Blockchain for Future Wireless Networks: A Decade Survey
Abstract
:1. Introduction
1.1. Motivations and Novelty
- Despite the essential benefits of WN, it is still imperiled by various security and privacy issues that impede its widespread applications in smart homes, smart cities, smart vehicular communication, and many more.
- Many researchers across the globe have provided their resistant solutions to confront the security and privacy issues of WN. However, the attackers are constantly upgrading their motives and formulating newer attacks that are challenging to tackle with the existing solutions.
- There is an imperative need for a technology, i.e., blockchain, which can overcome the security and privacy prospect of the WN by offering an immutable ledger and a decentralized and transparent network. However, the scientific community has not fully explored the integration of blockchain into the WN. Mostly the existing survey presents the integration of blockchain in a specific WN application and explores a few WN-based security attacks.
- This motivates us to write an exhaustive survey that investigates different security and privacy aspects of WN along with their blockchain-based solution. In addition, we proposed a taxonomical representation of different WN attacks and their possible solutions. Further, the proposed blockchain and a 6G-enabled WN architecture encourage to incorporate blockchain in every WN application.
1.2. Survey Contributions
- This paper presents a systematic and comprehensive survey on WNs by exploring the security and privacy issues in various WN-enabled smart applications. It also bridges the gap between security and privacy issues by utilizing blockchain-based solutions.
- A taxonomy is proposed that contains a detailed description of security attacks and their countermeasures with the available security and privacy solutions of WNs.
- A blockchain-based WN architecture is proposed with layer-wise in-depth discussion.
- Finally, the paper highlights several open issues and research challenges for blockchain-based security and privacy solutions in WN.
1.3. Highlights of the Proposed Survey
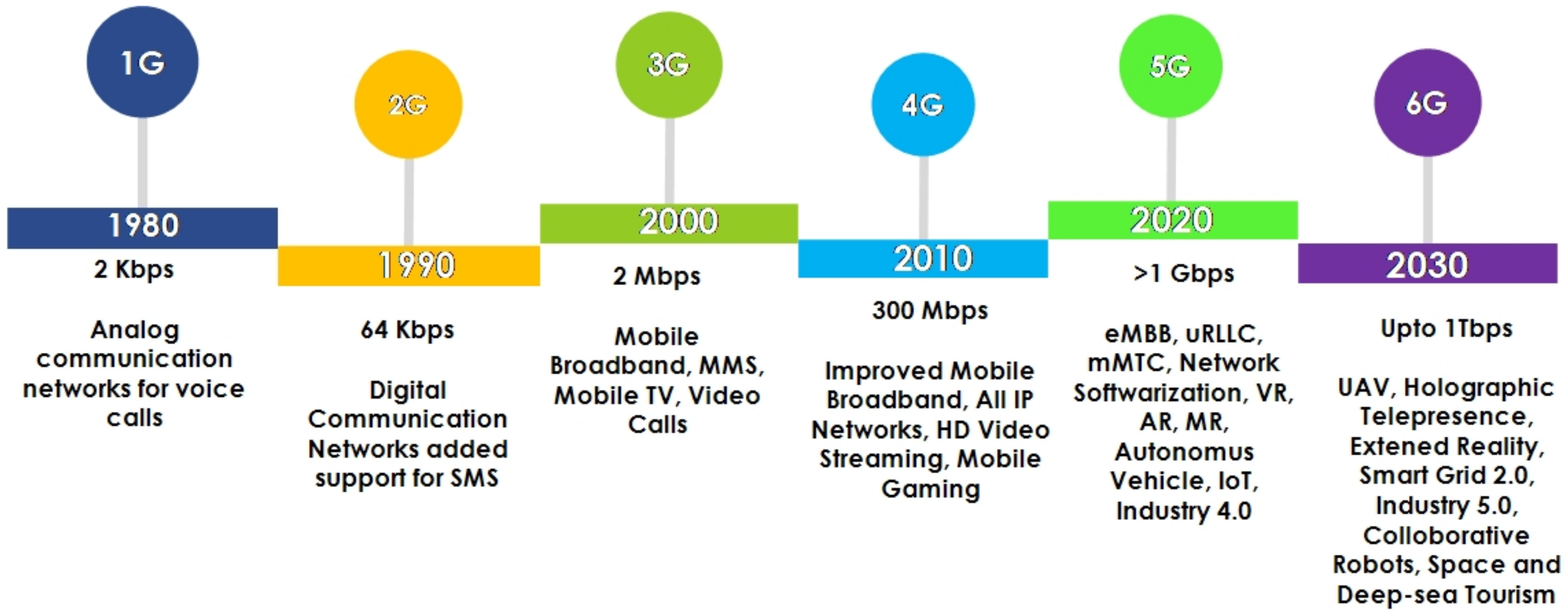
- Identifying the security and privacy issues with a different generation of WNs, i.e., 1G, 2G, 3G, 4G, and 5G, along with their existing solutions.
- A comprehensive explanation of different attacks in modern generation wireless networks, i.e., 4G, 5G, and 6G, discussed how they dampen the performance of the WN-based applications and their existing solutions proposed by the research community across the globe.
- Further, the influence of blockchain technology is explored to alleviate the security and privacy issues from WN-based applications.
- Then, an exhaustive comparative analysis of the existing survey with the proposed survey is formulated to showcase the importance of the proposed survey.
- The OSI model is a core on which the entire WN is operated; therefore, we explore active and passive attacks in each layer of the OSI along with their blockchain-based solutions. To support that, we propose an exhaustive taxonomy to provide an illustrative representation of each attack in the OSI model.
- Moreover, we present a blockchain and 6G-enabled WN architecture to confront the security and privacy issues of the WN. Then, the proposed architecture is evaluated with different performance metrics, such as packet loss ratio, scalability, and latency.
- Lastly, we mention open issues and research challenges in blockchain-based WNs to encourage other researchers to find novel solutions to mitigate the security and privacy challenges of the WNs.
1.4. Methods and Materials
1.5. Key Take-Aways
- The reader gets an idea of detailed concepts of WNs and their evolution from a security and privacy perspective.
- This article presents how blockchain handles security and privacy issues in WNs for various smart applications, for instance, traffic monitoring, smart cities, smart home, smart grids, smart industries etc.
- Readers/researchers can get the gist of possible security attacks in WNs that resists blockchain.
- This paper delivers the open research issues and future directions for further enhancement in WNs while using blockchain technology.
1.6. Survey Organization
2. Background
2.1. Wireless Networks: An Overview
2.2. Security in Wireless Networks (From 4G to 6G)
- Authentication—A standard example of WN is the internet, where tons of internet services serve the end users. A sender sends confidential information from these services to the receiver, which in return, the sender expects that the information reaches the correct receiver. Thus, before sending the data, both users have to authenticate themselves for reliable communication. Formally, authentication states that a user has to validate who he/she claims to be with the help of authentication factors, such as a strong password, personal identification number (PIN), one-time password (OTP), and biometrics. However, the attackers can attack the single layer authentication; for example, a password can be cracked using dictionary attacks, OTP can be brute-forced, and biometrics can be manipulated using masterprints or techniques, such as image processing, which generates similar finger prints of the authentic user. Therefore, multi-layer authentication systems are adopted by several organizations to secure their sensitive resources and provide seamless services to the users without any security hindrances.
- Authorization—Once the user in the public internet is authenticated, he/she can utilize various internet applications. However, from the security perspective, an attacker can impersonate the authentic user to maliciously read and write confidential information of the validated user or may use the services that are not meant for him. Therefore, there is a need to regulate access control mechanisms after authenticating the user, permitting only authorized users to access the system’s services and resources. For that, the administrator has to assign roles and permission to the legitimate user in the access control list. For example, a person can authenticate himself by inserting a username and password into the website; once authenticated, based on the roles and permission assigned, he can access or deny the further services in the website. This helps in poising the security and privacy of the WN-based application.
- Encryption—Authentication and authorization help in preserving the privacy of the system. For instance, a web application utilizes the WN to transmit messages from one user to another. One can guarantee that the users who are enrolled with the application are authenticated and authorized to use this service. This is because they are validated and verified by the authentication scheme and authorization mechanism prior to using this application. Nevertheless, the security is violated when the message is in transit; an adversary can access the transit message and try to manipulate it, disobeying the data integrity principles. Therefore, there is a need for incorporating proper encryption standards that obfuscate the message in a way that is not readable by the attackers. There are various encryption methods available, such as public and private cryptosystems comprising advanced encryption standards (AES), Rivest–Shamir–Adleman (RSA), blowfish, triple data encryption standard (DES), and many more. Further, to augment the user’s security and privacy, encryption algorithms can employ hashing algorithms, such as secure hash algorithm (SHA) and message digest, that strengths the WN security.
- Characteristic of channel—The aforementioned design factors are for higher-layer WN applications, but with the current exploration of radio frequencies, the attackers dwell in the physical layer security, wherein they exploit radio waves to intercept the ongoing communication. Thus, it is indispensable to understand the wireless channel and secure it by analyzing characteristics, such as bandwidth, data rates, channel quality indicators, i.e., signal-to-noise ratio (SNR), the reference signal received power and received signal strength indicators of the channel. Furthermore, a message generated at the sender machine has to pass through the dynamic wireless channel, which is time variant and has a lot of obstructions, such as interference, multipath propagation, delay, attenuation, path loss, and fading, which deteriorates the data rates of the WN. Therefore, an attacker tries to investigate such indicators to proliferate their physical attacks that dampen the performance of the wireless communication. Hence, it is essential to reinforce the wireless channel with effective channel coding, equalization techniques, and embracing physical layer security.
- Secrecy capacity—The notion of security and privacy in WN is not limited to studying the application and middle layer security, but also needs to investigate different malicious intent propagated at the physical layer. One such mechanism is the secrecy capacity, which is intrinsically associated with the channel capacity, where the channel is the broadcasting or transmitting the message from the legitimate user. Here the intended receiver is treated as an illegitimate user or an eavesdropper who is trying to intercept and decode the message from the legitimate user. An eavesdropper can decode the message if the channel gain between the transmitter and an eavesdropper is higher than the channel gain between the transmitter and receiver. This also means that the eavesdropper has a higher channel capacity resulting in decoding the messages of the users in close proximity. Therefore, as a network analyst, it is imperative to analyze channel gains and data rates to eliminate the eavesdropper from future communication.

2.2.1. Security in 4G
2.2.2. Security in 5G
2.2.3. Security in 6G
2.3. Blockchain Technology
2.3.1. Blockchain Hierarchy
2.3.2. Integration of Blockchain and WNs
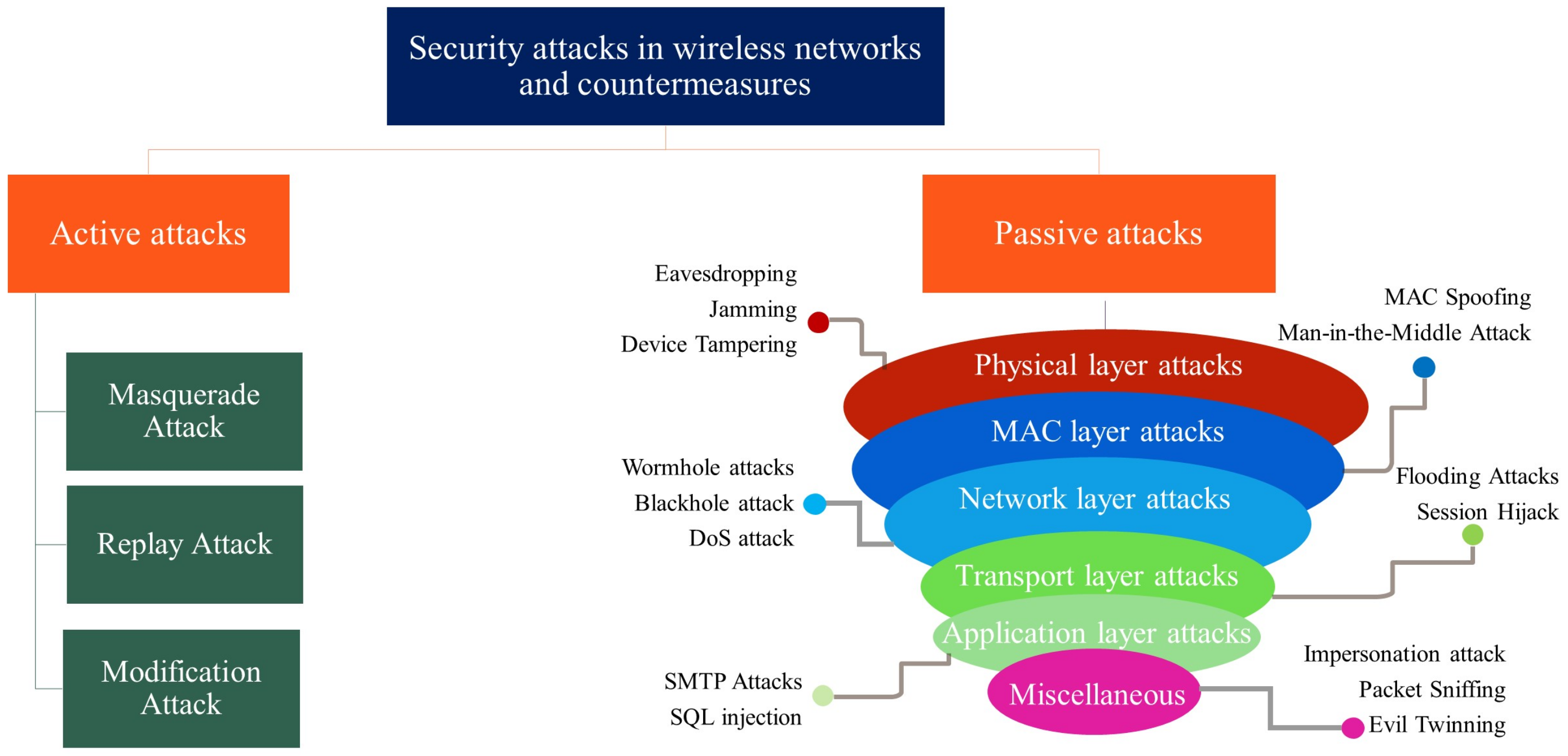
3. The Proposed Taxonomy for Security Attacks and Countermeasures
3.1. Active Attacks
- Masquerade attack—A malicious user behaves like an authorized person to deprive the resources of the system [77]. They can capture authentication sequences and legitimately retrieve the access privileges to the target system. This attack creates a fake network identity that affects the financial transaction systems by phishing emails [78]. Furthermore, it makes counterfeit servers and sends data-stealing malware for their own malicious usage. In [79], the author proposed a signal strength fluctuation model to perform significant testing of masquerade attacks in a mobile ad hoc network (MANET). Moreover, using a masquerade attack, a malicious user can hack and remotely control modern vehicles. For that, ref. [80] proposed an authentication protocol that protects the electronic control units. Furthermore, Li et al. [81] introduced a blockchain-based solution using renewable hash chains that resist masquerade attacks in the identity authentication approach.
- Replay attack—In this attack, an intruder intercepts the communication and captures user data, then modifies it and sends it back to the destination to misdirect him [82]. It creates duplicate transactions in-network and gains information. Secure socket layer (SSL) or transport layer security (TLS) protocols, one-time passwords, timestamp methods, and session key encryption methods are used to prevent replay attacks [83]. Multiple researchers offer various solutions to prevent replay attacks for applications, such as vehicular ad hoc networks (VANETs), mobile ad hoc networks (MANETs), and IoT networks. For that, the author of [84] analyzed the existing schemes that prevent replay attacks in VANETs. In [85], the author proposed a model that overcomes replay attack breaches in authentication conditions of a smart city. In identity authentication scheme [81], Li et al. proposed a timeout mechanism that prevents replay attacks. Apart from these, Yavari et al. [86] introduced shared session values and freshly random values that create different session messages, which can be used to mitigate the replay attack probability.
- Modification attack—An attacker modifies some portion of the message transmitted from sender to receiver, which results in delivering corrupted and delayed messages [82]. It affects the data integrity and re-configuring of system hardware. A malicious user performs three types of modifications, i.e., change information, insert information, and remove existing information. To prevent this attack, encryption algorithms, traffic padding, and various messaging techniques, such as authentication code, sequence numbers, and checksums, are used [87]. Many researchers work to mitigate the issue of modification attacks in WN security. For that, [88] discussed how to overcome price modification attacks in smart grid applications. In [89], Al-shareeda et al. discussed a existing method that suppresses the modification of attack in VANETs. Moreover, Lin et al. [90] proposed a blockchain-based message authentication code and group signature mechanism that eliminates the effect of modification attacks for smart homes systems.
| Layer | Attacks | Countermeasures | Ref |
|---|---|---|---|
| Physical layer | Eavesdropping attack |
| [91,92,93] |
| Jamming |
| [94,95,96] | |
| Device tampering |
| [97,98] | |
| MAC layer | MAC Spoofing |
| [99,100,101] |
| MiTM attack |
| [102,103,104,105] | |
| Network layer | Wormhole attack |
| [106,107,108] |
| Blackhole attack |
| [109,110,111] | |
| DoS attacks |
| [112,113,114] | |
| Transport layer | Flooding attacks |
| [115,116] |
| Session Hijack |
| [117,118,119] | |
| Application layer | SMTP attack |
| [120,121] |
| SQL injection |
| [122,123] |
3.2. Passive Attacks
- Physical layer attacks—This layer consists of data transmission, signal detection, encoding, modulation, and frequency selection tasks in the wireless medium [124,125]. A detailed description of each passive attack on the physical layer is given as follows.
- Eavesdropping attack—It is also referred to as wireless sniffing, where an attacker eavesdrops over ongoing communications between sender and receiver [126]. This attack uses an eavesdropping device that monitors network activity, a listening port that records phone conversations, and a tapping transmission link. It silently impacts the performance of the WN in terms of privacy loss and identity theft [127]. Various methods are available to shove the eavesdropper from the authentic communication line, such as limiting the resources of the eavesdropper by network segmentation, avoiding opening untrusted links, and applying jammers or beamforming techniques to minimize the signal power of an eavesdropper. For that, many researchers provide various solutions; for example, [128] discussed eavesdropper attacks on 802.11ad mmWave systems. Moreover, ref. [91] prevented eavesdropping on radio-frequency (RF) and free-space optical (FSO) systems. In [92], Shi et al. proposed blockchain-based solution for dynamic honeypot system. They introduced the encryption algorithm RSA 2048-bit that resists eavesdropping attacks in the communication channel. In [93], Cheikhrouhou et al. came up with a blockchain-enabled secure localization algorithm that prevents eavesdropping attacks in IoT applications.
- Jamming—It is a similar attack to the DoS attack, where the adversarial WN nodes obstruct legitimate communication by raising the interference or noise of the signal. It uses severe radio interference that makes the wireless channel busy, interrupts the ongoing communications, and reduces the signal-to-noise ratio (SINR), resulting in loss of communication [129]. It can be prevented with the help of an effective radio resource allocation mechanism [130], anti-jamming systems, cryptographic, and steganography techniques [131]. The authors of [94] overcame the jamming attack in the WNs control system by estimating the channel state estimation of the wireless channel. In [95], the author discussed anti-jamming methods for jamming attacks in VANETs, cognitive radio networks (CRNs), ZigBee networks, and GPS systems. Moreover, in [96] Danish et al. proposed a blockchain-enabled lightweight two-factor authentication mechanism for long-range wide area network (WAN).
- Device tampering—It is the most straightforward way to attack the physical layer by making a modification in a WN device and extracting sensitive data from it [124]. The most popular way to perform this attack is to mirror a port of a medium access control (MAC) layer switch or hub. Once port mirroring is implemented, the data directed to the legitimate user are redirected to the malicious user. Such attacks can be controlled using firewalls, encryption mechanisms, hash-based message authentication code (HMAC), access restriction, and file integrity monitoring [98]. Moreover, Lee et al. [97] proposed blockchain-enabled data tamper-proof gateway architecture for secure resource management in smart home applications.
- MAC layer attacks—The transmission of data packets is controlled by the MAC layer, using remotely shared channels [132]. The possible passive attacks on MAC layer are as follows.
- MAC spoofing—It is a common attack in the MAC layer, where the attacker changes the MAC address of transmitted frames to spoof the security devices and protocols [133]. In this attack, malicious users spread malware, steal user information, and bypass the network access control systems. Encrypted protocols, alert-enabled traffic monitoring, and reverse address resolution protocol prevent MAC spoofing attacks [134]. In [99], the authors presented a comprehensive survey to detect and prevent MAC attacks on monitoring systems. Moreover, ref. [100] proposed a cooperative spoofing attack detection technique to identify MAC attacks. In [101], Islam et al. presented a blockchain-based secure data handover approach in non-orthogonal multiple access (NOMA) transmission schemes. They discussed a two-phase encryption algorithm to prevent MAC spoofing in WNs.
- Man-in-the-middle attack (MiTM)—It permits an intruder to eavesdrop and preclude the communication between sender and receiver. Here, attackers modify the information, intercept and replace data between sender and receiver [135,136]. They steal user information such as card details and credentials of an e-commerce site, businesses, and financial applications. This attack makes interception by exploiting address resolution protocol (ARP) and spoofing the MAC addresses to mislead the data frame from their original path [137]. To mitigate the effect of the MiTM attack, various techniques are employed, such as public-key authentication, a WAP encryption mechanism, and the use of a virtual private network (VPN) [138]. The authors of [102] proposed a SQL injection, brute force attack, and cross-site scripting to avoid MiTM attacks. Further, in [103] the authors analyzed the MiTM attack in Wi-Fi networks, where they proposed a secure mechanism to prevent the content addressable memory (CAM) table of the wireless switch from the attackers. Further, Kulkarni et al. [105] discussed how to accomplished MITM attack in HTTPS. They proposed Nebulas blockchain technology-based solution to prevent MITM attacks in internet communication. In [104], Li et al. proposed a blockchain-enabled lightweight digital signature approach to secure UAV communication.
- Network layer attacks—This layer is most vulnerable to various types of network attacks, which are discussed as follows.
- Wormhole attacks—In this attack, the attacker creates a forged link between sender and receiver to drop or modify the data packets. The wormhole hole attack impacts confidentiality, availability, and data integrity [139] in applications such as VANETs, IoT networks, and MANETs. The packet leashes approach is used to prevent and defend against the wormhole attack. Moreover, separate route algorithms, watchdog models, and Delphi techniques are feasible solutions to avoid wormhole attacks [140]. In [106], the authors considered wormhole attacks as traffic attacks and presented trust-enabled techniques that detect and prevent such attacks in MANETs. The authors of [107] analyzed and resolved wormhole attacks in IoT networks by simulating the attacks in an IoT environment using NS2 simulation. In addition, Mohanty et al. [108] discussed security and privacy issues in payment channel network (PCN). They proposed Neo hashed time-lock commitment (n-HTLC) and a key encryption-based protocol that prevents wormhole attacks in the PCN.
- Blackhole attack—In this attack, the router destroys and deletes all the messages that are supposed to forward to the legitimate destination (maybe the next router or intended receiver) [141]. Using this attack, the malicious user isolates the network and drops the incoming packets. To overcome the aforementioned issues, the authors of [142] used a time-based baited approach, and [143] proposed fake route request (RREQ) packets that find blackhole attacks in MANETs. Then, the authors of [109] analyzed various detection methods of blackhole attack [110] and proposed a hidden Markov model approach that prevents the attack in wireless sensor networks. Furthermore, Kudva et al. [111] presented a blockchain-based two-level detection system in the VANET routing protocol. This method eliminates blackhole attacks and calculates a trust score that increases VANET performance.
- DoS attacks—The attacker often floods the data packets to the targeted access point, which shuts down the network and creates a resource starvation attack (DoS) [144]. In a DoS attack, the attacker sends spoofed, ping, and malformed packets to the target network, which slows down the network performance losing connectivity to the device. Using this attack, malicious users target sensitive data of the government, personnel, and the financial department [145]. Limiting broadcasting, protecting endpoints, and rejecting fake traffic using firewalls and routers prevent DoS attacks [146]. The bandwidth prediction technique [147], a simple and light-weight statistical detection and mitigation approach, can also be used to avoid DoS in WN applications [112,148]. Moreover, ref. [112] prevented flooding-based DoS attack in MANETs. Spathoulas et al. [113] proposed the use of lightweight agents in various IoT applications such as smart homes, smart grids, smart industries, etc. that detect DoS attacks. They offer blockchain-based smart contracts that resist DoS attacks in IoT botnets and ensure data integrity. As well, Hewa et al. [114] presented a security service blockchain (SSB) solution that mitigates DoS attacks in network slice broker.
- Transport layer attacks—An end-to-end connection set-up is done for transferring the data packets, congestion, and flow control in the transport layer [149]. It uses transmission control protocol (TCP) and user datagram protocol (UDP). TCP is used for reliable data transmission while UDP reduces the overhead and latency. Due to their security vulnerability, these protocols suffer from flooding and session hijack attacks.
- Flooding attacks—TCP sends numerous ping requests in this type of attack, whereas UDP sends several UDP packets. It creates network congestion to legitimate traffic and makes the system unresponsive [150]. Malicious users perform this attack using route requests (RREQ) or data flooding. A flooding attack is prevented by configuring the firewall and installing an intrusion prevention system (IPS) to identify network traffic patterns [151]. The authors of [152,153] presented TCP SYN flooding (half-open attack) prevention and mitigation techniques in a WN-based software-defined network. Moreover, ref. [115] proposed an OpenFlow-based TCP SYN authentication approach that overcomes the issue of flooding. Zhu et al. [116] proposed a decentralized blockchain solution that provides security in named data networking (NDN) of things by mitigating flooding attacks and data phishing.
- Session hijack—In this attack, a session is taken away by an attacker between sender and receiver. In addition, the attacker takes off the victim’s session and behave like a legitimate user over the communication [154]. Session sniffing, cross-site scripting, and predictable sessions token ID are the most responsible parameters that perform session attacks. The adverse effect of this attack deteriorates the security of WN systems; for example, the attack can authenticate malicious users for banking systems, commits identity theft, and steal web server and enterprise data [155]. Encryption algorithm, user authentication scheme, secure cookies, ciphering the packets, internet protocol security (IPSec), and SSL approaches are used to prevent session hijacking [156]. The authors of [117] discussed various techniques to avoid session hijacking, and ref. [118] provided a proxy server that overcame the session hijacking problem on the web server. Bera et al. [119] proposed a blockchain-based access control scheme that detects UAVs and mitigates session hijacking on the Internet of drone environment (IoD).
- Application layer attacks—A user interface layer with file transfer protocol (FTP) and real-time transport protocol (RTP) delivers applications and services to the end-user to maintain QoS.
- Simple mail transfer protocol (SMTP) attacks - Here, the connection between the mail server and the attacker’s machine is exploited, wherein the server sends the web banner (HTTP version, encoding style, server version, etc.) back to the attacker side [157] Consequently, the attackers can find valuable information about the application using this web banner. The malicious user performs this attack by sending phishing emails and spam messages. The user’s SMTP server continues sending multiple emails to other servers until that server crashes. This happens because there is no strong access control that restricts the device’s physical access, due to which the SMTP server cannot withstand the attack. Employing SSL, TLS, and inserting a security layer into the SMTP server prevents this attack [120]. To do so, Chaudhary et al. [121] proposed a cryptocurrency and blockchain-enabled email system that prevents SMTP attacks and controls mail spamming.
- SQL injection—In structured query language (SQL) injection, attackers parse SQL commands in the SQL database and gain unauthorized access to several websites [158]. Malicious users retrieve confidential information from database tables, alter those tables, and drop it. To alleviate the risk of SQL injection, one can make more than one database user account, deploy a secure web applications firewall, limit privileges, and add input validation [159]. In [123,160], the author discussed the SQL injection prevention technique for the content delivery system, for which they used an obfuscation technique to secure their database queries. Furthermore, Tanrıverdi et al. [122] introduced a blockchain-enabled signature-based detection approach in a web attack detection application. This method detects web-based attacks and prevents SQL injection, cross-site scripting (XSS), and command injection techniques. Ref. [123] overcame the issue of SQL injection in the content delivery system.
- Miscellaneous—Apart from the aforementioned attacks, there are some more security threats in WNs, which are as follows.
- Impersonation attack—These attacks are performed by hacktivist and nation-state criminals that have a sophisticated agenda targeting critical organizations [126]. It can be provisioned by creating fake emails on the company site, social media, and e-commerce websites, and then the attackers can impersonate themselves by using those fake emails and accounts [161]. Moreover, they also create fake domains, unauthenticated accounts, and fraud applications to imperil the security schemes applied in the organizations. To prevent impersonation attacks, the user must avoid randomly clicking links on social media sites and emails, confirm the suspicious email request before any financial transaction, and verify a padlock icon next to a URL [162]. Ref. [163] proposed cross-technology impersonation attack prevention techniques for location-based services. Then, ref. [164] provided a solution to overcome the issue of voice impersonation attacks in smart devices.
- Packet sniffing—This attack checks and analyze the data packets that are sent to the WNs [165]. Malicious users create data traffic and extract the packets using unencrypted mechanisms. Attackers illegally steal unencrypted data from companies, advertising agencies, and government agencies using a packet sniffing attack. Network monitoring and scanning activity, use of VPN, prevention of unsecured network, and encrypted messaging prevent packet sniffing attacks [166].
- Evil twinning—Through a wireless access point, the attacker can configure the existing WNs [165]. The access point of the attacker’s system may have a strong signal than any other access point in the network so that the clients can choose the evil twin over the genuine access points [167]. In an evil twin attack, the malicious user creates a fake Wi-Fi network that steals the users’ personal information, log activity, and credentials. To prevent evil twin attacks, visit only secure websites, protect AP using a private security key, and take care of connecting Wi-Fi hot-spots [168].
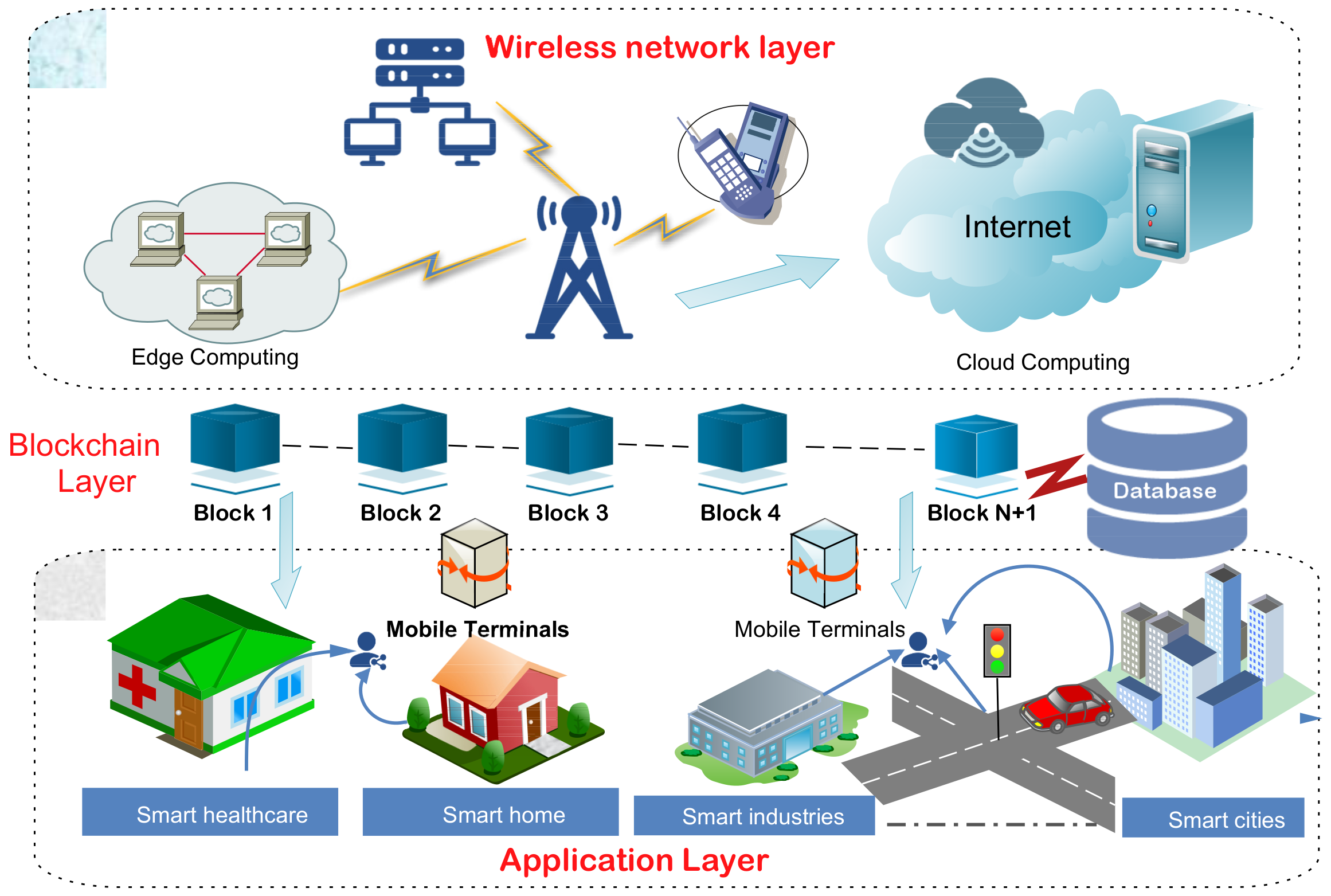
4. Blockchain: A Solution for Security and Privacy in WNs
4.1. Application Layer
4.2. Blockchain Layer
- Access Control: It is a physical layer security that restricts unauthorized users from accessing authorized services running on WN. The conventional access control is centralized and utilizes the standard encryption techniques that lack in providing trust in the WN application. Such a centralized system has a risk of single-point failures and privacy leakages from the key generator schemes. Therefore, as an alternative to centralized access control, trusted blockchain-based access control can help in resolving the above-mentioned issues in WN. To do that, access control permission, i.e., read and write permissions, are only granted to an authorized user, device, and machine. In addition, blockchain uses a smart contract (a set of codes to establish contracts within two parties) to secure the system against any malevolent threat [183].
- Data integrity: Data integrity is another such issue where the attackers tamper with the data of the smart application. As a consequence, the falsified data can mislead the behavior of the smart application. Therefore, storing the data inside the blockchain can ensure that the data are not manipulated. Furthermore, it performs data integrity verification of both the communicating parties by auditing all the transactions that occurred between them [184].
- Authentication: blockchain incorporates authentication capabilities to increase the robustness of the network, which detects and prevents malicious activity in the network resources. Smart contracts perform request authentication to avoid unauthorized access from malicious users [184]. Moreover, it offers a secure and authenticated environment to create virtual WNs (VWNs). Using this network, wireless resource owners can rent their resources, such as infrastructure and a slice of the RF spectrum, to the mobile virtual network operator [10].
4.3. Wireless Network Layer
5. Result Analysis
5.1. Experimental Setup And Tools
5.2. Performance Evaluation
6. Open Issues and Research Challenges
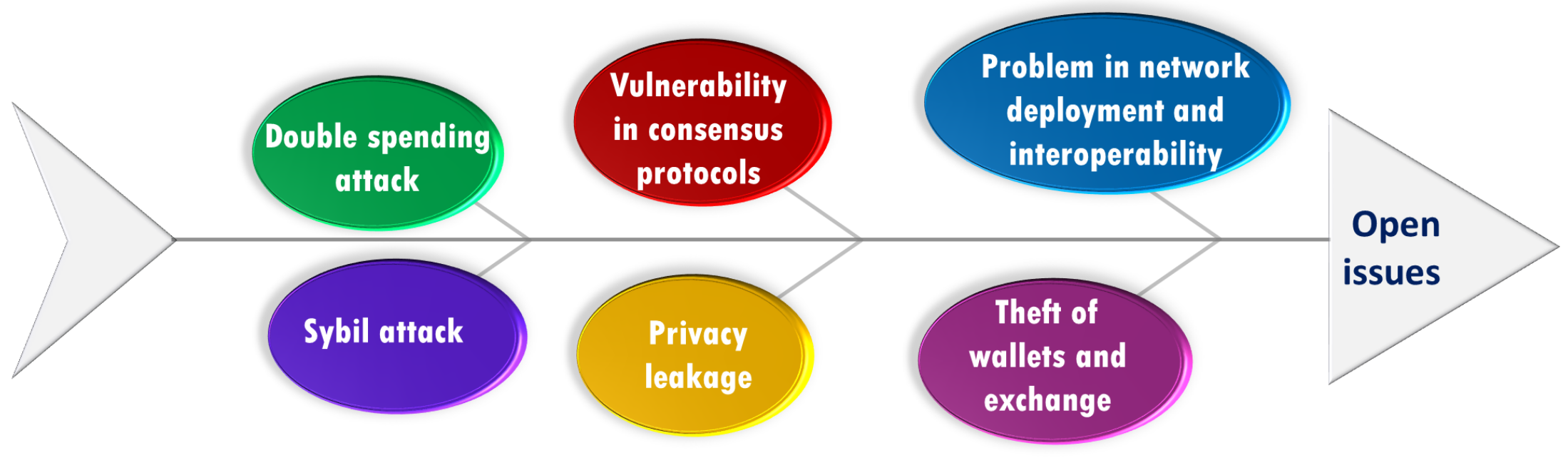
- Double spending attack comprises spending of a single token multiple times by user over blockchain, which needs to be handled to secure WNs [3].
- Transactions are calculated in blockchain before they are accepted or rejected, which is done using consensus protocols. It is vulnerable to malicious activity, so it requires to be tested before deploying in the large-scale WN environment [14].
- Unauthenticated users can access wallets and exchanges using DDoS attacks. They successfully perform the theft of wallets.
- Malicious user controls more than 50% of nodes known as 51% attacks in the blockchain. Therefore, an attacker would be able to manipulate a user’s information by introducing this type of attack [10].
- Sybil attack runs multiple malicious nodes on the network. They make restrictions for new nodes to access and add new blocks in the network [185].
- The problem of network deployment and interoperability comes when blockchain deploys in 5G and beyond networks with SDN, NFV, and MEC technologies that need to mitigate future WNs.
- Blockchain and smart contract in WNs facing leakage of transaction data privacy, smart contract logic privacy, and user privacy, which is also grabbing the attention of researchers [186].
- In permissioned blockchain, when nodes join the network, the system needs to ensure authenticity and authority, which raises concern for authentication and control over data [14].
- In LTE networks, payload and control signalling are required to be encrypted, and the ratio between the amount of data transmitted and encryption overhead needs to be considered [187].
- Memory and resource consumption in large-scale networks is enormous. In addition, data collection, filtering, data sampling, and pre-processing are challenging because of heterogeneous data, which require security assurance and privacy protection [188].
- MIMO fulfills the requirements of services and data rate, but from a security point of view, resource allocation in MIMO needs to be elaborate.
- To improve network traffic and security, it requires further investigations in beamforming [43].
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 1G | First Generation |
| 2G | Second Generation |
| 3G | Third Generation |
| 3GPP | Third Generation Partnership Project |
| 4G | Fourth Generation |
| 5G | Fifth Generation |
| AMF | Access and Mobility management Function |
| ARQ | Automatic Repeat Request |
| CDMA | Code-Division Multiple Access |
| CRC | Cyclic Redundancy Check |
| DoS | Denial of Service |
| D2D | Device to Device |
| eNodeB/eNB | Evolved Node B |
| EPC | Evolved Packet Core |
| EPS | Evolved Packet System |
| ERLLC/eURLLC | Ultra-Reliable Low Latency Communications |
| E-UTRAN | Evolved UMTS Terrestrial Radio Access Network |
| FeMBB | Further Enhanced Mobile Broadband |
| FEC | Forward Error Correction |
| FL | Federated Learning |
| GSM | Global System for Mobile Communications |
| GUTI | Global Unique Temporary Identifier |
| HARQ | Hybrid Automatic Repeat Request |
| IDM | Identity Management |
| IMS | IP Multimedia Subsystem |
| IMSI | International Mobile Subscriber Identity |
| IMT | International Mobile Telecommunications |
| IoE | Internet of Everything |
| IoMT | Internet of Military Things |
| ITU | International Telecommunications Union |
| LTE | Long-Term Evolution |
| MAC | Medium Access Control |
| MIMO | Multiple Input Multiple Output |
| MTC | Machine-Type Communications |
| NAS | Non-Access Stratum |
| NFV | Network Function Virtualization |
| OFMD | Orthogonal Frequency Division Multiplexing |
| P2P | Peer-to-Peer |
| QoS | Quality of Service |
| RAN | Radio Access Network |
| RFID | Radio Frequency Identification |
| RTP | Real-Time Transport Protocol |
| SC | Smart Contract |
| SDN | Software defined Network |
| STBC | Space Time Block Coding |
| SUPI | Subscription Permanent Identifier |
| SUPI | Subscription Permanent Identifier |
| TCP | Transmission Control Protocol |
| UDP | User Datagram Protocol |
| umMTC | Ultra Massive Machine-Type Communications |
| WEP | Wired Equivalent Privacy |
| WiMAX | Worldwide Interoperability for Microwave Access |
| WN | Wireless Network |
| WPA | Wi-Fi Protected Access |
References
- Moya Osorio, D.P.; Ahmad, I.; Sánchez, J.D.V.; Gurtov, A.; Scholliers, J.; Kutila, M.; Porambage, P. Towards 6G-Enabled Internet of Vehicles: Security and Privacy. IEEE Open J. Commun. Soc. 2022, 3, 82–105. [Google Scholar] [CrossRef]
- Chen, L.; Ji, Z.Z. Wireless Network Security: Theories and Applications; Higher Education Press: Beijing, China, 2013. [Google Scholar]
- Porambage, P.; Gür, G.; Osorio, D.P.M.; Liyanage, M.; Gurtov, A.; Ylianttila, M. The Roadmap to 6G Security and Privacy. IEEE Open J. Commun. Soc. 2021, 2, 1094–1122. [Google Scholar] [CrossRef]
- Timeline from 1G to 5G: A Brief History on Cell Phones. Available online: https://www.cengn.ca/timeline-from-1g-to-5g-a-brief-history-on-cell-phones/ (accessed on 12 May 2021).
- Ahmad, I.; Shahabuddin, S.; Kumar, T.; Okwuibe, J.; Gurtov, A.; Ylianttila, M. Security for 5G and Beyond. IEEE Commun. Surv. Tutorials 2019, 21, 3682–3722. [Google Scholar] [CrossRef]
- 4G-LTE/LTE-A Coursework for Computer Networks II. Available online: https://www.gta.ufrj.br/ensino/eel879/trabalhos_vf_2014_2/rafaelreis/background.html (accessed on 2 March 2022).
- Tanwar, S.; Vora, J.; Tyagi, S.; Kumar, N.; Obaidat, M. A systematic review on security issues in vehicular ad hoc network. Secur. Priv. 2018, 1, e39. [Google Scholar] [CrossRef] [Green Version]
- Seddigh, N.; Nandy, B.; Makkar, R.; Beaumont, J.F. Security advances and challenges in 4G wireless networks. In Proceedings of the 2010 Eighth International Conference on Privacy, Security and Trust, Ottawa, ON, Canada, 17–19 August 2010; pp. 62–71. [Google Scholar]
- Kundu, S.; Pados, D.A.; Batalama, S.N. Hybrid-ARQ as a communications security measure. In Proceedings of the 2014 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Florence, Italy, 4–9 May 2014; pp. 5681–5685. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for 5G and beyond networks: A state of the art survey. J. Netw. Comput. Appl. 2020, 166, 102693. [Google Scholar] [CrossRef]
- Makki, S.K.; Reiher, P.; Makki, K.; Pissinou, N.; Makki, S. Mobile and Wireless Network Security and Privacy; Springer US: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Hakak, S.; Khan, W.Z.; Gilkar, G.A.; Imran, M.; Guizani, N. Securing Smart Cities through Blockchain Technology: Architecture, Requirements, and Challenges. IEEE Netw. 2020, 34, 8–14. [Google Scholar] [CrossRef]
- Everything You Need to Know about 5G. Available online: https://www.qualcomm.com/5g/what-is-5g (accessed on 3 March 2022).
- Tahir, M.; Habaebi, M.H.; Dabbagh, M.; Mughees, A.; Ahad, A.; Ahmed, K.I. A Review on Application of Blockchain in 5G and Beyond Networks: Taxonomy, Field-Trials, Challenges and Opportunities. IEEE Access 2020, 8, 115876–115904. [Google Scholar] [CrossRef]
- Tanwar, S.; Vora, J.; Kaneriya, S.; Tyagi, S.; Kumar, N.; Sharma, V.; You, I. Human Arthritis Analysis in Fog Computing Environment Using Bayesian Network Classifier and Thread Protocol. IEEE Consum. Electron. Mag. 2020, 9, 88–94. [Google Scholar] [CrossRef]
- 6G Wireless: What It Is and When It’s Coming. Available online: https://www.spglobal.com/marketintelligence/en/news-insights/latest-news-headlines/6g-wireless-what-it-is-and-when-it-s-coming-networks/ (accessed on 13 May 2021).
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. 5G security: Analysis of threats and solutions. In Proceedings of the 2017 IEEE Conference on Standards for Communications and Networking (CSCN), Helsinki, Finland, 18–20 September 2017; pp. 193–199. [Google Scholar] [CrossRef] [Green Version]
- The Role of Cryptography in Information Security. Available online: https://www.triskelelabs.com/blog/the-role-of-cryptography-in-information-security (accessed on 4 March 2022).
- Cryptography Benefits & Drawbacks. Available online: https://www.tutorialspoint.com/cryptography/benefits_and_drawbacks.htm (accessed on 4 March 2022).
- Liu, X.; Huang, H.; Xiao, F.; Ma, Z. A Blockchain-Based Trust Management With Conditional Privacy-Preserving Announcement Scheme for VANETs. IEEE Internet Things J. 2020, 7, 4101–4112. [Google Scholar] [CrossRef]
- Yaqoob, I.; Salah, K.; Uddin, M.; Jayaraman, R.; Omar, M.; Imran, M. Blockchain for Digital Twins: Recent Advances and Future Research Challenges. IEEE Netw. 2020, 34, 290–298. [Google Scholar] [CrossRef]
- Cryptography in Blockchain: Types & Applications [2022]. Available online: https://www.upgrad.com/blog/cryptography-in-blockchain/ (accessed on 4 March 2022).
- Bodkhe, U.; Mehta, D.; Tanwar, S.; Bhattacharya, P.; Singh, P.K.; Hong, W.C. A Survey on Decentralized Consensus Mechanisms for Cyber Physical Systems. IEEE Access 2020, 8, 54371–54401. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Tyagi, S.; Kumar, N.; Obaidat, M.S.; Sadoun, B. HaBiTs: Blockchain-based Telesurgery Framework for Healthcare 4.0. In Proceedings of the 2019 International Conference on Computer, Information and Telecommunication Systems (CITS), Beijing, China, 28–31 August 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Hathaliya, J.; Sharma, P.; Tanwar, S.; Gupta, R. Blockchain-Based Remote Patient Monitoring in Healthcare 4.0. In Proceedings of the 2019 IEEE 9th International Conference on Advanced Computing (IACC), Tiruchirappalli, India, 13–14 December 2019; pp. 87–91. [Google Scholar] [CrossRef]
- Wang, J.; Ling, X.; Le, Y.; Huang, Y.; You, X. Blockchain-enabled wireless communications: A new paradigm towards 6G. Natl. Sci. Rev. 2021, 8, nwab069. [Google Scholar] [CrossRef] [PubMed]
- Vora, J.; Tanwar, S.; Tyagi, S.; Kumar, N.; Rodrigues, J.J.P.C. Home-based exercise system for patients using IoT enabled smart speaker. In Proceedings of the 2017 IEEE 19th International Conference on e-Health Networking, Applications and Services (Healthcom), Dalian, China, 12–15 October 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Generations of Mobile Networks: Explained. Available online: https://justaskthales.com/us/generations-mobile-networks-explained/ (accessed on 12 May 2021).
- Gupta, R.; Tanwar, S.; Tyagi, S.; Kumar, N. Tactile Internet and its Applications in 5G Era: A Comprehensive Review. Int. J. Commun. Syst. 2019, 32, e3981. [Google Scholar] [CrossRef]
- Gupta, R.; Reebadiya, D.; Tanwar, S. 6G-enabled Edge Intelligence for Ultra -Reliable Low Latency Applications: Vision and Mission. Comput. Stand. Interfaces 2021, 77, 103521. [Google Scholar] [CrossRef]
- Kakkar, R.; Gupta, R.; Tanwar, S.; Rodrigues, J.J.P.C. Coalition Game and Blockchain-Based Optimal Data Pricing Scheme for Ride Sharing Beyond 5G. IEEE Syst. J. 2021, 1–10. [Google Scholar] [CrossRef]
- Zou, Y.; Zhu, J.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances, and future trends. Proc. IEEE 2016, 104, 1727–1765. [Google Scholar] [CrossRef] [Green Version]
- Tanwar, S.; Tyagi, S.; Kumar, N.; Obaidat, M.S. LA-MHR: Learning Automata Based Multilevel Heterogeneous Routing for Opportunistic Shared Spectrum Access to Enhance Lifetime of WSN. IEEE Syst. J. 2019, 13, 313–323. [Google Scholar] [CrossRef]
- Check Point Software Technology Limited: What is Network Security? Available online: https://www.checkpoint.com/cyber-hub/network-security/what-is-network-security/ (accessed on 17 May 2021).
- Unhelkar, B. Handbook of Research in Mobile Business: Technical, Methodological, and Social Perspectives: Technical, Methodological, and Social Perspectives; Idea Group Reference: Hershey, PA, USA, 2006. [Google Scholar]
- Erskine, S.; Wu, Z. Securing the IEEE 802.16 OFDM WiMAX PHYSICAL AND MAC Layer Using STBC Coding and Encryption. arXiv 2013, arXiv:1309.5069. [Google Scholar]
- Sankaran, C. Network access security in next- generation 3GPP systems: A tutorial. IEEE Commun. Mag. 2009, 47, 84–91. [Google Scholar] [CrossRef]
- Cole, E. Network Security Bible; Bible, Wiley: Hoboken, NJ, USA, 2011. [Google Scholar]
- Wu, Q. 4G Communication Technology Wireless Network Secure Communication. In Proceedings of the 2021 International Wireless Communications and Mobile Computing (IWCMC), Harbin, China, 28 June–2 July 2021; pp. 915–918. [Google Scholar] [CrossRef]
- Wu, S.; Yeoh, P.L.; Hardjawana, W.; Vucetic, B. Identifying Security and Privacy Vulnerabilities in 4G LTE and IoT Communications Networks. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 14 June–31 July 2021; pp. 512–517. [Google Scholar] [CrossRef]
- Jasim, K.F.; Ghafoor, K.Z.; Maghdid, H.S. Analysis of Encryption Algorithms Proposed for Data Security in 4G and 5G Generations. In Proceedings of the ITM Web of Conferences, EDP Sciences, Sale Medina, Morocco, 12–13 May 2022; Volume 42, p. 01004. [Google Scholar]
- Bai, L.; Liang, X.; Xiao, Z.; Jin, R.; Yu, Q. Spatial Multidimensional Cooperative Transmission Theories And Key Technologies; World Scientific Publishing Company: Singapore, 2020. [Google Scholar]
- Everything You Need to Know about 5G-IEEE Spectrum. Available online: https://spectrum.ieee.org/video/telecom/wireless/everything-you-need-to-know-about-5g (accessed on 22 June 2021).
- Park, J.H.; Rathore, S.; Singh, S.K.; Salim, M.M.; Azzaoui, A.; Kim, T.W.; Pan, Y.; Park, J.H. A comprehensive survey on core technologies and services for 5G security: Taxonomies, issues, and solutions. Hum.-Centric Comput. Inf. Sci 2021, 11, 1–22. [Google Scholar] [CrossRef]
- Qian, Y.; Ye, F.; Chen, H.H. Security in 5G Wireless Networks. In Security in Wireless Communication Networks; Wiley: Hoboken, NJ, USA, 2022; pp. 279–310. [Google Scholar] [CrossRef]
- Wang, M.; Zhu, T.; Zhang, T.; Zhang, J.; Yu, S.; Zhou, W. Security and privacy in 6G networks: New areas and new challenges. Digit. Commun. Netw. 2020, 6, 281–291. [Google Scholar] [CrossRef]
- Porambage, P.; Gür, G.; Moya Osorio, D.P.; Livanage, M.; Ylianttila, M. 6G Security Challenges and Potential Solutions. In Proceedings of the 2021 Joint European Conference on Networks and Communications 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 622–627. [Google Scholar] [CrossRef]
- Siyal, A.A.; Junejo, A.Z.; Zawish, M.; Ahmed, K.; Khalil, A.; Soursou, G. Applications of blockchain technology in medicine and healthcare: Challenges and future perspectives. Cryptography 2019, 3, 3. [Google Scholar] [CrossRef] [Green Version]
- Kumari, A.; Gupta, R.; Tanwar, S.; Kumar, N. Blockchain and AI Amalgamation for Energy Cloud Management: Challenges, Solutions, and Future Directions. J. Parallel Distrib. Comput. 2020, 143, 148–166. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Kumar, N.; Tyagi, S. Blockchain-based Security Attack Resilience Schemes for Autonomous Vehicles in Industry 4.0: A Systematic Review. Comput. Electr. Eng. 2019, 86, 106717. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Vollala, S.; Chaudhry, R. Blockchain-based secured event-information sharing protocol in internet of vehicles for smart cities. Comput. Electr. Eng. 2020, 86, 106719. [Google Scholar] [CrossRef]
- Gupta, R.; Kumari, A.; Tanwar, S.; Kumar, N. Blockchain-Envisioned Softwarized Multi-Swarming UAVs to Tackle COVID-I9 Situations. IEEE Netw. 2021, 35, 160–167. [Google Scholar] [CrossRef]
- Gupta, R.; Shukla, A.; Tanwar, S. BATS: A Blockchain and AI-Empowered Drone-Assisted Telesurgery System Towards 6G. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2958–2967. [Google Scholar] [CrossRef]
- Shaik, V.A.; Malik, P.; Singh, R.; Gehlot, A.; Tanwar, S. Adoption of blockchain technology in various realms: Opportunities and challenges. Secur. Priv. 2020, 3, e109. [Google Scholar] [CrossRef] [Green Version]
- Xu, H.; Klaine, P.V.; Onireti, O.; Cao, B.; Imran, M.; Zhang, L. Blockchain-enabled resource management and sharing for 6G communications. Digit. Commun. Netw. 2020, 6, 261–269. [Google Scholar] [CrossRef]
- Verma, A.; Singh, P.; Singh, N. Study of blockchain-based 6G wireless network integration and consensus mechanism. Int. J. Wirel. Mob. Comput. 2021, 21, 255–264. [Google Scholar] [CrossRef]
- Wang, C.; Cheng, X.; Li, J.; He, Y.; Xiao, K. A survey: Applications of blockchain in the Internet of Vehicles. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 77. [Google Scholar] [CrossRef]
- Boudguiga, A.; Bouzerna, N.; Granboulan, L.; Olivereau, A.; Quesnel, F.; Roger, A.; Sirdey, R. Towards Better Availability and Accountability for IoT Updates by Means of a Blockchain. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS PW), Paris, France, 26–28 April 2017; pp. 50–58. [Google Scholar] [CrossRef] [Green Version]
- Ferrag, M.A.; Maglaras, L.; Argyriou, A.; Kosmanos, D.; Janicke, H. Security for 4G and 5G cellular networks: A survey of existing authentication and privacy-preserving schemes. J. Netw. Comput. Appl. 2018, 101, 55–82. [Google Scholar] [CrossRef] [Green Version]
- Pohrmen, F.H.; Das, R.K.; Saha, G. Blockchain-based security aspects in heterogeneous Internet-of-Things networks: A survey. Trans. Emerg. Telecommun. Technol. 2019, 30, e3741. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inf. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Rouhani, S.; Deters, R. Security, Performance, and Applications of Smart Contracts: A Systematic Survey. IEEE Access 2019, 7, 50759–50779. [Google Scholar] [CrossRef]
- Aggarwal, S.; Chaudhary, R.; Aujla, G.S.; Kumar, N.; Choo, K.K.R.; Zomaya, A.Y. Blockchain for smart communities: Applications, challenges and opportunities. J. Netw. Comput. Appl. 2019, 144, 13–48. [Google Scholar] [CrossRef]
- Liu, Y.; He, D.; Obaidat, M.S.; Kumar, N.; Khan, M.K.; Raymond Choo, K.K. Blockchain-based identity management systems: A review. J. Netw. Comput. Appl. 2020, 166, 102731. [Google Scholar] [CrossRef]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Blockchain for cloud exchange: A survey. Comput. Electr. Eng. 2020, 81, 106526. [CrossRef]
- Wazid, M.; Das, A.K.; Shetty, S.; Gope, P.; Rodrigues, J.J.P.C. Security in 5G-Enabled Internet of Things Communication: Issues, Challenges, and Future Research Roadmap. IEEE Access 2021, 9, 4466–4489. [Google Scholar] [CrossRef]
- Hewa, T.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2021, 177, 102857. [Google Scholar] [CrossRef]
- Saraswat, D.; Verma, A.; Bhattacharya, P.; Tanwar, S.; Sharma, G.; Bokoro, P.N.; Sharma, R. Blockchain-Based Federated Learning in UAVs Beyond 5G Networks: A Solution Taxonomy and Future Directions. IEEE Access 2022, 10, 33154–33182. [Google Scholar] [CrossRef]
- Abualsauod, E.H. A hybrid blockchain method in internet of things for privacy and security in unmanned aerial vehicles network. Comput. Electr. Eng. 2022, 99, 107847. [Google Scholar] [CrossRef]
- Grover, J. Security of Vehicular Ad Hoc Networks using blockchain: A comprehensive review. Veh. Commun. 2022, 34, 100458. [Google Scholar] [CrossRef]
- Pattewar, G.; Mahamuni, N.; Nikam, H.; Loka, O.; Patil, R. Management of IoT Devices Security Using Blockchain—A Review. Sentim. Anal. Deep. Learn. 2022, 1408, 735–743. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Liu, D.; Xing, R.; Luan, T.H.; Shen, X. A Survey on Metaverse: Fundamentals, Security, and Privacy. arXiv 2022, arXiv:2203.02662. [Google Scholar] [CrossRef]
- Hussien, H.M.; Yasin, S.M.; Udzir, S.; Zaidan, A.A.; Zaidan, B.B. A systematic review for enabling of develop a blockchain technology in healthcare application: Taxonomy, substantially analysis, motivations, challenges, recommendations and future direction. J. Med Syst. 2019, 43, 1–35. [Google Scholar] [CrossRef]
- Privacy Challenges and Security Solutions for 5G Networks. Available online: https://www.nokia.com/networks/insights/privacy-challenges-security-solutions-5g-networks/ (accessed on 17 May 2021).
- Attacks on Cryptosystems. Available online: https://www.tutorialspoint.com/cryptography/attacks_on_cryptosystems.htm (accessed on 17 June 2021).
- Shiu, Y.S.; Chang, S.Y.; Wu, H.C.; Huang, S.C.H.; Chen, H.H. Physical layer security in wireless networks: A tutorial. IEEE Wirel. Commun. 2011, 18, 66–74. [Google Scholar] [CrossRef]
- Masquerade Attack. Available online: https://www.techopedia.com/definition/4020/masquerade-attack (accessed on 6 March 2022).
- Abbas, S.; Faisal, M.; Ur Rahman, H.; Khan, M.Z.; Merabti, M.; Khan, A.u.R. Masquerading Attacks Detection in Mobile Ad Hoc Networks. IEEE Access 2018, 6, 55013–55025. [Google Scholar] [CrossRef]
- Jo, H.J.; Kim, J.H.; Choi, H.Y.; Choi, W.; Lee, D.H.; Lee, I. MAuth-CAN: Masquerade-Attack-Proof Authentication for In-Vehicle Networks. IEEE Trans. Veh. Technol. 2020, 69, 2204–2218. [Google Scholar] [CrossRef]
- Li, Z.; Li, J.; Zhao, S.; Chen, X.; Feng, K.; Wang, W. A blockchain-based lightweight identity authentication scheme for the IEDs of security and stability control system. PLoS ONE 2022, 17, e0265937. [Google Scholar] [CrossRef] [PubMed]
- Ahmad, N. Security Issues in Wireless Systems. 2009. Available online: https://www.diva-portal.org/smash/get/diva2:833609/FULLTEXT01.pdf (accessed on 20 April 2022).
- What Is a Replay Attack. Available online: https://www.kaspersky.com/resource-center/definitions/replay-attack (accessed on 6 March 2022).
- Al-shareeda, M.A.; Anbar, M.; Hasbullah, I.H.; Manickam, S.; Abdullah, N.; Hamdi, M.M. Review of Prevention schemes for Replay Attack in Vehicular Ad hoc Networks (VANETs). In Proceedings of the 2020 IEEE 3rd International Conference on Information Communication and Signal Processing (ICICSP), Shanghai, China, 12–15 September 2020; pp. 394–398. [Google Scholar] [CrossRef]
- Elsaeidy, A.A.; Jamalipour, A.; Munasinghe, K.S. A Hybrid Deep Learning Approach for Replay and DDoS Attack Detection in a Smart City. IEEE Access 2021, 9, 154864–154875. [Google Scholar] [CrossRef]
- Yavari, M.; Safkhani, M.; Kumari, S.; Kumar, S.; Chen, C.M. An improved blockchain-based authentication protocol for iot network management. Secur. Commun. Netw. 2020, 2020, 8836214. [Google Scholar] [CrossRef]
- Attacks-Types of Attacks. Available online: https://eng.libretexts.org/Courses/Delta_College/Information_Security (accessed on 6 March 2022).
- Mishra, S.; Li, X.; Pan, T.; Kuhnle, A.; Thai, M.T.; Seo, J. Price Modification Attack and Protection Scheme in Smart Grid. IEEE Trans. Smart Grid 2017, 8, 1864–1875. [Google Scholar] [CrossRef]
- Al-shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Review of prevention schemes for modification attack in vehicular ad hoc networks. Int. J. Eng. Manag. Res. 2020, 10. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Kumar, N.; Huang, X.; Vijayakumar, P.; Choo, K.K.R. HomeChain: A Blockchain-Based Secure Mutual Authentication System for Smart Homes. IEEE Internet Things J. 2020, 7, 818–829. [Google Scholar] [CrossRef]
- Erdogan, E.; Altunbas, I.; Kurt, G.K.; Yanikomeroglu, H. The Secrecy Comparison of RF and FSO Eavesdropping Attacks in Mixed RF-FSO Relay Networks. IEEE Photon. J. 2022, 14, 1–8. [Google Scholar] [CrossRef]
- Shi, L.; Li, Y.; Liu, T.; Liu, J.; Shan, B.; Chen, H. Dynamic Distributed Honeypot Based on Blockchain. IEEE Access 2019, 7, 72234–72246. [Google Scholar] [CrossRef]
- Cheikhrouhou, O.; Koubâa, A. BlockLoc: Secure Localization in the Internet of Things using Blockchain. In Proceedings of the 2019 15th International Wireless Communications Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 629–634. [Google Scholar] [CrossRef] [Green Version]
- Yang, L.; Wen, C. Optimal Jamming Attack System Against Remote State Estimation in Wireless Network Control Systems. IEEE Access 2021, 9, 51679–51688. [Google Scholar] [CrossRef]
- Pirayesh, H.; Zeng, H. Jamming Attacks and Anti-Jamming Strategies in Wireless Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2022, 24, 767–809. [Google Scholar] [CrossRef]
- Danish, S.M.; Lestas, M.; Asif, W.; Qureshi, H.K.; Rajarajan, M. A Lightweight Blockchain Based Two Factor Authentication Mechanism for LoRaWAN Join Procedure. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Lee, Y.; Rathore, S.; Park, J.H.; Park, J.H. A blockchain-based smart home gateway architecture for preventing data forgery. Hum.-Centric Comput. Inf. Sci. 2020, 10, 9. [Google Scholar] [CrossRef]
- What is Data Tampering?-Definition & Prevention. Available online: https://study.com/academy/lesson/what-is-data-tampering-definition-prevention.html (accessed on 7 March 2022).
- Ullas, S.U.; Sandeep, J. Reliable Monitoring Security System to Prevent MAC Spoofing in Ubiquitous Wireless Network. In Proceedings of the Advances in Big Data and Cloud Computing, Chennai, India, 21–22 February 2019; pp. 141–153. [Google Scholar]
- Liu, S. MAC Spoofing Attack Detection Based on Physical Layer Characteristics in Wireless Networks. In Proceedings of the 2019 IEEE International Conference on Computational Electromagnetics (ICCEM), Shanghai, China, 20–22 March 2019; pp. 1–3. [Google Scholar] [CrossRef]
- Islam, A.; Uddin, M.B.; Kader, M.F.; Shin, S.Y. Blockchain Based Secure Data Handover Scheme in Non-Orthogonal Multiple Access. In Proceedings of the 2018 4th International Conference on Wireless and Telematics (ICWT), Nusa Dua, Bali, Indonesia, 12–13 July 2018; pp. 1–5. [Google Scholar] [CrossRef] [Green Version]
- Arnaldy, D.; Perdana, A.R. Implementation and Analysis of Penetration Techniques Using the Man-In-The-Middle Attack. In Proceedings of the 2019 2nd International Conference of Computer and Informatics Engineering (IC2IE), Banyuwangi, Indonesia, 10–11 September 2019; pp. 188–192. [Google Scholar]
- Idiyatullin, A.; Abdulkin, P.E. A Research of MITM Attacks in Wi-Fi Networks Using Single-board Computer. In Proceedings of the 2021 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (ElConRus), Moscow, Russia, 26–29 January 2021; pp. 396–400. [Google Scholar] [CrossRef]
- Li, Y.; Pu, C. Lightweight Digital Signature Solution to Defend Micro Aerial Vehicles Against Man-In-The-Middle Attack. In Proceedings of the 2020 IEEE 23rd International Conference on Computational Science and Engineering (CSE), Guangzhou, China, 29 December–1 January 2020; pp. 92–97. [Google Scholar] [CrossRef]
- Choi, J.; Ahn, B.; Bere, G.; Ahmad, S.; Mantooth, H.A.; Kim, T. Blockchain-Based Man-in-the-Middle (MITM) Attack Detection for Photovoltaic Systems. In Proceedings of the 2021 IEEE Design Methodologies Conference (DMC), Bath, UK, 14–15 July 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Shukla, M.; Joshi, B.K. A Trust Based Approach to Mitigate Wormhole Attacks in Mobile Adhoc Networks. In Proceedings of the 2021 10th IEEE International Conference on Communication Systems and Network Technologies (CSNT), Bhopal, India, 18–19 June 2021; pp. 776–782. [Google Scholar] [CrossRef]
- Tatar, E.E.; Dener, M. Wormhole Attacks in IoT Based Networks. In Proceedings of the 2021 6th International Conference on Computer Science and Engineering (UBMK), Ankara, Turkey, 15–17 September 2021; pp. 478–482. [Google Scholar] [CrossRef]
- Mohanty, S.K.; Tripathy, S. n-HTLC: Neo hashed time-Lock commitment to defend against wormhole attack in payment channel networks. Comput. Secur. 2021, 106, 102291. [Google Scholar] [CrossRef]
- Deswal, P.S.; Rani, B.; Rai, M. A Review on the Detection and Prevention Technique of Sybil Attack. Mukt Shabd J. 2020, 9, 1–6. Available online: http://www.shabdbooks.com/gallery/332-june2020.pdf (accessed on 19 June 2021).
- Preventing Black Hole Attack in Wireless Sensor Network Using HMM. Procedia Comput. Sci. 2019, 148, 552–561, The Second International Conference on Intelligent Computing in Data Sciences, ICDS2018. [CrossRef]
- Kudva, S.; Badsha, S.; Sengupta, S.; La, H.; Khalil, I.; Atiquzzaman, M. A scalable blockchain based trust management in VANET routing protocol. J. Parallel Distrib. Comput. 2021, 152, 144–156. [Google Scholar] [CrossRef]
- Nishanth, N.; Mujeeb, A. Modeling and Detection of Flooding-Based Denial-of-Service Attack in Wireless Ad Hoc Network Using Bayesian Inference. IEEE Syst. J. 2021, 15, 17–26. [Google Scholar] [CrossRef]
- Spathoulas, G.; Giachoudis, N.; Damiris, G.P.; Theodoridis, G. Collaborative Blockchain-Based Detection of Distributed Denial of Service Attacks Based on Internet of Things Botnets. Future Internet 2019, 11, 226. [Google Scholar] [CrossRef] [Green Version]
- Hewa, T.; Kalla, A.; Porambage, P.; Liyanage, M.; Ylianttila, M. How DoS attacks can be mounted on Network Slice Broker and can they be mitigated using blockchain? In Proceedings of the 2021 IEEE 32nd Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Helsinki, Finland, 13–16 September 2021; pp. 1525–1531. [Google Scholar] [CrossRef]
- Nagai, R.; Kurihara, W.; Higuchi, S.; Hirotsu, T. Design and Implementation of an OpenFlow-Based TCP SYN Flood Mitigation. In Proceedings of the 2018 6th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Bamberg, Germany, 26–29 March 2018; pp. 37–42. [Google Scholar] [CrossRef]
- Zhu, K.; Chen, Z.; Yan, W.; Zhang, L. Security Attacks in Named Data Networking of Things and a Blockchain Solution. IEEE Internet Things J. 2019, 6, 4733–4741. [Google Scholar] [CrossRef]
- Baitha, A.K.; Vinod, S. Session hijacking and prevention technique. Int. J. Eng. Technol. 2018, 7, 193–198. [Google Scholar] [CrossRef] [Green Version]
- Maurya, A.; Kulkarni, V. Efficient System to Prevent Session Hijacking Attack on Servers using Proxy Server. Int. J. Res. Appl. Sci. Eng. Tech. 2021, 9, 1–10. [Google Scholar] [CrossRef]
- Bera, B.; Das, A.K.; Sutrala, A.K. Private blockchain-based access control mechanism for unauthorized UAV detection and mitigation in Internet of Drones environment. Comput. Commun. 2021, 166, 91–109. [Google Scholar] [CrossRef]
- What Is an SMTP Hack? Available online: https://www.techslang.com/definition/what-is-an-smtp-hack/ (accessed on 6 March 2022).
- Choudhari, S.; Das, S. Spam E-mail Identification Using Blockchain Technology. In Proceedings of the 2021 International Conference on Communication, Control and Information Sciences (ICCISc), Idukki, India, 16–18 June 2021; Volume 1, pp. 1–5. [Google Scholar] [CrossRef]
- Tanrıverdi, M.; Tekerek, A. Implementation of Blockchain Based Distributed Web Attack Detection Application. In Proceedings of the 2019 1st International Informatics and Software Engineering Conference (UBMYK), Ankara, Turkey, 6–7 November 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Ravishankar, N.; Raju, M.; Vyuha, N.C.S. Secure Software Immune Receptors from SQL Injection and Cross Site Scripting Attacks in Content Delivery Network Web Applications. In Proceedings of the 2021 9th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 3–4 September 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Xing, K.; Srinivasan, S.S.R.; Rivera, M.J.M.; Li, J.; Cheng, X. Attacks and Countermeasures in Sensor Networks: A Survey. In Network Security; Huang, S.C.H., MacCallum, D., Du, D.Z., Eds.; Springer US: Boston, MA, USA, 2010; pp. 251–272. [Google Scholar] [CrossRef] [Green Version]
- Anand, P.; Singh, Y.; Selwal, A.; Alazab, M.; Tanwar, S.; Kumar, N. IoT Vulnerability Assessment for Sustainable Computing: Threats, Current Solutions, and Open Challenges. IEEE Access 2020, 8, 168825–168853. [Google Scholar] [CrossRef]
- Barbeau, M.; Hall, J.; Kranakis, E. Detecting impersonation attacks in future wireless and mobile networks. In Proceedings of the International Workshop on Secure Mobile Ad-hoc Networks and Sensors, Singapore, 20–22 September 2005; Volume 4074, pp. 80–95. [Google Scholar]
- Eavesdropping Definition: What Is An Eavesdropping. Available online: https://www.fortinet.com/resources/cyberglossary/eavesdropping (accessed on 6 March 2022).
- Balakrishnan, S.; Wang, P.; Bhuyan, A.; Sun, Z. Modeling and Analysis of Eavesdropping Attack in 802.11ad mmWave Wireless Networks. IEEE Access 2019, 7, 70355–70370. [Google Scholar] [CrossRef]
- What is Jamming Attack and How to Prevent It? Available online: https://www.thesecuritybuddy.com/wireless-network-and-security/what-is-jamming-attack-and-how-to-prevent-it (accessed on 6 March 2022).
- Bendale, S.P.; Rajesh Prasad, J. Security Threats and Challenges in Future Mobile Wireless Networks. In Proceedings of the 2018 IEEE Global Conference on Wireless Computing and Networking (GCWCN), Lonavala, India, 23–24 November 2018; pp. 146–150. [Google Scholar] [CrossRef]
- Jamming and Anti-Jamming Techniques. Available online: https://krazytech.com/technical-papers/jamming-and-anti-jamming-techniques (accessed on 7 March 2022).
- Reddy, K.G.; Thilagam, P.S. MAC layer security issues in wireless mesh networks. In Proceedings of the AIP Conference Proceedings; AIP Publishing LLC: Melville, NY, USA, 2016; Volume 1715, p. 020028. [Google Scholar]
- Ilyas, S.; Ahmed, S.; Ilyas, M.S.B.; Umar, S. Security Mechanisms for attacks on MAC Layer of Wireless Mesh Networks. Technical Report; EasyChair. 2018. Available online: https://easychair.org/publications/preprint_open/fhbH (accessed on 13 May 2021).
- A Guide to Spoofing Attacks and How to Prevent Them. Available online: https://www.comparitech.com/net-admin/spoofing-attacks-guide/ (accessed on 7 March 2022).
- Executing a Man-in-the-Middle Attack in just 15 Minutes. Available online: https://www.thesslstore.com/blog/man-in-the-middle-attack-2/ (accessed on 26 May 2021).
- Fang, D.; Qian, Y.; Hu, R.Q. Security for 5G Mobile Wireless Networks. IEEE Access 2018, 6, 4850–4874. [Google Scholar] [CrossRef]
- Man in the Middle (MITM) Attack. Available online: https://www.imperva.com/learn/application-security/man-in-the-middle-attack-mitm/ (accessed on 8 March 2022).
- Man-in-the-middle (MITM) Attacks. Available online: https://www.javatpoint.com/cyber-security-mitm-attacks (accessed on 8 March 2022).
- Bouabdellah, M.; Kaabouch, N.; El Bouanani, F.; Ben-Azza, H. Network layer attacks and countermeasures in cognitive radio networks: A survey. J. Inf. Secur. Appl. 2018, 38, 40–49. [Google Scholar] [CrossRef]
- Wormhole Attack in Wireless Sensor Networks. Available online: https://www.geeksforgeeks.org/wormhole-attack-in-wireless-sensor-networks/ (accessed on 8 March 2022).
- Walker, J. Chapter 7-Internet Security. In Network and System Security, 2nd ed.; Vacca, J.R., Ed.; Syngress: Boston, MA, USA, 2014; pp. 179–220. [Google Scholar] [CrossRef]
- Yasin, A.; Abu Zant, M. Detecting and isolating black-hole attacks in MANET using timer based baited technique. Wirel. Commun. Mob. Comput. 2018, 2018, 9812135. [Google Scholar] [CrossRef] [Green Version]
- Pathan, M.S.; He, J.; Zhu, N.; Zardari, Z.A.; Memon, M.Q.; Azmat, A. An efficient scheme for detection and prevention of black hole attacks in AODV-based MANETs. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 243–251. [Google Scholar] [CrossRef]
- What is a Denial of Service Attack (DoS). Available online: https://www.paloaltonetworks.com/cyberpedia/what-is-a-denial-of-service-attack-dos/ (accessed on 8 March 2022).
- Denial-of-Service (DoS) Attack. Available online: https://www.investopedia.com/terms/d/denial-service-attack-dos.asp (accessed on 8 March 2022).
- Denial of Service Attack: All You Need to Know in 6 Points. Available online: https://www.jigsawacademy.com/blogs/cyber-security/denial-of-service-attack/ (accessed on 8 March 2022).
- Wang, T.; Guo, Z.; Chen, H.; Liu, W. BWManager: Mitigating Denial of Service Attacks in Software-Defined Networks Through Bandwidth Prediction. IEEE Trans. Netw. Serv. Manag. 2018, 15, 1235–1248. [Google Scholar] [CrossRef]
- Imran, M.; Durad, M.H.; Khan, F.A.; Abbas, H. DAISY: A Detection and Mitigation System Against Denial-of-Service Attacks in Software-Defined Networks. IEEE Syst. J. 2020, 14, 1933–1944. [Google Scholar] [CrossRef]
- Soliman, J.N.; Mageed, T.A.; El-Hennawy, H.M. Taxonomy of security attacks and threats in cognitive radio networks. In Proceedings of the 2017 Japan-Africa Conference on Electronics, Communications and Computers (JAC-ECC), Alexandria, Egypt, 18–20 December 2017; pp. 127–131. [Google Scholar] [CrossRef]
- SYN Flood Attack-Transport Layer. Available online: https://www.distributednetworks.com/network-security-firewalls/module4/syn-flood-attack.php (accessed on 6 March 2022).
- How To Prevent A SYN Flood Attack. Available online: https://purplesec.us/prevent-syn-flood-attack/ (accessed on 6 March 2022).
- Mohammadi, R.; Javidan, R.; Conti, M. SLICOTS: An SDN-Based Lightweight Countermeasure for TCP SYN Flooding Attacks. IEEE Trans. Netw. Serv. Manag. 2017, 14, 487–497. [Google Scholar] [CrossRef]
- Kumar, P.; Tripathi, M.; Nehra, A.; Conti, M.; Lal, C. SAFETY: Early Detection and Mitigation of TCP SYN Flood Utilizing Entropy in SDN. IEEE Trans. Netw. Serv. Manag. 2018, 15, 1545–1559. [Google Scholar] [CrossRef]
- Ethical Hacking: Network or TCP Session Hijacking. Available online: https://www.greycampus.com/blog/information-security?page=2 (accessed on 26 May 2021).
- What Is Session Hijacking? Available online: https://www.venafi.com/blog/what-session-hijacking (accessed on 5 March 2022).
- Session Hijacking. Available online: https://www.geeksforgeeks.org/session-hijacking/ (accessed on 5 March 2022).
- Vulnerabilities in the Application and Transport Layer of the TCP/IP Stack. Available online: https://hub.packtpub.com/vulnerabilities-in-the-application-and-transport-layer-of-the-tcp-ip-stack/ (accessed on 26 May 2021).
- How to Prevent SQL Injection Attacks. Available online: https://www.esecurityplanet.com/threats/how-to-prevent-sql-injection-attacks/ (accessed on 26 May 2021).
- SQL (Structured query language) Injection. Available online: https://www.imperva.com/learn/application-security/sql-injection-sqli/ (accessed on 6 May 2022).
- Ma, L.; Zhao, D.; Gao, Y.; Zhao, C. Research on SQL Injection Attack and Prevention Technology Based on Web. In Proceedings of the 2019 International Conference on Computer Network, Electronic and Automation (ICCNEA), Xi’an, China, 27–29 September 2019; pp. 176–179. [Google Scholar] [CrossRef]
- What Is an Impersonation Attack? Available online: https://easydmarc.com/blog/what-is-an-impersonation-attack/ (accessed on 6 March 2022).
- What Is impersonation? Available online: https://www.bitdefender.com/blog/hotforsecurity/what-is-impersonation (accessed on 7 March 2022).
- Na, X.; Guo, X.; He, Y.; Xi, R. Wi-attack: Cross-technology Impersonation Attack against iBeacon Services. In Proceedings of the 2021 18th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Rome, Italy, 6–9 July 2021; pp. 1–9. [Google Scholar] [CrossRef]
- Huang, W.; Tang, W.; Jiang, H.; Luo, J.; Zhang, Y. Stop Deceiving! An effective Defense Scheme against Voice Impersonation Attacks on Smart Devices. IEEE Internet Things J. 2021, 9, 5304–5314. [Google Scholar] [CrossRef]
- Types of Wireless Network Attacks. Available online: https://www.logsign.com/blog/types-of-wireless-network-attacks/ (accessed on 17 May 2021).
- What Is Packet Sniffing Attack?–Types and How to Prevent It? Available online: https://www.thecrazyprogrammer.com/2021/12/packet-sniffing-attack.html (accessed on 4 March 2022).
- Typical Wi-Fi Attacks. Available online: https://splone.com/blog/2020/10/13/typical-wi-fi-attacks/ (accessed on 17 May 2021).
- What Is an Evil Twin Attack? How to Detect and Prevent It. Available online: https://switchvpn.net/blog/what-is-an-evil-twin-attack/ (accessed on 5 March 2022).
- How Can Blockchain Improve Data Security in 2020? Available online: https://readwrite.com/2020/10/13/how-can-blockchain-improve-data-security-in-2020/ (accessed on 17 May 2021).
- Cao, B.; Li, M.; Zhang, L.; Li, Y.; Peng, M. How Does CSMA/CA Affect the Performance and Security in Wireless Blockchain Networks. IEEE Trans. Ind. Inf. 2020, 16, 4270–4280. [Google Scholar] [CrossRef]
- Xu, H.; Zhang, L.; Liu, Y.; Cao, B. RAFT Based Wireless Blockchain Networks in the Presence of Malicious Jamming. IEEE Wirel. Commun. Lett. 2020, 9, 817–821. [Google Scholar] [CrossRef] [Green Version]
- Khan, R.; Kumar, P.; Jayakody, D.N.K.; Liyanage, M. A Survey on Security and Privacy of 5G Technologies: Potential Solutions, Recent Advancements, and Future Directions. IEEE Commun. Surv. Tutorials 2020, 22, 196–248. [Google Scholar] [CrossRef] [Green Version]
- Bouras, M.A.; Lu, Q.; Zhang, F.; Wan, Y.; Zhang, T.; Ning, H. Distributed Ledger Technology for eHealth Identity Privacy: State of The Art and Future Perspective. Sensors 2020, 20, 483. [Google Scholar] [CrossRef] [Green Version]
- Han, T.; Ribeiro, I.d.L.; Magaia, N.; Preto, J.; Segundo, A.H.F.N.; de Macêdo, A.R.L.; Muhammad, K.; de Albuquerque, V.H.C. Emerging Drone Trends for Blockchain-Based 5G Networks: Open Issues and Future Perspectives. IEEE Netw. 2021, 35, 38–43. [Google Scholar] [CrossRef]
- Sun, W.; Li, S.; Zhang, Y. Edge caching in blockchain empowered 6G. China Commun. 2021, 18, 1–17. [Google Scholar] [CrossRef]
- Rahman, A.; Islam, M.J.; Montieri, A.; Nasir, M.K.; Reza, M.M.; Band, S.S.; Pescape, A.; Hasan, M.; Sookhak, M.; Mosavi, A. SmartBlock-SDN: An Optimized Blockchain-SDN Framework for Resource Management in IoT. IEEE Access 2021, 9, 28361–28376. [Google Scholar] [CrossRef]
- Wu, Y.; Dai, H.N.; Wang, H.; Choo, K.K.R. Blockchain-Based Privacy Preservation for 5G-Enabled Drone Communications. IEEE Netw. 2021, 35, 50–56. [Google Scholar] [CrossRef]
- Wu, H.; Dwivedi, A.D.; Srivastava, G. Security and Privacy of Patient Information in Medical Systems Based on Blockchain Technology. ACM Trans. Multimed. Comput. Commun. Appl. 2021, 17, 1–17. [Google Scholar] [CrossRef]
- Jayabalan, J.; Jeyanthi, N. Scalable blockchain model using off-chain IPFS storage for healthcare data security and privacy. J. Parallel Distrib. Comput. 2022, 164, 152–167. [Google Scholar] [CrossRef]
- Fatima, N.; Agarwal, P.; Sohail, S.S. Security and Privacy Issues of Blockchain Technology in Health Care—A Review. In Proceedings of the ICT Analysis and Applications; Fong, S., Dey, N., Joshi, A., Eds.; Springer Nature: Singapore, 2022; pp. 193–201. [Google Scholar]
- Perez, A.J.; Zeadally, S. Secure and privacy-preserving crowdsensing using smart contracts: Issues and solutions. Comput. Sci. Rev. 2022, 43, 100450. [Google Scholar] [CrossRef]
- Qahtan, S.; Yatim, K.; Zaidan, A.A.; Alsattar, H.A.; Albahri, O.S.; Zaidan, B.B.; Alamoodi, A.H.; Zulzalil, H.; Osman, M.H.; Mohammed, R.T. Novel Multi Security and Privacy Benchmarking Framework for Blockchain-Based IoT Healthcare Industry 4.0 Systems. IEEE Trans. Ind. Inform. 2022, 1–9. [Google Scholar] [CrossRef]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2019, 6, 1594–1605. [Google Scholar] [CrossRef] [Green Version]
- Liu, B.; Yu, X.L.; Chen, S.; Xu, X.; Zhu, L. Blockchain Based Data Integrity Service Framework for IoT Data. In Proceedings of the 2017 IEEE International Conference on Web Services (ICWS), Honolulu, HI, USA, 25–30 June 2017; pp. 468–475. [Google Scholar] [CrossRef]
- Are Blockchains That Safe? How to Attack and Prevent Attacks. Available online: https://www.seba.swiss/research/are-blockchains-safe-how-to-attack-them-and-prevent-attacks (accessed on 23 June 2021).
- Bao, Z.; Wang, Q.; Shi, W.; Wang, L.; Lei, H.; Chen, B. When Blockchain Meets SGX: An Overview, Challenges, and Open Issues. IEEE Access 2020, 8, 170404–170420. [Google Scholar] [CrossRef]
- Cao, J.; Ma, M.; Li, H.; Zhang, Y.; Luo, Z. A Survey on Security Aspects for LTE and LTE-A Networks. IEEE Commun. Surv. Tutor. 2014, 16, 283–302. [Google Scholar] [CrossRef]
- He, L.; Yan, Z.; Atiquzzaman, M. LTE/LTE-A Network Security Data Collection and Analysis for Security Measurement: A Survey. IEEE Access 2018, 6, 4220–4242. [Google Scholar] [CrossRef]




| Year | Author | Contribution | Observations | Remarks |
|---|---|---|---|---|
| 2016 | Zou et al. [32] | Discussed security attacks, protocols, and algorithms in WNs for physical layer | Discussion about security and privacy in other layers have lacked | Cover security and privacy in every layer |
| 2017 | Boudguiga et al. [58] | Discussed blockchain infrastructure for IoT | Analyzed confidentiality, integrity and availability with different use case | Did not discuss the vulnerability in the security |
| 2018 | Ferrag et al. [59] | Analyzed existing privacy-preserving and authentication schemes for 4G and 5G | Did not discuss layer-wise security in WNs | Study on layer-wise security for different generation networks is required |
| 2019 | Pohrmen et al. [60] | Explored IoT-based system with Blockchain for SDN platforms | Application of blockchain in subsystem is lacking | Blockchain usage in smart applications, such as smart city, autonomous vehicle, identity management, etc., that need emphasis |
| 2019 | Casino et al. [61] | Review of blockchain-based applications through multiple domains, established trends, key themes, and emerging areas | Security requirement in different application domain has not been covered | Analyzed security requirements using blockchain with scalability, privacy, interoperability, audit, latency, and visibility issues |
| 2019 | Rouhani et al. [62] | Reviewed existing approaches and security tools for performance enhancement of decentralized applications based on smart contract | Did not discuss problems and limitations of smart contract in individual applications | A comparison of blockchain-based solutions with other existing solutions is required |
| 2019 | Wang et al. [65] | A Blockchain scheme for IoT | Comparison of existing security techniques with blockchain techniques is missing | Should provide a comparative analysis of existing techniques with blockchain-based approaches |
| 2019 | Aggarwal et al. [63] | Surveyed Blockchain for smart communities and analyzed process models for secure transactions | Comparison of Blockchain with existing security solutions is lacked | Survey on blockchain-based security and privacy challenges needs to be highlighted |
| 2019 | Hussien et al. [74] | Studied blockchain in healthcare domain with various features such as data integrity, access control, etc. | Comparison of consensus mechanism of blockchain is not included | Should emphasize application of blockchain for security and privacy perspective |
| 2020 | Liu et al. [64] | A blockchain-based identity management solutions | Highlighted conceptual analysis for identity management solutions | Real-time applicability of blockchain-based solution need to be taken into consideration |
| 2020 | Xie et al. [66] | Discussed blockchain for cloud data exchange based on transaction management, and reputation systems | Analysis of existing security methods with blockchain for cloud is lacking | Existing blockchain-based solutions for cloud data exchange need to be discussed in detail |
| 2020 | Tahir et al. [14] | Discussed blockchain in 5G and future WNs | Did not cover comparison of blockchain with another approaches of security and privacy | Cover existing security and privacy solutions based on blockchain |
| 2021 | Wazid et al. [67] | Examined the existing research in the field of 5G-enabled IoT communication environment and provided system model, security protocol, and attacks | Did not cover the detail about layer-wise security in WNs | Layer-wise security in WNs should be considered |
| 2021 | Hewa et al. [68] | Explored the applications for the blockchain-based smart contracts | Application of smart contract in security and privacy perspective is lacking | Should cover existing method and compare with smart contract-based with application |
| 2022 | Saraswat et al. [69] | Presented blockchain enabled federated learning in UAVs for trusted exchange of information | Discussed UAV security with blockchain and proposed case study | Security attacks for blockchain enabled UAV need to be highlighted |
| 2022 | Abualsauod et al. [70] | Studied blockchain and ML techniques for the security in UAVs | Analyzed the hybrid blockchain model for security and reliability and presented future direction | Real-time applicability needs to be discussed with case study |
| 2022 | Grover et al. [71] | Studied security of ITS in VANET | Discussed existing solution based on blockchain for VANET security | Did not consider layer-wise security attacks |
| 2022 | Pattewar et al. [72] | Analyzed existing solution for IoT security using blockchain | Discussed consensus algorithms for security and privacy in various use case | Did not specify the security vulnerability and attacks |
| 2022 | Wang et al. [73] | Studied security and privacy issues in metaverse | Analyzed security threat and blockchain based security solutions | Did not consider possibility of the security attacks |
| 2022 | The proposed approach | Analyzed security requirements and issues based on different layer, proposed taxonomy for existing security and privacy approaches envisioned security attacks and their countermeasures | Proposed a blockchain-based WNs architecture for security and privacy perspective with the scalability and latency comparison | - |
| Year | Author | Applications | Security Issues | Approach | Pros | Cons |
|---|---|---|---|---|---|---|
| 2020 | Cao et al. [170] | Wireless industrial IoT (IIoTs) | Scarcity of spectrum resources | Presented blockchain-based on CDMA/CA model | Introduced stochastic mode and double-spending attack on CDMA/CA | Not considered layer wise security |
| 2020 | Xu et al. [171] | IoT applications | Malicious jamming | Presented RAFT based blockchain network | Proposed consensus algorithm | Not considered multi-jammer problem |
| 2020 | Khan et al. [172] | 5G security for different technology like SDN, NFV etc | Detection and prevention of sabotage | Proposed 5G security model | Considered network and physical layer security | Other layer security is lacked |
| 2020 | Bouras et al. [173] | e-healthcare | Data tampering | Analyzed eHealth scenario using blockchain | Presented identity model with blockchain | Did not consider real-time scenario results |
| 2021 | Han et al. [174] | Unmanned aerial vehicles | Reliability and connectivity, energy efficiency, data privacy | Blockchain-based approach | Proposed drone-based architecture on 5G for with different technologies | Did not discuss security attacks |
| 2021 | Sun et al. [175] | Edge cache network | Data tempering and eavesdropper | Blockchain-based 6G framework | Used 6G edge caching and two-hop transmission, optimize the cashing for secure transaction | Did not incorporate a comparative analysis of the proposed approach with existing security solutions |
| 2021 | Rahman et al. [176] | Resource management for IoT | Energy efficiency and end-to-end delay for resource utilization | Blockchain-based SDN framework | Proposed cluster-head selection algorithm to secure network | Did not consider mobility |
| 2021 | Wu et al. [177] | Drone Communication | Drone ID management, privacy and trajectory protection | Presented blockchain-enabled trajectory privacy protection scheme | Used in military and civilian area | Did not cover security attacks |
| 2021 | Wu et al. [178] | Healthcare | Private information protection of medical system | Elliptic curve Diffie–Hellman key exchange approach and file authorization contracts | Enhanced reliability and bandwidth utilization of data transmission | Did not discuss security attacks on the existing approach |
| 2022 | Jayabalan et al. [179] | Healthcare | Monetary and resource loss | Temper register blockchain bad framework with IPFS storage for the healthcare | They used symmetric and asymmetric key encryption, digital signature and hashing algorithm and IPFS to deal with scalability issue | Did not discuss security and privacy attacks in the system |
| 2022 | Fatima et al. [180] | Healthcare | Data tampering | Blockchain-based cloud technology for healthcare | They presented state of the art on blockchain enabled healthcare system | Did not consider security issues of the existing solution |
| 2022 | Perez et al. [181] | Crowd-sensing systems | Data confidentiality, integrity, and system availability | Proposed crowd-sensing systems using smart contracts and blockchain | They discussed security and privacy issue with blockchain based solution in crowd-sensing systems | Did not discuss security and privacy problem to add blockchain and smart contract in the system |
| 2022 | Qahtan et al. [182] | IoT healthcare Industry 4.0 systems | User authentication, access control, and privacy protection | Analyzed MCDM problem in blockchain enabled IoT healthcare Industry 4.0 systems | Proposed spherical FWZIC for security and privacy, GRA-TOPSIS, and BES approach for optimization | Did not discuss security and privacy attacks and their countermeasures in the presented approach |
| Parameters | Values |
|---|---|
| Wireless network layer parameters | |
| Frequency range | 95 GHz |
| Channel bandwidth | 130 MHz |
| Subcarrier spacing | 60 KHz |
| Modultation | OFDM |
| Channel coding | Polar coding |
| Fading channel | comm.RayleighChannel |
| Blockchain layer parameters | |
| Solidity compiler | 0.8.10+commit.fc410830 |
| Remix environment | Injected Web3 |
| Gas limit | 3,000,000 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rathod, T.; Jadav, N.K.; Alshehri, M.D.; Tanwar, S.; Sharma, R.; Felseghi, R.-A.; Raboaca, M.S. Blockchain for Future Wireless Networks: A Decade Survey. Sensors 2022, 22, 4182. https://doi.org/10.3390/s22114182
Rathod T, Jadav NK, Alshehri MD, Tanwar S, Sharma R, Felseghi R-A, Raboaca MS. Blockchain for Future Wireless Networks: A Decade Survey. Sensors. 2022; 22(11):4182. https://doi.org/10.3390/s22114182
Chicago/Turabian StyleRathod, Tejal, Nilesh Kumar Jadav, Mohammad Dahman Alshehri, Sudeep Tanwar, Ravi Sharma, Raluca-Andreea Felseghi, and Maria Simona Raboaca. 2022. "Blockchain for Future Wireless Networks: A Decade Survey" Sensors 22, no. 11: 4182. https://doi.org/10.3390/s22114182
APA StyleRathod, T., Jadav, N. K., Alshehri, M. D., Tanwar, S., Sharma, R., Felseghi, R.-A., & Raboaca, M. S. (2022). Blockchain for Future Wireless Networks: A Decade Survey. Sensors, 22(11), 4182. https://doi.org/10.3390/s22114182








