A New Intrusion Detection System for the Internet of Things via Deep Convolutional Neural Network and Feature Engineering
Abstract
:1. Introduction
Contributions
- We proposed a DCNN technique for malicious activity identification in IoT networks.
- We improved performance and reduced the computational power of an IDS for low-power IoT devices in the network.
- We identified the subcategory of cyberattacks in the IoT networks.
- We compared the proposed scheme with other DL and traditional ML techniques.
2. Related Works
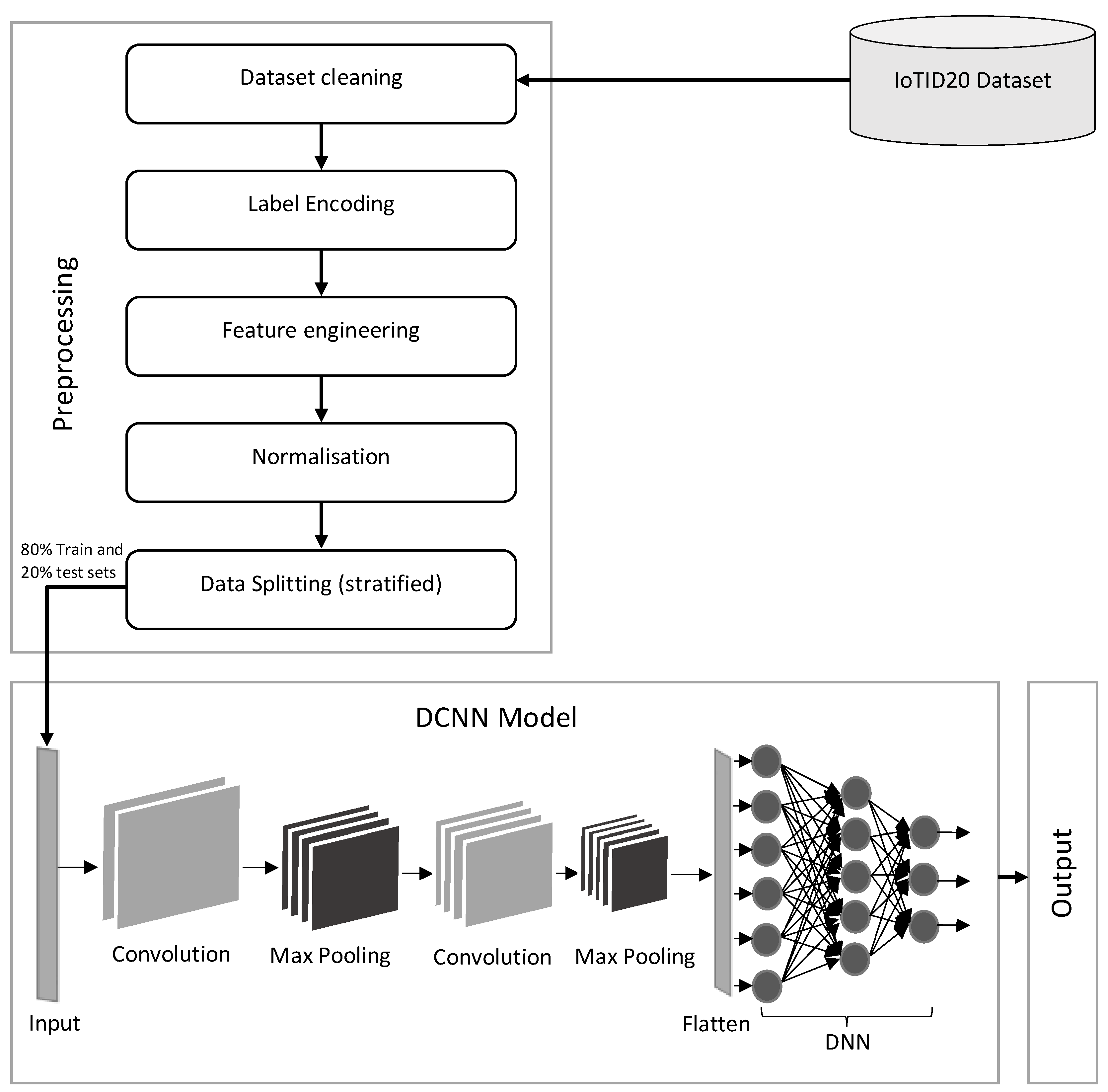
3. The Proposed Framework
3.1. IoTID20 Dataset
3.2. Preprocessing
3.2.1. Dataset Cleaning
3.2.2. Label Encoding
3.2.3. Feature Engineering
3.2.4. Normalization
3.2.5. Data Splitting
3.3. Designing the DCNN Model
3.4. Evaluation Metrics
3.5. Experimental Platform
4. Performance Analysis
4.1. Performance Evaluation of Convolutional and Dense Layers
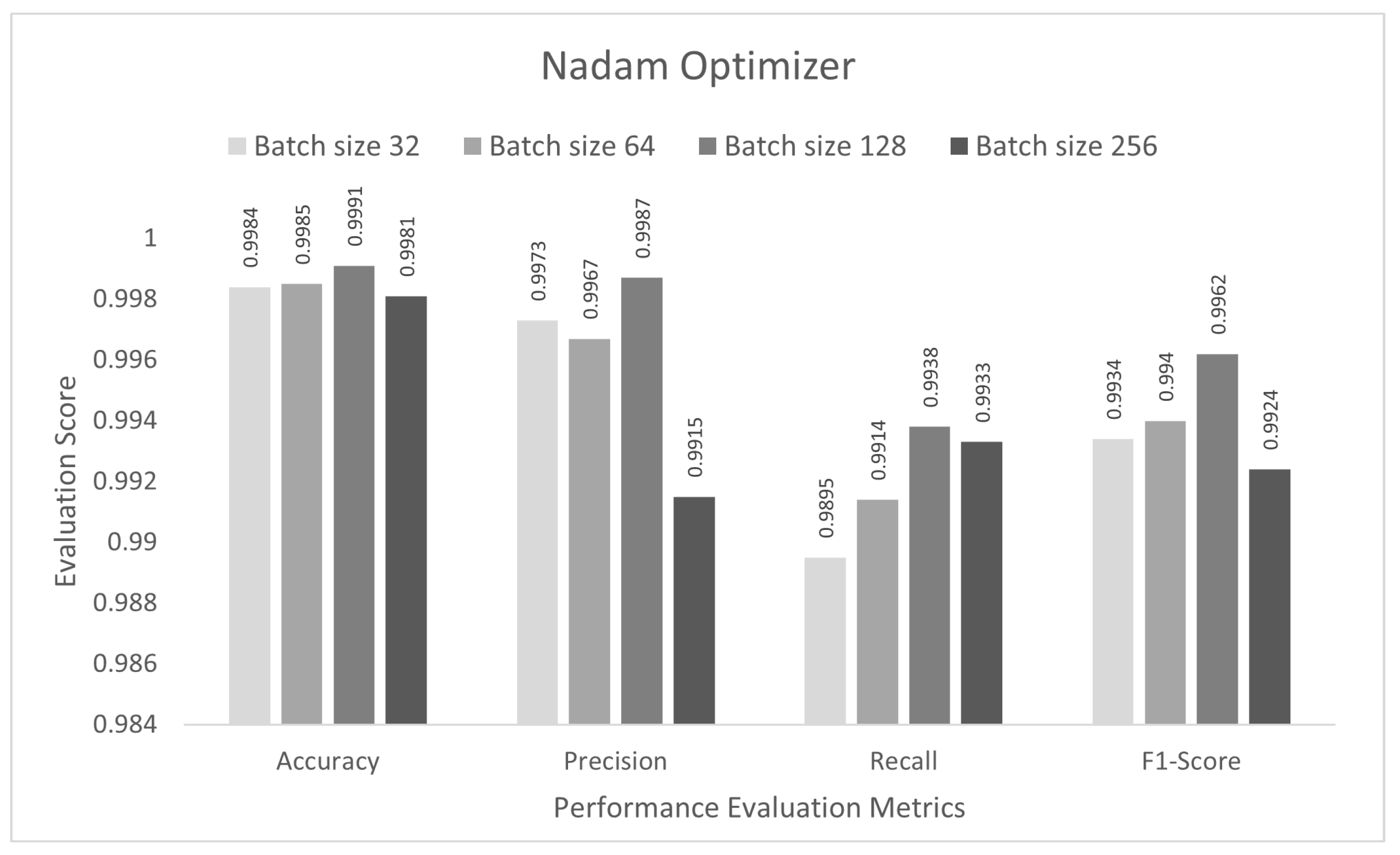
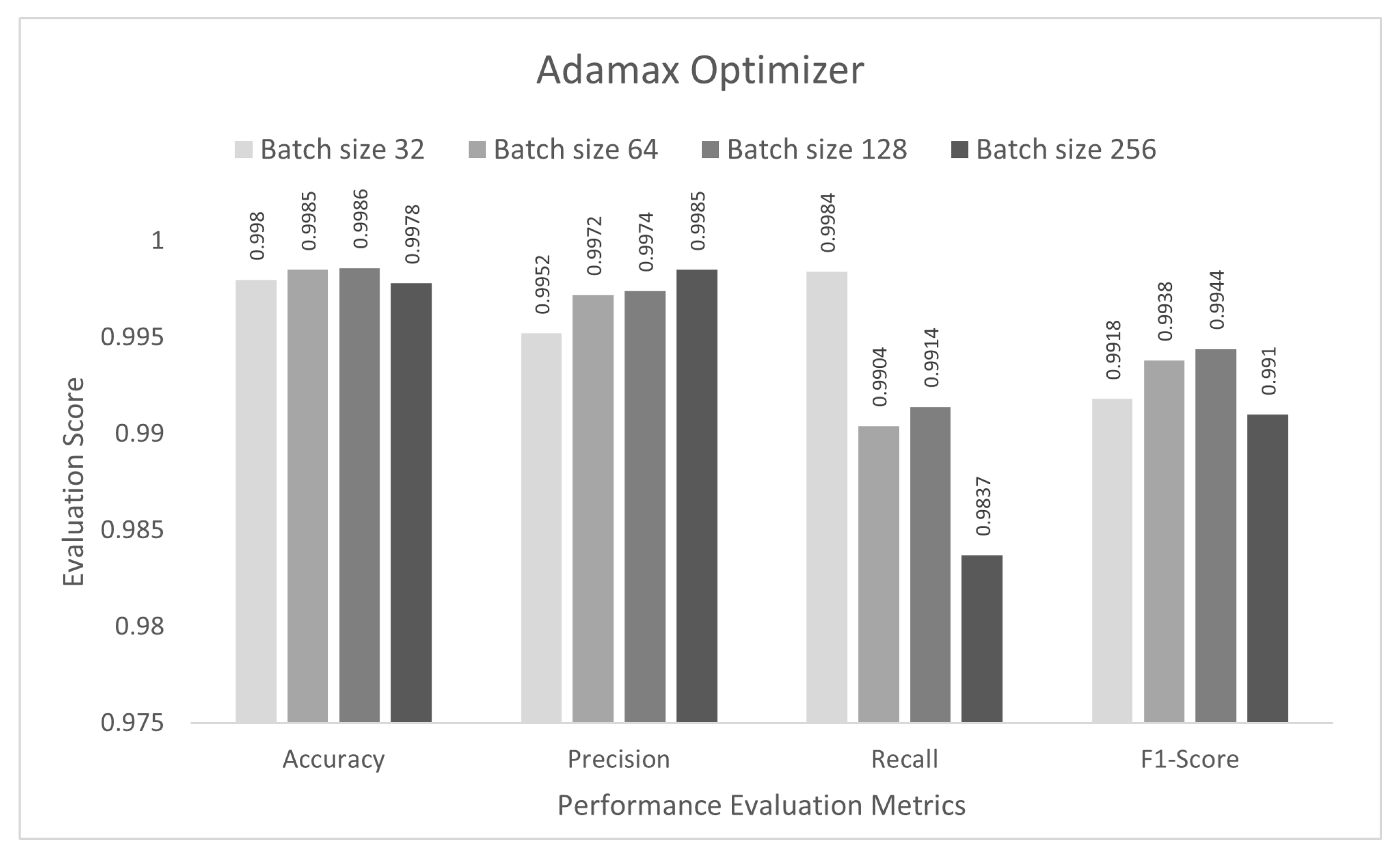
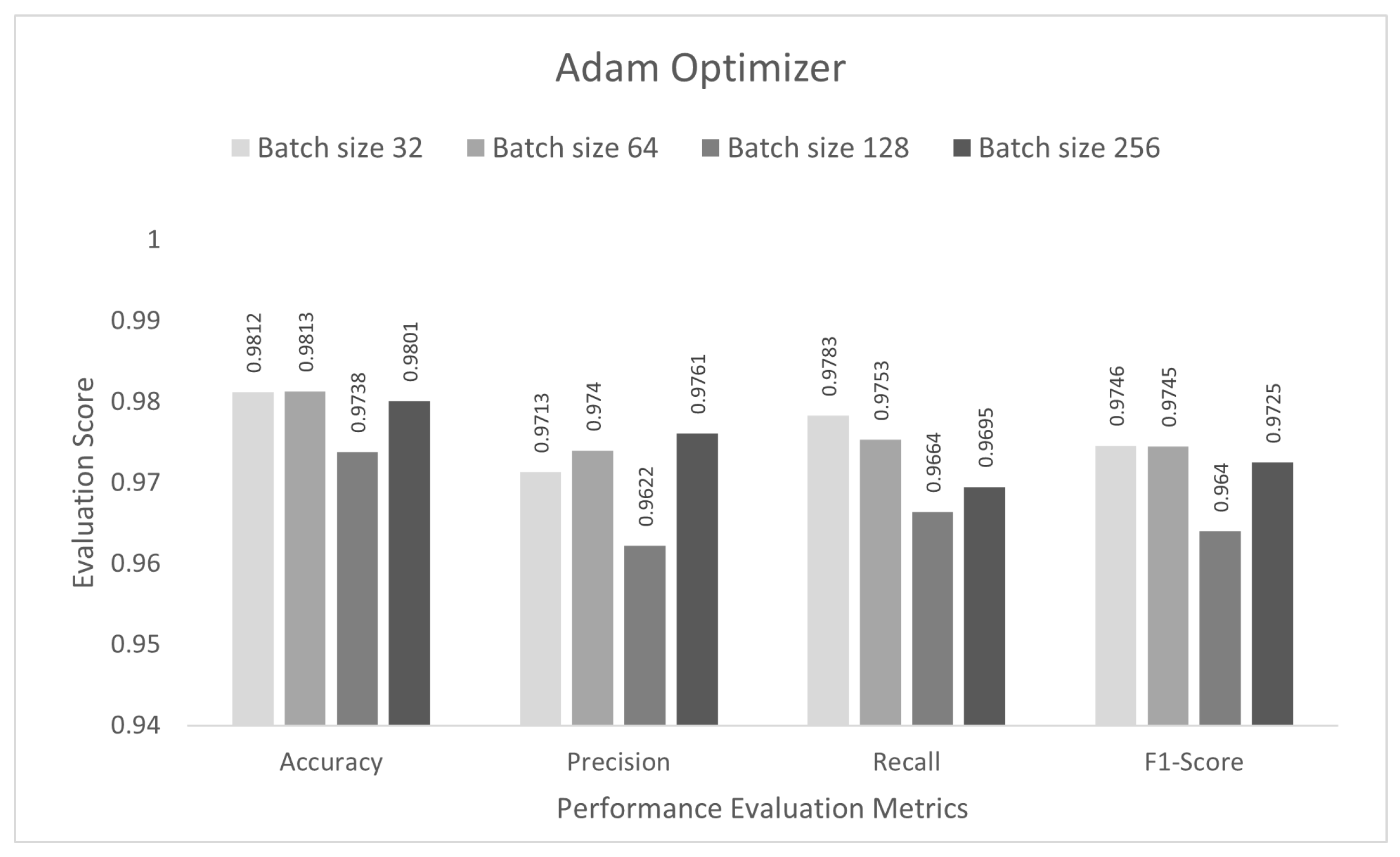
4.2. Performance Evaluation of Optimizers
4.3. Performance Analysis of the Proposed DCNN
4.3.1. DCNN Evaluation for Binary-Class Classification
4.3.2. DCNN Evaluation for Multi-Class Category Classification
4.3.3. DCNN Evaluation for Multi-Class Subcategory Classification
4.4. Performance Discussion
4.5. Performance Comparison with Other DL and Traditional ML-Based IDSs
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Farooq, M.S.; Sohail, O.O.; Abid, A.; Rasheed, S. A Survey on the Role of IoT in Agriculture for the Implementation of Smart Livestock Environment. IEEE Access 2022, 10, 9483–9505. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. Design and development of a deep learning-based model for anomaly detection in IoT networks. IEEE Access 2021, 9, 103906–103926. [Google Scholar] [CrossRef]
- Mezni, H.; Driss, M.; Boulila, W.; Atitallah, S.B.; Sellami, M.; Alharbi, N. SmartWater: A Service-Oriented and Sensor Cloud-Based Framework for Smart Monitoring of Water Environments. Remote Sens. 2022, 14, 922. [Google Scholar] [CrossRef]
- Alam, T. A Reliable Communication Framework and Its Use in Internet of Things (IoT). Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2018, 3, 450–456. [Google Scholar]
- Al-Bahri, M.; Yankovsky, A.; Borodin, A.; Kirichek, R. Testbed for identify IoT-devices based on digital object architecture. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 129–137. [Google Scholar]
- Nguyen, X.H.; Nguyen, X.D.; Huynh, H.H.; Le, K.H. Realguard: A Lightweight Network Intrusion Detection System for IoT Gateways. Sensors 2022, 22, 432. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.; Li, P.; Wang, X. Intrusion detection for IoT based on improved genetic algorithm and deep belief network. IEEE Access 2019, 7, 31711–31722. [Google Scholar] [CrossRef]
- Conti, M.; Dehghantanha, A.; Franke, K.; Watson, S. Internet of Things security and forensics: Challenges and opportunities. Future Gener. Comput. Syst. 2018, 78, 544–546. [Google Scholar] [CrossRef] [Green Version]
- Liu, H.; Lang, B. Machine learning and deep learning methods for intrusion detection systems: A survey. Appl. Sci. 2019, 9, 4396. [Google Scholar] [CrossRef] [Green Version]
- Gao, Z.J.; Pansare, N.; Jermaine, C. Declarative parameterizations of user-defined functions for large-scale machine learning and optimization. IEEE Trans. Knowl. Data Eng. 2018, 31, 2079–2092. [Google Scholar] [CrossRef]
- Guo, Z.; Qi, W.; Huang, Y.; Zhao, J.; Yang, H.; Koo, V.C.; Li, N. Identification of Crop Type Based on C-AENN Using Time Series Sentinel-1A SAR Data. Remote Sens. 2022, 14, 1379. [Google Scholar] [CrossRef]
- Liu, Z.Y.C.; Chamberlin, A.J.; Tallam, K.; Jones, I.J.; Lamore, L.L.; Bauer, J.; Bresciani, M.; Wolfe, C.M.; Casagrandi, R.; Mari, L.; et al. Deep Learning Segmentation of Satellite Imagery Identifies Aquatic Vegetation Associated with Snail Intermediate Hosts of Schistosomiasis in Senegal, Africa. Remote Sens. 2022, 14, 1345. [Google Scholar] [CrossRef]
- Salunkhe, S.S.; Pal, S.; Agrawal, A.; Rai, R.; Mole, S.; Jos, B.M. Energy optimization for CAN bus and media controls in electric vehicles using deep learning algorithms. J. Supercomput. 2022, 78, 8493–8508. [Google Scholar] [CrossRef]
- Lin, J.; Diekmann, P.; Framing, C.E.; Zweigel, R.; Abel, D. Maritime Environment Perception Based on Deep Learning. IEEE Trans. Intell. Transp. Syst. 2022. [Google Scholar] [CrossRef]
- Heaton, J. Ian goodfellow, yoshua bengio, and aaron courville: Deep learning. Genet. Program. Evolvable Mach. 2018, 19, 305–307. [Google Scholar] [CrossRef] [Green Version]
- Mighan, S.N.; Kahani, M. A novel scalable intrusion detection system based on deep learning. Int. J. Inf. Secur. 2021, 20, 387–403. [Google Scholar] [CrossRef]
- Al-Turaiki, I.; Altwaijry, N. A convolutional neural network for improved anomaly-based network intrusion detection. Big Data 2021, 9, 233–252. [Google Scholar] [CrossRef]
- Aldweesh, A.; Derhab, A.; Emam, A.Z. Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues. Knowl. Based Syst. 2020, 189, 105124. [Google Scholar] [CrossRef]
- Basati, A.; Faghih, M.M. DFE: Efficient IoT network intrusion detection using deep feature extraction. Neural Comput. Appl. 2022, 1–21. [Google Scholar] [CrossRef]
- Rashid, M.; Kamruzzaman, J.; Imam, T.; Wibowo, S.; Gordon, S. A tree-based stacking ensemble technique with feature selection for network intrusion detection. Appl. Intell. 2022, 1–14. [Google Scholar] [CrossRef]
- Fatani, A.; Dahou, A.; Al-Qaness, M.A.; Lu, S.; Abd Elaziz, M. Advanced Feature Extraction and Selection Approach Using Deep Learning and Aquila Optimizer for IoT Intrusion Detection System. Sensors 2022, 22, 140. [Google Scholar] [CrossRef]
- Alkahtani, H.; Aldhyani, T.H. Intrusion detection system to advance internet of things infrastructure-based deep learning algorithms. Complexity 2021, 2021, 5579851. [Google Scholar] [CrossRef]
- Keserwani, P.K.; Govil, M.C.; Pilli, E.S.; Govil, P. A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model. J. Reliab. Intell. Environ. 2021, 7, 3–21. [Google Scholar] [CrossRef]
- Qaddoura, R.; Al-Zoubi, A.; Almomani, I.; Faris, H. A multi-stage classification approach for iot intrusion detection based on clustering with oversampling. Appl. Sci. 2021, 11, 3022. [Google Scholar] [CrossRef]
- Saba, T.; Sadad, T.; Rehman, A.; Mehmood, Z.; Javaid, Q. Intrusion detection system through advance machine learning for the internet of things networks. IT Prof. 2021, 23, 58–64. [Google Scholar] [CrossRef]
- Kang, H.; Ahn, D.H.; Lee, G.M.; Yoo, J.D.; Park, K.H.; Kim, H.K. IoT Network Intrusion Dataset. 2019. Available online: https://ieee-dataport.org/open-access/iot-network-intrusion-dataset (accessed on 28 January 2022). [CrossRef]
- Ullah, I.; Mahmoud, Q.H. A scheme for generating a dataset for anomalous activity detection in iot networks. In Proceedings of the Canadian Conference on Artificial Intelligence, Ottawa, ON, Canada, 13–15 May 2020; pp. 508–520. [Google Scholar]
- Dahouda, M.K.; Joe, I. A Deep-Learned Embedding Technique for Categorical Features Encoding. IEEE Access 2021, 9, 114381–114391. [Google Scholar] [CrossRef]
- Riyaz, B.; Ganapathy, S. A deep learning approach for effective intrusion detection in wireless networks using CNN. Soft Comput. 2020, 24, 17265–17278. [Google Scholar] [CrossRef]
- Zhang, H.; Huang, L.; Wu, C.Q.; Li, Z. An effective convolutional neural network based on SMOTE and Gaussian mixture model for intrusion detection in imbalanced dataset. Comput. Netw. 2020, 177, 107315. [Google Scholar] [CrossRef]
- Vidhya, A. A Comprehensive Guide on Deep Learning Optimizers. Available online: https://www.analyticsvidhya.com/blog/2021/10/a-comprehensive-guide-on-deep-learning-optimizers/ (accessed on 7 October 2021).
- Ruder, S. An Overview of Gradient Descent Optimization Algorithms. Available online: https://ruder.io/optimizing-gradient-descent/ (accessed on 19 January 2016).
- Vani, S.; Rao, T.M. An experimental approach towards the performance assessment of various optimizers on convolutional neural network. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 331–336. [Google Scholar]




| Authors | Year | Technique | Dataset | Multi-Class Detection | Sub-Categories Multi-Class Detection |
|---|---|---|---|---|---|
| Basati et al. [19] | 2022 | DFE | KDDCup99, CICIDS2017, UNSW-NB15 | ✓ | × |
| Rashid et al. [20] | 2022 | Ensemble | NSL-KDD, UNSW-NB15 | × | × |
| Fatani et al. [21] | 2022 | AQU, PSO | CIC2017, NSL-KDD, BoT-IoT, KDD99 | ✓ | × |
| Alkahtani et al. [22] | 2021 | CNN-LSTM | IoTID20 | × | × |
| Keserwani et al. [23] | 2021 | GWO–PSO–RF | KDDCup99, NSL–KDD, CICIDS-2017 | ✓ | × |
| Qaddoura et al. [24] | 2021 | SLFN-SVM-SMOTE | IoTID20 | ✓ | × |
| Saba et al. [25] | 2021 | GA-(SVM, Ensemble, DT) | NSL-KDD | ✓ | × |
| Propose Study | 2022 | CNN-DNN | IoTID20 | ✓ | ✓ |
| Binary | Category | Subcategory |
|---|---|---|
| Normal | Normal | Normal |
| Anomaly | DoS | DoS-Synflooding |
| Mirai | Mirai-Ackflooding | |
| Mirai-HTTP Flooding | ||
| Mirai-Hostbruteforceg | ||
| Mirai-UDP Flooding | ||
| MITM | MITM ARP Spoofing | |
| Scan | Scan Port OS | |
| Scan Hostport |
| Type | Class | Instances | Train Set | Test Set |
|---|---|---|---|---|
| Binary | Anomaly | 585,342 | 468,274 | 117,068 |
| Normal | 40,073 | 32,058 | 8015 | |
| Total | 625,415 | 500,332 | 125,083 | |
| Category | Mirai | 415,309 | 332,247 | 83,062 |
| Scan | 75,265 | 60,212 | 15,053 | |
| DoS | 59,391 | 47,513 | 11,878 | |
| MITM ARP Spoofing | 35,377 | 28,302 | 7075 | |
| Normal | 40,073 | 32,058 | 8015 | |
| Total | 625,415 | 500,332 | 125,083 | |
| Sub-Category | Mirai-UDP Flooding | 183,189 | 146,551 | 36,638 |
| Mirai-Hostbruteforceg | 121,178 | 96,943 | 24,235 | |
| Mirai-HTTP Flooding | 55,818 | 44,654 | 11,164 | |
| Mirai-Ackflooding | 55,124 | 44,099 | 11,025 | |
| DoS-Synflooding | 59,391 | 47,513 | 11,878 | |
| Scan Port OS | 53,073 | 42,458 | 10,615 | |
| Scan Hostport | 22,192 | 17,754 | 4438 | |
| MITM ARP Spoofing | 35,377 | 28,302 | 7075 | |
| Normal | 40,073 | 32,058 | 8015 | |
| Total | 625,415 | 500,332 | 125,083 | |
| Convolutional Layers | Dense Layers | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|---|
| 1 | 1 | 0.9465 | 0.92 | 0.9297 | 0.9237 |
| 1 | 3 | 0.9798 | 0.9712 | 0.9723 | 0.9716 |
| 2 | 1 | 0.9791 | 0.9756 | 0.9656 | 0.9701 |
| 2 | 2 | 0.9823 | 0.9744 | 0.9753 | 0.9747 |
| 2 | 3 | 0.9833 | 0.9742 | 0.9788 | 0.9764 |
| 2 | 4 | 0.9794 | 0.9697 | 0.9735 | 0.9713 |
| 2 | 5 | 0.9813 | 0.974 | 0.9757 | 0.9744 |
| Convolutional Layers | Dense Layers | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|---|
| 1 | 1 | 0.7232 | 0.7056 | 0.6443 | 0.6182 |
| 1 | 3 | 0.7633 | 0.7660 | 0.7157 | 0.6804 |
| 2 | 1 | 0.7690 | 0.7518 | 0.6563 | 0.7008 |
| 2 | 2 | 0.7731 | 0.7955 | 0.7320 | 0.6989 |
| 2 | 3 | 0.7755 | 0.7876 | 0.7343 | 0.7600 |
| 2 | 4 | 0.7732 | 0.7890 | 0.6790 | 0.6541 |
| 2 | 5 | 0.7650 | 0.8499 | 0.6527 | 0.6160 |
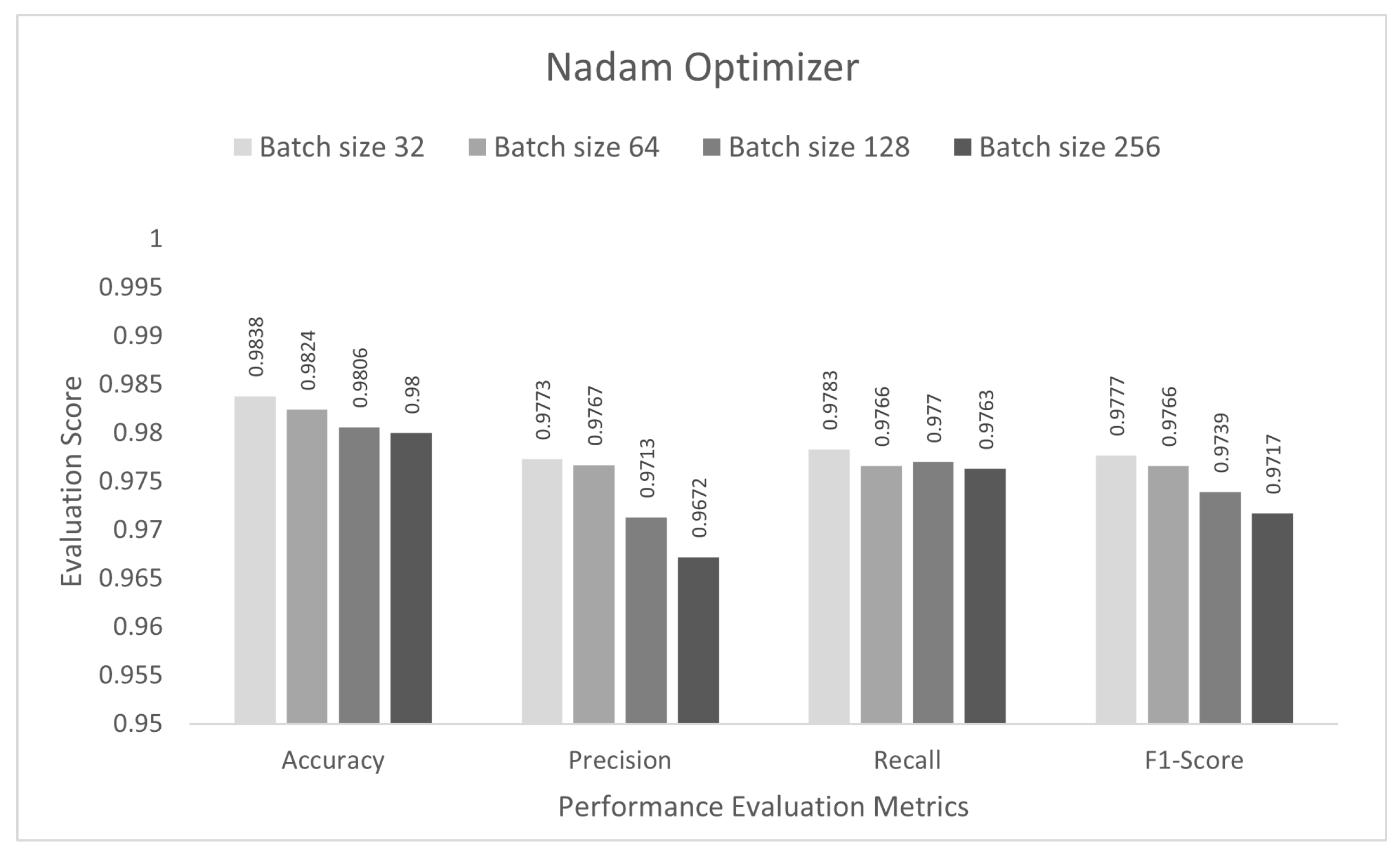
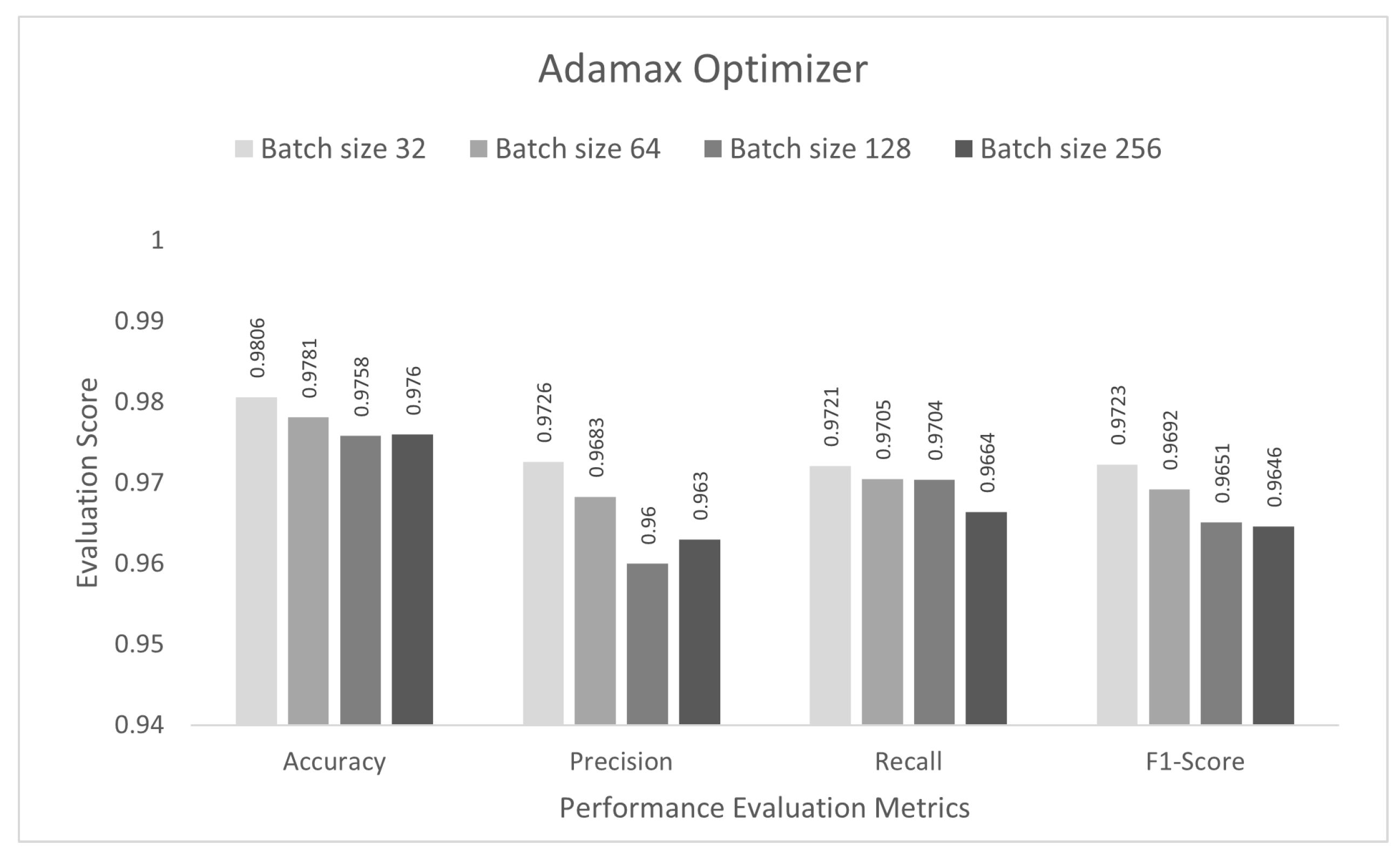
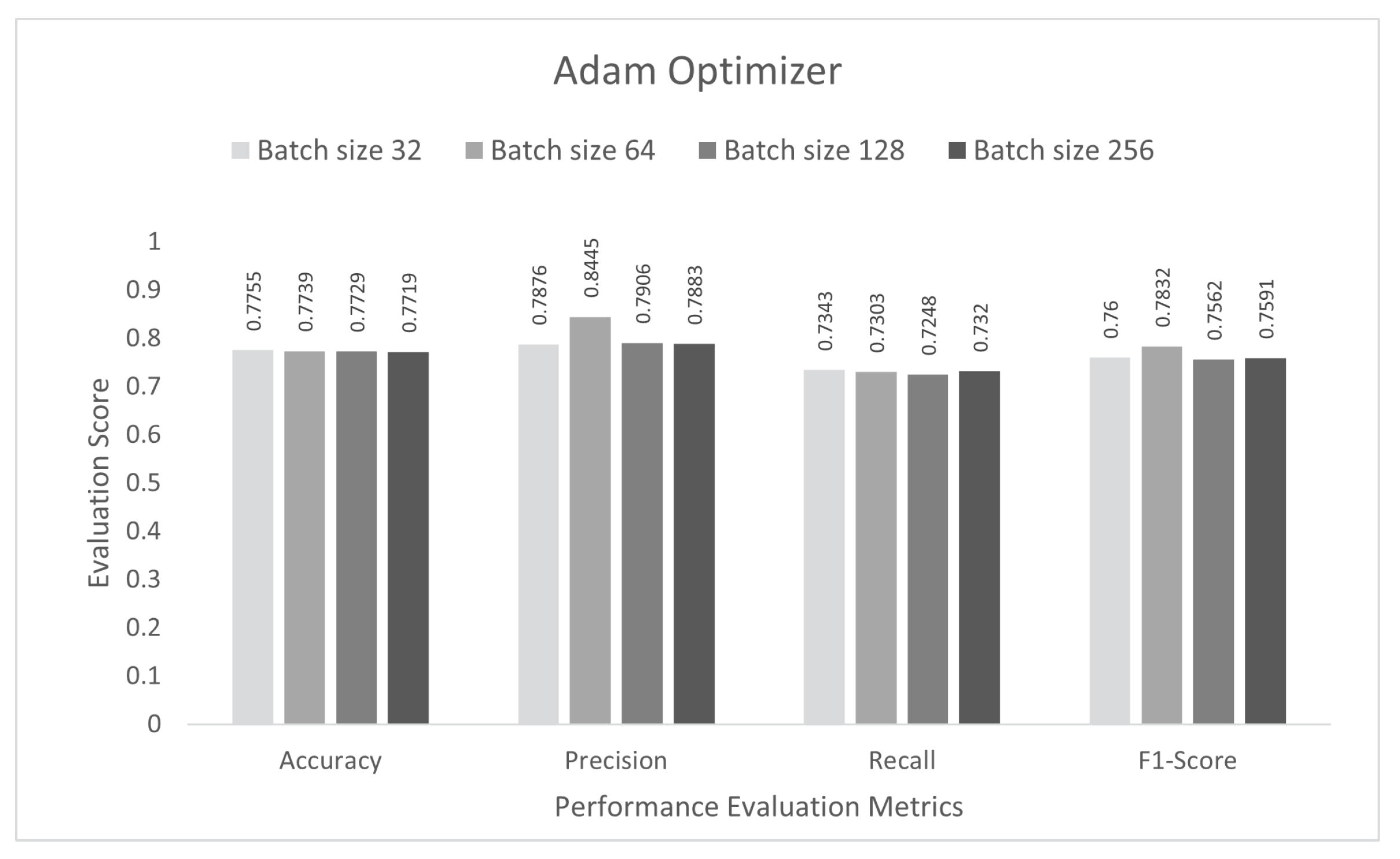
| Optimizer | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| SGD | 0.9789 | 0.9676 | 0.9706 | 0.9690 |
| RMSprop | 0.7630 | 0.7457 | 0.7195 | 0.6527 |
| Adam | 0.9801 | 0.9761 | 0.9695 | 0.9725 |
| Nadam | 0.9838 | 0.9773 | 0.9783 | 0.9777 |
| AdaMax | 0.9806 | 0.9726 | 0.9721 | 0.9723 |
| Optimizer | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| SGD | 0.9789 | 0.9676 | 0.9706 | 0.969 |
| RMSprop | 0.7630 | 0.7457 | 0.7195 | 0.6527 |
| Adam | 0.9801 | 0.9761 | 0.9695 | 0.9725 |
| Nadam | 0.9838 | 0.9773 | 0.9783 | 0.9777 |
| Adamax | 0.9806 | 0.9726 | 0.9721 | 0.9723 |
| Models | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| LSTM | 0.9952 | 0.9943 | 0.9662 | 0.9797 |
| GRU | 0.9959 | 0.9856 | 0.9807 | 0.9832 |
| DNN | 0.9981 | 0.9983 | 0.9862 | 0.9922 |
| DBN | 0.9969 | 0.9937 | 0.9807 | 0.9871 |
| AE | 0.9974 | 0.9895 | 0.9887 | 0.9891 |
| MLP | 0.9972 | 0.9938 | 0.9832 | 0.9884 |
| DT | 0.9857 | 0.9819 | 0.9861 | 0.9840 |
| LR | 0.9659 | 0.9034 | 0.7879 | 0.8345 |
| NB | 0.6504 | 0.5765 | 0.8093 | 0.6733 |
| SVM | 0.9744 | 0.9199 | 0.8552 | 0.8844 |
| KNN | 0.9983 | 0.9964 | 0.9894 | 0.9929 |
| Proposed DCNN | 0.9984 | 0.9967 | 0.9902 | 0.9934 |
| Model | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| LSTM | 0.9584 | 0.9543 | 0.9201 | 0.9355 |
| GRU | 0.9681 | 0.9576 | 0.9468 | 0.9519 |
| DNN | 0.9547 | 0.9340 | 0.9447 | 0.9367 |
| DBN | 0.9589 | 0.9430 | 0.9549 | 0.9469 |
| AE | 0.9644 | 0.9515 | 0.9440 | 0.9456 |
| MLP | 0.9238 | 0.8933 | 0.8436 | 0.8529 |
| DT | 0.9770 | 0.9744 | 0.9737 | 0.9741 |
| LR | 0.8314 | 0.7728 | 0.7297 | 0.7311 |
| NB | 0.6772 | 0.6628 | 0.7381 | 0.6479 |
| SVM | 0.8557 | 0.8416 | 0.7845 | 0.7883 |
| KNN | 0.9793 | 0.9746 | 0.9699 | 0.9722 |
| Proposed DCNN | 0.9812 | 0.9713 | 0.9783 | 0.9746 |
| Model | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| LSTM | 0.7141 | 0.6993 | 0.5992 | 0.6453 |
| GRU | 0.7615 | 0.7571 | 0.6996 | 0.7272 |
| DNN | 0.7483 | 0.7244 | 0.6610 | 0.6912 |
| DBN | 0.6888 | 0.6916 | 0.6166 | 0.6519 |
| AE | 0.7535 | 0.7805 | 0.7016 | 0.7389 |
| MLP | 0.7065 | 0.7124 | 0.6263 | 0.6665 |
| DT | 0.7530 | 0.7508 | 0.7362 | 0.7413 |
| LR | 0.5481 | 0.4457 | 0.4239 | 0.4142 |
| NB | 0.5298 | 0.4878 | 0.5032 | 0.4481 |
| SVM | 0.6240 | 0.4888 | 0.4741 | 0.4624 |
| KNN | 0.7621 | 0.7634 | 0.7477 | 0.7515 |
| Proposed DCNN | 0.7755 | 0.7876 | 0.7343 | 0.7600 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ullah, S.; Ahmad, J.; Khan, M.A.; Alkhammash, E.H.; Hadjouni, M.; Ghadi, Y.Y.; Saeed, F.; Pitropakis, N. A New Intrusion Detection System for the Internet of Things via Deep Convolutional Neural Network and Feature Engineering. Sensors 2022, 22, 3607. https://doi.org/10.3390/s22103607
Ullah S, Ahmad J, Khan MA, Alkhammash EH, Hadjouni M, Ghadi YY, Saeed F, Pitropakis N. A New Intrusion Detection System for the Internet of Things via Deep Convolutional Neural Network and Feature Engineering. Sensors. 2022; 22(10):3607. https://doi.org/10.3390/s22103607
Chicago/Turabian StyleUllah, Safi, Jawad Ahmad, Muazzam A. Khan, Eman H. Alkhammash, Myriam Hadjouni, Yazeed Yasin Ghadi, Faisal Saeed, and Nikolaos Pitropakis. 2022. "A New Intrusion Detection System for the Internet of Things via Deep Convolutional Neural Network and Feature Engineering" Sensors 22, no. 10: 3607. https://doi.org/10.3390/s22103607
APA StyleUllah, S., Ahmad, J., Khan, M. A., Alkhammash, E. H., Hadjouni, M., Ghadi, Y. Y., Saeed, F., & Pitropakis, N. (2022). A New Intrusion Detection System for the Internet of Things via Deep Convolutional Neural Network and Feature Engineering. Sensors, 22(10), 3607. https://doi.org/10.3390/s22103607









