Abstract
Ensuring the reliability of data gathering from every connected device is an essential issue for promoting the advancement of the next paradigm shift, i.e., Industry 4.0. Blockchain technology is becoming recognized as an advanced tool. However, data collaboration using blockchain has not progressed sufficiently among companies in the industrial supply chain (SC) that handle sensitive data, such as those related to product quality, etc. There are two reasons why data utilization is not sufficiently advanced in the industrial SC. The first is that manufacturing information is top secret. Blockchain mechanisms, such as Bitcoin, which uses PKI, require plaintext to be shared between companies to verify the identity of the company that sent the data. Another is that the merits of data collaboration between companies have not been materialized. To solve these problems, this paper proposes a business-to-business collaboration system using homomorphic encryption and blockchain techniques. Using the proposed system, each company can exchange encrypted confidential information and utilize the data for its own business. In a trial, an equipment manufacturer was able to identify the quality change caused by a decrease in equipment performance as a cryptographic value from blockchain and to identify the change one month earlier without knowing the quality value.
1. Introduction
In order to promote Society 5.0, the Industrial Internet of Things, Industry 4.0, and so forth, it is important to connect and share data so that all IoT devices and all members can trust them. Blockchain (BC) technology is attracting attention as an advanced tool. Blockchain is a digital ledger for record-keeping over peer-to-peer (P2P) networks [1,2]. It is decentralized and dispersed in nature with tamper-resistant and tamper-evident features [3,4,5]. Each peer stores a copy of the blockchain and verifies the validity of the stored data, such that no peers can tamper with the data. For example, in the blockchain, all money in and out is stored in the block as historical data and connected in chronological order. The hash value of the previous block is included in the next block. Even if a peer participating in the network falsifies the data of a certain block, the hash value of the block will change, so it will not match the hash of the next block connected to it. Therefore, the fraud of the peer can be immediately revealed.
The concept of blockchain technology was derived from Bitcoin cryptocurrency, and then it spread to the financial field. This is still the main field in which blockchain technology is used [6,7]. Currently, in addition to the financial field, the blockchain technique is used in smart homes [8], smart cities [9,10], smart agriculture [11,12], smart power grids [13], smart transportation and automotives [14], smart healthcare [15,16], IoT networks [17,18], and security privacy [19]. In the smart-manufacturing field, much research has been conducted related to the certificate of origin, procurement, production, inspection, logistics, and sales [20,21,22,23,24,25,26,27]. In the business-to-business (B2B) manufacturing industry, the demands for high-quality product development and plan optimization can be met by sharing manufacturing data among companies in the supply chain (SC) [28,29,30,31]. To meet these demands, manufacturers need an environment where the data shared by the company cannot be tampered with. Additionally, each company’s manufacturing and inspection process data must be connected throughout the SC, from materials to products. BC technology is one an effective approach for building such an environment. However, production or inspection data collaboration using BC has not progressed sufficiently among companies in the industrial SC. One of the main reasons is that production and inspection data are highly confidential and therefore difficult to disclose to other companies (e.g., product quality data, equipment data, and order-shipping data) [32].
There are movements to improve data infrastructure beyond companies, mainly in Europe [33,34]. Attention is also focused on efforts to optimize the entire SC by constructing twin digital platforms. However, no matter how much infrastructure and how many platforms are built, in terms of B2B manufacturing data collaboration, it will be difficult to freely link highly confidential data unless two companies can agree on a contract. With data collaboration based on a contract between two companies, it is difficult to build an ecosystem in which data is widely and freely linked among companies. Even if a consortium were to be formed, as long as there is competition among companies, companies would not be able to safely disclose their data, which is the source of their revenue.
Regarding this issue, refs. [35,36] proposed methods for privacy protection for the IoT by combining encryption with BC or IOTA. Ref. [37] proposed an algorithm of the privacy-preserving OLPA for big data analysis. However, there is another major reason why data collaboration between companies is not progressing; the merits of data collaboration in a concrete manufacturing scene are not readily apparent, and its implementation with respect to both business and technology is difficult. It is important to design the benefits of being able to put data into a BC while ensuring a company’s competitive advantage. The authors of [35,36,37] have not been able to propose a protocol in consideration of the utilization in business after encryption. In order to achieve B2B collaboration between companies in the industrial SC, it is important to have a protocol and a system that can both “protect data” and “utilize data in the manufacturing process”.
This paper proposes a B2B collaboration system using homomorphic encryption (HE) and BC techniques. Using the proposed system, each company in the industrial SC can exchange confidential information, such as quality data, in an encrypted manner and utilize the data in their own manufacturing. In addition, this paper shows a scenario, system architecture, and protocol for upstream companies to grasp changes in the manufacturing quality of downstream companies. In this scenario, this paper evaluates the merit of concrete data collaboration in actual business using the proposed system.
The paper is structured as follows: Section 2 describes the blockchain issue in data linkage, a scenario for realizing B2B collaboration in the production process in the SC, and the issue of numerical comparison while maintaining the encryption required in the scenario. Section 3 proposes a secure comparison protocol and a B2B collaboration system to resolve these issues. Section 4 demonstrates the usefulness of the proposed system and protocol in an actual business scenario, and Section 5 evaluates the safety of the proposed system.
2. Preliminaries
2.1. The Problem of BC Utilization and the Secure Approach in B2B Collaboration in the SC
In the B2B manufacturing industry, it is difficult for each company to disclose confidential information regarding its manufacturing know-how, even if it is a company that transacts in the SC. Blockchain mechanisms such as Bitcoin, which uses public key cryptography (PKI), require that plaintext be sent to identify a company (Figure 1a). Therefore, blockchains are not widely used for collaboration between companies in the manufacturing SC [32].
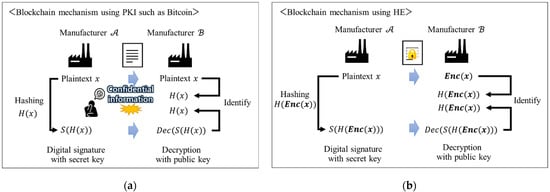
Figure 1.
The issue of BC utilization and the secure approach in B2B collaboration. (a) Issue of BC utilization; (b) Secure approach in B2B collaboration.
Regarding this issue, this paper proposes a secure B2B collaboration system in the SC that enables open data transfer and business coordination by combining blockchain technology and homomorphic encryption. In 1978, Ronald Rivest et al. suggested a proposal on the concept of homomorphic encryption [38]. Later, Craig Gentry proposed fully homomorphic encryption that computes an arbitrary number of additions and multiplications to encrypted data [39]. This scheme enables the programs for any desirable functionality, such as homomorphic property, to run on encrypted data and produce an encryption of the result. A partial homomorphic encryption exhibits either an additive or multiplicative homomorphism, but not both. In addition, the efficiency of some partial homomorphic encryption schemes is high enough for practical applications [40].
In a secure collaboration system that uses partial HE and blockchain techniques, each company in the SC can exchange confidential information using encrypted data and utilize it for their own business needs (Figure 1b). In this paper, as shown in Figure 1b, the encryption of plaintext using HE is denoted as .
2.2. A B2B Collaboration Scenario on the Industrial SC
Let us consider a scenario in which manufactures a product of quality with equipment and delivers to . uses as a material to manufacture a product of quality with equipment . At this time, wants to optimize the production plan by identifying the level of quality that can be produced when the product is put into the equipment of . Although wants a stable supply of high-quality materials from , it does not want to disclose its own manufacturing information because it is confidential. For this scenario, in this research, sends to using HE. Therefore, can calculate its relationship and compatibility with without knowing the specific product name , quality , and equipment , and it can formulate the optimum production plan for .
In the field of chemistry, products are manufactured by reacting materials. Therefore, the impact on product quality caused by the physical properties of materials and the compatibility of equipment is important. The utilization of the proposed scenario in real businesses can be expected.
In regard to the above scenario, this paper focuses on quality data. wants to catch the change of at time and , and if there is a big change, will identify its own manufacturing factors, leading to optimum production. Therefore, in order to realize the proposed scenario, it is important to have a comparison protocol for the values of and so as to encrypt them. In the protocol, a function to put quality data into the blockchain and a function to get them from the blockchain are also important for implementing the proposed scenario.
The final system for the B2B collaboration is shown in Figure 2. In this final system, manufacturing companies can chain data without disclosing their quality data, while also guaranteeing their identities using blockchain. Even if the encrypted quality data were to be tampered with by an attacker, the hash value of the encrypted quality data would not match the value after decrypting the signature. Therefore, tampering could be detected immediately. In addition, traceability in the SC is possible by including the lot number of each company’s products in the encryption. Under such a secure data linkage, will be able to identify changes in the quality data of downstream companies in a timely manner and to utilize that information in its own manufacturing.
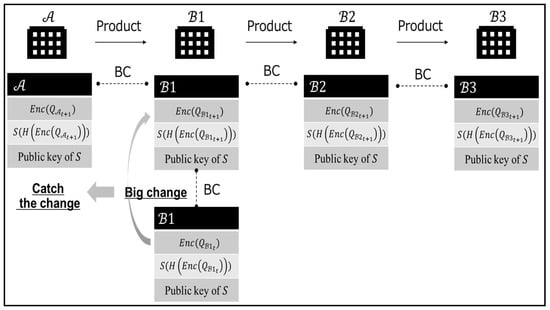
Figure 2.
The final system of the B2B collaboration.
2.3. Conventional Comparison Protocol Using HE and Issues with B2B Collaboration
In 2016, Wu et al. proposed a comparison protocol based on Paillier cryptography, a kind of additive homomorphic encryption [41]. In the protocol, the client and server have the values and , respectively. Neither party learns anything else about the other party’s input.
In the protocol, suppose the binary representations of and are (k bits) and (k bits), respectively. Using the following proposition, or is determined.
Proposition 1.
if and only if there exists some index that satisfies Formula (1). if and only if there exists some index that satisfies Formula (2).
Here are the details. The client and server encrypt and with the public key, respectively. The client sends to the server. The server calculates Formula (1) or (2) by substituting and and using plaintext for XOR. The client receives the calculation result, decrypts it with the secret key, and checks for zero. Therefore, the client can determine that or without disclosing the value of to the server.
In the proposed scenario for B2B collaboration, has both and of the quality data, and has and . Therefore, cannot calculate XOR using the above formula, and this conventional protocol is difficult to apply to B2B collaboration in the SC. In addition, in order to realize the proposed scenario in an actual business, it is necessary to consider a system architecture, including business viewpoints and a comparison protocol, according to the architecture.
3. Proposal B2B Collaboration System on the SC
In [42], our previous work showed a secure comparison protocol for B2B collaboration in the SC at ICCE-TW2021. This paper shows the concrete system architecture required to implement the proposed scenario for the actual business. This paper also shows the usefulness of the proposal system by adding the evaluation results in specific business situations.
3.1. System Architecture of the B2B Collaboration
This paper shows the system architecture for implementing the proposed scenario in Figure 3. In a real business, it is necessary to have a servicer that provides value by exchanging data and guaranteeing the service level. In other words, the servicer is the company responsible for realizing the proposed scenario and the solution engineer who builds the data platform business. Therefore, the proposed system has a servicer , as well as the manufacturers and . Each organization has at least one peer and certificate authority (CA) that manages the members of the organization, and the data is put into the blockchain by the orderer. Each peer has a state database that records the state of the data and a chaincode that holds the history of data transfers as a distributed ledger of the blockchain.
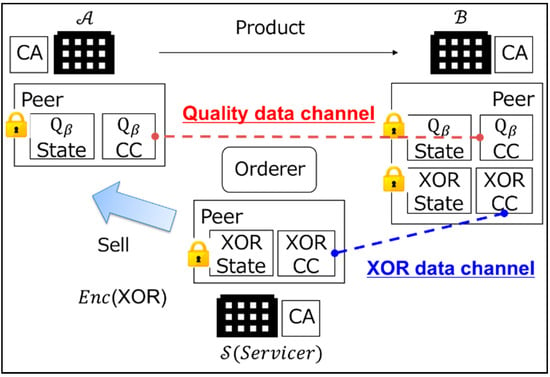
Figure 3.
Proposed B2B collaboration system.
As shown in Figure 3, this paper proposes a multi-channel system architecture that separates the chaincode for the quality data and the XOR data. has both and of the quality data and puts and into the quality chaincode of ( CC). can get and from CC. In the proposed scenario, the XOR data of are essential for the calculation of Formulas (1) and (2). These are important key data, from both a technical and a business perspective. Therefore, in the proposed system architecture, calculates and puts into the XOR chaincode (XOR CC). can get from XOR CC and sell to as a servicer. The reason that the servicer does not have the quality data is that the servicer and may be in a competitive relationship. The servicer is only positioned to provide the key XOR data. Only , which has a transaction with in the SC, can grasp the change in quality.
There is another secondary reason for the architecture to have multiple channels with . It is robust access control. If the product of is manufactured from the materials of and , might get the big quality change in the material of from CC as a business opportunity and make an offer to to replace an order for the material of . Even if obtains the private key of by some means, if manages the XOR data and does not sell the data to , cannot calculate Formula (1) or (2) without the XOR data.
3.2. Implementation of the Comparison Protocol to Realize the B2B Collaboration System
This paper proposes an improved secure comparison protocol for implementation in the B2B collaboration system using a variant of Wu’s protocol, which is based on Paillier cryptography. and are the quality data (plaintexts) of at time and , respectively.
In this proposed protocol, , , and are encrypted with Paillier cryptography [43]. In Paillier cryptography, message is encrypted by (3) with integers , , where and are prime numbers of about 3000 bits, is a random number , and . The public key is (). The secret key is ().
Decryption is carried out via the following formula using Carmichael’s theorem: . Here, and a function
Therefore,
- Cryptographic Protocol ofTable 1 shows the cryptographic protocol of . First, binary-expands the quality data and . Additionally, encrypts the bit of , the bit of , and using Formula (3). Then, it puts , , , and the public key into the blockchain, as shown in Figure 3 and Appendix A.
 Table 1. Encryption Protocol of .
Table 1. Encryption Protocol of . - Calculation Protocol ofTable 2 shows the calculation protocol of . gets and saves and the public key from XOR CC, as seen in Figure 3. If there is a request from , uses the public key as a key to identify and sends the to . is a servicer that handles important XOR data in this B2B collaboration system.
 Table 2. Calculation Protocol of .
Table 2. Calculation Protocol of . - Calculation Protocol ofTable 3 shows the calculation protocol of . gets , and the public key from CC, as seen in Figure 3. Additionally, gets from by sending a public key of and , where wants to identify the change. calculates those quality data using Formulas (1) and (2) while keeping them encrypted.
 Table 3. Calculation Protocol of .In the proposed protocol for Step 3, it is necessary to calculate from . This proposed protocol uses Formula (6) from Paillier cryptography to calculate .
Table 3. Calculation Protocol of .In the proposed protocol for Step 3, it is necessary to calculate from . This proposed protocol uses Formula (6) from Paillier cryptography to calculate . - Decryption Protocol ofTable 4 shows the decryption protocol of . Using the secret key and Formula (5), decrypts and searches for the bit, where .
 Table 4. Decryption Protocol of .
Table 4. Decryption Protocol of . - Comparison Protocol ofTable 5 shows the comparison protocol of . Finally, receives or knows that did not occur. If receives while using Formula (1), then can be determined. If receives while using Formula (2), then can be determined. Here, is the first different bit when comparing and from the most significant bit. Therefore, using this proposed protocol, can grasp or and the scale of the difference between and without knowing the numbers that and represent; that is, can confirm the change in quality data in the time series.
 Table 5. Comparison Protocol of .
Table 5. Comparison Protocol of .
3.3. System Configuration
The proposed system was constructed as shown in Figure 4. A company was set up as one organization in a docker container on the AWS EC2. A blockchain network was built using Hyperledger Fabric, which utilizes the Amazon Managed Blockchain (AMB) service. Hyperledger Fabric was adopted to build a private blockchain for companies in the SC. In order to efficiently calculate multi-length arithmetic, the encryption, decryption, and calculation of the data were programmed by C++. APIs for both putting data into and getting data from the blockchain were developed by Golang.
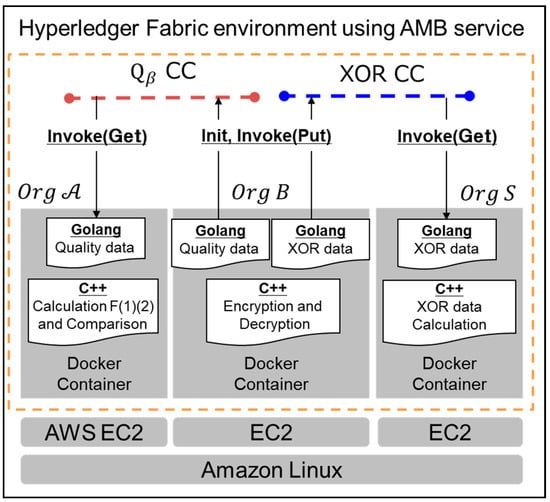
Figure 4.
Configuration of proposed the B2B collaboration system.
4. Evaluation Result of the Concrete Data-Collaboration’s Merits
Finally, this paper considers the usefulness of the proposed system and protocol. In the actual case in Figure 5, manufacturer provided dry dehumidifiers to the dry products of manufacturer . One day, a complaint was made about the decreased performance of the dehumidifiers from , and it turned out that the friction-reducing film, which should have been attached to the dehumidifying rotors, was not attached. It took four months from delivery for the performance reduction of be noticed. By applying the proposed protocol, was able share product moisture data, which are confidential manufacturing data, with in an encrypted manner. This paper evaluates whether was able to notice the quality change at an early stage in the actual business setting.
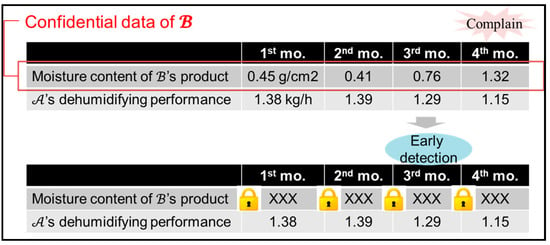
Figure 5.
An actual business example of concrete data collaboration.
Figure 6 shows the result of an experiment where the proposed protocol and system were applied. was able to provide confidential moisture data encrypted as messages 1 and 2. Using the proposed system, was able to detect the decreased performance in the third month by getting 10-times the encrypted moisture data from the quality chaincode and encrypted XOR data from the XOR chaincode so as to observe the changes in quality each month. In Paillier cryptography, message is required, so the quality data are multiplied by 10. As can be seen in Figure 6, does not know the specific numerical value of the quality data. This paper confirms the behavior and usefulness of the proposed system.
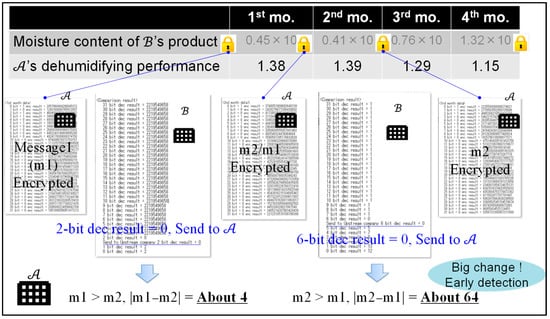
Figure 6.
Evaluating the result of the concrete data collaboration.
5. Safety Evaluation of the Proposed System
This paper does not consider the case where maliciously puts incorrect quality data and to CC in Step 2 of Table 1. The incorrect quality data put by means to disrupt the SC for their own material procurement. Such cases are nonsensical from a business perspective and are not worth considering.
In Paillier cryptography, since does not know () and is masked by in Formula (3), it is difficult to solve the discrete logarithmic problem in the exponential part of Formula (3). Thus, the message cannot be identified [43].
In the proposed comparison protocol of the B2B collaboration system, since ciphertexts are encrypted using random number in Formula (3), cannot identify or by comparing , , and , as can be seen in Figure 6.
In the B2B collaboration system, there is a risk that company , participating in the quality channel, will impersonate . Since participates in the quality channel, can get the public keys. If intercepts ’s , falsifies the encrypted data with Paillier cryptography, and sends it to , will not be able to grasp the change in quality. However, since is also a company in the SC related to ’s products, when it is found that it is impersonating , will receive great punishment. That is, will not be able to trade with any other company. Therefore, it is unlikely that spoofing by a company such as will occur in the proposal system. Even if the encrypted data were to be leaked to a company that does not participate in a blockchain channel, it would not be tampered with unless the public key were leaked.
6. Conclusions
This paper proposed a secure comparison protocol for the sharing and grasping of changes to even highly sensitive data between companies by keeping the data encrypted. By implementing the protocol on a blockchain that connects companies in the industrial SC, this paper also proposed a B2B collaboration system. In a scenario with a business focusing on quality data, which is the most sensitive data in manufacturing, this paper showed that a company can grasp the change in the quality data of their business partner, while keeping the data encrypted, and subsequently feed that change back into its own manufacturing.
By using the proposed system, upstream companies will be able to grasp the quality changes of downstream companies. Combined with data from IoT sensors attached to their equipment, upstream companies will be able to proactively respond to the decreased performance of delivery equipment, which is directly linked to quality. In addition, small- and medium-sized manufacturers are said to lack sales resources, but the proposed system enables them to grasp the quality improvement needs of downstream companies in advance and reflect those needs in their own functional development. Upstream companies, many of which are large companies, do not disclose the quality value to other companies via encryption, and there is no concern that quality data will be tampered with by other companies by BC, so data can be provided with peace of mind. The social implementation of this research will create an ecosystem of collaboration among companies in the industrial SC, which will enable highly efficient manufacturing.
Note that the proposed protocol uses Paillier cryptography, which requires the use of a 6000-bit space for secure encryption and decryption. Investigating speed-up using elliptic cryptography or other methods is the goal for future research.
Author Contributions
Conceptualization, methodology, validation, and formal analysis, H.N.; software, H.N.; writing—original draft preparation, H.N.; writing—review and supervision, Y.N. and Y.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the JSPS KAKENHI Grant-in-Aid for Challenging Research (Pioneering) (20K20484).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
This work was partially supported by the Research Support Program toward Society 5.0 provided by Cypher at Okayama University, Japan. We are grateful to Ryota Miyamoto, who participated in helpful discussions and prototype development.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Figure A1a,b shows the data structure of CC and XOR CC, respectively. Quality data and XOR data are put into the BC with a common lot number and public key to identify when they were put and the production lot data to which they correspond. In Figure A1, “Pubkey_n” is the Paillier cryptography public key. Figure A1 shows an example where is 32 bits. “T1Q_args” and “T2Q_args” are the quality data of times and , respectively. “XOR_args” is the XOR data. The quality data and XOR data are bit-expanded and encrypted, respectively. The public key is updated every time, for a set of and .

Figure A1.
Data structure. (a) Data structure of CC; (b) Data structure of XOR CC.
References
- Satoshi, N. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 21 June 2022).
- Gadekallu, T.R.; Pham, Q.V.; Nguyen, D.C.; Maddikunta, P.K.R.; Deepa, N.; Prabadevi, B.; Pathirana, P.N.; Zhao, J.; Hwang, W.J. Blockchain for edge of things: Applications, opportunities, and challenges. IEEE Internet Things 2021, 9, 964–988. [Google Scholar] [CrossRef]
- Mills, J.; Hu, J.; Min, G. Multi-Task Federated Learning for Personalised Deep Neural Networks in Edge Computing. IEEE Trans. Parallel Distrib. Syst. 2021, 33, 630–641. [Google Scholar] [CrossRef]
- Yu, Z.; Hu, J.; Min, G.; Zhao, Z.; Miao, W.; Hossain, M.S. Mobility-aware proactive edge caching for connected vehicles using federated learning. IEEE Trans. Intell. Transp. Syst. 2020, 22, 5341–5351. [Google Scholar] [CrossRef]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain technology overview. arXiv 2019, arXiv:1906.11078. [Google Scholar]
- KPMG LLP. Blockchain and the Future of Finance: A Potential New World for CFOs—And How to Prepare. Available online: https://assets.kpmg/content/dam/kpmg/ca/pdf/2019/05/blockchain-and-the-future-of-finance.pdf (accessed on 21 June 2022).
- Du, M.; Chen, Q.; Xiao, J.; Yang, H.; Ma, X. Supply Chain Finance Innovation Using Blockchain. IEEE Trans. Eng. Manag. 2020, 67, 1045–1058. [Google Scholar] [CrossRef]
- Alam, M.R.; Reaz, M.B.I.; Ali, M.A.M. A Review of Smart Homes—Past, Present, and Future. IEEE Trans. Syst. Man Cybern. Part C 2012, 42, 1190–1203. [Google Scholar] [CrossRef]
- Batty, M.; Axhausen, K.W.; Giannotti, F.; Pozdnoukhov, A.; Bazzani, A.; Wachowicz, M.; Ouzounis, G.; Portugali, Y. Smart Cities of the Future. Eur. Phys. J. Spec. Top. 2012, 214, 481–518. [Google Scholar] [CrossRef] [Green Version]
- Sun, M.; Zhang, J. Research on the application of block chain big data platform in the construction of new smart city for low carbon emission and green environment. Comput. Commun. 2020, 149, 332–342. [Google Scholar] [CrossRef]
- Dagar, R.; Som, S.; Khatri, S.K. Smart Farming—IoT in Agriculture. In Proceedings of the International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 11–12 July 2018. [Google Scholar]
- Saurabh, S.; Dey, K. Blockchain technology adoption, architecture, and sustainable agri-food supply chains. J. Clean. Prod. 2021, 284, 124731. [Google Scholar] [CrossRef]
- Shahinzadeh, H.; Moradi, J.; Gharehpetian, G.B.; Nafisi, H.; Abedi, M. IoT Architecture for Smart Grids. In Proceedings of the International Conference on Protection and Automation of Power System (IPAPS), Tehran, Iran, 8–9 January 2019. [Google Scholar]
- Menon, V.G.; Jacob, S.; Joseph, S.; Sehdev, P.; Khosravi, M.R.; Turjman, F.A. An iot-enabled intelligent automobile system for smart cities. Internet Things 2022, 18, 100213. [Google Scholar] [CrossRef]
- Baker, S.B.; Xiang, W.; Atkinson, I. Internet of things for smart healthcare: Technologies, challenges, and opportunities. IEEE Access 2017, 5, 26521–26544. [Google Scholar] [CrossRef]
- Badhotiya, G.K.; Sharma, V.P.; Prakash, S.; Kalluri, V.; Singh, R. Investigation and assessment of blockchain technology adoption in the pharmaceutical supply chain. Mater. Today Proc. 2021, 46, 10776–10780. [Google Scholar] [CrossRef]
- Zheng, J.; Dike, C.; Pancari, S.; Wang, Y.; Giakos, G.C.; Elmannai, W.; Wei, B. An In-Depth Review on Blockchain Simulators for IoT Environments. Future Internet 2022, 14, 182. [Google Scholar] [CrossRef]
- Javed, A.R.; Hassan, M.A.; Shahzad, F.; Ahmed, W.; Singh, S.; Baker, T.; Gadekallu, T.R. Integration of Blockchain Technology and Federated Learning in Vehicular (IoT) Networks: A Comprehensive Survey. Sensors 2022, 22, 4394. [Google Scholar] [CrossRef] [PubMed]
- Mohanta, B.K.; Jena, D.; Panda, S.S.; Sobhanayak, S. Blockchain technology: A survey on applications and security privacy Challenges. Internet Things 2019, 8, 100107. [Google Scholar] [CrossRef]
- Santhi, A.R.; Muthuswamy, P. Influence of Blockchain Technology in Manufacturing Supply Chain and Logistics. Logistics 2022, 6, 6010015. [Google Scholar]
- Akaba, T.I.; Norta, A.; Udokwu, C.; Draheim, D. A Framework for the Adoption of Blockchain-Based e-Procurement Systems in the Public Sector: A Case Study of Nigeria. In Responsible Design, Implementation and Use of Information and Communication Technology; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; Volume 12066, pp. 3–14. [Google Scholar] [CrossRef] [Green Version]
- Guo, D.; Ling, S.; Li, H.; Ao, D.; Zhang, T.; Rong, Y.; Huang, G.Q. A framework for personalized production based on digital twin, blockchain and additive manufacturing in the context of Industry 4.0. In Proceedings of the 2020 IEEE 16th International Conference on Automation Science and Engineering (CASE), Hong Kong, China, 20–21 August 2020. [Google Scholar]
- Chen, J.; Xu, S.; Liu, K.; Yao, S.; Luo, X.; Wu, H. Intelligent Transportation Logistics Optimal Warehouse Location Method Based on Internet of Things and Blockchain Technology. Sensors 2022, 22, 1544. [Google Scholar] [CrossRef]
- Wu, L.; Lu, W.; Xue, F. Construction Inspection Information Management with Consortium Blockchain. In Proceedings of the 25th International Symposium on Advancement of Construction Management and Real Estate; Springer: Singapore, 2020; pp. 1397–1406. [Google Scholar] [CrossRef]
- Bellavista, P.; Esposito, C.; Foschini, L.; Giannelli, C.; Mazzocca, N.; Montanari, R. Interoperable Blockchains for Highly-Integrated Supply Chains in Collaborative Manufacturing. Sensors 2021, 21, 4955. [Google Scholar] [CrossRef]
- Tijan, E.; Aksentijevic, S.; Ivanic, K.; Jardas, M. Blockchain Technology Implementation in Logistics. Sustainability 2019, 11, 1185. [Google Scholar] [CrossRef] [Green Version]
- Jæger, B.; Bach, T.; Pedersen, S.A. A Blockchain Application Supporting the Manufacturing Value Chain. In Advances in Production Management Systems. Production Management for the Factory of the Future. IFIP Advances in Information and Communication Technology; Springer: Cham, Switzerland, 2019; Volume 566, pp. 466–473. [Google Scholar] [CrossRef]
- Leunga, S.C.H.; Tsanga, S.O.S.; Nga, W.L.; Wub, Y. A robust optimization model for multi-site production planning problem in an uncertain environment. Eur. J. Oper. Res. 2007, 181, 224–238. [Google Scholar] [CrossRef]
- Tao, F.; Qi, Q.; Liu, A.; Kusiak, A. Data-driven smart manufacturing. J. Manuf. Syst. 2018, 48, 157–169. [Google Scholar] [CrossRef]
- Johnson, J.S.; Friend, S.B.; Lee, H.S. Big Data Facilitation, Utilization, and Monetization: Exploring the 3Vs in a New Product Development Process. J. Prod. Innov. Manag. 2017, 34, 640–658. [Google Scholar] [CrossRef]
- METI. Connected Industries Tokyo Initiative 2017. In Proceedings of the Connected Industries Conference, Tokyo, Japan, 4 October 2017. [Google Scholar]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- The Federal Ministry for Economic Affairs and Climate Action; GAIA-X. Available online: https://www.data-infrastructure.eu/GAIAX/Navigation/EN/Home/home.html (accessed on 13 June 2022).
- IOTA. Available online: https://www.iota.org/ (accessed on 13 June 2022).
- Yan, X.; Wu, Q.; Sun, Y. A Homomorphic Encryption and Privacy Protection Method Based on Blockchain and Edge Computing. Wirel. Commun. Mob. Comput. 2020, 2020, 8832341. [Google Scholar] [CrossRef]
- Nakanishi, R.; Zhang, Y.; Sasabe, M.; Kasahara, S. IOTA-Based Access Control Framework for the Internet of Things. In Proceedings of the Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 27–30 September 2020. [Google Scholar]
- Cuzzocrea, A.; Maio, V.D.; Fadda, E. Experimenting and Assessing a Distributed Privacy-Preserving OLAP over Big Data Framework: Principles, Practice, and Experiences. In Proceedings of the 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020. [Google Scholar] [CrossRef]
- Ronald, R.L.; Adi, S.; Leonard, A. A method for obtaining digital signatures and public key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Gentry, C. A Fully Homomorphic Encryption Scheme. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 2009. [Google Scholar]
- Fen, B. Cryptanalysis of a provable secure additive and multiplicative privacy homomorphism. In Proceedings of the International Workshop on Coding and Cryptography (WCC), Versailles, France, 24–28 March 2003. [Google Scholar]
- Wu, D.J.; Feng, T.; Naehrig, M.; Lauter, K. Privately evaluating decision trees and random forests. Proceeding Priv. Enhancing Technol. (PoPETs) 2016, 2016, 335–355. [Google Scholar] [CrossRef] [Green Version]
- Nasu, H.; Kodera, Y.; Nogami, Y. Secure Comparison Protocol for Promoting Business to Business Collaboration on the Blockchain. In Proceedings of the International Conference on Consumer Electronics-Taiwan (ICCE-TW), Penghu, Taiwan, 15–17 September 2021. [Google Scholar]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Advances in Cryptology-EUROCRYPT ’99; Springer: Berlin/Heidelberg, Germany, 1999. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).