Proactive Caching in D2D Assisted Multitier Cellular Network
Abstract
:1. Introduction
1.1. Motivation and Related Work
1.2. Contributions and Outcomes
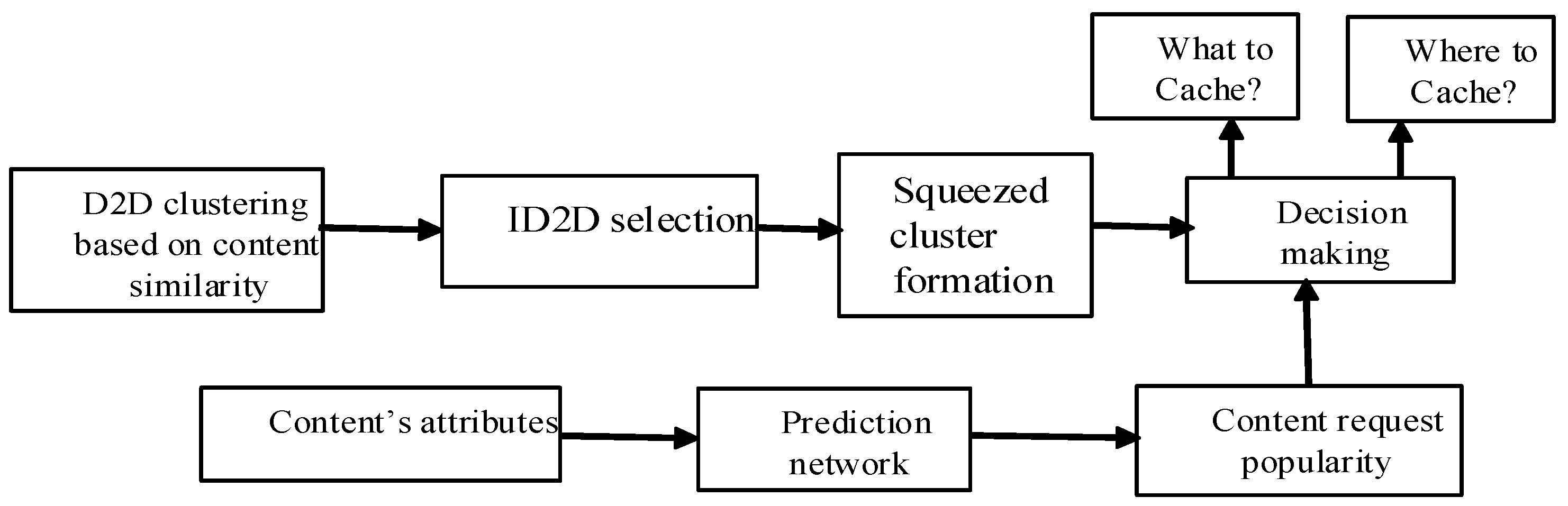
1.2.1. Novel Caching Scheme
1.2.2. Implementation of Content Placement Techniques
1.2.3. Content Delivery Decision Making
1.2.4. Maximization of Objective Function
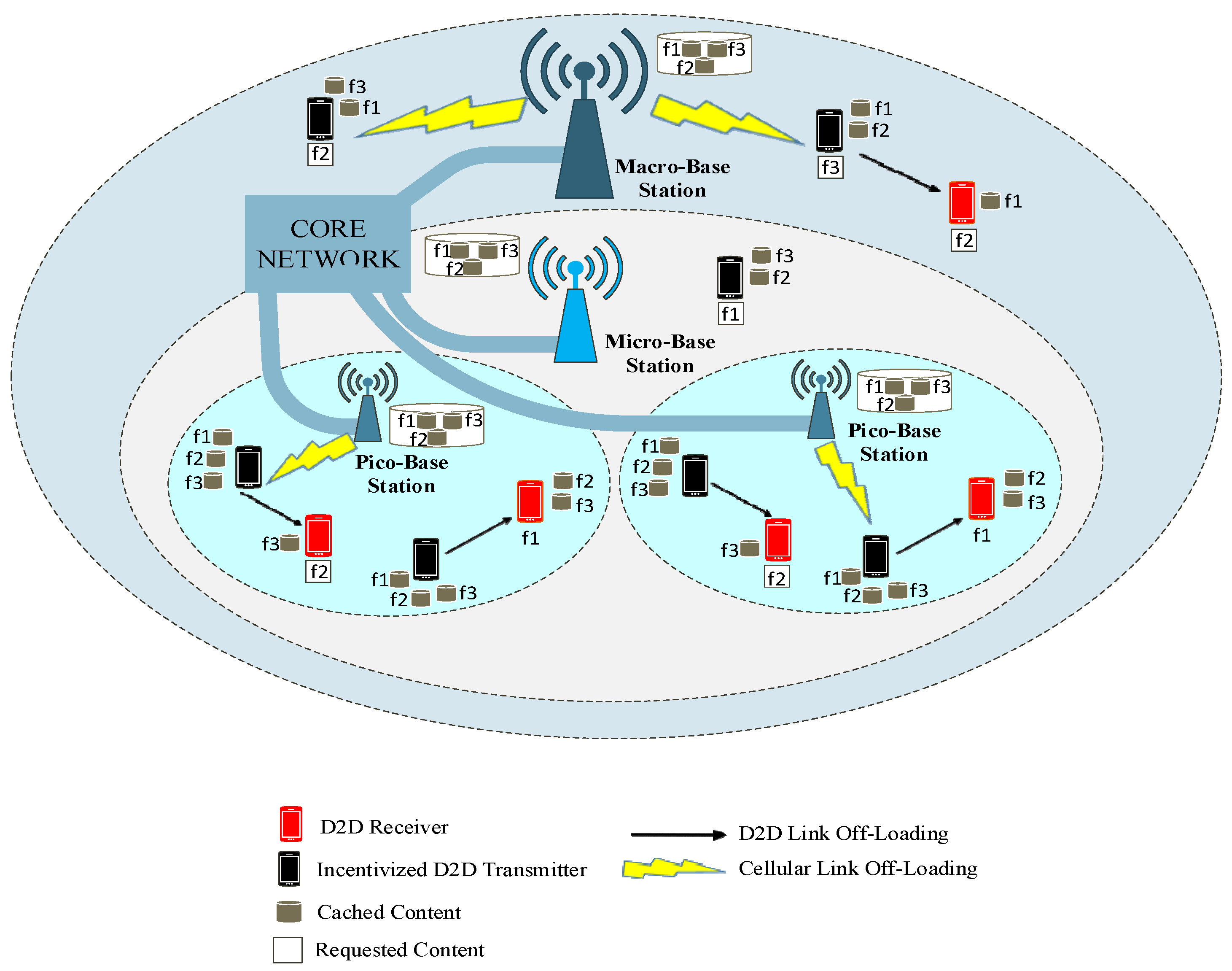
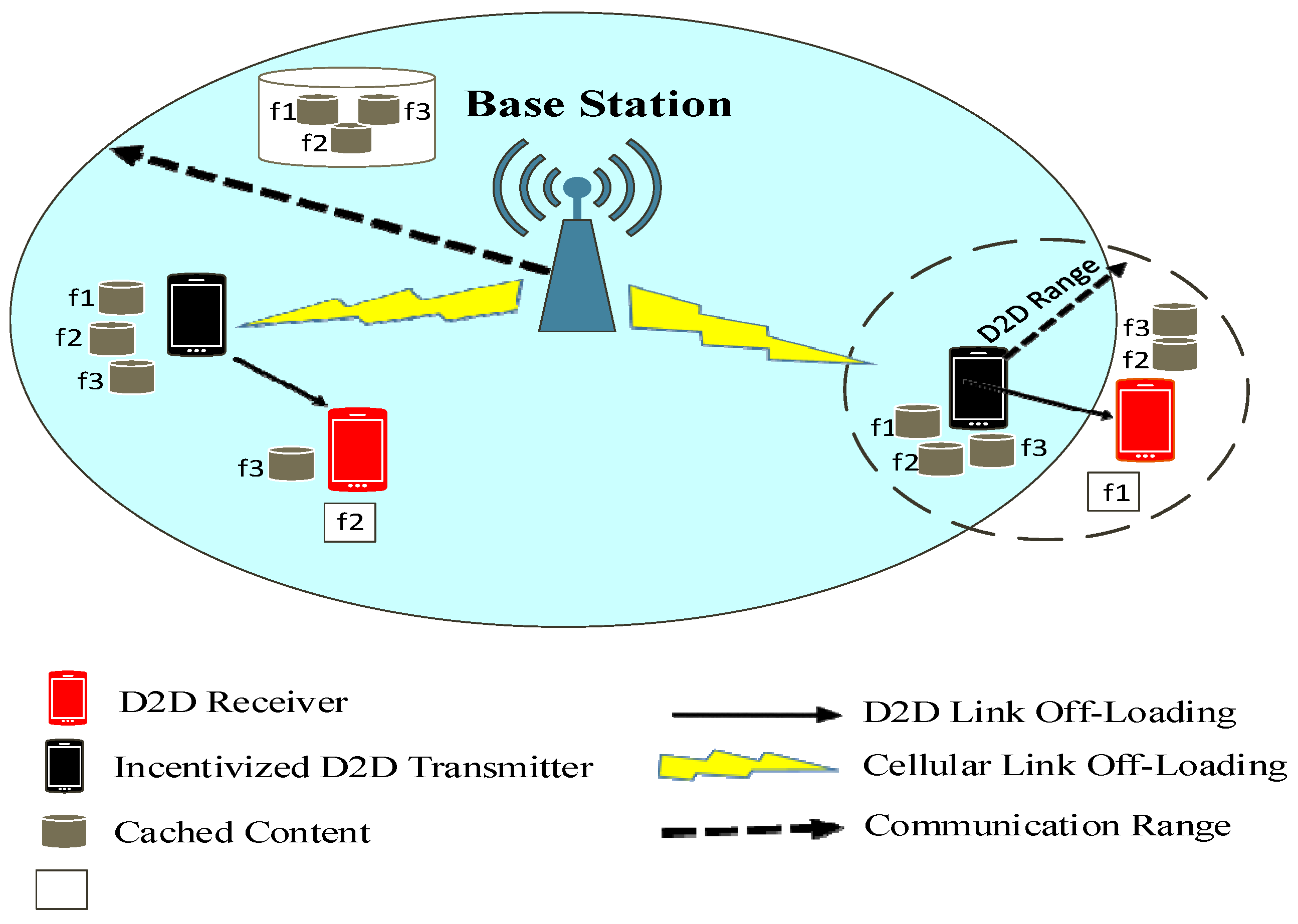
2. System Model
3. Problem Formulation
4. Clustering and Cache Making Strategy
4.1. K-means Clustering and the Concept of Squeezed Cluster
4.2. Support Vector Algorithm for Estimating the Popularity Matrix and Proactive Caching
4.3. Clustered-SVM
| Algorithm 1. Clustered-SVM to Predict Content Popularity and Implement Decision Making for Proactive Caching in Cache-Enabled D2DMCN |
| Require: |
| Ensure: |
| Step 0: Clustering and contents popularity predication |
| 1. Load , |
| 2. Create C clusters based on data set |
| 3. for do |
| 4. Randomly select a set of incentivized D2D transmitters |
| 5. for do |
| 6. determine vicinity of D2D transmitter, |
| 7. for do |
| 8. if |
| 9. // |
| 10. Update the D2D receiver in the squeezed cluster |
| 11. end if |
| 12. end for |
| 13. end for |
| 14. end for |
| 15. Train SVM using the data set |
| 16. Test and predict 1st day count in |
| 17. Determine the content popularity in each case. |
| 18. Sort the content popularity in descending order in each case |
| Step1: Content caching at incentivized D2D transmitter |
| 19. for |
| 20. Initialize the cache size and caching matrix |
| 21. for do |
| 22. if // is the size of the file to be cached at D2DT |
| 23. |
| 24. |
| 25. Else |
| 26. Break |
| 27. end if |
| 28. Return |
| 29. end for |
| 30. End for |
| Step 2: Content caching at pico BS |
| 31. Repeat 19–30 and replacing subscripts by and return |
| Step 3: Content caching at micro BS |
| 32. Repeat 19–30 and replacing subscripts by and return |
| Step 4: Content caching at macro BS |
| 33. Repeat steps 19–30, and replacing subscripts by and return |
| 34. Return |
| Step 5: Mode selection |
| 35. for do |
| 36. for do |
| 37. if then select D2D mode and |
| 38. Else if , then select pico mode and |
| 39. Else if , then select micro and |
| 40. Else select macro mode and |
| 41. end if |
| 42. end for |
| 43. end for |
| Step 6: For Cache hit ratio |
| 44. Optimize Equation (1) |
| 45. Return |
5. Hungarian Algorithm for Content Delivery
| Algorithm 2. Hungarian Algorithm to Perform Content Delivery Decision Making and Optimizaion of Reward of the System |
| 1. Definition: |
| 2. data set for distance between ID2D transmitters and D2D receiver |
| 3. data set for channel gains of link between ID2D transmitters and D2D receivers |
| 4. data set for distance between multi-tier BSs and D2D receivers |
| 5. data set for channel gains of multi-tier BSs and D2D receivers Weight coefficients |
| 6. Require: |
| 7. Ensure: |
| 8. Load |
| 9. Set values of |
| 10. for // , we have pico BS, |
| 11. for do |
| 12. for do |
| 13. Using to Compute |
| 14. Using in (7), (11), (13) and (16) to Compute |
| 15. end for |
| 16. end for |
| 17. end for |
| 18. for do |
| 19. for do |
| 20. Find common D2DRs set among squeezed clusters and MCN |
| 21. end for |
| 22. end for |
| 23. for = // for general transmitters |
| 24. for do |
| 25. Calculate the reward using formula (24) |
| 26. Use Hungarian algorithm maximize the reward of the system |
| 27. end for |
| 28. end for |
| 29. return |
6. Performance Evaluation
6.1. Simulation Setup
6.2. Numerical Results and Discussion
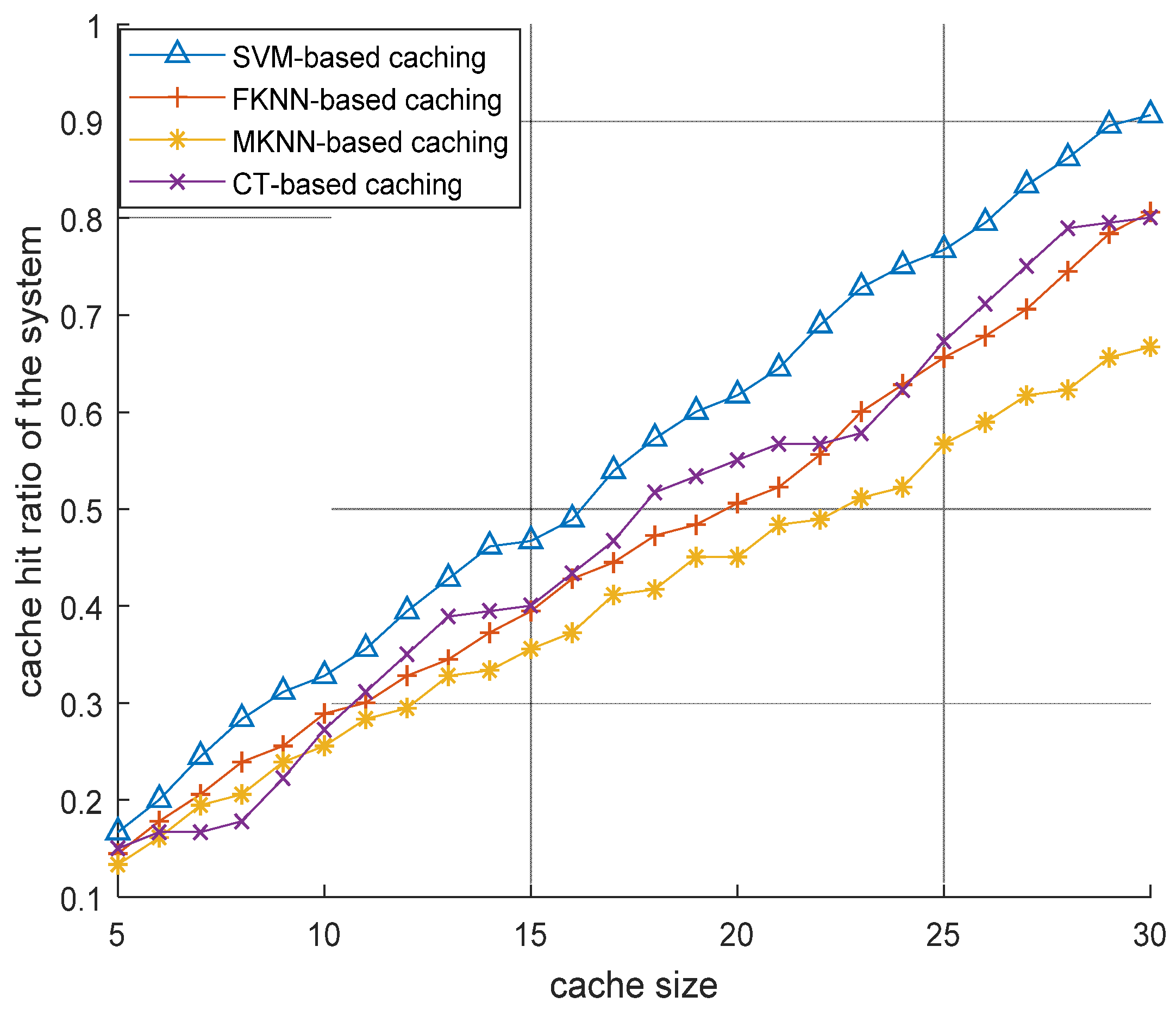
6.2.1. Performance Evaluation of Content Caching Based on Different Learning Algorithms for D2DMCN
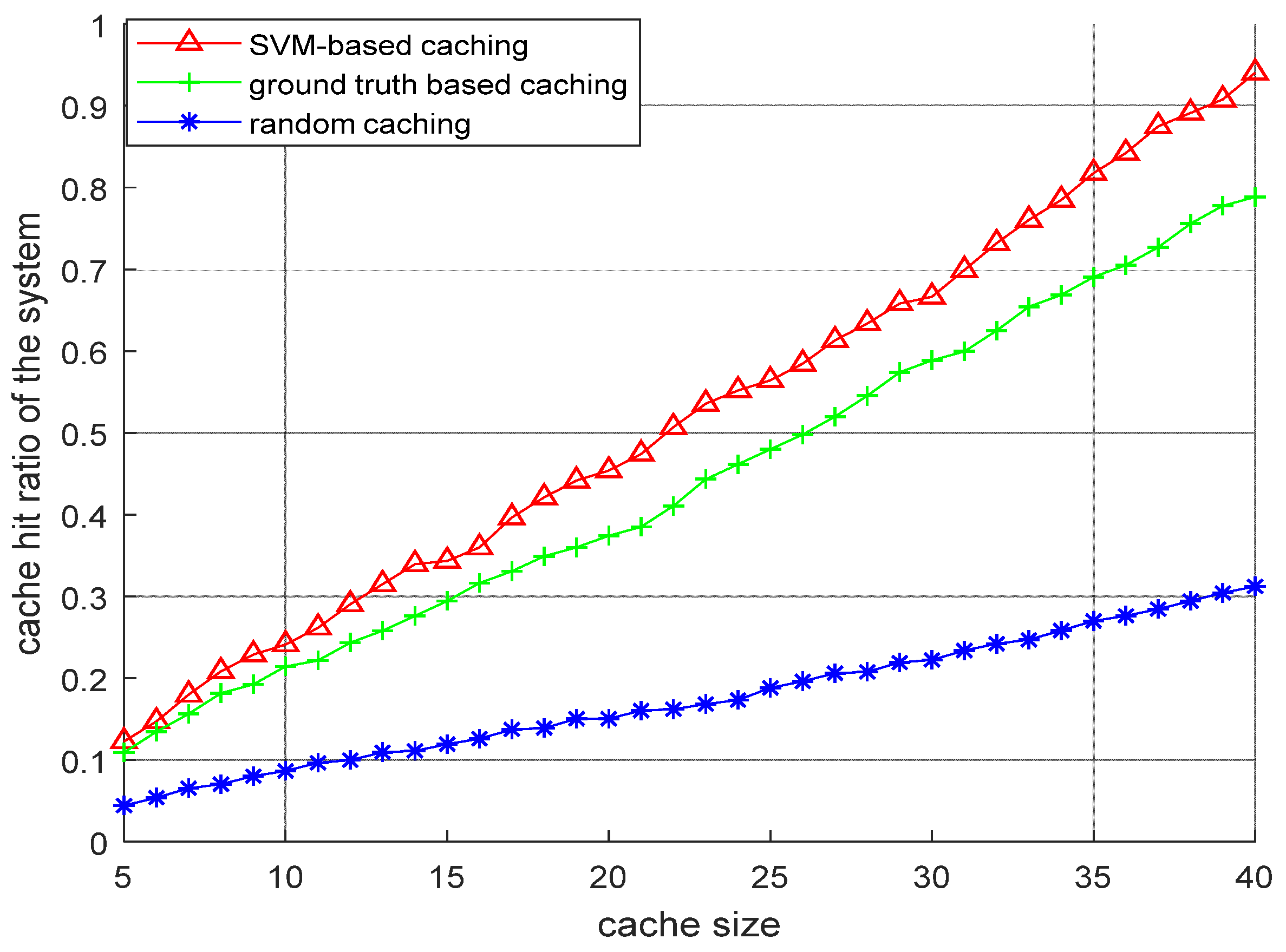
6.2.2. Performance Comparison of Different Proactive Content Caching Techniques for D2DMCN
- Ground truth content caching method
- Random content caching method
- SVM-based content caching method
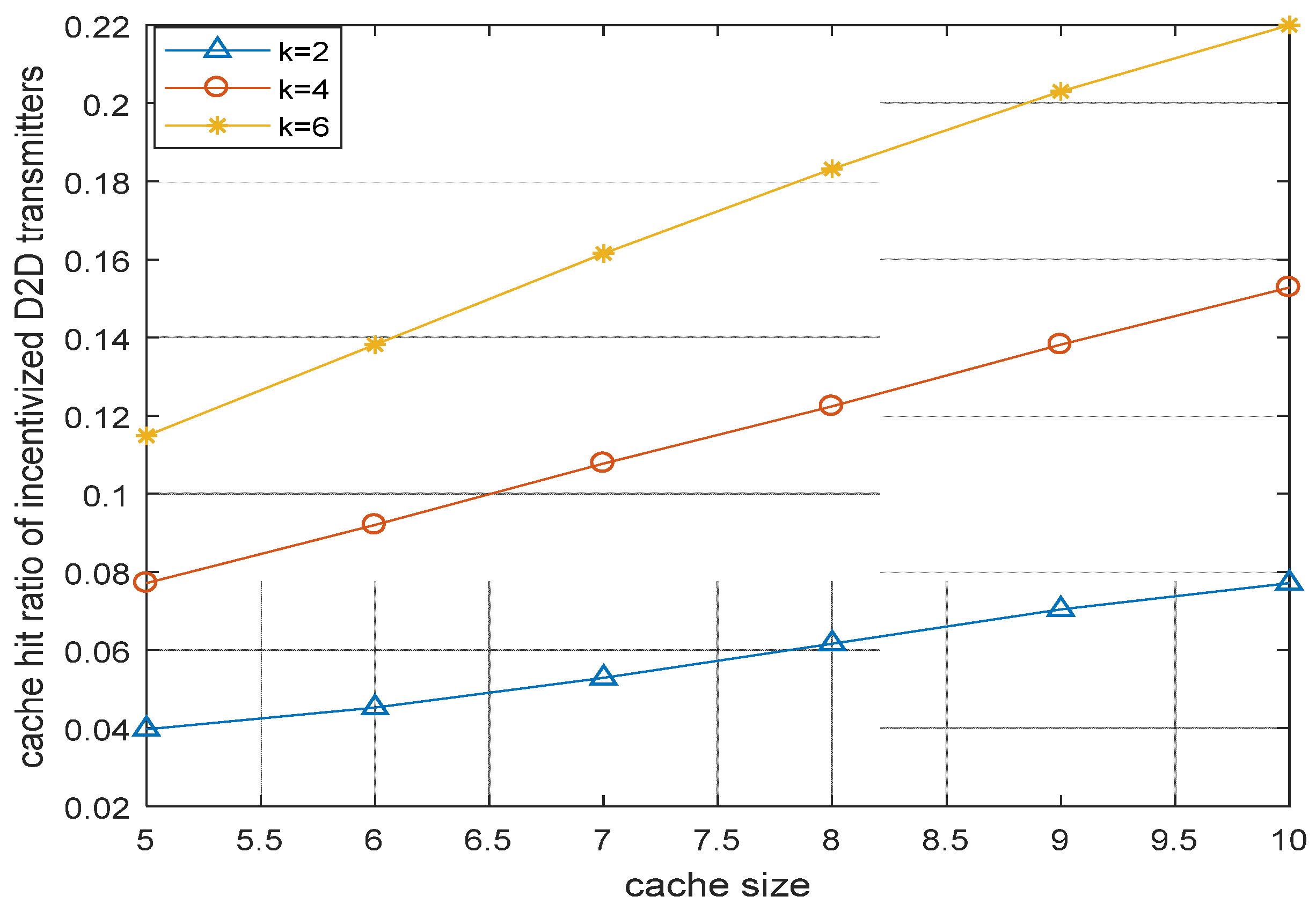
6.2.3. Improvement in the Cache Hit Ratio Due to Inclusion of ID2DTs in MCN
6.2.4. Content Caching at D2D Transmitters
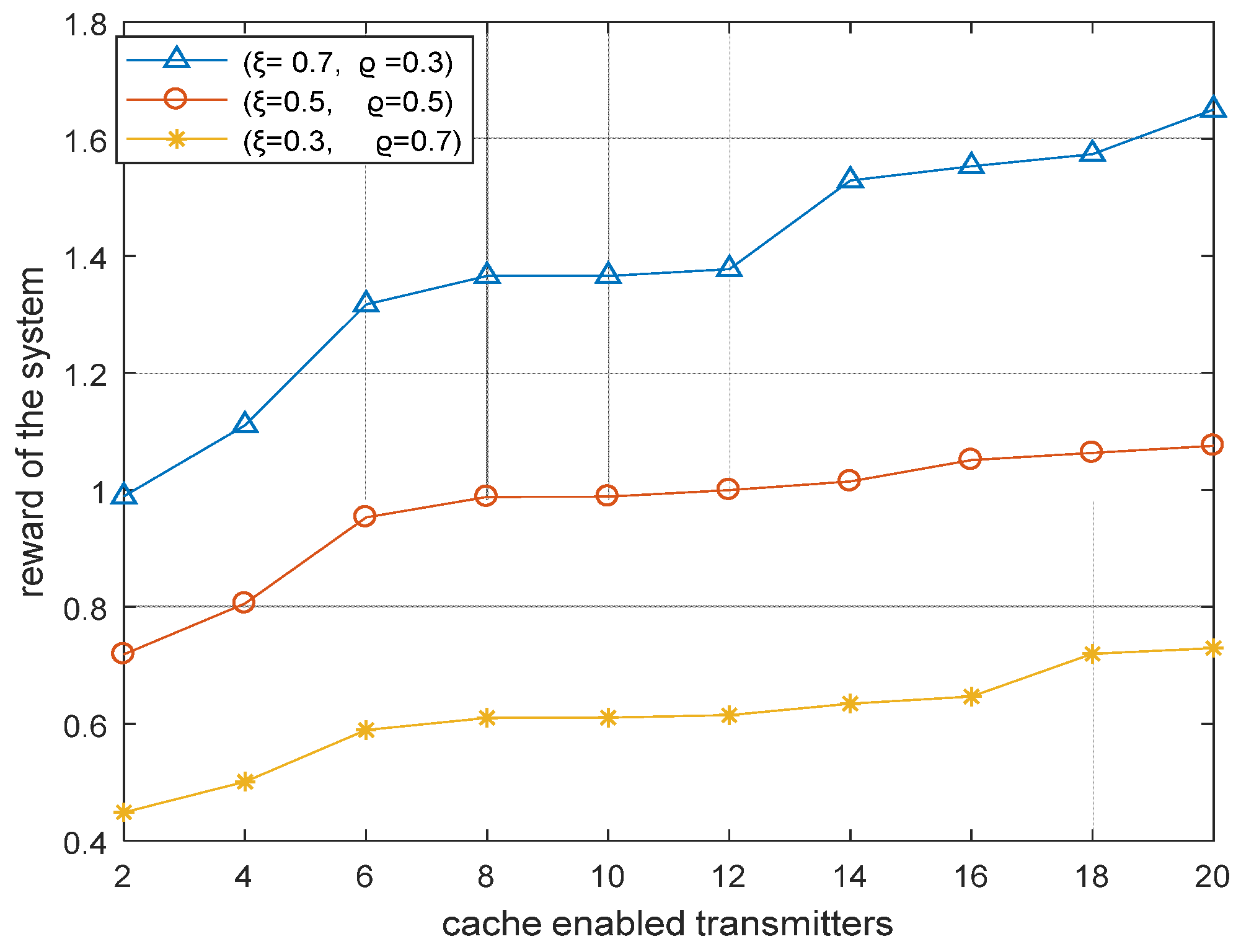
6.2.5. Impact of Varying Weight Coefficient on the Reward of the System
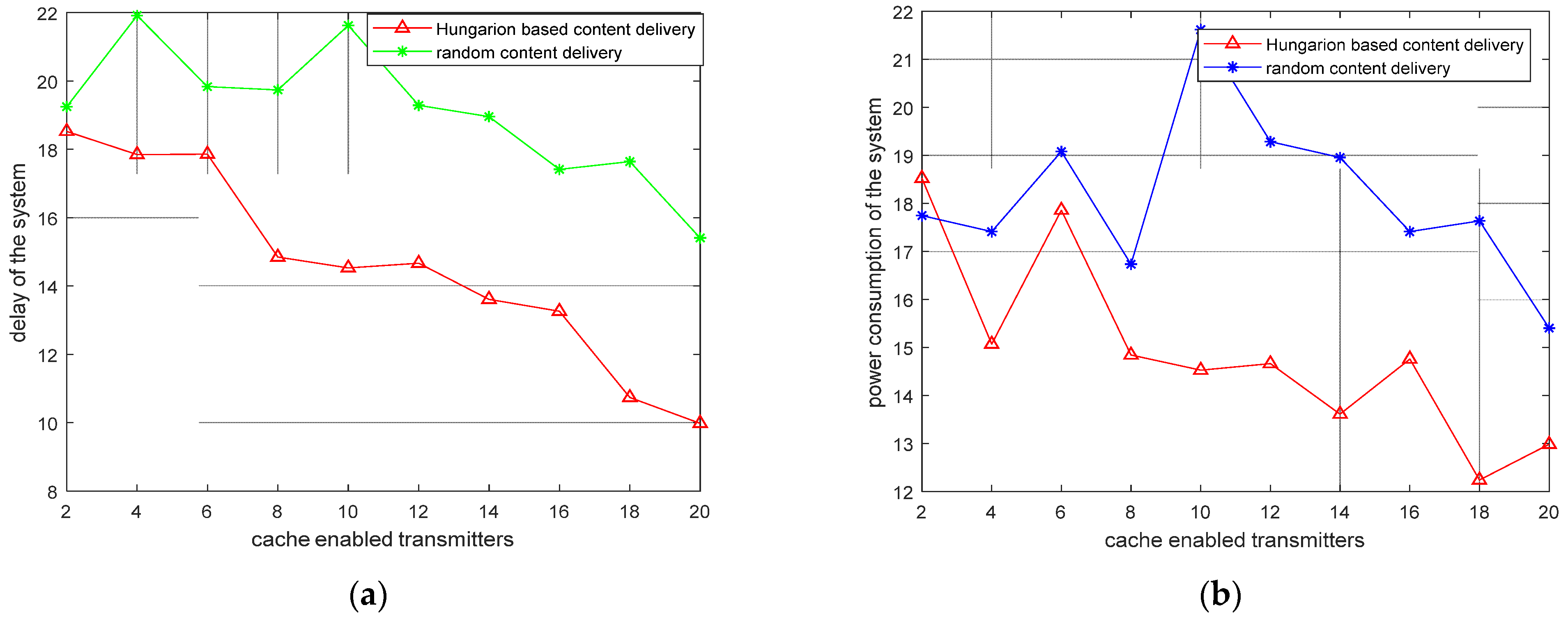
6.2.6. Performance Comparison for the Content Delay and Power Consumption
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Liu, A.; Lau, V.K.N.; Caire, G. Cache-induced hierarchical cooperation in wireless device-to-device caching networks. IEEE Trans. Inf. Theory 2018, 64, 4629–4652. [Google Scholar] [CrossRef] [Green Version]
- Jameel, F.; Hamid, Z.; Jabeen, F.; Zeadally, S.; Javed, M.A. A survey of device-to-device communications: Research issues and challenges. IEEE Commun. Surv. Tutor. 2018, 20, 2133–2168. [Google Scholar] [CrossRef]
- Chen, B.; Yang, C. Caching policy optimization for D2D communications by learning user preference. In Proceedings of the 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 4–7 June 2017; pp. 1–6. [Google Scholar]
- Shen, G.; Pei, L.; Zhiwen, P.; Nan, L.; Xiaohu, Y. Machine learning based small cell cache strategy for ultra dense networks. In Proceedings of the 2017 9th International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, 11–13 October 2017; pp. 1–6. [Google Scholar]
- Ahmad, F.; Ahmad, A.; Hussain, I.; Uthansakul, P.; Khan, S. Cooperation Based Proactive Caching in Multi-Tier Cellular Networks. Appl. Sci. 2020, 10, 6145. [Google Scholar] [CrossRef]
- Li, L.; Zhao, G.; Blum, R.S. A survey of caching techniques in cellular networks: Research issues and challenges in content placement and delivery strategies. IEEE Commun. Surv. Tutor. 2018, 20, 1710–1732. [Google Scholar] [CrossRef]
- Jiang, W.; Feng, G.; Qin, S.; Yum, T.S.P. Efficient D2D Content Caching Using Multi-Agent Reinforcement Learning. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018. [Google Scholar]
- Ullah, I.; Hussain, I.; Singh, M. Exploiting Grasshopper and Cuckoo Search Bio-Inspired Optimization Algorithms for Industrial Energy Management System: Smart Industries. Electronics 2020, 9, 105. [Google Scholar] [CrossRef] [Green Version]
- Lee, M.C.; Molisch, A.F. Individual Preference Aware Caching Policy Design for Energy-Efficient Wireless D2D Communications. In Proceedings of the GLOBECOM 2017—IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Ullah, H.; Khan, M.; Hussain, I.; Ullah, I.; Uthansakul, P.; Khan, N. An Optimal Energy Management System for University Campus Using the Hybrid Firefly Lion Algorithm (FLA). Energies 2021, 14, 6028. [Google Scholar] [CrossRef]
- Ji, M.; Caire, G.; Molisch, A.F. Wireless device-to-device caching networks: Basic principles and system performance. IEEE J. Sel. Areas Commun. 2015, 34, 176–189. [Google Scholar] [CrossRef] [Green Version]
- Chen, Z.; Pappas, N.; Kountouris, M. Probabilistic caching in wireless D2D networks: Cache hit optimal versus throughput optimal. IEEE Commun. Lett. 2016, 21, 584–587. [Google Scholar] [CrossRef] [Green Version]
- Zhao, N.; Liu, X.; Chen, Y.; Zhang, S.; Li, Z.; Chen, B.; Alouini, M.-S. Caching D2D connections in small-cell networks. IEEE Trans. Veh. Technol. 2018, 67, 12326–12338. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Pan, E.; Song, L.; Saad, W.; Dawy, Z.; Han, Z. Social network aware device-to-device communication in wireless networks. IEEE Trans. Wirel. Commun. 2015, 14, 177–190. [Google Scholar] [CrossRef]
- Zhang, N.; Zheng, K.; Tao, M. Using grouped linear prediction and accelerated reinforcement learning for online content caching. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Jiang, Y.; Ma, M.; Bennis, M.; Zheng, F.C.; You, X. User preference learning-based edge caching for fog radio access network. IEEE Trans. Commun. 2019, 67, 1268–1283. [Google Scholar] [CrossRef] [Green Version]
- Fan, H.; Zhang, T.; Loo, J.; Liu, D. Caching deployment algorithm based on user preference in device-to-device networks. In Proceedings of the 2017 IEEE Global Communications Conference (GLOBECOM), Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Wang, Y.; Ding, M.; Chen, Z.; Luo, L. Caching placement with recommendation systems for cache-enabled mobile social networks. IEEE Commun. Lett. 2017, 21, 2266–2269. [Google Scholar] [CrossRef]
- Ullah, I.; Hussain, I.; Rehman, K.; Wróblewski, P.; Lewicki, W.; Kavin, B.P. Exploiting the Moth–Flame Optimization Algorithm for Optimal Load Management of the University Campus: A Viable Approach in the Academia Sector. Energies 2022, 15, 3741. [Google Scholar] [CrossRef]
- Chen, Z.; Kountouris, M. D2D caching vs. small cell caching: Where to cache content in a wireless network? In Proceedings of the IEEE International Workshop on Signal Processing Advances in Wireless Communications, Edinburgh, UK, 3–6 July 2016; pp. 1–6. [Google Scholar]
- Hussain, I.; Ullah, I.; Ali, W.; Muhammad, G.; Ali, Z. Exploiting lion optimization algorithm for sustainable energy management system in industrial applications. Sustain. Energy Technol. Assess. 2022, 52, 102237. [Google Scholar] [CrossRef]
- Golrezaei, N.; Shanmugam, K.; Dimakis, A.G.; Molisch, A.F.; Caire, G. FemtoCaching: Wireless video content delivery through distributed caching helpers. In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 1107–1115. [Google Scholar]
- Bastug, E.; Bennis, M.; Debbah, M. Living on the edge: The role of proactive caching in 5G wireless networks. IEEE Commun. Mag. 2014, 52, 82–89. [Google Scholar] [CrossRef] [Green Version]
- Yang, C.; Yao, Y.; Chen, Z.; Xia, B. Analysis on cache-enabled wireless heterogeneous networks. IEEE Trans. Wirel. Commun. 2016, 15, 131–145. [Google Scholar] [CrossRef] [Green Version]
- Hu, L.; Qian, Y.; Chen, M.; Hossain, M.S.; Muhammad, G. Proactive Cache-based Location Privacy Preserving for Vehicle Networks. IEEE Wirel. Commun. 2018, 25, 77–83. [Google Scholar] [CrossRef]
- Shahjehan, W.; Hussain, I.; Amin, K.; Ali, I.; Riaz, A.; Uthansakul, P. Hepta-Band Antenna for 5G Applications. Wirel. Pers. Commun. 2022, 1–24. [Google Scholar] [CrossRef]
- Tao, M.; Chen, E.; Zhou, H.; Yu, W. Content-centric sparse multicast beamforming for cache-enabled cloud RAN. IEEE Trans. Wirel. Commun. 2016, 15, 6118–6131. [Google Scholar] [CrossRef] [Green Version]
- Liu, A.; Lau, V.K.N. Exploiting base station caching in MIMO cellular networks: Opportunistic cooperation for video streaming. IEEE Trans. Signal Process. 2014, 63, 57–69. [Google Scholar] [CrossRef]
- Li, X.; Wang, X.; Li, K.; Chi, H.; Leung, V.C.M. Resource allocation for content delivery in cache-enabled OFDMA small cell networks. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (IEEE VTC-Fall), Sydney, Australia, 24–27 September 2017; pp. 1–6. [Google Scholar]
- Ullah, I.; Hussain, I.; Uthansakul, P.; Riaz, M.; Khan, M.N.; Lloret, J. Exploiting Multi-Verse Optimization and Sine-Cosine Algorithms for Energy Management in Smart Cities. Appl. Sci. 2020, 10, 2095. [Google Scholar] [CrossRef] [Green Version]
- Malak, D.; Al-Shalash, M.; Andrews, J.G. Optimizing content caching to maximize the density of successful receptions in device-todevice networking. IEEE Trans. Commun. 2016, 64, 4365–4380. [Google Scholar]
- Li, L.; Xu, Y.; Yin, J.; Liang, W.; Li, X.; Chen, W.; Han, Z. Deep Reinforcement Learning Approaches for Content Caching in Cache-Enabled D2D Networks. IEEE Internet Things J. 2020, 7, 544–557. [Google Scholar] [CrossRef]
- Li, Q.; Wen, Z.; He, B. Adaptive Kernel Value Caching for SVM Training. IEEE Trans. Neural Netw. Learn. Syst. (TNNLS) 2019, 31, 2376–2386. [Google Scholar] [CrossRef] [Green Version]
- Goian, H.S.; Al-Jarrah, O.Y.; Muhaidat, S.; Al-Hammadi, Y.; Yoo, P.; Dianati, M. Popularity-Based Video Caching Techniques for Cache-Enabled Networks: A Survey. IEEE Access J. 2019, 7, 27699–27719. [Google Scholar] [CrossRef]
- Hussain, I.; Samara, G.; Ullah, I.; Khan, N. Encryption for End-User Privacy: A Cyber-Secure Smart Energy Management System. In Proceedings of the 2021 22nd International Arab Conference on Information Technology (ACIT), Muscat, Oman, 21–23 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Hussain, I.; Ullah, M.; Ullah, I.; Bibi, A.; Naeem, M.; Singh, M.; Singh, D. Optimizing Energy Consumption in the Home Energy Management System via a Bio-Inspired Dragonfly Algorithm and the Genetic Algorithm. Electronics 2020, 9, 406. [Google Scholar] [CrossRef]
- Boujelbene, S.Z.; Mezghani, D.B.A.; Ellouze, N. Improving SVM by modifying kernel functions for speaker identification task. Int. J. Digit. Content Technol. Appl. 2010, 4, 100–105. [Google Scholar]
- Min, R.; Bonner, A.; Zhang, Z. Modifying kernels using label information improves SVM classification performance. In Proceedings of the 6th International Conference on Machine Learning and Applications (ICMLA 2007), Cincinnati, OH, USA, 13–15 December 2007; pp. 13–18. [Google Scholar]
- Nizam, F.; bin Roslee, M.; Yusoff, Z.; Anuar, K.; Alzoubi, K.H.; Elgamati, M.A.A.; Billah, M.J. Resource Allocation Algorithm for D2D Communication in Cellular Networks Based on Hungarian Algorithm. In Proceedings of the 2019 IEEE 14th Malaysia International Conference on Communication (MICC), Selangor, Malaysia, 2–4 December 2019. [Google Scholar]
- Khan, A.A.; Adve, R.S.; Yu, W. Optimizing Downlink Resource Allocation in Multiuser MIMO Networks via Fractional Programming and the Hungarian Algorithm. IEEE Trans. Wirel. Commun. 2020, 19, 5162–5175. [Google Scholar] [CrossRef]
- Buzzi, S.; D’Andrea, C.; Fresia, M.; Zhang, Y.P.; Feng, S. Pilot Assignment in Cell-Free Massive MIMO based on the Hungarian Algorithm. IEEE Wirel. Commun. Lett. 2020, 10, 34–37. [Google Scholar] [CrossRef]
- Jiang, W.; Feng, G.; Qin, S. Optimal Cooperative Content Caching and Delivery Policy for Heterogeneous Cellular Networks. IEEE Trans. Mob. Comput. 2017, 16, 1382–1393. [Google Scholar] [CrossRef]
- Altaheri, H.; Muhammad, G.; Alsulaiman, M.; Amin, S.U.; Altuwaijri, G.A.; Abdul, W.; Bencherif, M.A.; Faisal, M. Deep Learning Techniques for Classification of Electroencephalogram (EEG) Motor Imagery (MI) Signals: A Review. Neural Comput. Appl. 2021. [Google Scholar] [CrossRef]
- Muhammad, G.; Alshehri, F.; Karray, F.; El Saddik, A.; Alsulaiman, M.; Falk, T.H. A comprehensive survey on multimodal medical signals fusion for smart healthcare systems. Inf. Fusion 2021, 76, 355–375. [Google Scholar] [CrossRef]
- Muhammad, G.; Alqahtani, S.; Alelaiwi, A. Pandemic Management for Diseases Similar to COVID-19 Using Deep Learning and 5G Communications. IEEE Netw. 2021, 35, 21–26. [Google Scholar] [CrossRef]
- Ramachandran, V.; Ramalakshmi, R.; Kavin, B.P.; Hussain, I.; Almaliki, A.H.; Almaliki, A.A.; Elnaggar, A.Y.; Hussein, E.E. Exploiting IoT and Its Enabled Technologies for Irrigation Needs in Agriculture. Water 2022, 14, 719. [Google Scholar] [CrossRef]
- Baştuğ, E.; Bennis, M.; Zeydan, E.; Kader, M.A.; Karatepe, I.A.; Er, A.S.; Debbah, M. Big Data Meets Telcos: A Proactive Caching Perspective. J. Commun. Netw. 2015, 17, 549–557. [Google Scholar] [CrossRef] [Green Version]
- Liu, J.; Bai, B.; Zhang, J.; Letaief, K.B. Content Caching at the Wireless Network Edge: A Distributed Algorithm via Belief Propagation. In Proceedings of the IEEE international Conference on Communication 2016, Kuala Lumpur, Malaysia, 22–27 May 2016. [Google Scholar]
- Tsai, K.C.; Wang, L.; Han, Z. Mobile Social Media Networks Caching with Convolutional Neural Network. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops (WCNCW): Workshop on Intelligent Computing and Caching at the Network Edge 2018, Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Prabakaran, S.; Ramar, R.; Hussain, I.; Kavin, B.P.; Alshamrani, S.S.; AlGhamdi, A.S.; Alshehri, A. Predicting Attack Pattern via Machine Learning by Exploiting Stateful Firewall as Virtual Network Function in an SDN Network. Sensors 2022, 22, 709. [Google Scholar] [CrossRef]
- Zaman, S.; Khan, L.U.; Hussain, I.; Mihet-Popa, L. Fast Computation of Highly Oscillatory ODE Problems: Applications in High-Frequency Communication Circuits. Symmetry 2022, 14, 115. [Google Scholar] [CrossRef]
- Ullah, W.; Hussain, I.; Shehzadi, I.; Rahman, Z.; Uthansakul, P. Tracking a Decentralized Linear Trajectory in an Intermittent Observation Environment. Sensors 2020, 20, 2127. [Google Scholar] [CrossRef] [Green Version]
- Zaman, S.; Hussain, I.; Singh, D. Fast Computation of Integrals with Fourier-Type Oscillator Involving Stationary Point. Mathematics 2019, 7, 1160. [Google Scholar] [CrossRef] [Green Version]


| Parameters | Descriptions |
|---|---|
| [42] | proximity of the ID2DT |
| path loss coefficient for a link between pico BS p and D2DR j | |
| path loss coefficient for a link between micro BS m and D2DR j | |
| path loss coefficient for a link between macro BS M and D2DR j | |
| distance between pico BS p and D2DR j | |
| distance between micro BS m and D2DR j | |
| Parameters | Values/Types |
|---|---|
| Total number of D2D users | 200 |
| Radius of macrocell | 800 m |
| Radius of microcell | 300 m |
| Radius of picocell | 150 m |
| Total number of clusters | 2 |
| Path loss exponent | 4 |
| Thermal noise | 1 |
| Weight coefficient A and B | 0 to 1 |
| Size of each file | 1 |
| Software | MATLAB |
| Total number of contents | 2000 |
| System bandwidth | 900 MHz |
| Minimum sensitivity of D2D receiver | −70 dBm |
| Bandwidth per channel | 200 kHZ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmad, F.; Ahmad, A.; Hussain, I.; Muhammad, G.; Uddin, Z.; AlQahtani, S.A. Proactive Caching in D2D Assisted Multitier Cellular Network. Sensors 2022, 22, 5078. https://doi.org/10.3390/s22145078
Ahmad F, Ahmad A, Hussain I, Muhammad G, Uddin Z, AlQahtani SA. Proactive Caching in D2D Assisted Multitier Cellular Network. Sensors. 2022; 22(14):5078. https://doi.org/10.3390/s22145078
Chicago/Turabian StyleAhmad, Fawad, Ayaz Ahmad, Irshad Hussain, Ghulam Muhammad, Zahoor Uddin, and Salman A. AlQahtani. 2022. "Proactive Caching in D2D Assisted Multitier Cellular Network" Sensors 22, no. 14: 5078. https://doi.org/10.3390/s22145078
APA StyleAhmad, F., Ahmad, A., Hussain, I., Muhammad, G., Uddin, Z., & AlQahtani, S. A. (2022). Proactive Caching in D2D Assisted Multitier Cellular Network. Sensors, 22(14), 5078. https://doi.org/10.3390/s22145078








