A Combined Sensing System for Intrusion Detection Using Anti-Jamming Random Code Signals
Abstract
1. Introduction
2. Materials and Methods
2.1. Experimental Setup
2.2. Generation and Characteristics of Random Code Signal
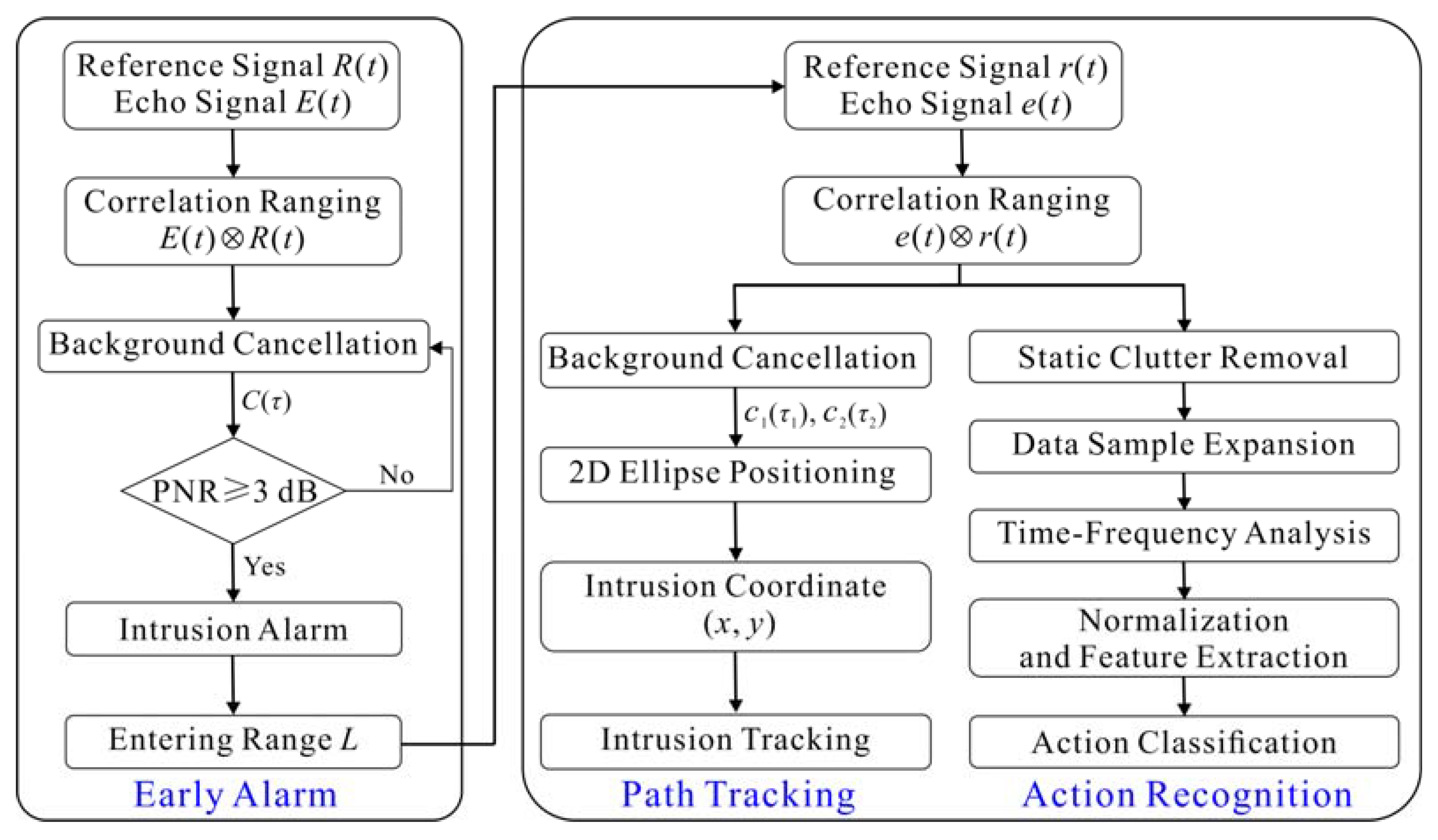
2.3. Intrusion Detection Algorithm
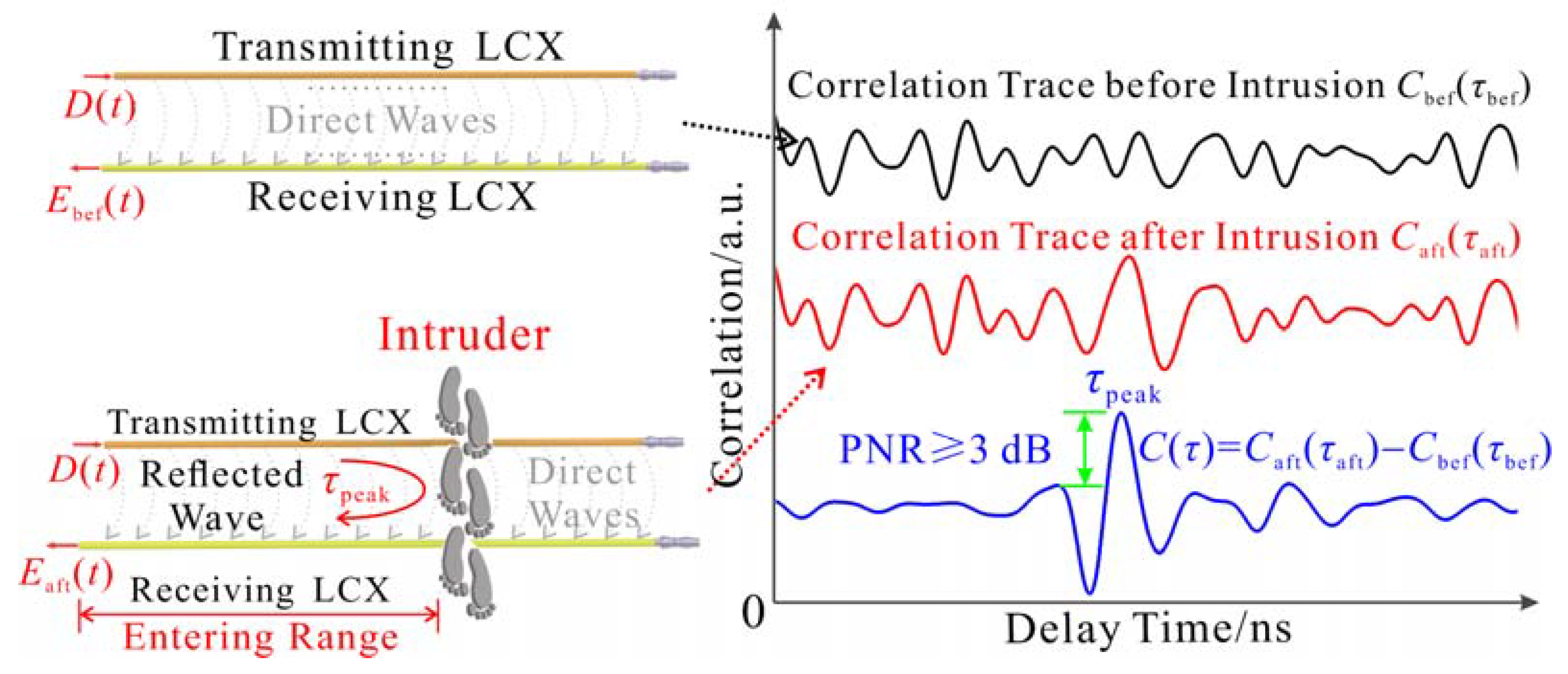
2.3.1. Early Alarm
2.3.2. Path Tracking
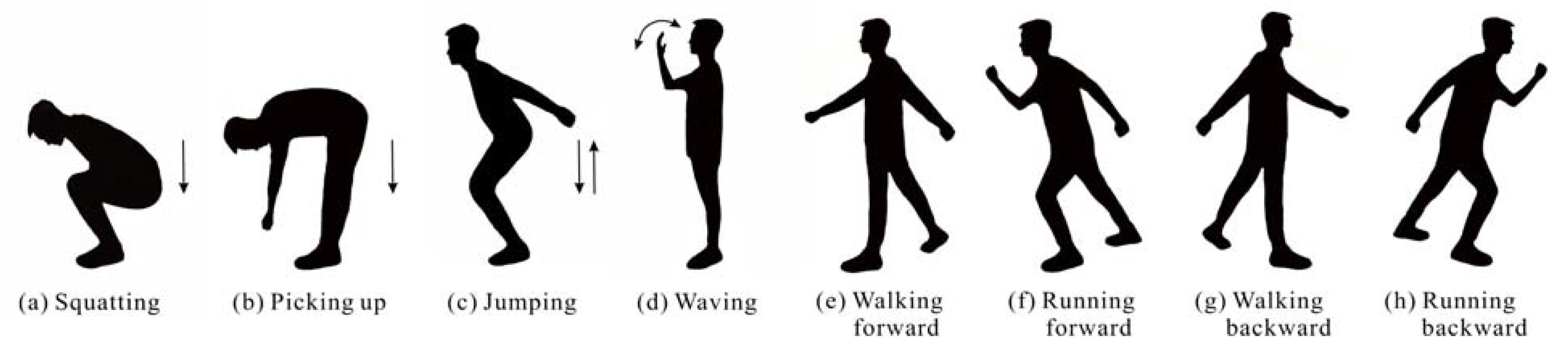
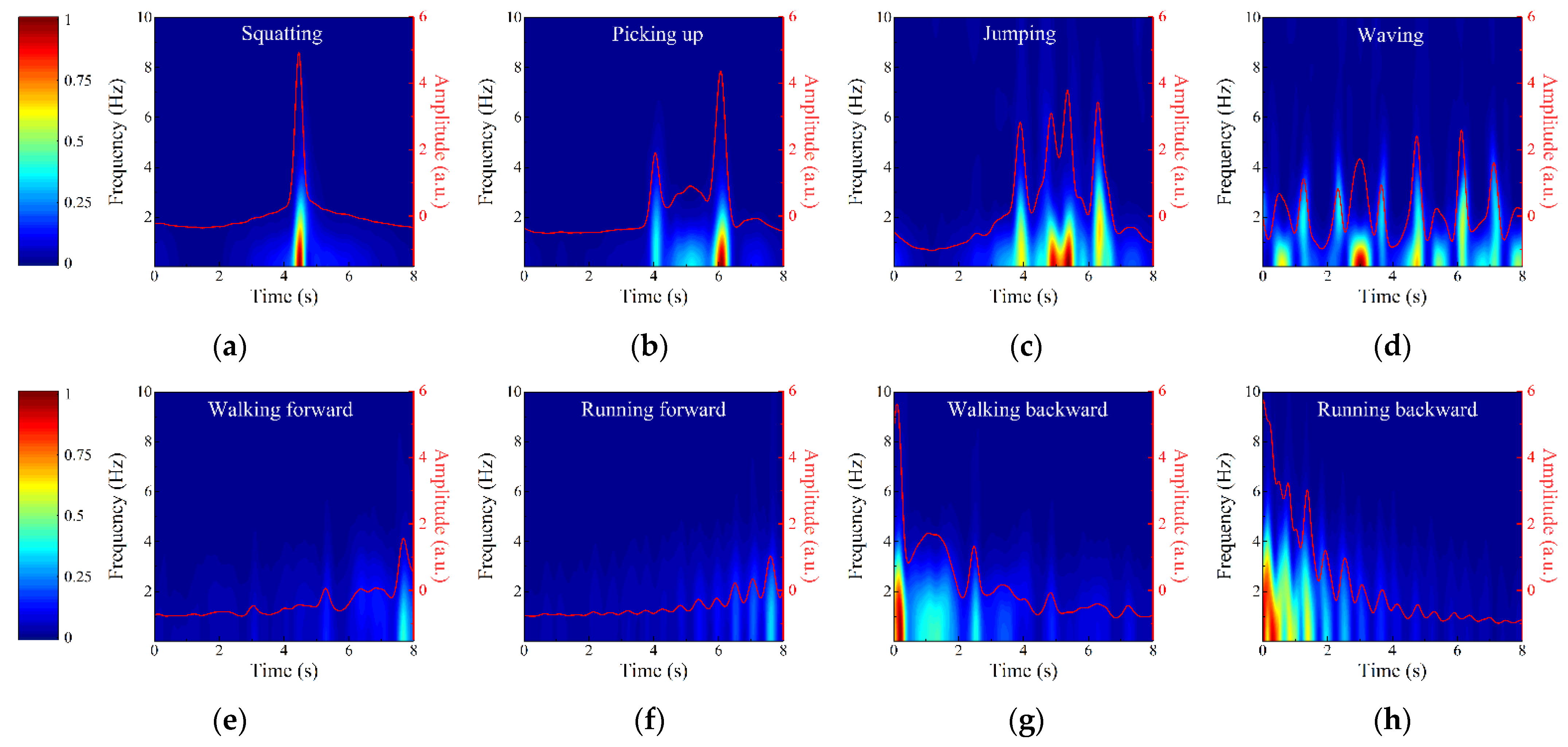
2.3.3. Action Recognition
- (1)
- Perform correlation processing on the echo signal eaft2(t) received by the RX2 and the corresponding reference signal raft2(t) to acquire the correlation trace caft2(τaft2) after intrusion, as given below:
- (2)
- Remove static clutters caused by the direct waves between the TX and RX2 from S by the linear trend subtraction method [37], and then a new TR matrix Ś without static clutters is generated.
- (3)
- Extend data sample, i.e., TR matrix Ś, to triple itself by time clipping on the observation time, so as to prevent model overfitting and improve system generalization performance.
- (4)
- Perform short-time Fourier transform (STFT) on each range bin of Ś to obtain the corresponding time-frequency (TF) matrix Ši, and the final TF matrix Ŝ is obtained as follows:where n is the number of range bins in Ś.
- (5)
- Normalize the values of Ŝ to between 0 and 1 by Equation (11), so as to eliminate the amplitude sensitivity.where ŝ∈Ŝ, ŝnorm is the normalized value of ŝ, and ŝmax and ŝmin are the maximum and minimum values of ŝ, respectively. On the basis of normalization, the feature extraction for Ŝnorm is further implemented by the fast principal component analysis, and its specific process is shown in Ref. [38]. By descending the orders of eigenvalues, the eigenvector of the first eigenvalue, i.e., the first principal component, is selected as the input of action classifier to reduce the data amount and classification complexity without losing the main action information.
- (6)
- Use the support vector machine (SVM) as the intruder’s action classifier, which adopts the LIBSVM with multi-classification function developed by C.-C. Chang and C.-J. Lin [39]. In addition, the radial basis function is selected as the kernel function, and the particle swarm optimization (PSO) is used to find the optimal combination of penalty coefficient c and kernel function parameter g. Finally, the PSO-SVM model [40] is constructed by adopting the optimal c and g to recognize the intruder’s activities.
3. Experimental Results
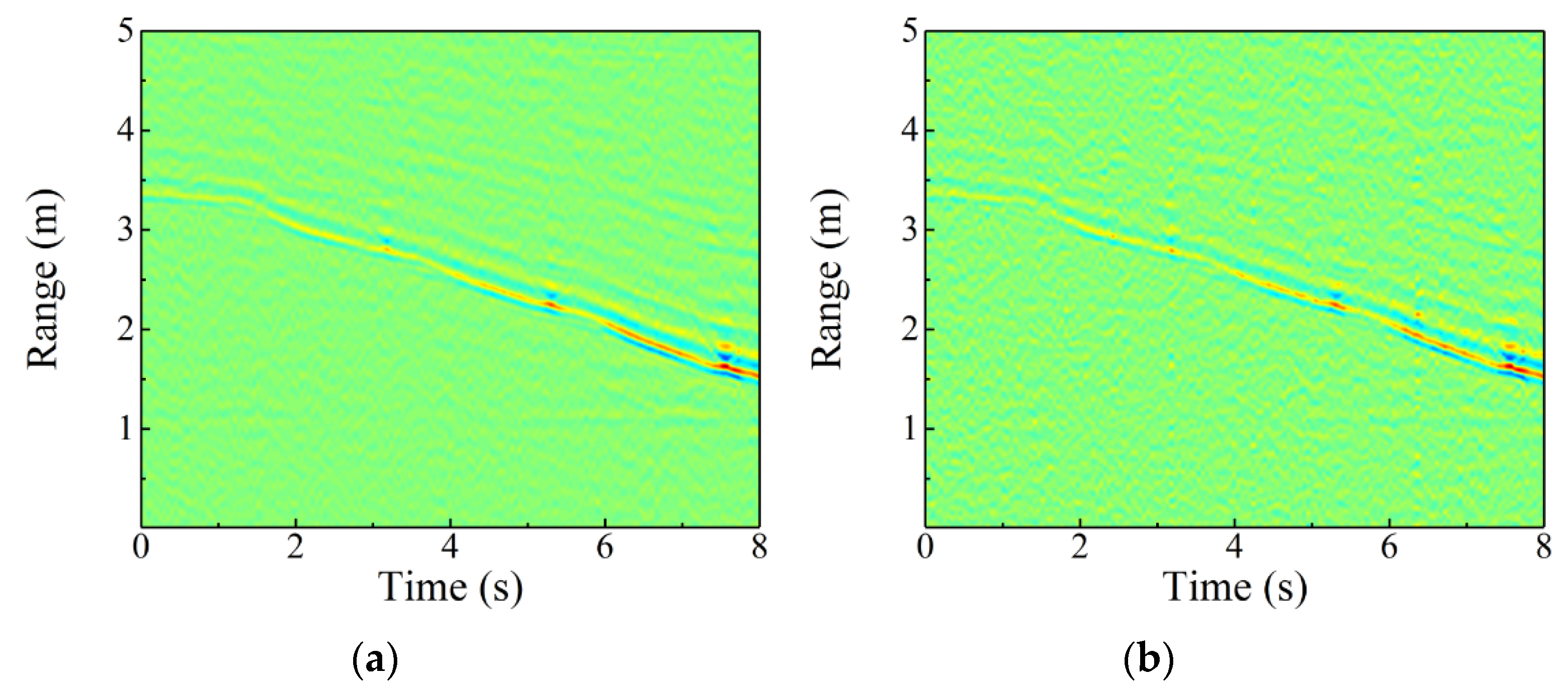
3.1. Early Alarm and Path Tracking
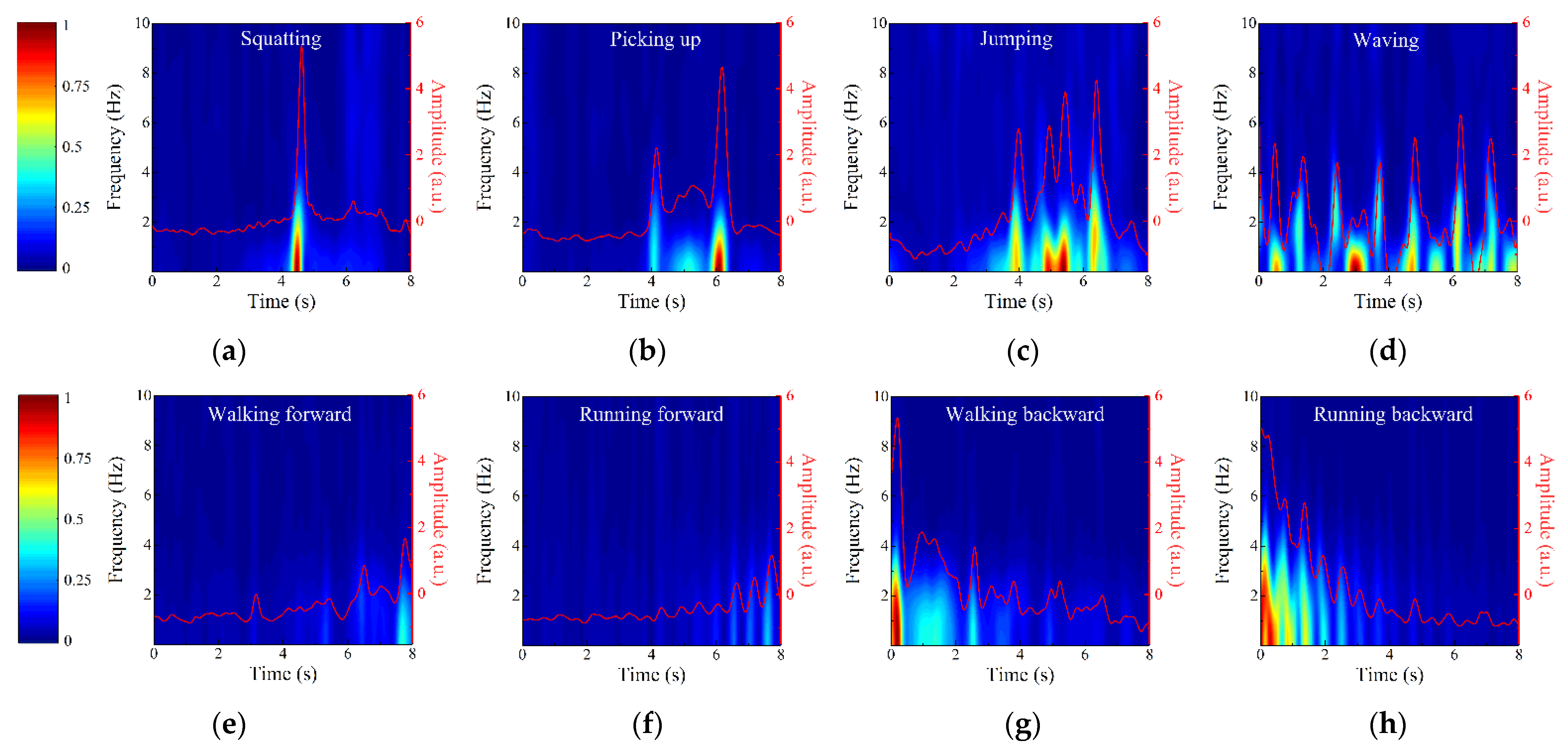
3.2. Action Recognition
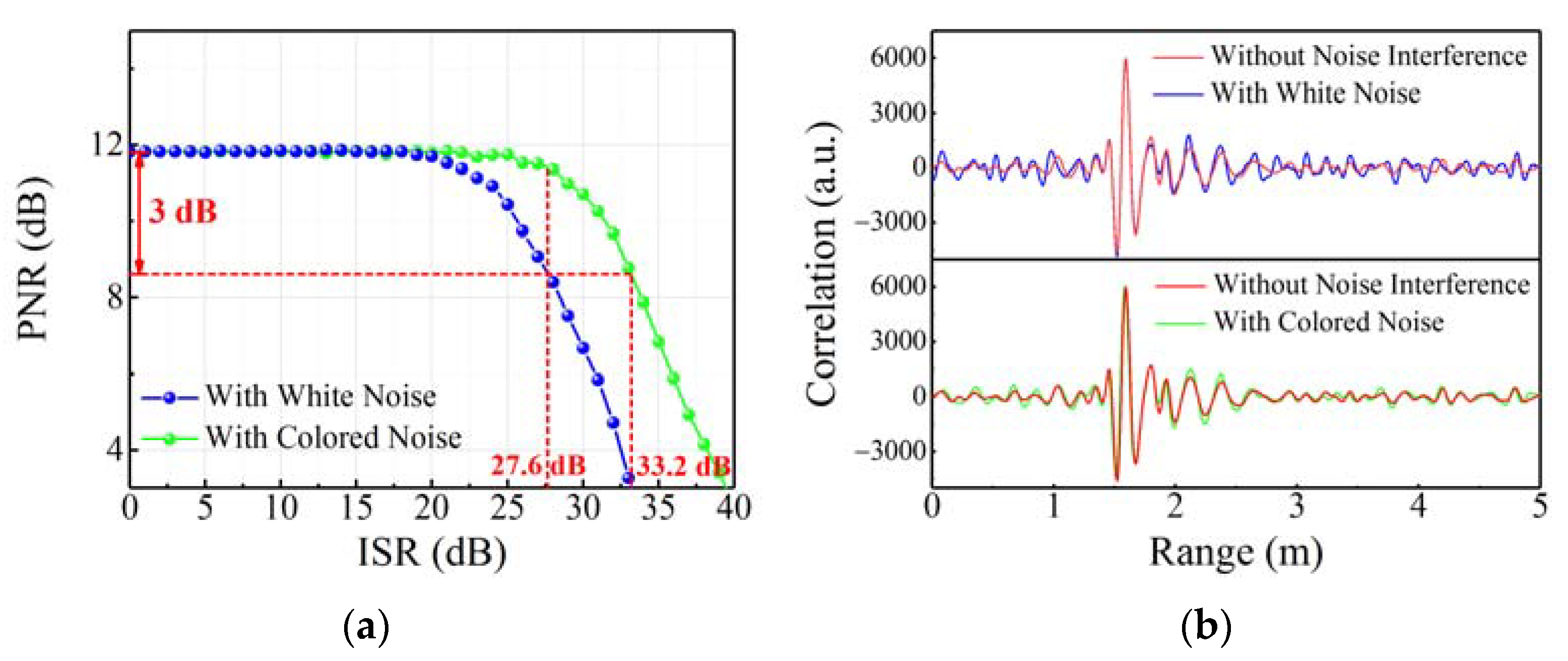
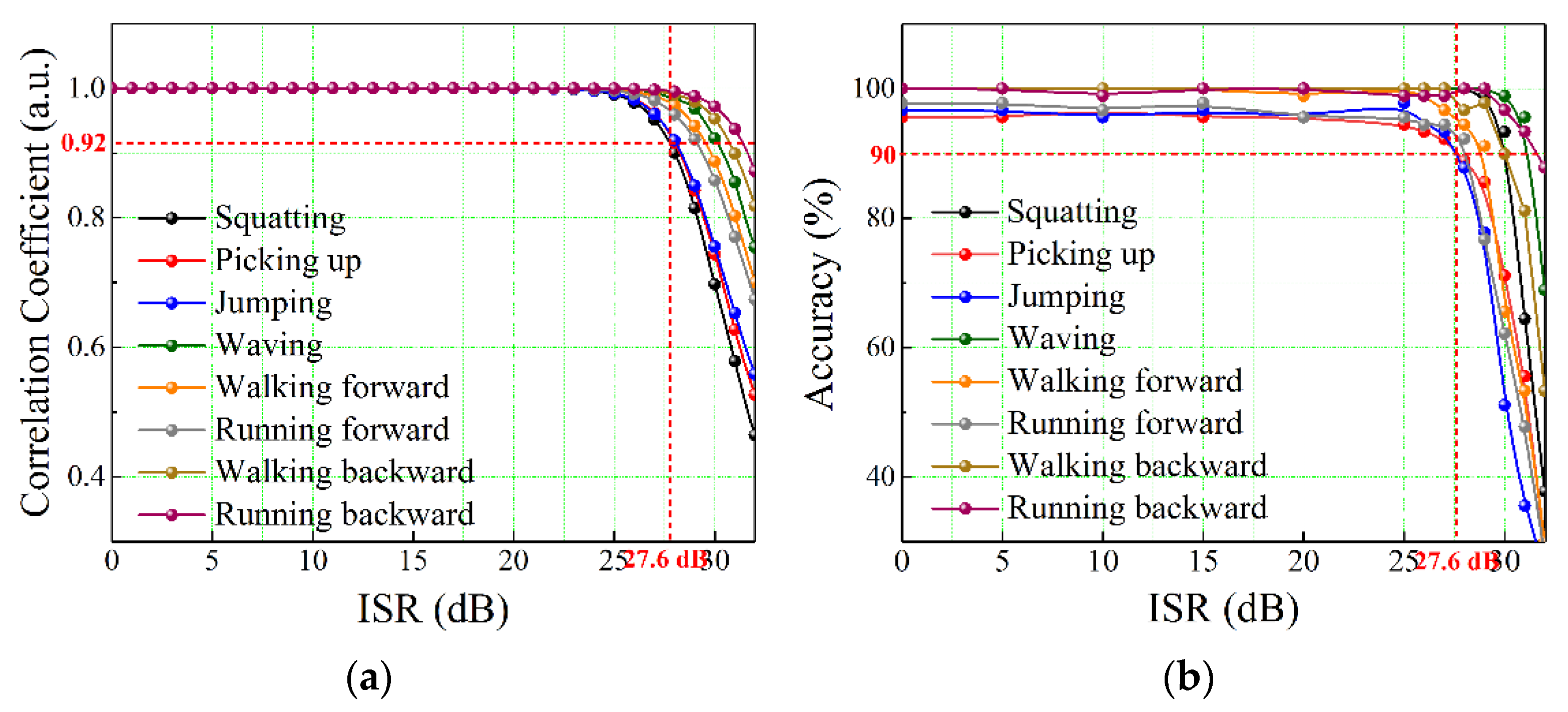
3.3. Anti-Jamming Ability Proof
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Aldalahmeh, S.A.; Hamdan, A.M.; Ghogho, M.; McLernon, D. Enhanced-Range Intrusion Detection Using Pyroelectric Infrared Sensors. In Proceedings of the Sensor Signal Processing for Defence (SSPD), Edinburgh, UK, 22–23 September 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Sahoo, K.C.; Pati, U.C. IoT based intrusion detection system using PIR sensor. In Proceedings of the 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, India, 19–20 May 2017; pp. 1641–1645. [Google Scholar] [CrossRef]
- Wang, J.-X. Research and implementation of intrusion detection algorithm in video surveillance. In Proceedings of the International Conference on Audio, Language and Image Processing (ICALIP), Shanghai, China, 11–12 July 2016; pp. 345–348. [Google Scholar] [CrossRef]
- Chen, H.; Chen, D.F.; Wang, X.F. Intrusion detection of specific area based on video. In Proceedings of the 9th International Congress on Image and Signal Processing, BioMedical Engineering and Informatics (CISP-BMEI), Datong, China, 15–17 October 2016; pp. 23–29. [Google Scholar] [CrossRef]
- Yang, S.; Bu, F.L. Design of Frequency Adjustable Pulse in Intelligent Electronic Fence System. In Proceedings of the 2nd International Conference on Telecommunications and Communication Engineering, Beijing, China, 28–30 November 2018; pp. 344–347. [Google Scholar] [CrossRef]
- Tang, Z.J.; Liu, P.L.; Luo, Q.; Ye, Z.F. Main Control System Design for Balanced Tension-Type Electronic Fence. Appl. Mech. Mater. 2014, 687, 349–352. [Google Scholar] [CrossRef]
- Tang, Z.J.; Li, T.L.; Leng, X.N. The hybrid time-frequency detection method based on EEMD for balanced tension-type electronic fence. Appl. Technol. Innov. 2015, 11, 52–62. [Google Scholar] [CrossRef][Green Version]
- Sun, X.R.; Ma, H.L.; Du, X.H. Round-Guard System Based on the Vibration Cable Transducer. Adv. Mater. Res. 2011, 383, 1891–1894. [Google Scholar] [CrossRef]
- Hong, X.B.; Wu, J.; Zuo, C.; Liu, F.S.; Guo, H.X.; Xu, K. Dual Michelson interferometers for distributed vibration detection. Appl. Opt. 2011, 50, 4333–4338. [Google Scholar] [CrossRef]
- Pi, S.H.; Wang, B.J.; Jia, B.; Sun, Q.; Xiao, Q.; Zhao, D. Intrusion localization algorithm based on linear spectrum in distributed Sagnac optical fiber sensing system. Opt. Eng. 2015, 54, 085105. [Google Scholar] [CrossRef]
- Liu, K.; Tian, M.; Jiang, J.F.; An, J.C.; Xu, T.H.; Ma, C.Y.; Pan, L.; Wang, T.; Li, Z.C.; Zheng, W.J.; et al. An Improved Positioning Algorithm in a Long-Range Asymmetric Perimeter Security System. J. Lightw. Technol. 2016, 34, 5278–5283. [Google Scholar] [CrossRef]
- Zhan, Y.G.; Song, Z.K.; Sun, Z.Y.; Yu, M.H.; Guo, A.J.; Feng, C.H.; Zhong, J.X. A distributed optical fiber sensor system for intrusion detection and location based on the phase-sensitive OTDR with remote pump EDFA. Optik 2021, 225, 165020. [Google Scholar] [CrossRef]
- Harman, R.K. Intrepid MicroTrack leaky cable sensor. In Proceedings of the 36th Annual IEEE International Carnahan Conference on Security Technology, Atlantic City, NJ, USA, 24 October 2002; pp. 191–197. [Google Scholar] [CrossRef]
- Guan, Q.; Lu, H.M.; Chen, C.C.; Wang, K.B. Research on human intruder detection and localization based on LCX sensor. Int. J. RF Microw. Comput. Aided Eng. 2019, 29, e21484. [Google Scholar] [CrossRef]
- Guan, Q.; Lu, H.M.; Wang, K.B.; Chen, C.C. A Novel Approach for Intruder Localization Based on Leaky Coaxial Cable Sensor with IQ Demodulation and Synchronous Subtraction. Appl. Comput. Electromagn. Soc. J. 2018, 33, 1483–1488. [Google Scholar]
- Guan, Q.; Chen, C.C.; He, C.X. A novel sensor using VHF zigzag-slotted leaky coaxial cable for intruder localization. Microw. Opt. Technol. Lett. 2018, 60, 634–639. [Google Scholar] [CrossRef]
- Guan, Q.; Lu, H.M.; Chen, C.C.; He, C.X. Multiple Human Targets Detection and Localization Using Leaky Coaxial Cable Sensing Technique. Appl. Comput. Electromagn. Soc. J. 2018, 33, 973–978. [Google Scholar]
- Liu, Y.; Guan, Q.; Lu, H.M.; Tan, K.B.; Lan, Y.R. A New Location Method of Leaky Coaxial Cable Sensor Based on Pulse Compression. J. Microw. 2018, 34, 79–83. (In Chinese) [Google Scholar] [CrossRef]
- Harman, K.; Hodgins, B. The next generation of GUIDAR technology. In Proceedings of the 38th Annual IEEE International Carnahan Conference on Security Technology, Albuquerque, NM, USA, 11–14 October 2004; pp. 169–176. [Google Scholar] [CrossRef]
- Harman, K.; Hodgins, B.; Patchell, J. Experience with Ranging Buried Cable Sensing. In Proceedings of the 41st Annual IEEE International Carnahan Conference on Security Technology, Ottawa, ON, Canada, 8–11 October 2007; pp. 193–200. [Google Scholar] [CrossRef]
- Foley, E.; Harman, K.; Cheal, J. Improving intrusion detection radar. IEEE Aerosp. Electron. Syst. Mag. 2002, 17, 22–27. [Google Scholar] [CrossRef]
- Butler, W.; Poitevin, P.; Bjomholt, J. Benefits of Wide Area Intrusion Detection Systems using FMCW Radar. In Proceedings of the 41st Annual IEEE International Carnahan Conference on Security Technology, Ottawa, ON, Canada, 8–11 October 2007; pp. 176–182. [Google Scholar] [CrossRef]
- Martínez, F.P.; Galeano, F.C. New microwave sensors for intrusion detection systems. In Proceedings of the IEEE 33rd Annual International Carnahan Conference on Security Technology (Cat. No.99CH36303), Madrid, Spain, 5–7 October 1999; pp. 49–53. [Google Scholar] [CrossRef]
- Xiong, D.D.; Cui, G.L.; Feng, L.F.; Yi, W.; Kong, L.J.; Yang, X.B. A location and tracking method for indoor and outdoor target via multi-channel phase comparison. In Proceedings of the 20th International Conference on Information Fusion (Fusion), Xi’an, China, 10–13 July 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Im, Y.-T.; Park, S.-O. An FMCW and chirp pulse-doppler radar system for surveillance in X-band. Microw. Opt. Technol. Lett. 2013, 55, 474–479. [Google Scholar] [CrossRef]
- Rosin, D.P.; Rontani, D.; Gauthier, D.J. Ultrafast physical generation of random numbers using hybrid Boolean networks. Phys. Rev. E 2013, 87, 040902. [Google Scholar] [CrossRef] [PubMed]
- Okada, K.; Hashimoto, K.; Shibata, T.; Nagaki, Y. Optical cable fault location using correlation technique. Electron. Lett. 1980, 16, 629–630. [Google Scholar] [CrossRef]
- Sharma, C.R.; Furse, C.; Harrison, R.R. Low-Power STDR CMOS Sensor for Locating Faults in Aging Aircraft Wiring. IEEE Sensors J. 2007, 7, 43–50. [Google Scholar] [CrossRef]
- Zhang, Y.F.; He, Y.; Yang, F.; Luo, Y.; Chen, W.B. Three-dimensional imaging lidar system based on high speed pseudorandom modulation and photon counting. Chin. Opt. Lett. 2016, 14, 111101. [Google Scholar] [CrossRef][Green Version]
- She, C.-Y.; Abo, M.; Yue, J.; Williams, B.P.; Nagasawa, C.; Nakamura, T. Mesopause-region temperature and wind measurements with pseudorandom modulation continuous-wave (PMCW) lidar at 589 nm. Appl. Opt. 2011, 50, 2916–2926. [Google Scholar] [CrossRef]
- Aftanas, M.; Zaikov, E.; Drutarovský, M.; Sachs, J. Through Wall Imaging of the Objects Scanned by M-sequence UWB Radar System. In Proceedings of the 18th International Conference Radioelektronika, Prague, Czech Republic, 24–25 April 2008; pp. 1–4. [Google Scholar] [CrossRef]
- Xia, Z.H.; Fang, G.Y.; Ye, S.B.; Zhang, Q.Y.; Chen, C.; Yin, H.J. A novel handheld pseudo random coded UWB radar for human sensing applications. IEICE Electron. Exp. 2014, 11, 20140981. [Google Scholar] [CrossRef]
- Gong, L.S.; Zhang, J.G.; Sang, L.X.; Liu, H.F.; Wang, Y.C. The Unpredictability Analysis of Boolean Chaos. IEEE Trans. Circuits Syst. II Exp. Briefs 2020, 67, 1854–1858. [Google Scholar] [CrossRef]
- Zhang, R.; Cavalcante, H.L.D.D.S.; Gao, Z.; Gauthier, D.J.; Socolar, J.E.S.; Adams, M.M.; Lathrop, D.P. Boolean chaos. Phys. Rev. E 2009, 80, 045202. [Google Scholar] [CrossRef] [PubMed]
- Xu, H.; Qiao, J.; Zhang, J.G.; Han, H.; Li, J.X.; Liu, L.; Wang, B.J. A High-Resolution Leaky Coaxial Cable Sensor Using a Wideband Chaotic Signal. Sensors 2018, 18, 4154. [Google Scholar] [CrossRef] [PubMed]
- Svecová, M.; Kocur, D.; Zetik, R. Object Localization Using Round Trip Propagation Time Measurements. In Proceedings of the 18th International Conference Radioelektronika, Prague, Czech Republic, 24–25 April 2008; pp. 1–4. [Google Scholar] [CrossRef]
- Xu, H.; Li, L.Q.; Li, Y.; Zhang, J.G.; Han, H.; Liu, L.; Li, J.X. Chaos-Based Through-Wall Life-Detection Radar. Int. J. Bifurc. Chaos 2019, 29, 1930020. [Google Scholar] [CrossRef]
- Li, X.-Y.; Lin, Z.-X. Face Recognition Based on HOG and Fast PCA Algorithm. In Proceedings of the Fourth Euro-China Conference on Intelligent Data Analysis and Applications, Málaga, Spain, 9–11 October 2017; pp. 10–21. [Google Scholar] [CrossRef]
- Chang, C.-C.; Lin, C.-J. LIBSVM: A library for support vector machines. ACM Trans. Intell. Syst. Technol. 2011, 2, 1–27. [Google Scholar] [CrossRef]
- Long, Y.; Du, Z.-J.; Wang, W.-D.; Zhao, G.-Y.; Xu, G.-Q.; He, L.; Mao, X.-W.; Dong, W. PSO-SVM-Based Online Locomotion Mode Identification for Rehabilitation Robotic Exoskeletons. Sensors 2016, 16, 1408. [Google Scholar] [CrossRef]





| Intrusion Detection Technologies | Intruder Location | Multiple Intrusion Detection | Intruder Tracking Inside the Area | Ambient Interference | |
|---|---|---|---|---|---|
| Infrared Sensor | Active | No | No | No | Visibility and Floating Debris |
| Passive | Yes | Yes | Yes | Temperature and Large Shields | |
| Video Surveillance System | Yes | Yes | Yes | Visibility and Obstructions | |
| Electronic Fence | Pulsed | Yes | No | No | Humidity in Wet Weather |
| Tension | No | Animal Climbing | |||
| Vibration Cable Transducer | No | No | No | Vehicle Vibration and Animal Climbing | |
| Optical Fiber Vibration Sensor | Yes | Yes | No | Ambient Vibration | |
| LCX Sensor | Yes | Yes | No | Electromagnetic Waves | |
| Radar Sensor | Yes | Yes | Yes | Electromagnetic Waves | |
| Pred/True (%) | (a) | (b) | (c) | (d) | (e) | (f) | (g) | (h) |
|---|---|---|---|---|---|---|---|---|
| (a) | 100 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| (b) | 0 | 95.56 | 4.44 | 0 | 0 | 0 | 0 | 0 |
| (c) | 1.11 | 2.22 | 96.67 | 0 | 0 | 0 | 0 | 0 |
| (d) | 0 | 0 | 0 | 100 | 0 | 0 | 0 | 0 |
| (e) | 0 | 0 | 0 | 0 | 100 | 0 | 0 | 0 |
| (f) | 0 | 0 | 0 | 0 | 2.22 | 97.78 | 0 | 0 |
| (g) | 0 | 0 | 0 | 0 | 0 | 0 | 100 | 0 |
| (h) | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 100 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, H.; Li, Y.; Ma, C.; Liu, L.; Wang, B.; Li, J. A Combined Sensing System for Intrusion Detection Using Anti-Jamming Random Code Signals. Sensors 2022, 22, 4307. https://doi.org/10.3390/s22114307
Xu H, Li Y, Ma C, Liu L, Wang B, Li J. A Combined Sensing System for Intrusion Detection Using Anti-Jamming Random Code Signals. Sensors. 2022; 22(11):4307. https://doi.org/10.3390/s22114307
Chicago/Turabian StyleXu, Hang, Yingxin Li, Cheng Ma, Li Liu, Bingjie Wang, and Jingxia Li. 2022. "A Combined Sensing System for Intrusion Detection Using Anti-Jamming Random Code Signals" Sensors 22, no. 11: 4307. https://doi.org/10.3390/s22114307
APA StyleXu, H., Li, Y., Ma, C., Liu, L., Wang, B., & Li, J. (2022). A Combined Sensing System for Intrusion Detection Using Anti-Jamming Random Code Signals. Sensors, 22(11), 4307. https://doi.org/10.3390/s22114307






