Recent Advances in Evolving Computing Paradigms: Cloud, Edge, and Fog Technologies
Abstract
1. Introduction
2. Contribution of This Survey
- A comprehensive account of computing paradigms is rendered, especially cloud computing, fog computing, edge computing, and how they are related to other similar paradigms such as mist, cloudlet, MEC, etc.
- A detailed illustration of the motives that instigated the evolution of edge/fog computing and related paradigms is furnished.
- A comparison of cloud, edge, and fog computing paradigms are presented and ML convergence’s significance with fog/edge is discussed.
- A list of challenges and future research directions concerning computing paradigms is devised.
2.1. Survey Methodology
2.1.1. Search Strategy and Literature Sources
2.1.2. Inclusion Criteria
2.1.3. Elimination Criteria
2.1.4. Results
3. Evolving Computing Paradigms and Related Concepts
3.1. Cloud Computing
- Software as a service (SaaS)—the cloud provider presents consumers with applications accessible via the program interface or web browser, and the consumer has limited control over user-specific applications.
- Platform as a service (PaaS)—On the cloud infrastructure, the consumers are allowed to build and distribute applications. They can exercise control on applications deployed but not on the cloud infrastructure.
- Infrastructure as a service (IaaS)—The customer is furnished with essential computing resources vital to processing, storing, and networking. The user exercises control upon storage, applications, and operating systems, but not cloud infrastructure. The cloud service models and deployment models are depicted in Figure 4.
- Private cloud—a particular organization that can also be a third party exclusively owns and controls the private cloud, which can be available on or off-premises.
- Community cloud—the specific community comprises of organizations that share common concerns may provide cloud infrastructure for exclusive usage available on or off-premises, managed by organizations within the community or by a third party.
- Public cloud—the public cloud available on the cloud provider’s premises can be owned or managed by any enterprise and is open to the use of the general public.
- Hybrid cloud—it may be composed of two or more cloud models (private, community, or public); although they are distinct entities, they are bound by technology permitting the portability of application as well as data.
3.2. Internet-of-Things
3.2.1. Essential Features
- Interconnectivity—the IoT may be connected to global communication infrastructure.
- Things-related services—IoT is adept at offering physical/virtual things, privacy, as well as semantic consistency services within the limits of things.
- Heterogeneity—the IoT devices pertain to diverse hardware platforms and networks.
- Constrained resources—the IoT devices encounter computational and energy restrictions.
- Dynamic change—the state of devices and the related environment are subject to dynamic change.
- Uncontrolled environment—the IoT devices are deployed in an uncontrolled setting.
- Massive scale—the devices to be monitored and those that connect with one another are enormous and will continue to surge exponentially into the future.
3.2.2. New Challenges in IoT
- High network bandwidth—The escalating amount of IoT devices produce sizable data [50], which may be rendered useless due to high bandwidth usage to transfer it to the cloud or denied due to privacy concerns; hence, entails to be dealt with locally.
- Limited resources—numerous IoT-connected devices possess limited resources to interact directly with the cloud, demanding intensive computation and complex protocols.
- IT and OT convergence—In industrial systems, the confluence of information technology (IT) and operational technology (OT) creates new needs. As offline systems may cause business loss or consumer annoyance, contemporary cyber-physical systems demand continual and safe operation. Thus, the upgradation of the system software and hardware causes concern.
- Intermittent connectivity—When IoT devices have intermittent network connectivity, it is difficult to provide uninterrupted cloud services to those devices.
- Geographical distribution—the majority of IoT devices entail services of computing and storage that are dispersed across large geographic areas, and it is highly challenging to position them at a location that meets IoT demands [51].
- Context-awareness—Local contextual data must be accessed and processed by IoT applications (vehicular networks and augmented reality), for which the physical distance between IoT devices and the centralized cloud is a hindrance.
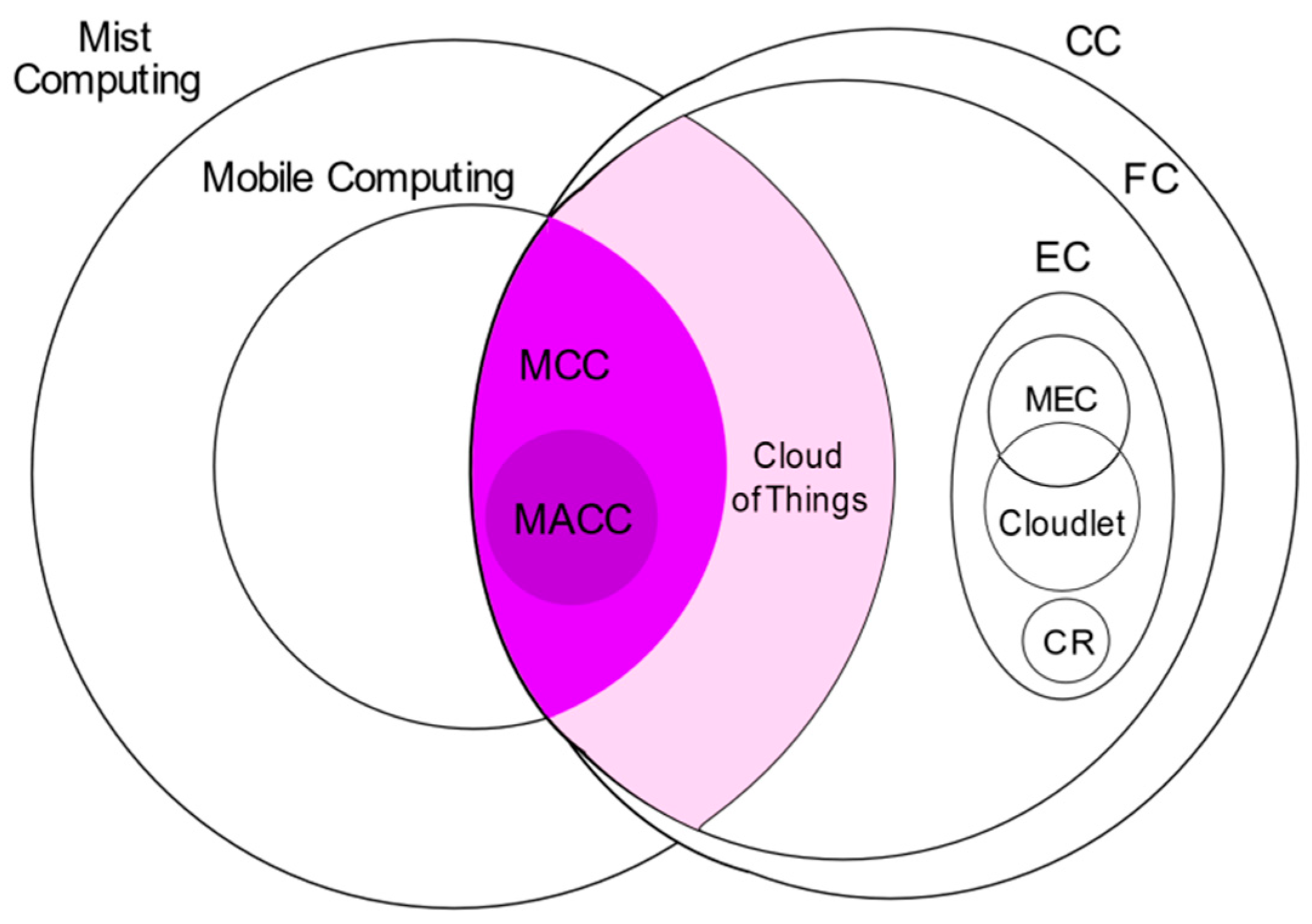
3.3. Mobile Computing
3.4. Mobile Cloud Computing
3.5. Mobile Ad hoc Cloud Computing
3.6. Cloud of Things
3.7. Mist Computing
3.8. Edge Computing
3.9. Multi-Access Edge Computing (MEC)
3.10. Cloudlet
3.11. Cloud Robotics
3.12. Fog Computing
3.12.1. Essential Features
- Low latency: The proximity of fog nodes to end devices that generate data, such as sensors and actuators, entails a significantly faster reaction and analysis than from the centralized cloud data center. This feature considerably minimizes the data transfer across the internet and enables a low latency to manage real-time applications, notably sensitive to latency and time.
- Save bandwidth: As the fog model allows data computation and storage between conventional cloud and end nodes, less complex pre-processing tasks are handled locally. It dramatically minimizes data transfer across the internet, with endpoints offering fast and premium localized computer and storage services. Transferring only appropriate data to the cloud substantially reduces the network transmission and bandwidth usage, befitting the big data era.
- Multi-tenancy: On account of the vastly virtualized and distributed infrastructure, multi-tenancy in a constrained environment is possible.
- Support for mobility: Due to the direct interaction between fog applications and mobile devices, more control over mobile devices is maintained. Thus, the fog model facilitates better control of users along with mobile devices to administrators and satisfies mobility demands that are location-based and the way information is accessed, resulting in enhanced system performance and service quality.
- Interaction in real-time: Contrary to the cloud, fog applications deliver services in real-time because of their low-latency feature.
- Context-awareness: the nodes and end devices in the fog setting are aware of the contextual location.
- Geographically wide distribution: The fog model’s decentralized architecture facilitates geographically distributed deployment with a large number of widely dispersed nodes. It imparts closer data analysis, rapid big data processing, improved decision-making potential in real-time and location-based services to consumers.
- Wireless access networking: Though fog is deployed in wired environments, it is also suitable for IoT wireless networks.
- Support for heterogeneity: The fog infrastructure encompasses high-speed lines to the data center and wireless access methods to the edge devices. Fog nodes are available physically or virtually, and service interfaces are incredibly dynamic, operating in wired and wireless settings coming from different hardware and software vendors and heterogeneous to cater to the low latency demand of globally distributed applications.
- Seamless interoperability and federation: Owing to its heterogeneous nature, fog nodes and devices originate from various vendors and are generally deployed in diverse settings. For the effective interaction of devices from different providers, fog computing must enable interoperability with federated services across domains. Thus, to allow interoperability and cooperation across diverse resources and devices, fog computing employs policies for resource management.
- Real-time analytics: With data collected and processed close to the sources, real-time analytics is possible.
- Scalability: Fog computing exhibits scalability and adaptability to varying conditions with the data load, resource pooling, network demands, and flexible computing.
- Support for industrial applications: As computing and analyses are conducted in real-time, industrial applications widely benefit.
- Security and privacy: Fog computing brings facilities nearer to end consumers while ensuring privacy and security of sensitive and private data using integrity checking, access control, and encryption methods by fog nodes. Moreover, it can mitigate the vulnerabilities associated with system upgrades and limit updates at the fog end.
- Low energy consumption: as fog nodes are spatially distributed and do not require a cooling system, fog computing is more ecologically friendly; communication within a short-range as well as energy management rules obviously minimize the communication energy use.
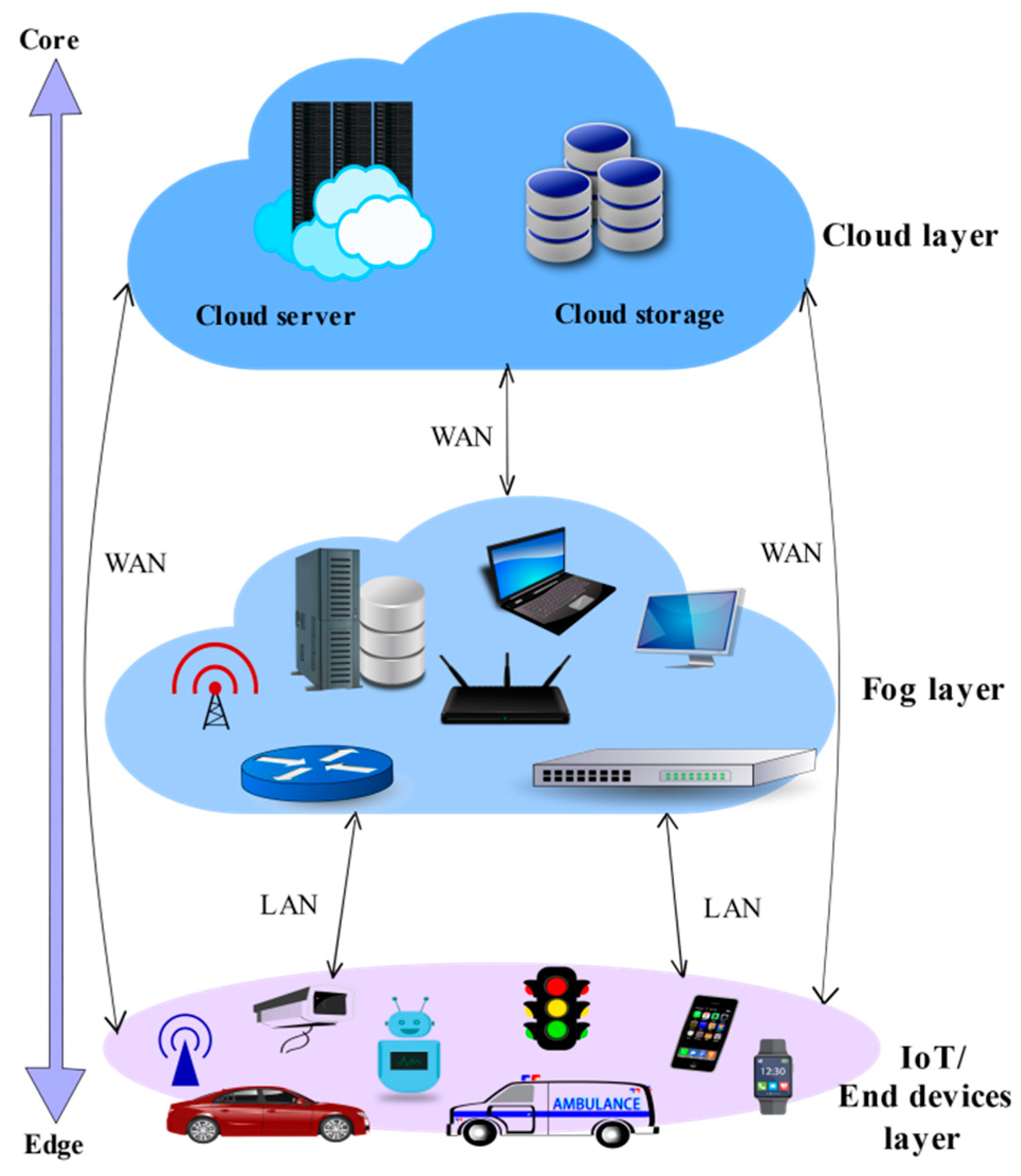
3.12.2. Architecture
- Three-Layer Architecture
- IoT Layer
- b.
- Fog Layer
- c.
- Cloud Layer
- 2.
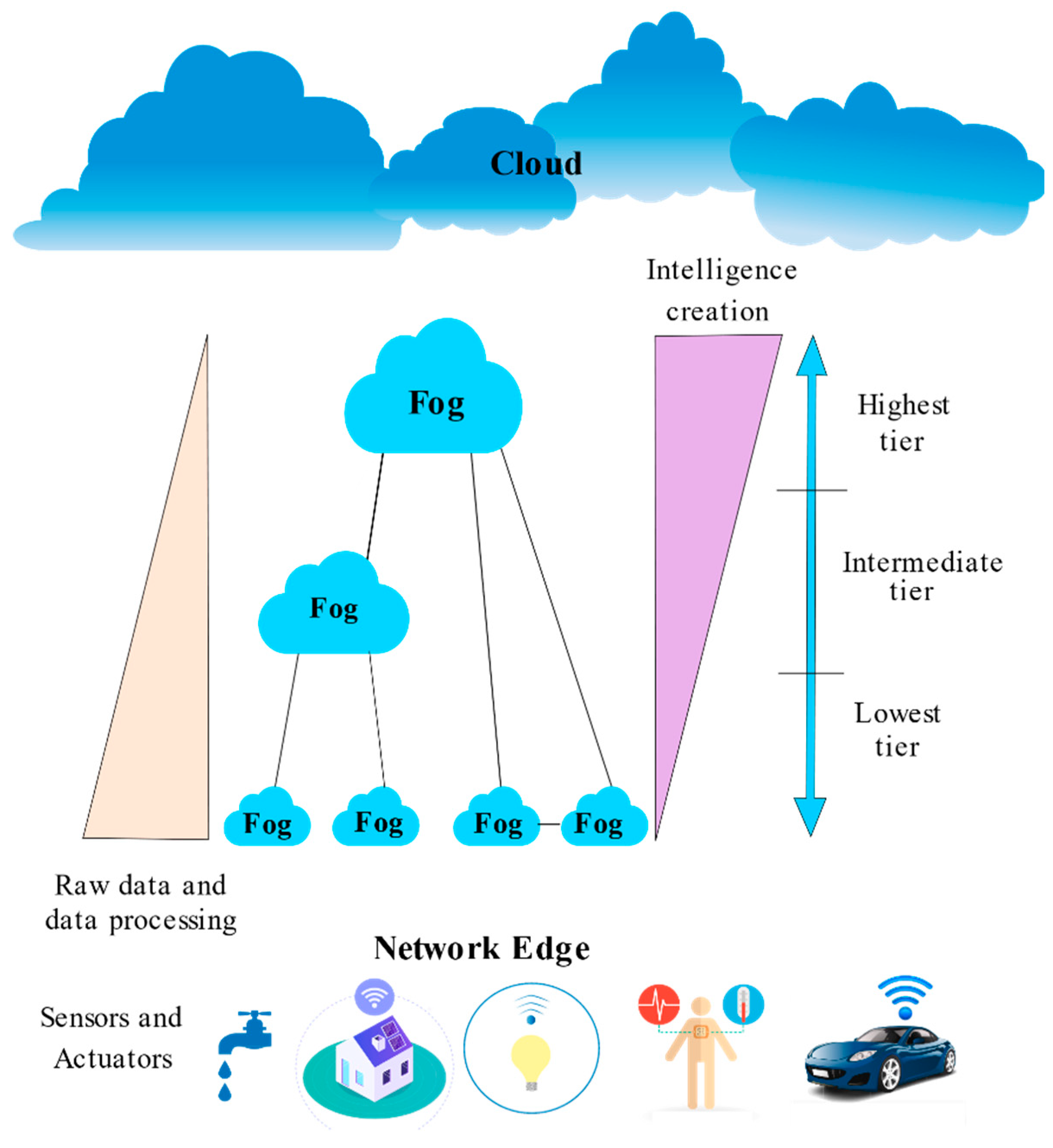
- OpenFog N-Tier Architecture
- Lowest tier: with the primary focus on the acquisition, normalization, and collection of data obtained at the sensors, and the actuators are managed by fog nodes.
- Intermediate tier: filtering, compressing, and altering data received from the bottom layer is the responsibility of fog nodes in the intermediate tier; on average, these nodes are better at analyzing data.
- Highest tier: aggregating data and eliciting knowledge from it is the intent of fog nodes at this tier.
- 3.
- Seven-Layer Architecture
- Physical layer
- b.
- Fog device, server, and gateway layer
- c.
- Monitoring layer
- d.
- Pre- and post-processing layer
- e.
- Storage layer
- f.
- Resource management layer
- g.
- Security layer
- h.
- Application Layer
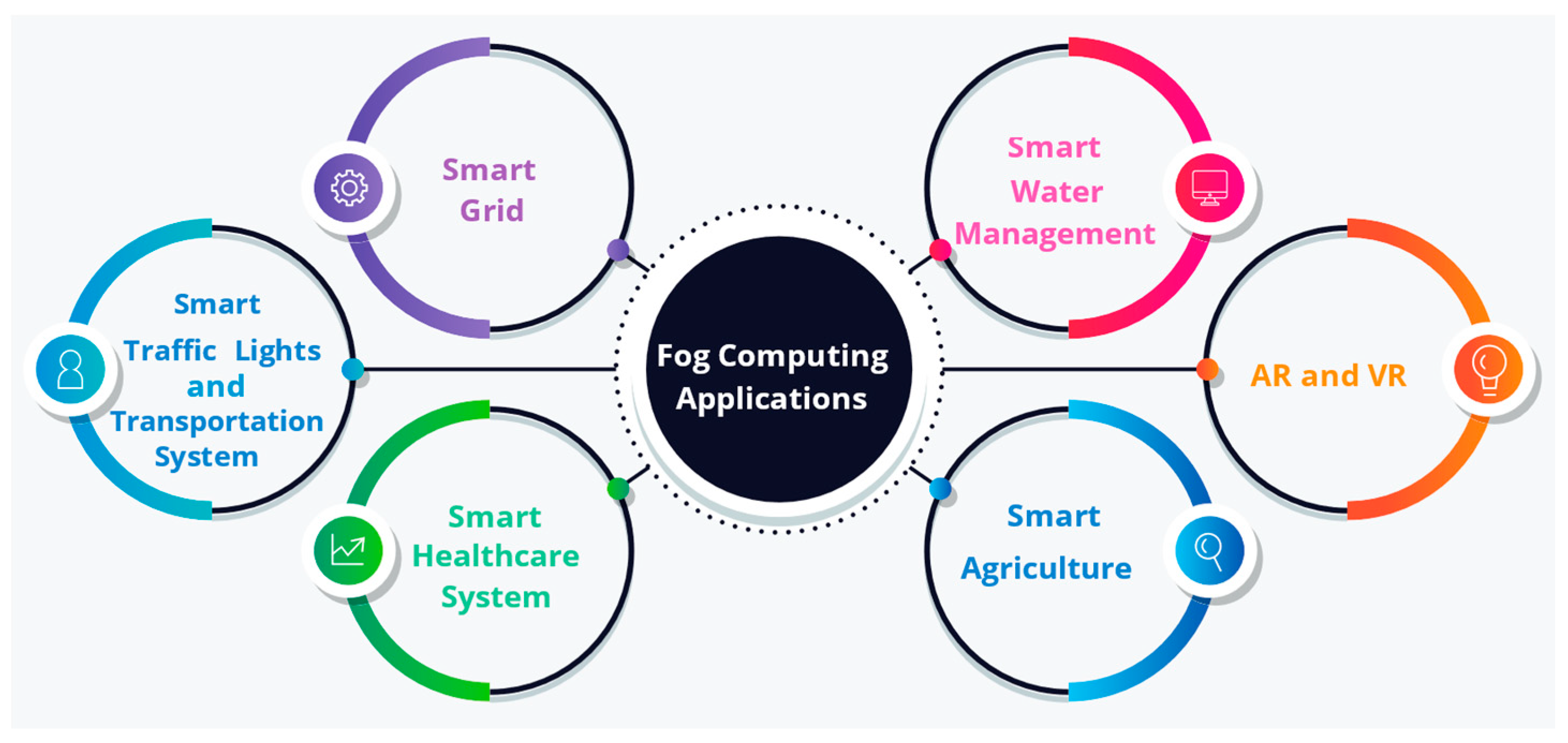
3.12.3. Fog Computing Applications
- Smart grid
- b.
- Smart traffic lights and transportation systems
- c.
- Augmented reality (AR) and virtual reality (VR)
- d.
- Smart healthcare system
- e.
- Smart agriculture
- f.
- Smart water management
4. Challenges and Opportunities
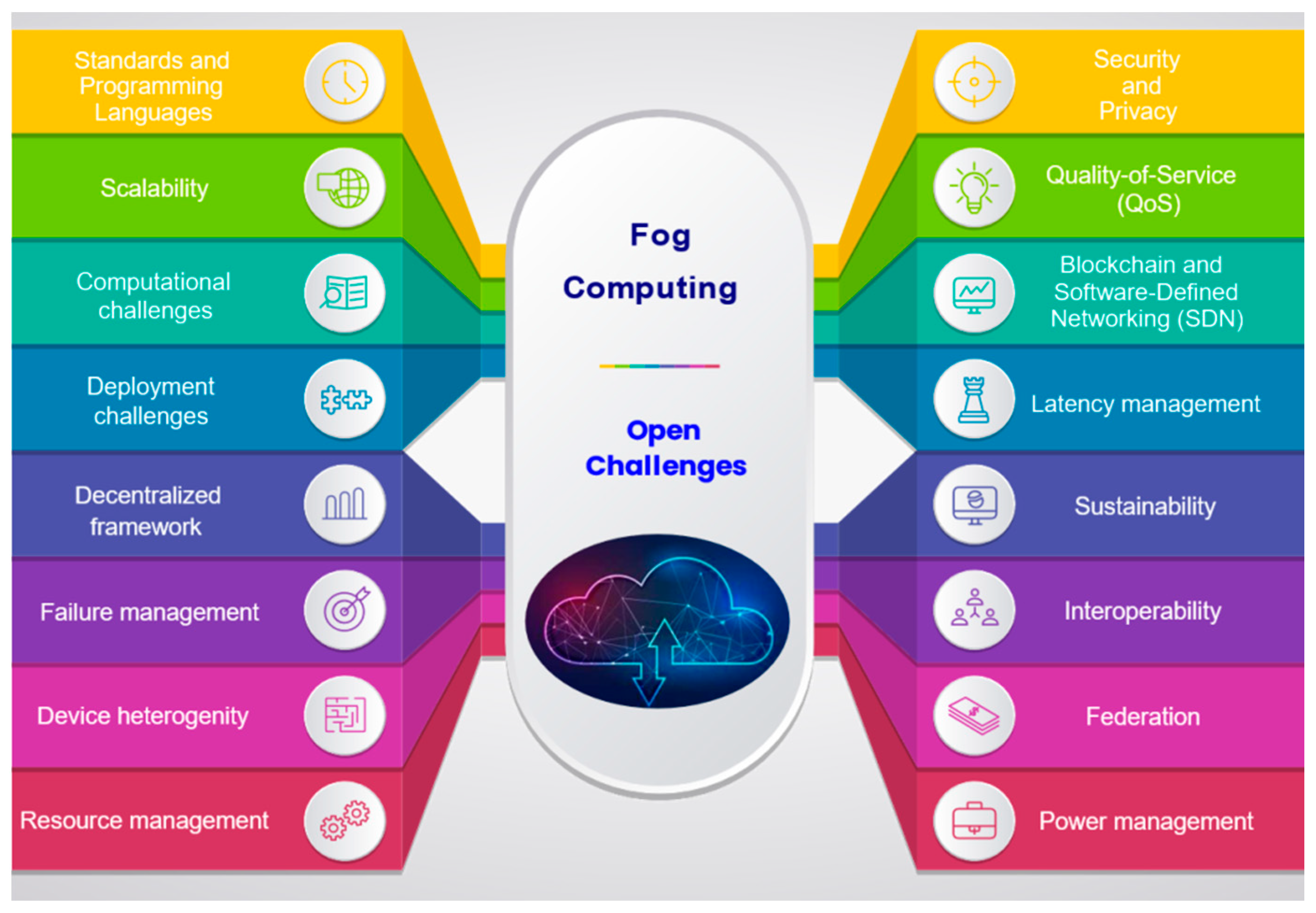
4.1. Fog Computing: Open Challenges
- Standards and programming languages
- Scalability
- Computational challenges
- Deployment challenges
- Decentralized framework and failure management
- Device heterogeneity and resource management
- Security and privacy
- QoS
- Blockchain and Software-Defined Networking (SDN)
- Latency management
- Sustainability
- Interoperability and federation of fog
- Power management
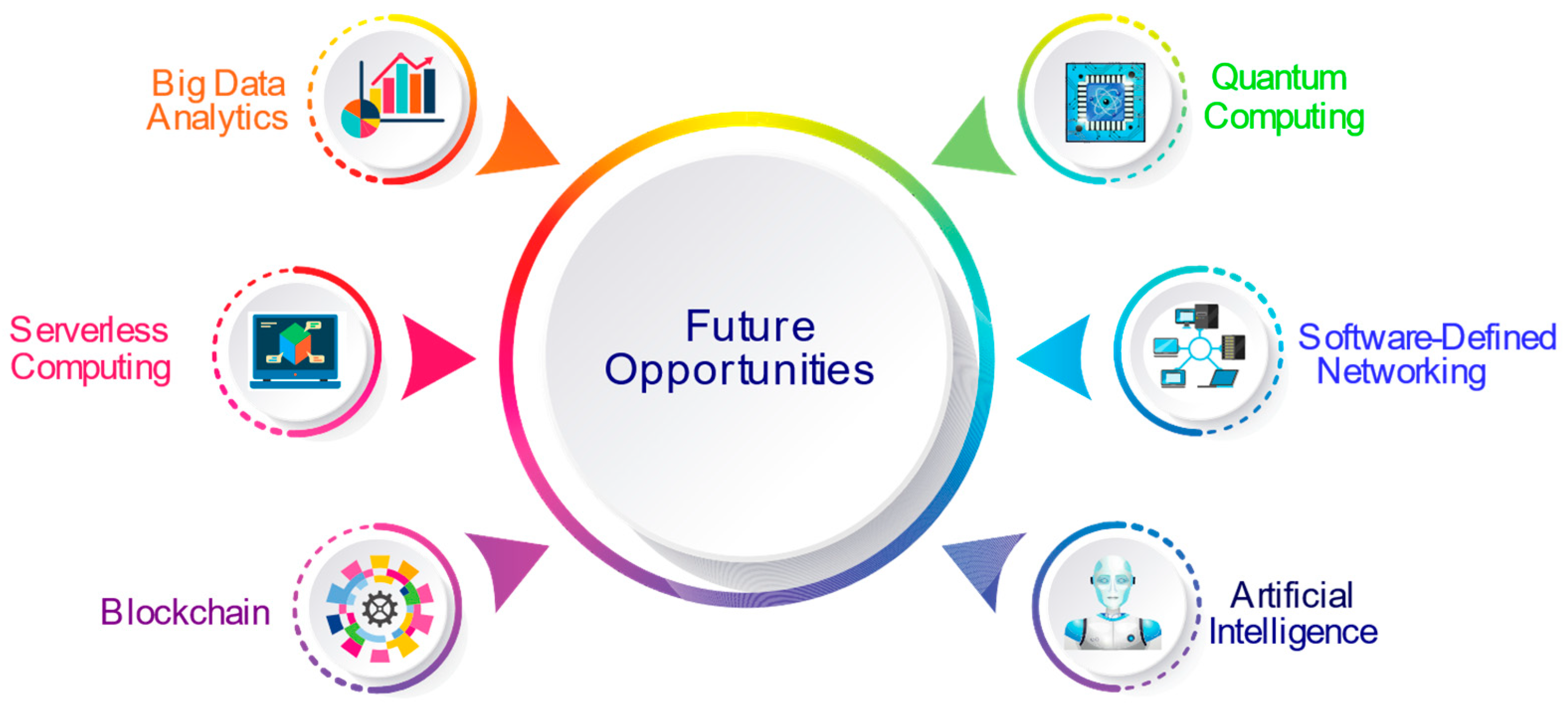
4.2. Future Prospects of Fog/Edge Computing
4.2.1. Big Data Analytics
4.2.2. Serverless Computing
4.2.3. Blockchain
4.2.4. Quantum Computing
4.2.5. Software-Defined Networking
4.2.6. Artificial Intelligence (AI)
5. Sustainable/Green Computing in Fog/Edge
5.1. Energy Sustainability
5.2. Security Sustainability
6. Confluence of ML and Fog/Edge
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I.; et al. A View of Cloud Computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All One Needs to Know about Fog Computing and Related Edge Computing Paradigms: A Complete Survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Ortiz, G.; Zouai, M.; Kazar, O.; Garcia-de-Prado, A. Atmosphere: Context and Situational-Aware Collaborative IoT Architecture for Edge-Fog-Cloud Computing. Comput. Stand. Interfaces 2022, 79, 103550. [Google Scholar] [CrossRef]
- Berger, C.; Eichhammer, P.; Reiser, H.P.; Domaschka, J.; Hauck, F.J.; Habiger, G. A Survey on Resilience in the IoT: Taxonomy, Classification, and Discussion of Resilience Mechanisms. ACM Comput. Surv. 2022, 54, 1–39. [Google Scholar] [CrossRef]
- Fersi, G. Fog Computing and Internet of Things in One Building Block: A Survey and an Overview of Interacting Technologies. Cluster Comput. 2021, 24, 2757–2787. [Google Scholar] [CrossRef]
- Sen, A.A.A.; Yamin, M. Advantages of Using Fog in IoT Applications. Int. J. Inf. Tecnol. 2021, 13, 829–837. [Google Scholar] [CrossRef]
- Shi, W.; Dustdar, S. The Promise of Edge Computing. Computer 2016, 49, 78–81. [Google Scholar] [CrossRef]
- Dolui, K.; Datta, S.K. Comparison of Edge Computing. In 2017 Global Internet of Things Summit (GIoTS); IEEE: Geneva, Switzerland, 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, Y.; Fieldsend, J.E.; Min, G. A Framework of Fog Computing: Architecture, Challenges, and Optimization. IEEE Access 2017, 5, 25445–25454. [Google Scholar] [CrossRef]
- IEEE Standard 1934–2018; IEEE Standard for Adoption of OpenFog Reference Architecture for Fog Computing. 2018; pp. 1–176. Available online: https://ieeexplore.ieee.org/document/8423800 (accessed on 22 December 2021).
- Okewu, E.; Misra, S.; Maskeliūnas, R.; Damaševičius, R.; Fernandez-Sanz, L. Optimizing Green Computing Awareness for Environmental Sustainability and Economic Security as a Stochastic Optimization Problem. Sustainability 2017, 9, 1857. [Google Scholar] [CrossRef]
- Venckauskas, A.; Stuikys, V.; Damasevicius, R.; Jusas, N. Modelling of Internet of Things Units for Estimating Security-Energy-Performance Relationships for Quality of Service and Environment Awareness: Modelling of IoT Units for Estimating Quality of Service. Secur. Comm. Netw. 2016, 9, 3324–3339. [Google Scholar] [CrossRef]
- Maskeliūnas, R.; Damaševičius, R.; Segal, S. A Review of Internet of Things Technologies for Ambient Assisted Living Environments. Future Internet 2019, 11, 259. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. Understanding the Internet of Things: Definition, Potentials, and Societal Role of a Fast Evolving Paradigm. Ad Hoc Netw. 2017, 56, 122–140. [Google Scholar] [CrossRef]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on Fog Computing: Architecture, Key Technologies, Applications and Open Issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog Computing: A Taxonomy, Survey and Future Directions. In Internet of Everything. Internet of Things (Technology, Communications and Computing); Di Martino, B., Li, K.-C., Yang, L.T., Esposito, A., Eds.; Springer: Singapore, 2018; pp. 103–130. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A Survey on Mobile Edge Computing: The Communication Perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef]
- Yong, B.; Wei, W.; Li, K.C.; Shen, J.; Zhou, Q.; Wozniak, M.; Damaševičius, R. Ensemble machine learning approaches for webshell detection in Internet of things environments. Trans. Emerg. Telecommun. Technol. 2020, e4085. [Google Scholar] [CrossRef]
- Mouradian, C.; Naboulsi, D.; Yangui, S.; Glitho, R.H.; Morrow, M.J.; Polakos, P.A. A Comprehensive Survey on Fog Computing: State-of-the-Art and Research Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 416–464. [Google Scholar] [CrossRef]
- Mukherjee, M.; Shu, L.; Wang, D. Survey of Fog Computing: Fundamental, Network Applications, and Research Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 1826–1857. [Google Scholar] [CrossRef]
- Elazhary, H. Internet of Things (IoT), Mobile Cloud, Cloudlet, Mobile IoT, IoT Cloud, Fog, Mobile Edge, and Edge Emerging Computing Paradigms: Disambiguation and Research Directions. J. Netw. Comput. Appl. 2019, 128, 105–140. [Google Scholar] [CrossRef]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog Computing and the Internet of Things: A Review. Big Data Cogn. Comput. 2018, 2, 10. [Google Scholar] [CrossRef]
- Bangui, H.; Rakrak, S.; Raghay, S.; Buhnova, B. Moving to the Edge-Cloud-of-Things: Recent Advances and Future Research Directions. Electronics 2018, 7, 309. [Google Scholar] [CrossRef]
- Abdulkareem, K.H.; Mohammed, M.A.; Gunasekaran, S.S.; Al-Mhiqani, M.N.; Mutlag, A.A.; Mostafa, S.A.; Ali, N.S.; Ibrahim, D.A. A Review of Fog Computing and Machine Learning: Concepts, Applications, Challenges, and Open Issues. IEEE Access 2019, 7, 153123–153140. [Google Scholar] [CrossRef]
- Khan, W.Z.; Ahmed, E.; Hakak, S.; Yaqoob, I.; Ahmed, A. Edge Computing: A Survey. Future Gener. Comput. Syst. 2019, 97, 219–235. [Google Scholar] [CrossRef]
- Cao, K.; Liu, Y.; Meng, G.; Sun, Q. An Overview on Edge Computing Research. IEEE Access 2020, 8, 85714–85728. [Google Scholar] [CrossRef]
- Yunana, K.; Alfa, A.A.; Misra, S.; Damasevicius, R.; Maskeliunas, R.; Oluranti, J. Internet of Things: Applications, Adoptions and Components—A Conceptual Overview. In Hybrid Intelligent Systems. HIS Advances in Intelligent Systems and Computing; Abraham, A., Hanne, T., Castillo, O., Gandhi, N., Nogueira Rios, T., Hong, T.P., Eds.; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Moura, J.; Hutchison, D. Fog Computing Systems: State of the Art, Research Issues and Future Trends, with a Focus on Resilience. J. Netw. Comput. Appl. 2020, 169, 102784. [Google Scholar] [CrossRef]
- Aslanpour, M.S.; Gill, S.S.; Toosi, A.N. Performance Evaluation Metrics for Cloud, Fog and Edge Computing: A Review, Taxonomy, Benchmarks and Standards for Future Research. Internet Things 2020, 12, 100273. [Google Scholar] [CrossRef]
- Alli, A.A.; Alam, M.M. The Fog Cloud of Things: A Survey on Concepts, Architecture, Standards, Tools, and Applications. Internet Things 2020, 9, 100177. [Google Scholar] [CrossRef]
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing; National Institute of Standards & Technology: Gaithersburg, MA, USA, 2011; p. 2. [Google Scholar]
- Liu, F.; Tong, J.; Mao, J.; Bohn, R.; Messina, J.; Badger, L.; Leaf, D. NIST Cloud Computing Reference Architecture. NIST Special Publication, Technology Report. 2011. Available online: https://bigdatawg.nist.gov/_uploadfiles/M0007_v1_3376532289.pdf (accessed on 14 September 2011).
- Dorsemaine, B.; Gaulier, J.-P.; Wary, J.-P.; Kheir, N.; Urien, P. Internet of Things: A Definition & amp; Taxonomy. In Proceedings of the 2015 9th International Conference on Next Generation Mobile Applications, Services and Technologies, Cambridge, UK, 9–11 September 2015; IEEE: Cambridge, UK, 2015; pp. 72–77. [Google Scholar] [CrossRef]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of Things (IoT) Security: Current Status, Challenges and Prospective Measures. In Proceedings of the 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015; pp. 336–341. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A Vision, Architectural Elements, and Future Directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Recommendation-ITU-T Y.2060 Overview of the Internet of Things, Document, International Telecommunication Union. June 2012. Article No. E 38086. Available online: https://www.itu.int/rec/T-REC-Y.2060-201206-I (accessed on 15 June 2012).
- Khan, W.Z.; Aalsalem, M.Y.; Khan, M.K.; Arshad, Q. Enabling Consumer Trust upon Acceptance of IoT Technologies through Security and Privacy Model. In Advanced Multimedia and Ubiquitous Engineering; Park, J.J., Jin, H., Jeong, Y.-S., Khan, M.K., Eds.; Lecture Notes in Electrical Engineering; Springer Singapore: Singapore, 2016; Volume 393, pp. 111–117. [Google Scholar] [CrossRef]
- Saichaitanya, P.; Karthik, N.; Surender, D. Recent Trends in Iot. J. Inf. Comput. Sci. 2016, 9, 9. [Google Scholar]
- Khan, N.; Naim, A.; Hussain, M.R.; Naveed, Q.N.; Ahmad, N.; Qamar, S. The 51 V’s Of Big Data: Survey, Technologies, Characteristics, Opportunities, Issues and Challenges. In Proceedings of the International Conference on Omni-Layer Intelligent Systems, Crete, Greece, 5–7 May 2019; ACM: Crete, Greece, 2019; pp. 19–24. [Google Scholar] [CrossRef]
- Martinez, I.; Hafid, A.S.; Jarray, A. Design, Resource Management, and Evaluation of Fog Computing Systems: A Survey. IEEE Internet Things J. 2021, 8, 2494–2516. [Google Scholar] [CrossRef]
- Storey, V.C.; Song, I.-Y. Big Data Technologies and Management: What Conceptual Modeling Can Do. Data Knowl. Eng. 2017, 108, 50–67. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile Edge Computing, Fog et al.: A Survey and Analysis of Security Threats and Challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, New York, NY, USA, 17 August 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Chiang, M.; Zhang, T. Fog and IoT: An Overview of Research Opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Zhang, T.; Zheng, Y.; Zheng, R.; Antunes, H. Securing the Internet of Things: Need for a New Paradigm and Fog Computing. In Fog for 5G and IoT; Chiang, M., Balasubramanian, B., Bonomi, F., Eds.; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2017; pp. 261–283. [Google Scholar] [CrossRef]
- Puliafito, C.; Mingozzi, E.; Longo, F.; Puliafito, A.; Rana, O. Fog Computing for the Internet of Things: A Survey. ACM Trans. Internet Technol. 2019, 19, 1–41. [Google Scholar] [CrossRef]
- Weiner, M.; Jorgovanovic, M.; Sahai, A.; Nikolie, B. Design of a Low-Latency, High-Reliability Wireless Communication System for Control Applications. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; IEEE: Sydney, NSW, Australia, 2014; pp. 3829–3835. [Google Scholar] [CrossRef]
- Gedeon, J.; Brandherm, F.; Egert, R.; Grube, T.; Muhlhauser, M. What the Fog? Edge Computing Revisited: Promises, Applications and Future Challenges. IEEE Access 2019, 7, 152847–152878. [Google Scholar] [CrossRef]
- Yannuzzi, M.; Milito, R.; Serral-Gracia, R.; Montero, D.; Nemirovsky, M. Key Ingredients in an IoT Recipe: Fog Computing, Cloud Computing, and More Fog Computing. In Proceedings of the 2014 IEEE 19th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Athens, Greece, 1–3 December 2014; IEEE: Athens, Greece, 2014; pp. 325–329. [Google Scholar] [CrossRef]
- Caiza, G.; Saeteros, M.; Oñate, W.; Garcia, M.V. Fog Computing at Industrial Level, Architecture, Latency, Energy, and Security: A Review. Heliyon 2020, 6, e03706. [Google Scholar] [CrossRef]
- Seitz, A.; Buchinger, D.; Bruegge, B. The Conjunction of Fog Computing and the Industrial Internet of Things—An Applied Approach. In Proceedings of the 2018 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Athens, Greece, 19–23 March 2018; IEEE: Athens, Greece, 2018; pp. 812–817. [Google Scholar] [CrossRef]
- Mahmoudi, C.; Mourlin, F.; Battou, A. Formal Definition of Edge Computing: An Emphasis on Mobile Cloud and IoT Composition. In Proceedings of the IEEE 2018 Third International Conference on Fog and Mobile Edge Computing (FMEC), Barcelona, Spain, 23–26 April 2018; IEEE: Barcelona, Spain, 2018; pp. 34–42. [Google Scholar] [CrossRef]
- Bashar, A. Secure and cost efficient implementation of the mobile computing using offloading technique. JITDW 2019, 1, 48–57. [Google Scholar] [CrossRef]
- Al-Janabi, S.; Al-Shourbaji, I.; Shojafar, M.; Abdelhag, M. Mobile Cloud Computing: Challenges and Future Research Directions. In Proceedings of the 2017 10th International Conference on Developments in eSystems Engineering (DeSE), Paris, France, 14–16 June 2017; IEEE: Paris, France, 2017; pp. 62–67. [Google Scholar] [CrossRef]
- Dinh, H.T.; Lee, C.; Niyato, D.; Wang, P. A Survey of Mobile Cloud Computing: Architecture, Applications, and Approaches: A Survey of Mobile Cloud Computing. Wirel. Commun. Mob. Comput. 2013, 13, 1587–1611. [Google Scholar] [CrossRef]
- Fernando, N.; Loke, S.W.; Rahayu, W. Mobile Cloud Computing: A Survey. Future Gener. Comput. Syst. 2013, 29, 84–106. [Google Scholar] [CrossRef]
- Mansouri, Y.; Babar, M.A. A Review of Edge Computing: Features and Resource Virtualization. J. Parallel Distrib. Comput. 2021, 150, 155–183. [Google Scholar] [CrossRef]
- Shiraz, M.; Gani, A.; Khokhar, R.H.; Buyya, R. A Review on Distributed Application Processing Frameworks in Smart Mobile Devices for Mobile Cloud Computing. IEEE Commun. Surv. Tutor. 2013, 15, 1294–1313. [Google Scholar] [CrossRef]
- Yaqoob, I.; Ahmed, E.; Gani, A.; Mokhtar, S.; Imran, M.; Guizani, S. Mobile Ad Hoc Cloud: A Survey: Mobile Ad Hoc Cloud. Wirel. Commun. Mob. Comput. 2016, 16, 2572–2589. [Google Scholar] [CrossRef]
- Hubaux, J.-P.; Gross, T.; Le Boudec, J.-Y.; Vetterli, M. Toward Self-Organized Mobile Ad Hoc Networks: The Terminodes Project. IEEE Commun. Mag. 2001, 39, 118–124. [Google Scholar] [CrossRef]
- Ari, A.A.A.; Ngangmo, O.K.; Titouna, C.; Thiare, O.; Kolyang; Mohamadou, A.; Gueroui, A.M. Enabling privacy and security in Cloud of Things: Architecture, applications, security & privacy challenges. Appl. Comput. Inform. 2019. ahead-of-print. [Google Scholar] [CrossRef]
- Aazam, M.; Khan, I.; Alsaffar, A.A.; Huh, E.-N. Cloud of Things: Integrating Internet of Things and Cloud Computing and the Issues Involved. In Proceedings of 2014 11th International Bhurban Conference on Applied Sciences & Technology (IBCAST), Islamabad, Pakistan, 14–18 January, 2014; IEEE: Islamabad, Pakistan, 2014; pp. 414–419. [Google Scholar] [CrossRef]
- Mahmoud, M.M.E.; Rodrigues, J.J.P.C.; Ahmed, S.H.; Shah, S.C.; Al-Muhtadi, J.F.; Korotaev, V.V.; De Albuquerque, V.H.C. Enabling Technologies on Cloud of Things for Smart Healthcare. IEEE Access 2018, 6, 31950–31967. [Google Scholar] [CrossRef]
- Abdelwahab, S.; Hamdaoui, B.; Guizani, M.; Znati, T. Cloud of Things for Sensing-as-a-Service: Architecture, Algorithms, and Use Case. IEEE Internet Things J. 2016, 3, 1099–1112. [Google Scholar] [CrossRef]
- Preden, J.S.; Tammemae, K.; Jantsch, A.; Leier, M.; Riid, A.; Calis, E. The Benefits of Self-Awareness and Attention in Fog and Mist Computing. Computer 2015, 48, 37–45. [Google Scholar] [CrossRef]
- Galambos, P. Cloud, Fog, and Mist Computing: Advanced Robot Applications. IEEE Syst. Man Cybern. Mag. 2020, 6, 41–45. [Google Scholar] [CrossRef]
- Yogi, M.K.; Chandrasekhar, K.C.; Kumar, G.V. Mist Computing: Principles, Trends and Future Direction. IJCSE 2017, 4, 19–21. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Ren, J.; Guo, H.; Xu, C.; Zhang, Y. Serving at the Edge: A Scalable IoT Architecture Based on Transparent Computing. IEEE Netw. 2017, 31, 96–105. [Google Scholar] [CrossRef]
- Chen, G.; Kang, B.-T.; Kandemir, M.; Vijaykrishnan, N.; Irwin, M.J.; Chandramouli, R. Studying Energy Trade Offs in Offloading Computation/Compilation in Java-Enabled Mobile Devices. IEEE Trans. Parallel Distrib. Syst. 2004, 15, 795–809. [Google Scholar] [CrossRef]
- Patel, M.; Hu, Y.; Hédé, P.; Joubert, J.; Ramos, J.R.; Sprecher, N.; Abeta, S.; Neal, A.; Cosimini, P.; Pollard, A.; et al. Contributing Organizations and Authors. Mobile-Edge Computing Introductory Technical White Paper. White Paper, Mobile-Edge Computing (MEC) Industry Initiative. 2014. Available online: https://portal.etsi.org/portals/0/tbpages/mec/docs/mobile-edge_computing_-_introductory_technical_white_paper_v1%2018-09-14.pdf (accessed on 1 September 2014).
- Shahzadi, S.; Iqbal, M.; Dagiuklas, T.; Qayyum, Z.U. Multi-Access Edge Computing: Open Issues, Challenges and Future Perspectives. J. Cloud Comp. 2017, 6, 30. [Google Scholar] [CrossRef]
- Giust, F.; Verin, G.; Antevski, K.; Chou, J.; Fang, Y. MEC Deployments in 4G and Evolution towards 5G. ETSI White Paper No. 24. First Edition. February 2018. Available online: https://www.etsi.org/images/files/ETSIWhitePapers/etsi_wp24_MEC_deployment_in_4G_5G_FINAL.pdf (accessed on 20 February 2018).
- Pan, J.; McElhannon, J. Future Edge Cloud and Edge Computing for Internet of Things Applications. IEEE Internet Things J. 2018, 5, 439–449. [Google Scholar] [CrossRef]
- Hu, Y.; Patel, M.; Sabella, D.; Sprecher, N.; Young, V. Mobile Edge Computing A Key Technology towards 5G. ETSI White Paper No. 11. First Edition. Available online: https://www.etsi.org/images/files/etsiwhitepapers/etsi_wp11_mec_a_key_technology_towards_5g.pdf (accessed on 5 September 2015).
- Sabella, D.; Vaillant, A.; Kuure, P.; Rauschenbach, U.; Giust, F. Mobile-Edge Computing Architecture: The Role of MEC in the Internet of Things. IEEE Consumer Electron. Mag. 2016, 5, 84–91. [Google Scholar] [CrossRef]
- Abedin, S.F.; Bairagi, A.K.; Munir, M.S.; Tran, N.H.; Hong, C.S. Fog Load Balancing for Massive Machine Type Communications: A Game and Transport Theoretic Approach. IEEE Access 2019, 7, 4204–4218. [Google Scholar] [CrossRef]
- Zbakh, M.; Essaaidi, M.; Manneback, P.; Rong, C. (Eds.) Cloud Computing and Big Data: Technologies, Applications and Security. In Lecture Notes in Networks and Systems; Springer International Publishing: Cham, Switzerland, 2019. [Google Scholar] [CrossRef]
- Yu, Y. Mobile edge computing towards 5G: Vision, recent progress, and open challenges. China Commun. 2016, 13, 89–99. [Google Scholar] [CrossRef]
- Klas, G.I. Fog Computing and Mobile Edge Cloud Gain Momentum Open Fog Consortium, ETSI MEC and Cloudlets. 2015. Available online: https://yucianga.info/wp-content/uploads/2015/11/15_11_22-_Fog_computing_and_mobile_edge_cloud_gain_momentum_Open_Fog_Consortium-ETSI_MEC-Cloudlets_v1_1.pdf (accessed on 22 December 2021).
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog Computing: A Platform for Internet of Things and Analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Bessis, N., Dobre, C., Eds.; Studies in Computational Intelligence; Springer International Publishing: Cham, Switzerland, 2014; Volume 546, pp. 169–186. [Google Scholar] [CrossRef]
- Talebkhah, M.; Sali, A.; Marjani, M.; Gordan, M.; Hashim, S.J.; Rokhani, F.Z. Edge Computing: Architecture, Applications and Future Perspectives. In Proceedings of the 2020 IEEE 2nd International Conference on Artificial Intelligence in Engineering and Technology (IICAIET), Kota Kinabalu, Malaysia, 26–27 September 2020; IEEE: Kota Kinabalu, Malaysia, 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, F.; Zhang, M.; Wang, X.; Ma, X.; Liu, J. Deep Learning for Edge Computing Applications: A State-of-the-Art Survey. IEEE Access 2020, 8, 58322–58336. [Google Scholar] [CrossRef]
- Chang, Z.; Liu, S.; Xiong, X.; Cai, Z.; Tu, G. A Survey of Recent Advances in Edge-Computing-Powered Artificial Intelligence of Things. IEEE Internet Things J. 2021, 8, 13849–13875. [Google Scholar] [CrossRef]
- Nayyer, M.Z.; Raza, I.; Hussain, S.A. A Survey of Cloudlet-Based Mobile Augmentation Approaches for Resource Optimization. ACM Comput. Surv. 2019, 51, 1–28. [Google Scholar] [CrossRef]
- Satyanarayanan, M.; Bahl, V.; Caceres, R.; Davies, N. The Case for VM-Based Cloudlets in Mobile Computing. IEEE Pervasive Comput. 2009, 8, 14–23. [Google Scholar] [CrossRef]
- Gusev, M.; Dustdar, S. Going Back to the Roots—The Evolution of Edge Computing, An IoT Perspective. IEEE Internet Comput. 2018, 22, 5–15. [Google Scholar] [CrossRef]
- Hao, P.; Bai, Y.; Zhang, X.; Zhang, Y. Edgecourier: An Edge-Hosted Personal Service for Low-Bandwidth Document Synchronization in Mobile Cloud Storage Services. In Proceedings of the Second ACM/IEEE Symposium on Edge Computing, San Jose, CA, USA, 12–14 October 2017; ACM: San Jose, CA, USA, 2017; pp. 1–14. [Google Scholar] [CrossRef]
- Jararweh, Y.; Tawalbeh, L.; Ababneh, F.; Dosari, F. Resource Efficient Mobile Computing Using Cloudlet Infrastructure. In Proceedings of the 2013 IEEE 9th International Conference on Mobile Ad-hoc and Sensor Networks, Dalian, China, 11–13 December 2013; IEEE: Dalian, China, 2013; pp. 373–377. [Google Scholar] [CrossRef]
- Bahl, V. Emergence of Micro Datacenter (Cloudlets/Edges) for Mobile Computing; Microsoft Devices & Networking Summit: Paris, France, 2015. [Google Scholar]
- Siriweera, A.; Naruse, K. Survey on Cloud Robotics Architecture and Model-Driven Reference Architecture for Decentralized Multicloud Heterogeneous-Robotics Platform. IEEE Access 2021, 9, 40521–40539. [Google Scholar] [CrossRef]
- Pignaton de Freitas, E.; Olszewska, J.I.; Carbonera, J.L.; Fiorini, S.R.; Khamis, A.; Ragavan, S.V.; Barreto, M.E.; Prestes, E.; Habib, M.K.; Redfield, S.; et al. Ontological Concepts for Information Sharing in Cloud Robotics. J. Ambient Intell. Human Comput. 2020, 1–12. [Google Scholar] [CrossRef]
- Kehoe, B.; Patil, S.; Abbeel, P.; Goldberg, K. A Survey of Research on Cloud Robotics and Automation. IEEE Trans. Automat. Sci. Eng. 2015, 12, 398–409. [Google Scholar] [CrossRef]
- Quintas, J.; Menezes, P.; Dias, J. Interoperability in Cloud Robotics—Developing and Matching Knowledge Information Models for Heterogenous Multi-Robot Systems. In Proceedings of the 2017 26th IEEE International Symposium on Robot and Human Interactive Communication (RO-MAN), Lisbon, Portugal, 28 August–1 September 2017; IEEE: Lisbon, Portugal, 2017; pp. 1291–1296. [Google Scholar] [CrossRef]
- Bozcuoglu, A.K.; Kazhoyan, G.; Furuta, Y.; Stelter, S.; Beetz, M.; Okada, K.; Inaba, M. The Exchange of Knowledge Using Cloud Robotics. IEEE Robot. Autom. Lett. 2018, 3, 1072–1079. [Google Scholar] [CrossRef]
- Yazdani, F.; Kazhoyan, G.; Bozcuoglu, A.K.; Haidu, A.; Balint-Benczedi, F.; Bebler, D.; Pomarlan, M.; Beetz, M. Cognition-Enabled Framework for Mixed Human-Robot Rescue Teams. In Proceedings of the 2018 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Madrid, Spain, 1–5 October 2018; IEEE: Madrid, Spain, 2018; pp. 1421–1428. [Google Scholar] [CrossRef]
- Saha, O.; Dasgupta, P. A Comprehensive Survey of Recent Trends in Cloud Robotics Architectures and Applications. Robotics 2018, 7, 47. [Google Scholar] [CrossRef]
- Xie, X.; Zeng, H.-J.; Ma, W.-Y. Enabling Personalization Services on the Edge. In Proceedings of the 10th ACM International Conference on Multimedia (MULTIMEDIA ’02), New York, NY, USA, 1–6 December 2002; Association for Computing Machinery: New York, NY, USA, 2002; pp. 263–266. [Google Scholar] [CrossRef]
- Gelsinger, P.P. Microprocessors for the New Millennium: Challenges, Opportunities, and New Frontiers. In Proceedings of the 2001 IEEE International Solid-State Circuits Conference, San Francisco, CA, USA, 7 February 2001; Digest of Technical Papers. ISSCC (Cat. No.01CH37177); IEEE: San Francisco, CA, USA, 2001; pp. 22–25. [Google Scholar] [CrossRef]
- Ibrahim, S.; Jin, H.; Cheng, B.; Cao, H.; Wu, S.; Qi, L. CLOUDLET: Towards Mapreduce Implementation on Virtual Machines. In Proceedings of the 18th ACM International Symposium on High Performance Distributed Computing—HPDC ’09, Garching, Germany, 11–13 June 2009; ACM Press: Garching, Germany, 2009; p. 65. [Google Scholar] [CrossRef]
- Minh, Q.T.; Nguyen, D.T.; Van Le, A.; Nguyen, H.D.; Truong, A. Toward Service Placement on Fog Computing Landscape. In Proceedings of the 2017 4th NAFOSTED Conference on Information and Computer Science, Hanoi, Vietnam, 24–25 November 2017; IEEE: Hanoi, Vietnam, 2017; pp. 291–296. [Google Scholar] [CrossRef]
- Gonzalez, N.M.; Goya, W.A.; de Fatima Pereira, R.; Langona, K.; Silva, E.A.; Melo de Brito Carvalho, T.C.; Miers, C.C.; Mangs, J.-E.; Sefidcon, A. Fog Computing: Data Analytics and Cloud Distributed Processing on the Network Edges. In Proceedings of the 2016 35th International Conference of the Chilean Computer Science Society (SCCC), Valparaíso, Chile, 10 October 2016–10 February 2017; IEEE: Valparaiso, Chile, 2016; pp. 1–9. [Google Scholar] [CrossRef]
- Li, C.; Xue, Y.; Wang, J.; Zhang, W.; Li, T. Edge-Oriented Computing Paradigms: A Survey on Architecture Design and System Management. ACM Comput. Surv. 2018, 51, 1–34. [Google Scholar] [CrossRef]
- Chiang, M.; Ha, S.; Risso, F.; Zhang, T.; Chih-Lin, I. Clarifying Fog Computing and Networking: 10 Questions and Answers. IEEE Commun. Mag. 2017, 55, 18–20. [Google Scholar] [CrossRef]
- Iorga, M.; Feldman, L.; Barton, R.; Martin, M.J.; Goren, N.; Mahmoudi, C. Fog Computing Conceptual Model; Special Publication (NIST SP) 500-325; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S. The Fog Computing Paradigm: Scenarios and Security Issues. In Proceedings of the Federated Conference on Computer Science and Information Systems, Warsaw, Poland, 7–10 September 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Yi, S.; Hao, Z.; Qin, Z.; Li, Q. Fog Computing: Platform and Applications. In Proceedings of the 2015 Third IEEE Workshop on Hot Topics in Web Systems and Technologies (HotWeb), Washington, DC, USA, 12–13 November 2015; IEEE: Washington DC, DC, USA, 2015; pp. 73–78. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2018, 20, 601–628. [Google Scholar] [CrossRef]
- Aazam, M.; Huh, E.-N. Fog Computing Micro Datacenter Based Dynamic Resource Estimation and Pricing Model for IoT. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications, Gwangju, Korea, 25–27 March 2015; IEEE: Gwangiu, Korea, 2015; pp. 687–694. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Gupta, H.; Calheiros, R.N.; Ghosh, S.K.; Buyya, R. Fog Computing: Principles, Architectures, and Applications. In Internet of Things: Principles and Paradigms; Morgan Kaufmann: San Francisco, CA, USA, 2016; pp. 61–75. [Google Scholar]
- Abujubbeh, M.; Al-Turjman, F.; Fahrioglu, M. Software-Defined Wireless Sensor Networks in Smart Grids: An Overview. Sustain. Cities Soc. 2019, 51, 101754. [Google Scholar] [CrossRef]
- Barik, R.K.; Gudey, S.K.; Reddy, G.G.; Pant, M.; Dubey, H.; Mankodiya, K.; Kumar, V. FogGrid: Leveraging Fog Computing for Enhanced Smart Grid Network. In Proceedings of the 2017 14th IEEE India Council International Conference (INDICON), Roorkee, India, 5–17 December 2017; IEEE: Roorkee, India, 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Brzoza-Woch, R.; Konieczny, M.; Kwolek, B.; Nawrocki, P.; Szydło, T.; Zieliński, K. Holistic Approach to Urgent Computing for Flood Decision Support. Procedia Comput. Sci. 2015, 51, 2387–2396. [Google Scholar] [CrossRef][Green Version]
- Fog Computing: Concepts, Frameworks and Technologies; Mahmood, Z., Ed.; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Malekloo, A. Smart Parking in IoT-Enabled Cities: A Survey. Sustain. Cities Soc. 2019, 49, 101608. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Buyya, R. Fog Computing: Helping the Internet of Things Realize Its Potential. Computer 2016, 49, 112–116. [Google Scholar] [CrossRef]
- Gia, T.N.; Jiang, M.; Rahmani, A.-M.; Westerlund, T.; Liljeberg, P.; Tenhunen, H. Fog Computing in Healthcare Internet of Things: A Case Study on ECG Feature Extraction. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; IEEE: Liverpool, UK, 2015; pp. 356–363. [Google Scholar] [CrossRef]
- Stantchev, V.; Barnawi, A.; Ghulam, S.; Schubert, J.; Tamm, G. Smart Items, Fog and Cloud Computing as Enablers of Servitization in Healthcare. Sens. Transducers. 2015, 185, 121–128. [Google Scholar]
- Zahmatkesh, H.; Al-Turjman, F. Fog Computing for Sustainable Smart Cities in the IoT Era: Caching Techniques and Enabling Technologie—An Overview. Sustain. Cities Soc. 2020, 59, 102139. [Google Scholar] [CrossRef]
- Perera, C.; Qin, Y.; Estrella, J.C.; Reiff-Marganiec, S.; Vasilakos, A.V. Fog Computing for Sustainable Smart Cities: A Survey. ACM Comput. Surv. 2017, 50, 1–43. [Google Scholar] [CrossRef]
- Hajibaba, M.; Gorgin, S. A Review on Modern Distributed Computing Paradigms: Cloud Computing, Jungle Computing and Fog Computing. CIT 2014, 22, 69. [Google Scholar] [CrossRef]
- Puthal, D.; Sahoo, B.P.S.; Mishra, S.; Swain, S. Cloud Computing Features, Issues, and Challenges: A Big Picture. In Proceedings of the 2015 International Conference on Computational Intelligence and Networks, Jabalpur, India, 12–14 December 2015; IEEE: Odisha, India, 2015; pp. 116–123. [Google Scholar] [CrossRef]
- Varghese, B.; Buyya, R. Next Generation Cloud Computing: New Trends and Research Directions. Future Gener. Comput. Syst. 2018, 79, 849–861. [Google Scholar] [CrossRef]
- Moura, J.; Hutchison, D. Review and Analysis of Networking Challenges in Cloud Computing. J. Netw. Comput. Appl. 2016, 60, 113–129. [Google Scholar] [CrossRef]
- Abbas, Z.; Yoon, W. A Survey on Energy Conserving Mechanisms for the Internet of Things: Wireless Networking Aspects. Sensors 2015, 15, 24818–24847. [Google Scholar] [CrossRef]
- Silva, B.N.; Khan, M.; Han, K. Internet of Things: A Comprehensive Review of Enabling Technologies, Architecture, and Challenges. IETE Tech. Rev. 2018, 35, 205–220. [Google Scholar] [CrossRef]
- Bouzarkouna, I.; Sahnoun, M.; Sghaier, N.; Baudry, D.; Gout, C. Challenges Facing the Industrial Implementation of Fog Computing. In Proceedings of the 2018 IEEE 6th International Conference on Future Internet of Things and Cloud (FiCloud), Barcelona, Spain, 6–8 August 2018; IEEE: Barcelona, Spain, 2018; pp. 341–348. [Google Scholar] [CrossRef]
- Olaniyan, R.; Fadahunsi, O.; Maheswaran, M.; Zhani, M.F. Opportunistic Edge Computing: Concepts, Opportunities and Research Challenges. Future Gener. Comput. Syst. 2018, 89, 633–645. [Google Scholar] [CrossRef]
- Ullah, R.; Ahmed, S.H.; Kim, B.-S. Information-Centric Networking with Edge Computing for IoT: Research Challenges and Future Directions. IEEE Access 2018, 6, 73465–73488. [Google Scholar] [CrossRef]
- Nguyen, B.M.; Thi Thanh Binh, H.; The Anh, T.; Bao Son, D. Evolutionary Algorithms to Optimize Task Scheduling Problem for the IoT Based Bag-of-Tasks Application in Cloud–Fog Computing Environment. Appl. Sci. 2019, 9, 1730. [Google Scholar] [CrossRef]
- Singh, S.P.; Nayyar, A.; Kumar, R.; Sharma, A. Fog Computing: From Architecture to Edge Computing and Big Data Processing. J. Supercomput. 2019, 75, 2070–2105. [Google Scholar] [CrossRef]
- Singh, J.; Singh, P.; Gill, S.S. Fog Computing: A Taxonomy, Systematic Review, Current Trends and Research Challenges. J. Parallel Distrib. Comput. 2021, 157, 56–85. [Google Scholar] [CrossRef]
- Gill, S.S.; Buyya, R. Bio-Inspired Algorithms for Big Data Analytics: A Survey, Taxonomy, and Open Challenges. In Advances in Ubiquitous Sensing Applications for Healthcare, Big Data Analytics for Intelligent Healthcare Management; Academic Press: Cambridge, MA, USA, 2019; pp. 1–17. [Google Scholar] [CrossRef]
- Oussous, A.; Benjelloun, F.-Z.; Ait Lahcen, A.; Belfkih, S. Big Data Technologies: A Survey. J. King Saud Univ.—Comput. Inf. Sci. 2018, 30, 431–448. [Google Scholar] [CrossRef]
- Gandomi, A.; Haider, M. Beyond the Hype: Big Data Concepts, Methods, and Analytics. Int. J. Inf. Manag. 2015, 35, 137–144. [Google Scholar] [CrossRef]
- Hariri, R.H.; Fredericks, E.M.; Bowers, K.M. Uncertainty in Big Data Analytics: Survey, Opportunities, and Challenges. J. Big Data 2019, 6, 44. [Google Scholar] [CrossRef]
- Badidi, E.; Mahrez, Z.; Sabir, E. Fog Computing for Smart Cities’ Big Data Management and Analytics: A Review. Future Internet 2020, 12, 190. [Google Scholar] [CrossRef]
- Hussain, M.M.; Beg, M.M.S.; Alam, M.S. Fog Computing for Big Data Analytics in IoT Aided Smart Grid Networks. Wireless Pers. Commun. 2020, 114, 3395–3418. [Google Scholar] [CrossRef]
- Baldini, I.; Castro, P.; Chang, K.; Cheng, P.; Fink, S.; Ishakian, V.; Mitchell, N.; Muthusamy, V.; Rabbah, R.; Slominski, A.; et al. Serverless Computing: Current Trends and Open Problems. In Research Advances in Cloud Computing; Chaudhary, S., Somani, G., Buyya, R., Eds.; Springer: Singapore, 2017; pp. 1–20. [Google Scholar] [CrossRef]
- McGrath, G.; Brenner, P.R. Serverless Computing: Design, Implementation, and Performance. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems Workshops (ICDCSW), Atlanta, GA, USA, 5–8 June 2017; IEEE: Atlanta, GA, USA, 2017; pp. 405–410. [Google Scholar] [CrossRef]
- Fox, G.C.; Ishakian, V.; Muthusamy, V.; Slominski, A. Status of Serverless Computing and Function-as-a-Service (FaaS) in Industry and Research. arXiv Preprint 2017, arXiv:1708.08028. [Google Scholar]
- Aslanpour, M.S.; Toosi, A.N.; Cicconetti, C.; Javadi, B.; Sbarski, P.; Taibi, D.; Assuncao, M.; Gill, S.S.; Gaire, R.; Dustdar, S. Serverless Edge Computing: Vision and Challenges. In Proceedings of the 2021 Australasian Computer Science Week Multiconference, Dunedin, New Zealand, 1–5 February 2021; ACM: Dunedin, New Zealand, 2021; pp. 1–10. [Google Scholar] [CrossRef]
- Bouraga, S. A Taxonomy of Blockchain Consensus Protocols: A Survey and Classification Framework. Expert Syst. Appl. 2021, 168, 114384. [Google Scholar] [CrossRef]
- Mamdiwar, S.D.; R, A.; Shakruwala, Z.; Chadha, U.; Srinivasan, K.; Chang, C.-Y. Recent Advances on IoT-Assisted Wearable Sensor Systems for Healthcare Monitoring. Biosensors 2021, 11, 372. [Google Scholar] [CrossRef] [PubMed]
- Ankenbrand, T.; Bieri, D.; Cortivo, R.; Hoehener, J.; Hardjono, T. Proposal for a Comprehensive (Crypto) Asset Taxonomy. In Proceedings of the 2020 Crypto Valley Conference on Blockchain Technology (CVCBT), Rotkreuz, Switzerland, 11–12 June 2020; IEEE: Rotkreuz, Switzerland, 2020; pp. 16–26. [Google Scholar] [CrossRef]
- Gill, S.S. Quantum and blockchain based Serverless edge computing: A vision, model, new trends and future directions. Internet Technol. Lett. 2021, e275. [Google Scholar] [CrossRef]
- Gill, S.S.; Kumar, A.; Singh, H.; Singh, M.; Kaur, K.; Usman, M.; Buyya, R. Quantum Computing: A Taxonomy, Systematic Review and Future Directions. Softw: Pract. Exper. 2022, 52, 66–114. [Google Scholar] [CrossRef]
- Gill, S.S. A Manifesto for Modern Fog and Edge Computing: Vision, New Paradigms, Opportunities, and Future Directions. In Operationalizing Multi-Cloud Environments; Nagarajan, R., Raj, P., Thirunavukarasu, R., Eds.; EAI/Springer Innovations in Communication and Computing; Springer International Publishing: Cham, Switzerland, 2022; pp. 237–253. [Google Scholar] [CrossRef]
- Liu, W.; Chen, J.; Wang, Y.; Gao, P.; Lei, Z.; Ma, X. Quantum-Based Feature Selection for Multiclassification Problem in Complex Systems with Edge Computing. Complexity 2020, 2020, 8216874. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.M.V.; Esteves Verissimo, P.; Esteve Rothenberg, C.; Azodolmolky, S.; Uhlig, S. Software-Defined Networking: A Comprehensive Survey. Proc. IEEE 2015, 103, 14–76. [Google Scholar] [CrossRef]
- Duan, Y.; Li, W.; Fu, X.; Luo, Y.; Yang, L. A Methodology for Reliability of WSN Based on Software Defined Network in Adaptive Industrial Environment. IEEE/CAA J. Autom. Sinica 2018, 5, 74–82. [Google Scholar] [CrossRef]
- Rafique, W.; Qi, L.; Yaqoob, I.; Imran, M.; Rasool, R.U.; Dou, W. Complementing IoT Services through Software Defined Networking and Edge Computing: A Comprehensive Survey. IEEE Commun. Surv. Tutorials 2020, 22, 1761–1804. [Google Scholar] [CrossRef]
- Deng, S.; Zhao, H.; Fang, W.; Yin, J.; Dustdar, S.; Zomaya, A.Y. Edge Intelligence: The Confluence of Edge Computing and Artificial Intelligence. IEEE Internet Things J. 2020, 7, 7457–7469. [Google Scholar] [CrossRef]
- Zou, Z.; Nevalainen, P.; Huan, Y.; Heikkonen, J.; Westerlund, T. Edge and Fog Computing Enabled AI for IoT—An Overview. In Proceedings of the 2019 IEEE International Conference on Artificial Intelligence Circuits and Systems (AICAS), Hsinchu, Taiwan, 18–20 March 2019; IEEE: Hsinchu, Taiwan, 2019. [Google Scholar]
- Huh, J.-H.; Seo, Y.-S. Understanding Edge Computing: Engineering Evolution with Artificial Intelligence. IEEE Access 2019, 7, 164229–164245. [Google Scholar] [CrossRef]
- Murugesan, S. Harnessing Green IT: Principles and Practices. Green Comput. 2008, 10, 24–33. [Google Scholar] [CrossRef]
- Anand, P.; Singh, Y.; Selwal, A.; Alazab, M.; Tanwar, S.; Kumar, N. IoT Vulnerability Assessment for Sustainable Computing: Threats, Current Solutions, and Open Challenges. IEEE Access 2020, 8, 168825–168853. [Google Scholar] [CrossRef]
- Lopez, O.L.A.; Alves, H.; Souza, R.D.; Montejo-Sanchez, S.; Fernandez, E.M.G.; Latva-Aho, M. Massive Wireless Energy Transfer: Enabling Sustainable IoT Toward 6G Era. IEEE Internet Things J. 2021, 8, 8816–8835. [Google Scholar] [CrossRef]
- Kumari, A.; Gupta, R.; Tanwar, S.; Kumar, N. Blockchain and AI Amalgamation for Energy Cloud Management: Challenges, Solutions, and Future Directions. J. Parallel Distrib. Comput. 2020, 143, 148–166. [Google Scholar] [CrossRef]
- Khairy, S.; Han, M.; Cai, L.X.; Cheng, Y. Sustainable Wireless IoT Networks with RF Energy Charging over Wi-Fi (CoWiFi). IEEE Internet Things J. 2019, 6, 10205–10218. [Google Scholar] [CrossRef]
- Banerjee, U.; Juvekar, C.; Fuller, S.H.; Chandrakasan, A.P. EeDTLS: Energy-Efficient Datagram Transport Layer Security for the Internet of Things. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; IEEE: Singapore, 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Ram, S.K.; Sahoo, S.R.; Das, B.B.; Mahapatra, K.; Mohanty, S.P. Eternal-Thing: A Secure Aging-Aware Solar-Energy Harvester Thing for Sustainable IoT. IEEE Trans. Sustain. Comput. 2021, 6, 320–333. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of Threats to the Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1636–1675. [Google Scholar] [CrossRef]
- Dhanda, S.S.; Singh, B.; Jindal, P. Lightweight Cryptography: A Solution to Secure IoT. Wireless Pers. Commun. 2020, 112, 1947–1980. [Google Scholar] [CrossRef]
- Samie, F.; Bauer, L.; Henkel, J. From Cloud down to Things: An Overview of Machine Learning in Internet of Things. IEEE Internet Things J. 2019, 6, 4921–4934. [Google Scholar] [CrossRef]
- Samann, F.E.F.; Abdulazeez, A.M.; Askar, S. Fog Computing Based on Machine Learning: A Review. Int. J. Interact. Mob. Technol. 2021, 15, 21. [Google Scholar] [CrossRef]
- Hurbungs, V.; Bassoo, V.; Fowdur, T.P. Fog and Edge Computing: Concepts, Tools and Focus Areas. Int. J. Inf. Tecnol. 2021, 13, 511–522. [Google Scholar] [CrossRef]
- Losavio, M. Fog Computing, Edge Computing and a Return to Privacy and Personal Autonomy. Proc. Comp. Sci. 2020, 171, 1750–1759. [Google Scholar] [CrossRef]
- Wang, M.; Cui, Y.; Wang, X.; Xiao, S.; Jiang, J. Machine Learning for Networking: Workflow, Advances and Opportunities. IEEE Netw. 2018, 32, 92–99. [Google Scholar] [CrossRef]
- Laghari, A.A.; Jumani, A.K.; Laghari, R.A. Review and State of Art of Fog Computing. Arch. Computat. Methods Eng. 2021, 28, 3631–3643. [Google Scholar] [CrossRef]
- Hegarty, R.; Taylor, M. Digital Evidence in Fog Computing Systems. Comp. Law Secur. Rev. 2021, 41, 105576. [Google Scholar] [CrossRef]
- Mehta, S.; Singh, A.; Singh, K.K. Role of Machine Learning in Resource Allocation of Fog Computing. In Proceedings of the 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 28–29 January 2021; IEEE: Noida, India, 2021; pp. 262–266. [Google Scholar] [CrossRef]
- Suryadevara, N.K. Energy and Latency Reductions at the Fog Gateway Using a Machine Learning Classifier. Sustain. Comput. Inform. Syst. 2021, 31, 100582. [Google Scholar] [CrossRef]
- Cui, L.; Yang, S.; Chen, F.; Ming, Z.; Lu, N.; Qin, J. A Survey on Application of Machine Learning for Internet of Things. Int. J. Mach. Learn. Cyber. 2018, 9, 1399–1417. [Google Scholar] [CrossRef]
- Adi, E.; Anwar, A.; Baig, Z.; Zeadally, S. Machine Learning and Data Analytics for the IoT. Neural. Comp. Applic. 2020, 32, 16205–16233. [Google Scholar] [CrossRef]
- Ayoubi, S.; Limam, N.; Salahuddin, M.A.; Shahriar, N.; Boutaba, R.; Estrada-Solano, F.; Caicedo, O.M. Machine Learning for Cognitive Network Management. IEEE Commun. Mag. 2018, 56, 158–165. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Tang, F.; Mao, B.; Kato, N.; Akashi, O.; Inoue, T.; Mizutani, K. State-of-the-Art Deep Learning: Evolving Machine Intelligence toward Tomorrow’s Intelligent Network Traffic Control Systems. IEEE Commun. Surv. Tutor. 2017, 19, 2432–2455. [Google Scholar] [CrossRef]
- Hammerschmidt, C.A.; Garcia, S.; Verwer, S.; State, R. Reliable Machine Learning for Networking: Key Issues and Approaches. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks (LCN), Singapore, 9–12 October 2017; IEEE: Singapore, 2017; pp. 167–170. [Google Scholar] [CrossRef]
- Casas, P.; Vanerio, J.; Fukuda, K. GML Learning, a Generic Machine Learning Model for Network Measurements Analysis. In Proceedings of the 2017 13th International Conference on Network and Service Management (CNSM), Tokyo, Japan, 26–30 November 2017; IEEE: Tokyo, Japan, 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Sobecki, A.; Szymański, J.; Gil, D.; Mora, H. Deep Learning in the Fog. Int. J. Distrib. Sens. Netw. 2019, 15, 155014771986707. [Google Scholar] [CrossRef]








| Acronym | Full Form |
|---|---|
| AI | Artificial Intelligence |
| AR | Augmented Reality |
| CoT | Cloud of Things |
| CC | Cloud Computing |
| CCTV | Closed-Circuit Television |
| CPU | Central Processing Unit |
| CR | Cloud Robotics |
| DDoS | Distributed Denial of Service |
| DL | Deep Learning |
| EC | Edge Computing |
| ETSI | European Telecommunications Standard Institute |
| FaaS | Function-as-a-Service |
| FC | Fog Computing |
| IaaS | Infrastructure-as-a-Service |
| ICT | Information and Communications Technology |
| IDC | International Data Corporation |
| IoT | Internet-of-Things |
| IT | Information Technology |
| ITS | Intelligent Transport System |
| ITU | International Telecommunication Union |
| MACC | Mobile Ad hoc Cloud Computing |
| MEC | Multi-access Edge Computing |
| MC | Mobile Computing |
| MCC | Mobile Cloud Computing |
| MDC | Micro Data Center |
| mist | Mist Computing |
| ML | Machine Learning |
| MMA | Man-in-the-Middle Attack |
| MIT | Massachusetts Institute of Technology |
| NIST | National Institute of Standards and Technology |
| OP | Operational Technology |
| PaaS | Platform-as-a-Service |
| PRISMA | Preferred Reporting Items for Systematic Reviews and Meta-Analyses |
| QoE | Quality of Experience |
| QoS | Quality of Service |
| RAN | Radio Access Network |
| RAS | Reliability Availability Serviceability |
| SaaS | Software-as-a-Service |
| SDN | Software-Defined Networking |
| SLA | Service-Level Agreement |
| VM | Virtual Machine |
| VR | Virtual Reality |
| WSN | Wireless Sensor Network |
| Author and Year | Articles Referenced | Time Span | Systematic Study | Survey/Review Outline | Computing Paradigms | Future Directions | ||
|---|---|---|---|---|---|---|---|---|
| Cloud Computing | Fog Computing | Edge Computing | ||||||
| Atzori et al. [14], 2016 | 119 | 1999 – 2016 | × | The survey examines the prospect of Internet-of-Things from the evolutionary perspective, the role of IoT in modern society and ensuing challenges. | ✓ | × | ✓ | × |
| Hu et al. [15], 2017 | 123 | 2001 – 2017 | × | The review presents fog computing features, architecture, compares with other computing paradigms, and summarizes key technologies that aid in application and deployment. | ✓ | ✓ | ✓ | ✓ |
| Mahmud et al. [16], 2017 | 47 | 2012 – 2016 | × | The work presents a taxonomy from a comprehensive analysis of fog features and challenges pertaining to the structure, service, and security and identifies research gaps. | ✓ | ✓ | ✓ | ✓ |
| Lin et al. [17], 2017 | 167 | 2001 – 2017 | × | The article offers a comprehensive overview of state-of-the-art IoT-enabling technologies, system architecture, privacy, security issues, and concerns of IoT and fog/edge computing integration during real-world deployment. | × | ✓ | ✓ | ✓ |
| Mao et al. [18], 2017 | 242 | 2003 – 2017 | × | An exhaustive outline of state-of-the-art MEC from a communication viewpoint, resource management, comparison with MCC is presented. | ✓ | × | ✓ | ✓ |
| Naha et al. [19], 2018 | 142 | 2001 – 2018 | × | The survey article presents fog computing overview, architecture, related technologies, taxonomy by analyzing fog requirement and reviewing challenges, research issues, and trends. | ✓ | ✓ | ✓ | ✓ |
| Mouradian et al. [20], 2018 | 168 | 2006 – 2017 | ✓ | An exhaustive survey is tendered on fog computing architectures, algorithms, affiliated concepts, and their dissimilarities; additionally, challenges and research directions were discussed. | × | ✓ | × | ✓ |
| Mukherjee et al. [21], 2018 | 225 | 1997 – 2017 | × | The survey extends an overview of fog computing basics, architecture and highlights the approach for service and allocation of resources to overcome latency, bandwidth, and energy consumption. | × | ✓ | × | ✓ |
| Elazhary [22], 2018 | 412 | 1991 – 2018 | × | The exhaustive review researches arenas such as IoT, cloud computing, mobile computing, and related concepts and attempts to disambiguate emerging paradigms as well as technologies. | ✓ | ✓ | ✓ | ✓ |
| Atlam et al. [23], 2018 | 63 | 2012 – 2017 | × | This work reviews fog computing state-of-the-art, including fog features, architecture, and merits, and insists on fog being an IoT enabler. | × | ✓ | × | ✓ |
| Bangui et al. [24], 2018 | 114 | 2012 – 2018 | × | The review outlines edge computing technology and the challenges and concerns that accompany Distributed environments while shifting services from cloud’s centralized to edge’s decentralized platforms. | × | ✓ | ✓ | ✓ |
| Yousefpour et al. [2], 2019 | 450 | 2001 – 2018 | × | A comprehensive survey is furnished that emphasizes fog computing, associated computing paradigms, and presents a taxonomy of research subjects, underlying challenges, and future leanings of fog. | ✓ | ✓ | ✓ | ✓ |
| Abdulkareem et al. [25], 2019 | 95 | 2011 – 2019 | × | This review highlights recent advancements of ML techniques related to the accuracy, resource management and security of fog computing and its role in edge computing. | × | ✓ | ✓ | ✓ |
| Donno et al. [9], 2019 | 71 | 2004 – 2019 | × | The review article offers clarification for beginners into research on cloud computing, edge computing, and fog computing by illustrating features and architecture of each paradigm and concludes by stating fog computing’s relevance as fog binds cloud, edge computing, and IoT together. | ✓ | ✓ | ✓ | ✓ |
| Khan et al. [26], 2019 | 101 | 2009 – 2019 | × | The study focuses on cloud and state-of-the-art edge computing concepts, critical requirements, limitations and identified unaddressed issues. | ✓ | ✓ | ✓ | ✓ |
| Cao et al. [27], 2020 | 62 | 2005 – 2020 | × | The article reviews research related to edge computing, summarizes key concepts, technologies, architecture, privacy, and security. | ✓ | × | ✓ | ✓ |
| Habibi et al. [28], 2020 | 191 | 2002 – 2019 | × | The survey covers existing computing paradigms and emphasizes fog computing research areas by presenting a taxonomy and analyses from fog’s architectural viewpoint. | ✓ | ✓ | ✓ | ✓ |
| Moura et al. [29], 2020 | 194 | 1999 – 2020 | × | This work surveys state-of-the-art fog computing systems, offers insights into designing and managing resilient fog systems and illustrates research issues and upcoming future trends. | × | ✓ | × | ✓ |
| Aslanpour et al. [30], 2020 | 50 | 2010 – 2020 | × | The study offers a taxonomy of real-world performance metrics to assess the computing paradigms of cloud, fog, and edge. | ✓ | ✓ | ✓ | ✓ |
| Alli et al. [31], 2020 | 102 | 2009 – 2020 | × | The article delves into the ecosystems of IoT–fog–cloud, analyzing concepts, architecture, standards, tools of fog Cloud-of-Things, and presents a taxonomy on emerging issues. It concludes that ML and AI in fog ecosystems would be appropriate for latency-sensitive and resource-constrained systems. | ✓ | ✓ | ✓ | ✓ |
| Characteristic | Fog | Edge | Cloud |
|---|---|---|---|
| Operators | Users and cloud provider | Local enterprise or network infrastructure providers | Cloud provider |
| Participating Nodes | Fog devices (switches, routers, access points, etc.) and IoT devices | Edge devices | Fewer nodes spanning cloud to IoT devices |
| Service Type | Less global | Local | Global |
| Management | Distributed/centralized | Local business and service provider | Centralized |
| Hardware | Devices with virtualization facility (access points, routers, switches, servers) | Edge devices with compute capacity | Massive data centers and equipment with virtualization potential |
| Computation Device | Any device capable of computation, networking, and storage | Edge devices | Powerful cloud servers |
| Available Computing Resources | Moderate | Moderate | High |
| Nature of Failure | Highly diverse | Highly diverse | Predictable |
| Main Driver | Academia/ Industry | Academia/industry | Academia/industry |
| User Connectivity | Mostly wireless | Mostly wireless | High speed (Both wired and wireless) |
| Distance from Users | Relatively close | Close | Far |
| Internal Connectivity | Operate autonomously with intermittent or no internet connectivity | Operate autonomously with intermittent or no internet connectivity | Requires internet connectivity throughout service duration |
| Main Standardization Entity | OpenFog Consortium, IEEE | - | National Institute of Standards and Technology (NIST), Cloud Security Alliance (CSA), Distributed Management Task Force (DMFT), Open Commons Consortium (OCC), Global Inter-Cloud Technology Forum (GICTF) |
| Power Source | Battery/green energy/ direct power | Battery/green energy/direct power | Direct power |
| Power Consumption | Low | Low | High |
| Application Type | High computation with lower latency | Low latency computation | Ample computation |
| Architecture | Decentralized/hierarchical | Localized/distributed | Centralized/hierarchical |
| Computation Capacity | Moderate | Moderate | High |
| Storage Capacity | Limited | Limited | Massive storage capacity |
| Availability | High | Average | High |
| Latency | Low | Low | Relatively high |
| Node mobility | High | High | Very low |
| Security/Vulnerability | Must be provided on participant nodes | Must be provided on edge devices | Must be provided along Cloud-to-Things continuum |
| Server Location | Can be deployed at edge or dedicated locations | Near edge devices | Stationed in huge dedicated buildings |
| Number of Intermediate Hops | One/few | One | Multiple |
| Hardware Connectivity | WAN, LAN, WLAN, Wi-Fi, cellular | WAN, LAN, WLAN, Wi-Fi___33, cellular, ZigBee | WAN |
| Application Handling—real-time | Achievable | Achievable | Difficult owing to increased latency |
| Service Access | Through connected devices from the edge to the core | At the edge of the internet | Through core |
| Computation Cost | Low | Low | High |
| Cooling Cost | Very low | Very low | High |
| Deployment Space | Less | Less | Massive |
| Delay Cost | Less | Less | More |
| Feature | Fog | Edge | Cloud |
|---|---|---|---|
| Heterogeneity support | Yes | Yes | Yes |
| Connection to cloud | Yes | Yes or No | Yes |
| Infrastructure need | Yes | Yes | Yes |
| Geographically distributed | Yes | Yes | No |
| Virtualization technology | Yes | No | Yes |
| Location awareness | Yes | Yes | No |
| Ultra-low latency | Yes | Yes | No |
| Scalability | Yes | Yes | Yes |
| Mobility support | Yes | Yes | No |
| Application support—real-time | Yes | Yes | No |
| Application support—large-scale | Yes | Yes | Yes |
| Standardized | Yes | Yes | Yes |
| Multiple IoT applications | Yes | No | Yes |
| Data persistence | Yes | No | Yes |
| Computation migration | Yes | No | No |
| Conserving energy | Yes | Yes | No |
| Open Issue | Limitations Prevalent | Potential Solutions or Research Prospect | Related Specifics | Impact |
|---|---|---|---|---|
| Standardization of fog computing | Several fog definitions and related concepts are being proposed. | Formulate fog definition that can be universally accepted. | Foundation | Standards and Definition |
| Scalability | Major fog system schemes in practice fail to scale IoT vastitude. | Design algorithms and procedures that ensure scalability. | Scalability | Placement; Service Provisioning; Scheduling; Load Balancing; Offloading |
| Bandwidth-aware system | Although reducing bandwidth usage is key, fewer fog computing regard conserving bandwidth through fog systems. | Deliberate on saving bandwidth through fog systems and measure bandwidth usage under fog systems. | Bandwidth | Testbeds and Experiments; Control and Monitoring; Infrastructure Design |
| SLA for fog system | SLAs for cloud system are defined, but SLAs for fog systems are not defined. | Devise new SLA compatible for fog computing systems that supports multi-vendors. | Cost, QoS | Fog Infrastructure; Control and Monitoring |
| Mobility | Major existing work considers fixed fog nodes and mobile IoT devices. | Propose fog systems with mobile fog nodes and design suitable task offloading and scheduling plans ensuring availability to IoT nodes. | Mobility, Management | Concepts and Framework; Security and Privacy; Scheduling, Load Balancing and Offloading |
| Fog node site selection | The issue of site selection for fog node is highlighted by limited studies. The placing of fog servers at appropriate positions is crucial to offer maximum service. Analysis of demand and workload of a specific node prior to placement minimizes maintenance cost. | Devise site selection policies for fog nodes, addressing computation, communication, storage, and cost. | QoS, Cost, RAS | Resource Analysis and Estimation; Infrastructure Design |
| SDN support | Fog computing does not provide native support to SDN. | Improving and standardizing SDN for fog systems. | Programmability | Software and Tools; Definition and Standards |
| Resource Monitoring | Fog resource monitoring is addressed by very few studies. | Formulate procedures that monitor resources of fog systems involving multi-operators. | Management, Programmability | Software and Tools; Control and Monitoring |
| High-speed user support | Existing communication protocols do not assist high-speed users. | Develop protocols supporting high-speed users and mobility-predicting algorithms based on machine learning. | Mobility | Architecture and Framework |
| Federation | Federation schemes or application for fog is unavailable. | Formulate new fog node federation strategy operating across diverse domains. | Programmability, Management | Software and Tools |
| Fog node security | The fog nodes positioned at proximity of end user incites security challenge. | Configure secure fog nodes with robust access control policies that handle site attacks and secure hardware design to withstand physical damage. | Security, Device Heterogeneity | Security and Privacy; Hardware Design |
| Trust and authentication | Heterogeneous IoT nodes and fog nodes make the traditional authentication and trust strategies inept. The providers of fog service may be internet service provider, cloud vendor, or end-users, which jeopardizes the trust in fog. | Design of novel trust and authentication structure for user, service, and nodes is needful. | Heterogeneity, Security | Security and Privacy; Definition and Standards |
| Security for fog offloading | Fog node task offloading may lead to security and privacy concern. | Devise secure offloading technique and integrity, correctness checking scheme for task offloaded. | Security, QoS | Offloading, Security, and Privacy |
| Privacy | With various networks involved and fog operating predominantly on wireless technology, privacy issues arise. The end user can access numerous fog nodes which involves sensitive data. | Maintaining the privacy of sensitive personal data is vital. | Privacy | Privacy and Security |
| Flexibility | Fault or failure at network is not regarded by existing fog networks, with fog nodes being more prone to DoS attacks due to limited resources. | Regard fault prevention, detection, and recovery in fog networks and design DoS-resilient fog system. | Security | Security and Privacy; Infrastructure Design; Control and Monitoring |
| Green fog computing | Enhancing energy efficiency of overall fog system has to be deliberate. | Utilize battery storages and energy harvesting for IoT sensors and devices and place fog nodes near renewable energy sources. | Energy | Resource analysis, Estimation; Infrastructure Design |
| Energy consumption | With huge number of fog nodes, energy consumed is large. The energy demand of fog nodes should be reduced to mitigate cost and energy. | Device resource provisioning strategy that is energy efficient, while being aware of fog node positions. | Energy | Resource Analysis, Estimation; Infrastructure Design |
| Multi-objective design | Many existent schemes reckon certain objectives and overlook other objectives. | Propound schemes that regard multiple objectives concurrently (task offload strategy that deems availability, bandwidth, energy, and security). | QoS | Scheduling, Load Balancing, and Offloading; Resource Analysis and Estimation; Testbeds and Experiments |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Angel, N.A.; Ravindran, D.; Vincent, P.M.D.R.; Srinivasan, K.; Hu, Y.-C. Recent Advances in Evolving Computing Paradigms: Cloud, Edge, and Fog Technologies. Sensors 2022, 22, 196. https://doi.org/10.3390/s22010196
Angel NA, Ravindran D, Vincent PMDR, Srinivasan K, Hu Y-C. Recent Advances in Evolving Computing Paradigms: Cloud, Edge, and Fog Technologies. Sensors. 2022; 22(1):196. https://doi.org/10.3390/s22010196
Chicago/Turabian StyleAngel, Nancy A, Dakshanamoorthy Ravindran, P M Durai Raj Vincent, Kathiravan Srinivasan, and Yuh-Chung Hu. 2022. "Recent Advances in Evolving Computing Paradigms: Cloud, Edge, and Fog Technologies" Sensors 22, no. 1: 196. https://doi.org/10.3390/s22010196
APA StyleAngel, N. A., Ravindran, D., Vincent, P. M. D. R., Srinivasan, K., & Hu, Y.-C. (2022). Recent Advances in Evolving Computing Paradigms: Cloud, Edge, and Fog Technologies. Sensors, 22(1), 196. https://doi.org/10.3390/s22010196








