Cellular and Virtualization Technologies for UAVs: An Experimental Perspective
Abstract
1. Introduction
2. Related Work and Background
2.1. Communications
2.2. Virtualization and UAVs
3. Testbed Components Description
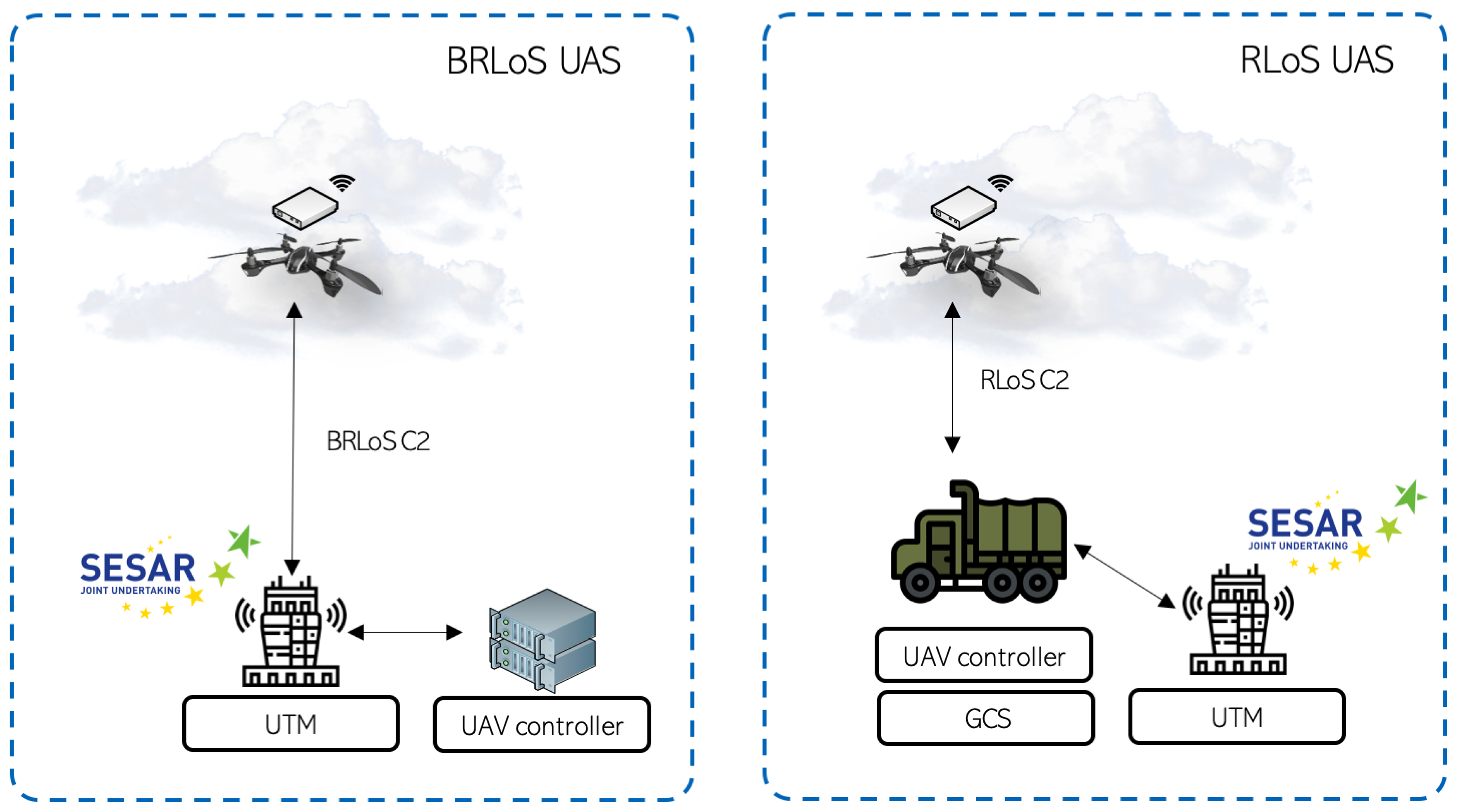
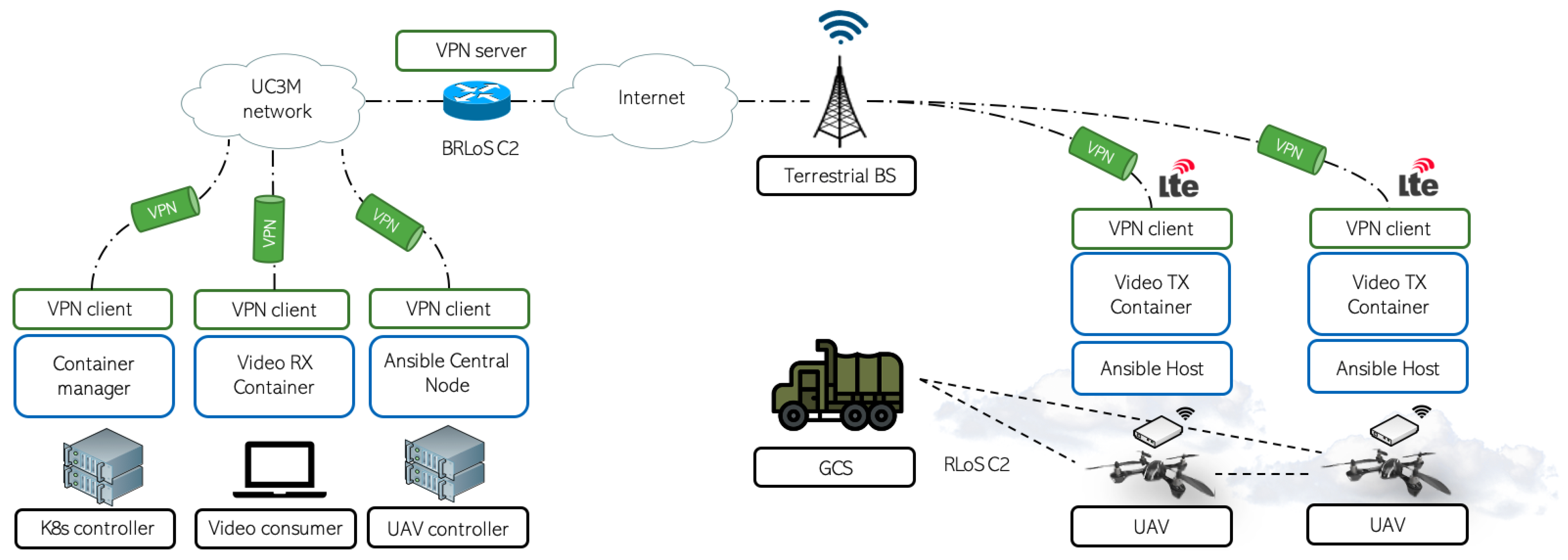
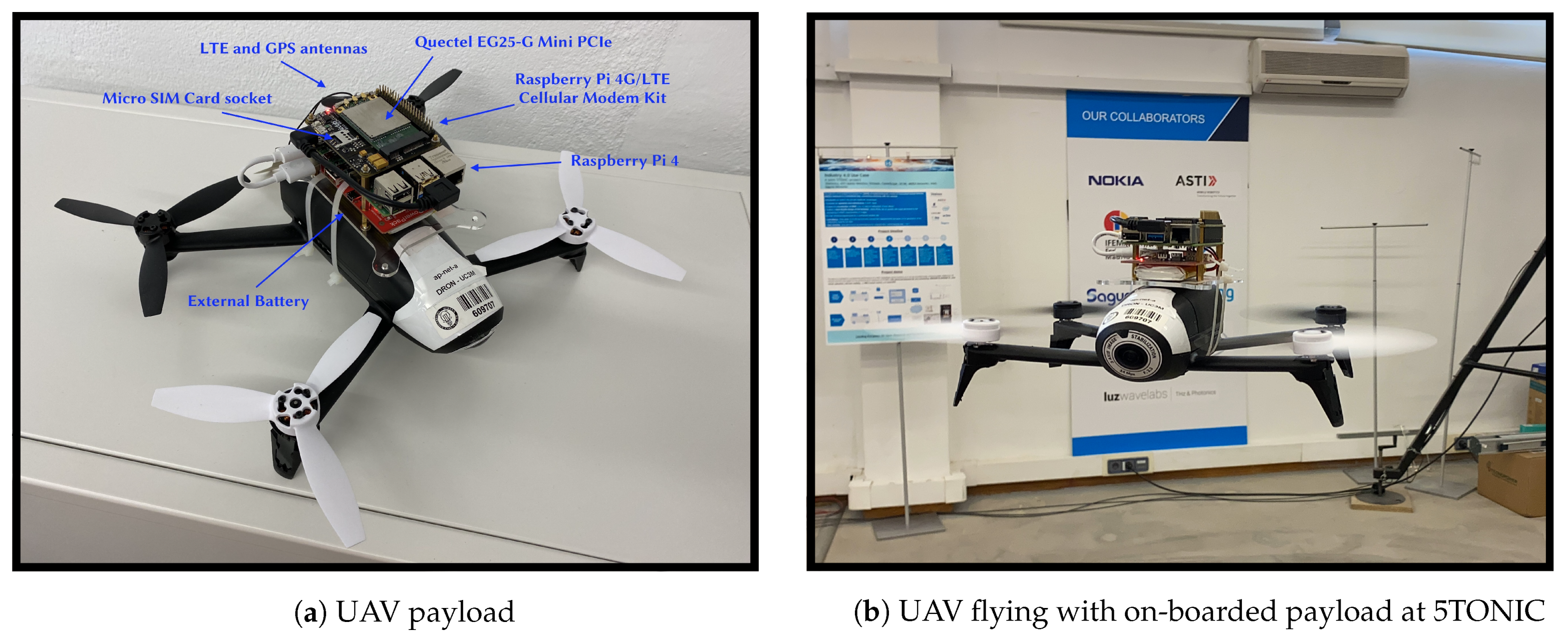
3.1. Cellular-Assisted UAV Communications
3.2. Automated UAV Control System
3.3. Virtualization in UAVs: The Power of Containers in Aerial Networks
- Controller-plane: this component is in charge of the management and orchestration of the K8s cluster and the applications running inside. Its main tasks include the instantiation of pods (minimal unit where containers have to be deployed) & services, and react to cluster events such as scaling up/down a deployment, managing cluster errors, pod re-deployments, etc. This control-plane unit, commonly referred to as the “master” node, is usually deployed in one single host, although it can be deployed across multiple machines if necessary.
- Worker node: these nodes are in charge of providing the resources to the cluster. Inside these nodes, pods will be deployed to run the applications in the Kubernetes cluster, maintaining their functionality and reporting their status to the master node. In every cluster, there must be at least a single worker node, and they are not limited to a single host, i.e., inside a host there could be multiple workers (for example, multiple VMs).
4. Testbed Experimentation
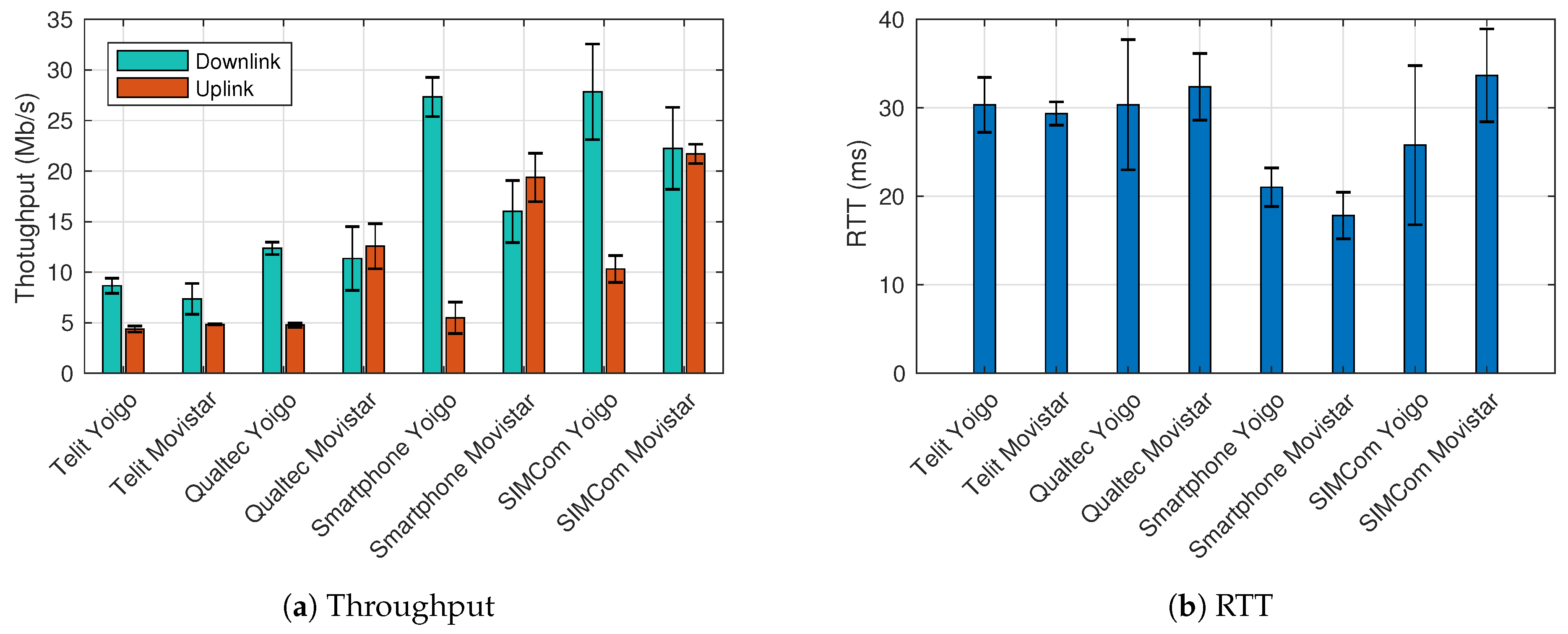
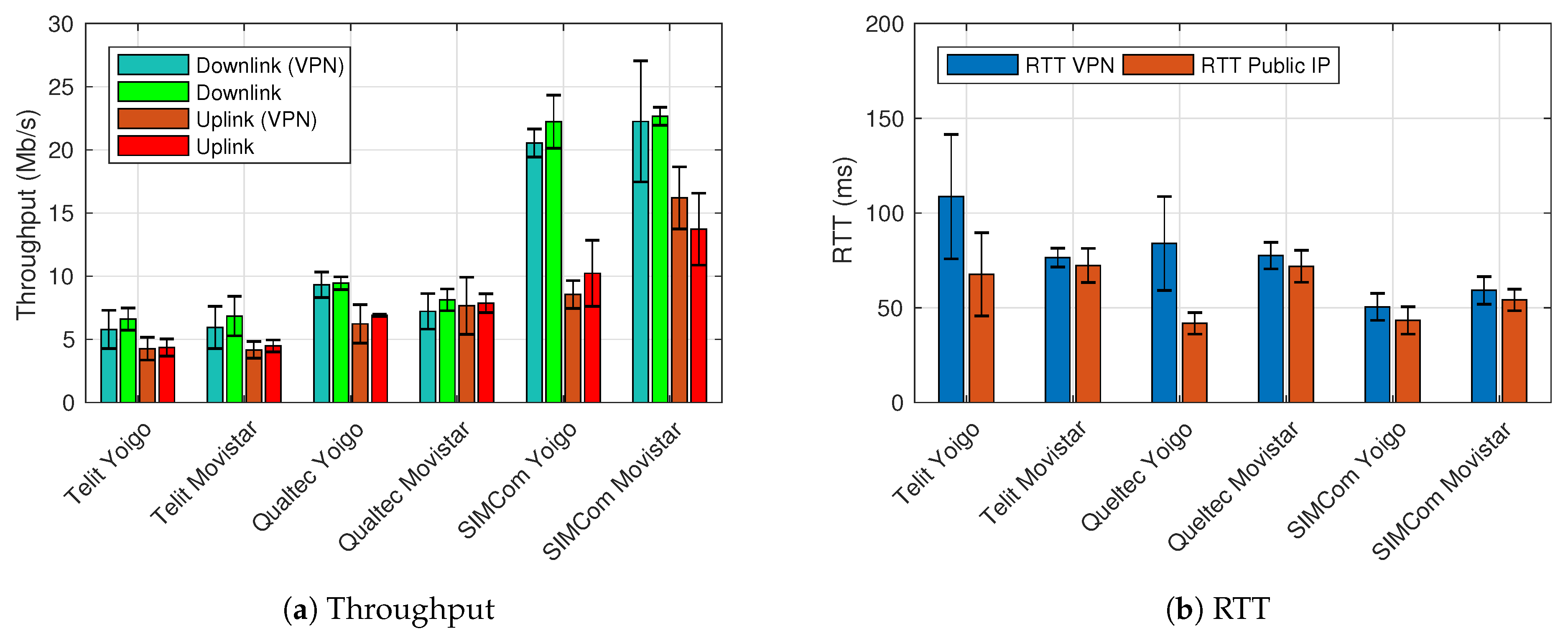
4.1. Communication Performance Evaluation
4.2. 5G Standalone Benchmark
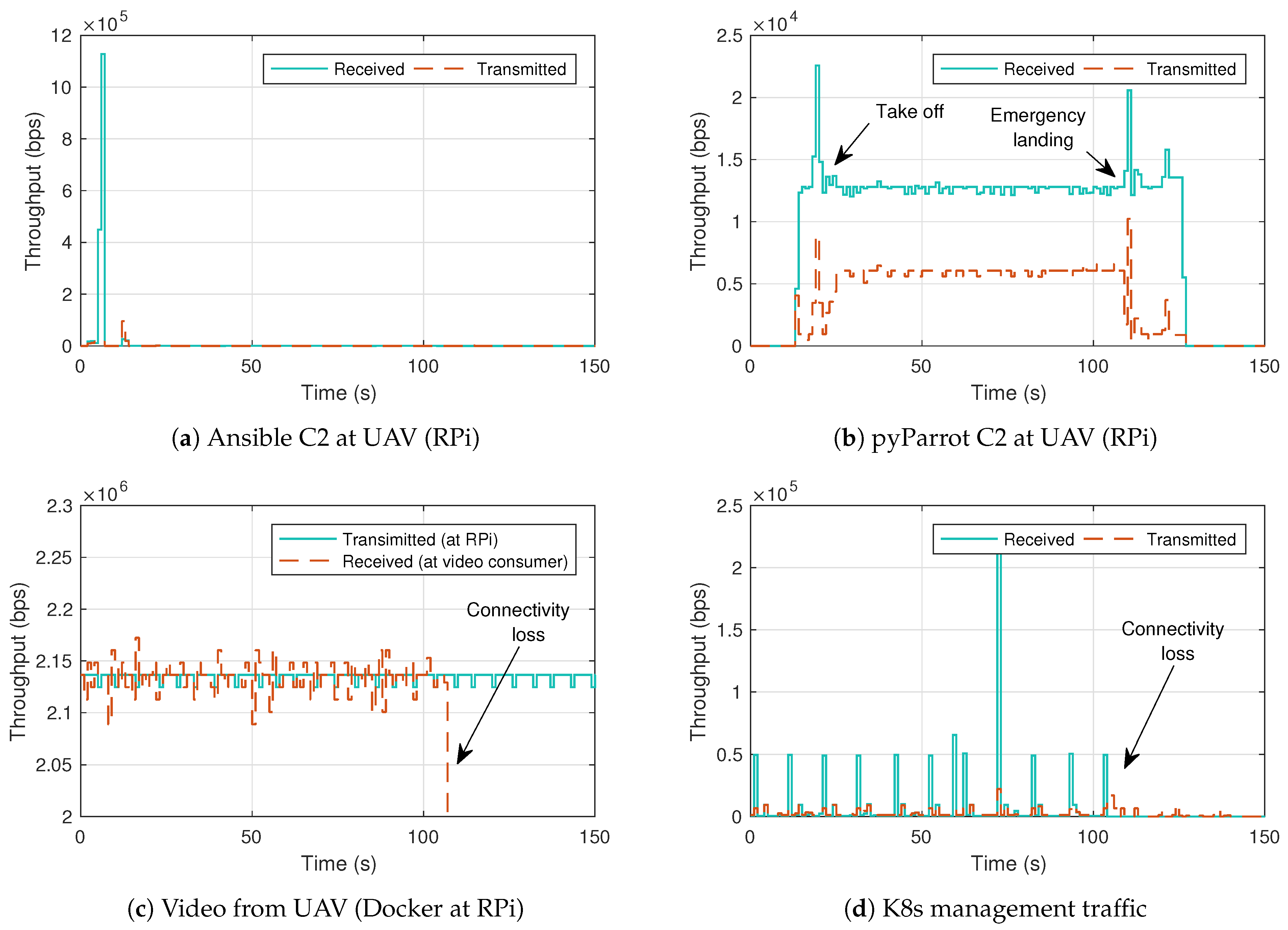
4.3. Indoor Flight Validation
4.4. Indoor Flight with Connectivity Loss
5. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| UAS | Unmanned Aircraft System |
| UAV | Unmanned Aerial Vehicle |
| FAA | Multidisciplinary Digital Publishing Institute |
| UTM | Directory of open access journals |
| ATM | ATM |
| RLoS | Radio Line-of-Sight |
| BRLoS | Beyond Radio Line-of-sight |
| C2 | Command and control |
| 5G | Fifth-generation mobile technologies |
| SA | Stand Alone |
| 3GPP | The 3rd Generation Partnership Project |
| KPI | Key Performance Indicator |
| SESAR | Single European Sky ATM Research |
| FANET | Flying Ad-hoc Network |
| D2D | Device to Device |
| MANET | Mobile Ad-hoc Network |
| NFV | Network Function Virtualization |
| SUAV | Small Unmanned Aerial Vehicles |
| FIM | Fog Infrastructure Manager |
| DDS | Data Distribution Service |
| OS | Operating System |
| ISP | Internet Service Provider |
| VPN | Virtual Private Network |
| RTV | Real Time Video |
References
- Xiao, X.; Wang, W.; Chen, T.; Cao, Y.; Jiang, T.; Zhang, Q. Sensor-Augmented Neural Adaptive Bitrate Video Streaming on UAVs. IEEE Trans. Multimed. 2020, 22, 1567–1576. [Google Scholar] [CrossRef]
- Unmanned Aircraft System Traffic Management (UTM); 2020. Available online: https://www.faa.gov/uas/research_development/traffic_management/ (accessed on 27 April 2021).
- What Is Unmanned Aircraft Systems Traffic Management? 2020. Available online: https://www.nasa.gov/ames/utm (accessed on 27 April 2021).
- Huttunen, M. The u-space concept. Repr. Air Space Law 2019, 44, 69–89. [Google Scholar]
- Lappas, V.; Zoumponos, G.; Kostopoulos, V.; Shin, H.; Tsourdos, A.; Tantarini, M.; Shmoko, D.; Munoz, J.; Amoratis, N.; Maragkakis, A.; et al. EuroDRONE, A European UTM Testbed for U-Space. In Proceedings of the 2020 International Conference on Unmanned Aircraft Systems (ICUAS), Athens, Greece, 1–4 September 2020; pp. 1766–1774. [Google Scholar]
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.H.; Debbah, M. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems. IEEE Commun. Surv. Tutor. 2019, 21, 2334–2360. [Google Scholar] [CrossRef]
- Mishra, D.; Natalizio, E. A survey on cellular-connected UAVs: Design challenges, enabling 5G/B5G innovations, and experimental advancements. Comput. Netw. 2020, 182, 107451. [Google Scholar] [CrossRef]
- Fuller, D. AT&T Detail Network Testing Of Drones In Football Stadiums; 2016; Available online: https://www.androidheadlines.com/2016/09/att-detail-network-testing-of-drones-in-football-stadiums.html (accessed on 27 April 2021).
- Bor-Yaliniz, I.; Yanikomeroglu, H. The new frontier in RAN heterogeneity: Multi-tier drone-cells. IEEE Commun. Mag. 2016, 54, 48–55. [Google Scholar] [CrossRef]
- Nogales, B.; Silva, M.; Vidal, I.; Luís, M.; Valera, F.; Sargento, S.; Azcorra, A. Using Aerial and Vehicular NFV Infrastructures to Agilely Create Vertical Services. Sensors 2021, 21, 1342. [Google Scholar] [CrossRef] [PubMed]
- Lyu, J.; Zeng, Y.; Zhang, R. UAV-aided offloading for cellular hotspot. IEEE Trans. Wirel. Commun. 2018, 17, 3988–4001. [Google Scholar] [CrossRef]
- Baldini, G.; Karanasios, S.; Allen, D.; Vergari, F. Survey of wireless communication technologies for public safety. IEEE Commun. Surv. Tutor. 2013, 16, 619–641. [Google Scholar] [CrossRef]
- Merwaday, A.; Guvenc, I. UAV assisted heterogeneous networks for public safety communications. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), New Orleans, LA, USA, 9–12 March 2015; pp. 329–334. [Google Scholar]
- Albanese, A.; Sciancalepore, V.; Costa-Pérez, X. SARDO: An automated search-and-rescue drone-based solution for victims localization. arXiv 2020, arXiv:2003.05819. [Google Scholar]
- Muruganathan, S.D.; Lin, X.; Maattanen, H.L.; Sedin, J.; Zou, Z.; Hapsari, W.A.; Yasukawa, S. An overview of 3GPP release-15 study on enhanced LTE support for connected drones. arXiv 2018, arXiv:1805.00826. [Google Scholar]
- Ullah, H.; Nair, N.G.; Moore, A.; Nugent, C.; Muschamp, P.; Cuevas, M. 5G communication: An overview of vehicle-to-everything, drones, and healthcare use-cases. IEEE Access 2019, 7, 37251–37268. [Google Scholar] [CrossRef]
- Mozaffari, M.; Kasgari, A.T.Z.; Saad, W.; Bennis, M.; Debbah, M. Beyond 5G with UAVs: Foundations of a 3D wireless cellular network. IEEE Trans. Wirel. Commun. 2018, 18, 357–372. [Google Scholar] [CrossRef]
- Kovacs, I.; Amorim, R.; Nguyen, H.C.; Wigard, J.; Mogensen, P. Interference analysis for UAV connectivity over LTE using aerial radio measurements. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–6. [Google Scholar]
- Mukherjee, A.; Keshary, V.; Pandya, K.; Dey, N.; Satapathy, S.C. Flying ad hoc networks: A comprehensive survey. Inf. Decis. Sci. 2018, 701, 569–580. [Google Scholar]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE Commun. Surv. Tutor. 2015, 18, 1123–1152. [Google Scholar] [CrossRef]
- Sanchez-Aguero, V.; Valera, F.; Nogales, B.; Gonzalez, L.F.; Vidal, I. VENUE: Virtualized environment for multi-UAV network emulation. IEEE Access 2019, 7, 154659–154671. [Google Scholar] [CrossRef]
- Leonov, A.V. Application of bee colony algorithm for FANET routing. In Proceedings of the 2016 17th International Conference of Young Specialists on Micro/Nanotechnologies and Electron Devices (EDM), Erlagol, Russia, 30 June–4 July 2016; pp. 124–132. [Google Scholar]
- Bujari, A.; Palazzi, C.E.; Ronzani, D. A comparison of stateless position-based packet routing algorithms for FANETs. IEEE Trans. Mob. Comput. 2018, 17, 2468–2482. [Google Scholar] [CrossRef]
- Quaritsch, M.; Stojanovski, E.; Bettstetter, C.; Friedrich, G.; Hellwagner, H.; Rinner, B.; Hofbaur, M.; Shah, M. Collaborative microdrones: Applications and research challenges. In Proceedings of the 2nd International Conference on Autonomic Computing and Communication Systems, Turin, Italy, 23–25 September 2008; pp. 1–7. [Google Scholar]
- Branco, K.R.L.J.C.; Pelizzoni, J.M.; Neris, L.O.; Trindade, O.; Osório, F.S.; Wolf, D.F. Tiriba—A new approach of UAV based on model driven development and multiprocessors. In Proceedings of the 2011 IEEE International Conference on Robotics and Automation, Shanghai, China, 9–13 May 2011; pp. 1–4. [Google Scholar] [CrossRef]
- Rametta, C.; Schembra, G. Designing a Softwarized Network Deployed on a Fleet of Drones for Rural Zone Monitoring. Future Internet 2017, 9, 8. [Google Scholar] [CrossRef]
- Sara, M.; Jawhar, I.; Nader, M. A Softwarization Architecture for UAVs and WSNs as Part of the Cloud Environment. In Proceedings of the 2016 IEEE International Conference on Cloud Engineering Workshop (IC2EW), Berlin, Germany, 4–8 April 2016; pp. 13–18. [Google Scholar] [CrossRef]
- Lu, K.; Xie, J.; Wan, Y.; Fu, S. Toward UAV-Based Airborne Computing. IEEE Wirel. Commun. 2019, 26, 172–179. [Google Scholar] [CrossRef]
- Nogales, B.; Vidal, I.; Sanchez-Aguero, V.; Valera, F.; Gonzalez, L.F.; Azcorra, A. Automated deployment of an Internet protocol telephony service on unmanned aerial vehicles using network functions virtualization. JoVE 2019, e60425. [Google Scholar] [CrossRef]
- Gonzalez, L.F.; Vidal, I.; Valera, F.; Nogales, B.; Sanchez-Aguero, V.; Lopez, D.R. Transport-Layer Limitations for NFV Orchestration in Resource-Constrained Aerial Networks. Sensors 2019, 19, 5220. [Google Scholar] [CrossRef] [PubMed]
- Kämäräinen, T.; Shan, Y.; Siekkinen, M.; Ylä-Jääski, A. Virtual machines vs. containers in cloud gaming systems. In Proceedings of the 2015 International Workshop on Network and Systems Support for Games (NetGames), Zagreb, Croatia, 3–4 December 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Dua, R.; Raja, A.R.; Kakadia, D. Virtualization vs. Containerization to Support PaaS. In Proceedings of the 2014 IEEE International Conference on Cloud Engineering, Zagreb, Croatia, 3–4 December 2014; pp. 610–614. [Google Scholar] [CrossRef]
- Burns, B.; Beda, J.; Hightower, K. Kubernetes; Dpunkt: Heidelberg, Germany, 2018. [Google Scholar]
- Hong, C.; Shi, D. A Control System Architecture with Cloud Platform for Multi-UAV Surveillance. In Proceedings of the 2018 IEEE SmartWorld, Ubiquitous Intelligence Computing, Advanced Trusted Computing, Scalable Computing Communications, Cloud Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), Guangzhou, China, 8–12 October 2018; pp. 1095–1097. [Google Scholar] [CrossRef]
- Behnke, D.; Müller, M.; Bök, P.B.; Schneider, S.; Peuster, M.; Karl, H.; Rocha, A.; Mesquita, M.; Bonnet, J. NFV-driven intrusion detection for smart manufacturing. In Proceedings of the 2019 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Dallas, TX, USA, 12–14 November 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Atutxa, A.; Astorga, J.; Huarte, M.; Jacob, E.; Unzilla, J. Enhancing Rescue Operations With Virtualized Mobile Multimedia Services in Scarce Resource Devices. IEEE Access 2020, 8, 216029–216042. [Google Scholar] [CrossRef]
- Hao, Y. A scalable cloud for Internet of Things in smart cities. J. Comput. 2015, 26, 1–13. [Google Scholar]
- Pardo-Castellote, G. Omg data-distribution service: Architectural overview. In Proceedings of the 23rd International Conference on Distributed Computing Systems Workshops, Providence, RI, USA, 19–22 May 2003; pp. 200–206. [Google Scholar]
- Ribeiro, J.P.; Fontes, H.; Lopes, M.; Silva, H.; Campos, R.; Almeida, J.M.; Silva, E. UAV cooperative perception based on DDS communications network. In Proceedings of the OCEANS 2017-Anchorage, Anchorage, AK, USA, 18–21 September 2017; pp. 1–8. [Google Scholar]
- Park, H.S.; Jang, J.H.; Kim, J.D.; Jung, H.I.; Lee, S.H. Bandwidth-aware DDS communication in WLAN. In Proceedings of the 2012 International Conference on Systems and Informatics (ICSAI2012), Yantai, China, 19–20 May 2012; pp. 1542–1546. [Google Scholar]
- Rigazzi, G.; Kainulainen, J.P.; Turyagyenda, C.; Mourad, A.; Ahn, J. An edge and fog computing platform for effective deployment of 360 video applications. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference Workshop (WCNCW), Marrakech, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar]
- Nogales, B.; Sanchez-Aguero, V.; Vidal, I.; Valera, F. Adaptable and Automated Small UAV Deployments via Virtualization. Sensors 2018, 18, 4116. [Google Scholar] [CrossRef] [PubMed]
- Sanchez-Aguero, V.; Vidal, I.; Valera, F.; Nogales, B.; Mendes, L.L.; Damascena Dias, W.; Carvalho Ferreira, A. Deploying an NFV-Based Experimentation Scenario for 5G Solutions in Underserved Areas. Sensors 2021, 21, 1897. [Google Scholar] [CrossRef] [PubMed]
- Maltese, D.; Farjon, J. Detect and avoid function for UAVs: Presentation of an EO/IR sensor solution. In Infrared Technology and Applications XLVI; International Society for Optics and Photonics: London, UK, 2020; Volume 11407, p. 1140713. [Google Scholar]
- Krishnan, P.; Manimala, K. Implementation of optimized dynamic trajectory modification algorithm to avoid obstacles for secure navigation of UAV. Appl. Soft Comput. 2020, 90, 106168. [Google Scholar] [CrossRef]
- Allignol, C.; Barnier, N.; Durand, N.; Blond, E. Detect & avoid, UAV integration in the lower airspace traffic. In Proceedings of the 7th International Conference on Research in Air Transportation (ICRAT), Philadelphia, PA, USA, 20–24 June 2016. [Google Scholar]
- Atoev, S.; Kwon, K.R.; Lee, S.H.; Moon, K.S. Data analysis of the MAVLink communication protocol. In Proceedings of the 2017 International Conference on Information Science and Communications Technologies (ICISCT), Tashkent, Uzbekistan, 2–4 November 2017; pp. 1–3. [Google Scholar]
- Koubâa, A. Robot Operating System (ROS); Springer: Berlin/Heidelberg, Germany, 2017; Volume 1. [Google Scholar]
- Tipantuña, C.; Hesselbach, X.; Sánchez-Aguero, V.; Valera, F.; Vidal, I.; Nogales, B. An NFV-based energy scheduling algorithm for a 5G enabled fleet of programmable unmanned aerial vehicles. Wirel. Commun. Mob. Comput. 2019, 2019, 4734821. [Google Scholar] [CrossRef]
- V0.3.1, G.T. Technical Specification Group Radio Access Network: Study on Enhanced LTE Support for Aerial Vehicles (Release 15). 2018. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3231 (accessed on 27 April 2021).
- 5TONIC. The 5TONIC Laboratory. 2020. Available online: https://www.5tonic.org (accessed on 27 April 2021).
- Ericsson 5G Radio Access. Available online: https://www.ericsson.com/en/ran (accessed on 27 April 2021).
- Ericsson’s Dual-Mode 5G Core. Available online: https://www.ericsson.com/en/core-network/5g-core (accessed on 27 April 2021).
- Hu, X.; Pang, B.; Dai, F.; Low, K.H. Risk Assessment Model for UAV Cost-Effective Path Planning in Urban Environments. IEEE Access 2020, 8, 150162–150173. [Google Scholar] [CrossRef]
- Geramifard, A.; Redding, J.; Roy, N.; How, J.P. UAV cooperative control with stochastic risk models. In Proceedings of the 2011 American Control Conference, San Francisco, CA, USA, 29 June–1 July 2011; pp. 3393–3398. [Google Scholar]
- IBM: Internet Connection and Recommended Encoding Settings. Available online: https://support.video.ibm.com/hc/en-us/articles/207852117-Internet-connection-and-recommended-encoding-settings (accessed on 27 April 2021).

Short Biography of Authors
 | Victor Sanchez-Aguero completed a BSc Audiovisual Systems Engineering in 2017, at University Carlos III of Madrid (UC3M). During this period, he worked as an internship student at the said university collaborating with researchers from the Telematics Engineering department. He received their MSc degree in Telematics Engineering at UC3M in 2018 and is now a PhD student at IMDEA Networks Institute. He has published different papers in their research field in different national and international conferences and journals. He has also participated in international and national research projects, including the H2020 5GRANGE and 5GCity. |
 | Luis F. Gonzalez completed the Telematics Engineering Bachelor degree in 2018 and the Telematics Engineering Master degree in 2019 from University Carlos III of Madrid. He is currently a Ph.D. candidate in Telematics Engineering at UC3M. He has been involved in the European research projects Labyrinth and 5GinFIRE, as well as the national research project 5GCity. His research interests include Network Functions Virtualization (NFV), 5G networking, and Unmanned aerial vehicles (UAVs), publishing in various international conferences and journals. |
 | Francisco Valera received the Telecommunication Engineering degree in 1998, from the Technical University of Madrid (UPM) and the Ph.D. in Telecommunications in 2002, from UC3M, where he is currently a tenured associate professor and Deputy Director of the Telematic Engineering Department. He has been involved in several national and international research projects and contracts related with experimental facilities, unmanned aerial vehicles, protocol design, interdomain routing, protocol engineering, next-generation networks, and multimedia systems, serving there as PI, work package leader, and also as coordinator. Some of the recent research projects in which he has participated are IST 5GRANGE, IST Trilogy, IST LEONE, and DRONE or IST MUSE. Dr Valera has published over 80 papers in the field of advanced communications in magazines and conferences. He has also participated in the scientific committee, organization, and technical review in different national and international conferences. |
 | Ivan Vidal received the Ph.D. in Telematics Engineering in 2008 from the University Carlos III of Madrid, where he is currently working as visiting professor. His research interests include Unmanned aerial vehicles (UAVs), 5G networks, and Multimedia Networking. He has been involved in several international and national research projects, including the H2020 5GinFIRE and 5GCity, and has published more than 50 scientific papers in several conferences and international journals. |
 | Rafael A. López da Silva received their Telecommunication Engineering degree from the Polytechnic University of Valencia (UPV) in 1997. He joined Telefonica I+D in 1997. Over the years, he has worked in different research and transformation projects for the Telefonica group in the IP Metro and Core network segments. His current focus is on preparing Telefonica Transport networks for being 5G capable and on their evolution to make use of disaggregated network elements. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sanchez-Aguero, V.; Gonzalez, L.F.; Valera, F.; Vidal, I.; López da Silva, R.A. Cellular and Virtualization Technologies for UAVs: An Experimental Perspective. Sensors 2021, 21, 3093. https://doi.org/10.3390/s21093093
Sanchez-Aguero V, Gonzalez LF, Valera F, Vidal I, López da Silva RA. Cellular and Virtualization Technologies for UAVs: An Experimental Perspective. Sensors. 2021; 21(9):3093. https://doi.org/10.3390/s21093093
Chicago/Turabian StyleSanchez-Aguero, Victor, Luis F. Gonzalez, Francisco Valera, Ivan Vidal, and Rafael A. López da Silva. 2021. "Cellular and Virtualization Technologies for UAVs: An Experimental Perspective" Sensors 21, no. 9: 3093. https://doi.org/10.3390/s21093093
APA StyleSanchez-Aguero, V., Gonzalez, L. F., Valera, F., Vidal, I., & López da Silva, R. A. (2021). Cellular and Virtualization Technologies for UAVs: An Experimental Perspective. Sensors, 21(9), 3093. https://doi.org/10.3390/s21093093







