Enabling Reliable UAV Control by Utilizing Multiple Protocols and Paths for Transmitting Duplicated Control Packets
Abstract
1. Introduction
- We propose MuTran which reduces the control packet transfer delay, so UAVs can be controlled more reliably by using MuTran.
- We come up with a technique that selectively duplicates only control packets, not data packets, and transfers the originals and copies of them through different paths.
- We design MuTran to be able to utilize multiple protocols for transmitting data and control packets separately, so the control packets can be transferred to UAVs with guaranteed low-latency regardless of data traffic.
- We implemented MuTran on real devices and demonstrated its value by conducting many experiments using the devices.
- We demonstrate the validity of MuTran by theoretically analyzing it from various perspectives.
2. Related Work
3. System Design and Implementation
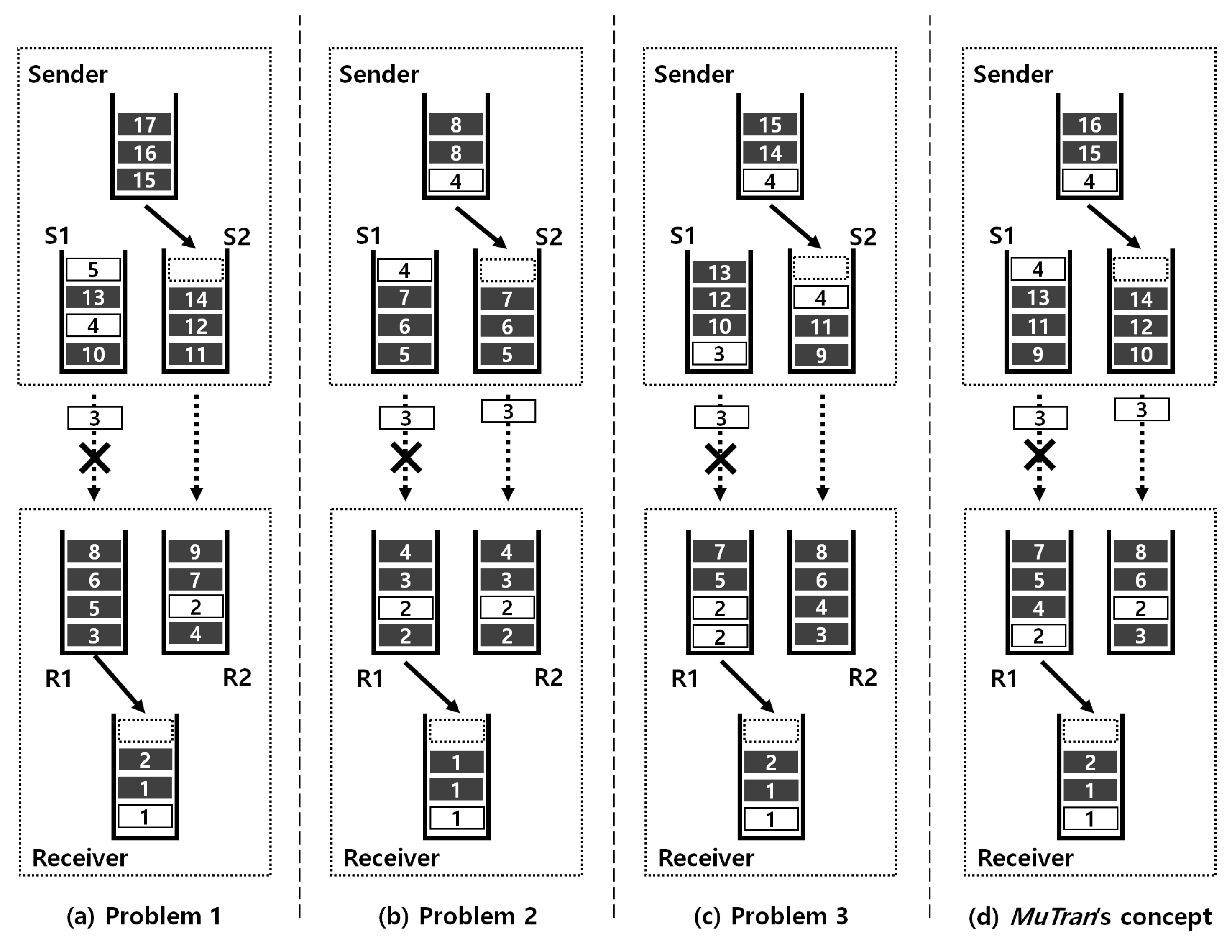
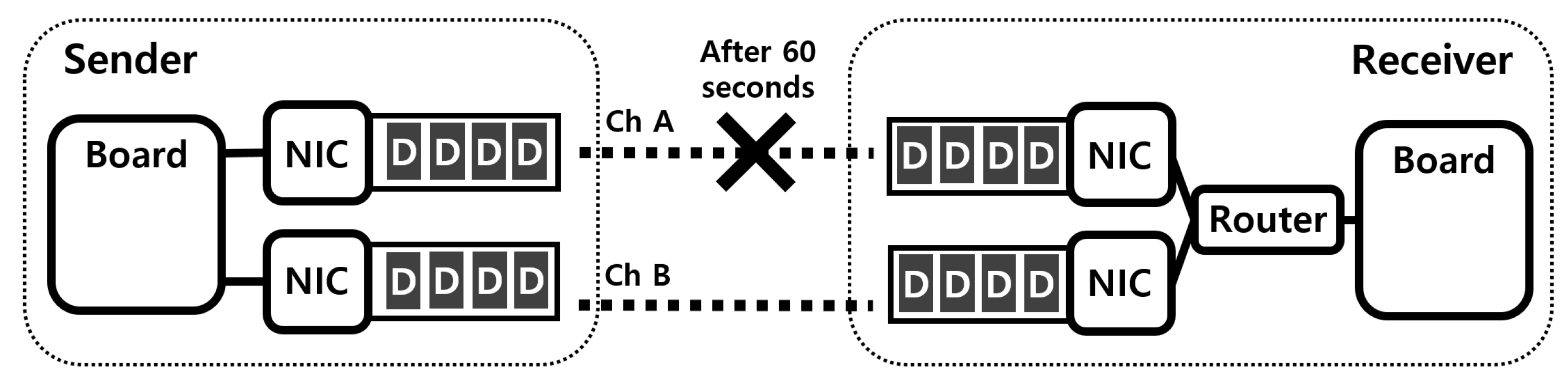
3.1. Problem Statement
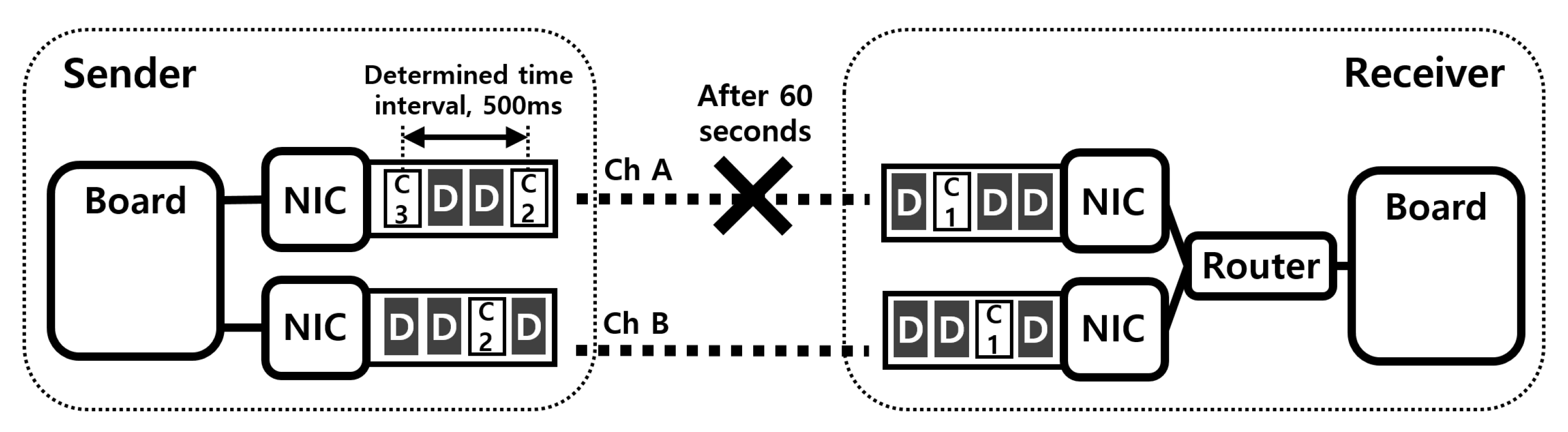
3.2. Duplicated Control Packet Transmission
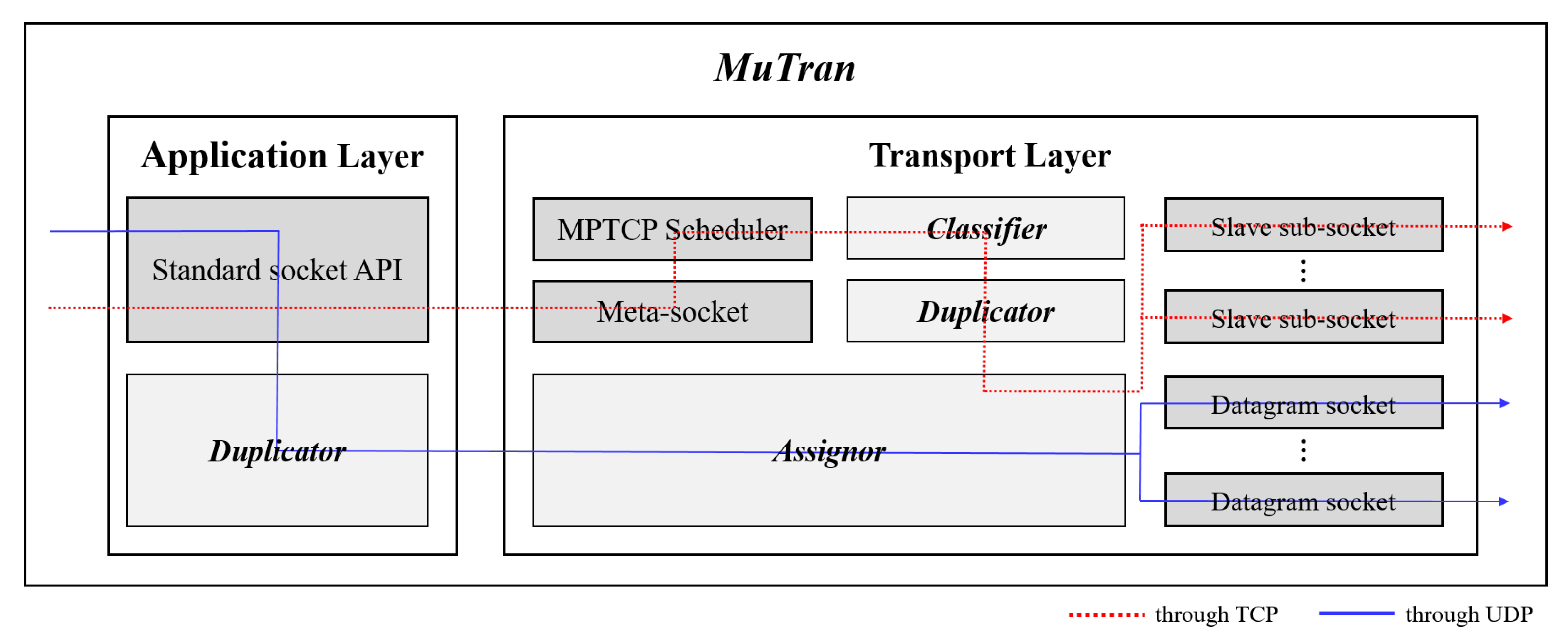
3.3. Design of MuTran
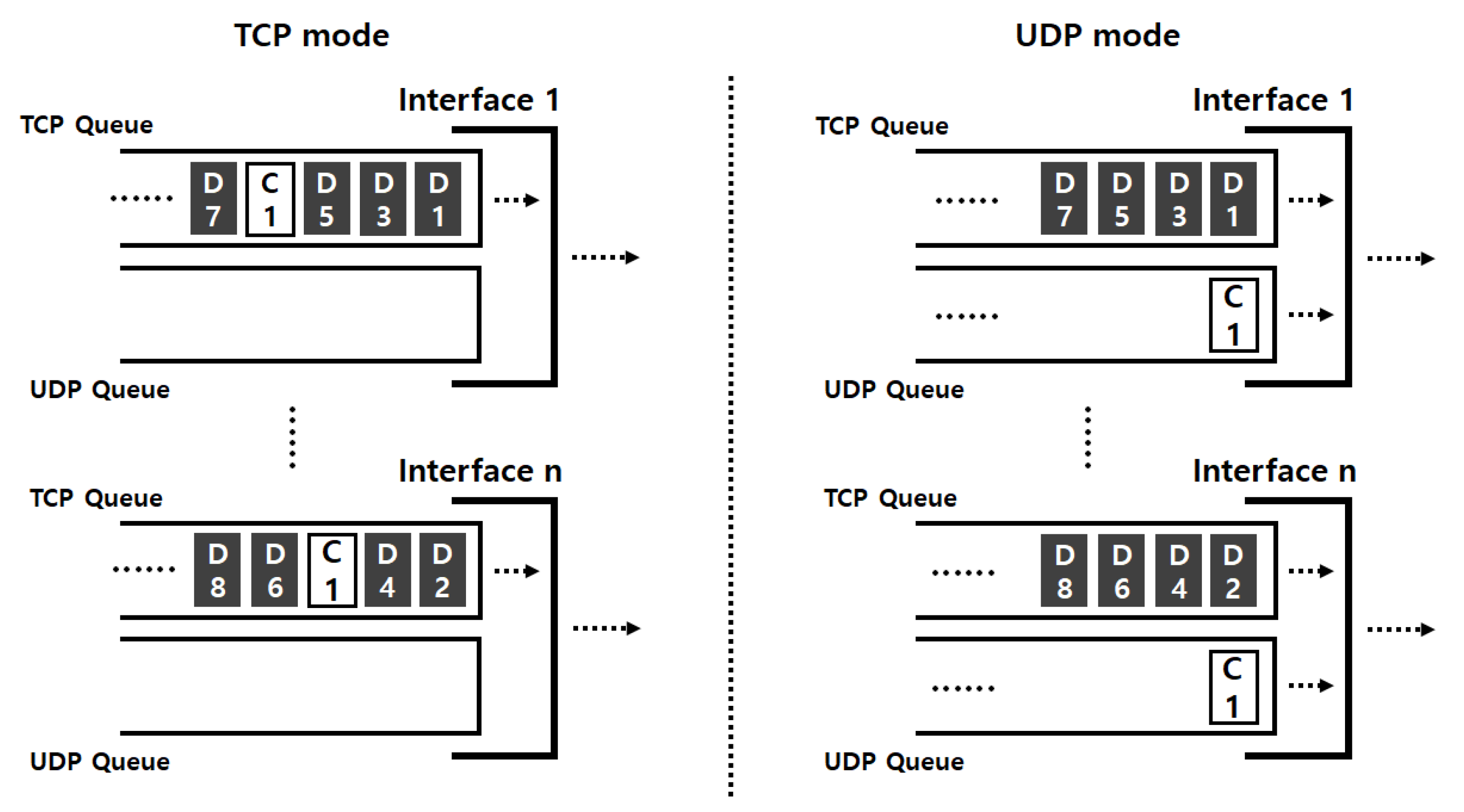
3.3.1. Mutran with MPTCP
3.3.2. Classifier
3.3.3. Duplicator
3.3.4. Assignor
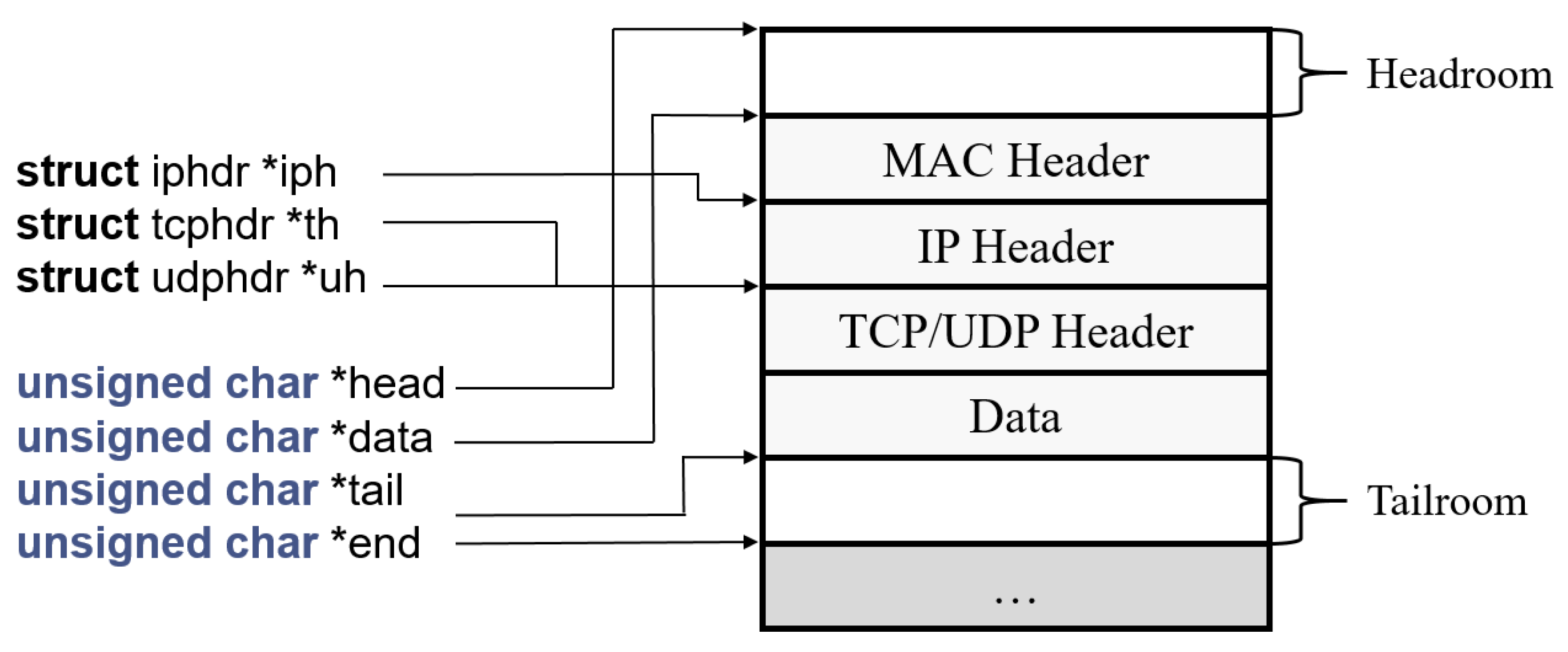
3.4. Implementation
4. Theoretical Analysis
4.1. Element Delays of Control Packet Transmission
4.2. Analysis of the Control Packet Transmission over TCP
4.3. Analysis of the Control Packet Transmission with Considering Retransmission
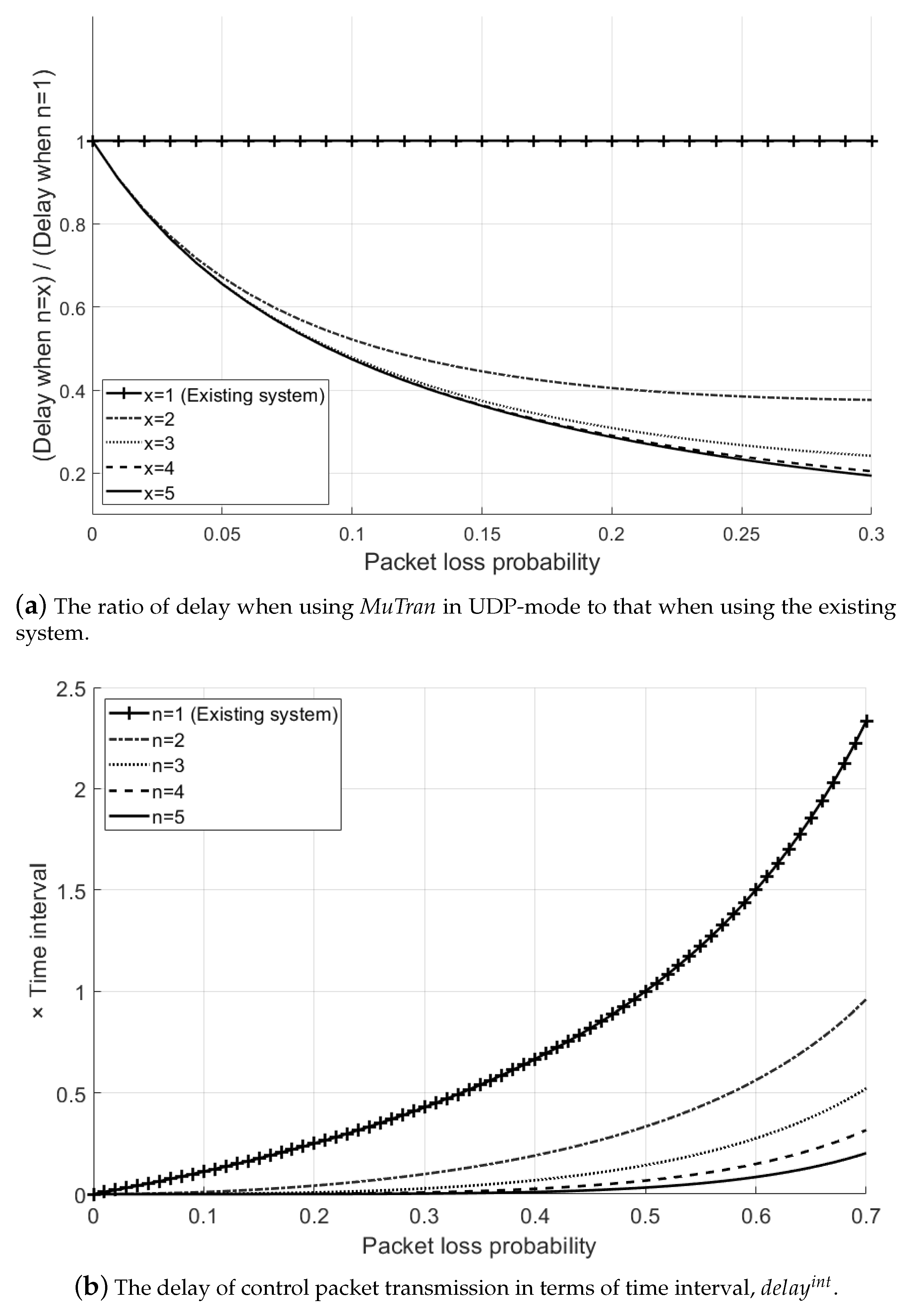
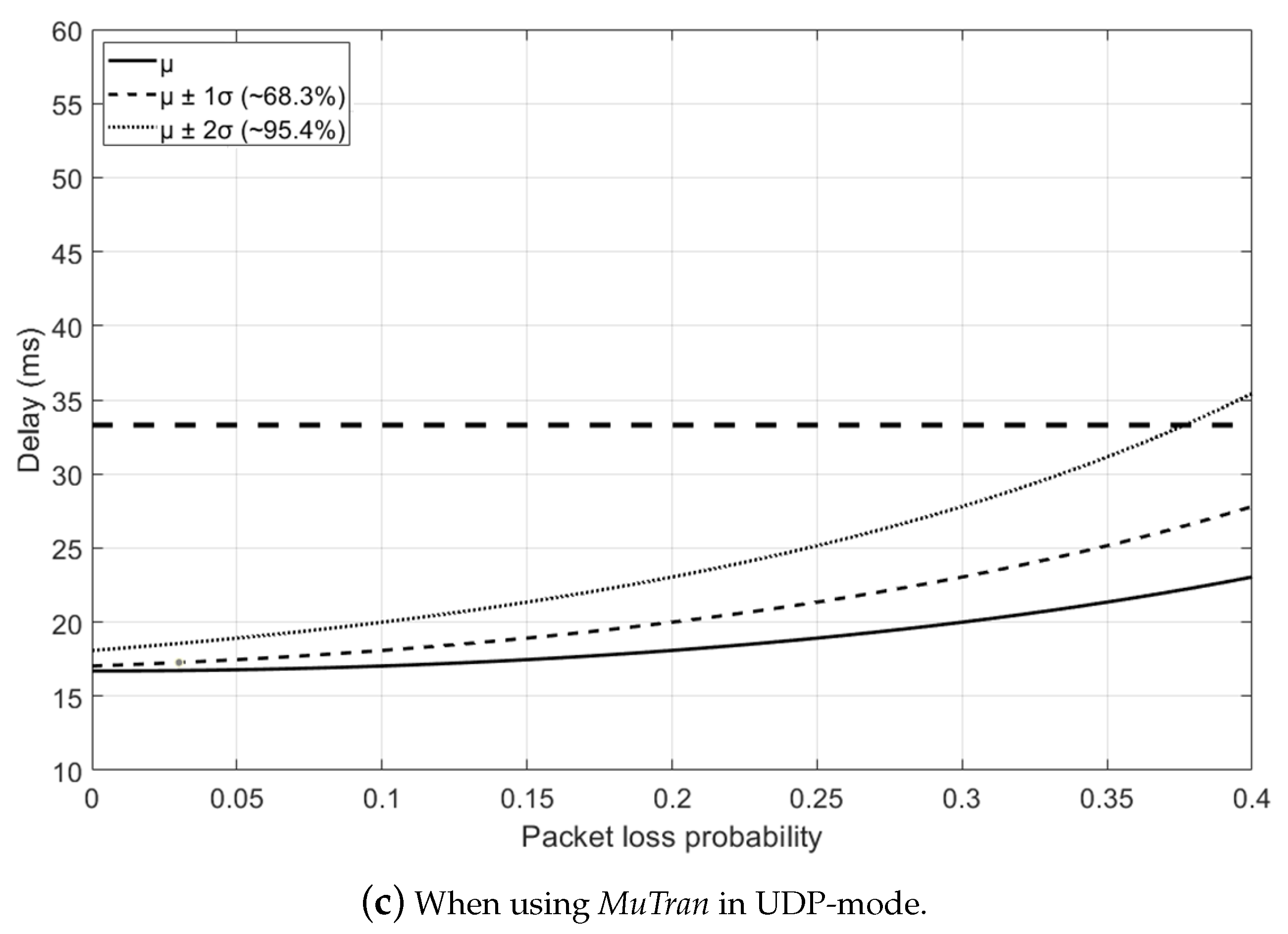
4.4. Analysis of the Control Packet Transmission of MuTran in UDP-Mode
4.5. Analysis of Practical Cases with MuTran
4.6. Analysis of the Number of Subflows Required to Guarantee the Target Delay
4.7. Analysis of Overhead Due to Duplication in MuTran
4.8. Analysis of Control Packet Transmission Rate When Using MuTran
5. Performance Evaluation
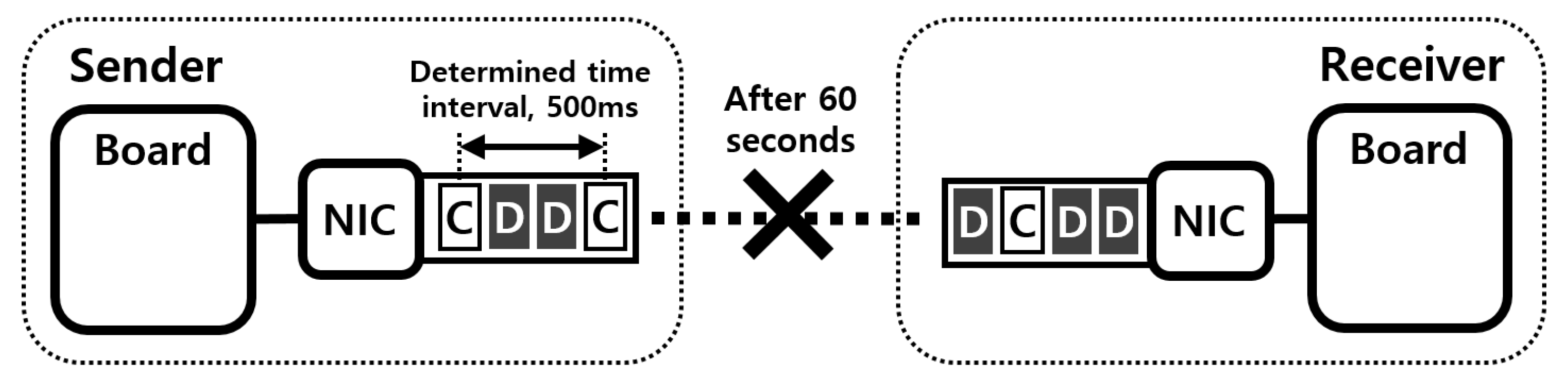
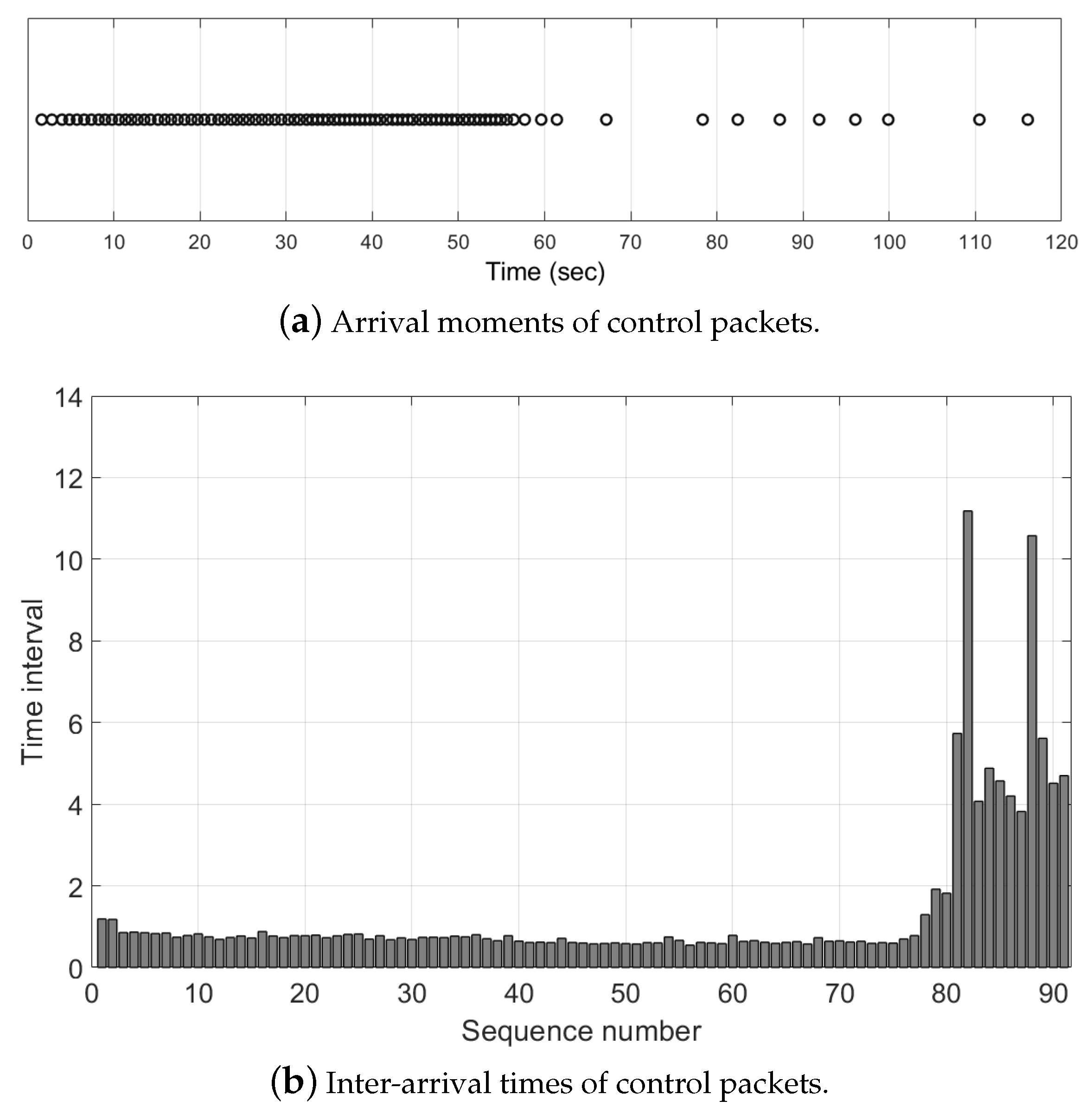
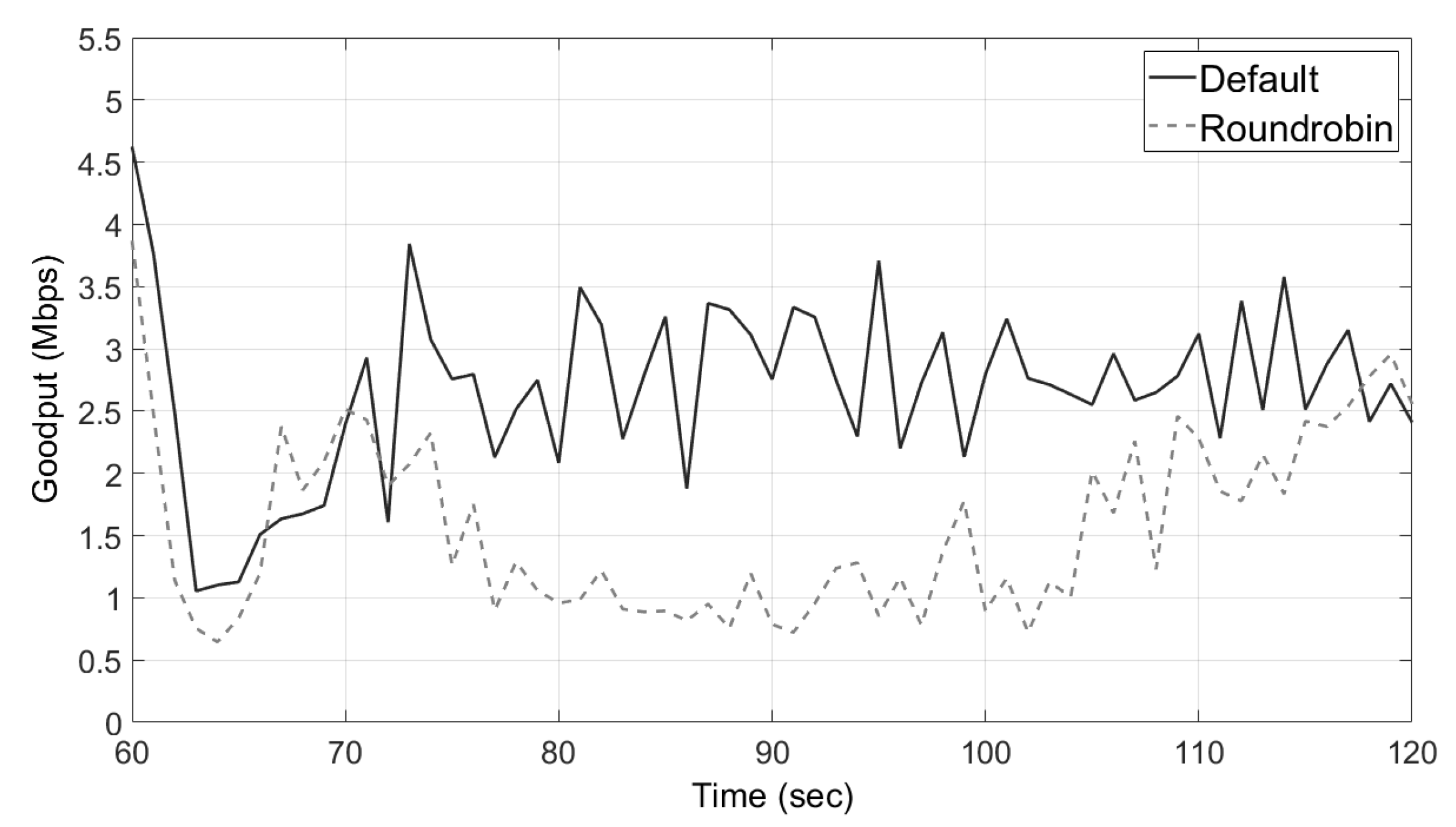
5.1. Performance of Existing System in the Problem Situation
5.2. Evaluation of Transmitting Packets in a Round-Robin Fashion
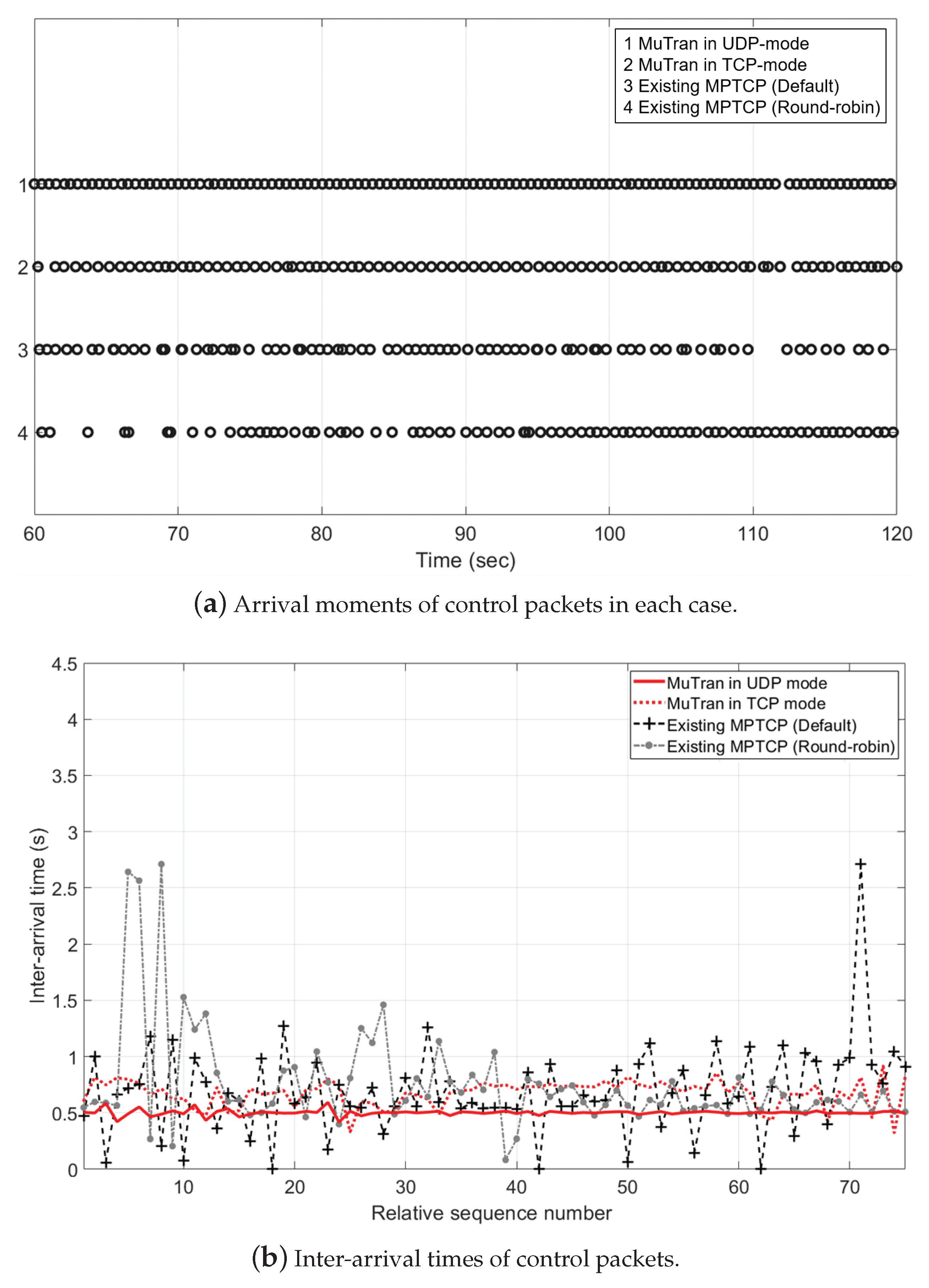
5.3. Evaluation on the Performance of MuTran
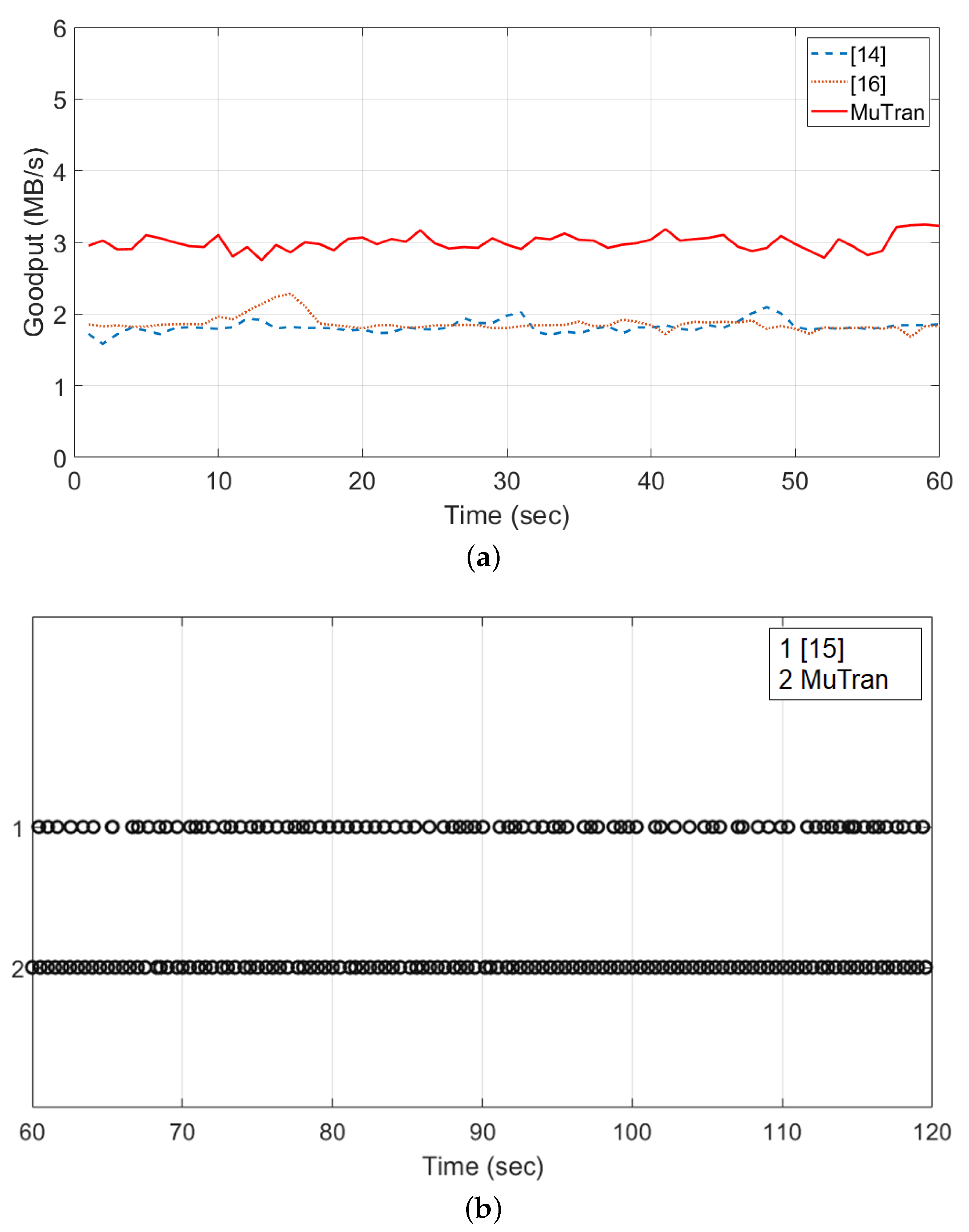
5.4. Performance Comparison with Related Techniques
6. Discussion
6.1. Complexity and Feasibility of MuTran
6.2. Applicability of MuTran in UAV-Based Scenarios
6.2.1. Physical Aspects in Aerial Scenarios
6.2.2. High Mobility and Frequent Topology Change
6.2.3. A Wide Range of Networks and Communications
6.2.4. Diverse Applications and Systems Using UAVs
7. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| UAV | Unmanned Aerial Vehicle |
| TCP | Transmission Control Protocol |
| MPTCP | Multipath Transmission Control Protocol |
| UDP | User Datagram Protocol |
| MAC | Media Access Control |
| SDN | Software Defined Network |
| LTE | Long Term Evolution |
| RC | Radio Controller |
| MIMO | Multiple Input Multiple Output |
| MPR | Multi-Packet Reception |
| HRI | Human-Robot Interaction |
| FEC | Forward Error Correction |
| SRTT | Smoothed Round Trip Time |
| API | Application Programming Interface |
| GCS | Ground Control System |
| U2U | UAV to UAV |
| U2I | UAV to Infrastructure |
| FANET | Flying Ad hoc Network |
| MANET | Mobile Ad hoc Network |
| VANET | Vehicular Ad hoc Network |
Appendix A
References
- Mac, T.T.; Copot, C.; Duc, T.T.; De Keyser, R. AR. Drone UAV control parameters tuning based on particle swarm optimization algorithm. In Proceedings of the Automation, Quality and Testing, Robotics (AQTR), 2016 IEEE International Conference on IEEE, Cluj-Napoca, Romania, 19–21 May 2016; pp. 1–6. [Google Scholar]
- Park, S.; Kim, H.T.; Lee, S.; Joo, H.; Kim, H. Survey on Anti-Drone Systems: Components, Designs, and Challenges. IEEE Access 2021, 9, 42635–42659. [Google Scholar] [CrossRef]
- Lee, J.; Kim, K.; Yoo, S.; Chung, A.Y.; Lee, J.Y.; Park, S.J.; Kim, H. Constructing a reliable and fast recoverable network for drones. In Proceedings of the Communications (ICC), 2016 IEEE International Conference on IEEE, Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Lee, W.; Lee, J.Y.; Lee, J.; Kim, K.; Yoo, S.; Park, S.; Kim, H. Ground control system based routing for reliable and efficient multi-drone control system. Appl. Sci. 2018, 8, 2027. [Google Scholar] [CrossRef]
- Scharf, M.; Ford, A. Multipath TCP (MPTCP) Application Interface Considerations. Available online: https://tools.ietf.org/html/rfc6897 (accessed on 10 May 2021).
- Paasch, C.; Ferlin, S.; Alay, O.; Bonaventure, O. Experimental evaluation of multipath TCP schedulers. In Proceedings of the 2014 ACM SIGCOMM Workshop on Capacity Sharing Workshop, Chicago, IL, USA, 18 August 2014; pp. 27–32. [Google Scholar]
- Chandhar, P.; Danev, D.; Larsson, E.G. Massive MIMO for communications with drone swarms. IEEE Trans. Wirel. Commun. 2018, 17, 1604–1629. [Google Scholar] [CrossRef]
- Ruan, Y.; Zhang, Y.; Li, Y.; Zhang, R.; Hang, R. An Adaptive Channel Division MAC Protocol for High Dynamic UAV Networks. IEEE Sens. J. 2020, 20, 9528–9539. [Google Scholar] [CrossRef]
- Dai, T.; Li, A.; Wang, H. Design and Implementation of a Relay Mechanism in Restricted UAVs Ad-hoc Networks. In Proceedings of the 2019 IEEE 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019; pp. 605–611. [Google Scholar]
- Zhu, X.; Bian, C.; Chen, Y.; Chen, S. A low latency clustering method for large-scale drone swarms. IEEE Access 2019, 7, 186260–186267. [Google Scholar] [CrossRef]
- Bousbaa, F.Z.; Kerrache, C.A.; Mahi, Z.; Tahari, A.E.K.; Lagraa, N.; Yagoubi, M.B. GeoUAVs: A new geocast routing protocol for fleet of UAVs. Comput. Commun. 2020, 149, 259–269. [Google Scholar] [CrossRef]
- Zhang, Q.; Jiang, M.; Feng, Z.; Li, W.; Zhang, W.; Pan, M. IoT enabled UAV: Network architecture and routing algorithm. IEEE Internet Things J. 2019, 6, 3727–3742. [Google Scholar] [CrossRef]
- Hong, L.; Guo, H.; Liu, J.; Zhang, Y. Toward Swarm Coordination: Topology-Aware Inter-UAV Routing Optimization. IEEE Trans. Veh. Technol. 2020, 69, 10177–10187. [Google Scholar] [CrossRef]
- Chiba, N.; Ogura, M.; Nakamura, R.; Hadama, H. Dual transmission protocol for video signal transfer for real-time remote vehicle control. In Proceedings of the Communications (APCC), 2014 Asia-Pacific Conference on IEEE, Pattaya, Thailand, 1–3 October 2014; pp. 315–320. [Google Scholar]
- Lee, W.; Lee, J.Y.; Joo, H.; Kim, H. An MPTCP-Based Transmission Scheme for Improving the Control Stability of Unmanned Aerial Vehicles. Sensors 2021, 21, 2791. [Google Scholar] [CrossRef] [PubMed]
- Shailendra, S.; Aniruddh, K.; Panigrahi, B.; Simha, A. Multipath TCP Path Scheduler for Drones: A Segregation of Control and User Data. In Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Chennai, India, 10–14 July 2017; p. 40. [Google Scholar]
- Erdelj, M.; Saif, O.; Natalizio, E.; Fantoni, I. UAVs that fly forever: Uninterrupted structural inspection through automatic UAV replacement. Ad Hoc Netw. 2019, 94, 101612. [Google Scholar] [CrossRef]
- Team, P.D. Offboard-PX4 User Guide. 2018. Available online: https://docs.px4.io/en/flight_modes/offboard.html (accessed on 10 May 2021).
- Meier, L.; Honegger, D.; Pollefeys, M. PX4: A node-based multithreaded open source robotics framework for deeply embedded platforms. In Proceedings of the Robotics and Automation (ICRA), 2015 IEEE International Conference on IEEE, Seattle, WA, USA, 26–30 May 2015; pp. 6235–6240. [Google Scholar]
- Chandhar, P.; Larsson, E.G. Massive MIMO for Drone Communications: Applications, Case Studies and Future Directions. arXiv 2017, arXiv:1711.07668. [Google Scholar]
- MAVLink. MAVLink Developer Guide. 2021. Available online: https://mavlink.io/en (accessed on 10 May 2021).
- Panda, K.G.; Das, S.; Sen, D.; Arif, W. Design and deployment of UAV-aided post-disaster emergency network. IEEE Access 2019, 7, 102985–102999. [Google Scholar] [CrossRef]
- Jaakkola, A. Implementation of Transmission Control Protocol in Linux. Proc. Semin. Netw. Protoc. Oper. Syst. 2013, 1, 10. [Google Scholar]
- Paasch, C.; Barré, S. Multipath TCP in the Linux Kernel. 2013. Available online: www.multipath-tcp.org (accessed on 10 May 2021).
- Intel. Intel Aero Compute Board Hardware Features and Usage. 2018. Available online: https://www.intel.com/content/dam/support/us/en/documents/drones/development-drones/intel-aero-compute-board-guide.pdf (accessed on 10 May 2021).
- Mathis, M.; Semke, J.; Mahdavi, J.; Ott, T. The macroscopic behavior of the TCP congestion avoidance algorithm. ACM SIGCOMM Comput. Commun. Rev. 1997, 27, 67–82. [Google Scholar] [CrossRef]
- Barrett, D.; Desai, P. Low-Latency Design Considerations for Video-Enabled Drones. 2016. Available online: http://www.ti.com/lit/wp/spry301/spry301.pdf (accessed on 10 May 2021).
- Muzaffar, R. Routing and Video Streaming in Drone Networks. Ph.D. Thesis, Queen Mary University of London, London, UK, 2017. [Google Scholar]
- Asadpour, M.; Giustiniano, D.; Hummel, K.A. From ground to aerial communication: Dissecting WLAN 802.11n for the drones. In Proceedings of the 8th ACM International Workshop on Wireless Network Testbeds, Experimental Evaluation & Characterization, Miami, FL, USA, 30 September 2013; pp. 25–32. [Google Scholar]
- MPTCP. Manual Configuration. 2021. Available online: https://multipath-tcp.org/pmwiki.php/Users/ConfigureRouting (accessed on 10 May 2021).
- Du, J.; Liu, X.; Rao, L. Proactive doppler shift compensation in vehicular cyber-physical systems. IEEE/ACM Trans. Netw. 2018, 26, 807–818. [Google Scholar] [CrossRef]
- Yanmaz, E.; Kuschnig, R.; Bettstetter, C. Achieving air-ground communications in 802.11 networks with three-dimensional aerial mobility. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 120–124. [Google Scholar]
- Tareque, M.H.; Hossain, M.S.; Atiquzzaman, M. On the routing in flying ad hoc networks. In Proceedings of the 2015 Federated Conference on Computer Science and Information Systems (FedCSIS), Lodz, Poland, 13–16 September 2015; pp. 1–9. [Google Scholar]
- Purohit, A.; Mokaya, F.; Zhang, P. Demo abstract: Collaborative indoor sensing with the SensorFly aerial sensor network. In Proceedings of the 2012 ACM/IEEE 11th International Conference on Information Processing in Sensor Networks (IPSN), Beijing, China, 16–20 April 2012; pp. 145–146. [Google Scholar]
- Jawhar, I.; Mohamed, N.; Al-Jaroodi, J.; Agrawal, D.P.; Zhang, S. Communication and networking of UAV-based systems: Classification and associated architectures. J. Netw. Comput. Appl. 2017, 84, 93–108. [Google Scholar] [CrossRef]
- Van der Bergh, B.; Chiumento, A.; Pollin, S. LTE in the sky: Trading off propagation benefits with interference costs for aerial nodes. IEEE Commun. Mag. 2016, 54, 44–50. [Google Scholar] [CrossRef]
- Lin, X.; Yajnanarayana, V.; Muruganathan, S.D.; Gao, S.; Asplund, H.; Maattanen, H.L.; Bergstrom, M.; Euler, S.; Wang, Y.P.E. The sky is not the limit: LTE for unmanned aerial vehicles. IEEE Commun. Mag. 2018, 56, 204–210. [Google Scholar] [CrossRef]
- Lee, W.; Lee, J.Y.; Kim, H. Improving Reliability of Real-Time Remote Vehicle Control through Duplicating Control Packets. In Proceedings of the 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Limassol, Cyprus, 15–17 October 2018; pp. 1–8. [Google Scholar]



| Notation | Definition |
|---|---|
| W | The maximum size of congestion window in the steady-state |
| The round trip time in the steady-state | |
| The maximum segment size | |
| c | The speed of light |
| The distance between the sender and receiver | |
| p | The probability of transmission success |
| q | The probability of transmission failure |
| The total delay of ith subflow | |
| The buffer queuing delay of ith subflow in the sender | |
| The buffer queuing delay of ith subflow in the receiver | |
| The propagation delay of ith subflow | |
| The sum of propagation delay and buffer queuing delay of ith subflow in the sender, ( | |
| The determined time interval for control packet transmission | |
| The target delay to meet the required service quality | |
| The queue size of ith subflow in the sender | |
| The queue size of ith subflow in the receiver | |
| The size of control packet | |
| The total size of control packets without duplication | |
| The total size of control packets with duplication | |
| The processing rate of ith subflow in the receiver | |
| The sending rate of ith subflow in the sender | |
| The control packet transmission rate in TCP-mode | |
| The control packet transmission rate in UDP-mode |
| Normal Situation | Problematic Situation | |||
|---|---|---|---|---|
| Case | Mean | Std | Mean | Std |
| 1 | 0.5002 | 0.0027 | 0.5046 | 0.0511 |
| 2 | 0.5849 | 0.1155 | 0.6591 | 0.1665 |
| 3 | 0.6095 | 0.142 | 0.8929 | 0.6721 |
| 4 | 0.5879 | 0.1638 | 0.6993 | 0.4067 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, W. Enabling Reliable UAV Control by Utilizing Multiple Protocols and Paths for Transmitting Duplicated Control Packets. Sensors 2021, 21, 3295. https://doi.org/10.3390/s21093295
Lee W. Enabling Reliable UAV Control by Utilizing Multiple Protocols and Paths for Transmitting Duplicated Control Packets. Sensors. 2021; 21(9):3295. https://doi.org/10.3390/s21093295
Chicago/Turabian StyleLee, Woonghee. 2021. "Enabling Reliable UAV Control by Utilizing Multiple Protocols and Paths for Transmitting Duplicated Control Packets" Sensors 21, no. 9: 3295. https://doi.org/10.3390/s21093295
APA StyleLee, W. (2021). Enabling Reliable UAV Control by Utilizing Multiple Protocols and Paths for Transmitting Duplicated Control Packets. Sensors, 21(9), 3295. https://doi.org/10.3390/s21093295






