A Business-to-Business Collaboration System That Promotes Data Utilization While Encrypting Information on the Blockchain
Abstract
:1. Introduction
2. Preliminaries
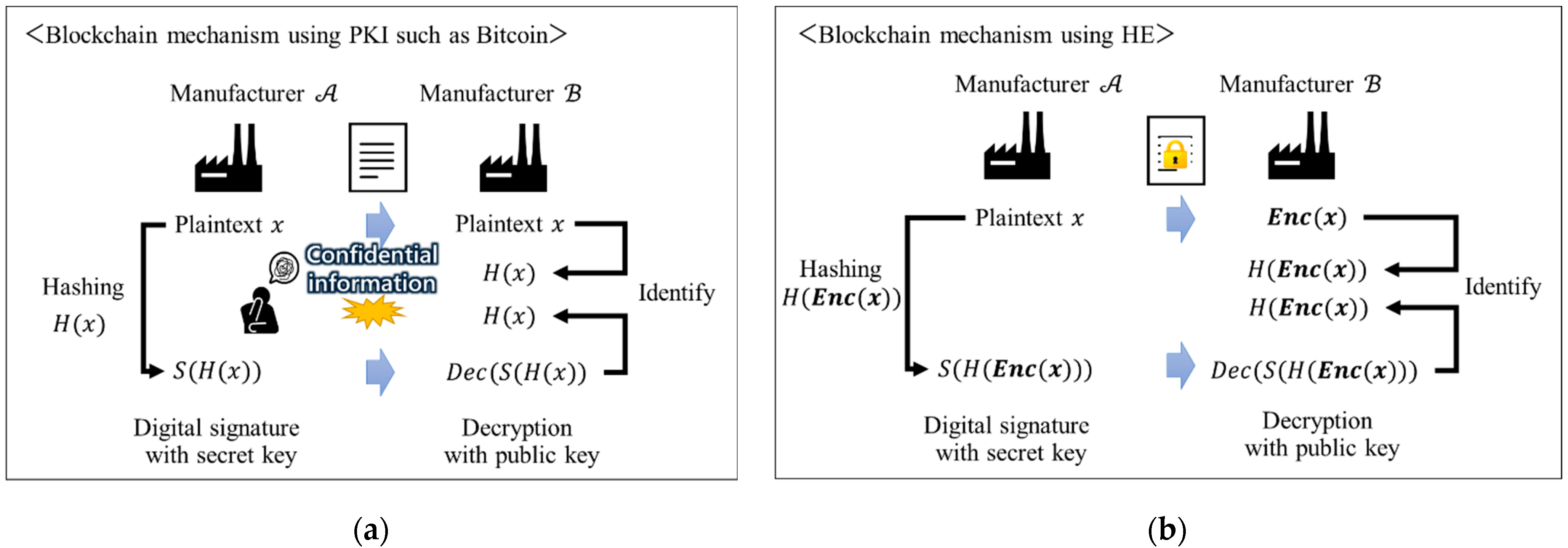
2.1. The Problem of BC Utilization and the Secure Approach in B2B Collaboration in the SC
2.2. A B2B Collaboration Scenario on the Industrial SC
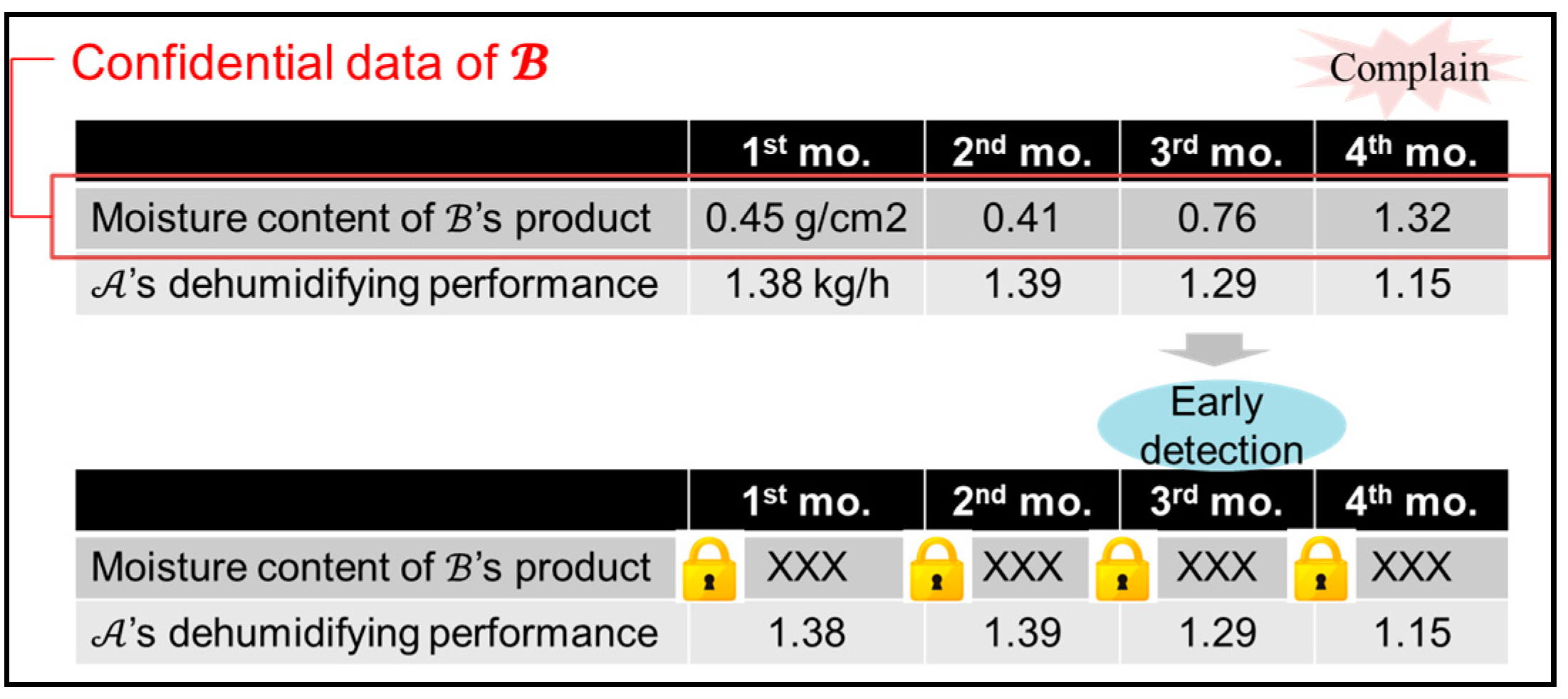
2.3. Conventional Comparison Protocol Using HE and Issues with B2B Collaboration
3. Proposal B2B Collaboration System on the SC
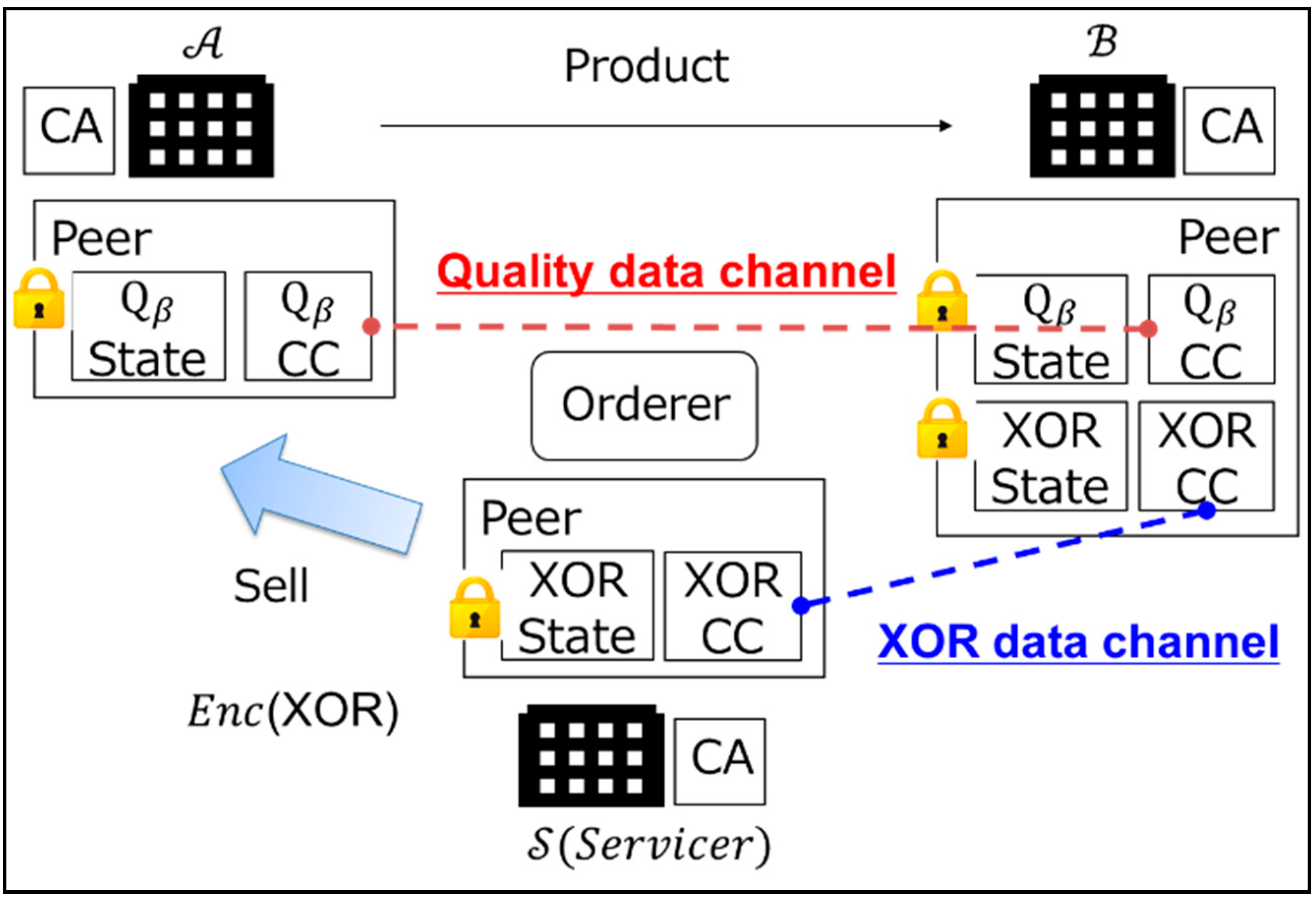
3.1. System Architecture of the B2B Collaboration
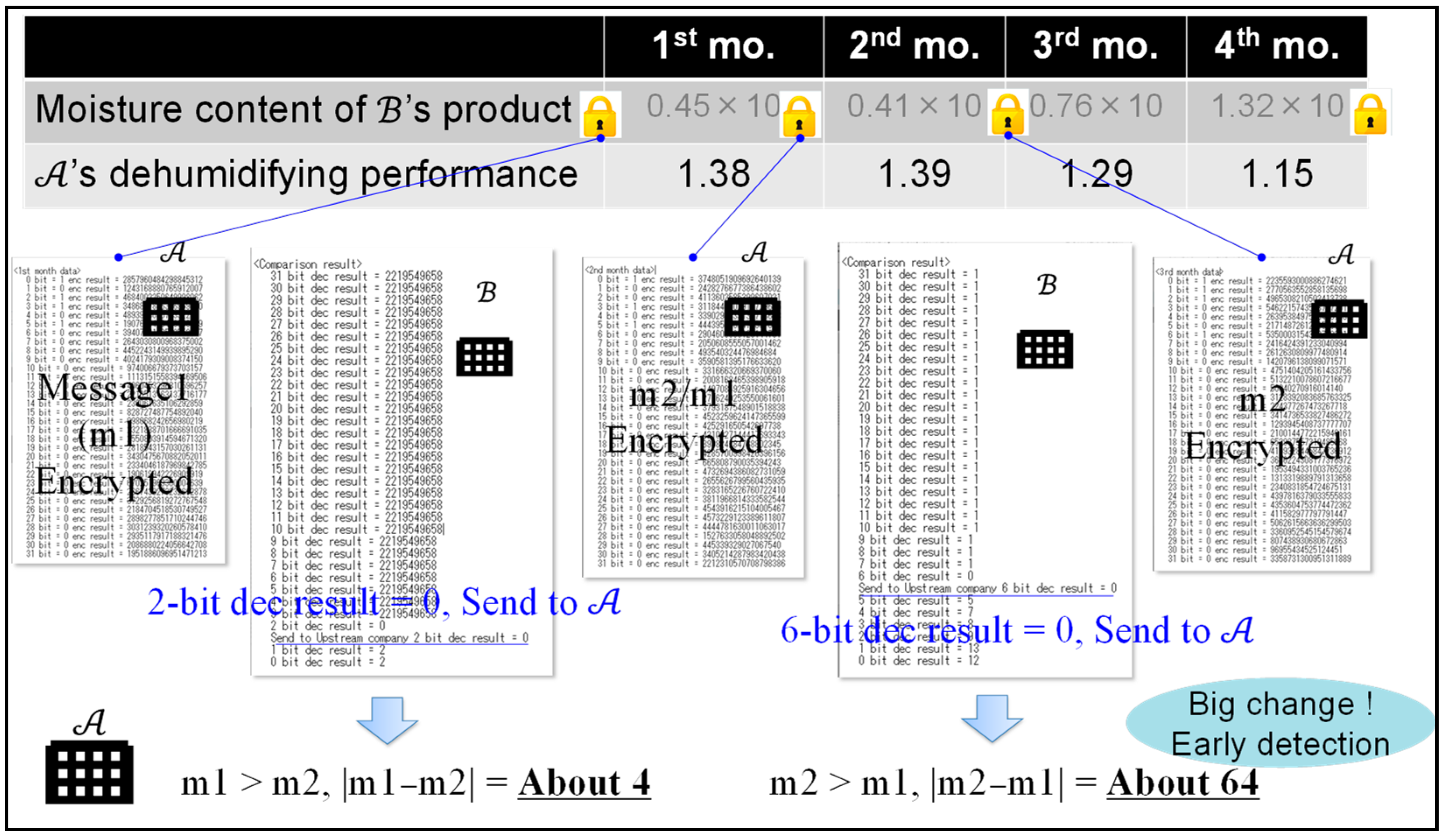
3.2. Implementation of the Comparison Protocol to Realize the B2B Collaboration System
- Cryptographic Protocol ofTable 1 shows the cryptographic protocol of . First, binary-expands the quality data and . Additionally, encrypts the bit of , the bit of , and using Formula (3). Then, it puts , , , and the public key into the blockchain, as shown in Figure 3 and Appendix A.
- Calculation Protocol of
- Calculation Protocol ofTable 3 shows the calculation protocol of . gets , and the public key from CC, as seen in Figure 3. Additionally, gets from by sending a public key of and , where wants to identify the change. calculates those quality data using Formulas (1) and (2) while keeping them encrypted.In the proposed protocol for Step 3, it is necessary to calculate from . This proposed protocol uses Formula (6) from Paillier cryptography to calculate .
- Decryption Protocol ofTable 4 shows the decryption protocol of . Using the secret key and Formula (5), decrypts and searches for the bit, where .
- Comparison Protocol ofTable 5 shows the comparison protocol of . Finally, receives or knows that did not occur. If receives while using Formula (1), then can be determined. If receives while using Formula (2), then can be determined. Here, is the first different bit when comparing and from the most significant bit. Therefore, using this proposed protocol, can grasp or and the scale of the difference between and without knowing the numbers that and represent; that is, can confirm the change in quality data in the time series.
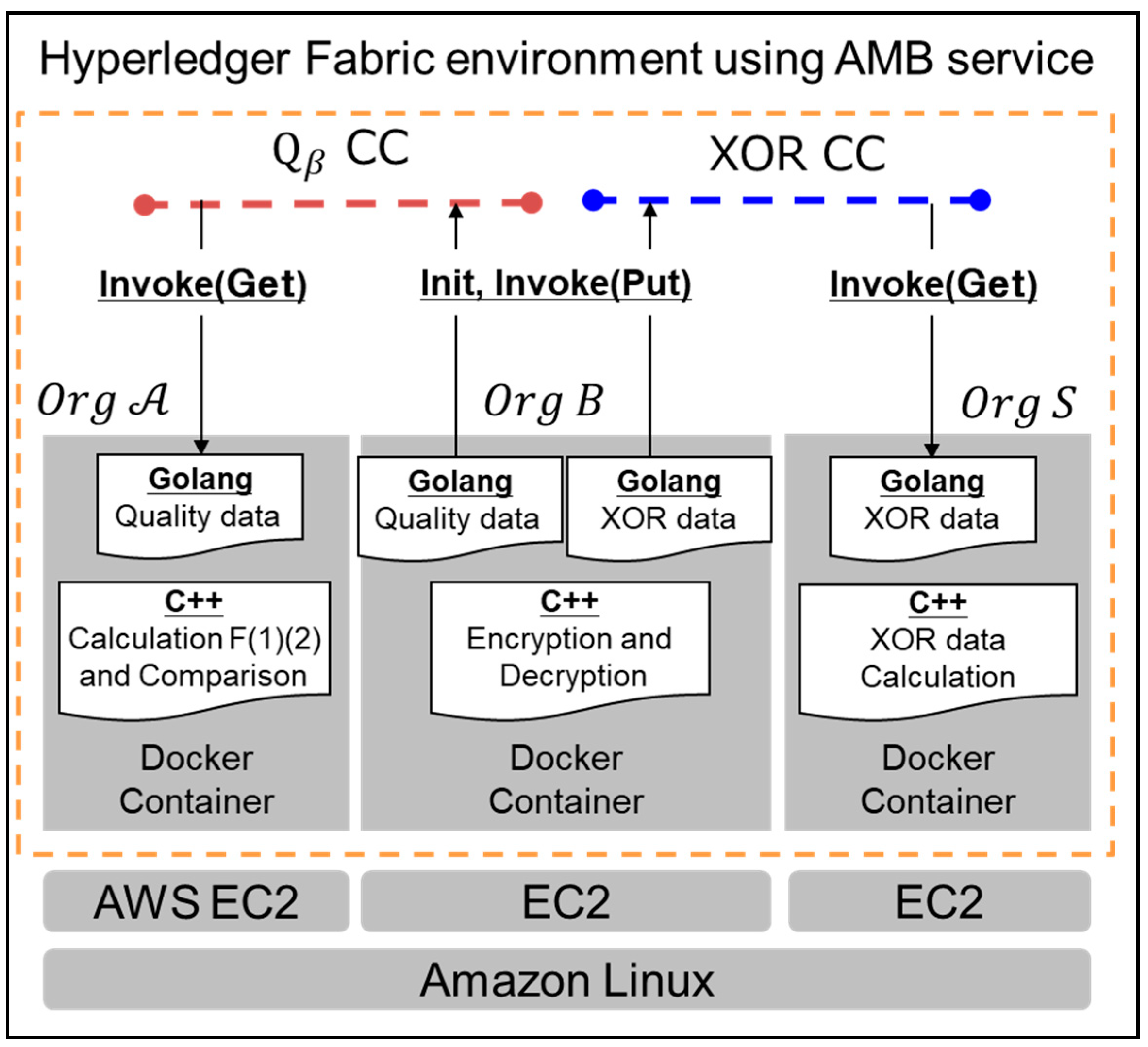
3.3. System Configuration
4. Evaluation Result of the Concrete Data-Collaboration’s Merits
5. Safety Evaluation of the Proposed System
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
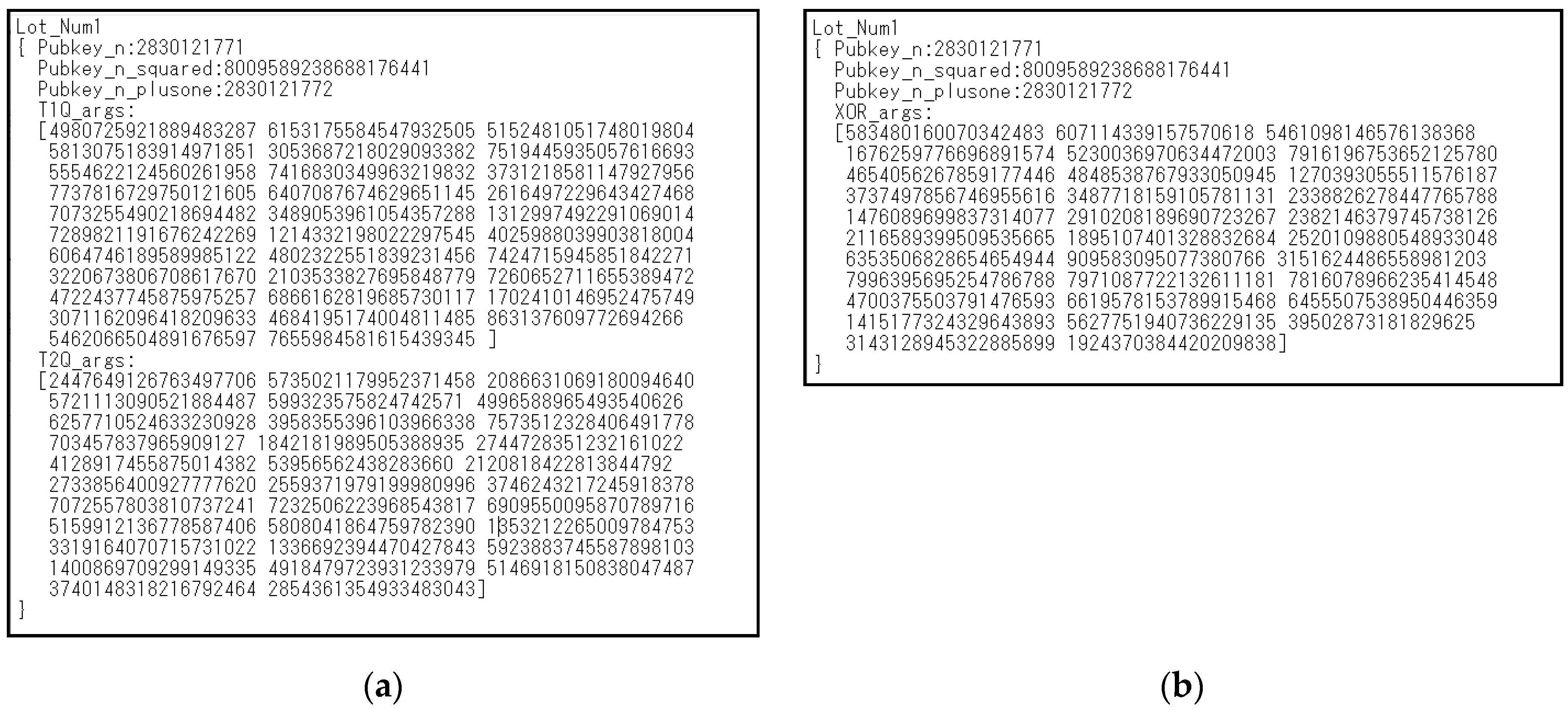
Appendix A
References
- Satoshi, N. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 21 June 2022).
- Gadekallu, T.R.; Pham, Q.V.; Nguyen, D.C.; Maddikunta, P.K.R.; Deepa, N.; Prabadevi, B.; Pathirana, P.N.; Zhao, J.; Hwang, W.J. Blockchain for edge of things: Applications, opportunities, and challenges. IEEE Internet Things 2021, 9, 964–988. [Google Scholar] [CrossRef]
- Mills, J.; Hu, J.; Min, G. Multi-Task Federated Learning for Personalised Deep Neural Networks in Edge Computing. IEEE Trans. Parallel Distrib. Syst. 2021, 33, 630–641. [Google Scholar] [CrossRef]
- Yu, Z.; Hu, J.; Min, G.; Zhao, Z.; Miao, W.; Hossain, M.S. Mobility-aware proactive edge caching for connected vehicles using federated learning. IEEE Trans. Intell. Transp. Syst. 2020, 22, 5341–5351. [Google Scholar] [CrossRef]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain technology overview. arXiv 2019, arXiv:1906.11078. [Google Scholar]
- KPMG LLP. Blockchain and the Future of Finance: A Potential New World for CFOs—And How to Prepare. Available online: https://assets.kpmg/content/dam/kpmg/ca/pdf/2019/05/blockchain-and-the-future-of-finance.pdf (accessed on 21 June 2022).
- Du, M.; Chen, Q.; Xiao, J.; Yang, H.; Ma, X. Supply Chain Finance Innovation Using Blockchain. IEEE Trans. Eng. Manag. 2020, 67, 1045–1058. [Google Scholar] [CrossRef]
- Alam, M.R.; Reaz, M.B.I.; Ali, M.A.M. A Review of Smart Homes—Past, Present, and Future. IEEE Trans. Syst. Man Cybern. Part C 2012, 42, 1190–1203. [Google Scholar] [CrossRef]
- Batty, M.; Axhausen, K.W.; Giannotti, F.; Pozdnoukhov, A.; Bazzani, A.; Wachowicz, M.; Ouzounis, G.; Portugali, Y. Smart Cities of the Future. Eur. Phys. J. Spec. Top. 2012, 214, 481–518. [Google Scholar] [CrossRef] [Green Version]
- Sun, M.; Zhang, J. Research on the application of block chain big data platform in the construction of new smart city for low carbon emission and green environment. Comput. Commun. 2020, 149, 332–342. [Google Scholar] [CrossRef]
- Dagar, R.; Som, S.; Khatri, S.K. Smart Farming—IoT in Agriculture. In Proceedings of the International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 11–12 July 2018. [Google Scholar]
- Saurabh, S.; Dey, K. Blockchain technology adoption, architecture, and sustainable agri-food supply chains. J. Clean. Prod. 2021, 284, 124731. [Google Scholar] [CrossRef]
- Shahinzadeh, H.; Moradi, J.; Gharehpetian, G.B.; Nafisi, H.; Abedi, M. IoT Architecture for Smart Grids. In Proceedings of the International Conference on Protection and Automation of Power System (IPAPS), Tehran, Iran, 8–9 January 2019. [Google Scholar]
- Menon, V.G.; Jacob, S.; Joseph, S.; Sehdev, P.; Khosravi, M.R.; Turjman, F.A. An iot-enabled intelligent automobile system for smart cities. Internet Things 2022, 18, 100213. [Google Scholar] [CrossRef]
- Baker, S.B.; Xiang, W.; Atkinson, I. Internet of things for smart healthcare: Technologies, challenges, and opportunities. IEEE Access 2017, 5, 26521–26544. [Google Scholar] [CrossRef]
- Badhotiya, G.K.; Sharma, V.P.; Prakash, S.; Kalluri, V.; Singh, R. Investigation and assessment of blockchain technology adoption in the pharmaceutical supply chain. Mater. Today Proc. 2021, 46, 10776–10780. [Google Scholar] [CrossRef]
- Zheng, J.; Dike, C.; Pancari, S.; Wang, Y.; Giakos, G.C.; Elmannai, W.; Wei, B. An In-Depth Review on Blockchain Simulators for IoT Environments. Future Internet 2022, 14, 182. [Google Scholar] [CrossRef]
- Javed, A.R.; Hassan, M.A.; Shahzad, F.; Ahmed, W.; Singh, S.; Baker, T.; Gadekallu, T.R. Integration of Blockchain Technology and Federated Learning in Vehicular (IoT) Networks: A Comprehensive Survey. Sensors 2022, 22, 4394. [Google Scholar] [CrossRef] [PubMed]
- Mohanta, B.K.; Jena, D.; Panda, S.S.; Sobhanayak, S. Blockchain technology: A survey on applications and security privacy Challenges. Internet Things 2019, 8, 100107. [Google Scholar] [CrossRef]
- Santhi, A.R.; Muthuswamy, P. Influence of Blockchain Technology in Manufacturing Supply Chain and Logistics. Logistics 2022, 6, 6010015. [Google Scholar]
- Akaba, T.I.; Norta, A.; Udokwu, C.; Draheim, D. A Framework for the Adoption of Blockchain-Based e-Procurement Systems in the Public Sector: A Case Study of Nigeria. In Responsible Design, Implementation and Use of Information and Communication Technology; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; Volume 12066, pp. 3–14. [Google Scholar] [CrossRef] [Green Version]
- Guo, D.; Ling, S.; Li, H.; Ao, D.; Zhang, T.; Rong, Y.; Huang, G.Q. A framework for personalized production based on digital twin, blockchain and additive manufacturing in the context of Industry 4.0. In Proceedings of the 2020 IEEE 16th International Conference on Automation Science and Engineering (CASE), Hong Kong, China, 20–21 August 2020. [Google Scholar]
- Chen, J.; Xu, S.; Liu, K.; Yao, S.; Luo, X.; Wu, H. Intelligent Transportation Logistics Optimal Warehouse Location Method Based on Internet of Things and Blockchain Technology. Sensors 2022, 22, 1544. [Google Scholar] [CrossRef]
- Wu, L.; Lu, W.; Xue, F. Construction Inspection Information Management with Consortium Blockchain. In Proceedings of the 25th International Symposium on Advancement of Construction Management and Real Estate; Springer: Singapore, 2020; pp. 1397–1406. [Google Scholar] [CrossRef]
- Bellavista, P.; Esposito, C.; Foschini, L.; Giannelli, C.; Mazzocca, N.; Montanari, R. Interoperable Blockchains for Highly-Integrated Supply Chains in Collaborative Manufacturing. Sensors 2021, 21, 4955. [Google Scholar] [CrossRef]
- Tijan, E.; Aksentijevic, S.; Ivanic, K.; Jardas, M. Blockchain Technology Implementation in Logistics. Sustainability 2019, 11, 1185. [Google Scholar] [CrossRef] [Green Version]
- Jæger, B.; Bach, T.; Pedersen, S.A. A Blockchain Application Supporting the Manufacturing Value Chain. In Advances in Production Management Systems. Production Management for the Factory of the Future. IFIP Advances in Information and Communication Technology; Springer: Cham, Switzerland, 2019; Volume 566, pp. 466–473. [Google Scholar] [CrossRef]
- Leunga, S.C.H.; Tsanga, S.O.S.; Nga, W.L.; Wub, Y. A robust optimization model for multi-site production planning problem in an uncertain environment. Eur. J. Oper. Res. 2007, 181, 224–238. [Google Scholar] [CrossRef]
- Tao, F.; Qi, Q.; Liu, A.; Kusiak, A. Data-driven smart manufacturing. J. Manuf. Syst. 2018, 48, 157–169. [Google Scholar] [CrossRef]
- Johnson, J.S.; Friend, S.B.; Lee, H.S. Big Data Facilitation, Utilization, and Monetization: Exploring the 3Vs in a New Product Development Process. J. Prod. Innov. Manag. 2017, 34, 640–658. [Google Scholar] [CrossRef]
- METI. Connected Industries Tokyo Initiative 2017. In Proceedings of the Connected Industries Conference, Tokyo, Japan, 4 October 2017. [Google Scholar]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- The Federal Ministry for Economic Affairs and Climate Action; GAIA-X. Available online: https://www.data-infrastructure.eu/GAIAX/Navigation/EN/Home/home.html (accessed on 13 June 2022).
- IOTA. Available online: https://www.iota.org/ (accessed on 13 June 2022).
- Yan, X.; Wu, Q.; Sun, Y. A Homomorphic Encryption and Privacy Protection Method Based on Blockchain and Edge Computing. Wirel. Commun. Mob. Comput. 2020, 2020, 8832341. [Google Scholar] [CrossRef]
- Nakanishi, R.; Zhang, Y.; Sasabe, M.; Kasahara, S. IOTA-Based Access Control Framework for the Internet of Things. In Proceedings of the Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 27–30 September 2020. [Google Scholar]
- Cuzzocrea, A.; Maio, V.D.; Fadda, E. Experimenting and Assessing a Distributed Privacy-Preserving OLAP over Big Data Framework: Principles, Practice, and Experiences. In Proceedings of the 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020. [Google Scholar] [CrossRef]
- Ronald, R.L.; Adi, S.; Leonard, A. A method for obtaining digital signatures and public key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Gentry, C. A Fully Homomorphic Encryption Scheme. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 2009. [Google Scholar]
- Fen, B. Cryptanalysis of a provable secure additive and multiplicative privacy homomorphism. In Proceedings of the International Workshop on Coding and Cryptography (WCC), Versailles, France, 24–28 March 2003. [Google Scholar]
- Wu, D.J.; Feng, T.; Naehrig, M.; Lauter, K. Privately evaluating decision trees and random forests. Proceeding Priv. Enhancing Technol. (PoPETs) 2016, 2016, 335–355. [Google Scholar] [CrossRef] [Green Version]
- Nasu, H.; Kodera, Y.; Nogami, Y. Secure Comparison Protocol for Promoting Business to Business Collaboration on the Blockchain. In Proceedings of the International Conference on Consumer Electronics-Taiwan (ICCE-TW), Penghu, Taiwan, 15–17 September 2021. [Google Scholar]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Advances in Cryptology-EUROCRYPT ’99; Springer: Berlin/Heidelberg, Germany, 1999. [Google Scholar]

| Step | Processing |
|---|---|
| 1 | binary-expands and and encrypts and ( = 0~k-1 bits) with the public key. |
| 2 | puts , , and the public key into the quality data chaincode CC, as seen in Figure 3. |
| 3 | calculates with the public key. |
| 4 | puts and the public key into the XOR data chaincode XOR CC, as seen in Figure 3. |
| Step | Processing |
|---|---|
| 1 | gets and saves and the public key from the XOR data chaincode XOR CC, as seen in Figure 3. |
| 2 | receives an XOR data request and a public key from . |
| 3 | identifies the that has the same public key sent by in Step 2. |
| 4 | If there is an , sends the to . |
| Step | Processing |
|---|---|
| 1 | gets , , and the public key from the quality data chaincode CC as seen in Figure 3. |
| 2 | sends the public key to and receives from . |
| 3 | From the most significant bit, calculates . |
| 4 | sends to . |
| Step | Processing |
|---|---|
| 1 | receives from . |
| 2 | decrypts with the secret key. |
| 3 | If there is , sends to . |
| Step | Processing |
|---|---|
| 1 | receives when or knows that did not occur. |
| 2 | If
receives while using Formula (1), then can be determined. If receives while using Formula (2), then can be determined. |
| 3 | checks the difference between the numbers at times and by calculating |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nasu, H.; Kodera, Y.; Nogami, Y. A Business-to-Business Collaboration System That Promotes Data Utilization While Encrypting Information on the Blockchain. Sensors 2022, 22, 4909. https://doi.org/10.3390/s22134909
Nasu H, Kodera Y, Nogami Y. A Business-to-Business Collaboration System That Promotes Data Utilization While Encrypting Information on the Blockchain. Sensors. 2022; 22(13):4909. https://doi.org/10.3390/s22134909
Chicago/Turabian StyleNasu, Hiroaki, Yuta Kodera, and Yasuyuki Nogami. 2022. "A Business-to-Business Collaboration System That Promotes Data Utilization While Encrypting Information on the Blockchain" Sensors 22, no. 13: 4909. https://doi.org/10.3390/s22134909
APA StyleNasu, H., Kodera, Y., & Nogami, Y. (2022). A Business-to-Business Collaboration System That Promotes Data Utilization While Encrypting Information on the Blockchain. Sensors, 22(13), 4909. https://doi.org/10.3390/s22134909






