Covert Performance for Integrated Satellite Multiple Terrestrial Relay Networks with Partial Relay Selection
Abstract
:1. Introduction
1.1. Related Work
1.2. Motivation and Contributions
- We first pioneer the study of covert communication in the ISMTRN with the partial relay selection scheme, where the selected relay opportunistically transmits covert information;
- Furthermore, considering the actual signal transmission situation, the statistical characteristics of the channels are given;
- On this basis, the closed-form expression of error detection probability (EDP) under this covert communication network is deduced to obtain more in-depth insights. Besides, the average covert communication rate (ACR) is given to measure the covert performance of this system;
- Finally, the numerical simulation results are given to analyze covert performance considerably. Moreover, observation results are summarized in detail.
2. System Model and Problem Formulation
2.1. System Description
2.2. Transmission Model
2.3. Problem Formulation
3. Performance Analysis
3.1. Statistical Properties of Channels
3.2. EDP
3.3. ACR
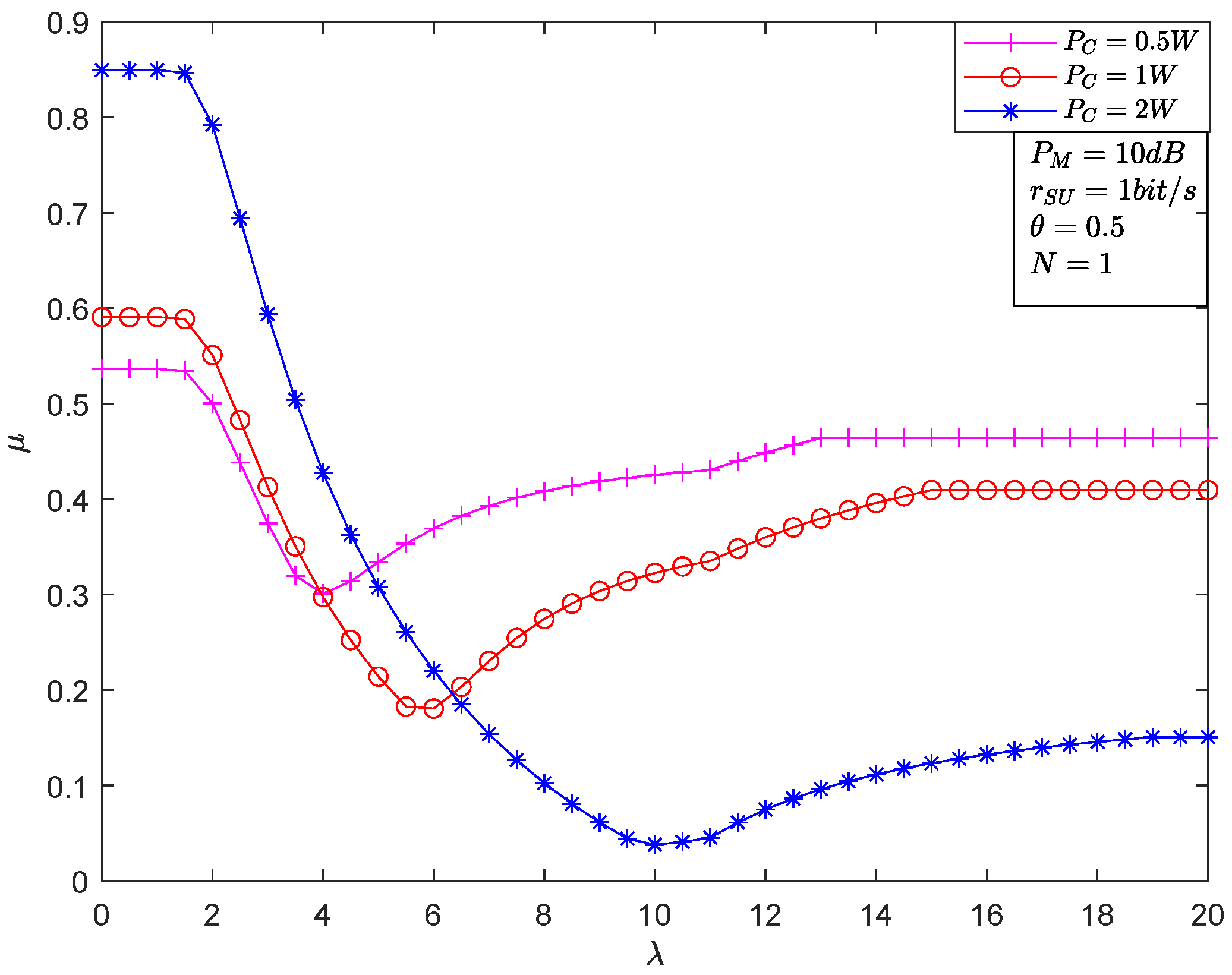
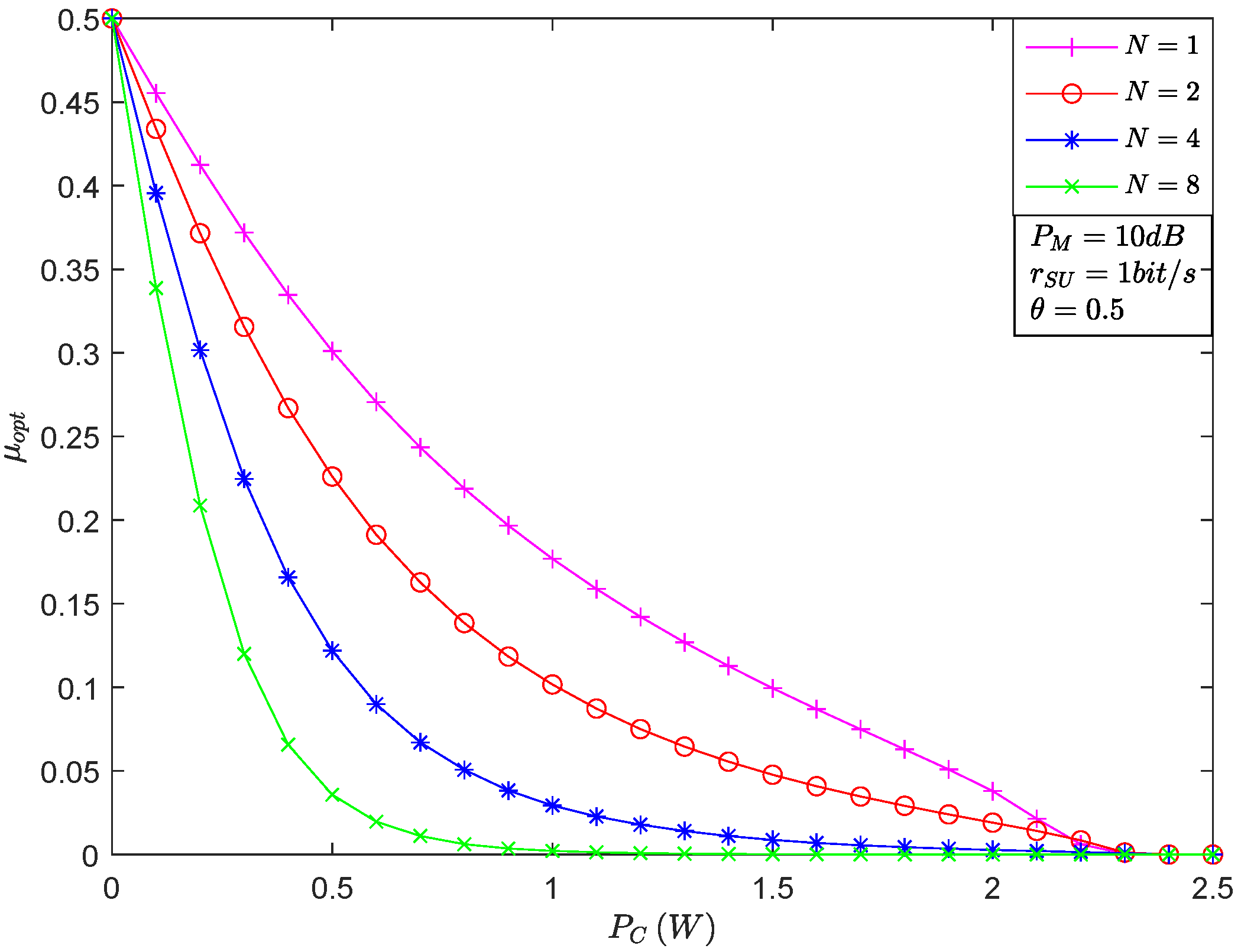
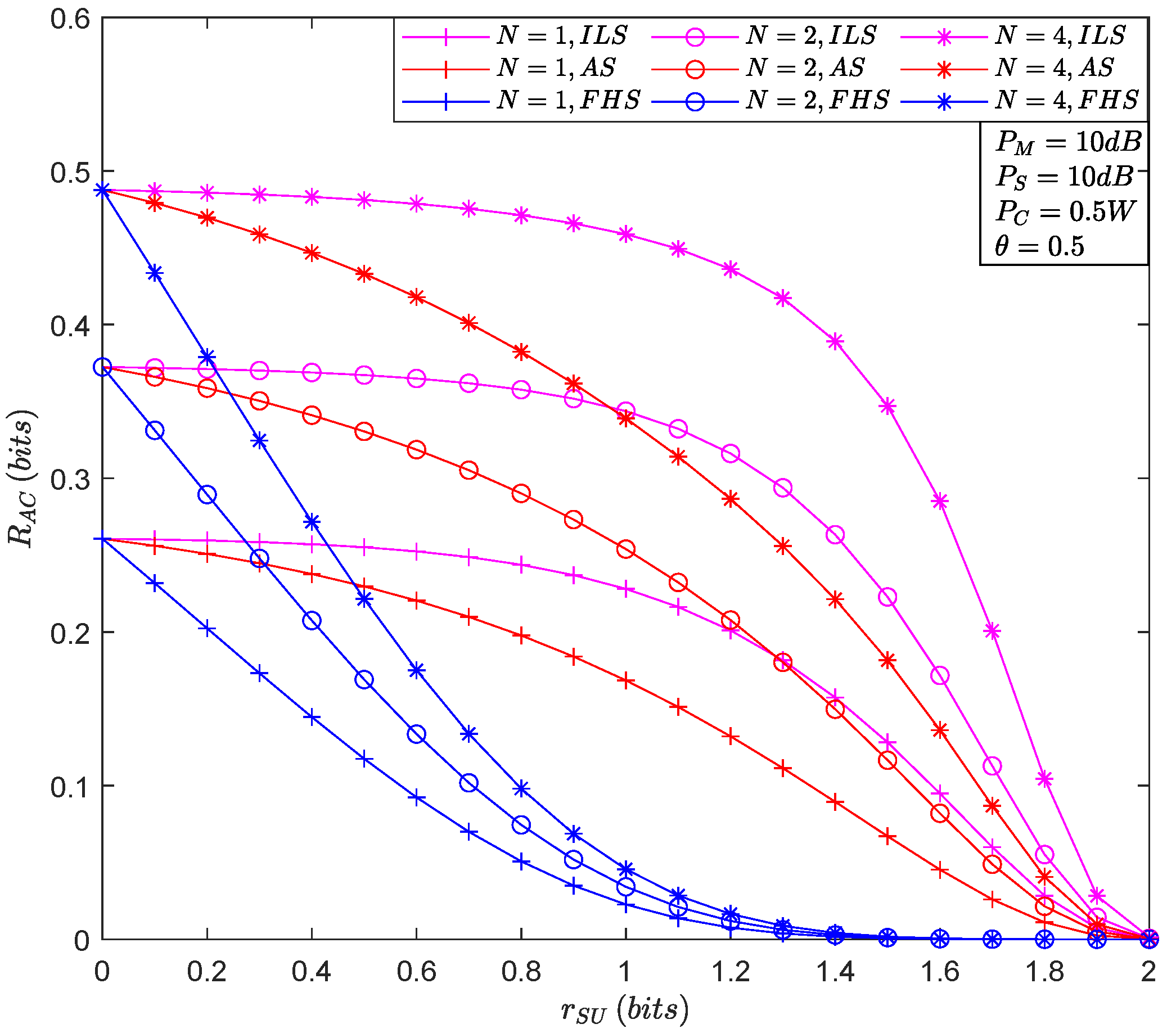
4. Numerical Results
5. Discussion
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ACR | Average covert communication rate |
| AN | Artificial noise |
| AS | Average shadow |
| AWGN | Addictive white Gaussian noise |
| CDF | Cumulative distortion function |
| DF | Decode-and-forward |
| EDP | Error detection probability |
| FA | False alarm |
| FHS | Frequent heavy shadowing |
| GEO | Geosynchronous earth orbit |
| HSTRN | Hybrid satellite-terrestrial relay network |
| HSTSs | Hybrid satellite-terrestrial systems |
| ILS | Infrequent light shadowing |
| IoE | Internet-of-Everything |
| IoT | Internet of Things |
| IRC | Intelligent Reflection Communication |
| ISAC | Integrated Sensing and Communication |
| ISMTRN | Integrated satellite multiple terrestrial relay network |
| LOS | Line-of-sight |
| MD | Missed detection |
| NOMA | Non-orthogonal multiple access |
| Probability distribution function | |
| PLS | Physical Layer Security |
| QoS | Quality of service |
| SatCom | Satellite communication |
| SINR | Signal-to-interference-plus-noise ratio |
| SNR | Signal-to-noise ratio |
| SR | Shadowed-Rician |
| TDMA | Time division multiple access |
| UAV | Unmanned aerial vehicle |
Appendix A
Appendix B
References
- Li, B.; Fei, Z.; Zhou, C.; Zhang, Y. Physical-layer security in space information networks: A survey. IEEE Internet Things J. 2020, 7, 33–52. [Google Scholar] [CrossRef]
- Guo, K.; An, K.; Zhang, B.; Huang, Y.; Tang, X.; Zheng, G.; Tsiftsis, T.A. Physical layer security for multi-user satellite communication systems with threshold-based scheduling scheme. IEEE Trans. Veh. Technol. 2020, 69, 5129–5141. [Google Scholar] [CrossRef]
- An, K.; Li, Y.; Yan, X.; Liang, T. On the performance of cache-enabled hybrid satellite-terrestrial relay networks. IEEE Wirel. Commun. Lett. 2019, 8, 1506–1509. [Google Scholar] [CrossRef]
- Zhang, X.; Guo, D.; An, K.; Zheng, G.; Chatzinotas, S.; Zhang, B. Auction-based multichannel cooperative spectrum sharing in hybrid satellite-terrestrial IoT networks. IEEE Internet Things J. 2021, 8, 7009–7023. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Zhu, W.-P.; Wang, J.-B.; Chen, J. Robust secure beam-forming for wireless powered cognitive satellite-terrestrial networks. IEEE Trans. Cognit. Commun. Netw. 2021, 7, 567–580. [Google Scholar] [CrossRef]
- Liu, R.; Guo, K.; An, K.; Zhu, S. NOMA-based overlay cognitive integrated satellite-terrestrial relay networks with secondary network selection. IEEE Trans. Veh. Technol. 2022, 71, 2187–2192. [Google Scholar] [CrossRef]
- Cao, W.; Zou, Y.; Yang, Z.; Zhu, J. Relay selection for improving physical-layer security in hybrid satellite-terrestrial relay networks. IEEE Access 2018, 6, 65275–65285. [Google Scholar] [CrossRef]
- Yan, S.; Wang, X.; Li, Z.; Li, B.; Fei, Z. Cooperative jamming for physical layer security in hybrid satellite terrestrial relay networks. China Commun. 2019, 16, 154–164. [Google Scholar] [CrossRef]
- Guo, K.; An, K.; Zhang, B.; Huang, Y.; Guo, D. Physical layer security for hybrid satellite terrestrial relay networks with joint relay selection and user scheduling. IEEE Access 2018, 6, 55815–55827. [Google Scholar] [CrossRef]
- Huang, Q.; Lin, M.; Zhu, W.; Chatzinotas, S.; Alouini, M. Performance analysis of integrated satellite-terrestrial multi-antenna relay networks with multi-user scheduling. IEEE Trans. Aerosp. Electron. Syst. 2020, 56, 2718–2731. [Google Scholar] [CrossRef]
- Huang, M.; Gong, F.; Zhang, N.; Li, G.; Qian, F. Reliability and security performance analysis of hybrid satellite-terrestrial multi-relay systems with artificial noise. IEEE Access 2020, 17, 34708–34721. [Google Scholar] [CrossRef]
- El-Latif, A.; Abd-El-Atty, B.; Mazurczyk, W.; Fung, C.; Venegas-Andraca, S.E. Secure data encryption based on quantum walks for 5G IoT scenario. IEEE Trans. Netw. Serv. Manag. 2021, 9, 118–131. [Google Scholar]
- Zeng, M.; Qian, H.; Chen, J.; Zhang, K. Forward secure public key encryption with keyword search for outsourced cloud storage. IEEE Trans. Cloud Comput. 2022, 10, 426–438. [Google Scholar] [CrossRef]
- Soderi, S.; Nicola, R.D. 6G networks physical layer security using RGB visible light communications. IEEE Access 2022, 10, 5482–5496. [Google Scholar] [CrossRef]
- Zhao, H.; Zhang, Y.; Huang, X.; Xiang, Y.; Su, C. A physical-layer key generation approach based on received signal strength in smart homes. IEEE Internet Things J. 2022, 9, 4917–4927. [Google Scholar] [CrossRef]
- Wei, Z.; Masouros, C.; Poor, H.V.; Petropulu, A.P.; Hanzo, L. Physical layer anonymous precoding: The path to privacy-preserving communications. IEEE Wirel. Commun. 2022, 29, 154–160. [Google Scholar] [CrossRef]
- Shi, W.; Xu, W.; You, X.; Zhao, C.; Wei, K. Intelligent reflection enabling technologies for integrated and green Internet-of-Everything beyond 5G: Communication, sensing, and security. IEEE Wirel. Commun. 2022. [Google Scholar] [CrossRef]
- Wei, Z.; Liu, F.; Masouros, C.; Su, N.; Petropulu, A.P. Toward multi-functional 6G wireless networks: Integrating sensing, communication, and security. IEEE Commun. Mag. 2022, 60, 65–71. [Google Scholar] [CrossRef]
- Wei, Z.; Liu, F.; Masouros, C.; Poor, H.V. Fundamentals of physical layer anonymous communications: Sender detection and anonymous precoding. IEEE Trans. Wirel. Commun. 2022, 21, 64–79. [Google Scholar] [CrossRef]
- Simmons, G.J. The prisoners’ problem and the subliminal channel. In Advances in Cryptology; Springer: Boston, MA, USA, 1984; pp. 51–67. [Google Scholar]
- Hu, J.; Yan, S.; Zhou, X.; Shu, F.; Li, J.; Wang, J. Covert communication achieved by a greedy relay in wireless networks. IEEE Trans. Wirel. Commun. 2018, 17, 4766–4779. [Google Scholar] [CrossRef] [Green Version]
- Zhou, X.; Yan, S.; Hu, J.; Sun, J.; Li, J.; Shu, F. Joint optimization of a UAV’s trajectory and transmit power for covert communications. IEEE Trans. Signal Process. 2019, 67, 4276–4290. [Google Scholar] [CrossRef] [Green Version]
- Bash, B.A.; Goeckel, D.; Towsley, D. Limits of reliable communication with low probability of detection on AWGN channels. IEEE J. Sel. Areas Commun. 2013, 31, 1921–1930. [Google Scholar] [CrossRef] [Green Version]
- Wang, L.; Wornell, G.W.; Zheng, L. Fundamental limits of communication with low probability of detection. IEEE Trans. Inf. Theory 2016, 62, 3493–3503. [Google Scholar] [CrossRef] [Green Version]
- Bloch, M.R. Covert communication over noisy channels: A re-solvability perspective. IEEE Trans. Inf. Theory 2016, 62, 2334–2354. [Google Scholar] [CrossRef] [Green Version]
- Lee, S.; Baxley, R.J.; Weitnauer, M.A.; Walkenhorst, B. Achieving undetectable communication. IEEE J. Sel. Top. Signal Process. 2015, 9, 1195–1205. [Google Scholar] [CrossRef]
- He, B.; Yan, S.; Zhou, X.; Lau, V.K.N. On covert communication with noise uncertainty. IEEE Commun. Lett. 2017, 21, 941–944. [Google Scholar] [CrossRef] [Green Version]
- Liu, Z.; Liu, J.; Zeng, Y.; Ma, J. Covert wireless communications in IoT systems: Hiding information in interference. IEEE Wirel. Commun. 2018, 25, 46–52. [Google Scholar] [CrossRef]
- Su, Y.; Sun, H.; Zhang, Z.; Lian, Z.; Xie, Z.; Wang, Y. Covert communication with relay selection. IEEE Wirel. Commun. Lett. 2021, 10, 421–425. [Google Scholar] [CrossRef]
- Gao, C.; Yang, B.; Jiang, X. Covert communication in relay-assisted IoT systems. IEEE Internet Things J. 2021, 8, 6313–6323. [Google Scholar] [CrossRef]
- Michalopoulos, D.S.; Suraweera, H.A.; Karagiannidis, G.K.; Schober, R. Amplify-and-forward relay selection with outdated channel estimates. IEEE Trans. Commun. 2012, 60, 1278–1290. [Google Scholar] [CrossRef]
- Sobers, T.V.; Bash, B.A.; Guha, S.; Towsley, D.; Goeckel, D. Covert communication in the presence of an uninformed jammer. IEEE Trans. Wirel. Commun. 2017, 16, 6193–6206. [Google Scholar] [CrossRef]
- Wang, J.; Tang, W.; Zhu, Q.; Li, X.; Rao, H.; Li, S. Covert communication with the help of relay and channel uncertainty. IEEE Wirel. Commun. Lett. 2019, 8, 317–320. [Google Scholar] [CrossRef]
- Arnau, J.; Christopoulos, D.; Chatzinotas, S.; Mosquera, C.; Ottersten, B. Performance of the multi-beam satellite return link with correlated rain attenuation. IEEE Trans. Wirel. Commun. 2014, 13, 6286–6299. [Google Scholar] [CrossRef]
- ITU-R P.452-15; Prediction Procedure for the Evaluation of Interference between Stations on the Surface of the Earth at Frequencies above about 0.1 GHz. ITU-R: Geneva, Switzerland, 2013.
- An, K.; Liang, T.; Zheng, G.; Yan, X.; Li, Y.; Chatzinotas, S. Performance limits of cognitive-uplink FSS and terrestrial FS for Ka-Band. IEEE Trans. Aerosp. Electron. Syst. 2019, 55, 2604–2611. [Google Scholar] [CrossRef]
- Miridakis, N.I.; Vergados, D.D.; Michalas, A. Dual-hop communication over a satellite relay and shadowed rician channels. IEEE Trans. Veh. Technol. 2015, 64, 4031–4040. [Google Scholar] [CrossRef]
- The Wolfram Function Site. Available online: http://functions.wolfram.com (accessed on 14 June 2022).
- Brychkov, Y.A. Handbook of Special Functions: Derivatives, Integrals, Series and Other Formulas; Chapman Hall/CRC Press: Boca Raton, FL, USA, 2008. [Google Scholar]
- Yan, X.; Xiao, H.; An, K.; Zhen, G.; Chatzainotas, S. Ergodic capacity of NOMA-based uplink satellite networks with randomly deployed users. IEEE Syst. J. 2020, 14, 3343–3350. [Google Scholar] [CrossRef]


| Shadowing | |||
|---|---|---|---|
| Frequent heavy shadowing (FHS) | 1 | 0.063 | 0.0007 |
| Average shadowing (AS) | 5 | 0.251 | 0.279 |
| Infrequent light shadowing (ILS) | 10 | 0.158 | 1.29 |
| Parameter | Value |
|---|---|
| Satellite Orbit | GEO |
| Carrier Frequency | GHz |
| 3 dB angle | |
| Maximal Beam Gain | dB |
| Maximal Receive Antenna Gain | dB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Z.; Liu, R.; Shuai, H.; Zhu, S.; Li, C. Covert Performance for Integrated Satellite Multiple Terrestrial Relay Networks with Partial Relay Selection. Sensors 2022, 22, 5524. https://doi.org/10.3390/s22155524
Wu Z, Liu R, Shuai H, Zhu S, Li C. Covert Performance for Integrated Satellite Multiple Terrestrial Relay Networks with Partial Relay Selection. Sensors. 2022; 22(15):5524. https://doi.org/10.3390/s22155524
Chicago/Turabian StyleWu, Zeke, Rui Liu, Haifeng Shuai, Shibing Zhu, and Changqing Li. 2022. "Covert Performance for Integrated Satellite Multiple Terrestrial Relay Networks with Partial Relay Selection" Sensors 22, no. 15: 5524. https://doi.org/10.3390/s22155524
APA StyleWu, Z., Liu, R., Shuai, H., Zhu, S., & Li, C. (2022). Covert Performance for Integrated Satellite Multiple Terrestrial Relay Networks with Partial Relay Selection. Sensors, 22(15), 5524. https://doi.org/10.3390/s22155524






