops (GC Wkshps), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Hajiyat, Z.; Sali, A.; Mokhtar, M.; Hashim, F. Channel Coding Scheme for 5G Mobile Communication System for Short Length Message Transmission. Wirel. Pers. Commun. 2019, 106, 377–400. [Google Scholar] [CrossRef]
- Masmoudi, A.; Le-Ngoc, T. A Maximum-Likelihood Channel Estimator for Self-Interference Cancelation in Full-Duplex Systems. IEEE Trans. Veh. Technol. 2016, 65, 5122–5132. [Google Scholar] [CrossRef]
- ITU. Guidelines for Evaluation of Radio Transmission Technologies for IMT-2000; International Telecommunication Union: Geneva, Switzerland, 1997. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).