Author Contributions
Conceptualization, A.A.A.E.-L.; methodology, F.N., B.A.-E.-A.; software, F.N., B.A.-E.-A.; formal analysis, A.A.A.E.-L., S.J., B.A.-E.-A.; investigation, A.A.A.E.-L.; resources, L.L., F.N.; data curation, S.J.; writing—original draft preparation, A.A.A.E.-L., B.A.-E.-A.; writing—review and editing, S.J., K.R.; supervision, K.R.; project administration, L.L.; funding acquisition, L.L. All authors have read and agreed to the published version of the manuscript.
Figure 1.
Proposed framework for the secure transmission of multimedia data in IoT environment.
Figure 1.
Proposed framework for the secure transmission of multimedia data in IoT environment.
Figure 2.
The chaotic dynamics of Equation (
1) with
and
in (
a)
; (
b)
; (
c)
; (
d)
.
Figure 2.
The chaotic dynamics of Equation (
1) with
and
in (
a)
; (
b)
; (
c)
; (
d)
.
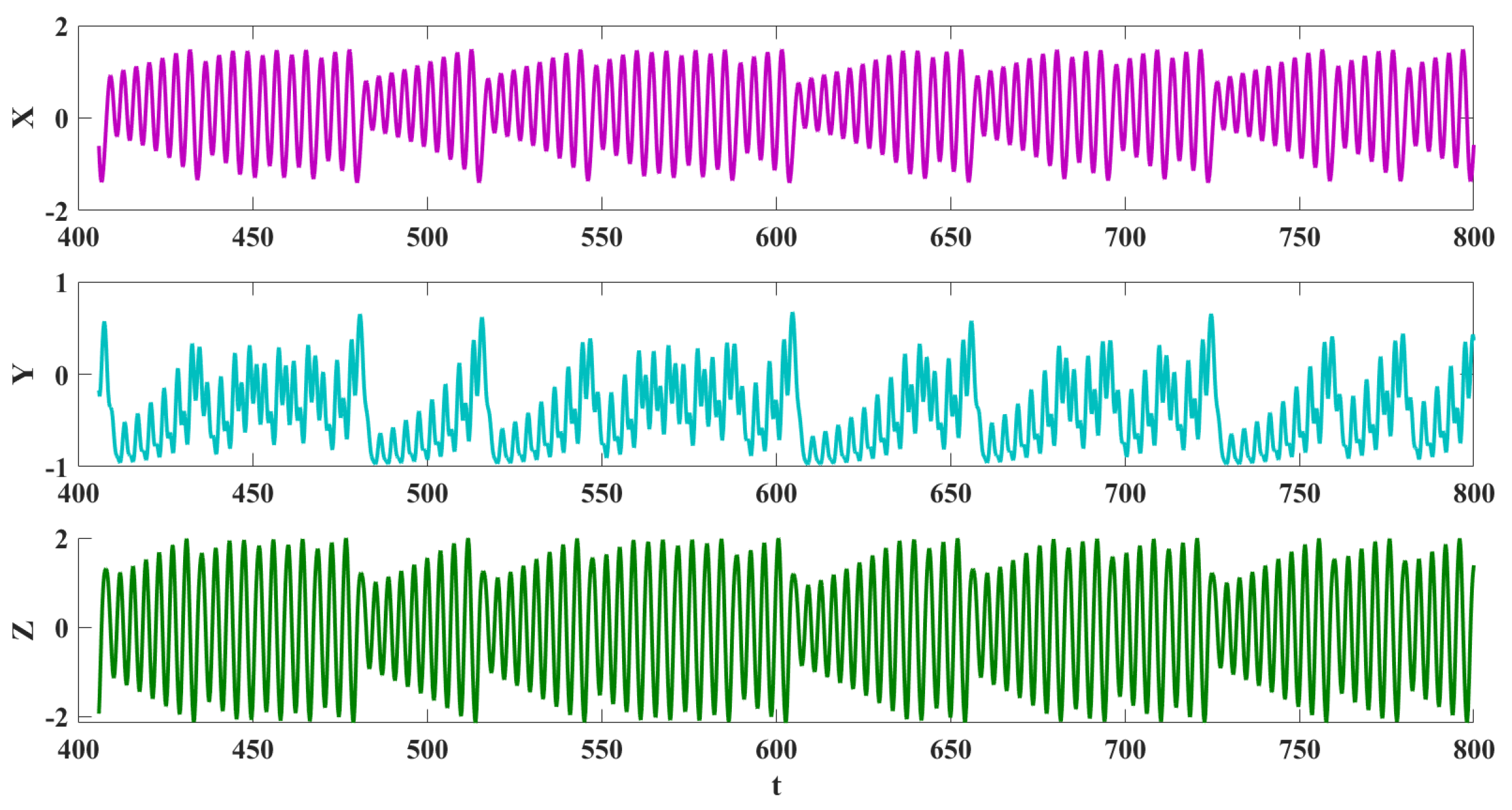
Figure 3.
Time series of Equation (
1) with
and
.
Figure 3.
Time series of Equation (
1) with
and
.
Figure 4.
3D chaotic dynamics of Equation (
1) and the three pre-located manifolds (
a–
c).
Figure 4.
3D chaotic dynamics of Equation (
1) and the three pre-located manifolds (
a–
c).
Figure 5.
Bifurcation diagram of Equation (
1) by changing parameter
a and backward continuation method; maximum values of (
a)
x variable; (
b)
y variable; (
c)
z variable.
Figure 5.
Bifurcation diagram of Equation (
1) by changing parameter
a and backward continuation method; maximum values of (
a)
x variable; (
b)
y variable; (
c)
z variable.
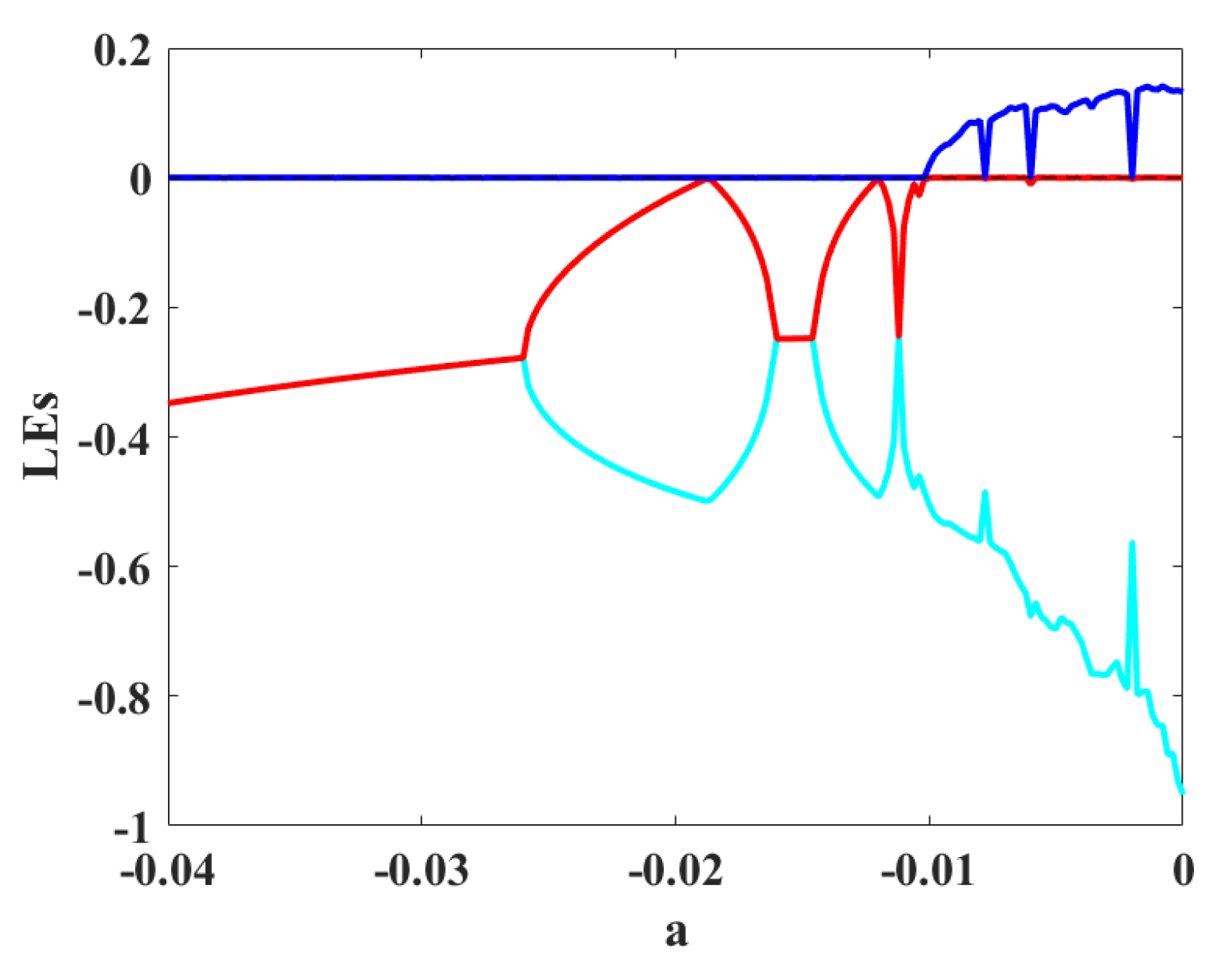
Figure 6.
The diagram of LEs by changing parameter a.
Figure 6.
The diagram of LEs by changing parameter a.
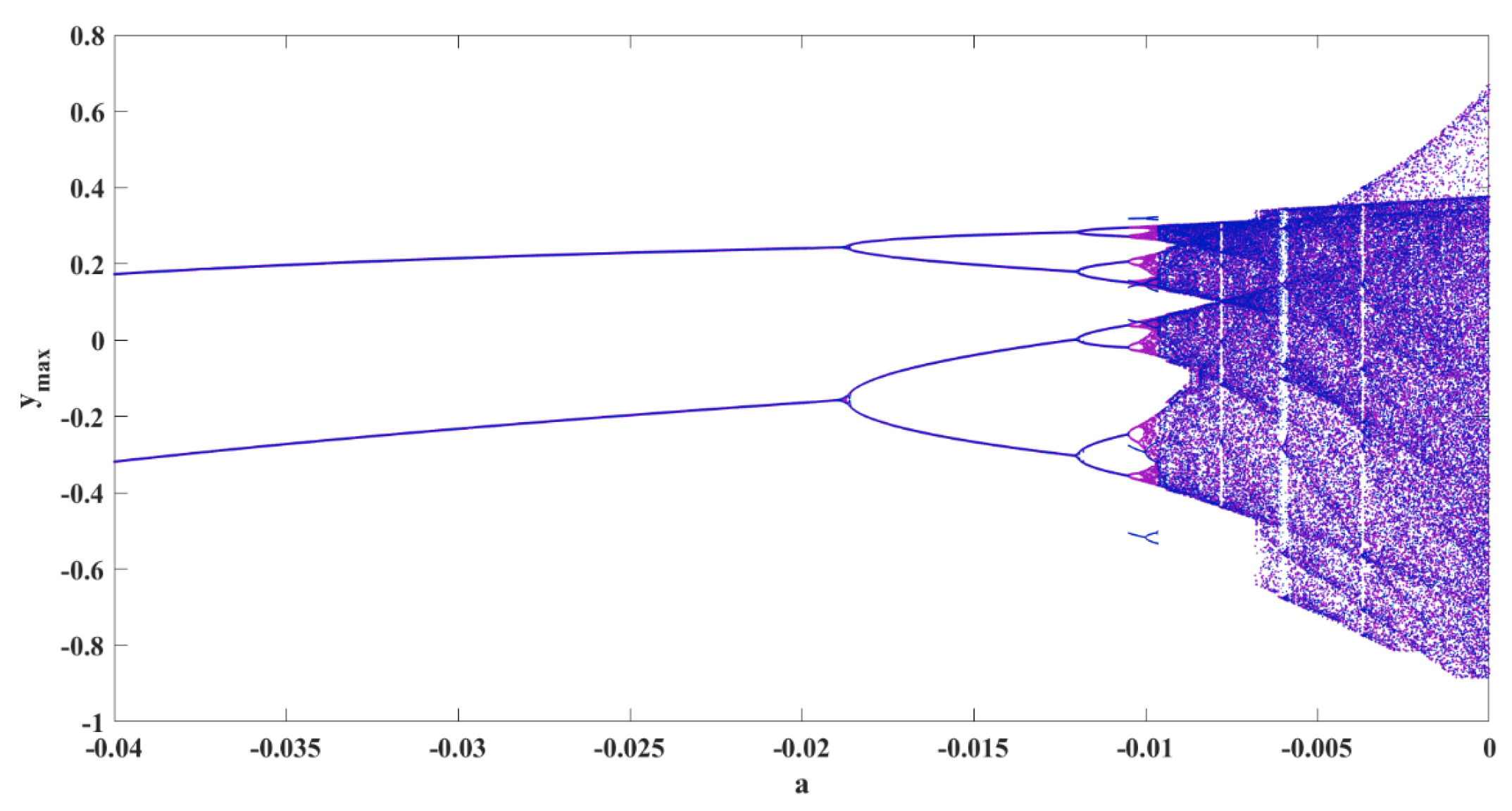
Figure 7.
Bifurcation diagram of the oscillator by changing parameter a; bifurcation with backward continuation method is shown in purple and with constant initial conditions is shown in blue.
Figure 7.
Bifurcation diagram of the oscillator by changing parameter a; bifurcation with backward continuation method is shown in purple and with constant initial conditions is shown in blue.
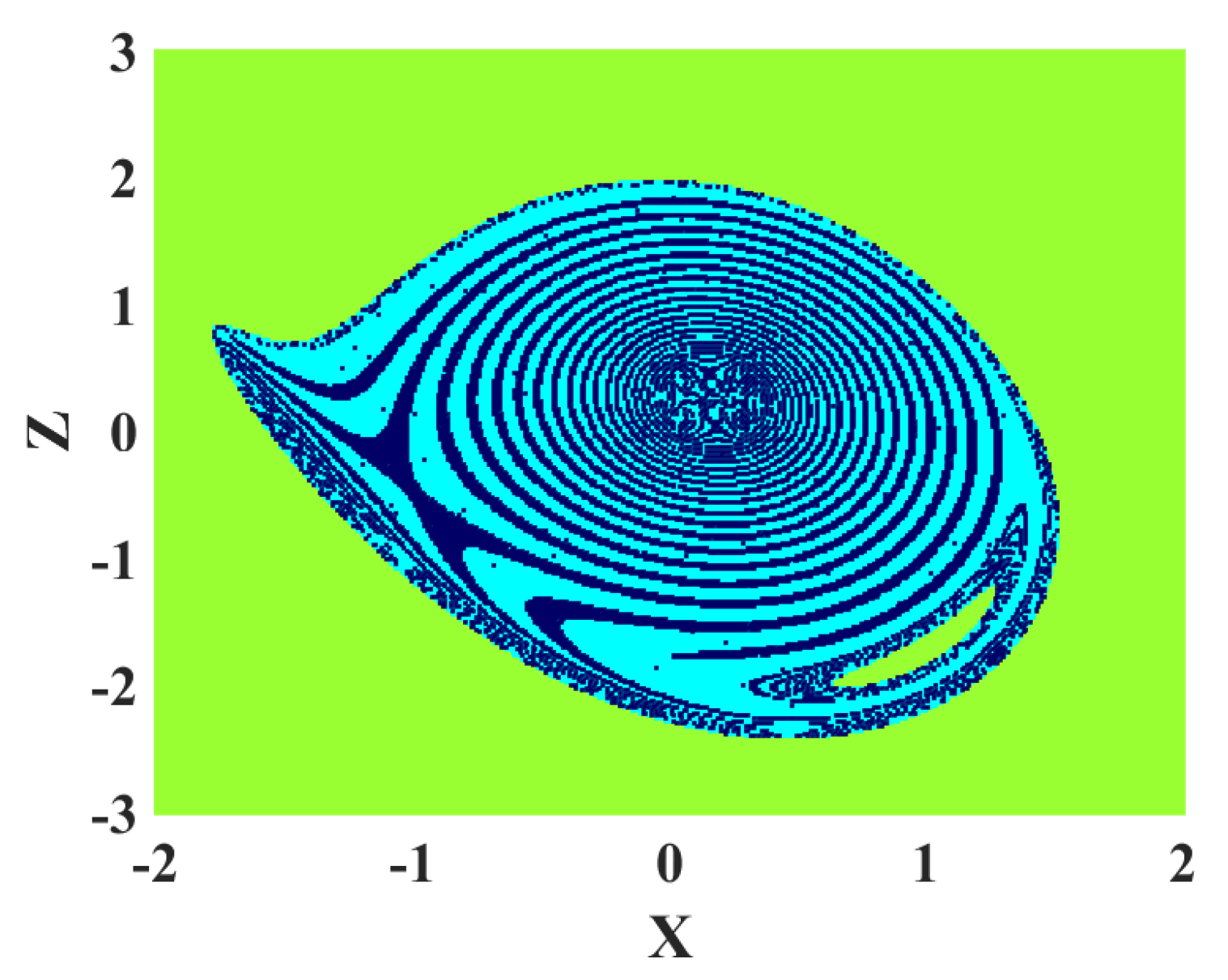
Figure 8.
Basin of attraction of the oscillator; green, dark blue, and cyan regions show the basin of attraction for unbounded, periodic, and chaotic solutions, respectively.
Figure 8.
Basin of attraction of the oscillator; green, dark blue, and cyan regions show the basin of attraction for unbounded, periodic, and chaotic solutions, respectively.
Figure 9.
Description of the proposed cryptosystem for multimedia images.
Figure 9.
Description of the proposed cryptosystem for multimedia images.
Figure 10.
Experimented image dataset of dimensional 768 × 512, in which the first row denotes the plain images, while the second row describes the corresponding ciphered images.
Figure 10.
Experimented image dataset of dimensional 768 × 512, in which the first row denotes the plain images, while the second row describes the corresponding ciphered images.
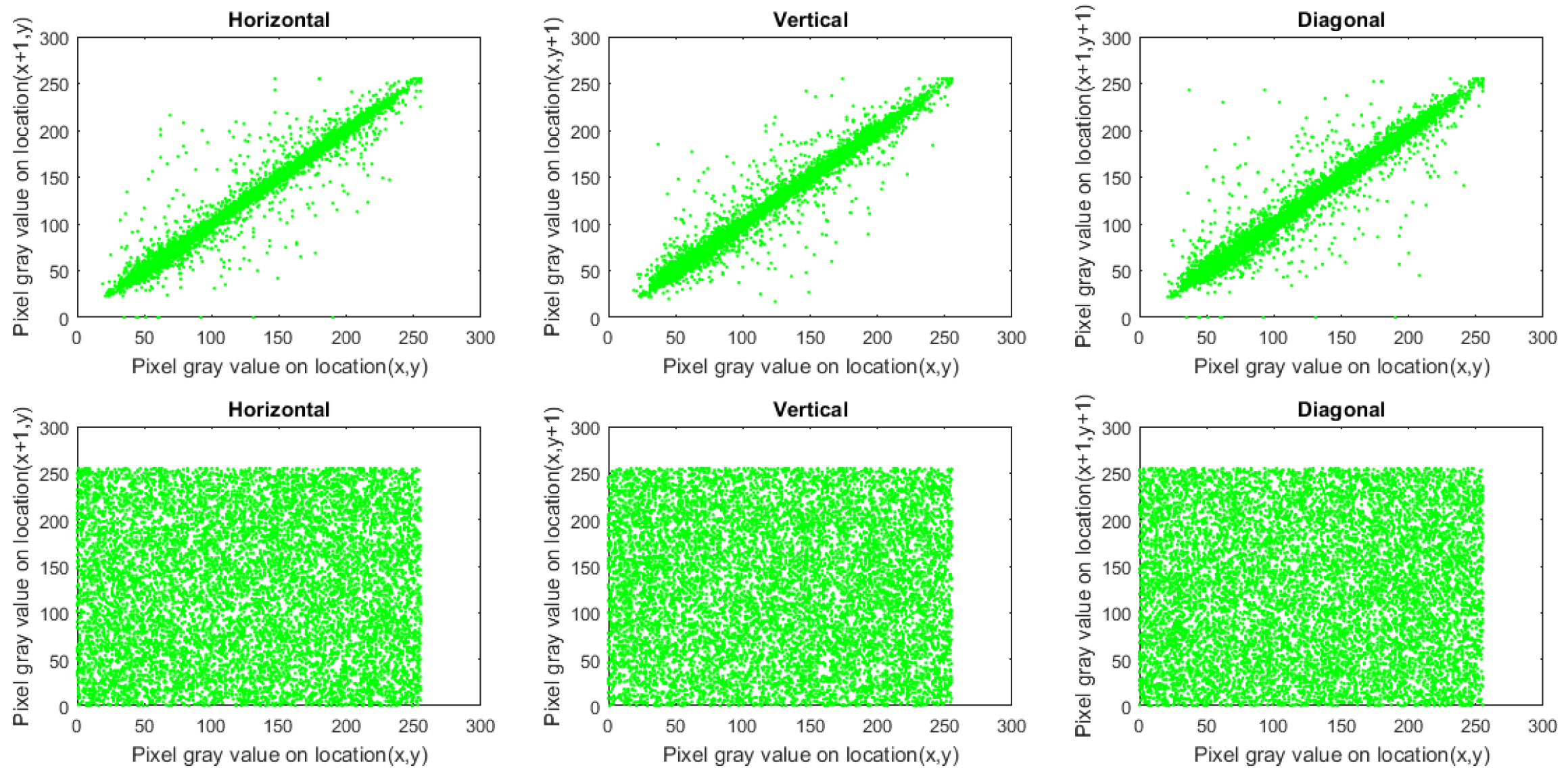
Figure 11.
Plots of correlation distribution (in each direction) for Macaws image (Red channel), in which the first row denotes the plain Macaws image, while the bottom row signifies the ciphered Macaws image.
Figure 11.
Plots of correlation distribution (in each direction) for Macaws image (Red channel), in which the first row denotes the plain Macaws image, while the bottom row signifies the ciphered Macaws image.
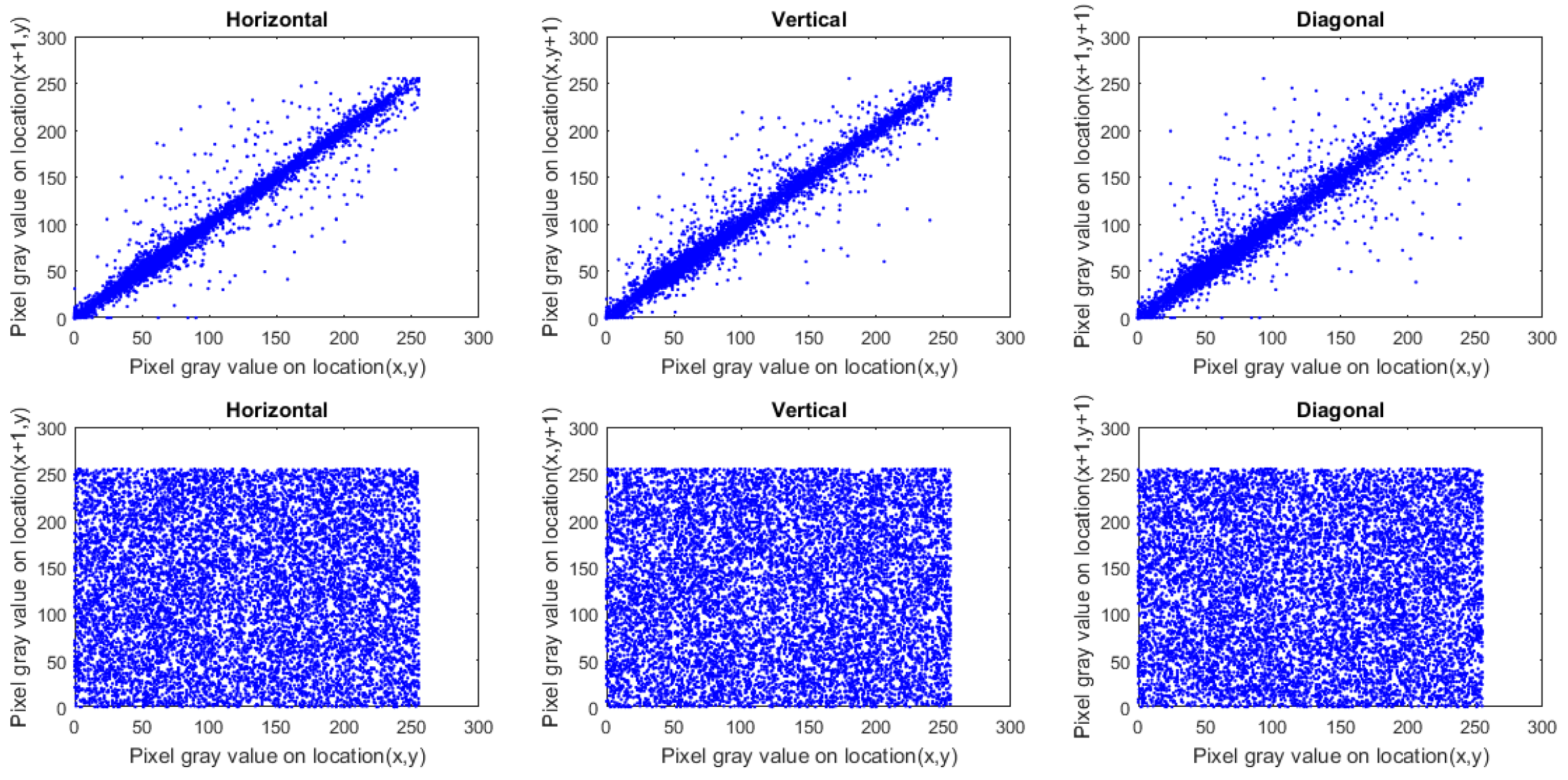
Figure 12.
Plots of correlation distribution (in each direction) for Macaws image (Green channel), in which the first row denotes the plain Macaws image, while the bottom row signifies the ciphered Macaws image.
Figure 12.
Plots of correlation distribution (in each direction) for Macaws image (Green channel), in which the first row denotes the plain Macaws image, while the bottom row signifies the ciphered Macaws image.
Figure 13.
Plots of correlation distribution (in each direction) for Macaws image (Blue channel), in which the first row denotes the plain Macaws image, while the bottom row signifies the ciphered Macaws image.
Figure 13.
Plots of correlation distribution (in each direction) for Macaws image (Blue channel), in which the first row denotes the plain Macaws image, while the bottom row signifies the ciphered Macaws image.
Figure 14.
Outcomes of decrypting Cipher–Macaws image using slight changes in the confidential key. (a) The confidential key; (b) The confidential key except = 0.627500000000001; (c) The confidential key except = 0.3854000000000001; (d) The confidential key except = 0.7261000000000001; (e) The confidential key except = 0.627499999999999; (f) The confidential key except = 0.38539999999999.
Figure 14.
Outcomes of decrypting Cipher–Macaws image using slight changes in the confidential key. (a) The confidential key; (b) The confidential key except = 0.627500000000001; (c) The confidential key except = 0.3854000000000001; (d) The confidential key except = 0.7261000000000001; (e) The confidential key except = 0.627499999999999; (f) The confidential key except = 0.38539999999999.
Figure 15.
Plots of histograms for experimented images, in which the left three columns except the first one represent the histograms of plain images, while the right three columns represent the histograms of cipher images.
Figure 15.
Plots of histograms for experimented images, in which the left three columns except the first one represent the histograms of plain images, while the right three columns represent the histograms of cipher images.
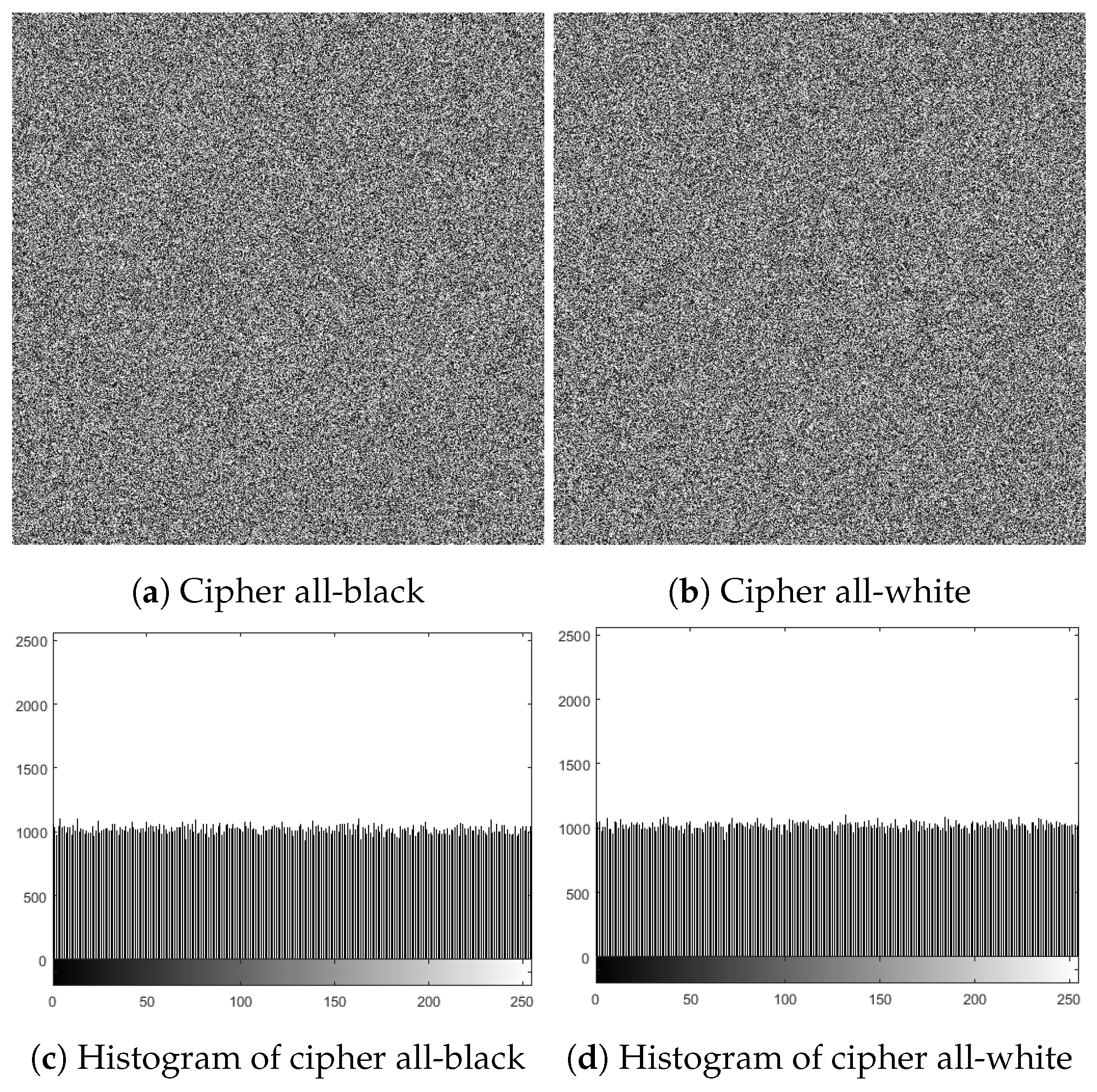
Figure 16.
Ciphers of all-black and all-white images, and their analog histograms.
Figure 16.
Ciphers of all-black and all-white images, and their analog histograms.
Figure 17.
Outcomes of noise attack, in which the top row refers to the defective Cipher–Macaws image by adding Salt and Pepper noise with variable densities (D) while the bottom row represents the corresponding decipher image.
Figure 17.
Outcomes of noise attack, in which the top row refers to the defective Cipher–Macaws image by adding Salt and Pepper noise with variable densities (D) while the bottom row represents the corresponding decipher image.
Figure 18.
Outcomes of data loss attack, in which the top row refers to the defective Cipher–Macaws image by performing a cutting block for data with various sizes, while the bottom row represents the corresponding decipher image.
Figure 18.
Outcomes of data loss attack, in which the top row refers to the defective Cipher–Macaws image by performing a cutting block for data with various sizes, while the bottom row represents the corresponding decipher image.
Table 1.
Comparison of time encryption for the presented cryptosystem with other related cryptosystems, as reported in [
30,
31,
32].
Table 1.
Comparison of time encryption for the presented cryptosystem with other related cryptosystems, as reported in [
30,
31,
32].
| Image Cryptosystem | Number of Encrypted Bits Per Second |
|---|
| Proposed | 9,713,394 |
| Ref. [30] | 8,025,072 |
| Ref. [31] | 6,381,110 |
| Ref. [32] | 4,224,509 |
Table 2.
Outcomes of randomness test.
Table 2.
Outcomes of randomness test.
| Test-Name | p-Value | Passed |
|---|
| Key Stream | Cipher-Macaws |
|---|
| Runs | 0.7913189 | 0.5294244 | √ |
| DFT | 0.6543473 | 0.6036850 | √ |
| Linear complexity | 0.7024604 | 0.1581112 | √ |
| Block-frequency | 0.5686530 | 0.3487918 | √ |
| Frequency | 0.6559749 | 0.4300353 | √ |
| Universal | 0.3457104 | 0.9949709 | √ |
| Serial test 1 | 0.3920807 | 0.3989737 | √ |
| Serial test 2 | 0.5967691 | 0.5770354 | √ |
| Overlapping templates | 0.7827032 | 0.4365690 | √ |
| No overlapping templates | 0.9636127 | 0.5941496 | √ |
| Long runs of ones | 0.3969673 | 0.7129090 | √ |
| Approximate entropy | 0.2772607 | 0.1420810 | √ |
| Rank | 0.0996206 | 0.5740640 | √ |
| Random excursions variant x = 1 | 0.0963609 | 0.6213966 | √ |
| Random excursions x = 1 | 0.3570832 | 0.8722024 | √ |
| Cumulative sums (reverse) | 0.0620619 | 0.5399098 | √ |
| Cumulative sums (forward) | 0.1740884 | 0.7368549 | √ |
Table 3.
Correlation coefficient of neighboring pixels for the experimented images.
Table 3.
Correlation coefficient of neighboring pixels for the experimented images.
| Image | Direction |
|---|
| Hor. | Ver. | Dia. |
|---|
| R | G | B | R | G | B | R | G | B |
|---|
| Macaws | 0.98685 | 0.98074 | 0.98562 | 0.98874 | 0.98460 | 0.98550 | 0.98024 | 0.97349 | 0.97804 |
| Cipher-Macaws | −0.00001 | −0.00005 | 0.00073 | 0.00026 | 0.00051 | −0.00078 | −0.00010 | 0.00056 | −0.00125 |
| Chalet | 0.93698 | 0.92077 | 0.91862 | 0.94179 | 0.93844 | 0.92290 | 0.91195 | 0.90044 | 0.89372 |
| Cipher-Chalet | 0.00083 | −0.00002 | 0.00006 | 0.00044 | −0.00044 | 0.00114 | −0.00017 | −0.00018 | 0.00058 |
| Window | 0.95772 | 0.94235 | 0.95532 | 0.97114 | 0.96285 | 0.96658 | 0.93616 | 0.92107 | 0.93504 |
| Cipher-Window | 0.00087 | −0.00088 | −0.00066 | 0.00012 | 0.00062 | 0.00144 | 0.00007 | 0.00033 | −0.00008 |
| Houses | 0.92373 | 0.92224 | 0.90793 | 0.88870 | 0.88994 | 0.86135 | 0.82085 | 0.81976 | 0.77976 |
| Cipher-Houses | 0.00085 | −0.00004 | −0.00066 | 0.00059 | 0.00072 | 0.00061 | −0.00040 | 0.00128 | −0.00075 |
Table 4.
Outcomes of NPCR and UNCI.
Table 4.
Outcomes of NPCR and UNCI.
| Image | NPCR | UNCI |
|---|
| Macaws | 99.60556% | 33.49106% |
| Chalet | 99.61565% | 33.45562% |
| Window | 99.60988% | 33.47213% |
| Houses | 99.60751% | 33.44994% |
Table 5.
outcomes for the investigated images.
Table 5.
outcomes for the investigated images.
| Image | Value | Outcome |
|---|
| Red | Green | Blue |
|---|
| Macaws | 303,687.9661 | 254,324.4518 | 603,349.4934 | Irregular |
| Chalet | 817,766.5013 | 677,362.4271 | 616,936.1705 | Irregular |
| Window | 515,942.4335 | 551,843.4661 | 728,008.0781 | Irregular |
| Houses | 285,277.4635 | 219,680.6289 | 221,228.6081 | Irregular |
| Cipher-Macaws | 244.5221 | 251.6953 | 233.6315 | Regular |
| Cipher-Chalet | 258.3451 | 215.8021 | 243.8919 | Regular |
| Cipher-Window | 209.8372 | 277.1874 | 254.2682 | Regular |
| Cipher-Houses | 226.9335 | 248.9882 | 241.1497 | Regular |
Table 6.
Local and global information entropies.
Table 6.
Local and global information entropies.
| Image | Global Entropy | Local Entropy |
|---|
| Plain | Cipher | Plain | Cipher |
|---|
| Macaws | 7.601941 | 7.999837 | 5.396978 | 7.902671 |
| Chalet | 7.136653 | 7.999834 | 5.673345 | 7.903744 |
| Window | 7.309858 | 7.999855 | 5.441143 | 7.902341 |
| Houses | 7.673795 | 7.999874 | 6.552062 | 7.902232 |
Table 7.
Statistical analyses of the cipher all-black and all-white images.
Table 7.
Statistical analyses of the cipher all-black and all-white images.
| Image | Correlation | Value | Entropy |
|---|
| Hor. | Ver. | Dia. | Global | Local |
|---|
| All-black | −0.0002 | −0.0004 | 0.0001 | 267.7656 | 7.99926 | 7.90340 |
| All-white | 0.0006 | 0.0001 | 0.0004 | 226.8008 | 7.99937 | 7.90343 |