2. System Model and Problem Formulation
As shown in
Figure 1, we consider a UAV communication system in which multiple mobile users need to receive information from the BS, while an eavesdropper EVE is located around mobile users and attempts to intercept the downlink signal between UAV and mobile users. There is no direct communication link between BS and the users due to obstacle occlusion. Therefore, we establish a two-hop wireless relaying transmission link by using a UAV relay. Without loss of generality, a three-dimensional (3D) Cartesian coordinate system is considered. Suppose that a set of
mobile users are randomly distributed on the ground, and the UAV, which is denoted as R, can adjust its 3D position. Then, the coordinates of BS, UAV, and the
nth mobile user are
,
, and
, respectively. The rough location of EVE can be detected by an optical camera or synthetic aperture radar (SAR) [
22]. In practice, the eavesdroppers always try to hide their existence, and the location detection may suffer from errors [
23]. Therefore, we assume that the error between the measured value and the actual coordinates is
.
According to [
17], the probability of LoS communication between the UAV R and the ground communication node m is
where
and
are constants depending on the environment type, while
and
are the distance and elevation angle between the UAV and node m, respectively.
To ensure the reliability of the LoS communication between UAV and the BS/mobile users, the probability of LoS needs to meet
[
24], where the
is a constant close to 1. To facilitate the analysis, this constraint can be rewritten as follows
To guarantee the security of information transmission, we consider the worst case, i.e., it is a LoS link between the UAV and EVE. The Doppler effect is assumed to be perfectly compensated [
25]. Then, the channel gain between the UAV and BS, EVE, and the
nth mobile user can be expressed as the following free-space path loss model [
26],
where
, and
denotes the channel power gain at the reference distance
d = 1 m, which depends on the carrier frequency, antenna gain, etc., and
is the distance between X and R. Considering the worst case, the minimum distance between the UAV R and the EVE is
.
We assume that the downlink between UAV and mobile users adopts frequency division multiple access (FDMA), and the UAV adopts the decode-and-forward (DF) relaying method. The UAV transmits information to mobile users with bandwidth allocation
and power allocation
. Considering the limited spectrum resources, the maximum bandwidth for this downlink is denoted as
, and the maximum transmitting power of the UAV is
. The channel capacity between the UAV and the
nth mobile user is
where
,
, and
is the noise power spectrum density.
Similarly, the channel capacity between the UAV and the EVE as well as the BS can be expressed as follows, respectively
where
W is the bandwidth between the R and BS,
, and
is the noise power at the UAV.
According to [
12], the security capacity is defined as the difference between the legitimate channel capacity and the eavesdropping channel capacity, i.e.,
In this paper, we aim to maximize
by jointly optimizing the UAV’s 3D trajectory, bandwidth, and power allocation with the constraints on information causality [
27], LoS communication reliability, and the QoS requirement of mobile users. We formulate the problem of interest as follows
where (8b) and (8c) are information causality constraints in the relaying system, i.e., UAV R can only forward the data that has already been received from BS during the relaying process [
27]; (8d) and (8e) guarantee the reliability of the LoS communication; and (8h) guarantees the QoS requirement of mobile users. In addition, (8f) and (8g) limit the maximum available bandwidth and maximum transmission power.
3. Problem Formulation
Note that the above problem contains nonconvex constraints and nonconvex objective functions, and the UAV location, power allocation, and bandwidth allocation are coupled with each other. To solve this problem, we propose an efficient iterative optimization algorithm, i.e., P1 is decomposed into three subproblems to optimize the UAV’s position, power allocation, and bandwidth allocation, respectively.
3.1. 3D Trajectory Optimization
In this section, the trajectory of the UAV is optimized with fixed power and bandwidth allocations. The slack variables
are introduced, and the subproblem can be formulated as
It can be seen that P1.1 is equivalent to the trajectory optimization subproblem of P1 when the constraints (9d)–(9f) are satisfied with equality. For any
, if (9d) or (9e) is strictly unequal,
will increase as
decreases or
increases. Therefore, the optimal solution of P1.1 is necessarily obtained when (9d)–(9f) are satisfied with equality, i.e., the optimal solution to P1 can be obtained by equivalently solving the P1.1 when power and bandwidth allocation are fixed. However, it is still nonconvex programming due to the nonconvex constraints (9b), (9c) and (9e). To solve this problem, the UAV’s location will be updated iteratively based on the SCA algorithm [
28].
Define the coordinate of the UAV in the
mth iteration of the SCA algorithm as
, the communication rates between BS-R/n-R are
, respectively. Let
. According to [
28], we can estimate the lower bounds
/
of
/
by a first-order Taylor expansion, i.e.,
where
,
,
,
,
.
Based on the above analysis, the SCA algorithm solves P1.1 at the
mth iteration by transforming it as follows:
P1.1.1 is a convex optimization problem, which can be solved by CVX. After obtaining the optimal solution
of P1.1.1, it will be used as the input for the next iteration. Finally, the optimization result
of the UAV trajectory can be obtained by several iterations. In summary, let
,
,
,
; then, the subproblem of trajectory optimization can be solved by Algorithm 1.
| Algorithm 1 SCA algorithm |
- 1:
Initialize the location matrix , , define maximum iteration M, tolerance of accuracy , objective function values - 2:
Find the optimal solution to problem by CVX, and calculate - 3:
Ifor -
Update - 4:
Output - 5:
Else -
Let , repeat 2
|
3.2. Power Allocation Optimization
In this subsection, we focus on the subproblem to find the optimal power allocation, while the UAV’s trajectory and bandwidth are fixed. Obviously, the function
is concave, so the optimization problem cannot be solved directly. Similar to P1.1.1, we use the SCA algorithm to solve it. Specifically, in the
mth iteration, the upper bound
of
can be estimated by the first-order Taylor expansion as follows
The optimization problem can be rewritten as
P1.2 is then reduced to a convex programming problem and can be solved by CVX. Since the objective function and constraints contain the
function, CVX processing requires a large number of approximation iterations [
29]. In order to solve this problem, we introduce two sets of auxiliary variables
, and transform the constraints into LMI constraints or SOC constraints. Then, the optimization problem is expressed as
where
is the lower bound obtained by performing a Taylor expansion on
at
, i.e.,
For the constraint (14e), it can be transformed into an SOC constraint by simple transformation, i.e.,
P1.2.1 is a simple second-order cone programming (SOCP) problem, which can also be solved by CVX effectively. In summary, let ; then, the subproblem of power allocation optimization can be solved by Algorithm 1.
3.3. Bandwidth Allocation Optimization
This section investigates the optimization of bandwidth allocation with a fixed location of UAV and power allocation.
Similar to
Section 3.2, in the iterative process using the SCA algorithm, we introduce auxiliary variables
to transform the constraints into LMI or SOC constraints. Then, the optimization problem is expressed as follows
where
is the upper bound obtained by the first-order Taylor expansion of
at
, and
is the lower bound obtained by the first-order Taylor expansion of
at
.
and
are approximated by the following convex quadratic functions:
P1.3 is a simple SOCP problem, which can also be solved by CVX. In summary, let , , ; then, the subproblem of bandwidth optimization can be solved by Algorithm 1.
3.4. Joint Optimization Algorithm
Combining the analysis of the three subproblems, a joint optimization algorithm for secrecy capacity is proposed, which uses Alternating Iterative Optimization until the objective function converges.
(1) P1.1.1 mainly involves variables, i.e., ;
(2) According to the definitions of LMI constraints and SOC constraints, (8d), (8e), (8h), and (11d) are the SOC constraints of dimension 4 with a total number of , and (11e) is an LMI constraint of dimension 5.
(3) Constraint (11b) can be simply expressed in the following form
Thus, (11b) is an SOC constraint of dimension 4. Similarly, (11c) is also an SOC constraint of dimension 4. Combining (2) and (3), it is known that P2.1 has a total of SOC constraints of dimension 4. In summary, we can see that Algorithm 1 contains one LMI constraint of dimension 5, SOC constraints of dimension 4, and one SOC constraint of dimension 3; thus, the complexity of the algorithm can be expressed as .
Similarly, the complexity of subproblems 2 and 3 are , , and , respectively. In summary, the complexity of the joint optimization algorithm is .
Combined with [
24], it can be seen that each subproblem obtains a lower bound on the original optimization problem, and the objective function is monotonically non-decreasing during the alternating iterations, i.e.
Thus, P1 can be obtained by Algorithm 2 with finite iterations to obtain a convergent solution.
| Algorithm 2 Joint optimization of coordinate and resource allocation algorithm |
- 1:
Initialize , , define maximum iteration , tolerance of accuracy - 2:
while - 3:
Let , solve problem (1) with Algorithm 1, find optimal coordinate - 4:
Let , solve problem (2) with Algorithm 1, find optimal power allocation - 5:
Let , solve problem (3) with Algorithm 1, find optimal bandwidth allocation - 6:
Update, let - 7:
End while - 8:
Output
|
4. Simulation Results
In this section, we assume that the mobile users are randomly distributed in a circle area with the radius of 500 m, and
represents the distance between the center of the circle and the BS. Other simulation parameters are given in
Table 1.
Figure 2 provides the secrecy capacity versus the number of iterations under different parameters, which can show the convergence characteristics of the proposed joint optimization algorithm. It can be seen that when the number of iterations is larger than 15, the secrecy capacity tends to be stable. Therefore, the proposed optimization algorithm has good convergence under different conditions. In addition, it can be seen that the number of iterations required for the convergence of the algorithm is mainly influenced by the convergence accuracy and the number of ground users. The number of iterations of the algorithm decreases with the value of
. The number of iterations required for the algorithm to converge also increases with the number of ground users due to more variables being involved.
Considering the mobility of ground users,
Figure 3a shows the trajectory of the UAV relay versus the network mobility to clearly describe the relationship between the UAV’s position and mobile users.
Figure 3a shows that the center of the mobile user group makes a circular motion, and the number and coordinates of mobile users are randomly generated after each location update. From
Figure 3a, the UAV’s height increases gradually with the distance between the mobile users and the BS. The reason is that the flight altitude of the UAV needs to be increased to raise the elevation angle between mobile users and UAV with the increasing communication distance so as to ensure the probability of LoS communication.
Figure 3b shows the projection of the UAV trajectory on the horizontal plane. For ease of elaboration, the projection of the UAV in horizontal plane is denoted as
, and the corresponding center of mobile users is denoted as
. It can be seen that
is always on the right side of
, which is influenced by the information causality constraint and the eavesdropper’s position. The offset between
and
is more pronounced when the ground user is far from the BS and close to the EVE.
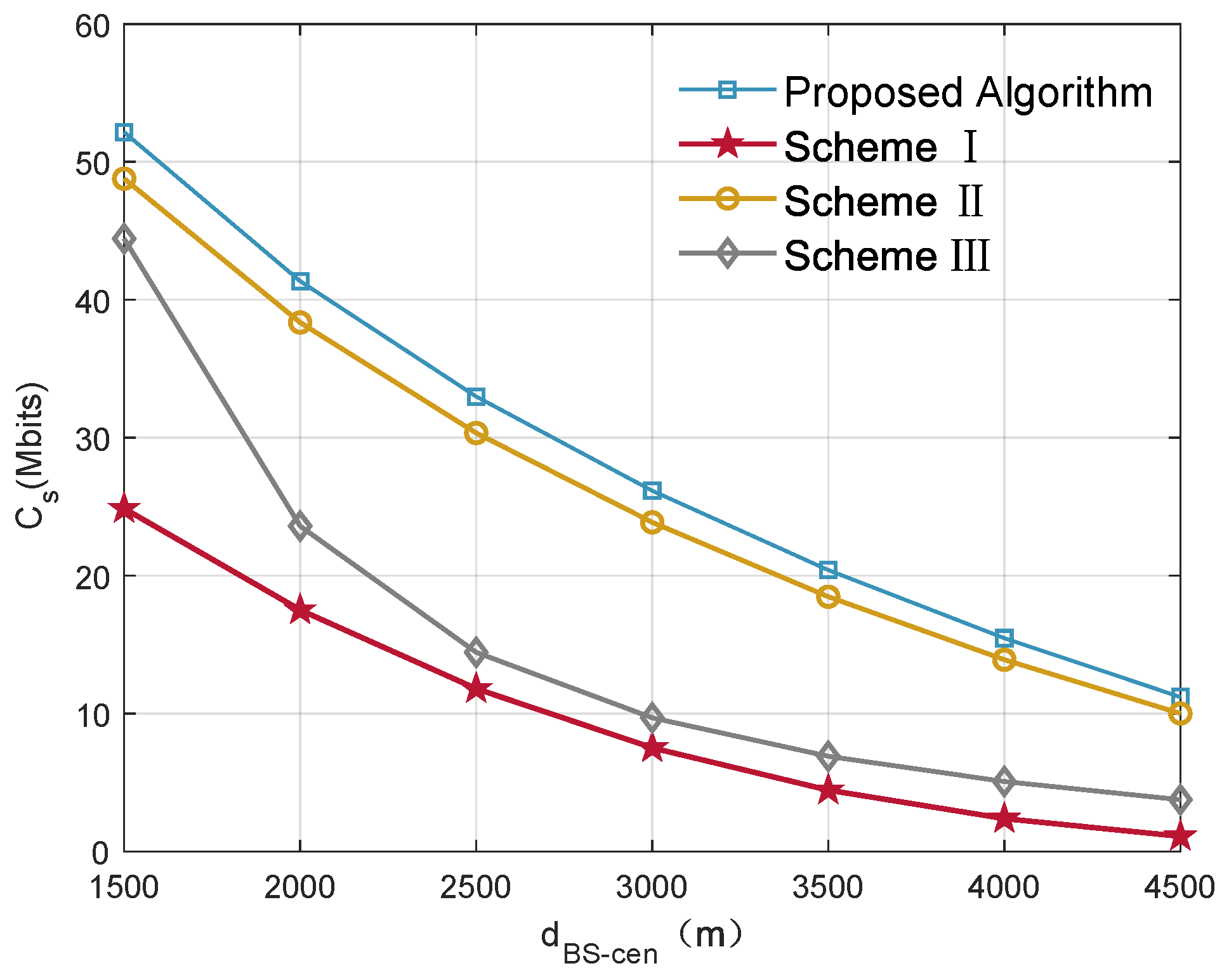
To illustrate the effectiveness of the proposed designs, the proposed joint trajectory and communication resource optimization scheme is compared with other three benchmark schemes proposed in [
15,
24,
30].
Scheme 1—The UAV is deployed at the center of mobile users. The height of UAV relay, bandwidth and power allocation are designed to maximize the secrecy communication capacity of this system [
30].
Scheme 2—The transmission power and bandwidth are evenly allocated following the principle of fairness [
24], and the 3D location of the UAV is optimized.
Scheme 3—With fixed altitude of the UAV relay [
15], the 2D trajectory, power and bandwidth allocation are optimized, and the probability of LoS is considered in the simulation process.
From
Figure 4, it can be seen that the secrecy capacity obtained by all schemes is decreasing with the distance between the BS and the center of mobile users increasing. This can be easily understood: as the communication distance increases, the signal experiences more fading, and the legitimate channel capacity will decrease. In addition, as the UAV moves far away from the BS, the distance between the UAV and the EVE decreases, causing an increase in eavesdropping channel capacity; then, the secrecy capacity decreases. In scheme 1, the UAV is always located in the mobile users’ center, and the downlink channel quality in the UAV-enabled relay system is better than other schemes at this time. However, this scheme ignores the impact on EVE and BS, resulting in the limitation of legitimate channel capacity by information causality constraint and the increasement of eavesdropping channel capacity. Scheme 2 shows that the power and bandwidth are evenly allocated based on the principle of fairness. For users with relatively poor channel quality, the allocation of the same communication resources cannot achieve the optimal overall performance. In scheme 3, UAV trajectory is optimized at a fixed altitude, which is difficult to ensure the reliability of LoS communication, so the system performance will be worse than the proposed algorithm.
Figure 5 shows the secrecy capacity
versus
for different maximum available powers
. It can be seen that at a certain value of
,
firstly increases with
and then remains constant. This is due to the fact that the relay communication process is limited by the information causality constraint; i.e., the maximum secrecy capacity of the system is constrained by the channel capacity between the BS and the UAV. In other words, increasing power and bandwidth cannot consistently improve the communication performance of the relay system.
Figure 6 shows the secrecy capacity of each mobile user under different schemes. For each mobile user, the algorithm proposed in the paper also has better performance than existing schemes. The reason is that the reliability of LoS communication is considered in the proposed optimization scheme, and we make full use of the location information to achieve dynamic multi-domain optimization. It can be seen that the proposed algorithm is more adaptable to the scenario of multiple mobile users.
5. Conclusions
In this paper, we investigate the secrecy capacity optimization problem when the UAV relay serves multiple mobile ground users in the presence of a malicious user eavesdropping on the ground. A joint optimization algorithm for trajectory design and resource allocation is proposed based on the proposed SCA-AIO algorithm. The secrecy capacity of the relay system is improved by jointly optimizing the UAV’s trajectory, power allocation, and bandwidth allocation while ensuring the reliability of LoS communication links, QoS requirements of users, and the information causality constraint. At the end of the paper, the effectiveness of the proposed optimization algorithm is demonstrated by numerical results. In addition, this paper reveals the impacts of different parameters on the system performance and the UAV trajectory trend of UAV relay with mobile ground users. In the text, to ensure the reliability of LoS communication, the UAV’s altitude changes drastically. Considering the limited energy of the UAV, the proposed optimization algorithm will affect the endurance of the UAV relay. In practical applications, it may be necessary to sacrifice some throughput performance to extend the endurance of the UAV. Futhermore, an energy efficiency (EE) maximization UAV trajectory design based on fly–hover will be the next step in our research to compromise the energy consumption and throughput in a UAV-enabled communication system.